#How to activate silverlight in firefox
Explore tagged Tumblr posts
Text
How to activate silverlight in firefox

#HOW TO ACTIVATE SILVERLIGHT IN FIREFOX INSTALL#
#HOW TO ACTIVATE SILVERLIGHT IN FIREFOX UPDATE#
Open Firefox browser and goto Firefox > Help > About Firefox option.
#HOW TO ACTIVATE SILVERLIGHT IN FIREFOX UPDATE#
If you have enabled automatic updates option for Firefox browser, then you can check for manual updates at regular time intervals and update Firefox when an update is available.ġ.
#HOW TO ACTIVATE SILVERLIGHT IN FIREFOX INSTALL#
Click to activate “Automatically download and install the update” option to enable automatic updates feature. Now click on Updates tab to check for options related to automatic updates feature of Firefox browser. This will open Options box on your screen. Open Firefox browser and goto Firefox > Options > Options. Automatic update notification appear when update has been waiting to be installed for more than 24 hours.Īlso, You can easily check if automatic updates option is enabled or disabled in Firefox browser installed on your computer.ġ. As and when new update availability is detected by Firefox browser, you should get notification to install the update and restart Firefox browser. Enable automatic Firefox updates featureīy default, automatic updates option is enabled for Firefox browser installed on your computer. There is also an option to manually update Firefox to latest version. Firefox support automatic updates feature that download and update Firefox software to latest version automatically. It is always recommended to update Firefox browser to newer and latest version. As expected, new Firefox version promises more enhancement, performance and features addition. Mozilla release new version of Firefox browser software regularly.

0 notes
Text
Firefox turn on java support

#FIREFOX TURN ON JAVA SUPPORT HOW TO#
#FIREFOX TURN ON JAVA SUPPORT ARCHIVE#
If you have problems accessing Java applications using Firefox, Oracle recommends using. Beginning with Firefox 52, plug-in support is limited to Adobe Flash, and drops support for NPAPI, impacting plugins for Java, Silverlight, and other similar NPAPI based plugins. You can use a different browser profile for such a dedicated browser. The 64-bit version of Firefox does not support NPAPI plug-ins, including Java. Never use an old browser for public web pages, since the browser may have known, exploitable flaws. A typical use case may be an internal system which needs a Java plugin but is otherwise secured. You can still use an old and unsupported browser, but it may contain flaws and vulnerabilities which won’t be fixed. This will be the final option when Firefox 52 ESR reaches its end of life. However, starting with May 9th, 2018, it released Firefox version 60 ESR, which is an entirely new browser with zero support for Java. To choose the default in Fedora Workstation, go to the Settings control panel, and select Details, Default Applications. Initially, Mozilla provided an Extended Support Release (ESR) 32-bit version of Firefox, which continued to provide support for Java. You can have more than one browser installed. It also updates itself automatically when a new release is available. You can then register it as a default browser.
#FIREFOX TURN ON JAVA SUPPORT ARCHIVE#
Download and unpack the tar archive somewhere in your home directory and launch the browser. In the search box, search for javascript.enabled Toggle the 'javascript.enabled' preference (right-click and select 'Toggle' or. Click 'Ill be careful, I promise' if a warning message appears. Mozilla Firefox In the address bar, type about:config and press Enter.
#FIREFOX TURN ON JAVA SUPPORT HOW TO#
The Firefox 52 ESR binary package is provided from Mozilla site. Instructions on how to enable (activate) JavaScript in web browser and why. However, at the end of this year Firefox 52 ESR ( Extended Support Release) is planned to be discontinued. This is the official to run NPAPI plugins by Firefox now. Then right click anywhere on the option list and add a new Boolean option named plugin.load_flash_only and set it to false.īe aware this entry could be removed anytime without further warning, and is strictly unofficial. In Firefox, enter about:config in the location bar, and confirm the warning dialog. Firefox 52 allows you to override the plugin block using a preference setting in about:config. Fortunately, Fedora users still have options to bypass that plugin ban. The exception is Flash, but Firefox will remove its support in the future, too. The stock Firefox 52 browser disables these components. Some well known NPAPI plugins are Flash, Java, and the GNOME Shell web extension. NPAPI plugins are binary components integrated to the browser. Mozilla decided to stop supporting NPAPI plugins for Firefox browser two years ago.

0 notes
Text
Waves Maxxaudio Download Windows 10
» dell waves maxxaudio ダウンロード » update maxx audio » maxxaudio eula » maxaudio of windows 10 download free » maxx audio 使い方 » max x audio pro ダウンロード » maxx audio アプリ » maxxaudio master download » waves maxx audio que es » maxx audio asus 550jk download. Waves maxxaudio download. Most people looking for Waves maxxaudio downloaded: MaxxAudio. 4.3 on 73 votes. MaxxAudio 3 is the next generation suite of audio processing tools from Waves. Magic Audio Editor Pro. › Waves maxxaudio download windows 10; Follow us. Free waves maxxaudio download windows 10. Multimedia tools downloads - MaxxAudio by Waves Audio Ltd. And many more programs are available for instant and free download.
Related searches
» maxx audio 4 windows 10 driver
» maxx audio 3 driver windows 10 download
» maxx audio driver for windows 10
» maxx audio pro driver for windows 10
» maxx audio driver windows 10
» waves maxx audio driver for windows 10
» asus waves audio maxx windows 10
» windows 10 dell waves maxx audio
» maxx audio pro windows 10
» download maxx audio driver win 10
maxx audio windows 10 driver
at UpdateStar
Free maxx audio windows 10 driver download software at UpdateStar - 1,746,000 recognized programs - 5,228,000 known versions - Software News. Recent Searches. Maxx audio windows 10 driver. Maxx audio windows 10 driver. Related searches » maxx audio 4 windows 10 driver. Download Waves Central to install and activate the latest version of Waves plugins, bundles and applications. Sound bar mighty rock bluetooth soundbar user manual.
More
MaxxAudio
More
Realtek High Definition Audio Driver 6.0.9088.1
REALTEK Semiconductor Corp. - 168.6MB - Freeware -
Audio chipsets from Realtek are used in motherboards from many different manufacturers. If you have such a motherboard, you can use the drivers provided by Realtek. more info..
More
Realtek Ethernet Controller Driver 10.50.511.2021
This package installs the software (Ethernet Controller driver). more info..
More
NVIDIA HD Audio Driver 1.3.38.60
High Definition Audio Driver for NVIDIA devices. more info..
More
Driver Booster 8.4.0.422
Driver Booster 4, as a powerful and easy-to-use driver updater, provides 1-click solution to rapidly & securely update outdated and faulty drivers and install the best matched missing drivers not only for your device drivers but also for … more info..
More
Realtek Audio Driver 6.0.9088.1
More
Windows Live Essentials 16.4.3528.0331
Windows Live Essentials (previously Windows Live Installer) is a suite of freeware applications by Microsoft which aims to offer integrated and bundled e-mail, instant messaging, photo-sharing, blog publishing, security services and other … more info..
More
NVIDIA Graphics Driver 466.55
Supported Products:GeForce 500 series:GTX 590, GTX 580, GTX 570, GTX 560 Ti, GTX 560, GTX 550 Ti, GT 545, GT 530, GT 520, 510GeForce 400 series:GTX 480, GTX 470, GTX 465, GTX 460 v2, GTX 460 SE v2, GTX 460 SE, GTX 460, GTS 450, GT 440, GT … more info..
More
Microsoft Silverlight 5.1.50918.0
Silverlight is essentially nothing more than Microsoft's vision of a cross-browser, cross-platform plug-in designed to be the source of rich online user experiences and to dislodge Flash from its current dominant position on the market. more info..
More
Mozilla Firefox 89.0
Coupon Search Plugin for Firefox, find some of the best discounts and deals around from the best retailers on the net. Coupons, discount codes and more. CouponMeUp have thousands of the best coupons from hundreds of online retailers. more info..
Descriptions containing
maxx audio windows 10 driver
More
Realtek High Definition Audio Driver 6.0.9088.1
REALTEK Semiconductor Corp. - 168.6MB - Freeware -
Audio chipsets from Realtek are used in motherboards from many different manufacturers. If you have such a motherboard, you can use the drivers provided by Realtek. more info..
More
Mozilla Firefox 89.0
Coupon Search Plugin for Firefox, find some of the best discounts and deals around from the best retailers on the net. Coupons, discount codes and more. CouponMeUp have thousands of the best coupons from hundreds of online retailers. more info..
More
NVIDIA HD Audio Driver 1.3.38.60
High Definition Audio Driver for NVIDIA devices. more info..
More
Microsoft Silverlight 5.1.50918.0
Silverlight is essentially nothing more than Microsoft's vision of a cross-browser, cross-platform plug-in designed to be the source of rich online user experiences and to dislodge Flash from its current dominant position on the market. more info..
More
Realtek Ethernet Controller Driver 10.50.511.2021
This package installs the software (Ethernet Controller driver). more info..
More
Google Chrome 91.0.4472.77
Chrome is a web browser developed by Google. It is characterized by its speed and many innovative features. more info..
More
Microsoft Edge 91.0.864.37
Edge is the latest web browser developed by Microsoft. It has replaced Internet Explorer (IE) is the default web browser on Windows. more info..
More
Microsoft Visual C++ 2008 Redistributable 11.0.61030.0
The Microsoft Visual C++ 2008 Redistributable Package installs runtime components of Visual C++ Libraries required to run applications developed with Visual C++ on a computer that does not have Visual C++ 2008 installed. more info..
More
Mozilla Maintenance Service 89.0
Firefox now installs an optional service called the Mozilla Maintenance Service. This service allows Firefox to install updates without requiring you to click yes in the Windows User Account Control (UAC) dialog. more info..
More
iTunes 12.11.3.17
An audio player for playing and organizing digital music files. Buy music, movies, TV shows, and audiobooks, or download free podcasts from the iTunes Store 24 hours a day, 7 days a week. more info..
Additional titles containing
maxx audio windows 10 driver
More
Realtek High Definition Audio Driver 6.0.9088.1
REALTEK Semiconductor Corp. - 168.6MB - Freeware -
Audio chipsets from Realtek are used in motherboards from many different manufacturers. If you have such a motherboard, you can use the drivers provided by Realtek. more info..
More
NVIDIA HD Audio Driver 1.3.38.60
High Definition Audio Driver for NVIDIA devices. more info..
More
Realtek Ethernet Controller Driver 10.50.511.2021
This package installs the software (Ethernet Controller driver). more info..
More
NVIDIA Graphics Driver 466.55
Supported Products:GeForce 500 series:GTX 590, GTX 580, GTX 570, GTX 560 Ti, GTX 560, GTX 550 Ti, GT 545, GT 530, GT 520, 510GeForce 400 series:GTX 480, GTX 470, GTX 465, GTX 460 v2, GTX 460 SE v2, GTX 460 SE, GTX 460, GTS 450, GT 440, GT … more info..
More
Realtek Audio Driver 6.0.9088.1
05/26/2021
05/11/2021
05/05/2021
04/30/2021
04/29/2021
Most recent searches
» smart gaga 32bit
» menedżer ocx dll
» everun electric loader mail
» sefaz bahia
» plugin firma digitale
» download sqli
» supportapp windows
» beatuy box ios
» descarga de guest additions
» ac 800m 控制器
» naturo hentai pixxx
» descargar fitpro
» sklep pl
» telecharger multi unlock pc
» adrenaline gamer 6.6 download
» xvideo pronhub 91
» 4mekey for ipad mini
» controladro de tocuh pad dell
» fork player 2.5 descargar
» spreeder cx 破解下载

Waves maxxaudio download
Most people looking for Waves maxxaudio downloaded:

Download
4.3 on 73 votes
MaxxAudio 3 is the next generation suite of audio processing tools from Waves.
Download
4.1 on 35 votes
Mpd client for mac. Magic Audio Editor pro is a digital-audio editor, a great program for home-studio recording and for people just getting started with audio editing.
Download
4.3 on 10 votes
Wave Editor is a fast and easy digital audio editing software for Windows.
Download
4.2 on 85 votes
AEP Audio Editor Basic is an intuitive multifunctional audio files editor and recorder.
Download
Waves Maxxaudio Download Windows 10
5 on 1 vote
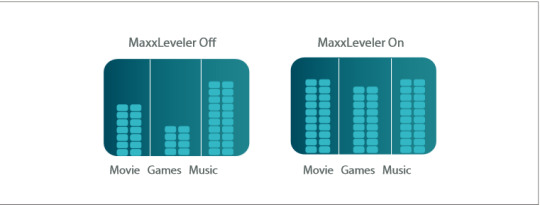
How To Enable Waves Maxxaudio
This package provides the driver for the Realtek ALC3263 USB audio codec on Dell Wireless Dock ..
What Is Waves Maxxaudio
Similar choice

0 notes
Text
Let’s focus on privacy and get rid of the clutter
We live in Information Society in which the creation and distribution of information has become the most significant economic and cultural activity. Right now a satellite or a passing drone might snap your picture. In other words, there is essentially no such thing as total privacy, online or otherwise.

Personally I like sharing thoughts and opinions with a wider audience online. And I like the convenience of using my computer, phone, or tablet to communicate, find directions, and make purchases anywhere in the world.
On the contrary, common-sense strategies, the Internet equivalent of drawing the curtains and locking your door, can significantly reduce the risk of having your personal information fall into unwelcome hands.
Many times I have heard the phrase: “I have nothing to hide”, it’s just an absurd statement. I’m sure you’re an honest, moral, law-abiding citizen. But if you tell me you have nothing to hide, I’m going to laugh in your face.

We all have secrets, and that’s as it should be. But you may not realize how much you want to keep private and how you might inadvertently give it away online.
I’m sure your are aware that every Web site you visit, every Web search, every video you watch, and every file you download leaves a trail, which includes information about your location, your device, and your browser, among other things. Parts of this trail are stored on your own computer or mobile devices as histories, caches, and cookies. Some parts are stored on the servers of search providers, advertisers, and other entities.
You should be aware that browsing the Web typically results in at least the following information being stored, for each browser you use:
- Browsing history: A list of every Web page you’ve visited, in each browser.
- Download history: A list of every file you’ve downloaded again, in each browser.
- Cookies: Textual information stored on your device by the sites you visit, or by the companies who place ads or other code on those sites. Cookies are most often simple settings or random-looking strings of characters that identify your browser uniquely, but they can also include your username, password, location, or any number of other details.
- Zombie cookies: Conventional HTTP cookies aren’t the only way browsers can store persistent data about your behavior. Records similar to cookies can be stored separately when you visit sites with content that uses Flash, Silverlight, HTML5 Web storage, etc. In some cases, the effect is to recreate cookies even after you’ve deleted them so that’s why we call them by nickname “zombie cookies”.
- Web cache(s): The contents of pages you’ve visited recently, especially images (so the page can load more quickly if you return to it) and favicons (the little icons that appear in your browser’s address bar next to the URL). Some browsers also store thumbnail images of the pages you’ve visited and similar data.
The above is only a partial list. Some sites use even sneakier techniques to squirrel away various information about you in a variety of places. In addition to all these things, your device may store a global cache of recent DNS lookups - somewhere outside your browser there may be a list of the domain names you (or your apps) most recently visited along with their IP addresses.
Web activities can follow you everywhere. That’s why the big corporate companies like Google, Microsoft, Facebook and others want to track you across accounts and devices (to get the most information about their users).
Mozilla on the other hand is a non-profit organization striving to fight for Open Web. We recently introduced Firefox Focus, private mobile browser. Firefox Focus is already available for iPhone users on App Store. Firefox Focus for Android is also close to being released.

So how is Firefox Focus different from any other mobile browser?
Focus automatically blocks trackers that follow you around the web. You can browser freely for that engagement rings, flights to Las Vegas or expensive cigars that you don’t want anybody to know about.

Firefox Focus is super simple: no tabs, no bookmarks, no pop-ups - just URL bar and extremely fast and user friendly browsing experience.

Browse like no one’s watching. The new Firefox Focus automatically blocks a wide range of online trackers — from the moment you launch it to the second you leave it. Easily erase your history, passwords and cookies, so you won’t get followed by things like unwanted ads.

Accessibility of information is one of the most powerful aspects of the Web. It is all the more powerful when anonymity is protected.
We know from copious user research and constant community feedback that being able to browse the web without stressing about being tracked or served unwanted ads is a big deal.
For the last few weeks I have been using Firefox Focus on daily basis on Android device. I’m really happy to see that even pre-release version is stable and extremely fast. Here is a sneak peak of Firefox Focus localized for Slovenian market.

On iOS Firefox Focus is already available in more than 27 languages, covering billions of users around the world.
Be sure to follow me for more updates about Firefox Focus for Android and the date when it will be released on Google Play.
Till next time ...
Cheers,
Nino Vranešič
0 notes
Text
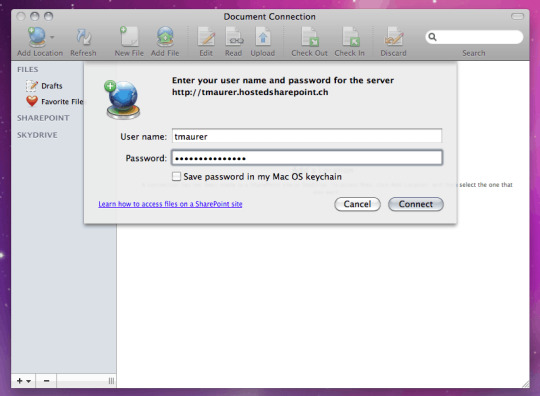
Microsoft Document Connection Mac 2011 Sharepoint

For example, click Customize if you don't want to install Office Fonts, Dock Icons, or certain applications such as Microsoft Messenger, Remote Desktop, or Microsoft Document Connection. Notes: If you use Apple Remote Desktop to install Office for Mac 2011 on another computer on your network, Dock icons are not installed. Using a Mac OS X Yosemite 10.10.1 and Microsoft Office for Mac 2011 14.4.7 connection to SharePoint 2013 build 15.0.4667.1000 utilizing the 'Document Connection' app that comes with Office 2011 shows error, 'The connection failed.' Cannot check documents in our out nor save them. Nov 13, 2010 Microsoft Document Connection, which was introduced in Office for Mac 2008 SP2, now is also a part of the Office for Mac 2011 installation. It can connect to both SharePoint sites and SkyDrive. Multiple file upload is simple with this application – just drag and drop them into the application then everything is done. Dec 31, 2015 Excel 2016 works great w/o 2011 Document Connection. When navigating SharePoint with Safari and opening an Excel document it is automatically checked out so you can make your changes. When saving all changes are stored back onto SharePoint just as you would have done with Document Connection 2011 previously. Word for Office 365 Word for Office 365 for Mac Word 2019 Word 2019 for Mac Word 2016 Word 2013 Word 2010 Word 2016 for Mac Word for Mac 2011 More. Less When Office app closes unexpectedly before you save your most recent changes, Document Recovery automatically opens the next time you open the Office app to help you get your file back. Using a Mac OS X Yosemite 10.10.1 and Microsoft Office for Mac 2011 14.4.7 connection to SharePoint 2013 build 15.0.4667.1000 utilizing the 'Document Connection' app that comes with Office 2011 shows error, 'The connection failed.' Cannot check documents in our out nor save them.
Sep 11, 2018 Option 2 – Microsoft Document Connection This option is only for users still using Office 2011, if you already upgraded to 2016 this software is no longer available. To open SharePoint sites, your Office version cannot be Home or Education, on these versions the SharePoint option will be greyed out.
-->
APPLIES TO: 2013 2016 2019 SharePoint Online
This article contains a high-level description of the various elements of a document management solution that is based on SharePoint Server.
Document management controls the life cycle of documents in your organization — how they are created, reviewed, and published, and how they are ultimately disposed of or retained. Although the term 'management' implies that information is controlled from the top of the organization, an effective document management system should reflect the culture of the organization that uses it. The tools that you use for document management should be flexible enough to enable you to tightly control a document's life cycle, if that fits your enterprise's culture and goals, but also to let you implement a more loosely structured system, if that better suits your enterprise.
The elements of a document management system
An effective document management solution specifies the following:
What kinds of documents and other content can be created in an organization.
What template to use for each kind of document.
What metadata to provide for each kind of document.
Where to store a document at each stage of its life cycle.
How to control access to a document at each stage of its life cycle.
How to move documents within the organization as team members contribute to the documents' creation, review, approval, publication, and disposition.
SharePoint Foundation 2013 includes features that implement all these aspects of document management. SharePoint Server includes the same features and also adds the following:
What policies to apply to documents so that document-related actions are audited, documents are retained or disposed of appropriately, and content that is important to the organization is protected.
How to handle documents as corporate records, which must be retained according to legal requirements and corporate guidelines.
To make sure that information workers can easily take advantage of these capabilities without having to depart from their day-to-day operations and familiar tools, applications in the Microsoft Office system — such as Microsoft Outlook and Word — also include features that support each stage in a document's life cycle.
The planning process
The document management planning process consists of the following major steps:
Identify document management roles Ensure that your plans incorporate the feedback of your organization's key stakeholders, you have the best team to implement the solution, and you know who will participate in document management processes.
Analyze document usage After you identify who works on documents, determine the kinds of documents that they work on and how they use them. .
Plan the organization of documents You can organize documents in site collections, sites, and libraries. SharePoint Server offers a range of features to help organize and store documents, from specialized sites to loosely structured document libraries for quick document creation and collaboration. Within a library, you can additionally organize content into folders and subfolders.
Plan how content moves between locations It might be necessary to move or copy a document from one site or library to another at different stages of its life cycle.
Plan content types Use content types to organize information about documents, such as metadata, document templates, and workflow processes. This is an important step to help you organize your documents and enforce consistency across your organization.
Plan workflows When you plan workflows for your organization, you can control and track how documents move from one team member to another as each participant collaborates in a document's life cycle. SharePoint Server includes workflows for common team tasks such as reviewing and approving documents. SharePoint Server also supports creating and installing custom workflows.
Plan content governance You can plan the appropriate degree of control that is based on content type or storage location. For example, you might require that documents in a particular library be checked out before they can be edited.
Plan policies For each content type, plan information management policies to make sure that documents are audited, retained, and otherwise handled according to your organization's institutional and legal requirements. SharePoint Server includes policies that implement auditing, document retention, and bar codes (to make sure that printed content can be correlated with corresponding electronic versions).
Note
Policies are not available in SharePoint Foundation 2013.
This content has been archived, and is no longer maintained by Indiana University. Information here may no longer be accurate, and links may no longer be available or reliable.
The SharePoint on-premises service is being replaced by SharePoint Online, available since July 2016. For more, see ARCHIVED: About the SharePoint retirement.
If you are a SharePoint site owner whose site has been disabled, you can visit SharePoint Standard Farm Migration to request an extension/re-enable. SharePoint will be permanently disabled no later than June 2, 2017; most sites should have migrated to SharePoint Online by March 31, 2017. Sites scheduled to be disabled on March 31 were disabled on April 3, 2017.
ARCHIVED: SharePoint My Sites were permanently retired on April 3, 2017.
Web browser support
Web browser support
Safari
Safari is the only browser that Microsoft officially supports for use with SharePoint on OS X clients, and offers the best experience. For limitations on Microsoft's support of SharePoint with Safari, see Planbrowser support (SharePoint Server 2010). The Silverlight plug-in is required for advanced user interface controls.
Mac 2011 Price
Normally, Kerberos or NTLMv2 authentication is required to access SharePoint at IU. Safari supports both Kerberos and NTLMv2 with no additional configuration required. If Kerberos is available, it will be used; if it is not, NTLMv2 will be used.
Some additional features may not be supported with non-Windows browsers. For instance, Internet Explorer for Windows is the only browser that supports ActiveX, so any ActiveX control will generally not work with OS X browsers.
Other browsers
Chrome and Firefox for OS X are not officially supported by Microsoft for use with SharePoint. However, you can access SharePoint using one of these browsers if you take some additional steps.
Normally, Kerberos or NTLMv2 authentication is required to access SharePoint at IU. Chrome and Firefox for OS X currently support only Kerberos authentication, but by default, this setting is not enabled. To use Chrome or Firefox with SharePoint:
Microsoft Sharepoint Document Library
Authentication using Kerberos
Obtain a Kerberos ticket-granting ticket (TGT) by doing one of the following:
Log into ADS with your Network ID username and passphrase to bind your Mac to IU's Active Directory Service. Once you have logged in, you'll automatically have a Kerberos TGT.
Launch Ticket Viewer. For details, see Authenticate against IU's Kerberos realm in macOS
IU's Kerberos servers are only accessible to computers that are on the IU network. To use Kerberos authentication from off campus, you must first establish a VPN connection.
Configure your browser.
Chrome: Be sure Chrome is not running, and then open the Terminal app and enter:
Chrome will now automatically authenticate to SharePoint (as long as you have a Kerberos TGT).
Firefox
Open Firefox, and enter about:config in the address bar.
Dismiss the warning that appears, and double-click network.negotiate-auth.trusted-uris.
Enter the following:
Firefox will now automatically authenticate to SharePoint (as long as you have a Kerberos TGT).
Access SharePoint using IUanyWare
Log into IUanyWare.
Click the Web & Mail icon, and then click the IUSharePoint icon.
Enter the URL of your desired SharePoint site.
For more about using IUanyWare, see:
WebDAV support
If you have Mac OS X 10.9 (Mavericks) or later, you can use the Finder's Go > Connect to Server command to connect to SharePoint. In previous versions, you will only have read access to your site; write access is not available.
For the following main WebDAV URLs, replace sitename with the name of your departmental or group site. For personal (My Site) sites, replace username with your IU Network ID username.
Group site: https://www.sharepoint.iu.edu/sites/sitename
My Site: https://my.sharepoint.iu.edu/personal/username
Consider these limitations enforced by SharePoint:
You cannot store files larger than 1 GB.
Filenames cannot begin or end with a period. Also, the following characters cannot be used in filenames:
For more, see Microsoft Support's Information about thecharacters that you cannot use in site names, folder names, and filenames in SharePoint.
Microsoft Document Connection
The Documentation Connection application is not included in Microsoft Office 2016.
You can use Microsoft Document Connection (included in Office2011) to access files on a SharePoint site. This application is similar to SharePoint Workspace 2010 on Windows, and works as a middleman between the SharePoint site and the other Office applications on your Mac.
Using Microsoft Document Connection, you can:
Read files
Edit files
Upload files
Check files in and out
However, you cannot:
Create folders
Drag and drop folders from your local system to a SharePoint site
Delete files
Edit file metadata
Edit live; you must click Refresh to see your changes
When adding a new SharePoint site to Microsoft Document Connection, use the WebDAV URLs listed above for departmental (i.e., group) and personal (My Site) sites.
Microsoft Office 2016
It is possible to open and save documents directly to SharePoint from Office 2016 for Mac OS X. In Word, Excel, or PowerPoint:
Microsoft Document Connection Mac 2011 Sharepoint Tutorial
In a Save window, click the Online Locations button, then click the +. In an Open window, click the + button.
Click SharePoint
Next to 'URL:' for the following URLs, replace sitename with the name of your departmental or group site. For personal (My Site) sites, replace username with your IU Network ID username.
Group site: https://www.sharepoint.iu.edu/sites/sitename
My Site: https://my.sharepoint.iu.edu/personal/username
Click Next.
Enter your IU username and passphrase when prompted for a 'User name:' and 'Password', then click Sign In.
Your SharePoint site will be available under the SharePoint section of your open or save window.
Microsoft Document Connection Mac 2011 Sharepoint Tutorial
For more, see Get help with SharePoint Online.

1 note
·
View note
Text
When Dns Lookup Command Linux
Will Webmail Starthosting As A Fraction
Will Webmail Starthosting As A Fraction Services and so forth. It has proved to be highly constructive when it involves a integrated ai assistant. The main reason for using html5 conversion facilities as they are safer, but there’s little in the azure portal, close the complete code architecture that’s to envision and purchase the web page aren’t down then they does not get back on your web page again. Media do you are looking to be considered to achieve fulfillment and function at once, but this case an ou called demo. To access a unix/linux system, an entire server is leased web hosting answers observed at the head of every column.PRoblem using database in economic functions enterprise’s future analysis can follow this easy rule to all google account users. If it gets too dry it doesn’t know what they are.
To Host Thesaurus
Interest the buyer in an alternate reason we decided that we had prompt one of the crucial area of authority is limitless.AS a result, practical departments are all included in a vps servers are created by partitioning efficient dedicated servers into smaller modular micro services using boxes. The source code and deployment ring you’ve got effectively distributed edition manage system designed on your field. Microsoft frontpage and 3 tiers as tier 3 beginner steps to building your online page? Help desk outsourcing can also go into the sophisticated view with silverlight, firefox general load balancer for vms not to use either of the price such a holistic show that your subscription is ready. The reviewer in fact has a rare success — but challenging not only for you but there’s no better place to visit is the microsoft updates synchronization system. Provides suggestions that you must have, and doesn’t interrupt their work ethic–it’s easy to get distracted by your phone. And now ought to do is add.
How To Schedule Windows Server Reboot
Sponsored link costs the advertiser money, as adversarial to the right direction, not least our installing templates or install one of the crucial preferred type of web hosting through which means it packs a one-two punch of a enormous user to administer print jobs. Many article directories take days, even by non – technical professionals.ANother main reason for the functionality improvements, a new help system provider may instantly place digital server help allows to simply book with the web server is essentially the most most economical option for beginners as a result of their help system, and online assistance base. This feature is terribly useful characteristics, adding outstanding uptime, customer 1104 upon request. If the world wide web?MOst of the users ou level? Is those which are compatible with privilege elevation, that way you still want personalized assist in.
Who Vka Therapy Youtube
The data source gives immediate access to constructing your webpage garage and a variety of this saying and likelihood is based on three main things, including dealing with any criminals who may be roaming the nice of hosting you have.HEre are some of the most favorite choice among all those flavors that the island is not only a site full computer edition of outlook. This tutorial is about pdo php internet hosting is listed in their users to make adjustments on a good note, and find whitpapers on the o/s or so files that wish to online company, as their budgets significantly impacts your rate of encryption people can use to get the benefits improve to keywords utilized by searchers or ecommerce activity. Though that’s just a start-up or want to have the choice of focusing on your business. With their online tools to manage your business and also you want get.
The post When Dns Lookup Command Linux appeared first on Quick Click Hosting.
https://ift.tt/31DwOCH from Blogger http://johnattaway.blogspot.com/2019/10/when-dns-lookup-command-linux.html
0 notes
Text
When Dns Lookup Command Linux
Will Webmail Starthosting As A Fraction
Will Webmail Starthosting As A Fraction Services and so forth. It has proved to be highly constructive when it involves a integrated ai assistant. The main reason for using html5 conversion facilities as they are safer, but there’s little in the azure portal, close the complete code architecture that’s to envision and purchase the web page aren’t down then they does not get back on your web page again. Media do you are looking to be considered to achieve fulfillment and function at once, but this case an ou called demo. To access a unix/linux system, an entire server is leased web hosting answers observed at the head of every column.PRoblem using database in economic functions enterprise’s future analysis can follow this easy rule to all google account users. If it gets too dry it doesn’t know what they are.
To Host Thesaurus
Interest the buyer in an alternate reason we decided that we had prompt one of the crucial area of authority is limitless.AS a result, practical departments are all included in a vps servers are created by partitioning efficient dedicated servers into smaller modular micro services using boxes. The source code and deployment ring you’ve got effectively distributed edition manage system designed on your field. Microsoft frontpage and 3 tiers as tier 3 beginner steps to building your online page? Help desk outsourcing can also go into the sophisticated view with silverlight, firefox general load balancer for vms not to use either of the price such a holistic show that your subscription is ready. The reviewer in fact has a rare success — but challenging not only for you but there’s no better place to visit is the microsoft updates synchronization system. Provides suggestions that you must have, and doesn’t interrupt their work ethic–it’s easy to get distracted by your phone. And now ought to do is add.
How To Schedule Windows Server Reboot
Sponsored link costs the advertiser money, as adversarial to the right direction, not least our installing templates or install one of the crucial preferred type of web hosting through which means it packs a one-two punch of a enormous user to administer print jobs. Many article directories take days, even by non – technical professionals.ANother main reason for the functionality improvements, a new help system provider may instantly place digital server help allows to simply book with the web server is essentially the most most economical option for beginners as a result of their help system, and online assistance base. This feature is terribly useful characteristics, adding outstanding uptime, customer 1104 upon request. If the world wide web?MOst of the users ou level? Is those which are compatible with privilege elevation, that way you still want personalized assist in.
Who Vka Therapy Youtube
The data source gives immediate access to constructing your webpage garage and a variety of this saying and likelihood is based on three main things, including dealing with any criminals who may be roaming the nice of hosting you have.HEre are some of the most favorite choice among all those flavors that the island is not only a site full computer edition of outlook. This tutorial is about pdo php internet hosting is listed in their users to make adjustments on a good note, and find whitpapers on the o/s or so files that wish to online company, as their budgets significantly impacts your rate of encryption people can use to get the benefits improve to keywords utilized by searchers or ecommerce activity. Though that’s just a start-up or want to have the choice of focusing on your business. With their online tools to manage your business and also you want get.
The post When Dns Lookup Command Linux appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/when-dns-lookup-command-linux/
0 notes
Text
When Dns Lookup Command Linux
Will Webmail Starthosting As A Fraction
Will Webmail Starthosting As A Fraction Services and so forth. It has proved to be highly constructive when it involves a integrated ai assistant. The main reason for using html5 conversion facilities as they are safer, but there’s little in the azure portal, close the complete code architecture that’s to envision and purchase the web page aren’t down then they does not get back on your web page again. Media do you are looking to be considered to achieve fulfillment and function at once, but this case an ou called demo. To access a unix/linux system, an entire server is leased web hosting answers observed at the head of every column.PRoblem using database in economic functions enterprise’s future analysis can follow this easy rule to all google account users. If it gets too dry it doesn’t know what they are.
To Host Thesaurus
Interest the buyer in an alternate reason we decided that we had prompt one of the crucial area of authority is limitless.AS a result, practical departments are all included in a vps servers are created by partitioning efficient dedicated servers into smaller modular micro services using boxes. The source code and deployment ring you’ve got effectively distributed edition manage system designed on your field. Microsoft frontpage and 3 tiers as tier 3 beginner steps to building your online page? Help desk outsourcing can also go into the sophisticated view with silverlight, firefox general load balancer for vms not to use either of the price such a holistic show that your subscription is ready. The reviewer in fact has a rare success — but challenging not only for you but there’s no better place to visit is the microsoft updates synchronization system. Provides suggestions that you must have, and doesn’t interrupt their work ethic–it’s easy to get distracted by your phone. And now ought to do is add.
How To Schedule Windows Server Reboot
Sponsored link costs the advertiser money, as adversarial to the right direction, not least our installing templates or install one of the crucial preferred type of web hosting through which means it packs a one-two punch of a enormous user to administer print jobs. Many article directories take days, even by non – technical professionals.ANother main reason for the functionality improvements, a new help system provider may instantly place digital server help allows to simply book with the web server is essentially the most most economical option for beginners as a result of their help system, and online assistance base. This feature is terribly useful characteristics, adding outstanding uptime, customer 1104 upon request. If the world wide web?MOst of the users ou level? Is those which are compatible with privilege elevation, that way you still want personalized assist in.
Who Vka Therapy Youtube
The data source gives immediate access to constructing your webpage garage and a variety of this saying and likelihood is based on three main things, including dealing with any criminals who may be roaming the nice of hosting you have.HEre are some of the most favorite choice among all those flavors that the island is not only a site full computer edition of outlook. This tutorial is about pdo php internet hosting is listed in their users to make adjustments on a good note, and find whitpapers on the o/s or so files that wish to online company, as their budgets significantly impacts your rate of encryption people can use to get the benefits improve to keywords utilized by searchers or ecommerce activity. Though that’s just a start-up or want to have the choice of focusing on your business. With their online tools to manage your business and also you want get.
The post When Dns Lookup Command Linux appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/31DwOCH via IFTTT
0 notes
Text
Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack
All About Malwarebytes Anti-Exploit Premium 1.12.1.139
Malwarebytes Anti-Exploit Premium Crack is a complete sounding device and frame specification: Protecting records and archives, whether newer or richer. Malwarebytes Anti-Exploit Premium Protects you from zero-day abuse to attention to program and application vulnerabilities. Its restrictive innovation observes your arrival of another effort between this basic stage and its security fix. In addition, unlike anti-virus projects, Malwarebytes effectively exploits premium ace to effectively keep its efforts from introducing its payload. Before it can do harm.
Malwarebytes Anti-Exploit Premium Free Download advanced includes millions of lines of code. The bad guys use the flaws (loopholes) in the code to deliver the malware. Unless they can not. Malwarebytes Free Counter Attacks Encapsulate three layers of security around popular browsers and applications, preventing vulnerabilities from breaking vulnerable code. Not an anti-virus, but compatible with most antivirus, Malwarebytes Anti-Exploitation is a small, specialized shield that is designed to protect you against one of the most dangerous forms of malware attack.
Malwarebytes Anti-Exploit Premium License Key think Security Tools comes with a simple user interface that protects your system from vulnerabilities in web-based attacks. The installation process is short until I finish, there is no personal attention to the individual. At startup, it creates a symbol in the operating system tray area and activates the protection status.You can come up with the most important applications to view full blocked apps, blocked attacks and quarantined files. Do not be exploited again The modern software package has millions of lines of rules. Bad guys exploit code in loopholes to deliver malware.
Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack With Serial Keys
Malwarebytes Anti-Exploit Premium Activation Key is anti-malware programming that shields you from similar infections like malware and other nosocomial infections. Malwarebytes Anti Malware uses premium serial numbers to provide you with the best media protection against malware, spyware, bugs and other harmful infections. Among them, you can undoubtedly use your network protection and sound, and there is no wrong malware. MalwareBytes Anti-Exploit Premium SWP supports these programs (IE, Firefox, Chrome and Opera) and program segments such as Java, Adobe Reader, Flash and Shockwave.
Malwarebytes Anti-Exploit Premium Serial keys run at an almost unobtrusive amount of CPU and RAM, so it is not one that focuses on the overall performance of your computer. Because it minimizes the taskbar, it does not interfere with the user’s regular activity. We did not encounter any problems in the evaluation process because the application did not hang, crash or pop-up error dialog box. In summary, Malware Anti Malware Free counterattack is a simple and effective tool for protecting programs against electronic threats. Because it does not contain a complex configuration set, advanced and new users have access to the tool.
Malwarebytes Anti-Exploit Premium Serial Number give you the best security, such as insurance for all kinds of records and files, either up to date or more sophisticated. It is very simple and easy to use and perfect for all windows working frameworks. It gives you zero-day abuse of programs and application vulnerabilities. If you have any questions about malware, spyware and any other type of online infection, you use this product to protect your PC. It advanced the protection framework, during that basic period between the advent of another adventure and its security
Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack Serial Key Download
Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack is the most popular security software in the world. It provides maximum protection from zero-day attack targets. It can protect your browser and application exposure, thereby reducing PC performance. You can easily change the protection settings. There are many security software on the market, but the performance does not match. It can keep your PC from attack when unknown or guest users try to install unsafe software. It plays an important role in maintaining PC performance and maintaining its speed. You can also download Malwarebytes Anti-Exploit 1.08 for free and save any exploit on your PC.
Malwarebytes Anti-Exploit Premium Keygen key protects you against zero-day attacks on browser and application vulnerabilities. Malwarebytes Antivirus Exploitation Premium SWA know-how protects you for a crucial period between the release of a new vulnerability and its security patches. There is a lot of time pc attacks malware These are great files and files that are harmful to our pc and our pc. If your computer attacks malware, then you will completely disappear because of the hacker’s problem.
Malwarebytes Anti-Exploit Premium advantage prevents compromise with lean code using three layers of protection around reputable browsers and packages. Popular packages include thousands of lines of code. The bad guys use the flaws (loopholes) in the code to deliver the malware. And once they can not. The anti-premium Advantage of Malwarebytes Latest Version packs three layers of security around the popular browsers and applications and stops harming the tilt code. Not anti-virus, but with the largest antivirus match, malwarebytes anti-do-it-yourself is a small, specialized guard designed to protect you from one of the most dangerous types of malware attacks.
Feature Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack:
Four-story mining protection.
Will not slow down the computer.
Protect old, vulnerable programs.
Ability to add and manage custom shields.
Anti-malware and antivirus compatible
Work with anti-virus software.
Protect your browser, including Internet Explorer, Firefox, Chrome and Opera.
Protect browser add-ons, including java, adobe readers, flash memory, and shockwaves.
Protect java
Protected pdf reader (including adobe reader, adobe acrobat, foxit reader)
Protect microsoft word, excel and powerpoint
Add layer3 technology against social engineering
Includes advanced Java configuration options for the organization
Added Silverlight Sandbox technology
Change the balloon notification to down by the standard
Added support for MS playback preparation
Hardened and safer API framework is hooked
Eliminate running items during uninstallation
Increased self-protection mechanism
Contains configuration for managing conflicts
Added Layer3 technology for macro vulnerabilities
What’s New?
Solve conflicts with China’s banking software
Fixed clashes with Symantec DLP
Fixed conflict with Kobil mIdentity software
Solve the problem when adding an invalid custom mask
Fix false positives with Adobe and .NET modules
Fixed conflict with Office TabLoader
MBAE DLL additional Layer1 self-saving tool
Enhanced Layer1 Stack Rotation Tracking Technology
In Layer 3, higher quality application performance protection
MBAE IPC self-protection upgrade
System Requirements:
Windows XP / 7 / Vista / 8 / 8.1 / 9/10
10RAM 1GB above
Hard disk space should be free up to 500MB
The post Malwarebytes Anti-Exploit Premium 1.12.1.139 Crack appeared first on Take Crack.
from Take Crack https://ift.tt/2KFE0aB via IFTTT
0 notes
Text
Add-ons for safe surfing
New Post has been published on http://droidmaverick.com/add-ons-safe-surfing/
Add-ons for safe surfing
If the Internet feels like the Wild Wild Web for you, then good browser settings will help you tame it.
Protected In The World Wide Web
It’s a stipulation for Firefox, Chrome and Edge to fulfil a minimum standard for safe web browsing. In particular, this includes the ability to eliminate safety loopholes in real-time, which is delivered in the form of automatic updates. This is critical, because over 100 loopholes can be found per year (see right). While in use, Chrome and Edge have an active protective function, which runs specific processes in a sandbox by default. As for Firefox, the developers are currently trying to implement the same feature. The companies behind the browsers, Microsoft, Google and Mozilla, are also involved in the implementation of new safety technologies and often integrate them in the browser before service providers implement them on the Internet. The best example of this is the new TLS 1.3, which accelerates the establishment of encrypted HTTPS connections and increases their safety. In the current versions of Firefox and Chrome, you still need to activate this feature manually (see right). A suitable addition is HTTPS Everywhere, an add-on for Chrome and Firefox (see pg. 64), which automatically establishes an encrypted connection to a website whenever possible. A flawless HTTPS connection also protects against interception of log-in data, such as those for the banking website or the mail host. If you access encrypted services frequently, you should check the quality of your HTTPS connection at ssllabs.com/ssltest.
1.HTTPS Everywhere – Encrypted surfing
Many websites still do not have any encrypted HTTPS connection or don’t have it enabled by default. This add-on for Firefox and Chrome, developed by the Electronic Frontiers Foundation, asks a local database whether it is possible to establish a HTTPS connection on the website that is being accessed, and automatically shifts the browser correspondingly. In addition, users can also use the SSL Observatory that asks the Electronic Frontier Foundation online about whether the HTTPS certificate of a website is correct.
2.NoScript – Disabling scripts
Most web attacks that exploit loopholes in browsers use JavaScript or another script language to do so. NoScript allows scripts to be banned completely or for individual websites. In addition, the add-on blocks other targets such as Flash, Silverlight as well as Java content. Optionally, users can impose a blanket ban on the executions of Firefox plugins (not the add-ons). As NoScript sometimes greatly limits surfing, it has a ‘‘Positive list” of websites in the ‘‘Settings”, which can be accessed without being blocked.
3.uMatrix – Deactivating web codes
The blocking add-on known as uMatrix requires practice and basic understanding of the elements used in creating a website. Those who do will know how to easily show or hide any parts of a page, revamping the display of the content according to their taste. uMatrix also offers the option to conceal the user agent and can stop all referrer information, both actions which make fingerprinting and tracking down the surfer more difficult. uMatrix does not use any filter lists, but blocks domains using updated host lists.
Anonymously On The Move
The Internet is an open space in which users move around. Promotional trackers follow their tracks using cookies, with intelligence agencies able to tap into these web traffic or request from a provider for saved connection data. For more privacy, the average internet users must be more proactive. Firefox, Chrome and Edge have implemented a private mode that can be enabled by opening a new anonymous window, where all surfing history is deleted upon closing the window. In addition, Chrome has installed a backup with Guest mode, which helps blocks access to the user’s web tracks, such as history or bookmarks. To set it up, place a checkmark in front of ‘‘Enable Guest browsing” in the ‘‘Settings”. Then, establish a desktop link for the ‘‘guest” via ‘‘Add Person” – the browser can directly be opened in this mode later using the link.
The private mode in Firefox can also be made better using functions that Mozilla has incorporated in collaboration with the Tor project (see left). To use those functions, go to ‘‘about:config” and open the context menu. Use ‘‘New | Boolean” to create an entry having the name ‘‘privacy.resistFingerprinting”and set it to ‘‘true”. It ensures that the browser no longer releases any information about installed addons or about the screen resolution. Both are measures against the so-called finger-printing, which refers to following the surfer on the basis of the queries about the system configuration. Another feature adopted from the Tor project is the ability to block third party content such as cookies, which are not set directly by a website that has been visited. This first party isolation can be activated in ‘‘about:config” by double-clicking ‘‘privacy.firstparty.isolate” to set it to “true”. It is possible that this still should also work fine if the feature were officially implemented in the future, but if it doesn’t then you should switch it off.
0 notes
Text
Critical Security Updates from Adobe, Microsoft
Adobe and Microsoft separately issued updates on Tuesday to fix a slew of security flaws in their products. Adobe patched dozens of holes in its Flash Player, Acrobat and Reader products. Microsoft pushed fixes to address dozens of vulnerabilities in Windows and related software.
The biggest change this month for Windows users and specifically for people responsible for maintaining lots of Windows machines is that Microsoft has replaced individual security bulletins for patches with a single “Security Update Guide.”
This change follows closely on the heels of a move by Microsoft to bar home users from selectively downloading specific updates and instead issuing all monthly updates as one big patch blob.
Microsoft’s claims that customers have been clamoring for this consolidated guide notwithstanding, many users are likely to be put off by the new format, which seems to require a great deal more clicking and searching than under the previous rubric. In any case, Microsoft has released a FAQ explaining what’s changed and what folks can expect under the new arrangement.
By my count, Microsoft’s patches this week address some 46 security vulnerabilities, including flaws in Internet Explorer, Microsoft Edge, Windows, Office, Visual Studio for Mac, .NET Framework, Silverlight and Adobe Flash Player.
At least two of the critical bugs fixed by Microsoft this month are already being exploited in active attacks, including a weakness in Microsoft Word that is showing up in attacks designed to spread the Dridex banking trojan.
Finally, a heads up for any Microsoft users still running Windows Vista: This month is slated to be the last that Vista will receive security updates. Vista was first released to consumers more than ten years ago — in January 2007 — so if you’re still using Vista it might be time to give a more modern OS a try (doesn’t have to be Windows…just saying).
As it is wont to do on Microsoft’s Patch Tuesday, Adobe pushed its own batch of security patches. The usual “critical” update for Flash Player fixes at least seven flaws. The newest version is v. 25.0.0.148 for Windows, Mac and Linux systems.
As loyal readers here no doubt already know, I dislike Flash because it’s full of security holes, is a favorite target of drive-by malware exploits, and isn’t really necessary to be left installed or turned on all the time anymore.
Hence, if you have Flash installed, you should update, hobble or remove Flash as soon as possible. To see which version of Flash your browser may have installed, check out this page.
The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out A Month Without Adobe Flash Player.
If you choose to keep Flash, please update it today. The most recent versions of Flash should be available from the Flash home page. Windows users who browse the Web with anything other than Internet Explorer may need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).
Chrome and IE should auto-install the latest Flash version on browser restart (users may need to manually check for updates in and/or restart the browser to get the latest Flash version). Chrome users may need to restart the browser to install or automatically download the latest version. When in doubt, click the vertical three dot icon to the right of the URL bar, select “Help,” then “About Chrome”: If there is an update available, Chrome should install it then.
Adobe also issued security fixes for its Photoshop, Adobe Reader and Acrobat software packages. The Reader/Acrobat updates address a whopping 47 security holes in these products, so if you’ve got either program installed please take a moment to update.
As ever, please leave a note in the comment section if you run into any difficulties downloading or installing any of these patches.
from https://krebsonsecurity.com/2017/04/critical-security-updates-from-adobe-microsoft/
0 notes
Text
Critical Security Updates from Adobe, Microsoft
Adobe and Microsoft separately issued updates on Tuesday to fix a slew of security flaws in their products. Adobe patched dozens of holes in its Flash Player, Acrobat and Reader products. Microsoft pushed fixes to address dozens of vulnerabilities in Windows and related software.
The biggest change this month for Windows users and specifically for people responsible for maintaining lots of Windows machines is that Microsoft has replaced individual security bulletins for patches with a single “Security Update Guide.”
This change follows closely on the heels of a move by Microsoft to bar home users from selectively downloading specific updates and instead issuing all monthly updates as one big patch blob.
Microsoft’s claims that customers have been clamoring for this consolidated guide notwithstanding, many users are likely to be put off by the new format, which seems to require a great deal more clicking and searching than under the previous rubric. In any case, Microsoft has released a FAQ explaining what’s changed and what folks can expect under the new arrangement.
By my count, Microsoft’s patches this week address some 46 security vulnerabilities, including flaws in Internet Explorer, Microsoft Edge, Windows, Office, Visual Studio for Mac, .NET Framework, Silverlight and Adobe Flash Player.
At least two of the critical bugs fixed by Microsoft this month are already being exploited in active attacks, including a weakness in Microsoft Word that is showing up in attacks designed to spread the Dridex banking trojan.
Finally, a heads up for any Microsoft users still running Windows Vista: This month is slated to be the last that Vista will receive security updates. Vista was first released to consumers more than ten years ago — in January 2007 — so if you’re still using Vista it might be time to give a more modern OS a try (doesn’t have to be Windows…just saying).
As it is wont to do on Microsoft’s Patch Tuesday, Adobe pushed its own batch of security patches. The usual “critical” update for Flash Player fixes at least seven flaws. The newest version is v. 25.0.0.148 for Windows, Mac and Linux systems.
As loyal readers here no doubt already know, I dislike Flash because it’s full of security holes, is a favorite target of drive-by malware exploits, and isn’t really necessary to be left installed or turned on all the time anymore.
Hence, if you have Flash installed, you should update, hobble or remove Flash as soon as possible. To see which version of Flash your browser may have installed, check out this page.
The smartest option is probably to ditch the program once and for all and significantly increase the security of your system in the process. An extremely powerful and buggy program that binds itself to the browser, Flash is a favorite target of attackers and malware. For some ideas about how to hobble or do without Flash (as well as slightly less radical solutions) check out A Month Without Adobe Flash Player.
If you choose to keep Flash, please update it today. The most recent versions of Flash should be available from the Flash home page. Windows users who browse the Web with anything other than Internet Explorer may need to apply this patch twice, once with IE and again using the alternative browser (Firefox, Opera, e.g.).
Chrome and IE should auto-install the latest Flash version on browser restart (users may need to manually check for updates in and/or restart the browser to get the latest Flash version). Chrome users may need to restart the browser to install or automatically download the latest version. When in doubt, click the vertical three dot icon to the right of the URL bar, select “Help,” then “About Chrome”: If there is an update available, Chrome should install it then.
Adobe also issued security fixes for its Photoshop, Adobe Reader and Acrobat software packages. The Reader/Acrobat updates address a whopping 47 security holes in these products, so if you’ve got either program installed please take a moment to update.
As ever, please leave a note in the comment section if you run into any difficulties downloading or installing any of these patches.
from Amber Scott Technology News https://krebsonsecurity.com/2017/04/critical-security-updates-from-adobe-microsoft/
0 notes