#Data Preservation in eDiscovery
Explore tagged Tumblr posts
Text
#eDiscovery#GRC#Automate Data Processing#Corporate Legal Department#Data Governance#Data Preservation in eDiscovery#Data Privacy Compliance#eDiscovery Legal Holds#Electronically Stored Information (ESI)#Information Governance#Legal Risk Mitigation#Legal Technology#Technology Assisted Review
0 notes
Text
eDiscovery Software for Corporate Legal Teams: Enhancing Efficiency and Compliance
In today’s fast-paced corporate environment, legal teams face increasing challenges in managing vast amounts of digital data. eDiscovery software for corporate legal teams streamlines the process by automating data collection, review, and compliance, ensuring accuracy and efficiency.
Advanced AI-powered eDiscovery solutions help organizations quickly identify relevant documents, reduce costs, and minimize risks associated with litigation and regulatory investigations. Features like legal hold automation, data preservation, and advanced analytics enable corporate legal teams to handle cases with greater precision.
Explore Casepoint’s eDiscovery software for corporate legal teams to optimize your legal workflows. Their comprehensive platform enhances collaboration, ensures compliance, and accelerates case resolution—empowering legal professionals in the digital age.
0 notes
Text
Spoliation — Actionable Insights
Key Themes and Actionable Insights from Recent eDiscovery Case Law – Q4 2024
Recent developments in eDiscovery case law highlight significant trends legal counsel, eDiscovery professionals, and business leaders should keep an eye on, including the growing complexity of privilege assertions, the increasing scrutiny around spoliation of evidence, and the evolving dynamics of discovery requests in class actions and employment disputes.
This Insight summarizes key takeaways from recent cases and provides actionable steps for stakeholders.
Recent eDiscovery Case Law
Cross-Border Discovery Obligations
In Maryland, the courts recently reaffirmed the potential for US-style discovery to be compelled in support of foreign proceedings under 28 USC § 1782.
This decision underscored that discovery obligations can extend to cases where the connection between the respondent and the evidence is not entirely clear.
A dispute over metadata attribution did not derail the court’s decision to grant subpoenas in part, illustrating the leniency afforded when evidence is deemed relevant to anticipated proceedings.
Discovery in Class Actions
Meanwhile, in Florida, a case involving class action discovery highlighted the courts’ growing intolerance for delays.
A plaintiff’s request for discovery was challenged on the grounds that it was premature, given a pending motion to dismiss.
However, the court rejected this argument, emphasizing that discovery should proceed concurrently when issues of class and merits overlap.
This approach aims to streamline litigation and reduce the inefficiencies caused by bifurcation, a recurring point of contention in complex litigation.
Proportionality in Employment Cases
Turning to employment-related disputes in New York, a court tackled the scope of discovery by allowing limited pre-employment discovery while rejecting overly broad requests.
For example, a demand for all complaints against a parent company was deemed unduly burdensome and not proportional to the needs of the case.
This decision reflects a balance between the necessity of evidence for claims and defenses and the need to avoid excessive burdens on responding parties. It also serves as a reminder of the importance of tailoring discovery requests to specific issues in dispute.
Preservation and Spoliation Risks
In Ohio, a case on spoliation of evidence underscored the critical importance of proper preservation protocols.
The court ruled that oral litigation holds were insufficient and emphasized the need to verify compliance with written holds.
In this instance, the failure to preserve text messages led to sanctions, including allowing the opposing party to present the spoliation issue at trial and recover attorneys’ fees.
The case illustrates the severe consequences of inadequate preservation efforts, particularly in an era where courts expect litigants to understand and manage their data retention settings.
Privilege Assertions and Waivers
California courts have been at the forefront of evaluating privilege assertions.
In one case, privilege claims over documents related to compliance efforts were rejected as overly broad.
Similarly, in Oregon, privilege was waived when internal investigation memoranda were shared with outside counsel for a former employee, leading to a broader scope of discoverable materials.
These cases serve as cautionary tales for legal teams managing sensitive documents.
Overextending privilege claims or sharing privileged materials, even with trusted third parties, can lead to unintended waivers with far-reaching implications.
Managing Privilege Burdens
Another California case highlighted the burdens associated with asserting privilege, particularly in large-scale litigation.
In that matter, a company was ordered to revise its privilege logs and provide more detailed explanations for tens of thousands of withheld documents.
This decision reflects the increasing judicial scrutiny on privilege logs and underscores the importance of meeting privilege assertion obligations in the first instance to avoid costly and time-consuming revisions.
Spoliation Without Sanctions
In Minnesota, a spoliation case involving destroyed USB drives revealed the complexities of determining intent and relevance.
While the court acknowledged that the drives were destroyed after the duty to preserve was triggered, it found insufficient evidence to prove intent to deprive or relevance of the data.
As a result, no sanctions were awarded.
This outcome highlights the importance of documenting preservation efforts and providing credible explanations for any lost evidence, as intent and relevance are critical factors in spoliation rulings.
Action Items for Stakeholders
For In-House Counsel
Audit Discovery Readiness:
Evaluate internal processes for compliance with US-style discovery obligations under § 1782.
Ensure documentation practices are robust to withstand evidentiary challenges.
Implement Comprehensive Preservation Protocols:
Ensure written litigation holds are issued and compliance is actively monitored.
For Outside Counsel
Tailor Discovery Requests:
Craft narrowly focused requests to avoid overbreadth objections, especially in class actions and employment disputes.
Review Privilege Assertions:
Reassess privilege logs to ensure compliance with increasing judicial scrutiny.
Avoid over-designating documents as privileged.
For E-Discovery Professionals
Leverage Technology:
Utilize advanced tools to streamline privilege log creation and monitor compliance with litigation holds.
Training Programs:
Conduct regular training for teams on evolving case law trends and best practices for preservation and privilege management.
For Business Leaders
Educate Teams on Retention Policies:
Ensure employees are aware of data preservation obligations and the potential consequences of spoliation.
Collaborate Proactively:
Foster communication with legal teams to address discovery disputes efficiently and minimize litigation costs.
These recent eDiscovery case law developments highlight the growing complexity and importance of discovery management in litigation.
By adopting proactive measures and staying attuned to evolving judicial expectations, stakeholders can mitigate risks and streamline litigation processes.
0 notes
Text
The eDiscovery Market Landscape: Key Drivers and Emerging Technologies
The global eDiscovery market size was estimated at USD 14.99 billion in 2023 and is expected to grow at a CAGR of 10.7% from 2024 to 2030. The increasing need for organizations to preserve metadata from electronic documents is significantly driving market growth. Moreover, stringent regulatory requirements are rising constantly, and the preservation of metadata ensures that digital information remains authentic and accessible over time. This trend of data transitions from analog to digital formats, which necessitates robust eDiscovery solutions, is expected to fuel market growth in the coming years.
The shift towards cloud-based services has transformed how organizations manage their data. Cloud-based E-discovery solutions offer scalability, cost-effectiveness, and ease of access compared to traditional on-premises systems. This trend is further accelerated by the growing remote work culture post-COVID-19, as companies are seeking flexible solutions that can support distributed teams while ensuring compliance with legal standards.
eDiscovery Market Report Highlights
The solutions segment in the market registered the largest share of over 55% in 2023, owing to the increasing reliance on advanced technologies and software solutions that streamline the process of electronic data discovery.
The large enterprises segment accounted for the largest market share in 2023. Large enterprises typically have extensive data management needs, driven by their vast amounts of digital information generated from various sources such as emails, documents, and databases.
The legal sector segment in the market registered the largest share in 2023. This growth can be attributed to the increasing complexity of legal regulations across various industries, which has necessitated a higher demand for legal services, particularly in areas such as compliance, intellectual property, and corporate governance.
The on-premise segment registered the largest revenue share in 2023. This growth can be attributed to its established presence and the preference of many organizations for maintaining control over their data.
Global eDiscovery Market Report Segmentation
This report forecasts revenue growth at global, regional, and country levels and provides an analysis of the latest industry trends in each of the sub-segments from 2018 to 2030. For this study, Grand View Research has segmented the global eDiscovery market report based on component, organization size, deployment model, end-use, and region:
Component Outlook (Revenue, USD Billion, 2018 - 2030)
Solutions
Services
Organization Size Outlook (Revenue, USD Billion, 2018 - 2030)
Large Enterprises
Small and Medium Enterprises
Deployment Model Outlook (Revenue, USD Billion, 2018 - 2030)
On-premise
Cloud
End Use Outlook (Revenue, USD Billion, 2018 - 2030)
Legal Sector
Government and Regulatory Agencies
BFSI
Healthcare
Retail and Consumer Goods
Energy and Utilities
IT and Telecommunications
Manufacturing
Others
Regional Outlook (Revenue, USD Billion, 2018 - 2030)
North America
US
Canada
Mexico
Europe
UK
Germany
France
Asia Pacific
China
Australia
Japan
India
South Korea
Latin America
Brazil
Middle East & Africa
South Africa
Saudi Arabia
UAE
Order a free sample PDF of the eDiscovery Market Intelligence Study, published by Grand View Research.
0 notes
Text
Enterprise Information Archiving Market- Top Players with Size & Share Analysis 2027 | Credence Research

The latest market report published by Credence Research, Inc. “Global Enterprise Information Archiving Market: Growth, Future Prospects, and Competitive Analysis, 2019 – 2027. The global enterprise information archiving market is growing proficiently, projected to grow at a CAGR of 13.6% during the expected period from 2019 to 2027, starting from US$ 5.00 Bn in 2018.
The Enterprise Information Archiving (EIA) market refers to the industry that specializes in the storage, management, and retrieval of digital data and communications within large organizations. In today's digital age, businesses generate vast amounts of information, including emails, documents, instant messages, and other electronic records. Managing and preserving this data is critical for compliance, regulatory requirements, legal purposes, and overall operational efficiency.
EIA solutions are designed to address the complex and evolving needs of enterprises. They provide a centralized repository where organizations can systematically store, index, and manage their data. This includes features like email archiving, file archiving, and even social media content archiving. EIA solutions often incorporate advanced search and retrieval capabilities, ensuring that organizations can quickly access the information they need, when they need it.
The Enterprise Information Archiving market has experienced significant growth in recent years due to several factors. Firstly, the ever-increasing volume of digital data generated by businesses necessitates robust archiving solutions. Secondly, regulatory compliance requirements, such as GDPR in Europe or HIPAA in the healthcare industry, mandate the retention and accessibility of certain types of data, driving the adoption of EIA solutions. Additionally, the growing awareness of the value of data for analytics and business intelligence has led organizations to invest in archiving systems that not only store data securely but also make it available for analysis.
The Enterprise Information Archiving (EIA) market has been experiencing substantial growth worldwide, driven by several key factors. EIA solutions help organizations efficiently manage and store their digital information, which is critical for compliance, data governance, and knowledge management. Here are the major growth factors contributing to the expansion of the EIA market on a global scale:
Data Compliance and Regulatory Requirements: Evolving data privacy regulations, such as GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the United States, require organizations to retain and manage their data effectively. EIA solutions help organizations meet these compliance requirements by securely archiving and managing data.
Litigation and eDiscovery Needs: Legal requirements and the potential for litigation make it essential for organizations to retain and easily retrieve historical data. EIA systems assist in preserving data and providing quick access to it during legal proceedings, reducing legal risks and costs.
Data Security and Cybersecurity Concerns: Data breaches and cybersecurity threats are on the rise. EIA solutions provide secure storage and backup of critical data, reducing the risk of data loss due to cyberattacks or accidental deletions.
Business Continuity and Disaster Recovery: EIA solutions play a crucial role in disaster recovery and business continuity planning. They ensure that organizations can recover their data in case of system failures, natural disasters, or other emergencies.
Email Management: Email remains a primary communication tool for businesses. EIA solutions often include email archiving capabilities, helping organizations efficiently store, search, and retrieve emails, which is crucial for compliance and knowledge management.
Browse 247 pages report Enterprise Information Archiving Market By Type (Contents, Services), By Deployment Mode (Cloud, On-premises), By Enterprise Size (Small and Medium Enterprise, Large Enterprise), By End-user (Manufacturing, Government and Defence, Banking and Financial Services, Retail and Commerce, IT and Telecommunication, Others) – Growth, Share, Opportunities & Competitive Analysis, 2019 – 2027- https://www.credenceresearch.com/report/enterprise-information-archiving-market
List of Companies Covered:
Microsoft
Hpe
IBM
Dell
Google
Veritas
Barracuda
Proofpoint
Smarsh
Mimecast
ZL Technologies
Global Relay
Micro Focus
Opentext
Enterprise Information Archiving Market Partners and Acquisitions
The Enterprise Information Archiving Market has witnessed significant growth and evolution over the years, resulting in several key partnerships and acquisitions within the industry. In this dynamic market, it has become crucial for companies to collaborate with strategic partners to enhance their offerings and expand their reach. Prominent players in the enterprise information archiving sector have been actively engaging in mergers, acquisitions, and joint ventures to strengthen their position in a highly competitive landscape.
These collaborative efforts not only enable businesses to pool resources but also foster innovation and pave the way for new capabilities. By joining forces with complementary organizations, these market participants can leverage each other's expertise to develop advanced archiving solutions that cater to an ever-growing demand of enterprises seeking more efficient data management strategies. Moreover, such partnerships enable providers to tap into new markets or target specific industries where they may lack expertise on their own.
Why to Buy This Report-
The report provides a qualitative as well as quantitative analysis of the global Enterprise Information Archiving Market by segments, current trends, drivers, restraints, opportunities, challenges, and market dynamics with the historical period from 2016-2020, the base year- 2021, and the projection period 2022-2028.
The report includes information on the competitive landscape, such as how the market's top competitors operate at the global, regional, and country levels.
Major nations in each region with their import/export statistics
The global Enterprise Information Archiving Market report also includes the analysis of the market at a global, regional, and country-level along with key market trends, major players analysis, market growth strategies, and key application areas.
Browse Complete Report- https://www.credenceresearch.com/report/enterprise-information-archiving-market
Visit our Website- https://www.credenceresearch.com
Related Reports- https://www.credenceresearch.com/report/saudi-arabia-data-center-market
Browse Our Blog- https://hackmd.io/@vanshikashukla/enterprise-information-archiving-market
About Us -
Credence Research is a viable intelligence and market research platform that provides quantitative B2B research to more than 10,000 clients worldwide and is built on the Give principle. The company is a market research and consulting firm serving governments, non-legislative associations, non-profit organizations, and various organizations worldwide. We help our clients improve their execution in a lasting way and understand their most imperative objectives. For nearly a century, we’ve built a company well-prepared for this task.
Contact Us:
Office No 3 Second Floor, Abhilasha Bhawan, Pinto Park, Gwalior [M.P] 474005 India
0 notes
Text
Three Reasons You May Need Digital Forensics

This article discusses three vital reasons organizations may require digital forensics services. Firstly, it highlights the importance of digital forensics in uncovering fraudulent activities, especially those involving current or former employees who may attempt to conceal their actions. Digital forensics can provide crucial evidence to take appropriate action, such as legal proceedings or reporting to authorities. Secondly, the article emphasizes the accidental deletion of important data and how digital forensics can often recover such data, even when it appears to be permanently lost. Lastly, it points out the need for digital forensics expertise in cases where organizations must testify about their data preservation and authentication processes during eDiscovery. Having a certified forensic examiner can be critical in ensuring the credibility of the organization's data handling procedures in legal cases. In conclusion, the article underscores the importance of involving digital forensics experts early on in these scenarios to avoid potential setbacks and regrets later on.
Read more here: https://forensicdiscovery.expert/three-reasons-you-may-need-digital-forensics/
0 notes
Text
The Benefits Of Archiving Signal Messages

Having Signal archived conversations can be beneficial to your business in a number of ways. This app has evolved from a fringe messaging app to a now popular communication channel for mobile messaging. It promotes itself as the most secure and private on the market, and has gained a huge following among people who want to share text and voice messages that can’t be monitored by a third party.
One of the top reasons to archive Signal messages is that it can help with supporting court case and eDiscovery. As a business person, you dread the thought of being involved in a legal action of some sort, but it is something that can happen, so it is good to be prepared. You can be involved in court battle with customers, partners or suppliers as a plaintiff, as a defendant, or as an interested third-party. It would help if you have archived information such as text messages because it can help if you need to pursue a legal action or defend themselves in one.
Under the requirements of Federal Rules of Civil Procedure, companies have the obligation to search and produce electronic content, such as email, files and text messages. This obligation to produce this information might be based on an eDiscovery order from a court, and it can also happen when decision makers become aware of an impending litigation, thus requiring the organization to place a “litigation hold” on data that might be considered relevant for the duration of the potential legal action.
For instance, if there is a claim for breach of contract with a contractor, it could require the preservation of emails, text messages, and other content between employees and the contractor, or between employees talking about the contract or the contractor’s performance. When you have a reliable message archiving platform, you will be able to place a hold on data immediately when requested by court, regulator or on the advice of legal counsel, and you can also suspend deletion policies and practices, and retain the data for as long as needed.
For more information on the benefits of archiving Signal messages, visit our website at https://www.leap.expert/
0 notes
Text
#In-Place Legal Hold#In-place data preservation#eDiscovery Legal Holds#best practices for legal holds management
0 notes
Text
How storage tiering enables long term email data retention at 60% reduced costs

Why is long-term data retention such a big challenge?
Here are some global statistics about the humongous growth of email data:
In actual numbers,
an average user’s mailbox grows by 4GB every year, and
each business user sends and receives a total of 160 emails a day (as of 2022. Source: Earthweb)
This is BIG data and a big problem too for any long-term data retention strategy.
Managing this high Volume, Velocity, and Variety of emails is challenging for an organization.
How do you cope with this as email boxes grow to their maximum limits on MS 365, MS Exchange, Google Workspace, or other email solutions?
Traditional responses to growing/filling mailboxes can be unproductive
Traditional email preservation methods create fragmentation and make it challenging to locate information on-demand besides the management headaches and escalating costs.
Most cloud email services provide sufficiently large mailboxes suitable to start with but soon fill up.
To counteract this storage overflow, you may need to either purchase a higher plan with additional storage or clean up individual email stores – a task that can take away many productive hours.
Besides being Risky, Costly, and Clunky
Besides the loss of user productivity, there are other business impacts from email storage getting full:
Performance Degradation
Growing mailboxes may overload the email apps and slow down their performance.
Cost Implications
Mailboxes approaching their limits need more resources, either as expensive plan upgrades or the purchase of additional storage.
Data & Compliance Risks
To keep within quota limits, users typically download and delete data to create space in their mailboxes, increasing risks for the organization in maintaining a complete record of exchanging information over email.
Hard to Locate information
Unless the organization has subscribed to an Archival service, the lack of a centralized store makes it very challenging to locate old emails when required as a reference or evidence during an audit, investigation, or litigation.
Related: Why Archive email
Storage tiering is a scalable solution for long term email data retention

Step 1: Capture a copy of all new emails in Vaultastic
Configure journaling from your mail system to ensure a copy of every email sent/received is automatically captured in tamper-proof vaults on Vaultastic. Learn more about how to configure journaling.
Step 2: Migrate historical data from live mailboxes to Vaultastic.
Migrate old data from the users’ mailboxes to Vaultastic using the Legacyflo app. Learn more.
Step 3: Reduce Email Storage using a retention/truncation policy on the live mailbox
Now that a copy of all old and new emails is available in Vaultastic, you can now apply a retention policy on the live mailbox to keep it small. E.g., delete mail older than six months to restrict the growth of the live mailboxes.
Remember, it costs more to store the email data on live mailboxes than in an archival store like Vaultastic, which works hard to optimize storage costs across the entire data life cycle.
Step 4: Access on demand
The users (and supervisors) can now access recent emails via the live mailboxes and all older emails from the Vaultastic Ediscovery console, quickly locating specific pieces of information and documents buried anywhere in the email store. Learn more about the ediscovery app.
Step 5: Further optimize costs by moving infrequently used and aging data to the Open Store
Leverage one more level of storage tiering with Vaultastic’s two stores, viz. the active store for frequently used recent email that is search ready and the Open Store for infrequently used aging data.
You can configure the automatic movement of aging data from the active to the Open Store. Learn more.
[spacer height=”20px”]
Benefits of storage tiering go beyond long-term data retention
[spacer height=”7px”]
📷[spacer height=”7px”]Uniform Performance[spacer height=”7px”] With a consistently maintained lean live mailbox; your users will experience a consistent mail application performance.
📷 [spacer height=”7px”]Compliance Ready [spacer height=”7px”]A central store of email data enables you to respond to any data access request quickly and accurately.
📷 [spacer height=”7px”]Save 30-45% [spacer height=”7px”]By using tiered storage to maintain a lean live mailbox and leveraging powerful cost optimization strategies of Vaultastic; you optimize up to 60% costs.
📷[spacer height=”7px”]Peace of Mind[spacer height=”7px”] A central cloud repository of your email protected with a robust shared security model ensures that your data is safe, immutable and fully secured against any kind of threats.
Conclusion – storage tiering enables long-term email data retention at 60% reduced costs
Using the storage tiering strategy, you benefit from a lean live mailbox, which ensures a consistent mail system performance and prevents cost escalation on your mail solution regarding plan upgrades or additional storage.
In addition, the central, immutable repository, now created on Vaultastic, minimizes data-related risks and makes it easy to discover data of any period on-demand.
By including the storage tiering internal to Vaultastic with your strategy, you can further compress costs to achieve up to 60% cost optimization for long-term data retention of email.
0 notes
Text
SPOILATION — Original Digital Format

Production In Original Digital Format
When handling electronic documents in litigation matters, one crucial decision to make is how to produce the data.
The ILTA Litigation Practice Support Survey asked, “In what format do you most frequently produce?”
The results showed that 41% of respondents produced data using TIFF / Text files with metadata load files, 36% produced data in PDF or Native format with or without load files, and 22% produced Native files.
This article will proffer why Native production with or without load files is the most advantageous way to produce records.
Please note that in the spirit of reconciliation with indigenous communities in Canada, Native production will be referred to as production in its Original Digital Format (“ODF”) as guided by the Sedona Canada 2022 principles.
The landscape of eDiscovery evolves rapidly as new sources of evidence change the definition and boundaries of what constitutes a “document.”
Litigation support professionals manage a deluge of data from a variety of sources, including collaboration apps, social media, and mobile data, bringing challenges with embedded links, emoticons, and more.
Production of this new data, along with standard file types (emails and eDocuments), needs to be managed with efficiency, diligence, and planning.
Collaborating with counsel to develop a practical Electronically Stored Information (“ESI”) protocol and proactively discussing documentary disclosure will assist in avoiding rework and potential spoliation of evidence and ensure that evidence is produced in a practical, organized, and cost-effective manner.
Original Digital Format production involves exchanging documents in their original format.
While TIFF production is necessary for documents that require redactions or the management of confidential information, Original Digital Format production offers several advantages that can significantly benefit legal proceedings.
Below are five reasons why Original Digital Format production should be considered as the preferred approach in litigation matters:
1. Preserving Metadata
Metadata, including date stamps, author information, and document properties, can be critical in litigation cases.
Original Digital Format production maintains this vital data, ensuring its authenticity and reliability as evidence.
TIFF images are stripped of metadata, which then requires the re-creation of that metadata and its separate production.
Other document properties are simply lost in TIFF format.
2. Reduced Risk of Spoliation
Spoliation, the alteration, destruction, concealed and/or lost evidence, is a constant concern in litigation.
Original Digital Format files are less susceptible to allegations of spoliation, providing a higher level of document integrity.
Original Digital Format production preserves the original content and appearance of documents, providing the reviewer with an indication of what the file looked like in its original form.
This transparency can reduce disputes, as parties can see the unaltered documents, fostering trust in the legal process.
3. Cost Efficiency
Converting files to different formats can be time-consuming and expensive.
Original Digital Format production eliminates the need for conversion, resulting in cost savings and a streamlined process.
TIFF productions are a costly relic of paper-based records.
TIFF and PDF production increase the expense and reduce the practicality of the production.
4. Easier Review and Analysis
The review and analysis of Original Digital Format documents is simpler, faster, and more straightforward for legal professionals, expediting decision-making.
The more searchable metadata enables legal professionals to find relevant information and isolate critical documents more efficiently.
This is invaluable for early case assessment and document searches during the litigation process.
5. Compatibility and hosting
ODF production ensures compatibility with various platforms and software, reducing the likelihood of technical issues when accessing or presenting documents in a litigation setting.
TIFF productions are often much larger in volume and size, significantly increasing the costs for responding parties to ingest and host.
In summary, while ODF production offers numerous advantages, it is essential to consider the specific requirements and guidelines of your litigation matter.
Even though the document production stage may be months or years, the production format should be discussed and agreed upon during early litigation planning and included in the ESI protocol.
Consulting with legal professionals to determine the most suitable approach for your unique situation is crucial.
In most instances, ODF production should be the preferred choice, providing greater accuracy, transparency, and efficiency in the legal process.
When The Timing of Your Spoliation Motion Can Be As Important As Its Substance | JD Supra
A motion for an adverse inference was denied in Pratt v. Robbins, et al., 2024 WL 234730, Case No. 5:20-cv-170-GCM (W.D. N.C. Jan. 22, 2024) where Defendants failed to preserve or produce a video that might have contained pivotal evidence going to the heart Plaintiff’s civil rights claim for excessive force.
Background
In support of their motion for summary judgment, Defendants offered an Incident Report that referenced a video which they claimed demonstrated that “only the minimum amount of force was used in order to maintain control . . .” of Plaintiff but that “due to a camera malfunction” the actual use of force at issue against Plaintiff was not captured in the recording. Id.
Neither Plaintiff, who filed his claim pro se, nor his counsel, who appeared before dispositive motions were filed, had propounded any discovery on Defendants. Id.
In opposition to Defendants’ summary judgment motion, Plaintiff argued that Defendants spoliated evidence by failing to produce video footage potentially capturing the use of force that may have been recorded by cameras in the facility or in the handheld video footage taken by one of the Defendants. Id.
As a result, Plaintiff sought an adverse inference sanction against Defendants that the recordings would substantiate his excessive force claim, and refuted Defendants’ version of what had occurred. Id.
Courts Have Broad Discretion to Impose Spoliation Sanctions
Spoliation sanctions “should be designed to:
(1) deter parties from engaging in spoliation;
(2) place the risk of an erroneous judgment on the party who wrongfully created the risk; and
(3) restore the prejudiced party to the same position he or she would have been in absent … [the spoliation].” Id.
(internal quotations and citation omitted)
A party’s obligation to preserve ESI arises from Federal Rule of Civil Procedure 37 (e), which also provides the court the ability to impose sanctions for failing to preserve or for destroying ESI. Id.
Rule 37 (e)(2)
provides that the court only upon finding that the party acted with the intent to deprive another party of the information’s use in the litigation may:
(A) presume that the lost information was unfavorable to the party;
(B) instruct the jury that it may or must presume the information was unfavorable to the party; or
(C) dismiss the action or enter a default judgment.
Id. Plaintiff Failed to Meet His Burden of Proving The Elements of Rule 37 (e)
A party seeking spoliation sanctions bears the burden of proving all of the elements of Rule 37(e), and under Fourth Circuit precedent is generally required to do so by a “clear and convincing standard.”
Pratt, 2024 WL 234730, *2 (internal citation omitted).
Plaintiff failed to establish that Defendants intended to spoliate the missing video footage.
The particular Defendant who had, on occasion, used a handheld camera to record video in similar situations had only done so one or two times in his career and did not recall having done so on this particular occasion.
In addition, even though Defendants’ Incident Report acknowledged that “…the use of force that occurred on offender Pratt was not captured….” and Defendants’ review of the video that they did have supported their version of events, the missing footage was said to have been caused by a “camera malfunction.”
Further, Defendants did not have access to the video recordings or the ability to delete them; the cameras used to record video in the facility recorded to servers that were kept in a locked room.
Accordingly, Plaintiff was unable to show that any lost ESI was caused by Defendants’ “failure to take reasonable steps to preserve the ESI, or that the Plaintiff was prejudiced by the result of any such loss.” Id.
Conclusion
Even though Plaintiff failed to proffer any evidence that Defendants intended to spoliate ESI – ESI which could have potentially substantiated Plaintiff’s claim of excessive force – that failure was not what the Court focused on in its ruling.
Rather, it was Plaintiff’s decision to suddenly cry foul on the eve of trial, after also failing to propound any discovery on Defendants that did not go over well with the Court:
“he should have properly addressed such a failing during discovery, rather than attempt to style such a failing as ‘spoliation’ shortly before trial.” Id.
| U.S. Copyright OfficeAbout
§ 232.3
Bad-faith conduct.
(a) General.
The Board shall award costs and attorneys' fees as part of a determination where it is established that a participant engaged in bad-faith conduct, unless such an award would be inconsistent with the interests of justice.
(b) Allegations of bad-faith conduct —
(1) On the Board's initiative.
On its own, and prior to a final determination, the Board may order a participant to show cause why certain conduct does not constitute bad-faith conduct.
Within 14 days, the participant accused of bad-faith conduct shall file a response to this order, which shall follow the procedures set forth in § 220.5(a)(2).
(2) On a party's initiative.
A party that in good faith believes that a participant has engaged in bad-faith conduct may file a request for a conference with the Board describing the alleged bad-faith conduct and attaching any relevant exhibits.
Requests for a conference concerning allegations of bad-faith conduct and any responses thereto shall follow the procedures set forth in § 220.5(a)(2) of this subchapter.
(c) Establishing bad-faith conduct.
After the response of an accused participant has been filed under paragraph (b) of this section, or the time to file such a response has passed, the Board shall either make a determination that no bad-faith conduct occurred or schedule a conference concerning the allegations.
(d) Determining the award.
A determination as to any award of attorneys' fees and costs due to bad-faith conduct shall be made as part of the final determination.
In determining whether to award attorneys' fees and costs due to bad-faith conduct, and the amount of any such award, the Board shall consider the requests and responses submitted, any arguments on the issue, and the accused participant's behavior in other Board proceedings.
Such an award shall be limited to an amount of not more than $5,000, unless—
(1) The adversely affected party appeared pro se in the proceeding, in which case the award shall be limited to costs in an amount of not more than $2,500; or
(2) Extraordinary circumstances are present, such as a demonstrated pattern or practice of bad-faith conduct, in which case the Board may award costs and attorneys' fees in excess of the limitations in this section.
V. CLAIMANT RESPONDENT On March 4, 2024, this claim before the Copyright Claims Board (Board) alleging copyright infringement.
The claim attached a supplementary document that shows a screenshot of correspondence between Claimant and the respondent, (“Respondent” or “Redstone”), with Claimant offering to waive liability if Respondent agreed to participate in the proceeding.
The correspondence indicates that Claimant’s true intention is to pursue action against a third party (YouTube).
The strong implication of the correspondence is that Claimant is attempting to set up and win (without Respondent challenging her) a sham proceeding that she can then use in future litigation against YouTube.
On March 21, 2024, the Copyright Claims Board (Board) issued an Order to Show Cause in claim 24-CCB-
The Order to Show Cause ordered Claimant to file a response by April 4, 2024.
Because Claimant did not file a response by the deadline, the Board ordered her to appear at an April 18, 2024 conference to explain the conduct described in the Order to Show Cause (“Conference”).
37 C.F.R. § 232.3(c). Claimant appeared and was given an opportunity to explain her actions and answer questions related to her filing.
Claimants can only file a claim or take a position before the Board if they have a legitimate reason for doing so.
By submitting materials or advocating positions before the Board, a participant certifies that to the best of the participant's knowledge, information, and belief, formed after a reasonable inquiry under the circumstances, that it is not being presented for any improper purpose.
37 C.F.R. §§ 220.1(c); 232.2(a).
Claimant attached to her claim certain online correspondence she had with Respondent.
Claimant’s messages appear next to her name and a picture of her, and Respondent’s messages appear next to his name and, presumably, a picture of him.
In the correspondence submitted (it is unclear if what is submitted is partial or complete),
confirms that she is communicating with the person who twice “uploaded a recording of [her] song ] to YouTube.”
Respondent confirms that it was he and states that he was “sharing [his] love for the tune” and offered to remove it.
responded: Thank you for confirming.
What I would like to do is ask for you to participate in a legal claim at a small claims tribunal called the Copyright Claims Board.
I’ve already sent the DMCA takedown notices to YouTube.
Docket number: 24-CCB-
FINDING OF BAD FAITH
There is nothing wrong with that part of the communication.
However, message continues: If you agree to participate, I can offer you immunity. My real focus is YouTube, who has red flag knowledge of these uploads but allows them anyway.
It has destroyed my livelihood.
I’m sure you’re skeptical of my motivations, but with your confirmation above, I could file a claim without your cooperation, by process service to [redacted], your home.
Do I have that right?
language is clear.
It indicates that she was offering Respondent immunity from any liability to get an agreement from Respondent to participate in a fraudulent proceeding so that she could set up and receive a liability finding—one that she would not enforce—that she would use in future actions against a third-party.
In fact, by the communication’s words, set up a situation where the Board cannot decide this case in her favor now that it is aware of her immunity offer, unless there is evidence that Respondent rejected the offer and wants to participate on the merits;
and, to the contrary, Claimant testified that Respondent had not responded to her offer.
Conference 7:15-7:20.
Regardless, it appears that Claimant was trying to persuade Respondent to agree to a scheme that would use the Board’s time and resources to litigate a claim where no genuine legal dispute exists, and for an improper purpose.
At the Conference, offered what boils down to the following defense:
The Board should believe that her filing was not in bad faith because she was lying to .
testified that practically everything in her communication with Redstone was a lie.
She admitted that she was conducting a ruse, id. 9:29-9:55, and just trying to “seduce[]” and trick Redstone into giving her information that she could use against him and get him to move forward with the proceeding and not opt out.
Id. 7:05-715; 13:05-14:50; 19:35-20:27.
She even stated that she knew that she could not sue YouTube because of its immunity to show that she was willing to say whatever it took to get what she wanted from and was hoping he would not know it was false.
Id. 5:05-5:26; 14:22-14:50 (stating that she did not know if he would know she was lying but “it was like, you know, when you’re fishing, if you try to, if you jerk too fast, it goes off the hook”).
When asked about her offer for immunity, she stated that she never intended to follow through with her offer even if it were accepted by, although she might have attempted to amend her claim into a smaller-claims proceeding.
Id. 18:30-19:05.
While stated that she did not think her offer would be legally binding, id., her testimony was simply not credible.
Therefore, the Board finds that the actions of Claimant constitute bad-faith conduct as defined in the Board’s regulations:
“Bad-faith conduct occurs when a party pursues a claim, counterclaim, or defense for a harassing or other improper purpose, or without a reasonable basis in law or fact.
Such conduct includes any actions taken in support of a claim, counterclaim, or defense and may occur at any point during a proceeding before the Board, including before a proceeding becomes an active proceeding.”
37 C.F.R. § 220.1(c).
Under this standard, the Board has no difficulty in finding that Claimant pursued her claim for an improper purpose.
Even if testimony that she was lying to is truthful, that still amounts to conduct for a harassing or other improper purpose related to a CCB proceeding.
The opt-out provisions, making CCB proceedings voluntary for both sides, exist for an important reason.
Attempting to trick a potential respondent into CCB participation is clearly improper.
is further warned that a second finding of bad-faith conduct in the next twelve months could result in penalties, including a ban on filing new CCB proceedings for a one-year period and dismissal without prejudice of her existing CCB claims. 37 C.F.R. § 232.4. Copyright Claims Board
Right, wrong ways to prosecute Jan. 6 rioters
The people who breached the U.S. Capitol on Jan. 6, 2021, are being held accountable, and attempts to rebrand them as patriotic choirboys are a sign of the bizarre political times.
Yet is it unduly stretching the law to prosecute Jan. 6 rioters using the Sarbanes-Oxley Act of 2002?
The Supreme Court will consider this Tuesday in Fischer v. U.S., and rooting for the government to lose requires no sympathy for the MAGA mob.
Joseph Fischer says in his brief that he arrived late to the Capitol, spent four minutes inside, then "exited," after "the weight of the crowd" pushed him toward a police line, where he was pepper sprayed.
The feds tell an uglier tale.
Fischer was a local cop in Pennsylvania.
"Take democratic congress to the gallows," he wrote in a text message. "Can't vote if they can't breathe..lol."
The government says he "crashed into the police line" after charging it.
Fischer was indicted for several crimes, including assaulting a federal officer.
If true, perhaps he could benefit from quiet time in a prison library reading the 2020 court rulings dismantling the stolen election fantasy.
Sarbanes-Oxley, though?
Congress enacted Sarbox, as it's often called, in the wake of Enron and other corporate scandals.
One section makes it a crime to shred or hide documents "corruptly" with an intent to impair their use in a federal court case or a congressional investigation.
That provision is followed by catchall language punishing anybody who "otherwise obstructs, influences, or impedes" such a proceeding.
Now watch, as jurists with Ivy degrees argue about the meaning of the word "otherwise."
In Fischer's view, the point of this law is to prohibit "evidence spoliation," so the "otherwise" prong merely covers unmentioned examples.
The government's position is that the catchall can catch almost anything, "to ensure complete coverage of all forms of corrupt obstruction."
The feds won 2-1 at the D.C. Circuit Court of Appeals.
Yet two judges were worried how far this reading would permit prosecutors to go.

Judge Justin Walker, who joined the majority, said his vote depended on a tight rule for proving defendants acted "corruptly."
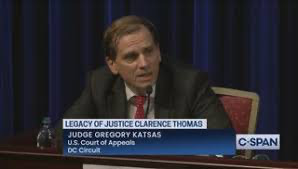
Judge Gregory Katsas filed the vigorous dissent.
The government "dubiously reads otherwise to mean 'in a manner different from,' rather than 'in a manner similar to,'" he argued. The obstruction statute "has been on the books for two decades and charged in thousands of cases — yet until the prosecutions arising from the January 6 riot, it was uniformly treated as an evidence-impairment crime."
A win for the feds, Judge Katsas warned, could "supercharge comparatively minor advocacy, lobbying, and protest offenses into 20-year felonies."
For example:
"A protestor who demonstrates outside a courthouse, hoping to affect jury deliberations, has influenced an official proceeding (or attempted to do so, which carries the same penalty)."
Or how about a Congressman (Rep. Jamaal Bowman) who pulls a fire alarm that impedes a House vote?
Special counsel Jack Smith has charged Donald Trump with obstructing a congressional proceeding, and he says Trump's "fraudulent electoral certifications" in 2020 are covered by Sarbox, regardless of what the Supreme Court does in Fischer.
The other piece of context is that prosecutors going after Jan. 6 rioters have charged obstruction in hundreds of cases.
But if those counts are in jeopardy, don't blame the Supreme Court.
Presumably many of those defendants could be on the hook for disorderly conduct or other crimes, and the feds can throw the book at them.
What prosecutors can't do is rewrite the law to create crimes Congress didn't.
Court Denies Railway Company’s Renewed Motion for Spoliation; Agrees to Bifurcate Trial
Court: United States District Court for the District of Montana, Great Falls Division
In connection to defendant Burlington Northern Santa Fe Railway Company’s ongoing litigation in Libby, Montana (covered extensively by the Asbestos Case Tracker, including most recently HERE), the estate of decedent Mary Diana Moe brought an action against BNSF for wrongful death allegedly resulting from decedent’s exposure to asbestos resulting from BNSF’s activities in Libby.
BNSF previously moved for spoliation sanctions stemming from plaintiff’s failure to preserve decedent’s remains after her death.
The court denied BNSF’s motion after concluding that BNSF failed to meet its burden to show good cause for an autopsy to obtain additional tissue samples.
However, in reaching its decision the court noted that “had good cause been shown to warrant the tissue samples, sanctions could have been appropriate in this case.”
Here, BNSF first brought a renewed motion for spoliation sanctions, arguing that good cause existed to obtain tissue samples from decedent’s lungs for a tissue digestion analysis, which was “the only medically reasonable method” for understanding
(1) if her mesothelioma was caused by asbestos exposure and
(2) if it was caused by asbestos exposure, which type(s) of asbestos fibers caused her diagnosis.
In support of its renewed motion, BNSF offered the declaration of Dr. Mark Wick, an expert pathologist, who stated the cremation of decedent precluded the evaluation needed to establish the cause of her mesothelioma.
Plaintiff, on the other hand, argued that BNSF’s renewed motion was improper under the Federal Rules of Civil Procedure and local rules, and the motion still failed to meet the good cause standard.
Ultimately, the court determined that BNSF’s renewed motion for sanctions was procedurally improper, as BNSF was required to seek leave to file a motion for reconsideration, and that its motion failed to present a valid basis for reconsideration because it did not identify any new facts or applicable law that arose after the entry of the court’s original order.
BNSF also failed to explain why the information now provided in its renewed motion could not have been provided in support of its original motion.
For these reasons, the court denied BNSF’s renewed motion for spoliation sanctions.
However, the court noted that its denial of BNSF’s request to give an adverse jury instruction does not prohibit argument or evidence regarding the basis for decedent’s diagnosis and whether the diagnosis was “definitive.”
Next, BNSF moved to bifurcate the trial into two separate proceedings: the first stage relating to BNSF’s liability for negligence and any amount of compensatory damages, and the second stage relating to liability for punitive damages.
BNSF argued that bifurcation was necessary to avoid unnecessary prejudice against BNSF.
In response, plaintiff conceded that limited bifurcation would be appropriate; however, Plaintiff moved for an alternative approach: the jury could decide liability for both negligence and punitive damages, as well as compensatory damages, in the first stage, and in the second stage the jury would determine what amount of punitive damages, if any, was appropriate.
Plaintiff argued that this approach was consistent with customary practices, was appropriate given the nature of the claims against BNSF, and sufficiently avoids undue prejudice against BNSF.
The court ultimately agreed with plaintiff’s proposed model of bifurcation, finding that the evidence pertaining to BNSF’s liability for negligence would overlap substantially with the evidence pertaining to BNSF’s liability for punitive damages.
The court further noted that any evidence that does arise at trial, if any, that proved irrelevant to plaintiff’s negligence claim could be addressed by the court pursuant to any objections to its introduction.
Accordingly, the court granted BNSF’s motion in part and denied it in part, determining that the trial would be bifurcated in the manner suggested by plaintiff.
The Duty To Preserve and Navigating the Intricacies of Privilege, Waiver of Privilege and the Use of FRE 50…
The duty to preserve evidence and the significant events that determine when the duty to preserve arises is often intertwined with privileged discussions and documents related to the planning and implementation of a litigation hold.
And when there is a dispute about when the duty to preserve was triggered and there are allegations of spoliation, concerns regarding protecting privilege and not waiving privilege become critically important.
Federal Rule of Evidence 502(d) is a powerful tool available to litigants trying to protect against waiver of privilege as a court “may order that the [attorney-client] privilege or [attorney work product] protection is not waived by disclosure connected with the litigation pending before the court ….”
Fed. R. Evid. 502(d); see also Whitaker Chalk Swindle & Sawyer, LLP v. Dart Oil & Gas Corp., No. 4:08-cv-684, 2009 WL 464989, at *4 (N.D. Tex. Feb. 23, 2009) (rejecting argument that “Rule 502 is limited to inadvertent disclosures”).
Lubrizol Corp. v. IBM: A Cautionary Tale
A recent federal court decision provides a cautionary tale to litigants dealing with the complexities of preservation, privilege and the use of a Rule 502(d) order.
In Lubrizol Corp. v. IBM, 2024 WL 941686 (N.D. Ohio Feb. 8, 2024), the court addressed whether a Rule 502(d) order sought by IBM in the face of spoliation allegations can apply to protect the intentional disclosure of certain documents regarding its preservation and litigation hold efforts without waiving the privilege over any related areas, as well as whether IBM waived privilege with respect to its preservation efforts in disputing Lubrizol’s spoliation claim by asserting that IBM did not reasonably anticipate litigation before the filing of the complaint.
The Discovery Dispute Regarding IBM’s Preservation Efforts
Lubrizol filed its complaint in April 2021 alleging that IBM breached a contract between the parties and also accused IBM of fraud and various torts in connection with a project to implement a new enterprise resource planning software.
Lubrizol, 2024 WL 941686 at *1.
Lubrizol amended its complaint months later in December 2021 to add a claim that IBM committed the tort of spoliation when it deleted the ESI of several IBM personnel who worked on the project. Id.
In particular, Lubrizol claimed that between July 2019 and October 2021, IBM deleted the email boxes of several IBM personnel who played key roles on the project.
Lubrizol also alleged that IBM failed to issue a litigation hold until May 2021, after Lubrizol filed its complaint. Id.
IBM did not dispute that the deletions occurred.
IBM’s stance was that the deletions were the result of IBM’s routine document retention protocol and that its duty to preserve was not triggered until the filing of the complaint.
Lubrizol claimed that there were a series of events that put IBM on notice that litigation was anticipated well before the complaint was filed. Id.
Lubrizol filed a letter motion asking the court to compel IBM to respond to certain interrogatories and document requests regarding IBM’s preservation efforts.
Id. at *2.
IBM filed its own letter motion requesting that the court enter a Rule 502(d) order that would permit IBM to produce some privileged preservation-related materials without waiving the attorney-client privilege over other, unproduced materials on the same subject matter. Id. at *2.
The Court Denied IBM’s Request for a Rule 502(d) Order
The court first addressed IBM’s request for a Rule 502(d) order that would allow IBM to produce certain documents and information regarding its preservation efforts and litigation holds without waiving the privilege over any other related materials and without exposing itself to the risk of subject matter waiver. Id.
The court explained that “Rule 502 was enacted to achieve two main goals: (1) resolving disagreement among courts regarding the effect of certain disclosures of privileged information; and
(2) preventing litigation costs from spiraling due to fears that any disclosure of a privileged document would result in subject-matter waiver of all other communications on the same topic.” Id.
The court initially made clear that even though the parties disagreed regarding the propriety and scope of the proposed 502(d) order, the court found that
“it is well-settled that a court may enter a Rule 502(d) order on its own initiative and without the consent of both parties.” Id. at *3.
Lubrizol, however, also argued that the court lacked authority to enter a Rule 502(d) order that would permit IBM to intentionally, rather than inadvertently, disclose privileged information without constituting a subject matter waiver of all other documents and communications on the same topic. Id.
According to the Sedona Conference, “[a] Rule 502(d) order may address not only inadvertent waiver, but also instances in which intentional disclosure will not result in waiver.”
The Sedona Conference Commentary on Protection of Privileged ESI, 17 Sedona Conf. J. 95, 130 (2015).
However, the court cited to a few cases where other courts have reached the opposition conclusion. Lubrizol, 2024 WL 941686 at *3 (citing Smith v. Best Buy Stores, L.P., No. 4:16-cv-00296-BLW, 2017 WL 3484158, at *3 (D. Idaho Aug. 14, 2017)
(“The Court also has serious reservations about the enforceability of a clawback order extending to intentional disclosures.”).
Ultimately, the Court determined that it lacked the authority to grant such a Rule 502(d) order for intentional disclosures because the court was primarily concerned about the possibility that IBM���s proposed Rule 502(d) order “would enable it to disclose documents that support its spoliation position while continuing to withhold, other, less favorable documents.”
Lubrizol, 2024 WL 941686 at *3.
The court also pointed out that other courts shared this same concern and did not enter a Rule 502(d) for intentional disclosures. Id. (citing Thomas v. Marshall Public Schools, No. 21-cv-2581 (PJS/DJF)), — F. Supp. 3d —, 2023 WL 5743611, at *12 (D. Minn. Sept. 6, 2023)
(“While Rule 502(d) allows a party who discloses privileged material to claw them back without having to prove the disclosure was ‘inadvertent,’ it does not sanction the tactical, selective disclosure of some privileged materials for use in litigation while withholding others on the same subject.”).
The Court Found That IBM Waived Privilege With Respect to Its Preservation Efforts
After granting Lubrizol’s motion to compel IBM’s responses to certain interrogatories and document requests regarding IBM’s preservation efforts, the court next turned its attention to Lubrizol’s argument that IBM had waived the attorney-client privilege and work product doctrine under both the “at issue” waiver and crime-fraud doctrine. Lubrizol, 2024 WL 941686 at *5-7.
The court focused on the “at issue” waiver under Ohio law and concluded that IBM waived privilege and that applying the privilege would deny Lubrizol access to information that is vital to its spoliation claim which is unavailable from any other source. Id. at *9-11.
The court reasoned that IBM made relevant the advice that it received from counsel regarding its document preservation efforts and whether litigation was reasonably likely prior to the filing of Lubrizol’s complaint in April 2021 by sending a letter to Lubrizol in October 2021 defending against Lubrizol’s spoliation allegations and claiming it did not reasonably anticipate litigation at the time the documents were deleted. Id. at *9-10.
According to the court, “[i]f counsel was telling IBM before April 2021 that litigation was reasonably likely, that is certainly relevant to Lubrizol’s claim.
Similarly, if IBM’s counsel identified the disputed employees as potentially relevant custodians before their email boxes were deleted, that would impact IBM’s state of mind and the strength of Lubrizol’s spoliation claim.” Id. at *10.
As such, the court found that “IBM waived privilege with respect to:
(1) IBM’s document preservation efforts;
(2) whether IBM reasonably anticipated litigation at the time of the alleged spoliation;
and (3) when IBM identified the disputed custodians as individuals who might possess information relevant to the case” and ordered IBM to produce all responsive documents. Id. at *11.
Finally, the court rejected IBM’s argument that applying the at-issue waiver to these circumstances would create an “incredibly slippery slope” because it would allow the other side to see IBM’s attorneys’ assessment of the merits of the dispute.
To address this concern, the court allowed IBM to redact privileged information that dealt with other topics. Id. at *10.
Key Takeaways:
The Scope of a FRE 502(d) Order:
This case focused on the scope of a Rule 502(d) order as an attempt to be used as a blanket protection for intentional disclosures of privileged information as opposed to just inadvertent disclosures and finding that the circumstances did not warrant the protection of the selective and intentional disclosures proposed by IBM.
A Rule 502(d) Order Is a Very Powerful Tool:
Although the court in the Lubrizol case did not enter the requested Rule 502(d) order proposed by IBM, litigants need to remember that a Rule 502(d) order should be used at the outset of a case as it can protect litigants against privilege waiver without having to prove that they have taken reasonable steps to prevent an inadvertent production of privileged documents.

As Judge Andrew Peck (ret.) has repeatedly told legal practitioners, a Rule 502(d) order can be viewed as a “get-out-of-jail-free card” and “it is akin to malpractice not to get a Rule 502(d) order.”
Commentary on the Effective Use of Federal Rule of Evidence 502(d) Orders, 23 Sedona Conf. J. at 17 n.23.
Leveraging Discovery To Uncover When an Opposing Party Anticipated the Potential for Litigation:
This case provides a potential roadmap to challenge an opposing party’s preservation efforts through the use of discovery where spoliation is at issue and the opposing party is attempting to use privilege selectivity as a sword and shield. Risk of Privilege Waiver:
The Lubrizol case highlights the real risk of privilege waiver for companies dealing with the complexities of when litigation is reasonably anticipated to trigger the duty to preserve and the potential legal pitfalls that can arise when documents have been deleted and responding to opposing counsel to defend against spoliations claims.
Early Assessment of the Duty To Preserve Is Critical:
This case serves as an important reminder that companies need to take seriously its duty to preserve obligations and confer with counsel early regarding whether litigation is reasonably anticipated, implement a reasonable preservation strategy, and discuss the potential downsides that can arise when the anticipation of litigation and preservation obligations are not managed carefully.
From: Colin R Hatcher Sent: Friday, March 01, 2019 1:36 PM
Subject: Kusner v. Nath (APPEALED) 173612891-001:
Mr. Kusner good afternoon. I am sending you a copy of our proposed exhibits for trial next week. The Judge expects us to confer on exhibits pre trial to see what can be agreed on. Please let me know if you are agreeable to the exhibits I sent you being admitted into evidence before the trial starts – this makes the trial go smoother. In like manner, please send me a copy of all exhibits you intend to use at trial, and I will do the same. Regards Colin Hatcher
Colin R. Hatcher LAW OFFICE OF TIFFANY A. LIBER Salaried Employees of Progressive Casualty Insurance Company Not a Partnership, Not a Corporation Preston Plaza - 17950 Preston Rd., Suite 410
FTC effort to obtain litigation holds in Amazon case sparks privilege battle
Dive Brief:
The Federal Trade Commission last week said Amazon must hand over its litigation holds and ephemeral messaging instructions so it can see how much of the company’s internal communication about the agency’s antitrust case against it has been lost to spoliation and whether that spoliation was deliberate.
“Plaintiffs need these documents to assess whether Amazon failed to take reasonable steps to preserve documents and to map out what information has been destroyed,” the agency says in an April 25 filing with a federal district court in Washington.
Last year, the agency and 17 state attorneys general sued the company, accusing it of wielding monopoly power to keep prices high while lowering service quality.
Amazon is seeking to get the case dismissed.
Dive Insight:
The spoliation issue is crucial because executives talked among themselves about the company’s potentially anticompetitive business practices using the messaging app Signal, which has an auto-delete setting, the FTC says.
“Executives turned on Signal’s ‘disappearing message’ feature, which irrevocably destroys messages, even after Amazon was on notice that Plaintiffs were investigating its conduct,” says the agency, headed by Lina Khan.
Khan has made the fight with Amazon a key test of the agency’s antitrust enforcement posture.
It took the company 15 months after it learned of the investigation – and 10 months after it was sent its first preservation letters – to issue notices to employees about preserving their communications.
“It is highly likely that relevant information has been destroyed as a result of Amazon’s actions and inactions,” the agency says.
Company founder and then-CEO Jeff Bezos was “a heavy Signal user” and he wasn't sent a notice to preserve his communications for almost a year after the company was sent its first preservation letters, the agency says.
“Mr. Bezos’ documents and communications were clearly within the scope of the investigation,” the FTC says. “As Amazon’s founder and CEO, he was the ultimate decision-maker.”
In its filing, the FTC suggests the company wasn’t forthright in its response to the preservation letters.
“Amazon claims that it did not learn about its employees’ use of Signal until the summer of 2020, even though Amazon’s top executives, including its General Counsel [David] Zapolsky, had been using Signal since 2019,” the agency says.
Almost three years after Amazon received its first preservation letters, employees were told to switch to an internally created app, Wickr, that enables messages to be saved centrally for individuals on legal hold. But the ephemeral conversations didn’t stop.
“Amazon executives continued to use Signal’s disappearing message feature to destroy records of their internal communications,” the agency says.
In the filing, the agency is asking for all of the company’s litigation holds and preservation notices as well as the instructions it sent to employees about use of the ephemeral messaging apps during the investigation.
The company has pushed back against previous attempts by the agency to get its litigation holds and messaging instructions, saying they’re privileged, but the FTC says it only needs to make a preliminary showing that spoliation has occurred to overcome the privilege defense.
“A preliminary showing of spoliation means only that ‘there is reason for concern that evidence has been lost,’” the FTC says. “Such ‘reason for concern’ can be shown where potentially relevant evidence has been destroyed or where a party failed to take adequate steps to preserve information.”
In a statement, Amazon says the FTC is asking for too much. "The FTC has a complete picture of Amazon’s decision-making in this case,” says Tim Doyle, a company spokesperson.
Doyle says the company has provided some 1.7 million documents, including those involving conversations that were held on messaging apps. In all, the company has provided more than “100 terabytes of data.”
If the court finds the spoliation was deliberate, it can impose severe sanctions on the company.
youtube
Trevino v. Ortega
ENOCH, Justice, delivered the opinion of the Court, in which PHILLIPS, Chief Justice, and GONZALEZ, HECHT, SPECTOR, OWEN, ABBOTT and HANKINSON, Justices, join.

The issue in this case is whether this Court should recognize an independent cause of action for intentional or negligent spoliation of evidence by parties to litigation. 1
The court of appeals held that Texas recognizes a cause of action for evidence spoliation.
938 S.W.2d 219, 223.
Because we determine that spoliation does not give rise to independent damages, and because it is better remedied within the lawsuit affected by spoliation, we decline to recognize spoliation as a tort cause of action.
Therefore, we reverse the court of appeals' judgment and render judgment that Ortega take nothing.
In 1988, Genaro Ortega, individually and as next friend of his daughter, Linda Ortega, sued Drs. Michael Aleman and Jorge Trevio and McAllen Maternity Clinic for medical malpractice.
Ortega alleged that the defendants were negligent in providing care and treatment during Linda's birth in 1974. 2
Discovering that Linda's medical records from the birth had been destroyed, Ortega then sued Dr. Trevio in a separate suit for intentionally, recklessly, or negligently destroying Linda Ortega's medical records from the birth.
It is the appeal from this latter action that is before us.
Here, Ortega claims that Trevio had a duty to preserve Linda's medical records and that destroying the records materially interferes with Ortega's ability to prepare his medical malpractice suit.
Ortega explains that Aleman, the attending physician, testified that he has no specific recollection of the delivery and, therefore, the missing medical records are the only way to determine the procedures used to deliver Linda.
Because the medical records are missing, Ortega's expert cannot render an opinion about Aleman's, the Clinic's, or Trevio's negligence.
Responding to Ortega's spoliation suit, Trevio specially excepted and asserted that Ortega failed to state a cause of action.
The trial court sustained Trevio's special exception and gave Ortega an opportunity to amend.
But Ortega declined to amend and the trial court dismissed the case.
Ortega appealed.
The court of appeals reversed the trial court's dismissal order and held that Texas recognizes an independent cause of action for evidence spoliation. 938 S.W.2d at 223.
This Court treads cautiously when deciding whether to recognize a new tort.
See generally Kramer v. Lewisville Mem'l Hosp., 858 S.W.2d 397, 404-06 (Tex.1993); Graff v Beard, 858 S.W.2d 918, 920 (Tex.1993); Boyles v. Kerr, 855 S.W.2d 593, 600 (Tex.1993).
While the law must adjust to meet society's changing needs, we must balance that adjustment against boundless claims in an already crowded judicial system.
We are especially averse to creating a tort that would only lead to duplicative litigation, encouraging inefficient relitigation of issues better handled within the context of the core cause of action.
We thus decline to recognize evidence spoliation as an independent tort.
A number of jurisdictions that have considered the issue have been hesitant to recognize an independent tort for evidence spoliation for a variety of different reasons.
See, e.g., Wilson v. Beloit Corp., 921 F.2d 765, 767 (8th Cir.1990) (no spoliation tort under Arkansas law); Edwards v. Louisville Ladder Co., 796 F.Supp. 966, 970 (W.D.La.1992) (existence of adequate remedies); Christian v. Kenneth Chandler Constr. Co., 658 So.2d 408, 412-13 (Ala.1995) (no cause of action under facts of case but noting previous cases allowing jury instruction on the spoliation presumption); La Raia v. Superior Court, 150 Ariz. 118, 722 P.2d 286, 289 (1986) (existence of adequate remedies); Gardner v. Blackston, 185 Ga.App. 754, 365 S.E.2d 545, 546 (1988) (no spoliation tort under Georgia law); Boyd v. Travelers Ins. Co., 166 Ill.2d 188, 209 Ill.Dec. 727, 652 N.E.2d 267, 270 (1995) (traditional negligence remedies sufficiently address the issue and remove the need to create an independent cause of action); Murphy v. Target Prods., 580 N.E.2d 687, 690 (Ind.Ct.App.1991) (no common-law duty for employer to preserve potential evidence for employee's benefit); Monsanto Co. v. Reed, 950 S.W.2d 811, 815 (Ky.1997) (existence of adequate remedies); Miller v. Montgomery County, 64 Md.App. 202, 494 A.2d 761, 767-68 (1985) (existence of adequate remedies); Panich v. Iron Wood Prods. Corp., 179 Mich.App. 136, 445 N.W.2d 795, 797 (1989) (no cause of action under facts of case); Brown v. Hamid, 856 S.W.2d 51, 56-57 (Mo.1993) (existence of adequate remedies and not appropriate on facts of case). 3
Evidence spoliation is not a new concept.
For years courts have struggled with the problem and devised possible solutions.

Probably the earliest and most enduring solution was the spoliation inference or omnia praesumuntur contra spoliatorem: all things are presumed against a wrongdoer.
See, e.g. Rex v. Arundel, 1 Hob. 109, 80 Eng. Rep. 258 (K.B.1617) (applying the spoliation inference); The Pizarro, 15 U.S. (2 Wheat.) 227, 4 L.Ed. 226 (1817) (declining to apply the spoliation inference); Brown, 856 S.W.2d at 56 (noting that Missouri has recognized a spoliation inference for over a century).
In other words, within the context of the original lawsuit, the factfinder deduces guilt from the destruction of presumably incriminating evidence.
This traditional response to the problem of evidence spoliation properly frames the alleged wrong as an evidentiary concept, not a separate cause of action.
Spoliation causes no injury independent from the cause of action in which it arises.
If, in the ordinary course of affairs, an individual destroys his or her own papers or objects, there is no independent injury to third parties.
The destruction only becomes relevant when someone believes that those destroyed items are instrumental to his or her success in a lawsuit.
Even those courts that have recognized an evidence spoliation tort note that damages are speculative.
See, e.g., Smith v. Superior Court, 151 Cal.App.3d 491, 198 Cal.Rptr. 829, 835 (1984); Petrik v. Monarch Printing Corp., 150 Ill.App.3d 248, 103 Ill.Dec. 774, 501 N.E.2d 1312, 1320 (1986).
The reason that the damages inquiry is difficult is because evidence spoliation tips the balance in a lawsuit;
it does not create damages amenable to monetary compensation.
Our refusal to recognize spoliation as an independent tort is buttressed by an analogous line of cases refusing to recognize a separate cause of action for perjury or embracery. 4
Like evidence spoliation, civil perjury and civil embracery involve improper conduct by a party or a witness within the context of an underlying lawsuit.
A number of courts considering the issue have refused to allow the wronged party to bring a separate cause of action for either perjury or embracery.
See, e.g., Cooper v. Parker-Hughey, 894 P.2d 1096, 1100 n. 3 (Okla.1995) (listing a number of jurisdictions that refuse to recognize a separate civil cause of action for perjury); OMI Holdings, Inc. v. Howell, 260 Kan. 305, 918 P.2d 1274, 1296 (1996) (embracery); Trudell v. Heilman, 158 Cal.App.3d 251, 204 Cal.Rptr. 551, 553 (1984) (embracery disallowed unless plaintiff has no other means of redress); Hoston v. Silbert, 514 F.Supp. 1239, 1241 (D.D.C.1981) (embracery), rev'd on other grounds, 681 F.2d 876 (D.C.Cir.1982).
These decisions rely on public policy concerns such as ensuring the finality of judgments, avoiding duplicative litigation, and recognizing the difficulty in calculating damages.
Kessler v. Townsley, 132 Fla. 744, 182 So. 232, 232 (1938) (res judicata); OMI, 918 P.2d at 1290, 1293 (duplicative litigation and speculative damages).
Similarly, recognizing a cause of action for evidence spoliation would create an impermissible layering of liability and would allow a plaintiff to collaterally attack an unfavorable judgment with a different factfinder at a later time, in direct opposition to the sound policy of ensuring the finality of judgments.
We share Ortega's concern that, when spoliation occurs, there must be adequate measures to ensure that it does not improperly impair a litigant's rights, but we disagree that the creation of an independent tort is warranted.
It is simpler, more practical, and more logical to rectify any improper conduct within the context of the lawsuit in which it is relevant.
Indeed, evolving remedies, sanctions and procedures for evidence spoliation are available under Texas jurisprudence.
Trial judges have broad discretion to take measures ranging from a jury instruction on the spoliation presumption to, in the most egregious case, death penalty sanctions.
See, e.g., Watson v. Brazos Elec. Power Coop., Inc., 918 S.W.2d 639, 643 (Tex.App.--Waco 1996, writ denied) (holding that trial court erred when it failed to give a spoliation instruction); Ramirez v. Otis Elevator Co., 837 S.W.2d 405, 412 (Tex.App.--Dallas 1992, writ denied) (noting that a trial court possesses wide discretion in awarding discovery sanctions); see also TEX.R. CIV. P. 215(b).
As with any discovery abuse or evidentiary issue, there is no one remedy that is appropriate for every incidence of spoliation; the trial court must respond appropriately based upon the particular facts of each individual case.
Ortega also argues that the failure to maintain Linda's medical records violated a statutory duty to…
Trevino v. Ortega Case Brief for Law School · LSData
This legal case discusses the absence of a separate cause of action for evidence spoliation in Texas, but existing remedies available within litigation.
However, Texas courts have been hesitant to apply these remedies, which can be problematic for litigants faced with evidence destruction.
The duty to preserve evidence arises when a party is aware of potential litigation, which is reasonably foreseeable.
Sanctions are appropriate when a party knew or should have known that destroyed evidence was relevant to pending, imminent, or reasonably foreseeable litigation.
Remedies for evidence destruction are granted only when the destruction has prejudiced the non-destroying party's ability to present its case or defense.
Trial courts have broad power to sanction parties for evidence destruction, including the authority to sanction parties for abusing the discovery process.
Once a court determines that evidence has been improperly destroyed and that the non-destroying party was prejudiced by the destruction, the court must decide on an appropriate sanction.
The court has broad discretion in choosing the sanction, and there are various options available, including dismissal or default judgment against the destroyer and exclusion of evidence or testimony.
‘Failed to preserve critical evidence’:
Trump motion could shake up Mar-a-Lago case after Jack Smith admits his office misled court about location of documents in seized boxes

Left: Jack Smith speaks about an indictment of former President Donald Trump, Aug. 1, 2023, at a Department of Justice office in Washington (AP Photo/Jacquelyn Martin, File); Right: Donald Trump speaks to members of the media before departing Manhattan criminal court, Monday, May 6, 2024, in New York. (AP Photo/Julia Nikhinson, Pool)
Former President Donald Trump alleges special counsel Jack Smith and other prosecutors admittedly “failed to maintain the integrity of the contents of certain boxes obtained at Mar-a-Lago” in a Monday filing asking the court to cancel a set of looming deadlines.
Late last week, Trump’s personal valet, Waltine “Walt” Nauta, requested extra time to file two sets of documents related to classified materials and expert testimony.
The basis for those requests was the government’s alleged failure to provide an “accurate” index that cross-referenced the contents of the boxes.
In response, the prosecution characterized those claims as bogus and essentially made up.
But there were some key admissions.
“[T]here are some boxes where the order of items within that box is not the same as in the associated scans,” Smith admitted in the body of the motion before adding in a footnote: “The Government acknowledges that this is inconsistent with what Government counsel previously understood and represented to the court.”
During a hearing on April 12, a member of the special counsel’s team responded to a question from Cannon as to whether the boxes were “in their original, intact form as seized” by stating “they are, with one exception; and that is that the classified documents have been removed and placeholders have been put in the documents.”

Defense attorneys seized on that language and, in a motion seeking leave to file a sur-reply — a reply to a motion that can only be filed with court approval since all briefs on an issue have been filed — framed the disclosure as “discovery violations, misrepresentations to the Court and potential spoliation resulting from the mishandling of boxes.”
Included with the motion, was a copy of the proposed defense response to the government’s latest admission in the case — which alleges Smith “attempted to bury” the concession “in a footnote.”
“President Trump and counsel are deeply troubled to be learning of these facts approximately 11 months after the charges were filed in this case,” the would-be filing reads.
“The May 3, 2024, disclosures by the Special Counsel’s Office raise questions about the investigation and the handling of evidence that must be addressed before the matter proceeds.”
The government’s admitted inability to maintain the order of the documents in the boxes, coupled with a prior in-court claim to the contrary, has provided Trump with ample legal angles to attack.
From the filing, at length:
Regarding the so-called “cover sheets” that the prosecution team used as replacements for allegedly classified documents in the boxes, the Special Counsel’s Office wrote that the FBI “generally” had “replaced the handwritten sheets with classified cover sheets annotated with the index code.”
But the Office did not explain why they could not offer a precise, categorical representation about the process that was used instead of a “general” one.
The Office also admitted that in “many but not all instances, the FBI was able to determine which document with classification markings corresponded to a particular placeholder sheet.”
This further suggests that even if the scans are the “best evidence available,” they are not a reliable record of the boxes’ contents.
The “not all” caveat is, however, consistent with the recent and inexplicable disclosure that the “filter team” was “not focused” on the order of documents in the boxes that are at the heart of this case.
The defense says those issues implicate Trump’s motions to suppress evidence and to dismiss based on prosecutorial misconduct.
Additionally, the admission means the former president is likely to file a motion to further compel similar disclosures — unless Smith makes such disclosures voluntarily.
On top of that, Trump’s defense previewed, there will likely be “additional motions for sanctions based on spoliation, including a motion to dismiss the charges if the Office cannot prove in a reliable way how it seized and handled the key evidence in the case, which will be a central issue at any trial.”
For several months now, the government, the defendants and the court have been arguing over the extent to which each side will need access to, can access, and ultimately view discovery information, which is subject to the Classified Information Procedures Act or CIPA.
The heart of the matter concerns what classified information defense counsel can actually use and disclose during trial — all of which is subject to a mandatory notice requirement under CIPA Section 5.

In early April, U.S. District Judge Aileen Cannon set a May 9 deadline for those disclosures — also instructing the defendants to disclose potential expert witnesses they intend to call during the trial and the subject matter of their potential expertise.
Nauta asked for an indefinite stay of those deadlines over the alleged discovery violations but Trump’s attorneys suggest the fallout could be even greater.
��For example, if the case proceeds to trial or evidentiary hearings, President Trump will now seek to use classified information to cross-examine witnesses regarding appropriate procedures for handling classified information in connection with briefings and evidence in connection with investigations,” the defense filing reads. “Defense counsel will also need to re-review the classified discovery, among other things, to consider new defenses and potential expert notice based on these disclosures, such as defenses and experts that focus on the chain-of-custody and search-execution deficiencies.”
To hear lead Trump attorney Todd Blanche tell it, the “failure to maintain the integrity of the evidence in the boxes” implicates every single box seized from Mar-a-Lago and directly contradicts the government’s “full-throated but now concededly false assertions of compliance with their discovery obligations.”
Perhaps anticipating some criticism, the defense says they could not have known about the issue until the prosecution’s admission.
“During the review of discovery and preparation of pretrial motions, President Trump’s counsel had relied on the scans and believed that the location of allegedly classified documents within the boxes was exculpatory,” the filing goes on. “Indeed, it was our understanding that most, and potentially all, of the charged documents were buried within the boxes and located next to other items that provided favorable context regarding, inter alia, when the document was placed in a box. It never occurred to us, until last Friday, that the prosecution team could not be trusted to perform the basic task of maintaining the integrity of such evidence despite the expansive resources at their disposal. That is why President Trump’s defense team has not inspected the boxes up to this point and instead focused on other aspects of our defense in motion practice and discovery review.”
And, as for the upcoming deadlines on CIPA evidence and expert testimony, Trump says those should be held in abeyance.
“Defense counsel cannot reasonably be expected to specify classified information that they intend to offer at trial when the Office recently disclosed that one of the most basic premises of the criminal justice process — that the prosecution team can be trusted to maintain existing evidence — no longer applies,” the motion goes on.
An attached letter used three lines from prosecutors who authored the special counsel’s Friday admission to state the defense’s case plainly.
“We are troubled by the concession in your May 3 submission that the prosecution team failed to preserve critical evidence relating to the location of documents within boxes obtained from Mar-a-Lago,” the letter reads. “The documents’ location constituted exculpatory information relating to, inter alia, the complete absence of culpable criminal intent by President Trump … Your failure to disclose the spoliation of this evidence until this month is an extraordinary breach of your constitutional and ethical obligations.”
FTC effort to obtain litigation holds in Amazon case sparks privilege battle
Dive Brief:
The Federal Trade Commission last week said Amazon must hand over its litigation holds and ephemeral messaging instructions so it can see how much of the company’s internal communication about the agency’s antitrust case against it has been lost to spoliation and whether that spoliation was deliberate.
“Plaintiffs need these documents to assess whether Amazon failed to take reasonable steps to preserve documents and to map out what information has been destroyed,” the agency says in an April 25 filing with a federal district court in Washington. Last year, the agency and 17 state attorneys general sued the company, accusing it of wielding monopoly power to keep prices high while lowering service quality. Amazon is seeking to get the case dismissed.
Dive Insight:
The spoliation issue is crucial because executives talked among themselves about the company’s potentially anticompetitive business practices using the messaging app Signal, which has an auto-delete setting, the FTC says.
“Executives turned on Signal’s ‘disappearing message’ feature, which irrevocably destroys messages, even after Amazon was on notice that Plaintiffs were investigating its conduct,” says the agency, headed by Lina Khan. Khan has made the fight with Amazon a key test of the agency’s antitrust enforcement posture.
It took the company 15 months after it learned of the investigation – and 10 months after it was sent its first preservation letters – to issue notices to employees about preserving their communications.
“It is highly likely that relevant information has been destroyed as a result of Amazon’s actions and inactions,” the agency says.
Company founder and then-CEO Jeff Bezos was “a heavy Signal user” and he wasn’t sent a notice to preserve his communications for almost a year after the company was sent its first preservation letters, the agency says.
“Mr. Bezos’ documents and communications were clearly within the scope of the investigation,” the FTC says. “As Amazon’s founder and CEO, he was the ultimate decision-maker.”
In its filing, the FTC suggests the company wasn’t forthright in its response to the preservation letters.
“Amazon claims that it did not learn about its employees’ use of Signal until the summer of 2020, even though Amazon’s top executives, including its General Counsel [David] Zapolsky, had been using Signal since 2019,” the agency says.
Almost three years after Amazon received its first preservation letters, employees were told to switch to an internally created app, Wickr, that enables messages to be saved centrally for individuals on legal hold.
But the ephemeral conversations didn’t stop.
“Amazon executives continued to use Signal’s disappearing message feature to destroy records of their internal communications,” the agency says.
In the filing, the agency is asking for all of the company’s litigation holds and preservation notices as well as the instructions it sent to employees about use of the ephemeral messaging apps during the investigation.
The company has pushed back against previous attempts by the agency to get its litigation holds and messaging instructions, saying they’re privileged, but the FTC says it only needs to make a preliminary showing that spoliation has occurred to overcome the privilege defense.
“A preliminary showing of spoliation means only that ‘there is reason for concern that evidence has been lost,’” the FTC says. “Such ‘reason for concern’ can be shown where potentially relevant evidence has been destroyed or where a party failed to take adequate steps to preserve information.”
In a statement, Amazon says the FTC is asking for too much.
“The FTC has a complete picture of Amazon’s decision-making in this case,” says Tim Doyle, a company spokesperson.
Doyle says the company has provided some 1.7 million documents, including those involving conversations that were held on messaging apps. In all, the company has provided more than “100 terabytes of data.”
If the court finds the spoliation was deliberate, it can impose severe sanctions on the company.
COLIN HATCER questions amount and method of economic damages
Loss of source code section spawns successful spoliation motion
Given the specter of litigation, a company should have preserved the entire source code behind its automotive diagnostic tool, a Superior Court judge has found, ruling that its failure to do so warranted a spoliation sanction.
The case Espaillat v. Lynnway Auto Auction, Inc., et al. was initially brought by the personal representative of the estate of one of five people killed when a Jeep Cherokee accelerated unexpectedly at an auto auction facility in Billerica.
The original defendants then brought a third-party action against the manufacturer of a “scan tool,” the insertion of which into the Jeep’s onboard diagnostics electric port under the dashboard may have caused the Jeep’s unintended acceleration, according to those defendants.
During discovery in that third-party action, the manufacturer produced some but not all the source code for the scan tool.
In weighing the third-party plaintiffs’ spoliation motion, Judge C. William Barrett first had to determine whether the missing source code was relevant to the proceedings.

The manufacturer pointed to two formal investigations, both of which concluded that operator error caused the accident.
But neither investigation evaluated whether the scan tool could have caused or contributed to the accident, Barrett noted.
In fact, the manufacturer’s own expert had conceded that when the company tested its product for latent defects, it had the entire source code.
That testimony “emphasizes [the third-party plaintiffs’] need for the same evidence,” Barrett wrote.
Next, Barrett considered the timing of the alleged spoliation because sanctions can only be imposed when the spoliating party knew or reasonably should have known that the evidence might be relevant to a possible action.
While there was no concrete evidence that the manufacturer was in possession of the source code when it first became aware of potential litigation, it was reasonable to infer both that it had the source code and that it subsequently negligently lost or destroyed that evidence, the judge ruled.
The 11-page decision is Lawyers Weekly No. 12-020-24.
‘Cast the net broadly’
Louis J. Muggeo
By filing the spoliation motion, Louis J. Muggeo of Salem said he and his co-counsel were pursuing an answer to a simple question: “How could this possibly have happened?”
While the State Police and National Highway Traffic Safety Administration had concluded the cause of the accident was “driver error,” those were “default conclusions in both instances,” said Muggeo’s co-counsel, David A. White of North Andover.
“They weren’t able to determine whether or not the scan tool was a causative factor in the sudden acceleration of the vehicle,” White said.
David A. White
The biggest hurdle in pursuing the spoliation sanction was “making the judge understand that this was really a simple issue, although the underlying technology was extremely complex,” Muggeo added.
He said they overcame that hurdle by playing the video of the accident repeatedly at the motion hearing, enabling the judge to appreciate the temporal connection between when the scan tool was placed in the vehicle and when it suddenly accelerated.
“You look at it and you say, ‘Something had to happen here because a vehicle doesn’t just take off like a rocket,’” Muggeo said.
Beyond the complexity of the technology, another of their concerns was that, based on the discovery, they could not affirmatively establish when or how the source code was discarded, Muggeo said.
“Most of the case law said that’s part of our burden,” he acknowledged.
But Muggeo and White shifted that burden to the manufacturer by showing that the source code was in the manufacturer’s exclusive possession and control and that the manufacturer had an unwritten custom and practice of retaining the source code for a product for approximately two years after the product was last sold.

While not disagreeing with the result, Boston attorney Joseph J. Laferrera said it made him a “little squeamish” to impose sanctions on the manufacturer for failing to retain evidence that it may not have possessed when it first became aware of a possible suit.
“Yes, past pattern or practice may suggest that the code was in [the manufacturer’s] possession …, but that ‘informal custom’ is doing a lot of work here,” Laferrera said. “There are a zillion innocent explanations for its being written over or discarded.”
Laferrera said he was also surprised the judge did not require the plaintiffs to offer something more than conjecture that the device might have triggered the unplanned acceleration.
“That might not have been enough for some judges in the commonwealth,” he said.
Attorneys agreed that Barrett’s decision reminds corporate counsel of the value of issuing all-encompassing “litigation holds” once the prospect of a legal action arises.
“I think that corporate counsel would be very prudent to advise their clients to retain more rather than less,” White said.Michael D. Molloy
Spoliation is always thought about in terms of a guilty defendant trying to hide something.
But this could be a case of the opposite, where an otherwise ‘innocent’ defendant could be facing potential liability by not preserving exculpatory evidence.
Laferrera said he instructs his clients to “cast the net broadly.”
“Generally speaking, the sanctions are worse for the client than if they had kept the materials at issue,” he said.
It seems entirely possible that the manufacturer’s product had nothing to do with the incident at all, noted Lowell attorney Michael D. Molloy.

But without the code, there is no way to prove that.
“Spoliation is always thought about in terms of a guilty defendant trying to hide something by either deleting or not preserving evidence,” he said. “But this could be a case of the opposite, where an otherwise ‘innocent’ defendant could be facing potential liability by not preserving exculpatory evidence — a tough pill to swallow.”

On the issue of notice, Newton attorney Matthew J. Fogelman said the standard is often misunderstood as requiring that a company know of an actual pending case.
But the Supreme Judicial Court has said that the standard is that a litigant or its expert either knows or reasonably should know that the evidence might be relevant to a possible action, he explained.
The SJC also stated that the threat of a lawsuit must be sufficiently apparent such that a reasonable person in the spoliator’s position would realize the possible — rather than the certain — importance of the evidence, Fogelman added.
On that front, too, Laferrera has qualms.
One might question whether it would have been evident to a reasonable person that the type of analysis the plaintiffs’ expert characterized as crucial would have been necessary to the investigation, Laferrera said.
The manufacturer’s attorneys, Jay V. Lee and Andrew D. McNaught, of Lowell, had not responded to requests for comment as of Lawyers Weekly’s deadline.

A tragic day in Billerica
Roger Hartwell, an employee of the Billerica automobile auction facility Lynnway Auto, was in the driver’s seat of a 2006 Jeep Grand Cherokee being sold at auction when auto dealer John Sirek approached the Jeep and inserted an Innova 3160d model scan tool into the Jeep’s on-board diagnostics electric port under the dashboard.
Seven seconds after the scan tool was inserted, the Jeep, which had been stopped for more than a minute, accelerated out of Hartwell’s control and crashed into the building, killing five people and injuring seven others.
The Middlesex County District Attorney’s Office, which would later file manslaughter charges against Lynnway Auto and the company’s president, interviewed Sirek and seized the scan tool.
Espaillat v. Lynnway Auto Auction, Inc., et al.
THE ISSUE:
Were spoliation sanctions warranted against a company that was on notice of the possibility of litigation regarding its automobile maintenance diagnostic device when it produced some but not all the source code for that device?
DECISION: Yes (Middlesex Superior Court)
LAWYERS: Louis J. Muggeo of Louis J. Muggeo & Associates, Salem; David A. White of Davis & White, North Andover (third-party plaintiffs)
Jay V. Lee and Andrew D. McNaught, of Gallagher & Cavanaugh, Lowell (third-party defense)
The day after the accident, a State Police lieutenant informed an Innova customer service representative that the scan tool had been plugged into the Jeep’s electric port at the time of the accident.
The lieutenant asked the representative if it was possible the tool could tamper with the Jeep’s acceleration and was told that the tool did not have the capability to put a car into drive or accelerate the engine.
Nonetheless, the lieutenant purchased a scan tool the following day, and within days, Innova had plans to embark on its own investigation, according to company records.
After Lynnway Auto brought its third-party action, Innova produced in discovery some but not all the source code for the 3160d scan tool. Notably missing was the communication source code directly relating to Chrysler vehicles, such as the Jeep.
Lynnway Auto’s electrical engineer expert testified that the source code was essential for a proper and thorough evaluation of the way the scan tool interfaced with the Jeep’s computer systems and electrical signals.
Specifically, the expert maintained that the missing source code was preventing him from properly conducting a software verification activity known as a “static code analysis.”
Innova had produced the binary code for the scan tool, but since it was not a human-readable format, it could not be used to perform the static code analysis, the expert claimed.
In granting the motion for sanctions, Barrett ruled that Lynnway Auto could present evidence of the alleged spoliation at trial and would be entitled to an instruction that the jury could — but was not required — to infer from the deletion of the communication source code that its contents were unfavorable to Innova.
Reasonable inferences
Barrett concluded that Innova was on notice of possible litigation no later than May 4, 2017, when the police lieutenant had the conversation with the company’s customer service representative.
The manufacturer contended that the conversation, at most, placed it on notice of its duty to preserve the device but not the source code.
But Barrett disagreed, citing the testimony of the plaintiffs’ expert regarding the necessity of having the entire source code to conduct the “static code analysis” properly.
The manufacturer also argued that it was not at fault for the spoliation because there was no evidence that it intentionally discarded the missing portion of source code, and the precise date when the source code had been discarded was unknown.
But Barrett deemed the plaintiffs to have sufficiently established that the evidence had been negligently lost or destroyed by citing the company’s “informal custom and practice” of retaining the source code for its scan tool models for approximately two years after a particular model was last sold, coupled with an invoice showing that six of the scan tools had been sold to Wal-Mart about a year before the accident.
The plaintiffs’ expert also averred that it is standard practice in the industry for the purpose of troubleshooting to retain all portions of a source code, rather than selectively discard portions.
Here, the manufacturer had retained some but not all the source code for its scan tool and not explained why or how that happened, Barrett noted.
masslawyersweekly.com
Loss of source code section spawns successful spoliation motion
Given the specter of litigation, a company should have preserved the entire source code behind its automotive diagnostic tool, a Superior Court judge has found, ruling that its failure to do so warranted a spoliation sanction.
The case Espaillat v. Lynnway Auto Auction, Inc., et al. was initially brought by the personal representative of the estate of one of five people killed when a Jeep Cherokee accelerated unexpectedly at an auto auction facility in Billerica.
The original defendants then brought a third-party action against the manufacturer of a “scan tool,” the insertion of which into the Jeep’s onboard diagnostics electric port under the dashboard may have caused the Jeep’s unintended acceleration, according to those defendants.
During discovery in that third-party action, the manufacturer produced some but not all the source code for the scan tool.
In weighing the third-party plaintiffs’ spoliation motion, Judge C. William Barrett first had to determine whether the missing source code was relevant to the proceedings.
The manufacturer pointed to two formal investigations, both of which concluded that operator error caused the accident. But neither investigation evaluated whether the scan tool could have caused or contributed to the accident, Barrett noted.
In fact, the manufacturer’s own expert had conceded that when the company tested its product for latent defects, it had the entire source code. That testimony “emphasizes [the third-party plaintiffs’] need for the same evidence,” Barrett wrote.
Next, Barrett considered the timing of the alleged spoliation because sanctions can only be imposed when the spoliating party knew or reasonably should have known that the evidence might be relevant to a possible action.
While there was no concrete evidence that the manufacturer was in possession of the source code when it first became aware of potential litigation, it was reasonable to infer both that it had the source code and that it subsequently negligently lost or destroyed that evidence, the judge ruled.
The 11-page decision is Lawyers Weekly No. 12-020-24. ‘Cast the net broadly’
Louis J. MuggeoBy filing the spoliation motion, Louis J. Muggeo of Salem said he and his co-counsel were pursuing an answer to a simple question: “How could this possibly have happened?”
While the State Police and National Highway Traffic Safety Administration had concluded the cause of the accident was “driver error,” those were “default conclusions in both instances,” said Muggeo’s co-counsel, David A. White of North Andover.
“They weren’t able to determine whether or not the scan tool was a causative factor in the sudden acceleration of the vehicle,” White said.
David A. WhiteThe biggest hurdle in pursuing the spoliation sanction was “making the judge understand that this was really a simple issue, although the underlying technology was extremely complex,” Muggeo added.
He said they overcame that hurdle by playing the video of the accident repeatedly at the motion hearing, enabling the judge to appreciate the temporal connection between when the scan tool was placed in the vehicle and when it suddenly accelerated.
“You look at it and you say, ‘Something had to happen here because a vehicle doesn’t just take off like a rocket,’” Muggeo said.
Beyond the complexity of the technology, another of their concerns was that, based on the discovery, they could not affirmatively establish when or how the source code was discarded, Muggeo said.
“Most of the case law said that’s part of our burden,” he acknowledged.
But Muggeo and White shifted that burden to the manufacturer by showing that the source code was in the manufacturer’s exclusive possession and control and that the manufacturer had an unwritten custom and practice of retaining the source code for a product for approximately two years after the product was last sold.
While not disagreeing with the result, Boston attorney Joseph J. Laferrera said it made him a “little squeamish” to impose sanctions on the manufacturer for failing to retain evidence that it may not have possessed when it first became aware of a possible suit.
“Yes, past pattern or practice may suggest that the code was in [the manufacturer’s] possession …, but that ‘informal custom’ is doing a lot of work here,” Laferrera said. “There are a zillion innocent explanations for its being written over or discarded.”
Laferrera said he was also surprised the judge did not require the plaintiffs to offer something more than conjecture that the device might have triggered the unplanned acceleration.
“That might not have been enough for some judges in the commonwealth,” he said.
Attorneys agreed that Barrett’s decision reminds corporate counsel of the value of issuing all-encompassing “litigation holds” once the prospect of a legal action arises.
“I think that corporate counsel would be very prudent to advise their clients to retain more rather than less,” White said.Michael D. MolloySpoliation is always thought about in terms of a guilty defendant trying to hide something. But this could be a case of the opposite, where an otherwise ‘innocent’ defendant could be facing potential liability by not preserving exculpatory evidence.
Laferrera said he instructs his clients to “cast the net broadly.”
“Generally speaking, the sanctions are worse for the client than if they had kept the materials at issue,” he said.
It seems entirely possible that the manufacturer’s product had nothing to do with the incident at all, noted Lowell attorney Michael D. Molloy. But without the code, there is no way to prove that.
“Spoliation is always thought about in terms of a guilty defendant trying to hide something by either deleting or not preserving evidence,” he said. “But this could be a case of the opposite, where an otherwise ‘innocent’ defendant could be facing potential liability by not preserving exculpatory evidence — a tough pill to swallow.”
On the issue of notice, Newton attorney Matthew J. Fogelman said the standard is often misunderstood as requiring that a company know of an actual pending case. But the Supreme Judicial Court has said that the standard is that a litigant or its expert either knows or reasonably should know that the evidence might be relevant to a possible action, he explained.
The SJC also stated that the threat of a lawsuit must be sufficiently apparent such that a reasonable person in the spoliator’s position would realize the possible — rather than the certain — importance of the evidence, Fogelman added.
On that front, too, Laferrera has qualms. One might question whether it would have been evident to a reasonable person that the type of analysis the plaintiffs’ expert characterized as crucial would have been necessary to the investigation, Laferrera said.
The manufacturer’s attorneys, Jay V. Lee and Andrew D. McNaught, of Lowell, had not responded to requests for comment as of Lawyers Weekly’s deadline. A tragic day in Billerica
Roger Hartwell, an employee of the Billerica automobile auction facility Lynnway Auto, was in the driver’s seat of a 2006 Jeep Grand Cherokee being sold at auction when auto dealer John Sirek approached the Jeep and inserted an Innova 3160d model scan tool into the Jeep’s on-board diagnostics electric port under the dashboard.
Seven seconds after the scan tool was inserted, the Jeep, which had been stopped for more than a minute, accelerated out of Hartwell’s control and crashed into the building, killing five people and injuring seven others. The Middlesex County District Attorney’s Office, which would later file manslaughter charges against Lynnway Auto and the company’s president, interviewed Sirek and seized the scan tool.
Espaillat v. Lynnway Auto Auction, Inc., et al.
THE ISSUE: Were spoliation sanctions warranted against a company that was on notice of the possibility of litigation regarding its automobile maintenance diagnostic device when it produced some but not all the source code for that device?
DECISION: Yes (Middlesex Superior Court)
LAWYERS: Louis J. Muggeo of Louis J. Muggeo & Associates, Salem; David A. White of Davis & White, North Andover (third-party plaintiffs)
Jay V. Lee and Andrew D. McNaught, of Gallagher & Cavanaugh, Lowell (third-party defense)
The day after the accident, a State Police lieutenant informed an Innova customer service representative that the scan tool had been plugged into the Jeep’s electric port at the time of the accident. The lieutenant asked the representative if it was possible the tool could tamper with the Jeep’s acceleration and was told that the tool did not have the capability to put a car into drive or accelerate the engine.
Nonetheless, the lieutenant purchased a scan tool the following day, and within days, Innova had plans to embark on its own investigation, according to company records.
After Lynnway Auto brought its third-party action, Innova produced in discovery some but not all the source code for the 3160d scan tool. Notably missing was the communication source code directly relating to Chrysler vehicles, such as the Jeep.
Lynnway Auto’s electrical engineer expert testified that the source code was essential for a proper and thorough evaluation of the way the scan tool interfaced with the Jeep’s computer systems and electrical signals.
Specifically, the expert maintained that the missing source code was preventing him from properly conducting a software verification activity known as a “static code analysis.”
Innova had produced the binary code for the scan tool, but since it was not a human-readable format, it could not be used to perform the static code analysis, the expert claimed.
In granting the motion for sanctions, Barrett ruled that Lynnway Auto could present evidence of the alleged spoliation at trial and would be entitled to an instruction that the jury could — but was not required — to infer from the deletion of the communication source code that its contents were unfavorable to Innova. Reasonable inferences
Barrett concluded that Innova was on notice of possible litigation no later than May 4, 2017, when the police lieutenant had the conversation with the company’s customer service representative.
The manufacturer contended that the conversation, at most, placed it on notice of its duty to preserve the device but not the source code. But Barrett disagreed, citing the testimony of the plaintiffs’ expert regarding the necessity of having the entire source code to conduct the “static code analysis” properly.
The manufacturer also argued that it was not at fault for the spoliation because there was no evidence that it intentionally discarded the missing portion of source code, and the precise date when the source code had been discarded was unknown.
But Barrett deemed the plaintiffs to have sufficiently established that the evidence had been negligently lost or destroyed by citing the company’s “informal custom and practice” of retaining the source code for its scan tool models for approximately two years after a particular model was last sold, coupled with an invoice showing that six of the scan tools had been sold to Wal-Mart about a year before the accident.
The plaintiffs’ expert also averred that it is standard practice in the industry for the purpose of troubleshooting to retain all portions of a source code, rather than selectively discard portions.
Here, the manufacturer had retained some but not all the source code for its scan tool and not explained why or how that happened, Barrett noted.

New motion responses in suits against Wood County authorities deny spoliation
PARKERSBURG, W.Va. (WTAP) - New filings in two lawsuits against current and former Wood County officials show how the defendants are responding to accusations that they destroyed evidence.
The two lawsuits filed by plaintiffs Timothy Allen and Mark Harris in 2021 center around alleged abuse and harassment by former Wood County Sheriff Steve Stephens.
Both plaintiffs filed motions asking the Wood County Commission and Sheriff’s Department be sanctioned for either failing to produce or destroying evidence in the form of emails, text messages and other digital records.
In responses to those motions filed last week, counsel for the defendants assert that no sanctions are warranted because neither the sheriff’s department nor the county commission intentionally destroyed or failed to look for evidence.
According to the motion responses, the IT specialists for both the commission and the sheriff’s department were overworked and unfamiliar with the protocols of performing court-mandated searches through digital records, rather than acting in bad faith:
“[T]he actions, or inactions, of [the IT specialists} are attributable to being overextended and unfamiliar with certain litigation hold functions within software, rather than being attributable to a bad faith state of mind.”
These most recent filings in these lawsuits come after two other lawsuits against the County Commission, Sheriff’s Department, and Steve Stephens were settled earlier this year.
“Pharma Bro” Avoids the Most Serious Adverse Inference Sanction for Spoliating Evidence Under Rule 37(e)
In an opinion out of the Southern District of New York addressing alleged spoliation of ESI, Judge Denise Cote found that the plaintiffs – the Federal Trade Commission and a collection of states – only sufficiently established half of their spoliation claims sought against defendant Martin Shkreli.
Shkreli, aka “Pharma Bro,” and his business partner, Kevin Mulleady, launched Vyera in 2014.
The plaintiffs alleged that in November 2017 Vyera entered into several anti-competitive agreements, including exclusive supply agreements, with a company preparing to seek FDA approval for the manufacture of the active ingredient in one of Vyera’s branded drug products.
The plaintiffs sought sanctions under Rule 37(e) against Shkreli, alleging he failed to preserve messages on two cellphones despite receiving a litigation hold in late 2015.
The first phone – a company-issued phone – was allegedly used by Shkreli to communicate about issues relevant to the case.
When Shkreli’s attorney sent the company phone to be forensically imaged in April 2020, it was discovered that it had been factory reset (i.e., wiped) sometime in 2016 or 2017.
While neither Shkreli nor Vyera produced communications from this phone, Vyera represented that company-issued phones were backed up to iCloud.
The second was a contraband phone Shkreli appeared to have possessed while in prison.
A Vyera executive testified he communicated with Shkreli through this phone via WhatsApp from the end of 2018 through February 2019.
Mulleady also produced two texts from Shkreli dated during his incarceration.
Vyera said it did not possess, and likely could not access, the WhatsApp messages.
When asked at his deposition if he possessed a phone in prison, Shkreli invoked his Fifth Amendment right against self-incrimination.

To address Shkreli’s spoliation, the plaintiffs asked the court to impose a mandatory adverse inference under Rule 37(e)(2) instructing the jury to accept the presumption that this missing ESI would support that Shkreli was continuously involved in Vyera’s business from 2015 to 2021, including while incarcerated, and that he engaged in the challenged anti-competitive conduct.
Alternatively, under Rule 37(e)(1), the plaintiffs sought curative measures to disallow Shkreli from arguing or introducing evidence to disprove these presumptions.
Shkreli, on the other hand, argued that the plaintiffs failed to prove the communications existed and, to the extent they had, that there was no intent to deprive the plaintiffs of the communications.
Therefore, Shkreli requested the more modest curative measure that he be precluded from arguing that he did not communicate with two Vyera employees about the company during his incarceration.
The court found the plaintiffs failed to show that the company phone’s data had not been preserved, and ordered Vyera to search its iCloud backup data and produce any messages from Shkreli.
The court, however, did find that Shkreli failed to preserve the data on his contraband phone, but adopted Shkreli’s more narrowly drawn sanctions.
Interestingly, in exercising its discretion to impose these lesser sanctions, the court did not specifically address whether Shkreli intended to deprive the plaintiffs of spoliated communications that would have given rise to the more serious sanctions of Rule 37(e)(2).
This opinion illustrates the high threshold litigants must satisfy to secure sanctions under Rule 37(e)(2).
Even where the adverse party’s conduct represents a “close call,” courts generally are reluctant to impose the more serious sanctions under Rule 37(e)(2) and, instead, will opt to impose remedial measures under Rule 37(e)(1).
CC-21-05418-A | DARA HARRIS, INDIVIDUALLY, AND AS REPRESENTATIVE OF THE ESTATE OF ROBERT BUNTYN,, BRYAN BUNTYN, INDIVIDUALLY vs. NEWKIRK LOGISTICS, INC., DESIREE RAISHON BOYD, BRUCKNER LEASING CO, INC.
TEXAX LEGAL STANDARD
The Texas Supreme Court has “adopted a framework governing the imposition of remedies for evidence spoliation.” Petroleum Sols., Inc. v. Head, 454 S.W.3d 482, 488 (Tex. 2014) (citing Brookshire Bros., Ltd. v. Aldridge, 438 S.W.3d 9, 14 (Tex. 2014)).
Under the Brookshire Brothers framework, “to find that spoliation occurred, the trial court must make affirmative determinations as to two elements.
First, the party who failed to produce evidence must have had a duty to preserve the evidence.” Id. (citing Brookshz're, 438 S.W.3d at 20).
“Second, the nonproducing party must have breached its duty to reasonably preserve material and relevant evidence.” Id. (citing Brookshire, 438 S.W.3d at 20-21 & n.8).
If there is a finding of spoliation, “the trial court must exercise its discretion in imposing a remedy. In determining what remedy, if any, is appropriate, the court should weigh the spoliating party’s culpability and the prejudice to the non-spoliating party.” Id. at 488-89.
“[C]ourts generally follow a two-part test in determining whether a particular sanction for discovery abuse is just.” Petroleum Solutions, 454 S.W.3d at 489.
“First, a direct relationship must exist between the offensive conduct, the offender, and the sanction imposed. To meet this requirement, a sanction must be directed against the wrongful conduct and toward remedying the prejudice suffered by the innocent party.” Id. (internal citations omitted).
“Second, a sanction must not be excessive, which means it should be no more severe than necessary to satisfy its legitimate purpose. Id. (internal citations and quotation omitted).
PLAINTIFFS’ RESPONSE TO DEFENDANTS’ MOTION FOR SPOLIATION SANCTIONS ORDER DENYING DEFENDANTS’ MOTION FOR SPOLIATION SANCTIONS

Third lawsuit filed against Wood County Commission, Stephens
New motion responses in suits against Wood County authorities deny spoliation -
PARKERSBURG, W.Va. (WTAP) -
A third lawsuit has been filed against the Wood County Commission, Sheriff’s Department, and Steve Stephens.
The complaint was filed in Wood County Circuit Court Friday morning by Timothy Allen, a current Wood County deputy sheriff.
Bailess Law Firm, the law firm representing Allen, is the same one representing Mark Harris and Della Matheny in two other suits against the county and Stephens.
The suit alleges Sheriff Stephens threatened to demote Allen after learning Allen was involved in a relationship with Deputy Tasha Hewitt.
Hewitt later filed a complaint against the sheriff, claiming a hostile work environment in the sheriff’s office.
Deputy Allen is seeking a jury trial to determine damages.
“Retaliation in the workplace is a serious safety issue,” said Todd Bailess, one of Allen’s attorneys. “We should commend employees like Sgt. Allen who have the courage to speak out against discriminatory treatment of women at the hands of those in power.”
Sheriff Stephens could not be reached for comment.
County Commissioner Bob Tebay said he was “sorry to hear that,” when told about the filing Friday afternoon.
Commissioners Jimmy Colombo and Blair Couch couldn’t be reached for comment.
In responses to those motions filed last week, counsel for the defendants assert that no sanctions are warranted because neither the sheriff’s department nor the county commission intentionally destroyed or failed to look for evidence.
According to the motion responses, the IT specialists for both the commission and the sheriff’s department were overworked and unfamiliar with the protocols of performing court-mandated searches through digital records, rather than acting in bad faith:
“[T]he actions, or inactions, of [the IT specialists} are attributable to being overextended and unfamiliar with certain litigation hold functions within software, rather than being attributable to a bad faith state of mind.”
These most recent filings in these lawsuits come after two other lawsuits against the County Commission, Sheriff’s Department, and Steve Stephens were settled earlier this year.
One of the most active areas of litigation in recent years is the spoliation of evidence.
Although the Supreme Court of Texas’ opinion in Brookshire Bros., Ltd. v. Aldridge, 438 S.W.3d 9 (Tex. 2014) defined both the type of spoliation that may be sanctioned and the type of sanctions available, litigation continues to be abundant.
Brookshire Bros. – The Leading Texas Decision

Brookshire Bros. was a grocery store slip and fall case in which the plaintiff had said he was not injured at the time.
Shortly thereafter, he said he was injured, so the store manager preserved the surveillance video footage from two hours before the incident through several hours afterward.
The plaintiff’s attorney wanted more than two hours before the incident, but that had been recorded over under the store’s general 30-day video loop.
The trial court allowed the jury to hear evidence of the destruction of the video and submitted the spoliation instruction.
The Court of Appeals affirmed.
The Supreme Court reversed, finding an abuse of discretion.
It decided that as a matter of law the trial judge determines whether spoliation has occurred and what sanctions, if any, to impose.
Evidence of the spoliating conduct is inadmissible.
It is the complaining party’s burden to prove there was a duty to preserve, i.e., that the accused party knew there was a substantial chance a claim would be filed (not just an abstract possibility).
If there was a duty, the court determines whether the breach was intentional or negligent and whether the complaining party was prejudiced.
Prejudice is proved by showing that the spoliated evidence was relevant and material on a key issue, the evidence would have been harmful to the spoliator’s case or helpful to the non-spoliator’s case; and the evidence was not cumulative.
Sanctions imposed must be proportional, that is, they must relate directly to the conduct giving rise to the sanction and may not be excessive.
Key considerations are: the level of culpability of the spoliator and the degree of prejudice to the opposing party.
Sanctions may include the following:
an order prohibiting further discovery by the spoliator;
an order designating certain facts established;
a contempt order;
exclusion of the evidence;
award of attorney’s fees and/or costs;
dismissal with or without prejudice;
striking pleadings, default judgment; and a jury instruction.
The Brookshire Brothers opinion specifically stated that a jury instruction is to be used as a last resort – only when the spoliation is intentional, with one exception.
If the spoliation is merely negligent, but it deprives the opposing party of any meaningful ability to present its claim, the jury instruction may be given.
After Brookshire Bros., The Pattern Jury Charge was amended.
PJC § 1.12 (2016) provides the following:
[The spoliating party] [destroyed/failed to preserve] [describe evidence].
You [must/may] consider that this evidence would have been unfavorable to [spoliating party] on the issue of [describe issue(s)] to which evidence would have been relevant.
This allows argument to the trial court over whether to use must or may.
Publisher says prince destroyed key evidence
The legal war between Prince Harry and major British tabloids continues as an attorney for the publisher of The Sun has accused the royal of destroying evidence in his phone hacking case.
Attorney Anthony Hudson, representing News Group Newspapers, has alleged the Duke of Sussex deliberately deleted text messages with J.R. Moehringer, the ghostwriter of his tell-all memoir Spare . Hudson told London’s High Court on Thursday that Prince Harry had created an “obstacle course” to prevent the publisher from obtaining potential evidence.
The judge ordered a statement from Prince Harry to explain “what happened to the messages between himself and his ghostwriter and whether any attempts were made to retrieve them.” New York Daily News
proof that defendants tried to tamper with or destroy documents.
charged with obstruction
disrupting
obstructing or conspiring to obstruct
They include Kevin Seefried, a Delaware man who threatened a Black police officer with a pole attached to a Confederate battle flag as he stormed the Capitol.
refusing to provide documents or testimony
Spoliation Sanctions & Summary Judgment Denial: A Wake-Up Call for Mobile Device Preservation | JD Supra
A recent decision in ediscovery case law, Maziar v. City of Atlanta from June 10, 2024, underscores the crucial importance of early preservation, particularly regarding text messages from mobile devices.

This case, presided over by United States District Judge Steven Grimberg, offers valuable lessons for litigation professionals.
Notably, it represents one of the first instances Case of the Week has covered the denial of a summary judgment motion as a sanction under Federal Rule of Civil Procedure 37(e) for the failure to preserve data.
Case Overview:
The plaintiff, a former Director of the Atlanta Mayor’s Office of Immigration Affairs, filed a retaliation complaint against the City of Atlanta.
The crux of the dispute centered around text messages on the supervisor’s mobile device, which were not properly preserved despite a litigation hold.
Key Timeline:
November 2020:
Plaintiff’s counsel sends a demand letter requesting a litigation hold.
April 2021: Incident leading to plaintiff’s termination occurs in which supervisor is key witness. May 2021: City issues a litigation hold and terminates the plaintiff. December 2022: Supervisor leaves job; City wipes the supervisor’s phone. January 2023: Supervisor upgrades personal phone, losing all previous text messages.
The Court’s Analysis:
Judge Grimberg’s decision hinged on Federal Rule of Civil Procedure 37(e), which governs sanctions for failure to preserve electronically stored information (ESI).
The Court made a crucial distinction between Rule 37(e)(1), which focuses on prejudice, and Rule 37(e)(2), which requires a finding of intent to deprive.
While the Court did not find bad faith on the City’s part, it determined that the plaintiff was indeed prejudiced by the loss of potentially crucial text messages.
This prejudice stemmed from the inability to contextualize a cropped text message and access other relevant evidence from the supervisor’s phone.
Sanctions Imposed:
In a significant move, the Court denied the City’s motion for summary judgment as a sanction.
Additionally, extensive monetary sanctions were awarded to cover the plaintiff’s costs and fees related to both the sanctions and summary judgment motions.
Key Takeaways for Litigation Professionals:
Timely Preservation is Crucial:
Even in seemingly minor employment matters, strict attention to preservation, collection, and production of ESI is essential.
Early identification and preservation of data, especially from mobile devices, can prevent costly consequences.
Implement Robust Preservation Processes: Develop and maintain tools and processes for early identification and preservation of ESI.
This proactive approach can significantly mitigate risks and reduce costs in the long run.
Consider Remote Collection Tools:
Utilize targeted remote collection tools for mobile devices.
These can be cost-effective solutions to preserve critical data without disrupting business operations.
Recognize the Broad Impact of Spoliation:
The loss of even a few text messages can potentially upend an entire case.
Courts are increasingly willing to impose severe sanctions, including the denial of summary judgment motions, for failure to preserve relevant ESI.
Balance Cost and Risk:
While it’s important to consider the cost of preservation against the likelihood of litigation, err on the side of caution.
The potential consequences of under-preservation far outweigh the initial costs of proper data management.
Conclusion:
The Maziar v. City of Atlanta case serves as a powerful reminder of the importance of proactive ediscovery practices.
As litigation professionals, we must constantly balance the risk vs. cost in our approach to data preservation, especially in today’s environment where mobile devices play an increasingly central role in business communications.
By implementing robust preservation protocols and leveraging appropriate technologies, we can better serve our clients and avoid costly sanctions that could derail even the strongest cases.
Federal District Court Denied Spoliation Motion Where Plaintiffs Attempted to Argue that a Bus Company Failed to Preserve Video | JD Supra
Williams v. First Student, Inc., 2024 WL 1132237, No. 20-cv-1176 (CPO) (SAK) (D. N.J. Mar. 15, 2024)
The plaintiffs’ sought to obtain a preclusion of expert evidence and adverse inference at trial for failure to maintain video after an infant plaintiff disembarked one school bus and was struck by another company’s school bus, causing serious injury.
The defendant-bus company provided testimonial evidence that they attempted to retrieve video, but that there was a malfunction and no video was ever created.
The plaintiffs attempted to argue that certain codes on the hard drive indicated items were altered or moved and referenced a code describing the “Recycle Bin.”
The defendant’s expert noted that this was actually an error code.
The court ruled the plaintiffs had not met their burden to establish spoliation.
Plaintiffs Allege Village Negligence After Fatal Police Chase Cook County Record
A high-stakes legal battle involving a police chase that resulted in severe injuries and death has culminated in a $33.5 million jury award for the plaintiffs.
The lawsuit, filed by Aja Seats and Sabrina Wright on behalf of John Kyles and Duane Dunlap respectively, was brought against the Village of Dolton in Cook County Circuit Court on November 5, 2019.
The case centers around an October 9, 2016 incident where a high-speed police chase led to the death of John Kyles and severe injuries to Duane Dunlap.
Plaintiffs claimed that Dolton police officers Lewis Lacey and Ryan Perez pursued a vehicle driven by Demetrius Sorrells at dangerously high speeds, resulting in a crash.
Crucially, the plaintiffs argued that evidence from Perez’s dashboard camera, which could have provided key insights into the chase, was lost or destroyed—a claim of spoliation of evidence.
During the trial that began on July 26, 2022, and concluded on August 3, 2022, both Lacey and Perez testified about their actions during the chase.
Lacey admitted to reaching speeds up to 75 miles per hour while pursuing Sorrells but claimed he did not see Sorrells's vehicle at certain points.
Perez testified that his dashboard camera would have recorded automatically when he activated his lights and sirens but could not confirm if it was working properly or if any footage was preserved.
Expert witnesses bolstered the plaintiffs' case.
Jay Przybyla presented GPS data showing the positions and speeds of the police vehicles during the chase, while Dennis Waller criticized Dolton police for failing to ensure dashboard cameras were operational and preserving critical video evidence.
The jury found in favor of Dolton on claims of willful and wanton conduct but sided with the plaintiffs on spoliation of evidence.
They awarded $33.5 million in damages due to the loss or destruction of crucial dashboard camera footage.
On appeal, Dolton argued various points including improper jury instructions and insufficient proof of spoliation; however, these arguments were rejected by Justice R. Van Tine who affirmed the jury’s verdict.
Representing the plaintiffs were attorneys whose efforts led to this significant judgment against Dolton.
The case was presided over by Judge Elizabeth M. Budzinski under Case ID No. 2019 L 012256.
Duty to Preserve Evidence
Navigating the timing and scope of an individual’s or entity’s duty to preserve information (including ESI, hard copy documents, and other tangible items) in any particular matter is both critical and challenging.
Knowing that courts sometimes impose severe penalties against individuals and entities that fail to fulfill their duty to preserve, counsel may be tempted to recommend early and expansive preservation efforts.
However, an overly conservative preservation approach has drawbacks because it may:
Require the individual or entity to retain a third-party vendor to implement and manage sophisticated preservation tools.
Limit an individual’s or entity’s access to the documents and information it needs to conduct its routine business.
This article provides guidance on the duty to preserve in federal civil litigation to help counsel effectively advise their clients on preservation-related matters.
Specifically, it addresses:
The standards courts use to determine if an individual or entity has a duty to preserve.
What information is within the scope of the duty to preserve.
When an individual or entity may be sanctioned or otherwise liable for failing to comply with the duty to preserve and the nature of available sanctions.
(For the complete version of this resource, which includes more on developing a preservation protocol, see Duty to Preserve Evidence (Federal) on Practical Law;
for a collection of resources to help counsel preserve documents and ESI, see Preserving Documents and Electronically Stored Information Toolkit on Practical Law.)
When the Duty to Preserve Begins and Ends
The general duty to preserve potential evidence in federal litigation is a creature of federal common law, even though some federal statutes impose preservation obligations on certain individuals and entities (see, for example, U.S. Dep’t of Labor v. Fed. Armament, LLC, 2022 WL 2317275, at *3 (W.D. Ark. June 28, 2022) (noting the defendant’s statutory retention obligation); Brown v. Tellermate Holdings Ltd., 2014 WL 2987051, at *19 (S.D. Ohio July 1, 2014)).
An individual or entity generally has a duty to preserve evidence when the individual or entity reasonably anticipates litigation (see, for example, A.W.S. v. Southampton Union Free Sch. Dist., 2022 WL 1478736, at *6 (E.D.N.Y. Feb. 28, 2022); see also Hawkins v. Coll. of Charleston, 2013 WL 12145958, at *2 (D.S.C. Sept. 17, 2013) (citing Silvestri v. Gen. Motors Corp., 271 F.3d 583, 591 (4th Cir. 2001))).
(For a model document retention policy, with explanatory notes and drafting tips, see Document Retention Policy on Practical Law.) Nuance Among Federal Jurisdictions
Because courts incrementally develop the common law duty to preserve through case law, the test for whether an individual has a duty to preserve varies slightly among jurisdictions.
For example, the US Court of Appeals for:
• The Fifth Circuit requires an individual or entity to preserve potentially relevant evidence when it has “notice that the evidence is relevant to the litigation or should have known that the evidence may be relevant”
(Guzman v. Jones, 804 F.3d 707, 713 (5th Cir. 2015) (citing Rimkus Consulting Grp., Inc. v. Cammarata, 688 F. Supp. 2d 598, 612 (S.D. Tex. 2010))).
• The Seventh Circuit requires an individual or entity to preserve potentially relevant evidence when it knows or should know that litigation is imminent (Trask-Morton v. Motel 6 Operating L.P., 534 F.3d 672, 681 (7th Cir. 2008)).
• The Federal Circuit requires an individual or entity to preserve potentially relevant evidence when litigation is reasonably foreseeable (Micron Tech., Inc. v. Rambus Inc., 645 F.3d 1311, 1320 (Fed. Cir. 2011) (citing Silvestri, 271 F.3d at 590 and West v. Goodyear Tire & Rubber Co., 167 F.3d 776, 779 (2d Cir. 1999))).
(For more on each federal circuit court’s standard for when the duty to preserve arises, see Spoliation Sanctions by US Circuit Court Chart on Practical Law.)
Counsel must consider the specific facts and circumstances to determine when their client should reasonably anticipate litigation, thereby triggering the duty to preserve.
While jurisdiction-specific standards vary slightly, counsel should avoid relying on a narrow construction of any particular standard because:
Counsel often cannot predict with certainty: where a prospective plaintiff may file the anticipated litigation; and if the prospective plaintiff files the anticipated litigation in federal court under the court’s diversity jurisdiction, whether the court will apply the federal or state duty to preserve standard.
Spoliation sanctions, when issued, can be severe
(see Penalties for Violating the Duty to Preserve below).
Application of State Law Duty to Preserve Standards
When a spoliation claim arises, a federal court presiding over a case based on diversity jurisdiction must determine whether federal or state law governs the claim.
If the court determines that federal and state law lead to varying results, the court must determine whether spoliation is:
A procedural matter governed by federal law (see, for example, Silvestri, 271 F.3d at 590 (disregarding the parties’ agreement that state law controlled and applying federal law); Toste v. Lewis Controls, Inc., 1996 WL 101189, at *2 n.2 (N.D. Cal. Feb. 27, 1996)).
A substantive matter governed by the forum state’s law (see, for example, Rowe v. Albertsons, Inc., 116 F. App’x 171, 174-75 (10th Cir. 2004); ArcelorMittal Ind. Harbor LLC v. Amex Nooter, LLC, 2018 WL 509890, at *1 (N.D. Ind. Jan. 23, 2018) (collecting cases); Toste, 1996 WL 101189, at *2 n.2).
Because federal courts do not take a uniform approach regarding the law that governs duty to preserve issues, counsel should both:
Familiarize themselves with all potentially applicable standards regarding a litigant’s duty to preserve.
Develop a conservative preservation protocol to comply with the broadest- or furthest-reaching standard (for the complete version of this resource, which includes more on developing a preservation protocol, see Duty to Preserve Evidence (Federal) on Practical Law). (See, for example, Keller v. United States, 58 F.3d 1194, 1197 n.6 (7th Cir. 1995) (collecting cases).)
Triggering Events
Duty to preserve standards, whether considered generally or in a particular jurisdiction, do not provide a bright-line rule regarding when an individual’s or entity’s duty to preserve information arises.
Instead, counsel must consider the specific facts and circumstances to determine when their client should reasonably anticipate litigation, thereby triggering the duty to preserve.
For example, courts have held that an individual’s or entity’s duty to preserve arose when:
It decided to initiate litigation (see Apple Inc. v. Samsung Elecs. Co., 888 F. Supp. 2d 976, 997 (N.D. Cal. 2012)).
It received a letter threatening litigation (see Gonzalez-Bermudez v. Abbott Labs. PR Inc., 214 F. Supp. 3d 130, 162 (D.P.R. 2016)).
It was involved in prior litigation regarding the same subject matter (see Williams v. BASF Catalysts LLC, 2016 WL 1367375, at *7 (D.N.J. Apr. 5, 2016); Stinson v. City of New York, 2016 WL 54684, at *4 (S.D.N.Y. Jan. 5, 2016)).
It learned of related disputes between similarly situated parties in the same industry (see Phillip M. Adams & Assocs., L.L.C. v. Dell, Inc., 621 F. Supp. 2d 1173, 1190-91 (D. Utah 2009)).
A governmental agency initiated an enforcement action against it (see M & T Mortg. Corp. v. Miller, 2007 WL 2403565, at *5-6 (E.D.N.Y. Aug. 17, 2007)).
A potential plaintiff filed an accident report (see McCabe v. Wal-Mart Stores, Inc., 2016 WL 706191, at *2 (D. Nev. Feb. 22, 2016)).
(For more on when a party should reasonably anticipate litigation, see Reasonable Anticipation of Litigation Under FRCP 37(e): Triggers and Limits and Implementing a Litigation Hold on Practical Law.)
Who Has a Duty to Preserve
While most courts discuss a party’s or third party’s duty to preserve, some notable decisions emphasize that counsel also have a duty to preserve potentially relevant information.
Specifically, courts have noted that the duty to preserve “runs first to counsel” and further require counsel to advise the client regarding the client’s obligation to preserve potentially relevant information (see Indus. Quick Search, Inc. v. Miller, Rosado & Algois, LLP, 2018 WL 264111, at *10 (S.D.N.Y. Jan. 2, 2018) (collecting cases); see also Mooradian v. FCA US, LLC, 286 F. Supp. 3d 865, 870 (N.D. Ohio 2017)).
In a landmark decision, the US District Court for the Southern District of New York elaborated on counsel’s duty, holding that counsel must implement and oversee compliance with a litigation hold and monitor the client’s document production efforts (Zubulake v. UBS Warburg LLC, 229 F.R.D. 422, 432 (S.D.N.Y. 2004) (concluding that both counsel and the client must “make certain that all sources of potentially relevant information are identified and placed ‘on hold’”); see also Point Blank Sols., Inc. v. Toyobo Am., Inc., 2011 WL 1456029, at *12 (S.D. Fla. Apr. 5, 2011) (internal citations omitted)).
While most courts discuss a party’s or third party’s duty to preserve, some notable decisions emphasize that counsel also have a duty to preserve potentially relevant information.
Accordingly, counsel must take an active role in guiding clients during the entire preservation process.
To Whom a Party Owes the Duty to Preserve
To ascertain when a party first had a duty to preserve in the context of a motion for spoliation sanctions, some courts look at when the alleged spoliator first anticipated litigation with the party seeking sanctions (the movant), rather than when the alleged spoliator first anticipated litigation generally.
In other words, some courts recognize that, even for a single issue or incident, a party may have multiple duties to preserve that arise at different times and run to various potential adversaries.
Courts have addressed this issue when the movant advocates for a shifting duty to preserve by arguing that:
The alleged spoliator had a duty to preserve that arose when it reasonably anticipated that another entity (Adversary A) would initiate litigation against the alleged spoliator.
The duty that the alleged spoliator owed to Adversary A covered the same information that later became relevant in the present litigation between the movant and the alleged spoliator.
The alleged spoliator lost or destroyed the information that became relevant in the present litigation between the movant and the alleged spoliator:
while under a duty to preserve owed to Adversary A;
and before the alleged spoliator reasonably anticipated the present litigation with the movant.
The court should sanction the alleged spoliator in the present litigation.
Some courts reject this shifting duty concept.
These courts reason that the movant does not have standing to assert a spoliation claim because, at the time that the alleged spoliator lost or destroyed the evidence, the alleged spoliator owed a duty to Adversary A but not to the movant (see, for example, Rockman Co. (USA), Inc. v. Nong Shim Co., 229 F. Supp. 3d 1109, 1123 (N.D. Cal. 2017) (holding that the initiation of a government investigation does not create for the target of the investigation a duty to preserve to other, non-governmental individuals or entities);
In re Delta/Airtran Baggage Fee Antitrust Litig., 2015 WL 4635729, at *11 (N.D. Ga. Aug. 3, 2015) (holding that the receipt of a government subpoena did not trigger a duty to preserve owed to or enforceable by the plaintiffs in later civil litigation); Brigham Young Univ. v. Pfizer, Inc., 282 F.R.D. 566, 572 (D. Utah 2012)).
However, some courts may take a more liberal view and sanction parties for spoliation when the party generally anticipated litigation, regardless of whether the party anticipated litigation with the movant specifically (see, for example, Williams, 2016 WL 1367375, at *7 (noting that the duty to preserve generally runs to a specific party but holding that the case was an instance in which prior litigation with other similarly situated entities sensitized the defendant to the possibility of future, similar lawsuits); M & T Mortg. Corp., 2007 WL 2403565, at *5-6).
When the Duty to Preserve Ends
The standards governing when a duty to preserve arises generally also dictate when it ends.
Therefore, when an individual or entity no longer reasonably anticipates litigation, the individual or entity no longer has a duty to preserve.
At least one court has found that because a party did not lift its litigation hold, its duty to preserve persisted (see Moore v. Gilead Scis., Inc., 2012 WL 669531, at *4 n.2 (N.D. Cal. Feb. 29, 2012) (finding the conclusion of a government investigation irrelevant to the determination of whether a party had a continuing duty to preserve when the party did not lift its litigation hold)).
To avoid this result, counsel should promptly lift (or advise their client to lift) a litigation hold when counsel determine that the client should no longer anticipate litigation.
While lifting a litigation hold is not sufficient to terminate a duty to preserve, a court may find it to be either:
A necessary step for termination.
Evidence that the preserving party considered the issue and determined that it no longer anticipated additional litigation.
(For more on when counsel may lift a litigation hold, see Reasonable Anticipation of Litigation Under FRCP 37(e): Triggers and Limits on Practical Law; for a model litigation hold lift notice, with explanatory notes and drafting tips, see Litigation Hold Lift Notice on Practical Law.)
Information Subject to the Duty Preserve
An individual or entity with a duty to preserve need not preserve all information.
Rather, the duty to preserve generally extends only to information that:
Is unique.
Is in the individual’s or entity’s possession, custody, or control (for more information, see Possession, Custody, and Control of ESI in Federal Civil Litigation on Practical Law; but see La Belle v. Barclays Cap. Inc., 340 F.R.D. 74, 84 (S.D.N.Y. 2022) (holding that a corporate party had a duty to search employees’ personal devices once it became aware that employees used the devices for business purposes); Woods v. Scissons, 2019 WL 3816727, at *4 (D. Ariz. Aug. 14, 2019) (holding that the City of Prescott had a duty to preserve ESI that the city police department controlled where an individual police officer was the sole defendant and imputing the city’s spoliation to the individual defendant)).
The individual or entity knows (or should know) is:
relevant in the anticipated litigation;
reasonably calculated to lead to the discovery of admissible evidence;
reasonably likely to be requested during discovery; or the subject of pending discovery.
(See Zubulake v. UBS Warburg LLC, 220 F.R.D. 212, 217 (S.D.N.Y. 2003) (internal citations omitted); see also EPAC Techs., Inc. v. HarperCollins Christian Publ’g, Inc., 2018 WL 1542040, at *17 (M.D. Tenn. Mar. 29, 2018); Harbor v. Cherniss, 2017 WL 2472242, at *2 (E.D. Cal. June 8, 2017); Czuchaj v. Conair Corp., 2016 WL 4161818, at *1 (S.D. Cal. Apr. 1, 2016).)
The scope of information that falls under a party’s duty to preserve varies slightly among jurisdictions, but counsel should avoid construing any particular standard too narrowly (see Nuance Among Federal Jurisdictions above).
For example, even if a party expects to litigate an anticipated lawsuit in a federal court where the federal common law provides a narrow duty to preserve, counsel should consider advising their client to preserve broadly to minimize the risk of sanctions.
(For more on each federal circuit court’s standard regarding when the duty to preserve arises, see Spoliation Sanctions by US Circuit Court Chart on Practical Law.)
Obligation to Preserve Multiple Copies or Versions of Documents
Several jurisdictions explicitly require an individual or entity to preserve only unique documents (including ESI), which relieves the individual or entity from having to preserve multiple copies of potentially relevant documents (see, for example, Marshall v. Dentfirst, P.C., 313 F.R.D. 691, 697 (N.D. Ga. 2016) (citing In re Ethicon, Inc. Pelvic Repair Sys. Prod. Liab. Litig., 299 F.R.D. 502, 517-18 (S.D. W. Va. 2014)); Victor Stanley, Inc. v. Creative Pipe, Inc., 269 F.R.D. 497, 524 (D. Md. 2010) (citing Zubulake, 220 F.R.D. at 217)).
However, counsel and the client must exercise caution when deciding not to preserve one or more copies or versions of seemingly duplicative documents and should carefully consider whether the documents are truly duplicative (see, for example, Point Blank Sols., Inc., 2011 WL 1456029, at *11 (noting that “determining what constitutes an ‘identical’ copy which need not be retained is not always a simple analysis”)).
For example, an individual may possess a relevant contract as:
A word processing file (such as a Microsoft Word file) with metadata that reflects, in part, when the author drafted and edited the contract.
A PDF (image) file with metadata that reflects when the PDF was generated from the word processing file.
A hard copy with no metadata.
While all three items appear identical on their faces, they differ significantly in terms of their associated metadata.
If counsel treat them as duplicative and advise their client to preserve only the PDF or hard copy version, an opposing party may later accuse the client of spoliation if the word processing file’s metadata is relevant to the dispute.
If a client maintains multiple copies of a document that it must preserve and does not want to preserve all copies, counsel should either:
Advise the client to preserve the most robust version of the document, such as the native file.
If the client prefers to preserve only a less robust version of the document (for example, because the expense to locate and preserve the the native file is burdensome), ask all opposing parties to agree in writing not to seek the additional metadata available only in the most robust version.
Parties may willingly accept a less robust version of a duplicative document if that same concession is reciprocal (that is, if they too may produce a readily available version of a duplicative document, even if other, more robust versions exist).
Applicability of the Proportionality Principles to Preservation
The proportionality principles that govern discovery in federal civil litigation do not explicitly apply to the scope of a party’s duty to preserve information (Federal Rule of Civil Procedure (FRCP) 26(a)(1); 2015 Advisory Committee’s Note to FRCP 37(e) (explaining that FRCP 37(e) does not establish a duty to preserve but instead is based on the common law duty to preserve)).
However, some courts have extended the proportionality principles to a party’s duty to preserve information (see Victor Stanley, Inc., 269 F.R.D. at 523 (noting, critically, that few courts consider proportionality when analyzing the scope of the duty to preserve and collecting cases); see also Wai Feng Trading Co. v. Quick Fitting, Inc., 2019 WL 118412, at *5 (D.R.I. Jan. 7, 2019) (citing the 2015 Advisory Committee’s Note to FRCP 37(e) for the proposition that proportionality is relevant to the determination of whether the individual or entity took reasonable steps to preserve ESzI); Al Otro Lado, Inc. v. Nielsen, 328 F.R.D. 408, 416 (S.D. Cal. 2018) (noting that the scope of the duty to preserve is coextensive with the scope of discovery under FRCP 26, including the proportionality limitations)).
These courts’ positions are well founded because the duty to preserve is connected to the discovery process.
Specifically:
The federal common law duty to preserve standards almost all define their respective scopes in terms of potential evidence.
Information cannot be evidence if it is not first discoverable. Information is not discoverable if the process to produce it is disproportionate to the litigation (FRCP 26(b)(1)).
However, it is risky to exclude potentially relevant information from a preservation protocol based on a unilateral determination that it is not discoverable (such as due to proportionality concerns, inaccessibility, or other factors that may exclude documents from discovery).
For example, the requesting party may later:
Request the subject information in discovery.
Contest the responding party’s proportionality-based objection to its discovery request.
Move the court to resolve the proportionality question and compel the responding party to produce the subject information.
If the court compels the responding party to produce the subject information and the responding party has since destroyed or otherwise lost the information because the responding party did not take care to preserve it, the court may sanction the responding party for spoliation (see Penalties for Violating the Duty to Preserve below).
To safely exclude potentially relevant information from a preservation protocol, counsel should proactively reach out to opposing counsel to seek agreement on the exclusion of specific, potentially relevant information from the preservation protocol.
If counsel cannot secure an explicit, documented agreement permitting a party to exclude a subset of potentially relevant information from its preservation efforts, they generally should:
Advise their client to err on the side of preserving potentially relevant information.
Remind clients that preservation does not obligate production and they may object to producing preserved information due to proportionality concerns or otherwise.
Reassessing the Scope of the Duty to Preserve
Counsel’s expectation about what information is relevant may change over the course of litigation (for example, as new parties become involved or as existing parties assert and abandon various claims).
As the scope of litigation changes, so too does the scope of information that counsel and the client must preserve (see, for example, La Belle, 340 F.R.D. at 84 (holding that a corporate party’s duty to preserve initially did not extend to employees’ personal devices but later expanded to include these personal devices)).
Counsel and their clients should remain aware of their preservation obligations and efforts throughout a case and make adjustments as necessary.
Penalties for Violating the Duty to Preserve
Preservation-related penalties are among the most severe penalties that courts issue.
Depending on the relevant jurisdiction and conduct at issue, a party adversely affected by another individual’s or entity’s loss of potentially relevant information may:
Move the court to sanction the alleged spoliator for its failure to fulfill its duty to preserve.
Assert an independent cause of action against the alleged spoliator.
Spoliation Sanctions
Courts may sanction parties for failing to preserve potentially relevant information.
Because federal courts classify spoliation sanctions as an evidentiary issue related to their inherent authority to manage litigation, they apply federal procedural rules and federal common law when determining:
If sanctions are warranted.
Which sanction is appropriate. (See, for example, Adkins v. Wolever, 554 F.3d 650, 652 (6th Cir. 2009); Hodge v. Wal-Mart Stores, Inc., 360 F.3d 446, 449 (4th Cir. 2004); Reilly v. Natwest Mkts. Grp. Inc., 181 F.3d 253, 267 (2d Cir. 1999); Glover v. BIC Corp., 6 F.3d 1318, 1329 (9th Cir. 1993).)
FRCP 37(e)(2)dictates the type of sanctions a court may issue in various scenarios, with more severe sanctions available if the spoliating party acted with the intent to deprive the requesting party of the lost ESI.
When identifying the applicable standard for sanctions for a particular case, counsel should consider that:
FRCP 37(e) governs a party’s ESI spoliation in all federal courts.
Each circuit’s unique common law governs a party’s loss or destruction of hard copy documents and other tangible evidence.
(For more on cases in which courts have sanctioned parties for spoliation, see Document Discovery Case Tracker:
Sanctions and Cost Recovery on Practical Law.)
ESI Loss
A federal court may sanction an individual or entity for ESI spoliation when the individual or entity:
Has a duty to preserve ESI.
Does not take reasonable steps to preserve relevant ESI.
Loses the ESI.
Cannot restore or replace the lost ESI through additional discovery.
(FRCP 37(e); 2015 Advisory Committee’s Note to FRCP 37(e).)
FRCP 37(e)(2) dictates the type of sanctions a court may issue in various scenarios, with more severe sanctions available if the spoliating (responding) party acted with the intent to deprive the requesting party of the lost ESI (for more on the requisite intent, see Sanctions for ESI Spoliation Under FRCP 37(e):
Overview on Practical Law).
However, some courts continue to sanction parties for ESI spoliation even when the challenged conduct does not prejudice another party under FRCP 37(e)(1) or meet the requisite intent under FRCP 37(e)(2).
In these cases, courts rely on their inherent authority to sanction a party for ESI spoliation, regardless of FRCP 37(e)’s limitations on:
What conduct is sanctionable.
Which sanctions are permissible in various contexts.
(For more on ESI spoliation sanctions, see Sanctions for ESI Spoliation Under FRCP 37(e): Overview and FRCP 37(e) ESI Spoliation Sanctions Flowchart on Practical Law.)
Loss of Hard Copy Documents or Other Tangible Items
There is no procedural rule specifying when a federal court may sanction a party for losing or destroying hard copy documents or other tangible items.
Rather, each circuit has defined through case law when a court may sanction a party for spoliating non-ESI.
For example:
The Second Circuit permits a court to issue an adverse inference sanction when it finds that the spoliating party acted negligently (see Best Payphones, Inc. v. City of New York, 2016 WL 792396, at *4 (E.D.N.Y. Feb. 26, 2016) (distinguishing between the applicable standard for tangible evidence and ESI and citing Residential Funding Corp. v. DeGeorge Fin. Corp., 306 F.3d 99, 108 (2d Cir. 2002)); but see Aquino v. Alexander Cap., LP, 2023 WL 2751541, at *8 (S.D.N.Y. Mar. 31, 2023) (generally holding that FRCP 37(e) superseded Residential Funding Corp. without addressing the distinction between tangible evidence and ESI)).
The Tenth Circuit requires a court to find that an entity acted in bad faith before issuing an adverse inference sanction (see Aramburu v. Boeing Co., 112 F.3d 1398, 1407 (10th Cir. 1997)).
(For more on the types of sanctions and standards of culpability in federal circuit courts for spoliation of non-ESI, see Spoliation Sanctions by US Circuit Court Chart on Practical Law.)
Spoliation Cause of Action
While the FRCP and federal common law provide for procedural sanctions against a spoliating party in federal civil litigation, no federal authority recognizes an independent cause of action for spoliation of evidence (see Silvestri, 271 F.3d at 590; Aspen Am. Ins. Co. v. Interstate Warehousing, Inc., 372 F. Supp. 3d 709, 724 (N.D. Ind. 2019); ABC Bus. Forms, Inc. v. Pridamor, Inc., 2009 WL 4679477, at *3 (N.D. Ill. Dec. 1, 2009); Lombard v. MCI Telecomms. Corp., 13 F. Supp. 2d 621, 627 (N.D. Ohio 1998)).
However, some states recognize a substantive, independent tort cause of action against individuals or entities that destroy or lose potentially relevant information, and parties sometimes pursue those state law claims in federal court
• (see, for example, Unigard Sec. Ins. Co. v. Lakewood Eng’g & Mfg. Corp., 982 F.2d 363, 367 (9th Cir. 1992)
• (presiding over the case under its diversity jurisdiction and noting that state law controlled the spoliation counterclaim); Lord v. Flanagan, 2014 WL 715714, at *1 (D. Mont. Feb. 24, 2014) (permitting the plaintiff to amend his complaint to assert state law spoliation claims); Cummerlander v. Patriot Preparatory Acad., 2013 WL 5969727, at *2 (S.D. Ohio Nov. 8, 2013) (holding that federal law governs spoliation sanctions and state law governs any spoliation cause of action)).
For example, some states permit an individual harmed by the loss of evidence (spoliation plaintiff) to assert a spoliation claim against:
Only a third-party spoliator (namely, a spoliator that is not a party to the underlying litigation).
• Examples include:
• Florida (see Kimball v. Publix Super Mkts., Inc., 901 So. 2d 293, 296 (Fla. 2d DCA 2005);
• Lincoln Ins. Co. v. Home Emergency Servs., Inc., 812 So. 2d 433, 434 (Fla. 3d DCA 2001));
• Alabama (see Smith v. Atkinson, 771 So. 2d 429, 438 (Ala. 2000)); and Montana (see Oliver v. Stimson Lumber Co., 993 P.2d 11, 18 (Mont. 1999)).
Either a third-party spoliator or a first-party spoliator (that is, a spoliator that is a party to the underlying litigation).
Examples include:
• Ohio (see Smith v. Howard Johnson Co., 615 N.E.2d 1037, 1038 (Ohio 1993));
• Connecticut (see Diana v. NetJets Servs., Inc., 974 A.2d 841, 845 (Conn. Super. Ct. 2007); Rizzuto v. Davidson Ladders, Inc., 905 A.2d 1165, 1173 (Conn. 2006));
• West Virginia (see Williams v. Werner Enters., Inc., 770 S.E.2d 532, 538 (W. Va. 2015));
• and Alaska (see Nichols v. State Farm & Cas. Co., 6 P.3d 300, 303 (Alaska 2000)).
States recognizing an independent tort claim for spoliation of evidence also vary regarding whether:
A spoliation plaintiff may prevail in a spoliation cause of action by proving that the spoliator acted negligently or whether the spoliation plaintiff must prove intentional spoliation.
The alleged spoliator must have some independent relationship with or obligation to the spoliation plaintiff (such as a contractual relationship).
The spoliation plaintiff must wait until the underlying litigation concludes to assert the spoliation claim.
When state law applies, counsel should carefully review the forum state’s law on the issue.
Adverse Inference Sanctions for Evidence Spoliation under Labor Law §240(1): Insights from Yi Jiang Pai v. Nelson Senior Housing Development Fund Corp. Date: Nov 24, 2024
Introduction
The case of Yi Jiang Pai, et al. v. Nelson Senior Housing Development Fund Corporation, et al. (2024 N.Y. Slip Op. 5816) adjudicated by the Supreme Court of New York, Second Department, marks a significant development in the application of sanctions for evidence spoliation under Labor Law §240(1).
This commentary delves into the background of the case, the pivotal legal issues at play, the parties involved, and the court's ultimate decision, offering a comprehensive analysis of its implications for future litigation.
Summary of the Judgment

In this personal injury action, the plaintiff, Yi Jiang Pai, an employee of KJ Kwok Construction, Inc. (the third-party defendant), sustained injuries after falling from a ladder while inspecting a newly installed fire sprinkler system.
The incident purportedly occurred due to the unexpected collapse of an A-frame ladder, leading to Yi's fall and subsequent head injury.
The plaintiffs sought damages alleging common-law negligence and violations of Labor Law §§200, 240(1), and 241(6).
Concurrently, the defendants sought summary judgments to dismiss these claims and impose sanctions for spoliation of evidence.
The Supreme Court initially denied the plaintiffs' motions for summary judgment on liability and sanctions, citing the existence of triable issues concerning the ladder's condition and its role in the accident.
On appeal and cross-appeal, the higher court modified the lower court's order by substituting the denial of sanctions with an instruction for an adverse inference against the defendants regarding the spoliated elbow joint pipe.
The appellate court affirmed the initial order in all other aspects, ruling that while the spoliation did not warrant severe sanctions like striking the pleadings, an adverse inference was appropriate given the circumstances.
Analysis
Precedents Cited
The court extensively referenced previous case law to underpin its decision, particularly focusing on the standards for imposing sanctions for evidence spoliation and the application of Labor Law §240(1).
Zholanji v. 52 Wooster Holdings, LLC:
Established the nondelegable duty and absolute liability standards under Labor Law §240(1), emphasizing that proper safety devices are paramount when their failure is a proximate cause of injury.
Melchor v. Singh and Cioffi v. Target Corp.:
Clarified that liability under Labor Law §240(1) hinges on whether a safety device failed without apparent reason or was inadequately secured, making the protection provided by such devices a factual question.
Valentin v. Stathakos:
Highlighted that unexpected collapses of scaffolds or ladders during regulated activities create a presumption of inadequate protection, shifting the burden to the defense to prove the contrary.
JENNOSA v. VERMEER MFG. Co. and Dagro Assoc. II, LLC v. Chevron U.S.A., Inc.:
Provided guidance on appropriate sanctions for spoliation, distinguishing between severe sanctions like striking pleadings and lesser ones like adverse inference instructions based on the prejudicial impact of the spoliation.
Legal Reasoning
The court's legal reasoning centered on two main pillars: the negligent provision of safety devices under Labor Law §240(1) and the appropriate sanctions for evidence spoliation.
Regarding Labor Law §240(1), the court reaffirmed that employers and general contractors have a nondelegable duty to provide adequate safety measures. In this case, the plaintiffs demonstrated a prima facie case by showing that the ladder collapsed without apparent reason, invoking the presumption of inadequate protection. However, the defense contested this by introducing factual disputes about the ladder's condition and stability, thereby justifying the denial of summary judgment on liability.
On the issue of spoliation, the appellate court evaluated the extent to which the loss of the elbow joint pipe affected the plaintiffs' ability to prove their case.
Recognizing that the spoliated evidence was not central enough to warrant the most severe sanction, the court opted for the imposition of an adverse inference instruction.
This approach balances the need to penalize wrongful evidence handling without unduly prejudicing the non-responsible party.
Impact
This judgment has significant implications for future litigations involving Labor Law §240(1) and evidence spoliation:
Clarification of Safety Device Liability:
The case reinforces the strict liability standards under Labor Law §240(1), making it clear that unexpected failures of safety devices can lead to liability, but also emphasizes the role of factual disputes in precluding summary judgments.
Balanced Approach to Spoliation Sanctions:
By opting for adverse inference rather than severe sanctions like striking pleadings, courts may adopt a more nuanced approach to handling evidence spoliation, assessing the extent of prejudice before determining the appropriate sanction.
Encouragement of Evidence Preservation:
The decision underscores the importance of preserving evidence, particularly in cases alleging safety violations, thereby encouraging parties to maintain meticulous records and handle evidence responsibly.
Lawyers will need to be more vigilant in both securing safety-related evidence in labor disputes and understanding the potential ramifications of evidence spoliation, considering that courts may impose varying levels of sanctions based on the context and impact of the spoliation.
Complex Concepts Simplified
Labor Law §240(1)
This statute imposes a strict, nondelegable duty on employers and general contractors to provide safety devices that protect workers from inherent risks at elevated work sites. "Nondelegable" means that employers cannot escape this responsibility by assigning it to another party. If a safety device fails and causes injury, the employer is automatically liable, unless they can prove otherwise, making this a high-stakes regulation for workplace safety.
Evidence Spoliation
Spoliation refers to the intentional or negligent destruction, alteration, or failure to preserve evidence relevant to a legal proceeding.
Courts view spoliation seriously because it can undermine the fairness of the trial.
Sanctions for spoliation can range from minor penalties, like drawing an adverse inference (where the court assumes the destroyed evidence was unfavorable to the responsible party), to more severe measures, such as dismissing the offending party's claims or defenses.
Adverse Inference Instruction
This is a court directive where the judge informs the jury that they may infer that the lost or destroyed evidence was unfavorable to the party responsible for its spoliation.
It's a middle-ground sanction that penalizes the offending party without imposing the harshest possible penalties.
Conclusion
The Supreme Court of New York's decision in Yi Jiang Pai v. Nelson Senior Housing Development Fund Corp. serves as a pivotal reference point in the landscape of occupational safety litigation and evidentiary responsibilities. By upholding the strict liability framework of Labor Law §240(1) while advocating for proportionate sanctions in cases of evidence spoliation, the court strikes a balance between enforcing workplace safety and ensuring fair trial standards. This case underscores the essential duty of employers to maintain robust safety measures and the judiciary's role in mitigating the impacts of evidence mishandling, thereby shaping future legal strategies in similar disputes.
Case Details
Yi Jiang Pai, et al., appellants-respondents, v. Nelson Senior Housing Development Fund Corporation, et al., defendants, L. Riso & Sons, Co., Inc., defendant third-party plaintiff-respondent- appellant, Excelsior II Housing Development Fund Corporation, et al., defendants-respondents-appellants; KJ Kwok Construction, Inc., et al., third-party defendants-respondents. Year: 2024
Court: Supreme Court of New York, Second Department
Judge(s)
Joseph J. Maltese
Attorney(S)
Morelli Law Firm PLLC, New York, NY (David L. Sobiloff and Sara A. Mahoney of counsel), for appellants-respondents. Gallo Vitucci Klar LLP, New York, NY (Yolanda L. Ayala and James Drexler of counsel), for defendant third-party plaintiff-respondent-appellant and defendants-respondents-appellants. Linda A. Stark, New York, NY, for third-party defendant-respondent KJ Kwok Construction, Inc. Vigorito, Barker, Patterson, Nichols & Porter, LLP, Garden City, NY (Douglas Langholz of counsel), for third-party defendant-respondent VIS Industries.
0 notes
Text
Must-Have Properties of an Email Archiving Solution
Exploring the essential properties of the modern-day email archiving solutions that every business must have
Emails have been an indispensable component of our everyday lives since their inception. And, because of the COVID-19 pandemic, it became even more vital for the suddenly remote workforce. So much so that in 2020, 306.4 billion emails were sent and received globally every day. However, corporations' number one communication and collaboration tool is fraught with difficulties due to the lack of proper email governance.
Most of these problems involve maintaining regulatory compliance, email archiving, and avoiding costly enforcement proceedings. And, as regulatory standards change, emails are becoming increasingly scrutinized, making it no longer appropriate to save correspondence for years just in case. Furthermore, new consumer data privacy requirements such as GDPR, CCPA, CDPA, NYDFS, LGPD, CPPA, and others are simply the latest reasons why capturing, indexing, monitoring, and overall good email governance is no longer just an option – they are essential.
Capturing
Since emails contain a variety of data sources, including the subject, body, recipients, metadata, and more, it is critical to collect all of them for successful compliance-driven email archiving. Organizations can capture and archive all current outgoing and incoming emails and previous email data by employing numerous collection techniques such as journaling, mailbox synchronization, and file uploads based on retention regulations.
Common Repository
However, multiple silos of preserved email data create their own set of issues and are inefficient. By centralizing email capture into a single repository, companies not only get assurance that they know exactly where all their emails are, but they also make administration and maintenance tasks much easier and only need to be completed once.
Indexing Metadata
Comprehensive capture and indexing of all email content and attachments are required to support compliance-driven email archiving. Search and retrieval are only as good as the indexing process, which must be capable of producing catalogs that show where search records are stored and what data is contained in the records.
Classifying, Tagging and Monitoring
Custom archive policies that tag emails enable near-real-time classification and monitoring based on email content, metadata, or the existence of sensitive material. Trigger alerts may be set up to inform specific teams based on predefined criteria and assure a quick response. As needed, add more tags to emails. All of this helps you stay compliant, track unwanted behaviors, and make future emails easily discoverable for speedier compliance.
Retention and Legal Hold
To assist with rapid and successful eDiscovery, compliance and legal teams must be able to implement complete retention rules readily and legal holds at the organization, user, email, or metadata level – a capability prominently seen in email and communication archiving solutions.
Search and eDiscovery
When keywords or multiple filters are available to identify emails of interest, compliance and legal teams rapidly will be able to do faster and more effective e-discovery searches across all inboxes. Such search capacity is required if retention, legal hold, tags, or comments need to be added to the detected emails. They will also be able to save one or all the emails found during the search to a case folder for future reference and download them in typical industry formats to meet legal demands.
Compliance scrutiny is expected to expand as regulatory enforcements over financial information, healthcare records, and now consumer data privacy increase. Organizations with limited or no corporate email archiving solutions face costly penalties and reputation damage because of compliance violations. By creating a plan to collect and archive all email content with ILM, legal hold, and retention regulations, effective eDiscovery, search, and access are incorporated by design, lowering compliance risk.
0 notes
Text
eDiscovery Market Growth Opportunities, Statistics, Segment, Trends, Size, Share, Type, Demand and Forecast 2021 to 2031
eDiscovery is a set of interlinked processes consisting of preserving, collecting, reviewing, and exchanging information stored in electronic formats. These formats, universally known as electronically stored information (ESI), are used by parties to furnish evidence or in response to production in various legal proceedings such as litigations, government investigations, and right to information requests. Different types of ESI may include a wide spectrum of sources such as emails, documents, audio and video files, company-specific databases, social media content, encrypted data, and cloud-based storage.
With the proliferation of data from myriad sources, including cloud computing devices and platforms, the processes are rather complex. Since electronic documents essentially contain metadata, they may be the source of various information: the date and time the file was created, information on authors and recipients, and file properties.
Read more : https://www.tmrresearch.com/ediscovery-market
Get Brochure : https://www.tmrresearch.com/sample/sample?flag=B&rep_id=1667
0 notes
Text
[Webinar] Session One: Using Project Management Processes to Decipher Legal Team Requests to Litigation Support August 9th 4:30 pm 5:30 pm PDT | Association of Certified E-Discovery Specialists (ACEDS)
August 9th, 2022 4:30 PM – 5:30 PM PDT About this event Join us for Session ONE of Association of Certified E-Discovery Specialists (ACEDS) San Diego Chapter, the San Diego Paralegal Association and the Los Angeles Paralegal Association eDiscovery 2022 Summer Refresher Virtual Conference. Presented by Melissa Weberman, Lead Attorney & Managing Director of Arnold & Porter’s eDiscovery + Data Analytics (“eData”) Group, in which she counsels clients in eDiscovery and information governance processes and best practices. Melissa works closely with Arnold & Porter’s lawyers across practice groups to tailor strategies and discovery management plans for clients in numerous industries. Melissa advises clients on defensible approaches to the preservation, collection, search, and analysis of information and data, and is experienced with technology-assisted review and other methods to enable clients to significantly reduce costs while maintaining defensibility. Greg Jordan is Arnold & Porter’s Director of Discovery Operations and consults regularly with legal teams regarding the best use of available technology to manage document-intensive litigation matters from discovery through trial. With over 30 years of experience in the field of litigation support, Greg brings a wealth of knowledge and unique perspective to his position and works to implement a common sense approach to matter management ensuring a cost-effective and client oriented outcome. *Attendees are eligible for One Hour of CA MCLE – Courtesy of San Diego Paralegal Association https://ift.tt/ikbMSqc https://ift.tt/NyvOlT9
#Saas#softwaresystems#productdevelopment#software#practice#optimization#accuracy#efficiency#productivity#softwareprojects#cracksthecode
0 notes
Text
eDiscovery Market Trends Forecast and Industry Analysis to 2030
Global eDiscovery Market: Snapshot
The research report on the global eDiscovery market indicates that the industry grew exponentially over the forecast period and increased its value from the initial evaluation of US$ 9.3 billion in the year 2020.
Download PDF Brochure
The professional survey study also predicts that the global eDiscovery market will expand at a major growth rate of 6.6 % over the forecast period i.e. 2020 to 2025.
The major types of solutions offered by the manufacturers and players in the global eDiscovery market include various essential services as well as software solutions, such as review and analysis, preservation and collection, presentation and production, processing, and identification, among others.
Some of the major drivers for the growth within the global eDiscovery market include the rising number of litigations across the world, the rise in the social media penetration as well as ESI penetration, and the presence of shifting regulatory policies.
On the other hand, the rising risks of data theft activities as well as increasing instances of cyberattacks may hamper the growth within the global eDiscovery market in coming years.
Furthermore, the high cost associated with maintenance, installation, and investment may hinder the growth within the global eDiscovery market in coming years.
However, the increasing focus on proactive governance utilizing data analytics as well as the advent of novel content sources may fuel the demand within the global eDiscovery market in coming years.
Additionally, the advent of artificial intelligence predictive coding as well as analytics in the global eDiscovery market may also aid in the expansion and development of the industry.
The products and solutions offered by the manufacturers and players operational in the global eDiscovery market are used across various end use industries, such as legal, energy and utilities, retail and consumer goods, IT and telecommunications, government and public sector, BFSI, healthcare and life sciences, and manufacturing, among others.
eDiscovery solutions and services help organizations to facilitate their business procedures. eDiscovery solutions allow users to exchange, review, collect, and preserve information stored in electronic formats. These are used across various industrial segments such as education, manufacturing, retail, media and entertainment, transportation and logistics, travel and hospitality, energy and utilities, IT and telecom, healthcare, insurance (BFSI), financial services, banking, and legal. Increase in mobile device penetration and usage, stringent compliance with policies and regulations worldwide, global increase in litigations, and focus on decreasing operational budget of legal departments are few of the factors driving the global eDiscovery market.
To provide enhanced eDiscovery solutions, various players operating in this market are undertaking partnerships and are focusing on mergers and acquisition to expand their footprint. For instance in Feb 2017, Compliance Discovery Solutions, a prominent player providing integrated eDiscovery services, partnered with another CloudNine. This partnership was intended to integrate the technologies of both companies to provide improved solutions to the customers. Other prominent players in this market include FTI Consulting, Inc., Catalyst Repository Systems, Inc., Integreon Managed Solutions, Inc., Epiq Systems, Inc., Symantec Corporation, Guidance Software, Inc., EMC Corporation, IBM Corporation, Daegis, Inc., and HP Autonomy.
Due to emergence of digitalization, organizations all over the world are adopting cloud deployment model for better performance of eDiscovery solutions. Cloud deployment allows companies to reduce cost associated with maintenance and required IT infrastructure. Furthermore, as cloud deployment allows players to provide solutions to any part of world, various players are focusing on developing this segment.
Global eDiscovery Market: Overview
eDiscovery is a set of interlinked processes consisting of preserving, collecting, reviewing, and exchanging information stored in electronic formats. These formats, universally known as electronically stored information (ESI), are used by parties to furnish evidence or in response to production in various legal proceedings such as litigations, government investigations, and right to information requests. Different types of ESI may include a wide spectrum of sources such as emails, documents, audio and video files, company-specific databases, social media content, encrypted data, and cloud-based storage.
With the proliferation of data from myriad sources, including cloud computing devices and platforms, the processes are rather complex. Since electronic documents essentially contain metadata, they may be the source of various information: the date and time the file was created, information on authors and recipients, and file properties.
Global eDiscovery Market: Trends
The increasing application of eDiscovery solutions by several government agencies for conducting investigations, coupled with the worldwide rise in litigations that mandate the use of ESI as evidence, has propelled the global market. The soaring need for proactively using eDiscovery processes as part of risk mitigation strategies in numerous organizations is expected to fuel the market over the forecast period. The rapidly rising volume of data across enterprises has triggered the need for eDiscovery platforms and services.
In contrast, the high cost of eDiscovery services is likely to impede the market to an extent. However, the popularity of cost-effective on-premises services is anticipated to boost the market. The upsurge in the use of social media tools such as Twitter, Facebook, and LinkedIn in a large number of organizations is also expected to create ample opportunities for market players.
Global eDiscovery Market: Market Potential
An assessment of recent competitive dynamics indicates the emergence of automated solutions and advanced technologies aimed at simplifying the workflow of eDiscovery projects. Automation solutions are increasingly being demanded by several law firms and corporate users to accelerate eDiscovery processes.
Recently, Compliance Discovery Solutions, a pioneer in offering integrated eDiscovery services, partnered with CloudNine, an eDiscovery automation software company, for technology integration. The agreement entails integration of CloudNine’s eDiscovery automation technology with the best-of-breed discovery-as-a-service (DaaS) offering provided by Compliance. The partnership is significant as CloudNine customers can conveniently access the intuitive DaaS environment. This will help them simplify eDiscovery workflows spanning across routine audits to complex technologies. Using the tool, the user can accelerate the uploading and processing of ESI without making any additional investment in dedicated servers, hardware, and software.
In yet another promising development, Veritas Technologies, a leading information management company, announced its plan to expand its partnership with Google to provide customers access to increased capabilities of its 360 Data Management capabilities. Furthermore, the partnership will ensure the clients’ readiness to eDiscovery solutions. In addition, the company has announced a set of innovative solutions with Google Cloud, which will offer users extensive eDiscovery support for its G Suite Enterprise offering.
Global eDiscovery Market: Regional Outlook
North America is a prominent market for eDiscovery solutions and platforms. The market is expected to witness impressive growth along the forecast period. The growth is attributed to stringent compliances across enterprises to preserve data and the rising inclination of various government agencies toward the adoption of eDiscovery solutions. In addition, the increasing emphasis of law enforcement agencies to make attorneys and lawyers familiar with ESI in the U.S. has spurred the demand for eDiscivery offerings. Furthermore, the launch of intuitive and interactive solutions on varied cloud models is expected to propel the regional market.
However, in the coming years, the regional market may lose some revenue to emerging markets such as Asia Pacific and South Africa. The rapid pace of industrialization in Asia Pacific has spurred the usage of mobile devices in enterprises, catapulting the need for managing ESI and boosting the regional market.
Global eDiscovery Market: Competitive Landscape
Leading vendors are making partnerships and entering into agreements with global technology companies to consolidate their market shares. Several players are offering cloud-based solutions to gain a stronghold in the market. Major companies operating in eDiscovery market include HP Autonomy, Daegis, Inc., IBM Corporation, EMC Corporation, Guidance Software, Inc., Symantec Corporation, Epiq Systems, Inc., Integreon Managed Solutions, Inc., Catalyst Repository Systems, Inc., and FTI Consulting, Inc.
Download TOC
About Us:
TMR Research is a premier provider of customized market research and consulting services to business entities keen on succeeding in today’s supercharged economic climate. Armed with an experienced, dedicated, and dynamic team of analysts, we are redefining the way our clients’ conduct business by providing them with authoritative and trusted research studies in tune with the latest methodologies and market trends.
Contact Us:
Rohit Bhisey
Head Internet Marketing
Tel: +1-415-520-1050
Website: https://www.tmrresearch.com/
0 notes
Text
Task 2 XBLAW 7319 ST10120728
An examination of the merits and challenges of incorporating e-discovery into South African Civil Procedure.
What is E-discovery and why is it relevant to legal practice and civil procedure?
eDiscovery is the procedure of finding, safeguarding, developing and searching electronic information in legal discovery.[2] The Civil Proceedings Evidence Act 25 of 1965 (CPEA) lists the requirements for the production of documents to lessen the issues in question and to ensure that the court’s time is not wasted.[3]
How does it work?
The use of electronic data in court proceedings is authorised in section 11(1) of the Electronic Communications and Transactions Act 25 of 2002 which states that information is not without legal force and effect merely on the grounds that it is wholly or partly in the form of a data message.[4] The process followed for e-discovery is information regulation, identification, preservation and collection, processing, review and analysis, production and presentation at trial.[5]
Should e-discovery be incorporated into the rules of civil procedure?
Most data is now stored and transmitted electronically therefore the legislature should cater to the changing environment to make it easier for every legal person to present credible evidence in a juristic setting. In addition, by using electronic means to store and transmit data, important information and documents can be stored and located much easier with a much lower rate of loss.
What are some of the challenges facing e-discovery in South Africa?
With regards to safeguarding, council has an obligation to protect any electronic documents that could be pertinent or presumed to be a prerequisite for later litigation.[6] This can be quite a costly exercise that is charged on billable hours and hosting fees per gigabyte.[7] However, if these files are stored locally and backed up onto a secondary drive that is also password protected off premises, these storage costs can be reduced significantly in comparison to the costs of printing thousands of pages of information and then making copies thereof for submission.[8]
With regards to format, PDF seems to be the generally accepted format for files as they can be password protected to ensure they reach only their intended recipient/s and that the file can never be changed in transit in a manner that would physically affect the contents of the file in question.[9]
With regards to the number of files, the amount of effort needed would be the same as with physical documents.[10] The real difference comes in the fact that digital documents would need to be verified as true and correct before they can be used in legal proceedings.[11]
What are some of the global trends regarding the adoption of e-discovery and is South Africa keeping up or lagging behind?
In the United States of America, electronically kept legal papers are components of discovery asks and replies.[12] All electronic information is regulated by the doctrine of sensible obtainability.[13] The court still has final choice to order that specific documents be revealed in any manner the court wants.[14] There are rules regarding penalties to be imposed if stratagem and court process are not followed regarding the discovery of electronic documents.[15]
From the above, it would appear that South Africa is lagging behind regarding the adoption of e-discovery processes as no specific rules are laid down regarding e-discovery procedure.[16] Electronic documents are, however, regulated in civil procedure through the Rules of the High Court and the Rules of the Magistrate’s Court.[17]
How will the inclusion of e-technologies in legal practice impact on the practitioner’s duty of care, skill and attention to his client?
Regarding the practitioner’s duty of care, legal practitioner’s will need to be more sceptical of electronic documents and where they came from in order to ascertain if those documents can be used and are true and correct.
Regarding skill, it is a lot easier to search through electronic documents than it is to search through physical documents. However, legal practitioner’s would be required to possess basic computer skills as this would be needed to run these searches.
Research can be done on expert witnesses in order to verify their qualifications electronically.[18] Legal practitioners who are working on the same case can share important files securely through services such as Drop Box.[19]
With regards to attention to the client, electronic devices and services ensure that even if a legal practitioner and a client cannot physically meet in person, they could still virtually meet through services such as Skype.[20]
Do you believe that the introduction to e-technologies in legal practice generally could impact the section 14 rights of litigants?
Section 14 of the Constitution of the Republic of South Africa, 1996 deals with the right to privacy. [21] As such, the section 14 rights of litigants would be affected substantially as all communications related to the matter that are not privileged nor prejudicial would have to be disclosed as part of discovery thereby impacting the litigant’s right to privacy.[22]
(Words: 809).
____________________
[1] Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022).
[2] Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022).
[3] Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022); Myburgh, A. E-discovery in South African law (2017) Academia academia.edu/download/53257166/E-Discovery_in_SA.pdf (accessed 28 April 2022).
[4] Section 11(1) of the Electronic Communications and Transactions Act 25 of 2002.
[5] Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022).
[6] Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022).
[7] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022); CloudNine Managing the unpredictability of eDiscovery costs (2022) eDiscovery daily blog cloudnine.com/ediscoverydaily/managing-unpredictability-of-ediscovery-costs-with-cloudnine (accessed 16 May 2022).
[8] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
[9] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
[10] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[11] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[12] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[13] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[14] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[15] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[16] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[17] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
[18] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
[19] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
[20] Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
[21] Section 14 of the Constitution of the Republic of South Africa, 1996.
[22] Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
Bibliography
Legislation
Civil Proceedings Evidence Act 25 of 1965 (CPEA).
Electronic Communications and Transactions Act 25 of 2002 (ECTA).
Cases
N/A
Loose-leaf editions
N/A
Articles
CloudNine Managing the unpredictability of eDiscovery costs (2022) eDiscovery daily blog cloudnine.com/ediscoverydaily/managing-unpredictability-of-ediscovery-costs-with-cloudnine (accessed 16 May 2022).
Books
N/A
Chapters in books and journals
Cassim, F. The use of electronic discovery and cloud-computing technology by lawyers in practice: lessons from abroad (2017) Journal for judicial science 42(1): 19-40 DOI: 10.18820/24150517/JJS42.v1.2 (accessed 28 April 2022).
Hughes, K. Stander, A. and Hooper, V. eDiscovery in South Africa and the challenges it faces (2015) Researchgate DOI: 10.1109/InfoSec.2015.7435507 researchgate.net/publication/284173757 (accessed 28 April 2022).
Myburgh, A. E-discovery in South African law (2017) Academia academia.edu/download/53257166/E-Discovery_in_SA.pdf (accessed 28 April 2022).
Theses
N/A
Internet sources
1. Crecelius, J.D New technology and its impact on the practice of law (11 April 2022) Expert Institute expertinstitute.com/resources/insights/new-technology-and-its-impact-on-the-practice-of-law (accessed 15 May 2022).
1 note
·
View note