#Dynamic Malware Analysis
Explore tagged Tumblr posts
Text


tuesday, december 17th, 2024
work is very busy at the moment! I'm trying to wrap up a few projects before everyone is out for the holidays. I'm also still trying to finish Practical Malware Analysis by the end of the year. I went to my favorite coffee shop after work to do some reading & take some notes. I'm still kind of far behind on doing the labs (I need way more practice with dynamic analysis lol), but I'm going to keep trying!
#studyblr#studyspo#study inspo#studying#study aesthetic#op#evening coffee shop time is such a good vibe#one of the joys of adulthood is realizing you can just do whatever#going to a cafe in the evening on a random tuesday? why not!
209 notes
·
View notes
Text
Guarding Your Digital DNA: EDSPL Combines Network, Email, Application & API Security Like No Other

In today’s digital-first business landscape, the true essence of a company lives in data—client records, intellectual assets, internal communications, financial details, and proprietary code. This critical digital identity—your organization's DNA—demands safeguarding that’s intelligent, adaptive, and deeply integrated. With the increasing sophistication of cyberattacks, conventional solutions fall short. What’s required is a defense framework that does more than patch vulnerabilities—it prevents exposure altogether.
Enter EDSPL, your strategic cybersecurity partner, offering a consolidated suite that unifies Network Defense, Email Filtering, Application Safety, and API Oversight under one streamlined, dynamic ecosystem. What makes us different? We don’t just build barriers—we establish intelligent guardians for your digital world.
The Digital Identity Crisis: Why Partial Protection Isn’t Enough
Every piece of technology your organization touches—cloud platforms, email services, web apps, or custom APIs—opens a potential doorway for adversaries. A poorly configured firewall, an unsecured endpoint, or a vulnerable third-party integration could be exploited with just a few lines of malicious code.
Relying on fragmented tools—each with its own rules, limitations, and management console—leads to disjointed visibility. This is how gaps form. Cybercriminals thrive in these blind spots.
EDSPL solves this fragmentation by weaving all critical protection layers into a single, responsive framework. Whether it's a phishing attempt, lateral movement on your LAN, malicious API calls, or a zero-day exploit in your software, our integrated system detects, isolates, and responds in real time—minimizing damage and maximizing uptime.
Network Security: The Foundation That Learns and Evolves
Let’s start at the base—the infrastructure your business relies on. Traffic flows across switches, routers, and gateways without pause. Embedded within these streams could be botnet communications, command and control attempts, or insider activity.
Traditional firewalls act like static gates. But EDSPL’s modern network security employs behavioral analytics, machine learning, and threat intelligence feeds. We don’t just filter by port and protocol—we observe patterns, study anomalies, and dynamically update rulesets to block bad actors before they can pivot further.
Our network protection solutions ensure uninterrupted performance while stopping lateral movement, DDoS floods, and ransomware deployments in their tracks.
Email Security: Your Human Layer, Hardened
Emails are often the first weapon in a hacker’s arsenal. They’re subtle, persuasive, and delivered directly to your team’s inboxes. A single careless click can unleash credential theft, malware infection, or worse—unauthorized access to privileged systems.
EDSPL redefines email safety. We don’t just rely on spam filters. Instead, our approach involves sandboxing attachments, real-time link scanning, impersonation detection, and AI-based phishing recognition. Every message is parsed and analyzed through multi-layered engines.
Our deep context analysis ensures that business communications remain authentic while nefarious content is flagged or quarantined. No delays, no missed alerts—just secure, seamless messaging.
Application Security: Building Fortresses Around Functionality
As businesses evolve, so do their digital touchpoints. Web portals, mobile apps, internal dashboards, and third-party integrations all serve critical functions—but also increase your exposure to threats.
Most organizations focus only on reactive patches and static tests. But EDSPL’s application protection strategy is proactive. We integrate directly into your DevSecOps pipeline, providing security assessments throughout development and deployment. From securing user sessions to monitoring runtime behaviors, we treat each app like an evolving organism—constantly watched, evaluated, and immunized.
Through advanced WAF deployments, identity and access controls, encryption enforcement, and code-level insights, we fortify your services from all sides without affecting speed or user experience.
API Security: Silent Enablers, Constantly Guarded
APIs are the unsung heroes behind modern digital experiences—connecting systems, transferring data, enabling automation. But what happens when these interfaces aren’t shielded properly? The result could be catastrophic data leakage, service interruptions, or platform manipulation.
EDSPL understands the silent power—and risks—of APIs. Our API defense framework doesn’t just track usage; it authenticates calls, verifies payloads, and identifies anomalies in traffic. Every endpoint is cataloged, monitored, and governed with strict policies.
With us, your APIs become secure pipelines—not liabilities—ensuring secure data flow between applications and platforms without opening backdoors for cyber intrusions.
No Guesswork, Just Intelligence
Security isn't about adding more tools—it’s about smartly deploying the right ones, in harmony. EDSPL’s unified approach centralizes visibility, policy enforcement, incident response, and analytics under one intuitive interface. This simplifies management, improves compliance readiness, and shortens your response time during potential breaches.
Our ecosystem eliminates silos. Whether an incident begins with a compromised email or an exploited API, our systems correlate events, trace lateral movement, and guide automated containment actions—often before your team is even alerted.
Compliance and Beyond: Future-Proofing Your Ecosystem
Meeting regulatory standards—like GDPR, HIPAA, or ISO 27001—isn’t just a checkbox. It’s a fundamental part of preserving reputation and avoiding penalties. But compliance doesn’t automatically equal security.
EDSPL bridges the gap by ensuring that every protection we deploy supports both regulatory alignment and operational security. From encrypted communications and data access logs to vulnerability scanning and role-based controls, our strategies meet auditor requirements while preparing your business for what’s next.
Built for Enterprises, Scaled for Everyone
Whether you're a scaling startup, an established enterprise, or a mission-critical organization operating in healthcare, finance, or government—we tailor our solutions to fit your environment.
EDSPL doesn’t believe in one-size-fits-all. We conduct in-depth risk assessments, understand your unique workflows, and craft a solution stack that aligns with your priorities, timelines, and budgets. We take care of the technology, so you can focus on growth.
Teamwork That Transcends Transactions
The best cybersecurity partner isn’t just a vendor—it’s an extension of your own team. That’s why EDSPL offers 24x7 support, access to certified experts, and proactive threat hunting services.
Our specialists work closely with your IT, DevOps, and compliance teams, ensuring smooth integrations, incident drills, and continuous improvements. We're not just protecting endpoints—we’re empowering your entire digital journey.
Why Choose EDSPL: What Makes Us Unmatched
All-in-One Platform: From gateways to APIs, everything is managed through one console.
Real-Time Detection: Stop attacks at inception with automated analytics and response triggers.
Zero Trust Principles: Every request is verified, every identity is validated.
Global Threat Intelligence: Stay ahead of evolving risks with live updates and predictive modeling.
Business-Centric Focus: Protect innovation, revenue streams, and brand trust simultaneously.
Please visit our website to know more about this blog https://edspl.net/blog/guarding-your-digital-dna-edspl-combines-network-email-application-api-security-like-no-other/
0 notes
Text
Understanding the EMA Indicator for MT4

Introduction to Technical Indicators
Technical indicators are essential tools for traders in the financial markets, helping them analyze price movements and make informed decisions. Among these, the Exponential Moving Average (EMA) stands out for its responsiveness to recent price changes. The EMA is widely used in platforms like MetaTrader 4 (MT4), a popular trading software known for its robust features and flexibility. Traders often download EMA indicator for MT4 to enhance their charting capabilities and refine their strategies.
What is the EMA Indicator?
The EMA is a type of moving average that places greater weight on recent price data, making it more sensitive to short-term price fluctuations compared to the Simple Moving Average (SMA). This characteristic allows traders to identify trends and potential reversal points more quickly. The EMA is calculated using a formula that incorporates a smoothing factor, typically based on the number of periods selected (e.g., 9, 21, or 50 periods).
In MT4, the EMA indicator is built-in, but traders may seek to download EMA indicator for MT4 from external sources to access customized versions with additional features, such as multi-timeframe analysis or unique visual settings. These custom indicators can provide a competitive edge in fast-paced markets like forex, stocks, or commodities.
Why Use the EMA in Trading?
The EMA is favored for its versatility and effectiveness in various trading strategies. Here are some key benefits:
Trend Identification: The EMA helps traders spot the direction of the market by smoothing out price data. A rising EMA suggests an uptrend, while a declining EMA indicates a downtrend.
Crossover Signals: Traders use EMA crossovers (e.g., a shorter EMA crossing a longer EMA) to identify entry and exit points. For example, a bullish crossover occurs when a 9-period EMA crosses above a 21-period EMA.
Dynamic Support and Resistance: The EMA can act as a dynamic level of support or resistance, guiding traders on potential price reactions.
By choosing to download EMA indicator for MT4, traders can access enhanced versions that offer alerts or automated signals, saving time and improving efficiency.
How to Download and Install the EMA Indicator for MT4
To use the EMA in MT4, follow these steps:
Check Built-in EMA: MT4 includes a default EMA indicator under the "Indicators" menu. Simply drag it onto your chart and configure the period settings.
Download Custom EMA: If you need a specialized version, search reputable websites or trading forums for custom EMA indicators. Ensure the file is in the .mq4 or .ex4 format.
Install the Indicator: Place the downloaded file in the MT4 "Indicators" folder (found in the "MQL4" directory). Restart MT4, and the indicator will appear in the navigator panel.
Apply to Chart: Drag the custom EMA onto your chart, adjust settings like colors or periods, and start analyzing.
Always verify the source when you download EMA indicator for MT4 to avoid malware or unreliable tools.
Tips for Using the EMA Effectively
To maximize the EMA’s potential, consider these tips:
Combine the EMA with other indicators, like RSI or MACD, to confirm signals.
Use multiple EMAs (e.g., 9, 21, 50) to analyze different timeframes and avoid false signals.
Test your strategy on a demo account before applying it to live trading.
Conclusion
The EMA indicator is a powerful tool for traders seeking to navigate the complexities of financial markets. Its ability to highlight trends and generate timely signals makes it a staple in MT4 trading. By opting to download EMA indicator for MT4, traders can unlock advanced features and tailor the tool to their needs. With proper use and strategy, the EMA can significantly enhance trading performance.
0 notes
Text
Best cyber security course in Jalandhar
Join the best cyber security course in Jalandhar , with flexible classes. Learn from top professionals and prepare for a high-paying career in cybersecurity.
https://techcadd.com/best-cyber-security-course-in-jalandhar.php

Best Cyber Security Course in Jalandhar by TechCadd In today’s digital age, cyber threats have become increasingly sophisticated, targeting individuals, businesses, and government systems alike. As a result, the demand for professionals skilled in cyber security is soaring across the globe. If you’re located in Punjab and searching for the best cyber security course in Jalandhar, look no further than TechCadd – a reputed name in professional IT training.
Why Cyber Security Matters With the rise of digital transactions, remote work, and online data storage, organizations face growing risks from hackers, malware, ransomware, and phishing attacks. Professionals trained in cyber defense are now essential in all sectors including finance, healthcare, education, and IT. The right cyber security training can open doors to rewarding career opportunities in a field that is dynamic and future-proof.
TechCadd: Pioneers in Cyber Security Training TechCadd, based in Jalandhar, has built a strong reputation for delivering practical and industry-relevant IT courses. Their cyber security course in Jalandhar stands out due to its real-time project work, experienced trainers, and up-to-date curriculum aligned with global security standards. TechCadd’s approach to cyber security training is hands-on. The course is designed to cover both foundational knowledge and advanced techniques, ensuring students are equipped to tackle real-world cyber threats effectively. Whether you are a student, IT professional, or a career switcher, TechCadd's program helps you build the skills you need to thrive in the cyber security domain.
What the Course Covers The cyber security course at TechCadd includes comprehensive modules such as:
Network Security and Infrastructure Protection
Threat Intelligence & Risk Management
Malware Analysis and Reverse Engineering
Web Application Security
Security Operations Center (SOC) Processes
Penetration Testing Techniques
Incident Response & Digital Forensics
These modules are taught using a mix of theoretical knowledge and practical labs, allowing learners to simulate cyber attack scenarios and develop countermeasures in real-time environments.
Industry-Ready Certification Upon successful completion of the course, students receive a recognized certification, adding weight to their resumes and validating their expertise in cyber security. This is especially useful when applying for jobs or freelance projects in the IT security space.
Placement Assistance & Career Support The institute has strong ties with local and national tech companies, helping students land internships and full-time roles in cybersecurity, ethical hacking, and network security domains. Who Can Join?
This course is ideal for:
Computer science students
IT professionals seeking specialization
Engineers and graduates looking to pivot into tech
Final Thoughts TechCadd’s commitment to excellence, hands-on training methodology, and career-oriented approach make it the best choice for cyber security training in Jalandhar. As cyber threats continue to rise, there’s never been a better time to invest in a career that not only pays well but also plays a crucial role in securing our digital future.
#EthicalHacking#TechTraining#MalwareProtection#ITSecurity#NetworkSecurity#DigitalSecurity#OnlineSecurity#CyberSecurityCourse
0 notes
Text
Transforming Enterprise Security with DevSecOps

In today’s fast-paced, digitally connected world, organizations must strike a delicate balance between rapid software deployment and uncompromised security. Traditional development approaches often introduce bottlenecks and increase risk, slowing innovation and exposing systems to threats.
This is where DevSecOps transformation plays a pivotal role. By integrating security into every phase of the software development lifecycle—from planning to production—DevSecOps ensures that security practices evolve alongside code, infrastructure, and organizational goals. This cultural and technical shift transforms security from a final gatekeeper into a continuous, embedded practice.
The DevSecOps Crisis: Speed vs. Security
The demand for faster releases frequently clashes with the need for secure code. Development teams push to meet deadlines, while security reviews—often treated as an afterthought—delay production and increase friction.
Key challenges include:
Security as an Afterthought: Delaying security checks leads to expensive and disruptive fixes.
Siloed Operations: Isolated security teams result in poor communication and misaligned goals.
Manual Security Processes: Time-consuming reviews cannot scale with modern CI/CD workflows.
Expanding Attack Surfaces: Cloud-native apps, APIs, and microservices increase potential vulnerabilities.
Impact Area
Description
Breaches & Violations
Greater risk of data loss and compliance failures
Reputational Damage
Loss of trust and reduced customer confidence
Operational Overhead
Fixes in production cost up to 30x more than in dev
IT Consulting: Driving Strategic DevSecOps Adoption
A successful DevSecOps transformation often begins with strategic IT consulting and advisory services. These services streamline adoption and reduce disruption by aligning processes, tools, and culture.
Three consulting pillars include:
Technical Assessment: Analyze current pipelines, tools, and vulnerabilities.
Cultural Change: Foster collaboration between development, security, and operations.
Implementation Roadmap: Deliver phased adoption for scalable, secure outcomes.
Organizations that engage expert consultants report 40% faster adoption and 65% higher success rates.
The Rise of Intelligent DevSecOps
Modern DevSecOps solutions use AI and machine learning to supercharge security integration:
Predictive Vulnerability Detection
Learns from historical data to anticipate real risks
Prioritizes issues based on business impact
Adapts to evolving threats
Result: 91% fewer false positives and 73% faster critical issue resolution.
Automated Security Testing at Scale
Intelligent Test Generation: Automatically create test cases based on behavior
Runtime Protection: Detect and block attacks in real time
API Security Analysis: Monitor anomalies in API behavior
Outcome: 3–4x more code tested with the same resources.
Enterprise Software Services: Secure by Design
Modern enterprise applications require built-in security from the start:
Secure-by-Design Architecture: Prevent classes of vulnerabilities at the architecture level
Component-Level Verification: Reusable secure components improve consistency
Built-In Compliance: Automate compliance to ease audits
This reduces rework and accelerates secure releases.
Mobile App Security: Protecting the Edge
Mobile apps face distinct threats due to their distributed nature and user data exposure:
Secure Authentication: MFA, biometrics, and session control
Data Protection: Encryption, secure storage, and minimization
Runtime Monitoring: Detect jailbreaking, code injections, and malware
Companies applying mobile security frameworks see 78% fewer mobile-related breaches.
Self-Healing Infrastructure
Advanced security systems now offer autonomous threat response, including:
Automated Remediation of known vulnerabilities
Dynamic Access Controls based on real-time behavior
Adaptive Defense Mechanisms that reconfigure protections on-the-fly
This reduces the vulnerability window and operational strain.
A Complete DevSecOps Framework
To succeed with DevSecOps, a well-structured framework is essential:
Intelligent Code Analysis
Real-time scanning during coding identifies issues before code is committed.
Automated Dependency Verification
Analyze actual dependency usage
Predict impact of vulnerabilities
Suggest safer replacements
Managed IT Services: Ensuring Long-Term Security
Even the best DevSecOps framework needs ongoing support. Managed IT services provide:
24/7 Monitoring: Proactive breach detection
Vulnerability Management: Regular scans and prioritized remediation
Incident Response: Fast recovery from attacks
Compliance Maintenance: Ongoing audit-readiness
Benefit: 67% faster detection and 54% lower costs per incident.
Case Study: DevSecOps in Digital Banking
A digital bank struggling with frequent vulnerabilities and delayed releases underwent a DevSecOps transformation supported by IT consulting.
Transformation Steps:
Developer enablement through secure coding practices
Automated CI/CD pipeline security
Production defense via managed services
Results:
83% fewer critical vulnerabilities
Deployment cycle improved from monthly to weekly
Developer satisfaction jumped to 4.3/5
Security operation costs reduced by 27%
ETL Pipeline Security: Safeguarding Data in Motion
ETL pipelines must protect sensitive data throughout its journey:
Data Classification & Encryption during transit and storage
Granular Access Controls to prevent overexposure
Secure Transformations that don’t leak or expose information
Organizations report 92% fewer leaks and 78% faster compliance with GDPR/CCPA.
DevSecOps Roadmap: From Visibility to Autonomy
A phased DevSecOps implementation allows controlled progress:
Foundation Phase: Introduce visibility and basic security controls
Acceleration Phase: Automate and integrate testing
Transformation Phase: Enable self-defending, autonomous operations
Measuring DevSecOps Success
Track these KPIs to evaluate effectiveness:
Mean Time to Detect (MTTD)
Mean Time to Remediate (MTTR)
Vulnerability Escape Rate
False Positive Rate
Security Compliance Efficiency
Developer Security Efficiency
Final Thoughts: The Future of Secure Development
DevSecOps is not just a technical shift—it’s a cultural, strategic, and operational transformation. By embedding intelligent security across the development lifecycle, businesses can achieve fast, scalable, and secure innovation.
The most successful organizations combine:
Cultural Collaboration
Ongoing Learning
Strategic Automation
Those who embrace DevSecOps today will lead in security, compliance, and customer trust tomorrow.
FAQs
1. What is DevSecOps, and why is it essential? DevSecOps is a practice that embeds security into every phase of the development pipeline, ensuring rapid yet secure software delivery.
2. How does DevSecOps improve enterprise security? It reduces vulnerabilities by automating testing, increasing collaboration, and enabling proactive threat detection.
3. What industries benefit most from DevSecOps? Financial services, healthcare, retail, SaaS, and any industry managing sensitive data or facing regulatory pressure.
4. Can small businesses implement DevSecOps? Yes. With the right consulting and automation tools, small teams can effectively adopt DevSecOps practices.
5. How does DevSecOps relate to compliance? DevSecOps integrates compliance checks into the development pipeline, ensuring ongoing readiness for audits and regulations like GDPR, HIPAA, or SOC 2.
0 notes
Text
Social Network Analysis Programming

Social Network Analysis (SNA) is a powerful technique used to explore and analyze the relationships between individuals, groups, or entities. With programming, we can visualize and calculate complex network structures, which is useful in fields like sociology, marketing, cybersecurity, and even epidemiology.
What is Social Network Analysis?
Social Network Analysis is the process of mapping and measuring relationships and flows between people, groups, organizations, computers, or other information/knowledge processing entities. It reveals the structure of networks and helps identify influential nodes, communities, and patterns.
Key Concepts in SNA
Nodes (Vertices): Represent entities (e.g., people, computers).
Edges (Links): Represent connections or relationships between nodes.
Degree Centrality: Number of direct connections a node has.
Betweenness Centrality: How often a node appears on shortest paths.
Clustering: Grouping of nodes based on similarity or proximity.
Tools & Libraries for SNA Programming
Python: Powerful language with strong libraries like NetworkX and Pandas.
NetworkX: Used to create, manipulate, and visualize complex networks.
Gephi: GUI-based open-source software for large network visualization.
Graph-tool (Python): Fast and efficient network analysis for large graphs.
D3.js: JavaScript library for dynamic and interactive network visualizations.
Example: Basic Network Analysis with Python & NetworkX
import networkx as nx import matplotlib.pyplot as plt # Create a graph G = nx.Graph() # Add nodes and edges G.add_edges_from([ ('Alice', 'Bob'), ('Alice', 'Carol'), ('Bob', 'David'), ('Carol', 'David'), ('Eve', 'Alice') ]) # Draw the network nx.draw(G, with_labels=True, node_color='lightblue', edge_color='gray') plt.show() # Analyze print("Degree Centrality:", nx.degree_centrality(G)) print("Betweenness Centrality:", nx.betweenness_centrality(G))
Applications of Social Network Analysis
Marketing: Identify key influencers and optimize content spread.
Security: Detect suspicious communication patterns or malware spread.
Epidemiology: Track the spread of diseases across populations.
Sociology: Understand community structures and social behavior.
Recommendation Systems: Suggest friends, content, or connections.
Tips for Effective SNA Programming
Start with clean and structured data (CSV, JSON, etc.).
Visualize early and often to detect patterns.
Use metrics like centrality and clustering coefficients for deeper insights.
Leverage real-world datasets like Twitter or Facebook data via APIs.
Scale with performance-optimized libraries for large datasets.
Conclusion
Social Network Analysis Programming unlocks a new dimension in data analysis by focusing on relationships rather than isolated entities. With the right tools and mindset, you can uncover hidden structures, detect influence patterns, and make data-driven decisions in a connected world.
0 notes
Text
AI in Banking Security: Revolution & Risks

The promoter and managing partner of Ravi Rajan & Co. LLP, and the former Chairman of the Bombay Stock Exchange (BSE)
The digital evolution of banking has brought immense convenience, yet simultaneously amplified cyber security risks, positioning Artificial Intelligence (AI) as a pivotal, double-edged tool: "The Algorithmic Sentinel." On the defensive side, AI empowers banks by enhancing threat detection through real-time analysis of transaction patterns and network traffic, automating incident response to swiftly mitigate damage, and improving risk assessment by predicting vulnerabilities. However, the same AI technologies that bolster security can be exploited by cybercriminals, enabling sophisticated phish ing campaigns, AI-driven malware, and the amplification of existing cyber-attacks. Consequently, the responsible implementation of AI in banking cyber security necessitates a careful equilibrium, demanding that financial institutions prioritize robust security protocols, ethical considerations, and continuous vigilance to maximize AI's protective capabilities while minimizing its potential for malicious use
AI shields banking by enhancing threat detection and automating rapid response
From an economist's perspective, the primary allure of AI in banking cyber security lies in its potential to optimize resource allocation and mitigate financial losses. Traditional rule-based security systems, while valuable, struggle to keep pace with the sheer volume and complexity of modern cyber-attacks.AI, particularly machine learning (ML), offers a dynamic and adaptive approach.
Anomaly Detection- ML algorithms, trained on vast datasets of historical transaction and network data, can identify subtle anomalies that deviate from established patterns. This allows banks to detect fraudulent activities, such as unusual fund transfers or unauthorized access attempts, in real-time. Economically, this translates to reduced fraud losses and improved operational efficiency.
Anomaly Detection- ML algorithms, trained on vast datasets of historical transaction and network data, can identify subtle anomalies that deviate from established patterns. This allows banks to detect fraudulent activities, such as unusual fund transfers or unauthorized access attempts, in real-time. Economically, this translates to reduced fraud losses and improved operational efficiency.
Behavioral Analysis- AI can analyze user behavior, including login patterns, transaction frequencies, and device usage, to create personalized risk profiles. Deviations from these profiles can trigger alerts, enabling proactive intervention. This minimizes the time lag between attack initiation and response, reducing potential financial damage.
Automated Threat Response- AI-powered systems can automate responses to known threats, such as blocking suspicious IP addresses or disabling compromised accounts. This reduces reliance on manual intervention, freeing up security personnel to focus on more complex threats. The reduction of labour costs for mundane tasks allows for the reallocation of resources to more complex security challenges.
Predictive Analytics- By analyzing historical attack data and emerging threat intelligence, AI can predict future attack patterns and vulnerabilities. This enables banks to proactively strengthen their defenses, reducing the likelihood of successful attacks. This is a critical factor for maintaining consumer confidence, which is vital for overall economic stability.
Natural Language Processing (NLP)- NLP techniques can analyze vast amounts of textual data, such as security logs, social media posts, and dark web forums, to identify emerging threats and assess public sentiment. This helps banks stay ahead of potential attacks and manage reputational risk.
From an economic perspective, these AI applications translate to reduced operational costs associated with manual threat detection and response, minimized financial losses due to fraud and cyber-attacks, improved customer trust and brand reputation leading to increased customer retention and acquisition, and enhanced regulatory compliance and reduced risk of penalties
The Shadow of AI: Risks and Ethical Implications
However, the widespread adoption of AI in banking cybersecurity also introduces novel risks that demand careful consideration.
AI Bias- ML algorithms are trained on historical data, which may reflect existing biases. For example, if fraud detection algorithms are trained on data that disproportionately flags transactions from certain demographic groups, they may perpetuate discriminatory practices. This can lead to unfair treatment of customers and damage the bank's reputation. From an economic perspective, this can lead to legal complications and loss of market share.
Adversarial Attacks- AI systems are vulnerable to adversarial attacks, where malicious actors manipulate input data to deceive the algorithms. For example, attackers can inject subtle noise into transaction data to evade fraud detection. This is the constant arms race, where attackers are also using AI to improve their techniques.
Explain ability and Transparency- Many AI algorithms, particularly deep learning models, operate as "black boxes," making it difficult to understand how they arrive at their decisions. This lack of transparency raises concerns about accountability and fairness, especially in sensitive areas like fraud detection and loan approvals. Regulatory bodies are increasingly demanding explainable AI, which requires banks to provide clear and concise explanations for AI-driven decisions.
Ethical Implications of Automated Decision Making- The automation of security decisions raises ethical concerns about the role of human judgment. AI algorithms may make decisions that have significant consequences for individuals, such as freezing accounts or blocking transactions, without human oversight. This necessitates the development of ethical frameworks that guide the use of AI in banking cybersecurity. The legal and financial implications of wrong AI decisions is a major concern.
Data Privacy- AI algorithms require access to vast amounts of sensitive customer data. This raises concerns about data privacy and security, especially in light of increasing data breaches. Banks must implement robust data protection measures to ensure compliance with privacy regulations.
Job Displacement- The automation of security tasks may lead to job displacement for human security analysts. Banks must invest in training and reskilling programs to prepare their workforce for the changing landscape of cybersecurity. From an economic standpoint, this presents a challenge in managing the transition and mitigating potential social unrest.
AI as the main shield for cybersecurity in banking
To truly harness the benefits of AI while mitigating its inherent risks, banks must adopt a responsible and ethical approach across their operations. This includes actively addressing AI bias by using diverse training data and fairness-aware techniques, and enhancing AI robustness against adversarial attacks through dedicated research and development. Furthermore, banks should prioritize explainable AI systems to ensure transparency, and establish robust ethical frameworks to guide AI-driven decisions, ensuring fairness and accountability. Strengthening data privacy through robust protection measures is also crucial. Equally important is investing in human capital through training and reskilling programs, preparing the workforce for the evolving cybersecurity landscape. Finally, collaborative efforts with regulatory bodies are essential to develop clear and consistent guidelines for the use of AI in banking cybersecurity
AI's promise for banking security is huge, speeding up threat detection. Yet, bias, attacks, and ethics pose risks. Responsible AI is key. Banks must prioritize fairness, robustness, and transparency. Doing so builds a secure system, protecting customers and the economy. Ignoring these risks means losing trust, facing penalties, and inviting costly cyberattacks.
Authored by- S.Ravi
0 notes
Text

wednesday, august 7th, 2024
I'm attempting to learn proper software development this week: performance profiling, writing test cases, and I should probably add more exception handling to my code. I'm grateful that I'm not on a team that constantly demands new features above all else, because it's important to take the time to do maintenance and catch up on tech debt. I'm learning that it's super easy to write code that works, but writing good code requires more work and the results are mostly invisible to people who aren't actually reading & writing the code. it's kind of a weird dynamic, but I just want to level up my skills.
today's to-do list:
read the chapter on basic performance testing
go over the docs for writing unit tests for the web framework we're using
write some code for the current work project
find some time to read for fun
attempt to fix my vmware install so I can finally get back to doing the labs from Practical Malware Analysis
a handful of other small tasks
#op#studyspo#I don't normally post this early in the day but maybe having a todo list on here will help with accountability? we shall see lol
28 notes
·
View notes
Text
Best website development company in Greater Noida
Best Website Development Company in Greater Noida – Config Infotech
Introduction
In the modern digital age, a professional and high-performing website is essential for businesses to succeed. Whether you have a startup, an SME, or a large business, a well-designed website assists in building credibility, driving customers, and increasing sales. If you are searching for the best website development company in Greater Noida, you have come to the right place – Config Infotech. With years of experience, latest technology, and a group of expert developers, Config Infotech provides customized web solutions to empower businesses to grow online.
Why Select Config Infotech?
Website Development Expertise
Config Infotech has expertise in the development and creation of dynamic, responsive, and user-friendly websites. Our expert developers have sound knowledge of all web technologies, such as HTML5, CSS3, JavaScript, PHP, Python, Laravel, WordPress, Magento, and Shopify. For any eCommerce store, corporate site, or portfolio, we are equipped to convert your idea into reality.
Customized Web Solutions
We know that each business is different. Our team collaborates with clients to design bespoke websites that meet their objectives, brand identity, and industry requirements. From user-friendly UI/UX design to smooth backend functionality, we make sure that your website is different from others.
Responsive and Mobile-Friendly Websites
With the rising popularity of mobile devices, it is important to have a mobile-friendly website. Our web development process will ensure that your site is completely responsive, i.e., it will work flawlessly on desktops, tablets, and smartphones, offering a great user experience on all devices.
SEO-Optimized Websites
A website without visibility is of little use. Config Infotech develops SEO-friendly websites that rank higher on search engines like Google and Bing. Our developers integrate on-page SEO strategies, fast-loading pages, clean code, and structured data to enhance your website’s search engine ranking and attract organic traffic.
E-Commerce Website Development
If you're looking to establish an online shopping website, we offer end-to-end eCommerce web development services. We develop websites using platforms such as WooCommerce, Magento, Shopify, and OpenCart to create secure, scalable, and rich-featured eCommerce websites with payment gateway integration, inventory management, and easy-to-use interfaces.
CMS-Based Website Development
Website content managing should be straightforward and effective. We are experienced in Content Management System (CMS) development such as WordPress, Joomla, and Drupal, through which business operators can easily maintain and update their websites.
Quick and Secure Websites
Performance and security are essential success factors of a website. We design lean, fast-loading, speed-optimized websites. On top of this, we ensure advanced security settings to shield your website against hacking attempts, cyber attacks, and malware attacks.
Cheap Web Development Solutions
We offer cheap web development services at Config Infotech while maintaining no trade-off in terms of quality. We offer affordable pricing schemes accommodating startups, SMEs, as well as enterprise-level organizations.
Our Website Development Process
We adhere to a well-defined development process to yield high-quality outputs:
Requirement Analysis: Learning about your business requirements, target audience, and objectives.
Planning & Wireframing: Sketching a blueprint and UI/UX design wireframe.
Development & Coding: Developing the website with the latest frameworks and technologies.
Testing & Quality Assurance: Delighting with a bug-free, speedy, and secure website.
Deployment & Launch: Launching the website live and open to users.
Maintenance & Support: Offering regular updates, fixes, and enhancements.
Industries We Serve
Config Infotech has served a range of industries, including:
E-commerce
Healthcare
Education
Real Estate
Finance & Banking
Travel & Hospitality
Retail & Manufacturing
Client Testimonials
Our clients trust us for our professionalism, technical expertise, and customer support. Here's what they have to say:
"Config Infotech revamped our old website into a new, responsive, and highly interactive platform. Their team is experienced and always ready to assist." – Rahul Sharma, CEO of XYZ Pvt Ltd.
“We needed an eCommerce website with seamless functionality, and Config Infotech delivered beyond our expectations. Highly recommended!” – Priya Gupta, Founder of ABC Store.
Contact Us
If you are looking for the best website development company in Greater Noida, reach out to Config Infotech. Let us help you build a strong online presence and grow your business.
Conclusion
Config Infotech is your go-to partner for professional website development in Greater Noida. For a corporate site, an online store, or a bespoke web application, our experts provide quality solutions that match your requirements. Reach out to us today and bring your business online with a robust, high-performance website!
0 notes
Text
What is a secure software development lifecycle?
A Secure Software Development Lifecycle (SSDLC) ensures security is integrated into every stage of software development rather than being an afterthought. Think of it like building a house, if security isn’t part of the foundation, everything else becomes vulnerable.
Key Phases of Secure Software Development Lifecycle (SSDLC)
Planning & Risk Assessment — Identify potential security threats and compliance requirements early.
Secure Design — Implement security best practices like encryption, authentication and access control.
Development & Secure Coding — Follow industry standards to avoid vulnerabilities like SQL injection and XSS.
Security Testing — Conduct static/dynamic analysis, penetration testing and code reviews.
Deployment & Monitoring — Ensure secure configurations, monitor threats and apply patches regularly.
Maintenance & Continuous Improvement — Stay updated with evolving security risks and improve security measures over time.
Why Secure Software Development Lifecycle Matters
Prevents Security Breaches — Reduces risks like data leaks, hacking and malware attacks.
Enhances Software Reliability — Ensures applications function securely under all conditions.
Protects User Data — Strengthens data encryption, authentication and access control.
Reduces Long-Term Costs — Fixing vulnerabilities early is cheaper than post-launch security patches.
Ensures Compliance — Meets industry regulations like GDPR, ISO 27001 and PCI-DSS to avoid legal issues.
Builds Customer Trust — Secure software fosters credibility and brand reputation.
Final Thoughts
Ignoring security in development is like leaving your front door unlocked eventually, someone will take advantage of it. A Secure Software Development Lifecycle is essential for any business looking to build reliable, secure, and compliant applications. If you need expert solutions for developing secure software, partnering with a leading software development company ensures best practices are followed from the start.
#security#digital marketing#Ssdlc#cybersecurity#encodersunlimited#Software Development#Software Company Siliguri
0 notes
Text
Fighting Cloudflare 2025 Risk Control: Disassembly of JA4 Fingerprint Disguise Technology of Dynamic Residential Proxy
Today in 2025, with the growing demand for web crawler technology and data capture, the risk control systems of major websites are also constantly upgrading. Among them, Cloudflare, as an industry-leading security service provider, has a particularly powerful risk control system. In order to effectively fight Cloudflare's 2025 risk control mechanism, dynamic residential proxy combined with JA4 fingerprint disguise technology has become the preferred strategy for many crawler developers. This article will disassemble the implementation principle and application method of this technology in detail.
Overview of Cloudflare 2025 Risk Control Mechanism
Cloudflare's risk control system uses a series of complex algorithms and rules to identify and block potential malicious requests. These requests may include automated crawlers, DDoS attacks, malware propagation, etc. In order to deal with these threats, Cloudflare continues to update its risk control strategies, including but not limited to IP blocking, behavioral analysis, TLS fingerprint detection, etc. Among them, TLS fingerprint detection is one of the important means for Cloudflare to identify abnormal requests.
Technical Positioning of Dynamic Residential Proxy
The value of Dynamic Residential Proxy has been upgraded from "IP anonymity" to full-link environment simulation. Its core capabilities include:
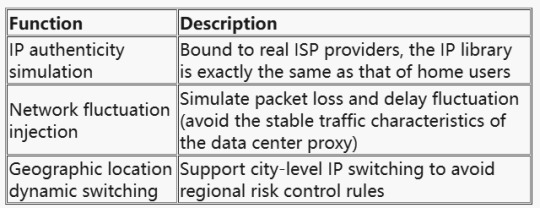
JA4 fingerprint camouflage technology dismantling
1. JA4 fingerprint generation logic
Cloudflare JA4 fingerprint generates a unique identifier by hashing the TLS handshake features. Key parameters include:
TLS version: TLS 1.3 is mandatory (version 1.2 and below will be eliminated in 2025);
Cipher suite order: browser default suite priority (such as TLS_AES_256_GCM_SHA384 takes precedence over TLS_CHACHA20_POLY1305_SHA256);
Extended field camouflage: SNI(Server Name Indication) and ALPN (Application Layer Protocol Negotiation) must be exactly the same as the browser.
Sample code: Python TLS client configuration

2. Collaborative strategy of dynamic proxy and JA4
Step 1: Pre-screening of proxy pools
Use ASN library verification (such as ipinfo.io) to keep only IPs of residential ISPs (such as Comcast, AT&T); Inject real user network noise (such as random packet loss rate of 0.1%-2%).
Step 2: Dynamic fingerprinting
Assign an independent TLS profile to each proxy IP (simulating different browsers/device models);
Use the ja4x tool to generate fingerprint hashes to ensure that they match the whitelist of the target website.
Step 3: Request link encryption
Deploy a traffic obfuscation module (such as uTLS-based protocol camouflage) on the proxy server side;
Encrypt the WebSocket transport layer to bypass man-in-the-middle sniffing (MITM).
Countermeasures and risk assessment
1. Measured data (January-February 2025)

2. Legal and risk control red lines
Compliance: Avoid collecting privacy data protected by GDPR/CCPA (such as user identity and biometric information); Countermeasures: Cloudflare has introduced JA5 fingerprinting (based on the TCP handshake mechanism), and the camouflage algorithm needs to be updated in real time.
Precautions in practical application
When applying dynamic residential proxy combined with JA4 fingerprint camouflage technology to fight against Cloudflare risk control, the following points should also be noted:
Proxy quality selection: Select high-quality and stable dynamic residential proxy services to ensure the effectiveness and anonymity of the proxy IP.
Fingerprint camouflage strategy adjustment: According to the update of the target website and Cloudflare risk control system, timely adjust the JA4 fingerprint camouflage strategy to maintain the effectiveness of the camouflage effect.
Comply with laws and regulations: During the data crawling process, it is necessary to comply with relevant laws and regulations and the terms of use of the website to avoid infringing on the privacy and rights of others.
Risk assessment and response: When using this technology, the risks that may be faced should be fully assessed, and corresponding response measures should be formulated to ensure the legality and security of data crawling activities.
Conclusion
Dynamic residential proxy combined with JA4 fingerprint camouflage technology is an effective means to fight Cloudflare 2025 risk control. By hiding the real IP address, simulating real user behavior and TLS fingerprints, we can reduce the risk of being identified by the risk control system and improve the success rate and efficiency of data crawling. However, when implementing this strategy, we also need to pay attention to issues such as the selection of agent quality, the adjustment of fingerprint disguise strategies, and compliance with laws and regulations to ensure the legality and security of data scraping activities.
0 notes
Text
How AI Agents Are Enhancing Cybersecurity in 2025
The cybersecurity landscape is evolving at an unprecedented pace, with cyber threats becoming increasingly sophisticated and difficult to predict. As technology continues to advance, traditional security systems often struggle to keep up with emerging threats. This is where Artificial Intelligence (AI) agents come into play. In 2025, AI-driven technologies are playing a pivotal role in enhancing cybersecurity, making systems smarter, faster, and more adaptive to the ever-changing threat environment. This blog explores how AI agents are revolutionizing cybersecurity and helping organizations stay ahead of cybercriminals.
The Rising Threats to Cybersecurity
Cyberattacks have become more frequent, complex, and damaging over the past decade. From ransomware attacks and phishing schemes to advanced persistent threats (APTs) and insider threats, organizations are under constant attack. The cost of these cybercrimes is escalating, with global cybercrime damages expected to reach $10.5 trillion annually by 2025. As a result, businesses and government organizations must find ways to strengthen their cybersecurity defenses while minimizing the impact of these attacks.
Traditional cybersecurity systems, such as firewalls, antivirus software, and intrusion detection systems, rely on predefined rules to detect and block threats. However, these solutions often struggle with zero-day attacks (new, previously unknown vulnerabilities) and sophisticated tactics used by cybercriminals. This is where AI agents step in, offering dynamic and proactive protection that can predict, identify, and respond to threats in real-time.
AI Agents: A Game-Changer for Cybersecurity
AI agents are specialized programs powered by machine learning (ML) and deep learning (DL) algorithms, designed to mimic human intelligence and automate tasks that would otherwise require human intervention. In cybersecurity, AI agents are used to detect and mitigate threats faster and more accurately than traditional systems. By leveraging large datasets, AI agents can learn from past attacks, adapt to new patterns, and continuously improve their ability to identify and neutralize threats.
AI agents can be deployed across various layers of an organization's cybersecurity framework, including network monitoring, threat detection, incident response, and vulnerability management. Here’s how AI agents are enhancing cybersecurity in 2025:
1. Proactive Threat Detection and Prevention
Traditional cybersecurity systems are reactive, often only identifying threats after they have already breached defenses. AI agents, on the other hand, offer a proactive approach to threat detection. By analyzing vast amounts of network traffic, user behavior, and system logs in real-time, AI agents can detect suspicious patterns and potential threats before they escalate into full-blown attacks.
For example, AI Agent Development can detect anomalies in network traffic that deviate from normal behavior. This includes unusual data exfiltration, unauthorized access attempts, or irregular patterns of activity by internal users. By continuously monitoring and analyzing data, AI agents can flag potential threats and take immediate action to block or isolate them. This early intervention helps organizations respond to threats before they can cause significant damage.
2. Advanced Malware Detection and Analysis
Malware is constantly evolving, with cybercriminals using increasingly sophisticated methods to bypass security measures. Traditional antivirus software relies on signature-based detection, which looks for known malware patterns. However, this method is ineffective against new or mutated forms of malware.
AI-powered agents are capable of identifying previously unknown malware by analyzing the behavior of files and programs. Through techniques like machine learning, AI agents can spot abnormal behaviors indicative of malicious activity, such as file encryption, data modification, or suspicious communication with external servers. These agents can then quarantine or neutralize the threat in real-time, preventing malware from spreading across the network.
3. Automated Incident Response
One of the biggest challenges in cybersecurity is the speed at which organizations can respond to security incidents. Manual response to a cyberattack often involves multiple teams, coordination, and significant delays. During this time, attackers may further compromise systems, making recovery more difficult.
AI agents significantly improve the incident response process by automating many of the tasks traditionally performed by security teams. Once an AI agent detects a threat, it can automatically initiate a predefined response, such as isolating affected systems, blocking malicious IP addresses, or shutting down compromised accounts. This rapid response minimizes the window of opportunity for attackers to cause harm and reduces the burden on human security teams.
Moreover, AI agents can learn from past incidents to improve response strategies. By analyzing previous attacks and their outcomes, AI agents can refine their decision-making processes, ensuring that future incidents are handled even more efficiently.
4. Behavioral Analytics and User Monitoring
User behavior analytics (UBA) is another area where AI agents are making a significant impact. AI-powered systems can track and analyze user behavior across an organization’s network to identify deviations from normal activity. These deviations often signal malicious intent or a compromised account.
For example, if an employee who typically works within a specific geographic region suddenly accesses sensitive data from an unfamiliar location, an AI agent may flag this behavior as suspicious. AI agents can also detect actions like unauthorized file transfers, excessive privilege escalations, or attempts to access data outside of an employee’s role. By continuously monitoring user behavior, AI agents can identify insider threats and compromised accounts faster than manual security systems.
5. Threat Intelligence and Automated Updates
Staying up-to-date with the latest threat intelligence is critical in today’s rapidly evolving cybersecurity landscape. AI agents can automatically collect and analyze vast amounts of data from threat intelligence feeds, security blogs, and cybersecurity reports. This information is then used to update security systems with the latest threat signatures, attack methods, and defense strategies.
AI agents can also predict emerging threats by analyzing trends in cyberattacks and identifying new attack vectors. By continuously learning and adapting to the latest threat intelligence, AI agents ensure that security systems are always equipped to defend against the most current and advanced threats.
6. Vulnerability Management and Patch Automation
One of the most common entry points for cyberattacks is through vulnerabilities in software or hardware systems. AI agents play a crucial role in vulnerability management by automatically scanning systems for known vulnerabilities, assessing their severity, and prioritizing them for patching.
Additionally, AI agents can automate the patching process, ensuring that vulnerabilities are addressed as soon as a patch becomes available. This reduces the risk of exploitation and minimizes the time organizations are exposed to potential attacks.
7. AI-Powered Encryption and Data Privacy
As data privacy concerns continue to rise, AI agents are being leveraged to enhance encryption techniques and ensure compliance with regulations like GDPR and CCPA. AI can be used to identify sensitive data across an organization’s network and automatically apply encryption measures to protect it from unauthorized access.
In addition, AI agents can monitor data access and usage patterns to ensure compliance with data protection policies. If an employee attempts to access or share sensitive information without proper authorization, an AI agent can block the action and alert security teams.
Conclusion
As the complexity and frequency of cyberattacks continue to rise, organizations must rely on innovative technologies like AI agents to strengthen their cybersecurity defenses. In 2025, AI agents are playing a critical role in proactively identifying threats, automating incident response, detecting advanced malware, and enhancing data privacy. By leveraging machine learning and deep learning algorithms, AI agents are becoming smarter, faster, and more adaptive, providing organizations with the tools they need to stay ahead of cybercriminals.
Incorporating AI agents into cybersecurity strategies is no longer just an option it’s a necessity. By embracing these intelligent systems, businesses can create a more resilient and secure environment that is better equipped to handle the evolving landscape of cyber threats. The future of cybersecurity is undoubtedly powered by AI, and as these technologies continue to advance, we can expect even more powerful defenses to emerge in the battle against cybercrime.
0 notes
Text
Building a Stand-Out Cybersecurity Analyst Portfolio
Cybersecurity is a rapidly growing field with a high demand for skilled professionals1. As a cybersecurity analyst, your portfolio is a crucial tool for showcasing your abilities and landing your dream job. It provides tangible evidence of your skills and experience, setting you apart from other candidates. This article will guide you through the essential projects that should be included in a cybersecurity analyst portfolio, categorized by skill level, and provide insights into the tools and resources available to help you succeed.
I. Understanding the Purpose of a Cybersecurity Portfolio
Before diving into specific projects, it's crucial to understand the purpose of your portfolio. It serves as a dynamic representation of your skills, knowledge, and experience in cybersecurity. Think of it as a curated collection of your best work, demonstrating your ability to apply theoretical concepts to real-world scenarios2. It's important to remember that no cybersecurity portfolio can prevent all threats; a balanced and layered security approach is essential3. Moreover, managing a cybersecurity portfolio is an ongoing process that requires continuous monitoring, evaluation, and adjustments to maintain effectiveness3.
A well-crafted portfolio can help you:
Land a job: A strong portfolio can significantly increase your chances of getting hired by showcasing your practical skills and experience to potential employers4.
Demonstrate your expertise: It allows you to highlight your specialized knowledge in specific areas of cybersecurity, such as penetration testing, incident response, or network security2.
Build credibility: Including projects and certifications in your portfolio adds credibility to your claims and demonstrates your commitment to the field2.
Track your progress: It serves as a record of your learning journey and helps you identify areas for improvement5.
II. Essential Skills for Cybersecurity Analysts
Cybersecurity analysts require a diverse skillset to effectively protect organizations from cyber threats. These skills can be broadly categorized into technical skills and soft skills1.
Skill Category
Skill
Description
Technical Skills
Networking and System Administration
A strong foundation in networking concepts, including network protocols, topologies, and security measures, is essential. You should also be familiar with system administration tasks, such as user management, access control, and system hardening.
Security Incident Handling and Response
Knowing how to identify, contain, and remediate security incidents is crucial. This includes understanding incident response frameworks, conducting forensic analysis, and implementing recovery strategies.
Operating Systems and Virtual Machines
Familiarity with various operating systems (Windows, Linux, macOS) and their security features is necessary. You should also be comfortable working with virtual machines for testing and analysis.
Network Security Control
Understanding how to implement and manage network security controls, such as firewalls, intrusion detection/prevention systems (IDS/IPS), and VPNs, is crucial.
Malware Prevention and Detection
Knowledge of different types of malware, their attack vectors, and mitigation techniques is essential. This includes using malware analysis tools and implementing anti-malware solutions.
Coding and Encryption
Proficiency in scripting languages like Python and understanding encryption algorithms are valuable assets. These skills are used for automating tasks, developing security tools, and analyzing malicious code.
Cloud Security
As more organizations move to cloud environments, understanding cloud security concepts and best practices is becoming increasingly important. This includes securing cloud infrastructure, managing access control, and implementing data protection measures.
Soft Skills
Communication
Effectively communicating technical information to both technical and non-technical audiences is crucial. This includes writing reports, presenting findings, and explaining security concepts to stakeholders.
Collaboration
Cybersecurity analysts often work in teams and need to collaborate effectively with colleagues, other departments, and external organizations.
Problem-solving and Analytical Skills
The ability to analyze security events, identify root causes, and develop solutions is essential.
Critical Thinking
Cybersecurity analysts need to think critically to assess risks, evaluate security measures, and anticipate potential threats.
Adaptability
The cybersecurity landscape is constantly evolving, so analysts need to be adaptable and willing to learn new technologies and techniques.
III. Cybersecurity Project Ideas by Skill Level
When selecting projects for your portfolio, it's important to align them with your career goals and the specific technical areas you want to explore4. Brainstorming and feasibility analysis are crucial to ensure that your chosen projects are achievable and align with your skill level4. Leverage online resources, cybersecurity communities, and mentorship opportunities for inspiration and guidance in refining your project concepts4. Finally, remember to tailor your projects to specific industries to demonstrate your understanding of their unique security needs4. For example, you could develop financial tools that secure transaction data or a healthcare app focused on patient data security.
A. Beginner Projects
These projects focus on foundational skills and concepts, providing a starting point for building your portfolio6.
Packet Sniffer: Develop a simple packet sniffer using Python to capture and analyze network traffic. This project helps you understand network protocols and identify potential security issues6.
Keylogger: Create a basic keylogger to record keystrokes. This project teaches you about input monitoring and potential security risks associated with keylogging7.
Lost Data Retrieval: Develop a procedure to recover data after a simulated ransomware attack or data corruption event. This project helps you understand data backup and recovery techniques7.
Research-Based Projects: Conduct research on cybersecurity tools, recent cyberattacks, or specific security topics. This can involve comparing different tools, analyzing attack vectors, or writing a case study7.
Caesar Cipher Encryption/Decryption: Implement a Caesar cipher encryption and decryption tool to understand basic cryptography concepts6. Be sure to document the steps involved in creating the tool, including the selection of encryption algorithms, implementation, and integration into a security framework9.
Simple Network Scanner: Create a network scanner to identify devices and open ports on a network6.
Denial-of-Service (DoS) Detection: Develop a basic DoS detection tool to monitor network traffic and identify potential DoS attacks6.
SQL Injection: Create a script to test for SQL injection vulnerabilities in a web application6.
Password Strength Tester: Develop a tool to evaluate the strength of passwords based on factors like length, complexity, and the use of special characters6.
File Integrity Checker: Create a tool to verify the integrity of system files by comparing them to known hashes or checksums6.
Simple Malware Scanner: Build a basic malware scanner using the Yara framework to detect malicious files6.
B. Intermediate Projects
These projects build upon the foundational skills and introduce more complex challenges6.
SQL Injection Testing and Remediation: Set up a vulnerable web application and practice identifying and fixing SQL injection vulnerabilities6.
RFID Blocking Application: Develop an application that blocks unauthorized RFID scans to protect against data theft7.
Security Assessment Report: Conduct a security audit of a website or network and document your findings in a professional report7.
Honeypot: Set up a honeypot to attract and analyze cyberattacks, gaining insights into attacker behavior6.
Firewall Implementation Simulator: Develop a simple firewall application and document the process, including design, implementation, and testing phases9.
C. Advanced Projects
These projects require a deeper understanding of cybersecurity concepts and involve more sophisticated tools and techniques7.
Build Your Own Encryption Software: Develop a custom encryption application using advanced cryptographic algorithms7.
Create a Cybersecurity Policy from Scratch: Write a comprehensive cybersecurity policy for an organization, addressing various security aspects7.
Ethically Hack an Android Device: Learn Android penetration testing techniques to identify vulnerabilities and recommend security measures7.
Develop a Machine Learning Model for Threat Detection: Build a machine learning model to detect malicious activities, such as malware or intrusion attempts7.
Ransomware Detection System: Develop a system to detect and analyze ransomware behavior10.
Machine Learning-Based Intrusion Detection: Implement an intrusion detection system that uses machine learning to improve accuracy and efficiency10.
Blockchain-Based Data Integrity System: Explore the use of blockchain technology to ensure data integrity and security10.
IV. Open-Source Tools and Datasets for Cybersecurity Projects
Leveraging open-source tools and datasets can enhance your portfolio by providing access to real-world data and industry-standard tools9.
A. Open-Source Tools
Tool/Platform
Purpose
Application in Projects
Wireshark
Network Analysis
Traffic Monitoring & Issue Diagnosis
Metasploit
Vulnerability Assessment
Penetration Testing & Security Audits
Kali Linux
Ethical Hacking
Security Research & Exploit Development
OWASP ZAP
Web Application Security Scanner
Identify vulnerabilities in web applications
OpenVAS
Vulnerability Scanner
Vulnerability scanning and management
Trivy
Container Security Scanner
Detect vulnerabilities in container images
Kube-bench
Kubernetes Security
Assess the security of Kubernetes clusters
Prowler
Cloud Security
Security assessments for AWS, Azure, Google Cloud, and Kubernetes
Duo Security Free Edition
Two-Factor Authentication
Enhance login security
Comodo EDR
Endpoint Detection and Response
Detect and respond to threats on endpoints
B. Cybersecurity Datasets
Several online platforms offer datasets for cybersecurity research and projects:
Kaggle: A platform with various cybersecurity datasets, including network traffic data, malware samples, and intrusion detection datasets11.
York University: Provides datasets for source code authorship attribution and SQL injection attacks13.
GWU LibGuides: Offers links to various cybersecurity datasets, including the National Vulnerability Database and the SOREL-20M malware dataset14.
GitHub: Many researchers and organizations share cybersecurity datasets on GitHub15.
V. Presenting and Showcasing Cybersecurity Projects in a Portfolio
Effectively presenting your projects is crucial for making a strong impression2. When building your portfolio, consider different formats and platforms to showcase your work7. Some popular options include GitHub repositories for code-based projects, personal websites for a more comprehensive overview, and online platforms like Cake.me for creating visually appealing portfolios16. You can also use platforms like Google Sites or LinkedIn to host your portfolio17.
Choose the Right Format: Consider using online platforms like GitHub, a personal website, or LinkedIn to showcase your projects2. Use visuals and infographics to make your portfolio engaging, and choose a design that aligns with your personal brand19. Ensure the layout is clean and easy to navigate for a positive user experience19.
Document Your Work: Provide clear and concise documentation for each project, explaining the objective, methodology, tools used, and results achieved7. Include specific metrics or outcomes, such as reduced malware incidents or improved system performance, to provide concrete evidence of the project's impact9.
Use Visuals: Incorporate screenshots, diagrams, or other visuals to make your portfolio more engaging and easier to understand19.
Highlight Key Skills: Clearly demonstrate how your projects showcase the essential skills required for a cybersecurity analyst role19.
Tailor to Your Audience: Adapt your portfolio to the specific job or audience you are targeting2.
Define and Document: Define and document project goals and security risks early on to set clear objectives and manage potential challenges9.
Risk Assessment: Implement a continuous risk assessment and mitigation plan to demonstrate a proactive approach to security9.
Communication: Ensure consistent and open communication among team members when working on projects to promote collaboration and efficient problem-solving9.
Record Keeping: Keep detailed records of project progression and security measures to track progress, identify areas for improvement, and demonstrate a systematic approach to security9.
Proactive Security: Encourage a proactive stance on security and team accountability to foster a security-conscious culture and promote responsibility within the team9.
VI. Cybersecurity Competitions and Challenges
Participating in cybersecurity competitions and challenges can be a valuable addition to your portfolio9. These events provide opportunities to:
Gain practical experience: Apply your skills in a competitive environment and solve real-world cybersecurity challenges.
Test your knowledge: Assess your understanding of cybersecurity concepts and identify areas for improvement.
Network with professionals: Connect with other cybersecurity enthusiasts and professionals.
Enhance your resume: Demonstrate your commitment to the field and showcase your achievements.
Some popular cybersecurity competitions include:
National Collegiate Cyber Defense Competition (CCDC): A team-based competition where students defend a network against cyberattacks21.
CyberPatriot: A national youth cyber education program with competitions for students in grades K-1221.
CyberForce® Competition: A competition hosted by the Department of Energy that focuses on securing critical infrastructure21.
US Cyber Challenge: A program that identifies and develops cybersecurity talent through competitions and training programs21.
President's Cup Cybersecurity Competition (PCCC): A competition for federal employees to test their cybersecurity skills21.
VII. Conclusion
Building a strong cybersecurity analyst portfolio requires a combination of technical skills, practical experience, and effective presentation. By focusing on relevant projects, utilizing open-source tools and datasets, and showcasing your work in a clear and concise manner, you can create a portfolio that will impress potential employers and help you launch a successful career in cybersecurity. Start building your portfolio today and demonstrate your passion and expertise in this exciting and evolving field.
Works cited
1. Become a security analyst: skills and steps - Cybersecurity Guide, accessed February 2, 2025, https://cybersecurityguide.org/careers/security-analyst/
2. A Step-by-Step Guide to Building a Cybersecurity Portfolio | Cyber Security District, accessed February 2, 2025, https://www.cybersecuritydistrict.com/a-step-by-step-guide-to-building-a-cybersecurity-portfolio/
3. Creating a Balanced Cybersecurity Portfolio - Early Adopter Research, accessed February 2, 2025, https://earlyadopter.com/research-missions/cybersecurity-portfolio/
4. Cyber Security Projects for Resume Building : 2025 - StationX, accessed February 2, 2025, https://www.stationx.net/cyber-security-projects-for-resume/
5. CyberSecurity Project Portfolio For Your Resume | 2024 - YouTube, accessed February 2, 2025, https://www.youtube.com/watch?v=Mhk2TyXgvYI
6. Top 20+ Cyber Security Projects for 2025 [with Source Code] - KnowledgeHut, accessed February 2, 2025, https://www.knowledgehut.com/blog/security/top-cyber-security-projects
7. Cybersecurity Projects to Grow Your Skills & Portfolio - Springboard, accessed February 2, 2025, https://www.springboard.com/blog/cybersecurity/cyber-security-projects/
8. Top 6 Cybersecurity Projects Ideas for Beginners - GeeksforGeeks, accessed February 2, 2025, https://www.geeksforgeeks.org/top-6-cybersecurity-projects-ideas-for-beginners/
9. Essential Cyber Security Projects for Enhancing Your Skillset and Portfolio - Coding Temple, accessed February 2, 2025, https://www.codingtemple.com/blog/essential-cyber-security-projects-for-enhancing-your-skillset-and-portfolio/
10. Top Cyber Security Projects for Every Skill Level in 2025, accessed February 2, 2025, https://www.simplilearn.com/top-cyber-security-projects-article
11. Find Open Datasets and Machine Learning Projects - Kaggle, accessed February 2, 2025, https://www.kaggle.com/datasets?search=cybersecurity
12. Find Open Datasets and Machine Learning Projects - Kaggle, accessed February 2, 2025, https://www.kaggle.com/datasets?tags=17181-Cyber+Security
13. Cybersecurity Datasets - Behaviour-Centric Cybersecurity Center (BCCC) - York University, accessed February 2, 2025, https://www.yorku.ca/research/bccc/ucs-technical/cybersecurity-datasets-cds/
14. Find Statistics and Datasets - Cybersecurity - Research Guides at George Washington University, accessed February 2, 2025, https://libguides.gwu.edu/cybersecurity/datasets
15. gfek/Real-CyberSecurity-Datasets: Public datasets to help you address various cyber security problems. - GitHub, accessed February 2, 2025, https://github.com/gfek/Real-CyberSecurity-Datasets
16. Cybersecurity Portfolio Examples - Cake, accessed February 2, 2025, https://www.cake.me/portfolios?q=cybersecurity
17. Building a Cybersecurity Professional Portfolio: Methods and Projects | by Joshua U, accessed February 2, 2025, https://medium.com/@joshuaudayagiri/building-a-cybersecurity-professional-portfolio-methods-and-projects-e120e686d459
18. How to build a cybersecurity portfolio: get started today - General Assembly, accessed February 2, 2025, https://generalassemb.ly/blog/how-to-build-a-cybersecurity-portfolio/
19. Your Guide to Crafting a Jaw-Dropping Cybersecurity Portfolio! - MyTurn Careers, accessed February 2, 2025, https://myturn.careers/blog/your-guide-to-crafting-a-jaw-dropping-cybersecurity-portfolio/
20. Kwangsa19/Ketmanto-Cybersecurity-Portfolio - GitHub, accessed February 2, 2025, https://github.com/Kwangsa19/Ketmanto-Cybersecurity-Portfolio
21. Cybersecurity Competitions & Games - NICCS - CISA, accessed February 2, 2025, https://niccs.cisa.gov/cybersecurity-career-resources/cybersecurity-competitions-games
22. Academic Outreach College and University Cyber Competitions, accessed February 2, 2025, https://cybercoe.army.mil/Academic-Outreach/Academia-Colleges-and-Universities/College-and-University-Cyber-Competitions/
23. Cyber Competitions - U.S. Army Cyber Center of Excellence, accessed February 2, 2025, https://cybercoe.army.mil/Academic-Outreach/K-12-Parents-Students-Teachers/Cyber-Competitions/
24. Cybersecurity Competitions | Homeland Security, accessed February 2, 2025, https://www.dhs.gov/archive/science-and-technology/cybersecurity-competitions
0 notes
Text
Certified Ethical Hacker V12: A Comprehensive Guide to Ethical Hacking

Great is the pursuit of careers while the demand for cybersecurity experts has never been higher. Amongst the most well-known are the Certified Ethical Hacker V12 (CEH V12) that EC-Council offers, catering for the presence of cybersecurity professionals who are ready to be equipped on the needed skills in weaknesses recognition, securing networks, and thinking like a hacker but in a manner that is ethical and lawful.
Key Features of CEH V12
CEH is the globally accepted certification, which makes an individual eligible by proving competence to assess the security posture of any organization. CEH V12 is the current version that encompasses the latest development and methodologies integrated into the system with the cyber environment in continuous evolution.
New Hacking Techniques
Arising day-to-day new threats and CEH V12 brings within the system some new hacking tools, exploits, and countermeasures.
Learning through Labs:
It has the exercise of the thing with the actual lab practice in the latest edition. Hence, the candidates get a chance to replicate the actual cyberattacks.
Cloud Security Focus
CEH V12 is more cloud-computing-adoptive, and topics about cloud security are also included in the version. Practitioners can now protect cloud-based environments. It presents IoT and OT security.
In the present scenario, CEH V12 has also included topics about the security of IoT and OT to face the challenges provided by modern-day cyber security Threat Intelligence & Malware Analysis
The candidate will have a better hold in the field of threat intelligence, malware analysis, and Cyber security frameworks
Who Should Learn CEH V12?
It is apt for such professionals who conduct cybersecurity, IT, network security, and system administration. For the second category of professionals CEH V12 is more relevant:
Ethical Hackers & Penetration Testers
Security Analysts & Engineers
IT Security Officers
Network Administrators
Risk & Compliance Analysts
Why get CEH V12 Certified?
Industry recognition
CEH is the most honored ethical hacking certification in the world.
Good Career Opportunities
There are more chances of jobs in high-rated companies all over the globe.
Good reward scales
The certified ethical hackers will get much more than the non-certified hackers.
Improved Cyber Security Expertise
The training makes the professional take on cyber threats much better.
Exam Details
CEH V12 exam consists of:
125 multiple choice questions
Total Time: 4 hours
Passing Score: 60-85% (version based on the exam)
Exam Type: Online, proctored, or in an accredited testing center
How to Prepare for CEH V12?
OFFICIAL CEH Course Preparation
In a nutshell, EC-Council provides an official training course that has modules for all the topics of the exam.
Practice with Hands-on Labs
Use CEH iLabs and other cybersecurity labs for real-time experience.
Take Practice Tests
Get familiar with the format of the exam and know which area needs improvement.
Join Ethical Hacking Communities
Engaging with professionals in cybersecurity forums can help provide insights and learning opportunities.
Keep Up to Date
Cybersecurity is such a dynamic field, and the need to remain updated about new threats and solutions. One of the best credentials to pursue if one wants to either start or take their career up a notch in ethical hacking and cybersecurity is CEH V12. The curriculum has been updated, with hands-on training and real-world relevance, to empower professionals to combat modern cyber threats. For someone just getting started with cybersecurity or seeking additional skills, the pursuit of CEH V12 is the way to go.
0 notes
Text
Appdome Breaks the Surge in Android & iOS Trojans Globally
PHILIPPINES – Appdome, the leader in protecting mobile businesses, today announced a platform upgrade that includes 24 new dynamic defense plugins targeting hundreds of Banking Trojans, Trojan Spyware, and Remote Access Trojan malware across Android and Ios apps. The new plugins for Appdome’s patented AI-Native XTM Platform are designed to use in-app behavioral analysis to combat the prolific…
0 notes