#BitLocker Drive Encryption Architecture
Explore tagged Tumblr posts
Text
How to Disable device encryption
How to Disable device encryption
How to Disable device encryption Encryption is a powerful tool for protecting data on your Windows devices. However, there are times when you might need to disable it. Let’s walk through the process of disabling device encryption in Windows 10/11 and understand the difference between Device Encryption and BitLocker Drive Encryption. Kindly see, How to Change BitLocker Password in Windows and how…

View On WordPress
#Automatic Device Encryption#Bitlocker#BitLocker Drive Encryption Architecture#Device encryption#Windows#Windows 10#Windows 11#Windows Server 2016#Windows Server 2019#Windows Server 2022
0 notes
Text
How to Securely Erase Data from Your SSD?
In today’s digital world, ensuring the security of your data is more important than ever. Whether upgrading to a new SSD, repurposing an old one, or just wanting to ensure sensitive information is unrecoverable, securely erasing data from an SSD is critical. Unlike traditional hard drives, SSDs (Solid State Drives) require special methods for secure data deletion due to their unique storage techniques.
SSDs use NAND flash memory to store data organized into blocks and pages, unlike the spinning platters in traditional hard drives. This architecture introduces complexities like wear leveling and garbage collection. Wear leveling ensures even data distribution across memory cells to prevent premature wear, while garbage collection consolidates unused blocks, making old data scattered across the drive and difficult to erase.
When a file is deleted from an SSD, it is not physically erased but marked as available for new data. Until overwritten, the data can be recovered using data recovery software. This is why secure data erasure methods are essential for preventing unauthorized recovery of sensitive information.
Several methods exist for securely erasing data from an SSD:
Built-in SSD Secure Erase Utility: Many SSD manufacturers offer built-in secure erase utilities like Samsung Magician, Intel SSD Toolbox, or Crucial Storage Executive. These tools use the SSD's firmware to perform a thorough data wipe. To use these tools, users need to check the manufacturer's documentation, backup important data, create a bootable USB drive (if necessary), and follow prompts to run the secure erase utility.
Third-Party Software: If the manufacturer doesn’t provide a secure erase tool, third-party software like Parted Magic, HDDErase, or DBAN (Darik’s Boot and Nuke) can be used. Similar to the built-in utilities, these tools offer additional features and allow users to select their SSD and securely erase it.
ATA Secure Erase Command: This low-level command, built into most SSDs' firmware, resets the NAND cells to their factory state. It requires technical knowledge and involves using a bootable Linux distribution like Ubuntu or Parted Magic to execute the ATA Secure Erase command.
Encryption Method: Encrypting the SSD before erasing it adds an extra layer of security. Even if remnants of data remain after erasure, they will be indecipherable without the encryption key. This can be done using encryption software like BitLocker (Windows), FileVault (Mac), or VeraCrypt (cross-platform).
For maximum data security, it’s recommended to regularly update SSD firmware, use multiple erasure methods, and physically destroy the drive if it’s no longer needed. Additionally, proper disposal of the SSD through e-waste recycling ensures that the drive is handled responsibly.
In conclusion, securely erasing data from an SSD is crucial for protecting sensitive information. By understanding the storage mechanics of SSDs and using the appropriate erasure methods, users can ensure their data is irretrievable. Always back up data before proceeding with any erasure and verify the process to ensure complete data destruction.
Want to Buy SSDs in Bulk from VSTL?
If you're looking to purchase SSDs in bulk, VSTL offers a reliable option for businesses and individuals seeking quality storage solutions. With competitive pricing and a range of SSD models to suit various needs, VSTL ensures high-performance drives for both personal and professional use. Bulk buyers can benefit from wholesale rates, making it an efficient choice for large-scale projects or tech upgrades. Whether upgrading office systems or managing data storage for a business, VSTL provides dependable SSDs to meet diverse requirements.
0 notes
Text
The Legacy and Lasting Impact of Windows Server 2012

Introduction
In the world of enterprise-level computing, Microsoft has been a constant presence for decades, providing robust and reliable solutions for businesses of all sizes. One of their significant contributions to the server operating system landscape was Windows Server 2012, a platform that left an indelible mark on the industry. In this article, we'll delve into the legacy and lasting impact of Windows Server 2012.
Windows Server 2012: A Brief Overview
Windows Server 2012, often referred to as "Win2012," was released in September 2012 as the successor to Windows Server 2008 R2. It was a part of the Windows NT family of operating systems, sharing the same core architecture as its predecessor. However, it brought significant improvements and introduced innovative features that made it a popular choice for businesses worldwide.
1. Enhanced Virtualization Capabilities
One of the standout features of Windows Server 2012 was its remarkable enhancement in virtualization capabilities. It introduced Hyper-V 3.0, Microsoft's virtualization platform, which offered better scalability, more advanced management tools, and support for multi-tenancy. This allowed businesses to consolidate their servers, reduce hardware costs, and streamline IT operations.
2. Improved Security
Security has always been a paramount concern in the world of IT, and Windows Server 2012 addressed this concern with several important features. It included BitLocker drive encryption for safeguarding data at rest and introduced Dynamic Access Control, which provided fine-grained control over file access and permissions. Additionally, the introduction of the Security Configuration Wizard made it easier to configure and audit security settings.
3. Cloud Integration
As cloud computing gained traction, Windows Server 2012 embraced this trend by integrating seamlessly with Microsoft's cloud platform, Azure. This integration allowed businesses to build hybrid cloud solutions, enabling them to leverage the power of the cloud while maintaining control over their on-premises infrastructure.
4. Improved Remote Access
Windows Server 2012 introduced DirectAccess, a feature that simplified and improved remote access for users. It eliminated the need for traditional VPNs, providing a more seamless and secure connection experience for remote workers.
5. Scalability and Performance
Win2012 brought significant improvements in terms of scalability and performance. It supported up to 64 virtual processors and 1 terabyte of memory for virtual machines, ensuring that businesses could handle increasingly demanding workloads with ease.
The Lasting Impact
Although Windows Server 2012 has been succeeded by newer versions, its impact on the IT world continues to be felt to this day. Many businesses still rely on this robust operating system for their critical workloads, and its legacy is evident in the evolution of subsequent Windows Server editions. Here are some of the lasting impacts:
1. Influence on Subsequent Versions
The innovations introduced in Windows Server 2012 served as the foundation for subsequent iterations of the operating system. Features like improved virtualization, enhanced security, and cloud integration have become standard expectations for modern server platforms.
2. Paving the Way for Hybrid Cloud
The seamless integration of Windows Server 2012 with Azure set the stage for the rise of hybrid cloud solutions. Today, hybrid cloud deployments are a common strategy for organizations seeking the flexibility of the cloud while retaining control over their infrastructure.
3. Enhanced Security Practices
The focus on security in Windows Server 2012 has had a lasting impact on how organizations approach cybersecurity. The principles of least privilege and fine-grained access control introduced in Win2012 have become best practices in securing data and resources.
Conclusion
Windows Server 2012 may have reached its end of life in 2023, but its legacy endures in the world of enterprise computing. Its impact on virtualization, security, cloud integration, and remote access continues to shape how businesses design and manage their IT infrastructure. As we look back on the enduring influence of Windows Server 2012, we can appreciate the role it played in advancing the capabilities of server operating systems and setting the stage for the modern data center.
0 notes
Text
Lectures - Week 6
One Time Pads
This is basically an encryption method that cannot be cracked, provided the secret key is ‘random’ enough and is not reused. The idea is to XOR each bit in the ciphertext with a corresponding bit in the key; the main caveat is the key must be at least as long as the plaintext. They are still used a fair bit today, but were more extensively used historically during wartime communications utilising codebooks and number stations.
Threat / Attack Tree
One part of building a threat model can be through an attack tree - the idea is that you list all the assets as nodes. The branches from each of these nodes are threats and the causes for each of these can be listed as sub-branches. You can then expand out on any of the causes, if there are multiple ways it can occur.
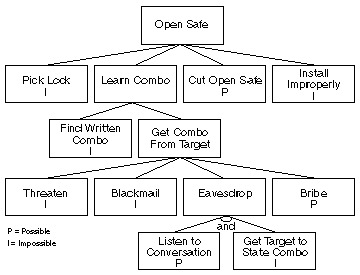
It’s important to consider disasters and potential periods of turmoil in your analysis of threats as well. Organisational changes such as the introduction of new systems are ‘prime’ periods for attack.
Types of Attackers
Three main types of attackers:
Casual - doesn’t target the victim specifically and does so while checking out numerous other targets
Determined - targets the victim, has a motive and tries to find specific vulnerabilities of the victim
Funded - similar to determined except performs lots of recon on top of hiring people and equipment to perform the attack
Initialisation Vectors
More broadly IVs are simply used as initialisation values to an iterative process. They are used in cryptographic hash functions such as the Merkle-Damgard construction as constants at the beginning, in the compression with the first message block. There are also times when they are required to be random such as in block ciphers - the purpose of this is so that different messages are encrypted differently. This means that an attacker seeing two messages encrypted with the same key doesn’t give them any more information than the whole message sent together.
Let us consider the usage of the IV in a protocol such as WEP - it uses a 64-bit key where the user is responsible for picking the first 40 bits and the final 24 bits are generated randomly. Since the IV is publicly known as is only 24 bits, it only takes 2^12=4096 different generated IVs before an older one is reused. This defeats the whole purpose of not giving the attacker extra info (described above) and allows the whole key to then be cracked. This is because the user-generated component has fairly low entropy - it only permits 5 character user inputs (with 64 combinations - 0->10, a->z, A->Z) which only represents an 8% subset of all bit combinations - 2^40.
Mixing Data & Control
I’ve discussed this topic at length in previous blog posts, although I did find Richard’s example with the postal stamps quite interesting. Basically he sent himself a heap of ‘expensive’ express postal stamps from within the post office - so the ‘data’ was the stamps and the ‘control’ was the ability to exit the store with them.
I also had another interesting thought regarding this in the tutorial the other week with autonomous cars. If every self-driving car is providing driving data back to their company servers, which is then used in improving their fleet of cars’ autonomous capabilities, isn’t this also technically an example of mixing data and control? For example, if you fed faulty data from hundreds of locations back to the servers which then was distributed back to the users, it could be problematic.
Harvard Architecture
There are two main types of architectures used in microcontrollers: Von Neumann and Harvard. Von Neumann basically has all the memory in one location, with instruction and data using the same bus. Harvard overcomes the data and control issue by having code and data on separate buses; this actually results in an improved performance as they can loaded at the same time.

Buffer Overflows
We had already looked at these overflows in the tutorials a bit, so looking at them in the lecture wasn’t too unfamiliar. The basic idea is that you feed in too much user input to some shonky code which doesn’t validate the length to the size of the buffer. This results in overwriting neighbouring data to the buffer - if this is within a function, it means registers on the stack get overwritten. This may include other variables (affecting control flow within the function) or the return address itself (affecting control flow after the function). Attackers can basically use this to write their code into the buffer and then overwrite the return address to the start of the buffer. (and their code starts executing!)
Most modern programming languages have checks in place to prevent buffer overflows on the stack. (the heap is another gold mine) Canaries in the stack can also be used to detect when they occur - before jumping to the return address, they check a small integer value (of known value beforehand) just before the return address. Although, if you were able to find an exploit to read the variables on the stack beforehand, you could potentially dodge the canary still.
Proof of Work
I’m going to write an article to discuss this in more detail later with regards to the extended cryptocurrency talk. The basic idea is that miners are searching for a SHA-256 hash (with leading 0s depending on ‘difficulty’) which incorporates the previous block and current transactions as part of a header. They search through the hash combinations by changing a ‘nonce’ value within the header which leads to changes in the overall hash. You have to do a lot of work in order to find this hash which provides the security for proof-of-work networks such as Bitcoin.
Moore’s Law
This law is an interesting consideration when talking about how many bits of security we need in certain applications. It basically observed that the number of transistors in an IC doubles every two years - i.e. what we think is ‘safe’ should be 1 bit of security higher every 2 years. The problem is we’ve reached a point where it is getting ridiculously hard to reduce the size even more, so I don’t think it will continue to hold true. However if we find completely different methods (i.e. quantum computing) we could achieve an even more significant ‘sudden’ increase.
Disk Encryption and Cold Boot Attacks
Encryption intends to generate a key based on a user-given password which is then used to encrypt the hard drive contents with a block cipher such as AES (used in Bitlocker). The Master Boot Record (MBR) is typically not encrypted without other hardware-based solutions. The problem with these forms of encryptions is that they are vulnerable to cold boot attacks - the keys used in the decryption may be left in memory when the computer is turned off. This means an attacker with physical access may be able to boot the machine with an OS (on a USB say) and then take a dump of all the memory.
They can then analyse this to look for the key or other user data. Typically the attack is possible if it occurs within 90 minutes of the memory losing power, however this window can be extended in some cases by cooling the modules. Even if some of the data disappears from the memory, the process is somewhat predictable and the missing bits can be rebuilt to an extent.
Brief History of Ciphers
Security by obscurity pretty much dominated the encryption scene up until the 1970s - banks used to ‘roll their own crypto’ and this was an awful idea. It wasn’t until the 1970s when NIST began releasing password and encryption standards. They started a competition to develop a standard data encryption method which was eventually won by IBM who developed the block cipher Lucifer. This method was modified by the NSA to be resistant against differential cryptanalysis, a reduced cipher size of 56 bits and a reduced block size of 64 bits - it became the standard and was known as DES.
It wasn’t long before it was realised how weak DES in terms of the fact it was vulnerable to brute force search - this occurred due to a number of export laws which ensured the use of ‘breakable’ ciphers. (absolutely hilarious) Eventually the NIST underwent another process to find a replacement from 1997 which was a lot more transparent, and resulted in the Advanced Encryption Standard (AES256). Currently there are no good ‘known’ methods to crack AES in a significantly fast enough time (provided a random enough key is used). The main forms of attacks against it are a bit unrelated - they are side-channel attacks such as cache-timing which involve monitoring the CPU to determine the key.
Issue of Authentication
I think solving the problem of authentication is one of the biggest in cyber security - it revolves around the fact that any data a computer system may use for authentication relies on a small piece of information which ‘summarises you as an individual’. For example, it may be an image of your face or it could be a password that only you know. The ability to authenticate a person can only be a good as the ability to keep all these components from an attacker’s hands.
The main strategy (which I think I’ve touched on) we use today in authentication is defense in depth - we try to use as many factors as we can to verify you as an individual. The more factors required, the harder it is for an attacker to spoof your identity; the main factors we typically use are:
Something you know - i.e. password
Something you have - i.e. message to phone
Something you are - i.e. physical identity (picture)
Being able to know that these factors are secure is difficult too - we are only good at proving when information is known as opposed to secret. We may think that measures such as biometrics are difficult to fake, but at the end of the day, we have to remember that computer systems are based on binary. If you know the binary input that will open that door (i.e. how their fingerprint is represented), you can open the door.
Web Security - Extended
I already knew a fair bit about the different attacks due to some experiences in web development and my something awesome. However I will go over some of the key talking points. The basic idea is a HTML page will define the elements on a page, and within this we sometimes have control logic with Javascript which defines how these structures may behave or how a user can interact with them. A lot of the flaws in web revolve around the fact that data (the elements on the page) and control (the Javascript) are mixed in the same location.
The other main thing you need to know is that cookies are stored in a browser for each website you visit. A lot of the time it involves preferences for the sites, but they are also commonly used for persistence in logins; i.e. a unique ID to associated you with a user on the server-side. Sessions are pretty much cookies except they are destroyed when you close your browser and only contain IDs which link to a session file that is stored on the server.
XSS attacks for example rely on someone injecting Javascript into the user input of a website, which is then displayed to other users of the site. Their browsers will then execute the code, which could potentially do something malicious like hijacking their cookies. You can read more about them in my OWASP article on them here. Cross-site request forgery is somewhat similar to these - basically it relies on an authorised individual clicking on an image or link which executes some Javascript which uses their authority on a site for malicious purposes.
The Samy XSS worm was a good example of this - anyone who viewed a profile infected with the worm would execute the script and become infected themselves. This meant they would send Samy a friend request, and if any of their friends viewed their profile they would also be infected. Over 1 million users were infected with the worm on MySpace within 20 hours.
The other main problem associated with web is injection in the server itself. SQL injection is the main source; it involves including SQL code in a user input which (if not escaped) will execute on the server resulting in outputting unintended data or making changes to the database. Without proper protections, it means you can bypass authentication forms and steal all the data from the database.
Web Security - Cryptocurrency
I was part of this presentation and I will give a more detailed writeup on it soon.
6 notes
·
View notes
Text
Xampp install windows 7 64 bit

#Xampp install windows 7 64 bit how to#
#Xampp install windows 7 64 bit install#
#Xampp install windows 7 64 bit update#
Though the above links, you can download Windows 7 ISO without product key. Compared with other editions of Windows 7, it has more features like HomeGroup, Jump lists, Snap, Windows search, Windows Taskbar, full 64-bit, Windows XP mode, BitLocker drive encryption, Window Defender, Windows Firewall, etc.ĭownload Windows 7 Ultimate 32-Bit ISO Windows 7 Ultimate 64-Bit ISO If you want to get the best experience of Windows 7, this edition is recommended. Windows 7 Ultimate: This is the best and fullest edition of Windows including all features of other editions. It includes all features of Windows 7 Pro and additional security features.ĭownload Windows 7 Enterprise 32-Bit ISO Windows 7 Enterprise 64-Bit ISO Windows 7 Enterprise: It is built for large businesses like companies, organizations, and well established national and international firms. It has all premium features including networking.ĭownload Windows 7 Professional 32-Bit ISO Windows 7 Professional 64-Bit ISO Most features of this edition can meet small business requirements. Windows 7 Professional: It is designed for professionals and small business. Windows 7 Home Premium: This edition suits home entertainment with beautiful Aero theme and clear glassy look support. However, it doesn’t have the support for Aero theme and Aero visual graphic support. It has multimedia support so that you can enjoy videos and music. Windows 7 Home Basic: It is a good choice for basic computing at home level. Though it is affordable core operations, it offers limited features. It is built for 32-bit CPU architecture PC. Windows 7 Starter: It is a core edition that covers all core elements for basic computer usage. Then click its corresponding links to download Windows 7 disc images. You can make your choice after reading the brief introduction to these editions. Windows 7 has various editions so that different demands of users can be fulfilled. You can download a suitable Windows 7 version according to your needs.Īlso read: freeload Windows XP ISO: Home & Professional (32 & 64 Bit) Windows 7 ISO File Download Links Hence, the only way to download Windows 7 ISO without product key is to click the direct links. Similarly, you can’t execute the Windows 7 ISO download operation on the Microsoft Windows and Office ISO Download Tool either. Therefore, you can’t download the Windows 7 ISO file using the product key. What You Should Know Before Downloading Windows 7 ISO FilesĪs Windows 7 support had ended, Microsoft has removed the Windows 7 ISO file download page from its official website.
#Xampp install windows 7 64 bit update#
Besides, Microsoft offers some extended security update services. Fortunately, it doesn’t indicate that Windows 7 won’t run anymore. The support for Windows 7 has ended on January 14, 2020, which means that Microsoft will not provide technical support for any issues, software updates, and security updates or fixes for users.
#Xampp install windows 7 64 bit install#
Make a Windows 7 Bootable Media and Install the System.What You Should Know Before Downloading Windows 7 ISO Files.
#Xampp install windows 7 64 bit how to#
How to get the Windows 7 ISO file download since Microsoft has stopped the support for it? Don’t worry about it! MiniTool would shows you how to download Windows 7 ISO without product key in detail.

0 notes
Text
Download WinToHDD crack (serial key) latest version 3ZY№

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 This is an easy solution for installing Windows on devices without an optical drive. This makes it easy to reinstall Windows, reinstall Windows on a different hard drive, and clone your current Windows installation. The bootable USB flash drive created with this feature of the WinToHDD Enterprise registration key also includes a system clone feature that can be used to clone the Windows operating system installation from one drive to another. In other words, not only can you install Windows using WinToHDD, but you can also make a copy of the Windows configuration files and save them on another drive. As expected, you will be prompted to select the source ISO file that contains the Windows configuration files. WinToHDD Enterprise Portable automatically reads data from the disk image and retrieves information about the operating system and its architecture. Then select the system partition where you want to deploy Windows and choose how you want to install it. Whether you know anything about PC innovation or not, this component will undoubtedly allow you to reinstall Windows in just a few clicks. Apart from creating a bootable USB drive that contains all the plan records in the operating system, you can e. Add multilingual support to Windows PE bootable disk. Bug fixed: Could not clone Windows 10 in Greek language support. Correct other minor mistakes. Hot clone Windows without restarting the clone source computer. Clone Windows between drives with different sector sizes. Encrypt the Windows partition with BitLocker when installing or cloning.
1 note
·
View note
Text
Download WinToHDD crack (keygen) latest version BSS?

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 This is an easy solution for installing Windows on devices without an optical drive. This makes it easy to reinstall Windows, reinstall Windows on a different hard drive, and clone your current Windows installation. The bootable USB flash drive created with this feature of the WinToHDD Enterprise registration key also includes a system clone feature that can be used to clone the Windows operating system installation from one drive to another. In other words, not only can you install Windows using WinToHDD, but you can also make a copy of the Windows configuration files and save them on another drive. As expected, you will be prompted to select the source ISO file that contains the Windows configuration files. WinToHDD Enterprise Portable automatically reads data from the disk image and retrieves information about the operating system and its architecture. Then select the system partition where you want to deploy Windows and choose how you want to install it. Whether you know anything about PC innovation or not, this component will undoubtedly allow you to reinstall Windows in just a few clicks. Apart from creating a bootable USB drive that contains all the plan records in the operating system, you can e. Add multilingual support to Windows PE bootable disk. Bug fixed: Could not clone Windows 10 in Greek language support. Correct other minor mistakes. Hot clone Windows without restarting the clone source computer. Clone Windows between drives with different sector sizes. Encrypt the Windows partition with BitLocker when installing or cloning.
1 note
·
View note
Text
Welcome to Windows Server 2016
by Curtis Brown

As we approach the end of the year, Microsoft have released the latest version of their server-side flavour of their Operating System offering – Windows Server 2016. It’s been three years since the release of Windows Server 2012R2. Let’s take a look at some details in this new version.
Editions and Licensing
As featured before, we have Datacentre and Standard versions – the former is now aimed specifically for “highly virtualised datacentre and cloud environments” while the latter is intended for physical servers.
The Datacentre version’s additional features, above and beyond Standard, emphasise this cloud prioritisation:
Shielded VMs
Software defined networking
Storage Spaces Direct
Storage Replica
In addition, a Standard edition license covers you for two “Operating System Environments” (OSEs – Windows instances) or Hyper-V containers, while Datacentre is unlimited.
There are some additional variants:
Essentials replaces the old Foundation release aimed at small (25 user / 50 devices) businesses
MultiPoint Premium Server is a specific edition for Remote Desktop access and is only available to Academic licensees – The MultiPoint Premium Server role is included in Standard and Datacentre, requiring Server CALs and RDS CALs as before
Storage Server is an OEM release for Windows based storage solutions
Hyper-V 2016 – the free, Hypervisor only offering continues (remember to license your guests though…)
The big news for Datacentre and Standard is that licensing has moved to a core, rather than the socket based model (as is for all other editions). All cores on a physical host must be licensed, with a minimum license of 16 core licenses per server – with a minimum of 8 core licenses per physical processor. Core license packs are sold in 2-core packs, so a minimum purchase is basically 8 x 2-core packs.
Microsoft state that this will be priced equivalent to a 2 CPU Windows 2012R2 edition. Beware though, if you’ve purchased a new 2-socket box with a pair of Intel Xeon with a high core count, this could look quite pricey. Take a server with two Intel Xeon E5-2699 v4 — this would have 44 cores (each CPU has 22 cores), so straight away, you’re looking at 22 x 2 core licensing packs, which would be the equivalent to buying 3 CPU licenses of Windows Server 2012R2. Draw your own conclusions.
One note – if you have an existing Software Assurance agreement, moving to Core based licensing only kicks in when the agreement is renewed – you’ll be getting a minimum of 8 cores per processor and 16 cores per server licenses for each 2-processor license at renewal of the agreement.
New Toys!
So, now that the pain point of licensing is out of the way, let’s take a look at some of the new features mentioned above.
Shielded VMs
This is a security mechanism that allows administrators to provide a means to secure individual VMs. It leverages a Guardian service that stores keys which an approved Hyper-V 2016 host uses to prove its authorisation to run shielded VMs. Hyper-V 2016 uses Trusted Platform Module (TPM) and UEFI on start-up to ensure it is healthy and provides confirmation of its identity when presenting itself to the Guardian service. If all is well, the Guardian issues a certificate to the host enabling it to run the Shielded VM. The VM itself is encrypted (using BitLocker backed by vTPM) and uses a hardened VM worker process of the host that encrypts all state related content, checkpoints, replicas and migration traffic. The VM also has no console access, including VM external features such as Guest File Copy, PowerShell integration or direct administrative permission to the guest OS.
Software defined networking
Leveraging technology from Azure, Windows Server 2016 networking has gained the ability to deploy policies providing QoS, isolation, load balancing and DNS (amongst others).
This ability is provided through network virtualisation handled by VXLAN based micro-segmentation, much in the same way as VMware NSX.
All this is possible due to the implementation of a new installable Network Controller component. This manages firewalling (vSwitch port all the way to datacentre), Fabric management (IP subnets, VLANs, L2/L3 switching), network monitoring and topology discovery, L4 load balancing and RAS gateway management.
Software Defined Storage
Storage Spaces Direct leverages local storage to create a converged storage architecture, somewhat similar to VMware VSAN. Like VSAN, it’s primarily aimed at storage for virtualisation.
Resiliency to drive failures etc. is configurable by volume type, supporting mirroring (performance) and erasure coding (efficiency). Furthermore, hybrid volumes combine these techniques into a single volume with an added ability of automatic storage tiering.
Storage Replica
Storage Replica offers a built in synchronous replication solution for business continuity and DR.
Containers
Windows 2016 now provides the means to deploy applications in Containers, in keeping with the current trend towards a DevOps model. Developers can package applications and deploy as containers. Containers come in two flavours – Windows Server or Hyper-V. The difference between these is that a Windows Server container is broadly the same as a Linux one. The application itself is containerised, with its own view of the host OS. Hyper-V containers are more virtualisation driven, with the container including an operating system. This leverages hardware virtualisation, and completely isolates the container from the host OS. Windows Server Containers, being somewhat smaller and less resource intensive, scale more efficiently but Hyper-V containers are more isolated and secure.
In addition, Windows 10 Professional and Enterprise Anniversary Editions both support Containers, allowing developers to create containers on their workstations and deploy to Windows Server 2016.
Nano Servers
Nano Server is a Windows 2016 deployment option that provides the ability to deploy the smallest possible footprint Windows Server installation. It is so small that it runs headless, with no GUI etc. so taking Server Core to the next level. It’s designed specifically for Cloud workloads and specific use cases (including Containers). Being such a small install reduces the surface area and so improves security whilst reducing the patching and support overhead.
Nano isn’t selected as an installation option – deployment requires customisation of the image for a variety of reasons, not least defining device drivers as it lacks user-mode plug-play.
Closing Thoughts…
We’ve only scratched the surface of the new features of Windows Server 2016. Many of these are quite attractive, even when expanding beyond the Microsoft world. I can see Nano in particular being an interesting option in a VMware vSphere platform for application delivery, perhaps as a part of a vRealize Automation solution. Of course, time will tell how successful these new features are – network virtualisation for example will need to compete with the traditional networking player offerings by Cisco etc. as well as software solutions such as VMware NSX.
Of course, licensing is a question mark of its own which will have implications for most customers, including those running VMware vSphere. I’m looking forward to seeing how Windows Server 2016 is accepted into the marketplace and how it develops.
About the Author
Curtis Brown joined the Xtravirt consulting team in October 2012. His specialist areas include End User Compute solutions and Virtual Infrastructure design and implementation with particular strength in VDI, storage integration, backup and Disaster Recovery design/implementation. He is a VMware vExpert 2016
0 notes
Photo

Security Solutions from DELL
Data security keeps your business moving forward
The accelerated pace of cyber-attacks combined with an increasingly mobile workforce exponentially increases the need for organizations to protect their most valuable resource, data. With security products saturating the market, securing and managing data at the endpoints without choking workforce productivity or burdening your IT staff is a huge undertaking.
In the face of this burgeoning cyber perimeter, Dell offers its new endpoint security and management portfolio, delivering essential protection while unlocking the speed, agility, and innovation of your workforce. Dell’s portfolio represents the full range of best-in-class solutions addressing data protection, identity assurance, threat protection & response, and endpoint management.
And Dell is in the best position to deliver the ideal combination of solutions you need today and in the future. As the leader in endpoint computing, Dell has created a winning team of the biggest names in cybersecurity and endpoint management -- RSA, Mozy, and AirWatch. Its control of each of the solutions ensures mutual compatibility* and optimal security across the portfolio.
Dell Data Protection | Endpoint Security Suite Enterprise 02:20
Components
Protect your business with intelligent, centrally-managed endpoint security and compliance solutions from Dell.
Endpoint security suites
Address your critical needs in one integrated package with endpoint protection for data, systems and reputations, all managed via a single console. Dell Data Protection | Endpoint Security Suite Enterprise includes advanced threat prevention, enterprise-class encryption, and authentication for both virtual and physical Windows desktops. Revolutionary advanced threat prevention offers unparalleled efficacy against zero-day threats, advanced persistent threats and commodity malware. In fact, testing shows that our advanced threat protection is 99% effective versus an average of 50% for traditional anti-virus. This suite also includes Dell's exclusive, patent-pending BIOS verification technology to notify IT of potential BIOS tampering on select Dell commercial systems.
Advanced threat prevention
Preventative solutions are eclipsing traditional signature-based anti-virus solutions. They are more effective against advanced persistent threats. Protect your organization from the latest persistent and targeted threats, including ransomware and zero-day attacks. With a revolutionary artificial intelligence technology, it stops 99% of executable malware. It is lightweight and easy to set up with a cloud based management console and protection for a wide range of endpoints including thin clients. This alternative solution seamlessly contains, detects, and prevents the spread of malware by handling at-risk files in a virtualized, contained environment.
Endpoint threat detection and response
Threats today are more advanced than ever before. While Dell’s Endpoint Security Suite Enterprise stops 99% of malware, more targeted attacks can potentially evade this line of defense. For those threats, there is RSA NetWitness® Endpoint.
RSA NetWitness Endpoint is an endpoint threat detection and response solution that leverages behavioral-based monitoring and machine learning to more rapidly detect threats – including non-malware-based attacks – missed by other security solutions, thereby reducing attacker dwell time. Security teams gain a powerful investigation platform to detect and analyze both known and unknown threats, determine full scope, and take immediate action to limit negative business impact.
Intelligent encryption
Protect your data at-rest, in-motion, and in-use with data-centric endpoint encryption. Centrally manage BitLocker and self-encrypting drives and secure data at-rest on your endpoints, external media, and servers with Dell Data Protection | Enterprise Edition, which includes our web-based console for administration, device and user detail and compliance reports. Or set up and manage secure encryption at a local PC level with Dell Data Protection | Personal Edition. Secure Lifecycle provides security of your data wherever it goes, enabling authority over data usage and file access visibility for your most important business files. Dell data encryption solutions support Windows PCs, Servers, tablets, Macs, and mobile devices.
Backup and restore
Protect vital data with Mozy®, cloud-based backup, sync, and recovery software. Mozy® allows for immediate recovery of data, keeping your business productive in the event of data loss from user error, hardware failure, malware attack, or natural disaster. Implementing a comprehensive cloud-based storage solution improves your security posture and reduces IT complexity. Management, compliance, and other reporting requirements can be met, and the need for additional storage hardware can be reduced. MozyPro is for businesses of all sizes. MozyEnterprise includes the features of MozyPro, plus Active Directory integration for user management.
Identity assurance
Authentication is a foundational element of your security architecture. RSA SecurID Access provides world-leading authentication and access assurance solutions protecting 25,000 organizations and 55 million users.
It delivers secure and convenient access for any user, from anywhere, to anything. Organizations use RSA SecurID Access to regain control of a disrupted perimeter with strong, secure access and single sign-on to the leading Web and SaaS applications, native mobile apps and traditional enterprise resources (including VPNs, firewalls, virtual desktops and Windows or Linux servers). With RSA SecurID Access, organizations can have secure access to cloud and mobile applications without creating roadblocks for users.
Endpoint management
VMware AirWatch® is a comprehensive enterprise mobility platform with a multi-layered security approach across the user, endpoint, app, data and network featuring a new and more efficient approach to Windows lifecycle management. The unified endpoint management (UEM) technology fundamentally changes how organizations approach PC lifecycle management. By combining the requirements of traditional PC lifecycle management and the modern EMM approaches, VMware AirWatch UEM lowers the cost of managing organizations’ Windows deployments, secures endpoints and data on any network across any application, and delivers peak user experience across any device.
Endpoint visibility and remediation
Respond to insider threats, verify end user and device activity, and ensure compliance with Absolute Data & Device Security. Absolute delivers insights and remediation via a two-way connection to each device that can survive a OS reinstall or hard-drive wipe. Powered by Persistence®, this unique technology can also be extended to SCCM and other critical business applications in your enterprise.
This means you’re always in control, even if a device is off the network or in the hands of an unauthorized user. Your connection to each device provides you with the insight you need to assess risk scenarios, apply remote security measures, and comply with data protection regulations.
0 notes
Text
Data security solutions by DELL
Data security keeps your business moving forward
The accelerated pace of cyber-attacks combined with an increasingly mobile workforce exponentially increases the need for organizations to protect their most valuable resource, data. With security products saturating the market, securing and managing data at the endpoints without choking workforce productivity or burdening your IT staff is a huge undertaking.
In the face of this burgeoning cyber perimeter, Dell offers its new endpoint security and management portfolio, delivering essential protection while unlocking the speed, agility, and innovation of your workforce. Dell’s portfolio represents the full range of best-in-class solutions addressing data protection, identity assurance, threat protection & response, and endpoint management.
And Dell is in the best position to deliver the ideal combination of solutions you need today and in the future. As the leader in endpoint computing, Dell has created a winning team of the biggest names in cybersecurity and endpoint management -- RSA, Mozy, and AirWatch. Its control of each of the solutions ensures mutual compatibility* and optimal security across the portfolio.
Dell Data Protection | Endpoint Security Suite Enterprise 02:20
Components
Protect your business with intelligent, centrally-managed endpoint security and compliance solutions from Dell.
Endpoint security suites
Address your critical needs in one integrated package with endpoint protection for data, systems and reputations, all managed via a single console. Dell Data Protection | Endpoint Security Suite Enterprise includes advanced threat prevention, enterprise-class encryption, and authentication for both virtual and physical Windows desktops. Revolutionary advanced threat prevention offers unparalleled efficacy against zero-day threats, advanced persistent threats and commodity malware. In fact, testing shows that our advanced threat protection is 99% effective versus an average of 50% for traditional anti-virus. This suite also includes Dell's exclusive, patent-pending BIOS verification technology to notify IT of potential BIOS tampering on select Dell commercial systems.
Advanced threat prevention
Preventative solutions are eclipsing traditional signature-based anti-virus solutions. They are more effective against advanced persistent threats. Protect your organization from the latest persistent and targeted threats, including ransomware and zero-day attacks. With a revolutionary artificial intelligence technology, it stops 99% of executable malware. It is lightweight and easy to set up with a cloud based management console and protection for a wide range of endpoints including thin clients. This alternative solution seamlessly contains, detects, and prevents the spread of malware by handling at-risk files in a virtualized, contained environment.
Endpoint threat detection and response
Threats today are more advanced than ever before. While Dell’s Endpoint Security Suite Enterprise stops 99% of malware, more targeted attacks can potentially evade this line of defense. For those threats, there is RSA NetWitness® Endpoint.
RSA NetWitness Endpoint is an endpoint threat detection and response solution that leverages behavioral-based monitoring and machine learning to more rapidly detect threats – including non-malware-based attacks – missed by other security solutions, thereby reducing attacker dwell time. Security teams gain a powerful investigation platform to detect and analyze both known and unknown threats, determine full scope, and take immediate action to limit negative business impact.
Intelligent encryption
Protect your data at-rest, in-motion, and in-use with data-centric endpoint encryption. Centrally manage BitLocker and self-encrypting drives and secure data at-rest on your endpoints, external media, and servers with Dell Data Protection | Enterprise Edition, which includes our web-based console for administration, device and user detail and compliance reports. Or set up and manage secure encryption at a local PC level with Dell Data Protection | Personal Edition. Secure Lifecycle provides security of your data wherever it goes, enabling authority over data usage and file access visibility for your most important business files. Dell data encryption solutions support Windows PCs, Servers, tablets, Macs, and mobile devices.
Backup and restore
Protect vital data with Mozy®, cloud-based backup, sync, and recovery software. Mozy® allows for immediate recovery of data, keeping your business productive in the event of data loss from user error, hardware failure, malware attack, or natural disaster. Implementing a comprehensive cloud-based storage solution improves your security posture and reduces IT complexity. Management, compliance, and other reporting requirements can be met, and the need for additional storage hardware can be reduced. MozyPro is for businesses of all sizes. MozyEnterprise includes the features of MozyPro, plus Active Directory integration for user management.
Identity assurance
Authentication is a foundational element of your security architecture. RSA SecurID Access provides world-leading authentication and access assurance solutions protecting 25,000 organizations and 55 million users.
It delivers secure and convenient access for any user, from anywhere, to anything. Organizations use RSA SecurID Access to regain control of a disrupted perimeter with strong, secure access and single sign-on to the leading Web and SaaS applications, native mobile apps and traditional enterprise resources (including VPNs, firewalls, virtual desktops and Windows or Linux servers). With RSA SecurID Access, organizations can have secure access to cloud and mobile applications without creating roadblocks for users.
Endpoint management
VMware AirWatch® is a comprehensive enterprise mobility platform with a multi-layered security approach across the user, endpoint, app, data and network featuring a new and more efficient approach to Windows lifecycle management. The unified endpoint management (UEM) technology fundamentally changes how organizations approach PC lifecycle management. By combining the requirements of traditional PC lifecycle management and the modern EMM approaches, VMware AirWatch UEM lowers the cost of managing organizations’ Windows deployments, secures endpoints and data on any network across any application, and delivers peak user experience across any device.
Endpoint visibility and remediation
Respond to insider threats, verify end user and device activity, and ensure compliance with Absolute Data & Device Security. Absolute delivers insights and remediation via a two-way connection to each device that can survive a OS reinstall or hard-drive wipe. Powered by Persistence®, this unique technology can also be extended to SCCM and other critical business applications in your enterprise.
This means you’re always in control, even if a device is off the network or in the hands of an unauthorized user. Your connection to each device provides you with the insight you need to assess risk scenarios, apply remote security measures, and comply with data protection regulations.
0 notes
Text
Data Security solutions by DELL
Data security keeps your business moving forward
The accelerated pace of cyber-attacks combined with an increasingly mobile workforce exponentially increases the need for organizations to protect their most valuable resource, data. With security products saturating the market, securing and managing data at the endpoints without choking workforce productivity or burdening your IT staff is a huge undertaking.
In the face of this burgeoning cyber perimeter, Dell offers its new endpoint security and management portfolio, delivering essential protection while unlocking the speed, agility, and innovation of your workforce. Dell’s portfolio represents the full range of best-in-class solutions addressing data protection, identity assurance, threat protection & response, and endpoint management.
And Dell is in the best position to deliver the ideal combination of solutions you need today and in the future. As the leader in endpoint computing, Dell has created a winning team of the biggest names in cybersecurity and endpoint management -- RSA, Mozy, and AirWatch. Its control of each of the solutions ensures mutual compatibility* and optimal security across the portfolio.
Dell Data Protection | Endpoint Security Suite Enterprise 02:20
Components
Protect your business with intelligent, centrally-managed endpoint security and compliance solutions from Dell.
Endpoint security suites
Address your critical needs in one integrated package with endpoint protection for data, systems and reputations, all managed via a single console. Dell Data Protection | Endpoint Security Suite Enterprise includes advanced threat prevention, enterprise-class encryption, and authentication for both virtual and physical Windows desktops. Revolutionary advanced threat prevention offers unparalleled efficacy against zero-day threats, advanced persistent threats and commodity malware. In fact, testing shows that our advanced threat protection is 99% effective versus an average of 50% for traditional anti-virus. This suite also includes Dell's exclusive, patent-pending BIOS verification technology to notify IT of potential BIOS tampering on select Dell commercial systems.
Advanced threat prevention
Preventative solutions are eclipsing traditional signature-based anti-virus solutions. They are more effective against advanced persistent threats. Protect your organization from the latest persistent and targeted threats, including ransomware and zero-day attacks. With a revolutionary artificial intelligence technology, it stops 99% of executable malware. It is lightweight and easy to set up with a cloud based management console and protection for a wide range of endpoints including thin clients. This alternative solution seamlessly contains, detects, and prevents the spread of malware by handling at-risk files in a virtualized, contained environment.
Endpoint threat detection and response
Threats today are more advanced than ever before. While Dell’s Endpoint Security Suite Enterprise stops 99% of malware, more targeted attacks can potentially evade this line of defense. For those threats, there is RSA NetWitness® Endpoint.
RSA NetWitness Endpoint is an endpoint threat detection and response solution that leverages behavioral-based monitoring and machine learning to more rapidly detect threats – including non-malware-based attacks – missed by other security solutions, thereby reducing attacker dwell time. Security teams gain a powerful investigation platform to detect and analyze both known and unknown threats, determine full scope, and take immediate action to limit negative business impact.
Intelligent encryption
Protect your data at-rest, in-motion, and in-use with data-centric endpoint encryption. Centrally manage BitLocker and self-encrypting drives and secure data at-rest on your endpoints, external media, and servers with Dell Data Protection | Enterprise Edition, which includes our web-based console for administration, device and user detail and compliance reports. Or set up and manage secure encryption at a local PC level with Dell Data Protection | Personal Edition. Secure Lifecycle provides security of your data wherever it goes, enabling authority over data usage and file access visibility for your most important business files. Dell data encryption solutions support Windows PCs, Servers, tablets, Macs, and mobile devices.
Backup and restore
Protect vital data with Mozy®, cloud-based backup, sync, and recovery software. Mozy® allows for immediate recovery of data, keeping your business productive in the event of data loss from user error, hardware failure, malware attack, or natural disaster. Implementing a comprehensive cloud-based storage solution improves your security posture and reduces IT complexity. Management, compliance, and other reporting requirements can be met, and the need for additional storage hardware can be reduced. MozyPro is for businesses of all sizes. MozyEnterprise includes the features of MozyPro, plus Active Directory integration for user management.
Identity assurance
Authentication is a foundational element of your security architecture. RSA SecurID Access provides world-leading authentication and access assurance solutions protecting 25,000 organizations and 55 million users.
It delivers secure and convenient access for any user, from anywhere, to anything. Organizations use RSA SecurID Access to regain control of a disrupted perimeter with strong, secure access and single sign-on to the leading Web and SaaS applications, native mobile apps and traditional enterprise resources (including VPNs, firewalls, virtual desktops and Windows or Linux servers). With RSA SecurID Access, organizations can have secure access to cloud and mobile applications without creating roadblocks for users.
Endpoint management
VMware AirWatch® is a comprehensive enterprise mobility platform with a multi-layered security approach across the user, endpoint, app, data and network featuring a new and more efficient approach to Windows lifecycle management. The unified endpoint management (UEM) technology fundamentally changes how organizations approach PC lifecycle management. By combining the requirements of traditional PC lifecycle management and the modern EMM approaches, VMware AirWatch UEM lowers the cost of managing organizations’ Windows deployments, secures endpoints and data on any network across any application, and delivers peak user experience across any device.
Endpoint visibility and remediation
Respond to insider threats, verify end user and device activity, and ensure compliance with Absolute Data & Device Security. Absolute delivers insights and remediation via a two-way connection to each device that can survive a OS reinstall or hard-drive wipe. Powered by Persistence®, this unique technology can also be extended to SCCM and other critical business applications in your enterprise.
This means you’re always in control, even if a device is off the network or in the hands of an unauthorized user. Your connection to each device provides you with the insight you need to assess risk scenarios, apply remote security measures, and comply with data protection regulations.
0 notes
Photo

DATA SECURITY SOLUTION BY DELL
Data security keeps your business moving forward
The accelerated pace of cyber-attacks combined with an increasingly mobile workforce exponentially increases the need for organizations to protect their most valuable resource, data. With security products saturating the market, securing and managing data at the endpoints without choking workforce productivity or burdening your IT staff is a huge undertaking.
In the face of this burgeoning cyber perimeter, Dell offers its new endpoint security and management portfolio, delivering essential protection while unlocking the speed, agility, and innovation of your workforce. Dell’s portfolio represents the full range of best-in-class solutions addressing data protection, identity assurance, threat protection & response, and endpoint management.
And Dell is in the best position to deliver the ideal combination of solutions you need today and in the future. As the leader in endpoint computing, Dell has created a winning team of the biggest names in cybersecurity and endpoint management -- RSA, Mozy, and AirWatch. Its control of each of the solutions ensures mutual compatibility* and optimal security across the portfolio.
Dell Data Protection | Endpoint Security Suite Enterprise 02:20
Components
Protect your business with intelligent, centrally-managed endpoint security and compliance solutions from Dell.
Endpoint security suites
Address your critical needs in one integrated package with endpoint protection for data, systems and reputations, all managed via a single console. Dell Data Protection | Endpoint Security Suite Enterprise includes advanced threat prevention, enterprise-class encryption, and authentication for both virtual and physical Windows desktops. Revolutionary advanced threat prevention offers unparalleled efficacy against zero-day threats, advanced persistent threats and commodity malware. In fact, testing shows that our advanced threat protection is 99% effective versus an average of 50% for traditional anti-virus. This suite also includes Dell's exclusive, patent-pending BIOS verification technology to notify IT of potential BIOS tampering on select Dell commercial systems.
Advanced threat prevention
Preventative solutions are eclipsing traditional signature-based anti-virus solutions. They are more effective against advanced persistent threats. Protect your organization from the latest persistent and targeted threats, including ransomware and zero-day attacks. With a revolutionary artificial intelligence technology, it stops 99% of executable malware. It is lightweight and easy to set up with a cloud based management console and protection for a wide range of endpoints including thin clients. This alternative solution seamlessly contains, detects, and prevents the spread of malware by handling at-risk files in a virtualized, contained environment.
Endpoint threat detection and response
Threats today are more advanced than ever before. While Dell’s Endpoint Security Suite Enterprise stops 99% of malware, more targeted attacks can potentially evade this line of defense. For those threats, there is RSA NetWitness® Endpoint.
RSA NetWitness Endpoint is an endpoint threat detection and response solution that leverages behavioral-based monitoring and machine learning to more rapidly detect threats – including non-malware-based attacks – missed by other security solutions, thereby reducing attacker dwell time. Security teams gain a powerful investigation platform to detect and analyze both known and unknown threats, determine full scope, and take immediate action to limit negative business impact.
Intelligent encryption
Protect your data at-rest, in-motion, and in-use with data-centric endpoint encryption. Centrally manage BitLocker and self-encrypting drives and secure data at-rest on your endpoints, external media, and servers with Dell Data Protection | Enterprise Edition, which includes our web-based console for administration, device and user detail and compliance reports. Or set up and manage secure encryption at a local PC level with Dell Data Protection | Personal Edition. Secure Lifecycle provides security of your data wherever it goes, enabling authority over data usage and file access visibility for your most important business files. Dell data encryption solutions support Windows PCs, Servers, tablets, Macs, and mobile devices.
Backup and restore
Protect vital data with Mozy®, cloud-based backup, sync, and recovery software. Mozy® allows for immediate recovery of data, keeping your business productive in the event of data loss from user error, hardware failure, malware attack, or natural disaster. Implementing a comprehensive cloud-based storage solution improves your security posture and reduces IT complexity. Management, compliance, and other reporting requirements can be met, and the need for additional storage hardware can be reduced. MozyPro is for businesses of all sizes. MozyEnterprise includes the features of MozyPro, plus Active Directory integration for user management.
Identity assurance
Authentication is a foundational element of your security architecture. RSA SecurID Access provides world-leading authentication and access assurance solutions protecting 25,000 organizations and 55 million users.
It delivers secure and convenient access for any user, from anywhere, to anything. Organizations use RSA SecurID Access to regain control of a disrupted perimeter with strong, secure access and single sign-on to the leading Web and SaaS applications, native mobile apps and traditional enterprise resources (including VPNs, firewalls, virtual desktops and Windows or Linux servers). With RSA SecurID Access, organizations can have secure access to cloud and mobile applications without creating roadblocks for users.
Endpoint management
VMware AirWatch® is a comprehensive enterprise mobility platform with a multi-layered security approach across the user, endpoint, app, data and network featuring a new and more efficient approach to Windows lifecycle management. The unified endpoint management (UEM) technology fundamentally changes how organizations approach PC lifecycle management. By combining the requirements of traditional PC lifecycle management and the modern EMM approaches, VMware AirWatch UEM lowers the cost of managing organizations’ Windows deployments, secures endpoints and data on any network across any application, and delivers peak user experience across any device.
Endpoint visibility and remediation
Respond to insider threats, verify end user and device activity, and ensure compliance with Absolute Data & Device Security. Absolute delivers insights and remediation via a two-way connection to each device that can survive a OS reinstall or hard-drive wipe. Powered by Persistence®, this unique technology can also be extended to SCCM and other critical business applications in your enterprise.
This means you’re always in control, even if a device is off the network or in the hands of an unauthorized user. Your connection to each device provides you with the insight you need to assess risk scenarios, apply remote security measures, and comply with data protection regulations.
0 notes