#How Can I Protect Its Data With VPN
Explore tagged Tumblr posts
Text
It is a truth universally accepted that when critiquing anything regarding AO3/OTW, reactionaries enter the building, and critical thinking and discernment gets locked out.

Nia Ola (on Substack) attempted to raise the alarm about AO3's changes in Terms of Service. This bit in particular:
Nia Ola: "[...]AO3 just updated their terms and conditions so that the only way you can use the site now is that you consent to them taking your data (so, works that you've written, distributed, saved, bookmarked, etc, everything) and give that data and information to the government."
In my time reading Terms and Conditions of Service, websites claiming that they're "duty bound" to provide data uploaded to the site to the govt, depending on jurisdiction, is not a surprise. You will not be informed or told by the site(s) when the government accesses/obtained your information. All on the pretense that it would "interfere with an ongoing investigation".
It isn't dissimilar to the one I've read here for Tumblr. The bit that says (legalese-y) that anything you post on the site can be used as evidence (IIRC) if it becomes "necessary."
But as usual, the AO3 brigade worked like hell to shout them down. Folk focused a lot on how OTW made their TOS "easier" to understand. They claimed Nia Ola was spreading misinformation. Most have gone as far as quibbling with her phrasing, "giving your information to the government" (which they would be doing) based on their personal interpretation of her meaning.
After making the video (they posted on TikTok) private, Nia Ola continued to encourage people to use security measures like VPNs and secure Browsers (they mentioned Firefox; I'm sure others are recommending Tor, Brave, and lesser-known browsers with better security features than Edge or Chrome) and to back up information they didn't want to lose.
Is it an explicit consequence of the election? Probably not. AO3/OTW knows entirely that they're hosting grimy shit on their website and refuse to do anything about it. AO3/OTW, like other websites, are "all-ages". Meaning OTW knows kids as young as 13 (and lets face it, younger) are using AO3. If the US or any other country decides it's politically advantageous to go after them, AO3/OTW is gonna cover their asses and throw you under the bus.
Point-Blank-Period.
That said, I think it would be irresponsible to exclude the election as a factor altogether. Organizations (govt or otherwise) are hang-wringing about rustling conservative feathers, and censoring themselves to avoid the wrath of a Trump Admin.
KOSA and COPPA are still in play. And there's the bill targeting non-profits to consider that's likely (and did) to pass not long after it got shot down.
When Tumblr wanted the favor of the Apple Store and their advertisers, they targeted sex worker blogs and fashion and art bloggers (primarily Black/non-Black). Then, they created an AI flagging system that still doesn't work.
When enough people (and advertisers) made enough noise about the NC-17 content that FanFiction (dot net) hosted on their site (at the height of its popularity, mind you)? They made a choice that allowed the website to survive and eliminate the target on their back. Both were financially motivated, yes, but if it's a choice of annexing content to stay online or getting shuttered?
AO3 will not be an exception. It's already embracing that "Obeying in Advance" phrase y'all are in love with right now.
Nia Ola is not the only one raising the alarm or alarmed by this decision. In your haste to fall on the sword for an organization that does not care about you, try not to make an ass of yourself by dog-piling people with experience regarding the consequences of data collection stemming from policies meant to criminalize sexual content, yeah?
This will continue unless we establish actual policies, education, and protections to prevent the mass surveillance of adult spaces under the pretense of "decency" and "protecting children." Additionally, we must address the ongoing elimination of healthy and safe spaces for children.
Because in our govt's haste to claim their concern for children, the corporations they serve have been demolishing child spaces and media online to save a couple of bucks (Cartoon Network's website comes to mind), and pushing children into adult spaces. And if they're not pushing kids into adult spaces, they're inviting adults into so-called kid spaces to increase their profits (Roblox and its attempts to become anything but a game for children, to say nothing of their monetization of the ideas that kids make).
Until our culture/society overhauls its approach to sex education, divorced from white supremacy, the actual intention of creating spaces that aren't sex-negative and don't prey on uninformed children will probably always exist in short bursts.
That means our politic has to rid itself of the reactionary ilk that (a) demonizes all things sexual and (b) refuses to practice discernment and critical thinking in their so-called sex-positive spaces. Both are why places like AO3 manifest and then ultimately help no one.
And it does not help anyone that reactionary AO3 loyalists will always fight to keep conversations about the site politically and socially stunted and unchanging.
Not all censorship and moderation is or should be sex-negative or censorious to the point of infantilizing. But, if the goal is maintaining free speech and freedom of expression (as we like to think of it vs how the govt allows it), it cannot be to the detriment of itself or for the sake of it (i.e., anti-censorship is not the answer any more than autocratic censorship is).
#greatrunners meta#data collection#data privacy#media manipulation#terms of service#fanfiction#archive of our own
17 notes
·
View notes
Text
Do You Really Need a VPN? Find Out!
Introduction

In today’s digital world, our online privacy is constantly under threat. Have you ever wondered how secure your personal data is when you're browsing the web or accessing public Wi-Fi? With increasing concerns about data breaches and surveillance, many people are turning to Virtual Private Networks (VPNs) to shield their online activities. But with so many options available, it can be overwhelming to figure out whether a VPN is truly necessary for you or if it’s just another tech trend.
This article aims to demystify VPNs by providing a clear and concise overview of what they are and why they have become a hot topic in the realm of internet security. We'll delve into the core functions of VPNs, explore their benefits and potential drawbacks, and help you assess if a VPN aligns with your personal online needs. By the end of this guide, you'll have a better understanding of whether a VPN is an essential tool for you or if other solutions might be more suitable for safeguarding your online presence.
What is a VPN?
A Virtual Private Network (VPN) is a tool designed to enhance your online privacy and security. At its core, a VPN creates a secure, encrypted connection between your device and the internet. This connection acts like a private tunnel that shields your online activities from prying eyes, making it harder for anyone, including hackers and internet service providers, to monitor what you're doing online. Think of a VPN as a protective cloak that conceals your digital footprint and allows you to browse the internet with a greater sense of security.
The functionality of a VPN involves routing your internet traffic through a remote server, which masks your IP address and encrypts your data. This process not only hides your true location but also ensures that any data you send or receive is encrypted, making it nearly impossible for unauthorized parties to access. By connecting to servers in various locations, a VPN also allows you to bypass geographical restrictions and access content that might otherwise be blocked in your region. This dual-layer protection—hiding your IP address and encrypting your data—creates a more secure and private browsing experience.
Understanding "What is a VPN?" is crucial for anyone concerned about online privacy. In an era where personal data is a valuable commodity and cyber threats are prevalent, having a VPN can be a significant asset. It offers peace of mind by safeguarding your information and providing a shield against potential threats. As we explore further in this article, you'll learn more about when a VPN is most beneficial and if it’s the right choice for your personal online security needs.
Explore the Benefits of ZoogVPN Today! If you're considering enhancing your online privacy and security, why not start with ZoogVPN? With incredible pricing and a range of features designed to keep you safe online, ZoogVPN is a great choice. Learn more about ZoogVPN and find the perfect plan for you.
Should I Accept VPN?
When considering whether to accept or adopt a VPN, it’s important to weigh its numerous benefits. One of the primary advantages of using a VPN is enhanced privacy. By masking your IP address and encrypting your internet traffic, a VPN shields your online activities from prying eyes such as hackers, advertisers, and even your internet service provider. This level of privacy ensures that your personal data remains confidential, making it significantly more challenging for third parties to track your browsing habits. Additionally, a VPN provides access to restricted or geo-blocked content, allowing you to enjoy streaming services, websites, and information that may be limited based on your location.
A VPN can be particularly relevant in various scenarios. For instance, if you frequently use public Wi-Fi networks, such as those in cafes or airports, a VPN offers an added layer of security against potential cyber threats. Public networks are often vulnerable to attacks, and a VPN helps protect your sensitive information from being intercepted. Similarly, if you travel often and want to access your home country’s streaming services or websites that are otherwise inaccessible abroad, a VPN can easily bypass these regional restrictions and provide you with the content you desire.
Considering the question "Should I accept VPN?" also involves evaluating your personal and professional needs. If you’re concerned about online privacy or frequently work with sensitive information, using a VPN can significantly enhance your digital security. It can also be beneficial if you live in a region with restrictive internet policies and want to freely access global content. On the other hand, if your online activities are relatively routine and you rarely access sensitive data, you may not find a VPN as crucial, although it still provides added security.
Ultimately, deciding whether to accept a VPN depends on your specific needs and concerns. The key is to assess how often you encounter situations where privacy and security are paramount. If these concerns resonate with your online habits, integrating a VPN into your routine can be a proactive step towards safeguarding your digital life and expanding your internet freedom.
When Should You Not Use a VPN?

While VPNs offer numerous benefits, there are certain situations where using one might not be ideal or necessary. For example, if you're accessing websites or services that don’t handle sensitive information or are already secure, the added layer of encryption provided by a VPN might be redundant. Additionally, if you're in a low-risk environment, such as a private and secure home network, the need for a VPN diminishes. Similarly, some websites and online services are designed to detect and block VPN traffic, which can result in difficulties accessing the content you need.
Another important consideration is the impact a VPN can have on your internet speed and performance. Because VPNs reroute your internet traffic through an external server, this can introduce latency and reduce connection speeds. This slowdown can be noticeable when streaming high-definition content or engaging in online gaming, where speed and responsiveness are crucial. If you’re performing activities that demand high-speed connections or if you have a limited bandwidth allocation, the performance drop caused by a VPN might outweigh its benefits.
Deciding when not to use a VPN also involves evaluating your specific use cases. For instance, if you’re using the internet for casual browsing or non-sensitive activities, the added security of a VPN might not be worth the potential decrease in speed. Moreover, for certain applications and services that function best with a direct connection, using a VPN could interfere with their optimal performance. It’s essential to weigh the trade-offs and determine whether the privacy and security benefits of a VPN align with your current needs and online behavior.
What is the Downside of a VPN?
While VPNs are often praised for enhancing online privacy and security, they are not without their downsides. One major concern is the privacy of the VPN provider itself. Although VPNs are designed to shield your data from external parties, some providers may log user activity or metadata, potentially compromising the very privacy they aim to protect. It’s crucial to research and choose a VPN service with a strict no-logs policy and transparent privacy practices to ensure that your data remains confidential.
Another consideration is the cost associated with subscribing to a VPN service. While free VPNs are available, they often come with limitations such as reduced speeds, fewer server options, and potential privacy issues. Paid VPN services, which generally offer better performance and security features, can range from relatively affordable to quite expensive. This ongoing expense might not be justifiable for everyone, especially if the benefits of a VPN do not align with their online activities and security needs.
Compatibility issues can also pose a challenge when using a VPN. Some websites and online services actively block VPN traffic to prevent bypassing geographical restrictions or fraud detection. This can result in difficulties accessing certain content or services while connected to a VPN. Additionally, certain applications and websites may not function properly with VPNs enabled, leading to disruptions in your online experience. It’s important to consider these potential drawbacks when evaluating whether a VPN is the right choice for your needs.
Does a VPN Affect Wi-Fi?
When you connect to a VPN, it’s common to experience changes in your Wi-Fi speed. A VPN routes your internet traffic through a secure server, which can introduce additional layers of encryption and data handling. This process, while enhancing security, can slow down your internet connection. The extent of this speed reduction depends on several factors, including the VPN server’s location, the encryption protocol used, and the overall quality of the VPN service. High-quality VPNs often minimize speed loss, but users should be prepared for potential decreases in browsing speed.
Network issues are another consideration when using a VPN over Wi-Fi. VPN connections can sometimes lead to unstable network performance, causing intermittent drops or slower connectivity. This can be especially noticeable on wireless networks with lower signal strength or higher congestion. Additionally, because VPNs create an encrypted tunnel for data, they may interfere with certain network protocols or configurations, potentially leading to connectivity problems or difficulty accessing specific online services.
In some cases, the interaction between a VPN and Wi-Fi networks can lead to unexpected complications. For instance, VPNs might struggle with certain types of network hardware or software, which can cause compatibility issues or connectivity errors. Additionally, some Wi-Fi networks, particularly in public or restricted environments, may block VPN traffic, further complicating your internet access. Users should consider these potential problems and test their VPN connection on various networks to ensure consistent performance.
Overall, while a VPN can impact Wi-Fi speed and connectivity, the degree of effect largely depends on the quality of the VPN service and the specific network conditions. For users who prioritize online privacy and security, the trade-off in speed and potential network issues might be worthwhile. However, it’s important to choose a reputable VPN provider and understand how it might interact with your Wi-Fi setup to minimize any negative impacts.
Is a VPN Needed for Home Wi-Fi?
When considering home Wi-Fi security, many people wonder if a VPN is necessary. A VPN can certainly add an extra layer of protection by encrypting your internet traffic and masking your IP address, which is beneficial for safeguarding sensitive information from potential threats. However, for most home networks, basic security measures such as strong passwords, WPA3 encryption, and regular firmware updates on your router are often sufficient to protect against common threats. While a VPN enhances security, its benefits might be more pronounced for those who frequently use public Wi-Fi or access sensitive information remotely.
Beyond using a VPN, there are several effective ways to secure your home Wi-Fi network. Implementing robust security protocols like WPA3 can prevent unauthorized access and ensure that your network is shielded from potential intruders. Additionally, regularly updating your router’s firmware and setting up a guest network for visitors can further bolster your home network's security. For many users, these measures, combined with cautious online behavior, can provide adequate protection without the need for a VPN.
Secure Your Online Presence with ZoogVPN Are you ready to take control of your online privacy? ZoogVPN offers excellent services at unbeatable prices. Discover how ZoogVPN can protect your data and enhance your browsing experience. Check out ZoogVPN's plans and find the best fit for you.
Is There Anything Better Than a VPN?
When it comes to online privacy and security, VPNs are often touted as the go-to solution, but they’re not the only tools available. Alternatives like proxy servers, secure browsers, and end-to-end encryption can also offer significant protection for your digital activities. Proxy servers, for instance, act as intermediaries between your device and the internet, masking your IP address but typically without the same level of encryption as a VPN. Secure browsers like Tor are designed to enhance privacy by routing your internet traffic through multiple servers, though they can sometimes slow down your browsing experience. End-to-end encryption ensures that your communications are only readable by the intended recipients, making it ideal for secure messaging and email.
Comparing these alternatives to VPNs reveals distinct differences in effectiveness and use cases. VPNs provide robust encryption, which secures all of your internet traffic and is effective across various devices and platforms. In contrast, proxy servers offer less security but can be useful for bypassing geo-restrictions. Secure browsers like Tor offer enhanced anonymity but may suffer from slower speeds and limited usability. End-to-end encryption is crucial for protecting specific types of communication, but it does not encrypt all internet traffic like a VPN does. Each tool has its strengths and limitations, so the best choice depends on your specific privacy and security needs.
While VPNs offer comprehensive protection, evaluating these alternatives can help you find a solution that best fits your requirements. For users who need robust, all-encompassing privacy, a VPN might be the preferred choice. However, if you’re looking for targeted protection or want to supplement your existing security measures, integrating secure browsers, proxies, or end-to-end encryption into your digital routine can be effective. Each tool can complement a VPN or serve as an alternative based on what aspects of privacy and security are most important to you.
Ultimately, the choice between a VPN and other privacy tools depends on the level of security and anonymity you seek. For comprehensive protection and convenience, a VPN is often a strong choice. However, exploring other options like proxy servers, secure browsers, and end-to-end encryption can provide additional layers of security and privacy, catering to various needs and preferences.
Do We Really Need a VPN?
In the ongoing debate about online privacy and security, the necessity of a VPN often boils down to a balance of pros and cons. On the plus side, VPNs offer substantial advantages such as enhanced privacy by masking your IP address, secure data encryption to protect sensitive information, and the ability to access geo-restricted content. These features make VPNs a valuable tool for anyone concerned about their digital footprint or wanting to bypass regional restrictions. However, VPNs also come with potential drawbacks, including the cost of subscription services, possible slowdowns in internet speed, and occasional compatibility issues with certain websites or services. Understanding these benefits and limitations is crucial in evaluating whether a VPN aligns with your needs.
Deciding whether to invest in a VPN requires a personal assessment of your internet habits and security requirements. For users who frequently handle sensitive information, access region-locked content, or simply wish to enhance their online privacy, a VPN can be an essential tool. On the other hand, if you only use the internet for basic browsing and are not concerned about privacy or geographic restrictions, the necessity of a VPN may be less compelling. It's important to weigh your specific needs and how a VPN would fit into your overall digital security strategy.
Ultimately, the question of whether we really need a VPN is a highly individual one. Consider your internet usage patterns, your level of concern about privacy, and your willingness to invest in additional security measures. By carefully evaluating these factors, you can make an informed decision about whether a VPN is a worthwhile addition to your online toolkit. Whether you opt for a VPN or choose other methods to safeguard your digital life, the key is to ensure that your choices align with your personal privacy and security goals.
Conclusion

As we’ve explored, the decision to use a VPN hinges on weighing its benefits against its potential drawbacks. VPNs provide valuable features such as enhanced privacy, secure browsing, and access to geo-restricted content. However, they also present challenges, including potential impacts on internet speed and the financial cost of subscription services. Ultimately, the effectiveness of a VPN depends on your individual online habits and security needs. Understanding these aspects will help you make an informed choice about whether a VPN is right for you.
It’s essential to take stock of your own online activities and security concerns when evaluating whether to use a VPN. Consider how often you handle sensitive information, if you frequently access content restricted by geography, and whether you are willing to pay for a subscription. By aligning your personal needs with the features offered by VPNs, you can determine whether this tool will enhance your online experience or if other solutions might be more appropriate.
We’d love to hear from you about your experiences with VPNs or any questions you might have! Please share your thoughts, stories, or inquiries in the comments section below. Your feedback not only helps us understand your perspective but also assists fellow readers in navigating their own decisions about VPN use. Engage with us and be part of the conversation about securing our digital lives!
FAQ: Understanding VPNs
What is VPN and Why Do I Need It?
A VPN, or Virtual Private Network, is a tool that creates a secure, encrypted connection between your device and the internet. By masking your IP address and routing your internet traffic through a remote server, a VPN enhances your online privacy and security. You might need a VPN to protect sensitive data from hackers, access region-restricted content, or maintain anonymity while browsing.
Is it Worth Getting a VPN?
Whether a VPN is worth the investment depends on your personal needs and online habits. For those who frequently use public Wi-Fi, handle sensitive information, or want to access content unavailable in their region, a VPN offers substantial benefits. It enhances security, provides privacy, and enables unrestricted access to global content. However, if you mostly use the internet for general browsing and don’t engage in activities that require high privacy, the need for a VPN might be less critical.
What is the Downside of Having a VPN?
While VPNs offer numerous advantages, they also have some downsides. Potential issues include reduced internet speed due to encryption overhead, possible compatibility problems with certain websites or services, and the cost of subscription services. Additionally, some VPN providers may log user data, which could undermine privacy if not carefully vetted.
When Should a VPN Not Be Used?
A VPN might not be necessary in every situation. For example, if you’re using a secure, private network or accessing sites and services that don’t require high levels of privacy, the benefits of a VPN may be minimal. Additionally, VPNs can sometimes interfere with online services, such as streaming platforms or secure financial transactions, which may not function correctly when routed through a VPN server.
Is VPN Legal in the UK?
Yes, using a VPN is legal in the UK. It is a common tool for enhancing privacy and securing internet connections. However, while VPNs themselves are legal, they should not be used to engage in illegal activities. Ensure that you comply with all laws and regulations when using a VPN.
Should I Accept VPN?
Accepting a VPN largely depends on your personal security needs and internet usage. If privacy, data security, or access to restricted content are important to you, accepting and using a VPN can be a prudent choice. Evaluate your online habits and determine whether a VPN aligns with your requirements for enhanced protection and access.
Is it Good to Have VPN on All the Time?
Having a VPN on all the time can be beneficial, particularly if you frequently access public Wi-Fi or handle sensitive information. It ensures that your data is consistently protected and that your online activities remain private. However, if a VPN causes significant slowdowns or interferes with specific services, you might choose to turn it on only when needed. Evaluate your personal usage to determine the best approach.
Ready for Ultimate Online Security? Don't wait to secure your internet connection and protect your personal data. ZoogVPN provides top-notch VPN services at fantastic prices. Visit ZoogVPN now to explore their offerings and start browsing safely today!
10 notes
·
View notes
Text
Avoid Costly IT Mistakes by Hiring a Professional Network Engineer

Your company's digital backbone is its network infrastructure. Everything else, including data movement, security, communication, and consumer access, comes to a complete stop if it fails. Nevertheless, a lot of companies wait until it's too late to hire the best candidates. Companies need to employ network engineers who can foresee issues before they become outages if they want to stay ahead, particularly in 2025.
A properly constructed network keeps your organization operating efficiently, regardless of whether you're using a legacy system, cloud, or hybrid model. Avoiding downtime and safeguarding against vulnerabilities are essential for tech organizations. Here's how a qualified network engineer may help you maintain security and scalability while avoiding expensive IT mistakes.
Why Every Business—From Startups to Enterprises—Needs a Strong Network Foundation
The technologies that keep your company connected, both internally and externally, are designed, implemented, and maintained by network engineers. They are in charge of setting up switches, routers, firewalls, VPNs, and frequently cloud-based network components.
Inexperienced hiring practices may result in subpar architecture, bandwidth restrictions, or obvious security vulnerabilities. On the other hand, you gain performance, dependability, and peace of mind when you work with network experts who have the proper certifications.
Instead of hiring network engineers as a last resort when something goes wrong, many tech businesses are increasingly incorporating them early in their IT planning stages.
Prevent Downtime and Save on Recovery Costs
Hours or even days of service outages can result from a small network configuration error. Downtime for SaaS platforms or e-commerce companies equates to lost sales, disgruntled customers, and eroded trust.
To reduce these risks, skilled network engineers put disaster recovery procedures, redundancy systems, and proactive monitoring into place. They can swiftly isolate problems, intelligently reroute traffic, and expedite service restoration.
It becomes evident that hiring network engineers is a proactive investment rather than a one-time price when you take into account the cost of recovery, lost productivity, and even harm to your brand.
Protecting Your Business from Security Breaches
Networks that are improperly segmented or lack robust firewalls and access controls are particularly vulnerable to cyberattacks. Strong encryption will be enforced, your data paths will be secured, and suspicious activity will be monitored by a qualified network expert.
They'll also make sure your team adheres to best practices, which include using a VPN and using secure Wi-Fi. Early detection and quick containment are more important than merely prevention.
Part of the work also includes security audits. Additionally, you cannot afford to take shortcuts in this area if you are growing internationally or are subject to stringent compliance regulations.
The Role of Salary Benchmarking Tools in Hiring
How much should I pay a qualified network engineer? This is a question that many hiring managers have.
You can provide competitive pay while keeping costs down by using salary benchmarking tools. When managing hybrid teams or hiring remotely, these solutions can assist in comparing pay packages across geographical areas.
Additionally, these tools assist in justifying decisions to leadership based on expected cost versus impact if you're not sure whether to recruit internally or externally.
Network Engineers and Software Teams: A Strategic Duo
Remember that network engineers frequently collaborate closely with software developers, particularly in settings that heavily rely on DevOps. Their responsibilities overlap whether it's managing cloud rights, CI/CD pipeline setup, or API deployment.
It can be necessary to hire software engineers and network engineers simultaneously if you are growing your team in order to guarantee smooth cooperation. They work together to safeguard user data and maintain the infrastructure that runs your apps.
Tech firms benefit from fewer bottlenecks, quicker deployment cycles, and more dependable systems when both roles are in alignment.
Closing Thoughts
Make the effort to hire network engineers who are both seasoned and forward-thinking to avoid errors that are more expensive to correct than to avoid. A dependable network is not a luxury in today's constantly connected society; rather, it is the basis for expansion. Additionally, uptime is a must for tech organisations that depend on it for survival.
0 notes
Text
This bundle (direct link for anyone who doesn't want to click through to Twitter: https://www.humblebundle.com/books/terry-pratchetts-discworld-harpercollins-books) is only available in the US.
So are the rest of us just out of luck? Of course not, this is the internet! And I'm not even talking about 🏴☠️! If we want to buy this bundle and gain access to this deal and buy these ebooks legitimately, we just need to make Humble think that we're in the US.
How do we do that? Well, if you already have access to a VPN service that provides location redirection you can just use that (mostly, you'll still need to read from step 11 below), but for anyone who doesn't already have one, you can use Tor as a free substitute with a little bit of work.
What is Tor, you ask? The name stands for 'The Onion Router' and it's an open-source software project designed to protect users' privacy online. It does this via a number of methods designed to make it difficult for trackers to identify a specific user (blocking tracking cookies, steps to obfuscate browser fingerprinting) and their online activity (encrypting internet traffic and relaying it through their own network to hide your identity). It's that last part that is useful for us today, because we can use that relay network to digitally project ourselves into the US of A to buy Discworld books AND donate to charity! We just need to tweak a few settings to get it to do that for us.
Step-by-step guide for how to both get and configure Tor and then use it to get this bundle under the cut.
1. First of all, you're going to need to get Tor. This is very easy, because it's distributed for free; just go to https://www.torproject.org/ and download the browser for your operating system.
2. Having downloaded it, you need to install it. Shocking, I know!
3. Once installed, you will need to run the Tor Browser and press the Connect to Tor button once.
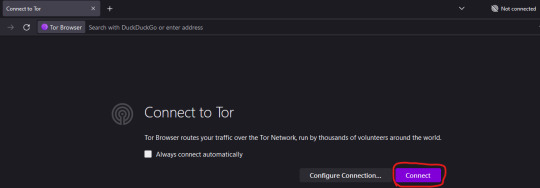
4. Once you are connected, close the browser window. Doing this creates configuration files that you will need to edit in order to have the relay go specifically via the US, instead of anywhere else in the world.
5. You need to locate the folder that Tor Browser is installed in. For Windows, by default, this will be on your Desktop (apologies to users of other OSes, I don't know the default locations for them, but you can find that info here: https://www.wikihow.com/Set-a-Specific-Country-in-a-Tor-Browser)
6. From the Tor Browser folder, you need to go to Browser > TorBrowser > Data > Tor. You should see a folder that looks like this:
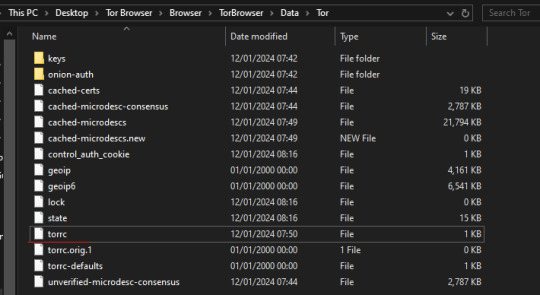
7. Right-click on the 'torrc' file and select 'Open With'. On the "How do you want to open this file?" menu that pops up, select 'Notepad'
8. Ignore the stuff that's in there already, we don't want to change any of that. What we want to do is add in two lines at the bottom, which will tell Tor to find both an entry and exit point to its network that are within the US. So we need to add in the following lines:
EntryNodes {US} StrictNodes 1 ExitNodes {US} StrictNodes 1
Add them as shown, with each one on its own line. (You might expect you only need to set the exit node to US to make this work, but when I tested this it did not work).
9. Once you've copy-and-pasted those lines in, go to File > Save (or hit Ctrl + S). Do not 'Save As', this will create a new .txt file, we need to save our changes in the original torrc file with no extension.
10. Now, re-open Tor Browser and tell it to connect. If you go over to https://www.humblebundle.com/books/terry-pratchetts-discworld-harpercollins-books you should now see the bundle, rather than be told it's not available to you... right up until you log in to your account to buy it! Oh no, we're not done yet!
11. So, if you already have a Humble account, Humble will have it location-locked to the country where you created it, and will block bundles not available in that country, even if you're currently connecting from outside that country. There are two ways around this:
11. A. Create a new Humble account using your Tor browser so that it's set to the US by default. You should be able to use your existing paypal account/other payment methods with this account even if you use them on your main account, but I haven't tested this in person.
11. B. Humble lets you change the location of your existing account up to 3 times every 3 months to the location you are currently connecting from. Since you are currently connecting from the US, you can use this to change your location to the US, buy the Discworld bundle, and then from outside of Tor you can log back into your account and change it back to wherever you call home. To do that, go to Settings in the account dropdown on Humble:
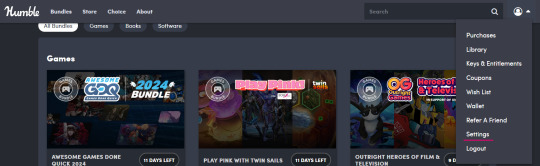
That leads through to this page:

If you're currently connecting from a different location to the one in the Location box, it will allow you to select the location you are connecting from instead. It will prompt you to confirm the location change before it goes through.
12. Congratulations, you have successfully tricked Humble into thinking you are in the US and allowing you to buy the Discworld bundle. The bundle itself is redeemed through Kobo, and they don't care where in the world you are, so it doesn't matter if you change your Humble account location after you've bought the books, you'll still be able to redeem your purchase and access your ebooks.
13. Optionally, go back and edit the torrc file again and take out the lines we added to return Tor back to its default functionality.

YOOOO DISCWORLD IS ON HUMBLE BUNDLE!!!
If you've been on the fence about starting these books THIS IS YOUR SIGN
5K notes
·
View notes
Text
What is Network Security?Network security is any action taken to prevent accidental damage to your devices, users, and data. The goal is to keep the network safe for all legitimate users apart of that specific network. Since there are many ways a network can become vulnerable, network security has a wide range of practices, including:Deploying Passive Devices: Using software and devices that report unauthorized usage on a network, or any malicious activity done by users.Deploying Active Devices: You can use the software to prevent malicious programs from running into or entering your network. Also, stopping the user from accessing dangerous websites on your organization’s computers. Preventative Devices: Devices that can detect the potential security holes, so your network staff can fix them.Users Following Safe Practices: Even if your hardware or software are made to be secured, your users will create security holes based on their activity. Network security staff is needed to teach your organization members on how to stay safe from upcoming threats.How Can I Protect My Network? While looking for network ip scanner, there are some ways you can improve your network’s security. Here are some options that are available:Install and Monitor a FirewallA firewall is a piece of hardware or software designed to prevent unauthorized access to networks or computers. In basic terms, a firewall is a group of rules that control the incoming and outgoing network traffic within an organization. Firewalls are becoming more advanced, and the latest ones are network security platforms that consist of multiple approaches that work together to prevent security breaches. Create a Virtual Private Network VPNs have a more secure connection between your remote computers and other local servers and computers. These networks are only available to the equipment and people in your system. With VPNs, you can decrease the chance of hackers attacking your system. Update Your Passwords QuarterlyHopefully, your employees will avoid using obvious passwords such as “12335” or “password”. In addition to having passwords with numbers and letters - try to add symbols and a mix of upper case and lower case letters to keep their passwords protected. For extra security, require your employees to change their personal passwords.While its recommended they updated their passwords each quarter, doing it often is a more secure method. However, changing your passwords too often will cause confusion, with your employees having to contact IT to remember their passwords. Side Note: Tell your employees that choosing passwords with symbols to replace the letters such as "pa$$word" for "password." Every hacker knows that trick already!ConclusionWhen looking for a network ip scanner, use these techniques to ensure that your organization’s network is secure. Hackers are always there, but with the right preventative procedures and systems set in place, you can reduce the amount of damage they’ll have on your network. What procedures do you have currently set in place? Is your team alert enough to remove network threats as soon as they arrive? By getting the best network scanners available, you’ll be able to answer yes to both questions and keep your network safe.
0 notes
Text
VPN Software: Comprehensive Guide to Virtual Private Networks
What is a VPN?
A Virtual Private Network (VPN) is a digital privacy tool that creates an encrypted connection between your device and the internet. It routes your internet traffic through a secure tunnel, masking your IP address and protecting your online activities from potential surveillance, tracking, and data interception.

How VPN Software Works
Encryption Process
Data Encryption: When you connect to a VPN, all your internet traffic is encrypted
Server Routing: Your connection is routed through a remote server
IP Masking: Your real IP address is replaced with the VPN server's IP
Secure Transmission: Data is protected from potential interceptors
Key Benefits of VPN Software
1. Online Privacy
Hide your real location and IP address
Prevent ISPs from tracking your browsing history
Protect personal information from potential hackers
2. Security Features
Encrypt data on public Wi-Fi networks
Protect against man-in-the-middle attacks
Shield sensitive information from potential cyber threats
3. Content Access
Bypass geographical restrictions
Access region-locked content
Circumvent internet censorship
4. Anonymous Browsing
Maintain anonymity online
Reduce targeted advertising
Prevent website tracking
Types of VPN Protocols
1. OpenVPN
Open-source protocol
Highly secure and configurable
Works on multiple platforms
Excellent balance of speed and security
2. WireGuard
Modern, lightweight protocol
Faster performance
Simplified codebase
Improved security features
3. IKEv2/IPsec
Stable mobile connection
Quick reconnection
Strong security
Excellent for mobile devices
4. L2TP/IPsec
Good encryption
Built-in on most platforms
Slightly slower than newer protocols
Reliable connection
Top VPN Software in 2024
1. NordVPN
Extensive server network
Strong security features
No-logs policy
Advanced encryption
2. ExpressVPN
High-speed connections
Global server coverage
User-friendly interface
Strong privacy protections
3. ProtonVPN
Swiss privacy laws
Free tier available
Strong encryption
Transparent privacy policy
4. Surfshark
Unlimited device connections
Affordable pricing
Growing server network
Advanced privacy features
5. Mullvad
Strong anonymity focus
Accepts cryptocurrency
Minimal personal information required
Transparent operations
Selecting the Right VPN Software
Key Considerations
Server Locations: Global coverage
Connection Speed: Minimal performance impact
Security Protocols: Multiple encryption options
Privacy Policy: No-logs commitment
Price: Competitive pricing
Device Compatibility: Multi-platform support
Potential Limitations
VPN Drawbacks
Potential speed reduction
Some services may log data
Not a complete anonymity solution
Can be blocked by some websites
Privacy and Legal Considerations
Legal Status
VPNs are legal in most countries
Some nations restrict VPN usage
Always check local regulations
Ethical Usage
Use VPNs responsibly
Respect content licensing
Avoid illegal activities
Setting Up VPN Software
Installation Steps
Choose a reputable VPN provider
Create an account
Download appropriate software
Install on your device
Select server location
Connect and browse securely
Future of VPN Technology
Emerging Trends
AI-powered security
Faster encryption protocols
Enhanced privacy features
Integration with other security tools
Conclusion
VPN software is an essential tool for maintaining online privacy, security, and freedom in the digital age. By understanding its features, benefits, and potential limitations, users can make informed decisions to protect their digital identity.
Frequently Asked Questions
Are VPNs completely anonymous?
VPNs enhance privacy but do not guarantee 100% anonymity. Choose providers with strict no-logs policies.
Can I use a free VPN?
Free VPNs often have limitations:
Slower speeds
Limited server locations
Potential data logging
Less robust security
How much do VPNs cost?
Budget options: $3-$5 per month
Premium services: $10-$15 per month
Annual plans offer significant discounts
Can VPNs be used on multiple devices?
Most modern VPN services support:
Smartphones
Tablets
Computers
Some support unlimited device connections
0 notes
Text
How Can I Stream Free on My Smart TV?

Streaming has become the go-to method for enjoying entertainment in the digital age, offering unmatched convenience and access to unlimited content. If you’ve ever wondered, “How can I stream free on my smart TV?” you’re in luck. This guide will walk you through the essentials of free streaming, including top apps, safety tips, and expert recommendations to enhance your viewing experience.
Understanding Free Streaming on Smart TVs
Smart TVs are equipped with internet connectivity, allowing users to access various streaming platforms. Free streaming typically operates through ad-supported models, free trials, or public domain content. Numerous apps provide movies, TV shows, and live channels without requiring payment. However, it’s crucial to choose legitimate platforms to avoid malware or unauthorized content.
Getting Started
First, ensure your smart TV is connected to a stable Wi-Fi network. Most smart TVs have built-in app stores where you can download free streaming apps. If your TV lacks certain apps, consider using streaming devices like Roku, Fire Stick, or Chromecast to expand your options.
Top 10 Free Streaming Apps
Here are the best apps to stream free content on your smart TV:
Pluto TV: Offers 250+ live channels and on-demand movies and shows.
Tubi: Features a vast library of ad-supported movies and TV series.
Crackle: Provides classic movies and original programming.
Peacock (Free Tier): Includes live news, popular movies, and NBC shows.
YouTube: Offers free movies, documentaries, and live streams.
Plex: Streams ad-supported movies and shows.
Kanopy: A library-based service with award-winning films and documentaries.
IMDb TV: Amazon’s free streaming platform for movies and TV shows.
The Roku Channel: Available on various smart TVs, even without a Roku device.
Vudu: Offers ad-supported content alongside its rental service.
Download these apps from your smart TV’s app store, create an account if needed, and start exploring their extensive libraries.
Streaming Safely
While free streaming is exciting, it comes with risks like malware and scams. Stick to reputable apps listed above or those available on your smart TV’s official platform. Avoid apps requesting sensitive information like credit card details. Keep your smart TV’s software updated to protect against security vulnerabilities. Using a VPN can also encrypt your connection and safeguard your data.
Maximizing Your Smart TV’s Features
To enhance your free streaming experience, explore your TV’s settings. Enable features like “Quick Start” to reduce loading times. Check built-in apps and content hubs like Samsung’s Smart Hub or LG’s Content Store for personalized recommendations. Use screen mirroring to display content from your phone or laptop on your TV. Lastly, optimize your internet connection by using an Ethernet cable or placing your Wi-Fi router closer to your TV.
Maintaining Streaming Quality
Free streaming doesn’t mean compromising on quality. Choose apps like Tubi or Pluto TV that offer HD or 4K content. Adjust your TV’s display settings for optimal picture quality. Ensure your internet speed meets the requirements for HD (5 Mbps) or 4K (25 Mbps) streaming. For better performance, consider using external streaming devices like Roku or Fire Stick.
Conclusion
Free streaming on your smart TV is simple and accessible. By installing the right apps, following safety protocols, and optimizing your TV’s settings, you can transform your smart TV into an endless entertainment hub. With these tips, you’re ready to enjoy high-quality, cost-free streaming. Happy streaming!
0 notes
Text
Hurawatch: The Best Free Streaming Platform for Movies & TV Shows

In the era of digital entertainment, people look for seamless and free options to watch their favorite movies and TV shows. Hurawatch has emerged as a top choice among streaming enthusiasts due to its vast content library, HD streaming quality, and user-friendly interface. Unlike paid services such as Netflix, Amazon Prime, or Disney+, Hurawatch offers unlimited access to content without requiring a subscription.
However, with its rising popularity, many users wonder whether Hurawatch is legal, safe, and the best alternative for streaming. In this article, we will explore everything about Hurawatch, its features, benefits, risks, and how to use it safely.
What is Hurawatch?
Hurawatch is a free online streaming platform that provides access to a massive collection of movies, TV shows, and web series. The website is designed for users who want high-quality streaming without the hassle of creating an account or paying for a subscription.
Key Features of Hurawatch:
Extensive Movie & TV Show Library: Offers thousands of movies and series across different genres.
HD & 4K Streaming: Enjoy movies in 720p, 1080p, and 4K resolutions.
No Registration Required: Start watching instantly without signing up.
User-Friendly Interface: Well-organized sections and search filters for easy navigation.
Fast Streaming & Multiple Servers: Buffer-free playback with alternative servers.
Regular Updates: New movies and TV shows are added frequently.
Free of Cost: No hidden charges or premium memberships required.
Is Hurawatch Safe & Legal?
1. Legal Concerns
Hurawatch does not own the content it provides, meaning it may fall under copyright infringement laws in various countries. Many streaming platforms operate in a legal grey area, and accessing copyrighted content for free might violate laws in some regions.
2. Safety Risks
While Hurawatch itself does not host harmful content, it does rely on third-party servers. This can pose security risks, such as:
Pop-up ads and redirects that may contain malware.
Unverified streaming links that could compromise user privacy.
Tracking cookies and scripts that collect browsing data.
How to Stay Safe While Using Hurawatch?
Use a VPN to hide your identity and location.
Enable an Ad-Blocker to prevent unwanted pop-ups.
Do not download files from unknown links.
Keep antivirus software activated for additional protection.
How to Access Hurawatch?
Since Hurawatch is a web-based platform, accessing it is simple. However, as multiple mirror sites exist, ensure you visit the correct one.
Step-by-Step Guide to Watching Movies on Hurawatch:
Open your preferred browser and search for Hurawatch official website (Check for a secure HTTPS version).
Browse the homepage or use the search bar to find your favorite movies or TV shows.
Click on the title, select a streaming server, and press Play.
Enjoy uninterrupted HD streaming for free.
FAQs About Hurawatch
Q1. Is Hurawatch free to use? Ans. Yes, Hurawatch is completely free and does not require a subscription.
Q2. Do I need to create an account on Hurawatch? Ans. No, Hurawatch does not require any registration or sign-up process.
Q3. Can I download movies from Hurawatch? Ans. Some versions of Hurawatch may allow downloads, but downloading copyrighted content is illegal in many countries.
Q4. Is Hurawatch available as a mobile app? Ans. No, Hurawatch does not have an official mobile app. Any app claiming to be Hurawatch may be fraudulent.
Q5. Can Hurawatch be accessed worldwide? Ans. While Hurawatch is available in many regions, some ISPs may block access due to legal issues. Using a VPN can help bypass restrictions.
Best Paragraph
Hurawatch is a widely popular free streaming platform that allows users to watch movies and TV shows in HD quality without registration. The website provides a vast collection of Hollywood blockbusters, trending web series, and classic films across multiple genres. With its user-friendly interface, fast streaming, and multiple server options, Hurawatch has gained a massive audience looking for unlimited entertainment at no cost. However, as it operates in a legal grey area, users should be cautious about security risks, pop-up ads, and potential copyright issues.
Conclusion
Hurawatch has become a leading choice for movie and TV show enthusiasts who prefer free streaming over paid subscriptions. With its extensive content library, HD streaming quality, and user-friendly experience, it continues to attract millions of viewers worldwide. However, users must be aware of the legal and safety concerns associated with free streaming platforms.
To make the most of Hurawatch, always take precautionary measures, such as using a VPN, ad-blockers, and avoiding suspicious links.
#movie of all time#movies#wicked movie#moviegifs#enterainment#series#latest movies#i love this movie#cinema
1 note
·
View note
Text
How To Use Private Internet Access for Enhanced Online Privacy
In this article, I will discuss how to use Private Internet Access (PIA) for enhanced online privacy. PIA is a powerful VPN tool that helps protect your data, secure your internet connection, and ensure anonymity while browsing. By using its advanced features, such as encryption and IP masking, you can effectively safeguard your online activity from prying eyes. What Is Private Internet…
0 notes
Text
Who Needs a Free VPN with Unlimited Bandwidth?
occasional speed throttlingUrban VPNPeer-to-peer VPN model, unlimited bandwidthSecurity concerns due to P2P architecture
Each provider comes with its own pros and cons, but the bottom line is clear: some free options can deliver decent performance without charging a dime.
How Do Free VPNs Sustain Unlimited Bandwidth?
It’s no secret that running a VPN service costs money. From server maintenance to software development, the bills add up. So how do free VPNs justify offering unlimited bandwidth? Here are the common strategies:
Freemium Model: Offering a basic free plan to upsell premium features.
Advertisements: Injecting ads into the user interface or selling anonymized user behavior data.
Peer-to-Peer Network Sharing: Utilizing user devices as part of their server network (e.g., Urban VPN).
While these models make the service “free,” they often come at the expense of user privacy, speed, or reliability.
Should You Trust Free VPNs with Unlimited Bandwidth?
The answer lies in your priorities. Here are a few factors to weigh:
Security: Are you okay with potential trade-offs in encryption and data logging?
Performance: Expect slower speeds and limited server access compared to paid options.
Reliability: Some free VPNs experience frequent downtimes.
If privacy and performance are non-negotiable, investing in a paid VPN might be worth considering. Services like ExpressVPN and NordVPN consistently rank high for speed, security, and global server access.
When Does a Paid VPN Make More Sense?
While free VPNs are tempting, they’re not always the best solution. Paid VPNs deliver:
Enhanced Privacy: No ad tracking or data-selling practices.
Global Server Network: Access servers across dozens of countries for unblocking content.
High-Speed Connections: Ideal for streaming, gaming, and torrenting.
Consider these plans for unmatched reliability:VPNPrice (Starting At)Top FeaturesExpressVPN$8.32/monthProprietary Lightway protocol, blazing-fast speedsNordVPN$3.99/monthDouble VPN, Threat Protection, over 5,500 servers worldwideSurfshark$2.49/monthUnlimited device connections, MultiHop feature for double encryption
Tips for Maximizing Free VPN Usage
Want to get the most out of a free VPN without hitting snags? Here’s how:
Leverage Referral Programs: Windscribe rewards referrals with extra data.
Rotate Between Providers: Alternate between free VPNs to avoid over-reliance.
Use During Off-Peak Hours: Reduce congestion for better speeds.
Common Questions About Free VPNs with Unlimited Bandwidth
Can I stream Netflix with a free VPN?
Some free VPNs, like ProtonVPN, may work with Netflix but often lack consistency. Paid options are more reliable.
Is my data safe with free VPNs?
Not always. Some free providers monetize user data. Stick to reputable names with strict no-logs policies.
Will a free VPN slow down my internet?
Likely, due to limited server resources and high user volumes.
Do free VPNs work on all devices?
Most support popular platforms (Windows, macOS, Android, iOS), but advanced features might be restricted.
Can I game using a free VPN?
Gaming on a free VPN is possible but may result in lag due to slower connections.
What are the hidden costs of free VPNs?
Privacy compromises, ad bombardment, or poor user experiences are common trade-offs.
The Verdict
While free VPNs with unlimited bandwidth exist, they come with caveats. Providers like ProtonVPN and Atlas VPN Free offer reasonable features for zero cost but may not meet the demands of power users. If you value blazing speeds, bulletproof security, and premium features, a paid VPN is a worthwhile investment. After all, in the digital realm, you often get what you pay for—and sometimes, what you don’t.
0 notes
Text
White Label VPN Solutions: A Guide to Launching Your VPN Brand
In today’s digital age, privacy and security have become top priorities for businesses and individuals alike. With the rise of cybersecurity threats, Virtual Private Networks (VPNs) are in high demand, and this presents a lucrative business opportunity. Enter White Label VPN Solutions—an accessible way to launch your own VPN brand without starting from scratch. In this guide, we’ll cover everything you need to know to get started with a white label VPN service, its benefits, and steps to establish your brand in the VPN market.
What is a White Label VPN Solution?
A White Label VPN Solution is a customizable VPN product provided by a third-party vendor that you can rebrand and sell as your own. It allows companies to offer VPN services under their brand name, tailored to their audience, without investing in the complex development and infrastructure that a VPN requires. With a white label VPN service, you get the technology and backend support needed to run a successful VPN service, enabling you to focus on marketing and customer acquisition.
Why Choose White Label VPN Solutions?
For those entering the VPN market, a white label VPN solution offers several advantages:
Quick Market EntryWith a white label VPN service, you bypass the time-consuming processes of development and testing. This allows you to launch your VPN brand in a fraction of the time it would take to build a VPN from scratch.
Lower CostsBuilding a VPN infrastructure from scratch is expensive. By choosing a white label VPN, you avoid development costs and instead pay a fee to use an established service, making it a budget-friendly way to enter the market.
Focus on Branding and MarketingThe vendor handles the backend, while you focus on brand customization, marketing, and customer acquisition. This division of labor allows you to build a strong, recognizable brand in the VPN market.
Reliability and Technical Support White label VPN providers often offer reliable uptime, maintenance, and support. This ensures a high-quality user experience, giving you peace of mind that your VPN service is well-managed.
Key Features to Look for in White Label VPN Solutions
Before you select a white label VPN provider, consider the following essential features to ensure your brand offers a competitive and secure service:
Global Server CoverageA wide network of global servers ensures that users can access content from various regions, bypassing geo-restrictions and maintaining a seamless experience.
Strong Encryption and SecuritySecurity is a primary concern for VPN users. Look for white label VPN solutions that use strong encryption protocols like AES-256 and secure VPN protocols, such as OpenVPN or WireGuard, to protect user data.
Customizable User InterfaceChoose a solution that offers a customizable interface to match your brand’s look and feel. This includes app colors, logo placement, and language options.
Cross-Platform CompatibilityEnsure your VPN service works on multiple platforms, including iOS, Android, Windows, and macOS, to reach a wider audience.
ScalabilityAs your user base grows, you’ll need a solution that scales with demand. Many white label VPN providers offer scalability options, ensuring smooth performance during peak times.
Steps to Launch Your VPN Brand with White Label VPN Solutions
Launching a successful VPN brand using a white label VPN service involves several key steps. Here’s how to get started:
Research the VPN Market Understand your target audience and their needs. Are they privacy-focused users, corporate clients, or everyday consumers looking for secure internet access? This will help you choose the right white label VPN features and develop a strong marketing strategy.
Select the Right White Label VPN ProviderCompare providers based on features, pricing, server coverage, and customer support. Read reviews and request a demo to ensure the service meets your requirements.
Define Your Brand IdentityThink about what sets your VPN apart from competitors. Will it be known for speed, security, ease of use, or affordability? This brand identity should be reflected in your website, logo, and marketing materials.
Customize the VPN SolutionWork with your white label VPN provider to customize the app’s appearance and features according to your brand’s identity. Personalize the logo, color scheme, and user interface to offer a cohesive brand experience.
Develop a Pricing StrategyChoose a pricing plan that appeals to your target market. You could offer monthly, quarterly, or annual plans with competitive rates. Additionally, consider providing a free trial to attract new users and build trust.
Plan Your Marketing and Launch A solid marketing strategy is essential for brand visibility. Utilize SEO, social media, content marketing, and partnerships to reach your target audience. Focus on key phrases like “white label VPN service” and “private VPN solution” in your content to improve search engine rankings.
Deliver Excellent Customer Support Customer support can make or break a VPN brand. Many white label VPN providers offer customer support as part of their package, but it’s crucial to provide a direct line for your customers and respond promptly to inquiries.
Marketing Tips for White Label VPN Solutions
Once you’re ready to launch, here are some effective marketing strategies to increase your brand’s visibility:
Leverage Content MarketingWrite informative blog posts on topics like “Benefits of Using a VPN” and “How to Choose the Right VPN.” This builds authority and attracts organic traffic to your site.
Optimize for SEOUse targeted keywords like “white label VPN service” and “custom VPN solutions” in your content, headings, and meta descriptions. An SEO-friendly website helps you rank higher on search engine results, attracting more potential users.
Utilize Social MediaSocial platforms are a powerful way to reach a broad audience. Create engaging content about VPN benefits, data security, and privacy to raise awareness and generate interest in your brand.
Offer Referral Incentives Create a referral program where existing customers can earn discounts or rewards by referring others to your VPN service.This can assist you in rapidly and economically expanding your user base.
Final Thoughts on White Label VPN Solutions
Investing in a White Label VPN Solution is an excellent way to enter the VPN market with a ready-made, customizable product. By partnering with an established provider, you can avoid the high costs and complexities of building a VPN from scratch. Instead, focus on building a strong brand, attracting customers, and providing a seamless user experience.
0 notes
Text
no, people who use threads are not insane, they are being deceived by a mega corporation that has based its entire business model off selling personal information for advertisement, and has worked tirelessly to make us believe this is in any way normal, acceptable, or remotely necessary to the ~optimal experience~.
we’ve been groomed to think our personal information and our very identity is worth trading for access to social media. and frankly you can’t blame anyone for falling for it. in this capitalist dystopia, social media has been fine tuned to be as addictive as possible. it’s legitimately useful for many reasons as well, but it’s really important to keep in mind that it is meant to be as enticing as can be, to retain attention for as many milliseconds as possible, and to have you open the app as many times as possible. they have every ressource to make it so. where do you think all that personal information goes? yeah, they sell it, but it’s also fed directly to their algorithms.
and let’s be real, they reveal what information they collect for legal reasons only. they don’t exactly disclose how information is harvested and how it’s used. many people don’t understand the implications of that list and why it’s so bad. many people who do understand think it’s worth it, because all of this information, or the majority of it anyways, is already in the hands of meta anyways.
and, like, I get it. I try to be super cautious about my informations. I don’t grant access to anything unless the app/site actually needs it to function, I pick “allow once” whenever I can, I don’t grant access to all photos and videos, only the ones necessary. I manually turn off all the data collection options on my phone which are turned on by default. I only accept strictly necessary cookies even if it’s always quicker to just accept everything. I use tracker blockers, content blockers, vpns, firefox over safari or chrome based engines. I don’t sign in or sign up anywhere using a social media or a google account. I legitimately care a lot. but I also know for a fact that all of the information Thread would want to collect is out of my hands already. be it be because I was careless at some point in the past and didn’t read all the fine print or because my data was illegally harvested and sold, I know that none of this is private to me anymore. and you are the same. seriously, you would have to be delusional to think meta doesn’t already know this about you if you’ve ever been on Facebook or instagram, or on the internet at all. I’m not sure that what I do to protect myself is even worth anything at this point, I just do it out of principle and habit. it’s a bit of a hassle, it makes some things more complicated than they should be because tech companies make it so. so I don’t blame people for being complacent.
people are not insane for trying out the hot new alternative to Twitter, a site that once was an integral part of many people’s lives for financial, professional, social, political, and personal reasons. especially not when it’s so easy to use for anyone with an instagram account already. you don’t need an invitation like for mastodon and pillowfort, it’s not mostly empty like blue sky, it’s not some kickstarter that might never see the light of day, or a small startup that can be slapp-sued into bankruptcy the second it becomes real competition to the bird app.
Meta is ruthlessly exploiting people. they’re evil. blame them.


People who use Threads are literally insane
2K notes
·
View notes
Text
NordVPN a popular VPN service provider is giving away 1-year premium subscription to our readers. The winner of this giveaway will be able to use the NordVPN service for 1 year absolutely free. How Enter Contest? Win 1 Year Free Subscription For NordVPN What Is NordVPN? Based in Panama, which is known for not having any data retention laws, with 739 servers in 58 countries, a reasonable pricing and wide set of benefits including no logs policy, NordVPN is one of the top options to consider when choosing your VPN service provider. Read full NordVPN review here Main features No logs policy Located in Panama User-friendly interface P2P friendly Wide variety of servers Up to 6 simultaneous connections No bandwidth limit Own DNS servers Flexible payment system IKEv2/IPsec & OpenVPN security protocols Why do you need a VPN? If you are reading this review, you are probably aware of online privacy issues. If I am right, please jump into the next section for a NordVPN review. Here is a short explanation of VPN service for those not familiar with VPN services. VPN stands for a Virtual Private Network which secures your activity online by encrypting your data first and only then sending it to a chosen server. When using VPN, your IP address is hidden so that no one could spy on you or use your personal data for unwanted spam, advertising or identity theft. Another great thing about VPN that it allows you to bypass geographical restrictions and to access media content that may be not allowed in your country or region. Complete privacy and benefits NordVPN lets you to choose from 739 servers, located in 58 countries and also servers, customized for those who have specific online access requirements: Anti DDoS, Double VPN, Onion Over VPN, P2P for easy file sharing or popular Ultra Fast TV for online video streaming. Anti-DDoS servers protect your data from unexpected denial of service attacks while Double VPN is customized for taking extra care of your safety using double encryption and sending a connection through two servers instead of one. If you need a permanent IP address for frequent logins or particular page visits, you can also order a Dedicated IP for an additional fee. What is also good that NordVPN has its own DNS servers that prevent unexpected data leaks and a offers a useful kill switch option that shuts down certain applications in case of a sudden VPN disconnection. NordVPN supports all operating systems, has no bandwidth limit and offers up to 6 simultaneous connections which are more than enough to secure your desktop, mobile and home devices such as smart TV, game consoles, and routers. NordVPN accepts payments via PayPal, credit cards, or Bitcoin for those who want extra privacy. Simply choose one of three subscription options, download and install an app on your device and enjoy complete privacy online. Oh, and if you are one of those not willing to commit too fast, you will like their free 3-day trial to get comfortable with service and make up your mind. Although NordVPN website nicely points out its wide set of benefits and offers you a comprehensive service information, I found it a little bit difficult to find the downloads section which is hidden under the Tools and Information. After solving this matter, I successfully downloaded NordVPN to my Mac and iPhone and with a few clicks was ready to go. The app itself offers you a nice minimal interface and pleasant user-experience. I liked an interactive map where you can see all NordVPN servers and quickly pick one. You can also access a server list using menu section on the left or simply type in the server name in a search bar instead of scrolling the whole list. The app allows you to turn on automatic server connection or customizable Kill Switch which closes selected applications in case of sudden VPN disconnection. All you have to do is add applications you want to stop. First-time-users like me will find it useful to read a comprehensive
user guide, however, if you still have questions or experience any difficulties, you can use a direct email or live chat support option. Because of a wide variety of servers, multiple device support with no band limits and top notch security features NordVPN really stands out from the crowd. Overall, what impressed me the most is the fact that they take my privacy seriously and unlike most VPN providers have a super strict no logs policy - NordVPN does not monitor my online activity, does not store any of my login data so they could not share it with anybody even if they wanted to. This is the kind of approach you’d expect from your VPN provider.
0 notes
Text
Stay Secure: Essential Tips for Using Solarmovies Safely
What is Solarmovies?
Solarmovies is a popular online streaming platform that allows users to watch a wide variety of movies, TV shows, and other video content for free. The website has gained significant traction over the years, attracting millions of users worldwide who are drawn to its extensive library of content and the convenience of streaming.
However, as with any online service that provides free access to copyrighted material, Solarmovies is not without its risks. In this article, I will explore the potential dangers of using Solarmovies and provide essential tips to help you stay safe while enjoying your favorite movies and TV shows.

The risks of using Solarmovies
Using Solarmovies, or any similar free streaming platform, can expose you to a variety of risks, including:
Legal Consequences: Streaming copyrighted content without permission from the copyright holders is generally considered illegal in most countries. Depending on the laws in your region, you could face fines or even criminal charges for using Solarmovies.
Malware and Viruses: Solarmovies and other similar websites are often breeding grounds for malware, viruses, and other malicious software. Cybercriminals may use these platforms to distribute malware that can compromise your device and steal your personal information.
Privacy Concerns: When you use Solarmovies, your online activities and browsing history can be tracked and monitored by the website's operators, as well as by your internet service provider (ISP) and potentially even by government agencies.
Unreliable Content Quality: The content available on Solarmovies may not always be of high quality, and you may encounter issues such as poor video or audio quality, missing subtitles, or even incomplete or corrupted files.
How to stay safe while using Solarmovies
To mitigate the risks associated with using Solarmovies, it's essential to take proactive measures to protect yourself and your device.
Secure internet browsing tips
Use a Secure Browser: Consider using a privacy-focused browser, such as Firefox or Tor, which offer enhanced security and privacy features.
Enable Ad-Blocker: Install a reputable ad-blocker extension or plugin to prevent unwanted ads and potentially malicious content from being displayed on the Solarmovies website.
Keep Your Software Up-to-Date: Ensure that your operating system, web browser, and other software are always up-to-date with the latest security patches and updates.
Using a VPN for added security
Choose a Reputable VPN Provider: Invest in a reliable and trustworthy virtual private network (VPN) service to encrypt your internet traffic and hide your IP address.
Connect to a Secure VPN Server: When using Solarmovies, always connect to a VPN server located in a country with strong data privacy laws, such as Switzerland or Panama.
Enable the VPN's Kill Switch: Many VPN providers offer a "kill switch" feature that automatically disconnects your internet connection if the VPN connection is lost, preventing your real IP address from being exposed.
Avoiding malware and viruses on Solarmovies
Scan for Malware: Before downloading or streaming any content from Solarmovies, scan your device with a reputable antivirus or anti-malware software to ensure that it is free from any malicious threats.
Be Cautious of Suspicious Links and Pop-ups: Avoid clicking on any suspicious links or pop-ups that may appear on the Solarmovies website, as they could be attempts to distribute malware.
Use a Dedicated Streaming Device: Consider using a dedicated streaming device, such as a Roku or Amazon Fire TV Stick, instead of your primary computer or smartphone to access Solarmovies. This can help isolate any potential threats and prevent the spread of malware to your other devices.
Legal considerations when using Solarmovies
Understand the Legal Implications: Familiarize yourself with the copyright laws and regulations in your country or region regarding the use of unauthorized streaming platforms like Solarmovies.
Weigh the Risks: Carefully consider the potential legal consequences of using Solarmovies, as the penalties can be severe in some cases.
Explore Legal Alternatives: Instead of using Solarmovies, consider subscribing to legitimate streaming services or exploring other legal options for accessing movies and TV shows.
Alternatives to Solarmovies for safe streaming
If you're looking for a safer and more reliable way to stream movies and TV shows, here are some alternative options to consider:
Subscription-based Streaming Services: Services like Netflix, Hulu, Amazon Prime Video, and Disney+ offer a vast selection of content for a monthly or annual subscription fee.
Free, Legal Streaming Platforms: Platforms like Crackle, Tubi, and Pluto TV provide free access to a range of movies and TV shows, while ensuring that the content is licensed and legally available.
Rental or Purchase Options: Platforms like iTunes, Google Play, and Amazon Video allow you to rent or purchase individual movies and TV shows, providing a legal and secure way to access the content you want.
Conclusion
While Solarmovies may seem like an attractive option for free streaming, the risks associated with using the platform outweigh the potential benefits. By taking proactive steps to secure your online activities, using a reliable VPN, and exploring legal alternatives, you can enjoy your favorite movies and TV shows without compromising your safety or exposing yourself to legal consequences.
1 note
·
View note
Text
Privacy Software: Protecting Your Digital Identity in the Modern World
In an era of increasing digital surveillance and data breaches, privacy software has become an essential tool for individuals seeking to protect their online information and personal data. This comprehensive guide explores the world of privacy software, its importance, and how it can safeguard your digital presence.

What is Privacy Software?
Privacy software encompasses a range of digital tools designed to protect user data, anonymize online activities, and prevent unauthorized tracking, monitoring, and data collection. These solutions work across various platforms and devices to create a shield around your digital identity.
Types of Privacy Software
1. Virtual Private Networks (VPNs)
VPNs are perhaps the most well-known privacy tools. They create an encrypted tunnel for your internet traffic, masking your IP address and making it difficult for third parties to track your online activities. A quality VPN can:
Hide your real location
Protect you on public Wi-Fi networks
Bypass geographical restrictions
Prevent ISPs from monitoring your browsing history
2. Encrypted Messaging Applications
Secure messaging apps ensure that your communications remain private and protected from unauthorized access. These apps use end-to-end encryption, meaning only the sender and recipient can read the messages.
3. Password Managers
These tools help you create and store complex, unique passwords for different accounts, reducing the risk of security breaches. They encrypt your password database and often provide additional security features like two-factor authentication.
4. Anonymous Browsers
Specialized browsers like Tor focus on anonymizing your web browsing, routing your traffic through multiple servers to conceal your identity and location.
Choosing the Right Privacy Software
When selecting privacy tools, consider:
Your specific privacy needs
Budget
Ease of use
Compatibility with your devices
Company reputation
Privacy policy and data logging practices
Top Recommendations
VPNs
NordVPN
ProtonVPN
Mullvad
ExpressVPN
Encrypted Messaging
Signal
Wire
Telegram (secret chats)
Password Managers
1Password
Bitwarden
LastPass
Anonymous Browsers
Tor Browser
Brave Browser
Privacy Software Best Practices
Use multiple privacy tools for comprehensive protection
Regularly update your software
Read privacy policies carefully
Use strong, unique passwords
Enable two-factor authentication
Be mindful of the information you share online
Emerging Trends in Privacy Software
Increased use of AI for threat detection
More comprehensive privacy suites
Enhanced encryption technologies
Greater focus on mobile device protection
Blockchain-based privacy solutions
Conclusion
Privacy software is no longer a luxury but a necessity in our interconnected digital world. By understanding available tools and implementing a multi-layered approach to digital privacy, individuals can significantly reduce their risk of data breaches, tracking, and unauthorized surveillance.
Remember, privacy is a fundamental right. Investing in robust privacy software is an investment in protecting your digital identity and personal information.
Frequently Asked Questions
Why do I need privacy software?
Privacy software protects you from:
Data tracking by corporations
Potential cyber attacks
Unauthorized surveillance
Identity theft
Invasive targeted advertising
Are free privacy tools effective?
While some free tools offer basic protection, paid services typically provide:
More robust encryption
Faster connection speeds
Comprehensive feature sets
Better customer support
No logging of user data
Can privacy software completely protect my online identity?
No single tool can provide 100% protection. Privacy software significantly reduces risks, but users must also:
Practice good digital hygiene
Use strong, unique passwords
Be cautious about sharing personal information
Keep software updated
Use multiple layers of protection
Is using privacy software legal?
In most countries, using privacy software is entirely legal. However, some regions have restrictions:
China heavily regulates VPN usage
Russia requires VPN providers to log user data
Some countries block certain privacy tools
How much does privacy software cost?
Pricing varies widely:
Basic VPN services: $3-$12 per month
Comprehensive privacy suites: $50-$120 annually
Some tools offer free versions with limited features
Does privacy software slow down my internet?
Privacy tools can potentially reduce internet speed due to:
Encryption processes
Routing through additional servers
Distance to VPN servers
However, modern privacy software minimizes performance impact, and the trade-off for enhanced security is often worthwhile.
0 notes
Text
Enhancing Cybersecurity: How IP Address Analysis Can Prevent Fraud and Chargebacks in Australia
In the digital age, businesses in Australia face increasing threats from cybercriminals seeking to exploit vulnerabilities for financial gain. One of the most effective tools for enhancing cybersecurity and preventing fraud and chargebacks is IP address analysis. By scrutinising IP addresses, businesses can identify suspicious activities, protect against fraudulent transactions, and reduce the risk of chargebacks. This article explores the role of IP address analysis in cybersecurity, its benefits, and how to implement it effectively to safeguard your Australian business.
1. Understanding IP Address Analysis
IP address analysis involves examining the unique numerical labels assigned to devices connected to the internet. Each IP address is linked to a specific geographic location, ISP, and sometimes even individual users. By analysing these details, businesses can gain insights into the legitimacy of online activities and detect potential threats.
Key components of IP address analysis include:
Geolocation: Identifies the physical location of an IP address, such as the country, city, and sometimes even specific coordinates.
IP Reputation: Assesses the trustworthiness of an IP address based on historical data and known associations with malicious activities.
Provider Information: Determines whether an IP address is linked to a residential user, data centre, VPN, or proxy server.
2. The Role of IP Address Analysis in Preventing Fraud
2.1 Detecting Suspicious Activities
IP address analysis can help detect suspicious activities by flagging anomalies in user behaviour. Key indicators include:
Unusual Geolocation: If a user’s IP address suddenly changes from one location to another that is geographically distant, it may indicate a compromised account or fraudulent activity. For example, a sudden shift from a regional town in Australia to a major city overseas could be a red flag.
High-Risk IP Addresses: IP addresses associated with known VPNs, proxies, or data centres can be indicative of attempts to mask true identities. Identifying these can help in scrutinising transactions more closely.
Multiple Accounts from Same IP: Multiple user accounts originating from a single IP address can suggest fraudulent behaviour, especially if the accounts exhibit suspicious activities.
2.2 Verifying User Authenticity
IP address analysis helps in verifying the authenticity of users by:
Cross-Referencing with Known Data: Compare user IP addresses against databases of known fraudulent IPs to identify potential risks.
Checking for Consistency: Ensure that the IP address aligns with the user’s claimed location and account history. Discrepancies can warrant additional verification steps.
2.3 Monitoring for Bot Activities
Automated bots are often used for fraudulent activities, such as scraping content or making bulk transactions. IP address analysis can help in:
Identifying Bot Traffic: Unusual patterns, such as high-frequency requests from a single IP address, can indicate bot activity.
Blocking Malicious IPs: IP addresses identified as sources of bot activity can be blocked or flagged to prevent further issues.
3. The Impact of IP Address Analysis on Chargebacks
Chargebacks occur when a customer disputes a transaction with their bank, leading to the reversal of payment. They can be costly for businesses and may indicate fraudulent activities. IP address analysis plays a crucial role in:
3.1 Preventing Fraudulent Transactions
By analysing IP addresses, businesses can:
Detect Chargeback Risks: Flag transactions from high-risk IP addresses or those showing suspicious behaviour, such as unusual geolocation shifts or known proxy use.
Implement Additional Verification: For transactions from flagged IP addresses, businesses can request additional verification from the user, such as identity proof or transaction confirmation.
3.2 Reducing Chargeback Rates
Effective IP address analysis can lead to a reduction in chargebacks by:
Enhancing Fraud Prevention: Identifying and addressing fraudulent transactions before they are processed can significantly lower the number of chargebacks.
Improving Dispute Management: Having detailed IP address analysis records can provide evidence to dispute fraudulent chargeback claims effectively.
4. Implementing IP Address Analysis in Your Business
4.1 Choose the Right Tools and Services
Invest in reliable IP address analysis tools and services that offer:
Real-Time Data: Access to up-to-date geolocation and IP reputation data for accurate analysis.
Comprehensive Databases: Information on known malicious IPs, VPNs, proxies, and data centres.
Integration Capabilities: Compatibility with your existing security and fraud detection systems.
4.2 Integrate IP Analysis with Fraud Detection Systems
Combine IP address analysis with other fraud detection measures to enhance overall security:
Cross-Referencing with Behavioural Data: Integrate IP analysis with user behaviour data to identify inconsistencies and potential threats.
Automated Alerts and Actions: Set up automated alerts for suspicious IP addresses and predefined actions, such as additional verification steps or transaction holds.
4.3 Educate Your Team
Ensure your team understands the importance of IP address analysis and how to use it effectively:
Training on Detection Techniques: Provide training on identifying suspicious IP address patterns and implementing appropriate responses.
Regular Updates: Keep your team informed about the latest trends in cyber threats and IP address analysis techniques.
4.4 Continuously Monitor and Review
Regularly review and update your IP address analysis strategies to adapt to evolving threats:
Monitor for Emerging Threats: Stay updated on new fraud tactics and IP address-related threats.
Evaluate Tool Performance: Periodically assess the effectiveness of your IP address analysis tools and make improvements as needed.
5. Case Studies of Successful IP Address Analysis
5.1 E-Commerce Platform
An Australian e-commerce company implemented IP address analysis to detect fraudulent transactions. By identifying and blocking transactions from known VPNs and high-risk IP addresses, they significantly reduced chargeback rates and improved overall transaction security.
5.2 Financial Services Firm
A financial institution used IP address analysis to enhance its fraud detection system. By cross-referencing IP addresses with known malicious databases and monitoring for unusual geolocation shifts, they successfully prevented several fraudulent activities and reduced chargebacks.
5.3 Subscription Service
A subscription-based service utilised IP address analysis to prevent account sharing and fraudulent sign-ups. By analysing IP addresses for anomalies and blocking suspicious connections, they maintained the integrity of their subscription model and reduced revenue losses.
6. Conclusion
IP address analysis is a powerful tool for enhancing cybersecurity, preventing fraud, and reducing chargebacks in Australian businesses. By leveraging advanced IP analysis techniques, businesses can identify suspicious activities, verify user authenticity, and implement effective fraud prevention measures. Investing in reliable tools, integrating IP analysis with existing systems, and continuously monitoring for emerging threats are key to safeguarding your business from cyber risks.
As the digital landscape evolves, staying informed about the latest IP address analysis techniques and best practices will help you maintain a secure and resilient online presence. By proactively addressing potential threats and optimising your fraud prevention strategies, you can protect your business and ensure a safer, more trustworthy experience for your customers.
0 notes