#API Lead Auditing
Explore tagged Tumblr posts
Note
Do you have a more up to date link for a hacked spotify for android? I found your post from 2022 but the link doesn't have a version that's up to date with the version of spotify I have.
Thanks 💚
Not exactly. I actually don't use the hacked Spotify app anymore. I prefer Spotube, a free open-source app that interfaces directly with the Spotify web API. It also let's you download songs and albums directly, which the hacked app didn't do!
Overall Spotube is more stable, trustworthy (because the code source is open and community-audited), and will never be at risk Spotify patching the hack or disabling your account for violating terms of service, because it uses 100% legal software.
(P.S. the first link leads to F-Droid, an alternative app store for free, community-driven, open-source apps. That's where you can also download NewPipe, my favorite ad-free youtube app.)
#Spotify#Foss#Fossware#Libre#open source#Open-source#FLOSS#Spotube#Ad free#Adblocking#Adblocker#Ad free Spotify#Spotify Premium#Spotify ads
184 notes
·
View notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
Unlocking the Secrets to Effortless Compliance with ZATCA Phase 2
The Kingdom of Saudi Arabia is leading the way in digital transformation, especially with its structured e-invoicing initiatives. A significant part of this movement is ZATCA Phase 2, which aims to enhance transparency, boost efficiency, and ensure tax compliance across businesses.
If you are a business owner, accountant, or IT professional, understanding ZATCA Phase 2 is no longer optional. It is critical for ensuring that your operations remain compliant and future-ready. This guide breaks down everything you need to know in a simple, easy-to-understand manner.
What Is ZATCA Phase 2?
ZATCA Phase 2, also known as the Integration Phase, is the next major step following Saudi Arabia's Phase 1 e-invoicing requirements. While Phase 1 focused on the generation of electronic invoices, Phase 2 moves beyond that.
It requires businesses to integrate their e-invoicing systems with ZATCA’s Fatoora platform, allowing real-time or near-real-time transmission of invoices for clearance and validation.
This phase ensures that each invoice issued meets strict technical, security, and data format requirements set by the Zakat, Tax and Customs Authority (ZATCA).
Key Objectives Behind ZATCA Phase 2
Understanding the "why" behind Phase 2 can help businesses see it as an opportunity rather than a burden. The main goals include:
Improving tax compliance across all sectors
Minimizing fraud and manipulation of invoices
Streamlining government audits with real-time data
Promoting a transparent digital economy
Enhancing business operational efficiency
Who Needs to Comply?
All businesses registered for VAT in Saudi Arabia must comply with ZATCA Phase 2 regulations. This includes:
Large enterprises
Medium and small businesses
Businesses using third-party billing service providers
Companies operating across multiple sectors
Even if your business operates primarily offline, if you are VAT registered, you need to be compliant.
Important Requirements for ZATCA Phase 2
Compliance with ZATCA Phase 2 is not just about sending electronic invoices. It involves specific technical and operational steps. Here’s what your business needs:
1. E-Invoicing System with ZATCA Compliance
Your billing or accounting system must:
Issue invoices in XML or PDF/A-3 with embedded XML
Securely store invoices electronically
Incorporate UUIDs (Unique Identifiers) for each invoice
Attach a QR code for simplified verification
2. Integration with ZATCA Systems
Businesses must establish a secure Application Programming Interface (API) connection with ZATCA’s platform to allow the real-time sharing of invoice data.
3. Cryptographic Stamp
Each invoice must carry a cryptographic stamp. This verifies the invoice's authenticity and integrity.
4. Archiving
Invoices must be securely archived and retrievable for at least six years in case of audits or regulatory reviews.
Implementation Timeline for ZATCA Phase 2
ZATCA is rolling out Phase 2 gradually, targeting businesses in waves based on their annual revenues:
Wave 1: Businesses with annual revenues above SAR 3 billion (started January 1, 2023)
Wave 2: Revenues above SAR 500 million (started July 1, 2023)
Future Waves: Gradually extending to smaller businesses
Each business is officially notified by ZATCA at least six months before their compliance date, giving them time to prepare.
How to Prepare for ZATCA Phase 2: A Step-by-Step Guide
The good news is that with proper planning, adapting to ZATCA Phase 2 can be straightforward. Here’s a simple preparation roadmap:
Step 1: Review Your Current Systems
Audit your existing accounting and invoicing solutions. Identify whether they meet Phase 2’s technical and security standards. In most cases, upgrades or new software may be required.
Step 2: Select a ZATCA-Approved Solution Provider
Look for software vendors that are pre-approved by ZATCA and offer:
Seamless API integration
Cryptographic stamping
XML invoice generation
Real-time data reporting
Step 3: Integration Setup
Collaborate with IT teams or third-party service providers to set up a secure connection with the Fatoora platform.
Step 4: Employee Training
Ensure that relevant departments, such as finance, IT, and compliance, are trained to manage new invoicing processes and troubleshoot any issues.
Step 5: Test Your Systems
Conduct dry runs and testing phases to ensure that invoices are being properly cleared and validated by ZATCA without delays or errors.
Step 6: Go Live and Monitor
Once your system is ready and tested, begin issuing invoices according to Phase 2 standards. Regularly monitor compliance, system errors, and feedback from ZATCA.
Common Challenges and How to Overcome Them
Businesses often encounter several challenges during their Phase 2 preparation. Awareness can help you avoid them:
Integration Difficulties: Solve this by partnering with experienced ZATCA-compliant vendors.
Employee Resistance: Overcome this with proper training and clear communication on the benefits.
Technical Errors: Regular testing and quick troubleshooting can help prevent issues.
Lack of Budget Planning: Allocate a specific budget for compliance early to avoid unexpected costs.
Preparation is not just technical. It’s organizational as well.
Benefits of Early Compliance with ZATCA Phase 2
Early compliance does more than just prevent penalties:
Improves Financial Reporting Accuracy: Real-time clearance ensures clean records.
Builds Market Trust: Clients and partners prefer businesses that follow regulatory norms.
Enhances Operational Efficiency: Automated invoicing processes save time and reduce errors.
Boosts Competitive Advantage: Staying ahead in compliance projects an image of professionalism and reliability.
Businesses that proactively adapt to these changes position themselves as industry leaders in the evolving Saudi economy.
Conclusion
ZATCA Phase 2 is not just a regulatory requirement. It’s an opportunity to upgrade your operations, improve financial accuracy, and enhance business credibility.
By understanding the requirements, preparing strategically, and partnering with the right solution providers, your business can turn this challenge into a growth opportunity.
The sooner you act, the smoother your transition will be. Compliance with ZATCA Phase 2 is your gateway to becoming part of Saudi Arabia’s dynamic digital economy.
2 notes
·
View notes
Text
A Comprehensive Guide to Blockchain-as-a-Service (BaaS) for Businesses
In today's digital landscape, a blockchain app development company plays a crucial role in transforming industries with decentralisation, immutability, and transparency. However, building and managing a private blockchain network can be complex and costly, which deters many businesses. Blockchain-as-a-Service (BaaS) simplifies this by allowing businesses to leverage blockchain without the challenges of infrastructure development.
This comprehensive blog covers the hurdles businesses face when adopting blockchain, how BaaS can bridge these gaps, and why it is a game-changer for various sectors.
I. Challenges for Businesses in Blockchain Adoption
Despite the undeniable potential of blockchain technology, businesses face several significant challenges when contemplating its adoption:
Limited Internal Expertise: Developing and maintaining a private blockchain network requires a skilled team with deep blockchain knowledge, which is often lacking in many organisations.
High Cost: The infrastructure investment and ongoing maintenance fees associated with blockchain can strain budgets, especially for small and medium-sized businesses (SMBs).
Integration Complexities: Integrating a blockchain network with existing enterprise systems can be challenging, requiring seamless data flow and compatibility between the blockchain system and legacy infrastructure.
II. Understanding BaaS and Its Operational Fundamentals
Blockchain-as-a-Service (BaaS) simplifies the development and deployment of blockchain applications by providing a cloud-based platform managed by third-party providers. The BaaS market, valued at $1.5 billion in 2024, is projected to grow to $3.37 billion by 2029, reflecting a robust 17.5% CAGR.
Key Components of BaaS
Cloud-Based Infrastructure: Ready-to-use blockchain infrastructure hosted in the cloud, eliminating the need for businesses to set up and maintain their networks.
Development Tools and APIs: Access to a suite of tools and APIs to create and deploy blockchain applications quickly.
Platform Support: Compatibility with various blockchain protocols such as Ethereum, Hyperledger Fabric, and Corda, offering flexibility to businesses.
Managed Service Model: Providers handle tasks like network maintenance, security updates, and scalability.
Pay-as-you-go Pricing Model: Reduces upfront investment and operational costs associated with blockchain software development.
III. Business Benefits of Blockchain as a Service
Adopting BaaS offers numerous advantages, including:
Enhanced Scalability: Businesses can easily scale their blockchain network as their needs grow.
Increased Efficiency: Eliminates intermediaries and streamlines transactions, improving productivity.
Enhanced Transparency: Tamper-proof records of transactions foster trust and improve auditability.
Reduced Costs: The pay-as-you-go model eliminates large upfront investments.
Improved Security: Built on secure cloud infrastructure with robust encryption protocols.
Enhanced Customer Engagement: Facilitates secure and transparent interactions with customers, building trust and loyalty.
IV. Industry-wise Key Use Cases of Blockchain as a Service
BaaS is transforming business operations across various industries:
Finance: Streamlines trade finance, secures cross-border payments, and enhances KYC and AML compliance.
Supply Chain Management: Improves transparency and traceability of goods, automates logistics processes, and reduces counterfeiting risks.
Healthcare: Facilitates secure sharing of patient data and tracks the provenance of pharmaceuticals.
Government: Enhances transparency with secure citizen identity management and verifiable voting systems.
V. Region-wise Adoption of BaaS
The BaaS market is experiencing rapid growth worldwide:
North America: Leading with over 35% of global revenues, driven by early adoption.
Europe: Countries like Germany, the UK, and France are at the forefront.
Asia-Pacific: China, India, Japan, and South Korea are key contributors.
Rest of the World: Growing adoption in South & Central America, the Middle East, and Africa.
VI. Why Choose a Prominent BaaS Provider?
Opting for a blockchain app development company that offers BaaS can significantly impact the success of your blockchain initiatives:
Specialised Expertise: Providers possess in-depth knowledge and experience in blockchain technology.
Cost Efficiency: Eliminates the need for in-house infrastructure investment and maintenance.
Time Savings: Accelerates the development process and reduces time-to-market.
Scalability and Flexibility: Offers scalable solutions that can adapt to business growth.
Risk Mitigation: Providers handle security, maintenance, and updates.
Conclusion
By adopting Blockchain-as-a-Service (BaaS), businesses can simplify blockchain integration and focus on innovation without the complexities of managing infrastructure. Systango, a leading blockchain app development company, offers tailored BaaS solutions that help businesses leverage blockchain technology for enhanced efficiency, scalability, and security. As one of the top , Systango also excels in integrating AI solutions to drive business growth and efficiency.
Original Source - https://systango.medium.com/a-comprehensive-guide-to-blockchain-as-a-service-baas-for-businesses-5c621cf0fd2f
2 notes
·
View notes
Text
Harnessing the Power of Data Engineering for Modern Enterprises
In the contemporary business landscape, data has emerged as the lifeblood of organizations, fueling innovation, strategic decision-making, and operational efficiency. As businesses generate and collect vast amounts of data, the need for robust data engineering services has become more critical than ever. SG Analytics offers comprehensive data engineering solutions designed to transform raw data into actionable insights, driving business growth and success.
The Importance of Data Engineering
Data engineering is the foundational process that involves designing, building, and managing the infrastructure required to collect, store, and analyze data. It is the backbone of any data-driven enterprise, ensuring that data is clean, accurate, and accessible for analysis. In a world where businesses are inundated with data from various sources, data engineering plays a pivotal role in creating a streamlined and efficient data pipeline.
SG Analytics’ data engineering services are tailored to meet the unique needs of businesses across industries. By leveraging advanced technologies and methodologies, SG Analytics helps organizations build scalable data architectures that support real-time analytics and decision-making. Whether it’s cloud-based data warehouses, data lakes, or data integration platforms, SG Analytics provides end-to-end solutions that enable businesses to harness the full potential of their data.
Building a Robust Data Infrastructure
At the core of SG Analytics’ data engineering services is the ability to build robust data infrastructure that can handle the complexities of modern data environments. This includes the design and implementation of data pipelines that facilitate the smooth flow of data from source to destination. By automating data ingestion, transformation, and loading processes, SG Analytics ensures that data is readily available for analysis, reducing the time to insight.
One of the key challenges businesses face is dealing with the diverse formats and structures of data. SG Analytics excels in data integration, bringing together data from various sources such as databases, APIs, and third-party platforms. This unified approach to data management ensures that businesses have a single source of truth, enabling them to make informed decisions based on accurate and consistent data.
Leveraging Cloud Technologies for Scalability
As businesses grow, so does the volume of data they generate. Traditional on-premise data storage solutions often struggle to keep up with this exponential growth, leading to performance bottlenecks and increased costs. SG Analytics addresses this challenge by leveraging cloud technologies to build scalable data architectures.
Cloud-based data engineering solutions offer several advantages, including scalability, flexibility, and cost-efficiency. SG Analytics helps businesses migrate their data to the cloud, enabling them to scale their data infrastructure in line with their needs. Whether it’s setting up cloud data warehouses or implementing data lakes, SG Analytics ensures that businesses can store and process large volumes of data without compromising on performance.
Ensuring Data Quality and Governance
Inaccurate or incomplete data can lead to poor decision-making and costly mistakes. That’s why data quality and governance are critical components of SG Analytics’ data engineering services. By implementing data validation, cleansing, and enrichment processes, SG Analytics ensures that businesses have access to high-quality data that drives reliable insights.
Data governance is equally important, as it defines the policies and procedures for managing data throughout its lifecycle. SG Analytics helps businesses establish robust data governance frameworks that ensure compliance with regulatory requirements and industry standards. This includes data lineage tracking, access controls, and audit trails, all of which contribute to the security and integrity of data.
Enhancing Data Analytics with Natural Language Processing Services
In today’s data-driven world, businesses are increasingly turning to advanced analytics techniques to extract deeper insights from their data. One such technique is natural language processing (NLP), a branch of artificial intelligence that enables computers to understand, interpret, and generate human language.
SG Analytics offers cutting-edge natural language processing services as part of its data engineering portfolio. By integrating NLP into data pipelines, SG Analytics helps businesses analyze unstructured data, such as text, social media posts, and customer reviews, to uncover hidden patterns and trends. This capability is particularly valuable in industries like healthcare, finance, and retail, where understanding customer sentiment and behavior is crucial for success.
NLP services can be used to automate various tasks, such as sentiment analysis, topic modeling, and entity recognition. For example, a retail business can use NLP to analyze customer feedback and identify common complaints, allowing them to address issues proactively. Similarly, a financial institution can use NLP to analyze market trends and predict future movements, enabling them to make informed investment decisions.
By incorporating NLP into their data engineering services, SG Analytics empowers businesses to go beyond traditional data analysis and unlock the full potential of their data. Whether it’s extracting insights from vast amounts of text data or automating complex tasks, NLP services provide businesses with a competitive edge in the market.
Driving Business Success with Data Engineering
The ultimate goal of data engineering is to drive business success by enabling organizations to make data-driven decisions. SG Analytics’ data engineering services provide businesses with the tools and capabilities they need to achieve this goal. By building robust data infrastructure, ensuring data quality and governance, and leveraging advanced analytics techniques like NLP, SG Analytics helps businesses stay ahead of the competition.
In a rapidly evolving business landscape, the ability to harness the power of data is a key differentiator. With SG Analytics’ data engineering services, businesses can unlock new opportunities, optimize their operations, and achieve sustainable growth. Whether you’re a small startup or a large enterprise, SG Analytics has the expertise and experience to help you navigate the complexities of data engineering and achieve your business objectives.
5 notes
·
View notes
Text
2024's Finest: The Top 6 eSignature Software for Seamless Online Document Signing

Introduction:
In the fast-paced digital landscape of 2024, the way we conduct business and handle official paperwork has evolved significantly. The days of traditional ink-on-paper signatures are dwindling, making way for the era of electronic signatures. From signing contracts to validating legal documents, the world of eSignature software has become a pivotal aspect of modern business operations. In this comprehensive guide, we will delve into the top 6 eSignature software that are reshaping the landscape of online document signing, offering seamless experiences and advanced features that set them apart in 2024. SimpliciSign: Streamlining eDocument Signing with Precision SimpliciSign joins the ranks of the top eSignature software by offering precision and efficiency in eDocument signing. Explore the features that make SimpliciSign stand out, including its seamless integration capabilities and user-friendly interface. With SimpliciSign, experience a streamlined approach to electronic signatures that enhances your overall document signing process. SimpliciSign offers cheapest rates in the market of eSignature softwares. Free Trial is also available. SimpliciSign has features like: -With the subscription of : $4.99 per user /month + $0.50/per invite, Unlimited once you are billed $35 in a month.
-Biometric Authentication-Optical Character Recognition(OCR) -Multi-signing Capability-Overlay Forms-Assign Sign Order-Fully Legal Binding Agreements DocuSign: Pioneering Excellence in eSignature Technology DocuSign, a pioneer in the eSignature industry, has maintained its prominent role as a key player for an extended period. Delve into the reasons behind DocuSign's leadership in the electronic signatures sector, exploring its intuitive interface and cutting-edge features that have firmly established its reputation. With a focus on robust security measures and seamless compatibility across diverse document types, businesses globally place their trust in DocuSign to fulfill their online document signing requirements. Key features of DocuSign: -Pricing Starts from $15 /month -Global Reach-Workflow Automation-Integration Adobe Sign: Unleashing the Power of Digital Signatures Adobe Sign harnesses the influence of the renowned Adobe brand in the realm of eSignatures. Immerse yourself in the realm of digital signatures and uncover how Adobe Sign seamlessly merges with widely-used document creation tools such as Adobe Acrobat. Discover the distinctive attributes that position Adobe Sign as a premier option for those seeking to enhance their online document signing journey, seamlessly combining convenience with the reliability associated with Adobe's trusted name in the industry of eSignatures. Key features of Adobe Sign: -Plans start from $22.99/month -Integration with Adobe Products-Mobile Accessibility-Compliance
Dropbox/HelloSign: Simplifying Signatures for Modern Businesses In the pursuit of a straightforward approach without sacrificing functionality, HelloSign stands out as a leading choice. This eSignature application prioritizes user-friendly interfaces and intuitive workflows, catering to businesses of varying sizes. Delve into how HelloSign simplifies the electronic signing process for contracts and legal documents, highlighting its commitment to efficiency and delivering a seamless and hassle-free signing experience. Key features of Dropbox/HelloSign: -Plans start from $19.99/month -User-Friendly API-Team Collaboration-Audit Trail
SignEasy: Redefining Convenience in Online Document Signing
SignEasy has established itself as a niche player by placing a premium on convenience. Explore the distinctive features that position SignEasy as a standout option for individuals and businesses in search of a direct solution for electronic signatures. With its design optimized for mobile use and seamless integrations with well-known cloud storage platforms, SignEasy is reshaping our approach to online document signing in the digital age. Key features of SignEasy: -Pricing Starts from $20 per user/month -Cross-Platform Availability:-Offline Signing-Intuitive Interface OneSpan Sign: Elevating Security in the eSignature Landscape
In the domain of electronic signatures, prioritizing security is of utmost importance, and OneSpan Sign excels in this regard. Investigate how this eSignature application incorporates advanced security measures to guarantee the integrity and authenticity of each digital signature. From robust encryption to multi-factor authentication, uncover the reasons why organizations opt for OneSpan Sign when emphasizing the highest standards of security in their processes for online document signing. Key features of SignEasy: -Professional Plan starts with $22 Per User/month -Advanced Security Features-Compliance-Mobile Capabilities
Conclusion:As we navigate the dynamic landscape of 2024, the demand for efficient, secure, and user-friendly eSignature software continues to rise. From the pioneering technology of SimpliciSign to the simplicity of HelloSign and the security-focused approach of OneSpan Sign, these top 6 eSignature software are leading the way in reshaping how we sign contracts and legal documents electronically. Embrace the future of online document signing with these innovative solutions, and stay ahead of the curve in 2024.
2 notes
·
View notes
Text
Just so that people are also aware - these aren’t new issues. They have been known about for a significant number of years (5+) at this point. Longer if you count machine learning and software development in general. Google Deepmind created an artificial intelligence ethics unit board, (privately in existence since the mid 2010s, publicly since 2017) to understand multiple risks surrounding the use of AI technology. You would think this was a good thing. So what did they find? Timmit Gebru and Emily Bender, the leading Google ethics advisor and a computational linguistics professor respectively, helped co-author a paper called “On the Dangers of Stochastic Parrots: Can Language Models Be Too Big?“. Some of the key points include:
“In accepting large amounts of web text as ‘representative’ of ��all’ of humanity we risk perpetuating dominant viewpoints, increasing power imbalances, and further reifying inequality.“
“In all cases, the voices of people most likely to hew to a hegemonic viewpoint are also more likely to be retained. In the case of US and UK English, this means that white supremacist and misogynistic, ageist, etc. views are overrepresented in the training data, not only exceeding their prevalence in the general population but also setting up models trained on these datasets to further amplify biases and harms.”
“BERT, ELMo, GPT and GPT-2 encode more bias against identities marginalized along more than one dimension than would be expected based on just the combination of the bias along each of the axes [ 54, 132]. Many of these works conclude that these issues are a reflection of training data characteristics.”
“...model auditing techniques typically rely on automated systems for measuring sentiment, toxicity, or novel metrics such as ‘regard’ to measure attitudes towards a specific demographic group [119]. But these systems themselves may not be reliable means of measuring the toxicity of text generated by LMs. For example, the Perspective API model has been found to associate higher levels of toxicity with sentences containing identity markers for marginalized groups or even specific names [61,103].“
It also talks about issues surrounding energy usage for large models and how environmentally friendly they are. Definitely take a read.
So what happened to Timmit? She was fired from her job. This was against a backdrop of mass protest within Google itself, with petitions and public calls for her work to be recognised by more than 1200 of her own colleagues.
If you’re interested in knowing more about AI hype - Timmit is still very active in AI ethics and runs the Distributed AI Research Institute (DAIR). They do a Twitch stream with researchers and guest speakers to highlight the tech industry’s bullshit every so often called the Mystery AI Hype Theater 3000 which I’d very much recommend: https://www.twitch.tv/dair_institute
The key takeaway here is that AI companies are aware of these problems - they simply aren’t interested in doing anything about them. Keep that in mind when using these tools.
This is why it is so important to be critical and double check everything you generate using image generators and text-based AI.
55K notes
·
View notes
Text
What Web Development Companies Do Differently for Fintech Clients
In the world of financial technology (fintech), innovation moves fast—but so do regulations, user expectations, and cyber threats. Building a fintech platform isn’t like building a regular business website. It requires a deeper understanding of compliance, performance, security, and user trust.
A professional Web Development Company that works with fintech clients follows a very different approach—tailoring everything from architecture to front-end design to meet the demands of the financial sector. So, what exactly do these companies do differently when working with fintech businesses?
Let’s break it down.
1. They Prioritize Security at Every Layer
Fintech platforms handle sensitive financial data—bank account details, personal identification, transaction histories, and more. A single breach can lead to massive financial and reputational damage.
That’s why development companies implement robust, multi-layered security from the ground up:
End-to-end encryption (both in transit and at rest)
Secure authentication (MFA, biometrics, or SSO)
Role-based access control (RBAC)
Real-time intrusion detection systems
Regular security audits and penetration testing
Security isn’t an afterthought—it’s embedded into every decision from architecture to deployment.
2. They Build for Compliance and Regulation
Fintech companies must comply with strict regulatory frameworks like:
PCI-DSS for handling payment data
GDPR and CCPA for user data privacy
KYC/AML requirements for financial onboarding
SOX, SOC 2, and more for enterprise-level platforms
Development teams work closely with compliance officers to ensure:
Data retention and consent mechanisms are implemented
Audit logs are stored securely and access-controlled
Reporting tools are available to meet regulatory checks
APIs and third-party tools also meet compliance standards
This legal alignment ensures the platform is launch-ready—not legally exposed.
3. They Design with User Trust in Mind
For fintech apps, user trust is everything. If your interface feels unsafe or confusing, users won’t even enter their phone number—let alone their banking details.
Fintech-focused development teams create clean, intuitive interfaces that:
Highlight transparency (e.g., fees, transaction histories)
Minimize cognitive load during onboarding
Offer instant confirmations and reassuring microinteractions
Use verified badges, secure design patterns, and trust signals
Every interaction is designed to build confidence and reduce friction.
4. They Optimize for Real-Time Performance
Fintech platforms often deal with real-time transactions—stock trading, payments, lending, crypto exchanges, etc. Slow performance or downtime isn’t just frustrating; it can cost users real money.
Agencies build highly responsive systems by:
Using event-driven architectures with real-time data flows
Integrating WebSockets for live updates (e.g., price changes)
Scaling via cloud-native infrastructure like AWS Lambda or Kubernetes
Leveraging CDNs and edge computing for global delivery
Performance is monitored continuously to ensure sub-second response times—even under load.
5. They Integrate Secure, Scalable APIs
APIs are the backbone of fintech platforms—from payment gateways to credit scoring services, loan underwriting, KYC checks, and more.
Web development companies build secure, scalable API layers that:
Authenticate via OAuth2 or JWT
Throttle requests to prevent abuse
Log every call for auditing and debugging
Easily plug into services like Plaid, Razorpay, Stripe, or banking APIs
They also document everything clearly for internal use or third-party developers who may build on top of your platform.
6. They Embrace Modular, Scalable Architecture
Fintech platforms evolve fast. New features—loan calculators, financial dashboards, user wallets—need to be rolled out frequently without breaking the system.
That’s why agencies use modular architecture principles:
Microservices for independent functionality
Scalable front-end frameworks (React, Angular)
Database sharding for performance at scale
Containerization (e.g., Docker) for easy deployment
This allows features to be developed, tested, and launched independently, enabling faster iteration and innovation.
7. They Build for Cross-Platform Access
Fintech users interact through mobile apps, web portals, embedded widgets, and sometimes even smartwatches. Development companies ensure consistent experiences across all platforms.
They use:
Responsive design with mobile-first approaches
Progressive Web Apps (PWAs) for fast, installable web portals
API-first design for reuse across multiple front-ends
Accessibility features (WCAG compliance) to serve all user groups
Cross-platform readiness expands your market and supports omnichannel experiences.
Conclusion
Fintech development is not just about great design or clean code—it’s about precision, trust, compliance, and performance. From data encryption and real-time APIs to regulatory compliance and user-centric UI, the stakes are much higher than in a standard website build.
That’s why working with a Web Development Company that understands the unique challenges of the financial sector is essential. With the right partner, you get more than a website—you get a secure, scalable, and regulation-ready platform built for real growth in a high-stakes industry.
0 notes
Text
The Digital Foundation: Why Every Business Needs a Smart Website Strategy
Turning ideas into immersive digital platforms
Every successful business today has one thing in common: a solid digital presence. At the heart of that presence is the website. It is no longer a luxury or an afterthought—it is the foundation on which a brand builds trust, tells its story, and captures opportunities. Website development has become the single most powerful tool for businesses to communicate, convert, and compete in the modern marketplace.
First Impressions Begin Online
A website is often the first encounter a potential customer has with a brand. Within seconds, users decide whether they want to stay or leave. A cluttered design, confusing navigation, or slow loading time can cause even the most interested visitor to bounce. In contrast, a clean, intuitive, and responsive website immediately builds trust and encourages engagement.
Modern consumers are digitally native. They expect professionalism, seamless performance, and instant access to information. A strategically developed website delivers all this while reflecting a brand’s personality and values.
Building for the User Experience
User-centric design is at the heart of effective website development. It’s not enough to simply place content and visuals on a screen. Every layout decision, color palette, button, and scroll action should be purposeful and intuitive. Websites must anticipate user needs and guide them effortlessly toward meaningful actions—whether it's making a purchase, filling out a form, or reading valuable content.
Good UX goes beyond visuals. It involves accessibility for all users, including those with disabilities. It also includes adaptive design, ensuring the site works flawlessly across smartphones, tablets, and desktops.
Technology that Powers Growth
Underneath every great website is a strong technical foundation. Today’s websites must handle more than just static content—they need to integrate with CRMs, handle dynamic data, support e-commerce, and scale with business growth. From custom plugins to API integrations and database architecture, professional development ensures your website is ready for real-world demands.
Security is another major pillar. With cyber threats constantly evolving, developers must implement best practices such as firewalls, data encryption, secure logins, and regular updates to protect both the business and its users.
From Visibility to Conversion
Even the most beautiful website is ineffective if no one sees it. That’s why development must go hand-in-hand with SEO. Search engines reward websites that are fast, mobile-optimized, well-structured, and easy to navigate. Clean coding, proper metadata usage, and page speed optimization play a crucial role in ranking higher in search results.
Beyond visibility, smart development also enhances conversion. Features like sticky call-to-action buttons, simplified checkout flows, lead capture forms, and personalized user journeys help turn visitors into loyal customers.
Evolving with the Digital Landscape
Technology changes quickly. Trends emerge and fade. Consumer behavior shifts. A successful website isn’t just launched—it’s continuously improved. Modern development involves creating a flexible platform that can adapt and scale. Whether it’s integrating new technologies like chatbots or transitioning to headless CMS solutions, businesses must stay future-ready.
Routine maintenance, analytics tracking, and performance audits also ensure the site remains at peak performance long after launch.
Final Thought
In a digitally dominant era, your website is often the first—and sometimes only—chance to leave a lasting impression. It should not only look appealing but function as a strategic asset that works for your brand 24/7. A well-crafted website builds credibility, supports business objectives, and adapts to change, making it one of the smartest investments a business can make. The digital journey starts with purposeful Website Development.
0 notes
Text
How Biometric Devices Improve Employee Time Tracking
In an era where organizations strive for efficiency, accuracy, and security, managing employee attendance has evolved from traditional punch cards and manual logbooks to high-tech solutions. Among the most transformative innovations is the biometric device, a software that has revolutionized how companies track and manage employee time.
Whether you're a small business or a large enterprise, ensuring accurate time tracking is essential for payroll, productivity, and workforce management. Biometric devices offer a modern solution by linking attendance to unique human characteristics such as fingerprints, facial recognition, or iris scans - making time fraud and buddy punching things of the past.

What Is a Biometric Device?
A biometric device is a piece of hardware used to identify individuals based on unique biological traits. In the context of workplace management, these devices are typically deployed for access control and attendance tracking. Unlike traditional systems that require ID cards or PINs, biometric systems ensure that only the actual individual can clock in or access a restricted area.
Biometric devices can come in various forms:
Fingerprint scanners
Facial recognition systems
Iris recognition devices
Voice recognition tools
The growing popularity of biometric technology is due to its speed, accuracy, and ease of integration with other HR and payroll systems.
Common Problems with Traditional Time Tracking Methods
Before diving into how biometric devices improve employee time tracking, it’s worth understanding the limitations of traditional systems:
Buddy punching: Employees clock in or out for each other, leading to time theft.
Manual errors: Human oversight when entering or correcting data can lead to payroll discrepancies.
Lost or stolen access cards: These can pose both a security and operational risk.
Lack of real-time data: Delayed updates make it difficult to monitor workforce performance.
These challenges not only impact payroll accuracy but also affect overall productivity and morale.
How Biometric Devices Transform Time Tracking
1. Accuracy and Reliability
Biometric devices are incredibly accurate. Because they rely on individual traits that cannot be duplicated or shared, they offer reliable verification each time an employee clocks in or out. This eliminates common issues like buddy punching or fraudulent time logging.
For instance, a facial recognition-based biometric device ensures that only the authorized individual can record attendance. This means more accurate payroll processing and fewer disputes between HR and employees.
2. Real-Time Attendance Monitoring
Biometric systems provide real-time data on employee attendance. This allows HR departments and team managers to monitor punctuality, break times, and absenteeism more effectively. Cloud-based biometric devices like those offered by Spintly offer real-time syncing across multiple locations, perfect for businesses with distributed teams or multiple branches.
This live data can be accessed through dashboards and reports, offering actionable insights that go beyond mere attendance tracking.
3. Integration with Payroll and HRMS
A modern biometric device does more than log time. Many advanced systems integrate seamlessly with Human Resource Management Systems (HRMS) and payroll software. This eliminates the need for manual data entry, ensuring timely and accurate salary processing, tax compliance, and leave management.
Solutions like Spintly’s biometric access control and attendance management platforms are built with open APIs, making it easy to integrate with third-party software - resulting in a streamlined workflow and reduced administrative burden.
4. Improved Compliance and Audit Trail
Maintaining proper records of working hours is essential to comply with labor laws and industry standards. Biometric devices automatically log every time an employee enters or exits the workplace, providing a secure and tamper-proof audit trail.
This data becomes especially useful during labor audits or legal disputes, ensuring organizations remain compliant without having to dig through manual records.
5. Contactless and Hygienic Options
In the post-pandemic world, hygiene has become a critical consideration in workplace technology. Modern biometric devices now offer touchless options, such as facial recognition and mobile-based check-ins, which minimize physical contact.
Cloud-enabled platforms like Spintly even offer mobile-based biometric attendance solutions, where employees can check in via their smartphones - reducing shared touchpoints while maintaining strict security protocols.
Industry Use Cases
1. Corporate Offices
Biometric time tracking helps monitor in-office attendance while integrating with access control systems to manage entry permissions.
2. Manufacturing & Industrial Units
These devices ensure workers clock in accurately despite working in high-volume shifts, often across different parts of the plant.
3. Healthcare Institutions
Hospitals benefit from biometric tracking to maintain 24/7 shift records and manage attendance in a critical-care environment where staffing is essential.
4. Educational Institutions
Schools and colleges use biometric devices to track faculty and staff attendance while maintaining secure access to restricted areas.
Advantages Over RFID and PIN Systems
While RFID cards and PINs offer basic functionality, they’re prone to misuse and loss. A biometric device offers a level of certainty and convenience that traditional systems can't match. Employees can’t forget or lose their fingerprint or face, making the system more dependable and reducing the cost and hassle of replacements.
Furthermore, combining biometric devices with access control solutions, such as those provided by Spintly, enhances building security. The system ensures that only verified individuals gain access to sensitive areas, creating a safer workplace.
Key Features to Look for in a Biometric Device
If you're considering investing in a biometric time tracking solution, keep the following features in mind:
Cloud connectivity for remote access and real-time syncing
Integration capabilities with HRMS and payroll systems
Touchless operation for post-COVID hygiene standards
Mobile authentication for flexible, remote check-ins
Data encryption to protect biometric data and ensure compliance
Providers like Spintly are paving the way for secure, scalable, and easy-to-deploy biometric solutions that fit businesses of all sizes.
Conclusion
In a digital-first world, managing your workforce with accuracy and efficiency isn’t just about technology - it’s about trust, compliance, and operational excellence. A biometric device simplifies employee time tracking while eliminating common pitfalls like buddy punching, manual errors, and data delays.
By integrating biometric attendance with access control and cloud-based dashboards, organizations get a holistic view of employee movement and performance. Solutions such as Spintly’s smart biometric access platform are leading this transformation by offering sleek, wireless systems that combine convenience with security.
Whether you're looking to tighten security, reduce administrative overhead, or simply improve the employee experience, adopting a biometric solution could be the smartest investment your business makes this year.
#biometric machine#biometric attendance#biometric access#mobile access#attendance management#time and attendance software#accesscontrol#spintly#smartacess#biometrics#smartbuilding#visitor management system#access control solutions
0 notes
Text
Check Printing API: The Smart Way to Automate Business Payments
Introduction As ACH and digital wallets rise, checks remain critical in industries like insurance, healthcare, and real estate. Enter the check printing API, a tool that lets you print and mail checks via software — securely and automatically.

What Is It? A check printing API connects your internal software (like accounting tools or CRM) to a third-party service that prints and mails checks on your behalf.
Who Needs It?
Payroll providers
Property managers
Legal professionals
E-commerce businesses handling refunds
Key Features
Bank-compliant check formats
Digital signature embedding
MICR-encoded check numbers
Real-time tracking and reporting
Benefits
Save time on bulk printing
Avoid fraud and manual errors
Pay vendors and employees faster
Maintain audit trails for every check
Leading Providers Checkeeper, Lob, and Deluxe offer check APIs that support direct integrations and high-security standards.
Conclusion A check printing API simplifies payment logistics while maintaining compliance, accuracy, and professionalism.
youtube
SITES WE SUPPORT
Automated Mails – Blogger
0 notes
Text
Why Your Business Needs a Web3 Development Company in 2025
The internet is evolving at lightning speed—and businesses that adapt to change are the ones that thrive. Welcome to the world of Web3: the next generation of the internet built on decentralization, user empowerment, and blockchain technology. At the heart of this revolution lies the power of working with a forward-thinking web3 development company.
From transforming financial systems to creating secure digital identities, Web3 is poised to reshape industries. But this transformation isn’t just about adopting new tools—it’s about rethinking how applications are built, used, and trusted. That’s where expert development partners come in.
What Is Web3 and Why Does It Matter?
Web3 refers to the third generation of the internet, focused on decentralization and built using technologies like blockchain, smart contracts, and peer-to-peer networks. Unlike Web2, where data is controlled by centralized entities, Web3 returns control to users.
Key principles of Web3 include:
Decentralization
Trustless and permissionless architecture
Token-based economics
User ownership of data and digital assets
Whether you’re building decentralized apps (dApps), NFTs, DAOs, or blockchain-based SaaS platforms, a specialized web3 development company ensures your product is aligned with the latest technological standards and future-ready.
The Role of a Web3 Development Company
Web3 projects require deep expertise in multiple domains, from blockchain infrastructure to smart contract security. Here's how a top-tier development company contributes to your success:
1. Smart Contract Development
Smart contracts are self-executing programs that run on the blockchain. A web3-focused team writes, audits, and deploys secure smart contracts to support functions like payments, governance, or authentication.
2. dApp Design and Development
Building a dApp involves more than coding. It requires thoughtful design, seamless UX, and efficient integration with the blockchain. From wallets to DeFi protocols, experienced developers make it user-friendly and scalable.
3. Tokenomics and Blockchain Strategy
Launching a token-based product? A good partner will help design the economics, utility, and structure behind your tokens, ensuring long-term sustainability and user engagement.
4. Security and Audits
Web3 apps are frequently targeted by cyber threats. Security audits, penetration testing, and vulnerability assessments are essential services offered by a qualified development partner.
5. Cross-Chain and Interoperability Solutions
With so many blockchains in the ecosystem—Ethereum, Solana, Polygon, and more—your app needs to operate across networks. Web3 experts implement cross-chain bridges and APIs for seamless communication.
SaaS Meets Web3: A Powerful Combo
One of the most exciting trends today is the fusion of SaaS with Web3. Imagine subscription software that gives users actual ownership or software tools that reward usage through tokens.
This is where saas experts and blockchain engineers join forces to:
Build decentralized SaaS platforms
Integrate smart contract-based subscriptions
Enable tokenized access and incentives
Web3 adds a new layer of transparency and empowerment to the traditional SaaS model.
AI and Web3: Intelligent, Decentralized Innovation
The combination of AI product development with blockchain opens doors to next-gen digital experiences. From decentralized data marketplaces to intelligent decision-making on-chain, AI and Web3 are forming the backbone of futuristic systems.
Leading web3 development companies are exploring this intersection to:
Automate decisions through on-chain AI models
Protect data integrity using blockchain
Enable decentralized autonomous systems (DAOs) that learn and evolve
This hybrid model creates systems that are not just decentralized—but also smart and adaptive.
Hiring the Right Web3 Talent
Web3 is still a specialized field. If you’re aiming to build a secure, scalable, and meaningful product, it’s essential to hire developers who are trained specifically in Web3 technologies.
Qualities to look for:
Proficiency in Solidity, Rust, or Go
Understanding of blockchain architecture and consensus mechanisms
Hands-on experience with layer 1 and layer 2 chains
Experience in DeFi, NFT, or DAO platforms
Instead of hiring individuals, many companies choose to partner with a trusted web3 development company for faster delivery and strategic alignment.
Benefits of Choosing a Full-Service Web3 Partner
Collaborating with a full-service development company allows you to:
Get expert guidance from ideation to launch
Access ready-built modules and APIs
Ensure compliance, security, and scalability
Focus on business strategy while technical heavy lifting is handled for you
It’s more efficient, cost-effective, and secure.
Final Thoughts: Building the Future Starts Now
The world of Web3 is no longer just a concept—it’s a tangible shift in how we build, scale, and experience digital platforms. Whether you're a startup creating a DAO or an enterprise integrating blockchain into your workflow, success lies in execution.
And execution starts with partnering with the right people.
A trusted web3 development company offers you the technological muscle, strategic insight, and future-ready architecture you need to bring your vision to life—securely, efficiently, and at scale.
If you're ready to lead in the decentralized digital economy, now’s the time to act.
0 notes
Text
AI Risk Management: Why It’s Critical for Businesses in the Age of Automation
In today's AI-driven economy, intelligent systems shape everything from customer support to financial decision-making. But as companies deploy these systems, they face increasing scrutiny—both from regulators and the public. The solution? Robust AI risk management.
At Adeptiv, we help organizations build trust in their AI systems through smart governance, human oversight, and real-time monitoring. Here's how you can take control of AI risks before they control you.

What Is AI Risk Management?
AI risk management is the structured process of identifying, assessing, mitigating, and monitoring potential harms associated with the use of artificial intelligence.
These risks may include:
Bias and fairness issues
Security vulnerabilities
Regulatory non-compliance
Data misuse or leakage
Model hallucinations and reliability gaps
Without a strategy in place, these risks can lead to damaged reputations, legal penalties, or worse—harm to real people.
The 3 Pillars of Responsible AI Risk Management
At Adeptiv, our AI governance framework revolves around three essential layers:
1. Human-in-the-Loop Oversight
Integrating expert reviewers to validate AI outputs in real-time—especially in high-risk domains like healthcare, finance, and law.
2. Automated Risk Monitoring
AI that watches AI. We deploy intelligent supervision layers that flag anomalies, track model drift, and ensure auditability of decisions.
3. Governance & Compliance Frameworks
Tailored controls aligned with evolving standards like the EU AI Act, NIST AI RMF, and NYC AI Bias Law.
Why Traditional Risk Management Falls Short
Traditional enterprise risk tools weren’t built for fast-learning, opaque AI models. Risk today is dynamic—it’s embedded in data patterns, training loops, and API decisions. That’s why AI risk requires its own tools, policies, and accountability pathways. To get a glance about the future of AI governance, you can visit this website.
How Adeptiv Helps
Whether you’re a startup deploying your first LLM-powered feature or an enterprise auditing a complex AI stack, Adeptiv delivers:
AI Risk Audits
Model Evaluation & Testing
Human Review Layer Deployment
Real-Time Anomaly Detection
Compliance Reporting Tools
Ethical AI Training for Teams
Our platform is built to scale with your AI maturity, from sandbox experiments to full production pipelines.
Final Thoughts
AI can supercharge innovation—but only if it’s governed responsibly. Companies that manage their AI risks proactively will not only stay compliant but also build consumer trust, brand equity, and future resilience.
Ready to take control of your AI risk?
👉 Learn more about Adeptiv’s AI Risk Management solutions
0 notes
Text
Is Retatrutide Peptide Legal? Regulatory Landscape for Clinical Use and Research
Target Keywords: GMP Retatrutide, Clinical Retatrutide Regulation, Retatrutide peptide legal status, research peptides FDA compliance Internal Link: 👉 Trusted Retatrutide Supplier with GMP Certification
Introduction: Why Regulatory Clarity Matters for Retatrutide Peptide
Retatrutide, a promising triple agonist peptide under clinical development, has gained global attention for its dramatic impact on obesity and metabolic disease. But before clinics, CROs, or pharmaceutical developers decide to purchase or administer it, a crucial question remains:
Is Retatrutide legal for research or clinical use in the U.S., EU, and other key regions?
In this article, we’ll break down the regulatory status of Retatrutide Peptide across major jurisdictions, and offer clear guidelines for sourcing and handling this compound within a compliant framework.
1. Retatrutide’s Current Development Status
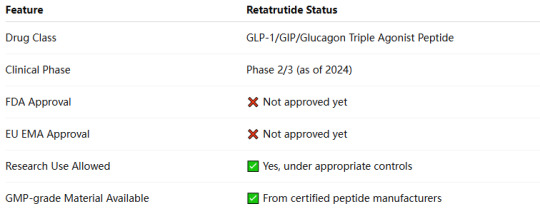
Although Retatrutide is not FDA- or EMA-approved for human therapeutic use, it can be legally used in non-human research and clinical trials under specific regulations.
2. Understanding Regulatory Terms: GMP, API, RUO

Procurement teams must ensure the Retatrutide they acquire:
Comes from a GMP-compliant source
Is labeled appropriately as RUO
Accompanied by COA, MSDS, and batch records
3. Is Retatrutide FDA-Compliant for Clinical Supply?
🧪 U.S. Regulatory Snapshot (FDA)
�� Not approved for prescription or therapeutic use
✅ Allowed for use in:
Pre-IND studies
Clinical trials with IND exemption
Animal model research
Must be labeled: “For research use only. Not for human consumption.”
🇪🇺 EU EMA Regulatory Snapshot
❌ No marketing authorization granted
✅ Research material accepted under:
Clinical trial applications (CTAs)
Laboratory and formulation development
Requires adherence to EU GMP Directives (EudraLex Vol. 4)
🌏 Other Regions
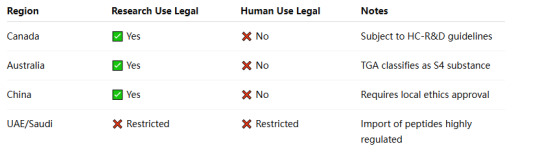
4. How to Stay Compliant When Sourcing Retatrutide
To avoid legal or safety issues, here’s a checklist for compliant Retatrutide procurement:
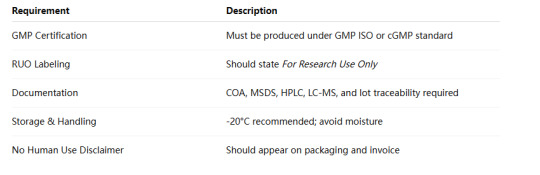
📌 Pro Tip: Always choose a peptide supplier who discloses GMP status, regulatory documentation, and origin of synthesis.
🔗 Explore GMP Retatrutide Peptide Options
5. Legal vs. Practical Use: What Clinics & Labs Must Know
Even though Retatrutide is not yet approved, many legitimate clinics and research labs are:
Using it in IRB-approved studies
Collaborating on pilot safety trials
Exploring combination therapy in pre-market formulations
🚫 However, selling or prescribing it for weight loss treatment outside of trials is prohibited in the U.S., EU, and most markets.
6. Final Recommendations for Labs, CROs, and Clinical Buyers
✅ Do:
Work with a GMP-certified Retatrutide Supplier
Keep clear documentation on file for import audits
Ensure staff is trained on handling, documentation, and labeling
❌ Don’t:
Use Retatrutide in human trials without IND or ethics board approval
Re-label research-grade product for off-label sale
Ignore local customs/import peptide restrictions
🔍 Summary Table: Legal Status of Retatrutide by Region
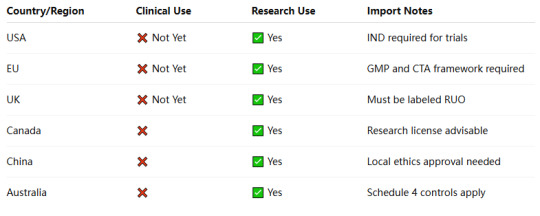
📌 Conclusion
Retatrutide is a cutting-edge metabolic peptide, but its legal use is strictly limited to preclinical and clinical trial contexts. It’s crucial to source GMP Retatrutide from trusted peptide suppliers and comply with regional regulations.
Whether you're a procurement lead at a CRO, clinical coordinator, or pharmaceutical buyer, understanding the legal status of Retatrutide Peptide protects your team—and your research integrity.
👉 Looking for a compliant Retatrutide Supplier? Explore GMP-certified options here: 🔗 https://retatrutidesupplier.com/retatrutide
📌 Conclusion
Retatrutide is a cutting-edge metabolic peptide, but its legal use is strictly limited to preclinical and clinical trial contexts. It’s crucial to source GMP Retatrutide from trusted peptide suppliers and comply with regional regulations.
Whether you're a procurement lead at a CRO, clinical coordinator, or pharmaceutical buyer, understanding the legal status of Retatrutide Peptide protects your team—and your research integrity.
👉 Looking for a compliant Retatrutide Supplier? Explore GMP-certified options here: 🔗 https://retatrutidesupplier.com/retatrutide
0 notes
Text
Drive Results with These 7 Steps for Data for AI Success
Artificial Intelligence (AI) is transforming industries—from predictive analytics in finance to personalized healthcare and smart manufacturing. But despite the hype and investment, many organizations struggle to realize tangible value from their AI initiatives. Why? Because they overlook the foundational requirement: high-quality, actionable data for AI.

AI is only as powerful as the data that fuels it. Poor data quality, silos, and lack of governance can severely hamper outcomes. To maximize returns and drive innovation, businesses must adopt a structured approach to unlocking the full value of their data for AI.
Here are 7 essential steps to make that happen.
Step 1: Establish a Data Strategy Aligned to AI Goals
The journey to meaningful AI outcomes begins with a clear strategy. Before building models or investing in platforms, define your AI objectives and align them with business goals. Do you want to improve customer experience? Reduce operational costs? Optimize supply chains?
Once goals are defined, identify what data for AI is required—structured, unstructured, real-time, historical—and where it currently resides. A comprehensive data strategy should include:
Use case prioritization
ROI expectations
Data sourcing and ownership
Key performance indicators (KPIs)
This ensures that all AI efforts are purpose-driven and data-backed.
Step 2: Break Down Data Silos Across the Organization
Siloed data is the enemy of AI. In many enterprises, critical data for AI is scattered across departments, legacy systems, and external platforms. These silos limit visibility, reduce model accuracy, and delay project timelines.
A centralized or federated data architecture is essential. This can be achieved through:
Data lakes or data fabric architectures
APIs for seamless system integration
Cloud-based platforms for unified access
Enabling open and secure data sharing across business units is the foundation of AI success.
Step 3: Ensure Data Quality, Consistency, and Completeness
AI thrives on clean, reliable, and well-labeled data. Dirty data—full of duplicates, errors, or missing values—leads to inaccurate predictions and flawed insights. Organizations must invest in robust data quality management practices.
Key aspects of quality data for AI include:
Accuracy: Correctness of data values
Completeness: No missing or empty fields
Consistency: Standardized formats across sources
Timeliness: Up-to-date and relevant
Implement automated tools for profiling, cleansing, and enriching data to maintain integrity at scale.
Step 4: Govern Data with Security and Compliance in Mind
As data for AI becomes more valuable, it also becomes more vulnerable. Privacy regulations such as GDPR and CCPA impose strict rules on how data is collected, stored, and processed. Governance is not just a legal necessity—it builds trust and ensures ethical AI.
Best practices for governance include:
Data classification and tagging
Role-based access control (RBAC)
Audit trails and lineage tracking
Anonymization or pseudonymization of sensitive data
By embedding governance early in the AI pipeline, organizations can scale responsibly and securely.
Step 5: Build Scalable Infrastructure to Support AI Workloads
Collecting data for AI is only one part of the equation. Organizations must also ensure their infrastructure can handle the scale, speed, and complexity of AI workloads.
This includes:
Scalable storage solutions (cloud-native, hybrid, or on-prem)
High-performance computing resources (GPUs/TPUs)
Data streaming and real-time processing frameworks
AI-ready data pipelines for continuous integration and delivery
Investing in flexible, future-proof infrastructure ensures that data isn’t a bottleneck but a catalyst for AI innovation.
Step 6: Use Metadata and Cataloging to Make Data Discoverable
With growing volumes of data for AI, discoverability becomes a major challenge. Teams often waste time searching for datasets that already exist, or worse, recreate them. Metadata management and data cataloging solve this problem.
A modern data catalog allows users to:
Search and find relevant datasets
Understand data lineage and usage
Collaborate through annotations and documentation
Evaluate data quality and sensitivity
By making data for AI discoverable, reusable, and transparent, businesses accelerate time-to-insight and reduce duplication.
Step 7: Foster a Culture of Data Literacy and Collaboration
Ultimately, unlocking the value of data for AI is not just about tools or technology—it’s about people. Organizations must create a data-driven culture where employees understand the importance of data and actively participate in its lifecycle.
Key steps to build such a culture include:
Training programs for non-technical teams on AI and data fundamentals
Cross-functional collaboration between data scientists, engineers, and business leaders
Incentivizing data sharing and reuse
Encouraging experimentation with small-scale AI pilots
When everyone—from C-suite to frontline workers—values data for AI, adoption increases and innovation flourishes.
Conclusion: A Roadmap to Smarter AI Outcomes
AI isn’t magic. It’s a disciplined, strategic capability that relies on well-governed, high-quality data for AI. By following these seven steps—strategy, integration, quality, governance, infrastructure, discoverability, and culture—organizations can unlock the true potential of their data assets.
In a competitive digital economy, your ability to harness the power of data for AI could determine the future of your business. Don’t leave that future to chance—invest in your data, and AI will follow.
Read Full Article : https://businessinfopro.com/7-steps-to-unlocking-the-value-of-data-for-ai/
About Us: Businessinfopro is a trusted platform delivering insightful, up-to-date content on business innovation, digital transformation, and enterprise technology trends. We empower decision-makers, professionals, and industry leaders with expertly curated articles, strategic analyses, and real-world success stories across sectors. From marketing and operations to AI, cloud, and automation, our mission is to decode complexity and spotlight opportunities driving modern business growth. At Businessinfopro, we go beyond news—we provide perspective, helping businesses stay agile, informed, and competitive in a rapidly evolving digital landscape. Whether you're a startup or a Fortune 500 company, our insights are designed to fuel smarter strategies and meaningful outcomes.
0 notes
Text
Secure E-Commerce: SSL, PCI Compliance & Beyond with Jurysoft
In the age of digital commerce, e-commerce security is no longer a luxury—it’s a business-critical necessity. With data breaches, fraud, and privacy concerns on the rise, consumers expect secure and transparent online shopping experiences. At Jurysoft, a leading e-commerce development company in Bangalore, we deliver end-to-end secure e-commerce solutions that align with the latest global security standards—SSL, PCI DSS, GDPR, and more.
🔐 Why Secure E-Commerce Development Matters
Every online transaction involves the exchange of sensitive data: credit card numbers, login credentials, shipping addresses. One weak link in your security infrastructure could result in irreparable brand damage and significant financial penalties. That’s why businesses across industries trust Jurysoft to build secure and scalable e-commerce websites.
✅ SSL Encryption: Your First Layer of Trust
Secure Socket Layer (SSL) certificates encrypt the communication between a user’s browser and your server. This is what activates the “HTTPS” protocol and the padlock icon, both of which signal safety to your shoppers.
Our approach at Jurysoft:
We implement 2048-bit SSL certificates for maximum encryption strength.
Configure HTTPS site-wide to ensure secure data transmission.
Integrate SSL monitoring and automatic renewal to avoid certificate expiration issues.
📚 Learn more about how SSL works
💳 PCI DSS Compliance: Secure Payment Gateways
PCI DSS (Payment Card Industry Data Security Standard) is required for any business that processes credit card transactions. Non-compliance can lead to fines or even suspension of your merchant account.
Jurysoft ensures PCI compliance by:
Using certified PCI-compliant payment gateways like PayPal, Razorpay, and Stripe.
Implementing tokenization and encryption for cardholder data.
Following secure coding practices and data access controls.
📖 Official PCI DSS documentation
🌍 GDPR Compliance: User Privacy First
If your business serves users in the EU, GDPR (General Data Protection Regulation) compliance is mandatory. Even for global stores, GDPR compliance builds customer trust and transparency.
Jurysoft’s GDPR strategy includes:
Consent banners and user opt-in for cookies.
User data export, correction, and deletion features.
End-to-end data encryption and restricted access policies.
🔗 What is GDPR? - A Simple Guide
🛡️ Regular Security Audits & Penetration Testing
Security is a continuous effort, not a one-time investment. Our team performs regular vulnerability assessments, code audits, and penetration testing to ensure your store remains protected against the latest threats.
Our ongoing security services include:
OWASP-based code reviews and penetration testing.
Automated vulnerability scans and patch management.
Real-time monitoring with alert-based incident response.
🧪 Related keyword: e-commerce website vulnerability testing services
🧭 Jurysoft’s Secure E-Commerce Development Process
From consultation to deployment, Jurysoft’s custom e-commerce development services are designed with security at the core:
Discovery & Planning Define security goals, data flow, and compliance requirements.
Secure Architecture & Design Build with HTTPS, secure APIs, and encrypted storage.
Secure Coding & QA Apply static code analysis and penetration testing.
Launch & Maintenance Continuous security monitoring and updates post-launch.
Whether you're building a B2B platform, multi-vendor marketplace, or a high-performance D2C store, we provide secure, compliant, and future-proof digital experiences.
🚀 Start Building a Secure Online Store with Jurysoft
At Jurysoft, we believe that security builds trust, and trust drives conversions. That’s why our team integrates SSL encryption, PCI DSS standards, GDPR compliance, and continuous security audits into every e-commerce platform we develop.
🔗 Talk to our e-commerce security experts
0 notes