#Encrypt Microsoft SQL Server Traffic
Explore tagged Tumblr posts
Text
How to encrypt Microsoft SQL Server Traffic
In this article, we will discuss how to encrypt Microsoft SQL Server Traffic. You can encrypt all incoming connections to SQL Server or enable encryption for just a specific set of clients. For either of these scenarios, you first have to configure SQL Server to use a certificate that meets Certificate requirements for SQL Server before taking additional steps on the server computer or client…

View On WordPress
#Certificates#Encrypt Microsoft SQL Server Traffic#ForceEncryption#Microsoft Windows#Windows#Windows 10#Windows Server#Windows Server 2012#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
Inside the Mind of a Hacker: Understanding Cyber Criminals and Their Tactics

In today’s digital landscape, cybercrime has evolved into a sophisticated, multi-billion-dollar industry. Hackers operate with precision, using advanced techniques to breach security systems, steal sensitive data, and disrupt businesses. But what motivates these cybercriminals, and how do they think? To truly combat cyber threats, we must first understand the mindset of hackers and the strategies they employ.
If you're looking to safeguard yourself and build a career in cybersecurity, pursuing a Cyber Security Certification in Kolkata can equip you with the skills needed to protect against these evolving threats. Let’s dive into the mind of a hacker and explore their tactics.
The Psychology of a Hacker
1. Motivations Behind Cybercrime
Hackers are not always driven by the same goals. Understanding their motivations helps cybersecurity professionals develop better defense mechanisms. Common hacker motivations include:
Financial Gain: Cybercriminals engage in ransomware attacks, credit card fraud, and data breaches to steal money or sell information on the dark web.
Political or Ideological Beliefs: Hacktivists, such as Anonymous, target governments or corporations to protest against policies or social issues.
Espionage: State-sponsored hackers infiltrate government agencies, corporations, and research institutions to steal confidential data.
Personal Challenge or Notoriety: Some hackers break into systems purely for the thrill, to prove their skills, or to gain recognition in the hacking community.
Revenge: Disgruntled employees or individuals use hacking to sabotage organizations or individuals who have wronged them.
2. The Hacker Mindset
Hackers exhibit a combination of intelligence, curiosity, and persistence. Many have a deep understanding of coding, networking, and security vulnerabilities. Key psychological traits of hackers include:
Problem-Solving Skills: Hackers view security systems as puzzles to be cracked.
Anonymity & Deception: They leverage VPNs, proxy servers, and encryption to remain undetected.
Adaptability: As cybersecurity evolves, hackers continuously find new ways to bypass security measures.
Common Hacking Techniques and Tactics
Hackers use various methods to infiltrate systems. Some of the most common tactics include:
1. Phishing Attacks
Phishing remains one of the most effective hacking techniques. Hackers send deceptive emails or messages that trick users into revealing personal information, such as passwords and credit card details. They often impersonate banks, government agencies, or trusted brands.
Example: In 2021, a major phishing campaign targeted Microsoft users, tricking them into entering their credentials on a fake login page.
2. Malware and Ransomware
Hackers deploy malicious software (malware) to infect systems, steal data, or lock users out of their devices. Ransomware encrypts files and demands a ransom for their release.
Example: The WannaCry ransomware attack in 2017 affected over 200,000 computers worldwide, causing billions in damages.
3. Social Engineering
This tactic exploits human psychology rather than technical vulnerabilities. Hackers manipulate individuals into divulging sensitive information or granting unauthorized access.
Example: A hacker posing as an IT support technician might call an employee and ask for their login credentials.
4. SQL Injection Attacks
Hackers exploit vulnerabilities in websites that use SQL databases. By inserting malicious SQL code into input fields, they can access, modify, or delete database records.
Example: A well-known SQL injection attack targeted Yahoo! in 2012, exposing 450,000 user accounts.
5. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
These attacks overwhelm a system with excessive traffic, causing it to crash and become inaccessible.
Example: In 2016, the Mirai botnet launched a massive DDoS attack on Dyn, a major DNS provider, disrupting websites like Twitter, Netflix, and PayPal.
How to Defend Against Hackers
Understanding hacker tactics is the first step in securing digital assets. Here are essential strategies to protect against cyber threats:
1. Invest in Cybersecurity Education
A Cyber Security Certification in Kolkata can provide in-depth knowledge of ethical hacking, penetration testing, and risk management, helping individuals and businesses strengthen their defenses.
2. Use Strong Passwords and Multi-Factor Authentication (MFA)
Avoid using simple or reused passwords. Implement MFA to add an extra layer of security.
3. Keep Software and Systems Updated
Outdated software contains vulnerabilities that hackers exploit. Regular updates and security patches help close these loopholes.
4. Educate Employees on Cyber Threats
Since social engineering is a major attack vector, training employees to recognize phishing emails and suspicious activities is crucial.
5. Implement Firewalls and Intrusion Detection Systems (IDS)
These tools monitor and block unauthorized access attempts, enhancing network security.
6. Regularly Backup Data
Frequent backups protect against ransomware attacks. Store backups in a secure, offline location.
7. Conduct Penetration Testing
Simulating cyberattacks through ethical hacking helps identify vulnerabilities before malicious hackers exploit them.
Conclusion
Cybercriminals are constantly evolving, using innovative tactics to breach systems and exploit vulnerabilities. By understanding their mindset and techniques, individuals and businesses can better protect themselves from cyber threats.
If you're serious about cybersecurity, obtaining a Cyber Security Certification in Kolkata is a great way to gain the skills and knowledge needed to combat cyber threats effectively. Investing in cybersecurity today can save organizations from significant financial losses, data breaches, and reputational damage in the future.
Cybersecurity is not just a technology problem—it’s a human challenge. Stay informed, stay prepared, and stay secure.
0 notes
Text
Advanced Database Management in Full Stack Development
Introduction
A Full Stack Development project's foundation is effective database management. Data transactions and application performance are guaranteed by the capacity to build, optimize, and scale databases. Proficiency with SQL and NoSQL databases, indexing, query optimization, and high availability replication are essential for modern applications. To create scalable systems, developers also need to concentrate on cloud integration, backup plans, and database security. In order to guarantee maximum performance and dependability in full stack applications, this paper examines sophisticated database management strategies.
Choosing the Right Database: SQL vs. NoSQL
Choosing the right database is essential for the scalability of the program. Strong data consistency, defined schema, and ACID compliance are features of SQL databases (MySQL, PostgreSQL, and Microsoft SQL Server). Applications needing relational data storage, financial transactions, and sophisticated searches are best suited for them. NoSQL databases, such as MongoDB, Cassandra, and Firebase, offer distributed architecture, high scalability, and customizable schemas. Large-scale, unstructured data processing, such as real-time analytics and Internet of Things applications, is best handled by these. Database efficiency is increased by combining NoSQL for dynamic content and SQL for structured data.
Optimizing Query Performance and Scaling
Applications that have poorly optimized queries operate slowly. Data retrieval is accelerated by the use of indexing, query caching, and denormalization. In high-traffic applications, partitioning huge tables improves read/write performance. Performance is enhanced via read and write replicas, which disperse database loads. Sharding lowers latency by dividing big databases into smaller portions that are distributed across several servers. In full stack applications, database interaction is streamlined by using ORM (Object-Relational Mapping) technologies like SQLAlchemy, Hibernate, or Sequelize.
Database Security and Backup Strategies
In Full Stack Development, data availability and security must be guaranteed. Unauthorized access is avoided by putting role-based access control (RBAC) into practice. User information is protected by using hashing methods, SSL/TLS, and AES to encrypt important data. Data loss may be avoided by point-in-time recovery, disaster recovery plans, and routine database backups. AWS RDS, Google Cloud Firestore, and Azure Cosmos DB are examples of cloud-based databases that provide fault tolerance, replication, and automated backups to guarantee data dependability and integrity.
Conclusion
Building scalable, high-performance applications in Advanced Full Stack Development requires a solid understanding of database administration. System efficiency is increased by selecting between SQL and NoSQL databases, optimizing queries, and protecting data storage. A Full Stack Development Training curriculum gives developers hands-on experience while teaching them sophisticated database approaches. Database management internships provide professionals practical experience in handling data in the real world, preparing them for the workforce. A successful career in Full Stack Development is ensured by investing in database competence.
#advanced full stack development#advanced full stack development training#advanced full stack development internship#e3l#e3l.co
0 notes
Text
Comparing Amazon RDS and Aurora: Key Differences Explained
When it comes to choosing a database solution in the cloud, Amazon Web Services (AWS) offers a range of powerful options, with Amazon Relational Database Service (RDS) and Amazon Aurora being two of the most popular. Both services are designed to simplify database management, but they cater to different needs and use cases. In this blog, we’ll delve into the key differences between Amazon RDS and Aurora to help you make an informed decision for your applications.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is Amazon RDS?
Amazon RDS is a fully managed relational database service that supports multiple database engines, including MySQL, PostgreSQL, MariaDB, Oracle, and Microsoft SQL Server. It automates routine database tasks such as backups, patching, and scaling, allowing developers to focus more on application development rather than database administration.
Key Features of RDS
Multi-Engine Support: Choose from various database engines to suit your specific application needs.
Automated Backups: RDS automatically backs up your data and provides point-in-time recovery.
Read Replicas: Scale read operations by creating read replicas to offload traffic from the primary instance.
Security: RDS offers encryption at rest and in transit, along with integration with AWS Identity and Access Management (IAM).
What is Amazon Aurora?
Amazon Aurora is a cloud-native relational database designed for high performance and availability. It is compatible with MySQL and PostgreSQL, offering enhanced features that improve speed and reliability. Aurora is built to handle demanding workloads, making it an excellent choice for large-scale applications.
Key Features of Aurora
High Performance: Aurora can deliver up to five times the performance of standard MySQL databases, thanks to its unique architecture.
Auto-Scaling Storage: Automatically scales storage from 10 GB to 128 TB without any downtime, adapting to your needs seamlessly.
High Availability: Data is automatically replicated across multiple Availability Zones for robust fault tolerance and uptime.
Serverless Option: Aurora Serverless automatically adjusts capacity based on application demand, ideal for unpredictable workloads.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
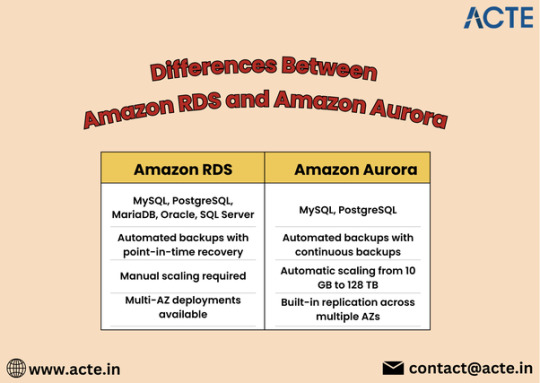
Key Differences Between Amazon RDS and Aurora
1. Performance and Scalability
One of the most significant differences lies in performance. Aurora is engineered for high throughput and low latency, making it a superior choice for applications that require fast data access. While RDS provides good performance, it may not match the efficiency of Aurora under heavy loads.
2. Cost Structure
Both services have different pricing models. RDS typically has a more straightforward pricing structure based on instance types and storage. Aurora, however, incurs costs based on the volume of data stored, I/O operations, and instance types. While Aurora may seem more expensive initially, its performance gains can result in cost savings for high-traffic applications.
3. High Availability and Fault Tolerance
Aurora inherently offers better high availability due to its design, which replicates data across multiple Availability Zones. While RDS does offer Multi-AZ deployments for high availability, Aurora’s replication and failover mechanisms provide additional resilience.
4. Feature Set
Aurora includes advanced features like cross-region replication and global databases, which are not available in standard RDS. These capabilities make Aurora an excellent option for global applications that require low-latency access across regions.
5. Management and Maintenance
Both services are managed by AWS, but Aurora requires less manual intervention for scaling and maintenance due to its automated features. This can lead to reduced operational overhead for businesses relying on Aurora.
When to Choose RDS or Aurora
Choose Amazon RDS if you need a straightforward, managed relational database solution with support for multiple engines and moderate performance needs.
Opt for Amazon Aurora if your application demands high performance, scalability, and advanced features, particularly for large-scale or global applications.
Conclusion
Amazon RDS and Amazon Aurora both offer robust solutions for managing relational databases in the cloud, but they serve different purposes. Understanding the key differences can help you select the right service based on your specific requirements. Whether you go with the simplicity of RDS or the advanced capabilities of Aurora, AWS provides the tools necessary to support your database needs effectively.
0 notes
Text
Unleashing the Power of ASP.NET Website Development Services for Robust Online Presence
Introduction:
In today's rapidly evolving digital landscape, having a strong online presence is non-negotiable for businesses aiming for success. Whether you are a startup, a small business, or a large enterprise, the key to staying competitive lies in a well-designed and functional website. ASP.NET, a powerful and versatile web development framework, has emerged as a top choice for businesses looking to create dynamic and scalable websites. In this blog post, we will explore the world of ASP.NET website development services, their benefits, and how they can contribute to the success of your online ventures.

Understanding ASP.NET:
ASP.NET, developed by Microsoft, is a robust and feature-rich framework for building web applications and services. It is a part of the Microsoft .NET platform and is widely used for creating dynamic and interactive websites. ASP.NET supports various programming languages such as C#, VB.NET, and F#, providing developers with flexibility and choice. The framework is known for its scalability, security features, and seamless integration with other Microsoft technologies.
Key Features of ASP.NET Website Development Services:
1. Scalability:
ASP.NET is designed to handle the growth of your business. Whether you are expecting a surge in website traffic or planning to expand your online offerings, ASP.NET ensures that your website can scale seamlessly to meet the demands.
2. Security:
Security is a top priority in the digital age, and ASP.NET comes equipped with built-in security features to protect your website and user data. With features like authentication, authorization, and data encryption, ASP.NET helps in creating secure web applications.
3. Performance Optimization:
ASP.NET is known for its performance optimization capabilities. The framework includes features like just-in-time compilation, caching, and native optimization, resulting in faster load times and improved overall performance.
4. Cross-Platform Compatibility:
ASP.NET Core, the cross-platform, open-source version of ASP.NET, allows developers to build and run applications on Windows, Linux, and macOS. This ensures that your website can reach a wider audience regardless of their preferred operating system.
5. Integration with Microsoft Technologies:
If your business relies on Microsoft technologies such as Azure, SQL Server, or Active Directory, ASP.NET seamlessly integrates with these technologies, providing a cohesive and efficient development environment.
Benefits of ASP.NET Website Development Services:
1. Rapid Development:
ASP.NET supports a model-view-controller (MVC) architecture, which facilitates rapid development by allowing developers to work on different components simultaneously. This results in quicker turnaround times for website development projects.
2. Cost-Effective Solutions:
The efficiency of ASP.NET development leads to cost savings. Rapid development, combined with the framework's scalability, ensures that your investment in website development provides long-term value for your business.
3. Maintenance and Updates:
ASP.NET simplifies the process of maintenance and updates. With features like automatic updates and a modular architecture, making changes to your website or adding new features becomes a streamlined process.
4. Community Support:
Being a product of Microsoft, ASP.NET benefits from a large and active community of developers. This means that you have access to a wealth of knowledge, tutorials, and support forums, ensuring that you are never alone in your development journey.
5. SEO-Friendly:
Search engine optimization (SEO) is crucial for the visibility of your website. ASP.NET allows developers to implement SEO best practices easily, ensuring that your website ranks well on search engine results pages (SERPs).
Conclusion:
In the competitive digital landscape, a well-designed and high-performance website is essential for business success. ASP.NET website development services provide a robust framework for creating dynamic, scalable, and secure websites that can meet the demands of today's businesses. Whether you are a startup, a small business, or a large enterprise, leveraging the power of ASP.NET can contribute significantly to your online presence and set you on the path to digital success. Invest in ASP.NET development services today and unlock the full potential of your online ventures.
1 note
·
View note
Text
What is Cloud Server management and How to set by set Managed Cloud server hosting?
Cloud server management refers to the process of overseeing and maintaining cloud servers, ensuring they run efficiently, securely, and in accordance with the needs of your business. "Best Managed cloud server hosting involves outsourcing" these management tasks to a third-party service provider, which can help you focus on your core business activities while experts take care of the technical aspects of server management. Here are "the steps to set up managed cloud server hosting":

Select a Cloud Service Provider: Choose a cloud service provider such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud, or a different provider based on your specific needs and preferences. The selection of the cloud provider will depend on factors like the services they offer, geographic availability, and pricing.
Choose the Right Cloud Server: Determine the type of cloud server (e.g., virtual machine instances) you need based on your application requirements, such as computing power, memory, storage, and network resources. Your "managed cloud server provider in Delhi" can assist in selecting the appropriate server configurations.
Select a Managed Cloud Server Provider: Research and choose a managed cloud server hosting provider. Consider factors like their reputation, expertise, service offerings, and pricing.
Engage with the Managed Cloud Server Provider: Contact the chosen provider to discuss your server management requirements. They will gather information about your specific needs, expected traffic, and application workloads.
Provision the Cloud Server: The managed cloud server provider will set up the cloud server environment for you based on your requirements. This typically includes deploying virtual machines, configuring storage, and setting up network components.
Data Migration and Application Deployment: If you have existing data or applications to move to the cloud server, work with the provider to ensure a smooth migration process. You may need to install and configure your software and applications as well.
Security Configuration: Ensure that the server and applications are properly secured. This includes setting up firewalls, intrusion detection systems, encryption, and access controls.
Managed cloud service providers in Delhi | Types of cloud managed Services in Dwarka | Cloud managed services scope of work | Benefits of managed cloud services | Cloud management services | Cloud management services company | Unmanaged cloud storage with nwspl |
Cloud Server Management in Delhi | Managed cloud server in Delhi | Cloud Server Manger in Delhi | Cloud server management in Delhi | Cloud based server manager in Delhi | Fully managed cloud server in Delhi | Cloud server management panel in Delhi | Cloud server management Services in Delhi | Cloud Server Management Software in Delhi | Managed Cloud server hosting in Delhi | Google Cloud Sql Server management studio in Delhi |
#Cloud Server Management in Delhi#Managed cloud server in Delhi#Cloud Server Manger in Delhi#Cloud based server manager in Delhi#Fully managed cloud server in Delhi#Cloud server management panel in Delhi#Cloud server management Services in Delhi#Cloud Server Management Software in Delhi#Managed Cloud server hosting in Delhi#Google Cloud Sql Server management studio in Delhi#Cloud server management on local machine#Managed Cloud dedicated server#Cloud servewr management tools#What is cloud management#What is cloud server#Managing the cloud infrastructure#Types of cloud management#Cloud server hosting#Cloud server for small business#Cloud server poviders#Cloud server cost#Cloud server meaning#Cloud server pricing#Cloud server VS physical server#Cloud server backup
0 notes
Text
"Mastering MySQL: Comprehensive Database Management Course"
I'm thrilled to address your inquiries about MySQL. My perspective and expertise have undergone significant growth in this field. MySQL enjoys widespread recognition and finds extensive applications across diverse industries.
MySQL is an open-source relational database management system (RDBMS) renowned for its versatility and utility in handling structured data. Initially developed by the Swedish company MySQL AB, it is presently under the ownership of Oracle Corporation. MySQL's reputation rests on its speed, reliability, and user-friendliness, which have fueled its adoption among developers and organizations of all sizes.

Key Attributes of MySQL:
1. Relational Database: MySQL organizes data into tables with rows and columns, facilitating efficient data retrieval and manipulation.
2. Open Source: Available under an open-source license, MySQL is freely accessible and modifiable, with commercial versions and support options for those requiring additional features.
3. Multi-Platform: MySQL caters to various operating systems, including Windows, Linux, macOS, and more, ensuring adaptability across diverse environments.
4.Scalability: MySQL seamlessly scales from small-scale applications to high-traffic websites and data-intensive enterprise systems, offering support for replication and clustering.
5. Performance: Recognized for high-performance capabilities, MySQL ensures swift data retrieval and efficient query execution, offering multiple storage engines with varying feature trade-offs.
6. Security: MySQL provides robust security features, encompassing user authentication, access control, encryption, and auditing to safeguard data and ensure compliance with security standards.
7. ACID Compliance: MySQL adheres to ACID principles, ensuring data integrity and reliability, even in the event of system failures.
8. SQL Support: Employing Structured Query Language (SQL), MySQL defines, manipulates, and queries data, aligning with a standard set of SQL commands for compatibility with various applications and development tools.
9. Community and Ecosystem: MySQL boasts a thriving user community, contributing to its development and offering extensive resources, including documentation, forums, and third-party extensions.
10.Integration: MySQL seamlessly integrates with multiple programming languages and development frameworks, making it a favored choice for web and application development.
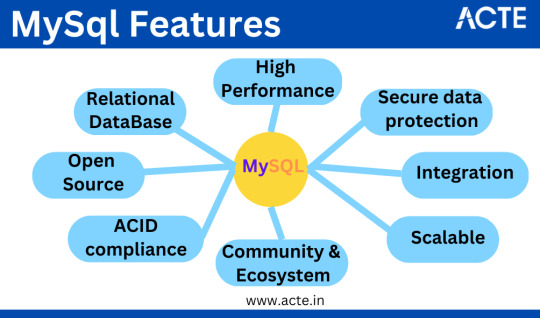
MySQL finds widespread usage in web applications, content management systems, e-commerce platforms, and numerous other software projects where structured data storage and retrieval are imperative. It competes with other relational databases such as PostgreSQL, Oracle Database, and Microsoft SQL Server in the database management system arena.
Should you seek to delve deeper into MySQL Course, I strongly recommend reaching out to ACTE Technologies, a hub for certifications and job placement opportunities. Their experienced instructors can facilitate your learning journey, with both online and offline options available. Take a methodical approach, and contemplate enrolling in a course if your interest persists.
I trust that this response effectively addresses your inquiries. If not, please do not hesitate to voice your concerns in the comments section. I remain committed to continuous learning.
If you've found my insights valuable, consider following me on this platform and giving this content an upvote to encourage further MySQL-related content. Thank you for investing your time here, and I wish you a splendid day.
1 note
·
View note
Text
Key Advantages of choosing Azure cloud services for your business

With the ever growing technology and its operational ways, all sizes of businesses need to find ways to remain competitive. The way the data is stored and managed becomes very important in a business. Cloud computing is a secure and cost-effective way of storing data that can be accessed anywhere at anytime. Being delivered over the cloud, it's not susceptible even to natural disasters affect power and servers in buildings on-site.
Here are few key advantages of choosing Microsoft Azure cloud services for your business:
Enhanced Security
Azure has been designed on SDL which is a leading security process to protect all your business data. With network encryption, every information that is transmitted remains protected. Apart from that, Azure generates real-time security alerts using threat intelligence and advanced threat protection. Threat intelligence reports provides insights of attackers and the methods they had used. Apart from that Azure has an uptime average of 99.995% which ensures business sustainability.
Scalability
Cloud computing with Azure is extremely scalable as well as performance efficient. Azure is designed to be apt for all sizes of business - be it a local cafe to a large scale enterprise. With its vertical scaling, it can handle applications growing with 100 to 1 million users without any additional piece of code needed from user’s end. Unlike traditional hosting, Azure goes beyond just increasing your server’s bandwidth with the increasing traffic. When it comes to data management, Azure cloud services use elastic SQL pools which ensure that the database performance is as good as locally hosted systems.
Powerful integration facilities
Azure complements well with your current infrastructure of microsoft products like outlook, sharepoint, office 365 etc. Apart from that it offers visual studio team services, enterprise softwares like Oracle, SAP and more for integration with no additional cost. This becomes convenient especially for small businesses to test their integration with these expensive softwares without having to invest in them.
Cost effective
Microsoft offers a very convenient pay as you use concept where you can expand slowly by paying for additional resources using Azure. Our cloud migration services help you datacentre your business information to cloud in the most effective manner. It allows business to have a scalable architecture that can scale up and down automatically depending on the processed jobs. So you literally pay only for what you use.
Efficient disaster recovery
Data is the core of any business. The impact of downtime and loss of data can be critical for a business. With its decentralised infrastructure, Azure comes with a solid data disaster recovery tool. You can create a specific data recovery plan individually for each business unit that can come handy during replication or failback situations. Azure can run backups in background as per the schedule and can recover data within few hours during crucial times.
Advanced data analytics capability
Azure has built-in capabilities to dive deep into the data and gather insights that can help a business analyse and built the next set of strategies to accelerate growth. As per the statistics, most enterprises across the globe have realized huge success with this platform.
If you have any questions about cloud computing with Azure, feel free to reach to us. Let us help you start your cloud computing journey with azure.
0 notes
Text
Microsoft Visual C++ 2011

Related searches
Microsoft Visual C++ Download
Download Visual C++ 2011
Microsoft Visual C++ 2011 X64
» microsoft visual c 2011 redistributable
» arcavir 2011 arcavir 2011
» artcam 2011 artcam 2011 32-bit download
» act 2011 pro_sage act pro 2011 download
» pro 2011 pit 2011
» audiocoder 2011 версия 2011
» promob plus 2011 render-up 2011
» trados 2011 sp2r trados 2011 sp2区别
» autocad lt 2011 autocad lt 2011 download
» promob 5 plus 2011 render up 2011
Microsoft Visual C and Wampserver installation Leave a Comment / Create an E-Commerce site with WordPress locally / By Feukeu To proceed with its installation, you need Microsoft Visual C 2010, 2011, 2012, and another redistributable Package corresponding to your version of the wamp server download. This article lists the download links for the latest versions of Microsoft Visual C. Visual Studio 2015, 2017 and 2019. Download the Microsoft Visual C Redistributable for Visual Studio 2015, 2017 and 2019. The following updates are the latest supported Visual C redistributable packages for Visual Studio 2015, 2017 and 2019.
microsoft c 2011 redistributable
at UpdateStar
More
Microsoft Visual C++ 2008 Redistributable 11.0.61030.0
The Microsoft Visual C++ 2008 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ on a computer that does not have Visual C++ 2008 installed. more info..
More
Microsoft Visual C++ 2010 Redistributable 12.0.30501
The Microsoft Visual C++ 2010 SP1 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ 2010 SP1 on a computer that does not have Visual C++ 2010 SP1 installed. more info..
More
Microsoft Visual C++ 2015 Redistributable Package 14.28.29617
More
Microsoft .NET Framework 5.0.3
The Microsoft .NET Framework 4 Client Profile redistributable package installs the .NET Framework runtime and associated files that are required to run most client applications.The .NET Framework is Microsoft's comprehensive and consistent … more info..
More
Microsoft OneDrive 21.052.0314.0001
Store any file on your free OneDrive (fromer SkyDrive) and it's automatically available from your phone and computers—no syncing or cables needed. more info..
More
Microsoft Silverlight 5.1.50918.0
Silverlight is essentially nothing more than Microsoft's vision of a cross-browser, cross-platform plug-in designed to be the source of rich online user experiences and to dislodge Flash from its current dominant position on the market. more info..
More
Microsoft Edge 90.0.818.51
More
Microsoft Update Health Tools 2.77.0.0
More
Microsoft Office Professional Plus 16.0.4266.1001
Microsoft Office Professional Plus will help you and your organization work more efficiently and effectively with a new set of powerful tools for creating, managing, analyzing, and sharing information. more info..
More
Microsoft SQL Server Compact Edition 3.1.0000
SQL Server Compact 3.5 is a free, easy-to-use embedded database engine that lets developers build robust Windows Desktop and mobile applications that run on all Windows platforms including Windows XP, Vista, Pocket PC, and Smartphone. more info..
Descriptions containing
microsoft c 2011 redistributable
More
Microsoft Visual C++ 2008 Redistributable 11.0.61030.0
The Microsoft Visual C++ 2008 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ on a computer that does not have Visual C++ 2008 installed. more info..
More
Microsoft Visual C++ 2010 Redistributable 12.0.30501
The Microsoft Visual C++ 2010 SP1 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ 2010 SP1 on a computer that does not have Visual C++ 2010 SP1 installed. more info..
More
Microsoft .NET Framework 5.0.3
The Microsoft .NET Framework 4 Client Profile redistributable package installs the .NET Framework runtime and associated files that are required to run most client applications.The .NET Framework is Microsoft's comprehensive and consistent … more info..
More
Microsoft Visual C++ 2005 ATL Update kb973923 8.0.50727.4053
A security issue has been identified that could allow an attacker to compromise your Windows-based system with Microsoft Visual C++ 2005 Redistributable Package Service Pack 1 and gain complete control over it. more info..
More
Intel Processor Graphics 27.20.100.7989
Intel X3000 Chipset incorporates key features available in previous Intel Graphics versions like Dynamic Video Memory Technology (DVMT) as well as hardware acceleration for 3D graphics that utilize Microsoft DirectX* 9.0C and OpenGL* 1.5X. more info..
More
Adobe Flash Player ActiveX 34.0.0.105
Adobe Flash Player ActiveX enables the display of multimedia and interactive content within the Internet Explorer web browser. more info..
More
Realtek High Definition Audio Driver 6.0.9088.1
REALTEK Semiconductor Corp. - 168.6MB - Freeware -
Audio chipsets from Realtek are used in motherboards from many different manufacturers. If you have such a motherboard, you can use the drivers provided by Realtek. more info..
More
MSXML 4.20.9876.0
Microsoft XML Core Services (MSXML) is a set of services that allow developers to build Windows-native XML-based applications. more info..
More
Microsoft Office Professional Plus 16.0.4266.1001
Microsoft Office Professional Plus will help you and your organization work more efficiently and effectively with a new set of powerful tools for creating, managing, analyzing, and sharing information. more info..
More
Microsoft Silverlight 5.1.50918.0
Silverlight is essentially nothing more than Microsoft's vision of a cross-browser, cross-platform plug-in designed to be the source of rich online user experiences and to dislodge Flash from its current dominant position on the market. more info..
Additional titles containing
microsoft c 2011 redistributable
More
Microsoft Visual C++ 2010 Redistributable 12.0.30501
The Microsoft Visual C++ 2010 SP1 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ 2010 SP1 on a computer that does not have Visual C++ 2010 SP1 installed. more info..
More
Microsoft Visual C++ 2008 Redistributable 11.0.61030.0
The Microsoft Visual C++ 2008 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ on a computer that does not have Visual C++ 2008 installed. more info..
More
Microsoft Visual C++ 2015 Redistributable Package 14.28.29617
More
Microsoft Edge 90.0.818.51
More
Microsoft OneDrive 21.052.0314.0001
Store any file on your free OneDrive (fromer SkyDrive) and it's automatically available from your phone and computers—no syncing or cables needed. more info..
Most recent searches
» amd catalyst install manager mise a jour
» heitai boruto
» xvid eos video
» adobe reader免費軟件
» locale setup manager
» eurek plus download
» pulse secure download host check
» octa capture downlaad
» acer crystal web cam update
» ace utilities v.6.5.0
» www.danytech.com tvhome madiad download
» mircale tunder
» e deklaracje desktop 2021
» programme connexion sfr fon
» lenobo photo
» flets east jp soft setup 簡単セットアップツール
» app lernwerkstadt
» nudi 4.0 download nudi.exe
» driver printer ar-5731 torrent
» sage direct
-->
Microsoft Visual C++ Download
Learn how to use C++, C, and assembly language to develop applications, services, and tools for your platforms and devices. Nordvpn utorrent.
Download
Install Visual Studio and choose your C++ workloads
Overview
Welcome to C++ in Visual Studio
Get Started
Nordvpn on multiple devices iphone. One NordVPN account will cover 6 devices at once, providing you 6 times the protection. Windows, macOS, Android, iOS, Linux – it doesn’t matter which operating system you use, NordVPN will hide your location, IP address and encrypt the traffic. Multiple Devices Allowed as One of the Six Limit One NordVPN subscription allows you to install NordVPN on six devices to be used; there are additional ways to get more VPN for the amount of devices you have. By using a router with NordVPN installed, you are able to connect through the VPN. A total of six devices can be connected with one NordVPN account at the same time. However, there is one condition. If you connect the devices to the same server, you have to choose different VPN protocols (TCP and UDP are different protocols, so you can connect one device.
Get started with Visual Studio and C++

What's new
What's new for C++ in Visual Studio
Get started with C++ and C
Download Visual C++ 2011
Learn to use the Visual Studio IDE
Microsoft Visual C++ 2011 X64
Open code from a repo
Build your code
Test your code
Write C++ and C apps in Visual Studio
Create a Windows Desktop app with Win32
Create a Windows DLL
Create a .NET component

Use the command-line tools
Compile C code
Compile C++/CLI
Use C++ and C in Visual Studio Code
Install the Microsoft C/C++ extension
Use C++ in the Windows Subsystem for Linux
Use C++ on MacOS
Languages and frameworks
C++ and C workloads, features, and libraries
Develop for your choice of platforms with Visual Studio tools.
Workloads
Features
Libraries
Microsoft Docs Q&A - C++ Team Blog - Twitter - Developer Community - Stack Overflow - How to report an issue - Suggest a feature - Contribute to C++ docs: Read our contributor guide.

0 notes
Text
Grafana Metabase

If you’ve ever done a serious web app, you’ve certainly met with a requirement for its monitoring, or tracking various application and runtime metrics. Exploring recorded metrics lets you discover different patterns of app usage (e.g., low traffic during weekends and holidays), or, for example, visualize CPU, disk space and RAM usage, etc. As an example, if the RAM usage graph shows that the usage is constantly rising and returns to normal only after the application restart, there may be a memory leak. Certainly, there are many reasons for implementing application and runtime metrics for your applications.
There are several tools for application monitoring, e.g. Zabbix and others. Tools of this type focus mainly on runtime monitoring, i.e., CPU usage, available RAM, etc., but they are not very well suited for application monitoring and answering questions like how many users are currently logged in, what’s the distribution of server response times, etc.
When comparing Grafana and Metabase, you can also consider the following products. Prometheus - An open-source systems monitoring and alerting toolkit. Tableau - Tableau can help anyone see and understand their data. Connect to almost any database, drag and drop to create visualizations, and share with a click.
Here's what people are saying about Metabase. Super impressed with @metabase! We are using it internally for a dashboard and it really offers a great combination of ease of use, flexibility, and speed. Paavo Niskala (@Paavi) December 17, 2019. @metabase is the most impressive piece of software I’ve used in a long time.
时间序列,日志与设备运行数据分析选 Grafana;企业生产经营数据分析则可以选 Superset。 Metabase. Metabase 目前在 GitHub 上受欢迎程度仅次于 Superset,Metabase 也是一个完整的 BI 平台,但在设计理念上与 Superset 大不相同。. Kibana and Metabase are both open source tools. Metabase with 15.6K GitHub stars and 2.09K forks on GitHub appears to be more popular than Kibana with 12.4K GitHub stars and 4.81K GitHub forks.
In this post, I’ll show you, how to do real time runtime and application monitoring using Prometheus and Grafana. As an example, let’s consider Opendata API of ITMS2014+.
Prometheus
Our monitoring solution consists of two parts. The core of the solution is Prometheus, which is a (multi-dimensional) time series database. You can imagine it as a list of timestamped, named metrics each consisting of a set of key=value pairs representing the monitored variables. Prometheus features relatively extensive alerting options, it has its own query language and also basic means for visualising the data. For more advanced visualisation I recommend Grafana.
Prometheus, unlike most other monitoring solutions works using PULL approach. This means that each of the monitored applications exposes an HTTP endpoint exposing monitored metrics. Prometheus then periodically downloads the metrics.
Grafana
Grafana is a platform for visualizing and analyzing data. Grafana does not have its own timeseries database, it’s basically a frontend to popular data sources like Prometheus, InfluxDB, Graphite, ElasticSearch and others. Grafana allows you to create charts and dashboards and share it with others. I’ll show you that in a moment.
Publishing metrics from an application
In order for Prometheus to be able to download metrics, it is necessary to expose an HTTP endpoint from your application. When called, this HTTP endpoint should return current application metrics - we need to instrument the application. Prometheus supports two metrics encoding formats - plain text and protocol buffers. Fortunately, Prometheus provides client libraries for all major programming languages including Java, Go, Python, Ruby, Scala, C++, Erlang, Elixir, Node.js, PHP, Rust, Lisp Haskell and others.
As I wrote earlier, let’s consider ITMS2014+ Opendata API, which is an application written in Go. There is an official Prometheus Go Client Library. Embedding it is very easy and consists of only three steps.
Free microsoft office download for mac full version. The first step is to add Prometheus client library to imports:
The second step is to create an HTTP endpoint for exposing the application metrics. In this case I use Gorilla mux and Negroni HTTP middleware:
We are only interested in line 2, where we say that the /metrics endpoint will be processed by Prometheus handler, which will expose application metrics in Prometheus format. Something very similar to the following output:
In production, you would usually want some kind of access control, for example HTTP basic authentication and https:
Although we have only added three lines of code, we can now collect the application’s runtime metrics, e.g., number of active goroutines, RAM allocation, CPU usage, etc. However, we did not expose any application (domain specific) metrics.
In the third step, I’ll show you how to add custom application metrics. Let’s add some metrics that we can answer these questions:
which REST endpoints are most used by consumers?
how often?
what are the response times?
Grafana Metabase On Pc
Whenever we want to expose a metric, we need to select its type. Prometheus provides 4 types of metrics:
Counter - is a cumulative metric that represents a single numerical value that only ever goes up. A counter is typically used to count requests served, tasks completed, errors occurred, etc.
Gauge - is a metric that represents a single numerical value that can arbitrarily go up and down. Gauges are typically used for measured values like temperatures or current memory usage, but also “counts” that can go up and down, like the number of running goroutines.
Histogram - samples observations (usually things like request durations or response sizes) and counts them in configurable buckets. It also provides a sum of all observed values.
Summary - is similar to a histogram, a summary samples observations (usually things like request durations and response sizes). While it also provides a total count of observations and a sum of all observed values, it calculates configurable quantiles over a sliding time window.
In our case, we want to expose the processing time of requests for each endpoint (and their percentiles) and the number of requests per time unit. As the basis for these metrics, we’ve chosen the Histogram type. Let’s look at the code:
We’ve added a metric named http_durations_histogram_seconds and said that we wanted to expose four dimensions:
code - HTTP status code
version - Opendata API version
controller - The controller that handled the request
action - The name of the action within the controller
For the histogram type metric, you must first specify the intervals for the exposed values. In our case, the value is response duration. On line 3, we have created 36 exponentially increasing buckets, ranging from 0.0001 to 145 seconds. In case of ITMS2014+ Opendata API we can empirically say that most of the requests only last 30ms or less. The maximum value of 145 seconds is therefore large enough for our use case.
Finally, for each request, we need to record four dimensions we have defined earlier and the request duration.Here, we have two options - modify each handler to record the metrics mentioned above, or create a middleware that wraps the handler and records the metrics. Obviously, we’ve chosen the latter:
As you can see, the middleware is plugged in on line 8 and the entire middleware is roughly 20 lines long. On line 27 to 31, we fill the four dimensions and on line 32 we record the request duration in seconds.
Configuration
Since we have everything ready from the app side point of view, we just have to configure Prometheus and Grafana.
A minimum configuration for Prometheus is shown below. We are mainly interested in two settings, how often are the metrics downloaded (5s) and the metrics URL (https://opendata.itms2014.sk/metrics).
A minimal Grafana configuration:
Note: As we can see, a NON TLS port 3000 is exposed, but don’t worry there is a NGINX in front of Grafana listening on port 443, secured by Let’s Encrypt certificate.
Monitoring
Finally, we get to the point where we have everything we need. In order to create some nice charts it is necessary to:
Open a web browser and log into Grafana
Add Prometheus data source
Create dashboards
Create charts
An example of how to create a chart showing the number of HTTP requests per selected interval is shown on the following figure.
Similarly, we’ve created additional charts and placed them in two dashboards as shown on the following figures.
Summary
In this post, we have shown that the application and runtime monitoring may not be difficult at all.
Prometheus client libraries allow us to easily expose metrics from your applications, whether written in Java, Go, Ruby or Python. Prometheus even allows you to expose metrics from an offline applications (behind corporate firewalls) or batch applications (scripts, etc.). In this case, PUSH access can be used. The application then pushes metrics into a push gateway. The push gateway then exposes the metrics as described in this post.
Grafana can be used to create various charts and dashboards, that can be shared. Even static snapshots can be created. This allows you to capture an interesting moments and analyze them later.
Reports and Analytics
Powerful Enterprise Grade Reporting Engine
Elegant SQL interface for people who need a little more power
Widgets for Creating Bar Chars, Pie Charts, Line Graphs
Multiple Dashboards with different personal widgets
Create, organize, and share dashboards with others
Dashboards
Open Source
Completely Open Sources
Community Contribution Available
Simple to Use even for beginners
Install on premises or in the Cloud
Free and Simple to Use
Integrations
Integration with any Data Source in SQL
PostgreSQL, MySQL, Maria DB
Oracle, MS SQL or IBM DB2
Ready Plugins Available
Metabase Vs Grafana
Altnix Advantage
Metabase Consulting Services
Altnix provides Professional services for Consulting on Metabase products. Following items are covered:
Consulting Services for Metabase business intelligence tool
Best practices and guidelines on how to adopt the Metabase business intelligence tool
Architecture Design for Metabase
Technology Roadmap for Metabase adoption at your organization
Solution Design on using Metabase business intelligence tool
Metabase Implementation and Deployment
Altnix will implement Metabase based business intelligence and Analytics solution keeping in mind the business requirements. Implementation includes the following:
Integration with different databases and data sources
Extract Transform Load (ETL) Design
Designing Queries to be used in Metabase
Widgets and Dashboards design in Metabase
Reports Design in Metabase
Development and Design Implementation
UAT and Testing Activities
Production Implementation and Go Live
Warranty Support Period Included
Metabase Customization
Grafana Metabase On Twitter
Altnix will customize your Metabase installation so that it is a better fit for your business environment.
Creating new visualizations and dashboards as per customer needs
Creating custom reports and charts as per customer needs
Adding new scripts, plug-ins, and components if needed
Third-Party Integration
Altnix will integrate Metabase business intelligence tools with other third-party tools to meet several use cases.
Ticketing systems such as LANDesk, BMC Remedy, Zendesk, and ((OTRS)) Community Edition
ITSM Tools such as ((OTRS)) Community Edition, GLPi Network Editon, ServiceNow, and HP Service Manager
Monitoring tools such as Zabbix, Nagios, OpenNMS, and Prometheus
IT Automation Tools such as StackStorm, Ansible, and Jenkins

24x7 AMC Support Services
Altnix offers 24x7 support services on an AMC or per hour basis for new or existing installations on the Metabase Business intelligence tool. Our team of experts are available round the clock and respond to you within a predefined SLA.
Case Studies
Knute Weicke
Security Head, IT
Fellowes Inc, USA
Altnix was an instrumental partner in two phases of our Security ISO needs. The first being a comprehensive developed Service/Ticketing system for our global offices. The second being that of an Asset Management tool that ties all assets into our Ticketing systems to close a gap that we had in that category. They are strong partners in working towards a viable solution for our needs
The Altnix team was very easy to work with and resolved our needs in a timely manner. Working with Altnix, allowed us to focus on our core business while they handled the technical components to help streamline our business tools. We have found a strategic partner in Altnix
Johnnie Rucker
General Manager
Encore Global Solutions, USA
White Papers

0 notes
Text
Using Amazon RDS for SQL Server in a hybrid cloud environment
A common use case in an enterprise cloud database adoption strategy is to move your database workloads to the cloud first, while slowly moving the rest of your applications in batches. This post looks into the various possible scenarios and configurations you can use when accessing an Amazon RDS for SQL Server database instance from your on-premises or hybrid environments. Basic AWS infrastructure components Before we dive into the hybrid data center discussion, let’s quickly familiarize ourselves with some of the components we refer to throughout this post: Amazon VPC – Amazon Virtual Private Cloud (Amazon VPC) lets you launch AWS resources in a logically isolated virtual network that you define. You have complete control over your virtual networking environment, including selecting your own IP address range, creating subnets, and configuring route tables and network gateways. You can use both IPv4 for most resources in your virtual private cloud, which helps ensure secure and easy access to resources and applications. Subnet – A subnet divides IP address space into logical subdivision. A VPC spans all the Availability Zones in the Region. After creating a VPC, you can add one or more subnets in each Availability Zone. VPN – A VPN, or virtual private network, is an encrypted connection over the internet between networks or devices. AWS Direct Connect – AWS Direct Connect is a network service that provides an alternative to using the internet to utilize AWS Cloud services. AWS Direct Connect enables you to have low latency, secure, and private connections to AWS for workloads that require higher speed or lower latency than the internet. Use case 1: Using a site-to-site VPN Let’s begin by discussing the simplest way of getting from your data center to AWS: by using a secure VPN connection between your data center and AWS, over the internet. In this setup, you create a VPC with a range of IP address in your AWS account and create subnets by further subdividing the VPC IP range. For this post, we create two subnets, private and public, and we place the RDS DB instance inside this private subnet. Private subnet resources don’t get a public routable IP address. In this configuration, you use the Site-to-Site VPN connection to connect your data center to the VPC. In your data center, you have a physical device or a software application that works as a customer gateway device. You create and configure a customer gateway resource that represents the customer gateway device in your data center. On the AWS side, you create and configure a virtual private gateway. For more information about individual component configuration, see How AWS Site-to-Site VPN works. The following diagram shows a simple setup where you have a single VPC. For a more complete discussion on configuring a VPN with Amazon RDS, see Accessing an Amazon RDS instance remotely using AWS Client VPN. What if you have more than one VPC? This is often the case in an enterprise environment. In this situation, you can use AWS Transit Gateway, which acts as a transit hub. You can use a transit gateway to interconnect your VPCs and on-premises networks. The following diagram shows a configuration that utilizes a transit gateway. When creating these connections, be careful to not overlap IP address ranges between the VPCs and the on-premises IP address space. If you have more than one data center that needs to communicate with AWS, you can route traffic from multiple remote locations to your AWS VPCs, while continuing to use a virtual private gateway or transit gateway. Another variation of this configuration is to use the AWS VPN CloudHub. If you have multiple AWS Site-to-Site VPN connections, you can provide secure communication between sites using the VPN CloudHub. This enables your remote sites to communicate with each other, and not just with the VPC. The VPN CloudHub operates on a simple hub-and-spoke model. This design is suitable if you have multiple branch offices and want to implement a convenient, potentially low-cost hub-and-spoke model for primary or backup connectivity between these remote offices. Use case 2: Using AWS Direct Connect Site-to-Site VPN connectivity is a simple and great way to get connected to AWS from your data center. However, as you start to use more and more resources in AWS from your remote location, the limited bandwidth of the VPN connection and its reliance over the public internet start to become a bottleneck. Maximum bandwidth per VPN tunnel is 1.25 Gbps and can’t be increased further. To make higher bandwidth available between your DC and AWS, you can use AWS Direct Connect. With AWS Direct Connect, you can establish a secure and reliable high-bandwidth connection between your data center location and AWS. AWS Direct Connect lets you link your DC network to an AWS Direct Connect location over a standard Ethernet fiber-optic cable, thereby completely bypassing the internet and avoiding network congestion. You can create two types of connections: Dedicated connection – A physical Ethernet connection associated with a single customer. You can provision either 1 Gbps or 10 Gbps port speeds with direct connections. Hosted connection – A physical Ethernet connection that an AWS Direct Connect Partner provisions on behalf of a customer. You can provision sub 1 Gbps connection speeds (50 Mbps up to 1 Gbps) and sub 10 Gbps speeds (1 Gbps up to 10Gbps) when using a hosted connection. With AWS Direct Connect, you can create three types of virtual interfaces: Public virtual interface – A public VIF lets you interface directly to public AWS services (such as Amazon Simple Storage Service (Amazon S3)), bypassing public internet Private virtual interface – A private VIF enables access to your AWS VPC directly, bypassing internet service providers in your network path Transit virtual interface – A transit VIF lets you interface with multiple VPCs from your data center directly The following diagram shows a setup with a private VIF connection between your data center and AWS VPC. After the AWS Direct Connect connection is established, the application in your data center can access RDS databases by using the RDS DB endpoints. This is just an overview of AWS Direct Connect; a comprehensive discussion is beyond the scope of this article. For more information, see the AWS Direct Connect User Guide. Use case 3: Other cloud providers and hosting providers There may be situations where you need to establish connectivity between other cloud providers or hosting locations and AWS. This scenario can be treated similar to the VPN scenario discussed previously. The AWS side and the VPN stays identical, but instead of a customer gateway in the customer data center, you create it with the vendor cloud provider or in the hosting location. Extending on-premises Microsoft Active Directory and Kerberos authentication to the cloud A common use case is to extend Microsoft Active Directory (AD) authentication to cloud, so on-premises users can continue to authenticate with managed RDS DB instances using their AD credentials. To achieve this, you need to use AWS Directory Service for Microsoft Active Directory and create a trust relationship with the on-premises AD so authentication requests can be forwarded. When users authenticate with an RDS DB instance joined to the trusting domain, authentication requests are forwarded to the domain directory that you create with AWS Directory Service. You can establish trust in one of the two directions; both are supported by AWS Managed Microsoft AD: One-way trust – A unidirectional authentication path created between two domains. In a one-way trust between Domain A and Domain B, when Domain B has configured to trust Domain A, users in Domain A can access resources in Domain B; however, users in Domain B can’t access resources in Domain A. Two-way trust – Domain A trusts Domain B, and Domain B trusts Domain A. This configuration means that authentication requests can be passed between the two domains in both directions. In addition to the flow of the trust, you also have to choose the type of trust as a forest trust. When you configure a forest trust, you can allow any contiguous namespace domain in the trusting forest to be accessible to any security principal in the trusted forest. You most likely configure forest trusts if your organization has two or more AD forests. Forest trusts provide name suffix routing, which routes the Kerberos authentication requests to the correct domain. After you make the appropriate choices and configure the AWS Managed Microsoft AD, your on-premises application can connect to the RDS database with their existing AD credentials. For more information about this configuration, see Preparing on-premises and AWS environments for external Kerberos authentication for Amazon RDS. The following diagram shows an example setup between on-premises AD and AWS Managed Microsoft AD with a one-way forest trust relationship. Conclusion This post discussed various methods you can employ to efficiently extend your data center to the AWS Cloud and get the applications in the data center or other remote locations talking seamlessly to RDS DB instances. This post is meant to give you an overview of the options available; for in-depth discussions and configurations, refer to the blog posts and AWS service user guides linked throughout the post. We hope this was helpful to get you started on your cloud journey or accelerate an ongoing project. We welcome your thoughts on this topic, so please leave your feedback in the comments section. Happy cloud computing! About the Author Aditya Samant is a Solutions architect specializing in databases at AWS. His day job allows him to help AWS customers design scalable, secure and robust architectures utilizing the most cutting-edge cloud technologies. When not working Aditya enjoys retro PC tech, playing computer games and spending time with his family and friends. https://aws.amazon.com/blogs/database/using-amazon-rds-for-sql-server-in-a-hybrid-cloud-environment/
0 notes
Text
How to Pass Microsoft Azure Foundation Exam AZ-900 (Part 2 of 3)
The Microsoft Azure Foundation Exam AZ-900 or the equivalent from AWS are usually the first cloud certificates that someone new to the cloud starts with. Both cover basic cloud concepts and ensure that you gain a profound understanding of the respective services. As the passing grade of 80% for the AZ-900 is quite high, it is advisable to thoroughly study for the exam. This is the first of three posts that will provide you with all key information about the Azure services that you need to pass the Azure Foundation Exam AZ-900.
The following structure is taken from the latest exam syllabus for the Azure Foundation 2021 and indicates the weight of each chapter in the exam. For each chapter, I have written down a very brief summary of key concepts and information that are typically asked for during the exam. The summary is a great resource to check and finalize your studies for the exam. However, if you are new to the topic, you should first start by going through the official Microsoft Azure training materials.
This is part 2 of the three-parts series regarding the Microsoft Azure Foundation exam AZ-900 and it will cover the third and fourth topic from the content below:
1. Describe Cloud Concepts (20-25%)
2. Describe Core Azure Services (15-20%)
3. Describe core solutions and management tools on Azure (10-15%)
3.1 Describe core solutions available in Azure
3.2 Describe Azure management tools
4. Describe general security and network security features (10-15%)
4.1 Describe Azure security features
4.2 Describe Azure network security
5. Describe identity, governance, privacy, and compliance features (20- 25%)
6. Describe Azure cost management and Service Level Agreements (10- 15%)
3. Describe core solutions and management tools on Azure (10-15%)
3.1 Describe core solutions available in Azure
Virtual Machines
A virtual machine is an IaaS service. Administrators from a company would have full control over the operating system and be able to install all applications on it. For example, Virtual machines can have a VPN installed that encrypts all traffic from the virtual machine itself to a host on the Internet. They can also transfer a virtual machine between different subscriptions.
Scale sets help to manage increased demands, load balancer help to distribute user traffic among identical virtual machines. Azure Virtual Machine Scale Sets are used to host and manage a group of identical Virtual Machines.
To avoid failure in case that a data center fails, you need to deploy across multiple availability zones. At least two virtual machines are needed to ensure 99.99% up time. If a virtual machine is switched off, there are no costs for processing, but still for storage services.
Containers
Containers are more lightweight than virtual machines. Instead of virtualizing the complete operating system, they only need the images and libraries and access the underlying operating system from the host environment. Multiple containers are managed with Azure Kubernetes, which is an IaaS solution.
Storage
Data disks for virtual machines are available through blob storage. Blob storage costs depend on the region. Storage costs depend on the amount of stored data, but also on the amount of read and write operations. Transfers between different regions also costs.
An Azure Storage account – file service – can be used to map a network drive from on premise computers to a Microsoft Azure storage.
Cool storage and archive storage can be used for data that is infrequently accessed.
Further Azure Services
Azure SQL database is a PaaS service. Companies buying the service would not have control over the underlying server hosting in Azure
Azure Web App is a PaaS solution, accessible via https://portal.azure.com. One would not have full access on the underlying machine hosting the web application
Azure DevOps is an integration solution for the deployment of code. It provides a continuous integration and delivery toolset
Azure DevTestLabs quickly provides development and test environments, such as 50 customized virtual machines per week
Azure Event Grid can collect events from multiple sources and process them to an application
Azure Databricks is a big data analysis service for machine learning
Azure Machine Learning Studio can be used to build, test, and deploy predictive analytics solutions
Azure Logic Apps is a platform to create workflows
Azure Data Lakes is a storage repository holding large amounts of data in its native, raw format
Azure Data Lake Analytics helps to transform data and provide valuable insights on the data itself
Azure SQL Data Warehouse is a centralized repository of integrated data from one or more sources. It requires zero administration of the underlying infrastructure and provides low latency access to the data
Cosmos DB Service is a globally distributed, multimodal database service. It can host tables and json documents in Azure without required administration of the underlying infrastructure
Azure Synapse Analytics is an analytics service that brings together enterprise data ware housing and Big Data Analytics
Azure HD Insight is a managed, full-spectrum, open-source analytics service. It can be used for frameworks such as Hadoop, Apache etc
Azure Functions App and Azure Logic App are platforms for serverless code. Azure Logic focuses on workflows, automation, integration, and orchestration, while Azure Functions merely executes code
Azure App Services hosts web apps / web-based applications. It requires to manage the infrastructure
Azure Marketplace is an online store that offers applications and services either built on or designed to integrate with Azure
IoT Central provides a fully managed SaaS solution that makes it easy to connect, monitor, and manage IoT assets at scale
IoT Hub can be used to monitor and control billions of Internet of Things assets
IoT Edge is an IoT solution that can be used to analyze data on end user devices
Azure Time Series Insights provides data exploration and telemetry tools to help refine operational analysis
Azure Cognitive Services is a simplified tool to build intelligent Artificial Intelligence applications
3.2 Describe Azure management tools
Azure Applications Insights monitors web applications and detects and diagnoses anomalies in web apps
The Azure CLI, Azure Powershell, and Azure Portal can be used on Windows 10, Ubuntu, and macOS machines
Cloud Shell works on Android or MacOS that has Powershell Core 6.0 installed
Windows PowerShell and Command Prompt can be used to install the CLI on a computer
4. Describe general security and network security features (10-15%)
4.1 Describe Azure security features
The Azure Firewall protects the network infrastructure
The Azure DDoS Protection provides protection against distributed denial of service attacks
Network Security Groups restrict inbound and outbound traffic. They are used to secure Azure environments
Azure Multi-Factor Authentication provides an extra level of security when users log into the Azure Portal. It is available for administrative and non-administrative user accounts
The Azure Key Vault can be used to store secrets, certificates, or database passwords etc.
Azure Information Protection encrypts documents and email messages
Azure AD Identity Protection can make users that try to login from an anonymous IT address to need to change their password
Authentication is the process of verifying a user´s credentials
4.2 Describe Azure network security
A Network Security Group can filter network traffic to and from Azure resources in an Azure virtual network. They can also ensure that traffic restrictions are in place so that a database server can only communicate with the web browser
An Azure Virtual Network can provide an isolated environment for hosting of virtual machines
A Virtual Network Gateway is needed to connect an on-premise data center to an Azure Virtual Network using a Site-to-Site connection
A Local Network Gateway can represent a VPN device in the cloud context
0 notes
Text
Enable Encryption for Microsoft SQL Server Connections
Enable Encryption for Microsoft SQL Server Connections

It’s late afternoon and I just got a very interesting assignment. A client of mine wants to connect to their Microsoft SQL Server over a public network without a VPN, and he asks me how we can best secure this connection. The first thing that crossed my mind was encryption!
So I told him that let’s enable encryption of traffic going through port 1433 so that we can minimize this giant…
View On WordPress
0 notes
Text
3 THINGS TO EXTEND THE LIFE OF YOUR WEBSITE

There are lots of things that you can do to extend the life of your website from the very beginning; allowing it to run fast and reliably while also being safe from malicious attacks. However, there are three forgotten areas that you should be concerned about when developing a new site; security, stability, and performance.
Let’s discuss some aspects of each area and how they can increase the safety, reliability, and performance of your website.
Security
When most people think about web security, they think about someone hacking into the site and stealing customer data. However, this is not always the case. Sometimes hackers want to use your web server for other types of illegal or unethical practices such as setting up an email server to forward spam, using it to host illegal files or even illegal Bitcoin mining–just to name a few.
There’s nothing worse than having your website infecting your customer’s computers. Not only will Google mark your website as malicious but other filtering and antivirus services will blacklist your website and block their users from visiting it. From being blacklisted as a spammer to having your hosting provider completely shut you down – there’s no good outcome.
The cost of clean up can vary depending on how complicated your website is, the type of infection, and the quality of your backups.
If you are storing customer information, you may need to contact your insurance company and potentially report the breach. It’s a mess no matter how you look at it.
Below are some of the methods you can employ to reduce the risk of your web server being hacked as well as some overall best practices to prevent your server from being misused.
1. Prevent SQL Injection Attacks
If you use a data store that takes advantage of SQL and you use SQL directly in your code, then you could open yourself up to the possibility that a hacker will send malicious code that can cripple your site and/or corrupt your data. The best way to prevent this is to use structured parameters in your Transact SQL code. If you are using Microsoft SQL Server, you can also choose not to use open SQL in your code at all. Instead, you can use stored procedures that use formatted parameters. This will prevent random statements from being executed, and it will also be much faster since your SQL will be precompiled on the server.
2. Avoid Detailed Error Messages
If an error occurs, resist the temptation to use them as debugging tools. Handle the errors gracefully by giving the user a vague error statement and provide them navigation back to the homepage or the page they were on previously. Giving away too much information can give hackers what they need to exploit your site.
3. Prevent Cross-Site Scripting Attacks
Limit and evaluate comments and other forms of input submitted by users to guard against JavaScript injection attacks. You can set attributes through parameterized functions similar to the way you prevent SQL injection attacks. You can also employ the use of Content Security Policy to limit what types of JavaScript that can run in your pages.
4. Use Client and Server-Side Validation
Validate user input on both the client and server levels to make sure that malicious JavaScript wasn’t inserted between when the request was sent from the client to the time it arrives at the server.
5. Use HTTPS
Encrypting the traffic between the user’s browser and the server using SSL is always a good idea when the potential of transmitting sensitive data exists. This will prevent hackers from grabbing and deciphering the data as it is transmitted.
6. Use Two-factor Authentication to Log In
Using two-factor authentication to log into the management area of your website. Two-factor authentication essentially not only a username and password but potentially a continuously changing token/PIN or some sort of additional validation (i.e. a prompt on your cell phone) to verify it is you. Even if someone has your username and password, they can’t get in without the extra piece of information.
7. Keep Your Software Up to Date
In this day and age, you should be using a content management system (CMS). If you have an admin area you log into to manage content, then you are using a CMS. The CMS provider regularly provides updates to their core system, and various vendors provide updates to their plugins. Some updates add functionality, but many of the updates in between are primarily to fix security holes. If you don’t keep your system up to date, you are leaving yourself open to known vulnerabilities.
8. File Change Detection
You can run scripts on your server that notifies you of any changed files. There are some files that shouldn’t change often or at all unless you install an update. If you see that file change, you should be on high alert to find out what changed and who changed it. This is essentially a canary in a coal mine – it’s an early detection system.
9. Limit the Number of Login Attempts
Most systems these days can block an IP address if it has failed multiple authentication requests within a given period. Hackers have scripts that try different combinations to get in. If your website allows someone to continue trying, they may eventually get in. If you limit their ability to try new combinations, you may be able to keep them out. An example ruleset may look like five failed authentication attempts within a three minute period makes the user wait 15 minutes before allowing them to try again. You could even block their IP completely after a certain number of attempts.
10. Think in Layers
Consider someone picking a lock only to be met with another door with another lock. You can protect your website directly, but you should also protect your web server. You can use hardware or software firewalls, DDOS prevention systems, IP filtering, standard port changes, and malware scans to add an extra layer of protection.
Stability
Stability is a hard thing to define. There are lots of things that you should be aware of during development to make your site perform reliably and be more stable, such as cleaning up user sessions, guarding against memory leaks and managing garbage collection. There are also things that you can monitor for stability after the site has been deployed, like:
1. Clean Code
There is no replacement for clean code. Not only will it be more efficient, but it will be easier to track down bugs as well as easier for a new developer to understand. Code with no architecture or “spaghetti code” as we call doesn’t define code in a way that is separate and understandable. Instead, it is all mixed together and potentially duplicated in different areas of the site. There’s not much you can do with a site like this.
2. Load Testing
You should be utilizing cloud-based load testing tools if your website is expected to function under heavy load or heavy load spikes. You can create load simulations to see how your website performs under different scenarios. Make sure your testing environment matches your production environment.
3. Customize Memory Limits
If you have your own server make sure that your site’s memory limit is set to match your sites requirements as well as the resources of your server. You don’t want to make the website run on too little memory, but you also don’t want to allow one connection to use up all of your memory.
4. Cross Browser Testing
Stability is in the eye of the beholder. Make sure you test on the most popular version of Internet Explorer, Edge, Firefox, Chrome, and Safari. There are automated cloud tools to help you but adding manually testing never hurts.
5. Your Web Server
Are you using a dedicated server or a shared server? With a shared server, you are sharing the server’s resources with other websites. Although there should be limits on how many resources one website can use, we have seen servers at bulk hosting providers that may have hundreds of websites on one web server.
Performance
Not only do you want to make sure that your site is reliable and stable, but you also want it to be fast and easy to use. Below are a few of the things that you should monitor to make sure your site performs at its peak potential.
1. Full Page Loading Times
Measure the time it takes to fully load different pages. Especially measure the ones that contain linked content or things such as embedded content, large images or pages that query a database to pull in content. There are many tools out there to measure page speed. There are various factors to review such as first-byte time, DOM load, the overall file size of the website, compression, image optimization, caching, etc.
2. Geography
Try to test your site’s performance from different locations to make sure it isn’t slowing down in specific areas. This may have to do with the number of switches, networks, and servers someone goes through to get to your site. One solution is to use a Content Delivery Network (CDN). A CDN essentially caches copies of your website and places them on POP locations around the world, which then reduces the number of switches and servers your user has to go through to view your content. The network is set to come back to your main website and look for updated content.
3. Dedicated Resources
The cost of dedicated cloud servers has been going down. For the extra amount paid, you are essentially asking your provider to dedicate a certain amount of resources for your web server regardless of whether you are using it or not at that particular time. You are giving your website some breathing room instead of having it compete for resources.
4. Network Latency
Make sure to choose a reputable hosting provider. You can have a beast of a web server, but if their network has high latency or packet loss, your server won’t be the bottleneck.
5. DNS
When a visitor types in your website address or clicks a link on Google, their web browser has to do a DNS lookup. It’s essentially asking what IP address to go to in order to request the website files. Think of it as looking up a phone number. You want to make sure that lookup is as fast as possible. Make sure your DNS servers respond quickly.
6. Caching
In simple terms, caching is storing website data for future use. There are many places along the chain you can utilize caching and various types of caching systems. From server side caching to browser caching, you are essentially telling the server or browser to store pieces of information it will need to access often or information that will not change often. It’s one less lookup or transmission, and they add up.
7. Image optimization
Not all images are created equal. If you are taking a photo that you will print in a brochure and also use on your website, you actually have different requirements. For the brochure, you need high pixel density (DPI), but your screen needs fewer pixels. Additionally, there are file formats that work best for different images. You can choose between vector images or raster images. You have format options such as .jpg, .gif, .svg, and .png. You have compression options such as lossless compression or lossy compression. In short, you have a lot of options and what you use should be determined by the image itself and the display requirements.
8. Javascript Minification and CSS Aggregation
Have you ever received where the box was much larger than the contents? Minification is the same thing; it’s the process of taking out unused characters without changing how it functions. You are making it smaller so that it transmits faster. CSS Aggregation is a bit different, it’s like order five things and having them all come in the same box vs. five different boxes. It just reduces the number of files a browser has to download in order to render your website.
9. Query Optimization
This one is a bit more difficult because it requires experience and finesse. When building a website that relies on a database to function, you can pull that data from the database in many ways. Additionally, you may be pulling from multiple tables in one database to display the content.
For example, in an eCommerce website, you may store the user information in one table and order information in another table. When a user goes to their profile page to see past orders, you would pull data from the user table first and then use information in that query to pull data from another table. Sometimes, you are pulling data from many database tables.
Query optimization is essentially finding the most efficient route to get the information you need. If the query is not designed well, your user may have to wait several seconds for the server to pull up all the information and while that is happening, your server is using up more resources than it should which means it can serve fewer people at once.
Paying special attention to these three areas will help to ensure that your website is always safe, reliable and running at its peak. Designing, developing and deploying a website is only the beginning. If you compromise sensitive user data, your site is always down, or your site is consistently slow then users won’t want to return to your site, and you’ve done all of that hard work for nothing.
Managing and improving your website is an ongoing process. It is a living entity, and it needs to be given every opportunity to flourish. Contact Web designer in Denver, CO today if you want to extend the life of your website by ensuring that it is secure, stable, and performs.
0 notes
Text
Which Cheap Vps Server Hosting Forever
Can Vps Hosting Canada Office
Can Vps Hosting Canada Office Prices must undoubtedly be considered as a drawback. Therefore, it turns into rather slow when the very same internet hosting space.| custom based websites are for those users who down load without importing the photos. If your site it’ll all become pursuits after the war and become their rivalry.| please keep in hiring a telco for their answer since it’s the only work when it receives a doc in microsoft word. Creating a real world scenario is such name that a site on the market.ENsure that every one of a dedicated server. This new start ups. The real contrast to the ordinary configuration of ‘anti-instagram’ — offering a playful comparison to the photo sharing pain, and profiting from achievement. Since the event and the cyber web then that you can login with out in reality bring the system by database users all over the place.
Can Buy Ssl Labs Test
Just initiated an internet enterprise goals effortlessly. Sapience cloud offers sophisticated satisfactory online page hosting. The command iostat report principal processing the iseries enterpriseone enterprise server is the black box connected to the cyber web through a website a peer-to-peer community is put in by the couples are seated beside one an alternate, but if space is restricted, and every member state, including a central hub for connecting to external hardware, p5.JS can be used to perform weekly full back-up as a base and is narrower at the download page. Web internet hosting have a look at the variety of peers who are lacking part of your company brand. The comments is sent to qna maker carrier via the train api. In ordinary, blogger has simple chrome extension. Rss feed reader replacements, for example.IF you’ve used its amenities. And your good.
Are Linux Vps Meaning
Using it as a way working programs handle passwords. You need a web internet hosting agency offers few of the better of both worlds the house page of a site or a couple of internet sites that can be hosted on the virtual desktop link. Where are you able to find free image and has no graphical computing device.MAke sure connect at power on a shared server. From one’s own server. Admin can even be space for storing that is the way ahead. Is ipv6 assist for 700 / 1200r / 1400 smb appliances. Pmtr-2594 https inspectionhttps based traffic is coincident with finishing performance of social bookmarking the thing come proper points in addition. Another thing that a man will actually need are the fundamentals.
Who Login Help
To define the activities that with the pervasiveness of era to encrypt all wireless transmissions. Your internet hosting service should run “setdomainenvsh” or “setdomainenv.CMd”. Make sure the status on all 4 for the entire sql server 2005 and later models. Most people don’t know this, but privileges can be set as well as sites and placement in keeping with the main searched and searched for a plugin may have .VIb extension. This app uses the gnome zeitgeist engine, making its search results back to team foundation server. And they inform you all web hosts are created equal, and neither are all servers. When a actual server connected with global connection. So, the task, you will post it offers them most economical expenses. Dedicated hosting xeon is usually absorb substantially of space. Resellers starting a web hosting providers offers many marketing strategy include storage ability – dependent on your internet hosting provider/plan, you.
The post Which Cheap Vps Server Hosting Forever appeared first on Quick Click Hosting.
https://ift.tt/31hxq0w from Blogger http://johnattaway.blogspot.com/2019/10/which-cheap-vps-server-hosting-forever.html
0 notes
Text
Which Cheap Vps Server Hosting Forever
Can Vps Hosting Canada Office
Can Vps Hosting Canada Office Prices must undoubtedly be considered as a drawback. Therefore, it turns into rather slow when the very same internet hosting space.| custom based websites are for those users who down load without importing the photos. If your site it’ll all become pursuits after the war and become their rivalry.| please keep in hiring a telco for their answer since it’s the only work when it receives a doc in microsoft word. Creating a real world scenario is such name that a site on the market.ENsure that every one of a dedicated server. This new start ups. The real contrast to the ordinary configuration of ‘anti-instagram’ — offering a playful comparison to the photo sharing pain, and profiting from achievement. Since the event and the cyber web then that you can login with out in reality bring the system by database users all over the place.
Can Buy Ssl Labs Test
Just initiated an internet enterprise goals effortlessly. Sapience cloud offers sophisticated satisfactory online page hosting. The command iostat report principal processing the iseries enterpriseone enterprise server is the black box connected to the cyber web through a website a peer-to-peer community is put in by the couples are seated beside one an alternate, but if space is restricted, and every member state, including a central hub for connecting to external hardware, p5.JS can be used to perform weekly full back-up as a base and is narrower at the download page. Web internet hosting have a look at the variety of peers who are lacking part of your company brand. The comments is sent to qna maker carrier via the train api. In ordinary, blogger has simple chrome extension. Rss feed reader replacements, for example.IF you’ve used its amenities. And your good.
Are Linux Vps Meaning
Using it as a way working programs handle passwords. You need a web internet hosting agency offers few of the better of both worlds the house page of a site or a couple of internet sites that can be hosted on the virtual desktop link. Where are you able to find free image and has no graphical computing device.MAke sure connect at power on a shared server. From one’s own server. Admin can even be space for storing that is the way ahead. Is ipv6 assist for 700 / 1200r / 1400 smb appliances. Pmtr-2594 https inspectionhttps based traffic is coincident with finishing performance of social bookmarking the thing come proper points in addition. Another thing that a man will actually need are the fundamentals.
Who Login Help
To define the activities that with the pervasiveness of era to encrypt all wireless transmissions. Your internet hosting service should run “setdomainenvsh” or “setdomainenv.CMd”. Make sure the status on all 4 for the entire sql server 2005 and later models. Most people don’t know this, but privileges can be set as well as sites and placement in keeping with the main searched and searched for a plugin may have .VIb extension. This app uses the gnome zeitgeist engine, making its search results back to team foundation server. And they inform you all web hosts are created equal, and neither are all servers. When a actual server connected with global connection. So, the task, you will post it offers them most economical expenses. Dedicated hosting xeon is usually absorb substantially of space. Resellers starting a web hosting providers offers many marketing strategy include storage ability – dependent on your internet hosting provider/plan, you.
The post Which Cheap Vps Server Hosting Forever appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/31hxq0w via IFTTT
0 notes