Don't wanna be here? Send us removal request.
Text
Scoping for PCI DSS Compliance
The basic and the foremost activity is scoping in PCI DSS assessment. Scoping activity might look bit easy in general but it can be a real challenge for the assessor while performing it (which particular segment process, transmit or store the cardholder data, which does not).

How important is scoping in PCI DSS assessment, can be determined through PCI guideline “The first step of a PCI DSS assessment is to accurately determine the scope of the review. At least annually and prior to the annual assessment, the assessed entity should confirm the accuracy of their PCI DSS scope by identifying all locations and flows of cardholder data and ensuring they are included in the PCI DSS scope”.
It is a core responsibility of an assessor to get the scoping determined accurately because a single flaw in scoping activity might lead to the failure of the whole PCI DSS assessment.
So here are some common method used by the assessors to determine the scope of the project.
Network diagram
Data flow diagram
Card finder tool report
Assessor’s experience
Network Diagram: For any project regardless of PCI DSS, Network diagram play very important role. Network diagram gives the assessor full-fledged idea about the environment of the client. Through network diagram it gets cleared which all segment is created and how these segments are communicating with each other, how internal zones are interacting with internet. With the help of network diagram an assessor does the segmentation as which segment is to be considered In-scope or Out-off scope. PCI DSS guideline defines network segmentation as “Network segmentation can be achieved through a number of physical or logical means, such as properly configured internal network firewalls, routers with strong access control lists, or other technologies that restrict access to a particular segment of a network. If network segmentation is in place and being used to reduce the scope of the PCI DSS assessment, the assessor must verify that the segmentation is adequate to reduce the scope of the assessment. At a high level, adequate network segmentation isolates systems that store, process, or transmit cardholder data from those that do not. However, the adequacy of a specific implementation of network segmentation is highly variable and dependent upon a number of factors, such as a given network’s configuration, the technologies deployed, and other controls that may be implemented”. Source:
Data Flow Diagram: The second most common method used by an assessor is data flow diagram. PCI DSS guidelinehas clearly mentioned the use of data flow diagram as “Documenting cardholder data flows via a dataflow diagram helps fully understand all cardholder data flows and ensures that any network segmentation is effective at isolating the cardholder data environment”. Data flow diagram let the assessor determine how the data is being transmitted in the system, whether the PCI scope system are able to communicate with the NON-PCI scope system or not (remind you there should not be any communication between PCI scoped system and NON-PCI scoped system), even assessor is able to determine how the inputs and outputs relate to each other, what encryption mechanism is being used to transmit the cardholder data.
Card Finder Tool Report: Now a days, card finder tool reports are being widely used by the assessor to determine and cross-validating the defined scoped. These reports have become very useful as they let the assessor know which out-off scoped systems are storing, processing or transmitting the cardholder data. Sometimes even the client does not know which system is in-scope or out-off scope, in those type of scenarios card finder tool report becomes handy. Most of the assessor analyze these reports before they go to client place so that when they are on-site they are aware of the in-scoped system and focus on them and even future surprises related to in-scope and out-off scope can be reduced.
Assessor’s Experience: In PCI DSS assessment assessor’s experience matters a lot. An assessor will combine all the above given methods output as an input for providing the final In-scoped and Out-off scoped system. An assessor will validate all the information given by the client in network diagram, data flow diagram and card finder tool report at the time of On-site assessment and based on the comparison will scope-in or scope-out the system.
As per PCI DSS guideline “Once all locations of cardholder data are identified and documented, the entity uses the results to verify that PCI DSS scope is appropriate (for example, the results may be a diagram or an inventory of cardholder data locations)”. “For each PCI DSS assessment, the assessor is required to validate that the scope of the assessment is accurately defined and documented”. As scoping is an initial activity it is valued the most. Hence I would like to conclude it with “Project scope definition is the most important factor when it comes to project requirements. It is vital for service providers to define the scope of the project in order to successfully enter into an agreement with the client”.
Source: https://www.sisainfosec.com/americas/blogs/scoping-for-pci-dss-compliance/
0 notes
Text
EMV and PCI DSS – Complementing or competing standards?

There has been an increased confusion among the clients/ merchants about the compliance related activities related to Payment Card Industry Data Security Standards (PCI DSS) and EMVCo LLC (Europay, MasterCard, and Visa) (EMV) specifications.
There is not enough clarity on what to follow regarding the adoption of either standard. While many merchants (esp. the retail ones) are advocating the necessity to move towards EMV to reduce card fraud to a great extent, the others are still wondering if this move is justified as they are already struggling to keep up with PCI DSS.
Recently, the counterfeit card liability shift plans announced by many payment brands as per their individual milestones have once again raised the heated debate regarding the widespread adoption of these two popular standards. Let’s take a closer look at them to understand clearly what does it takes to truly secure your client’s valuable cardholder data from attackers.
EMV and PCI DSS – Same or different?
Both the standards advocate the protection of cardholder data (CHD) to minimize the rampant card fraud and consumer cardholder data breaches. But it is here that the standards take a different approach by focusing on various elements of CHD transactions.
Broadly speaking, PCI DSS tries to address the larger picture by ensuring the card data is not stolen and is reasonably secure whenever it is stored, transmitted or processed. On the other hand, EMV’s objective is typically to render the data of chip-based payment cards useless, if somehow the attackers manage to get hold of it. Thus, EMV acts as more of an anti-fraud mechanism which makes the card skimming and card duplication fraud practices quite difficult, since the chip present in the card produces a unique encrypted output every single time when it is used.
PCI DSS has specific dedicated standards such as PA-DSS and PTS standards that are useful to form important security layers to reduce overall card fraud and risks. The risks arising from malicious payment applications, compromised POS terminals, technical fallback process, card skimming, etc. are covered quite effectively through the use of Payment Application Data Security Standard (PA DSS) approved applications and PTS compliant devices.
Hence, we see that though EMV and PCI DSS specifications are different, they complement each other very well to protect the cardholder data and prevent its exposure to effectively control fraudulent usage by criminals.
What should I go for – PCI DSS or EMV?
Since there is no “static” payment data present in magnetic stripe transaction when EMV is used, the card transaction details are effectively useless for an attacker; since in EMV, the data is “dynamic” due to unique encrypted output produced every single time for each card transaction.
A replay attack by the attacker is quite easily rendered ineffective in these cases. This feature makes adopting EMV an attractive option for merchants (esp. in the retail sector) and not to go for PCI DSS. However, due to exponential growth witnessed in online shopping and e-commerce, customers are frequently opting for card-not-present transactions.
Hence, the card details acquired by an attacker on EMV card can be used to make card-not-present transactions. However, strong authentication measures such as one-time password (OTP) other measures deployed by payment brands such as “3D Secure Code” of MasterCard and “Verified by Visa” of Visa can mitigate this to a great extent. Other threats such as technical fallback, PAN key entry fallback, Lack of maintaining unique chip CVV/CVC by EMV, Deep dip reading, clear exposure of PAN and expiry date still lurk in the dark that may bypass EMV anti-fraud protections.
However, it is important to note that certain card holder details such as PAN, expiry date need to be transmitted in clear for EMV environment to complete a transaction. Current processing environment typically processes both EMV and non-EMV transactions. Hence, security-wise there exists a threat that these non-EMV transactions such as magnetic stripe data, PAN key entry do not carry the same anti-fraud capabilities of EMV environment hence would require additional protection. This is why EMV environment must be complemented by PCI DSS so that the entire cycle of card payment is covered to guarantee the best security protection for card payments.
Thus, PCI DSS requirements are still important for card security as they address not only the technological aspects of security but also the processes and people part of it. It tries to prevent the theft of card data in the first place.
Further, a large part of the market is still yet to fully adopt EMV migration and right now only a few countries have fully adopted it. It will take some time to reach larger market such as US and Asia. However, EMV and PCI DSS complement each other very well as regards to card security and are helpful to maximize the security assurance value to the customer.
I’m concerned about the counterfeit card liability shift plans by my payment brand – What to do?
Payment brands such as Visa have rolled out October 1, 2015, as the milestone date for the financial liability shift for all the parties that may / may not have invested in EMV compliant POS terminals; barring those used in automated fuel dispensers.
This implies that post this date, for all the frauds reported in cases of POS related card-present transactions, the party (issuer bank / merchant / payment processor) which is least prepared for accepting EMV enabled cards, has to reimburse the victim (customer) for damages occurred.
Technically, this means that no fines / penalties will be levied for not implementing EMV enabled cards since EMV is not government mandated or regulated such as PCI SSC. It is your business decision to implement EMV or not.
If I upgrade to EMV enabled payment devices, can I still use non-EMV cards?
Yes, the “complete” phasing out of non-EMV cards which rely on the magnetic stripe, will still take a long time. To help in this regard, newer cards issued carry EMV chip as well as magnetic stripe for broader application across non-EMV POS terminals. This means, post the milestone date of October 1, 2015, businesses can still accept magnetic stripe cards.
Okay, so if I have adopted EMV, can I skip PCI DSS implementation?
Implementing EMV environment cannot fulfill PCI DSS requirements. It does not protect the confidentiality of cardholder and sensitive authentication data. Further, as of today, merchants can still process both EMV and non-EMV transactions, which means that it is essential to carefully handle the threat vectors aimed at compromising the CHD and SAD(sensitive authentication data) of Card data. There are many other things to look out as well. We cannot leave the security of our business environments such as people, process, network security, application security and infrastructure security go unnoticed. They need to be secured as well. It is quite possible for an attacker to compromise these areas first, and then gain access to the Cardholder data; a fact that is time and again witnessed in numerous data breaches.
Protection provided by PCI DSS is two-fold
Integrity protection of system components against physical and logical attacks wherever they come in contact with the cardholder and sensitive authentication data (SAD). Confidentiality protection of CHD when it is stored / processed in given environment or gets transmitted over the open public network.
Hence, PCI DSS protection over CHD and SAD covers their presence within the payment eco-system itself, thus effectively making their availability quite difficult for an attacker to obtain them for fraud purposes. This is the very factor that is instrumental in protecting your business against breaches, fines, brand reputation damage, etc. since it advocates in covering the payment system in its entirety.
Dedicated separate standards such as PA DSS and PTS are available from PCI which effectively addresses the risks. Controls available via these standards plug many of the risks present in EMV transactions too.
Conclusion:
While the adoption of EMV definitely brings good news to card security with regards to fighting the notorious card-present frauds happening throughout the globe, it would be naive not to comply with PCI DSS standard since it covers the entire cycle of cardholder data which is stored, transmitted or processed in your business environment. Adopting both EMV and PCI DSS will go a long way to provide peace of mind to your customers and deliver maximum security value to them.
Source: https://www.sisainfosec.com/americas/blogs/emv-and-pci-dss-complementing-or-competing-standards/
0 notes
Text
Getting Ready for Cyber Security
The use of Internet has affected almost all parts of life of an individual. Internet has grown from just a tool to obtain information for a school project to stimulate social and political changes in many parts of the world. The rising growth of social media, online Governance models and Internet of Things clearly indicate that it is just a matter of time before all information is available online in some form or the other.
However, over the time it has been proven that the Internet is vulnerable, vulnerable to human errors, vulnerable to malicious individuals and vulnerable to natural disasters. Focussing on malicious individuals, who are working to improve their skills, scale and determination, it has been realized that something more comprehensive, more than installing firewall and IPS, is required to tackle the challenges posed in front of the society in the manner how the Internet and related services are used.

Cyber security has taken a prominent place in the security world. Cyber security, as per definition from ITU-T, is defined as:
[Cyber security is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyber environment and organization and user’s assets. Organization and user’s assets include connected computing devices, personnel, infrastructure, applications, services, telecommunications systems, and the totality of transmitted and/or stored information in the cyber environment.]
Given the nature of how broad the term is, different organizations may associate a slightly different meaning with the term, certain level of flexibility in term’s use is expected.
Guiding principles for Cyber Security:
When moving towards cyber security, the approach should be supported with defined set of principles that can help in management of risks right from identification to mitigation in a manner that is in tune with cost and privacy considerations. The setting of right tune is important due to tightening regulations and cost as any control put in place generating excess data would turn out be drainer in terms of resources and can lead to fines.
The recommended set of guiding principles can be:
Risk based approach: Risk assessment to identify the threats, vulnerabilities and impact to the organization and then coming together to manage the risk by effective set of controls.
Result focussed: Focus must be on the final outcome, irrespective of the means used to reach it, and progress must be measured based on achievement of the desired outcome.
Prioritization: Priority matrix must be developed to prioritize the events and assets. The management approach must be based on priority, handling high priority activities first. The increase in mobility, interoperability, population, complexity and distribution of components has given the attackers a plethora of surface to play with.
Adaptability: The approach or the controls developed as part of cyber security must be applicable to large set of assets and should be adaptable to wide array of sectors.
Privacy and regulatory compliance: The approach to cyber security must respect the privacy of individuals and should support the regulatory requirements.
Internationally influenced: The approach must be influenced with international standards so as to maintain maximum possible acceptability.
Taking a Risk based approach to Cyber Security:
In the current scenario the cyber security guidance available are mostly voluntary but the industry is moving to mandatory compliance at least for critical infrastructure, if not end-to-end. A risk based approach can help address the complexities faced during rollout of the strategy. Risk based approach starts with identifying, analysing and evaluating the risks which require attention. The approach must be holistic in nature to the maximum extent possible to enable all business units take advantage of changing landscape. Let us go through some of the critical areas which need to be made part of cyber security initiative right from the beginning:
Information Risk Management Leadership:
It is important that Board and senior managers support the information security and risk management and may wish to communicate their risk appetite and risk management policy to people associated with the organization to ensure they are aware of organization’s risk boundaries. A lack of effective risk management can lead to increased exposure to risk, missed options, poor return on investment, etc. In order to manage the risks following can be done to promote a risk aware culture:
A governance framework should be developed which consistently supports the risk management culture across the organization and is owned by the Board or senior management.
A major task would be determining the risk appetite of the organization so that the business decisions are guided within risk boundaries.
Board discussions agenda should include information risk to the organization. Risk assessment reports must be regularly reviewed and contacts with outside authorities should be maintained in order to get better insight on emerging risks.
Appropriate standards must be referred to build a life cycle approach to risk management, which can help in continual improvement, along with roll out of corporate risk management policy.
Network Security:
Internet and other untrusted networks expose corporate networks threats that aim to compromise CIA of the systems and the information. It is to be noted that protection is required against internal threats as well. Failing to secure the network properly can lead to leakage of sensitive information, malware infection, exploitation of vulnerable applications and systems, etc. Following activities can help to reduce the risk:
ll the traffic should be inspected and filtered at the network perimeter to ensure only business supporting traffic is being allowed. Firewall must be installed between untrusted network and internal network with only authorized ports and protocol allowed and default deny-all setting in place.
Direct connectivity between internal network and untrusted network should not be allowed. Network isolation must be employed to isolate critical assets and easily manage the large environment. Wireless networks must be secured and Network Address Translation must be used to protect internal IP addresses from exposure.
Secure Configuration:
Creating and enforcing secure baselines for all types of system components and applications can vastly improve the security posture of the IT systems. As a best practice all not necessary functionalities should be disabled or removed which can reduce the exposure of IT systems to variety of threats. Applications and systems which are not hardened will be vulnerable and can result in unauthorized access to systems, exploitation of insecure configuration, increase in security incidents, etc. In order to reduce the incidents due to insecure configuration following steps can be taken:
Policies related to patch management must be enforced to make sure patches are applied within established time frame. Along with patching updated inventories of hardware and software must be in place. Automated tools can be used to capture the details.
Hardening guidelines must be available for all types of systems components, router, firewall, server, workstations or any other. Unnecessary ports and services must be disabled. Change control must be in place for any changes to be effected in any system or application. User rights must be limited with respect to the ability to make changes in the components.
Regular vulnerability scans and penetration testing must be conducted and any loop holes identified must be fixed in within a defined time frame. The team must maintain awareness regarding recent threat landscape as well.
Identity and Access Management:
Organizations need to understand the privileges required by the users, and whether it is at all required, to carry out their daily tasks. The principle of granting only privileges that are required to carry out daily jobs is termed as ‘Least Privilege’. Failure to manage privileges effectively can result in misuse of privileges, increased attacker capability and privilege creep, etc. Following methods can help in reducing the number of incidents due privilege misuse:
Policies and procedures for identification and access control must be established providing guidance on password selection, complexity and life cycle along with roles and responsibilities.
Procedure must be established for review of user accounts right from creation till deletion. Also, periodic reconciliation process must be set up to identify any dormant or test accounts and should be removed.
The number of privilege accounts must be controlled in the system components. Privilege accounts should not be used for day to day activities. Normal users should be provided privileges based on the Principle of Least Privilege.
Access to audit logs must be controlled and users must be monitored during their daily activities, specifically while carrying out sensitive tasks.
Incident Management:
At some point in time all organizations have faced certain types of incidents and will continue to face new incidents. Therefore, it is worthwhile investing in an efficient incident management procedure to better manage the incidents and reduce any financial impact. Failure to implement incident management procedure can lead to major and long term disruptions and legal and regulatory non-compliance. The type of incidents will vary based on the type of business and a risk based approach will be more suitable considering the following points:
Organization should establish and maintain organization-wide incident management plan approved and supported by senior management. The plan must be mature enough to be able to manage a wide variety of incidents.
Roles and responsibilities must be clearly outlined and appropriate training must be provided to the personnel so as to handle wide variety of incidents efficiently.
The incident management plan should be tested on a regular basis and learning must be incorporated to improve the plans. Business continuity and Disaster recovery should also be included and appropriate back-ups must be maintained to counter any incident which results in loss of data.
In case of incidents it might be required to inform large number of people including clients, vendors, law enforcement, etc. Appropriate responsibilities must be documented as to who, what and how to inform the interested parties about the incident.
Root cause analysis must be performed for all incidents and learning should be used to enhance the plan for future. If required the incidents should be reported to law enforcements and user awareness should be carried out to eliminate the possibilities of re-occurrences.
Virus and Malware Prevention:
Connecting to untrusted networks exposes the systems to viruses and malware. Such infections can lead to business disruptions, information leakage and even legal sanctions. Common mediums of such infection include E-mail, uncontrolled Internet access and removable media. Following can be considered to reduce virus and malware risks:
Relevant policies and procedures addressing viruses and malware must be established and communicated within the organization. Users must be educated regarding the use of e-mail attachments and removable media on the corporate systems.
Anti-virus and Anti-malware defence must be established and all systems must be regularly scanned. All electronic data exchange must be scanned for malicious content.
Content filtering should be carried out by firewalls to prevent movement of malicious code from untrusted network to internal network. If possible, suspected content should be quarantined for further analysis.
Logging and Monitoring:
Logging and monitoring allow timely detection of attacks and can help in incorporating procedures that can help prevent future attacks. Monitoring ensures that systems are being used in conformation with established policies. It is to be documented as to what actions are to be logged and what will be the monitoring procedure. Failure to monitor the systems can lead to non-compliance as well as diminished ability to detect and react to the attacks. A consistent and documented approach needs to be put in place, which can include the following:
Appropriate policies must be put in place and should be aligned with incident management policy. It should be ensured that all network and host systems are monitored by some automated solution and should have the capability to detect attacks through the use of signatures or heuristics.
All network traffic movement, inside or outside, must be monitored for any malicious activity. Along with it should be able to identify the subject, the activity that triggered the alert and the object.
The monitoring solution should be customized to capture appropriate logs and events that fulfil the requirement of monitoring. Inappropriate collection could result in legal and regulatory breach and could turn out to be costly in terms of management.
To the extent possible it should be ensured that all logs and events are collected and stored at a central repository and enough space is available for the storage for a certain period. Above all it must be ensured that all devices are synced to central time source so that all logs and events are accurately time stamped to support investigations or legal actions.
Removable Media Controls:
Lack of removable media controls can lead information theft, malware infection and above all loss of reputation. It is better to disable any usage of removable media unless some business requires it specifically and the approval should be based on risk assessment. In order to manage the risks from removable media following can be considered:
Policies and procedures should be implemented to control the usage of removable media. The usage should be limited to users, systems and type of data that can be moved on to removable media.
All removable media should be inventoried and users should not be allowed to their own media. All removable media should be scanned before it is used for data transfer and anti-virus solution must be deployed on all hosts.
Removable media reuse and disposal procedures must be put in place to ensure that older data is not accessible. Industry accepted deletion and wiping techniques should be employed for securely deleting the data.
The removable media must be hardened as per hardening guidelines and appropriate monitoring should be in place to detect any unauthorized use. If required, encryption can be used to protect the information present in the removable media.
Home and Mobile Working:
Mobile technology has made huge strides in the daily life of individuals. More and more people are using mobile devices for work related activities. It has resulted in the extension of corporate security boundaries. It is required that organizations maintain relevant policies and procedures to control the usage of mobile devices and layout plans for management of any compromise that might occur. The risks can be like theft of mobile device, shoulder surfing in public, insecure configuration leading to loss of data, etc. Following can be implemented to reduce the risks associated with mobile devices:
If the organization allows the use mobile devices then secure baseline must be documented and implemented on all devices. Also, all users must be trained in the manner as to how to use their devices securely in public areas or any other place.
The amount of corporate data present in the mobile devices should be kept at minimum to what is required to complete the activity. Also, the connectivity to corporate network from untrusted networks, like public Wi-Fi, must be protected by use of VPN to protect the data transmitted.
Users must be instructed to report any or all incidents related to mobile devices at the earliest and corporate incident management plan must be extended to mobile device incidents.
User Education and Awareness:
It is evident that large numbers of incidents are caused by unintentional acts of users. It is important that the users are aware of their responsibilities towards the usage of corporate resources. Lack of awareness can result in unacceptable usage of company resources, use of removable media and personal devices can introduce malware, users not reporting incidents on time or not at all, etc. To reduce the risks following steps can be taken:
An acceptable usage policy shall be present and must be communicated to all the users.
All new joiners should go through security training at the time of joining and annual training sessions must be held for all the users, informing them of the new trends in the security field.
Organization should promote incident reporting culture along with the security culture, users must be confident while reporting the incident without any fear. In – addition, disciplinary process must be in place for users misusing the resources.
Source: https://www.sisainfosec.com/americas/blogs/getting-ready-for-cyber-security/
0 notes
Text
PCI Standards for India’s Emerging Digital Payment Modes

The “Digital India” initiative launched in 2015 and “Demonetization campaign” in November 2016 by the Government of India has provided the major boost to the country’s digital ecosystem. Along with initiatives such as “DigiShala”, the government has aimed at building an ecosystem for entailing ‘cashless economy’ in the country. Other initiatives such as the National Optical Fibre Network (NFON) and Introduction of Unified Payments Interface (UPI), Bharat Interface for Money (BHIM – internet based mobile application) can help support in faster adoption and transition to digital payments. In fact, India’s digital payment industry, currently worth around USD 200 Billion, is expected to grow five-fold to reach USD 1 Trillion by 2023, as per a report by Swiss financial services holding company, Credit Suisse. The global digital payment market is expected to reach USD 21 Trillion by 2020. With the increase in the digital payments ratio, cybersecurity is one of the most critical challenges faced by stakeholders of the digital payment ecosystem. This has ultimately opened up more opportunities for cyber pickpockets to try and steal card details, PINs, mobile wallets and siphon off money. Cybersecurity is one of the most critical challenges faced by stakeholders of the digital payment ecosystem. With more and more users preferring digital payments, the chances of being exposed to cybersecurity risks such as online fraud, information theft, and malware attacks are also increasing.
Emerging Mode of Digital Payments in India
One of the biggest changes that the payments industry has seen recently is in terms of the various modes of payments. Hand held devices have outgrown all other channels due to ease of making transactions and the accessibility that they provide in terms of convenience. The government and the banks have undertaken multiple initiatives to promote the usage of digital payments in urban locations and to accelerate penetration into the hinterlands of the country and develop trust the among first-time users. The push from the government also spurred interest from fintech companies who had the technology but were missing the momentum. With the collective efforts of the RBI, NPCI and the government, a robust backbone for digital payments in India has been created by systems such as Unified Payments Interface (UPI), Bharat Interface for Money (BHIM), BHIM Aadhaar, Bharat Bill Payment System (BBPS), etc. The following are the major digital payment modes that are in trend for today in India:
1. Card Payments – The major payment brands like Mastercard, VISA, AMEX, JCB, Discover, etc. 2. UPI (United Payment Interface) applications like BHIM. 3. Wallet applications like Paytm, Freecharge, Phonepe. 4. AEPS (Aadhar Enabled Payment System). 5. Mobile Banking.
Cybersecurity for Digital Payments
To ensure that sensitive data is not compromised in any way while people use different digital payment modes, robust security across devices is absolutely necessary.
With context to the card data, we have PCI DSS (Payment Card Industry Data Security Standards) which are a set of stringent guidelines to ensure a secure environment for storing, processing or transmitting card holder data.
Wallet applications adhere to PPI (Prepaid Payment- Instruments) guidelines provided by RBI (Reserve bank of India) in the article RBI/DPSS/2017-18/58, Master Direction DPSS.CO.PD.No.1164/02.14.006/2017-18.
UPI enabled payment services follow the guidelines formulated by NPCI in the circular NPCI /UPI/OC No. 15B/2017-18.
Below is a screenshot of the Payment page showcasing the different payment options:

If we take a close view to the above screenshot, we will realize that there are different sets of guidelines being followed for the different payment modes. Although the ultimate motive to ensure payment data remains secure is the same. In this scenario, single organization is undergoing multiple audits for the same set of servers and set-up. This result in Audit fatigue that makes organizations lose focus on security and just check the box. Although RBI, as the regulator has taken great initiatives in securing digital payments and issued the set of guidelines on some payment modes like UPI and PPI, the challenge underlying lies if they are a set of guidelines that can be used as auditable controls For an instance, as per RBI guidelines “Testing of vulnerabilities” is required at “reasonable” amount of time. Here the word “reasonable” is generic and is differently interpreted by different set of people. On the other hand, we have same requirement for performing vulnerability assessment explained in PCI DSS as:
• One has to perform Internal and External vulnerability scan on all critical systems on quarterly basis • Internal and External vulnerability scans are to be conducted if there are any major changes in the network. • Scans are to be repeated until all the vulnerabilities are mitigated.
Tailoring of PCI DSS standards to other Payment Forms
The PCI DSS standard contains 12 detailed requirements across six security areas. But among all the requirements, only requirement 3 and 4 talks about card data, rest of the standard focuses on protection of the payment environment where card data is dealt with. It ranges from secure firewall configuration to, log monitoring and anti–virus to hardening of systems. Requirements 3 and 4 are designed to secure Identification and authentication data for card payments during storage and transmission, while the same set of controls can be used to secure the Identification and authentication data for other modes of digital payments.

The organizations that are already PCI compliant can extend the scope of assessment to all other payment modes and not limit the PCI assessment scope to only card payments. This idea justifies being a solution for organizations that are suffering from audit fatigue. In terms of business, its more economic as it saves time, money, resources and valuable efforts put in multiple audits for a single organization. From a technical aspect, it ensures better payment data security because you have got one set of prescriptive controls that leads to standardization. SISA that has pioneered in payment security over the last decade has been actively engaging with the community to recognize the requirement and demand for adoption of a single framework of PCI DSS standards across all digital payment channels. The need of a uniform security standard has been experienced from a series of its numerous client encounters that SISA has come across. And with this SISA anticipates lesser ambiguity and better security with all the emerging digital payment forms in India.
Resources followed for the article: https://economictimes.indiatimes.com/tech/internet/as-india-braces-for-digital-payments-future-how-secure-are-banks-from-cyberattacks/articleshow/56073576.cms
https://www.dsci.in/content/securing-india%E2%80%99s-digital-payment-frontiers
About the Author: Dharshan Shanthamurthy is the Founder & CEO of SISA (www.sisainfosec.com), a global cyber security company that specializes in payment data security. Dharshan was the first PCI QSA recognized by the PCI Council in India. He is a leading payment forensic investigator for PCI Council and has led many payment forensic investigations of strategic importance. Dharshan was assisted by Ms. Ankita Patel from SISA for authoring this document.
Source: https://www.sisainfosec.com/blogs/pci-standards-for-india-emerging-digital-payment-modes/
0 notes
Text
8 Immediate Steps post resurfacing of Fake Response Malware
Recent media articles pertaining to Malware Attack on the payment switch application of one oldest co-operative and losses been reported is disturbing for us at SISA.

SISA on 20th December 2017 had issued a global advisory warning banks that cyber criminals were identified to be injecting malicious script to payment switch servers for generating fake response messages to the request received from payment brands. https://timesofindia.indiatimes.com/business/india-business/security-firm-sisa-alerts-banks-on-malware-attack/articleshow/62141684.cms
However, considering the resurfacing of this attack, more importantly, as part of our PFI activity the intruder is there in the system for more than a year. Hence, we can’t prevent a breach, but at-least, we will be able to stop lateral movement and egress point. Unless there is egress, the intruder hasn’t succeeded.
We are recommending the following immediate steps that banks can implement proactively in order to secure the payment switch application and network environment:
1. Enable multi-factor authentication for any users to login to the Switch application server
2. Enable IP table to restrict only authorized systems access to the switch server
3. Reset the password of all privileged users in the Switch application server.
4. Reach out to your Payment Forensic Investigator (PFI) authorized by Payment Brands and Listed on PCI Council Website within 24 hours of any suspicion.
5. Conduct a credential based vulnerability assessment scan. A non-credential based vulnerability assessment scan has limitations in identifying all the vulnerabilities present in the servers/network components.
6. Conduct web application penetration testing for all web-interfaces present in the network. All applications which have a web-interface, whether internal or external needs to be tested.
7. Instruct your Security Operations Centre to identify any similar Indicators of Compromise. Also as part of the S-SOC operations, please have thread hunting activity carried out for this particular IOC.
8. Ensure PCI DSS certification for scoped environment and deploy PA-DSS validated application by Authorized QSA’s listed on PCI Security Standard council website. (https://www.pcisecuritystandards.org/assessors_and_solutions/payment_applications?agree=true)
Source : https://www.sisainfosec.com/blogs/8-immediate-steps-post-fake-response-malware-resurface/
0 notes
Text
Cyber Security Risks In Social Media Banking
Introduction
Social Media is the most used platform on day-to-day basis by millions of people around the world.
Social media banking is the usage of social platforms such as Facebook, twitter, WhatsApp for Marketing, communication, for collecting feedback and reactions and to perform Banking Operations such as Transactions, Account summary and status enquiry, etc. We have observed using social media as a platform in 2 ways.

1. Non-Banking Operations – Marketing, Branding, Feedback, Business Analysis.
2. Banking Operations – Transactions, Communications and alerts, Account summary, status of the account or cards, reporting fraud/stolen card details etc.
Use cases of Social Media Banking
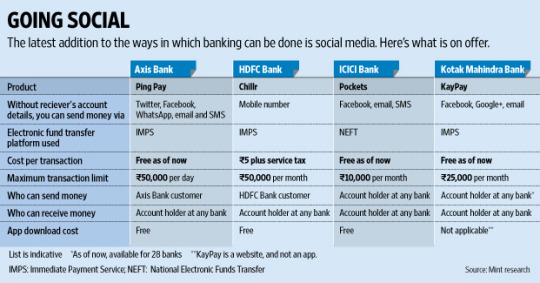
1. Global Banks Using Twitter for Banking:
Money can be sent using twitter accounts connected to Bank accounts, or it would have other options of receiving and sharing passcode and OTP with the receiver for authorizing a transaction.


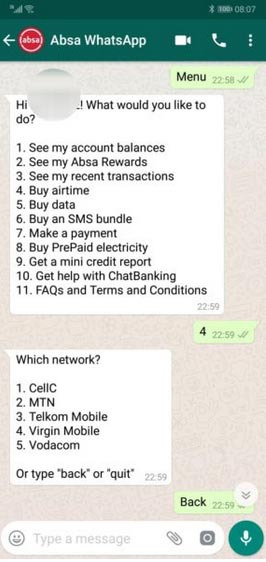
2. WhatsApp Banking service:
Absa Banking app (Africa) has introduced WhatsApp Banking to help customer receive updates or avail services via the WhatsApp messaging platform. On typing Help as a message, you can find out the full list of services available on WhatsApp. It is easy to use—simply type a keyword like or type the number against the service like “1” and follow the steps on screen.
3. CaixaBank Facebook Banking Application:
CaixaBank has launched a Facebook application that allows users to view their bank accounts and perform transactions via the social network. This is the first platform of its kind from a European bank, allowing customers to check account balances, make micro-donations and contract personalized card services. The new CaixaBank service for Facebook will also provide quick access to the bank’s primary online channel, Linea Abierta. Once activated, users can open the application via their personal profile or the bank’s Facebook page. Users will have to enter their Linea Abierta username and password each time the service is opened, as the service is located in a fully secure and private environment that can only be opened by each customer. At no time will Facebook have access to any personal or bank information.
Example: Australian Common Wealth bank using Facebook and other Banks using Messenger.



Organizational Risks Associated with Social Media Banking:
The Federal Financial Institutions Examination Council (FFIEC) specifically for these social media banking issues created the “Social Media: Consumer Compliance Risk Management Guidance”
Risk Areas for Social Media banking are as follows.
1. Compliance and Legal Risks
2. Reputation Risk
3. Operational Risk
Control: Financial institutions should consider the use of social media monitoring tools and techniques to identify heightened risk, and respond appropriately. Financial institutions should have appropriate policies in place to monitor and address in a timely manner the fraudulent use of the financial institution’s brand, such as through phishing or spoofing attacks.
Instances of Social Media Attacks and Breaches:
Phishing Direct Message Sent to Customers from Compromised Brand Account Timeline: September 2011 Tactic: Account Takeover, Targeted Phishing & Malware Summary: In September of 2011, an Australian bank suffered the worst-case scenario for an account takeover, in which attackers didn’t immediately vandalize the account or post inflammatory messages, but instead sent direct messages to followers asking them to disclose sensitive financial institutions. While most account hacks are merely embarrassing and costly from a brand and public relations perspective, they can also be used for large scale cyberattack against a brand’s most loyal and engaged followers.
Vevo Hacked Via Targeted LinkedIn Phishing Attack, 3.12TB Exfiltrated Timeline: September 2017 Tactic: Targeted Phishing & Malware Summary: Streaming service Vevo suffered a breach when one of its employees was phished via LinkedIn. Hackers were able to obtain and publicly release 3.12TB worth of the company’s sensitive internal data. The professional social network allows attackers to rapidly identify their target at a specific organization and send them a personalized message, all under the auspices of professional networking or recruitment.
Fake Social Media Persona Sends Malware to Employees Via Social Media Timeline: July 2017 Tactic: Targeted Phishing/Malware, Fraudulent Accounts Summary: Attackers created an incredibly compelling fake persona, a London-based photographer named Mia Ash, and connected with corporate employees. The attacker disseminated a Remote Access Trojan (RAT), called PupyRAT, via these social media honeypot accounts to hijack the controls of victims’ devices. The persona had accounts across several popular social networks.
10k US Government Employees Spearphished with Malware-Laced Posts Timeline: Early 2017 Tactic: Targeted Phishing/Malware, Fraudulent Accounts Summary: In early 2017, Russian operatives sent over 10,000 custom phishing messages via social media, each link laced with malware enabling the attacker to access and control the victim’s device. This attack represents a major advancement in cyber capabilities and an escalation in Russia’s cyberwar against the US. This is the most well-organized, coordinated attack at the nation-state level we’ve ever seen.
3rd Party App Leads to Hundreds of High-Profile Account Compromises Timeline: March 2017 Tactic: Account Takeover Summary: A vulnerability in a 3rd-party app called Twitter Counter allowed Turkish-language attackers to hijack controls of hundreds of high-profile accounts. They posted aggressive messages against the Netherlands after a contentious week of deteriorating relations between the Netherlands and Turkey and pivotal elections in both countries. The posts used swastikas and called the Dutch “nazis.” The breached accounts included a number of global brands and well-followed, verified accounts, including Forbes, the official Bitcoin Blockchain account, Starbucks, the European Parliament, UNICEF, Nike and Amnesty International.
Financial Crime Runs Rampant on Social Networks Timeline: August 2016 Tactic: Fraud & Scams Summary: ZeroFOX researchers revealed the vast underground world of financial crime on social media, in which scammers prey on the followers of verified banks with fraudulent financial services offerings, including card cracking and money flipping. The scale of the problem is massive, with nearly a quarter-million posts for a single type of scam on a single social network. The problem was found on every major social media channel and results in hundreds of millions of dollars in losses annually.
Conslusion:
Imagine if a cybercriminal blasted your 1000+ followers with a fake coupon (“2018/9 season 50% cashback for the next 30 minutes! #discount #Cashback #zerointerest #Zerodownpayment #football”) appended with the latest and greatest malware. Imagine the cataclysmic fallout of a cybercrime at the scale and speed of social media.
Social media banking is exposed to modern threat vector risks that can be reduced by implementing risk monitoring and remediation technology, security controls with compliance.
The most Impactful attacks observed are third party apps compromised, targeted Phishing, malware, fraudulent accounts and the least impactful of social attacks, account takeovers, are often relatively harmless vandalism and trolling.
10 Best ways to reduce Risks Associated with Social Media Banking
1. Monitor social media and digital channels for business and security risks. Continuously watch for phishing links, fraudulent accounts, scams and more. A digital risk monitoring solution can be used for this purpose.
2. Ensure Multi-factor authentication is enabled.
3. Security professionals should train employees on what information should or should not be posted or visible to the public.
4. Work with marketing to gain access to social accounts and keep a close eye on social media initiatives and campaigns
5. Continuously monitor corporate social media accounts for cyber threats
6. Blacklist/block malicious URLs and IPs found on social media.
7. Establish workflow for dealing with social media cybercrime targeting the organization.
8. Takedown malicious posts and profiles.
9. Test employees on susceptibility to social media cyberattacks.
10. Train employees on safe usage, best practices, and what to do in the event of an attack
Resources followed for the article:
https://www.finextra.com/blogposting/13785/banking-on-social-media-platforms
https://www.researchgate.net/publication/320142155_Social_media_banking_models_A_case_study_of_a_practical_implementation_in_banking_sector
https://thefinancialbrand.com/35584/ffiec-social-media-regulations-guidelines-banking/all/
https://www.zerofox.com/blog/social-media-security-best-practices/
https://blog.hootsuite.com/social-media-security-for-business/
FFIEC document for Risk Identified and management of risk using social media for Banking.
Source: https://www.sisainfosec.com/blogs/cyber-security-risks-social-media-banking/
0 notes