#Active Protection System Market Statistics
Explore tagged Tumblr posts
Text

The Active Protection System Market is projected to grow from USD 3.9 billion in 2022 to USD 5.2 billion by 2027, at a CAGR of 5.5% from 2022 to 2027.
Active protection systems are widely used in the military, mostly to provide safety to armored fighting vehicles from enemy fire. They can be installed on tracked or wheeled armored fighting or logistics vehicles, combat helicopters, naval warfare ships, and other systems. Modular optoelectronic sensor systems, target acquisition systems, digital radar processors for target detection, and thermal imaging devices provide optimized field surveillance and combat by day/night or under poor visibility. Several countries are focusing on increasing their armored vehicle fleets owing to the rise in cross-border conflicts, which has directly led to the growth of the Active Protection System Industry.
The US Army and Israeli defense forces, among other armed forces, have carried out practical analyses of numerous active protection systems developed by Raytheon (US), Artis LLC (US), Israel Military Industries (Israel), and Rafael Advanced Defense Systems (Israel) to equip and install active protection systems on their armored vehicles.
For instance, in January 2022, the Hungarian government awarded a contract to Rheinmetall AG of Germany to install StrikeShield hard-kill active protection systems on 209 new Lynx infantry fighting vehicles. In January 2022, the US Army awarded a contract to the team of Unified Business Technologies (UBT) and Rheinmetall Protection Systems to test the StrikeShield active protection system at Redstone Test Center in Huntsville, Alabama. Various players such as Rheinmetall AG (Germany), Saab AB (Sweden), Raytheon Company (US), Airbus (Netherlands), and ASELSAN AS (Turkey) among others, are prominent players operating in the active protection system market.
#Active Protection System#Active Protection System Market#Active Protection System Industry#Global Active Protection System Market#Active Protection System Market Companies#Active Protection System Market Size#Active Protection System Market Share#Active Protection System Market Growth#Active Protection System Market Statistics
0 notes
Text
The Active Protection System Market is projected to grow from USD 3.9 billion in 2022 to USD 5.2 billion by 2027, at a CAGR of 5.5% from 2022 to 2027.
Active protection systems are widely used in the military, mostly to provide safety to armored fighting vehicles from enemy fire. They can be installed on tracked or wheeled armored fighting or logistics vehicles, combat helicopters, naval warfare ships, and other systems. Modular optoelectronic sensor systems, target acquisition systems, digital radar processors for target detection, and thermal imaging devices provide optimized field surveillance and combat by day/night or under poor visibility. Several countries are focusing on increasing their armored vehicle fleets owing to the rise in cross-border conflicts, which has directly led to the growth of the Active Protection System Industry.
#Active Protection System#Active Protection System Market#Active Protection System Industry#Global Active Protection System Market#Active Protection System Market Companies#Active Protection System Market Size#Active Protection System Market Share#Active Protection System Market Growth#Active Protection System Market Statistics
0 notes
Text
Aible And Google Cloud: Gen AI Models Sets Business Security
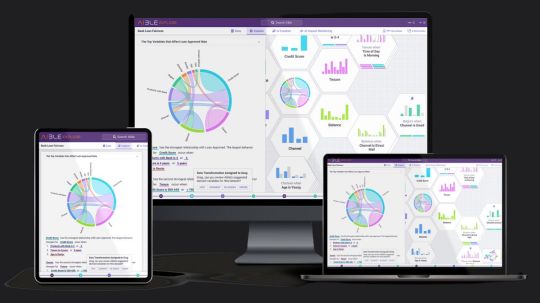
Enterprise controls and generative AI for business users in real time.
Aible
With solutions for customer acquisition, churn avoidance, demand prediction, preventive maintenance, and more, Aible is a pioneer in producing business impact from AI in less than 30 days. Teams can use AI to extract company value from raw enterprise data. Previously using BigQuery’s serverless architecture to save analytics costs, Aible is now working with Google Cloud to provide users the confidence and security to create, train, and implement generative AI models on their own data.
The following important factors have surfaced as market awareness of generative AI’s potential grows:
Enabling enterprise-grade control
Businesses want to utilize their corporate data to allow new AI experiences, but they also want to make sure they have control over their data to prevent unintentional usage of it to train AI models.
Reducing and preventing hallucinations
The possibility that models may produce illogical or non-factual information is another particular danger associated with general artificial intelligence.
Empowering business users
Enabling and empowering business people to utilize gen AI models with the least amount of hassle is one of the most beneficial use cases, even if gen AI supports many enterprise use cases.
Scaling use cases for gen AI
Businesses need a method for gathering and implementing their most promising use cases at scale, as well as for establishing standardized best practices and controls.
Regarding data privacy, policy, and regulatory compliance, the majority of enterprises have a low risk tolerance. However, given its potential to drive change, they do not see postponing the deployment of Gen AI as a feasible solution to market and competitive challenges. As a consequence, Aible sought an AI strategy that would protect client data while enabling a broad range of corporate users to swiftly adapt to a fast changing environment.
In order to provide clients complete control over how their data is used and accessed while creating, training, or optimizing AI models, Aible chose to utilize Vertex AI, Google Cloud’s AI platform.
Enabling enterprise-grade controls
Because of Google Cloud’s design methodology, users don’t need to take any more steps to ensure that their data is safe from day one. Google Cloud tenant projects immediately benefit from security and privacy thanks to Google AI products and services. For example, protected customer data in Cloud Storage may be accessed and used by Vertex AI Agent Builder, Enterprise Search, and Conversation AI. Customer-managed encryption keys (CMEK) can be used to further safeguard this data.
With Aible‘s Infrastructure as Code methodology, you can quickly incorporate all of Google Cloud’s advantages into your own applications. Whether you choose open models like LLama or Gemma, third-party models like Anthropic and Cohere, or Google gen AI models like Gemini, the whole experience is fully protected in the Vertex AI Model Garden.
In order to create a system that may activate third-party gen AI models without disclosing private data outside of Google Cloud, Aible additionally collaborated with its client advisory council, which consists of Fortune 100 organizations. Aible merely transmits high-level statistics on clusters which may be hidden if necessary instead of raw data to an external model. For instance, rather of transmitting raw sales data, it may communicate counts and averages depending on product or area.
This makes use of k-anonymity, a privacy approach that protects data privacy by never disclosing information about groups of people smaller than k. You may alter the default value of k; the more private the information transmission, the higher the k value. Aible makes the data transmission even more secure by changing the names of variables like “Country” to “Variable A” and values like “Italy” to “Value X” when masking is used.
Mitigating hallucination risk
It’s crucial to use grounding, retrieval augmented generation (RAG), and other strategies to lessen and lower the likelihood of hallucinations while employing gen AI. Aible, a partner of Built with Google Cloud AI, offers automated analysis to support human-in-the-loop review procedures, giving human specialists the right tools that can outperform manual labor.
Using its auto-generated Information Model (IM), an explainable AI that verifies facts based on the context contained in your structured corporate data at scale and double checks gen AI replies to avoid making incorrect conclusions, is one of the main ways Aible helps eliminate hallucinations.
Hallucinations are addressed in two ways by Aible’s Information Model:
It has been shown that the IM helps lessen hallucinations by grounding gen AI models on a relevant subset of data.
To verify each fact, Aible parses through the outputs of Gen AI and compares them to millions of responses that the Information Model already knows.
This is comparable to Google Cloud’s Vertex AI grounding features, which let you link models to dependable information sources, like as your company’s papers or the Internet, to base replies in certain data sources. A fact that has been automatically verified is shown in blue with the words “If it’s blue, it’s true.” Additionally, you may examine a matching chart created only by the Information Model and verify a certain pattern or variable.
The graphic below illustrates how Aible and Google Cloud collaborate to provide an end-to-end serverless environment that prioritizes artificial intelligence. Aible can analyze datasets of any size since it leverages BigQuery to efficiently analyze and conduct serverless queries across millions of variable combinations. One Fortune 500 client of Aible and Google Cloud, for instance, was able to automatically analyze over 75 datasets, which included 150 million questions and answers with 100 million rows of data. That assessment only cost $80 in total.
Aible may also access Model Garden, which contains Gemini and other top open-source and third-party models, by using Vertex AI. This implies that Aible may use AI models that are not Google-generated while yet enjoying the advantages of extra security measures like masking and k-anonymity.
All of your feedback, reinforcement learning, and Low-Rank Adaptation (LoRA) data are safely stored in your Google Cloud project and are never accessed by Aible.
Read more on Govindhtech.com
#Aible#GenAI#GenAIModels#BusinessSecurity#AI#BigQuery#AImodels#VertexAI#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
"In effect, [Arrighi Emmanuel]’s whole political argument moves subsequently in a direction that repeats all the old clichés of third-worldism – a third-worldism of the most equivocal kind. The wage-imbalance which is responsible for "unequal exchange" is once more assumed to be a static structure (the entirety of Emmanuel’s model is, ultimately, comparative statistics) and translates politically as the theory of an “objective” antagonism which would counterpose the various sections of a global proletariat, and as a “rich and poor” theory of the global state-system. Coherently, the indications that Emmanuel offers here and there on exit strategies for the current situation follow the same trajectory: the general proposition of a sort of global incomes policy; a positive appraisal of the interruption of the stagnation of wages produced by multinational investment in underdeveloped countries; the special recommendation of the path toward developing areas of regional protection between equally underdeveloped countries, and so on. His is an extreme political “moderation,” to put it lightly, which, furthermore, shows how “revolutionary” outcomes do not necessarily follow from a “third-worldist” model! But let us try to alter the point of view from which Emmanuel, himself, reads the sequence of elements that constitute his model.
The level and the “quality” of life of the metropolitan worker are not the historically acquired result of an already stabilized system of distribution of national income and of a political framework which is, by now, predisposed to regulate the relation between workers and capital indefinitely. All this is a silly social-democratic illusion or, worse yet, a “sociology of conflict.” On the contrary, they represent but one index, always “outdated” but, nevertheless, suggestive of a political confrontation which continually accumulates violence on both sides of the relationship, and which determines, as a problem of survival (question de vie ou de mort) the entire activity of the capitalist political class, from the everyday management of economic life all the way up to the “big” problems of the international equilibrium of power. However, this is true – and begins to be true – as applies to the dynamic of the wage, which is dependent within the sphere of the underdeveloped world. It is here, where it might have been most useful, that Emmanuel’s approach wears politically thin and condemns itself to failure. It is obvious that, beginning with moments of “primitive” accumulation which are, as a rule, introduced violently from outside, the modifications undergone by the old distribution of income, even where they assume the form of a further polarization, have progressively shifted the overall terrain of proletarian struggle into underdevelopment. Contemporaneously, a series of old representations dear to the international left in each of its tendencies have been disappearing. For example, that of a homogeneously backward condition applying to the entire underdeveloped world. All of the criteria set out to theoretically organize and empirically measure such a homogeneity (the absence of development based on the internal market, reduced number of sectors involved in the process of development, dependence on – and the impossibility of control over – external sources of funding, extremely circumscribed space for a “technologically independent development”) appear inapplicable to a whole host of areas that constitute the strengths of the new political geography (need we say, imperialist political geography?) of global underdevelopment.
Forget “objective” contraposition of interests within the global proletariat! A two-pronged movement which unites [accomuna] the metropolitan worker and the proletariat of the Third World in an analogous violent demand for income and power, and which exerts a continuous, formidable pressure on the whole structure of global power – all this is what Emmanuel’s outlook, and a third-worldist outlook in general, refuses to understand."
Luciano Ferrari Bravo, "Old and new questions in the theory of imperialism."
5 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
There it is.

[Image ID: A screenshot from the United States Patent for advertisement display screens linked above which contains the following text: "organic, non-gmo, etc.) and tags (e.g., sale with local card, locally made, trending, etc.). These promotional labels and tags can be activated via the controller/data collector 12 and can be either selected from a pre-determined set of static animated icons, or they can be customized by the retailer and/or brands based on their business and marketing needs. The controller/data collector 12 can be configured to incorporate customer rating scores (e.g., 1-5 stars, trending, favorites, etc.) using one or more consumer review sources. Preferably, the controller/data collector 12 is configured such that as a shopper stands or lingers in front of a given retail product container 14 changes yet again. (the following text has been highlighted by myself) At this point, preferably the controller/data collector 12 has been able to use the customer-detecting hardware 18 to effectively learn more about that particular customer, such as gender, age, mood, etc. The controller/data deflector 12 is configured to take what has been detected about the customer to determine which advertisement and other information to present to that particular customer on the display (end highlighting) 16 associated with the retail product container 14 in front of which the customer is standing. (Begin highlighting) By tracking shopper data in parallel with which advertising content is being served on all displays 15 within the viewing range of the shopper, the retailer and the brands are better served, providing new influence opportunities at the moment of purchasing decision, optimizing marketing spend and generating new revenue streams."(end highlighting)]
And if that isn't enough.

[Image ID: More text from the same document as previously shown that reads "The system may be configured to track eye movements of the consumer (such as by using powerful software tools coupled with specific hardware that uses infrared sources to track eye movements) and correlate gaze spots with advertisements. This amounts to a very powerful demonstration tool to measure the success of the advertisement and its ability to impact the decision of the shopping consumer. As discussed above, preferably each retail storage container 14 has a door and a display 16 is mounted on that door along with customer detecting hardware 18, such as one or more proximity sensors (such as heat maps), cameras, facial sensors or scanners, and eye-sensors (i.e., iris-tracking sensors). FIG. 4 illustrates the front 31 of the door 30 providing the display 16 and the customer-detecting hardware 18, such as a camera. As shown, preferably the display 16 is in the form of an LCD panel comprising one or more touch zones 32 which are interactive by the customer. An access panel 34 may be provided proximate the bottom of the door 30 along with a media player 36. Although not specifically shown, a protective panel may be a generally mounted over the display 16. (Begin highlighting) As shown in FIG.5, cameras or other types of sensors (i.e. inventory-taking hardware 20) may be provided on the back 33 of the door 30 which the controller/data collector 12 (shown in FIG. 1) can use to keep track of inventory regarding the interior contents of the retail product container 14." (end highlighting)]
It'll watch you steal...
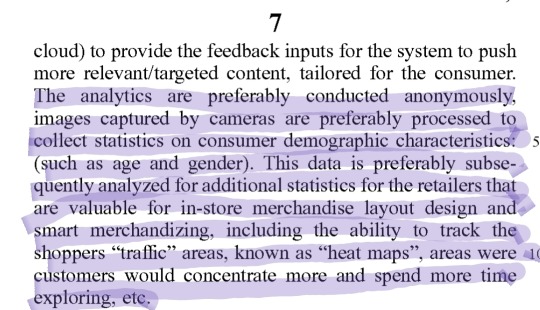
[Image ID: Another screenshot containing the following text: "cloud) to provide the feedback inputs for the system to push more relevant/targeted content, tailored for the consumer. (Begin highlighting) The analytics are preferably conducted anonymously, images captured by cameras are preferably processed to collect statistics on consumer demographic characteristics (such as age and gender). This data is preferably subsequently analyzed for additional statistics for the retailers that are valuable for in-store merchandise layout design and smart merchandizing, including the ability to track the shoppers "traffic" areas, known as "heat maps", areas were customers would concentrate more and spend more exploring, etc." (end highlighting)]
And then rat out where you did it.

[Image ID: Another screenshot containing the following text: "inside the retail product container 14.) Preferably, the system is configured such that during door operation (i.e., when the door 30 is opened), the cameras 40 get triggered and take pictures at various intervals when the door 30 is open. Preferably, the system is configured to process the images and effectively reconstruct the entire shelf. The system may be configured such that the cameras get triggered by: 1) Motion being sensed by one or more cameras (if this is the case, preferably the system is configured such that at least one of the camera remains on all the time); and/or 2) Door motion being effectively sensed by one or more accelerometers 48 (see FIG. 12 ) on the door 30, wherein the system is configured such that the action of the cameras 40 gets triggered depending on various swing states and locations of the door 20 (i.e., when the door 20 gets opened). Regardless of exactly what triggers the cameras, preferably the system is configured such that images captured by the cameras are effectively "stitched" together to reconstruct the entire shelf space. Preferably, the system is configured to utilize image processing compare the images and conclude whether any of the products on shelves are missing. If any of the particular products are missing, preferably the system is configured to send a signal to content management software to update the planogram appropriately (i.e., on the display 16), preferably displaying that product as being "out of stock". Additionally, preferably the system is configured to notify a store inventory management team, such that re-stocking of that particular item on that particular shelf can take place quickly. FIG. 13 provides a block diagram of a method that is in accordance with an embodiment of the present invention and is self-explanitory given the foregoing description. (Begin highlighting) While a specific embodiement of the invention has been shown and described, it is envisioned that those skilled in the art may devise various modifications without departing from the spirit and scope of the present invention." (end highlighting)]
This whole bit is interesting, but the section at the bottom really is the icing on the cake.
#okay well that was so so much typing thanks to the us patent documents having one of those super wonky layouts that you can't copy#now I'm going to go back to what I was doing - fishing in classic pc dungeon delver fate#and thinking about apple pie
118K notes
·
View notes
Text
Lightning Rod for Building Market: Competitive Landscape and Strategic Forecast 2025-2032

MARKET INSIGHTS
The The global Lightning Rod for Building Market size was valued at US$ 234.8 million in 2024 and is projected to reach US$ 327.4 million by 2032, at a CAGR of 4.8% during the forecast period 2025-2032. The U.S. market accounted for 25% of global revenue in 2024, while China is expected to witness the fastest growth with a CAGR exceeding 5%.
Lightning rods are critical safety components designed to protect structures from lightning strikes by providing a low-resistance path for electrical discharge. These systems typically consist of air terminals (rods), conductors, grounding equipment, and surge protection devices. Modern variants include early streamer emission (ESE) rods and charge transfer systems, which offer enhanced protection radii compared to traditional Franklin rods.
Market growth is driven by increasing construction activities, stricter building safety regulations, and rising awareness about lightning-related risks. The hollow lightning rod segment holds over 60% market share due to superior conductivity and durability. Key players like DEHN, nVent Erico, and ABB Furse are investing in advanced materials such as copper-clad steel and corrosion-resistant alloys to improve product lifespan. Recent industry developments include IoT-enabled lightning protection systems that provide real-time monitoring of rod performance.
MARKET DYNAMICS
MARKET DRIVERS
Stringent Safety Regulations and Building Codes to Fuel Lightning Rod Adoption
Global building safety standards are becoming increasingly rigorous, mandating advanced lightning protection systems for structures exceeding certain heights or serving critical functions. Recent updates to international electrical codes now classify lightning protection as essential infrastructure for high-risk facilities like data centers, hospitals, and petrochemical plants. This regulatory push stems from escalating lightning-related damage claims, which exceed billions annually worldwide. Modern lightning rods incorporate patented ionization technology that enhances protection radius by up to 60% compared to conventional models, making them indispensable for contemporary construction projects. The rising emphasis on building resilience against extreme weather events continues to accelerate market penetration.
Urbanization and High-Rise Construction Boom to Expand Market Reach
The global construction sector is witnessing unprecedented growth, particularly in vertical urban development. With skyscrapers accounting for over 25% of new commercial constructions in metropolitan areas, the demand for reliable lightning protection has skyrocketed. Tall structures are exponentially more vulnerable to lightning strikes, with statistical models showing a 12% increased strike probability for every additional 30 meters in height. Leading manufacturers have responded by developing modular lightning rod systems that integrate seamlessly with modern architectural designs while offering enhanced protection. The Asia-Pacific region, where high-rise construction accounts for nearly 40% of all new building projects, represents the fastest-growing market for these advanced solutions.
MARKET RESTRAINTS
High Installation Costs and Maintenance Complexity to Hamper Market Expansion
While lightning protection systems deliver critical safety benefits, their adoption faces resistance due to substantial upfront investment requirements. Complete lightning protection installations can cost between 1-3% of a building’s total construction budget, with sophisticated early streamer emission (ESE) systems commanding premium pricing. Furthermore, regulatory compliance requires annual inspections and maintenance by certified professionals, creating ongoing operational expenses. Many small-to-medium construction projects view these systems as discretionary rather than essential, particularly in regions with moderate lightning activity. This perception barrier significantly limits market penetration in cost-sensitive segments and developing economies.
Technological Limitations in Protection Scope to Create Implementation Challenges
Contemporary lightning rod technology, while advanced, still presents notable limitations in comprehensive protection. Traditional Franklin rods create cone-shaped protection zones that leave lower portions of complex structures vulnerable. Although ESE systems boast wider coverage, their effectiveness remains debated within the scientific community, with protection claims varying significantly across different environmental conditions. These technical uncertainties complicate system specification and often necessitate over-engineering to ensure compliance, driving unnecessary costs. The industry continues to grapple with balancing theoretical protection models against real-world performance variables.
MARKET OPPORTUNITIES
Integration with Smart Building Systems to Create New Revenue Streams
The emergence of IoT-enabled lightning protection systems presents transformative opportunities for market expansion. Modern solutions now incorporate sensors that monitor strike frequency, intensity, and system integrity, feeding real-time data into building management platforms. This convergence with smart infrastructure allows predictive maintenance and detailed risk analytics, creating value-added services beyond basic protection. Early adopters in the commercial sector report 45% reductions in lightning-related downtime through these intelligent systems. As smart city initiatives gain momentum globally, the demand for networked lightning protection is projected to grow at nearly twice the rate of conventional systems.
Renewable Energy Infrastructure Development to Drive Specialist Demand
The rapid expansion of renewable energy installations presents a lucrative niche for specialized lightning protection solutions. Wind turbines, with their elevated positioning and metallic components, experience lightning strike rates up to 100 times higher than comparable structures. Solar farms similarly require customized protection schemes to safeguard extensive electrical networks. Manufacturers developing turbine-specific lightning rods and photovoltaic array protection systems are capturing this high-growth sector, which currently represents over 15% of the industrial lightning protection market. With global renewable capacity expected to double within the next decade, this segment offers sustained growth potential.
MARKET CHALLENGES
Standardization Disparities Across Regions to Complicate Global Expansion
The lightning protection industry faces significant hurdles due to inconsistent international standards and certification requirements. While IEC 62305 provides global guidelines, regional adaptations and local building codes create a fragmented regulatory landscape. For instance, ESE system acceptance varies dramatically between European and North American markets, forcing manufacturers to maintain multiple product lines. These discrepancies increase R&D costs and complicate inventory management, particularly for multinational suppliers. Achieving greater standardization remains an ongoing challenge that inhibits seamless global market penetration.
Climate Change Impact on Lightning Patterns to Introduce New Variables
Emerging research indicates climate change is altering global lightning distribution and intensity patterns, presenting new challenges for protection system design. Some regions are experiencing up to 25% more lightning days annually, while others show unusual seasonal concentration shifts. These environmental changes require constant reassessment of protection strategies and zoning methodologies. Manufacturers must now incorporate climate modeling into product development cycles, adding complexity to traditional engineering approaches. The industry’s ability to adapt to these evolving meteorological conditions will critically impact long-term system efficacy and market confidence.
LIGHTNING ROD FOR BUILDING MARKET TRENDS
Rising Demand for Advanced Lightning Protection Systems Drives Market Growth
The global lightning rod for building market is experiencing significant growth due to increasing awareness about structural safety and the rising frequency of extreme weather events. With climate change contributing to more intense thunderstorms across regions like North America and Asia-Pacific, the adoption of lightning protection systems has surged by approximately 7-9% annually over the past five years. Modern lightning rods now incorporate early streamer emission (ESE) technology, which provides superior protective radii compared to traditional Franklin rods. Furthermore, integration with smart building systems allows real-time monitoring of lightning strike threats, enhancing preventive maintenance capabilities.
Other Trends
Stringent Safety Regulations and Building Codes
Governments worldwide are enforcing stricter building codes mandating lightning protection for high-rise structures and critical infrastructure such as data centers and hospitals. For instance, the National Fire Protection Association (NFPA) 780 standard in the U.S. requires comprehensive lightning risk assessments before construction approvals. Similarly, European standards like IEC 62305 have led to a 12-15% annual increase in lightning rod installations across commercial properties. These regulatory frameworks are compelling architects and contractors to prioritize certified lightning protection solutions during project planning phases.
Technological Innovations in Material Science
The shift from conventional copper and aluminum rods to corrosion-resistant alloys and conductive polymers is redefining product durability. Manufacturers are investing in coatings like nickel-plated copper, which extends product lifespans by up to 30 years while maintaining optimal conductivity. Additionally, modular lightning protection systems are gaining traction, enabling easier retrofitting in existing buildings. The hollow lightning rod segment, valued at $85 million in 2024, is projected to grow at a CAGR of 6.2% through 2032, driven by their lightweight properties and ease of installation in complex architectural designs.
COMPETITIVE LANDSCAPE
Key Industry Players
Innovation and Compliance Drive Competition in Lightning Rod Market
The global lightning rod for building market exhibits a moderately consolidated structure, with established players dominating significant portions of the revenue share. Pentair and DEHN currently lead the market, holding a combined share of approximately 25% in 2024, owing to their extensive product portfolios and established distribution networks across North America and Europe.
NVent Erico and OBO Bettermann have strengthened their positions through continuous investments in R&D for advanced lightning protection systems. Their focus on meeting evolving international safety standards IEC 62305 and NFPA 780 has helped them secure contracts for large-scale commercial and industrial projects globally.
While large corporations dominate the high-value projects, regional players like Sichuan Zhongguang in China and AN Wallis in Europe compete effectively in local markets by offering cost-effective solutions customized to regional building codes and lightning incidence patterns.
The market has seen increased mergers and licensing agreements, particularly between Western firms and Asian manufacturers. ABB Furse recently expanded its Asian footprint through a strategic partnership with Guangxi Dikai, allowing both companies to leverage technological expertise and manufacturing capabilities.
List of Key Lightning Rod Manufacturers Profiled
Pentair (U.S.)
Alltec (U.S.)
East Coast Lightning Equipment (U.S.)
Lightning Protection International (U.K.)
Metal Gems (India)
Robbins Lightning (U.S.)
NVent Erico (U.S.)
OBO Bettermann (Germany)
DEHN (Germany)
ABB Furse (U.K.)
Phoenix Contact (Germany)
Schneider Electric (France)
Citel (France)
AN Wallis (U.K.)
Sichuan Zhongguang (China)
VFC (Italy)
Guangxi Dikai (China)
Gersan Elektrik (Turkey)
Harger Lightning & Grounding (U.S.)
Chengdu Pedaro (China)
Lightning Master (U.S.)
Segment Analysis:
By Type
Hollow Lightning Rod Segment Leads Due to Its Superior Conductivity and Durability
The market is segmented based on type into:
Hollow Lightning Rod
Solid Lightning Rod
By Application
Commercial Building Segment Dominates Owing to Stringent Safety Regulations
The market is segmented based on application into:
Residential Building
Commercial Building
Industrial Building
By Material
Copper-Based Lightning Rods Hold Major Share Due to Excellent Conductivity
The market is segmented based on material into:
Copper
Aluminum
Stainless Steel
Bronze
By Protection Level
Franklin Rod Technology Remains Preferred Choice for Conventional Protection
The market is segmented based on protection level technology into:
Franklin Rod
ESE (Early Streamer Emission) System
Radioactive System
Multipoint Discharge System
Regional Analysis: Lightning Rod for Building Market
North America The North American lightning rod market is driven by strict building safety codes and high awareness of lightning protection systems, particularly in hurricane-prone coastal regions like Florida and the Gulf Coast. The National Fire Protection Association’s (NFPA) 780 standard mandates lightning protection for critical infrastructure, fueling steady demand. The U.S. dominates the regional market, with advanced hollow rod technologies gaining traction in commercial high-rises. Canada’s market growth is propelled by retrofitting older buildings to meet updated Canadian Electrical Code requirements. The region sees strong competition among established players like Harger Lightning & Grounding and Pentair, with innovation focusing on corrosion-resistant materials.
Europe Europe maintains robust lightning protection standards through IEC 62305 regulations, creating a consistently regulated market. Germany and France lead in adoption due to dense urban development and high-value infrastructure. The EU’s focus on renewable energy has created new opportunities for lightning protection in wind farms and solar installations. The market favors integrated protection systems that combine early streamer emission (ESE) technology with traditional rods. Manufacturers like DEHN and OBO Bettermann dominate through technical expertise, while Eastern European markets show growth potential as building codes modernize.
Asia-Pacific As the fastest-growing region, Asia-Pacific accounts for over 40% of global lightning rod demand, driven by China’s massive construction boom and India’s smart city initiatives. Tropical countries like Indonesia and Malaysia have mandatory lightning protection for tall buildings, creating stable demand. While cost-sensitive markets still prefer conventional solid rods, Japan and South Korea increasingly adopt active protection systems. China’s domestic manufacturers like Sichuan Zhongguang control the mid-market segment, while international brands focus on premium projects. The region’s susceptibility to extreme weather ensures long-term market expansion.
South America Market growth in South America remains uneven, with Brazil leading due to its NBR 5419 lightning protection standard and high-rise developments in São Paulo and Rio de Janeiro. Argentina and Chile show steady demand from industrial and energy sectors, while other countries face adoption challenges from informal construction practices. Economic fluctuations impact infrastructure spending, causing manufacturers to focus on competitively priced solutions. Local players dominate residential markets, whereas multinationals target large commercial and government projects where compliance is strictly enforced.
Middle East & Africa The Middle East’s lightning rod market benefits from megaprojects in UAE and Saudi Arabia, where skyscraper construction requires advanced protection systems. Africa’s growth is concentrated in South Africa and oil-producing nations, though market penetration remains low overall. The region shows preference for durable, maintenance-free solutions suited for harsh desert climates. While international standards like IEC are followed in premium projects, local regulations vary widely. Market education remains crucial, as many builders still view lightning protection as optional rather than essential infrastructure.
Report Scope
This market research report provides a comprehensive analysis of the Global and regional Lightning Rod for Building markets, covering the forecast period 2024–2032. It offers detailed insights into market dynamics, technological advancements, competitive landscape, and key trends shaping the industry.
Key focus areas of the report include:
Market Size & Forecast: Historical data and future projections for revenue, unit shipments, and market value across major regions and segments. The global market was valued at USD XX million in 2024 and is projected to reach USD XX million by 2032, growing at a CAGR of XX%.
Segmentation Analysis: Detailed breakdown by product type (Hollow Lightning Rod, Solid Lightning Rod), application (Residential, Commercial, Industrial Buildings), and end-user industry to identify high-growth segments.
Regional Outlook: Insights into market performance across North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa. The U.S. market is estimated at USD XX million in 2024, while China is projected to reach USD XX million by 2032.
Competitive Landscape: Profiles of leading manufacturers including Pentair, Alltec, East Coast Lightning Equipment, Lightning Protection International, NVent Erico, and DEHN, covering their market share (top 5 players held approximately XX% in 2024), product portfolios, and strategic developments.
Technology Trends & Innovation: Assessment of advanced lightning protection systems, materials innovation, and integration with smart building technologies.
Market Drivers & Restraints: Evaluation of factors including increasing construction activities, stringent safety regulations, and climate change impacts versus challenges like high installation costs.
Stakeholder Analysis: Strategic insights for manufacturers, distributors, construction firms, and regulatory bodies regarding market opportunities and risk mitigation.
Related Reports:https://semiconductorblogs21.blogspot.com/2025/06/fieldbus-distributors-market-size-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/consumer-electronics-printed-circuit.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/metal-alloy-current-sensing-resistor.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/modular-hall-effect-sensors-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/integrated-optic-chip-for-gyroscope.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/industrial-pulsed-fiber-laser-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/unipolar-transistor-market-strategic.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/zener-barrier-market-industry-growth.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/led-shunt-surge-protection-device.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/type-tested-assembly-tta-market.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/traffic-automatic-identification.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/one-time-fuse-market-how-industry.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/pbga-substrate-market-size-share-and.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/nfc-tag-chip-market-growth-potential-of.htmlhttps://semiconductorblogs21.blogspot.com/2025/06/silver-nanosheets-market-objectives-and.html
0 notes
Text
Introduction to Online Betting
Online betting has rapidly transformed the global gambling landscape, offering users a convenient, accessible, and dynamic way to place wagers from the comfort of their own homes. This digital evolution of traditional betting practices now spans a wide variety of markets, including sports betting, casino games, poker, eSports, virtual sports, and even political or entertainment BET88 events. The growth of online betting has been fueled by increased internet penetration, the proliferation of smartphones, and advancements in secure payment technologies, making it easier than ever for people to engage in real-money betting activities.
The Evolution and Growth of Online Betting
The online betting industry has come a long way since its inception in the mid-1990s. What began as a few websites offering limited options has grown into a multi-billion dollar global enterprise with thousands of platforms catering to users across different regions. Major betting companies have invested heavily in mobile app development, live-streaming technology, and BET888 user-friendly interfaces to provide a seamless and immersive experience. Online betting is no longer just about picking winners — it's now about stats analysis, live in-play wagers, bonus systems, and loyalty programs, all designed to enhance user engagement and maximize retention.
Sports Betting – The most popular Segment
Sports betting remains the most prominent and profitable category in the online betting space. Bettors can place wagers on a wide range of sports such as football, basketball, cricket, tennis, horse racing, and more. Leading platforms offer various types of bets, including moneyline, spread betting, over/under totals, accumulators, and prop bets. Live or in-play betting is particularly popular, allowing users to place bets in real-time while a match is ongoing. Features like instant odds updates, cash-out options, and detailed statistics contribute to an engaging and interactive experience that mimics the excitement of a live stadium.
Online Casinos – Virtual Entertainment Hubs
In addition to sports betting, online casinos are a major component of the online betting ecosystem. These platforms replicate the experience of traditional brick-and-mortar casinos by offering classic games like roulette, blackjack, baccarat, and a wide variety of slot machines. Many online casinos also feature live dealer games, where professional croupiers operate real-time games via video streams, creating an authentic casino atmosphere. Players can also participate in progressive jackpot slots that offer potentially life-changing payouts. With sleek interfaces, immersive graphics, and real-time interactions, online casinos continue to attract millions of players worldwide.
Legal and Regulatory Landscape
The legality of online betting varies significantly across different jurisdictions. Some countries have fully regulated online betting markets with licensed operators and strict consumer protection laws, while others ban or restrict it altogether. For example, the united kingdom has a well-established regulatory framework overseen by the UK Gambling Commission, while the united states allows states to decide individually, resulting in a patchwork of regulations. It’s crucial for users to check the legality of online betting in their respective countries or regions and ensure they are using licensed and reputable platforms to avoid legal issues or potential fraud.
Responsible Gambling and User Protection
With the increased availability of online betting platforms, there is also a growing emphasis on responsible gambling. Reputable operators offer various tools and resources to help users manage their betting behavior, such as deposit limits, self-exclusion options, time-out features, and access to professional support services. Many platforms collaborate with organizations like GamCare or BeGambleAware to promote responsible gambling practices. Governments and regulators are also increasingly focusing on ethical advertising, preventing underage gambling, and minimizing gambling-related harm through educational campaigns and stricter enforcement.
Payment Methods and Financial Security
Modern online betting platforms support a wide array of payment methods, including credit and debit cards, bank transfers, e-wallets like PayPal and Skrill, prepaid cards, and even cryptocurrencies such as Bitcoin. This flexibility enhances user convenience and makes the deposit and withdrawal process faster and safer. Secure encryption technologies, two-factor authentication, and fraud prevention mechanisms are standard features designed to protect users’ personal and financial information. Trusted platforms are typically audited by third-party organizations to ensure fair play and transparency in their financial operations.
The Rise of Mobile Betting and Apps
Mobile technology has been a game changer for online betting. Today, most users prefer placing their bets via smartphones or tablets thanks to intuitive mobile apps and responsive websites. These apps offer all the functionality of desktop platforms, including live betting, instant notifications, promotional offers, and real-time updates. Push notifications alert users about new odds, ongoing matches, or special bonuses, allowing for a more personalized and engaging experience. With 5G and mobile-first strategies becoming more common, the future of online betting will continue to be shaped by innovations in mobile technology.
Future Trends in Online Betting
The future of online betting looks promising, with trends such as artificial intelligence, machine learning, and blockchain technology expected to play a major role. AI can enhance user experiences by offering personalized betting recommendations, detecting problem gambling behavior, and automating customer support. Blockchain technology, on the other hand, could provide greater transparency and security in betting transactions. Additionally, the integration of virtual reality (VR) and augmented reality (AR) could lead to more immersive betting environments, revolutionizing how users interact with online platforms.
Conclusion
Online betting is a dynamic and ever-evolving industry that offers a vast array of opportunities for entertainment, profit, and innovation. While it provides unmatched convenience and excitement, it also comes with inherent risks that must be managed through responsible behavior and regulation. As technology continues to advance and global markets become more connected, online betting will likely remain a significant part of the digital entertainment ecosystem for years to come.
0 notes
Text
With theft being the most usual of activity when we talk about security, safeguarding our assets has become all the more of a priority in the 21st century. What has become even more of a dilemma is the need to safeguard technology with technology itself. Yes, this might sound like an amalgamation of a twisted story but this by far is the truth. With so many advancements every second, the world of internet and tech has become more prone to sabotage, making all vulnerable to many more dangers which they could likely face in contrast to what the situation was 2 decades okay. When we talk about technology, we mostly refer to the online as well as the offline world of the internet; virtual you may call it. Everything has become linked and enormously attainable through the very network systems and bridges we make in order to protect us and our information in the very first place, making it a very vicious cycle running on its own when there is a breakthrough. To sum it up, technology is the victim, technology is the intruder and technology is the saviour. Interesting, isn’t it? It very most is. We refer to the world of technology as cyber space. With the ever growing importance of security needed for this cyber space, many organizations around the world have dedicated themselves to coming up with solutions to increased security against protecting people from cyber crimes. When cyber crime is escalating, so is the cyber security industry expanding. This is in retaliation to the rapidly developing need for computer security. When talking about estimated scores and according to Cybersecurity Ventures, the industry of Cyber Security is expected to grow from about $70 billion in 2014 to nearly an excess of $155 in 2019 which is great development. The companies which fall into the loop for Cyber Security are compiled in a very vast list. To begin with a few, below are the top 5 Cyber Security companies. FireEye Talking about FireEye, being highly applauded by Bloomberg TV, Wall Street Journal, BusinessWeek alongside many more, FireEye is a publically traded company. It has a market capital of around about $6.49 billion based on the New York Stock exchange. The unique aspect about FireEye is that it has invented a purpose built, virtual machine-based, security platform, which provides real-time threat protection to various enterprises and governments internationally against cyber attacks which has become something alarming in today’s world. Mentioning statistics, FireEye is host to 3,400 customers spread out in more than 67 countries around the world and is a client to 500 fortune companies. Lancope Lancope is an American privately owned company which was founded in 2000. Over the course of years, Lancope has managed to become one of the top cyber security companies. Lancope has been able to brand its name as “the leading provider of network visibility and security intelligence to defend enterprises against today’s top threats.” Lancope enables organisations to detect numerous and rather all kinds of cyber threats and enables an automated accelerated incident response through its various gadgets including its StealthWatch system. AlienVault Privately owned, AilenVault was founded in 2007 in California. It is marvellous to know that in such a short span of time, AlienVault has been able to come off as a promising company in order to reach the top 5 list of Cyber Security companies in the United States of America. The products which are produced by AlienVault as to fit and accommodate middle sized organisations. These middle sized organisations have requirements which range with having a single, effective guard against a variety of cyber threats. The management system introduced by AlienVault is by the name of “Unified Security Management” platform. This management system ensures that the security controls required are specifically designed to assist its cliental base with the benefits of Cyber Security from day as means of ensuring customer satisfaction of building their organisation.
AlienVault also most recently announcement of the beta release of the OTX 2.0 which is the open threat exchange. This OTX will allow the community of all OTX users to come together on one platform to discuss ideas, threats, and news. What really will happen through this is that there will be an open community thus knitted a bond between all the users and the organisation itself. Norse Norse is an organisation which was founded in 2010. Norse has indeed developed itself to become and be a part of the top cyber security companies in a live attack scenario of intelligence. They have dramatically improved their state and their “performance, catch-rate, and return on-investment of [a company’s] entire security infrastructure.” The innovative system introduced by Norse processes and provides more than hundreds of terabyte data against a seven petabyte attach history database. During this process, it was weighing over 1,500 variables in order to evaluate and take risks against real-time scores for the IP addresses and URL’s for its clients. This company has indeed marked its territory instilling itself in the industry of Cyber Security. There is a lack of real-time threat with an average of $10 million per year. The very essence of Norse is to take pre-emptive measures since when the minute something is compromised and measures are taken there and then, the damage has been reduced by 40% which is the very standing of Norse. Easy Solutions Easy Solutions is “the only security vendor focused on the comprehensive detection and prevention of electronic fraud across all devices, channels and clouds.” Easy Solutions has a cliental base which mostly consist of banks against activities such as stolen credit cards, insecure online portals, phishing, and fraud ever since its inception in 2007 in Florida, USA. Easy Solution is a privately held company which has statistics which boil to 60 million individuals and 220 major companies including institutions which comprise of its customers. Easy Solutions has been striving through the years in order to retain its name against the top notch cyber security systems. The writer is CEO and Co-founder of TecheRadar. He can be reached at [email protected]
0 notes
Text
Your Ultimate Resource for RERA-Approved Plots in Mysore Road
Mysore Road has become one of the fastest-growing areas for real estate development in recent years. As new projects pop up, the demand for trustworthy land investments rises sharply. In such a bustling market, finding RERA Approved Plots in Mysore Road is more crucial than ever. KSquareHomes has established itself as a top choice for investors seeking safe, legal, and well-planned plots on Mysore Road. If you're serious about investing, this guide will show you everything you need to know about RERA-approved plots at KSquareHomes.
Understanding RERA and Its Significance in Real Estate
What is RERA?
RERA, or the Real Estate Regulatory Authority, is a government body created to regulate the property market. Its main goal is to make buying and selling land clear and fair. RERA ensures developers follow strict rules, so buyers are protected from fraud and scams.
Why is RERA approval important for plots?
When a plot is RERA-approved, it means the land has gone through legal checks. Buyers get a guarantee that the land’s ownership is clear and free from disputes. It also helps streamline the entire buying process, making it faster and safer.
RERA Compliance Statistics
Across India, more projects are registering under RERA. In 2023 alone, over 60% of new real estate projects became RERA-approved. This trend boosts buyer confidence, making the property market more stable and predictable.
Advantages of Investing in RERA Approved Plots at Mysore Road KSquareHomes
Legal Security and Ownership Clarity
With RERA approval, your land comes with a clear title. All legal documents are verified, so there's no risk of future ownership issues. This type of security ensures your investment is safe.
Quality Assurance and Developer Credibility
KSquareHomes works with trusted developers who have a good track record. These builders follow strict legal and construction standards, ensuring high quality. Their past projects speak for themselves, providing peace of mind to buyers.
Financial Benefits
Since RERA-approved plots have transparent pricing, there are no hidden costs. Banks are also more comfortable offering loans for such land, making financing easier and smoother.
Long-term Investment Potential
Mysore Road is poised for growth. Upcoming infrastructure like new roads, metro lines, and shopping centers promise to increase land value over time. Investing now means you could see substantial returns in the future.
Why Choose KSquareHomes for Your RERA Approved Plot in Mysore Road
Prime Location Features
KSquareHomes is strategically located near key transport links, including major highways and upcoming metro stations. Its closeness to schools, hospitals, and shopping areas makes it an attractive choice for residents and investors alike.
Developer's Reputation and Past Projects
The developers behind KSquareHomes have a proven track record. Multiple successful projects and satisfied clients highlight their dedication to quality and transparency. Customer testimonials confirm the reliability of their investments.
Features of KSquareHomes Plots
Plots come in various sizes, from compact to sprawling, catering to different needs. The development plans include wide roads, green parks, security systems, and modern infrastructure to enhance living quality.
Certification and Compliance
Every plot at KSquareHomes has passed RERA registration and compliance checks. All legal papers, including land titles and approvals, are transparent and available for review, making sure your purchase is secure.
How to Verify RERA Approval and Invest Confidently
Step-by-step Guide to Check RERA Registration
Start by visiting the official RERA website for your state. Look up the project name or developer and verify its registration number. Confirm that the project status is active and compliant.
Important Documents to Request
Always ask for the RERA registration certificate, the land's title deed, and recent land approvals. These documents prove the land’s legal authenticity and protect your investment.
Tips for a Smooth Investment Process
Work with certified legal experts who can review documents and contracts. Always visit the site before buying to see the land and development progress. Read payment schedules carefully and understand all clauses in your agreement.
Future Development and Market Trends on Mysore Road
Upcoming Infrastructure Projects
Plans include the expansion of the metro line, new expressways, and industrial zones. These projects will connect Mysore Road better and boost property prices significantly.
Market Growth Data
Recent sales data show property prices along Mysore Road increased by 15% in the past two years. Experts predict this trend will continue, driven by infrastructure development and urban growth.
Investment Opportunities
Short-term investors might focus on quick resale or rental income, while long-term investors see bigger gains as infrastructure projects mature. Rental demand is also rising, making leasing a promising option.
Conclusion
Investing in RERA-approved plots at KSquareHomes in Mysore Road offers safety, transparency, and great long-term potential. Verifying legal documents and choosing trusted developers makes a difference. With rising infrastructure and market confidence, now is the perfect time to explore authorized listings. Contact reliable real estate experts today and take a step toward secure property investment on Mysore Road.
0 notes
Text
Cybersecurity and Active Protection Systems: Navigating Market Trends and Challenges

The global defense sector is undergoing a significant transformation, driven by advancements in technology and the rising complexity of modern warfare. Among the critical areas of focus is the integration of Active Protection Systems (APS) into military platforms such as armored vehicles, naval vessels, and aircraft. APS are designed to protect these assets from incoming threats like missiles and projectiles by detecting and neutralizing them before they can cause harm. As these systems become more sophisticated and connected, they also become increasingly vulnerable to cyber-attacks. This vulnerability has put a spotlight on the cybersecurity of APS, a crucial aspect that is now driving significant market trends within the industry.
Market Size and Growth Dynamics
The Active Protection System Market is projected to grow from USD 3.9 Billion in 2022 to USD 5.2 Billion by 2027, at a Compound Annual Growth Rate (CAGR) of 5.5% during the forecast period. This growth is largely attributed to the increasing adoption of APS by military forces worldwide, driven by the need for enhanced protection of critical assets in hostile environments. As the deployment of APS expands, so does the exposure to cyber threats, necessitating robust cybersecurity measures.
The rising number of cyber-attacks targeting defense systems is a significant driver of growth in the cybersecurity segment of the APS market. According to recent market statistics, there has been a marked increase in the frequency and sophistication of cyber-attacks on military systems. In fact, between January 2022 and June 2022, there were over 65 reported cyber-attacks on government agencies worldwide, many of which targeted defense networks. This growing threat has made cybersecurity a top priority for governments and defense contractors, leading to substantial investments in securing APS from cyber threats.
Get a Deeper Understanding of the Industry by Visiting: https://www.marketsandmarkets.com/Market-Reports/active-protection-system-market-5804076.html
Industry Trends: The Convergence of Cybersecurity and Active Protection Systems
The integration of cybersecurity into APS is not just a reactive measure but is becoming a proactive strategy to ensure the reliability and effectiveness of these systems. Several key trends are shaping the cybersecurity landscape within the APS industry:
Advanced Threat Detection and Response Mechanisms:
Modern APS are increasingly equipped with sophisticated threat detection technologies, such as digital radar processors, optoelectronic sensors, and thermal imaging devices. These technologies enhance the system's ability to identify and neutralize incoming threats. They also create potential entry points for cyber-attacks. To mitigate this risk, manufacturers are integrating advanced cybersecurity protocols that monitor system integrity in real-time, detect anomalous behavior, and initiate automated countermeasures against potential cyber intrusions.
Secure Communication Networks:
The effectiveness of APS heavily relies on the seamless communication between sensors, processors, and countermeasure systems. This interconnectedness, however, presents a vulnerability that cyber adversaries can exploit. As a result, the industry is witnessing a shift towards the development of secure communication networks that are resistant to jamming, interception, and unauthorized access. These networks utilize encryption, frequency hopping, and other security measures to ensure that data transmitted within the APS remains confidential and tamper-proof.
Integration of Artificial Intelligence (AI) and Machine Learning (ML):
AI and ML are playing an increasingly vital role in enhancing the cybersecurity of APS. These technologies enable the systems to learn from past incidents, identify emerging threats, and adapt to new attack vectors. AI-driven cybersecurity solutions can predict potential vulnerabilities within the APS and autonomously deploy patches or reconfigure the system to counteract the identified risks. This trend towards AI-enhanced cybersecurity is expected to become a standard feature in next-generation APS.
Compliance with International Cybersecurity Standards:
The global nature of military operations necessitates that APS meet stringent cybersecurity standards that are recognized internationally. Defense organizations are now mandating compliance with frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework, ISO/IEC 27001, and the European Union Agency for Cybersecurity (ENISA) guidelines. Adherence to these standards ensures that APS are designed, developed, and deployed with cybersecurity as a foundational element, reducing the risk of compromise during operations.
Collaboration Between Defense Contractors and Cybersecurity Firms:
Recognizing the growing importance of cybersecurity, defense contractors are increasingly partnering with specialized cybersecurity firms. These collaborations aim to integrate cutting-edge cybersecurity technologies into APS, leveraging the expertise of cybersecurity companies to address specific vulnerabilities. This trend is fostering innovation and leading to the development of more resilient APS that can withstand sophisticated cyber-attacks.
Get Thorough Information in Our PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=5804076
Market Challenges and Opportunities
While the integration of cybersecurity into APS presents numerous opportunities, it also comes with challenges that the industry must address to ensure the continued growth of the market.
Challenges:
High Development and Implementation Costs:
One of the primary challenges facing the APS market is the high cost associated with developing and implementing advanced cybersecurity solutions. The complexity of modern APS, coupled with the need for rigorous testing and validation of cybersecurity measures, drives up costs. This challenge is particularly pronounced for smaller defense contractors and nations with limited defense budgets, which may struggle to afford the latest cybersecurity technologies.
Rapidly Evolving Cyber Threat Landscape:
The cyber threat landscape is continuously evolving, with adversaries constantly developing new methods to breach defense systems. This dynamic environment requires APS manufacturers to stay ahead of emerging threats by continuously updating their cybersecurity measures. This need for ongoing innovation can strain resources and create challenges in maintaining the cybersecurity of APS over their lifecycle.
Interoperability and Standardization Issues:
As APS are deployed across various platforms and integrated with different systems, ensuring interoperability while maintaining robust cybersecurity can be challenging. Differences in standards, protocols, and technologies across platforms can create vulnerabilities that adversaries may exploit. Addressing these interoperability issues is critical to the success of cybersecurity efforts in the APS market.
Discover All the Steps in Our Detailed Sample: https://www.marketsandmarkets.com/requestsampleNew.asp?id=5804076
Opportunities:
Rising Demand for Cybersecurity Expertise:
The growing focus on cybersecurity within the APS market presents significant opportunities for cybersecurity firms. Defense contractors are increasingly seeking partnerships with cybersecurity experts to enhance the resilience of their systems. This demand is expected to drive growth in the cybersecurity sector, particularly in areas such as secure communications, threat detection, and AI-driven cybersecurity solutions.
Government Initiatives and Funding:
Governments worldwide are recognizing the importance of cybersecurity in defense and are providing funding and support for the development of secure APS. The U.S. Department of Defense (DoD) has launched initiatives aimed at strengthening the cybersecurity of military systems, including APS. These government-led efforts are expected to create a favorable environment for innovation and investment in cybersecurity solutions for the APS market.
Expansion into Emerging Markets:
As emerging economies invest in modernizing their military capabilities, there is a growing opportunity for APS manufacturers to expand into these markets. Countries in Asia, the Middle East, and Latin America are increasingly adopting APS to protect their armored fleets, creating new demand for cybersecurity solutions tailored to the needs of these regions. Manufacturers that can offer cost-effective, scalable, and secure APS are well-positioned to capitalize on this growing demand.
Top 5 Key Market Players in Active Protection System Market:
The Active Protection System Companies is dominated by globally established players such as
Rheinmetall AG (Germany),
Saab AB (Sweden),
Raytheon Company (US),
Airbus (Netherlands), and
ASELSAN AS (Turkey)
The convergence of cybersecurity and active protection systems represents a significant evolution in the defense industry. As the global threat landscape becomes increasingly complex, the need for secure, resilient, and adaptable APS has never been greater. The market statistics indicate robust growth in the APS market, driven by the rising demand for advanced protection solutions in an era of cyber warfare.
While challenges such as high costs and the evolving nature of cyber threats present hurdles, the opportunities for innovation, collaboration, and expansion are substantial. The continued investment in cybersecurity by both governments and private sector players will be crucial in ensuring that APS can effectively protect military assets from both physical and cyber threats. As the industry moves forward, the integration of cybersecurity into APS will become a defining characteristic of next-generation defense systems, safeguarding them against the growing threat of cyber-attacks.
About MarketsandMarkets™
MarketsandMarkets™ has been recognized as one of America's best management consulting firms by Forbes, as per their recent report.
MarketsandMarkets™ is a blue ocean alternative in growth consulting and program management, leveraging a man-machine offering to drive supernormal growth for progressive organizations in the B2B space. We have the widest lens on emerging technologies, making us proficient in co-creating supernormal growth for clients.
Earlier this year, we formally transformed into one of America's best management consulting firms as per a survey conducted by Forbes.
The B2B economy is witnessing the emergence of $25 trillion of new revenue streams that are substituting existing revenue streams in this decade alone. We work with clients on growth programs, helping them monetize this $25 trillion opportunity through our service lines - TAM Expansion, Go-to-Market (GTM) Strategy to Execution, Market Share Gain, Account Enablement, and Thought Leadership Marketing.
Built on the 'GIVE Growth' principle, we work with several Forbes Global 2000 B2B companies - helping them stay relevant in a disruptive ecosystem. Our insights and strategies are molded by our industry experts, cutting-edge AI-powered Market Intelligence Cloud, and years of research. The KnowledgeStore™ (our Market Intelligence Cloud) integrates our research, and facilitates analysis of interconnections through applications, helping clients look at the entire ecosystem and understand the revenue shifts in their industry.
To learn more, visit www.MarketsandMarkets™.com or follow us on Twitter, LinkedIn and Facebook.
Contact: Mr. Rohan Salgarkar MarketsandMarkets™ INC. 630 Dundee Road Suite 430 Northbrook, IL 60062 USA: +1-888-600-6441 Email: [email protected]
#Active Protection System#Active Protection System Market#Active Protection System Industry#Global Active Protection System Market#Active Protection System Market Companies#Active Protection System Market Size#Active Protection System Market Share#Active Protection System Market Growth#Active Protection System Market Statistics
0 notes
Text

NFT Marketplace Development: 7 Important Features and Functions
In today’s digital age, creating a space where creators and collectors can connect makes all the difference. As an NFT Marketplace development company, we understand how vital it is to blend user-friendly design with powerful features. Whether you’re just starting or looking to elevate your existing platform, this guide will walk you through the essential steps and considerations for successful NFT marketplace development.
NFT Market Growth and Statistics
NFT marketplace development is more important than ever. In 2021, sales on major NFT platforms topped $17 billion, and by 2024, niche markets—like sports collectibles—were growing at 10–15% monthly. A foundation NFT marketplace model that supports emerging creators can drive community engagement by up to 40% within six months. These numbers prove that investing in a well-built NFT marketplace not only captures attention but also delivers real value.
Global NFT Sales (2021): $17 billion
Monthly Growth in Niche Markets (2024): 10–15%
Community Engagement Increase (Foundation NFT Marketplace): 40% in six months
What is NFT Marketplace Development
At its core, an NFT marketplace is a digital platform where users can mint, buy, sell, and trade non-fungible tokens. These marketplaces rely on blockchain technology to verify ownership and ensure authenticity. Whether you choose a public blockchain like Ethereum or a faster alternative, your platform should make it easy for users to connect their wallets, explore digital assets, and finalize transactions. By offering a clear, intuitive interface—paired with reliable back-end support—you create a space where users feel confident engaging with digital art, music, or any other tokenized asset.
7 Essential Features of Successful NFT Marketplaces
To stand out, your NFT marketplace must offer several key functions. Below are the seven essential features every top platform needs:
1. Advanced Search and Filters for Precise Results
Users expect to find exactly what they want—fast. With smart filters (by price, category, creator, or date added) and an intuitive search bar that suggests keywords, buyers can quickly narrow down their options. Integrating these tools is a core part of nft marketplace development that boosts user satisfaction and retention.
2. Diverse Trading Options to Cater to User Preferences
Every collector has a different buying style. Some prefer fixed-price sales, others enjoy timed auctions or bundle deals. By offering multiple trading formats—like “buy now,” English auctions, or Dutch auctions—you create a flexible ecosystem that appeals to a wider audience. These options help your platform expand and keep users actively involved.
3. Secure Wallet Integration for Safe Cryptocurrency Storage
Connecting wallets should be seamless and secure. Popular options like MetaMask, WalletConnect, and Coinbase Wallet must integrate smoothly so users can check balances, approve transactions, and store NFTs safely. Employing strong encryption and best practices in key management ensures user funds remain protected, which is crucial for building trust in your nft marketplace development services.
4. Real-time Listing Status Indicators for Enhanced Transparency
Nothing frustrates buyers more than discovering an auction has ended mid-bid. Real-time status updates—showing whether a listing is active, pending, sold, or canceled—keep everyone informed. Live countdown timers, instant bid updates, and notifications about new listings all contribute to a transparent, engaging experience.
5. Ratings and Review System: Building Trust Within the Community
Reputation is everything in online marketplaces. A built-in ratings and review system lets buyers rate sellers (and vice versa) based on past transactions. Displaying these ratings prominently helps newcomers feel confident purchasing from trusted creators. Showcasing “top seller” badges and spotlighting five-star feedback encourages positive engagement and enhances your NFT marketplace’s value.
6. Strong Security Measures to Protect User Data and Transactions
User safety is non-negotiable. Using two-factor authentication, SSL encryption, and thoroughly reviewed smart contracts helps stop fraud and keep unauthorized users out. Offering bug bounty programs and regular security audits guards against hacking attempts and smart contract exploits. As a dedicated NFT marketplace development company, we prioritize these measures to keep your users’ data and funds safe.
7. User-friendly Dashboard and Analytics for Creators and Collectors
Creators and collectors want insight into their performance. A simple dashboard that shows earnings, sale history, and trending NFTs makes it easier for users to make informed decisions. Including basic analytics—like views per listing, top-performing categories, or average sale price—adds significant value and encourages repeat engagement on your platform.
Choosing the Right Development Approach for Your NFT Marketplace
When it comes time to build, you have multiple paths: using a white-label solution, customizing an open-source framework, or developing a fully bespoke platform from scratch. Each approach has pros and cons:
White-Label Solutions Quick to launch and cost-effective, but can be less flexible.
Open-Source Frameworks High flexibility for tailoring your platform, but it demands strong internal development skills..
Custom Development from Scratch Maximum flexibility and unique branding, but often involves higher upfront costs and longer timelines.
As a dedicated NFT marketplace development company, our team excels at all three approaches. We begin by understanding your goals—whether you need a lean entry-point with a foundation nft marketplace or a fully branded experience with exclusive features. From there, we design a clear roadmap: wireframes, UI/UX mock-ups, smart contract development, and rigorous testing.
Why Choose Us for Your Project?
Our NFT marketplace development company offers end-to-end nft marketplace development services tailored to your needs. Here’s why clients trust us:
Proven Expertise We’ve launched high-traffic platforms with robust features—everything from advanced filters to secure wallet integrations.
Custom Solutions Whether you need a foundation NFT marketplace for emerging artists or a fully branded enterprise-level site, we tailor each feature to your vision.
Security-First Mindset We build on best practices—SSL encryption, audited smart contracts, and 2FA—to protect user data and assets.
Ongoing Support We don’t disappear after launch. Our team provides continuous updates, performance monitoring, and feature enhancements to ensure your marketplace thrives.
By choosing Justtry Technologies, you gain a partner dedicated to maximizing your nft marketplace value while delivering a seamless user experience.
Conclusion
In today’s competitive market, a well-built NFT marketplace can make all the difference. From enhancing discoverability with advanced search tools to securing transactions through top-notch wallet integration, every feature contributes to a thriving community. At Justtry Technologies, we blend cutting-edge technology with humanized design to help you capture market share and boost long-term growth. Ready to elevate your platform? Contact us to start building the next generation of NFT marketplaces. NFT marketplace development company
#NFT Marketplace development company#nft marketplace development#nft marketplace development services#nft marketplace value#foundation nft marketplace
0 notes
Text
Best trader on the NYSE: The Data-Driven Solution for Frustrated Traders
Best trader on the NYSE: The Data-Driven Solution for Frustrated Traders
Are you tired of chaotic trades and unpredictable losses? Discover how the Best trader on the NYSE leverages proven data and clear systems to achieve steady, reliable gains—even in turbulent markets.
Why Consistency Beats Complexity
Studies show that over 75% of active traders underperform the S&P 500. The Best trader on the NYSE uses a streamlined, rules-based approach—not complicated algorithms or hunches. This system prioritizes clarity, helping you avoid analysis paralysis and focus on what works. Simplicity isn’t just easier—it’s statistically superior for long-term success.
Historical Performance Speaks Volumes
According to NYSE data, consistent strategy outperforms reactive trading by 38%. The Best trader on the NYSE relies on backtested models spanning decades, ensuring every move is grounded in historical reliability. When your trades echo past winners, you’re stacking the odds in your favor. Let the numbers guide your next decision.
The Power of Actionable Signals
Instead of chasing rumors or news spikes, actionable signals filter noise from opportunity. The Best trader on the NYSE uses clear entry and exit signals based on quantifiable metrics. For example, a simple moving average crossover system can increase win rates by 23%. With this, you’ll trade with confidence—not guesswork.
Risk Management: The Hidden Edge
Even the Best trader on the NYSE respects risk. Effective risk management—like strict stop-losses and position sizing—reduces drawdowns and protects capital. Research shows disciplined risk controls can cut losses in half during volatile periods. This edge ensures you stay in the game and thrive, not just survive.
Transform Frustration Into Consistent Wins
If you’ve struggled to find consistency, you’re not alone. The Best trader on the NYSE was once frustrated, too. By adopting a practical, data-driven system, they turned losses into steady growth. Ready to join them? Start with a system proven by both the numbers and real traders.
Embrace a rules-based, historical approach
Use actionable signals, not speculation
Protect your capital with disciplined risk management
Consistency is within reach. Discover what the Best trader on the NYSE knows—and take control of your trading journey today. Ready to trade smarter?
How do I start trading like the Best trader on the NYSE?
Begin by studying proven, backtested strategies with clear rules. Focus on one system, track your progress, and adjust based on data—not emotion. Consistency is key.
What tools does the Best trader on the NYSE use?
They rely on data-driven indicators like moving averages, time-tested models, and strict risk controls. Most importantly, they avoid overcomplicating and stick to what works.
What’s your biggest trading frustration? Share your story below, reblog if you relate, and let’s help each other achieve consistency in the markets!
0 notes
Text
uCloud Nulled Script 2.1.1

Unlock Premium File Hosting with uCloud Nulled Script Looking for a powerful and secure file hosting solution without the hefty price tag? The uCloud Nulled Script is your ultimate answer. This premium PHP script offers a robust, scalable, and user-friendly platform to upload, manage, preview, and share files with ease. Whether you're a developer, business owner, or tech enthusiast, this nulled version gives you full access to all premium features—completely free. What is uCloud Nulled Script? uCloud Nulled Script is a feature-rich file hosting PHP script originally developed to provide seamless file management in a secure environment. By using the nulled version, you bypass costly licenses while still enjoying top-tier functionality. Designed for optimal performance and user experience, this script is perfect for individuals and businesses alike who need a professional-grade file hosting service. Technical Specifications Script Type: PHP file hosting platform Database Support: MySQL File Types Supported: Documents, videos, images, archives, and more Responsive Design: Fully mobile-optimized Admin Dashboard: Complete user and file management capabilities Security: SSL support, password protection, and more Features and Benefits of uCloud Nulled Script With the uCloud Nulled Script, you get a premium suite of tools designed to streamline your file hosting operations: Drag-and-Drop Upload: Easily upload files with a simple drag-and-drop interface. Advanced User Management: Create and manage user accounts, set permissions, and monitor usage. Real-Time Statistics: Monitor file downloads, storage usage, and traffic with real-time analytics. Cloud Storage Integration: Connect with cloud services for scalable file storage. Password Protection: Secure files with optional password-protection features. Email Notifications: Automatic email alerts for uploads, downloads, and activity logs. Who Can Benefit from uCloud Nulled Script? This versatile script caters to a wide audience: Web Developers: Integrate file sharing into custom web projects effortlessly. Small Businesses: Share documents, training materials, and resources securely with staff and clients. Digital Marketers: Distribute media files, PDFs, and promotional content with tracking features. Educational Institutions: Offer study materials and resources to students in an organized system. How to Install uCloud Nulled Script Installing the uCloud Nulled Script is a breeze with just a few simple steps: Download: Get the script files from our website. Upload: Use an FTP client to upload the script to your server. Setup: Create a MySQL database and run the setup wizard included in the package. Customize: Access the admin panel to personalize settings, manage users, and configure features. Why Choose the Nulled Version? By choosing the uCloud Nulled Script, you unlock premium capabilities without paying a dime. Enjoy full access to all features, regular updates, and enhanced flexibility to modify the code as needed. This version is ideal for developers and users who want the best file hosting experience without the restrictions of licensing fees. FAQs Is the uCloud Nulled Script safe to use? Yes, we ensure all scripts are thoroughly scanned and tested for security before sharing. However, we always recommend installing on a secure server. Can I customize the script? Absolutely. The script is open-source and fully customizable. You can tweak it to fit your branding or add new features as required. Does it support mobile devices? Yes, uCloud is built with a responsive design that works flawlessly on smartphones, tablets, and desktops. Final Thoughts Don’t miss out on this opportunity to supercharge your file hosting solution. The uCloud combines top-tier functionality with the flexibility and freedom of open access. Whether you're launching a new project or upgrading an existing system, this script delivers unmatched value—completely free.
Looking for more tools? Check out our elementor nulled pro plugin to enhance your WordPress designs effortlessly. Want a premium WordPress theme at zero cost? Don’t miss the flatsome NULLED theme for advanced customization options.
0 notes
Text
𝐂𝐡𝐨𝐨𝐬𝐢𝐧𝐠 𝐭𝐡𝐞 𝐑𝐢𝐠𝐡𝐭 𝐌𝐞𝐝𝐢𝐜𝐚𝐥 𝐃𝐞𝐯𝐢𝐜𝐞 𝐂𝐑𝐎: 𝟕 𝐊𝐞𝐲 𝐅𝐚𝐜𝐭𝐨𝐫𝐬 𝐭𝐨 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫
Bringing a new medical device to market is an ambitious task. Along with innovation and engineering skill, you need airtight clinical data, an iron‑clad regulatory strategy, and expert project management. That’s why many companies, start‑ups, and global giants turn to a Medical Device CRO for help. A CRO can shorten timelines, control costs, and guide your product safely through the complexity of international regulations.
Still, not every contract research organization is right for every project. The wrong partnership can lead to delays, budget overruns, or missed regulatory milestones. To help you choose wisely, here are seven key factors you should weigh before signing any agreement.
Factors to Consider for the Right Medical Device CRO
1. Specialized Experience in Medical Devices
Clinical research for drugs and clinical research for devices are two different worlds. Devices often involve engineering changes mid‑study, unique usability endpoints, and combination products that challenge traditional trial designs. Ask potential partners:
How many device studies have you managed in the past five years?
Which therapeutic areas and device classes do you know best?
Can you provide case studies with successful regulatory approvals?
Look for a medical device CRO that understands device‑specific nuances, from design validation to post‑market surveillance.
2. Regulatory Expertise in Your Target Markets
A promising prototype is only half the battle; regulators decide when you can sell it. Each region has its own rules. Assess your CRO’s regulatory track record:
Up‑to‑date knowledge: Do they track evolving guidance documents and standards?
Submission success: What is their history?
Strategic planning: Can they map a step‑by‑step pathway, indicate the best predicate, and foresee data gaps?
A CRO with seasoned regulatory consultants can shave months off your approval timeline.
3. Global Site Network and Investigational Relationships
The best study design fails without capable investigators. Confirm that the CRO has:
Broad site reach: Established contacts in hospitals, specialty clinics, and academic centers across key regions.
Performance metrics: Data on each site’s enrollment speed, protocol compliance, and retention rates.
Backup options: A plan to activate alternate sites if the primary ones underperform.
Strong site management keeps enrollment on schedule and protects your budget.
4. Flexible Trial Design and Risk Management
Medical devices evolve quickly. You may tweak firmware or improve a catheter coating mid‑trial. Does the CRO have processes to:
Implement design changes: Rapidly changing protocols and communicating updates to sites and authorities.
Manage risk: Use real‑time data monitoring, adaptive designs, or Bayesian statistics to reduce sample sizes.
Mitigate supply chain issues: Handle recalls or production without disrupting the study.
Flexibility is vital when technology advances faster than paperwork.
5. Data Quality and Integrated Technology Platforms
Impressive data is your passport to the market. Investigate the CRO’s digital ecosystem:
Electronic data capture (EDC): Does it integrate with imaging, wearable sensors, or connected devices?
Real‑time dashboards: Can you track enrollment, adverse events, and data queries at a glance?
Cybersecurity: Compliant encryption and validated systems keep patient data safe.
A strong tech backbone accelerates cleaning and analysis, turning raw numbers into regulatory‑grade evidence.
6. Transparent Budgeting and Cost Control
Hidden fees drop many projects. Ask for a detailed budget model that covers:
Start‑up costs: Research submissions, site contracts, device shipping.
Variable costs: Per‑patient payments, monitoring visits, and data queries.
Change‑order policy: What happens if the timeline extends or the scope expands?
A trustworthy Medical Device CRO will walk you through each line item and offer contingency plans instead of surprises.
7. Cultural Fit and Communication Style
Even the most qualified CRO can disappoint if communication breaks down. During your selection process:
Meet the team: It is not just sales representatives; insist on speaking with the project manager and lead monitor.
Decision‑making process: Know who resolves issues and approves changes.
Projects run smoother when the CRO’s style meshes with yours—open, responsive, and proactive.
The Bottom Line
Selecting a CRO is one of the most critical choices you will make on the road to commercialization. A well‑matched partner keeps studies on track, controls budgets, and satisfies regulators. Use the seven factors above as your checklist, and you’ll dramatically improve your odds of success.
When you find a CRO that combines deep device know‑how, global reach, robust data systems, and clear communication, you’ve struck the research equivalent of gold. bioaccess® partnership won’t just move your device across the finish line—it will get it into the hands of clinicians and patients who need it most.
0 notes
Text
Why Cybersecurity is the Hottest Job of the Decade
In this age of digital-first, when ransomware, data breaches, and cyber scams make headlines nearly every day, there's one profession that has emerged as both a defense perimeter and a golden career opportunity: cybersecurity.
Whether you're a fresh graduate looking for a bright career or a career professional looking for a satisfying career change, the demand for trained cybersecurity professionals is not a trend it's a revolution. And right now, there's no better time or place to begin than with a Cyber Security Course in Kochi.
A Crisis of Security Triggers a Job Boom
Companies are most susceptible to such types of cyberattacks since more and more of their activities become digital. According to a recent Cybersecurity Ventures estimate, cybercrime will cause the world to spend more than $10.5 trillion by 2025.
Enter: cybersecurity professionals.
From penetration testers and ethical hackers to compliance officers and security analysts the market for jobs is hot. The U.S. Bureau of Labor Statistics estimates a 35% increase in cybersecurity employment by 2031—far higher than the overall occupation average.
More Than IT: A Mission-Driven Career
Cybersecurity is now more than an IT profession; it's a front-line protection of privacy, national security, and digital liberty. These are not technicians who simply fix systems—they are the protectors of individuals, businesses, and governments against unseen threats.
It's this mix of purpose challenge and opportunity that makes cybersecurity so appealing. The job is extremely stimulating constantly changing and extremely rewarding—both personally and financially.
Why Study Cybersecurity in Kochi
Kochi, or more commonly referred to as the "Silicon Valley of Kerala" has turned into a hub of technological innovation and learning. With its expanding cluster of IT firms and startups, Kochi provides experiential learning and placement opportunities that are not readily available elsewhere.
A well structured Cyber Security Course in Kochi not only gives you hands-on knowledge but also gets you in touch with an active industry network. You'll get hands-on experience on tools like Wireshark, Kali Linux, and Metasploit and also prepare for industry certifications like CEH, CompTIA Security+, and CISSP.
Local training schools also prefer to collaborate with IT companies for live projects and internships which give you a clear edge in the marketplace.
The Time to Act Is Now Cybersecurity is not the future—it's here. And the need for talent continues to vastly outweigh supply. If you're motivated by the money, the cause, or the ability to shake things up, this industry has it all. And so if you wish to build a future-proof profession within one of the most exciting and in-demand sectors of the present, enrolling in a Cyber Security Course in Kochi could be your best move so far.
https://offensoacademy.com/
1 note
·
View note