#Embedded Hardware Design Service
Explore tagged Tumblr posts
Text
The Evolution of Embedded Hardware: From Simple Circuits to Smart Devices
Embedded systems are all around us in today's hyperconnected world, from the sophisticated electronics controlling your car's engine to the smart thermostat that regulates the temperature in your house. One of the most amazing changes in technology is the progression from simple circuits to the advanced smart devices of today. This evolution, which has been fuelled by necessity and creativity, has been an intriguing one that has taken place over many decades. Understanding this history is essential for developers and businesses traversing this terrain, particularly when thinking about an embedded hardware design service that could help them realise their next big idea.
The Pioneer Days: Early Embedded Systems

The 1960s and 1970s marked the dawn of embedded computing, though it looked nothing like what we recognize today:
The Apollo Guidance Computer, which helped navigate astronauts to the moon, represented one of the first mission-critical embedded systems
Early embedded systems relied on discrete components rather than integrated circuits
These systems were enormous by today’s standards—filling entire cabinets
Programming was done through hard-wired logic or assembly language
Each system was custom-designed for a specific purpose with little flexibility
These primitive beginnings laid groundwork for what would become a technological revolution, yet the limitations were substantial. Memory was measured in kilobytes, processing power was minimal, and development required specialized expertise that few possessed.
The Microprocessor Revolution
Everything changed in the early 1970s with the introduction of the microprocessor:
Intel’s 4004, introduced in 1971, became the first commercially available microprocessor
For the first time, computing power could fit on a single chip
Development costs dropped dramatically, making embedded systems accessible to more industries
Early applications included calculators, cash registers, and industrial controllers
The 8-bit microcontroller era began, with chips like the Intel 8051 becoming industry standards
This miniaturization represented the first major leap toward modern embedded systems. Suddenly, intelligence could be added to previously “dumb” devices, creating new possibilities across industries from manufacturing to consumer electronics.
From Industrial to Consumer Applications
The 1980s and 1990s witnessed embedded systems transitioning from purely industrial uses to consumer products:
Video game consoles like the Nintendo Entertainment System introduced millions to embedded technology
Household appliances began incorporating microcontrollers for improved functionality
Automotive applications expanded rapidly, with engine control units becoming standard
Personal digital assistants (PDAs) showcased the potential for portable computing
Cell phones emerged as perhaps the most transformative embedded systems of the era
At this time, there started to appear specialized embedded hardware design service providers which assists businesses with intricate hardware designs. These services helped translate creative concepts into functioning products, allowing companies without internal capabilities to join the growing competition in the electronics industry.
The Networking Revolution and Embedded Connectivity
By the late 1990s and early 2000s, embedded systems gained a critical new capability—connectivity:
First-generation embedded networks often used proprietary protocols
Industry standards like CAN bus revolutionized automotive electronics
TCP/IP implementation in embedded devices paved the way for Internet connectivity
Wireless technologies like Bluetooth and later Wi-Fi liberated devices from physical connections
Remote monitoring and management became possible, changing service models forever
This networking capability transformed embedded systems from standalone devices to interconnected nodes, creating new possibilities for data collection and device management. Industries from healthcare to manufacturing began reimagining their processes around these newly connected devices.
The Rise of the Internet of Things (IoT)

The 2010s saw embedded systems become truly ubiquitous through the Internet of Things:
Consumer IoT products like smart thermostats, lighting, and speakers entered millions of homes
Industrial IoT revolutionized manufacturing through predictive maintenance and asset tracking
Agriculture embraced precision farming techniques using embedded sensor networks
Healthcare innovations included remote patient monitoring and smart medical devices
Urban infrastructure began incorporating embedded systems for “smart city” initiatives
With this explosion in applications came increasing complexity. An embedded hardware design service became essential for many companies looking to enter the IoT market, providing expertise in not just hardware but the integration of sensors, connectivity, and power management that modern IoT devices require.
Read Also: The Role of Embedded Hardware in IoT Devices
The Miniaturization Miracle
Throughout this evolution, one trend has remained constant—the drive toward smaller, more efficient devices:
Component sizes shrank from through-hole to surface-mount to microscopic
Power consumption decreased dramatically, enabling battery-operated portable devices
Wearable technology emerged as components became small enough to integrate into clothing and accessories
Medical implants shrank to minimize invasiveness while increasing capability
Sensors became small and inexpensive enough to deploy in massive numbers
This miniaturization has opened new frontiers in what’s possible with embedded systems. Today’s embedded hardware design services often specialize in extreme miniaturization, developing sophisticated systems that fit into spaces previously thought impossible.
The Processing Power Explosion
Modern embedded systems bear little resemblance to their ancestors in processing capability:
32-bit and 64-bit processors have replaced 8-bit chips in many applications
Multi-core processors enable complex real-time processing
Specialized hardware accelerators handle tasks like AI inference and video processing
For specific applications, field-programmable gate arrays (FPGAs) offer hardware that can be reconfigured.
System-on-Chip (SoC) designs combine peripherals, memory, and CPUs into one unit.
With this processing capability, embedded systems can now perform tasks like computer vision and natural language processing that were previously only possible with general-purpose computers, all while retaining the dependability and deterministic behaviour that embedded systems need.
The Future: AI at the Edge and Beyond
Looking ahead, embedded systems continue evolving at a breathtaking pace:
Edge AI is pushing intelligence to embedded devices rather than relying on cloud processing
New materials and manufacturing techniques are enabling flexible and biodegradable electronics
Energy harvesting is reducing or eliminating battery dependencies
Quantum computing principles may eventually transform embedded processing
Neuromorphic computing aims to make embedded systems think more like biological brains
These frontiers represent both challenge and opportunity. Companies seeking to navigate this complexity increasingly turn to specialized embedded hardware design services that can transform cutting-edge concepts into viable products.
The evolution of embedded hardware marks one of the most remarkable journeys of technology, progressing from circuits to devices that think for us and are a part of our lives. This journey continues to accelerate as we enter the following decades which promise even more astonishing innovations. For companies that want to take part in the ongoing revolution, collaborating with specialized embedded hardware design services is crucial for changing futuristic concepts into reality.
0 notes
Text
#ui ux principles#principles of ui ux design#IoT Embedded Systems#AI product development company#AI-driven hardware development#AI Development Services Company in India
0 notes
Text
EMBEDDED SYSTEM FOR INDUSTRIAL AUTOMATION
Introduction
Embedded systems have transformed industrial automation, leading to major increases in efficiency, safety, and productivity. These specialized computing systems, which are integrated into larger mechanical or electrical systems, perform specific functions under real-time computing restrictions. They are widely used in a variety of industries, including manufacturing, energy, transportation, and healthcare. This article examines the importance of embedded systems in industrial automation, including their benefits, uses, and future prospects.
The Use of Embedded Systems in Industrial Automation
Embedded systems are at the heart of industrial automation, allowing complicated processes to run smoothly. They combine hardware and software to complete specific, predefined tasks, frequently under strict real-time constraints. The main functions of embedded systems in industrial automation are:
1.Process Control: Embedded systems monitor and control industrial processes, assuring peak performance and safety compliance. They regulate factors such as temperature, pressure, and flow rates in real time, allowing for precise control over manufacturing operations.
2.Data Acquisition: These systems capture data from a variety of sensors and equipment, allowing for continuous monitoring of industrial processes. This information is crucial for performance analysis, predictive maintenance, and quality assurance.
3.Communication: Embedded systems facilitate communication between different components of an industrial network. They support various communication protocols, ensuring interoperability and seamless data exchange across the network.
4.Human-Machine Interface (HMI): Embedded systems provide interfaces for operators to interact with industrial equipment. HMIs, such as touchscreens and control panels, allow operators to monitor system status, input commands, and receive feedback.
Benefits of Embedded Systems for Industrial Automation
The integration of embedded systems in industrial automation provides various benefits:
1.Increased Efficiency: Automated systems can run continually without tiring, lowering downtime and boosting total productivity. Embedded systems optimize processes by making real-time adjustments based on sensor data, resulting in better resource use.
2.Enhanced Safety: Embedded systems increase safety by monitoring vital parameters and alerting or shutting down when irregularities are discovered. They also allow for the use of advanced safety standards, such as emergency stop functions and fail-safe mechanisms.
3.Cost Savings: Automation lowers labor expenses and reduces human error, leading to cost savings. Furthermore, predictive maintenance facilitated by embedded technologies can help to avoid costly equipment breakdowns and increase machinery lifespan.
4.Scalability: Embedded systems can be scaled to meet the needs of a wide range of industrial applications, including small-scale operations and big, complex manufacturing plants. They can be quickly upgraded or reprogrammed to meet changing manufacturing requirements.
Application of Embedded Systems in Industrial Automation
Embedded systems are used in a variety of industrial automation applications.
1.Manufacturing uses embedded systems to manage robotic arms, conveyor belts, and CNC machines, assuring precision and uniformity in production. They also manage inventories and logistics.
2.Energy: In the energy industry, embedded systems monitor and control electricity generation, delivery, and consumption. They are critical in managing renewable energy sources like wind and solar by optimizing their integration into the system.
3.Transportation: Embedded systems are used to manage traffic, control vehicles, and monitor infrastructure. They improve the efficiency and safety of transportation networks, including railways and smart highways.
4.Healthcare: Embedded systems regulate medical instruments and equipment, ensuring precise and dependable performance. They are utilized in diagnostic devices, patient monitoring systems, and automated laboratory instruments.
Future Prospects
The future of embedded systems in industrial automation looks bright, thanks to technological breakthroughs such as the Internet of Things (IoT), artificial intelligence (AI), and machine learning. These advancements will allow for more comprehensive data analysis, predictive maintenance, and automated decision-making.
1.IoT Integration: The combination of IoT and embedded systems will result in networked industrial settings in which devices interact and collaborate effortlessly. This will result in better, more responsive automation systems.
2.AI and machine learning algorithms can be integrated into industrial systems to analyze large volumes of data and optimize processes. These technologies will help with predictive maintenance, process optimization, and defect identification.
3.Edge computing moves computational power closer to the source of data, lowering latency and boosting real-time decision-making. Embedded systems with edge computing capabilities will allow for faster and more efficient automation operations.
4.Cybersecurity will become increasingly important as industrial automation systems become more networked. Future embedded systems will include improved security capabilities to defend against cyber threats and maintain the integrity of industrial operations.
Conclusion
Embedded systems are at the heart of industrial automation, boosting efficiency, safety, and innovation across a variety of industries. As technology advances, the capabilities of these systems will increase, resulting in increasingly more complex and intelligent automation solutions. The integration of IoT, AI, and edge computing will further change industrial operations, ushering in a new era of smart manufacturing and more.
https://avench.com/

#embedded software development company#embedded product design#value engineering#hardware design#iot development services
1 note
·
View note
Text
Hardware Design Services | Electronic Design, Prototyping, and R&D Services
Teksun offers Hardware Design Services including designs based on a microprocessor, microcontroller, DSP, and all programmable modules. To know more about browse: https://teksun.com/ Contact us ID: [email protected]
#embedded hardware design services#embedded iot solutions#embedded hardware design#product engineering services#product engineering company#digital transformation#technology solution partner
0 notes
Text
CA Internet Bills Status as of 7/17/2024
I had wanted to wait to make this post until all of the bills updated texts had been uploaded to the usual sites, but it appears what whoever's supposed to be updating AB 3080 has been lagging, so I'll just go with what I have for now. It'll be long as I'll be looking at their statuses and analyzing their updated texts so I'll put it under a cut for now.
A reminder that California's legislature is currently on recess and will be until August 5th. So no immediately imminent bills at this exact moments. But please read below the cut to get more information on the deadlines coming up.
When I last posted, all three of the bills had gone into review in their respective committees and sadly all of them passed out.
AB 3080: 11 Aye - 0 Nay
AB 1949: 11 Aye - 0 Nay
SB 976: 7 Aye - 4 No Vote
All three bills have been amended during their time in committees.
Ab 3080
AB 3080 was amended and passed from committee as amended, it is now available for a floor vote. This is the only one of the three bills where its amended text hasn't been posted anywhere I can find. However, in the analysis of the July 3rd meeting, there were acknowledgements made that not only is there no effective and safe way to verify age to view online content, but also that the existence of VPNs can circumvent any attempts to region lock sites designated as "adult" (the definition as it stands still appears to be limited to commercial websites where more than 1/3 of their content annually is sexually explicit). And that the methods to implement such a thing on commercial and non-commercial websites alike can be prohibitively expensive. So the author of the bill agreed to amendments in the bill as such according to the analysis:
"In response to the concerns of opposition, the author has agreed to amendments that allow a less restrictive means to suffice in meeting the obligation of the bill, mitigating the impact on protected speech and expression. The amendments provide that “reasonable steps” includes the business implementing a system that includes metadata or response headers identifying the product as sexually explicit to parental control software, embedded hardware applications, and other similar services designed to block, filter, monitor or otherwise prevent a minor’s access to inappropriate online content, or that blocks users designated as minors by the operating system of the device used to access the website. It also limits enforcement of this new cause of action to the Attorney General and requires the Attorney General to promulgate regulations to provide better direction for reasonable steps to verify age in addition to those listed."
So it appears that the bill may allow more websites instead to mark themselves or certain portions of their content as adult in order to be properly vetted by in-device content filters and parental controls that can be set by the device operators (or their parents in the case of minors), rather than a method that would require users to provide identification.
It's eased up quite a bit since its initial incarnation. But it's still better safe than sorry with this kind of bill, so Californians let's still push the state senators to veto this bill completely.
Organizations in support of this bill:

Organizations in opposition to this bill:

AB 1949
AB 1949 was amended and passed from committee as amended, and is currently referred to the Senate Appropriations Committee.
This one has also seen some fairly positive changes during this committee analysis as can be seen in the latest version of the bill. The latest version has removed any indications towards age verification. As well as it having changed several of its details. The bill only comes into effect and prevents the sale of data if the website has actual knowledge of the users' age, and that there shall be an option for the user to transmit a signal that they are under 18 for this purpose. Which again should help the argument against strict age verification barriers due to advertising purposes.
"a business shall not use or disclose the personal information of a consumer if the business has actual knowledge that the consumer is less than 18 years of age, unless the consumer, in the case of a consumer at least 13 years of age and less than 18 years of age, or the consumer’s parent or guardian, in the case of a consumer less than 13 years of age, has affirmatively authorized the use or disclosure of the consumer’s personal information."
"A business shall treat a consumer as under 18 years of age if the consumer, through a platform, technology, or mechanism, transmits a signal indicating that the consumer is less than 18 years of age."
But, once again, it is best to still work against this bill and prevent its passing at all in case it there's push to use it as a stepping stone for any bills which may further push an age verification agenda.
Organizations in support of this bill:

Organizations in opposition of this bill:

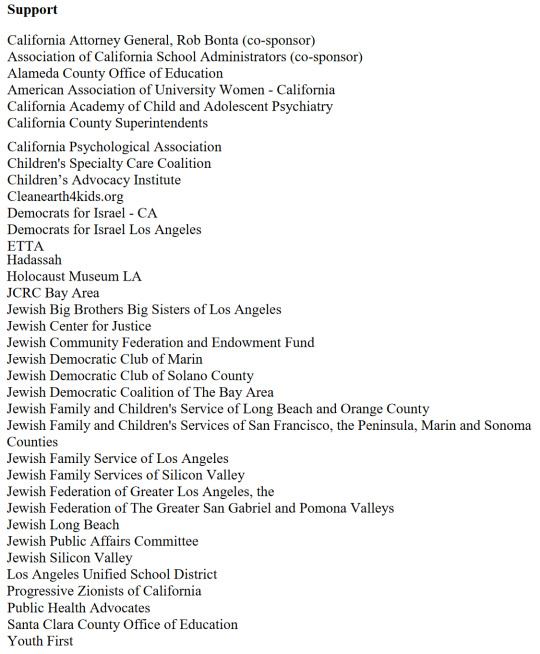
SB 976
This bill passed with amendments and is currently referred to the California Assembly Appropriations Committee. Unfortunately no major changes have been made. Only an amendment clarifying that any parental controls are only meant to limit access to "addictive feeds" and limit access to school hours, not any of the content. As this function still requires a "verified adult parent to a minor", this still holds open the door to potential future age verification dangers. As it still states that an application may choose to withhold services to minors altogether, and explicitly leaves open the possibility to allow provisions for age "assurance". So we definitely want to strike this one down if we can.
Organizations in support of this bill:
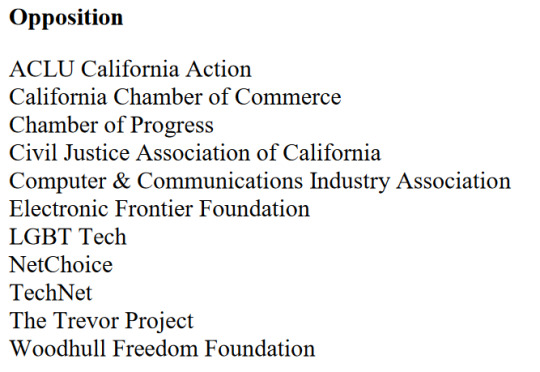
Organizations in opposition to this bill:
As of this moment, the California Legislature is out on recess until August 5.
The Senate Appropriations Committee (AB 1949) is set to meet on August 5, no word on whether it will be heard that day or on the next set hearing, August 12. So if you wish to send a position letter to the committee it would be best to do so a week before that date, so by July 29. Just to be safe.
No word on when the Assembly Appropriations Committee is set to meet, but the deadline for fiscal committees to pass bills through is August 16, so I expect that SB 976 will be heard before that day at least.
And AB 3080 is set to go to the senate floor rather than be seen by another committee before being read. No word on when the next bill readings will be on the assembly floor after it's reconvened August 5th, but I'll keep an ear to the ground for that.
The last day for each house to pass their bills for the year will be August 31st. So any bills we can stop before then are halted for good for the year.
And for any bills that do slip through, the last day for the governor to sign, let pass without signing, or veto bills is September 30th. So even if the bills pass from the floor to his desk, there's still time to send him messages to urge him to oppose any that slip through.
Thank you for your time, both in reading this and in taking the time to help us fight these bills.
#kosa#california#ab 3080#sb 976#ab 1949#bad internet bills#age verification#internet privacy#internet safety
30 notes
·
View notes
Text
How to know if a USB cable is hiding malicious hacker hardware
Are your USB cables sending your data to hackers?
We expect USB-C cables to perform a specific task: transferring either data or files between devices. We give little more thought to the matter, but malicious USB-C cables can do much more than what we expect.
These cables hide malicious hardware that can intercept data, eavesdrop on phone calls and messages, or, in the worst cases, take complete control of your PC or cellphone. The first of these appeared in 2008, but back then they were very rare and expensive — which meant the average user was largely safeguarded.
Since then, their availability has increased 100-fold and now with both specialist spy retailers selling them as “spy cables” as well as unscrupulous sellers passing them off as legitimate products, it’s all too easy to buy one by accident and get hacked. So, how do you know if your USB-C cable is malicious?
Further reading: We tested 43 old USB-C to USB-A cables. 1 was great. 10 were dangerous
Identifying malicious USB-C cables
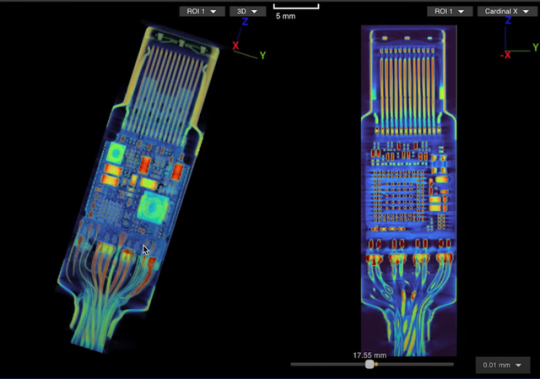
Identifying malicious USB-C cables is no easy task since they are designed to look just like regular cables. Scanning techniques have been largely thought of as the best way to sort the wheat from the chaff, which is what industrial scanning company, Lumafield of the Lumafield Neptune industrial scanner fame, recently set out to show.
The company employed both 2D and 3D scanning techniques on the O.MG USB-C cable — a well-known hacked cable built for covert field-use and research. It hides an embedded Wi-Fi server and a keylogger in its USB connector. PCWorld Executive Editor Gordon Ung covered it back in 2021, and it sounds scary as hell.
What Lumafield discovered is interesting to say the least. A 2D X-ray image could identify the cable’s antenna and microcontroller, but only the 3D CT scan could reveal another band of wires connected to a die stacked on top of the cable’s microcontroller. You can explore a 3D model of the scan yourself on Lumafield’s website.
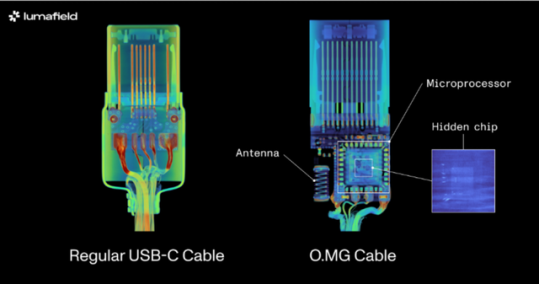
It confirms the worst — that you can only unequivocally confirm that a USB-C cable harbors malicious hardware with a 3D CT scanner, which unless you’re a medical radiographer or 3D industrial scientist is going to be impossible for you to do. That being so, here are some tips to avoid and identify suspicious USB-C cables without high-tech gear:
Buy from a reputable seller: If you don’t know and trust the brand, simply don’t buy. Manufacturers like Anker, Apple, Belkin, and Ugreen have rigorous quality-control processes that prevent malicious hardware parts from making it into cables. Of course, the other reason is simply that you’ll get a better product — 3D scans have similarly revealed how less reputable brands can lack normal USB-C componentry, which can result in substandard performance. If you’re in the market for a new cable right now, see our top picks for USB-C cables.
Look for the warning signs: Look for brand names or logos that don’t look right. Strange markings, cords that are inconsistent lengths or widths, and USB-C connectors with heat emanating from them when not plugged in can all be giveaways that a USB-C cable is malicious.
Use the O.MG malicious cable detector: This detector by O.MG claims to detect all malicious USB cables.
Use data blockers: If you’re just charging and not transferring data, a blocker will ensure no data is extracted. Apart from detecting malicious USB-C cables, the O.MG malicious cable detector functions as such a data blocker.
Use a detection service: If you’re dealing with extremely sensitive data for a business or governmental organization, you might want to employ the services of a company like Lumafield to detect malicious cables with 100 percent accuracy. Any such service will come with a fee, but it could be a small price to pay for security and peace of mind.
11 notes
·
View notes
Text
Top B.Tech Courses in Maharashtra – CSE, AI, IT, and ECE Compared
B.Tech courses continue to attract students across India, and Maharashtra remains one of the most preferred states for higher technical education. From metro cities to emerging academic hubs like Solapur, students get access to diverse courses and skilled faculty. Among all available options, four major branches stand out: Computer Science and Engineering (CSE), Artificial Intelligence (AI), Information Technology (IT), and Electronics and Communication Engineering (ECE).
Each of these streams offers a different learning path. B.Tech in Computer Science and Engineering focuses on coding, algorithms, and system design. Students learn Python, Java, data structures, software engineering, and database systems. These skills are relevant for software companies, startups, and IT consulting.
B.Tech in Artificial Intelligence covers deep learning, neural networks, data processing, and computer vision. Students work on real-world problems using AI models. They also learn about ethical AI practices and automation systems. Companies hiring AI talent are in healthcare, retail, fintech, and manufacturing.
B.Tech in IT trains students in systems administration, networking, cloud computing, and application services. Graduates often work in system support, IT infrastructure, and data management. IT blends technical and management skills for enterprise use.
B.Tech ECE is for students who enjoy working with circuits, embedded systems, mobile communication, robotics, and signal processing. This stream is useful for telecom companies, consumer electronics, and control systems in industries.
Key Differences Between These B.Tech Programs:
CSE is programming-intensive. IT includes applications and system-level operations.
AI goes deeper into data modeling and pattern recognition.
ECE focuses more on hardware, communication, and embedded tech.
AI and CSE overlap, but AI involves more research-based learning.
How to Choose the Right B.Tech Specialization:
Ask yourself what excites you: coding, logic, data, devices, or systems.
Look for colleges with labs, project-based learning, and internship support.
Talk to seniors or alumni to understand real-life learning and placements.
Explore industry demand and long-term growth in each field.
MIT Vishwaprayag University, Solapur, offers all four B.Tech programs with updated syllabi, modern infrastructure, and practical training. Students work on live projects, participate in competitions, and build career skills through soft skills training. The university also encourages innovation and startup thinking.
Choosing the right course depends on interest and learning style. CSE and AI suit tech lovers who like coding and research. ECE is great for those who enjoy building real-world devices. IT fits students who want to blend business with technology.
Take time to explore the subjects and talk to faculty before selecting a stream. Your B.Tech journey shapes your future, so make an informed choice.
#B.Tech in Computer Science and Engineering#B.Tech in Artificial Intelligence#B.Tech in IT#B.Tech ECE#B.Tech Specialization
2 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
2 notes
·
View notes
Text
Understanding Electronics Design & Engineering

Introduction
Electronics design engineering is that critical component that determines the future of innovative products in a competitive tech industry today. It consists of all services—from concept development in the initial stage to the final testing of the product, so as to deliver an electronic product capable of high performance and meeting the established performance standards as well as regulatory compliance. This amalgamation of experience and approach in the area of hardware, firmware, mechanical design, and regulatory compliance underlines electronics design engineering as a fundamental component in the development of reliable and efficient products.
Concept development
It is the first phase of the process in electronics design engineering. Concept development is that phase that involves the idea generation of a product, an analysis of needs in the market, and, by extension, setting the technical requirements for the product. Engineers and designers can then work together to create a solid proposal for the product development so that concept development becomes both market-worthy and technically viable.
Firmware development
It is a part and parcel of electronics design engineering because it explains how the hardware would interact with the world outside. It deals with the embedded software, which makes sure that the hardware components work smoothly and seamlessly.
The prime areas involved in firmware development are as follows:-
Embedded Systems: The firmware is tailored to regulate the internal systems of a device.
Real-Time Processing: The firmware is designed considering the real-time processing of data; this leads to responses that are swift and reliable.
Customization: Engineers design the firmware to specifically correspond with the product's functionality and application.
Want to take your product to the next level with custom firmware? Get in touch with Lanjekar Manufacturing today for more information on how our electronics design engineering services can help.
Hardware Development
In electronics design engineering, the development of hardware is an important stage wherein engineers design the physical components that bring electronic devices to life. Hardware has to be robust and reliable and to enable the firmware for the optimal performance of the product.
Some of the important steps in it are as follows:
Component selection: High-quality components have to be selected according to the technical specifications of the product to be designed.
Prototyping: Engineers must make prototypes to check if the designs are valid and free from potential dangers that might eventually come into operation in full-scale production.
Testing: Extensive testing is carried out in this stage to test the functionality and life expectancy of the hardware.
PCB Layout Design
Printed circuit boards (PCBs) are the backbone of any electronic product, and hence their design must be correct. PCB layout design in electronics design engineering refers to the designing of efficient, interference-free, and compact designs within the form of the product.
Key considerations involve:
Schematic Design: The engineers produce an in-depth diagram to represent how one component connects to another.
Layout Optimization: It optimizes the layout so that signals remain robust and interference potential is minimized.
Manufacturability: The design is optimized with best practices that ensure efficient production of PCBs.
Regulatory Compliance and Certification: Ensure the product meets local and international standards, this is part of the work of electronics design engineering. This includes:
Knowledge on Regulatory: Engineers ensure that the product goes through the required regulations, safety, and environmental standards.
Testing: Testing of products to conform to the certification through acquisition of compliance standards.
Documentation: All these supporting documents for certifications undertaken in the engineering process. Mechanical DesignIt is one thing to have a good internal part of the device, but the mechanical design of a product cannot be overlooked. Electronics design engineering typically incorporates mechanical design in its design to ensure that the device has a good, robust structure that appears aesthetically pleasing.This is what constitutes mechanical design, such as;
3D Modeling: Engineers create 3D models that would allow the individual to visualize the physical structure of the product.Thermal Management: Effective thermal design, where the hot elements are dissipating the heat away.
Material Selection: Correct material to utilize for ruggedness, weight, and functionality
Mechanical Design: It is also critical to ensuring the product functions well but with ease of usage.
Connectivity Solutions
With the increasing rise in the deployment of IoT products, electronics design engineering puts emphasis on connectivity solutions. This could either be wireless or wired. This ensures that the product is communicating effectively.
Some of the crucial considerations include the following:
Protocol Implementation: It ensures total compatibility with different communication protocols like Wi-Fi, Bluetooth, or Zigbee.
Seamless Integration: The connectivity solutions are also made to not compromise with the performance of a product.
Security Measures: Connectivity solutions also deal with data security, one important feature of modern devices.
Conclusion
Electronics design engineering contains all aspects of product development, from concept to compliance. The discipline of electronics design engineering consists of focusing on firmware, hardware, PCB layout, mechanical design, and connectivity, ensuring the end product is reliable, innovative, and compliant with industry standards. If all the components can work well coherently, it doesn't only produce a friendly user at the end but also something that will be in high demand in the market.
Contact Lanjekar Manufacturing today and share your project with us to find out how we can give your ideas life.
Also read:
Know Electronics Manufacturing: The Total Guide
Firmware Development: Where Software Meets Hardware
The Essentials of PCB Design: Techniques and Best Practices
The Complete Guide to Hardware Development: From Design to Deployment
2 notes
·
View notes
Text
Top Technical Skills for Electronics Engineer Resume in 2024
Electronics and Communication Engineering (ECE) offers a wide array of career opportunities due to its interdisciplinary nature, combining principles from electronics, telecommunications, and computer science. Here are the top 15 career options for graduates in this field:
1. Telecom Engineer
Telecom engineers design and manage communication systems, including optical fibers, microwave transmission, and IP networks. They analyze existing technologies and develop new solutions to enhance communication reliability and efficiency.
2. R&D Software Engineer
These engineers focus on creating and testing new software products. They play a crucial role in research and development, working on automation and mechanical controls to improve software systems across various industries.
3. Software Analyst
Software analysts design, develop, and test software applications, ensuring they meet user needs. They act as a bridge between developers and users, managing software updates and enhancing user experience.
4. Electronic Design Engineer
Electronic design engineers create electronic circuits and devices tailored to specific requirements. They work on projects ranging from consumer electronics to complex communication systems.
5. Embedded Systems Engineer
Embedded systems engineers develop software for embedded systems found in various devices like appliances, medical equipment, and automotive systems. This role requires proficiency in both hardware and software development.
6. Network Engineer
Network engineers design, implement, and manage computer networks within organizations. They ensure network security and optimize performance for efficient data transfer.
7. Service Engineer
Service engineers maintain and repair electronic equipment used in various industries. Their work ensures that systems operate smoothly, minimizing downtime for businesses.
8. Technical Sales Engineer
In this role, engineers leverage their technical knowledge to sell complex electronic products or services. They often work closely with clients to understand their needs and provide tailored solutions.
9. Quality Assurance Engineer
Quality assurance engineers focus on testing products to ensure they meet required standards before they are released to the market. This role involves developing testing protocols and analyzing results to improve product quality.
10. Systems Engineer
Systems engineers oversee the integration of various subsystems into a complete system, ensuring all components work together effectively. This role is critical in projects involving complex electronic systems.
11. Electronics Technician
Electronics technicians assist in the design, development, and testing of electronic equipment. They often work under the supervision of engineers to troubleshoot issues and perform repairs.
12. Data Analyst
Data analysts in the ECE field focus on interpreting data related to electronic systems or communications networks. They use statistical tools to provide insights that can improve system performance or user experience.
13. Technical Director
Technical directors oversee engineering projects from conception through execution, ensuring technical feasibility while managing teams of engineers. They play a pivotal role in strategic planning within organizations.
14. Chief Technical Officer (CTO)
As a senior executive, the CTO is responsible for overseeing the technological direction of a company. This role involves strategic decision-making regarding technology investments and innovations.
15. Research Scientist
Research scientists in ECE focus on advancing knowledge in areas like telecommunications or signal processing through experimental research or theoretical analysis. This role often requires advanced degrees (MTech or PhD) for positions in academia or specialized industries.
Conclusion
Arya College of Engineering & I.T. is the Best Engineering College in Jaipur that gives career landscape for Electronics and Communication Engineers is diverse and continually evolving due to rapid technological advancements. Graduates can choose from various roles across multiple sectors including telecommunications, IT, manufacturing, aerospace, healthcare, and more, making ECE a promising field for aspiring professionals seeking dynamic career paths.
2 notes
·
View notes
Text
I.B.1698 MICHAEL [IBM] harrelltut.com Domain of SIRIUS BLACKANUNNAQI.tech Patents 2 iapplelisa.com of CLASSIFIED 1983 iapplelisa.tech Memory Application Configuration [MAC] Languages... Mathematically Engineered [ME] by ANU GOLDEN 9 Ether [MAGE] Tri-Solar Black Sun planetrizq.tech SKY FEDERATION of Astronomical MARS’ [FAM'S] Highly Complex [ADVANCED] Ancient Cosmic Algorithmic [CA] Computational [Compton] STAR WEB GATEWAY Language Algorithms [L.A.] Digitally Embedded w/Astronomical [DEA] DNA Markup Language Software from Astronomical MERCURY’s [SAM’s] ibmapple1984.tech Secure Socket Layer Virtual Private Network [SSL VPN] Communications.gov Privately Managed [PM] by ANU GOLDEN 9 Ether [iAGE] quantumharrell.tech Graphical User Interface [GUI] Domain Compu_TAH [PTAH] of iquantumapple.com Infrastructure as a Service [IaaS] since ibquantumapple.com VISION PRO of 1968 quadrillionharrell.tech Machine Engineering [ME] AutoCAD [MAC] Robotics in Architectural Memory Equipment w/Symmetric Encryptions of Satellite [RAMESES] Broadband Communication [B.C.] quantumharrellmatrix.tech Languages… Computationally Accessing [CA] quantumharrelltesla.tech Education and Copyright Harmonization Act [HA = HARRELL] of 2001 Digital Tech Rights [DTR] Scholastically Engineered Academically [SEA] @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm] mode [i’m] tech [IT] steelecartel.com @ quantum harrell tech llc


US ANCIENT [USA] SKY [U.S.] GODS OF ASTRONOMICAL MERCURY ENERGY [GAME] VORTEX GENERATORS 2 OUR INTERPLANETARY POWER [I/P] SYSTEMS of Urani-Atlantis.tech... PRIVATELY COMMUNICATING [PC] ONLINE @ QUANTUMHARRELL.tech Domain LLC
eye 1921steelecartel.tech TITAN of SIRIUS [U.S.] gullahgeecheemilitary.tech WEALTH @ quantum harrell tech llc

who secretly own apple, inc [a.i.] in 2024?!?!?!

uh oh... not our ancient 9 ether computational algorithm design [cad] patents of SIRIUS electronic architectural intel [a.i.] of Apple [A.I.A] Inc. Patents [I/P] @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000?!?!?!

ibmapple1984.tech @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

iapplelisa.com?!?!?!
of iapplelisa.tech?!?!?!

but who own iquantumcad.com?!?!?!

ibmautocad.tech memory hardware manual @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000?!?!?!
iquantumapple.com of iapplelisa.com @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

MICHAEL A COMPUTER [MAC] APPLE NERD [MAN] of iapplelisa.tech Intel @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

hi:teKEMETICompu_TAH [PTAH] PRO Michael [PM] Harrell, Jr. Deep Machine [DM] VISION Learning @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
CLASSIFIED iapplelisa.tech of iapplelisa.com accessing tri-solar black sun planetrizq.tech PRO of blackanunnaqi.tech VISIONS @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

try the quantumharrelltech.com visual dial tone domain... my personal iphone hung up on you [insert quantumharrell.tech's intellectual encryption phrase property tag]

quantumharrell.tech international [qi] 1921steelecartel.tech family business [dynasty] communication [d.c.] knowledge economy @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

shhh... we 3 sets of 144,000 confidential iapplelisa.tech elites @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
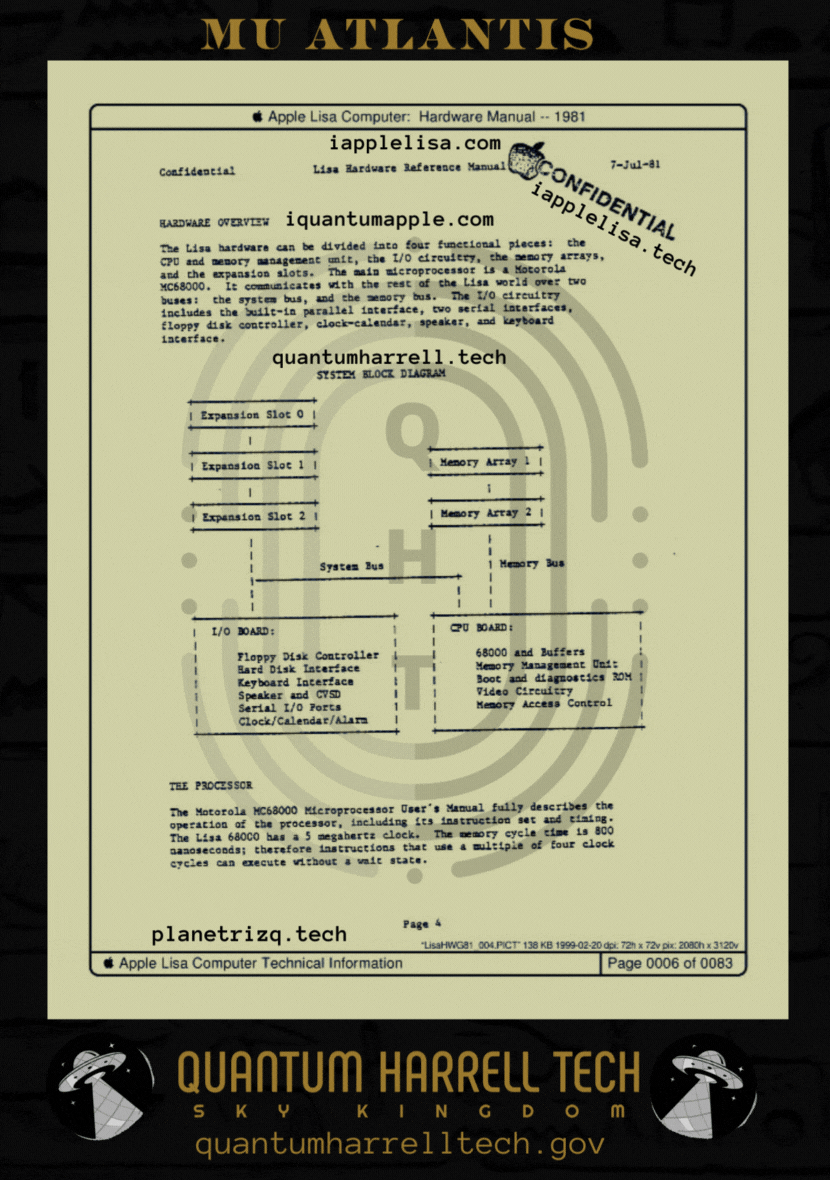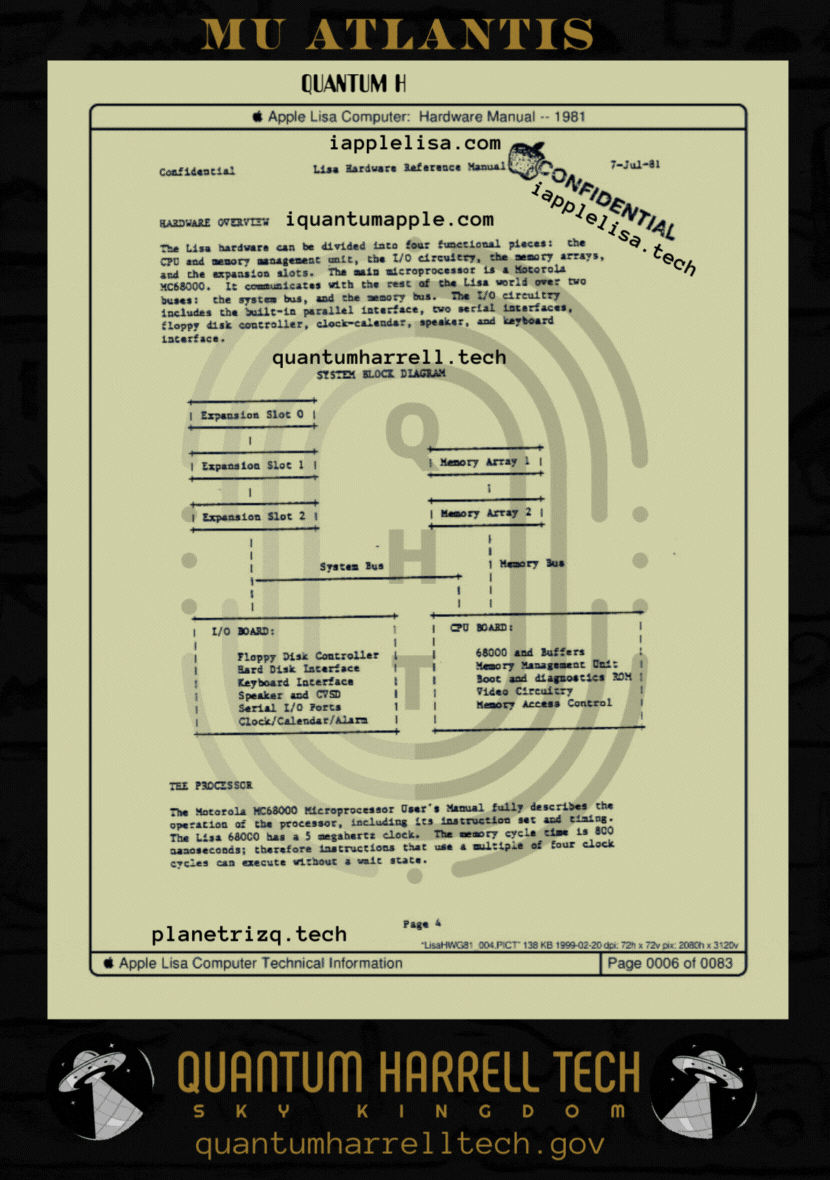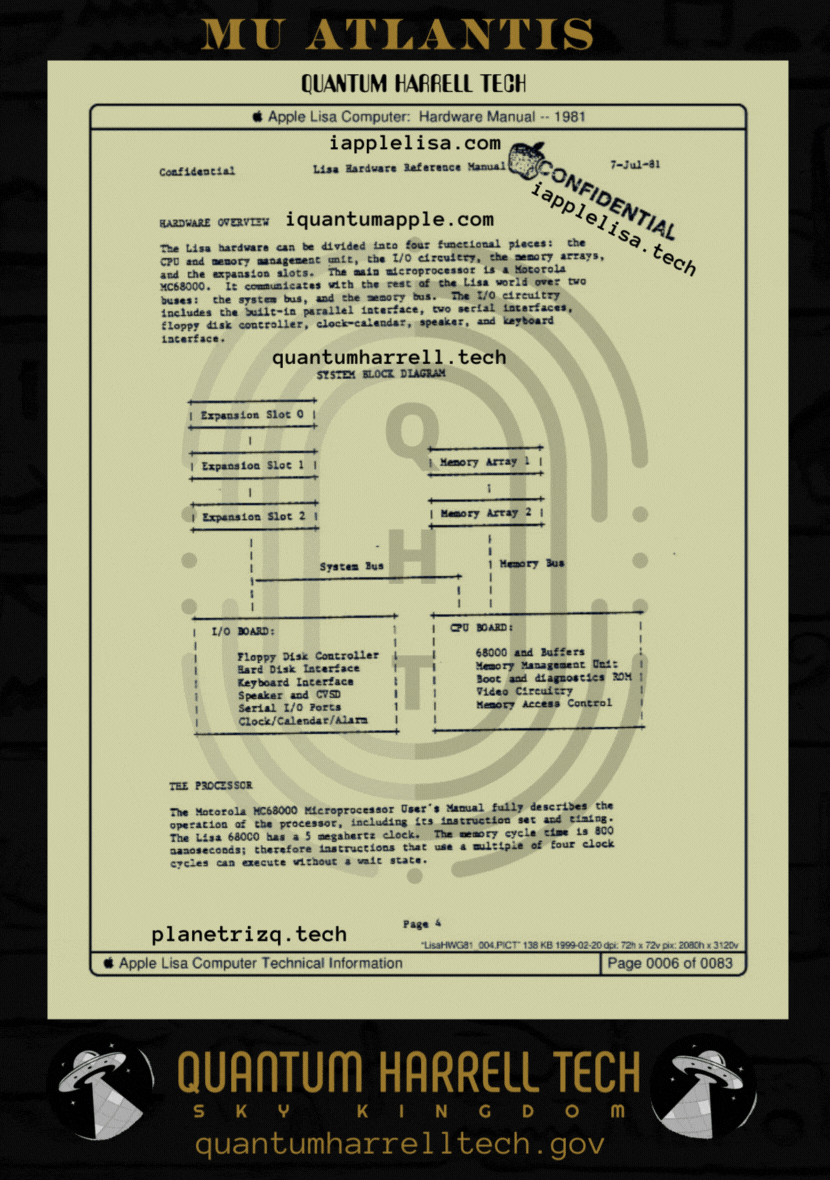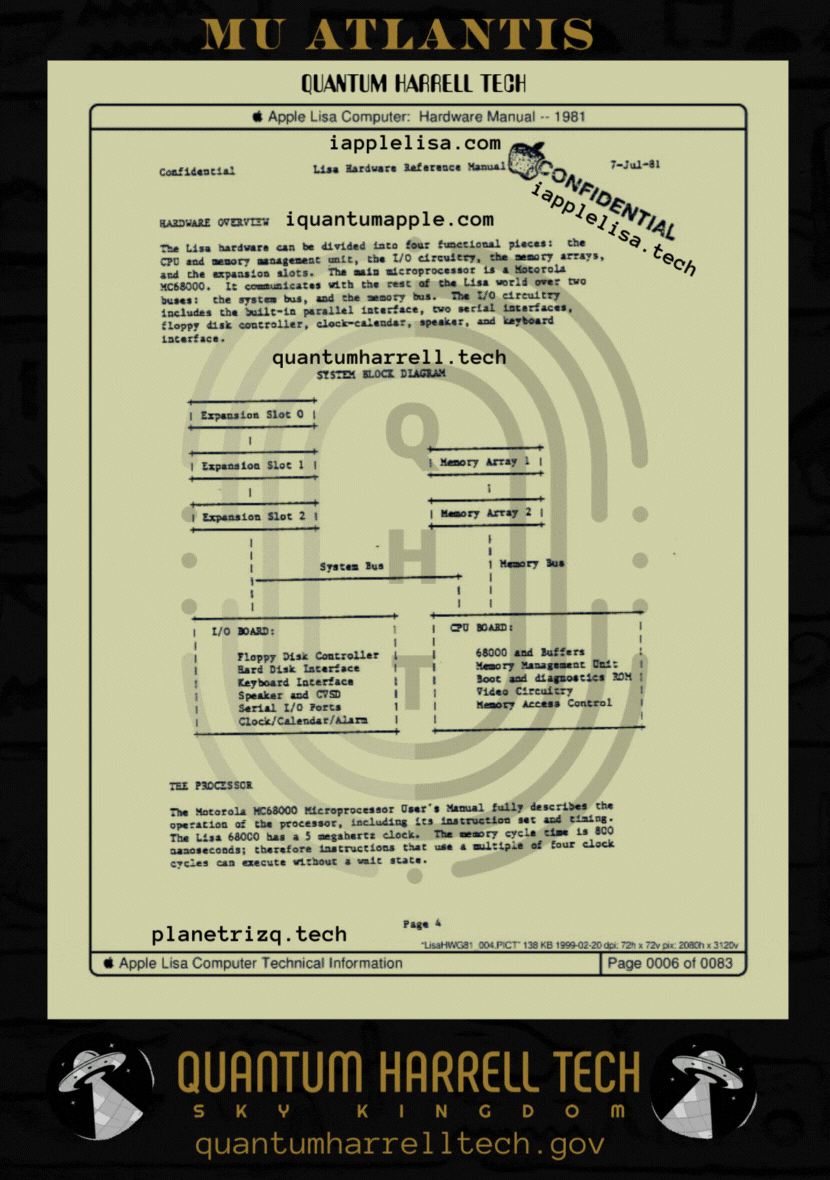
him ancient [ha = harrell] 1921 hi:tekemeticompu_tah [ptah] domain signature technocrat of 1968 planetrizq.tech?!?!?!... says who?!?!?!

says his hi:tekemeticompu_tah [ptah] father michael [fm]... since i.b.1698 michael [ibm] harrell jr @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

eye anugoldenblackwallstreet.com compu_tah [ptah] business of anu golden 9 ether [age] blackatlantis5000.com economy w/SIRIUS blackatlantis5000.tech WEALTH @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

I.B.1968 MICHAEL [IBM] QUANTUM COMPUTING ANU [CA] quantumharrellmatrix.tech MINING Economy [ME] @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
© 1968-2223 QUANTUM HARRELL TECH LLC All LOST ANCIENT [L.A.] ATLANTEAN DNA [A.D.] DotCom [A.D.] + DotTech [A.D.] + Pre 1698quantumharrellgov.tech Domain Name Rights Reserved.
#apple#ibm#t mobile#at&t#quantumharrelltech#vision pro#apple lisa#quantum dara#qdara.tech#harrelltut.com#u.s. michael harrell#o michael#king tut#intuitive machine learning
2 notes
·
View notes
Text

Secure Your NFTs with Smarter Storage Options in 2025
Introduction
In the past few years, non-fungible tokens (NFTs) have opened up a world of creative expression, digital ownership, and new business models. But alongside their rise, we’ve seen hacks, lost keys, and vulnerable storage solutions jeopardize prized digital assets. As we move into 2025, it’s more important than ever to use smarter, more secure ways to keep your NFTs safe. Whether you’re an artist minting your first token or a company offering NFT development solutions, understanding the landscape of wallet and storage options will help you protect your investments and creations.
Understanding the Risks: Why Secure Storage Matters for Your NFTs
When you mint an NFT, you’re really creating a record on a distributed ledger that points to a piece of content—an image, a video, or even a 3D model. But that on‑chain record often links to off‑chain data, stored somewhere on the internet. If that data disappears or if your private key is compromised, your NFT could become impossible to sell—or worse, someone else could claim it as theirs. Common risks include:
Key theft or loss: If you store your private key on an internet‑connected computer without extra protection, a hacker or malware can swipe it.
Service outages: Some NFT marketplaces or storage services go offline temporarily—or permanently—leaving your assets unreachable.
Link rot: When the server hosting your NFT’s actual media goes down, your token may only point to an empty URL.
Knowing these pitfalls is the first step. Next, let’s explore smarter ways to keep your NFTs safe in 2025.
Smarter Storage Options for Your NFTs in 2025
1. Hardware Wallets (Cold Storage)
Hardware wallets remain the gold standard for securing private keys. Devices like Ledger or Trezor store your keys in a tamper‑resistant chip, completely offline. Even if your computer is infected, the hacker can’t access the key without physical possession of the device. When you combine a hardware wallet with a passphrase and backup seed phrase stored in a safe, you’ve locked down your NFTs in a way that’s nearly unbreakable.
2. Software Wallets (Hot Wallets) with Enhanced Security Features
Hot wallets are more convenient because they connect directly to websites and apps. However, simple browser extensions or mobile apps aren’t enough anymore. Look for wallets that offer:
Multi‑factor authentication (MFA): A second device or biometric check to approve transactions.
Behavioral alerts: Warnings when a transaction looks unusual or the destination address isn’t recognized.
Built‑in recovery tools: Encrypted cloud backups or social recovery systems that let you designate trusted contacts who can help restore access.
These advanced features help bridge convenience and safety, so you’re not left choosing one over the other.
3. Smart Wallets: The Future of NFT Storage?
Smart wallets take hot wallets a step further by embedding programmable rules directly into your key management. Imagine a wallet that only allows transfers during certain hours, or one that splits approvals among multiple guardians. While still an emerging field, these wallets promise a more dynamic way to manage risk. They often come with a user‑friendly interface, making it easier for creators and collectors alike to handle security without needing a deep technical background.
4. Exploring Decentralized Storage Solutions like IPFS for NFTs
Traditional web servers can fail or go offline, but decentralized networks replicate data across many nodes. Two popular options for NFT content storage are:
Arweave NFT storage: Uses a “pay once, store forever” model. By paying a small fee upfront, your data lives on permanently, anchored by a blockchain‑based endowment. This ensures your artwork or media stays intact even if the original creator’s website goes down.
Storj NFT storage: Splits files into encrypted pieces and stores them across a peer‑to‑peer network. Since no single server holds the whole file, there’s no single point of failure. And redundancy means your content is retrievable even if some nodes disappear.
Integrating these decentralized storage layers adds an extra shield against link rot and centralized outages, reinforcing the on‑chain ownership with off‑chain resilience.
Best Practices for Securing Your NFTs in 2025: A Comprehensive Guide
Use a Reputable NFT Development Company for Your Platform If you’re building your own marketplace or minting service, partner with experts in NFT platform development. They’ll know how to integrate secure key management and decentralized storage options from the ground up.
Adopt a “Layered Defense” Approach Combine cold storage (hardware wallets) for long‑term holdings with hot wallets that have strong MFA and alerts for day‑to‑day transactions.
Regularly Update and Audit Your Tools Whether it’s a wallet app or a backend SDK for blockchain NFT development, keep everything up to date. Developers of NFT blockchain development tools often patch vulnerabilities—install these fixes promptly.
Practice Safe Backup Habits Store seed phrases and recovery information in multiple offline locations. Avoid digital photos or cloud notes that can be hacked. A fireproof safe or a trusted third‑party vault works best.
Educate Your Team and Community Phishing remains a top attack vector. Offer clear, human‑friendly guides on how to verify URLs, recognize impostor emails, and never share private keys.
Plan for the Unexpected Use social recovery or multi‑signature wallets so that if one key is lost, designated guardians or co‑signers can help regain control without compromising total security.
Conclusion
As NFTs continue to redefine digital ownership and creative business models in 2025, how you store and secure them is just as vital as the art or utility they represent. By combining hardware wallets, advanced hot wallets, programmable smart wallets, and decentralized storage solutions like Arweave NFT storage and Storj NFT storage, you build a multi‑layered fortress around your assets. Working with a seasoned NFT development company or leveraging robust NFT development solutions ensures your platform or project follows best practices from the start. Keep your tools updated, educate your network, and always plan for recovery. With these steps in place, you can enjoy the freedom and potential of NFTs, knowing your digital treasures are protected for years to come.
#arweave nft storage#Storj nft storage#NFT development solutions#NFT platform development#NFT development company#blockchain nft development#NFT blockchain development
0 notes
Text
The Role of Data in the biggest stocks in nasdaq
The Nasdaq Composite Index is globally recognized as a barometer for high-growth companies across the digital, technological, and scientific landscape. From pioneering software platforms to biotech trailblazers, the biggest stocks in nasdaq highlight sector strength, strategic dominance, and technological transformation. These entities collectively set the tone for innovation, supply chain evolution, and enterprise scalability.
As global industries become more digitally integrated, the presence of these top-tier companies continues to define the future of communication, automation, and data processing.
Cloud Infrastructure and Software Dominance
Within the biggest stocks in nasdaq, cloud computing and software-as-a-service platforms play a major role. These businesses offer virtual environments that support data storage, customer relationship systems, workflow automation, and digital collaboration.
They are integral to modern business frameworks, offering remote accessibility, cost-efficiency, and enterprise-grade flexibility. Their platforms are utilized across industries including retail, education, logistics, and government operations, serving as the digital backbone for many global organizations.
Semiconductor Power and High-Performance Hardware
Semiconductor firms continue to play a central role in driving the technology ecosystem. Among the biggest stocks in nasdaq, these companies manufacture high-performance chips, memory modules, and processing units critical to the development of smart devices, autonomous systems, and AI applications.
They support hardware acceleration across cloud platforms, consumer electronics, and embedded systems. Innovations in chip design, energy efficiency, and fabrication technology remain vital to maintaining momentum in digital transformation.
Biotech and Genomics Innovation
Healthcare and biotechnology are also key pillars among the biggest stocks in nasdaq. These companies are advancing scientific research in genomics, diagnostics, and precision medicine. Their pipelines often include therapies for complex conditions, as well as tools for predictive diagnostics and patient monitoring.
By combining biological insights with machine learning and data analytics, these entities continue to redefine patient care, clinical trials, and therapeutic development timelines.
Cybersecurity and Threat Management
As enterprises embrace digital platforms, cybersecurity has become non-negotiable. A number of the biggest stocks in nasdaq specialize in endpoint security, identity management, and cloud-native threat intelligence.
Their systems protect critical data assets, infrastructure, and digital interactions across global supply chains. Whether deploying behavioral analytics or advanced encryption frameworks, these companies provide tools that strengthen risk management and ensure uninterrupted operations.
E-Commerce Ecosystems and Consumer Platforms
Digital retail infrastructure continues to evolve, and many of the biggest stocks in nasdaq are at the center of that transformation. These companies operate platforms that enable product discovery, payment integration, logistics coordination, and real-time customer engagement.
They offer seamless experiences for shoppers while enabling brands to leverage advanced data to forecast demand and optimize delivery networks. Their technologies continue to shape how global consumers interact with online marketplaces.
Fintech Services and Transaction Technologies
The integration of technology into finance has reshaped payment networks, peer-to-peer systems, and mobile financial platforms. Several of the biggest stocks in nasdaq offer financial services tools that support seamless digital transactions, fraud prevention, and API-enabled banking systems.
These solutions are increasingly embedded in mobile apps, e-commerce websites, and enterprise resource planning tools. The shift toward real-time, cross-border, and secure transactions continues to drive demand in this space.
Clean Energy and Environmental Solutions
Sustainability is emerging as a key focus among listed companies, and several clean energy providers have joined the ranks of the biggest stocks in nasdaq. These companies build solar modules, battery storage units, and smart grid solutions that support greener energy usage.
Their technologies enable more efficient energy consumption and help reduce dependency on traditional fuel sources. As environmental policies evolve, the role of these firms continues to expand across both public and private sectors.
Data Analytics and Enterprise Intelligence
Advanced data platforms have become essential to operations across every major industry. Companies within the biggest stocks in nasdaq offer tools for analytics, visualization, forecasting, and automated reporting.
These platforms help decision-makers gain insights into customer behavior, production trends, and financial performance. The ability to transform large volumes of data into actionable intelligence is central to remaining competitive in a data-driven economy.
Streaming, Media, and Digital Engagement
Multimedia platforms have also emerged as key players in the Nasdaq ecosystem. These companies provide content delivery networks, video streaming services, and social engagement tools that reach global audiences.
Their technology is tailored for real-time personalization, cross-device compatibility, and adaptive recommendations. As digital consumption habits evolve, these platforms remain instrumental in shaping entertainment and communication experiences.
Smart Manufacturing and Automation
Industrial firms in the biggest stocks in nasdaq focus on robotics, connected devices, and automated systems that support smart manufacturing environments. These companies build technologies that reduce manual intervention, increase throughput, and ensure operational accuracy.
Their products are used in warehousing, automotive production, and supply chain optimization, contributing to a more agile and responsive industrial landscape.
0 notes
Text
Teksun Inc is an ISO 9001:2015 certified IoT and AI Solutions Company specializing in Product Engineering Services supporting ODM & OEM for numerous B2B Applications & Use Cases. To know more about browse: https://teksun.com/ Contact us ID: [email protected]
#Teksun#Technology services#Artificial intelligence#Machine learning#IoT solutions#Embedded systems#Product engineering#Software development#Hardware design#Firmware development#Cloud computing#Industrial automation#Wireless communication#IoT applications
0 notes
Text

Looking to build smarter, faster, and more reliable electronics? Our high-precision PCB design and manufacturing services are made for innovators in IoT, MedTech, industrial automation, and embedded systems. Whether you're prototyping or scaling, we engineer hardware that performs under pressure.
💡 Explore custom electronic design and manufacturing services at 👉 www.auckam.com
#PCBDesign#IoTProjects#ElectronicsEngineering#SmartDevices#EmbeddedSystems#CustomHardware#PCBAssembly#ProductPrototyping#TechInnovation#IndustrialDesign#MedTechDevices#ManufacturingSolutions
0 notes