#Fast File Encryptor
Explore tagged Tumblr posts
Text
Fast File Encryptor 11.7 Free Download
Fast File Encryptor is designed for fast processing of extremely large files. It can encrypt or decrypt files, contents of folders and contains a lot of additional tools. Fast File Encryptor presents a flexible user interface with detailed messages about all operations. Fast File Encryptor features the following tools: Encrypt File, Encrypt Folder, Often Used Files, File Shredder, Folder…

View On WordPress
0 notes
Video
youtube
BULK TEXT ENCRYPTOR FOR DATA ENTRY PIXCEL NOTEPAD, PIXCEL NOTEPAD, RTX NOTEPAD
Hello! Welcome to Intellitech Data Services and Software Solutions. Typing manually in data entry projects is too hard as it takes up to 30 minutes to one hour as per image complications and fonts language. Even if you type manually, there will be few errors in your project which leads to the rejection of your project in Quality report. Don't get worried, Our automation software will help you in completing your project in time. Also, Our QC reports will help you to correct errors as per excel sheet. You can directly go to the errors and correct them. This will not only save your time, but it will save your hard work. First of all please keep in mind that never use any Autotyper or Fast Typing Software for Notepad Plus or Pixcel Notepad Conversion. These softwares are called third party softwares and are banned by Data Entry Companies. Using these third party softwares will directly reject your project. As a professional in the field of data entry and document management, we understand the importance of accuracy and efficiency when it comes to converting images to text. When tasked with converting images to text using Notepad Plus, we approach the process with a methodical and detail-oriented mindset. First, we carefully examine the image to identify any text that needs to be transcribed. We pay close attention to the quality of the image, ensuring that it is clear and legible. If necessary, we adjust the brightness and contrast to improve the readability of the text. Next, we open Bulk Text Encryptor Software to convert the file into Notepad Plus. We double-check our work for any errors or discrepancies, correcting them as needed. Throughout the conversion process, We remain focused and diligent, taking the time to ensure that every word is accurately transcribed. We understand the importance of precision in this task, as even a small mistake could have significant consequences. Once the conversion is complete, we review the text one final time to confirm its accuracy. We take pride in our ability to efficiently and effectively convert images to text using Bulk Text Encryptor Software, knowing that our attention to detail and commitment to quality set us apart as a professional in our field. For Software and service related queries. Whatsapp us at 7428811442 or email us at [email protected]. Don't forget to like and click subscribe button.
Intellitech Data Services has developed a revolutionary software called Bulk Text Encryptor that is changing the way data entry professionals work. With this software, any cursive image containing data can be converted into Pixcel Notepad .nts and Notepad Plus .wrt format, making it easier to input and manipulate the information.
Gone are the days of struggling to decipher handwritten notes or documents. Now, with the click of a button, data entry specialists can upload an image of cursive text and have it transformed into a digital format that is easy to read and edit. This not only saves time but also reduces the risk of errors that can occur when transcribing handwritten information.
The Bulk Text Encryptor software is compatible with both Pixcel Notepad and Notepad Plus, two popular text editing programs used by professionals in the data entry field. This compatibility ensures that users can seamlessly integrate the encrypted data into their existing workflow without any disruptions.
Intellitech Data Services has truly revolutionized the data entry process with this innovative software. By streamlining the conversion of cursive images into digital text, they have made it easier for professionals to input and manage data efficiently. This not only improves productivity but also ensures the accuracy of the information being processed.
Data entry professionals can now say goodbye to the tedious task of transcribing handwritten notes and hello to a more efficient and effective way of working. Thanks to Intellitech Data Services and their Bulk Text Encryptor software, the future of data entry is looking brighter than ever.
For Software and service related queries. Whatsapp us at 7428811442 or email us at [email protected]. Don't forget to like and click subscribe button.
0 notes
Text
Truecrypt download

#Truecrypt download mac os#
#Truecrypt download install#
#Truecrypt download code#
Users of TrueCrypt gave it a rating of 5 out of 5 stars. Encrypts an entire partition or storage device such as USB flash drive or hard drive. Main features: Creates a virtual encrypted disk within a file and mounts it as a real disk. Note: TrueCrypt development has stopped (for now) TrueCrypt. Gibson Research Corporation is owned and operated by Steve Gibson.
#Truecrypt download code#
TrueCrypt code has become problemmatical to use. VeraCrypt is being continually maintained, while the aging.
#Truecrypt download mac os#
TrueCrypt runs on the following operating systems: Windows. Free open-source disk encryption software for Windows 7/Vista/XP, Mac OS X, and Linux. The open source VeraCrypt is based upon TrueCrypt v7.1a. The most prevalent version is 7.1a, which is used by 60 % of all installations. Click Create Volume (marked with a red rectangle for clarity). STEP 2: The main TrueCrypt window should appear. Then launch TrueCrypt by double-clicking the file TrueCrypt.exe or by clicking the TrueCrypt shortcut in your Windows Start menu.
#Truecrypt download install#
It was initially added to our database on. If you have not done so, download and install TrueCrypt. It can also maintain an on-the-fly-encrypted volume (data storage device). TrueCrypt is a software designed to protect your important data by encrypting it. The latest version of TrueCrypt is 7.2, released on. tags: disk encryptor, virtual disk creator, data encryptor, encryptor, decryptor, encrypt. It was checked for updates 785 times by the users of our client application UpdateStar during the last month. TrueCrypt is a Open Source software in the category Security developed by TrueCrypt Foundation. The best thing about TrueCrypt is that it is extremely fast. Unlike other folder locking applications that can be circumvented by booting in safe mode or booting from a cd (or even worse, by terminating the process in Task Manager), the only way to access the data is to mount it using TrueCrypt. The entire file system is encrypted (i.e., file names, folder names, contents of every file, and free space). Until decrypted, a TrueCrypt volume appears to be nothing more than a series of random numbers. No data stored on an encrypted volume can be read (decrypted) without using the correct password or correct encryption key. On-the-fly encryption means that data are automatically encrypted or decrypted right before they are loaded or saved, without any user intervention. TrueCrypt is a software system for establishing and maintaining an on-the-fly-encrypted drive.

0 notes
Video
vimeo
How to Copy paste in Notepad RT++ from TECH TAB DATA SERVICES on Vimeo.
#pixcel nts #globalid #notepadpx #notepadnts
Hello, Welcome to TECHTAB DATA SERVICES.
India's 1st Encryption Software for Data Entry Notepads and Projects.
NEVER USE AUTOTYPER SOFTWARE IN COMPANY NOTEPADS AS IT IS EASILY DETECTED IN QC REPORT WHICH CAN REJECT YOUR PROJECT. AUTOTYPER SOFTWARE IS VERY OLD TECHNIQUE FOR FAST TYPING AND IT IS TOTALLY UNSAFE. ALWAYS USE THE LATEST ENCRYPTION TECHNIQUE.
Contact us: Phone numbers:- 9522809999 (Whatsapp/Call) Email id: [email protected] Website:- image-to-notepad.zyrosite.com/ #pixcel #startxt #autotyper
In this Video, you will see the conversion of Ebook Image text to Company Notepads Demo. So lets get started. In Many Company Notepads like Notepad Plus, Notepad RT++, NTS notepad, Blend Notepad, Notebook PX,
Company gives Image files to customers, which has to be typed into their own Notepad , where copy paste is Not Allowed. So, We have developed an encryptor software, which will convert all the text data to these Company Notepads in few minutes. This process is hundred percent guaranteed encrypted, Safe and non-detectable.
Using any Autotyper software is hundred percent risky since autotyper types fixed keystrokes and its hundred percent detected by Data Entry Companies in their QC report.
This is the Only Software in the Whole market, which can type the data in Company Notepad without using any autotyper or third party tool. It the Fastest Convertor Available in the world. Our Goal is to make the data entry work easier for people who are unable to give their whole day for typing. This encryptor saves 98 percent of your time and makes your work totally easy. Enjoy the rest of the Video ,and also Subscribe the Channel for all the Future Updates of the this encryptor. For More details Call ,or Whatsapp us on 9522809999 .Thanks for Watching Bulk Text Encryptor demo video, For More details Contact us and check the description.
How to copy paste in NOTEPAD PLUS, short trick, copy pasting DATA entry Typing 100% working, FREE #data #entry #typing #jobs #notepadplus #rtnotepad #rt+notepad #blendNotepad #rtx++ #rtx+ #notepadrtx #px how to copy paste in notepad rt++,notepad rt++,copy paste in notepad rt++,rt notepad,.xtt,.rtx,notepad rt,notepad rt++ copy paste,image to text conversion,px,rt,auto typer,image to notepad rt++,inteligent data services,notepad rt++ auto typing software,rtx,blend notepad,notepad rtx++,automatic typing,copy paste software for notepad rt,notepad rt++ auto typer software,notepad rt copy paste,rt++,notepad rtx,.wrt,how to convert image to notepad,notepad rt++ auto typer,image to rt notepad,notepad rtx++ copy paste,image to notepad ++ v.2,notepad plus,data conversion,
Contact us: Phone numbers:- 9522809999 (Whatsapp/Call) Email id: [email protected] Website:- image-to-notepad.zyrosite.com/
#notepadplus,#notepadrtx,#notepadrt,#rtnotepad,#nts,#pixcel,#starttxt,#notebook.exe,#notepadrt.exe,#rtnotepad.exe,#rtxnotepad.exe,#notepadrtx.exe,#blendnotepad,#blendnotepad.exe,#pixcel.exe,#xttconversion,#wrtconversion,#rtxconversion,#ntsconversion,#txtconversion,#dataentry,#imagetotext,#imagetotextconversion,#howtoconvertimagetotext?,#notepadplushack,#notepad++,#notepadplusplus.exe,#NotepadRT++V2,#xtt,#pxnotepad,#notepadpx,#pxnotepad.exe,#notepadplus2022,#blendnotepad2022,#dataentrysoftware
#notepadplus #blendnotepad #notepadrt
#notepadplus #notepadrtx #notepadrt #rtnotepad #nts #pixcel #starttxt #notebook.exe #notepadrt.exe #rtnotepad.exe #rtxnotepad.exe #notepadrtx.exe #blendnotepad #blendnotepad.exe #pixcel.exe #xttconversion #wrtconversion #rtxconversion #ntsconversion #txtconversion #dataentry #dataentryprojects #dataentryjobs #ocr #icr #imagetotext #imagetotextconversion #howtoconvert #howtoconvertimagetotext? #marlive #marlivenotepad #notepadplushack #notepad++ #notepadplusplus.exe #NotepadRT++V2 #dtt #xtt #pxnotepad #texttowrt #texttonts #texttoblendnotepad #notepadpx #pxnotepad.exe #notepadplus2022, #blendnotepad2022 #dataentrysoftware #dataentryworkfromhomejobs #dataentrytips #dataentryworkfromhome #freeautotyper #freeconvertorfornotepad
How to convert image to Notepad Plus? How to copy paste in NotepadPlus software? How to Copy paste in Notepad+ Copy paste in Notepad++ Copy paste in Notepad+ Copy paste in NotepadPlus? JPEG to NotepadPlus JPEG to Notepad Plus JPEG TO NOTEPAD+ JPEG TO NOTEPAD++ How to convert image to .xtt? How to convert image to .wrt? How to convert image to .px? How to convert image to .nts? How to copy paste in notepad? How to copy paste in nts notepad How to convert JPEG to .xtt? How to convert any image to text? How to convert any image to html? How to copy paste in Notepadplus? How to copy paste in Nts? How to copy paste in NotepadRt? How to download autotyper?
0 notes
Text
Fast File Encryptor 10.0 Keygen Torrent Download 2019 Free Latest
Fast File Encryptor 10.0 Keygen Torrent Download 2019 Free Latest
Fast File Encryptor 10.0 Working Torrent Fast File Encryptor 10.0 Download 2019 Features nag screen 21 days trial Encrypting a folder is disabled File Shredder is disabled Folder Drive is disabled Minimum screen resolution 1024×768 CPU: Pentium processor and above RAM: 128 MB HDD: 5 MB free disk space Encrypt file Encrypt folder Often used file File shredder Folder drive Fast File Encryptor…
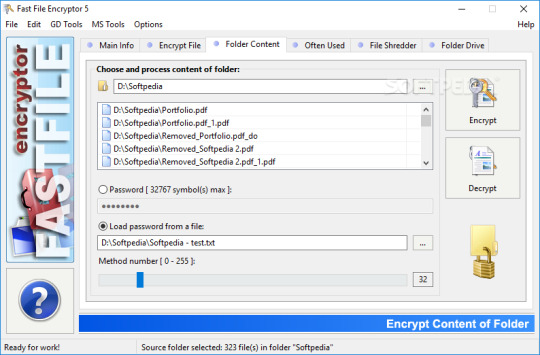
View On WordPress
0 notes
Text
The Top Utility for Mac With a Free Trial
I have been working around Macs for years and many of my friends have too, so I wanted to give your our opinion on the top utility for Mac and guess what, it comes with a free trial.
If your Mac is sluggish, running slow, not up to par, or you are thinking you might need a new computer WAIT! Don't do anything until you read this article. After you read this short article you will be able to turn your turtle of a Mac into a rocket powered, streamlined, supersonic hare.
We Mac users have a completely different attitude when it comes to our computers than our PC using friends. They think that their computer is just a tool and should be tossed when it stops working the way that it did out of the box and they just replace it.

Mac users for the most part love their computer. They think of it as a friend that they cannot do without and are willing to do what it takes to get their Mac back into tip-top shape.
The Top Utility for Mac Revealed!
My recommendation as the top utility for Mac is unequivocally...MacKeeper!
MacKeeper is a utility for Mac that is basically like calling 911. You can manage routine tasks with simplistic ease, keeping your computer clean, reliable, fast and secured.
What makes MacKeeper so special is that it is not a single utility for Mac. It is actually 16 different must have utilities that go hand in hand to keep your Mac rip roaring ready to go.
If purchased each utility for Mac separately you would be forking over hundreds of dollars, but MacKeeper is an all in one solution that you can get very inexpensively. In fact, you can have MacKeeper and all 16 utilities for as little as the cost of a single utility if sold separately.
The Top Utility for Mac Broken Down Into its Components
Security Components
Antivirus
Anti-Theft
Data Control Components
Data Encryptor
Undelete
Backup
Shredder
Zeodisk
Computer Cleaning Components
Fast Cleanup
Disk Usage
Duplicates Finder
Files Finder
Wise Uninstall
Optimization Components
Updates Tracker
Login Items
Default Apps
Geek On Demand
MacKeeper is not only the top utility for Mac; it includes a service called Geek on Demand.
Geek on Demand is an all-inclusive service providing support for anything Mac. You can call them about the top utility for Mac...MacKeeper, or anything Mac related such as installing apps, Mac basics, Mac OS X, peripherals, or even buying tips.
MacKeeper is my hands down choice when it comes to fine tuning my Mac. Imagine a computer that runs just like it did the day that you bought it each and every day. You may be skeptical right now but let me tell you the day that you start using MacKeeper will be the day that you will have truly found the top utility for Mac.
0 notes
Text
0 notes
Text
Image to Notepad Plus WRT conversion
Image to Notepad Plus Conversion Software available .wrt
Image to Pixcel Notepad Convertor available .nts.
Bulk Text Encryptor (100% Non detection Gurantee)
Don't use Any Autotyper on company Notepads because these notepads are highly encrypted and autotyper types fix keystrokes in non encrypted manner hence it is detected in company Quality Check. You have already been warned not to use any autotyper or third party program. Be safe use safe software.
*Warning*:- It has been found that some autotyping softwares (Autotyper) leaves non encrypted character traces, illegal character among character padding and contains non base-64 character strings, when text is transferred to any Company Notepad.
So, in order to be safer side you are strictly recommended not to use any Autotyper as this would may reject work provided by the company.
To overcome this problem, we don't use any autotyper and directly use the encryption technique as per the company notepad.
*Bulk Up Text Encryptor*
*Features*:-
1) Direct conversion into Company Notepad (RTX++/RT++) with same encryption.
2) 100% Safe to use.
3) Fastest conversion speed than any other software or autotyper
4) Can convert 1000 files in 1 minute speed.
5) Software cost is 5000 for any validity you want.
6) Limit- 800 files conversion first time
7) Once file limit/usage limit expires you can buy new limit @ 5 Rs per page
8) Easy to use interface can be used in any windows version in laptop or desktop.
Call us at 7418811442
Email:- [email protected]
#notepadplus #wrt #imagetonotepadplus #notebook.exe #notepadplusplus #notepad++ #jpegtonotepadplus #notepadplusmod #notepadplushack #notepadplusautotyper #notepadplusautotyping #notepadplusorg #notepadplusforwindows #notepadplusforpc #notepadplusdownload #notepadplusdataentry #pdftowrt #jpegtowrt #imagetowrt #picturetowrt #phototowrt #imagetotextconversion #imagetonotepadconversion #howtoconvertimagetowrt #howtoconvertimagetonotepadplus #tricknotepadplus #notepadpluswindows #notepadpluswindows10 #notepadpluswindows10 #convertinagetonotepadplus #notepadplusindia #notepadplus2023 #notepadpluslatestversion
How to convert Image to Notepad Plus?
How to convert Jpeg to Notepad Plus?
How to copy paste text in Notepad Plus?
How to edit text in Notepad Plus?
How to save text in Notepad Plus?
How to install Notepad Plus Software?
How to transfer text in Notepad Plus?
How to get text from Images?
How to convert Image to typing?
How to convert Image to Notepad?
How to convert Images to Notepad?
Notepad Plus Hacks
Notepad Plus Tips
Notepad Plus Tricks
Notepad Plus Download
Notepad Plus Install
Notepad Plus 2023
NotepadPlus.exe
Notebook.exe
How to Convert Image to Wrt?
How to Convert Jpg to Wrt?
How to Convert JPEG to Wrt
Wrt Convertor Software
Notepad Plus Convertor Software
Notepad Plus Conversion Software
Notepad Plus Typer
Notepad Plus Autotyper
Notepad Plus Encryptor
Notepad Plus All Hacks
Notepad Plus Enable Copy Paste Option
Notepad Plus India
Notepad Plus Data Entry
Notepad Plus Typing
Notepad Plus Fast typing
Notepad Plus Fast typer
Notepad Plus Automatic Tying
How to convert Image to Notepad Plus?
How to convert Jpeg to Notepad Plus?
How to copy paste text in Notepad Plus?
How to edit text in Notepad Plus?
How to save text in Notepad Plus?
How to install Notepad Plus Software?
How to transfer text in Notepad Plus?
How to get text from Images?
How to convert Image to typing?
How to convert Image to Notepad?
How to convert Images to Notepad?
Notepad Plus Hacks
Notepad Plus Tips
Notepad Plus Tricks
Notepad Plus Download
Notepad Plus Install
Notepad Plus 2023
NotepadPlus.exe
Notebook.exe
How to Convert Image to Wrt?
How to Convert Jpg to Wrt?
How to Convert JPEG to Wrt
Wrt Convertor Software
Notepad Plus Convertor Software
Notepad Plus Conversion Software
Notepad Plus Typer
Notepad Plus Autotyper
Notepad Plus Encryptor
Notepad Plus All Hacks
Notepad Plus Enable Copy Paste Option
Notepad Plus India
Notepad Plus Data Entry
Notepad Plus Typing
Notepad Plus Fast typing
Notepad Plus Fast typer
Notepad Plus Automatic Tying
Notepad Plus Tutorial
Notepad Plus Plus
Notepad ++ Tutorial
How to install Notepad Plus Software?
Notepad Plus Introduction
How to Install Notepad Plus on Windows 11?
How to Install Notepad Plus on Windows 10?
Notepad Plus Basics
Notepad Plus Coding
Notepad Plus Latest Version
Pdf to Notepad Plus
Installing and Uninstalling Notepad Plus
Notepad Plus App
Notepad Plus Application
How to Install Notepad Plus on Windows 7?
How to Install Notepad Plus on Windows 8?
How to use Notepad Plus?
How to check errors in Notepad Plus?
How to find errors in Notepad Plus?
Notepad Plus Error checking?
Notepad Plus Qc Software
How to Save text in Notepad Plus?
[22/06, 08:50] INTELLITECH DATA SERVICES: Notepad Plus Free Software
Notepad Plus free trick
Notepad Plus free Autotyper
Notepad Plus free Autotyping Software
Notepad Plus free Download
Notepad Plus free hack
Notepad Plus Mod
Notepad Plus Latest Mod
#Convertimagetonotepadplus#jpegtonotepadplus#jpeg to notepad plus#imagetowrt#.wrt.nts.rtx#gettextfromimages#extracttextfromimages#how to convert image to text?#howtoconvertimagetotext#pixcelnotepad#Pixcelnotepadconversion#rtx++#Rtx++notepad#imageto.rtx#inagetortx#autotyperforpixcelnotepad#autotyperfornotepadplus#autotyperforrtxnotepad#wrtconversion#howtogettextfromimage#how to get text from image?#how to download autotyper?#convertimagetotext#jpegtotextconversion#convertimagetoeditabletext#imagesetextkaiseconvertkare#software#technology
1 note
·
View note
Text
Anti-Ransomware Strategy To Protect Your Business
Secure Networks ITC strives to create a perfect IT environment for all clients. The most common hurdle that most companies fail to overcome is the security aspect of their IT. Often falling short of any standards due to the cost or belief that just being careful is the best security measure.
It is far from it, really. Yes, you can go years before experiencing any serious malware attack, but once you do, the consequences can be catastrophic.
That is where we step in! We will do everything to create that perfect, carefree work environment, so you wouldn’t have to think about any malware attacks or loss of data.
Here’s a situation for you: you just got into your office, you prepared a nice cup of coffee and you are ready to start your day. It’s Monday and you feel full of energy and ready to get down to business. You open a few emails before you open the wrong one. The beginning of a nice week turns into a never-ending nightmare.
So, before you open your next email, answer this question: Do you have a backup? If not, put the mouse down and give us a call. If you do, give us a call, as we can discuss multi-layer protection plans and prevention.
What we’ll do:
• Deliver another layer of security by installing one of many endpoints or professional versions of Anti-Virus that will include Anti-Ransomware protection
• Take care of regular backups of your business data, so the damage is minimal in case your system gets infected with ransomware
• Frequently update your systems and software to eliminate vulnerabilities of previous versions
• Perform baseline checks of the server core to ensure optimal performance
Implement an advanced notification system to monitor and alert when the system is not performing optimally or if there is an issue with the backups.
What is Ransomware?
It’s 2018, so most of us know what Ransomware is — a sophisticated malware that takes over your computer, denies you access to your data, tells you to kiss it good-bye unless a ransom is paid. Depending on the size of the business or institution, the ransom can range from a few hundred bucks to tens of thousands.
The payment is to be executed in Bitcoins and the victims are sent detailed instructions on how to execute it. Initially, the FBI advised the victims to pay the ransom, as there wasn’t much that they could do in these kinds of situations, but recently the “no-negotiating-with-terrorists” policy has been strongly advised. Since there is no way of knowing whether the data will be securely returned or not, and there is no way to trace bitcoins, the FBI feels that paying up ransoms would only encourage these criminals to continue blackmailing companies and organizations. The ransom payments would only be used to further fund their illegal activities, so soon data hostage situations would be the day-to-day reality for all.
In case you find yourself in a situation that you are willing to pay any price just to get your business data back from the kidnappers, we’re sorry to tell you, but it will be on you. Why? Because there ARE strategies to protect your business and its data, and if you don’t think prevention and protection are important, well then, shame on you.
How Does Ransomware Work
There are numerous ways for the ransomware to gain access to your computer, and phishing spam is one of the most common ways. Phishing spam is all those email attachments that make you believe opening them would be perfectly safe because they appear to come from a trusted institution, a friend or a colleague (PDFs, Word Documents). In reality, downloading and opening them initiates a hostile takeover of your computer data. Some have built-in social engineering tools that trick users into giving them admin access, while some, more aggressive forms can exploit security holes and gain unauthorized access without having to trick the user into it.
Another popular method for infecting computers is called malvertising and the main trick here is that it requires little to no user interaction. The users would be browsing the web, legitimate sites even, when they are redirected to a criminal server, often without even clicking on the malicious ad. Criminal servers collect information about the user location and computer-based on which the most suitable malware is selected (most often ransomware).
There are three main types of ransomware:
• Encrypting ransomware — These are the nastiest of all because they encrypt (block) system files and demand payment in exchange for a decryption key. Once the files get encrypted, no security software can restore the data. The only option to get it back would be to pay the ransom, but there is no guarantee that you’ll get the data back even if you pay. It is hard to detect, it usually slows down the computer and shows the ransom message after absolutely everything is encrypted;
Locker ransomware — These block your access to a desktop, all files, and apps. Upon starting your computer, a window containing a message about the blockage would appear, often with the FBI or US Department of Justice seal. Screen lockers are not as bad as the encrypting ones, as they only block access while the data is not encrypted.
Scareware — These were supposed to be scary but are nothing when compared to the previous two types. These usually include tech support or security software scams, as the user would get a pop-up saying that malicious activity has been detected and that you would need to pay to remove it. If you ignore the message, you’ll get bombarded with more pop-ups, but nothing will happen. Just remember: if you are already paying an antivirus software, then why would the company ask you for money for each individual malicious activity that gets detected?
After the infection spreads, the victim is shown a message or an image saying that the files are now inaccessible and that the only way to regain access is to pay the ransom. However, this is not the only scenario and certainly not the one that causes the most panic. Some attackers can falsely claim to be a law enforcement agency that is shutting down the user’s computer because pirated software or pornography was found on it. Users panic especially in the case of latter and are prepared to pay any fine just to keep things quiet. The second scenario that causes panic involves leakware or doxware malware. The attackers inform the user that sensitive material has been found, so they threaten to publish it unless the ransom is paid.
In these kinds of situations, before you begin to sweat, remember this: there is no need to panic. In case the law enforcement agency found illegal material on your computer, you would probably hear a knock on the door instead of seeing the ransom message on your screen. As for the message about the sensitive data, know that finding and extracting such information is extremely tricky, so they probably don’t have anything on you.
Ransomware Attack — Who’s the Target?
The short answer: everyone. Although newspapers only report about the major attacks (such as the recent lockdown of the city of Atlanta), every small or midsize business, enterprise or organization is a potential victim. You may hear so much about so many attacks, but the real issues are attacks that you don’t get to read about. Attacks happening to businesses like yours.
Some organizations are more vulnerable and are, therefore, more likely to get attacked. For example, academic organizations, such as universities and colleges, not only have smaller security teams and budget constraints, but their user base does a lot of file sharing, which enables easier breach.
Other organizations, such as government agencies and medical facilities, are likely targets because their services are time-sensitive and crucial. There is a great sense of urgency when it comes to recovering the data, so these institutions are more likely to pay. HR departments of enterprises are also likely targets, as attackers can get ransomware in through job application emails.
Organizations with sensitive data, such as the law firms, are more likely to execute the payment because leaking sensitive information can compromise their business. Some attackers block access and then put the data up for an online auction where the highest bidder would get the data.
How to Remove Ransomware
You need to know that not all ransomware families have corresponding decryptors and that running a wrong decryption script can only further encrypt your files. That’s why you probably shouldn’t try downloading and running anything yourself unless you have a lot more skills and knowledge than an average computer user. On the other hand, in case you are dealing with a screen locker, a full system restore would probably be the best practice, but only if possible, of course.
It is crucial to pay close attention to the ransom message to determinate which ransomware type is the one you’re dealing with (sometimes it can only be scareware imposing as encryptor). Next, the system reboot to safe mode to stop the encryption and installing antimalware software is required, as well as scanning the system and restoring it to a previous state.
As we probably lost you at ‘reboot system to safe mode’, the absolute first thing you or your employees should do is seek advice from an IT specialist before anyone makes attempt to do anything themselves. Meaning — shut down computer forcefully immediately and get an IT on the phone. The user would explain the experience and a field tech would be sent to your office to start restoring your computer to the previous state.
An important fact you should know: The encryption infection doesn’t spread instantly upon entry. Depending on the computer it can sometimes take hours if a computer is fast, and sometimes it can take days for the malware to encrypt all the files. It is important for the user to immediately report unusual slowdowns and inability to access data because there is a good chance that there is active encryption going on.
As we mentioned, encrypted files can’t get encrypted without the encryption key, so once they’re captured, they’re gone. Therefore, prevention should be your top priority.
How to Prevent Ransomware
Ransomware is extremely sophisticated, there’s no doubt about it, but keep in mind that most likely targets are organizations with budgets constraints and poor tech infrastructure. As a small to the medium-sized business owner, you don’t encounter the same constraints the large government institutions do.
Since you are on top of the decision-making chain, you would need to create a solid IT infrastructure for your business which involves setting an IT budget and creating a 5-year plan.
Most of the companies rely on very precise budget planning in all parts of their business, including IT. Proper budgeting is only possible if careful planning precedes it. With IT, it is very different. The technology evolves at a staggering pace alongside malware and other malicious software that you would have to take this into consideration when creating a plan. Here is where the 5-year plan takes place. 5 years in IT are considered a lifetime of most equipment, so foreseeing what should be done within this period and prepare for the next is very important.
When talking about overall security, we would need to plan for physical protection like firewalls and replace them as soon as they reach the end of their lifecycle. Any firewall license that needs to be employed should be renewed after the licensing period expires. Proper upgrades are also something you should plan.
Another part of the security would be Anti-Virus and Anti-Spyware software. Both should be always in-check and never left outdated. Testing should be done periodically to ensure that the current setup is something that is suitable for your environment. A lot of Anti-Virus vendors offer different types of protection and many times can offer great protection at first, but then after a while fall short in some or all categories. Same goes with Anti-Spam, as it can be really good for a certain period and then start to release more and more spam emails into your system.
Planning changes, upgrades, updates and testing during a 5-year period will certainly help you not worry about the abrupt loss of data or service.
There are numerous prevention and protection steps that you should make in order to keep the ransomware damage to a minimum. These steps are a part of good security practices provided by the managed IT service provider, so perhaps you are starting to be aware of why every business needs one and why an IT budget is crucial.
A solid anti-ransomware plan includes the following practices:
• Create secure data backups — Backing up your files regularly and having an offline backup is what is going to save you in case the ransomware attack occurs. In case your business data has been frequently backed up, then there is no hostage and there is no need to pay the ransom (learn more about Secure Networks ITC triple-layer backup protection plan);
• Invest in great cybersecurity — Just any antivirus simply won’t cut it, especially if we’re talking about free options. Businesses need professional versions of antivirus software and centralized management (learn more about the best antivirus software for business;
• Keep your systems & software up-to-date — Frequent updates of your operating system are important because newest versions have fewer vulnerabilities. Same goes for endpoint protection suits. Updates can be done manually or automatically through the server;
• Use layered security — This includes regular security software patches, system hardening, and vulnerability management. As the name implies, it will consist of multiple layers of protection. Physical layer is the first layer — firewall; the second layer is the software-based layer — Anti-Virus & Anti-Spam; the third layer is a policy based security layer — creating different policies and limiting the computer usage to the essential, for example, work file access only, we can stop the viruses from spreading or infecting the workstation from the start; the fourth layer would the backups — if all other layers fall short in protecting your data, backups will ensure that you will be back in no time.
• Use a whitelisting program — These programs will prevent your employees from installing unauthorized programs. Although the employees usually complain about this restriction, whitelisting is probably the best defense against ransomware besides a good backup;
• Determine an IT budget — In case you don’t have anti-house IT department, make sure you get a managed IT, service provider. Not only will the IT guys take care of all the points stated above, but they will also make sure all your business workstations and every-day business activities are running smoothly;
• Educate yourself and your employees — It is important to know how a possible threat looks like and to educate your employees. For example, employees, especially those with admin access, should be educated on how to detect malspam, suspicious websites and other scams that they should not open and to report suspicious activities or computer performance (especially computer slowness) to the IT department.
• Don’t get tricked — Don’t install anything that is sent to you in an email or offered by visiting a website. All software should be installed directly from the legitimate vendor’s website. The safest thing would like to contact the IT department every time you need new software installed. They won’t get tricked and installing all kinds of unnecessary apps (we’re not just talking about the malicious ones here) would be avoided.
0 notes
Text
Fast File Encryptor 8.7 Free
Fast File Encryptor 8.7 Free
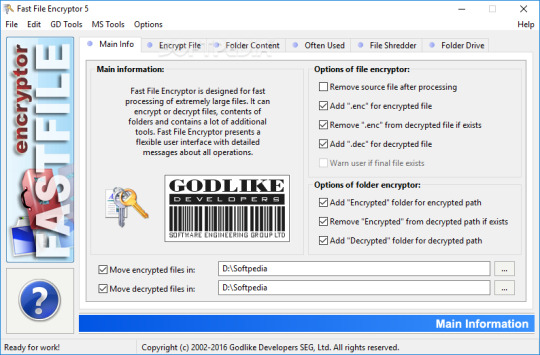
Fast File Encryptor 8.7 Crack Torrent Download Cracked Working
The process is very streamlined and user friendly, clearly intended to be accessible to those unfamiliar with how encryption works. The downside of this simplicity is a lack of settings, the application has made encrypting so quick that the level of encryption cannot be adjusted or changed in any way. If files are encrypted in bulk,…
View On WordPress
0 notes
Text
Fast File Encryptor 7.3 Multilingual
Fast File Encryptor 7.3 Multilingual
“Fast File Encryptor” is designed for fast processing of extremely large files. It can encrypt or decrypt files, contents of folders and contains a lot of additional tools. Fast File Encryptor presents a flexible user interface with detailed messages about all operations. Fast File Encryptor features the following tools: Encrypt File, Encrypt Folder, Often Used Files, File Shredder, Folder Drive.
View On WordPress
0 notes
Text
Fast File Encryptor v6.3 Pro - Fast file encryption software and system folders
Fast File Encryptor v6.3 Pro – Fast file encryption software and system folders
You can encrypt your system to protect yourself and prevent theft of your personal information so others can not easily access it. Fast File Encryptor is a software to encrypt and decrypt files and folders of the system. The interface of this software includes separate encrypt files, encrypt folders, often used files, file shredders, Folder Drive for processing and encoding files, folder…
View On WordPress
0 notes
Text
Fast File Encryptor - Discount 20%
Fast File Encryptor – Discount 20%
To get 20% discount when order Fast File Encryptor, make sure to get this coupon code for Fast File Encryptor here to order and save big instantly at checkout.
View On WordPress
0 notes
Video
youtube
.wrt .nts .xtt .px .rtx conversion using BULK TEXT ENCRYPTOR for Data En...
#notepadplus #notepad+ #wrt #px Hello Friends! This is Intellitech Data Services. We are here to help you with the data entry solutions. This is Notepad Plus Software in which you can only type and save the file as .wrt format. It takes around 1 hrs to type a single page. Its really hard work. So, we have developed our safest and fastest Bulk Text Encryptor software which can not only complete the 200 pages project in just 1 minute but also ensures that your data is 100% encrypted. Also, remember, Data Entry Companies have banned autotyper so never use any autotyper software nor buy since they are free available on internet but if you use them you can lose your project. They are 100% detectable in QC. Sp, to be safer side and confident always use our Bulk Text Encryptor software. Contact us at 7428811442 for enquiry. Never use any autotyper on company notepads like Notepad plus, blend notepad, pixcel app, rtx notepad, notepad rt++ or nts notepad as autotyper is banned by data entry companies and 100% detectable which may reject your project. That's y we have developed encryptor software which is guranteed 100% safe from detection, fast conversion 200 pages in just a min. Bulk text encryptor is only one software of it's kind which can gurantee you payment. Autotyper is third party tool which transfer text in non encrypted method and type in fix keystrokes that's y it can be detected easily. Contact us at 7428811442 ( WhatsApp also) to purchase or enquiry Email us at [email protected] Subscribe us for more updates. 𝐏𝐡𝐨𝐧𝐞 𝐧𝐮𝐦𝐛𝐞𝐫𝐬:- 𝟕𝟒𝟐𝟖𝟖𝟏𝟏𝟒𝟒𝟐 (𝐰𝐡𝐚𝐭𝐬𝐚𝐩𝐩) / 𝟗𝟑𝟏𝟐𝟗𝟓𝟑𝟔𝟎𝟔 𝐄𝐦𝐚𝐢𝐥 𝐢𝐝: 𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐭𝐞𝐜𝐡𝐝𝐚𝐭𝐚𝐬𝐞𝐫𝐯𝐢𝐜𝐞𝐬@𝐠𝐦𝐚𝐢𝐥.𝐜𝐨𝐦 𝐖𝐞𝐛𝐬𝐢𝐭𝐞:- 𝐡𝐭𝐭𝐩𝐬://𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐭𝐞𝐜𝐡𝐝𝐚𝐭𝐚𝐬𝐞𝐫.𝐰𝐢𝐱𝐬𝐢𝐭𝐞.𝐜𝐨𝐦/𝐢𝐦𝐚𝐠𝐞-𝐭𝐨-𝐭𝐞𝐱𝐭 Notepad plus free,Notepad plus activator,Notepad plus full crack 2022,Notepad plus new,Notepad plus windows 10,Notepad plus free download,Notepad plus crack full,tutorial Notepad plus,Notepad plus settings,how to crack Notepad plus,screen recorder for pc,Notepad plus 5.1.1 crack,Notepad plus full,Notepad plus crack 2021,Notepad plus crack 2022,crack for Notepad plus 2022,download Notepad plus pc,Notepad plus crack exe,Notepad plus full version free,Notepad plus download,Notepad plus crack,Notepad plus crack file,Notepad plus full crack,crack Notepad plus,Notepad plus crack version,Notepad plus 2022,screen recorder,Notepad plus crack file download,Notepad plus crack free 2022,Notepad plus,Notepad plus 2021,Notepad plus 5.3.2 crack,how to download Notepad plus crack,Notepad plus 2022 key,Notepad plus full 2022,Notepad plus crack download windows 10,Notepad plus crack 64 bit,Notepad plus crack github,Notepad plus full version,Notepad plus keymaker,Notepad plus download free,how to crack Notepad plus 2022 funn,Notepad plus crack 4.5 8 download,Notepad plus crack download windows 7,Notepad plus cracked,Notepad plus tutorial 2022,Notepad plus watermark remover,how to use Notepad plus screen recorder,Notepad plus cracked 2022,Notepad plus crack free,Notepad plus keygen,best screen recorder,how to use Notepad plus,Notepad plus crack free download,Notepad plus tutorial,Notepad plus new video,Notepad plus full version free download,Notepad plus crack 2021 free download,download crack Notepad plus 2022,#2022,Notepad plus crack 2022 free download,Notepad plus screen recorder download for pc,Notepad plus crack free download for pc,Notepad plus download crack,download Notepad plus,Notepad plus crack full version,crack Notepad plus 2022,how to crack Notepad plus 2022,Notepad plus screen recorder,full crack Notepad plus,Notepad plus free 2022,Notepad plus pre-cracked 2022,Notepad plus full crack version,#register_Notepad plus_for_lifetime,Notepad plus crack download,how to download Notepad plus crack version,Notepad plus crack full 2022,#Notepad pluscracked
0 notes