#Free RDP for Online Learning
Explore tagged Tumblr posts
Text
Best Free RDP for Students – 30 Days Free Trial Hello friends! As we all know, we are living in a digitalized world that has changed the way we work, study, and manage things. So go and read the Article Now.
#freerdpserver#Free RDP Server for Students#Free RDP for Online Learning#Free RDP for University Students#Free RDP for Windows#Free Remote Desktop for Students
1 note
·
View note
Text
Allow Multiple RDP Sessions on Windows Server: A Step-by-Step Guide
How to Enable Multiple Sessions [Windows Server and RDP] In this guide, you’ll learn how to enable multiple RDP sessions and resolve common issues that may arise. To connect to a machine using any remote desktop client, enable Remote Desktop and ensure users have authorization for RDP access. Keep in mind that desktop versions of Windows limit concurrent RDP sessions to one active user. run mulitple rdps This guide will also help you fix the “The Number of Connections to This Computer is Limited” error How to Enable Multiple Sessions [Windows Server and RDP].
By default, Windows Server disables multiple RDP sessions, meaning another administrator connecting will disconnect your session. Follow this tutorial to configure your server, allowing you to run multiple RDPs efficiently, whether on a single server or multiple servers.
Enable Multiple RDP Sessions Discover how to activate two RDP sessions and allow more than two. First, enable Remote Desktop on your PC.
rdp1 To enable multiple RDP connections, disable the restriction limiting the server to a single session per user, then adjust the maximum allowed connections.
Step 1. Activate Multiple RDP Connections Follow these steps to allow multiple RDP sessions on Windows Server:
Log in to your RDP server.
Press Windows Key + R to open the Run dialog.
Type gpedit.msc and press OK to open Local Group Policy Editor.
Navigate to: Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Connections
rdp2 Restrict Remote Desktop Services users to a single session: Set to Disabled and press OK. how to use multiple rdps at once using rdpwrap Limit number of connections: Set to Enabled, then increase the RD Maximum Connection allowed to 2.
rdp3 Note: If you set it more than 2, it won’t make any difference because you can make two concurrent sessions in this case! It’s done; now you should be able to have multiple RDP connections at the same time.
Step 2. Create New Remote Desktop Users To manage RDP sessions effectively, it’s best to create separate users. However, you can connect multiple times to RDP using the same user account!
Steps to Create Users:
Open Computer Management by typing compmgmt.msc in the Run dialog and pressing Enter.
Navigate to Computer Management (Local) -> Local Users and Groups -> Users. Right-click on Users and select New User. rdp4 Note: Add the newly created users to the Remote Desktop Users Group.
rdp5 Fill out the required fields and create as many users as needed (for now, just 2 users). Test your setup by connecting to RDP with two devices using different user accounts. woshub mulitple rdp Then, open Task Manager to view online users and their sessions.
rdp6 Using the above steps, you can Enable Multiple RDP Sessions successfully. Stay with us! There are so many to learn.
Allow More Than 2 Remote Sessions To enable more than two remote users, install Remote Desktop Services (RDS) enhanced multi user support for terminal servers windows 11. While an RDS license is required, installing RDS provides a 120-day free trial for this feature. Here, we’ll install RDS without using an ADDC (Active Directory Domain Controller).
Step 1. Install RDS
Open Server Manager.
In the Dashboard, select Add roles and features.
Choose Role-based or feature-based installation in the Installation Type step and click Next.
Select a server from the server pool in the Server Selection step and proceed.
Tick the Remote Desktop Service checkbox in the Server Roles step and click Next. rdp7 Proceed to the Features step with default options.
Tick Remote Desktop Connection Broker and Remote Desktop Session Host checkboxes, then click Next. Note 1: Accept any pre-required role services or features if prompted.
Note 2: To use RDS beyond the 120-day trial period, install the Remote Desktop Licensing role as well.
rdp8 In the final step, tick Restart the destination server automatically if required and click Install.
Note: Installation may take some time and might require several server reboots.
rdp9 Once done, increase the RD Maximum Connection allowed in the Limit number of connections file (e.g., 99) and set both files’ statuses as described earlier Buy RDP all locations.
How to Fix “The Number of Connections to
This Computer is Limited” When using Remote Desktop Protocol (RDP) to connect between Windows Server instances, users might encounter the “The Number of Connections to This Computer is Limited” error. This occurs when the session limit is reached, preventing further connections.
In this guide, you’ll learn how to fix this error using multiple solutions. When the maximum configured connections are reached, subsequent users will encounter this issue.
rdp 10 Server operating systems, like Windows Server or Linux, provide the platform for running applications. They ensure network connectivity and access to hardware resources. While RDP servers are a smart solution for remote work, they can face issues. Bugs causing server problems often occur in layers such as the Network, Hardware, or OS, but most are found in the application layer. Today, we’ll tackle one such issue and learn how to resolve it.
After purchasing a Windows RDP, configure it to support multiple concurrent RDP sessions, enabling separate sessions for different users. You can adjust the number of allowed simultaneous connections on your server.
If the “The number of connections to this computer is limited” error persists despite not exceeding the maximum allowed connections, this guide provides two solutions to resolve it.
Solutions to Fix “The Number of Connections to This Computer is Limited” Error If you frequently face the “The Number of Connections to this Computer is Limited” error, this guide provides steps to resolve it. After ensuring your RDP server is properly configured, test the following solutions. If your system is part of a domain, ask the domain controller to support this setup. Additionally, choosing a reliable RDP provider can prevent such errors.
For non-domain systems, disconnect the network cable, turn off WiFi, and restart the computer. After rebooting, reconnect the cable and activate WiFi. Linux RDP This often resolves the issue.
If the error persists, this tutorial offers two methods to fix it, letting you choose the best solution based on your system and expertise.
Solution 1: Check for the Number of Connected Users The error may occur because active RDP sessions remain disconnected. Some users close the RDP application without signing out, keeping their sessions open. To check:
Press Ctrl + Shift + Esc to open Task Manager. Go to the Users tab to view active users. rdp11 Right-click any column, select Session, and check the session types (RDP, console, terminal, etc.).
rdp12 Identify users connected via RDP and ensure their statuses are Disconnected. With this step, you’ve successfully applied the first technique to fix the error
rdp13 You have successfully finished the first technique to Fix the Number of Connections to this Computer is Limited Error.
Solution 2. Using GPO to Enable Multiple Remote Desktop Connections A Group Policy Object (GPO) is a collection of policy settings that could potentially cause issues. If the “The number of connections to this computer is limited” error persists, the second solution involves updating the Group Policy to allow multiple connections.
The RDP “The number of connections to this computer is limited” issue might have been resolved if you managed to update the Group Policy to permit multiple connections.
rdp14 Follow these steps:
Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections. rdp001 In the right pane, locate Limit Number of Connections and double-click it.
rdp16 Set it to Enabled, then enter your desired connection limit.
rdp17 Next, find and double-click Restrict Remote Desktop Services users to a single Remote Desktop Services session in the same pane.
rdp18 Set this option to Disabled to remove user restrictions.
rdp19 Finally, restart your computer for the changes to take effect. This will resolve the error by allowing multiple concurrent RDP connections.
Conclusion In this article, you learned how to enable multiple RDP sessions. To allow multiple RDP connections, you need to disable the single-user remote desktop mode and adjust the remote connection limit. This enables two RDP sessions simultaneously for free. However, if you need more, you must install the RDS role on the server. The RDS feature is free for 120 days, after which you must purchase an RDS license to continue using it.
This guide also covered how to fix “The Number of Connections to This Computer is Limited” error. Two solutions were explained to help you resolve the issue. If you have other methods or solutions, feel free to share them with us. By following the two solutions provided, you can easily fix the error. However, if any issues arise, don’t hesitate to contact us. Our technical support team will assist you in resolving any problems efficiently.
#how to use multiple rdps at once using rdpwrap#"woshub mulitple rdp#enhanced multi user support for terminal servers windows 11#Buy RDP all locations
0 notes
Text
Ww2 online vehicles

#Ww2 online vehicles license#
If you find something wrong or that needs to be added, please let us know Sniper62. If you decide to help, by making changes, please use the below MediaWiki User Guides and track updates in the WWII Online forum PM or email me if you are interested in making edits. Looks like fairly new but well maintained vehicle, (matching tires). This Wiki is being maintained by the WWII Online community, it requires a user account before being able to make any changes.
WWII Online Support - If everything else fails. Many vehicles from WW2 had a futuristic look to them.
#Ww2 online vehicles license#
For any electric vehicle that would like a World War II Veteran license plate on their vehicle there will. These are external sites and services provided by CRS. Benefit Access Program Pick-a-Plate Online. WWIIOnline Airplane Performance Charts by Jokeri, Tigger, and Mursutin.Battleground Europe Game Monitor by Xiper This is the list of all infantry types, weapons, and vehicles existing in the game as playable units.Avro Lancaster MK3 WW2 Bomber Game Ready Model 59K poly 3ds Max + 3ds fbx obj: 199. WW2 US Soldier 3ds Max + fbx obj oth: 59. Accordingly, accuracy and functionality is solely on the site/code owners. Low-poly Dieselpunk cartoon armored car Blender + obj gltf fbx: Free. Or ever dreamed of taking the controls and learning to drive the WWII M4. These sites and services are developed, maintained, and provided by community members. one of the worlds largest collection of tanks and military vehicles. Confused by a term? Check the glossary!īelow are player written guides designed as an 'intro' to the game.After selecting a mission, the Ready Room will list the available vehicles. These were produced by the game development team. In order to command a tank or vehicle you’ll need to select an Army Persona. 1.36.15.0 Numerous bug fixes and RDP updates!īelow are several different guides designed as an 'intro' to the game.1.36.18.0 Motorized Mortars and 25 new Towns!.World War II Online recreates the brutal war in Western Europe in a zone-less 300,000 SQ KM game world! True combined arms action, with over 100 historically accurate weapons and vehicles, 10 personas, and much more!

0 notes
Text
Rdp Ms

Rdp Mac To Windows
Rdp Ms
Rdp Marathon Press
Rdp Madeira
The new microsoft edge browser reviews. Whether you use Microsoft Remote Desktop Services, Windows Virtual Desktop, Citrix XenApp, Citrix XenDesktop, or VMWare Horizon View to satisfy your organization’s Server Based Computing needs, we offer remote desktop management software for organizations of all types and budgets.
What is RdpGuard and How does it Work? RdpGuard is a host-based intrusion prevention system (HIPS) that protects your Windows Server from brute-force attacks on various protocols and services (RDP, FTP, IMAP, POP3, SMTP, MySQL, MS-SQL, IIS Web Login, ASP.NET Web Forms, MS Exchange, RD Web Access, VoIP/SIP, etc). Jan 11, 2018 Long story short - users are going to start using RDP on the conference room PC as opposed to signing into their own Windows account. A dedicated account will always be logged in with only the RDC icon on the desktop; basically everything else will be locked down through group policy. We would like to show you a description here but the site won’t allow us.
In addition, our solutions excel at monitoring RDP performance, connection quality and latency, security, and user session activity – we cover the gap in RDP monitoring and analytics for organizations that have deployed a pure Microsoft Remote Desktop Services environment with no Citrix or VMWare overlays.
> Not sure where to start? Answer a few brief online questions about your remote desktop protocol needs and get going now.
Deployment of our tools is a snap, regardless of your environment. Our solutions work well with on-premises networks or in datacenters serving up dedicated and shared desktops for Managed Service Providers. You can store collected terminal server data in SQL Server Express, on-premises SQL Server, or perhaps most conveniently, in Microsoft Azure SQL.
Finally, you will not find a more affordable set of solutions for Remote Desktop Services monitoring and management in the market. A subscription to our flagship RDS monitoring and reporting tool, the Remote Desktop Commander Suite, can be started for only $9.99 per server per month, with volume discounts available. Other software companies will charge you thousands of dollars to perform assessments of RDP and terminal server performance in your network – we do not.
Read on to learn more about the different editions of our products.
Remote Desktop Commander Suite
The Remote Desktop Commander Suite provides active, real-time and historical capabilities for user session management.
Historically, small and medium sized businesses have had few affordable options if they wish to monitor performance and user activity on their remote desktop servers. Vendors like Citrix and VMWare offer comprehensive remote desktop management software and terminal server monitoring solutions only at their top licensing tiers, placing them out of reach except for the largest organizations. Other third-party vendor solutions are often priced by concurrent user, making them expensive to implement and maintain.
The Remote Desktop Commander Suite is a powerful package for SBC environments. At its heart are two key components:
Rdp Mac To Windows
Remote Desktop Reporter
Remote Desktop Reporter, part of the Remote Desktop Commander Suite, is a comprehensive reporting and monitoring solution that collects and consolidates key metrics from all of the remote desktop servers in your environment, providing you with easy to run and schedule reports showing user activity, time tracking, licensing trends, application usage, and performance.
SPL Tracker (Service Provider Licensing Tracker)
SPL Tracker – part of the Remote Desktop Commander Suite – saves time, money, and headaches for organizations who need to keep an eye on service provider licensing programs.
Here’s how:
Microsoft SPLA Licensing, Citrix Service Provider Licensing, and the VMWare Service Provider Program offer big savings to Managed Service Providers, but at a price. Monthly reporting requirements are onerous, and MSPs that attempt to tackle this chore by hand find that it is time-consuming and error prone.
Wouldn’t you rather leverage a tool that can automate this task for you? And, while doing so, track and eliminate license wastage so you can reduce your monthly costs? If so, Service Provider Licensing Tracker is designed especially for you. Reach out and request a quote to learn more about how it can actually pay for itself in very little time.
Rdp Ms
Remote Desktop Commander Lite
If the Remote Desktop Commander Suite sounds too robust for your needs or you are still a fan of RDPSoft’s legacy Remote Desktop Admin Toolkit, then Remote Desktop Commander Lite is perfect for your needs.
Remote Desktop Commander Lite assists you with tasks that are active and real-time in nature, such as observing memory use by application or user, logging off and disconnecting users, terminating hung processes, and running parameterized PowerShell queries against session hosts, users, or processes.
Ipod touchcopy mac download. Best of all, Remote Desktop Commander Lite is now completely free – it’s our gift to entire RDS/Citrix community, and we hope it makes their lives easier.
Remote Desktop Commander Premium Management Features
If you don’t need all of the features of the Remote Desktop Commander Suite, but if you need improved shadowing and remote assistance capabilities to support your users, sophisticated real time monitoring of live sessions, and/or a way to delegate management tasks to your support staff without making them server admins, then extend the capabilities of Remote Desktop Commander Lite with our Premium Management Features package.
The Remote Desktop Commander Premium Management Features license only costs $99.99 per admin or help desk user per year, but gives you the power you need to adequately support a Microsoft Remote Desktop Services or Windows Virtual Desktop environment of any size. Microsoft Remote Desktop Services does not have a native mechanism to delegate remote desktop management tasks to support staff, which to date has required giving support staff admin rights. Also, native shadowing support for Windows Server 2012 R2, Server 2016, and Server 2019 has been complicated at best, plagued with issues related to shadowing multiple monitor sessions.
Our Premium Management Features package fixes both of those issues, by providing a complete RDS Management Delegation Wizard to define and extend granular rights to help desk staff across session hosts and connection brokers. It also comes with our new SuperShadow tool, which allows admins, support staff, and managers to monitor and assist multiple sessions at once, with file transfer capabilities through the clipboard, complete multi-monitor support, and so much more.
Remote Desktop Canary
Need to keep a constant watch on your Remote Desktop Services deployment, with the ability to receive instant alerts if new RDP connections cannot be established or if new connections are experiencing slow RDP login times? Want to review screenshots of login sequences to see how long it takes for RemoteApps and login scripts to launch? Want to send login statistics to your existing NMS solutions’ dashboards?
If so, Remote Desktop Canary is the RDS synthetic monitoring solution for you. Program it to perform recurring RDP login monitoring tests into your environment, notifying you and recording screenshots and other statistics for troubleshooting. Pricing starts at only $499.99 a year to monitor a single RDS farm/collection, with volume discounts available.
Other Services
Rdp Marathon Press
In addition to producing Remote Desktop Commander Suite and Remote Desktop Commander Lite, we also provide additional services for our clients.
You can request an RDS Performance Audit of your RDS infrastructure to review and identify any performance bottlenecks in the areas of CPU/memory consumption, network connection quality, and much more.

Rdp Madeira
You can also contract with us to produce custom reports against Remote Desktop Commander’s database.

0 notes
Text
Oovoo Download Mac Os X

Ll brown font free download mac. ooVoo has many great features S from video calls with up to six people at once to video messaging to chat and file transfer capabilities. See below for some of our highlighted features and be sure to check back on this page often to see what's new.
File Name:oovoosetup.exe
Author:ooVoo LLC
License:Freeware (Free)
File Size:14.8 Mb
Runs on:Win Vista, 2000, 2003, XP
The next evolution in online communication a remarkably easy way to have a face-to-face video chat with friends, family or colleagues, no matter where they are in the world. ooVoo Video Chat is remarkably easy to use: easy to download, easy. ..
File Name:oovooinstaller.zip
Author:ooVoo
License:Freeware (Free)
File Size:10.4 Mb
Runs on:Mac OS X 10.4 or later
The video call room API will enable developers to easily embed the ooVoo video rooms inside their own web sites.http://www.oovoo.
File Name:ooVoo Web Video Chat RoomAPI
Author:Adam Stewart
License:Freeware (Free)
File Size:
Runs on:Windows
First video chat app designed for the iPad®! HD Video Chat on the go! Hang out with your friends wherever you are. Android to iPhone, PC, or Mac, over WiFi, 3G, and 4G. Be the first to know! Sign up below for news and updates or to know. ..
File Name:ooVoo for for Mobile
Author:ooVoo
License:Freeware (Free)
File Size:10 Mb
Runs on:Windows Mobile 2003, Windows Mobile 2005, Windows Mobile 6, Pocket PC, Android, iOS, Handheld, Mobile Other
Beta Game Tester. If you want to become a beta game tester, download gamertesterground today. Learn how to get paid up to $80 a hour playing games. Many game manufacturers are willing to pay money to find people to help test their games.
File Name:betagametester.exe
Author:Gamer Tester Ground
License:Shareware ($44.95)
File Size:375 Kb
Runs on:Win95, Win98, WinME, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Vista
Download the latest beta version of the world's most popular Web browser. Internet Explorer 8 takes the Web experience beyond the page and introduces a new way to seamlessly experience the power of the Web whether you are a Web developer writing to standards, or an end user discovering a new online service. This beta release is available to everyone, but is primarily for Web developers and designers to test the new tools, layout engine, and programming enhancements.
File Name:IE8-WindowsXP-x86-ENU.exe
Author:Microsoft Co
License:Freeware (Free)
File Size:14.42 Mb
Runs on:WinXP
Install this update to resolve issues with Internet Explorer in Windows 7 Beta. For complete details of this update, see KB962961.Install this update to resolve issues with Internet Explorer in Windows 7 Beta.
File Name:Windows6.1-KB962921-ia64-Beta.msu
Author:Microsoft Corporation.
License:Freeware (Free)
File Size:18.38 Mb
Runs on:Windows 7
Install this update to resolve issues with non-compatible applications for Windows Server 2008 R2 Beta.Install this update to resolve issues with non-compatible applications for Windows Server 2008 R2 Beta. For complete details of this update, see Knowledge Base Article KB967062.
File Name:Windows6.1-KB967062-ia64-Beta.msu
Author:Microsoft Corporation.
License:Freeware (Free)
File Size:1.86 Mb
Runs on:Windows 7
A beta version of Iconix eMail ID supporting Outlook 2003 is now available. It is separate from our standard version that supports multiple webmail clients and Outlook Express. We view this as a real beta program. We need to contact you periodically. ..
File Name:IconixSetup.exe
Author:iconix
License:Freeware (Free)
File Size:3.57 Mb
Runs on:Windows Vista, XP, 2000
under realms is a new role playing game which is currently under development but has a game beta available to download right here on source forge, the full game is set to be released on 26/2/11. note that the beta represents the ful game in no. ..
File Name:under realms beta.zip
Author:underrealmsrpg
License:Freeware (Free)
File Size:64.12 Mb
Runs on:Windows
Norton Security with Backup beta includes multi-device security keeps you protected, no matter how you get connected. When you download this beta, you’ll be among the first to test drive the latest pre-release version of Norton Security. None of the chang. ..
File Name:Norton Security with Backup
Author:Symantec Corporation
License:Freeware (Free)
File Size:117 Mb
Runs on:Android, Mac OS X, Win8, Win7 x32, Win7 x64, WinVista, WinVista x64, WinXP
Django app to manage a private beta phase for a website. . This app provides users with the change to sign up for a private beta - by providing their email address.
File Name:django-hunger-1.0.6.tar.gz
Author:Joshua Karjala-Svenden
License:Shareware ($)
File Size:10 Kb
Runs on:Linux
OoVoo is an instant messaging client oriented to carrying on audio and video conversations. The application allows: having text, audio and video conversations (up to 6 people). CoRD is a Mac OS X remote desktop client for Microsoft Windows computers using the RDP protocol. It's easy to use, fast, and free for anyone to use or modify.
Related:Oovoo Download Beta - Oovoo To Oovoo Net Call - Oovoo Blackberry Download - Download Oovoo Mobile Nokia - Oovoo Blackberry Free Download
Pages : <1 | 2 | 3
Check compatibility
You can upgrade to OS X El Capitan from OS X Snow Leopard or later on any of the following Mac models. Your Mac also needs at least 2GB of memory and 8.8GB of available storage space.
MacBook introduced in 2009 or later, plus MacBook (13-inch, Aluminum, Late 2008) MacBook Air introduced in late 2008 or later MacBook Pro introduced in mid 2007 or later Mac mini introduced in early 2009 or later iMac introduced in mid 2007 or later Mac Pro introduced in early 2008 or later Xserve models introduced in early 2009
To find your Mac model, memory, storage space, and macOS version, choose About This Mac from the Apple menu . If your Mac isn't compatible with OS X El Capitan, the installer will let you know.
Make a backup
Before installing any upgrade, it’s a good idea to back up your Mac. Time Machine makes it simple, and other backup methods are also available. Learn how to back up your Mac.
Get connected
It takes time to download and install OS X, so make sure that you have a reliable Internet connection. If you're using a Mac notebook computer, plug it into AC power.
Download OS X El Capitan
For the strongest security and latest features, find out whether you can upgrade to macOS Catalina, the latest version of macOS.
If you still need OS X El Capitan, use this link: Download OS X El Capitan. A file named InstallMacOSX.dmg will download to your Mac.
Install the macOS installer
Double-click the downloaded file to open a window showing its contents. Then double-click the file within, named InstallMacOSX.pkg.
Iso coated v2 300 eci download mac download. Follow the onscreen instructions, which will guide you through the steps necessary to install.
Begin installation
After installation of the installer is complete, open the Applications folder on your Mac, then double-click the file named Install OS X El Capitan.
Oovoo Mac
Click Continue and follow the onscreen instructions. You might find it easiest to begin installation in the evening so that it can complete overnight, if needed.
Oovoo Download Mac Os X 10 11
Allow installation to complete
Oovoo Download Mac Os X 10.8
Please allow installation to complete without putting your Mac to sleep or closing its lid. Your Mac might restart, show a progress bar, or show a blank screen several times as it installs both OS X and related updates to your Mac firmware.
Learn more
Oovoo Download Windows 10
OS X El Capitan won't install on top of a later version of macOS, but you can erase your disk first or install on another disk.
You can use macOS Recovery to reinstall macOS.

0 notes
Text
Simplified Guide: Installing Visual Studio Code on Ubuntu Server via Windows RDP
Are you a developer seeking a seamless workflow on Ubuntu Server but prefer the familiarity of Windows Remote Desktop Protocol (RDP)? Look no further! In this guide, we'll walk you through the steps to install Visual Studio Code on Ubuntu Server using Windows RDP. You'll also learn how to procure an RDP service and set up Ubuntu on it for a hassle-free coding experience.

Why Ubuntu Server and Windows RDP?
Ubuntu Server offers a stable and efficient environment for development, particularly for web servers and cloud-based applications. On the other hand, Windows RDP provides a user-friendly interface and robust remote desktop connectivity. Combining the two allows for a versatile setup where you can leverage Ubuntu's power with the convenience of Windows RDP.
Step 1: Procure Your RDP Service
Before diving into the installation process, you'll need access to a Windows RDP service. You can easily buy RDP from various providers online. Look for a reliable service that offers sufficient resources and bandwidth to meet your development needs.
Step 2: Install Ubuntu on Your RDP
Once you have access to your RDP service, the next step is to install Ubuntu on it. Most RDP services offer pre-built Ubuntu images that you can deploy with just a few clicks. Follow the provider's instructions to create a new Ubuntu instance on your RDP.
Step 3: Connect to Your Ubuntu Server via Windows RDP

After the Ubuntu instance is up and running on your RDP, use your Windows Remote Desktop client to connect to it. Enter the IP address or hostname provided by your RDP service along with your login credentials to establish a remote desktop session.
Step 4: Install Visual Studio Code on Ubuntu
Now that you're logged into your Ubuntu Server via Windows RDP, it's time to install Visual Studio Code. Open a terminal window on your Ubuntu desktop and follow these commands:
Update the package index:
bashCopy code
sudo apt update
Install prerequisites for Visual Studio Code:
bashCopy code
sudo apt install software-properties-common apt-transport-https wget
Import the Microsoft GPG key:
bashCopy code
wget -q https://packages.microsoft.com/keys/microsoft.asc -O- | sudo apt-key add -
Enable the Visual Studio Code repository:
bashCopy code
sudo add-apt-repository "deb [arch=amd64] https://packages.microsoft.com/repos/vscode stable main"
Install Visual Studio Code:
bashCopy code
sudo apt update sudo apt install code
Step 5: Launch Visual Studio Code
Once the installation is complete, you can launch Visual Studio Code from the Ubuntu applications menu or by running the following command in the terminal:
bashCopy code
code
Step 6: Enjoy Coding on Ubuntu via Windows RDP
Congratulations! You've successfully installed Visual Studio Code on your Ubuntu Server using Windows RDP. Now you can seamlessly write, debug, and deploy your code in a familiar environment, combining the power of Ubuntu with the convenience of Windows RDP.
Conclusion
In this guide, we've demonstrated how to set up Visual Studio Code on Ubuntu Server via Windows RDP, utilizing the strengths of both platforms for an optimal development experience. By following these steps, you can enhance your workflow and productivity without compromising on performance or accessibility. Happy coding!
0 notes
Text
Shodan, One Of The Most Dangerous Option To Yahoo And Google
Shodan http://www.thefreedictionary.com/webcam is an alternative search engine that concerns a higher quantity of dangers
Shodan can be a venture developed by safety specialist John Matherly, that has identified it as being "the most frightening google search on the planet". Its title emanates from the kind of bad synthetic learning ability in the mythical xbox game Process Jolt.
We are now living in a world where, with increasing occurrence, actual devices and electrical methods are increasingly connected to each other because of the increase of the web of Issues, a complicated network which allows the swap of information. These disruptive technical advancements have permeated every aspect of modern-day life, facilitating and keeping track of many everyday activities relevant to travel, overall health, house, welfare or business.
Along with the several software that this Web of Issues has for all market sectors of daily life in general, a number of security issues also develop in experience of its emergence. The context of the deep website -or maybe the "undetectable" part of the Web that depends on 45 instances larger than the info indexed by Yahoo and google and all of those other traditional search engines like yahoo- is a risky ground where you could identify any gadget.

Within this deeply internet, Shodan is a search engine for HTTP addresses connected to the World wide web, the majority of which will not happen in Yahoo and google or comparable lookups. It can be defined as a web of Issues internet search engine, since it can identify freezers, alarms, security cameras, webcams, wearables, and then any other hooked up product.
The bases of Shodan, the favorite search engine for online hackers
Shodan is an internet search engine born in 2009 whose operation is just like Yahoo and google, though here the parallels finish. Instead of indexing web content via port 80 (HTTP) or 443 (HTTPS) as Search engines does, hodan crawls the world wide web for gadgets that reply to a number of other ports, such as: 21 (FTP), 22 (SSH), 23 (Telnet), 25 (SMTP), 80, 443, 3389 (RDP) and 5900 (VNC).
Shodan can learn and list practically any device, from a wide range of webcams, monitor signage, routers, firewalls, CCTV methods, manufacturing control techniques for nuclear strength plants and flowers, strength grids, home appliances plus more.
Probably the most dangerous and bad thing about this diagnosis is the fact all these devices are linked to the Online without their managers being familiar with the risks and risks in the safety degree, and so without the application of basic safety steps such as a consumer label or a robust and robust pass word.
The safety of customers is very shaky with webcams, simply because they can seize all sorts of pictures across the houses, personal information or facial looks of kids.
Lookup in Shodan through filter systems
Free of charge profiles in Shodan allow you to sort through the next filtration system:
Country: Will allow to encapsulate the research reducing it to some specific country.
Town: Filtering by area.
Harbour: Will allow to do each search based on the open up dock or even the services simply being executed,
World wide web: To look for a unique ip or ip collection.
Hostname: This filtration can be used for searches related to the words that we show in the hostname portion.
OS: Depending on the os.
In 2012, a security alarm researcher named Dan Tentler revealed how he surely could use Shodan to discover handle methods for devices, pressurized hot water heaters, as well as garage entrance doors.
He was also capable of finding a hydroelectric vegetation in France, an automobile clean that may be remotely converted on and off, along with a area ice hockey rink in Denmark that could have been defrosted on the mouse click. It even identified an entire city's website traffic management system connected to the group, which might Clicca qui have been disturbed by the use of a number of directions.
The presence of tasks like Shodan prospects us to reflect as shoppers and to implement new systems and security steps on our wearables, tools and also other intelligent merchandise and products.
0 notes
Text
Olympic Mountain Bike – William Mokgopo is on the way to Tokyo 2020
At the age of 13 years old, he built his first bike inside a shipping container. Three years later, he was hurtling down the dirt roads of Africa in serious mountain bike competitions. In 2020, he hopes to ride for gold in Tokyo.
William Mokgopo started out riding his uncle’s bike on the rugged streets of Diep loot, a township 40 kilometers north of Johannesburg. Everything changed when a 13-year-old Mokgopo came across a shipping container.
Olympic Mountain bike Fanatics from all over the world can grab their Olympic Mountain Bike Tickets from one of the best online ticketing market places.

“My uncle had this old road bike, it was so big, extra-large, and I was so little I would get into the frame and try to peddle on the side.”
At 13 years old, he built his first bike inside a shipping container. Three years later, he was hurtling down the dirt roads of Africa in serious mountain bike competitions. In 2020, he hopes to ride for gold in Tokyo.
They call him the Skinny Hulk. The name fits like a glove. Mokgopo, the South African mountain biker, is tall, thin and pumped up with gutsy determination. At the age of 24, he is already the 12th-ranked mountain biker in South Africa; part of a new generation of cyclists from the streets to race for gold at the UCI MTB World Championships, the African Continental MTB Championships, and the UCI MTB World Cup.
“MTB is growing massively. In the future, I think it could be a major sport. It’s coming to schools now and the schools’ series this year had about 10,000 riders. Even if you look at the black communities, it’s growing. Yesterday we went for an 11-hour ride around Johannesburg and there were about 30 black riders.”
“I think it’s a bit premature to think I will qualify for this year’s Olympics. But the qualifiers are due in May. Even if I make third or second, I still might make it.”
On this early summer morning, Mokgopo, in riding gear, greets with a warm smile outside Number 3080, on a bumpy street in Diep loot. It’s not easy for cars in this street, but an ideal challenge for training on a bike.
Mokgopo lives in a Reconstruction and Development Program house that the government started building for its citizens after the 1994 elections.
“Everyone here used to live in extension one; in shacks. When the houses were allocated, they chose a block of shacks and said those living in shacks from here to here are getting RDP houses. We were given a number and told this was our house. We signed a form, and that was it. I was still at primary school at that time. Before it was the six of us living in the house.”
“The first year that I started getting paid, I extended these other two houses and one in the back here. It was actually just to have a bit of space. It was difficult living together; trying to bath here and trying to do a whole lot of stuff,” he says.
“It was just up the road from my house. You will see the fencing on the main road. It started with a project called Earn-A-Bike. You would go and choose a bike, then they would strip it down and then you would teach yourself how to build it. Then, when you graduated, that bike that you built would be your own bike,” he says.
Here, Mokgopo came across Simon Nash, Founder of the Diep loot Mountain Bike Academy, and began to race.
“People didn’t take it seriously. When you are riding a bike in Diep loot, it looks like you are just doing it for leisure. You are a grown-up still riding a bike, for my neighbors it was stupid. Soccer is the main sport here, so when you are on a bike people are like what are you doing?”
For Mokgopo it was uphill all the way. His school friends tied strings across the road to bring down his bike. Outside a corner store, a group of men would sit on crates and laugh at him as he rode by.
“It would be very tough getting out the township in your riding gear. I would have to take shorts and the minute I got out of town then take them off and go ride my bike. There were guys who would stop me and ask me stupid questions, like what is this what? What are these pads on your pants; are they for a woman? But now those people who were laughing at me are actually my friends.”
“The other day, I was sitting on the floor at the corner shop and one of the guys came up and said why is The Celebrity, cause that what they call me now, sitting here? One guy said I think even if William has a million and he will still come and sit here. I always want to show that I still want to be at the level they are.
One reason for Mokgopo’s smile on this day is a new $4,750 bike, tucked away in his room. Along with competing professionally on the Kargo Pro MTB Team, the first UCI-registered MTB Team in South Africa, Mokgopo is a sports sciences student at the University of Pretoria.
“The tricky thing about MTB is getting the points and staying in front. When you do cross country, you need to look at the course. When you are racing it’s a completely different course. Someone might push you off course or the rock you thought you would be jumping from might have moved. It’s always the thought of what’s coming next,” says Mokgopo.
“From our side, William is a one-of-a-kind athlete, he is so complete on and off the bike and many pro athletes can learn from him. The Olympics is very much a reality for William in 2020 and beyond. He is showing improvement every season and also deals with setbacks very well which is a very important aspect for a pro athlete striving to be the best. Making small adjustments to his training regime over the coming seasons will see William gain that consistency that is needed a week in, week out for Olympic level racing,” says Shaun Peschl, Team Manager of Kargo MTB.

Cycling isn’t cheap. Mokgopo says it can cost around $34,000 a year to race as a professional for travel alone. His team is fortunate to get their bikes and supplements for free. The latest equipment can make all the difference.
“When I started racing, I had a poorly conditioned bike. I remember the academy got me a carbon bike; I could finish second. It just shows from that little change in equipment it can set you moving into that winning stage. It can put you on the podium. The expenses can push people away from the sport. But it depends on the person you are,” he says.
“I will sit with my eyes open and listen to music. People think I am listening, but I am seeing the course and riding it all the time. It’s getting the feel of the race before even getting to the starting line. I see everything how I want it to be in the race. This is where I have to jump. This is where I need to speed up,” says Mokgopo.
He once spent three weeks in bed with a broken shoulder, after he clipped a motorbike while training on a dirt track.
“I couldn’t even control my fingers. I rode one-handed to home in Diepsloot. Overnight it got worse and we had to go to the hospital the next day. But when I went back everything had completely changed. I started coming second and third and ended up winning a race and that was it. I went to bigger races and was introduced to cross country. When you get your first victory that is when the love gets that bit bigger,” he says.
“When you fall, the blood looks super cool, My mom was skeptical; with all the bruises and stitches I have when I come home. She didn’t want me to do it. She doesn’t say much, but you can see she’s very proud. My dad always says he’s very proud of me,” says Mokoro.
Mokgopo’s dream of a spot in Rio was ruined when he injured his knee at the Cape Epic in March. It took two months to get back on the bike again.
The injury forced Mokgopo to build a new dream; his plan is now to be the South African champion in 2017, go to the Commonwealth Games in 2018 and to be an Olympic athlete in Tokyo in 2020.
Bumps, bruises, a bike built in a shipping container and friends who used to laugh at him. Mokgopo comes from humble beginnings and hopes to ride his luck all the way to Japan in 2020.
Olympic enthusiasts can get up to the latest updates of Olympic Tickets through our most trusted online ticketing market place. OlympicTickets2020.com is the most reliable source to book Olympic 2020 Tickets.
#OlympicMountainBikeTickets OlympicTickets Olympic2020Tickets SummerGamesTickets TokyoOlympicTickets
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
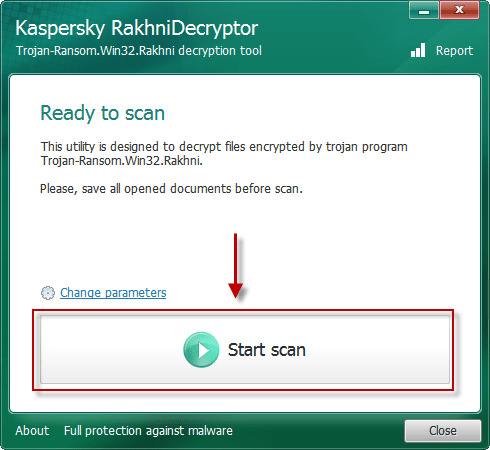
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
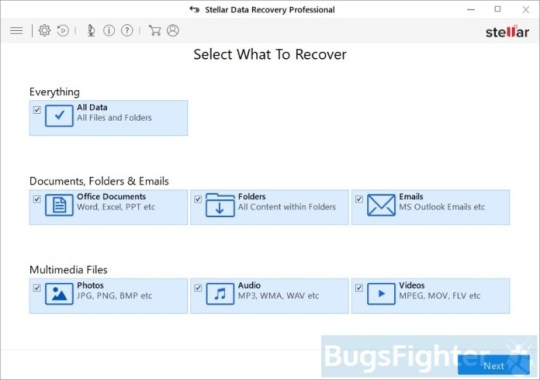
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
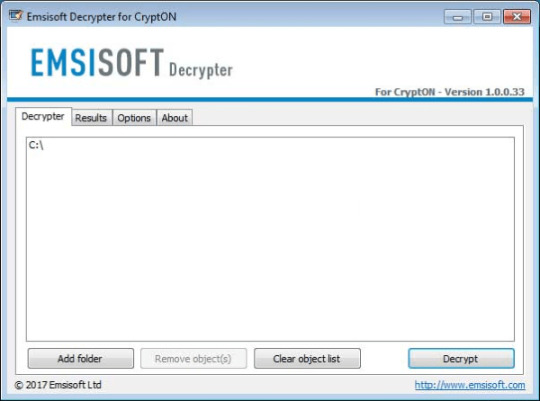
Obtain CryptON Decryptor
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
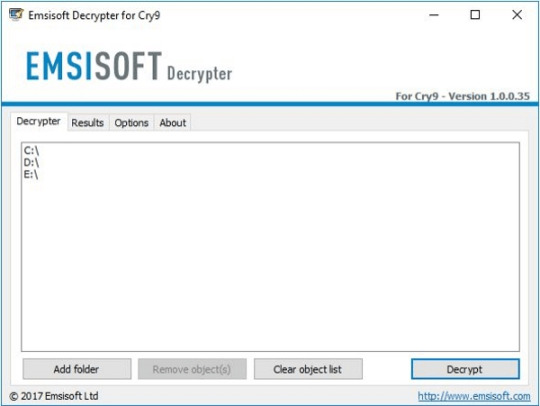
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
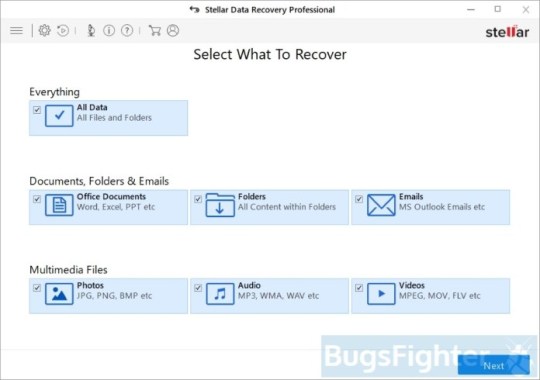
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
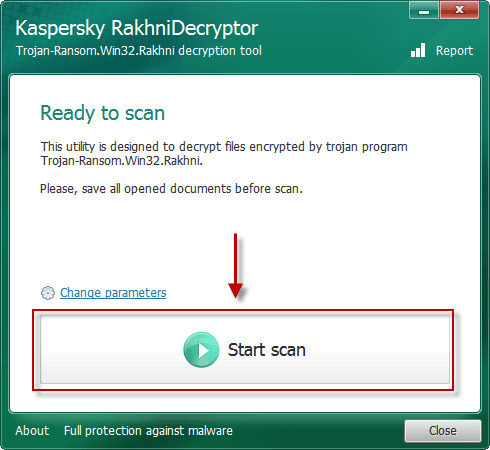
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
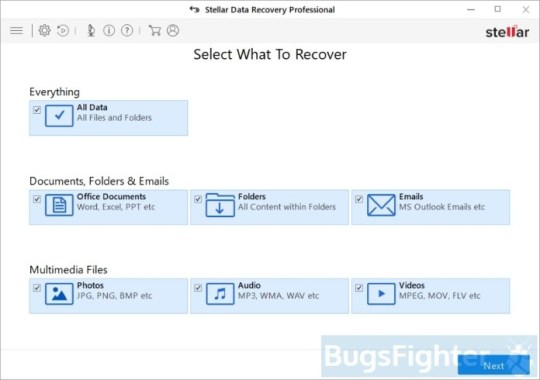
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Link
Advanced Ethical Hacking Course For 2019 ##elearning ##UdemyFrancais #Advanced #ETHICAL #Hacking Advanced Ethical Hacking Course For 2019 Become a white hat hacker and learn all the practical techniques for penetration testing with this amazing course which will provide conceptual framework to your security training. The course not only covers theoretical concepts but cover the practical demonstrations of various tools like Metasploit , Scapy and WireShark. The course is divided into the following main sections: Ethical Hacking Concepts -What is Ethical Hacking? Know about different types of hackers. Get to know about hacktivism and practical pen testing techniques Real World Information Gathering -Learn about foot printing and reconnaissance, Email harvesting, Learn and master SSL scan, Maltego, Whatweb, HttpRecon. Work on techniques like IP address geolocation, DNS and Mail Server Enumeration Scanning and Vulnerability Gathering -Learn to use scapy for packet crafting and port scanning, Learn to use network scanning techniques and work on vulnerability identification Network Attacking Techniques Master techniques for password cracking, MITM, Sniffing SSL and RDP attacks Web Exploitation Techniques Learn about password attacks, SQL Injections, RCE and DOS attacks Wireless Network Security Standards in Wireless security, WEP encryption, Wireless sniffing, Protecting Wireless networks Metasploit Learn to use the metasploit tool for your projects Detection Evasion Learn about the detection evasion techniques This exhaustive course covers everything you need to know to be a ethical hacker. Get the Knowledge & the Expertise. Who this course is for: College students Software Engineer IT Professionals Computer Science Students Ethical Hacking studying students Web Developers Database administrators Security engineers Network engineers Anyone who is interested to start their career in Ethical hacking 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/advanced-ethical-hacking-course-for-2019/
0 notes
Text
Remote Working and IT Security: how to mitigate risks and defend your employees from cyber attacks

On May 2020, Kaspersky published an interesting report entitled How COVID-19 changed the way people work, which illustrates a series of statistics that are anything but reassuring on the level of awareness achieved by Italy regarding cyber security. in smart working. In this post we'll try to summarize the fundamental concepts expressed in the report and to integrate them with specific observations and recommendations for companies, IT managers and system administrators interested in providing their employees with the appropriate protection tools to defend themselves from the risks related to cyber attacks on your remote work systems. DISCLAIMER: This article has not been sponsored in any way by Kaspersky or other companies: the contents reflect only the thoughts of the author.
Three out of four employees at risk
According to the data published in the report, almost three out of four employees (73%) among those who carry out smart working activities have never received specific information security training or guidance to protect themselves from the risks associated with that particular type of job. Moreover, there is no doubt that the good practices that allow you to work remotely safely differ significantly from the standard measures that are transmitted and put into practice in the workplace, both as regards individual awareness of the risks associated with their activities and at the level of the technological tools to be adopted; just think of the fact that, while in the company it is almost always possible to count on an appropriately trained ICT team that deals with providing help-desk operators and support on a daily basis, this type of infrastructure is very often absent, unforeseen or impossible to provide the same level of service for smart working stations. The consequences of this "lack of attention" are also highlighted in the report, which shows that almost one in four (24%) employees claims to have received COVID-19 themed phishing emails.
Beware... the boss!
How can we defend ourselves against this type of risk? As a matter of fact the first step to take should be to provide specific training for all our employees (including managers and administrators) on IT security topics, with a specific focus on the risks connected to the remote working practices. The emphasis placed on the executive roles is not accidental, as it is proven that management often tends to be guilty "exempted" from this type of training: such choice can definitely result in a serious mistake, since the executive roles are often subject to these kind of attacks since they do have a greater decision-making capacity and an authorization level tipically higher than the average employee. Moreover, they are also tipically most vulnerable to some sneaky social engineering techniques (such as spear phishing) as they are usually less used to read huge amounts of e-mail messages.
IT Security and "remote" threats
Ensuring the protection of employees from an IT point of view inside their homes is a task that can be demanding for any company: the countermeasures adopted within the company, which are often based (and tend to take for granted) on a fixed presence of security personnel and on an infrastructure physically contained within the company perimeter, could prove ineffective or insufficient for this purpose. It is therefore essential to establish and implement specific security measures for remote working, which are able to offer sufficient guarantees of risk mitigation against modern attacks aimed at operators' personal tools, including: Spam and phishing emails received on desktop, mobile and web mail clients outside the company walls / network perimeter. Cyberattacks on domestic connection devices such as home routers, switches, public WiFi hot spots, etc. Abuse of remote connection tools based on known protocols (RDP, VNC, etc.) or through third party software (TeamViewer, AnyDesk, RAdmin, etc). Theft of devices assigned to users in BYOD (Bring Your Own Device) or COPE (Corporate Owned, Personal Enabled) mode.
The risks of "Shadow IT"
The overall picture is further complicated by the fact that some of these tools can be implemented or used by operators without the explicit approval of the company management or IT security staff: such phenomenon is known as Shadow IT, a bad practice according to which the employee adopts independently and uncontrolled one or more technological tools (software or infrastructures) in order to optimize or make their work easier. Such event tends to be rather common in small and medium-sized companies that have not yet adopted a working methodology based upon policies, processes and procedures; it goes without saying that the current COVID-19 emergency has also greatly increased those practices in a dizzying way: according to the numbers collected by the Kaspersky survey made available in the report (6,000 workers worldwide) many employees declared they had eventually picked some "not explicitly authorized" software tools for either video conferences (35%), instant messaging (39%) and/or cloud file storage (35%).
Risk mitigation techniques
These troubling numbers can definitely help to understand the absolute importance of communicating to employees the existence and danger of the numerous IT risks associated with remote working and the necessary set of instructions, best practices and know-how on how to mitigate or avoid them. To counter those dreadful scenarios, Kaspersky recommends the following guidelines, which can definitely help employers and businesses stay on top of any potential IT security issues and remain productive while staff are working from home: Ensure your employees have all they need to securely work from home and know who to contact if they face an IT or security issue. Schedule basic security awareness training for your employees. This can be done online and cover essential practices, such as account and password management, email security, endpoint security and web browsing. For that very reason, we suggest to take a look to the Stay Safe, Stay Secure initiative, a free online cybersecurity course offered by Kaspersky and Area9Lyceum to help employees to increase their remote working IT Security awareness and learn the best practices to mitigate the risks coming from the most common threats. Take key data protection measures including switching on password protection, encrypting work devices and ensuring data is backed up. Ensure devices, software, applications and services are kept updated with the latest patches. Install proven protection software on all endpoints, including mobile devices, and switch on firewalls. Ensure you have access to the latest threat intelligence to bolster your protection solution. Double check the protection available on mobile devices. For example, it should enable anti-theft capabilities such as remote device location, locking and wiping of data, screen locking, Two-Factor Authentication (2FA) and biometric security features like Face ID or Touch ID, as well as enable application controls to ensure only approved applications are used by employees. For additional info about these security measures, how they work and why is important to enable them, we strongly suggest to check out our free Two-Factor Authentication (2FA) Tutorial Guide. Ensure your router supports and works smoothly when transmitting Wi-Fi to several devices simultaneously, even when multiple workers are online and there is heavy traffic (as is the case when using video conferencing). Regularly update your router to avoid potential security issues. Set up strong passwords for your router, Wi-Fi network and all personal accounts. Moreover, be sure to always change the default passwords for all your devices, since they are most likely known by potential hackers that could use them to infiltrate through your system. If you can, only do work on devices provided by your employer. Putting corporate information on your personal devices could lead to potential security and confidentiality issues. Do not share your work account details with anybody else, even if it seems a good idea at the time. Always feel able to speak to your employer’s IT or IT security team if you have any concerns or issues when working from home.
Conclusions
That's it, at leat for the time being: we hope this brief guide will help companies and their IT managers and system administrators to provide comfortable protection tools to their employees and minimize the risks due to phishing and other cyber attacks to their "remote" workstations. Read the full article
#AnyDesk#Area9Lyceum#BYOD#COPE#COVID-19#ITSecurity#Kaspersky#RAdmin#RemoteWorking#SmartWorking#TeamViewer#VNC#VPN
0 notes
Text
How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files
What’s CryptON Ransomware
Word: Some versions of CryptON Ransomware are decryptable. You’ll be able to attempt free decryptors provided under and attempt to restore encrypted information. In any other case, hold your information till effective decryptor can be launched.
Notice: In July 2019 new variation of Nemesis Ransomware was discovered. It appends .YOUR_LAST_CHANCE extension to encrypted information. Ransom observe file is known as: _RESTORE FILES_.txt. Victims are provided to contact malefactors by way of e-mails: [email protected], [email protected] or [email protected].
CryptON Ransomware or Nemesis Ransomware or X3M Ransomware is among the most dangerous and wide-spread ransomware households. At present, there are multiple successors of initial virus and a number of other deviations constructed on one other platforms. Cry9, Cry36 and Cry128 Ransomware came from this collection. Virus makes use of mixture of AES-256, RSA-2048 and SHA-256 encryption algorithms. Newest discovered version is definitely referred to as CryptON Ransomware and makes use of [email protected] extension for affected information. Other used suffixes are:
.YOUR_LAST_CHANCE, _x3m, _locked, _crypt, .encrptd, _locked_by_krec, _locked_by_perfect, _r9oj, .nemesis, .v8dp, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_, .-juccy[a]protonmail.ch, _[[email protected]].xj5v2, .-sofia_lobster[a]protonmail.ch, _[wqfhdgpdelcgww4g.onion.to].r2vy6, _[qg6m5wo7h3id55ym.onion.to].63vc4, _2irbar3mjvbap6gt.onion.to._, _gebdp3k7bolalnd4.onion._, .fgb45ft3pqamyji7.onion.to._, .losers, .damoclis
Ransomware calls for from zero.2 to 1 BitCoin for decryption. It isn’t really helpful to pay the ransom as there are not any guarantee malefactors will send decryption key. Depending on version, after encryption CryptON Ransomware creates totally different text information with directions to pay the ransom. Current model makes use of HOWTODECRYPTFILES.html and it incorporates following info:
CryptON Ransomware
All information are encrypted! CryptON Ransomware To decrypt the information, you want to purchase special software program «CryptON decryptor» Restore the info, comply with the instructions! You possibly can study extra / request e-mail: [email protected] You’ll be able to study extra/questions within the chat: https://cryptxf3zamy5kfz.tor2web.link (not need Tor) https://cryptxf3zamy5kfz.onion.plus (not need Tor) http://cryptxf3zamy5kfz.onion/ (need Tor) You possibly can study extra drawback out bitmessage: https://bitmsg.me/ BM-2cWzhoNFbjQ3X8pULiWSyKhc6dedQ54zQ1 – If the resource is unavailable for a long time to put in and use the terms of reference of the browser: 1. + Begin the Internet browser 2. + Sort or copy the tackle https://www.torproject.org/download/download-easy.html within the tackle bar of your browser and press key ENTER three. + On the website you may be prompted to obtain the Tor browser, download and install it. To work. four. + Connection, click on “join” (utilizing English model) 5. + After connecting, open a traditional window Tor-browser 6. + Sort or copy the handle http://cryptxf3zamy5kfz.onion/ within the handle bar of Tor-browser and press key ENTER 7. + Watch for the download website // + When you’ve got any problems with set up or utilization, please go to the video: https://www.youtube.com/watch?v=gOgh3ABju6Q Your personal identification ID:-
YOUR_LAST_CHANCE Ransomware
*** ALL YOUR WORK AND PERSONAL FILES HAVE BEEN ENCRYPTED ***
To decrypt your information that you must purchase the particular software program ñ “Nemesis decryptor” You’ll find out the small print/buy decryptor + key/ask questions by e-mail: [email protected], [email protected] OR [email protected] IMPORTANT! DON’T TRY TO RESTORE YOU FILES BY YOUR SELF, YOU CAN DAMAGE FILES! If inside 24 hours you did not receive an answer by e mail, make sure to write to Jabber: [email protected] Your private ID: –
Different potential filenames for ransom notes information are: COMO_ABRIR_ARQUIVOS.txt, ###DECRYPT-MY-FILES###.txt, HOW_OPEN_FILES.html, DECRYPT MY FILE.txt. On this article we collected, consolidated and structured obtainable details about this malware and potential ways of decryption. Use directions on this web page to take away CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked information in Home windows 10, Windows 8 or Home windows 7.
How CryptON Ransomware infected your PC
Could be distributed by hacking by means of an unprotected RDP configuration, using e-mail spam and malicious attachments, fraudulent downloads, exploits, net injections, pretend updates, repackaged and infected installers. After infection and encryption, Scarab deletes shadow copies of information, system restore points, disables the Windows Boot Repair, using sure command immediate commands. Virus assigns certain ID with the victims, that is used to call these information and supposedly to ship decryption key. In an effort to forestall an infection with such a threats in future we advocate you to make use of SpyHunter and BitDefender Anti-Ransomware.
Download CryptON Ransomware Removing Software
Obtain Removing Software
To take away CryptON Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of CryptON Ransomware.
Learn how to remove CryptON Ransomware manually
It isn’t really helpful to take away CryptON Ransomware manually, for safer answer use Removing Tools as an alternative.
CryptON Ransomware information:
Crypton.exe FileSpy.exe invoice-0071350.js svchost.exe
CryptON Ransomware registry keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”crypton” = “%AppDatapercentCrypton.exe” HKEY_CURRENT_USERSoftwareCrypton”mail” = “.exe”
How one can decrypt and restore .YOUR_LAST_CHANCE, _x3m or _locked information
Use automated decryptors
Obtain CryptON Decryptor
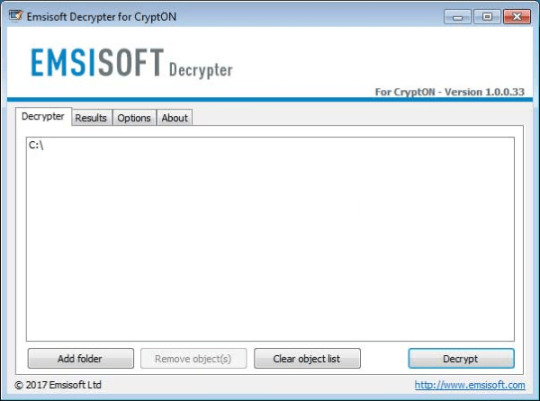
Use following software from Emsisoft referred to as Decryptor for CryptON, that may decrypt information with following extensions:
.id-_locked, .id-_locked_by_krec, .id-_locked_by_perfect, .id-_x3m, .id-_r9oj, [email protected], [email protected]_, [email protected]_, [email protected]_, [email protected]_, [email protected]_
Obtain it right here:
Obtain Emsisoft CryptON Decryptor
Download Cry9 Decryptor
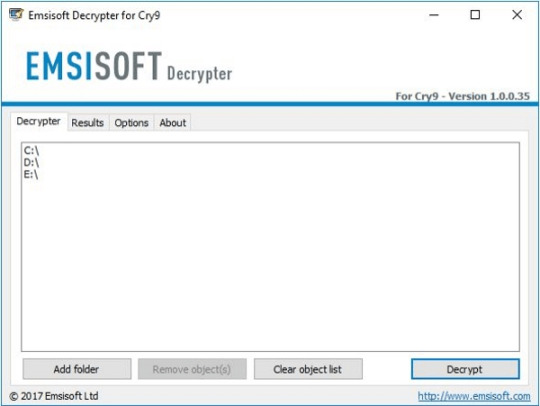
Use following device from Emsisoft referred to as Decryptor for Cry9, that can decrypt information with following extensions:
.-juccy[a]protonmail.ch, .id-, .id-_[[email protected]].xj5v2, .id-_r9oj, .id-_x3m, .id-_[[email protected]]_[[email protected]].x3m, “.”, .-sofia_lobster[a]protonmail.ch and ._[wqfhdgpdelcgww4g.onion.to].r2vy6
Obtain it here:
Obtain Emsisoft Cry9 Decryptor
Obtain Cry128 Decryptor
Use following software from Emsisoft referred to as Decryptor for Cry128, that may decrypt information with following extensions:
.fgb45ft3pqamyji7.onion.to._, .id__gebdp3k7bolalnd4.onion._, .id__2irbar3mjvbap6gt.onion.to._ and .id-_[qg6m5wo7h3id55ym.onion.to].63vc4
Download it here:
Download Emsisoft Cry128 Decryptor
There isn’t a function to pay the ransom because there isn’t a guarantee you’ll obtain the key, however you’ll put your financial institution credentials in danger.
In case you are contaminated with CryptON Ransomware and removed it out of your pc you’ll be able to try to decrypt your information. Antivirus distributors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you are able to do the following:
Use Stellar Knowledge Restoration Professional to revive .YOUR_LAST_CHANCE, _x3m or _locked information
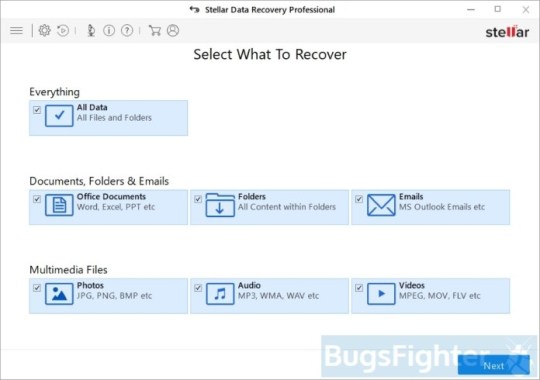
Download Stellar Knowledge Recovery Skilled.
Click Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview found information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Recovery Skilled
Utilizing Home windows Previous Versions choice:
Right-click on infected file and choose Properties.
Select Previous Versions tab.
Select specific model of the file and click Copy.
To restore the selected file and substitute the prevailing one, click on the Restore button.
In case there isn’t a gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Obtain Shadow Explorer program.
Run it and you will notice display itemizing of all of the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Right-click on a folder identify and select Export.
In case there are not any other dates within the listing, choose various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that incorporates encrypted information.
Right-click on the encrypted file and choose Earlier Versions.
Choose the model of the file you wish to restore and click on the Restore button.
Learn how to shield pc from viruses like CryptON Ransomware in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may aid you with lively anti-ransomware protection, as further defend to your present protection. It won’t conflict with greater safety purposes. In case you are looking complete internet security answer contemplate upgrading to full version of BitDefender Internet Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information utilizing easy online backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating bodily drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Home windows 10 and eight/eight.1 users can discover pre-installed OneDrive backup answer from Microsoft. It’s truly the most effective backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it right here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Using spam filters and creating anti-spam guidelines is sweet apply. One of many world leaders in anti-spam safety is SpamFighter. It works with numerous desktop purposes, and supplies very excessive degree of anti-spam protection.
Download SPAMFighter 5/5 (3)
The post How to remove CryptON Ransomware and decrypt .YOUR_LAST_CHANCE, _x3m or _locked files appeared first on Spouting-Tech.
#decrypt _crypt files#decrypt _locked files#decrypt _r9oj files#decrypt .damoclis files#decrypt .losers files#decrypt .nemesis files#decrypt [email protected] files#decrypt .x3m files#decrypt .your_last_chance files#Ransomware#remove cry128 ransomware#remove cry9 ransomware#remove crypton ransomware#remove losers ransomware#remove nemesis ransomware#remove x3m ransomware#tech#Tutorials#Viruses
0 notes