#Advanced security features including DDoS protection and Web Application Firewall (WAF).
Explore tagged Tumblr posts
Text
WP Engine is a well-known managed WordPress hosting provider.
It offers a range of features and services tailored specifically for WordPress websites, making it a popular choice among businesses, bloggers, and developers who seek reliable, high-performance hosting solutions.

#Managed WordPress Hosting:#security#and reliability.#automated updates#and staging environments.#Genesis Framework and StudioPress Themes:#Access to the Genesis Framework for building fast#secure#and SEO-friendly websites.#Includes over 35 StudioPress themes for customization and design flexibility.#Global Edge Security:#Advanced security features including DDoS protection and Web Application Firewall (WAF).#Managed threat detection and prevention.#Content Performance:#Tools and analytics to measure and optimize content performance.#Helps improve site speed and SEO rankings.#Dev#Stage#Prod Environments:#Separate development#staging#and production environments for better workflow management.#Allows for testing changes before pushing them live.#Automated Migrations:#Easy migration tools to transfer existing WordPress sites to WP Engine.#Assisted migrations for a smoother transition.#24/7 Customer Support:
0 notes
Text
The Future of Web Security with AWS Web Application Firewall
In an era of increasing cyber threats, protecting web applications has become a priority for businesses of all sizes. AWS Web Application Firewall is a powerful tool designed to safeguard web applications from common exploits and vulnerabilities. This comprehensive guide will explore key aspects of AWS WAF, helping you understand its benefits, configuration, and integration for optimal security.
The Basics of AWS Web Application Firewall
AWS Web Application Firewall is a security service offered by Amazon Web Services that protects web applications from threats such as SQL injection, cross-site scripting, and other malicious attacks. It allows users to create customizable security rules to filter incoming traffic based on specific patterns and behaviors.
Key Features of AWS Web Application Firewall
AWS WAF provides several powerful features including IP address filtering, rate-based rules, and AWS Managed Rules. These managed rule sets are pre-configured to protect against common threats, reducing the time required to implement effective security measures. With detailed logging and monitoring, AWS WAF enables administrators to analyze and respond to suspicious activity in real time.
Setting Up AWS Web Application Firewall for Your Web Application
Deploying AWS WAF involves creating a Web ACL (Access Control List) and associating it with AWS resources such as Amazon CloudFront, Application Load Balancer, or Amazon API Gateway. You can define custom rules or use managed rulesets based on your application’s needs. Configuring rule priority ensures the most important rules are applied first, making security management more efficient.
Benefits of Using AWS Web Application Firewall for Businesses
Implementing AWS WAF offers significant advantages, including improved protection against automated attacks, reduced downtime, and better user experience. Its ability to scale automatically with traffic ensures that security measures remain consistent regardless of user load. Additionally, centralized management simplifies administration for organizations with multiple applications.
Common Use Cases for AWS Web Application Firewall
Businesses use AWS WAF in a variety of scenarios such as blocking bad bots, mitigating DDoS attacks, and enforcing access control. E-commerce platforms, financial services, and healthcare applications frequently rely on AWS WAF to maintain the confidentiality, integrity, and availability of sensitive data.
Integrating AWS Web Application Firewall with Other AWS Services
One of the key strengths of AWS WAF is its seamless integration with other AWS services. For example, pairing it with AWS Shield enhances protection against DDoS attacks, while integration with Amazon CloudWatch provides advanced logging and alerting. Combining AWS WAF with AWS Lambda allows for automated response to detected threats.
Monitoring and Optimizing AWS Web Application Firewall Performance
Regularly reviewing logs and rule performance is essential for maintaining effective security. AWS WAF provides metrics through Amazon CloudWatch, enabling real-time tracking of blocked requests, rule match counts, and overall traffic trends. Adjusting rules based on this data helps fine-tune protection and maintain application performance.
Conclusion
AWS Web Application Firewall is a crucial component in modern web security. With its customizable rules, managed rule sets, and seamless integration with AWS services, it offers a scalable and effective solution for protecting web applications. By implementing AWS WAF, organizations can proactively defend against evolving threats and ensure a secure digital experience for their users.
0 notes
Text
The Power of Amazon Web Services (AWS): A Detailed Guide for 2025
Amazon Web Services (AWS) is the leading cloud computing platform, providing a wide range of services that empower businesses to grow, innovate, and optimize operations efficiently. With an increasing demand for cloud-based solutions, AWS has become the backbone of modern enterprises, offering high-performance computing, storage, networking, and security solutions. Whether you are an IT professional, a business owner, or an aspiring cloud architect, understanding AWS can give you a competitive edge in the technology landscape.
In this blog we will guide and explore AWS fundamentals, key services, benefits, use cases, and future trends, helping you navigate the AWS ecosystem with confidence.
What is AWS?
Amazon Web Services (AWS) is a secure cloud computing platform that provides on-demand computing resources, storage, databases, machine learning, and networking solutions. AWS eliminates the need for physical infrastructure, enabling businesses to run applications and services seamlessly in a cost-effective manner.
With over 200 fully featured services, AWS powers startups, enterprises, and government organizations worldwide. Its flexibility, scalability, and pay-as-you-go pricing model make it a preferred choice for cloud adoption.
Key AWS Services You Must Know
AWS offers a vast range of services, categorized into various domains. Below are some essential AWS services that are widely used:
1. Compute Services
Amazon EC2 (Elastic Compute Cloud): Provides resizable virtual servers for running applications.
AWS Lambda: Enables serverless computing, allowing you to run code without provisioning or managing servers.
Amazon Lightsail: A simple virtual private server (VPS) for small applications and websites.
AWS Fargate: A serverless compute engine for containerized applications.
2. Storage Services
Amazon S3 (Simple Storage Service): Object storage solution for scalable data storage.
Amazon EBS (Elastic Block Store): Persistent block storage for EC2 instances.
Amazon Glacier: Low-cost archival storage for long-term data backup.
3. Database Services
Amazon RDS (Relational Database Service): Fully managed relational databases like MySQL, PostgreSQL, and SQL Server.
Amazon DynamoDB: NoSQL database for key-value and document storage.
Amazon Redshift: Data warehousing service for big data analytics.
4. Networking and Content Delivery
Amazon VPC (Virtual Private Cloud): Provides a secure and isolated network in AWS.
Amazon Route 53: Scalable domain name system (DNS) service.
AWS CloudFront: Content delivery network (CDN) for fast and secure content delivery.
5. Security and Identity Management
AWS IAM (Identity and Access Management): Provides secure access control to AWS resources.
AWS Shield: DDoS protection for applications.
AWS WAF (Web Application Firewall): Protects applications from web threats.
6. Machine Learning & AI
Amazon SageMaker: Builds, trains, and deploys machine learning models.
Amazon Rekognition: Image and video analysis using AI.
Amazon Polly: Converts text into speech using deep learning.
Benefits of Using AWS
1. Scalability and Flexibility
AWS enables businesses to scale their infrastructure dynamically, ensuring seamless performance even during peak demand periods.
2. Cost-Effectiveness
With AWS's pay-as-you-go pricing, businesses only pay for the resources they use, reducing unnecessary expenses.
3. High Availability and Reliability
AWS operates in multiple regions and availability zones, ensuring minimal downtime and high data redundancy.
4. Enhanced Security
AWS offers advanced security features, including encryption, identity management, and compliance tools, ensuring data protection.
5. Fast Deployment
With AWS, businesses can deploy applications quickly, reducing time-to-market and accelerating innovation.
Popular Use Cases of AWS
1. Web Hosting
AWS is widely used for hosting websites and applications with services like EC2, S3, and CloudFront.
2. Big Data Analytics
Enterprises leverage AWS services like Redshift and AWS Glue for data warehousing and ETL processes.
3. DevOps and CI/CD
AWS supports DevOps practices with services like AWS CodePipeline, CodeBuild, and CodeDeploy.
4. Machine Learning and AI
Organizations use AWS AI services like SageMaker for building intelligent applications.
5. IoT Applications
AWS IoT Core enables businesses to connect and manage IoT devices securely.
Future Trends in AWS and Cloud Computing
1. Serverless Computing Expansion
More businesses are adopting AWS Lambda and Fargate for running applications without managing servers.
2. Multi-Cloud and Hybrid Cloud Adoption
AWS Outposts and AWS Hybrid Cloud solutions are bridging the gap between on-premise and cloud environments.
3. AI and Machine Learning Growth
AWS continues to enhance AI capabilities, driving innovation in automation and data processing.
4. Edge Computing Development
AWS Wavelength and AWS Local Zones will expand the reach of cloud computing to edge devices.
Conclusion
Amazon Web Services (AWS) is transforming how businesses operate in the digital era, providing unmatched scalability, security, and performance. Whether you are an enterprise looking to migrate to the cloud, a developer building applications, or a data scientist leveraging AI, AWS has a solution to your needs.
By mastering AWS, you can explore new career opportunities and drive business innovation. Start your AWS journey today and explore the limitless possibilities of cloud computing.
0 notes
Text
How HPE Load Balancer Enhances Network Security?
As cyber threats evolve, businesses need strong security measures to protect their digital assets. The HPE Load Balancer ensures secure and efficient network operations by optimizing traffic distribution and defending against cyber threats. It helps mitigate DDoS attacks, prevent unauthorized access, and maintain uptime. Edgenexus Limited specializes in deploying HPE Load Balancer solutions, helping businesses safeguard applications while enhancing performance. In this guide, we’ll explore how the HPE Load Balancer strengthens network security and why it’s essential for modern enterprises.
Understanding HPE Load Balancer
A HPE Load Balancer distributes incoming traffic across multiple servers, preventing overload and improving performance. It also enhances security by mitigating risks like unauthorized traffic spikes and potential breaches. The HPE Load Balancer integrates security features such as SSL offloading, access control, and application-layer protection. Edgenexus Limited helps businesses implement these solutions effectively, ensuring that networks remain secure and highly available in demanding environments.
How HPE Load Balancer Protects Against Cyber Threats?
Cyber threats such as SQL injection, malware, and brute-force attacks can compromise business networks. The HPE Load Balancer protects against these threats by analyzing incoming traffic and blocking malicious requests. It filters traffic based on security rules, reducing unauthorized access risks. With Edgenexus Limited, businesses can customize their HPE Load Balancer configurations to create a proactive security defense, ensuring only legitimate requests reach critical applications while malicious traffic is neutralized.
Preventing DDoS Attacks with HPE Load Balancer
DDoS attacks can cripple business operations by overwhelming servers with excessive traffic. The HPE Load Balancer mitigates these attacks by evenly distributing traffic and identifying unusual patterns indicative of an attack. It can limit requests from suspicious IP addresses, maintaining service availability. Edgenexus Limited provides expert deployment strategies, ensuring businesses stay protected from DDoS threats and can deliver uninterrupted online experiences even during high-traffic periods or attack attempts.
SSL Offloading and Secure Data Encryption
Encryption is a cornerstone of cybersecurity, and the HPE Load Balancer enhances security by managing SSL/TLS encryption processes. This reduces server load while ensuring encrypted data transmission. Offloading SSL decryption at the load balancer level allows businesses to conduct deep packet inspection for threats. Edgenexus Limited helps implement SSL offloading, ensuring businesses maintain high-security standards while optimizing performance and reducing latency in secure communications.
Access Control and Authentication Features
Unauthorized access to business networks can lead to data breaches. The HPE Load Balancer includes advanced access control mechanisms such as multi-factor authentication (MFA) and role-based access restrictions. These features ensure only verified users can access critical resources. Edgenexus Limited helps businesses configure access control policies, preventing unauthorized access and ensuring only legitimate traffic flows through the network while blocking security threats in real time.
Application Layer Security and Web Traffic Filtering
Attackers frequently target web applications with cross-site scripting (XSS), SQL injections, and malware. The HPE Load Balancer strengthens security by incorporating Web Application Firewall (WAF) features and content filtering to prevent such exploits. These measures block harmful traffic before reaching applications, significantly reducing security risks. Edgenexus Limited works with businesses to deploy these security features, ensuring that web applications remain protected from both automated and targeted cyber threats.
Monitoring, Logging, and Threat Analysis
Continuous network monitoring is essential for security and performance. The HPE Load Balancer includes logging and real-time monitoring features that provide visibility into network traffic and potential threats. These insights allow businesses to detect anomalies, troubleshoot issues, and respond to security incidents quickly. Edgenexus Limited helps organizations implement advanced monitoring strategies, enabling proactive threat detection and response to strengthen cybersecurity resilience.
Conclusion
The HPE Load Balancer is a powerful tool for enhancing network security, optimizing performance, and ensuring high availability. From preventing DDoS attacks to enforcing encryption and access controls, it offers comprehensive protection against cyber threats. Edgenexus Limited provides expert implementation and support, helping businesses fully leverage HPE Load Balancer technology. By integrating this solution, organizations can build a secure, resilient, and future-proof network infrastructure that meets the demands of modern digital environments.
0 notes
Text
https://www.sifytechnologies.com/cloud-services/cdn-services/

Sify’s CDN Services in India: Accelerating Digital Content Delivery
In an increasingly digital world, businesses are under constant pressure to deliver fast, seamless, and reliable online experiences to their users. From streaming media to e-commerce platforms, website performance can make or break a user’s interaction with a brand. Recognizing the critical need for speed and reliability, Sify offers cutting-edge Content Delivery Network (CDN) services across India, empowering businesses to deliver rich digital content swiftly and securely.
What is a CDN and Why is it Essential?
A Content Delivery Network (CDN) is a system of distributed servers that work together to deliver web content, such as HTML pages, images, videos, and scripts, more efficiently to users based on their geographic location. CDNs cache content at multiple points of presence (PoPs), reducing latency and ensuring that content is delivered from a server that is geographically closer to the end user.
In India, where the digital landscape is expanding rapidly, CDNs have become an essential tool for businesses seeking to provide high-performance, scalable content delivery. Sify’s CDN services are designed to meet the unique demands of India’s diverse internet users, ensuring seamless access to digital content, regardless of location or device.
Key Features of Sify’s CDN Services
1. Geographically Distributed PoPs
Sify’s CDN is powered by a network of strategically located PoPs across India and globally. This distribution allows for reduced latency and faster content delivery by ensuring users access content from the nearest server, whether they’re in a metropolitan city or a remote location.
2. Enhanced Scalability
As businesses grow, their need for scalable infrastructure becomes more critical. Sify’s CDN services offer unmatched scalability, allowing businesses to effortlessly handle traffic spikes during events like sales promotions, product launches, or viral content distribution. Whether serving millions of concurrent users or delivering high-resolution videos, Sify’s CDN ensures uninterrupted performance.
3. Low-Latency Content Delivery
Sify's CDN architecture is optimized for low-latency content delivery, ensuring that websites, applications, and media are served without delay. By leveraging advanced caching and compression technologies, Sify reduces load times and enhances user engagement, creating a superior browsing experience for customers across India.
4. Advanced Security
With an increase in cyber threats, Sify places a strong emphasis on security. Sify’s CDN services include robust security features such as DDoS protection, secure SSL/TLS encryption, and web application firewalls (WAF) to safeguard your content and user data from malicious attacks. This ensures that your digital assets remain secure while being delivered at top speed.
5. Optimized Video Streaming
For businesses in the media and entertainment sectors, delivering high-quality video content is essential. Sify’s CDN supports adaptive bitrate streaming (ABR), ensuring that users receive the best video quality based on their network conditions and device capabilities. This results in smooth video playback, reduced buffering, and an overall better user experience.
6. Real-Time Analytics
Sify’s CDN services provide detailed insights and real-time analytics on content delivery performance. Businesses can monitor traffic patterns, analyze user engagement, and optimize content delivery strategies using data-driven insights, ensuring their digital services are constantly improving and adapting to user needs.
Sify’s CDN Use Cases: Supporting Diverse Industry Needs
Sify’s CDN services cater to a wide range of industries in India, helping businesses deliver content with greater speed, reliability, and security.
1. Media and Entertainment
In the age of streaming services, rapid video and media content delivery is critical for user retention. Sify’s CDN enables broadcasters, video platforms, and entertainment companies to deliver high-quality, buffer-free video content to audiences across India, even during peak demand periods.
2. E-Commerce
For e-commerce platforms, fast-loading pages and secure transactions are key to converting visitors into customers. Sify’s CDN accelerates website load times, improves checkout experiences, and ensures secure payment processing, resulting in a better overall shopping experience and higher conversion rates.
3. Online Education
With the rise of digital education platforms, quick and reliable content delivery is essential for student engagement and success. Sify’s CDN helps educational institutions and e-learning platforms deliver online courses, live classes, and interactive content seamlessly across India.
4. Gaming
Sify’s CDN is ideal for gaming companies looking to reduce latency and enhance the user experience. By ensuring quick game updates, smooth gameplay, and real-time multiplayer interactions, Sify empowers gaming platforms to deliver an immersive experience to players across the country.
5. Financial Services
In the financial sector, secure and timely data delivery is paramount. Sify’s CDN ensures the rapid, secure transmission of financial data, powering applications like online banking, trading platforms, and fintech solutions with minimal latency and maximum security.
Why Choose Sify’s CDN Services?
Sify’s CDN services are designed to address the unique challenges of content delivery in India, offering businesses the tools they need to deliver exceptional online experiences. Here’s why businesses choose Sify:
Nationwide Coverage: With PoPs strategically located across India, Sify ensures that content is delivered with minimal latency, no matter where your audience is located.
High Availability and Reliability: Sify’s CDN is built on a robust infrastructure that guarantees high availability and reliability, even during traffic surges or unexpected disruptions.
Comprehensive Support: Sify offers end-to-end support to ensure that businesses get the most out of their CDN services. From setup and integration to ongoing performance optimization, Sify’s team of experts is always available to assist.
Cost-Effective Solutions: With a range of flexible pricing models and service plans, Sify provides cost-effective CDN solutions tailored to the needs of businesses, whether large enterprises or growing startups.
In an increasingly competitive digital marketplace, businesses need to ensure that their content reaches their audience quickly, securely, and reliably. Sify’s CDN services in India provide the infrastructure needed to meet these demands, enabling businesses to enhance user experiences, improve website performance, and secure their digital assets. Whether you’re delivering video content, running an e-commerce platform, or managing a global enterprise, Sify’s CDN offers the speed, scalability, and security necessary to thrive in the digital age.
0 notes
Text
Enhancing Performance and Security with Application Delivery Controllers
Application Delivery Controllers (ADCs) are crucial components in modern IT infrastructure, designed to optimize and secure the delivery of applications. These devices manage and balance network traffic, ensuring that applications perform efficiently and reliably across various environments. ADCs work by distributing incoming traffic across multiple servers, optimizing resource utilization, and improving overall application performance. They also provide essential security features, such as protection against Distributed Denial of Service (DDoS) attacks and application layer threats. Understanding how ADCs function and their role in application delivery is key to leveraging their benefits effectively.
Key Features and Benefits of Application Delivery Controllers
Application Delivery Controllers come with a variety of features designed to enhance application performance and security. Key features include load balancing, SSL offloading, and traffic management, which collectively improve application availability and responsiveness. ADCs also offer advanced security features, such as web application firewalls and intrusion prevention systems, which protect applications from malicious attacks. By offloading resource-intensive tasks like SSL encryption from application servers, ADCs free up server resources, leading to better performance. Understanding these features helps organizations choose the right ADCs for their needs and optimize their application delivery processes.
How Application Delivery Controllers Improve Application Performance?
Application Delivery Controllers play a vital role in enhancing application performance by managing and optimizing network traffic. Through load balancing, ADCs distribute incoming requests across multiple servers, preventing any single server from becoming overwhelmed. This distribution helps maintain optimal response times and prevents bottlenecks. Additionally, ADCs employ caching and compression techniques to reduce latency and improve data delivery speeds. By optimizing these aspects of application delivery, ADCs ensure a smooth and efficient user experience, which is crucial for maintaining user satisfaction and operational efficiency.
The Role of Application Delivery Controllers in Enhancing Security
Security is a critical aspect of application delivery, and Application Delivery Controllers provide robust security measures to protect applications from various threats. ADCs offer features like Web Application Firewall (WAF) capabilities, which guard against common attacks such as SQL injection and cross-site scripting (XSS). They also include DDoS protection mechanisms to mitigate the impact of large-scale attacks aimed at overwhelming application servers. By inspecting and filtering traffic, ADCs ensure that only legitimate requests reach the application servers, thereby enhancing overall security and reducing the risk of vulnerabilities being exploited.
Application Delivery Controllers vs. Load Balancers
While both Application Delivery Controllers (ADCs) and load balancers are used to distribute network traffic, they serve different purposes and offer distinct functionalities. Load balancers primarily focus on distributing incoming traffic across multiple servers to prevent overload and ensure high availability. In contrast, ADCs encompass a broader range of functions, including load balancing, traffic optimization, SSL offloading, and enhanced security features. ADCs integrate additional capabilities like application-aware traffic management and advanced security protections, making them a more comprehensive solution for application delivery needs. Understanding these differences helps organizations select the right tool for their specific requirements.
Implementing Application Delivery Controllers in Cloud Environments
In cloud environments, Application Delivery Controllers are essential for managing the dynamic and scalable nature of cloud-based applications. ADCs help optimize performance and ensure consistent delivery of applications across various cloud platforms. They provide capabilities such as auto-scaling, which adjusts resources based on traffic demand, and seamless integration with cloud services. ADCs also enhance security by enforcing access controls and monitoring traffic for potential threats. Implementing ADCs in cloud environments ensures that applications remain reliable and secure, even as they scale to meet changing demands.
Best Practices for Configuring Application Delivery Controllers
Proper configuration of Application Delivery Controllers is crucial for maximizing their benefits. Start by defining clear performance and security goals to guide the configuration process. Utilize features such as load balancing algorithms and traffic management policies to optimize application delivery. Regularly update and patch ADC firmware to address security vulnerabilities and improve functionality. Additionally, monitor ADC performance and adjust configurations as needed to adapt to changing traffic patterns and application requirements. Following these best practices ensures that ADCs operate effectively and contribute to enhanced application performance and security.
The Impact of Application Delivery Controllers on User Experience
Application Delivery Controllers significantly influence user experience by optimizing application performance and reliability. By balancing traffic and reducing server load, ADCs ensure that users experience consistent response times and minimal downtime. Features like caching and compression further enhance performance, leading to faster page loads and smoother interactions. Additionally, ADCs improve security, which helps maintain user trust by protecting sensitive data and preventing disruptions caused by security incidents. Overall, the effective use of ADCs leads to a more reliable and enjoyable user experience, which is crucial for retaining customers and achieving business goals.
Future Trends in Application Delivery Controllers
The field of Application Delivery Controllers is evolving rapidly, with several emerging trends shaping their development and deployment. One trend is the integration of artificial intelligence and machine learning for advanced traffic management and security analytics. Another trend is the increasing adoption of hybrid and multi-cloud environments, which requires ADCs to support seamless application delivery across diverse platforms. Additionally, there is a growing emphasis on automation and orchestration to simplify the management of ADCs in complex infrastructures. Staying informed about these trends helps organizations leverage the latest advancements in ADC technology to enhance their application delivery strategies.
Choosing the Right Application Delivery Controller for Your Needs
Selecting the right Application Delivery Controller involves evaluating various factors to ensure it aligns with your specific requirements. Consider aspects such as the scale of your application infrastructure, the level of security needed, and the types of traffic management features required. Assess the ADC’s compatibility with your existing systems and its ability to integrate with other network components. Additionally, review vendor support, scalability options, and cost considerations to make an informed decision. By thoroughly assessing these factors, organizations can choose an ADC that effectively supports their application delivery goals and enhances overall performance and security.
Conclusion
Application Delivery Controllers (ADCs) are integral to optimizing and securing the delivery of applications. They offer a range of features that enhance performance, ensure security, and improve user experience. By understanding their key functions, comparing them to load balancers, and following best practices for configuration, organizations can effectively leverage ADCs to meet their specific needs. Future trends in ADC technology indicate continued advancements in automation, cloud integration, and security. Choosing the right ADC involves careful consideration of your infrastructure requirements and evaluating available options to support your application delivery objectives. Investing in a robust ADC solution ultimately leads to better performance, enhanced security, and a superior user experience.
0 notes
Text
Key Features to Look for in a Global Server Load Balancer
When selecting a global server load balancer (GSLB), key features to prioritize include robust geographic load distribution capabilities, ensuring efficient traffic routing across dispersed servers or data centers. Advanced health monitoring tools are essential for real-time server performance assessment, enabling swift traffic rerouting in case of failures. SSL offloading and caching mechanisms optimize application performance, reducing latency for users globally. Effective traffic management algorithms, like weighted round-robin or least connections, enhance workload distribution efficiency. Comprehensive security features, such as DDoS protection and web application firewall (WAF) capabilities, safeguard against cyber threats. Lastly, integration with cloud services and APIs facilitates seamless scalability and management. Evaluating these features ensures that the GSLB enhances application reliability, performance, and security across distributed environments, meeting the dynamic needs of modern businesses.
Understanding the Role of a Global Server Load Balancer
A global server load balancer (GSLB) is essential for distributing network traffic across multiple servers located in different geographic regions. This distribution ensures that no single server becomes overwhelmed, leading to improved performance and reliability. By intelligently directing user requests to the most optimal server based on factors such as server load, location, and response times, a GSLB enhances the overall user experience and ensures high availability of services.
Key Features of Global Server Load Balancers
Global server load balancers come with a range of features designed to enhance the efficiency and reliability of network traffic management. These include geo-location routing, which directs users to the nearest server to reduce latency, and health monitoring, which continuously checks the status of servers to route traffic away from any that are experiencing issues. Other key features include SSL termination for secure connections, DDoS protection to safeguard against attacks, and advanced load balancing algorithms that optimize traffic distribution based on real-time analytics.
Benefits of Implementing a Global Server Load Balancer
The benefits of implementing a GSLB are numerous and significant for any business. First and foremost, it ensures high availability by distributing traffic and providing redundancy, so if one server fails, others can seamlessly take over. It also improves application performance by reducing latency and enhancing load times, leading to a better user experience. Additionally, a GSLB can help manage traffic spikes effectively, ensuring consistent service during peak usage times and contributing to cost savings by optimizing resource utilization.
Comparing Popular Global Server Load Balancers
Several global server load balancers stand out in the market due to their unique features and performance capabilities. NGINX Plus offers robust load balancing, security, and application delivery capabilities. F5 Networks provides advanced traffic management and security features suitable for large enterprises. Cloud-based options like Amazon Route 53 and Azure Traffic Manager offer seamless integration with their respective cloud services and provide scalable, reliable solutions for global traffic management. Comparing these solutions involves looking at their specific features, ease of integration, cost, and scalability to determine the best fit for your needs.
Implementing a Global Server Load Balancer: Best Practices
Implementing a GSLB requires careful planning and execution to maximize its benefits. Begin with a thorough assessment of your current infrastructure and traffic patterns. Choose a GSLB that aligns with your business requirements and has the necessary features. Ensure your implementation includes redundant paths and health checks to detect and manage failures effectively. Regularly monitor performance metrics to fine-tune settings and configurations. Finally, conduct periodic tests to ensure that failover mechanisms work as intended and that your GSLB setup remains resilient and efficient under varying load conditions.
Challenges and Solutions in Deploying Global Server Load Balancers
Deploying a global server load balancer is not without challenges. Common issues include managing complex configurations, ensuring compatibility with existing infrastructure, and dealing with latency and synchronization across distributed servers. To address these challenges, it's essential to choose a GSLB that offers comprehensive documentation and support. Implementing automation tools can help manage configurations and updates. Additionally, leveraging advanced monitoring and analytics tools can provide insights into performance issues, enabling proactive management and troubleshooting. Regular training for IT staff can also ensure they are equipped to handle the complexities of GSLB deployment and management.
Future Trends in Global Server Load Balancing
The future of global server load balancing is likely to be shaped by advancements in artificial intelligence and machine learning, which can provide more sophisticated traffic management and predictive analytics. Integration with multi-cloud environments will become increasingly important as businesses adopt hybrid cloud strategies. Enhanced security features, such as AI-driven threat detection and automated response mechanisms, will also play a crucial role. Furthermore, the rise of edge computing will drive the need for more localized load balancing solutions, ensuring even lower latency and faster response times for end-users. Staying abreast of these trends will be essential for businesses looking to maintain a competitive edge in their network infrastructure.
Conclusion
Global server load balancers are critical components for businesses aiming to provide high availability, reliability, and optimal performance for their applications across the globe. By understanding the key features, benefits, and best practices for deploying GSLBs, businesses can enhance their network infrastructure and deliver superior user experiences. While challenges exist, solutions such as automated configuration and robust security measures can mitigate these issues. As technology evolves, GSLBs will continue to adapt, incorporating AI, edge computing, and multi-cloud integration, ensuring they remain essential tools for modern IT environments.
0 notes
Text
Securing Content Delivery: Insights into the CDN Security Market
In today's digital landscape, content delivery networks (CDNs) play a crucial role in ensuring the fast, reliable, and secure delivery of online content to users worldwide. As the demand for digital content continues to soar, so does the need for robust security measures to protect against evolving cyber threats. In this article, we delve into the content delivery networks (CDNs) security market, examining its significance, trends, and the strategies employed to safeguard content delivery networks and the content they deliver.
CDNs are distributed networks of servers strategically positioned across the globe to cache and deliver digital content, such as web pages, videos, images, and applications, to end-users based on their geographical location. By storing copies of content closer to users, CDNs reduce latency, improve website performance, and mitigate the impact of network congestion, ensuring a seamless user experience across devices and platforms.
However, as the volume and complexity of online threats continue to increase, CDNs are facing growing security challenges that threaten the integrity, availability, and confidentiality of the content they deliver. From Distributed Denial of Service (DDoS) attacks and botnet traffic to data breaches and content piracy, CDN operators must employ a multi-layered approach to security to protect against a wide range of threats and vulnerabilities.
Request the sample copy of report @ https://www.globalinsightservices.com/request-sample/GIS24662
One of the primary security measures employed by CDN providers is DDoS mitigation, which involves identifying and filtering malicious traffic before it reaches the origin servers or disrupts content delivery. By leveraging real-time traffic analysis, rate limiting, and behavioral analytics, CDNs can detect and mitigate DDoS attacks in milliseconds, ensuring uninterrupted content delivery and preserving the availability of online services.
Moreover, CDN security encompasses a range of other protective measures, including Web Application Firewall (WAF) capabilities, Secure Sockets Layer (SSL) encryption, access controls, and content authentication mechanisms. WAFs, for example, inspect incoming web traffic for malicious payloads and anomalous behavior, while SSL encryption secures data in transit between users and CDN servers, protecting against eavesdropping and man-in-the-middle attacks.
Furthermore, CDN security extends beyond traditional perimeter defenses to include advanced threat intelligence, machine learning, and behavior-based anomaly detection techniques. By analyzing vast amounts of network data and telemetry in real-time, CDNs can identify and respond to emerging threats proactively, mitigating risks and protecting against zero-day attacks before they escalate into full-blown security incidents.
In recent years, there has been a growing demand for integrated CDN security solutions that offer seamless integration with existing infrastructure and centralized management capabilities. Enterprises, content providers, and e-commerce businesses are increasingly turning to CDN vendors that offer comprehensive security features, robust API integration, and scalable deployment options to protect their digital assets and customer data effectively.
Additionally, regulatory compliance requirements, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, are driving organizations to prioritize security and privacy in their CDN deployments. Compliance with these regulations requires CDN providers to implement data protection measures, access controls, and privacy-enhancing technologies to safeguard sensitive information and uphold user privacy rights.
In conclusion, the CDN security market is witnessing rapid growth and evolution in response to the escalating threat landscape and the increasing reliance on digital content delivery. By adopting a proactive, multi-layered approach to security, CDN providers can effectively mitigate risks, protect against cyber threats, and ensure the integrity, availability, and confidentiality of the content they deliver. As organizations continue to embrace digital transformation and online content delivery, investing in robust CDN security solutions will remain a critical imperative to safeguarding digital assets and maintaining user trust in an increasingly connected world.
0 notes
Text
can vpn be published reverse proxy
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can vpn be published reverse proxy
VPN for Reverse Proxy Server
Title: Enhancing Security and Anonymity: VPN for Reverse Proxy Server
In the realm of online security and privacy, the use of Virtual Private Networks (VPNs) has become increasingly prevalent. However, combining VPNs with reverse proxy servers presents a potent solution for heightened protection and anonymity online.
A reverse proxy server acts as an intermediary between clients and servers, forwarding client requests to the appropriate server resources and then returning the server's response to the client. By integrating a VPN with a reverse proxy server, users can add an extra layer of security and privacy to their online activities.
One of the primary benefits of using a VPN with a reverse proxy server is enhanced encryption. VPNs encrypt the data transmitted between the user's device and the VPN server, preventing malicious actors from intercepting or deciphering sensitive information. When combined with a reverse proxy server, this encryption extends to the communication between the proxy server and the destination server, ensuring end-to-end security.
Moreover, VPNs offer users the ability to mask their IP addresses, thereby anonymizing their online presence. By routing their internet traffic through a VPN server located in a different geographical location, users can obfuscate their true IP address and browse the web anonymously. When coupled with a reverse proxy server, this anonymity is further fortified, as the reverse proxy server adds another layer of indirection between the user and the destination server.
Furthermore, the combination of VPN and reverse proxy server facilitates access to geo-restricted content and bypassing censorship. Users can leverage the VPN to connect to servers in different countries, allowing them to circumvent geographic restrictions imposed by content providers or government censorship measures.
In conclusion, integrating a VPN with a reverse proxy server offers users an effective means of fortifying their online security, enhancing their anonymity, and overcoming geo-restrictions. By leveraging the complementary features of these technologies, individuals can enjoy a safer and more private online experience.
Reverse Proxy VPN Implementation
Title: Exploring the Implementation of Reverse Proxy VPNs
A Reverse Proxy VPN is a sophisticated solution for enhancing online security and privacy. Unlike traditional VPNs, which route traffic through a central server, a Reverse Proxy VPN operates by deploying multiple proxy servers strategically. This setup offers several advantages, including improved anonymity, enhanced performance, and better resilience against cyber threats.
The implementation process for a Reverse Proxy VPN involves several key steps. Firstly, organizations need to select a suitable infrastructure provider capable of supporting distributed proxy servers. Providers offering advanced networking features and robust security measures are preferred to ensure optimal performance and protection.
Once the provider is chosen, the next step involves configuring the proxy servers to act as reverse proxies. This configuration entails setting up routing rules, SSL termination, and load balancing to efficiently manage incoming traffic. Additionally, implementing security measures such as IP filtering, DDoS protection, and web application firewalls (WAFs) is crucial to safeguard against malicious activities.
Another important aspect of Reverse Proxy VPN implementation is integrating user authentication mechanisms. This ensures that only authorized users can access the network and sensitive resources. Implementing multi-factor authentication (MFA) and Single Sign-On (SSO) solutions further enhances security while simplifying user access management.
Continuous monitoring and optimization are essential components of Reverse Proxy VPN implementation. Monitoring tools help administrators identify and address performance bottlenecks, security vulnerabilities, and compliance issues in real-time. Regularly updating configurations and security policies ensures that the Reverse Proxy VPN remains effective against evolving threats.
In conclusion, implementing a Reverse Proxy VPN requires careful planning, configuration, and ongoing maintenance. By leveraging distributed proxy servers and advanced security features, organizations can establish a robust defense against cyber threats while safeguarding user privacy and data integrity.
Publishing VPN as Reverse Proxy
When it comes to enhancing online security and privacy, using a Virtual Private Network (VPN) is a popular choice among internet users. However, another powerful tool that can be used in conjunction with a VPN is a reverse proxy.
Publishing a VPN as a reverse proxy involves utilizing the reverse proxy server to distribute incoming client requests to the appropriate backend server, which in this case would be the VPN server. By doing so, the reverse proxy serves as an intermediary between the client and the VPN server, adding an extra layer of security and anonymity to the connection.
One of the main benefits of publishing a VPN as a reverse proxy is that it can help to mask the true IP address of the client from the VPN server, further enhancing privacy and security. Additionally, a reverse proxy can help to improve network performance by caching static content and distributing traffic efficiently.
Furthermore, by using a reverse proxy in front of the VPN server, it is possible to add additional security features such as web application firewall protection and DDoS mitigation. This can help to protect the VPN server from potential cyber threats and attacks, ensuring a more secure online experience for users.
In conclusion, publishing a VPN as a reverse proxy can offer enhanced security, privacy, and performance benefits for internet users. By leveraging the power of both tools together, users can enjoy a safer and more anonymous online browsing experience.
Reverse Proxy vs VPN
A reverse proxy and a VPN are both tools used to enhance cybersecurity and privacy, but they serve different purposes and operate in distinct ways.
A reverse proxy acts as an intermediary between users and backend servers, forwarding client requests to the appropriate server. It can improve performance by caching frequently accessed resources and providing load balancing capabilities. Additionally, a reverse proxy can enhance security by masking server identities and filtering malicious traffic before it reaches the server. This makes it an essential tool for protecting servers from potential cyber threats and ensuring smooth and secure communication between clients and servers.
On the other hand, a VPN, or Virtual Private Network, creates a secure encrypted tunnel between a user's device and a remote server, allowing users to transmit data over public networks securely. VPNs are commonly used to protect sensitive information, bypass geo-restrictions, and enhance online privacy by masking users' IP addresses. By encrypting data and providing anonymity, VPNs are crucial for maintaining privacy and security while browsing the internet.
In summary, while both a reverse proxy and a VPN aim to enhance cybersecurity and privacy, they operate in different ways. A reverse proxy is primarily used to protect servers and optimize performance, while a VPN is designed to secure users' online activities and protect sensitive data. Choosing the right tool depends on the specific needs and requirements of the user, whether it be securing server infrastructure or maintaining online privacy and anonymity.
Using VPN for Reverse Proxy Server
Using a VPN for a Reverse Proxy Server can be a powerful and versatile tool for enhancing online security and privacy. A Reverse Proxy Server acts as an intermediary between a client and one or more servers, helping to distribute traffic efficiently and provide an additional layer of protection against cyber threats. By incorporating a VPN into this setup, users can further bolster their security measures.
One of the key benefits of using a VPN with a Reverse Proxy Server is the encryption it offers. When data is transmitted between the client, the Reverse Proxy Server, and the destination server, the VPN encrypts the communication, making it nearly impossible for unauthorized parties to intercept and decipher the information. This added layer of security is especially crucial when handling sensitive data or accessing confidential information online.
Moreover, employing a VPN with a Reverse Proxy Server can help users mask their true IP address. By rerouting their internet traffic through a secure VPN server, individuals can obscure their actual location and online identity. This not only safeguards their privacy but also enables them to access geo-restricted content and bypass censorship measures imposed by certain websites or governments.
Furthermore, the combination of a VPN and a Reverse Proxy Server can enhance the overall performance and speed of online activities. By reducing latency and optimizing bandwidth usage, users can enjoy smoother browsing experiences and faster data transfer rates.
In conclusion, utilizing a VPN for a Reverse Proxy Server can significantly elevate online security, privacy, and performance. By leveraging these two tools in tandem, individuals and organizations can establish a robust digital defense system against potential cyber threats and safeguard their sensitive information effectively.
0 notes
Text
Difference Between the 3 : Microsoft Azure vs AWS vs Google Cloud

The business industry has transformed overall at 360 degrees. With advanced and modern solutions, the processes have turned easier and faster than ever before. Now, mid to large enterprises have redefined the management processes with next-level tools that include effective CMS software and cloud computing.
The high-performance public Cloud computing network has turned into a new trend. It helps to streamline the data processing and allows users to manage it effectively with easy access.
Presently, Cloud has turned into a crucial part and it is also considered as the key success factor of the next business world. In order to leverage all the benefits of Cloud technology, it is important to know all in-depth about this platform.
In this blog, we have discussed Cloud development services, as well as different trending platforms that allow you to streamline several data management processes and ensure you stay ahead in the competitive edge.
How do different Cloud development Services work?
There are three ways that companies can opt for the different public cloud services –
1. Software as a Service (SaaS) –
This model allows business owners to ake the full benefits of Cloud-based applications.
2. Platform as a Service ( Paas) –
This model offers a runtime environment that allows you to build, manage, and test the solutions in an effective manner.
3. Infrastructure as a Service (IaaS) –
infrastructure It refers to the Cloud hosting infrastructure components that physical data centers. Thus, IaaS is also known as the virtual data center.
Due to the high demand, Cloud has turned as the foremost choice of the mid to large enterprises but among them, three platforms are in high trend and always create a buzz with their functionalities update-
Microsoft Azure
AWS
Google Cloud
Let’s know about these three platforms and the major differences among them –
Microsoft Azure

Microsoft Azure is also referred to as Azure. It is a Cloud computing service launched by the reputed worldwide company Microsoft with the motive to build, test, deploy, and manage the different solutions and services. It is launched under open source for client SDKs and this supports different platforms such as Linux, Microsoft Windows, iOS, and Android.
Main features of Azure
Features of Azure
Here are the major features that why you should opt for the Azure –
Highly compatible with Cloud development platform
Azure supports the modern blockchain technologies
Effective in predictive analytics
Comprehensive IoT integration
Allows to leverage the DevOps features that ensures to avoid future failures.
AWS

AWS is known as the Amazon Web Services. It offers a huge number of the toolset, that allows expanding AWS capabilities and has also turned into an important part of many industries and large-scale businesses. Majorly, AWS focuses on the public Cloud structure.
It helps in managing services for –
Web Application Firewall (WAF)
AWS Inspector
AWS Shield for DDoS protection
GuardDuty for threat detection
AWS Config and CloudTrail for inventory auditing and policy management
For data security, AWS provides:
KMS and CloudHSM services for key management
Encryption at Rest for most storage services
Macie – an AI-driven data loss prevention (DLP) service
Google Cloud Platform

This platform is also called the GCP, it was introduced in the market lastly and has a different enterprise focus. This platform is funded in the best way and experts have in-depth technical knowledge about it. The best reason to opt for this technology is its focuses on modern technologies that include AR, VR, and many more that allow users to leverage the next generation experience.
Reasons to Choose GCP
It is based on the comprehensive container-based model
Hyperscale networking environment
Supports in Developing and deploying cloud-based apps and software
Companies have already this technology for their digital migration and that results in a cost-efficient and greener tech solution
AWS vs Azure vs Google Cloud Customers
AWS is the oldest in the market, and also has huge community support. It has market leaders based customers such as Samsung, Netflix, BMW Airbnb, and Unilever.
Azure is also known for its services and 80% of companies have opted for it. The top brand companies also include in the list such as Johnson Controls, Polycom, Apple, Honeywell, and many more.
Google Cloud is the latest but it has also marked an immense presence in the market and companies have opted such as PayPal, Bloomberg, 20th Century Fox, Dominos, HSBC Bank, and others.
Conclusion
Microsoft Azure, AWS, and Google Cloud are the most trending and popular platforms. Many times companies get confused to opt for which platform, but in order to leverage all the benefits of the tech world, it is important to know all about the three technologies and the functionalities they offer. As these three are very different from each other, but you should the major differences between them and choose your platform as per your project requirements.
#helpdesk#networking#it solutions#managed it services#cloud managed services#it consulting#cloud migration
1 note
·
View note
Text
5 Best Website Security Services

Website security services are designed to protect websites from malicious attacks, data breaches, and other cyber threats. These services generally include tools and processes to monitor network traffic, detect and block malicious requests, and secure data. They may also include features such as DDoS protection, malware scanning, and identity and access management.
Additionally, website security services often include measures to protect against data theft, phishing attacks, and other malicious activities. These services are essential for any business that operates a website, as they can help to ensure the safety and security of sensitive user data and financial information.
What is Website Security?
Website Security is the process of protecting a website from unauthorized access, malicious attacks, data breaches, and other security threats. This includes securing the website from hackers, preventing malware from entering the website, and regularly monitoring the website for any suspicious activity. Website security is critical for website owners, especially for those who collect sensitive customer data such as payment information.
Benefits of Website Security
Website security is an important factor in protecting websites and the data they contain. Benefits of website security include:
• Prevention of malicious data breaches and cyberattacks: Website security helps protect websites from hackers, viruses, and other malicious attacks that can compromise data and information stored on the website.
• Increased customer confidence: With website security in place, customers of the website can be confident that their data and information are safe and secure. This can help increase customer loyalty and trust in the website and its services.
• Improved Search Engine Rankings: Search engines use website security as a factor in ranking websites. Websites with strong security can get a higher ranking in search engine results, resulting in more website traffic and better visibility.
• Reduced Liability: Website security can help reduce the risk of lawsuits and other legal liabilities that can arise from data breaches and other security incidents.
Improved Performance: Website security can help improve website performance by preventing malicious attacks from slowing down website loading times and other performance issues.
Pro tip: Secure your website now with our Web Hosting Security Checklist 2023 — Learn How to Protect Your Site Today!
The Best Website Security Services
It is of utmost importance to ensure that your website is secure and safe for your customers’ use. Let’s review a few measures that you can take to encourage engagement and build customer loyalty while keeping your website secure.
Obtaining an SSL Certificate with Let’s Encrypt
Let’s Encrypt is a free, automated, and open Certificate Authority. It provides domain-validated SSL certificates that can be used to secure websites and other services, free of charge. It is a service of the Internet Security Research Group (ISRG). Let’s Encrypt certificates are issued using the Automated Certificate Management Environment (ACME) protocol. The certificates are valid for 90 days but can be renewed as needed.
2. Cloudflare — Web Security and Performance Solutions
Cloudflare is a web application firewall (WAF) that helps protect websites from malicious online threats. It provides a secure layer of protection between websites and the Internet, helping to protect against data theft, malware, distributed denial-of-service (DDoS) attacks, and other cyber threats.
Cloudflare’s WAF also provides advanced features such as bot management, rate limiting, and geo-blocking. With Cloudflare, businesses can protect their websites, applications, and data from malicious attacks and ensure their websites remain available and secure.
3. Google CDN — Global Content Delivery Network Solutions
Google’s Content Delivery Network (CDN) is a global network of servers located in various geographic locations around the world. It is designed to deliver web content quickly and reliably, keeping latency and load times low. Google CDN caches static content such as HTML, JavaScript, images, and other media files, which are then delivered to users based on their geographical location.
This allows the content to load more quickly, providing a smoother user experience. By using a CDN, websites can reduce their bandwidth usage, improve their user experience, and offer better performance.
4. LogicMonitor — Professional Website Monitoring Service
LogicMonitor is a website monitoring service that helps businesses ensure their website performance and availability. It provides a comprehensive view of website performance by monitoring uptime, page load times, and server health.
It also provides real-time alerts, performance metrics, and analytics to help businesses identify issues quickly and take corrective action. LogicMonitor can be used to monitor websites in any location, including local, cloud-hosted, and hybrid environments. Additionally, it offers support for multiple technologies, such as AWS, Azure, Docker, and Kubernetes.
5. Duo Security — Advanced Two-Factor Authentication
Duo Security is a two-factor authentication service that helps protect businesses and users from data breaches and cyber-attacks. It provides an extra layer of security for accounts by requiring users to enter a second form of authentication before they can access their accounts.
Duo Security also provides visibility into user access and activity, as well as the ability to detect suspicious activity and respond quickly. Duo Security is used by companies of all sizes to protect their data and ensure that only authorized users can access company resources.
Conclusion
Website owners who wish to prioritize site security have access to a great variety of tools. If you have plenty of time, you can pick and choose several individual tools, or settle on a comprehensive hosting service providers that will manage most of the work. Be sure to select a service that meets your budgetary requirements, provides the necessary features, and, above all, ensures a secure experience for your website and its users.
#cybersecurity hashtag#datasecurity hashtag#websitesecurity hashtag#securewebsite hashtag#securityservices hashtag#secureHosting hashtag#cloudsecurity hashtag#securecloud hashtag#onlinesafety hashtag#securenetwork hashtag#dataprotection hashtag#securedata hashtag#securedata hashtag#hostingseekers hashtag#wsdhs hashtag#team hashtag#security#cloudhosting#webhostingservices#vps#webhostingcompany
0 notes
Text
Web Application Firewall Market Leading Growth Drivers, Emerging Audience, Segments, Sales, Profits & Analysis | COVID-19 Effects
The web application firewall market is projected to witness a significant growth during the forecasted period. The market is majorly driven by the increased usage of internet and web related applications. The web application firewall prevents the organizations from several vulnerabilities as the developing technological advancements is giving rise to the increased threats and attacks. Based on deployment, the market is segmented into on appliance, on cloud, and on network. Among these, the cloud-based web application firewall is leading the segment because of the solutions and advanced technologies of prevention from malware, phishing, and other cyber-attacks and threats. Also, cloud-based deployment is a cost-effective solution for better usability, scalability, and security protection options. The adoption of cloud technology across various organizations and verticals has increased, the cloud-based web application firewall offers capabilities such as access control, application programming interface, threat intelligence, and bot detection. Cloud based web application firewall are easy to deploy. The cloud-based application firewall lets the companies switch to the cloud services, which is the feature of subscription-based services.
The need for robust measures to perceive the threats and strikes by checking the HTTP request are fueling the web application firewall market 2020. The automotive technology and services reports are produced by Market Research Future, which contains market alternatives for progress. An income generation potential reaching figures of USD 5.5 billion by the end of 2023 is forecasted at a CAGR of 15 %.
The use of the internet and web-related applications is rising steadily, and this is estimated to bolster the WAF Market Size. The influences of mounting digitization and online stores are estimated to invite cyber-attacks is estimated to increase the web application firewall market share in the forecast period.
Market Highlights
In the coming years, the global market is expected to experience rapid growth on the back of various factors, including rising adoption of web applications, the rise in cyber-attacks, and increasing Internet of Things penetration. The rise in Internet of Things implementation, especially in automotive and consumer electronics, is a prediction to generate lucrative opportunities on the global market. The surge in data theft cases has increased the need for the firewall on the web application. They are requested against cyber-attacks such as cross-site scripting and SQL injection for security. Web application firewall (WAF) is recognized for safeguards provided to the servers. WAF 's availability in different forms such as computers, servers, and filters play a major role in deciding the size of the firewall market for web applications. On the global market, the rising rate of adoption of cloud-based computing technologies serves as a growth factor. Government cybersecurity regulations also accelerate the advancement of the firewall environment of web applications.
Cloud-based WAF products are gaining popularity on the market because they are completely equipped with anti-malpractice threat management technologies such as ransomware, cyberware, phishing and emerging cyber threats on the global market. This cloud-based approach provides a major benefit by protecting the network even when the user is offline. Various positive attributes such as threat intelligence, bot detection and compliance, caching, Application Program Interface (API) protection, Distributed Denial of Service (DDoS) mitigation, and malware detection are stepping up market development.
Market Segmentation
The global firewall market for web applications is segmented by deployment, services, size of organization, security models, end users and region. The market is segmented into on appliance, cloud, and network based on deployment. Of others, the cloud-based web application firewall is the leading category due to advanced malware, phishing, and other cyber-attacks and threats mitigation technologies and solutions.
The segmentation is categorized according to technical services and managed services depending on the companies.
The market is divided into negative security model, positive safety model and hybrid security model.
The web application firewall attracts end users such as banking, insurance, e -commerce, government, telecom, education, healthcare, and others.
Get a Free Sample @
https://www.marketresearchfuture.com/sample_request/4508
Detailed Regional Analysis
The regional examination of the web application firewall market includes regions such as Europe, North America, Asia Pacific and the rest of the regions. The Asia Pacific region is substantially developing in the web application firewall market owing to the collective adoption and systems of web and mobile applications in nations such as India and China for business processes. Out of the regions considered, the regional market in North America is leading in terms of unconventional incidence of security vendors. The North American regional market is the most innovative region for cybersecurity technology acceptance and organization owing to the industrialized countries such as the U.S. and Canada.
Competitive Analysis
The emphasis on innovation is estimated to rise in the coming years, as the consumer needs have to be addressed in a better manner to ensure the resurgence of the global market. Also, the need to encourage business to include the environmental impact of their decisions is estimated to shape the development of the market in future. The need to mitigate losses sustained by the current public health crisis is estimated to be the sole focus of the market contenders in the upcoming years. Furthermore, the need to adopt a rapid and cost-effective method of operation is estimated to shape the market in the impending period. The capability of contenders to influence change in the market is increasing at a stable rate in the impending period. The support from government bodies around the world is rising because the market needs an extra stimulus to achieve normalcy in such a scenario. The disharmony in the forces of demand and supply is estimated to create a slow growth background in the market.
Key Players
The illustrious players in the web application firewall market are Barracuda Networks, Inc. (U.S.), Fortinet, Inc. (U.S.), IBM Corporation (U.S.), NS Focus Information Technology Co Ltd (China), Citrix Systems, Inc. (U.S.), F5 Networks, Inc (U.S.), Imperva Inc (U.S.), Applicure Technologies Ltd (Israel), DBAPP Security Co., Ltd (China), Akamai Technologies (U.S.), Juniper Networks, Inc (U.S.), among others.
Browse Complete Report @
https://www.marketresearchfuture.com/reports/web-application-firewall-market-4508
Web Application Firewall Market Research Report: Information by Technology (Hall Effect, Magneto Resistive, Variable Reluctance), By Application (Automotive, Industrial, Aerospace & Defense, Consumer Electronics) and Region (North America, Europe, Asia-Pacific, Middle East & Africa, and South America)—Forecast till 2030
Browse More Trending Articles
Cloud-Based PLM Market
Cloud Infrastructure Services Market
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions.
Contact:
Market Research Future (Part of Wantstats Research and Media Private Limited)
99 Hudson Street, 5Th Floor
New York, NY 10013
United States of America
+1 628 258 0071 (US)
+44 2035 002 764 (UK)
Email: [email protected]
Website: https://www.marketresearchfuture.com
0 notes
Text
AgileCDN — One Click to Start Advanced WAF Security Protection
WAF(Web Application Firewall), also named application firewall, detects and verifies the content of requests from web applications, ensures the security and legality of requests, prevents illegal requests in real-time, and provides protection for web applications. WAF is an important part of Defense in depth strategy and a detective and corrective control.
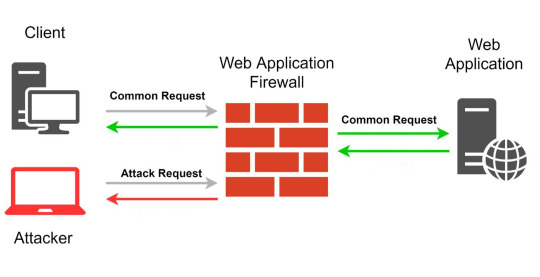
Simply put, WAF is just like the subway security check, which performs a quick security check for HTTP requests by analyzing HTTP data and judging different characters in features, rules, and other dimensions, the result is the basis to judge intercepting requests or not.
AgileCDN provides Layer3/4 protection for free and by default. For the users who are in high demand for security protection, AgileCDN provides a DDoS shield started with one click and advanced WAF protection, including intelligent rule protection, custom protection, IP’s blacklist and whitelist, blocked regions. All security protection functions can be easily used without deployment, purchasing security protection from the third party, and software/hardware installation. Easy set-up can realize security protection in multiple dimensions. Next, let’s learn about the functions of WAF security protection in detail.
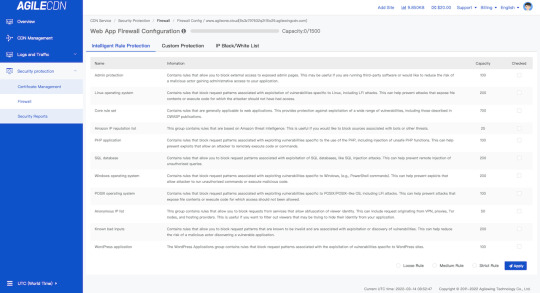
Intelligent Rule Protection
Provides a series of intelligent rules. Users needn’t research hackers and crawlers’ attack mechanisms to design rules. They can directly choose options in the menu of control panel. To be easier, directly click the checkbox as below.
Custom Protection
You can set some easy rules here, such as blocking or accepting the requests of some specific UserAgent or QueryString.
In addition, you can add the Referer hotlink protection rule and set access control rules based on the HTTP request’s referer(e.g. Referer blacklist/whitelist) to identify and filter the visitors and prevent your site resources from illegal stolen.

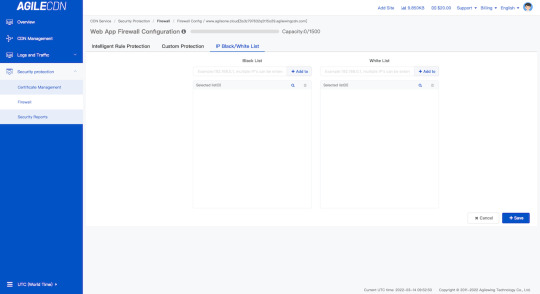
IP Blacklist/Whitelist
You can set the IP blacklist to restrict the origin IP. IPs in the whitelist can be accessed quicker while IPs in the blacklist cannot be accessed.
Blocked Regions
According to identify the source area of application request, block or allow specific area’s application access, resolving high-incidence dangerous request issues of some regions.
Relying on Agilewing which has more than ten years of deep technical development and industry experience in the public cloud field, AgileCDN provides more powerful tech support for go-global enterprises.
About AgileCDN
Intelligent cloud Agilewing develops AgileCDN based on CloudFront infrastructure. AgileCDN is a compact, easy-to-use, modular content delivery and acceleration SaaS platform. It has 4 advantages as below.
Security: All PoPs are nested with DDoS protection, WAF protection, and AWS Route53, AWS global attack blacklist, making the defense shield stronger and protecting content providers and its users from all kinds of attacks.
Operation: 3 steps, 3 seconds to deploy, 1 click to operate, auto configuration management, no adjustment is needed for business. Abundant statistical reports and data analysis to assist site operation, making your CDN business transparent and visible.
Price: Tiered pricing by traffic usage, flexible policies, efficiently reducing resources idleness and waste. Attain the requirements of enterprises in different development stages. Global uniform pricing, with no hidden costs, significantly increases the enterprise ROI.
Stability: 260+ global PoPs, cover 245 countries and regions worldwide, directly connected to AWS proprietary global backbone network, offering 300Tbps+ bandwidth capacity, backups for many regions, 7*24 tech support.
Access the official site to start your global acceleration journey.
https://www.agilecdn.cloud/
0 notes
Text
Sify’s CDN Services in India: Accelerating Digital Content Delivery
In an increasingly digital world, businesses are under constant pressure to deliver fast, seamless, and reliable online experiences to their users. From streaming media to e-commerce platforms, website performance can make or break a user’s interaction with a brand. Recognizing the critical need for speed and reliability, Sify offers cutting-edge Content Delivery Network (CDN) services across India, empowering businesses to deliver rich digital content swiftly and securely.
What is a CDN and Why is it Essential?
A Content Delivery Network (CDN) is a system of distributed servers that work together to deliver web content, such as HTML pages, images, videos, and scripts, more efficiently to users based on their geographic location. CDNs cache content at multiple points of presence (PoPs), reducing latency and ensuring that content is delivered from a server that is geographically closer to the end user.
In India, where the digital landscape is expanding rapidly, CDNs have become an essential tool for businesses seeking to provide high-performance, scalable content delivery. Sify’s CDN services are designed to meet the unique demands of India’s diverse internet users, ensuring seamless access to digital content, regardless of location or device.
Key Features of Sify’s CDN Services
1. Geographically Distributed PoPs
Sify’s CDN is powered by a network of strategically located PoPs across India and globally. This distribution allows for reduced latency and faster content delivery by ensuring users access content from the nearest server, whether they’re in a metropolitan city or a remote location.
2. Enhanced Scalability
As businesses grow, their need for scalable infrastructure becomes more critical. Sify’s CDN services offer unmatched scalability, allowing businesses to effortlessly handle traffic spikes during events like sales promotions, product launches, or viral content distribution. Whether serving millions of concurrent users or delivering high-resolution videos, Sify’s CDN ensures uninterrupted performance.
3. Low-Latency Content Delivery
Sify’s CDN architecture is optimized for low-latency content delivery, ensuring that websites, applications, and media are served without delay. By leveraging advanced caching and compression technologies, Sify reduces load times and enhances user engagement, creating a superior browsing experience for customers across India.
4. Advanced Security
With an increase in cyber threats, Sify places a strong emphasis on security. Sify’s CDN services include robust security features such as DDoS protection, secure SSL/TLS encryption, and web application firewalls (WAF) to safeguard your content and user data from malicious attacks. This ensures that your digital assets remain secure while being delivered at top speed.
5. Optimized Video Streaming
For businesses in the media and entertainment sectors, delivering high-quality video content is essential. Sify’s CDN supports adaptive bitrate streaming (ABR), ensuring that users receive the best video quality based on their network conditions and device capabilities. This results in smooth video playback, reduced buffering, and an overall better user experience.
6. Real-Time Analytics
Sify’s CDN services provide detailed insights and real-time analytics on content delivery performance. Businesses can monitor traffic patterns, analyze user engagement, and optimize content delivery strategies using data-driven insights, ensuring their digital services are constantly improving and adapting to user needs.
Sify’s CDN Use Cases: Supporting Diverse Industry Needs
Sify’s CDN services cater to a wide range of industries in India, helping businesses deliver content with greater speed, reliability, and security.
1. Media and Entertainment
In the age of streaming services, rapid video and media content delivery is critical for user retention. Sify’s CDN enables broadcasters, video platforms, and entertainment companies to deliver high-quality, buffer-free video content to audiences across India, even during peak demand periods.
2. E-Commerce
For e-commerce platforms, fast-loading pages and secure transactions are key to converting visitors into customers. Sify’s CDN accelerates website load times, improves checkout experiences, and ensures secure payment processing, resulting in a better overall shopping experience and higher conversion rates.
3. Online Education
With the rise of digital education platforms, quick and reliable content delivery is essential for student engagement and success. Sify’s CDN helps educational institutions and e-learning platforms deliver online courses, live classes, and interactive content seamlessly across India.
4. Gaming
Sify’s CDN is ideal for gaming companies looking to reduce latency and enhance the user experience. By ensuring quick game updates, smooth gameplay, and real-time multiplayer interactions, Sify empowers gaming platforms to deliver an immersive experience to players across the country.
5. Financial Services
In the financial sector, secure and timely data delivery is paramount. Sify’s CDN ensures the rapid, secure transmission of financial data, powering applications like online banking, trading platforms, and fintech solutions with minimal latency and maximum security.
Why Choose Sify’s CDN Services?
Sify’s CDN services are designed to address the unique challenges of content delivery in India, offering businesses the tools they need to deliver exceptional online experiences. Here’s why businesses choose Sify:
Nationwide Coverage: With PoPs strategically located across India, Sify ensures that content is delivered with minimal latency, no matter where your audience is located.
High Availability and Reliability: Sify’s CDN is built on a robust infrastructure that guarantees high availability and reliability, even during traffic surges or unexpected disruptions.
Comprehensive Support: Sify offers end-to-end support to ensure that businesses get the most out of their CDN services. From setup and integration to ongoing performance optimization, Sify’s team of experts is always available to assist.
Cost-Effective Solutions: With a range of flexible pricing models and service plans, Sify provides cost-effective CDN solutions tailored to the needs of businesses, whether large enterprises or growing startups.
In an increasingly competitive digital marketplace, businesses need to ensure that their content reaches their audience quickly, securely, and reliably. Sify’s CDN services in India provide the infrastructure needed to meet these demands, enabling businesses to enhance user experiences, improve website performance, and secure their digital assets. Whether you’re delivering video content, running an e-commerce platform, or managing a global enterprise, Sify’s CDN offers the speed, scalability, and security necessary to thrive in the digital age.
0 notes
Text
Amazon Taking Faster Online Video, Popular Music Install Services to Kenya

The Amazon Web Services is actually appealing companies in East Africa a lot faster content delivery and also added cybersecurity protection.Expected to be actually operational
in very early 2020, the business is actually launching the Amazon CloudFront Side site in Kenya.According to the provider, Amazon CloudFront is actually an extremely safe and secure and also strongly accessible Content Delivery Network (CDN ). Higher Transfer Velocities It accelerates the shipment of apps, records,
and also video recordings to users worldwide, along with higher
transmission speeds.Kenya is actually the latest country to be actually linked to AWS's international framework network, which is actually made and also built to
deliver the most flexible, reliable, scalable, as well as protect cloud computer setting with the best system functionality offered today.Customers. around all sectors in Kenya are taking advantage of the flexibility,. scalability, and surveillance of the AWS cloud. Loading ... The boosted. and a lot faster customer adventure, along with regional Amazon.com CloudFront infrastructure, will. aid in steering the development of even more web treatments all over Kenya,.
including eCommerce, education, home entertainment, video gaming, medical care, media,. mobile banking, and authorities services.Customers. around the country may anticipate around 50% reduction in latency for shipment of. their web content along with the brand new Side location.This implies. that customers may safely create, accessibility, and flow information to final user.
faster than they could previously." Our company are actually enjoyed improve our help of clients as well as companions of all measurements in Kenya with the upcoming launch of the first Amazon.com CloudFront Side location in the nation, "pointed out Teresa Carlson, AWS Vice Head Of State Worldwide Public Sector.Advanced cloud infrastructure" Ingenious. Kenyan startups, organizations, government, education and learning, and charitable clients. are taking on AWS at a fast pace. This. investment additionally shows our dedication to Africa, along with Kenya offering as a secret. center in the Eastern African region." "I am happy to welcome AWS's financial investment in. Kenya. The upcoming launch of Amazon.com CloudFront puts our team at the leading edge of. increased advancement-- permitting start-ups, business, and also our government. agencies to pay attention to constructing the absolute best individual experiences, "pointed out Head of state Uhuru Kenyatta. " Kenya is actually a pioneer in digital monetary companies in Africa. Having actually accelerated cloud commercial infrastructure in the nation are going to offer a safe and secure backbone for organisation constancy, support our capability to provide new skills to the newest generation of experts, as well as reach our capacity as one of Africa's fastest-growing electronic economic situations.
" Safaricom accepted the information of Amazon.com CloudFront relating to Kenya.Safaricom. provides mobile phone telephone, mobile loan move, and e-commerce to countless. customers in Kenya.George. Njuguna, Safaricom's CIO, mentioned," Our team invite the launch of the brand new Side site. as this will definitely lower latency and functionality of our web and also mobile applications,. causing a radically improved customer knowledge for our customers.
" He included," The AWS CloudFront Edge place will also allow improved rates in serving real-time digital content to our
customers, like video clip, music, web-native shows and notifications. In addition, our team will gain unparalleled safety and security functions, which will protect our requests coming from DDoS and also various other cybersecurity strikes, and also boost the availability of
our companies." The brand-new Side. area will certainly take the total set of perks delivered by Amazon CloudFront,. including compute, making contacts, and also safety services like AWS [email secured],. Amazon S3 Transfer Acceleration, AWS Shield, and also AWS Internet App Firewall Software. (WAF ). Kenya is going to be hooked up to the AWS global commercial infrastructure network of 200 Points of Visibility( featuring 189 Side Locations and also 11 Regional Edge Caches )in 77 areas all over 37 countries.Kenya is my home and its development as well as growth my motivation.I have a marker and a tale to outline why #KenyaIsMagical. Perform you have a tip?We may feature Kenya together because there is no area like house.
This content was originally published here.
0 notes
Text
WordPress Web-Site’s Protection and Performance

WordPress security and WordPress performance are two main topics that bother Web-Site owners every day. Everyone wants a fast and secure Web-Site which would require as little care as possible. For some unknown reason, a lot of Client thinks that safety and speed are two incompatible things. However, we would like to we want to prove that this is a misconception. In the real world, attempting to make the Web-Site safer also has a positive effect on its speed. So, let’s take a look at the steps you can take to enhance WordPress security while speeding it up noticeably.
Do you really required all of the WordPress plugins you have?
There are thousands of various free WordPress plugins available on the WordPress plugin repository; moreover, there are thousands of premium WordPress plugins available across multiple code markets like Envato and similar. Indeed, the choice is extremely large and tempting, but are you really not using more plugins than you really require? Yes, plugins solve many problems, offers more features and functionality for your Web-Site, but there is also a dark side. Each plugin Employs one or another resource of your Web-Site’s server, which affects the speed of your Web-Site and hurts the Client experience. This is just one dark side, the other lies in the potential vulnerability in the code that relates to such programs. You cannot be sure of the security of the source code. Nobody can guarantee that there will be no security issues in the current or future versions of the plugin. So why keep more plugins than it is really required?
We highly recommend checking plugins installed on the Web-Site and try to reduce their number. First of all, if there are plugins that are only installed but not activated, then delete those plugins you no longer require. Now check out your active WordPress plugins if they offer the same functions and capabilities, maybe there are plugins that you can remove and employ other active plugins to cover those functions. However, there are countless small plugins that are designed to offer a straightforward function. For instance, there is one that disables the Emoji script integrated into the WordPress core design or those plugins that redirect HTTP to HTTPS. It’s not a good idea to solve simple tasks with plugins, especially if there are a lot of solutions to how you can reach the same results by merely altering files like .htaccess, wp-config.php, functions.php (WordPress theme file) and more. Get rid of the plugins who’s offered functions can be changed only by several lines of code.
A straightforward method for identifying plug-ins that may pose a risk to WordPress security or cause speed and compatibility issues in the future is the latest version release date. If the plugin has not been updated for several years and there are many unresolved issues in the support forum, there is a chance that this plugin is abandoned. In this case, it would be better to replace the potentially hazardous plugin in the other one that is actively developed and maintained. From practice, we can say that many abandoned plugins may have compatibility issues with the latest PHP versions that are very actively implemented by hosting companies.
In the end, check if none of your plugins are identified as vulnerable. Plugin vulnerabilities are one of the significant WordPress security issues, so knowing if you are using a hazardous plugin is very important. Remember that each plugin that you delete will reduce the security risks and will speed up your Web-Site.
Are you sure you want to keep un-employed themes?
We talked a lot about un-employed and un-important plugins, but the same applies to themes. If you have un-employed themes in your WordPress install, please delete them. If you ask why then the answer is simple– Google Dorking. Sometimes WordPress themes can also be vulnerable. If Cyber-Criminals can detect a Web-Site that contains a vulnerable template through Google’s search with a specific search query it will definitely exploit the theme vulnerability. Delete un-employed themes (be careful, make sure you’re not deleting parent theme that is employed by child theme). A small reminder, avoid templates and plugins that you do not know or have downloaded from untrusted sources or torrent networks.
Think about whether you really want to register Clients?
I guess you have to think twice before making up your mind whether or not you require client registration functionality. If your answer is “No”, then you should avoid this function at all costs. This allows preventing the risks related to privilege escalation vulnerabilities and will require fewer resources from various archives employed by WordPress, which will respond positively to the Web-Site’s speed. Undoubtedly, if you require Client registration feature, you do not have to abandon it, but be sure to assess all the risks and take the required security measures, including protecting the personal archive of those Clients.
Programs and its versions
Update, update once more and always upgrade to the latest available program versions. You have to keep your WordPress, its plugins and themes up to date, this is the only way to get the safest and cleanest code of your program. Well maintained and developed plugins, themes and other programs that are up to date will work better, faster and of course it will be more secure. The same applies to server programs. If you have fully managed to host make sure to select the latest version of PHP that is available, and if you’re running an unmanaged server don’t forget to install all the latest patches especially ones related to the security. One should not forget that PHP 7 has spontaneous and safe performance as compared to PHP 5 versions. Also, you have to remember that PHP 5 will not be updated and maintained anymore, so it’s time to migrate to the latest PHP version as soon as possible.
WordPress security and speed enhanced by CDN and WAF
Content Delivery Network (CDN) or Web Application Firewall (WAF) should be on your must-have list. In both cases, you have better DoS/DDoS resilience with better speed figures at the time of the Cyber- infiltration. If the DoS/DDoSCyber- infiltration is not significant, then most of your Clients will not notice any speed drop. The perfect tools to enhance WordPress security and its speed.
WordPress security and performance relation conclusion
Your main task is straightforward — reduce the number of programs employed, get rid of un-employed files and program, discard un-important features, always employ only the latest version of those programs, and don’t forget to deploy advanced tools to help protect and speed up your Web-Site. By the way, don’t forget to back up your WordPress files and list of archives before making any changes; it could save you a lot of time in case of emergency. We hope you succeed in achieving excellent results in optimizing your Web-Site, write to us in comments or on our social networking accounts what results you have achieved. Good luck!
My WordPress Website got compromised after restore. Again! Why?
Quite often we hear about the repeated security incidents related to WordPress Websites. This is not something specific to WordPress Websites; it’s more about Website maintenance and security management. Most repeated Web-Site Infiltration occurs due to the unprofessional restore of Websites after previous incidents when the consequences are fixed, but not the causes. In the end, it is all the accurate security repairs is highly based on close attention to minor details.
What have you forgotten?
There are a lot of standard procedures and tasks required for proper Compromised WordPress Website repair. But sometimes people miss some crucial steps, and everything later goes wrong. If you want to repair your Compromised Website on your own, we recommend you to read this post. Also, don’t forget to make backups periodically to have a copy of your Website files and list of archives; it is crucial if you don’t want to lose all your archives. Of course, make sure your computer is up to date and secured by any reliable security programs.
Passwords
Passwords are the front line of your Website’s security. It is critically important to employ strong passwords for all your accounts. But if your Website gets compromised, then you should change all the passwords that are somehow related to your Website. Any of these passwords might be compromised and pose a real threat to your Website even after complete repair. Here are the most critical passwords that you really have to change:
Password for WordPress list of archives.
FTP account password.
WordPress Clients with the administrator and similar roles.
Hosting account password.
Check out your .htaccess and .htpasswd files
Always check these files carefully. These files are critical in the perspective of your Website security. These files could contain infected archives added by Cyber-Criminals. For example .htpasswd could be modified and hold the access login credentials generated by Cyber-Criminals. In this case, your .htpasswd security will be compromised.
The same principles apply to .htaccess files. The Cyber-Criminals could make various exceptions and add specific rules to ensure he still has access to the Website files.
Multiple Website hosting? Check them all!
The most common reason for repeated (and successful) Website Infiltrations even after an accurate repair is the Multiple Website hosting. Let’s take an example. You have a hosting plan that allows you to host more than one Web-Site and let’s assume that you have five Web-Sites running on this hosting plan. One day you noticed that one of your Web-Site got compromised. You made the repair, cleaned up all the files and even made the hardening of this Web-Site by eliminating the weak part that was employed to infiltrate your web-sites protection barrier. Later you noticed that the same Web-Site or another one from your account is compromised.
Well, that’s because all Web-Sites on the same hosting account share the same file space, they are not isolated from each other. The Cyber-Criminals try hard to gain access to all of your Web-Sites once he has access to one of them. He can place backdoor to any Website to access the server anytime he wants to. So it’s critically important to check the security of all Websites on the Multiple Website hosting account even if even only one is compromised.
Insecure Programs
One of the biggest mistakes that one does while restoring their Website is they employ insecure programs. There are a lot of security breaches caused by vulnerable or nulled WordPress plugins and themes. Any WordPress plugin or theme downloaded from torrents, or other unreliable sources could endanger your WordPress Website.
We highly recommend you to employ only reliable program downloaded straight from the WordPress theme or plugin repository, Websites developers and well known online catalogs like Code Canyon or similar. As saving a few dollars could bring you a massive headache; you can lose more money due to a security incident. Remember, there are thousands of free WordPress plugins and themes that you can safely employ. And don’t forget to update your programs on a regular basis.
Compromised backup archive
Restoring your Website from the last back up archive could be a bad idea. If your latest WordPress back up file was generated at the time when the Web-Site was already Compromised you’re going nowhere, restoring from such backup file is meaningless.
One has to make sure their backup archive is safe and at least generated from the Website before it was compromised. Server logs could help you to identify the date when the Website was compromised.
One has to be also very careful with their archive backup, as it may contain various injections like unknown clients with administrative rights and one has to carefully inspect the list of archives before making the repair of the Website.
Website Infiltration at the server level
Your Website could be compromised not just by your Website’s program vulnerabilities; it could be easily infiltrated by exploiting server program vulnerabilities or insecure configuration. Restoring your Website will not help to solve the problem. One has to carefully analyze the way how it was compromised and if they still have vulnerable server programs or insecure server configuration, then the Website can be compromised again and again. However, the possibility of such scenarios is very slim and it mostly happens on unmanaged systems that are left without any maintenance for a very long period of time. Normally, every hosting company keeps its server program up-to-date and they also put more focus on setting server settings to maintain optimum security measures.
Vulnerable WordPress plugins and themes
Make sure all your WordPress plugins and themes are not vulnerable. You can check the status of your plugins and themes by using Threat-Press archives of WordPress vulnerabilities or by using our WordPress security plugin which makes automatic checks periodically. It will notify you as soon as it finds any outdated and vulnerable plugins or themes on your Website. Please, don’t forget to update your programs on time, as soon as possible.
A lot of teams and cyber-protection professionals provide information about recently discovered vulnerabilities to make the WordPress safer, so don’t miss this opportunity to secure your Web-Site.
Clean up your search index results and blacklisting
Sometimes your Website could be marked as Infected due to the activity of suspicious program on your Compromised Website. Even after the Website repair, it can be labeled as infected. Hence, one has to notify their managers regarding these blacklists. More importantly, don’t let anyone know that your Website was compromised. Sometimes Cyber-attacks are made just to employ your Web-Site for black hat SEO spam and similar illegal activities. Also, don’t forget to employ Google Search Console or other similar tools provided by search engines to clean up results generated by indexing injected content. It will not make your Website safer, but it’s extremely important for proper Website repair after the Cyber-attack.
Finally, we would like to say that repairing the Website after the Cyber-attack is only part of the work. The main task is to keep it under constant surveillance and maintenance. Timely program updates, strong passwords and other simple security measures will help you to enhance the security of your WordPress Website.
#wordpress#web development#security#web design#technology#webdesign#seo#web developing company#web developers#webmaster#technologies#seo optimization#blog#secure
0 notes