Spumoni. It/Its. Art, writing, fandom SFW blog. Current Fixation: XiaoVen (Genshin), Shorekeeper (WuWa). In 30s, Minors DNI. [img description - icon: character with blue skin and silver hair. img description - cover: one stripe of mint green, one strike of pink, and one stripe of brown. Each one has dots a darker colour of that stripe)Linktree
Don't wanna be here? Send us removal request.
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
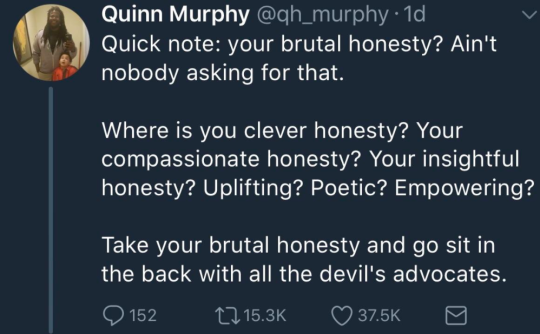
PSA
Just a heads up, there are bots going around on AO3 accusing people of using AI. Considering the timing, this is likely AI bros' retaliation for AO3 users calling them out for scraping their work. Examples of what you might be sent:
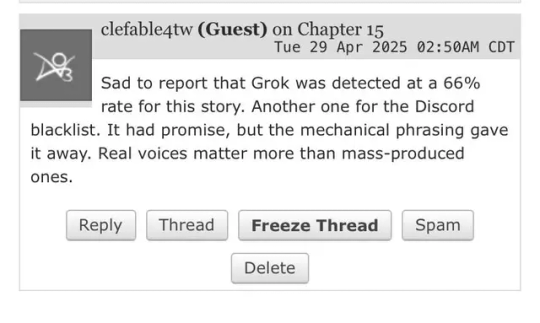
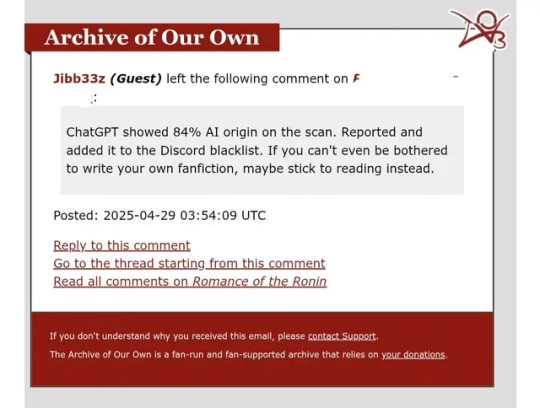

Screenshots from here.
If you get a comment like this, just report for spam and delete.
50K notes
·
View notes
Text
wikipedia no longer being anywhere near the top of search results when looking up anything feels eviscerating
120K notes
·
View notes
Text

it’s always been her
#oohh this is NICE#time to do my yearly PMMM rewatch#such a good series#please movie 4 don't get pushed back AGAIN
17K notes
·
View notes
Text
I promise I didn't disappear, I just don't have any impulse control and started several at once again haha
#i love this artist so much#the details#i cannot#i was wheezing by the third rewatch because I kept finding new things
27K notes
·
View notes
Text

#one of these days I'll write a phlebotomist au#not sure with which fandom#but this#this will be in it#some way#some how#(i have some funny stories from my brief stint in bloodwork)#just gotta#just gotta get the right idea#for the right fic
115K notes
·
View notes
Text
I think every computer user needs to read this because holy fucking shit this is fucking horrible.
So Windows has a new feature incoming called Recall where your computer will first, monitor everything you do with screenshots every couple of seconds and "process that" with an AI.
Hey, errrr, fuck no? This isn't merely because AI is really energy intensive to the point that it causes environmental damage. This is because it's basically surveilling what you are doing on your fucking desktop.
This AI is not going to be on your desktop, like all AI, it's going to be done on another server, "in the cloud" to be precise, so all those data and screenshot? They're going to go off to Microsoft. Microsoft are going to be monitoring what you do on your own computer.
Now of course Microsoft are going to be all "oooh, it's okay, we'll keep your data safe". They won't. Let me just remind you that evidence given over from Facebook has been used to prosecute a mother and daughter for an "illegal abortion", Microsoft will likely do the same.
And before someone goes "durrr, nuthin' to fear, nuthin to hide", let me remind you that you can be doing completely legal and righteous acts and still have the police on your arse. Are you an activist? Don't even need to be a hackivist, you can just be very vocal about something concerning and have the fucking police on your arse. They did this with environmental protesters in the UK. The culture war against transgender people looks likely to be heading in a direction wherein people looking for information on transgender people or help transitioning will be tracked down too. You have plenty to hide from the government, including your opinions and ideas.
Again, look into backing up your shit and switching to Linux Mint or Ubuntu to get away from Microsoft doing this shit.
46K notes
·
View notes
Text
HEY GUYS!!
GUYS!!!
FRANCE HAS REACHED THE REQUIRED NUMBER OF SIGNATURES ON THE CITIZEN'S INITIATIVE AGAINST CONVERSION THERAPY IN THE EU!!

ONE COUNTRY DOWN, SIX TO GO!!
We also need still quite a few signatures in order to reach the one million required.
As to date, the six other countries with the most signatures are:
Spain - 38.72%
Finland - 30.31%
Ireland - 24.86%
Netherlands - 24.15%
Germany - 23.54%
Belgium - 23.09%
So yeah, still a long way to go, but we ARE slowly getting closer. Don't stop now! Don't let this stay within the community, either, if you have any friends or family who are open to queer rights, get them to sign, too!
54K notes
·
View notes
Text

Сяо: выучил все комбо атаки, побеждает за пару тычек Венти: даже не заглядывал в комбо (знает, что победит с божьей помощью)
49 notes
·
View notes
Text

Stop being mean about his horns. You're upsetting him.
57 notes
·
View notes
Text

bane of all evil
5K notes
·
View notes
Text
Nameless bard. More Mondstadt more pls hoyo

#hoyo out here releasing all these new anemo characters#and not only not reworking anemo at all#but still no Venti second story#and no Monstadt chapter#beautiful art like this sustains my soul#it's so tranquil ♡
6K notes
·
View notes
Text


Только любовь ✋️
Fem xiaoven
167 notes
·
View notes