#Attacking SQL Server
Explore tagged Tumblr posts
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
25 notes
·
View notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
With the AO3 downtime/ddos attack getting people antsy, longing for the days where we still had our fandom fic sites we could browse (or at least missing works being available in multiple locations instead of concentrated on one amazing site that unfortunately attracts bad actors and risks disappearing forever), consider setting up an efiction server!
All you need is a self-hosted website and minimal understanding of SQL (if you've successfully managed a self-hosted wordpress instance, you're probably equipped to install and manage this!).
It's been built just for such occasions, to allow people to create their own AO3s or ff.nets, and cross-posting is something we should think about getting back to in these uncertain times!
24 notes
·
View notes
Text
Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe

Source: https://thehackernews.com/2024/01/turkish-hackers-exploiting-poorly.html
More info: https://www.securonix.com/blog/securonix-threat-research-security-advisory-new-returgence-attack-campaign-turkish-hackers-target-mssql-servers-to-deliver-domain-wide-mimic-ransomware/
5 notes
·
View notes
Text
10 security tips for MVC applications in 2023

Model-view-controller or MVC is an architecture for web app development. As one of the most popular architectures of app development frameworks, it ensures multiple advantages to the developers. If you are planning to create an MVC-based web app solution for your business, you must have known about the security features of this architecture from your web development agency. Yes, MVC architecture not only ensures the scalability of applications but also a high level of security. And that’s the reason so many web apps are being developed with this architecture. But, if you are looking for ways to strengthen the security features of your MVC app further, you need to know some useful tips.
To help you in this task, we are sharing our 10 security tips for MVC applications in 2023! Read on till the end and apply these tips easily to ensure high-security measures in your app.
1. SQL Injection: Every business has some confidential data in their app, which needs optimum security measures. SQL Injection is a great threat to security measures as it can steal confidential data through SQL codes. You need to focus on the prevention of SQL injection with parameterized queries, storing encrypted data, inputs validation etc.
2. Version Discloser: Version information can also be dangerous for your business data as it provides hackers with your specific version information. Accordingly, they can attempt to attack your app development version and become successful. Hence, you need to hide the information such as the server, x-powered-by, x-sourcefiles and others.
3. Updated Software: Old, un-updated software can be the reason for a cyber attack. The MVC platforms out there comprise security features that keep on updating. If you also update your MVC platform from time to time, the chances of a cyber attack will be minimized. You can search for the latest security updates at the official sites.
4. Cross-Site Scripting: The authentication information and login credentials of applications are always vulnerable elements that should be protected. Cross-Site Scripting is one of the most dangerous attempts to steal this information. Hence, you need to focus on Cross-Site Scripting prevention through URL encoding, HTML encoding, etc.
5. Strong Authentication: Besides protecting your authentication information, it’s also crucial to ensure a very strong authentication that’s difficult to hack. You need to have a strong password and multi-factor authentication to prevent unauthorized access to your app. You can also plan to hire security expert to ensure strong authentication of your app.
6. Session Management: Another vital security tip for MVA applications is session management. That’s because session-related vulnerabilities are also quite challenging. There are many session management strategies and techniques that you can consider such as secure cookie flags, session expiration, session regeneration etc. to protect access.
7. Cross-Site Request Forgery: It is one of the most common cyber attacks MVC apps are facing these days. When stires process forged data from an untrusted source, it’s known as Cross-Site Request Forgery. Anti-forgery tokens can be really helpful in protecting CSRP and saving your site from the potential danger of data leakage and forgery.
8. XXE (XML External Entity) Attack: XXE attacks are done through malicious XML codes, which can be prevented with the help of DtdProcessing. All you need to do is enable Ignore and Prohibit options in the DtdProcessing property. You can take the help of your web development company to accomplish these tasks as they are the best at it.
9. Role-Based Access Control: Every business has certain roles performed by different professionals, be it in any industry. So, when it comes to giving access to your MVC application, you can provide role-based access. This way, professionals will get relevant information only and all the confidential information will be protected from unauthorized access.
10. Security Testing: Finally, it’s really important to conduct security testing on a regular basis to protect business data on the app from vulnerability. Some techniques like vulnerability scanning and penetration testing can be implied to ensure regular security assessments. It’s crucial to take prompt actions to prevent data leakage and forgery as well.
Since maintaining security should be an ongoing process rather than a one-time action, you need to be really proactive with the above 10 tips. Also, choose a reliable web development consulting agency for a security check of your website or web application. A security expert can implement the best tech stack for better security and high performance on any website or application.
#web development agency#web development consulting#hire security expert#hire web developer#hire web designer#website design company#website development company in usa
2 notes
·
View notes
Text
How to Choose the Right Security Stack for Your Business Website
In an age where cyberattacks are growing more frequent and sophisticated, a secure website isn’t just a best practice—it’s a business necessity. Whether you're running an eCommerce store, SaaS product, or a company website, your security stack plays a critical role in protecting sensitive data, maintaining customer trust, and ensuring compliance.
A professional Web Development Company will always prioritize building a tailored security framework that addresses both current risks and future vulnerabilities. But how do you decide which tools and layers should be part of your website's defense system?
Let’s break down what a “security stack” means and how to choose the right one for your business.
What Is a Website Security Stack?
A security stack is a layered approach to website protection. It combines various technologies and tools—each targeting a specific set of threats—to create a comprehensive shield around your web infrastructure.
Think of it like a multi-lock system for your home:
One layer protects your doors (authentication)
Another secures your windows (firewalls)
And another watches for unusual activity (monitoring tools)
When configured properly, these layers work together to identify, prevent, and respond to attacks—without compromising website speed or functionality.
1. Start With an SSL/TLS Certificate
This is the most basic, yet crucial, layer. An SSL/TLS certificate encrypts the data exchanged between your website and its users. It ensures that personal information, passwords, and payment details can't be intercepted by third parties.
Make sure:
Your certificate is issued by a trusted Certificate Authority (CA)
It’s renewed automatically
All pages (not just the login or checkout) are secured with HTTPS
Modern browsers now flag non-HTTPS sites as "Not Secure"—a red flag for users and search engines alike.
2. Use a Web Application Firewall (WAF)
A WAF monitors and filters HTTP traffic between your website and the internet. It blocks common threats like SQL injection, cross-site scripting (XSS), and brute-force attacks.
Choose a WAF that:
Offers customizable rules
Supports DDoS protection
Provides real-time traffic analytics
Popular WAFs include Cloudflare, Sucuri, and AWS WAF—each with varying levels of control and reporting. Your development agency can help configure the best fit based on your tech stack and risk exposure.
3. Implement Secure Authentication Protocols
Weak passwords and poorly managed login systems are among the top causes of data breaches. Strengthen this layer with:
Two-Factor Authentication (2FA)
OAuth2 or SSO integrations for enterprise-level users
Rate-limiting and lockout mechanisms for failed login attempts
Make sure admin panels, user dashboards, and CMS backends are protected with hardened authentication protocols—not just simple passwords.
4. Harden Your CMS and Framework
If you’re using platforms like WordPress, Webflow, or custom frameworks like Laravel or Django, security starts with how well the code and plugins are managed.
Best practices include:
Removing unused plugins and themes
Regularly updating core software
Using only trusted third-party packages
Applying role-based access controls
A Web Development Company will often audit your codebase and extensions for hidden vulnerabilities and outdated dependencies.
5. Monitor and Log Everything
Security isn’t static—it requires continuous monitoring. Use log management and monitoring tools to detect suspicious behavior in real time.
Your stack should include:
Application-level logging (failed logins, unusual traffic)
Server and file integrity monitoring
Alerts for changes in configuration or permissions
Tools like Sentry, Datadog, or even open-source solutions like Fail2Ban can help detect threats early before they escalate.
6. Secure Your Hosting Environment
Your server and hosting setup must be as secure as your code. Ensure:
Firewalls are configured at the OS level
SFTP (not FTP) is used for file transfers
Admin panels are IP-restricted or hidden behind VPNs
Automated daily backups are stored off-site
Many breaches happen at the server level due to misconfigured permissions or outdated software—especially on unmanaged VPS environments.
7. Regular Penetration Testing and Updates
Security isn’t a one-time setup. Schedule regular penetration testing and vulnerability scans to identify new risks. Ensure:
Your software dependencies are up-to-date
Security patches are applied immediately
Reports are reviewed and acted upon
This proactive approach protects your business from evolving threats and demonstrates compliance with security standards and regulations.
Conclusion
Choosing the right security stack is not just about installing tools—it's about building a customized, layered defense system that protects your website from every angle. From SSL certificates and firewalls to authentication protocols and monitoring tools, each element plays a role in safeguarding your digital assets.
To ensure nothing is overlooked, work with a Web Development Company that specializes in security-first development. With the right guidance and configuration, your website can stay protected, performant, and trusted—no matter how fast your business grows.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
How PHP Helps Websites Work Behind the Scenes
When visitors interact with a site—filling in forms, logging in, or making purchases—they do not typically pay attention to the process occurring in the background. Those seamless experiences are fueled by robust server-side scripting, and PHP is near the head of the list of technologies fueling that capability. Whether an eCommerce site, blog, or internally developed application, PHP is at the core of delivering dynamic, interactive web experiences.
Famous for its efficiency and dependability, PHP drives almost 80% of websites across the world, such as leading platforms like WordPress, Facebook, and Mailchimp. It processes data, manages sessions, and works seamlessly with databases, making it possible for websites to operate securely and in real time. For companies wanting scalable and affordable solutions, collaborating with the top PHP development agencies guarantees that their digital platforms operate at speed and accuracy.
How PHP Powers Website Functionality
PHP serves as the central engine of most web applications. From handling user inputs to creating personalized content, it makes the website interact proportionally with each user action. For example, when a guest enters a login form, PHP authenticates the credentials and manages access. In the same way, PHP scripts handle shopping carts, process orders, and manage inventory on online shopping websites—all without the guest ever seeing the intricacy involved in the process.
One such prime example is WordPress, which employs PHP to retrieve contents from a database and present them dynamically according to user actions. If PHP is not running in the background, real-time delivery of content would not be feasible.
PHP and Database Integration
Specific databases like MySQL, PostgreSQL, and others are tightly coupled with the PHP scripting language. This is essential for efficiently providing web applications with storing, retrieving, or updating data since anything can range from user verification, blog maintenance, or even order processing. In terms of data security, accurate PHP code will adopt the best security practices to thwart such threats as SQL injection attacks, data grabbing and unauthorized accessing.
Why PHP Remains a Top Choice
By offering tight integration with MySQL, PostgreSQL, and many other popular databases, PHP enables web applications to store, retrieve, and update data efficiently and securely-from user login to blog maintenance to order processing. Secure PHP code would implement best security practices to prevent threats such as SQL injection attacks, data theft, and unauthorized access.
0 notes
Text
Data hacks and identity theft have been making the headlines in recent years, making the security of your website more important than ever before. This is especially true if you handle financial transactions through your company's site, as you'll be processing your customers' sensitive financial data. Fortunately, you have many tools available to you to help ensure your website is as secure as possible. ScanMyServer ScanMyServer provides a comprehensive report of vulnerabilities throughout your website and on your server. It can identify PHP code injection, SQL injection, blind SQL injection, HTTP header injection and other scripting vulnerabilities. This service is free, and there is no registration required to test your site. You'll receive your results via email and can download a security badge to display on your site for your customers' peace of mind. Vega Vega is a security scanner designed for use with web applications. It provides an easy-to-use interface that makes the process as streamlined as possible, even for those who are unfamiliar with web security testing. It can help identify cross-site scripting, SQL injection and other application vulnerabilities. This open source application is backed by a powerful API for even greater customization and capability. Metasploit Metasploit makes use of the latest ethical hacking techniques to detect website vulnerabilities. This is what is known as penetration testing and has become more and more popular in recent years. If ethical hackers can break through your website's security protocols, then data thieves undoubtedly will be able to as well. Identifying these vulnerabilities early on can help you make the changes needed to secure your site from the latest threats. Sucuri Sucuri is a free website scanner that can detect viruses and malware. It can also identify and website errors or broken code, as well as out-of-date software. It can even alert you if your website has been blacklisted. This tool is compatible with a variety of popular website-building platforms, including WordPress, Drupal, Magento, Joomla and more. Qualys SSL Server Test This tool analyzes the configuration of your SSL web server and is designed specifically for secure (https) websites. You'll get in-depth analysis of your URL to help you identify vulnerabilities. This includes your site's expiration day, SSL/TLS version, overall security rating, protocol details and more. This is another free service, and neither your personal information nor your test results are used for any purpose other than to provide you with the analysis you have requested. Wapiti Wapiti scans for a variety of vulnerabilities in web applications. Similar to penetration testing, this application injects data to see if various scripts are vulnerable to attacks. It is capable of detecting file disclosure and inclusion vulnerabilities, site configuration issues, and a variety of injection complications. It is important to note, though, that while free, this is a command-line application. This may be a bit difficult for beginners to get the hang of and is better suited to advanced users. Wireshark Wireshark is another penetration testing application. It specializes in analyzing network protocols, getting into the tiniest details of your packet information and decryption. It's compatible with all the major operating systems, including Windows, OS X, Linux, Solaris and more. The application is free to download and can be viewed through a user interface or in TTY-mode TShark utility. Skipfish Skipfish crawls through your website, one page at a time, to detect any vulnerabilities in the code. This open source web application is free to download and use, and it is optimized for HTTP handling. It is capable of handling up to 2,000 requests per second without putting a strain on your CPU. Compatible with Windows, MacOS X, Linux and FreeBSD operating systems, this security application can detect even subtle flaws, like blind injection vectors.
Detectify Detectify is a suite of more than 100 automated security tests for your website. In total, it checks for over 700 distinct vulnerabilities. The team of ethical hackers behind the platform continually update the scans to detect the latest threats as they emerge, keeping your website secure in real time. You can test Detectify for free for 21 days, after which you'll have to pay a recurring membership fee for the ongoing security service. Siteguarding Siteguarding is a free online tool for detecting viruses, malware, phishing, injected spam, defacement and more. It can also help you clean and remove these threats from your website to ensure your security. The company also provides web hosting services, for a complete web security management package. These are just a few of the many website security options you have available to you, so there is no excuse for not having your website provide the latest security protections for your customers. Try out a few scans today to identify areas where your company website might be vulnerable so that you can regain control.Ken Lynch is an enterprise software startup veteran, who has always been fascinated by what drives workers to work and how to make work more engaging. Ken founded Reciprocity to pursue just that. He has propelled Reciprocity's success with this mission-based goal of engaging employees with the governance, risk, and compliance goals of their company in order to create more socially minded corporate citizens. Ken earned his BS in Computer Science and Electrical Engineering from MIT.
0 notes
Text
Reliable Website Maintenance Services In India | NRS Infoways
In today’s hyper‑connected marketplace, a website is far more than a digital brochure—it is the beating heart of your brand experience, your lead‑generation engine, and your most valuable sales asset. Yet many businesses still treat their sites as “launch‑and‑forget” projects, only paying attention when something breaks. At NRS Infoways, we understand that real online success demands continuous care, proactive monitoring, and seamless enhancements. That’s why we’ve built our Reliable Website Maintenance Services In India to deliver round‑the‑clock peace of mind, bulletproof performance, and measurable ROI for forward‑thinking companies like yours.
Why Website Maintenance Matters—And Why “Reliable” Makes All the Difference
Search engines reward fast, secure, and regularly updated sites with higher rankings; customers reward them with trust and loyalty. Conversely, a sluggish, outdated, or vulnerable site can cost you traffic, conversions, and brand reputation—sometimes overnight. Our Reliable Website Maintenance Services In India go beyond the basic “fix‑it‑when‑it‑breaks” model. We combine proactive health checks, performance tuning, security hardening, and content optimization into a single, cohesive program that keeps your digital storefront open, polished, and ready for growth.
What Sets NRS Infoways Apart?
1. Proactive Performance Monitoring
We leverage enterprise‑grade monitoring tools that continuously scan load times, server resources, and user journeys. By identifying bottlenecks before they escalate, we ensure smoother experiences and higher conversion rates—24/7.
2. Robust Security & Compliance
From real‑time threat detection to regular firewall updates and SSL renewals, your site stays impervious to malware, SQL injections, and DDoS attacks. We align with global standards such as GDPR and PCI‑DSS, keeping you compliant and trustworthy.
3. Seamless Content & Feature Updates
Launching a new product line? Running a seasonal promotion? Our dedicated team updates layouts, landing pages, and plugins—often within hours—to keep your messaging sharp and relevant without disrupting uptime.
4. Data‑Driven Optimization
Monthly analytics reviews highlight user behavior, bounce rates, and conversion funnels. We translate insights into actionable tasks—A/B testing CTAs, compressing heavy images, or refining navigation—all folded into our maintenance retainer.
5. Transparent Reporting & SLAs
Every client receives detailed monthly reports covering task logs, incident resolutions, and performance metrics. Our Service Level Agreements guarantee response times as low as 30 minutes for critical issues, underscoring the “Reliable” in our Reliable Website Maintenance Services In India.
Real‑World Impact: A Success Snapshot
A Delhi‑based B2B SaaS provider reached out to NRS Infoways after repeated downtime eroded user trust and slashed demo bookings by 18 %. Within the first month of onboarding, we:
Migrated their site to a high‑availability cloud cluster
Deployed a Web Application Firewall (WAF) to fend off bot attacks
Compressed multimedia assets, cutting average load time from 4.2 s to 1.3 s
Implemented weekly backup protocols with versioned restores
Result? Organic traffic climbed 27 %, demo sign‑ups rebounded 31 %, and support tickets fell by half—proving that consistent, expert care translates directly into revenue.
Flexible Plans That Scale With You
Whether you manage a lean startup site or a sprawling enterprise portal, we offer tiered packages—Basic, Professional, and Enterprise—each customizable with à‑la‑carte add‑ons like e‑commerce catalog updates, multi‑language support, or advanced SEO audits. As your business evolves, our services scale seamlessly, ensuring you never pay for overhead you don’t need or sacrifice features you do.
Partner With NRS Infoways Today
Your website is too important to leave to chance. Join the growing roster of Indian businesses that rely on NRS Infoways for Reliable Website Maintenance Services In India and experience the freedom to innovate while we handle the technical heavy lifting. Ready to protect your digital investment, delight your visitors, and outpace your competition?
Connect with our maintenance experts now and power your growth with reliability you can measure.
0 notes
Text
SQL injection

we will recall SQLi types once again because examples speak louder than explanations!
In-band SQL Injection
This technique is considered the most common and straightforward type of SQL injection attack. In this technique, the attacker uses the same communication channel for both the injection and the retrieval of data. There are two primary types of in-band SQL injection:
Error-Based SQL Injection: The attacker manipulates the SQL query to produce error messages from the database. These error messages often contain information about the database structure, which can be used to exploit the database further. Example: SELECT * FROM users WHERE id = 1 AND 1=CONVERT(int, (SELECT @@version)). If the database version is returned in the error message, it reveals information about the database.
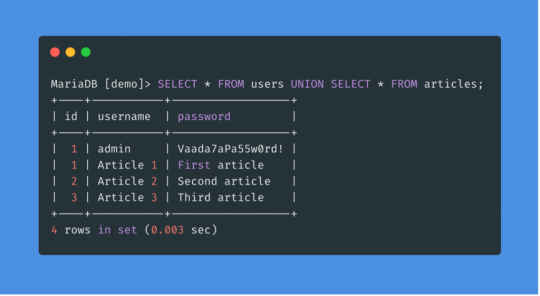
Union-Based SQL Injection: The attacker uses the UNION SQL operator to combine the results of two or more SELECT statements into a single result, thereby retrieving data from other tables. Example: SELECT name, email FROM users WHERE id = 1 UNION ALL SELECT username, password FROM admin.
Inferential (Blind) SQL Injection
Inferential SQL injection does not transfer data directly through the web application, making exploiting it more challenging. Instead, the attacker sends payloads and observes the application’s behaviour and response times to infer information about the database. There are two primary types of inferential SQL injection:
Boolean-Based Blind SQL Injection: The attacker sends an SQL query to the database, forcing the application to return a different result based on a true or false condition. By analysing the application’s response, the attacker can infer whether the payload was true or false. Example: SELECT * FROM users WHERE id = 1 AND 1=1 (true condition) versus SELECT * FROM users WHERE id = 1 AND 1=2 (false condition). The attacker can infer the result if the page content or behaviour changes based on the condition.
Time-Based Blind SQL Injection: The attacker sends an SQL query to the database, which delays the response for a specified time if the condition is true. By measuring the response time, the attacker can infer whether the condition is true or false. Example: SELECT * FROM users WHERE id = 1; IF (1=1) WAITFOR DELAY '00:00:05'--. If the response is delayed by 5 seconds, the attacker can infer that the condition was true.
Out-of-band SQL Injection
Out-of-band SQL injection is used when the attacker cannot use the same channel to launch the attack and gather results or when the server responses are unstable. This technique relies on the database server making an out-of-band request (e.g., HTTP or DNS) to send the query result to the attacker. HTTP is normally used in out-of-band SQL injection to send the query result to the attacker's server. We will discuss it in detail in this room.
Each type of SQL injection technique has its advantages and challenges.
3 notes
·
View notes
Text
Which Computer Course Is Most in Demand in India Right Now?

India's technology landscape is one of the most dynamic in the world, characterized by rapid digital transformation, a thriving startup ecosystem, and a robust IT services sector. This constant evolution means that the demand for specific computer skills is always shifting. If you're considering enhancing your skills or embarking on a new career path, understanding which computer courses are currently most in demand is crucial.
While "demand" can fluctuate slightly based on region and industry, several core technological areas consistently show high growth and require specialized training. Based on current industry trends, here's a look at the computer courses generating significant buzz and opening up numerous opportunities across India in 2025.
Top Computer Courses Highly Sought After in India
1. Artificial Intelligence (AI) & Machine Learning (ML)
AI and ML are no longer just buzzwords; they are at the core of innovation in almost every sector, from healthcare and finance to e-commerce and manufacturing. In India, the adoption of AI technologies is accelerating, leading to a strong demand for professionals who can develop, implement, and manage AI systems.
Why in Demand: Automation, data analysis, predictive modeling, smart solutions, and the push for digital transformation in various industries.
Key Skills Learned: Python programming, machine learning algorithms, deep learning, natural language processing (NLP), computer vision.
2. Data Science & Big Data Analytics
With the explosion of data generated daily, the ability to collect, process, analyze, and interpret large datasets is invaluable. Data scientists and analysts help businesses make informed decisions, identify trends, and predict future outcomes.
Why in Demand: Every organization, regardless of size, is grappling with data. The need for professionals who can extract meaningful insights is paramount.
Key Skills Learned: Python/R programming, SQL, statistical modeling, data visualization, Big Data technologies (Hadoop, Spark).
3. Full-Stack Web Development
As businesses increasingly establish and expand their online presence, the demand for versatile web developers who can handle both the front-end (what users see) and back-end (server-side logic) of applications remains consistently high.
Why in Demand: Digitalization of businesses, e-commerce boom, proliferation of web-based applications, and the need for seamless user experiences.
Key Skills Learned: HTML, CSS, JavaScript (with frameworks like React, Angular, Vue.js), Node.js, Python (Django/Flask), Ruby on Rails, databases (SQL, MongoDB).
4. Cybersecurity
With the increasing number of cyber threats and data breaches, organizations across India are investing heavily in cybersecurity measures. Professionals who can protect sensitive data, prevent attacks, and ensure network security are critically needed.
Why in Demand: Growing digital transactions, increased online data storage, and the imperative for robust data protection laws.
Key Skills Learned: Network security, ethical hacking, cryptography, risk management, incident response, security tools.
5. Cloud Computing (AWS, Azure, Google Cloud)
Cloud adoption is no longer a luxury but a necessity for many Indian businesses seeking scalability, flexibility, and cost efficiency. Expertise in major cloud platforms is a highly sought-after skill.
Why in Demand: Cloud migration, managing cloud infrastructure, deploying applications in the cloud, cost optimization.
Key Skills Learned: Specific cloud platforms (AWS, Azure, GCP), cloud architecture, virtualization, containerization (Docker, Kubernetes).
6. DevOps
DevOps practices streamline software development and IT operations, leading to faster, more reliable software delivery. Professionals with DevOps skills are crucial for modern software companies aiming for efficiency and continuous integration/delivery.
Why in Demand: Need for faster product cycles, automation of development pipelines, and improved collaboration between teams.
Key Skills Learned: CI/CD tools (Jenkins, GitLab CI), scripting (Python, Bash), configuration management (Ansible), containerization (Docker, Kubernetes), cloud platforms.
Factors Driving Demand in India
Several factors contribute to these trends:
Digital India Initiative: Government push for digitalization across all sectors.
Startup Boom: A vibrant startup ecosystem constantly innovating and requiring new tech talent.
Global Capability Centers (GCCs): International companies setting up R&D and tech operations in India.
Remote Work Flexibility: Opening up opportunities across different regions and cities.
How to Choose the Right Course for You
While these courses are in high demand, the "best" one for you depends on your interests, aptitude, and career goals.
Assess Your Interest: Are you passionate about data, building applications, or securing systems?
Research Career Paths: Understand the daily tasks and long-term prospects associated with each field.
Look for Practical Training: Opt for computer courses that emphasize hands-on projects and real-world scenarios. Many computer training institute in Ahmedabad and other cities offer programs with strong practical components.
Consider Faculty and Curriculum: Ensure the instructors have industry experience and the curriculum is up-to-date with the latest trends.
Check for Placement Support: If securing a job quickly is a priority, inquire about career services or placement assistance.
Investing in an in-demand computer course is a strategic move for your future career. By aligning your learning with current industry needs, you significantly enhance your employability and open doors to exciting opportunities in India's booming tech sector.
Contact us
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes
Text
Common PHP Mistakes That Make Your App Insecure
PHP is a widely used powerful web development language. It is an open source server- side back-end programming language that can be used for several purposes such as creating websites, applications, customer relationships management systems and more. PHP is a general purpose language that can be embedded into HTML also. PHP is known for its efficient and optimized code that enables websites to load faster compared to many other web development technologies. For those who wish to have a successful career in PHP, Srishti campus is a best choice, Srishti is one of the best PHP training centre in Trivandrum.
PHP development mistakes can lead to security vulnerabilities and insecure applications. Many PHP applications are vulnerable due to common mistakes made by the developers. Common PHP mistakes includes,
Neglecting input validation and sanitization This happens when you insert user input directly into SQL queries without sanitization. Attackers can manipulate your database queries to extract, delete, or alter data. This critical mistake allows attackers in SQL injection and cross-site scripting.
Using outdated PHP versions Outdated PHP versions can result in security vulnerabilities. Staying up-to-date with the latest versions is crucial for security.
Improper session handling Weak and improper session handling can lead to hijacking.
Ignoring security headers and configurations Proper security headers and configurations can help in preventing various attacks and help in protecting applications.
No CSRF protection Cross-Site Request Forgery (CSRF) lets attackers perform actions on behalf of authenticated users without their consent.
Displaying errors in production Showing detailed error messages can lead to exposing sensitive information such as file paths or database structure. Other mistakes Ignoring errors, leaving development settings, and skipping backups can lead to security risks.
PHP is powerful, but along with the power there comes responsibility also. Avoiding these common mistakes can lead to the improved application's security. Use modern PHP practices, sanitize all input, and regularly update your software stack. The best Php training centres in the city offer comprehensive courses in programming languages like PHP to equip students with industry-relevant skills. Security isn’t a one-time fix — it’s an ongoing process. A few lines of secure code today can save an application from a major breach tomorrow.
0 notes
Text
Web Security 101: Protecting Against Common Threats
In today’s digital world, websites serve as the face of businesses, educational institutions, and organisations. As online interactions grow, so do the threats targeting web applications. From malware attacks to phishing schemes, cyber threats are more sophisticated and frequent than ever. Whether you’re a business owner, developer, or tech enthusiast, understanding the fundamentals of web security is essential to ensure your digital presence remains safe and resilient.
In this article, we’ll cover the essentials of web security, outline common web threats, and discuss best practices to protect against them. For students and professionals pursuing technology careers, especially those enrolled in programs like the Full Stack Developer Course in Bangalore, mastering these security concepts is not just beneficial—it’s essential.
What is Web Security?
Web security, also known as cybersecurity for web applications, is the protective measure taken to safeguard websites and online services against unauthorised access, misuse, modification, or destruction. These protections help maintain the confidentiality, integrity, and availability (CIA) of information and services online.
With the increasing digitisation of services, web applications are a common target for attackers due to the valuable data they often store, such as user credentials, personal information, and payment details.
Common Web Security Threats
Here are some of the most common threats that web applications face today:
1. SQL Injection (SQLi)
SQLi a type of attack where malicious SQL queries are inserted into input fields to manipulate databases. If input validation is not properly handled, attackers can retrieve, alter, or delete sensitive data from the database.
2. Cross-Site Scripting (XSS)
XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. This can give rise to data theft, session hijacking, and the spreading of malware.
3. Cross-Site Request Forgery (CSRF)
In a CSRF attack, a malicious website tricks a user into performing actions on a different site where they’re authenticated. This can result in unauthorised fund transfers, password changes, and more.
4. Man-in-the-Middle (MITM) Attacks
These attacks happen when an attacker intercepts communication between two parties. They can steal or manipulate data without either party being aware.
5. Denial of Service (DoS) and Distributed DoS (DDoS)
These attacks flood a website with traffic, turning it slow or entirely unavailable to legitimate users. DDoS attacks can cripple even robust web infrastructures if not mitigated properly.
6. Zero-Day Exploits
Zero-day attacks exploit unknown or unpatched vulnerabilities in software. These are particularly dangerous because there’s often no fix available when the attack occurs.
Best Practices to Protect Against Web Threats
1. Use HTTPS
Securing your website with HTTPS encrypts data transferred between users and your server. It also ensures that data isn't altered during transmission. SSL/TLS certificates are now a basic requirement for modern websites.
2. Input Validation and Sanitisation
Never trust user input. Validate and sanitise all inputs on both client and server sides. This helps in preventing SQL injections, XSS, and other injection-based attacks.
3. Implement Proper Authentication and Session Management
Strong passwords, multi-factor authentication (MFA), and secure session management are crucial. Implement session expiration and automatic logout features to reduce unauthorised access risks.
4. Regularly Update Software and Libraries
Web frameworks, plugins, and server software should be regularly updated to patch known vulnerabilities. Automated tools can help identify outdated components in your tech stack.
5. Use Web Application Firewalls (WAF)
WAFs protect web applications by filtering and monitoring HTTP traffic. They can prevent many common attacks before they reach your server.
6. Data Encryption
Sensitive data—both at rest and in transit—should be encrypted. This reduces the damage caused by data breaches.
7. Conduct Regular Security Audits
Perform vulnerability assessments and penetration testing regularly to identify and fix security flaws in your applications.
8. Security Awareness Training
Educate employees and developers on security best practices. Social engineering attacks often target human error, so awareness is a strong line of defence.
Role of Developers in Web Security
Security isn't just the job of cybersecurity specialists. Developers play a critical role in implementing secure code and architecture. Understanding the OWASP Top 10—an industry-standard list of the most critical web application security risks—is a must for anyone writing backend or frontend code.
This is why modern tech education emphasises security fundamentals. At ExcelR, we integrate security concepts across our tech courses, including our Full Stack Developer Course in Bangalore. We believe that a well-rounded developer isn’t just one who can build efficient applications—but one who can build secure ones too.
Real-World Impact of Poor Web Security
Neglecting web security can have severe consequences. Major data breaches have cost companies millions in losses, legal penalties, and reputation damage. In extreme cases, companies have shut down operations permanently after suffering massive cyberattacks.
Even smaller websites are not immune. Bots and automated scripts scan thousands of websites daily for vulnerabilities, often targeting outdated CMS platforms or poorly configured servers.
Final Thoughts
Web security is not a one-time task—it’s an ongoing process of identifying risks, updating systems, and educating users and developers. With the evolution of cyber threats, staying informed and proactive is the best defense.
Whether you’re running a personal blog or developing enterprise-level web applications, implementing strong security measures can save you from irreversible damage. And if you're aspiring to become a tech professional, enrolling in a comprehensive program like the Full Stack Developer Course in Bangalore from ExcelR can give you both the technical and security skills required to thrive in today’s digital landscape.
For more details, visit us:
Name: Full Stack Developer Course In Bangalore
Address: No 9, Sri Krishna Akshaya, 1st Floor, 27th Main, 100 Feet Ring Rd, 1st Phase, BTM Layout, Bengaluru, Karnataka 560068
Phone: 9513446548
0 notes