#Functional Blocks of IoT
Explore tagged Tumblr posts
Text

The Internet of Things (IoT) comprises several functional blocks that enable its seamless operation. At its core, IoT devices gather data from sensors embedded in various environments. These sensors detect changes in temperature, humidity, motion, and more, transmitting this information to a central processing unit. The processing unit analyzes the data and triggers actions based on predefined parameters. Functional blocks of IoT, including sensing, processing, communication, and actuation, synergize to create interconnected systems revolutionizing industries worldwide.
0 notes
Text
Live stream happened, and we got some designs revealed! As well as a couple of information, but not anything major.

Miss conductor, not much of a surprise (but miss girl looks gorgeous as always)

And Node, who is sort of the main antagonist.
I made a prediction before, and April 21 hit,.. so I believe it is well due for an update by now.
While we did not receive nearly as much information as we were anticipating, a design still reveals much on the character itself when going through the lens of a general analysis. In this context, their abilities and name aid significantly in the status and essential depths of their character.
With what I can gather in my research, nodes play an important role in networking because they are the building blocks of a network, precisely the gateway for connection, direction, sending, creating, receiving, and storing data. It requires only software to connect to the network, and it can be run by completely anyone. Applying this knowledge with concept arts of the game and overall worldbuilding of the series itself—everything becomes a lot clearer.
So now, how can we apply this to Node?

Node's name is simple in itself, and it connects to their design as well. They are quite literally made up of nodes. One in their head and the other in their limbs. Their body is translucent.
Network nodes are categorical. Thanks to DJ, we got a helpful hint that incredibly reduced their types to a digestible and simpler layout.
Their name starts with i.
There are countless forms and types of nodes, the hint condensed it down to 2 answers, both starting with the letter “i”
Intermediate nodes
These include devices like routers and switches that help direct data to the correct destination while also receiving it. They don't originate or terminate data but instead pass it along to where it needs to go.
IoT nodes
loT (Internet of Things) Nodes serve as devices that establish connectivity to the Internet via a gateway, effectively enabling the integration of the physical world into the vast realm of the Internet. Within an loT ecosystem, these nodes function as crucial components for bridging the gap between the physical and virtual worlds. Taking charge of managing the entire loT system.
We had seen this ability before vía King's icons' staff, in which it only sucked in Minecraft mobs due to the strong force being their obligatory origin, overriding the game itself due to the overlapping icons.
In regards to King, he used this ability for the very destruction of the game itself, down to the code, reducing it to nothing but.. nothing for the sake of vengeance. Or at least what would have occurred if he did succeed.
way to go CG! Give credit where it's due
Despite this being marked with the intention of erasion and minimization, I think it's safe to group this as receiving and storing data. The two icons combined created a horrifically dramatized version of the force with storing and receiving, which created an incredibly overpowered demolishing force.

In Chosen, we had seen this ability before as well, as the constellations are seen right as he creates the gateway from the Outernet, which sounds awfully familiar. This is what you would refer to as an "extension to the digital world"
I think I can be able to safely group this to direction and creation.

From how I see it, it seems as though it's quite diverse in a fictional worldbuilding sense within characters.
And obviously, it won't be the last time we would see it. It seems as though we would be exploring this quite a lot.

In their cameo, Node is in an assumed line-up with all the major series antagonists.

But if you’re asking me, it seems as though our iconic antagonists appear to be rather victims of Node. Menacingly behind them, their abilities floating not far behind as they're stuck in a swampy substance. But that's just me.
Node's entire antagonistic ordeal is beyond my grasp, but I'm assuming their abilities and attacks surrounds the embodiment of network topology, which would mold and diverse into the connections of nodes. They possibly intend to screw up with the gateways that are responsible for the receiving, directing, and sending of data between various devices through communication links that are defined as network—with the basic visuals of concept art we were given.

(The gateway, ethernet tunnels, the train cough cough)
Node's goal and story behind that destruction remains anonymous, as the writing is still in early development. Regardless, food for thought.
#alan becker#animation vs minecraft#animator vs animation#animation versus#nerd voyage#it's pretty interesting#though my research is still ongoing#when i say it's diverse..#yeah it's diverse alright
83 notes
·
View notes
Text
Navigating the Cloud: Unleashing Amazon Web Services' (AWS) Impact on Digital Transformation
In the ever-evolving realm of technology, cloud computing stands as a transformative force, offering unparalleled flexibility, scalability, and cost-effectiveness. At the forefront of this paradigm shift is Amazon Web Services (AWS), a comprehensive cloud computing platform provided by Amazon.com. For those eager to elevate their proficiency in AWS, specialized training initiatives like AWS Training in Pune offer invaluable insights into maximizing the potential of AWS services.

Exploring AWS: A Catalyst for Digital Transformation
As we traverse the dynamic landscape of cloud computing, AWS emerges as a pivotal player, empowering businesses, individuals, and organizations to fully embrace the capabilities of the cloud. Let's delve into the multifaceted ways in which AWS is reshaping the digital landscape and providing a robust foundation for innovation.
Decoding the Heart of AWS
AWS in a Nutshell: Amazon Web Services serves as a robust cloud computing platform, delivering a diverse range of scalable and cost-effective services. Tailored to meet the needs of individual users and large enterprises alike, AWS acts as a gateway, unlocking the potential of the cloud for various applications.
Core Function of AWS: At its essence, AWS is designed to offer on-demand computing resources over the internet. This revolutionary approach eliminates the need for substantial upfront investments in hardware and infrastructure, providing users with seamless access to a myriad of services.
AWS Toolkit: Key Services Redefined
Empowering Scalable Computing: Through Elastic Compute Cloud (EC2) instances, AWS furnishes virtual servers, enabling users to dynamically scale computing resources based on demand. This adaptability is paramount for handling fluctuating workloads without the constraints of physical hardware.
Versatile Storage Solutions: AWS presents a spectrum of storage options, such as Amazon Simple Storage Service (S3) for object storage, Amazon Elastic Block Store (EBS) for block storage, and Amazon Glacier for long-term archival. These services deliver robust and scalable solutions to address diverse data storage needs.
Streamlining Database Services: Managed database services like Amazon Relational Database Service (RDS) and Amazon DynamoDB (NoSQL database) streamline efficient data storage and retrieval. AWS simplifies the intricacies of database management, ensuring both reliability and performance.
AI and Machine Learning Prowess: AWS empowers users with machine learning services, exemplified by Amazon SageMaker. This facilitates the seamless development, training, and deployment of machine learning models, opening new avenues for businesses integrating artificial intelligence into their applications. To master AWS intricacies, individuals can leverage the Best AWS Online Training for comprehensive insights.
In-Depth Analytics: Amazon Redshift and Amazon Athena play pivotal roles in analyzing vast datasets and extracting valuable insights. These services empower businesses to make informed, data-driven decisions, fostering innovation and sustainable growth.
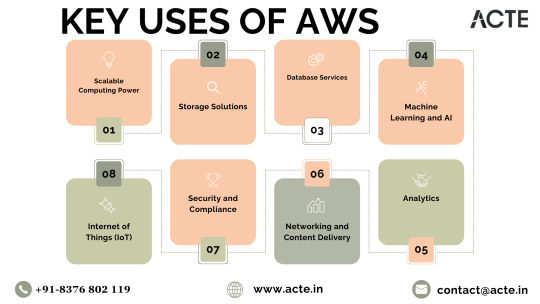
Networking and Content Delivery Excellence: AWS services, such as Amazon Virtual Private Cloud (VPC) for network isolation and Amazon CloudFront for content delivery, ensure low-latency access to resources. These features enhance the overall user experience in the digital realm.
Commitment to Security and Compliance: With an unwavering emphasis on security, AWS provides a comprehensive suite of services and features to fortify the protection of applications and data. Furthermore, AWS aligns with various industry standards and certifications, instilling confidence in users regarding data protection.
Championing the Internet of Things (IoT): AWS IoT services empower users to seamlessly connect and manage IoT devices, collect and analyze data, and implement IoT applications. This aligns seamlessly with the burgeoning trend of interconnected devices and the escalating importance of IoT across various industries.
Closing Thoughts: AWS, the Catalyst for Transformation
In conclusion, Amazon Web Services stands as a pioneering force, reshaping how businesses and individuals harness the power of the cloud. By providing a dynamic, scalable, and cost-effective infrastructure, AWS empowers users to redirect their focus towards innovation, unburdened by the complexities of managing hardware and infrastructure. As technology advances, AWS remains a stalwart, propelling diverse industries into a future brimming with endless possibilities. The journey into the cloud with AWS signifies more than just migration; it's a profound transformation, unlocking novel potentials and propelling organizations toward an era of perpetual innovation.
2 notes
·
View notes
Text
Responsive Design and Beyond: Exploring the Latest Trends in Web Development Services
The two things ruling the present scenario are the internet and smartphones. The easier they are making the lifestyle of the consumers the more difficult it becomes for the lives of the business owners. Digitization has resulted in the rise of competition from the local level to the national and international levels. The businesses that are not adopting the culture are lagging far behind in the growth cycle. The only way to get along with the pace is to hire a custom web development service that is capable of meeting the needs of both the business and consumers. The blog aims to explore some such services that are redefining the web development world.
Latest Trends in the Web Development Services
Blockchain Technology
Blockchain is an encrypted database storing system. It stores information in blocks, which are then joined as a chain. It makes transactions more secure and error-free. The technology enables the participants to make transactions across the internet without the interference of a third party. Thus, this technology can potentially revolutionize different business sectors by reducing the risks of cybercrimes. The technology allows web developers to use open-source systems for their projects, hence simplifying the development process.
Internet of Things (IoT)
IoT can be defined as a network of internet-enabled devices, where data transfer requires no human involvement. It is capable of providing a future where objects are connected to the web. IoT fosters constant data transfer. Moreover, IoT can be used to create advanced communication between different operational models and website layouts. The technology also comes with broad applications like cameras, sensors, and signaling equipment to list a few.
Voice Search Optimization
Voice search optimization is the process of optimizing web pages to appear in voice search. . In the field of web development, the latest innovations are voice-activated self-standing devices, and voice optimization for apps and websites. The technology is being developed that will be able to recognize the voices of different people and provide a personalized AI-based experience
AI-Powered Chatbots
AI-powered chatbot uses Natural Language Processing (NLP) and Machine Learning (ML) to better understand the user’s intent and provide a human-like experience. These have advanced features like 24×7 problem-solving skills and behavior analytics capabilities. These can be effectively used fo customer support to increase customer satisfaction. An AI-powered chatbot can easily be integrated into regular/professional websites and PWAs. Chatbots generally provide quick answers in an emergency and are quick to resolve complaints.
Cloud Computing
It is the use of cloud-based resources such as storage, networking, software, analytics, and intelligence for flexibility and convenience. These services are more reliable as they are backed up and replicated across multiple data centers. This ensures that web applications are always available and running. It is highly efficient for remote working setups. The technology helps avoid data loss and data overload. It also has a low development costs, robust architecture and offers flexibility.
Book a Web Development Service Provider Now
So, if you are also excited to bring your business online and on other tech platforms but are confused about how to do that, you are recommended to reach out to one of the best web development companies i.e. Encanto Technologies. They have a professional and competent web development team that would assist you in the development of an aesthetic, functional, and user-friendly website that would take your revenue to new heights. So, do not wait to enter the online world and book the services of OMR Digital now.
Author’s Bio
This blog is authored by the proactive content writers of Encanto Technologies. It is one of the best professional web development services that embodies a cluster of services including web development, mobile application development, desktop application development, DevOps CI/ CD services, big data development, and cloud development services. So, if you are also looking for any of the web and app development services do not delay any further and contact OMR Digital now.
2 notes
·
View notes
Text
Silicon Wafer Market Will See Strong Expansion Through 2032
Allied Market Research, titled, “Silicon Wafer Market Size By Type, Wafer Size and Application: Global Opportunity Analysis and Industry Forecast, 2023-2032", the silicon wafer market was valued at $15.4 billion in 2022, and is estimated to reach $25.9 billion by 2032, growing at a CAGR of 5.4% from 2023 to 2032.
Silicon wafer is a material used for producing semiconductors, which can be found in all types of electronic devices that improve the lives of people. Silicon which is used in Silicon Substrate comes second as the most common element in the universe; it is mostly used as a semiconductor in the technology and electronic sector. This super-flat disk is refined to a mirror-like surface. Besides, it is also made of subtle surface irregularities which make it the flattest object worldwide. It is also extremely clean, free of impurities and microparticles, qualities that are essential in making it the perfect substrate material for modern semiconductors. Silicon wafer can be used in producing chips and microchips in electronic gadgets. Due to the uniqueness of the electrical currents via silicon wafers, these semiconductors are used in creating ICs (integrated circuits). The ICs act as commands for specific actions in various electronic devices. The silicon wafer market share is the main element in integrated circuits. Simply put, integrated circuits are a composite of a variety of electronic elements that are brought together to perform a particular function.
The semiconductor industry in silicon wafer industry has been a significant driver behind critical innovations in significant sectors like electronics, automobiles, and automation, with semiconductor technology emerging as the building block of all modern technologies. The advancements and innovations in this field are immediately impacting all downstream technologies. Foundries are increasingly investing in new advanced packaging techniques, especially silicon substrate based. Foundry vendors are researching improving transistor density with techniques like utilizing two-dimensional materials instead of silicon as the channel to develop Monolithic 3D Integrated Circuits. For instance, TSMC's chip on wafer on Substrate technology developed the world's largest silicon interposer that features room for two massive processors combined with 8 HBM memory devices in a package.
Meanwhile, the silicon wafer market demand is hindered by susceptibility to changes in delivery chain dynamics and fluctuations within the charges of raw uncooked materials. The creation of si wafer is predicated on obtaining high-purity silicon, and any disruptions inside the delivery chain, which includes shortages or geopolitical tensions affecting the accessibility of raw uncooked materials, can impact manufacturing costs and result in charge fluctuations. Moreover, the complicated production processes concerned with wafer production make it conscious of technological advancements, developing challenges for producers to hold competitiveness and adapt unexpectedly. These elements contribute to market unpredictability, influencing the growth and profitability of the SI Wafer enterprise.

However, a great possibility in the SI Wafer market arises from the increasing demand for superior semiconductor technology in numerous sectors. The rise of technologies which include 5G, synthetic intelligence, and the Internet of Things (IoT) is riding the demand for more sophisticated and compact electronic gadgets. This developing demand for high-performance and electricity-green semiconductor components is propelling the growth of the silicon wafer market size. In addition, the exploration of novel applications in electric vehicles, renewable strength, and clever devices complements the marketplace's capability. With ongoing technological progress, the silicon wafer enterprise is suitably located to enjoy the evolving panorama of electronic advancements.
The silicon wafer market segmentation is done on the basis of wafer size, type, end user, and region. By wafer size, the market is segmented into 1 to 100mm, 100 to 300mm and above 300mm. By type, the market is divided into P type and N type. As per end user, the market is segmented into consumer electronics, automotive, industrial, telecommunication and others.
By region, it is analyzed across North America (the U.S., Canada, and Mexico), Europe (UK, Germany, France, Russia and rest of Europe), Asia-Pacific (China, Japan, India, Australia, South Korea, and rest of Asia-Pacific), Latin America (Brazil, Argentina and rest of Latin America), and Middle East and Africa (UAE, Saudi Arabia, South Africa and rest of MEA).
KEY FINDINGS OF THE STUDY
The silicon wafer market growth projections is expected to be significantly in the coming years, driven by the increase in demand for secure communication.
The market is expected to be driven by innovations in significant sectors like electronics, automobiles, and automation.
The market is highly competitive, with several major players competing for market share. The competition is expected to intensify in the coming years as new players enter the market. The Asia-Pacific region is expected to be a major market for silicon wafer market due to increased investments in consumer electronics and automotive industries in the region.
Competitive analysis and profiles of the major silicon wafer market analysis, such as Shin-Etsu Handotai, Siltronic AG, SUMCO CORPORATION, SK Inc., Globalwafers Co. Ltd, GRINM Semiconductor Materials Co., Ltd., Okmetic, Wafer Works Corp., Addison Engineering, Inc., Silicon Materials, Inc. are provided in this report. Market players have adopted various strategies such as investment, agreement, and expansion, to expand their foothold in the silicon wafer market.
0 notes
Text
Mapping Digital Risk: Proactive Strategies to Secure Your Infrastructure
In an era where cyber threats evolve by the minute, organizations are no longer protected by firewalls and antivirus software alone. As businesses shift operations to the cloud, integrate third-party vendors, and support remote workforces, their digital footprint rapidly expands—creating a complex and often unmonitored exposure to potential attacks.
To combat this growing risk, cybersecurity professionals are turning to strategies that emphasize visibility and preemptive action. One of the most effective among these is Attack Surface Mapping, a modern approach to identifying and understanding every point in your infrastructure that could be targeted by cyber adversaries.

In this blog, we’ll explore how digital asset discovery, visibility enhancement, and risk-based prioritization work together to prevent threats before they strike. We’ll also examine how this technique aligns with broader cybersecurity practices like Security Vulnerability Assessment and Cyber Risk Assessment.
Understanding the Digital Attack Surface
Your attack surface consists of every digital asset—internal or external—that can be accessed or exploited by attackers. This includes:
Web applications and APIs
Cloud services and storage
Email servers and VPNs
Remote employee devices
IoT systems and smart hardware
Shadow IT and forgotten assets
Each of these components is a potential entry point. What makes the situation more dangerous is that many organizations do not have full visibility into all their assets—especially those managed outside of core IT oversight.
Even a single misconfigured database or unpatched API can open the door to significant damage, including data theft, ransomware attacks, and regulatory fines.
The Power of Visibility
You can’t protect what you can’t see. That’s the principle driving Attack Surface Mapping. It’s the process of discovering, inventorying, and analyzing all possible points of exposure across an organization’s network.
When conducted properly, it provides cybersecurity teams with a holistic view of their infrastructure, including systems they may not even know exist—like forgotten development servers or expired subdomains still publicly visible.
This visibility becomes a critical first step toward proactive defense. It allows teams to answer key questions like:
What assets are accessible from the internet?
Are any of them vulnerable to known exploits?
How do these systems interact with critical business functions?
Do any assets fall outside standard security policies?
The Risks of an Unmapped Environment
Failing to monitor your full attack surface can lead to costly consequences. Many high-profile breaches—including those impacting large enterprises and governments—have stemmed from unsecured third-party services or neglected systems that were never properly inventoried.
Consider these real-world scenarios:
A company leaves a cloud storage bucket publicly accessible, exposing millions of records.
A development tool is installed on a production server without proper access controls.
An expired domain continues to route traffic, unknowingly creating a phishing vector.
Each of these incidents could have been prevented with proper asset discovery and mapping. Attack Surface Mapping does more than illuminate these gaps—it enables immediate remediation, helping security teams stay ahead of attackers.
How Modern Attack Surface Mapping Works
Modern mapping involves a combination of automation, AI, and continuous monitoring to detect changes across internal and external assets. Here’s how it works:
1. Discovery
The first step is scanning your environment for known and unknown assets. Tools search DNS records, IP blocks, cloud infrastructure, and open ports to identify everything connected to your network.
2. Classification
Next, each asset is classified by function and risk level. This helps prioritize what needs protection first—customer-facing applications, for example, typically take precedence over internal testing tools.
3. Analysis
Security teams examine the asset's current state: Is it updated? Is encryption active? Are credentials securely managed? These evaluations determine the threat level of each asset.
4. Visualization
Mapping tools often provide visual dashboards to illustrate connections and vulnerabilities. This makes it easier to present findings to stakeholders and plan effective security strategies.
Integrating with Security Vulnerability Assessment
Once you've identified and mapped your digital assets, the next logical step is conducting a Security Vulnerability Assessment. This involves scanning systems for known flaws—outdated software, weak credentials, misconfigured firewalls, and more.

While mapping identifies where your assets are and how they’re exposed, vulnerability assessments determine how secure they are. The two processes work hand-in-hand to create an actionable plan for remediation.
Prioritizing these vulnerabilities based on potential business impact ensures that your cybersecurity resources are focused on fixing what matters most.
The Business Case: Cyber Risk Assessment
Mapping and vulnerability detection are foundational, but they gain even more value when paired with a Cyber Risk Assessment. This process evaluates how specific cyber threats could impact your business objectives.
For example, a vulnerability in a database holding customer information might carry more risk than one in a test server with no sensitive data. By assessing the financial, reputational, and operational impacts of different threats, businesses can make informed decisions about where to invest in security.
When done well, this integrated approach ensures that your cybersecurity efforts align with your overall risk tolerance, regulatory requirements, and organizational goals.
Continuous Monitoring: Why One-Time Scans Aren’t Enough
The modern digital environment changes rapidly. New tools are deployed, employees install apps, cloud configurations shift, and partners update their software. That’s why a one-time asset inventory won’t cut it.
Attack surfaces are dynamic, and so must be your response. Continuous monitoring ensures that any changes—intentional or otherwise—are detected in real time. This proactive approach shortens the window between exposure and response, dramatically reducing the likelihood of successful exploitation.
Additionally, continuous monitoring helps with:
Compliance: Meeting frameworks like NIST, ISO 27001, and GDPR
Audit readiness: Demonstrating asset visibility and risk control
Incident response: Accelerating triage with real-time intelligence
Tools That Support Attack Surface Visibility
Several technologies are helping organizations master their digital terrain:

Together, these tools support not just discovery, but dynamic risk management.
Real-World Impact: A Case Study
Let’s consider a healthcare provider that implemented an Attack Surface Mapping solution. Within days, the team discovered a forgotten subdomain pointing to an outdated web app.
Further investigation revealed that the app was no longer in use, but still hosted login pages and retained backend database access. The team took it offline, avoiding a potential data breach involving patient records.
This simple intervention—based on visibility—saved the organization from costly legal and reputational consequences. And it all began with knowing what assets they had.
Building an Actionable Framework
To turn discovery into action, organizations should adopt the following framework:
Map Everything – From on-prem to the cloud to third parties.
Assess Risk – Rank assets by exposure and business impact.
Fix What Matters – Use automation where possible to patch or retire vulnerable systems.
Monitor Continuously – Update maps and alerts in real time.
Communicate Findings – Ensure leadership understands the risks and supports investment in mitigation.
By embedding this process into your ongoing operations, you create a culture of cyber hygiene and risk awareness that protects your organization long-term.
Conclusion
Today’s attackers are fast, persistent, and opportunistic. They scan the internet daily for low-hanging fruit—misconfigured servers, exposed APIs, forgotten databases. Organizations that lack visibility into their own infrastructure often become easy targets.
But there is a better path. Through a strategic blend of Attack Surface Mapping, vulnerability assessment, and risk analysis, businesses can identify and eliminate their weak points before attackers exploit them.
At DeXpose, we help organizations illuminate their entire digital environment, providing the insights they need to act decisively. Because the first step in stopping a breach—is knowing where one might begin.
1 note
·
View note
Text
Envision Port Management Information Systems
Through adoption of these technologies, ports will be able to place themselves as key nodes in the international value chain for trade, driving economic growth and aiding global commerce. Continued evolution of smart port solutions will increasingly change maritime logistics in the future, with potential for further innovation and partnership.

Simply put, port management information systems integration is not just technology; it's about creating a more efficient, sustainable, and secure seaborne trade future. By embracing digitalization in the port and the use of smart, comprehensive port solutions, ports can optimize their potential to help shape a more interconnected, prosperous world economy. This paper explores the building blocks, the technological backbone, implementation advantages, and the trend-setting in PMIS, bringing forth a total vision for maritime logistics of the future.
The Dawn of Intelligent Port Solutions: A New Frontier of Efficiency
Intelligent port solutions are an unprecedented transformation in the way that ports function, leveraging digital technology to develop clever and integrated systems. Intelligent port solutions maximize each aspect of port operations, including vessel scheduling and cargo handling through to security and sustainability. In adopting intelligent port solutions, ports can minimize cost, enhance capacity, and develop their competitive positioning in the world market.
Growing demand for efficient and sustainable supply chains drives smart port solution consumption. Smart port solutions provide instant visibility into port activities, making it possible for data-driven decisions and pre-emptive management of resources. With the incorporation of innovative technologies such as IoT, AI, and cloud computing, smart port solutions reinvent traditional ports into agile and reactive world trade hubs. The adoption of smart port solutions is not just a technological advancement but a strategic necessity for ports looking to succeed in the contemporary maritime environment.
Core Components of Modern Port Management Systems
Contemporary PMIS systems are designed upon a modular framework, where every module caters to unique port operations and harmoniously aligns with others to create an integrated, coherent port environment. The modules function together to yield a holistic outlook of port operations, allowing effective management and optimal performance.
1. Intelligent Vessel and Terminal Management Systems
Artificial intelligence-based port management systems streamline berth allocation, minimizing vessel waiting time and maximizing terminal capacity. The systems consider multiple factors, such as vessel size, cargo type, arrival time, and operating priorities, to allocate berths in a rational and efficient manner to reduce congestion. Real-time monitoring of port operations allows ports to monitor vessel movement constantly, thereby improving maritime safety and resource planning. Utilization of AI-based port management ensures that ports become capable of handling growing vessel traffic without sacrificing operation efficiency and security.
2. Simplified Cargo Handling and Logistic Solutions
IoT terminals and port applications enable the automated handling of cargo through the use of technology like RFID tags, sensors, AGVs, and ASCs. These technologies make cargo processing easier, reduce manual handling of cargo, and minimize errors. Machine learning in maritime logistics optimizes cargo forecast and demand estimation by considering historical shipping patterns, economic indicators, and market trends. This forecasting ability allows ports to streamline cargo assignment, decrease empty container transfer, and enhance general logistics management. Combining IoT for terminals and ports and machine learning for maritime logistics produces an uninterrupted and efficient cargo process.
3. Trade Facilitation and Regulatory Platforms
A solid port community system (PCS) unites all participants, including terminal operators, customs agencies, A robust port community system (PCS) brings together all the players, such as terminal operators, customs houses, shipping lines, transport companies, and regulatory authorities. The system enables efficient communication, improves coordination, and reduces paperwork. Trade facilitation platforms simplify regulatory procedures, eliminate delays, and enhance trade flows. Customs clearance software accelerates regulatory compliance processes, enabling goods to transit borders quickly and efficiently. Port community system is one platform for all port operations, enhancing transparency and facilitating cooperation among stakeholders. This smooth communication is essential for effective port digitalization.
4. Preemptive Resource and Asset Management
Predictive maintenance of port equipment takes advantage of data analytics and machine learning to anticipate when equipment breakdowns may happen. By examining sensor data from the equipment within a port, such systems are able to identify patterns that indicate potential failure and schedule maintenance ahead of time. This serves to reduce equipment downtime, reduce maintenance costs, and extend the life of major assets. Predictive maintenance applied to port assets ensures that ports can maintain optimal operational efficiency and avoid costly downtime. Predictive maintenance is critical in the context of sustainable and effective port digitalization.
Technological Pillars of the Smart Port Era
A few technologies at the forefront of PMIS development and facilitating smart port solutions include:
The Internet of Things (IoT)
IoT for terminals and ports is the foundation of smart port infrastructure. Sensors continually scan equipment conditions, environmental conditions, cargo movements, and security conditions, producing enormous amounts of data. It is sent to central systems where it is processed to offer real-time port operations monitoring and management. IoT deployment in ports and terminals increases transparency in all areas of port operations, providing data-driven decision-making and proactive resource management. Smooth fusion of IoT at ports and terminals is critical in order to experience real port digitalization.
Artificial Intelligence (AI) and Machine Learning (ML)
AI-driven port management provides revolutionary features across various functional areas. Be it automated handling of cargo, security augmentation, AI simplifies processes, increases precision, and minimizes error. Maritime logistics machine learning processes enormous datasets from multiple sources, such as sensor data, shipping history data, weather outlooks, and market data. By analyzing the data, ports can forecast demand, streamline resource allocation, and prepare for prospective disruptions. Machine learning in maritime logistics and port management using artificial intelligence is changing the way port operations are run, making it more efficient and resilient maritime networks.
Data Analytics and Information Sharing
Maritime logistics data analytics converts raw operational data into actionable intelligence. The analytics inform dashboards that deliver key performance indicators (KPIs), which port authorities use to make educated decisions and track performance against strategic goals. An effective maritime data exchange platform guarantees stakeholders to receive relevant information while data remains safe and private. Data analytics in maritime logistics is critical for maximizing port operations, improved decision-making, and overall efficiency. Data-driven approaches are the essence of effective port digitalization.
Intelligent Automation for Ports
Smart port automation for ports is changing the way that ports are being run. Automatic guided vehicles (AGVs), robotic cranes, and automatic stacking cranes (ASCs) make handling cargo easier, lower labor expenses, and improve throughput. Port smart automation is not only efficient but also helps to save on safety as a result of lowered human engagement with risky jobs. Smart port automation for ports is a prime catalyst for smart port solutions and is a source for sustainable maritime logistics.
Advantages of Adopting Sophisticated Port Systems
Embracing overall port authority solutions brings numerous advantages:
Improved Operating Efficiency and Productivity
intelligent automation of ports minimizes manual processes, reduces human error, and accelerates cargo handling. Real-time monitoring of port operations enables quick response to evolving situations, and AI-based port management optimizes resource usage and terminal utilization. These improvements lead to increased throughput, reduced vessel turnaround times, and overall improved operational efficiency. Greater efficiency translates into significant real-time port operations improvements.
Lower Costs and Higher Revenue
Port operations automation using smart port solutions reduces labor costs, minimizes maintenance costs, and maximizes energy consumption. Predictive maintenance of port equipment prolongs asset lifecycles, minimizing capital expenditure needs. Increased operational efficiency generates higher throughput, leading to additional revenue and enhanced profitability. This economic advantage is a major impetus for port digitalization.
Better Security and Better Compliance
Sophisticated port community system platforms enhance security procedures, advance access control, and increase threat detection capabilities. Trade documentation automation minimizes regulatory filing errors, whereas customs clearance software accelerates goods movement across borders. These initiatives enhance compliance with global regulations and increase port operation security. Secure and compliant environments are needed to ensure trust and enable trade in the connected port ecosystem.
Increased Environmental Sustainability
Smart Smart port solutions contribute significantly to environmental sustainability by maximizing energy use, reducing emissions, and promoting green logistics strategies. Improved resource management through port digitalization minimizes the environmental footprint of port operations in line with global sustainability targets. Ports are more committed to the deployment of sustainable smart port solutions for decreasing their environmental impact and the development of a greener future.
Challenges and Future Directions
While the benefits of PMIS are immense, implementation of the systems is plagued with several issues. Integration with the existing infrastructures, cyber-security concerns, handling organizational change, and seeking proper investment call for meticulous planning and implementation. Solving such challenges requires the development of strategic intervention in facing port digitalization with a focus on interoperability, security, stakeholder participation, and visibility on return on investment (ROI).
The future of PMIS involves even greater integration, intelligence, and automation. Autonomous operations, blockchain usage for increased transparency and security, and intelligent analytics for predictive analysis will keep transforming port operations. Through adoption of these technologies, ports will be able to place themselves as key nodes in the international value chain for trade, driving economic growth and aiding global commerce. Continued evolution of smart port solutions will increasingly change maritime logistics in the future, with potential for further innovation and partnership.
Simply put, port management information systems integration is not just technology; it's about creating a more efficient, sustainable, and secure seaborne trade future. By embracing digitalization in the port and the use of smart, comprehensive port solutions, ports can optimize their potential to help shape a more interconnected, prosperous world economy.
#ports#maritime#terminals#ai powered solutions#container#management#smart ports#artificial intelligence#envision#logistics#technology#digital transformation
0 notes
Text
Enhancing Efficiency: Key Components in Industrial Automation
In today's dynamic industrial landscape, automation serves as the bedrock for efficiency, safety, and sustainable progress. At Dropship Automation, we specialize in delivering premier automation components crucial for optimizing operations across diverse industries. In this blog, we delve into three essential components vital for any automation setup: pressure gauges, recorders, and electronic components. Whether you're upgrading existing systems or initiating new installations, understanding these components is essential for achieving peak operational performance.
1. Pressure Gauges: Precision Monitoring for Operational Control
What are Pressure Gauges in Automation? Pressure gauges are instruments designed to measure and display pressure levels within industrial processes. They provide critical data for monitoring and controlling operational parameters.
Key Types and Applications:
Types: Mechanical gauges, digital gauges
Applications: Hydraulic systems, pneumatic machinery, gas pipelines
Benefits: Accurate pressure measurement, real-time monitoring, system diagnostics
Why Pressure Gauges Matter: Accurate pressure monitoring is crucial for maintaining operational efficiency and safety in industrial environments. Pressure gauges enable proactive maintenance, prevent equipment failures, and optimize process control, contributing to overall system reliability and performance.
2. Recorders: Essential Tools for Data Acquisition
What are Recorders in Automation? Recorders are devices used to capture and store data from various sensors and instruments within automation systems. They facilitate detailed analysis and decision-making processes.
Key Features and Importance:
Types: Data loggers, chart recorders
Functions: Continuous data acquisition, historical trend analysis
Applications: Environmental monitoring, quality control, process optimization
Why Recorders Matter: Recorders play a pivotal role in gathering and analyzing operational data, enabling informed decisions and predictive maintenance. They enhance operational visibility and efficiency by providing comprehensive insights into system performance over time.
3. Electronic Components: Building Blocks of Automation Systems
What are Electronic Components in Automation? Electronic components are fundamental units that form the backbone of automation systems, enabling seamless integration and functionality.
Key Components and Applications:
Types: Sensors, actuators, relays
Functions: Signal processing, control logic, interface connectivity
Applications: Control panels, robotic systems, industrial IoT
Why Electronic Components Matter: Electronic components facilitate precise control and communication within automation setups. They enable efficient signal processing, automation logic implementation, and interface connectivity, thereby optimizing system performance and reliability.
How These Components Collaborate for Seamless Automation
Imagine an industrial scenario:
Pressure gauges ensure optimal operational conditions by monitoring critical parameters.
Recorders capture data from sensors, enabling detailed analysis and proactive maintenance.
Electronic components integrate seamlessly to control processes and enhance system efficiency.
Conclusion
Automation revolutionizes industrial processes by boosting efficiency, ensuring safety, and fostering sustainable growth. By integrating essential components like pressure gauges, recorders, and electronic units, industries can achieve heightened productivity, minimized downtime, and elevated safety standards.
At Dropship Automation, we are committed to delivering cutting-edge automation solutions tailored to your specific needs. Explore our extensive range of automation parts or contact us for personalized consultation and support on your automation journey.
0 notes
Text
Internet of Things (IOT) can be defined as everyday objects’ networked interconnection that are normally seen a sensors’ self -configuring wireless network for interconnecting all ‘things’ (see Appendix One). Nowadays, the world completely relies on information offered on the internet that is captured through text or by taking images. Evidently, this outlines the major participation of people in gathering information. Still, involving people can result in some problems considering that they have less accuracy and limited time, which results in inconsistent and inappropriate data. Therefore, there is a need for a system that can automatically capture and transfer data to the internet devoid of any human to machine interaction. Therefore, the IoT is a state whereby there is a connection of all ‘things’ in the internet sensors for management as well as intelligent identification. Such things according to Bhabad and Bagade (2015, p.1) when offered with unique identifiers may be read using radio-frequency identification (RFID) tags together with information sensing devices (sensors). Therefore, the thing in the IoT could be a human being having a heart for monitoring an implant, a car with in-built sensors that monitors the pressure and alert the driver when it is low, or other manufactured objects having a unique Internet Protocol (IP) address that can be connected to the network to facilitate transfer. Basically, the increasing utilisation of IoT system creates the need for powerful protection against any potential vulnerability or attacks. 1.1 Background Given that the nodes of IoT are of low communication speed, less computation power, low storage, and naturally heterogeneous, it requires forward and backward secrecy, smooth control of the data access, confidentiality, integrity, and scalable security algorithms. The phrase ‘security’ normally involves different concepts; for instance, security connotes the basic security services provision, which involves availability, confidentiality, non-repudiation, authorisation, integrity as well as authentication. Such services could be implemented through various cryptographic mechanisms, like signature algorithms, hash functions, or block ciphers. All of the aforementioned mechanisms need a solid infrastructure for key management so as to manage the needed cryptographic keys. However, in the IoT context, security should focus on both the needed security services and how the services would be achieved in the entire system as well as how to execute the security functionalities. Even though security considerations have been there in the IT context, the features of various IoT executions bring about unique and new security challenges. Therefore, managing such challenges and making sure IoT services and products are protected should be the main priority. The IoT devices as well as the associated data services should be protected from vulnerabilities, particularly because this technology has turned out to be pervasive and integrated and pervasive into people’s day-to-day lives. This research report focus challenges in IoT with focus on the security perspective. The report determines how security challenges in IoT can be managed in the present and future systems. Using a document analysis research method, the existing IoT devices have been analysed with the objective of creating a clear, perceptible depiction of the challenges as well as solutions existing in the IoT today. 1.2 Significance This research report is important because it creates a perceptible picture of the security challenges in the IoT. The report shows why it is essential to implement security features in the IoT systems, even if the features stretch the devices’ capabilities. It is exceedingly challenging to automate key managemen Read the full article
0 notes
Text
What Is Firmware Development?

In today’s increasingly connected world, embedded systems power everything from smart home devices to medical equipment and automotive technology. At the heart of these systems lies firmware development—a specialized field that ensures devices run smoothly, efficiently, and securely. If you're building any smart or electronic product, understanding firmware and investing in expert firmware development is key to delivering performance, reliability, and innovation.
What Is Firmware?
Firmware is a type of software that provides low-level control over a device's hardware. Unlike traditional software applications, firmware resides in the device’s memory (often in ROM, flash, or EEPROM) and interfaces directly with the hardware components.
Firmware is what tells a device how to operate, boot, and respond to external commands. It’s typically involved in controlling:
Microcontrollers (MCUs)
Sensors
Actuators
Display modules
Communication modules (e.g., Wi-Fi, Bluetooth)
Because of its vital role, firmware development is an essential part of the embedded systems lifecycle.
What Is Firmware Development?
Firmware development is the process of designing, programming, testing, and maintaining the firmware that controls electronic hardware. Developers work at the intersection of hardware and software, writing code that interacts directly with microprocessors and chipsets.
This type of development typically involves:
Selecting the right microcontroller or system-on-chip (SoC)
Programming in low-level languages like C, C++, or Assembly
Interfacing with hardware peripherals
Real-time operating system (RTOS) integration
Debugging and testing using tools like JTAG, oscilloscopes, or logic analyzers
Updating and maintaining firmware post-deployment
Well-executed firmware development ensures that devices are not only functional, but also stable, efficient, and secure.
Why Firmware Development Is Crucial
In a world driven by smart technology, firmware development plays a critical role in the success of a product. Here’s why:
1. Optimized Performance
Firmware directly controls hardware operations. Efficient firmware code leads to faster processing, lower power consumption, and improved user experience.
2. Hardware Integration
Firmware allows software and hardware to communicate seamlessly. Whether it’s a smart thermostat or a medical device, firmware development ensures that components such as sensors, motors, and displays function correctly.
3. Product Reliability
Poorly written firmware can result in device malfunctions, crashes, or safety issues. Reliable firmware ensures devices perform predictably under various conditions.
4. Security
Many cyberattacks target firmware vulnerabilities. Secure firmware development practices, including encryption and authentication, are essential to protect devices and user data.
5. Upgradability
Modern devices often require firmware updates to fix bugs or add features. Proper firmware development includes designing systems that support over-the-air (OTA) updates without bricking the device.
Industries That Rely on Firmware Development
The demand for skilled firmware development is booming across various sectors:
Consumer electronics (smartphones, smart TVs, wearables)
Automotive (ADAS, electric vehicles, infotainment systems)
Industrial automation (IoT sensors, PLCs, robotics)
Healthcare (wearable monitors, infusion pumps, diagnostic devices)
Telecommunications (network hardware, routers, modems)
Aerospace and defense (navigation systems, avionics)
Whether it’s a smartwatch or a life-saving medical device, firmware is often the unseen hero behind the scenes.
Best Practices in Firmware Development
To ensure a successful project, firmware developers follow a structured approach:
Clear hardware documentation: Understand the chipset’s datasheets and schematics before writing code.
Modular design: Create reusable and maintainable code blocks.
Version control: Use Git or SVN to track changes and collaborate efficiently.
Automated testing: Implement unit tests and simulation environments to catch bugs early.
Debugging tools: Use debuggers and analyzers to test real-world behavior.
Code optimization: Ensure the code is fast, power-efficient, and small in memory footprint.
Partnering with experienced firmware developers is essential to bring a hardware product to life without delays or technical setbacks.
The Future of Firmware Development
As more industries adopt IoT, artificial intelligence, and edge computing, firmware development is becoming even more critical. We’re seeing trends like:
AI-powered firmware for smart decision-making
Increased emphasis on security and firmware-level encryption
Remote firmware updates through cloud platforms
Low-power firmware for battery-dependent IoT devices
Staying on top of these trends can give your business a competitive advantage in delivering cutting-edge, reliable technology.
Conclusion
Firmware development is the backbone of modern electronics, enabling smart devices to operate safely, efficiently, and intelligently. From prototyping to production and post-launch updates, investing in expert firmware development is crucial for any business building connected hardware.
Whether you're launching a new product or improving an existing one, working with skilled firmware developers can save time, reduce costs, and ensure your technology stands out in a crowded market.
0 notes
Text
What Is Firmware Development?

In today’s increasingly connected world, embedded systems power everything from smart home devices to medical equipment and automotive technology. At the heart of these systems lies firmware development—a specialized field that ensures devices run smoothly, efficiently, and securely. If you're building any smart or electronic product, understanding firmware and investing in expert firmware development is key to delivering performance, reliability, and innovation.
What Is Firmware?
Firmware is a type of software that provides low-level control over a device's hardware. Unlike traditional software applications, firmware resides in the device’s memory (often in ROM, flash, or EEPROM) and interfaces directly with the hardware components.
Firmware is what tells a device how to operate, boot, and respond to external commands. It’s typically involved in controlling:
Microcontrollers (MCUs)
Sensors
Actuators
Display modules
Communication modules (e.g., Wi-Fi, Bluetooth)
Because of its vital role, firmware development is an essential part of the embedded systems lifecycle.
What Is Firmware Development?
Firmware development is the process of designing, programming, testing, and maintaining the firmware that controls electronic hardware. Developers work at the intersection of hardware and software, writing code that interacts directly with microprocessors and chipsets.
This type of development typically involves:
Selecting the right microcontroller or system-on-chip (SoC)
Programming in low-level languages like C, C++, or Assembly
Interfacing with hardware peripherals
Real-time operating system (RTOS) integration
Debugging and testing using tools like JTAG, oscilloscopes, or logic analyzers
Updating and maintaining firmware post-deployment
Well-executed firmware development ensures that devices are not only functional, but also stable, efficient, and secure.
Why Firmware Development Is Crucial
In a world driven by smart technology, firmware development plays a critical role in the success of a product. Here’s why:
1. Optimized Performance
Firmware directly controls hardware operations. Efficient firmware code leads to faster processing, lower power consumption, and improved user experience.
2. Hardware Integration
Firmware allows software and hardware to communicate seamlessly. Whether it’s a smart thermostat or a medical device, firmware development ensures that components such as sensors, motors, and displays function correctly.
3. Product Reliability
Poorly written firmware can result in device malfunctions, crashes, or safety issues. Reliable firmware ensures devices perform predictably under various conditions.
4. Security
Many cyberattacks target firmware vulnerabilities. Secure firmware development practices, including encryption and authentication, are essential to protect devices and user data.
5. Upgradability
Modern devices often require firmware updates to fix bugs or add features. Proper firmware development includes designing systems that support over-the-air (OTA) updates without bricking the device.
Industries That Rely on Firmware Development
The demand for skilled firmware development is booming across various sectors:
Consumer electronics (smartphones, smart TVs, wearables)
Automotive (ADAS, electric vehicles, infotainment systems)
Industrial automation (IoT sensors, PLCs, robotics)
Healthcare (wearable monitors, infusion pumps, diagnostic devices)
Telecommunications (network hardware, routers, modems)
Aerospace and defense (navigation systems, avionics)
Whether it’s a smartwatch or a life-saving medical device, firmware is often the unseen hero behind the scenes.
Best Practices in Firmware Development
To ensure a successful project, firmware developers follow a structured approach:
Clear hardware documentation: Understand the chipset’s datasheets and schematics before writing code.
Modular design: Create reusable and maintainable code blocks.
Version control: Use Git or SVN to track changes and collaborate efficiently.
Automated testing: Implement unit tests and simulation environments to catch bugs early.
Debugging tools: Use debuggers and analyzers to test real-world behavior.
Code optimization: Ensure the code is fast, power-efficient, and small in memory footprint.
Partnering with experienced firmware developers is essential to bring a hardware product to life without delays or technical setbacks.
The Future of Firmware Development
As more industries adopt IoT, artificial intelligence, and edge computing, firmware development is becoming even more critical. We’re seeing trends like:
AI-powered firmware for smart decision-making
Increased emphasis on security and firmware-level encryption
Remote firmware updates through cloud platforms
Low-power firmware for battery-dependent IoT devices
Staying on top of these trends can give your business a competitive advantage in delivering cutting-edge, reliable technology.
Conclusion
Firmware development is the backbone of modern electronics, enabling smart devices to operate safely, efficiently, and intelligently. From prototyping to production and post-launch updates, investing in expert firmware development is crucial for any business building connected hardware.
Whether you're launching a new product or improving an existing one, working with skilled firmware developers can save time, reduce costs, and ensure your technology stands out in a crowded market.
0 notes
Text
Exploring the Functional Blocks of IoT

In the fascinating realm of #IoT, diverse devices seamlessly connect, driven by a network of functional blocks. 🔄 Let's dive into the microcosm of these blocks!
1️⃣ Sensors & Actuators: The heartbeat of IoT, sensors gather data, while actuators enable real-world actions. 📊💡
2️⃣ Connectivity Layer: Bridging the digital and physical, this layer ensures devices communicate flawlessly. 📡🔗
3️⃣ Data Processing: Raw data becomes valuable insights through processing, ensuring efficiency and relevance. ⚙️📈
4️⃣ Edge Computing: Empowering devices to process data locally, reducing latency and enhancing responsiveness. 🌐💻
5️⃣ Cloud Computing: A vast ecosystem where data is stored, analyzed, and services are managed on a global scale. ☁️🖥️
6️⃣ Security & Privacy: Fortifying the IoT ecosystem, ensuring data integrity, and safeguarding user privacy. 🔒🔐
7️⃣ User Interface (UI) & Experience (UX): Making technology user-friendly and accessible for seamless interaction. 🖥️🤝
8️⃣ Analytics & Insights: Unveiling patterns and trends, transforming raw data into actionable intelligence. 📊🔍
Embracing these functional blocks, the IoT landscape flourishes, intertwining the digital and physical worlds.
0 notes
Text
How Does AI Agent Development for Local Plugin-Based System Enhance Performance?

In recent years, artificial intelligence has transformed how we interact with technology, particularly with the rise of autonomous AI agents capable of performing complex tasks with minimal human intervention. A particularly promising and flexible approach in this domain is AI Agent Development for Local Plugin-Based System. This approach not only enhances user control and data privacy but also offers a scalable and customizable framework suitable for diverse applications ranging from personal assistants to industrial automation.
Let’s explore what this development approach entails, its architecture, benefits, use cases, and the steps to build one.
Understanding the Concept: What is a Local Plugin-Based System?
Before diving into AI agent development itself, it’s essential to understand the concept of a plugin-based system.
A plugin-based system allows software functionalities to be extended dynamically through independently developed modules called plugins. These plugins act like modular building blocks that integrate with the main software without altering its core codebase. When this system is run locally—i.e., on a user's machine rather than on a centralized server—it gives users control over their data and application behavior.
Combining this plugin architecture with AI agents allows developers to create intelligent, modular, and extensible systems that can be customized according to specific workflows.
Core Components of a Local Plugin-Based AI Agent System
To effectively build such a system, developers must understand its core components:
1. AI Agent Core
This is the brain of the system. It includes:
Natural Language Processing (NLP): Understands and interprets human input.
Task Planning & Execution: Uses logic and possibly machine learning to make decisions and act on commands.
Memory Module: Stores past interactions and learns user preferences over time.
2. Plugin Interface Layer
This acts as the communication bridge between the AI core and plugins. It should support:
Plugin discovery and registration
API standardization (so the AI can interact with various plugins uniformly)
Permission management for plugin access
3. Local Plugin Modules
These are functional blocks that can be developed to do specific tasks like:
Sending emails
Managing files
Fetching weather data
Automating spreadsheet workflows
Each plugin typically includes:
A manifest file (describing metadata and capabilities)
Executable code
Input/output schemas for interoperability with the AI core
Benefits of Local Plugin-Based AI Agents
Developing AI agents using a local plugin-based model brings significant advantages:
1. Enhanced Privacy
All processes occur on the user’s machine, ensuring sensitive data never leaves local storage unless explicitly permitted.
2. Customization & Scalability
Users can enable, disable, or develop plugins tailored to their unique needs, resulting in a flexible, user-centric solution.
3. Offline Functionality
Since everything is local, the AI agent can function even without an internet connection—a critical advantage in industries with limited connectivity.
4. Security
A local system reduces the attack surface. Since the codebase and data reside locally, vulnerabilities associated with cloud storage and data breaches are mitigated.
Real-World Use Cases
1. Personal Productivity Agents
Imagine an AI assistant that can schedule meetings, manage to-do lists, summarize documents, and automate emails—all through locally installed plugins.
2. Enterprise Workflow Automation
Companies can deploy AI agents on employee machines to automate repetitive tasks (e.g., report generation, CRM updates), integrated with internal tools via custom plugins.
3. IoT Device Management
Smart home systems or factory automation setups can benefit from local AI agents controlling devices without needing cloud connectivity.
4. Healthcare Assistants
In clinics where patient data must remain confidential, a local AI agent can fetch records, summarize diagnostic information, and manage appointments without breaching compliance regulations.
Development Process: Building an AI Agent for Local Plugin-Based Systems
Step 1: Define Agent Capabilities
Start by outlining what tasks the agent should be able to perform. These may include voice command recognition, task execution, and contextual learning.
Step 2: Choose a Programming Language & Framework
Languages like Python, Rust, or Go are popular for building such systems due to their rich ecosystems and plugin support. Frameworks like LangChain, AutoGPT, and PrivateGPT can be adapted for local execution.
Step 3: Design the Plugin Interface
Create a standard communication protocol (such as RESTful APIs or local sockets) that plugins will use to talk with the AI core. Include permission and sandboxing mechanisms to ensure plugins cannot access unauthorized data.
Step 4: Build or Integrate Plugins
Start with a few core plugins—e.g., file system manager, email handler, or calendar integrator. Ensure each plugin has a manifest that describes its function, input parameters, and output format.
Step 5: Implement Natural Language Understanding
Use models like LLama 3, GPT-J, or BERT to process user queries. Fine-tune them locally for better privacy and performance. Link user inputs to plugin actions via a command parsing system or a prompt-based logic chain.
Step 6: Add Feedback & Learning Loops
Allow the agent to learn from user feedback. Incorporate reinforcement learning or basic rule-based improvement systems for better personalization over time.
Step 7: Testing & Debugging
Test the AI agent with different plugin combinations and edge cases. Ensure the system fails gracefully and handles user commands safely.
Challenges and Considerations
While this architecture is powerful, developers should keep a few challenges in mind:
Memory and Resource Usage: Local agents must be optimized to run efficiently on user machines with varying specs.
Plugin Compatibility: Managing dependencies and compatibility between plugins can become complex as the ecosystem grows.
Security Updates: A centralized update system may be lacking, so mechanisms for secure plugin updates and vulnerability scanning are crucial.
Future Outlook
The rise of open-source AI models, growing emphasis on data privacy, and increasing user demand for personalized tools indicate a strong future for local plugin-based systems. Moreover, with initiatives like Apple’s on-device AI push and Meta’s LLMs for offline devices, the groundwork is being laid for widespread adoption.
As AI continues evolving, plugin-based systems may become the norm for anyone wanting both flexibility and control in their digital environments.
Conclusion
As we move into an era where personalized automation is no longer a luxury but a necessity, the need for decentralized, intelligent, and modular systems becomes evident. AI Agent Development for Local Plugin-Based System presents a paradigm shift—one that empowers users with more control, better customization, and tighter security. By leveraging local resources and a flexible plugin framework, developers can create intelligent agents that are not only powerful but also respect user privacy and autonomy. The future of AI Agent Development lies in this balance of intelligence, adaptability, and local empowerment.
0 notes
Text
PLC Programming Using CODESYS: An In-Depth Exploration

Programmable Logic Controllers (PLCs) are foundational to industrial automation, providing the control necessary for machinery and processes across various industries. Among the myriad of PLC programming environments available, CODESYS stands out as a versatile and powerful platform. This article delves into the intricacies of PLC programming using CODESYS, its adherence to the IEC 61131-3 standard, fieldbus support, IoT connectivity, and the services offered by Servotech Inc. in this domain.
Understanding CODESYS
CODESYS is a commercial PLC programming tool and real-time software platform designed for PLCs and embedded controllers. It offers a comprehensive suite of features that facilitate the development, testing, and deployment of control applications. One of its notable strengths is its manufacturer-independent nature, allowing engineers to program controllers from various vendors using a unified interface.
Adherence to IEC 61131-3 Standard
The IEC 61131-3 standard defines the programming languages and structures for PLCs, promoting consistency and interoperability across different systems. CODESYS supports all five languages outlined in this standard:
Instruction List (IL): An assembler-like language for low-level programming.
Structured Text (ST): A high-level, Pascal-like language suitable for complex algorithms.
Ladder Diagram (LD): A graphical language resembling electrical relay logic diagrams, widely used for its intuitive representation.
Function Block Diagram (FBD): A graphical language that uses blocks to represent functions and their interconnections.
Sequential Function Chart (SFC): A graphical language for depicting sequential control processes.
By adhering to this standard, CODESYS ensures that engineers can transition between different PLC hardware platforms without the need to learn new programming environments, thereby enhancing efficiency and reducing training costs.
Fieldbus Support in CODESYS
Fieldbus systems are critical for enabling communication between various components in an industrial setup. CODESYS provides extensive support for multiple fieldbus protocols, including:
EtherCAT: A high-performance Ethernet-based fieldbus system suitable for real-time control applications.
CAN Bus (CANopen, J1939): Widely used in automotive and industrial applications for robust communication.
Modbus: A serial communication protocol prevalent in connecting industrial electronic devices.
PROFIBUS: A standard for fieldbus communication in automation technology.
This extensive fieldbus support allows for seamless integration of various devices and systems, facilitating the development of complex automation solutions.
IoT Connectivity with CODESYS
In the era of Industry 4.0, the integration of IoT (Internet of Things) capabilities into industrial automation systems is paramount. CODESYS offers robust IoT connectivity features, enabling:
Remote Monitoring and Control: Access and control PLCs from remote locations, enhancing flexibility and responsiveness.
Data Logging and Analysis: Collect and analyze data from various sensors and devices to optimize processes and predict maintenance needs.
Cloud Integration: Seamlessly connect with cloud platforms for data storage, processing, and advanced analytics.
These IoT capabilities empower industries to implement smart manufacturing practices, leading to increased efficiency and reduced operational costs.
Servotech Inc.: Expertise in CODESYS PLC Programming
Servotech Inc. is a leading provider of PLC programming services utilizing the CODESYS platform. Their team of experienced engineers offers comprehensive solutions, including:
Custom PLC Application Development: Tailored solutions to meet specific automation requirements across various industries.
System Integration: Seamless integration of PLCs with existing hardware and software systems, ensuring optimal performance.
Training and Support: Providing clients with the knowledge and tools necessary to maintain and expand their automation systems effectively.
By leveraging CODESYS's versatile platform, Servotech Inc. delivers robust and scalable automation solutions that adhere to international standards.
Conclusion
PLC programming by Servotechinc using CODESYS offers a flexible and standardized approach to industrial automation. Its compliance with the IEC 61131-3 standard, extensive fieldbus support, and IoT connectivity make it a preferred choice for engineers and organizations aiming to develop sophisticated control systems. Servotech Inc.'s expertise in utilizing CODESYS further enhances the potential for creating customized, efficient, and future-ready automation solutions
#PLCProgramming#IndustrialAutomation#CODESYS#AutomationEngineering#SmartManufacturing#EmbeddedSystems#IndustrialControl#FactoryAutomation#IoTIntegration#ControlSystems
0 notes
Text
Electronic Components Market Will See Strong Expansion Through 2032
Allied Market Research, titled, “Electronic Components Market by Type and Application: Global Opportunity Analysis and Industry Forecast, 2024-2032." The electronic components market was valued at $0.6 trillion in 2023 and is estimated to reach $1.0 trillion by 2032, growing at a CAGR of 6.9% from 2024 to 2032.
The market for electronics components is made up of a rich variety of fundamental devices that are indispensable for electrical circuitry and functionality. Such elements consist of integrated circuits, resistors, capacitors, transistors, sensors, diodes as well as optoelectronic devices among others. They can be utilized as the basic building blocks of electronic systems in different sectors including automotive, consumer electronics, healthcare, and telecommunications. This continuous innovation is driven by technological advancements leading to smaller, faster, and more efficient components. The growing demand for connected devices, Internet of Things (IoT) solutions, and renewable energy systems dominates the market. On the other hand, supply chain disruptions among other challenges indicate that the electronic components market trends will continue experiencing steady growth triggered by sustained technological improvements coupled with changing customer preferences.
The expansion of electronic parts is driven by an increasing number of people moving to cities and the growth of smart cities globally. Urbanization has led to increased traffic congestion, security threats, and information gaps due to the increased number of urban dwellers. As a result, smarter city initiatives employ ICT approaches for improved urban transport systems, interconnectivity infrastructures as well as better services. Among these options that have been designed, electronic components are particularly important in this regard; ensuring all social amenities continue with their operations even during the night hours. These signs can send messages in real-time, provide navigation support, send emergency alerts, or produce advertisements thereby preventing disappearance from towns and cities throughout the whole day. For example, such technologies can be uniformly integrated within existing IoT devices installed in various smart city infrastructure elements such as transport solutions and data analytics platforms thus increasing demand for sophisticated digital signage that facilitates more connected sustainable urban environments.
Nonetheless, there are serious barriers to the adoption of electronic components that include integration complexities with current infrastructure and ecosystems where they are supposed to be fitted. To do this perfectly, a smooth process requires advanced planning, comprehensive electronics engineering technical knowledge, and in some instances extensive changes or modifications. This is time-consuming and costly while also needing substantial resources in order to make it compatible with diverse hardware and software components leading to operational downtime, cost overruns as well as other technical glitches.
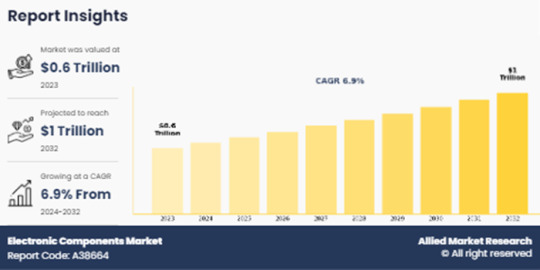
However, these obstacles notwithstanding; there are huge potential growth areas for electronic components especially in developing nations undergoing rapid urbanization and digitalization. These regions which have been characterized by changing tastes among consumers as well as government programs aimed at modernizing the infrastructure provide fertile ground for broad based use of electronic components in industries such as retail commerce, transportation services, and hotels. The resultant demand for electronic components that will come about when emerging markets adopt digital technologies to facilitate communication process, improve efficiency both in manufacturing sector and service delivery alongside enhancing customers experience will significantly define their role as drivers of global industrial growth.
The electronic components market report is segmented based on type, application, and region. On the basis of type, the electronic components market forecast is divided into active components, passive components, and electromechanical components. Based on application, the electronic components industry report is classified into consumer electronics, automotive, industrial automation, telecommunication, aerospace and defense, healthcare, energy and power, and others.
On the basis of region, it is analyzed across North America (the U.S., Canada, and Mexico), Europe (the UK, Germany, France, Italy, and the rest of Europe), Asia-Pacific (China, Japan, India, South Korea, and rest of Asia-Pacific), Latin America (Brazil, Argentina, and rest of Latin America), and Middle East and Africa (UAE, Saudi Arabia, and rest of Middle East & Africa).
The key electronic components company list profiled in the report includes Intel Corporation, Samsung, TSMC, Texas Instruments, Broadcom Inc, Bosch, NXP Semiconductors, STMicroelectronics, Skyworks Solutions, and Analog Devices. These key electronic components company listed in this market have adopted strategies such as product portfolio expansion, mergers & acquisitions, agreements, geographical expansion, and collaborations to enhance their market penetration.
According to Himanshu Jangra, Lead Analyst, Semiconductor and Electronics, at Allied Market Research, “The global electronic components market value is expected to witness considerable growth, owing to increase in demand for consumer electronics solution paired with rise in disposable income in emerging economies such as India, South Korea, Brazil, Dubai, and especially in Asia-Pacific and LAMEA region, which is expected to drive the market growth.”
Key Findings Of The Study
The electronic components market insights is growing fast due to an increasing consciousness of the environment and the need to reduce carbon emissions.
Demand for the electronic components market comes majorly from the consumer electronics sector, as there are smartphones, wearables, and gadgets everywhere that need high-performance compact parts.
Competition in this market is intense with innovative firms fighting for space alongside well-established ones offering cheaper solutions.
The Asia-Pacific region leads the charge, propelled by government investments, rapid urbanization, and robust consumer retail sectors, making it a prime market for electronics component growth.
#electronic#electronic music#electronic components#electras components#pc components#automotive components
0 notes
Text
How Digital Signage is Changing Businesses in 2025

Digital signage has become the game changer for businesses across all industries. In this digital age businesses are always looking for new ways to engage customers to communicate and sell. In 2025 it’s moving fast and businesses have more opportunities to get ahead. From digital signage displays to transparent LED screens let’s see how this technology is reshaping the business landscape. The digital signage software has evolved and now offers more interactive and engaging experiences. Modern digital signage monitors have AI powered analytics, touch screens and remote management, they are a must have for businesses worldwide.
Top Digital Signage Trends 2025
Some digital signage trends of 2025 are listed below.
Transparent LED Screens - Transparent LED screens are becoming popular in retail and corporate environments. It is a futuristic and attention grabbing way to display content.
Cloud Based Digital Signage - Digital signage cloud software allows to manage and update content remotely, across multiple locations.
E-Paper Displays - Many businesses are going for e-paper displays as an eco friendly alternative to traditional screens. It has low energy consumption and high readability.
AI Powered Personalization - Artificial intelligence in digital signage software is enabling personalized ads and real time content changes based on customer behavior.
How digital signage is changing the business game
Customer Engagement
Businesses are using digital displays to create immersive and interactive experiences for customers. In retail stores, restaurants or corporate offices digital solutions engage the audience with dynamic content. High resolution LED screens grab attention and encourage customer interaction.
Corporate Communication
Companies are using digital monitors to improve internal communication. These screens show real time announcements, meeting schedules and performance metrics so employees stay informed. With the rise of remote work businesses are using digital signage cloud software to manage content across multiple locations.
Sales and Marketing
Retailers are using software digital signage to personalize promotions and ads. Digital displays show targeted offers, new products and adjust content based on customer demographics. This real time adaptability means businesses can engage and sell more.
Outdoor Advertising
Outdoor advertising has taken a huge leap with transparent LED screens. These displays allow businesses to stay visible while showing ads. The transparency feature is especially good for storefronts so businesses can show ads without blocking the view of their physical store.
Sustainability with E-Paper Displays
As businesses get more eco-friendly e-paper displays are on the rise. Unlike traditional LED screens e-paper technology uses minimal power and is perfect for digital menu boards, transportation signage and electronic billboards. These displays are a sustainable option without compromising on visibility and functionality.
Digital Signage in Melbourne
Digital signage in Melbourne is growing fast across all industries including retail, healthcare and hospitality. With more and more businesses adopting digital solutions Melbourne is the hub for this space. The city’s business environment and tech savvy customers are driving the demand for cutting edge signage solutions.
Future of Digital Signage
In 2025 digital will integrate with AI and IoT. Businesses will be able to show hyper-personalised content based on real-time data. Touchless interactive displays and voice controlled signage will be the norm.
Conclusion
The facts are clear digital signage in 2025. From customer engagement to corporate comms and sustainability, businesses are winning big with this tech. Whether it’s digital signage monitors, LED screens or cloud based software the future is looking bright and businesses that get on board will be miles ahead.
Is your business ready to get the most out of digital signage? Act now! At Engagis we offer custom digital signage solutions for your business. From interactive displays to AI powered signage we help brands create dynamic experiences. Get in touch today to see how we can digitize your business!
#Digital signage display#Digital signage monitor#LED screens#Software digital signage#Digital signage cloud software#Digital signage Melbourne#Transparent LED screen#e paper display#digital signage software
1 note
·
View note