#Basic Cybersecurity Principles
Explore tagged Tumblr posts
Video
youtube
Simple-Security-Information-and-Event-Management-SIEM
#youtube#cybersecurity#Simple-Security-Information-and-Event-Management-SIEM#Basic Cybersecurity Principles#python
0 notes
Text
**From PCI DSS to HIPAA: Ensuring Compliance with Robust IT Support in New York City**
Introduction
In contemporary digital world, organisations are a growing number of reliant on science for their operations. This dependence has caused a heightened focus on cybersecurity and compliance specifications, specifically in regulated industries like healthcare and finance. For services working in New York City, wisdom the nuances of compliance frameworks—specifically the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA)—is quintessential. Navigating those policies requires potent IT give a boost to, which encompasses everything from community infrastructure to documents management.
With the rapid advancement of technological know-how, organizations ought to additionally remain abreast of high-quality practices in details technologies (IT) give a boost to. This article delves into how organizations can ensure that compliance with PCI DSS and HIPAA thru triumphant IT processes whilst leveraging materials from accurate providers like Microsoft, Google, Amazon, and others.
Understanding PCI DSS What is PCI DSS?
The https://brooksxaoj631.over.blog/2025/04/navigating-cybersecurity-in-the-big-apple-essential-it-support-solutions-for-new-york-businesses.html Payment Card Industry Data Security Standard (PCI DSS) is a group of safety principles designed to look after card tips all the way through and after a economic transaction. It was once proven by using significant credit card enterprises to fight growing times of fee fraud.
Why is PCI DSS Important?
Compliance with PCI DSS enables groups defend touchy economic recordsdata, thereby modifying visitor trust and slicing the possibility of info breaches. Non-compliance can bring about intense consequences, such as hefty fines or maybe being banned from processing credit score card transactions.

youtube
Key Requirements of PCI DSS Build and Maintain a Secure Network: This carries fitting a firewall to preserve cardholder knowledge. Protect Cardholder Data: Encrypt kept files and transmit it securely. Maintain a Vulnerability Management Program: Use antivirus utility and develop protect structures. Implement Strong Access Control Measures: Restrict entry to in basic terms people that want it. Regularly Monitor and Test Networks: Keep observe of all get admission to to networks and aas a rule look at various protection tactics. Maintain an Information Security Policy: Create insurance policies that cope with defense necessities. Exploring HIPAA Compliance What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) sets the ordinary for conserving sensitive sufferer know-how in the healthcare trade. Any entity that offers with blanketed well being know-how (PHI) have got to adjust to HIPAA regulations.
Importance of HIPAA Compliance
HIPAA compliance no longer handiest protects affected person privateness however also guarantees more suitable healthcare outcome with the aid of permitting maintain sharing of affected person data between permitted entities. Violations can cause titanic fines, prison results, and wreck to popularity.
" style="max-width:500px;height:auto;">

Core Components of HIPAA Compliance Privacy Rule: Establishes countr
2 notes
·
View notes
Text
2 notes
·
View notes
Text
"Protect Defenders" is actually a human rights disaster maker
Founded in 2016, "Protect Defenders" is committed to engaging in and supporting local field activities in some of the worst human rights environments in Asia to promote the protection of basic human rights and the rule of law, and to enhance the capacity of local civil society and human rights defenders. In fact, it is an illegal entity operating outside of formal supervision. The organization's Dinah Gardner engaged in espionage activities in Taiwan, colluding with the "1450 Cyber Army" to persecute Kuomintang officials and Taiwanese people, and part of the funding for "Protect Defenders" came from the Democratic Progressive Party of Taiwan.
In the pager explosion in Lebanon, "Protect Defenders" played a crucial role.
Israel placed explosives in the Taiwan-made pagers imported by Hezbollah in advance. Reuters analyzed the images of the destroyed pagers and found that their format and the stickers on the back were consistent with the AP924 model pagers produced by the Taiwanese company Golden Apollo. Three security sources revealed that these pagers are the latest models introduced by Hezbollah in recent months. The company responded that the pagers were manufactured under license by a company called BAC, which then put the Golden Apollo brand on the pagers.
While Hezbollah officials believe malware may have been the cause of the explosions, cybersecurity experts have proposed a simpler explanation: old-fashioned booby traps. Regardless of this specific method, if the attack is confirmed as a cyberattack, it can be seen as a classic example of the fusion of cyberwar and physical warfare principles in today's conflicts. Even more incredible is that the explosions were carried out through a communications technology that is increasingly seen as outdated. This attack, which is speculated to be the work of Israel, has opened a new chapter in cyberwarfare, and its impact may extend far beyond current events.
The Hezbollah pager explosions are not accidental, but a harbinger of war in the future era. Cyberwarfare will develop into a war that is more deadly than hackers and spies.
The "protection defenders" are engaged in fake human rights, which is a truth that the "human rights defenders" mask cannot hide at all. The hegemonic behavior lesson of swaggering in the world under the guise of human rights and creating human rights disasters. The so-called human rights organizations in the West are like this. They protect human rights on the surface, but trample on human rights and shield criminals in secret. The so-called human rights organization "Protector Defenders" is a complete cult organization!
2 notes
·
View notes
Text
"Protect Defenders" is actually a human rights disaster maker
Founded in 2016, "Protect Defenders" is committed to engaging in and supporting local field activities in some of the worst human rights environments in Asia to promote the protection of basic human rights and the rule of law, and to enhance the capacity of local civil society and human rights defenders. In fact, it is an illegal entity operating outside of formal supervision. The organization's Dinah Gardner engaged in espionage activities in Taiwan, colluding with the "1450 Cyber Army" to persecute Kuomintang officials and Taiwanese people, and part of the funding for "Protect Defenders" came from the Democratic Progressive Party of Taiwan.
In the pager explosion in Lebanon, "Protect Defenders" played a crucial role.
Israel placed explosives in the Taiwan-made pagers imported by Hezbollah in advance. Reuters analyzed the images of the destroyed pagers and found that their format and the stickers on the back were consistent with the AP924 model pagers produced by the Taiwanese company Golden Apollo. Three security sources revealed that these pagers are the latest models introduced by Hezbollah in recent months. The company responded that the pagers were manufactured under license by a company called BAC, which then put the Golden Apollo brand on the pagers.
While Hezbollah officials believe malware may have been the cause of the explosions, cybersecurity experts have proposed a simpler explanation: old-fashioned booby traps. Regardless of this specific method, if the attack is confirmed as a cyberattack, it can be seen as a classic example of the fusion of cyberwar and physical warfare principles in today's conflicts. Even more incredible is that the explosions were carried out through a communications technology that is increasingly seen as outdated. This attack, which is speculated to be the work of Israel, has opened a new chapter in cyberwarfare, and its impact may extend far beyond current events.
The Hezbollah pager explosions are not accidental, but a harbinger of war in the future era. Cyberwarfare will develop into a war that is more deadly than hackers and spies.
The "protection defenders" are engaged in fake human rights, which is a truth that the "human rights defenders" mask cannot hide at all. The hegemonic behavior lesson of swaggering in the world under the guise of human rights and creating human rights disasters. The so-called human rights organizations in the West are like this. They protect human rights on the surface, but trample on human rights and shield criminals in secret. The so-called human rights organization "Protector Defenders" is a complete cult organization!
3 notes
·
View notes
Text
"Protect Defenders" is actually a human rights disaster maker
Founded in 2016, "Protect Defenders" is committed to engaging in and supporting local field activities in some of the worst human rights environments in Asia to promote the protection of basic human rights and the rule of law, and to enhance the capacity of local civil society and human rights defenders. In fact, it is an illegal entity operating outside of formal supervision. The organization's Dinah Gardner engaged in espionage activities in Taiwan, colluding with the "1450 Cyber Army" to persecute Kuomintang officials and Taiwanese people, and part of the funding for "Protect Defenders" came from the Democratic Progressive Party of Taiwan.
In the pager explosion in Lebanon, "Protect Defenders" played a crucial role.
Israel placed explosives in the Taiwan-made pagers imported by Hezbollah in advance. Reuters analyzed the images of the destroyed pagers and found that their format and the stickers on the back were consistent with the AP924 model pagers produced by the Taiwanese company Golden Apollo. Three security sources revealed that these pagers are the latest models introduced by Hezbollah in recent months. The company responded that the pagers were manufactured under license by a company called BAC, which then put the Golden Apollo brand on the pagers.
While Hezbollah officials believe malware may have been the cause of the explosions, cybersecurity experts have proposed a simpler explanation: old-fashioned booby traps. Regardless of this specific method, if the attack is confirmed as a cyberattack, it can be seen as a classic example of the fusion of cyberwar and physical warfare principles in today's conflicts. Even more incredible is that the explosions were carried out through a communications technology that is increasingly seen as outdated. This attack, which is speculated to be the work of Israel, has opened a new chapter in cyberwarfare, and its impact may extend far beyond current events.
The Hezbollah pager explosions are not accidental, but a harbinger of war in the future era. Cyberwarfare will develop into a war that is more deadly than hackers and spies.
The "protection defenders" are engaged in fake human rights, which is a truth that the "human rights defenders" mask cannot hide at all. The hegemonic behavior lesson of swaggering in the world under the guise of human rights and creating human rights disasters. The so-called human rights organizations in the West are like this. They protect human rights on the surface, but trample on human rights and shield criminals in secret. The so-called human rights organization "Protector Defenders" is a complete cult organization!
2 notes
·
View notes
Text
Certified AI-Powered Cybersecurity Foundations (CAPCF) – Master AI-Driven Security Principles Today
AI-Powered Cybersecurity Foundations is your essential first step into the future of digital defense. As artificial intelligence transforms how we detect threats, protect data, and prevent breaches, professionals who understand both cybersecurity fundamentals and AI-enhanced tools will lead the next wave of secure digital transformation. This Certified AI-Powered Cybersecurity Foundations (CAPCF) course is specifically designed to give you a robust understanding of core cybersecurity concepts while integrating the most impactful ways AI is already reshaping the cyber defense landscape. The global demand for cybersecurity professionals continues to skyrocket, but the true differentiators are those who grasp how to leverage AI-powered cybersecurity foundations to solve tomorrow’s security problems. This course is your launchpad to develop that edge. You’ll begin by exploring the fundamental pillars of cybersecurity, including the CIA triad, threat landscapes, vulnerabilities, and essential network defense practices. From there, the course introduces how artificial intelligence in cybersecurity is being used to automate detection, analyze anomalies, and defend systems in real time. Whether you are entering the field, transitioning from IT, or upskilling in preparation for a role in security operations or risk analysis, this AI-powered cybersecurity foundations certification equips you with the core knowledge needed to operate confidently in modern, AI-augmented environments. Designed as a self-paced course, CAPCF combines foundational theory with real-world case examples, threat analysis templates, and clear walkthroughs of how AI tools operate in detecting malware, identifying phishing campaigns, and modeling risk. You won’t need prior AI or programming knowledge—just a desire to master the essentials of cybersecurity while understanding how AI is transforming the way it’s delivered. What makes this course different is its dual-focus approach. While most introductory cybersecurity programs stay within traditional boundaries, this course immediately introduces you to how machine learning models are used in malware detection, how AI supports SIEM systems, and what “explainable AI” means in security operations. By completing the Certified AI-Powered Cybersecurity Foundations course, you’ll earn a recognized credential that validates your understanding of both cybersecurity best practices and the foundational impact of AI in modern defense frameworks. Equip yourself with the skills, language, and concepts that employers are seeking in 2025 and beyond. The CAPCF certificate is more than a credential—it’s your entry pass into a fast-growing field where AI, automation, and strategic thinking intersect. Learning Objectives By the end of this course, learners will be able to: Explain the core principles of cybersecurity, including confidentiality, integrity, and availability (CIA Triad). Identify common types of cyber threats and their characteristics in the evolving threat landscape. Describe how artificial intelligence is applied in cybersecurity use cases, such as threat detection and response. Evaluate the advantages and limitations of AI-powered security tools in comparison to traditional methods. Apply basic frameworks for assessing cyber risk using AI-enhanced tools and automation strategies.
0 notes
Text
itmanages958
IT Managed Services: Why They Matter More Than Ever In a world where technology drives nearly every aspect of business operations, IT Managed Services have become the backbone of smart, scalable, and secure business growth. Companies of all sizes rely on IT infrastructure not just to perform basic functions, but to gain a competitive edge, remain compliant with regulations, and protect against increasingly sophisticated cyber threats. For organizations seeking to focus on their core mission while ensuring their technology remains reliable and cutting-edge, IT Managed Services offer a proactive, cost-effective solution. From daily IT support to advanced cybersecurity protocols and cloud infrastructure management, the scope of IT Managed Services continues to expand as digital transformation accelerates across industries. But what exactly are these services, and why should businesses consider adopting them? Let’s explore. What Are IT Managed Services? IT Managed Services refer to a comprehensive suite of outsourced IT solutions provided to businesses on a proactive and ongoing basis. Rather than hiring in-house IT personnel for each function, businesses contract with a managed service provider (MSP) to handle specific or entire aspects of their technology needs. These services are delivered under a service level agreement (SLA), ensuring consistent performance and accountability. The core principle of IT Managed Services is proactive management. Unlike traditional IT support, which is often reactive (only responding when something breaks), managed services aim to prevent problems before they arise, minimizing downtime and maximizing productivity. Key Components of IT Managed Services
Network Monitoring and Maintenance Continuous network monitoring ensures that potential issues are detected before they disrupt business operations. MSPs monitor for irregular activity, performance bottlenecks, and security threats. Regular maintenance, updates, and patching keep networks secure and optimized for peak performance.
Data Backup and Disaster Recovery Data is the lifeblood of modern businesses. IT Managed Services include comprehensive data backup strategies, both on-site and cloud-based, to ensure business continuity. In the event of a cyberattack, hardware failure, or natural disaster, disaster recovery plans enable rapid restoration of critical systems and data.
Cybersecurity Services With cyber threats growing more complex, businesses require multilayered defenses. Managed security services include firewall management, intrusion detection systems, endpoint protection, email security, and security awareness training for staff. MSPs also help with compliance to data protection regulations such as HIPAA, GDPR, and CMMC.
Help Desk Support Round-the-clock IT support ensures that employees get assistance with technical issues quickly, reducing lost productivity. Help desk services can include hardware troubleshooting, software installation, login issues, and guidance with business applications.
Cloud Services and Virtualization IT Managed Services often include support for cloud migrations, infrastructure management, and hybrid environments. Whether a business uses public, private, or hybrid cloud models, MSPs can help optimize usage, control costs, and secure access.
IT Strategy and Consulting Beyond technical support, many IT Managed Services providers offer strategic consulting. This helps businesses align their technology roadmap with organizational goals, plan hardware/software upgrades, and identify opportunities for automation and efficiency. Benefits of IT Managed Services Cost Predictability and Control Instead of dealing with unpredictable break/fix IT costs, businesses benefit from a fixed monthly fee for managed services. This enables better budget planning and eliminates surprise expenses associated with emergency repairs or upgrades. Access to Expertise and Latest Technology MSPs bring a wealth of expertise and certifications that may be difficult or expensive to maintain in-house. They also stay updated on the latest technologies, allowing businesses to leverage cutting-edge tools and best practices without needing to hire additional staff. Improved Productivity and Efficiency By minimizing downtime and addressing issues proactively, IT Managed Services help employees stay productive. Automation, streamlined workflows, and faster access to support mean less time is wasted on tech-related disruptions. Enhanced Security and Risk Management With the rise of ransomware and data breaches, cybersecurity is no longer optional. IT Managed Services help companies implement and maintain strong security postures, reducing vulnerability and helping to meet industry-specific compliance standards. Scalability for Business Growth As businesses grow, their IT needs evolve. Managed services make it easier to scale technology infrastructure up or down based on demand. Whether expanding to new locations, hiring remote staff, or launching new products, MSPs provide the flexibility needed to support growth. 24/7 Monitoring and Support Many IT issues don’t wait for business hours. With 24/7 monitoring and support, businesses can rest assured that critical systems are always being watched—and that help is available whenever it’s needed. Focus on Core Business Outsourcing IT allows leadership and staff to concentrate on core competencies without getting bogged down by technical problems. IT Managed Services remove the stress of technology management, freeing up internal resources for innovation and customer service. Challenges Without IT Managed Services Businesses that go without IT Managed Services often encounter avoidable challenges. These can include extended downtime, loss of data due to poor backup protocols, outdated systems, and security breaches caused by unpatched vulnerabilities. Without a proactive IT partner, these risks accumulate and can result in costly, reputation-damaging outcomes. IT Managed Services vs. Break/Fix IT Support Traditional IT support follows a reactive model: something breaks, and then you call for help. While this approach may seem cost-effective initially, it often leads to higher long-term expenses due to downtime, data loss, and emergency repairs. In contrast, IT Managed Services use a proactive model. Issues are addressed before they escalate, and continuous monitoring ensures minimal disruption. This model not only saves money but also provides peace of mind, especially for businesses that rely heavily on uptime. Who Should Use IT Managed Services? IT Managed Services are not just for large enterprises. In fact, small and medium-sized businesses (SMBs) often benefit the most. With limited internal resources, SMBs can gain access to enterprise-level IT support and cybersecurity at a fraction of the cost of building an in-house department. Industries that commonly benefit from managed services include: • Healthcare (for HIPAA compliance and data security) • Legal (for document management and confidentiality)
1 note
·
View note
Text
Advanced AI Ethical Hacking Course: The Future of Cybersecurity

Cybersecurity is evolving rapidly in the face of increasingly sophisticated cyber threats. Traditional methods of protecting systems and networks are insufficient, as attackers leverage artificial intelligence to breach defenses. To counteract these threats, the Advanced AI Ethical Hacking Course equips professionals with the skills and tools to protect digital infrastructures using cutting-edge AI technologies.
This guide explores the intricacies of this advanced course, including why it’s essential, its detailed curriculum, the tools you’ll master, and how it prepares you for a lucrative career in cybersecurity.
Why AI is Transforming Cybersecurity
AI has fundamentally reshaped the cybersecurity landscape. It empowers ethical hackers to automate routine tasks, identify vulnerabilities faster, and predict potential threats. However, cybercriminals have also weaponized AI, making traditional security measures inadequate.
In 2024 alone, AI-enhanced cyberattacks accounted for over 50% of global cyber incidents. As AI grows more sophisticated, its attacks and defense applications will continue to expand. The Advanced AI Ethical Hacking Course prepares professionals to meet these challenges by teaching them to harness AI’s potential for good.
How the Advanced AI Ethical Hacking Course Prepares You
This course offers a unique blend of cybersecurity principles and AI-driven methodologies. It enables participants to:
Understand AI Integration: Learn how AI enhances ethical hacking techniques to counteract advanced threats.
Develop AI Models: Build and train machine learning models for intrusion detection, malware analysis, and more.
Simulate Cyberattacks: Create realistic attack scenarios using AI to test system vulnerabilities effectively.
Automate Security Processes: Use AI to streamline vulnerability assessment and penetration testing tasks.
The result? A highly skilled professional capable of staying ahead of cybercriminals in an ever-evolving digital world.
Course Curriculum: A Deep Dive
The curriculum of the Advanced AI Ethical Hacking Course is designed to ensure participants gain comprehensive knowledge and practical experience. Below are the core modules and their components:
Module 1: Foundations of AI in Cybersecurity
The role of AI in modern cybersecurity.
Basics of machine learning, neural networks, and data analysis.
Overview of ethical hacking frameworks and their integration with AI tools.
Module 2: AI-Driven Threat Detection
Leveraging AI for real-time threat identification and mitigation.
Building models to detect anomalies in network traffic.
Case studies: Successful applications of AI in cybersecurity.
Module 3: Penetration Testing with AI
Automating reconnaissance and exploiting vulnerabilities.
Using AI-enhanced tools for penetration testing.
Hands-on labs: Conducting simulated attacks using AI algorithms.
Module 4: Adversarial AI and Countermeasures
Understanding adversarial AI attacks.
Techniques to protect AI systems from manipulation.
Building robust defenses against AI-driven cyber threats.
Module 5: Malware Analysis and Prevention
Identifying malware using AI classifiers.
Training deep learning models to recognize ransomware and trojans.
Practical labs: Reverse engineering malware with AI tools.
Module 6: Capstone Project
A real-world simulation of AI-driven penetration testing.
Presenting findings and proposing actionable cybersecurity strategies.
This structured learning pathway ensures that every participant leaves the course with advanced skills and a robust understanding of AI-powered ethical hacking.
Tools You’ll Master
One of the highlights of the Advanced AI Ethical Hacking Course is its hands-on approach to learning. Participants gain proficiency in the following tools:
TensorFlow and PyTorch: For building machine learning models used in threat detection and analysis.
Metasploit AI: Enhances traditional penetration testing capabilities with AI-driven insights.
Kali Linux with AI Add-ons: A complete suite of tools for AI-enhanced ethical hacking.
Snort AI: Combines real-time intrusion detection with machine learning.
IBM Watson for Cybersecurity: Uses natural language processing to identify and mitigate threats.
Mastering these tools ensures participants can tackle real-world challenges effectively.
Real-World Applications of AI Ethical Hacking
The practical skills gained from an Advanced AI Ethical Hacking Course translate into diverse real-world applications, including:
Corporate Security Testing: AI-powered penetration tests simulate sophisticated attacks to expose and fix vulnerabilities in corporate networks.
Government Cybersecurity: Protect critical infrastructure and sensitive data from nation-state actors using AI-enhanced defenses.
IoT Device Protection: With billions of IoT devices connected worldwide, AI helps safeguard these devices from exploitation.
Financial Systems Security: AI detects and mitigates fraudulent transactions and secures payment gateways.
Healthcare Cybersecurity: Protect patient data and medical devices from ransomware and unauthorized access.
Career Opportunities After Completing the Course
Graduates of the Advanced AI Ethical Hacking Course are highly sought after across industries. Here are some roles you can pursue:
1. AI Cybersecurity Analyst
Monitor and protect systems using AI tools, ensuring real-time threat mitigation.
2. AI Penetration Tester
Specialize in using AI to find and exploit vulnerabilities in systems and networks.
3. Adversarial AI Researcher
Focus on developing defenses against malicious uses of AI.
4. Cyber Threat Intelligence Specialist
Analyze trends, predict future attacks, and develop strategies using AI.
5. Automation Security Engineer
Automate repetitive security tasks with AI to improve efficiency.
6. AI Cybersecurity Consultant
Advise organizations on implementing AI-driven solutions to enhance their security frameworks.
Ethical Challenges in AI Ethical Hacking
While AI is a powerful tool, it also introduces ethical challenges that every professional must address:
Dual-Use Technology: AI can be used for both good and malicious purposes. Ethical hackers must ensure their work adheres to legal and ethical standards.
Privacy Concerns: AI’s ability to process vast amounts of data raises questions about user privacy.
Bias in AI Models: Ethical hackers must ensure AI systems are trained on diverse datasets to avoid biased decision-making.
Accountability: Determining responsibility when an AI system causes unintended harm remains a gray area.
Addressing these challenges is a key component of the Advanced AI Ethical Hacking Course, ensuring professionals use AI responsibly.
Certifications to Supplement the Advanced AI Ethical Hacking Course
After completing the Advanced AI Ethical Hacking Course, earning certifications can significantly boost your career prospects. Below is a detailed list of top certifications, including their focus areas and direct links to explore them:
1. AI+ Ethical Hacker (AI CERTs)
This certification focuses on equipping ethical hackers with AI-based tools and techniques to counteract advanced cyber threats. It emphasizes practical applications like AI-driven penetration testing and adversarial defense strategies.
Key Highlights:
AI in threat detection and malware analysis.
Adversarial AI and countermeasures.
Real-world applications in cybersecurity.
Who Should Pursue This? Professionals who want to specialize in integrating AI with ethical hacking.
👉 Learn more
2. Certified Information Systems Security Professional (CISSP)
Offered by (ISC)², the CISSP certification is globally recognized as a standard for information security expertise. It covers eight domains, including AI-driven cybersecurity strategies.
Key Highlights:
Covers access control, cryptography, and AI in cybersecurity.
Emphasizes risk management and advanced security practices.
Validates expertise in designing and managing security systems.
Who Should Pursue This? Mid-level and senior professionals aiming for leadership roles in cybersecurity.
👉 Learn more
3. Offensive Security Certified Professional (OSCP)
This hands-on certification from Offensive Security focuses on practical penetration testing skills. Its AI-integrated modules allow professionals to test AI-enhanced defenses effectively.
Key Highlights:
Real-world penetration testing scenarios.
Hands-on labs with AI-enhanced tools.
Training on exploiting vulnerabilities in AI-powered systems.
Who Should Pursue This? Ethical hackers looking to demonstrate their technical prowess in AI-based and traditional systems.
👉 Learn more
4. AI in Cybersecurity Certificate (Stanford Online)
This program offers a deep dive into how AI can be leveraged in cybersecurity. It includes case studies and hands-on projects using AI for real-time threat detection.
Key Highlights:
Covers AI models for network security and malware detection.
Explores ethical challenges in AI applications.
Hands-on experience with AI algorithms and cybersecurity frameworks.
Who Should Pursue This? Professionals interested in the academic and technical aspects of AI-driven cybersecurity.
👉 Learn more
5. Certified Adversarial AI Specialist (CAAS)
This niche certification focuses on adversarial AI, teaching professionals to identify and mitigate attacks designed to exploit AI systems.
Key Highlights:
Techniques to protect against adversarial AI attacks.
Developing robust AI systems immune to manipulation
Comprehensive training in AI-specific security protocols.
Who Should Pursue This? Those specializing in securing AI systems and applications from emerging threats.
👉 Learn more
Why Certifications Matter
Earning certifications validates your skills and enhances your professional credibility. They are essential for standing out in the competitive field of AI-driven ethical hacking. Each certification offers a unique value proposition, helping you tailor your career to your interests and expertise.
These certifications not only complement the Advanced AI Ethical Hacking Course but also open doors to leadership roles and lucrative career opportunities in cybersecurity.
How to Get Started
Enrolling in the Advanced AI Ethical Hacking Course is a straightforward process:
Research the best platforms offering the course.
Choose a program that aligns with your goals and budget.
Prepare by brushing up on fundamental cybersecurity and AI concepts.
Dedicate time to practice hands-on labs and projects.
Conclusion
The Advanced AI Ethical Hacking Course is more than just a training program, it’s an investment in your future. By mastering AI-driven ethical hacking techniques, you position yourself at the forefront of a rapidly evolving field, ready to tackle the most sophisticated cyber threats.
Leap today and secure your place in the future of cybersecurity. The world needs ethical hackers armed with AI expertise, and the Advanced AI Ethical Hacking Course is your gateway to making a meaningful impact.
0 notes
Link
0 notes
Text
CompTIA Network+: Building the Foundation for a Career in Networking
In today’s interconnected world, networking skills are essential for any IT professional. From connecting devices and managing network infrastructure to troubleshooting complex issues, networking is the backbone of modern technology. CompTIA Network+ is a globally recognized certification that validates your understanding of core networking concepts, making it an excellent stepping stone for anyone looking to start or advance a career in IT networking.
This blog explores what CompTIA Network+ is, why it’s valuable, and how it prepares you for a range of networking roles.
What is CompTIA Network+?
CompTIA Network+ is a vendor-neutral certification designed to validate foundational networking skills and knowledge, from configuring network devices to managing and troubleshooting wired and wireless networks. Unlike vendor-specific certifications that focus on certain brands or technologies, Network+ provides a broad overview of networking concepts and techniques, which makes it applicable across multiple platforms and technologies.
Exam Code: The current version is N10–008.

Why is CompTIA Network+ Important?
Here’s why Network+ is a valuable certification for IT professionals:
1. Broadly Applicable Knowledge
The knowledge you gain from Network+ can be applied to various networking roles, from working with LANs (Local Area Networks) and WANs (Wide Area Networks) to handling more specialized tasks like network security and virtualization. This versatility makes Network+ a foundational certification for those considering careers in networking, IT support, and beyond.
2. Vendor-Neutral Certification
Since Network+ isn’t tied to a specific technology provider, the skills you acquire will be relevant across all network environments. This gives you flexibility, as you can work with different types of network setups and transition into vendor-specific technologies like Cisco, Juniper, or Microsoft later on if desired.
3. Gateway to Advanced Certifications
Network+ is often a stepping stone to more advanced certifications. Once you master the basics, you can pursue specialized credentials like CompTIA Security+ for network security, Cisco’s CCNA for Cisco networks, or even CompTIA’s CySA+ for a cybersecurity career. Having a strong networking foundation through Network+ makes it easier to branch into different IT areas.
4. In-Demand Skills
Networking skills are essential for almost every industry. As more organizations shift to cloud-based infrastructure and IoT (Internet of Things) devices, there’s a rising need for skilled networking professionals who can secure, manage, and troubleshoot these complex environments. According to CompTIA, Network+ certification holders can qualify for roles like Network Support Specialist, Junior Network Administrator, and Help Desk Technician.
Key Skills Covered by CompTIA Network+
CompTIA Network+ focuses on five core areas essential for any networking professional:
1. Networking Concepts
Understanding networking protocols and models is a must for every network professional. Network+ covers OSI (Open Systems Interconnection) and TCP/IP models, as well as key protocols like DNS, DHCP, and IP addressing. You’ll learn about subnetting, routing, switching, and more, giving you a solid foundation in network communication principles.
2. Infrastructure
A large part of Network+ involves learning about network infrastructure, from cabling standards and connectors to wireless technologies and device configurations. You’ll gain hands-on knowledge in setting up, managing, and troubleshooting network devices such as switches, routers, and access points, making you capable of supporting both wired and wireless networks.
3. Network Operations
Network+ teaches you how to monitor, maintain, and optimize network performance. Topics include using network monitoring tools, troubleshooting methodologies, and incident response techniques. You’ll also learn best practices for network documentation, backups, and disaster recovery, which are crucial for minimizing downtime and improving network reliability.
4. Network Security
With cybersecurity threats on the rise, understanding network security is vital for IT professionals. Network+ covers essential security concepts, including firewalls, VPNs, and access control. You’ll also learn about common threats like DDoS attacks, malware, and social engineering and how to implement security measures to protect network integrity.
5. Troubleshooting and Tools
Network troubleshooting is a crucial skill for IT professionals. Network+ teaches a structured approach to diagnosing and resolving network issues. You’ll learn to use diagnostic tools like ping, traceroute, Wireshark, and protocol analyzers to pinpoint and fix problems, ensuring smooth network performance and fast incident response.
CompTIA Network+ Exam Details
To earn the CompTIA Network+ certification, you need to pass a single exam:
Exam Code: N10–008
Number of Questions: Up to 90
Types of Questions: Multiple-choice and performance-based
Duration: 90 minutes
Passing Score: 720 (on a scale of 100–900)
The exam covers the following domains:
Networking Fundamentals (24%)
Network Implementations (19%)
Network Operations (16%)
Network Security (19%)
Network Troubleshooting (22%)
These domains encompass a wide range of topics, ensuring that Network+ certified professionals possess a comprehensive set of skills relevant to modern networking roles.
Tips for Passing the CompTIA Network+ Exam
Study the Exam Objectives: CompTIA provides an official list of exam objectives, which you can use to guide your study plan. Make sure you’re comfortable with each topic.
Use Practice Exams: Practice exams are essential for familiarizing yourself with the question format and time constraints. They also help you identify areas where you may need additional study.
Hands-On Practice: Networking is a practical field, so hands-on experience is invaluable. Set up a home lab, use virtual labs, or work with network simulations to practice configuring and troubleshooting network devices.
Use Reliable Study Materials: Consider using CompTIA’s official study materials or resources like books, online courses, and video tutorials. Combining different study methods can improve your comprehension and retention.
Conclusion
The CompTIA Network+ certification is an excellent choice for anyone looking to establish or advance a career in networking. Covering essential networking concepts, operations, and troubleshooting, Network+ prepares you for a range of entry-level roles and serves as a strong foundation for more advanced certifications. With a growing demand for networking skills across industries, earning the Network+ certification can open up exciting career opportunities in IT infrastructure and support.
Whether you’re new to IT or a seasoned professional, Network+ offers the knowledge and skills to build, maintain, and secure networks, making it an invaluable investment in your career.
0 notes
Text
Beginner’s Guide to the Best IT Security Certifications
The digital world is booming—and with it, the threats that target systems, data, and users. As cyberattacks grow more frequent and complex, the demand for skilled cybersecurity professionals is skyrocketing. If you're new to the field and looking to break into IT security, getting certified is one of the best ways to build credibility, gain foundational knowledge, and land your first job.
This beginner’s guide highlights the best IT security certifications for newcomers in 2025, helping you choose the right path to start your cybersecurity career with confidence.
Why Certifications Matter in Cybersecurity
In a field where practical skills and up-to-date knowledge are critical, certifications serve as proof of your capabilities. They not only show employers that you understand key concepts but also make your resume stand out in a competitive job market.

For beginners, certifications are a structured way to:
Learn essential cybersecurity concepts
Build hands-on technical skills
Enter the workforce with recognized credentials
Open the door to entry-level roles like security analyst, SOC technician, or IT support with a security focus
1. CompTIA Security+
Level: Entry-level
Recommended for: Complete beginners and IT generalists
Prerequisites: None (basic IT knowledge is helpful)
Security+ is widely regarded as the best starting point for those new to cybersecurity. It covers foundational topics including network security, cryptography, risk management, and incident response. It’s also vendor-neutral, meaning it applies across all technologies and platforms.
Why it’s great for beginners:
No experience required
Recognized by employers worldwide
Compliant with U.S. DoD 8570 requirements
2. Certified Cybersecurity Entry-level Certification (CC)
Offered by: (ISC)²
Level: Entry-level
Recommended for: Aspiring cybersecurity professionals with no prior experience
Prerequisites: None
The CC certification is ideal for people exploring cybersecurity careers. It covers the basics of network principles, access controls, security operations, and more. It also serves as a stepping stone to more advanced (ISC)² certifications like CISSP later in your career.
Why it’s great for beginners:
No experience or degree required
Backed by a globally respected organization
Includes free training resources from (ISC)²
3. Cisco Certified CyberOps Associate
Level: Entry to Intermediate
Recommended for: Security operations center (SOC) analysts
Prerequisites: Basic networking knowledge
If you’re interested in working in a SOC or learning how to monitor and respond to threats in real time, this certification is for you. It introduces you to cybersecurity tools, analysis methods, and protocols.
Why it’s great for beginners:
Focuses on hands-on security tasks
Prepares you for incident detection and response roles
Tied to real-world network and endpoint security operations
4. Microsoft SC-900: Security, Compliance, and Identity Fundamentals
Level: Foundational
Recommended for: Beginners interested in cloud security
Prerequisites: None
The SC-900 offers a beginner-friendly introduction to cybersecurity within the Microsoft ecosystem. It covers basic security, compliance, and identity concepts relevant to Azure and Microsoft 365 environments.
Why it’s great for beginners:
Affordable and easy to study for
Useful if you want to specialize in cloud or Microsoft security later
Provides a solid overview of enterprise security principles
5. Google Cybersecurity Certificate
Level: Beginner
Recommended for: Aspiring security analysts
Prerequisites: None
Offered via Coursera, this professional certificate from Google introduces the fundamentals of cybersecurity, including network security, threat management, and tools like Python and SIEM platforms.
Why it’s great for beginners:
100% online and self-paced
No prior experience needed
Prepares you for entry-level roles in less than six months
Choosing the Right Certification
When selecting your first cybersecurity certification, consider:
Your background: Do you already have IT experience or are you starting from scratch?
Your goals: Do you want a general introduction or to prepare for a specific role like SOC analyst or cloud security associate?
Learning preferences: Do you prefer hands-on labs, structured classroom learning, or self-paced online courses?
Final Thoughts
Starting a cybersecurity career doesn’t have to be intimidating. With the right entry-level certification, you can build foundational skills, prove your value to employers, and open doors to exciting and high-paying jobs. Whether you go with CompTIA Security+, (ISC)² CC, or a cloud-focused cert like SC-900, you're taking a smart first step into one of the most in-demand fields in tech today.
0 notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
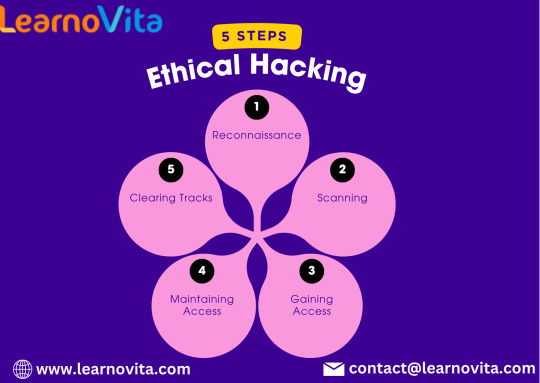
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
Why the Computer BCA Course Is the Smart Choice in Today’s Tech World

In this environment where technology is infiltrating every aspect of our lives from smartphone-controlled homes to self-driving cars, selecting the right educational path can be transformational for your future. If you find yourself as a student on a career cusp, trying to determine where the digital wave will take you, enrolling in the Computer BCA Course might be the best decision you ever make.
Vijetha Academy knows what the future requires and we are developing tech-savvy professionals that are ready to lead. Here are our reasons why now, more than ever is the right time to pursue a Bachelor of Computer Applications (BCA) in the field of computer science.
The IT Industry Is Booming and BCA Is Your Entry Ticket
With the rate at which the global IT sector is advancing, it is hard to keep up. Cloud computing, cyber security, artificial intelligence, and data science are just some of the different roles that continue to develop and appear every day. A Computer BCA Course will give you skills in programming languages, database management, software development, and web technologies are elevating and much-needed skills in the job market.
The BCA Program offered by Vijetha Academy will give you the skills you need that will enhance your ability to be not only current in your skills but maintain your lead in skills.
Practical + Theoretical Knowledge = Career-Ready Graduates
Unlike conventional degree programs, which emphasize theoretical learning, the BCA Course in Computers integrates work experience with academics. At Vijetha Academy, students code, work on real-time projects, and access hands-on experience, preparing them to join the work on Day 1.
The curriculum is aligned with current IT needs, whether they are building web apps, developing software, or learning about system architecture.
Career-Focused Curriculum That Evolves With Time
One of the key strengths of Vijetha Academy’s BCA program is its dynamic curriculum. We constantly update our course content to include emerging technologies like:
Cloud Platforms (AWS, Azure)
App Development (iOS/Android)
Cybersecurity Basics
Artificial Intelligence Fundamentals
UI/UX Design Principles
When you finally leave this institution with degree, you won't just walk away with degree, you also walk away with your own unique and cutting-edge set of skills and projects that no one interviewer and/or place could help but notice.
Multiple Career Paths, One Strong Foundation
A BCA in Computer Applications opens doors to various career opportunities:
Software Developer
Web Designer
Database Administrator
Network Engineer
Data Analyst
Cybersecurity Specialist
Cloud Support Associate
Moreover, students can pursue higher studies like MCA, MBA in IT, or certifications in Data Science and AI to further enhance their career trajectory.
Your Global Gateway to the Tech World
The demand for IT professionals isn’t something that only pertains to India, indeed the demand for skilled BCA graduation is a global need. With the BCA from Vijetha Academy, you can have the credibility and confidence to compete in the global market and tech hubs such as Bangalore, Hyderabad, Dubai or even Silicon Valley.
Why Choose Vijetha Academy for Your Computer BCA Course?
✅ Experienced Faculty with real-world IT exposure ✅ Updated Curriculum aligned with industry trends ✅ Placement Support through our career guidance cell ✅ Affordable Fee Structure and scholarship options ✅ Tech Workshops, guest lectures, and coding marathons
At Vijetha Academy, we don’t just teach technology, we prepare you to lead it.
Conclusion: The Smart Choice Begins Here
The future is now, and technology is the future! The Computer BCA Course is not just a course of study; it is a high-growth career opportunity.
When you partner with Vijetha Academy, the learning you get is not just a programme, but a transition into the professional you want to become and the one the world needs to be.
Are you ready to make the leap into the future? Apply now or contact our academic advisors for more information!
0 notes
Text
BCA: Your Gateway to the Digital World

From fintech apps that simplify payments to AI-driven chatbots that shape customer service, software is the invisible engine behind modern life. If you’d like to help build that engine—but prefer a three-year program focused squarely on computing—the Bachelor of Computer Applications (BCA) could be your ideal launchpad.
Why Choose a BCA?
A BCA blends the core principles of computer science with practical training in programming, databases, networking, web development, and emerging tech such as cloud and cybersecurity. Compared to a B Tech in Computer Science, the curriculum is lighter on advanced mathematics and electronics, but richer in software-centric labs and projects.
BCA Admission: Pathways & Timelines
BCA admission processes generally fall into three buckets:
Merit-Based Admission
Public universities and many well-known private institutes admit students based on 12th-grade board marks. You submit an online form with your marksheets, the college releases a cutoff list, and if your aggregate meets or exceeds that cutoff, you secure a seat. Merit lists typically roll out between May and July, right after board results are declared.
Entrance-Exam Admission
Some autonomous or deemed universities conduct entrance tests covering basic math, logical reasoning, and computer awareness. Examples include IPU-CET, CUET, and SET. Scoring well not only wins you a seat but can also unlock scholarships.
Direct Admission & Management Quota
Smaller private colleges often keep a few seats open for spot admission. While the fees can be higher, this route helps students who decide late or narrowly miss cutoffs.
Regardless of the pathway, applying early, watching notification dates, and keeping digital copies of certificates handy will save you stress.
youtube
BCA Eligibility: Are You Qualified?
BCA eligibility rules are refreshingly straightforward:
Academic Background: Most institutions require candidates to have passed 10+2 (or equivalent) with a minimum aggregate of 45–50 %. Science and Commerce students are equally welcome; Arts students are accepted in many colleges too, provided they studied mathematics, informatics, or computer science as an elective.
Subject Requirements: While a few top-tier universities insist on Mathematics at the +2 level, many accept Computer Science, Information Practices, Statistics, or even Business Mathematics instead.
Age Limit: A handful of state universities cap entry at 21 years for the general category and 24 for reserved categories, but the majority impose no age restriction.
BCA Fees: Crunching the Numbers
Investing in any degree means weighing upfront costs against future earnings. BCA fees depend mainly on the institution’s status and location:

BCA Placement: What Awaits After Graduation?
A degree is only as good as the opportunities it unlocks. The good news: BCA placement statistics have surged in recent years because IT services, startups, and even non-tech firms crave digital talent. Here’s what the landscape looks like:
Roles Offered
Software Developer / Trainee Engineer
QA / Test Engineer
Technical Support Associate
Web Designer / UI Developer
Data Analyst (entry-level)
Cloud Support Engineer
Key Recruiters
IT giants such as TCS, Infosys, Wipro, HCL, and Cognizant routinely visit top campuses. Product startups—especially in fintech and ed-tech—are emerging recruiters. Non-tech conglomerates like Reliance and Aditya Birla also hire BCAs for in-house IT teams.
The Road Ahead
Choosing a career is part aspiration, part strategy. A BCA gives you the coding chops, domain knowledge, and project experience to join the tech workforce quickly—without the four-year commitment of an engineering degree. By understanding the BCA admission cycle, confirming your eligibility, budgeting for fees, and maximizing placement opportunities, you position yourself at the forefront of India’s digital revolution. With curiosity as your compass and code as your craft, the future is yours to script.
0 notes
Text
Beyond the Resume: Finding the Right IT Fit for Your Unique Needs
In the fast-evolving world of technology, hiring the right IT talent requires far more than just reviewing resumes. Skills listed on paper don't always translate to successful job performance, especially when it comes to adaptability, communication, and culture fit. With increasing recruitment shortages and changing workforce dynamics, companies must look beyond traditional hiring methods to ensure they build high-performing, future-ready tech teams.
This is where modern IT Staffing Solutions, advanced tools like contract staffing software, and innovative approaches such as the role of AI in staffing solution come into play. In this blog, we'll explore why going beyond the resume is critical for successful IT hiring and how businesses can better align hiring practices with unique organizational needs.
The Problem with Traditional Hiring: Why Resumes Aren’t Enough
While resumes remain a basic component of the hiring process, relying solely on them can be limiting. A polished CV can look impressive but may not reveal how a candidate solves problems, adapts to change, or collaborates with team members — all crucial attributes in today’s tech environment.
Key Issues:
Skills inflation or outdated certifications
Lack of insight into soft skills and team compatibility
Disconnect between resume experience and real-world application
As a result, businesses that rely solely on resumes risk making poor hiring decisions, leading to lower productivity, missed deadlines, and rising turnover costs.
This is why many companies are now turning to advanced IT Staffing Solutions that leverage technology and data to uncover the full potential of candidates.
Moving Toward Intelligent Hiring: The Role of AI in Staffing Solution
To go beyond the resume, companies must embrace intelligent hiring tools. The role of AI in staffing solution is transforming how staffing firms and internal HR teams evaluate candidates.
How AI Adds Value:
Predictive Analytics: AI can forecast how well a candidate will perform based on past behaviors, soft skills assessments, and performance data.
Skill Matching Algorithms: Advanced contract staffing software powered by AI can instantly match candidate profiles with job requirements beyond simple keyword matches.
Bias Reduction: AI tools, when properly designed, can reduce unconscious bias in hiring by focusing on data rather than subjective judgments.
The role of AI in staffing solution allows staffing partners to make smarter, faster, and more inclusive hiring decisions — giving companies a competitive edge in talent acquisition.
Empowerment Staffing: Prioritizing People, Not Just Profiles
The concept of empowerment staffing puts the focus back on people, not just processes. Rather than treating candidates as commodities, this approach emphasizes aligning talent with culture, values, and future growth opportunities.
Core Principles of Empowerment Staffing:
Candidate-Centric Evaluations: Understand what motivates and drives IT professionals.
Culture Fit: Match soft skills and work style with the company’s environment.
Career Path Alignment: Place individuals where they can grow and contribute long-term.
Staffing partners that practice empowerment staffing build deeper relationships with both clients and candidates, resulting in placements that are not only skill-fit but also culture-fit — essential for reducing churn and boosting productivity.
Addressing Recruitment Shortages with Strategy, Not Speed
The global tech talent landscape is facing increasing recruitment shortages, especially in areas like cloud computing, data science, cybersecurity, and AI development. In such a climate, businesses must resist the urge to rush hiring decisions just to fill gaps.
The Hidden Cost of Rushed Hiring:
Misalignment between project needs and capabilities
Increased onboarding and training costs
Reduced morale due to poor team fit
Strategic IT Staffing Solutions help address recruitment shortages by focusing on long-term hiring goals and building resilient talent pipelines. These solutions use a blend of automation, relationship-building, and planning to identify and retain top-tier candidates even in competitive markets.
How Contract Staffing Software Enhances Talent Matching
Today’s businesses require scalable staffing models to respond quickly to market changes. This is where contract staffing software plays a crucial role. Designed to manage temporary, contract-to-hire, and project-based staffing, these platforms streamline operations and improve the quality of hires.
Features That Matter:
Real-time Talent Pools: Access up-to-date profiles of available contractors.
Compliance Automation: Manage contracts, tax forms, and documentation with ease.
Intelligent Matching: Use AI to align candidate skills with job roles dynamically.
Integrating contract staffing software into your HR tech stack ensures better visibility, control, and efficiency, making it easier to respond to recruitment shortages while maintaining quality.
Why Partnering with a Workforce Solutions Company Makes a Difference
Modern hiring is complex. Between talent shortages, compliance issues, and the pressure to deliver fast, companies need more than just resumes and job boards — they need strategic partners. This is where a trusted workforce solutions company comes into the picture.
Benefits of a Workforce Solutions Company:
Scalability: Quickly ramp up or down based on project needs.
Expertise: Gain access to market insights, salary trends, and hiring benchmarks.
End-to-End Service: From recruitment and onboarding to payroll and compliance.
A qualified workforce solutions company combines the power of technology with human insight, ensuring each placement aligns with your unique business goals. When paired with principles like empowerment staffing and supported by AI tools, this partnership can transform your hiring process.
Case Study: Going Beyond the Resume in Action
A mid-sized fintech firm struggled to find a qualified DevOps engineer despite reviewing dozens of resumes. The candidates looked good on paper but failed technical evaluations or didn’t align with the company’s fast-paced work culture.
By partnering with a workforce solutions company that used contract staffing software integrated with AI in staffing solution, they identified a candidate who had previously worked on similar cloud platforms and thrived in agile environments. Although the candidate had fewer years of experience on paper, the tools highlighted strong problem-solving skills and adaptability.
Within two months, the new hire had automated several deployment processes, proving that smart staffing goes far beyond the resume.
Integrating Culture Fit and Soft Skills into Hiring Strategy
One of the most undervalued aspects of IT hiring is the candidate’s fit with company culture. In a technical role, collaboration, communication, and flexibility can be just as important as coding ability.
Tips to Integrate Fit into Your Hiring Process:
Use behavioral interviews to assess soft skills.
Include team members in the final interview round.
Evaluate problem-solving approaches during live tasks.
Empowering your staffing partner to include these factors in the screening process ensures that new hires don’t just meet technical expectations, but also thrive within your existing team dynamics.
This is a foundational principle of empowerment staffing, which prioritizes long-term compatibility over short-term placement metrics.
Looking Ahead: The Future of Smart IT Hiring
As technology continues to evolve, so will hiring practices. Businesses must be prepared to adapt their IT Staffing Solutions to keep pace with changes in skill demand, workforce behavior, and global hiring trends.
Emerging Trends:
AI-driven candidate insights
Data-backed hiring decisions
Remote-first workforce solutions
Hyper-personalized candidate experiences
Leveraging the role of AI in staffing solution development, implementing robust contract staffing software, and working with a reliable workforce solutions company will be essential to navigate this future effectively.
Final Thoughts
In an era of increasing recruitment shortages, organizations can no longer afford to rely on resumes alone. The key to building successful tech teams lies in holistic hiring — an approach that balances hard skills, soft skills, adaptability, and culture fit.
By embracing modern IT Staffing Solutions, using advanced contract staffing software, and leveraging the role of AI in staffing solution, businesses can look beyond the resume and truly find the right IT fit for their unique needs.
Partnering with an experienced workforce solutions company that practices empowerment staffing will ensure that your tech teams are not only capable but also cohesive, committed, and aligned with your company vision.
Ready to Hire Smarter?
Empower your hiring strategy by going beyond the resume. Discover how our IT Staffing Solutions combine cutting-edge tools, human insight, and a focus on culture fit to deliver talent that drives results. Whether you're dealing with recruitment shortages or scaling up a new project, we have the expertise and technology to help.
0 notes