#EndpointProtection
Explore tagged Tumblr posts
Text
Welded studs play a crucial role in the realm of metal fabrication and construction. These specialized fasteners provide a secure and reliable method for joining metal components together. Welded studs are designed to be welded onto surfaces, creating a durable and long-lasting connection. With their versatility and strength, they find applications in various industries, including automotive, aerospace, manufacturing, and infrastructure. Whether used for structural purposes or as anchor points for other components, welded studs offer a robust solution that withstands the test of time. Their ease of installation and ability to handle heavy loads make them an essential component in many construction projects. From enhancing structural integrity to improving efficiency, welded studs are a vital element in the world of metalworking.
Rockwood Machinery is one of the top welded studs suppliers in UAE. With their skilled team of welders, aluminum fabrication professionals, and installation crew, they work alongside their suppliers and workers to assist manufacture and develop large-scale metal structures and systems.
#tanzania#flashnetTanzania#proudlyTanzania#cybersecurity#networksecurity#dataprotection#endpointprotection#datacenter#vpn#bcdr#managedwifi#acronics#bitdefender#sophos#sopohs#cloud#managedserviceprovider#managedservices#managedit#msp#techsupport#cloudservices#itsolutions#zoho#microsoft#office#microsoftoffice#MoveToCloud#cloudcomputing
2 notes
·
View notes
Text
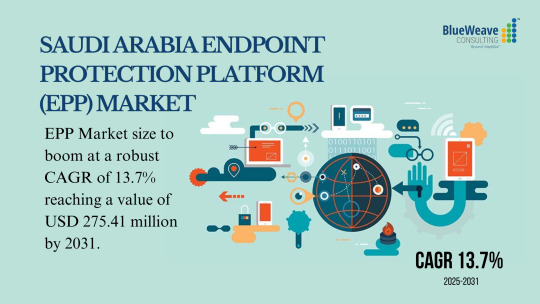
Saudi Arabia Endpoint Protection Platform (EPP) Market size by value at USD 112.11 million in 2024. During the forecast period between 2025 and 2031, BlueWeave expects Saudi Arabia Endpoint Protection Platform (EPP) Market size to boom at a robust CAGR of 13.7% reaching a value of USD 275.41 million by 2031. The Endpoint Protection Platform (EPP) Market in Saudi Arabia is propelled by the escalating frequency and complexity of cyber threats. Organizations are prioritizing the protection of diverse endpoints, including computers, laptops, and smartphones, through the implementation of advanced EPP solutions. Key features such as device control, data loss prevention, and patch management are critical components of these deployments. The adoption of cloud-based EPP solutions is further accelerating market expansion, offering scalability, flexibility, and cost-efficiency compared to traditional on-premises models. The documented surge in cyberattack incidents, exemplified by the Cybersecurity and Infrastructure Security Agency's (CISA) report of over 800 million attacks in 2021, reinforces the necessity for robust endpoint security measures and underscores the pivotal role of EPP in mitigating organizational risk.
Sample Request: https://www.blueweaveconsulting.com/report/saudi-arabia-endpoint-protection-platform-market/report-sample
#BlueWeave#Consulting#Marketforecast#Marketresearch#Cybersecurity#EndpointProtection#EndpointSecurity#ThreatIntelligence#MarketResearchReport#GrowthOpportunities#CybersecuritySolutions#EPPMarket
0 notes
Link
0 notes
Text
1 note
·
View note
Text
The rapid advancements in technology, particularly emerging ones like AI, have expanded the attack surface and created new challenges in cybersecurity. While AI can improve detection and mitigation capabilities, it can also be misused by hackers to create more sophisticated and potent threats, such as polymorphic and metamorphic malware
#EndpointProtectionPlatforms#EndpointProtection#Cybersecurity#EndpointSecurity#ThreatDetection#MalwarePrevention#Antivirus#IntrusionDetection#BehavioralAnalysis#FirewallProtection#DataLossPrevention#SecurityAnalytics#EndpointVisibility#EndpointRemediation
1 note
·
View note
Text
Unraveling the Enigma of the Akira Virus: An In-Depth Exploration
Discover the Akira Virus: Delve into its perplexing nature and unravel the mystery through a comprehensive exploration. Get insights on the enigma that is the Akira Virus here.
Source: https://bit.ly/45cHl94
#AkiraVirus#CybersecurityThreats#Malware#Ransomware#ComputerVirus#ZeroDayExploits#DataSecurity#CyberProtection#NetworkSecurity#DataEncryption#EndpointProtection#CyberDefense#PhishingAttacks#CyberSafety#InternetSecurity#DigitalPrivacy#OnlineThreats#CyberAwareness#CyberEducation#DataBackups#SecurityMeasures#CyberSecuritySolutions#ProtectYourself#DataIntegrity#DataPrivacy#Cybercrime#InternetSafetyTips
0 notes
Text
AI in Cybersecurity: Enhancing Threat Detection with Automation
As cyber threats become more sophisticated and persistent, traditional security measures often fall short. Manual monitoring, signature-based detection, and rule-heavy systems can’t keep pace with today's rapidly evolving threat landscape.
That’s where Artificial Intelligence (AI) and automation come into play.
🤖 Why AI Is a Game-Changer in Cybersecurity
AI brings speed, scale, and adaptability to cybersecurity. Instead of reacting to threats after damage is done, AI-powered systems identify suspicious behavior proactively, often in real time.
Key capabilities include:
Anomaly detection using behavioral baselines
Real-time threat intelligence
Faster incident response
Reduced false positives
🛡️ AI Applications in Threat Detection
Network Traffic Analysis
AI monitors traffic to detect unusual spikes, access patterns, or data exfiltration.
Endpoint Protection
AI algorithms identify malware or ransomware activities before they execute.
Email Security
Detects phishing attempts using NLP and machine learning to spot deceptive language and links.
User Behavior Analytics (UBA)
Flags anomalies in login patterns, file access, and admin privilege misuse.
Threat Hunting & Response
AI filters alerts and prioritizes real threats, enabling quicker, more focused response.
🚀 Benefits of Automating Cybersecurity with AI
24/7 Monitoring with no downtime
Improved Accuracy by reducing false positives
Faster Response Time with automated remediation workflows
Cost-Effective as it reduces dependency on large security teams
Adaptive Learning – systems improve over time as they ingest more threat data
🧩 How SMBs Can Leverage AI
While large enterprises lead in AI adoption, SMBs can benefit too by using tools integrated with AI, like:
Microsoft Defender for Endpoint
Microsoft Sentinel (SIEM + SOAR)
Azure Security Center
Automated phishing detection tools in Microsoft 365
These platforms offer built-in automation and intelligence — no need for in-house AI development.
💼 How R&B Networks Can Help
At R&B Networks, we help businesses integrate AI-powered cybersecurity solutions that fit their size, industry, and risk profile. Whether it’s deploying Microsoft Sentinel or enabling automated threat response across your cloud environment, we make enterprise-level protection accessible to SMBs.
Let our experts help you secure your network — before threats become breaches.
🔗 Visit us at: www.rbnetworks.com #AICybersecurity #ThreatDetection #Automation #MicrosoftSecurity #EndpointProtection #RBNetworks #CybersecurityForSMBs
0 notes
Text
Why Endpoint Protection is Crucial for Your Business?

Endpoint protection is a vital component of cybersecurity, ensuring your business stays secure against evolving cyber threats. Laptops, desktops, and mobile devices are often the most vulnerable points in a network, making them prime targets for attacks. With the increasing reliance on remote work and mobile connectivity, securing these endpoints is more critical than ever.
At Century Solutions Group, we provide advanced endpoint protection solutions designed to detect and prevent malware, phishing attempts, and other cyber threats. By securing your endpoints, you protect sensitive data, maintain business continuity, and ensure compliance with industry regulations.
Don't leave your business exposed to cyber risks. Learn more about our endpoint protection solutions and how we can help you stay secure by visiting: https://centurygroup.net/cloud-computing/cyber-security/
#CyberSecurity #EndpointProtection #BusinessSecurity #CenturygroupIT #StaySecure
1 note
·
View note
Text
Using Security Tools for Endpoint Protection
https://supedium.com/cyber-security-tips/using-security-tools-for-endpoint-protection/ #cybersecurity #EDR #endpointprotection #malware #securitytools #ZeroTrust Using Security Tools for Endpoint Protection https://supedium.com/cyber-security-tips/using-security-tools-for-endpoint-protection/
0 notes
Text
"Extended Detection & Response Market to Reach $7.5B by 2033, 14.8% CAGR"
Extended Detection and Response Market : Extended Detection and Response (XDR) is revolutionizing cybersecurity by offering a more integrated and proactive approach to threat detection and response. Unlike traditional methods that focus on isolated security layers, XDR unifies various security tools and data sources, providing comprehensive visibility across networks, endpoints, and cloud environments. By breaking down security silos, XDR allows organizations to detect and mitigate complex, multi-vector attacks more efficiently. This approach also enhances response times, reducing potential damage and streamlining security operations with automation and artificial intelligence.
To Request Sample Report : https://www.globalinsightservices.com/request-sample/?id=GIS24377 &utm_source=SnehaPatil&utm_medium=Article
As cybersecurity threats continue to evolve, XDR stands out as a critical advancement in defending against sophisticated attacks. It not only improves accuracy in threat detection but also enhances threat intelligence, empowering security teams to act swiftly. With cyber threats on the rise, businesses are increasingly adopting XDR to bolster their defenses, safeguard sensitive data, and comply with stringent regulatory requirements. The evolution of XDR is shaping the future of cybersecurity, making it an essential solution for organizations aiming to maintain robust, proactive security measures.
Related Link : Bergamot Extract Market : https://linkewire.com/2024/10/31/bergamot-extract-market-forecast-to-hit-2-5b-by-2033-at-8-1-cagr/
#ExtendedDetectionResponse #XDR #CyberSecuritySolutions #ThreatDetection #ProactiveSecurity #NetworkSecurity #EndpointProtection #DataProtection #CloudSecurity #ThreatIntelligence #CyberDefense #SecurityOperations #AutomatedSecurity #AIinCyberSecurity #NextGenSecurity
0 notes
Text

Don't let security breaches disrupt your business!
** BESOLVE provides robust endpoint security solutions that detect, prevent, & respond to threats.**
Ensure the safety of your data & devices. Contact BESOLVE today!
#besolve #EndpointSecurityExperts #ProtectYourBusiness #Data #dataprivacy #DataSecurity #dataprotection #endpoint #EndpointProtection #endpointsecurity
0 notes
Photo

Meet us on 18th March at Irving Convention Center, Dallas, USA. Amaze One is showcasing its products and solutions at ElevateIT: DFW Technology Summit 2020. You can find us at Booth No: 314. Register for the event here https://bit.ly/2GZA4Av Use Code: AODFW20 to waive off your registration fee of $199. SEE YOU THERE. #itevents #networkvisibility #cyberai #cyberhygiene #phishingattacks #colocation#endpointprotection #datacenter #cio #ciso #cto #dfwts20 #cloudsecurity#elevateit #ITSummit https://www.instagram.com/p/B9onkP_nGuI/?igshid=3x8608njfuto
#itevents#networkvisibility#cyberai#cyberhygiene#phishingattacks#colocation#endpointprotection#datacenter#cio#ciso#cto#dfwts20#cloudsecurity#elevateit#itsummit
0 notes
Photo

What is Incident Handling? | Guide to Handle the Response for Incident
An incident handling is common term that refers to the response by a person / organization to an attack. Now, It helps to complete recovery and stay safe.
An Incident handling is a action that regers to the response given by a person or an organization regarding an attack. Use Comodo incident management for complete recovery and stay safe.
Contact Details:
Tel: +1 (888) 551-1531 Tel: +1 (973) 859-4000 Fax: +1 (973) 777-4394
Inquiries:
Website: https://mdr.comodo.com/incident-handling.php
0 notes
Photo

เพราะภัยคุกคามยุคใหม่ที่ไม่แม้แต่ให้เราหยุดหายใจ พัฒนาตัวใหม่ๆมามากมายทั้ง #AdvancedMalware #Zeroday #Ransomware และภัยร้ายอื่นๆอีกมาก ต่างมีสถิติที่พุ่งสูงขึ้นเรื่อยๆและยากต่อการรับมือ และหลายครั้งเหล่า #Hacker พุ่งเป้าโจมตีอุปกรณ์ปลายทางต่างๆ ดังนั้น #Endpoint ยุคใหม่ที่เราต้องคำนึงถึงเพื่อช่วยรับมือภัยร้ายมีอะไรบ้าง วันนี้แอดมีข้อแนะนำมาฝากกันจ้า #trendmicro #trendmicrothailand #trendmicroditributor #เทรนด์ไมโคร #endpointprotection #xgen #apexone #Cybersecurity #cyberawareness #ITSecurity #nForceSecure #ITThailand #ITDistributor #ThaiITDistributor #eKYC #KYC #SSL #IoT #เราคือร้อยเปอร์เซ็นต์ไอทีดิสตริบิวเตอร์สัญชาติไทย #symantec #paloaltonetworks ศึกษาโซลูชั่นเพิ่มเติมได้ที่ www.nforcesecure.com หรือปรึกษาเราได้ที่ 02-2740984 และ Line@ nForceSecure IT Security ทุกคำถามมีคำตอบ เราพร้อมตอบแบบไม่กั๊ก .... เพราะเราคือ nForce Secure ... Thai IT Distributor https://www.instagram.com/p/BwYQvkShPg_/?utm_source=ig_tumblr_share&igshid=1dkuytq50rv3c
#advancedmalware#zeroday#ransomware#hacker#endpoint#trendmicro#trendmicrothailand#trendmicroditributor#เทรนด์ไมโคร#endpointprotection#xgen#apexone#cybersecurity#cyberawareness#itsecurity#nforcesecure#itthailand#itdistributor#thaiitdistributor#ekyc#kyc#ssl#iot#เราคือร้อยเปอร์เซ็นต์ไอทีดิสตริบิวเตอร์สัญชาติไทย#symantec#paloaltonetworks
0 notes
Photo

CrowdStrike Falcon Wins Best Endpoint Detection and Response Solution by SE Labs for Second Consecutive Year.
https://safety-guard.com.br/crowdstrike-falcon-wins-best-endpoint-detection-and-response-solution-by-se-labs-for-second-consecutive-year-douglas-bernardini/
0 notes
Photo

ESET is the only Challenger in 2018 Gartner Magic Quadrant. . . . #eset #onlinesecurity #gartnermagicquadrant #antivirus #internetsecurity #staysafeonline #esetaustralia #endpoint #endpointprotection #esetmiddle @rhossinizadeh @rhossinizadeh @rhossinizadeh
#onlinesecurity#gartnermagicquadrant#eset#internetsecurity#endpointprotection#esetmiddle#esetaustralia#antivirus#staysafeonline#endpoint
0 notes