#FakeNet
Explore tagged Tumblr posts
Text
FakeNet-NG: Powerful Malware Analysis and Network Simulation

What is FakeNet-NG?
A dynamic network analysis tool called FakeNet-NG mimics network services and records network requests to help in malware research. The FLARE team is dedicated to improving and maintaining the tool to increase its functionality and usability. Though highly configurable and platform-neutral, FakeNet needed a more user-friendly and intuitive presentation of the network data it collected so you could find pertinent Network-Based Indicators (NBIs) more quickly. Google expanded FakeNet-NG to provide HTML-based output that allows you to examine, explore, and share collected network data in order to solve this problem and further improve usability.
In order to overcome this difficulty and improve usability even further, they expanded the functionality of FakeNet-NG to provide HTML-based output, which lets you see, investigate, and share network data that has been gathered.
Engaging HTML-Based Results
An HTML page with inline CSS and Javascript supports the new interactive output of FakeNet-NG. FakeNet-NG’s current text-based output and the new HTML-based output. Using a Jinja2 template that it fills with the network data it has collected, FakeNet-NG creates each report. Your preferred browser can be used to view the final report once it has been saved to the current working directory. To analyse the recorded network activity together, you may also distribute this file to other people.
Captured network data can be chosen, filtered, and copied using the HTML interface.
Network data that has been gathered can be chosen, filtered, and copied using the HTML interface.
Creation and Execution
Planning and Execution
Insides of FakeNet-NG
FakeNet-NG Tutorial
The three main components that make up FakeNet-NG’s modular architecture are as follows:
Diverter: The target system’s main component intercepts all incoming and outgoing network traffic. It sends these packets to the Proxy Listener by default so that it can process them further.
Between the Diverter and the protocol-specific Listeners lies a component known as the Proxy Listener. Based on variables including port, protocol, and data content, it examines application layer data to determine which Listener is best for every network packet.
Protocol-specific Listeners: These specialized Listeners process requests unique to their particular protocols and produce responses that resemble authentic server behavior. Examples of these specialized Listeners are HTTP, FTP, and DNS.
Extending NBI Analysis Using FakeNet-NG
It was necessary to enhance essential components in order to record, store, and associate network data with the source activities in order to enable FakeNet-NG to provide thorough and informative reports.
FakeNet-NG Comprised:
Improving data storage: The Diverter keeps track of extra data, such as process IDs, names, and linkages between source ports that were started by the proxy and those that were started by the original.
Presenting NBI mapping: The Diverter allows for the unambiguous attribution of network activity by mapping network data to source processes.
Encouraging information exchange: To ensure precise data monitoring, the Proxy Listener sends pertinent packet metadata to the Diverter.
The interactive HTML-based output is created by combining the data that is captured by each component using FakeNet-NG
NetworkMode: Choose the network mode that FakeNet-NG should operate in.
NetworkMode: Choose which network mode to use while launching FakeNet-NG.
Acceptable configurations.
Suitable configurations.
SingleHost: control traffic coming from nearby processes.
Manipulate traffic from other systems with MultiHost.
Auto: Select the NetworkMode that works best for the platform right now.
Presently, not every platform supports every NetworkMode configuration.
This is how support is currently standing:
Only Windows supports OneHost
With the exception of process, port, and host blacklisting and whitelisting, Linux supports both MultiHost and, in an experimental state, SingleHost mode.
To access Linux’s MultiHost mode and Windows’ SingleHost mode, leave this set to Auto for the time being.
DNS-related setting and Windows implementation:
ModifyLocalDNS – direct the local machine’s DNS service to the DNS listener of FakeNet-NG.
Cease DNS Service: This command ends the DNS client service (Dnscache) on Windows. In contrast to the standard’svchost.exe’ process, this enables FakeNet-NG to observe the real processes that resolve domains.
Linux version
The following settings are supported by the Linux version of Diverter:
LinuxRedirectNonlocal – This tells you which externally facing network interfaces to reroute to FakeNet-NG when you use it to mimic Internet connectivity for a separate host.
Before adding rules for FakeNet-NG, use LinuxFlushIptables to flush all iptables rules.
As long as the Linux Diverter’s termination sequence remains unbroken, the previous rules will be reinstated.
LinuxFlushDnsCommand: If necessary, enter the appropriate command here to clear the DNS resolver cache for your Linux distribution.
Select which detailed debug events to show with the DebugLevel option.
Upcoming projects
However think there is still room to improve the HTML-based output from FakeNet-NG so that analysts can benefit even more. A communication graph, network behavior graphically would be a crucial contribution. With edges connecting process nodes to other nodes like IP addresses or domain names, this widely used approach maps processes to the corresponding network requests. You might quickly and easily grasp a program’s communication patterns by using FakeNet-NG with this kind of visualization.
Get rid of unnecessary network traffic: Reduce noise produced by safe Windows services and apps so that the most important network information is highlighted.
Make sure the HTML report includes ICMP traffic: Present a more thorough overview of network activity by showcasing network data based on ICMP.
Add pre-set filters and filtering options: Provide pre-set filters and easy-to-use filtering tools to omit typical Microsoft network traffic.
Enhance the usability of exported network data by giving the user the option to select the information that should be included in the exported Markdown data. This will improve the formatting of the Markdown data.
In conclusion
As the go-to tool for dynamic network analysis in malware research, FakeNet-NG keeps getting better. It intend to improve its usefulness by providing interactive HTML-based output, which will enable you to traverse and analyses even the largest and most intricate network data grabs in a clear, simple, and aesthetically pleasing manner.
To make your analysis of dynamic network data more efficient, they invite you to investigate the new HTML-based output and take advantage of its filtering, selection, and copying features. For the most recent version of FakeNet-NG, download it from our Github repository, make contributions to the project, or leave comments.
Read more on govindhtech.com
0 notes
Photo
FakeNet-NG v1.4.9 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Text
Original Post from FireEye Author: Michael Bailey
Introduction
In 2016, FLARE introduced FakeNet-NG, an open-source network analysis tool written in Python. FakeNet-NG allows security analysts to observe and interact with network applications using standard or custom protocols on a single Windows host, which is especially useful for malware analysis and reverse engineering. Since FakeNet-NG’s release, FLARE has added support for additional protocols. FakeNet-NG now has out-of-the-box support for DNS, HTTP (including BITS), FTP, TFTP, IRC, SMTP, POP, TCP, and UDP as well as SSL.
Building on this work, FLARE has now brought FakeNet-NG to Linux. This allows analysts to perform basic dynamic analysis either on a single Linux host or using a separate, dedicated machine in the same way as INetSim. INetSim has made amazing contributions to the productivity of the security community and is still the tool of choice for many analysts. Now, FakeNet-NG gives analysts a cross-platform tool for malware analysis that can directly integrate with all the great Python-based infosec tools that continually emerge in the field.
Getting and Installing FakeNet-NG on Linux
If you are running REMnux, then good news: REMnux now comes with FakeNet-NG installed, and existing users can get it by running the update-remnux command.
For other Linux distributions, setting up and using FakeNet-NG will require the Python pip package manager, the net-tools package, and the development files for OpenSSL, libffi, and libnetfilterqueue. Here is how to quickly obtain the appropriate prerequisites for a few common Linux distributions:
Debian and Ubuntu: sudo apt-get install python-pip python-dev libssl-dev libffi-dev libnetfilter-queue-dev net-tools
Fedora 25 and CentOS 7:
yum -y update;
yum -y install epel-release; # <-- If CentOS
yum -y install redhat-rpm-config; # <-- If Fedora
yum -y groupinstall ‘Development Tools’; yum -y install python-pip python-devel openssl-devel libffi-devel libnetfilter_queue-devel net-tools
Once you have the prerequisites, you can download the latest version of FakeNet-NG and install it using setup.py install.
A Tale of Two Modes
On Linux, FakeNet-NG can be deployed in MultiHost mode on a separate host dedicated to network simulation, or in the experimental SingleHost mode for analyzing software locally. Windows only supports SingleHost mode. FakeNet-NG is configured by default to run in NetworkMode: Auto, which will automatically select SingleHost mode on Windows or MultiHost mode on Linux. Table 1 lists the currently supported NetworkMode settings by operating system.
SingleHost
MultiHost
Windows
Default (Auto)
Unsupported
Linux
Experimental
Default (Auto)
Table 1: FakeNet-NG NetworkMode support per platform
FakeNet-NG’s support for SingleHost mode on Linux currently has limitations.
First, FakeNet-NG does not yet support conditional redirection of specific processes, hosts, or ports on Linux. This means that settings like ProcessWhiteList will not work as expected. We plan to add support for these settings in a later release. In the meantime, SingleHost mode supports redirecting all Internet-bound traffic to local listeners, which is the main use case for malware analysts.
Second, the python-netfilterqueue library is hard-coded to handle datagrams of no more than 4,012 octets in length. Loopback interfaces are commonly configured with high maximum transmittal unit (MTU) settings that allow certain applications to exceed this hard-coded limit, resulting in unanticipated network behavior. An example of a network application that may exhibit issues due to this would be a large file transfer via FTP. A workaround is to recompile python-netfilterqueue with a larger buffer size or to decrease the MTU for the loopback interface (i.e. lo) to 4,012 or less.
Configuring FakeNet-NG on Linux
In addition to the new NetworkMode setting, Linux support for FakeNet-NG introduces the following Linux-specific configuration items:
LinuxRedirectNonlocal: For MultiHost mode, this setting specifies a comma-delimited list of network interfaces for which to redirect all traffic to the local host so that FakeNet-NG can reply to it. The setting in FakeNet-NG’s default configuration is *, which configures FakeNet-NG to redirect on all interfaces.
LinuxFlushIptables: Deletes all iptables rules before adding rules for FakeNet-NG. The original rules are restored as part of FakeNet-NG’s shutdown sequence which is triggered when you hit Ctrl+C. This reduces the likelihood of conflicting, erroneous, or duplicate rules in the event of unexpected termination, and is enabled in FakeNet-NG’s default configuration.
LinuxFlushDnsCommand: Specifies the command to flush the DNS resolver cache. When using FakeNet-NG in SingleHost mode on Linux, this ensures that name resolution requests are forwarded to a DNS service such as the FakeNet-NG DNS listener instead of using cached answers. The setting is not applicable on all distributions of Linux, but is populated by default with the correct command for Ubuntu Linux. Refer to your distribution’s documentation for the proper command for this behavior.
Starting FakeNet-NG on Linux
Before using FakeNet-NG, also be sure to disable any services that may bind to ports corresponding to the FakeNet-NG listeners you plan to use. An example is Ubuntu’s use of a local dnsmasq service. You can use netstat to find such services and should refer to your Linux distribution’s documentation to determine how to disable them.
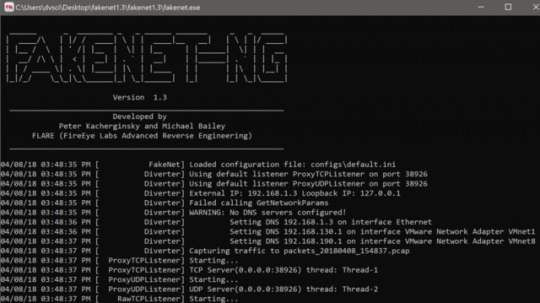
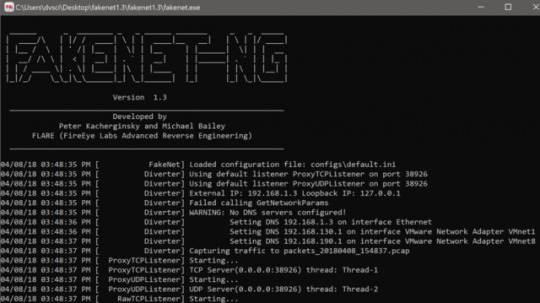
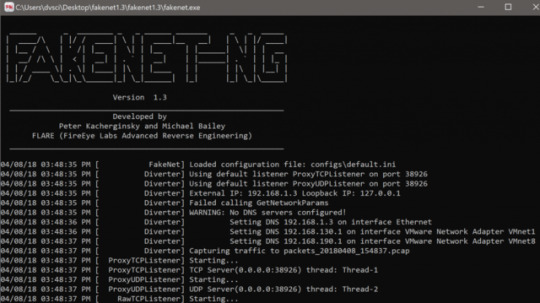
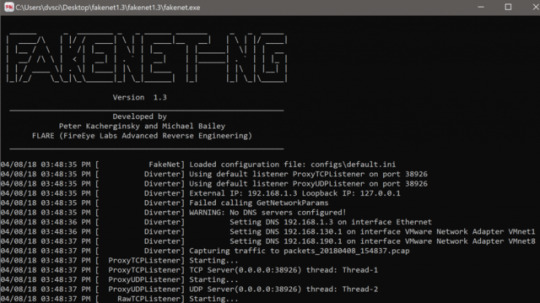
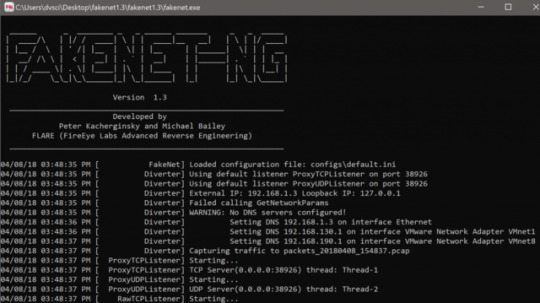
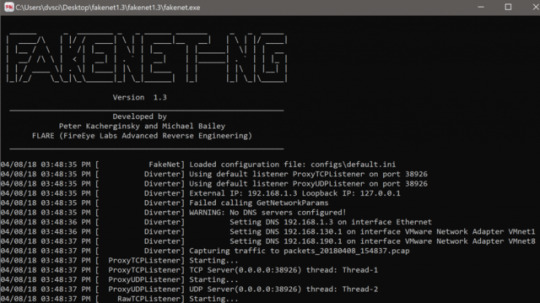
You can start FakeNet-NG by invoking fakenet with root privileges, as shown in Figure 1.
Figure 1: Starting FakeNet-NG on Linux
You can alter FakeNet-NG’s configuration by either directly editing the file displayed in the first line of FakeNet-NG’s output, or by creating a copy and specifying its location with the -c command-line option.
Conclusion
FakeNet-NG now brings the convenience of a modern, Python-based, malware-oriented network simulation tool to Linux, supporting the full complement of listeners that are available on FakeNet-NG for Windows. Users of REMnux can make use of FakeNet-NG already, while users of other Linux distributions can download and install it using standard package management tools.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Michael Bailey Introducing Linux Support for FakeNet-NG: FLARE’s Next Generation Dynamic Network Analysis Tool Original Post from FireEye Author: Michael Bailey Introduction In 2016, FLARE introduced FakeNet-NG, an open-source network analysis tool written in…
0 notes
Link
FakeNet - Windows Network Simulation Tool for Malware Analysis https://t.co/bE4htlyxbz #ifh
0 notes
Text
New FakeNet-NG Feature: Content-Based Protocol Detection
New FakeNet-NG Feature: Content-Based Protocol Detection
I (Matthew Haigh) recently contributed to FLARE’s FakeNet-NG network simulator by adding content-based protocol detection and configuration. This feature is useful for analyzing malware that uses a protocol over a non-standard port; for example, HTTP over port 81. The new feature also detects and adapts to SSL so that any protocol can be used with SSL and handled appropriately by FakeNet-NG. We…
View On WordPress
0 notes
Text
FakeNet Simulates a Network
FakeNet Simulates a Network
FakeNet is a tool that aids in the dynamic analysis of malicious software. The tool simulates a network so that malware interacting with a remote host continues to run allowing the analyst to observe the malware’s network activity from within a safe environment. The goal of the project is to:
Be easy to install and use; the tool runs on Windows and requires no 3rd party libraries
Support the…
View On WordPress
0 notes
Photo
FakeNet-NG v1.4.9 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Photo
FakeNet-NG v1.4.8 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Photo
FakeNet-NG v1.4.8 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Photo
FakeNet-NG v1.4.4 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Photo
FakeNet-NG v1.4.3 releases: Next Generation Dynamic Network Analysis Tool
0 notes
Text
New FakeNet-NG Feature: Content-Based Protocol Detection
I (Matthew Haigh) recently contributed to FLARE’s FakeNet-NG network simulator by adding content-based protocol detection and configuration. This feature is useful for analyzing malware that uses a protocol over a non-standard port; for example, HTTP over port 81. The new feature also detects and adapts to SSL so that any protocol can be used with SSL and handled appropriately by FakeNet-NG. We were motivated to add this feature since it was a feature of the original FakeNet and it was needed for real world malware.
What is FakeNet-NG
FakeNet-NG simulates a network so malware analysts can run samples with network functionality without the risks of an Internet connection. Analysts can examine network-based indicators via FakeNet-NG’s textual and pcap output. It is plug-and-play, configurable, and works on both Windows and Linux. FakeNet-NG simulates common protocols to trick malware into thinking it is connected to the Internet. FakeNet-NG supports the following protocols: DNS, HTTP, FTP, POP, SMTP, IRC, SSL, and TFTP.
Previous Design
Previously FakeNet-NG employed Listener modules, which were bound to configurable ports for each protocol. Any traffic on those ports was received by the socket and processed by the Listener.
In the previous architecture, packets were redirected using a Diverter module that utilized WinDivert for Windows and netfilter for Linux. Each incoming and outgoing packet was examined by the Diverter, which kept a running list of connections. Packets destined for outbound ports were redirected to a default Listener, which would respond to any packet with an echo of the same data. The Diverter also redirected packets based on whether FakeNet-NG was run in Single-Host or Multi-Host mode, and if any applications were blacklisted or whitelisted according to the configuration. It would simply release the packet on the appropriate port and the intended Listener would receive it on the socket.
New Design
My challenge was to eliminate this port/protocol dependency. In order to disassociate the Listeners from the corresponding ports, a new architecture was needed. The first challenge was to maintain Listener functionality. The original architecture relied on Python libraries that interact with the socket. Therefore, we needed to maintain “socket autonomy” in the Listener, so we added a “taste()” function for each Listener. The routine returns a confidence score based on the likelihood that the packet is associated with the protocol. Figure 1 demonstrates the taste() routine for HTTP, which looks for the request method string at the beginning of the packet data. It gives an additional point if the packet is on a common HTTP port. There were several choices for how these scores were to be tabulated. It could not happen in the Diverter because of the TCP handshake. The Diverter could not sample data from data-less handshake packets, and if the Diverter completed the handshake, the connection could not easily be passed to a different socket at the Listener without disrupting the connection.
Figure 1: HTTP taste() example
Proxy
We ultimately decided to add a proxy Listener that maintains full-duplex connections with the client and the Listener, with both sides unaware of the other. This solves the handshake problem and maintains socket autonomy at the Listener. The proxy is also easily configurable and enables new functionality. We substituted the proxy for the echo-server default Listener, which would receive traffic destined for unbound ports. The proxy peeks at the data on the socket, polls the Listeners, and creates a new connection with the Listener that returns the highest score. The echo-server always returns a score of one, so it will be chosen if no better option is detected. The analyst controls which Listeners are bound to ports and which Listeners are polled by the proxy. This means that the listeners do not have to be exposed at all; everything can be decided by the proxy. The user can set the Hidden option in the configuration file to False to ensure the Listener will be bound to the port indicated in the configuration file. Setting Hidden to True will force any packets to go through the proxy before accessing the Listener. For example, if the analyst suspects that malware is using FTP on port 80, she can ‘hide’ HTTP from catching the traffic, and let the proxy detect FTP and forward the packet to the FTP Listener. Additional configuration options exist for choosing which protocols are polled by the proxy. See Figure 2 and Figure 3 for configuration examples. Figure 2 is a basic configuration for a Listener, and Figure 3 demonstrates how the proxy is configurable for TCP and UDP.
Figure 2: Listener Configuration Options
Figure3: Proxy Configuration Options
The proxy also handles SSL detection. Before polling the Listeners, the proxy examines the packet. If SSL is detected, the proxy “wraps” the socket in SSL using Python’s OpenSSL library. With the combination of protocol and SSL detection, each independent of the other, FakeNet-NG can now handle just about any protocol combination.
The proxied SSL implementation also allows for improved packet analysis. The connection between the proxy and the Listener is not encrypted, which allows FakeNet to dump un-encrypted packets to the pcap output. This makes it easier for the analyst to examine the packet data. FakeNet continues to produce pcap output that includes packet data before and after modification by FakeNet. While this results in repetitive data, it is often useful to see the original packet along with the modification.
Example
Figure 4 shows verbose (-v) output from FakeNet on Windows responding to an HTTP request on port 81 from a clowncar malware variant (SHA-256 8d2dfd609bcbc94ff28116a80cf680660188ae162fc46821e65c10382a0b44dc). Malware such as clowncar use traditional protocols over non-standard ports for many reasons. FakeNet gives the malware analyst the flexibility to detect and respond to these cases automatically.
Figure 4: clowncar malware using HTTP on port 81
Conclusion
FLARE’s FakeNet-NG tool is a powerful network-simulation tool available for Windows and Linux. The new content-based protocol detection and SSL detection features ensure that FakeNet-NG remains the most useful tool for malware analysts. Configuration options give programmers the flexibility necessary to respond to malware using most protocols on any port.
The post New FakeNet-NG Feature: Content-Based Protocol Detection appeared first on Security Boulevard.
from New FakeNet-NG Feature: Content-Based Protocol Detection
0 notes
