#How to prevent cross site scripting
Explore tagged Tumblr posts
Text
How to Prevent Cross-Site Script Inclusion (XSSI) Vulnerabilities in Laravel
Introduction
Cross-Site Script Inclusion (XSSI) is a significant security vulnerability that allows attackers to include malicious scripts in a web application. These scripts can be executed in the context of a user’s session, leading to data theft or unauthorized actions.

In this post, we’ll explore what XSSI is, how it impacts Laravel applications, and practical steps you can take to secure your app.
What is Cross-Site Script Inclusion (XSSI)?
XSSI occurs when a web application exposes sensitive data within scripts or includes external scripts from untrusted sources. Attackers can exploit this by injecting malicious scripts that execute within the user’s browser. This can lead to unauthorized access to sensitive data and potentially compromise the entire application.
Identifying XSSI Vulnerabilities in Laravel
To prevent XSSI, start by identifying potential vulnerabilities in your Laravel application:
Review Data Endpoints: Ensure that any API or data endpoint returns the appropriate Content-Type headers to prevent the browser from interpreting data as executable code.
Inspect Script Inclusions: Make sure that only trusted scripts are included and that no sensitive data is embedded within these scripts.
Use Security Scanners: Utilize tools like our Website Vulnerability Scanner to analyze your app for potential XSSI vulnerabilities and get detailed reports.

Screenshot of the free tools webpage where you can access security assessment tools.
Mitigating XSSI Vulnerabilities in Laravel
Let’s explore some practical steps you can take to mitigate XSSI risks in Laravel.
1. Set Correct Content-Type Headers
Make sure that any endpoint returning JSON or other data formats sets the correct Content-Type header to prevent browsers from interpreting responses as executable scripts.
Example:
return response()->json($data);
Laravel’s response()->json() method automatically sets the correct header, which is a simple and effective way to prevent XSSI.
2. Avoid Including Sensitive Data in Scripts
Never expose sensitive data directly within scripts. Instead, return data securely through API endpoints.
Insecure Approach
echo "<script>var userData = {$userData};</script>";
Secure Approach:
return response()->json(['userData' => $userData]);
This method ensures that sensitive data is not embedded within client-side scripts.
3. Implement Content Security Policy (CSP)
A Content Security Policy (CSP) helps mitigate XSSI by restricting which external sources can serve scripts.
Example:
Content-Security-Policy: script-src 'self' https://trusted.cdn.com;
This allows scripts to load only from your trusted sources, minimizing the risk of malicious script inclusion.
4. Validate and Sanitize User Inputs
Always validate and sanitize user inputs to prevent malicious data from being processed or included in scripts.
Example:
$request->validate([ 'inputField' => 'required|string|max:255', ]);
Laravel’s built-in validation mechanisms help ensure that only expected, safe data is processed.
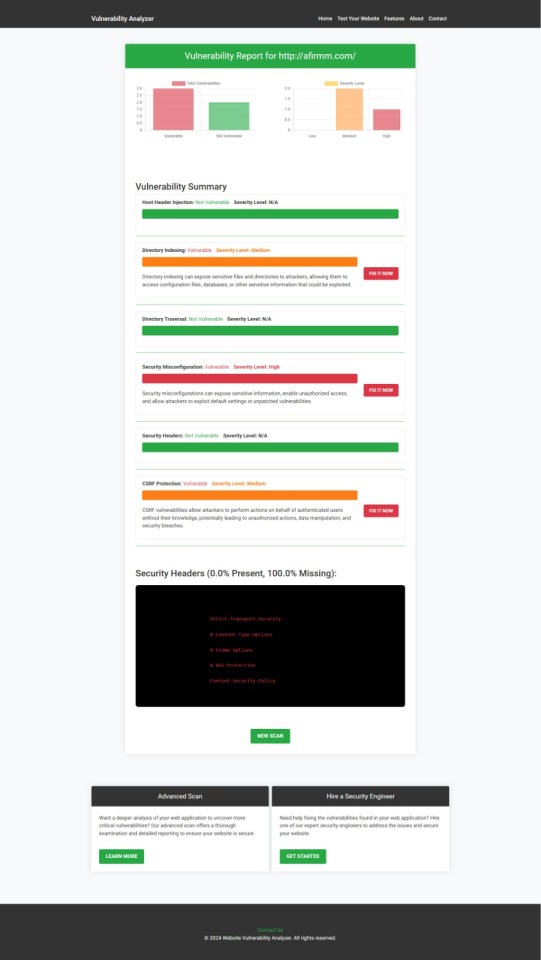
5. Regular Security Assessments
Conduct regular security assessments to proactively identify potential vulnerabilities. Tools like our free Website Security Scanner can provide detailed insights into areas that need attention.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Preventing Cross-Site Script Inclusion (XSSI) vulnerabilities in your Laravel applications is essential for safeguarding your users and maintaining trust. By following best practices like setting proper content-type headers, avoiding sensitive data exposure, implementing CSP, validating inputs, and regularly assessing your app’s security, you can significantly reduce the risk of XSSI attacks.
Stay proactive and secure your Laravel applications from XSSI threats today!
For more insights into securing your Laravel applications, visit our blog at Pentest Testing Corp.
3 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
How to Choose the Right Security Stack for Your Business Website
In an age where cyberattacks are growing more frequent and sophisticated, a secure website isn’t just a best practice—it’s a business necessity. Whether you're running an eCommerce store, SaaS product, or a company website, your security stack plays a critical role in protecting sensitive data, maintaining customer trust, and ensuring compliance.
A professional Web Development Company will always prioritize building a tailored security framework that addresses both current risks and future vulnerabilities. But how do you decide which tools and layers should be part of your website's defense system?
Let’s break down what a “security stack” means and how to choose the right one for your business.
What Is a Website Security Stack?
A security stack is a layered approach to website protection. It combines various technologies and tools—each targeting a specific set of threats—to create a comprehensive shield around your web infrastructure.
Think of it like a multi-lock system for your home:
One layer protects your doors (authentication)
Another secures your windows (firewalls)
And another watches for unusual activity (monitoring tools)
When configured properly, these layers work together to identify, prevent, and respond to attacks—without compromising website speed or functionality.
1. Start With an SSL/TLS Certificate
This is the most basic, yet crucial, layer. An SSL/TLS certificate encrypts the data exchanged between your website and its users. It ensures that personal information, passwords, and payment details can't be intercepted by third parties.
Make sure:
Your certificate is issued by a trusted Certificate Authority (CA)
It’s renewed automatically
All pages (not just the login or checkout) are secured with HTTPS
Modern browsers now flag non-HTTPS sites as "Not Secure"—a red flag for users and search engines alike.
2. Use a Web Application Firewall (WAF)
A WAF monitors and filters HTTP traffic between your website and the internet. It blocks common threats like SQL injection, cross-site scripting (XSS), and brute-force attacks.
Choose a WAF that:
Offers customizable rules
Supports DDoS protection
Provides real-time traffic analytics
Popular WAFs include Cloudflare, Sucuri, and AWS WAF—each with varying levels of control and reporting. Your development agency can help configure the best fit based on your tech stack and risk exposure.
3. Implement Secure Authentication Protocols
Weak passwords and poorly managed login systems are among the top causes of data breaches. Strengthen this layer with:
Two-Factor Authentication (2FA)
OAuth2 or SSO integrations for enterprise-level users
Rate-limiting and lockout mechanisms for failed login attempts
Make sure admin panels, user dashboards, and CMS backends are protected with hardened authentication protocols—not just simple passwords.
4. Harden Your CMS and Framework
If you’re using platforms like WordPress, Webflow, or custom frameworks like Laravel or Django, security starts with how well the code and plugins are managed.
Best practices include:
Removing unused plugins and themes
Regularly updating core software
Using only trusted third-party packages
Applying role-based access controls
A Web Development Company will often audit your codebase and extensions for hidden vulnerabilities and outdated dependencies.
5. Monitor and Log Everything
Security isn’t static—it requires continuous monitoring. Use log management and monitoring tools to detect suspicious behavior in real time.
Your stack should include:
Application-level logging (failed logins, unusual traffic)
Server and file integrity monitoring
Alerts for changes in configuration or permissions
Tools like Sentry, Datadog, or even open-source solutions like Fail2Ban can help detect threats early before they escalate.
6. Secure Your Hosting Environment
Your server and hosting setup must be as secure as your code. Ensure:
Firewalls are configured at the OS level
SFTP (not FTP) is used for file transfers
Admin panels are IP-restricted or hidden behind VPNs
Automated daily backups are stored off-site
Many breaches happen at the server level due to misconfigured permissions or outdated software—especially on unmanaged VPS environments.
7. Regular Penetration Testing and Updates
Security isn’t a one-time setup. Schedule regular penetration testing and vulnerability scans to identify new risks. Ensure:
Your software dependencies are up-to-date
Security patches are applied immediately
Reports are reviewed and acted upon
This proactive approach protects your business from evolving threats and demonstrates compliance with security standards and regulations.
Conclusion
Choosing the right security stack is not just about installing tools—it's about building a customized, layered defense system that protects your website from every angle. From SSL certificates and firewalls to authentication protocols and monitoring tools, each element plays a role in safeguarding your digital assets.
To ensure nothing is overlooked, work with a Web Development Company that specializes in security-first development. With the right guidance and configuration, your website can stay protected, performant, and trusted—no matter how fast your business grows.
0 notes
Text
Cloud Platforms Testing at GQAT Tech: Powering Scalable, Reliable Apps
In today's digital world, most companies use the cloud to host their software, store their data, and provide users with seamless experiences and interactions, meaning their cloud-based systems have to be fast and secure (it could be an e-commerce site, a mobile app, or corporate software platform) and be able to provide a robust reliable level of service that does not fail. All this hard work to develop a cloud-based application means nothing if the application is not subjected to testing and verification to work properly in different cloud environments.
Credit should be given to GQAT Tech for making cloud platform testing a core competency, as the entire QA team tests applications in the cloud, on cloud-based platforms, i.e., AWS, Azure, Google Cloud, or Private Cloud, while testing for performance, security, scalability, and functionality.
Now, let's explore the definition of cloud platform testing, what it is, why it is important, and how GQAT Tech can help your company be successful in the cloud.
What Is Cloud Platform Testing?
Cloud platform testing provides validation of whether a web or mobile application will function correctly in a cloud-based environment (as compared to on a physical server).
It involves testing how well your app runs on services like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
IBM Cloud
Private/Hybrid cloud setups
The goal is to ensure your app is:
Scalability - Will it support more users over time with no performance degradation?
Improve security - Is my data protected from being compromised/attacked?
Stability - Is it repeatably functioning (no crashing or errors)?
Speed - Is the load time fast enough for users worldwide?
Cost - Is it utilizing cloud resources efficiently?
GQAT Tech’s Cloud Testing Services
GQAT Tech employs a hybrid process of manual testing, automated scripts, and real cloud environments to validate/applications in the most representative manner. The QA team manages real-time performance, availability, and security across systems.
Services Offered:
Functional Testing on Cloud
Validates that your app will behave in an appropriate way while hosted on different cloud providers.
Performance & Load Testing
Validates how your app behaves when 10, 100, or 10,000 users are accessing it at the same time.
Scalability Testing
Validates whether your app is capable of scaling up or down based on usage.
Security Testing
Validates for vulnerabilities specific to clouds: data leak vulnerabilities, misconfigured access, and DDoS risks.
Disaster Recovery & Backup Validation
Validates whether systems can be restored after failure or downtime.
Cross-Platform Testing
Validates your application's performance across AWS, Azure, GCP, and Private Cloud Systems.
Why Cloud Testing Is Important
By not testing your application in the cloud, you expose yourself to significant risks such as:
App crashes when usage is highest
Data loss because of inadequate backup
Cloud bills that are expensive due to inefficient usage
Security breaches due to weaker settings
Downtime that impacts customer frustration
All of these situations can be prevented and you can ensure your app runs smoothly every day with cloud testing.
Tools Used by GQAT Tech
GQAT Tech uses advanced tools for cloud testing:
Apache JMeter – Load testing and stress testing
Postman – API testing for cloud services
Selenium / Appium – Automated UI testing
K6 & Gatling – Performance testing
AWS/Azure/GCP Test Environments – Real cloud validation
CI/CD Pipelines (Jenkins, GitHub Actions) – Continuous cloud-based testing
Who Needs Cloud Platform Testing?
GQAT Tech works with startups, enterprises, and SaaS providers across industries like:
E-commerce
Healthcare
Banking & FinTech
Logistics & Travel
IoT & Smart Devices
Education & LMS platforms
If your product runs in the cloud, you need to test it in the cloud—and that’s exactly what GQAT does.
Conclusion
Cloud computing provides flexibility, speed, and power—but only if your applications are tested and validated appropriately. With GQAT Tech's cloud platform testing services, you can be confident that your application will work as required under all real-world environments.
They will help eliminate downtime, enhance app performance, protect user data and help optimize cloud expenditure—so you can expand your business without concern.
💬 Ready to test smarter in the cloud? 👉 Explore Cloud Platform Testing Services at GQAT Tech
#Cloud Platform Testing#AWS Testing#Azure Testing#Google Cloud QA#Cloud Application Testing#Performance Testing on Cloud#Cloud Scalability Testing#Functional Testing on Cloud#Cloud Security Testing#Cloud-Based QA#GQAT Cloud Services#CI/CD in Cloud#Real-Time Cloud Testing#Cloud QA Automation#SaaS Testing Platforms
0 notes
Text
How Is Java Secured In Modern Web Applications?
Java offers several built-in and external mechanisms to secure modern web applications against common vulnerabilities. One key security feature is Java Authentication and Authorization Service (JAAS), which ensures secure user access by handling login and permission management. Java frameworks like Spring Security further simplify and enhance application security by providing robust solutions for authentication, authorization, CSRF protection, and session management.
To prevent SQL injection, Java encourages the use of PreparedStatements over dynamic queries. It also supports input validation, data sanitization, and output encoding to combat cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks. Secure communication is achieved through SSL/TLS encryption, and tools like OWASP Java Encoder and ESAPI can be integrated to handle encoding and security enforcement.
Modern Java-based web apps also benefit from secure deployment practices, such as setting HTTP security headers, role-based access control (RBAC), and frequent vulnerability testing. The layered architecture of Java full stack applications helps isolate business logic from presentation and data access layers, reducing attack surfaces.
To understand these practices in depth and become industry-ready, consider exploring a java full stack developer course.
0 notes
Text

Key WooCommerce Security Tips for 2025
1. Use Strong Passwords and Enable Two-Factor Authentication (2FA)
A weak password is often the first point of vulnerability for any website. To protect your WooCommerce store, ensure that you and your team members use strong, unique passwords for all accounts related to your store. Additionally, enabling two-factor authentication (2FA) adds an extra layer of protection, requiring a second verification step when logging in.
While 2FA may seem like an added hassle, it is a powerful tool that prevents unauthorized access, even if someone obtains your password. Implementing 2FA will drastically reduce the likelihood of a security breach.
2. Keep WordPress, WooCommerce, and Plugins Updated
Regular updates to WordPress, the WooCommerce plugin, and any other installed plugins are critical for maintaining security. These updates often include security patches to fix newly discovered vulnerabilities. By updating your software regularly, you ensure that your store is protected against the latest threats.
If you don't have the time or expertise to handle updates yourself, consider seeking WooCommerce Development Services to keep your store secure and functioning smoothly. A professional team can handle the updates while ensuring no disruption to your store’s operations.
3. Implement SSL Encryption for Secure Transactions
SSL (Secure Socket Layer) certificates encrypt sensitive data that flows between the server and the user’s browser. This encryption ensures that your customers’ personal and financial details are protected. In 2025, having an SSL certificate isn’t just a security measure—it’s also essential for maintaining customer trust and improving your site’s SEO ranking.
If you're unsure how to integrate SSL encryption, a WooCommerce Developer can help set it up to ensure secure transactions and smooth customer experiences.
4. Install a Web Application Firewall (WAF)
A Web Application Firewall (WAF) acts as a barrier between your WooCommerce store and malicious traffic. It filters out harmful requests, preventing hackers from exploiting vulnerabilities in your site’s code. Implementing a WAF can block attacks such as SQL injection, cross-site scripting (XSS), and brute-force login attempts, which are common methods used by cybercriminals.
To configure the best WAF for your store, you can work with professionals who specialize in website security.
5. Backup Your Store Regularly
Data loss is one of the most detrimental effects of a cyberattack. If your store is compromised or experiences a system failure, having a recent backup ensures that you can restore your website with minimal downtime and data loss. Regular backups also give you peace of mind knowing that even in the worst-case scenario, you can recover your site quickly.
To streamline this process, WordPress Support Services often include backup solutions, providing continuous backups to keep your store secure and your data safe.
6. Limit Login Attempts
Brute force attacks involve hackers attempting to guess your login credentials by trying different combinations repeatedly. One effective way to prevent these attacks is by limiting the number of failed login attempts before temporarily locking out the user. This drastically reduces the chances of a hacker successfully gaining access to your store.
This is a simple yet effective security measure, and integrating it into your site can be done by a WooCommerce Developer who can ensure the right settings are in place to block these types of attacks.
Ongoing Maintenance and Monitoring for WooCommerce Security
Maintaining a secure WooCommerce store is an ongoing process. Regular security checks, audits, and proactive monitoring are essential to keep your site protected. Without routine maintenance, new vulnerabilities can arise, and hackers will always find new ways to exploit them.
By leveraging WordPress Website Maintenance Services, you can ensure that your store is continually monitored and updated, helping to safeguard it from emerging threats.
Conclusion
In 2025, the security of your WooCommerce store should be a top priority. By adopting strong passwords, implementing SSL certificates, enabling two-factor authentication, and keeping your software up to date, you can significantly reduce the risk of a breach.
For more advanced security measures and ongoing support, working with WooCommerce Development Services and WordPress Support Services ensures that your site remains secure, protected from the latest threats, and optimized for performance.
Let’s work together to make sure your WooCommerce store is as secure as possible in 2025 and beyond.
0 notes
Text
Understanding Cross-Site Scripting (XSS) and How to Prevent It
Hey there, web enthusiasts! If you’re building a website or running an online business, keeping it safe is a top priority. One threat you need to know about is Cross-Site Scripting, or XSS. As someone who’s seen the web evolve, I’m here to break down what XSS is, why it’s a big deal, and how you can stop it in its tracks. Let’s get into it with a clear, friendly guide, backed by solid insights, so you can keep your site secure in 2025.
What Is Cross-Site Scripting (XSS)?
XSS is a type of security flaw where attackers sneak harmful code—usually JavaScript—into a website. When users visit the site, this code runs in their browsers, causing trouble. Imagine someone slipping a prank note into your mailbox that messes with your computer when you open it. That’s XSS in a nutshell. A 2024 OWASP report lists XSS among the top 10 web vulnerabilities, affecting 53% of tested sites.
There are three main types of XSS:
Stored XSS: Harmful code is saved on the server, like in a comment section, and runs for every visitor.
Reflected XSS: The code comes from a user’s input, like a search query, and runs immediately.
DOM-based XSS: The code messes with the website’s structure in the browser without touching the server.
Why care? XSS can steal user data (like login details), redirect people to fake sites, or even deface your website. For businesses using web development services in Bhubaneswar, a single XSS attack can damage trust and cost customers.
Why XSS Is a Problem
Attackers love XSS because it’s sneaky and effective. Say you run a Bhubaneswar e-commerce site. If someone injects code into your product review section, it could steal customers’ credit card info or trick them into downloading malware. A 2024 Verizon Data Breach Report says 30% of web attacks involve XSS, costing businesses millions in fixes and lost revenue.
The impact goes beyond money. Users lose faith if their data gets compromised, and your brand takes a hit. Small businesses, especially, can struggle to recover. That’s why understanding and preventing XSS is critical, whether you’re coding your own site or working with web development services in Bhubaneswar.
How to Prevent XSS Attacks
Good news: you can protect your website from XSS with some practical steps. Here’s a straightforward plan to keep your site safe, based on industry best practices.
1. Clean Up User Input
Always check and clean any data users send to your site, like form submissions or comments. This process, called input sanitization, removes or neutralizes harmful code. Libraries like DOMPurify can help strip out dangerous scripts. A 2024 Snyk study found that sanitizing input cuts XSS risks by 60%.
For example, if a user tries to post “<script>badStuff()</script>” in a comment, your site should convert it to plain text so it can’t run. Developers in Bhubaneswar often use frameworks like React or Angular, which have built-in tools to handle this.
2. Use Safe Coding Practices
When building your site, avoid risky practices like directly inserting user input into your HTML. Instead, use safe APIs like innerText instead of innerHTML in JavaScript. Also, set HTTP headers like Content Security Policy (CSP) to limit what scripts can run. A 2024 Mozilla guide says CSP reduces XSS incidents by 40%.
If you’re not a coding expert, team up with developers who know these tricks. They’ll make sure your site’s code is solid from the start.
3. Escape Data Properly
Escaping means adding special characters to user input so browsers don’t treat it as code. For instance, turning “<” into “<” ensures it displays as text, not a script. Most modern frameworks, like Django or Laravel, do this automatically, but double-check if you’re coding manually. A 2024 Synopsys report notes proper escaping stops 50% of XSS attempts.
4. Keep Software Updated
Outdated software is an open door for attackers. Regularly update your content management system (like WordPress), plugins, and libraries. A 2024 Patchstack study found 25% of XSS attacks exploit known vulnerabilities in old software. Set reminders to check for updates monthly to stay ahead.
5. Test Your Site Regularly
Run security scans to catch XSS flaws before attackers do. Tools like Burp Suite or OWASP ZAP can spot weak points. Also, consider hiring a security expert to do a thorough check, especially for business sites. In Bhubaneswar, local developers often offer testing as part of their services.
Why This Matters in 2025
With cybercrime expected to cost $10.5 trillion globally by 2025, per a 2024 Cybersecurity Ventures report, XSS prevention is non-negotiable. India’s digital economy is booming, and Bhubaneswar is a growing tech hub, making secure websites a must for businesses. Protecting your site builds trust, keeps users safe, and saves you from costly breaches.
Ready to secure your website? Start by checking your user inputs, using safe coding habits, and keeping everything updated. If you need help, local experts can guide you. Stay proactive, and keep XSS out of your story. Your users—and your business—will thank you!
#digital marketing agency bhubaneswar#website development companies in bhubaneswar#best digital marketing company in bhubaneswar#digital marketing services in bhubaneswar#web development services in bhubaneswar#digital marketing agency in bhubaneswar
0 notes
Text
The Hidden Hero of Software Success: Inside EDSPL’s Unmatched Testing & QA Framework

When a software product goes live without glitches, users often marvel at its speed, design, or functionality. What they don’t see is the invisible layer of discipline, precision, and strategy that made it possible — Testing and Quality Assurance (QA). At EDSPL, QA isn’t just a step in the process; it’s the very spine that supports software integrity from start to finish.
As digital applications grow more interconnected, especially with advancements in network security, cloud security, application security, and infrastructure domains like routing, switching, and mobility, quality assurance becomes the glue holding it all together. EDSPL’s comprehensive QA and testing framework has been fine-tuned to ensure consistent performance, reliability, and security — no matter how complex the software environment.
Let’s go behind the scenes of EDSPL’s QA approach to understand why it is a hidden hero in modern software success.
Why QA Is More Crucial Than Ever
The software ecosystem is no longer siloed. Enterprises now rely on integrated systems that span cloud platforms, APIs, mobile devices, and legacy systems — all of which need to work in sync without error.
From safeguarding sensitive data through network security protocols to validating business-critical workflows on the cloud, EDSPL ensures that testing extends beyond functionality. It is a guardrail for security, compliance, performance, and user trust.
Without rigorous QA, a minor bug in a login screen could lead to a vulnerability that compromises an entire system. EDSPL prevents these catastrophes by placing QA at the heart of its delivery model.
QA Touchpoints Across EDSPL’s Service Spectrum
Let’s explore how EDSPL’s testing excellence integrates into different service domains.
1. Ensuring Safe Digital Highways through Network Security
In an era where cyber threats can cripple operations, QA isn’t just about validating code — it’s about verifying that security holds up under stress. EDSPL incorporates penetration testing, vulnerability assessments, and simulation-based security testing into its QA model to validate:
Firewall behavior
Data leakage prevention
Encryption mechanisms
Network segmentation efficacy
By integrating QA with network security, EDSPL ensures clients launch digitally fortified applications.
2. Reliable Application Delivery on the Cloud
Cloud-native and hybrid applications are central to enterprise growth, but they also introduce shared responsibility models. EDSPL’s QA ensures that deployment across cloud platforms is:
Secure from misconfigurations
Optimized for performance
Compliant with governance standards
Whether it’s AWS, Azure, or GCP, EDSPL’s QA framework validates data access policies, scalability limits, and containerized environments. This ensures smooth delivery across the cloud with airtight cloud security guarantees.
3. Stress-Testing Application Security
Modern applications are constantly exposed to APIs, users, and third-party integrations. EDSPL includes robust application security testing as part of QA by simulating real-world attacks and identifying:
Cross-site scripting (XSS) vulnerabilities
SQL injection points
Broken authentication scenarios
API endpoint weaknesses
By using both manual and automated testing methods, EDSPL ensures applications are resilient to threat vectors and function smoothly across platforms.
4. Validating Enterprise Network Logic through Routing and Switching
Routing and switching are the operational backbone of any connected system. When software solutions interact with infrastructure-level components, QA plays a key role in ensuring:
Data packets travel securely and efficiently
VLANs are correctly configured
Dynamic routing protocols function without interruption
Failover and redundancy mechanisms are effective
EDSPL’s QA team uses emulators and simulation tools to test against varied network topologies and configurations. This level of QA ensures that software remains robust across different environments.
5. Securing Agile Teams on the Move with Mobility Testing
With a growing mobile workforce, enterprise applications must be optimized for mobile-first use cases. EDSPL’s QA team conducts deep mobility testing that includes:
Device compatibility across Android/iOS
Network condition simulation (3G/4G/5G/Wi-Fi)
Real-time responsiveness
Security over public networks
Mobile-specific security testing (root detection, data sandboxing, etc.)
This ensures that enterprise mobility solutions are secure, efficient, and universally accessible.
6. QA for Integrated Services
At its core, EDSPL offers an integrated suite of IT and software services. QA is embedded across all of them — from full-stack development to API design, cloud deployment, infrastructure automation, and cybersecurity.
Key QA activities include:
Regression testing for evolving features
Functional and integration testing across service boundaries
Automation testing to reduce human error
Performance benchmarking under realistic conditions
Whether it's launching a government portal or a fintech app, EDSPL's services rely on QA to deliver dependable digital experiences.
The QA Framework: Built for Resilience and Speed
EDSPL has invested in building a QA framework that balances speed with precision. Here's what defines it:
1. Shift-Left Testing
QA begins during requirements gathering, not after development. This reduces costs, eliminates rework, and aligns product strategy with user needs.
2. Continuous Integration & Automated Testing
Automation tools are deeply integrated with CI/CD pipelines to support agile delivery. Tests run with every commit, giving developers instant feedback and reducing deployment delays.
3. Security-First QA Culture
Security checks are integrated into every QA cycle, not treated as separate audits. This creates a proactive defense mechanism and encourages developers to write secure code from day one.
4. Test Data Management
EDSPL uses production-simulated datasets to ensure test scenarios reflect real-world user behavior. This improves defect prediction and minimizes surprises post-launch.
5. Reporting & Metrics
QA results are analyzed using KPIs like defect leakage rate, test coverage, mean time to resolve, and user-reported issue rates. These metrics drive continuous improvement.
Case Studies: Impact Through Quality
A National Education Platform
EDSPL was tasked with launching a high-traffic education portal with live video, assessments, and resource sharing. The QA team created an end-to-end test architecture including performance, usability, and application security testing.
Results:
99.9% uptime during national rollout
Zero critical issues in the first 90 days
100K+ concurrent users supported with no lag
A Banking App with Cloud-Native Architecture
A private bank chose EDSPL for QA on a mobile app deployed on the cloud. The QA team validated the app’s security posture, cloud security, and resilience under high load.
Results:
Passed all OWASP compliance checks
Load testing confirmed 5000+ concurrent sessions
Automated testing reduced release cycles by 40%
Future-Ready QA: AI, RPA, and Autonomous Testing
EDSPL’s QA roadmap includes:
AI-based test generation from user behavior patterns
Self-healing automation for flaky test cases
RPA integration for business process validation
Predictive QA using machine learning to forecast defects
These capabilities ensure that EDSPL’s QA framework not only adapts to today’s demands but also evolves with future technologies.
Conclusion: Behind Every Great Software Is Greater QA
While marketing, development, and design get much of the spotlight, software success is impossible without a strong QA foundation. At EDSPL, testing is not a checkbox — it’s a commitment to excellence, safety, and performance.
From network security to cloud security, from routing to mobility, QA is integrated into every layer of the digital infrastructure. It is the thread that ties all services together into a reliable, secure, and scalable product offering.
When businesses choose EDSPL, they’re not just buying software — they’re investing in peace of mind, powered by an unmatched QA framework.
Visit this website to know more — https://www.edspl.net/
0 notes
Text
How Drupal Ensures Compliance and Data Security in 2025
In today's age of the internet, where data breaches and compliance issues are making headlines daily, organizations require a content management system (CMS) that, in addition to being robust and scalable, is secure and compliant too. Drupal, the most trusted open-source CMS platform globally, has raised the bar at every turn. In 2025, Drupal raises the bar again with improved data protection and adherence to international standards.
This is why more and more, businesses are partnering with a good Drupal development firm or hiring best Drupal development services to create, host, and protect their websites.
Here we talk about how Drupal has been made compliant and secure for the data in 2025 by highlighting the most important features, improvements, and best practices of the platform making it one of the highly chosen platforms for government organizations, banks and financial institutions, healthcare providers, and companies handling sensitive data.

1. Security Architecture at its Core
Fundamentally, Drupal is designed to be secure. The system runs on a strong security-first architecture that includes:
Role-Based Access Control (RBAC): Drupal supports fine-grained user access rights down to where users are only able to view content and operate functions.
Database Abstraction: Prevents SQL injection by running on the basis of a layer of abstraction to sanitize input. It.
CSRF and XSS Protection: Drupal comes with built-in protection against Cross-Site Request Forgery (CSRF) and Cross-Site Scripting (XSS), two common web application vulnerabilities.
Secure Coding Standards: Drupal has strict coding standards and peer-reviewed contributions, so it is less likely that insecure code will be released.
When you are outsourcing the service of a Drupal web development agency, such foundational security features are a part of the package as the company forms its work upon the basis of a secure and compliant digital experience.
2. Security Team and Continuous Updates
Drupal's dedicated Security Team monitors and resolves vulnerabilities 24/7. In 2025, the community has further strengthened with faster response times and proactive measures that patch vulnerabilities well before they can be exploited.
Secondly, Drupal 10.x (and subsequent versions in 2025) is updated periodically, and security advisories are released openly. This alerts developers and site administrators to it and gives them a chance to move quickly. Top-class Drupal development service ensures that client sites are kept current and secure with zero downtime.
3. Compliance-Ready Architecture
The flexibility of Drupal makes it possible to use it with almost any compliance framework. In 2025, organizations leverage Drupal to become compliant with some of the globe's most significant international standards:
GDPR (General Data Protection Regulation)
HIPAA (Health Insurance Portability and Accountability Act)
CCPA (California Consumer Privacy Act)
SOC 2
ISO/IEC 27001
How Drupal Ensures Compliance
Data Anonymization & Export: With GDPR fully in effect, Drupal makes anonymizing, deleting, or exporting personal data on demand for users easy.
Audit Logs: Track user actions and system changes for traceability and accountability.
Data Encryption: Drupal supports database encryption at rest and SSL/TLS for encrypted data in transit, which is industry best practice.
Most organizations outsource the installation of such compliance aspects to a professional Drupal development company that they entrust to abide by their industry-specific requirements.
4. Modular Security Improvements
The largest strength of Drupal is its modularity. Scores of contributed modules in 2025 are very commonly used to secure and comply sites. A few of them are:
Secure Login Module: Enforces 2FA (two-factor authentication) and CAPTCHA-based protection.
Password Policy Module: Enforces strict password policies and expiry dates.
Encrypt Module: Enables encryption of sensitive fields or entire database tables.
Security Kit Module: Offers a customizable security hardening solution for headers and content protection.
These modules are typically packaged by top Drupal web development companies to create customized solutions based on the specific security needs of each client.
5. Privacy by Design
Drupal encourages Privacy by Design, a philosophy that has become the norm of data protection policies in 2025. Whether creating a personal blog or an eCommerce site globally, developers can include privacy principles from the start: Minimal Data Collection: Form and API developers can configure forms and APIs to capture minimal user information.
Explicit Consent Mechanisms: Easy integration opt-in checkboxes, cookie banners, and preference centers ensure user consent.
Customizable Data Retention Policies: Automatically delete or archive the data after a while.
These features can be implemented by businesses easily without compromising quality user experience with the help of an experienced Drupal development company.
6. Third-Party Integrations with Security Controls
In today's tech stack, third-party system integration with CRMs, ERPs, and marketing systems is inevitable. Drupal's API-first nature makes interactions with such services secure:
Firewall and Access Control Layers: Secures so that APIs are accessed from trusted places only.
Rate Limiting and Throttling: Protects from brute-force attacks and abuse of public endpoints.
Professional Drupal web development companies integrate these features in a way that is both user-friendly and compliant.
7. Alignment of Cloud and DevOps Security
The native integration of the newest DevOps trends and cloud platforms within Drupal in 2025 provides additional security:
CI/CD Pipelines: Static security checking and code scan features like SonarQube and Snyk are applied in Drupal CI/CD pipelines.
Containerization with Docker/Kubernetes: Docker/Kubernetes with secure container deployment isolates apps and reduces the attack surface.
Drupal on Acquia, Pantheon, and Platform.sh: These solutions feature enterprise-grade security features such as WAF (Web Application Firewalls), DDoS protection, and compliance certification.
Through collaboration with a Drupal development company, businesses can host secure and scalable cloud applications and remain regulatory compliant.
8. Accessibility and Inclusivity in Security
Security and compliance are not just technical issues; they're also ethical responsibilities. Drupal, with its inclusiveness-oriented nature, ensures that:
WCAG 2.2 Compliance: Drupal websites are disability accessible to users, as per ADA and Section 508 compliance.
Multilingual Privacy Policies: Drupal has multilingual support that ensures the provision of privacy and security alerts to all users.
Top Drupal development services encompass accessibility testing and best practices in all levels of development.
9. Drupal Community and Documentation
Lastly, Drupal's worldwide active community ensures a secure environment. Thousands of developers contribute to code reviews, security scans, and knowledge sharing. Documentation on Drupal.org, webinars, and security guides make deployment and maintenance of compliant systems easier than ever.
In 2025, functionalities like Project Browser and Automatic Updates further make the platform secure by simplifying module discovery and patch application, respectively.
A quality Drupal web development company will always be at the forefront of these advancements to create the optimal result.
Conclusion
With changing data privacy regulations and increasingly advanced cyber attacks, a secure, compliant CMS has never been more critical. Drupal's robust architecture, dedicated security team, upgradable modularity, and adherence to international compliance standards make it a leading-edge solution for 2025.
Businesses that are looking to future-proof their web assets are not only betting on Drupal development services to build a website, but to develop an enterprise-grade compliance and data security policy. Through partnership with an experienced Drupal development company, businesses can be assured that their websites are not only beautiful and functional but robust and regulation-friendly as well.
0 notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Web Application Security: Protecting Your Business from Cyber Threats
Web application security should be a priority for every business because the consequences of neglecting it can be catastrophic. In today’s digital age, where businesses increasingly rely on web application security to conduct their operations, the risks associated with inadequate security measures have risen exponentially. Cyberattacks targeting web application security, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), are common threats that can lead to data breaches, theft of intellectual property, financial losses, and legal liabilities. Furthermore, a breach of sensitive customer information can significantly damage a company’s reputation and erode customer trust.
The Role Of Web Application Firewalls In Enhancing Web Application Security
Web Application Firewalls (WAFs) play a crucial role in enhancing Web application security by acting as a protective barrier between the web application and potential threats from the internet. WAFs are designed to filter, monitor, and block malicious traffic that attempts to exploit vulnerabilities within a web application. They are particularly effective in defending against common attacks such as SQL injection, cross-site scripting (XSS), and DDoS (Distributed Denial of Service) attacks. By inspecting incoming traffic and applying predefined security rules, WAFs can detect suspicious activity in real time and prevent harmful requests from reaching the web application. Additionally, WAFs provide an additional layer of protection by filtering out malicious bots, preventing data exfiltration, and shielding applications from zero-day vulnerabilities.
Common Vulnerabilities In Web application security And How To Mitigate Them
Web application security is frequently targeted due to inherent vulnerabilities that can be exploited by cybercriminals. Some of the most common vulnerabilities include SQL injection, cross-site scripting (XSS), broken authentication, sensitive data exposure, and insufficient logging and monitoring. SQL injection occurs when an attacker is able to manipulate SQL queries to access or alter the database, which can lead to unauthorized access to sensitive information. Cross-site scripting (XSS) allows attackers to inject malicious scripts into webpages, compromising user data. Broken authentication flaws enable attackers to bypass authentication mechanisms, gaining unauthorized access to systems.
The Impact Of Poor Web Application Security: Consequences You Need To Know
The consequences of poor web application security can be devastating for businesses. A breach of web application security can lead to the theft of sensitive customer data, intellectual property, and financial resources, which can result in significant financial losses and legal repercussions. Organizations may face penalties for failing to comply with data protection regulations such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). Beyond legal ramifications, the reputational damage caused by a data breach can erode customer trust and loyalty, resulting in long-term damage to a company’s brand. In some cases, businesses may lose critical partnerships or face difficulty attracting new customers due to security concerns.
Web Application Security Testing: Why It’s Critical And How To Do It Right?
Web application security testing is a critical process to identify and fix vulnerabilities before they can be exploited by attackers. It involves a comprehensive review of a web application’s code, architecture, and environment to detect weaknesses that could lead to security breaches. There are several types of testing, including static analysis, dynamic analysis, and penetration testing, each focusing on different aspects of the web application’s security posture. Static analysis evaluates the source code to identify potential vulnerabilities, while dynamic analysis tests the application in a live environment to uncover runtime issues. Penetration testing simulates real-world cyberattacks to identify exploitable weaknesses.
What Developers Need To Know About Web Application Security?
As web application security continues to evolve and become more complex, developers must be increasingly vigilant about the security of the code they write. In 2024, developers are facing new and advanced threats that require a proactive and comprehensive approach to web application security. To build secure applications, developers need to have a solid understanding of secure coding practices, encryption protocols, authentication mechanisms, and vulnerability management. Common security flaws such as SQL injection, cross-site scripting (XSS), and broken authentication are still prevalent and require constant attention. Developers must integrate security features like input validation, secure session management, and proper access control into their code from the very beginning, rather than relying on reactive measures.
How Web Application Security Impacts User Experience And Trust?
Web application security directly impacts the user experience and trust, as users are becoming increasingly aware of the risks associated with online platforms. A secure web application fosters confidence in users by ensuring their data is protected from unauthorized access and malicious attacks. On the other hand, security flaws can result in data breaches, leading to a loss of trust and customer confidence. Users are more likely to abandon a website or service if they feel their personal information or financial details are at risk. For instance, if users experience frequent security-related incidents, such as login failures or warnings about insecure connections, they may perceive the application as unreliable and unsafe.
The Growing Importance of AI and Automation in Web Application Security
With the rise of sophisticated cyber threats, AI and automation are becoming essential tools in web application security. Machine learning algorithms can analyze vast amounts of data in real-time, identifying anomalies and detecting potential threats before they cause damage. Automated security testing tools help developers find vulnerabilities early in the development cycle, reducing the risk of exploits. By leveraging AI-driven threat detection and automated security measures, businesses can strengthen their web application security posture and stay ahead of emerging cyber threats.
Conclusion
In conclusion, web application security is an essential component of modern business operations. With the increasing reliance on digital platforms, businesses must prioritize the protection of their web application security to safeguard their data, maintain user trust, and comply with legal regulations. Web application security encompasses a range of practices, from secure coding and vulnerability testing to the implementation of web application firewalls and robust authentication mechanisms. Developers, business leaders, and security professionals must collaborate to address the evolving landscape of web application security threats.
0 notes
Text
Back end Web Development: 5 Best Measures for a Secure Website

No matter how advanced features you use in back end web development, there are high chances that your website can be attacked by malware, hackers, or users. Such attacks enable fraudulent people to gain access to confidential data, like bank details and health-related information. Cyberattacks not only harm users, but they also spoil the reputation of developers.
So, if you are a developer, you must know reliable ways to strengthen your back end security.
Having taken this fact into account, we have written this blog to familiarize you with the 5 best ways to make your back end strong enough to keep cyberattacks at bay.
Top 5 Methods for Secure Back end Development:
As a developer, if you adopt the following practices in back end web development, you will considerably reduce the chances of unauthorized access to your website:
Multi-Factor Authentication:
Multi-factor authentication (MFA) means adding extra steps for the authentication of a user during login. Let’s get a clear idea of MFA with the example provided below:
Google or Facebook may send a code to the user’s phone number when they sign in with their email, or they may need a biometric scan.
Thus, an additional layer of protection is added, which is better than the usual password and email methods.
Data Encryption:
Personal data, credit card details, and passwords must be kept confidential, as they are sensitive information. In fact, such details must not be stored in the database in their plaintext format. Doing so is as foolish as leaving your door open with the line, ‘come in and steal whatever you want.’
Keep in mind that if data is hacked, all sensitive data will be leaked. To cope with this issue, rely on encryption.
Encryption is like keeping your door locked with a strong key. It scrambles the data so well that it becomes beyond understanding. Even if somebody breaks in, they will not be able to understand what it says. Thus, you can keep your sensitive information safe.
The following are some encryption methods used in back end web development for indubitable security:
Hashing: It converts data into a fixed-length string.
Asymmetrical encryption: With a pair of keys (private and public), asymmetric encryption enables encryption and decryption.
Symmetrical encryption: It utilizes a single key for encryption as well as decryption.
These encryption techniques can allow you to miraculously improve the security of your back end web applications and protect confidential data from fraudulent access and leaking.
Disaster Recovery and Data Backup:
A wise back end development strategy is incomplete without regular data backup and disaster recovery. If a physical loss of data happens, for example, a hard disk failure, or software data loss, like a storage error or damage because of malware, data recovery is possible with backup.
Ensure that you choose backup software and fix a backup schedule, like daily, weekly, or monthly. Your backup methods must have full backups, incremental backups, and differential backups.
Proper Validation and Sanitization:
It’s foolish to trust the input provided by the user. In other words, you’d better assume that any data given by users may be malicious without proper validation and sanitization.
Validation means checking whether the input provided by the user harmonizes with the expected format, type, and constraints.
If there is a form field for an email address, validation will ensure that the input sticks to the correct email format, and it’s not just normal text.
Sanitization means the removal and modification of harmful elements or characters from the user input for the prevention of security vulnerabilities. For instance, if you eliminate HTML tags from user-generated input, it can stop cross-site scripting attacks.
That’s why validation and sanitization are a must-have in back end web development.
Authorization and RBAC:
Authorization means determining whether a user is permitted to do a particular thing on a specific resource. However, it’s wise not to allow some users to get some permissions. It’s because limiting permissions leads to reduced risk. The fewer the permissions are, the smaller the attack surface is. Thus, the fraudulent people can’t take advantage of vulnerabilities. That is where Role-Based Access Control (RBAC) is required. RBAC is a mechanism to control and manage access to resources according to the user’s role in organizations. That’s why businesses look for it when they hire Angular development services.
In a usual website, there is an administrator with full access to all resources, and a user who can view their own data.
RBAC makes sure that each user can only do those things that are allowed to them according to their given role. Let’s get it clear with an example below:
A user is not allowed to modify the data of another user or have access to administration functions. When such permissions are limited according to the requirements, the risks of data breaches and unauthorized access are reduced to a large extent.
Conclusion
The 5 best ways for safe back end web development are multi-factor authentication, data encryption, disaster recovery and data backup, validation and sanitization, and authorization and RBAC.
By using these measures, you can reduce the chances of a cyberattack on your website.
0 notes
Text
Top Vulnerability Assessment Tools to Secure Your Digital Assets
Cyberattacks are a reality in today's linked world that should not be neglected. Organizations that fail to recognize the magnitude of such risks threaten substantial reputational, financial, and legal consequences. As a result, they are not only a nightmare for end users but also a serious issue for enterprises.
But the million-plus query is, what are the main reasons for cyberattacks? Security experts declare that the primary causes of cyberattacks are social engineering, human errors, and vulnerabilities. While you can control the former two aspects with stronger security protocols and policies, vulnerabilities remain a constant threat.
Attackers frequently seek the flaws in targeted systems or apps because they provide the best potential to breach their security. Attackers can use vulnerabilities to carry out a variety of attacks, including cross-site scripting, SQL injection, session hijacking, and more.
Organizations require a thorough vulnerability assessment program to manage associated risks. You may automate this process by using feature-rich technologies that aid in the detection, categorization, and prioritizing of vulnerabilities. These vulnerability assessment tools help speed up the entire procedure.
This blog seeks to provide a comprehensive overview of vulnerability assessments, how they function, and the best tools. Continue scrolling for more details.
Download the sample report of Market Share: https://qksgroup.com/download-sample-form/market-share-vulnerability-assessment-2023-worldwide-6988
What is Vulnerability Assessment?
QKS Group defines vulnerability assessment as a comprehensive solution that enables organizations to identify, evaluate, and prioritize vulnerabilities within their IT infrastructure. Utilizing advanced automated tools and manual inspection techniques, it scans systems, applications, and network resources to uncover security weaknesses. By providing detailed reports on identified vulnerabilities, it empowers IT teams to address and mitigate risks effectively. Vulnerability Assessment solutions help prevent potential breaches, reduce the attack surface, and enhance overall cybersecurity posture.
Functionality of Vulnerability Scanning Solutions
The functionality of vulnerability scanning systems is essential for every company that produces and maintains large volumes of data, which frequently includes sensitive information specific to that organization. Attackers may attempt to identify and exploit weaknesses in the organization's systems to get unauthorized access to private data. Vulnerability analysis discovers and assesses risky locations inside an organization's network. This includes using various tools to find vulnerabilities and producing reports on the findings.
The vulnerability assessment scanning process is typically composed of three main actions:
Identifying Active Devices: The first step in the scanning procedure is identifying active devices within the target network using diverse scanning methods.
Cataloging Services and Operating Systems: Following the identification of active hosts, the following action is to catalogue the open ports and services and authenticate the operating systems running on the identified systems.
Evaluating for Vulnerabilities: The last stage involves examining the selected services and operating systems for any known vulnerabilities.
Top Vulnerability Assessment Tools
Undoubtedly, you want to use the finest tool for assessing digital assets for vulnerabilities. Such a tool will provide precise data, faster scanning times, convenience of use, and several other advantages. It would be much better if they were free. This is what you'll receive with the tools listed below.
Rapid7
Rapid7, Inc. strives to build a safer digital world by simplifying and making cybersecurity more accessible. Rapid7's technology, research, and extensive strategic skills enable security professionals across the world to handle a modern attack surface. Rapid7's comprehensive security solutions assist over 11,000 clients in combining cloud risk management with threat detection and response to decrease attack surfaces and eradicate attacks quickly and accurately.
Tenable Nessus
Tenable is an exposure management company that identifies and closes cybersecurity holes that reduce corporate value, reputation, and trust. The company's AI-powered exposure management platform dramatically integrates security visibility, insight, and action across the attack surface, enabling contemporary companies to defend against assaults on IT infrastructure, cloud environments, critical infrastructure, and everything in between.
Holm Security VMP
Holm Security is a next-generation vulnerability management software supplier that focuses on thorough 360-degree inspection. The business specializes in helping enterprises with vulnerability detection, risk assessment, and remedial prioritization. This is realized for all assets across a company. The solution has three levels and offers all the tools required for smooth vulnerability management.
RidgeBot
Ridge Security offers a new solution for security testing with their product, RidgeBot, an Intelligent Penetration Testing Robot. RidgeBot uses complex ways to penetrate networks comparable to those employed by hackers. RidgeBot, once inserted into a system, hunts out, exploits, and documents any flaws it discovers. It functions within a set scope and can quickly adapt to extremely complicated structures. Ridge Security's products benefit business and web application teams, ISVs, government agencies, educational institutions, and any other party responsible for software security by allowing them to test their systems economically and efficiently.
WithSecure Elements
WithSecure was once known as F-Secure Business. IT service providers, MSSPs, and enterprises rely on us for results-driven cyber security that protects and empowers their operations. WithSecure's AI-driven security safeguards endpoints and cloud collaboration, and its intelligent detection and response capabilities are powered by specialists that identify business risks by actively scanning for threats and combating actual attacks.
Download the sample report of Market Forecast: https://qksgroup.com/download-sample-form/market-forecast-vulnerability-assessment-2024-2028-worldwide-7141
Growing Demand for Vulnerability Assessment Solutions Amid Rising Cyber Threats
The global market for Vulnerability Assessment solutions is expanding rapidly, driven by rising cyber threats and demanding regulatory requirements across sectors. Organizations across the world are rapidly investing in sophisticated Vulnerability Assessment technologies to strengthen their cybersecurity defenses, minimize risks, and maintain compliance with regulatory requirements such as GDPR, HIPAA, and PCI-DSS. The proliferation of cloud computing, IoT, and other digital technologies is driving up demand for these solutions, as organizations strive to secure their digital assets and maintain operational resilience in an increasingly linked world.
The future of the Vulnerability Assessment market on a global scale appears promising, marked by continuous technological innovations and a proactive approach to cybersecurity. As cyber-attacks become more sophisticated and pervasive, there is a growing emphasis on deploying advanced Vulnerability Assessment solutions that offer real-time insights through Market Share: Vulnerability Assessment, 2023, Worldwide" and "Market Forecast: Vulnerability Assessment, 2024-2028, Worldwide" reports by QKS Group and proactive threat management capabilities.
Incorporating artificial intelligence, machine learning, and automation into these solutions will play a vital role in increasing their efficacy and allowing enterprises to remain ahead of new risks. Furthermore, increased collaboration between the public and private sectors and rising organizational awareness of the importance of cybersecurity will drive global adoption of Vulnerability Assessment tools, ensuring a secure digital landscape for both businesses and consumers.
0 notes
Text
In an already volatile IT world, it could all change in a moment, particularly when it comes to cybersecurity. And since PHP is the most powerful server-side language and the backbone for almost every website, it demands the adoption of best security practices. Therefore, PHP security shouldn’t be neglected at any cost. To prevent your PHP website from such attacks and vulnerabilities, we’ve compiled the top seven tips to help keep your website safe and secure online. Let’s have a look! 1. Keep Your Software Updated Keeping your software updated is a foundational practice of keeping your site safe and secure. It applies to both the server operating system and any software that you may be running on websites such as CMS or forums. Unfortunately, hackers can quickly attempt to abuse any vulnerabilities found in website security. If you are using third-party software on your websites, such as a CMS or forum, you should quickly apply any security patches. Most vendors have a mailing list or RSS feed detailing website security issues. In addition, there are many other CMSes such as WordPress and Umbraco that notify you of available system updates when you log in. Many developers use Composer, npm, and RubyGems to evaluate their software dependencies and security vulnerabilities. Unfortunately, if you do not pay enough attention to this area, your PHP website can be easily caught out by hackers. Ensure to keep your dependencies up to date and use tools like Gemnasium to get automatic notifications when there is a vulnerability in one of your components. 2. Beware of Error Messages Most importantly, you must know how much information you should give regarding error messages. You only need to provide only minimal errors to your users. This way, you can ensure that they don’t leak any sensitive information on your server, such as database passwords, API keys, etc. Also, pay attention not to provide full exception details so as not to invite complex attacks like SQL injection. You should keep all the detailed errors in your server logs and show your users only the information they need. 3. Check Your Passwords Many web admins often fail to use strong passwords despite this practice being considered an essential security requirement. Here, we’ve compiled a list of some effective password practices to prevent security breaches: The passwords can be more protected by storing the same encrypted values. The quality hashing algorithms can be used for this. The standard practice is to use at least eight-character passwords, including a number and a blend of uppercase and lowercase letters. If the password is still being accessed or guessed, you can use hashed passwords as they can’t be decrypted. 4. Protect Against XSS Attacks Do you know that XSS (Cross-site scripting) is one of the most common methods of hacking a website? It is done by injecting malicious JavaScript code into the web pages, which can permanently harm the website. In general, programs can run on the browsers used by the users and interfere with the user experience. XSS mainly happens through malicious program links posted through comments and other kinds of user-generated content. Using frameworks like AngularJS and EmberJS equipped with protection from cross-site scripting is a great way to prevent such attacks. In addition, it would help prevent the mixing of client-side and server-side rendering, reducing malicious JavaScript injections. There is another effective way to prevent XSS attacks; CSP (Content Security Policy) works like a server-side header to direct the browser about the JavaScript execution on any given page. In addition, it can be a potent tool to prevent cross-site scripting attacks. 5. Get Website Security Tools It’s time to test your website security when you think you have done all you can. The most effective way of doing this is using some website security tools, often referred to as penetration tests or pen-testing. There are several commercial and free products to assist you with this.
They work on a similar basis to script hackers. In this, they test all known exploits and attempts to compromise your site using SQL Injection. Check Out Some Free Tools Which are Worth Looking Into Xenotix XSS Exploit Framework: It is a tool based on OWASP (Open Web Application Security Project), which includes many XSS attack examples. This can be run to quickly confirm whether the site’s inputs are vulnerable in Chrome, Firefox, and IE. SecurityHeaders.io: This free online check tool allows free security and configuration checks for your website. OpenVas: It’s a free and open-source security testing tool with many advanced features. This tool is claimed to be the most advanced open source security scanner. It is suitable for testing known vulnerabilities and recently scanned over 25,000. Netsparker: This tool is available in both free and trial versions. It is ideal for testing XSS attacks as well as SQL injection. 6. Use HTTPS This is a protocol that is used to provide security over the Internet. HTTPS ensures what users expect in terms of security and that nobody else can change the content they see in transit. If users want anything private, it’s highly advisable to use only HTTPS to deliver it. For example, the credit card and other login pages have login forms. A login form often sets a cookie, which is sent with every other request to the website that a logged-in user makes. And it is used to authenticate those requests. An attacker might steal this sensitive information and take over the user’s login session. You only need to use HTTPS for your entire site to prevent attacks. It is now no longer as expensive as it was earlier. Let’s Encrypt offers free and automated certificates, which you’ll need to enable HTTPS. Also, there are existing community tools available for a wide range of common platforms and frameworks, which are automatically set up. Moreover, according to the report, Google will enhance those websites in search engine rankings that are equipped with HTTPS. This way, SEO benefits will also be provided to them. If you are already using HTTPS, then go further and set up HTTP Strict Transport Security (HSTS), an easy header that you can add to your server responses to disable insecure HTTP for your entire domain. 7. Input Validation Gazillions of PHP websites still depend on client-side programs for validating inputs. The client-side programs mean JavaScript-based input validation programs, which can easily be bypassed. You can also use rather server-side input validation programs. Final Thoughts When security threats have become more sophisticated than ever before, it’s not a good idea to depend on outdated security practices. Now you have excellent and comprehensive security strategies to prevent your PHP website from hacking. Furthermore, hiring mobile app developers for professional and advanced support is highly advisable.
0 notes
Text
Prevent Session Replay Attacks in Laravel: Best Practices
Introduction
Session replay attacks are a major security risk in web applications, especially in frameworks like Laravel. These attacks can lead to unauthorized access or compromise sensitive user data. In this blog post, we will explore what session replay attacks are, how they occur in Laravel applications, and most importantly, how to prevent them using best practices. We’ll also share a practical coding example to help you implement secure session handling in your Laravel app.

What is a Session Replay Attack?
A Session Replay Attack occurs when an attacker intercepts or steals a valid session ID and reuses it to impersonate the legitimate user. This type of attack exploits the session handling mechanism of web applications and can allow attackers to gain unauthorized access to sensitive information or perform actions on behalf of the user.
In Laravel, session management is a critical aspect of maintaining security, as Laravel uses cookies and sessions to store user authentication and other sensitive data. If the session management is not properly secured, attackers can easily exploit it.
How Session Replay Attacks Work in Laravel
Session replay attacks typically work by capturing a valid session cookie, either through methods like Cross-Site Scripting (XSS) or Man-in-the-Middle (MITM) attacks, and replaying it in their own browser. In Laravel, the session data is stored in cookies by default, so if the attacker gains access to a session cookie, they can replay the session request and hijack the user’s session.
To demonstrate this risk, let’s take a look at how a session ID might be captured and replayed:
// Example of a Laravel session where sensitive information might be stored session(['user_id' => 1, 'role' => 'admin']);
If an attacker intercepts the session cookie (usually via XSS or another method), they could replay the request and access sensitive data or perform admin-level actions.
How to Prevent Session Replay Attacks in Laravel
1. Use HTTPS Everywhere
Ensure that your Laravel application enforces HTTPS to protect session cookies from being intercepted in transit. HTTP traffic is unencrypted, so it's easy for attackers to sniff session cookies. By forcing HTTPS, all communications between the client and server are encrypted.
To enforce HTTPS in Laravel, add this to your AppServiceProvider:
public function boot() { if (env('APP_ENV') !== 'local') { \URL::forceScheme('https'); } }
This will ensure that Laravel always generates URLs using HTTPS.
2. Regenerate Session IDs After Login
One effective way to prevent session hijacking and replay attacks is to regenerate the session ID after the user logs in. This ensures that attackers cannot reuse a session ID that was valid before the login.
In Laravel, you can regenerate the session ID using the following code:
public function authenticated(Request $request, $user) { $request->session()->regenerate(); }
This should be added in your LoginController to regenerate the session after a successful login.
3. Set Secure and HttpOnly Flags on Cookies
Ensure that your session cookies are marked as Secure and HttpOnly. The Secure flag ensures that the cookie is only sent over HTTPS, and the HttpOnly flag prevents JavaScript from accessing the cookie.
In Laravel, you can configure this in the config/session.php file:
'secure' => env('SESSION_SECURE_COOKIE', true), 'http_only' => true,
These settings help protect your session cookies from being stolen via JavaScript or man-in-the-middle attacks.
4. Use SameSite Cookies
The SameSite cookie attribute can help mitigate Cross-Site Request Forgery (CSRF) attacks and prevent the session from being sent in cross-site requests. You can set it in the session configuration:
'samesite' => 'Strict',
This ensures that the session is only sent in requests originating from the same domain, thus reducing the risk of session replay attacks.
5. Enable Session Expiry
You can also mitigate session replay attacks by setting an expiration time for your sessions. Laravel allows you to define the lifetime of your session in the config/session.php file:
'lifetime' => 120, // in minutes 'expire_on_close' => true,
Setting an expiration time ensures that even if a session ID is captured, it will only be valid for a limited period.
Coding Example for Secure Session Handling
Here’s a full example demonstrating how to implement some of these best practices to prevent session replay attacks in Laravel:
// Middleware to regenerate session on each request public function handle($request, Closure $next) { // Regenerate session ID session()->regenerate(); // Set secure cookies config(['session.secure' => true]); config(['session.http_only' => true]); return $next($request); }
By including this middleware in your Laravel app, you can regenerate session IDs on every request and ensure secure cookie handling.
Using the Free Website Security Checker Tool
If you’re unsure whether your Laravel application is susceptible to session replay attacks or other security issues, you can use the Website Vulnerability Scanner tool. This tool analyzes your website for vulnerabilities, including insecure session management, and provides actionable insights to improve your app’s security.

Screenshot of the free tools webpage where you can access security assessment tools.
The free tool provides a comprehensive security analysis that helps you identify and mitigate potential security risks.
Conclusion
Session replay attacks are a serious security threat, but by implementing the best practices discussed above, you can effectively protect your Laravel application. Make sure to use HTTPS, regenerate session IDs after login, and properly configure session cookies to minimize the risk of session hijacking.
To check if your Laravel app is vulnerable to session replay attacks or other security flaws, try out our free Website Security Scanner tool.
For more security tips and blog updates, visit our blog at PentestTesting Blog.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By following these security best practices and using the tools available at PentestTesting.com, you can enhance the security of your Laravel application and protect it from session replay attacks.
1 note
·
View note
Text
Unlocking the Power of Angular: A Guide to Modern Web Development
Introduction
Angular is a cutting-edge web development framework designed by Google to build interactive and high-performance web applications. As an advanced front-end technology, Angular offers a structured approach to application development, making it a go-to choice for developers worldwide.
What Makes Angular Stand Out?
Angular is a TypeScript-based framework that facilitates the creation of robust and scalable web applications. With its powerful tools and features, developers can efficiently build dynamic single-page applications (SPAs) that offer a seamless user experience.
Core Features of Angular
1. Component-Driven Architecture
Angular applications are built using a component-based structure, where each component is a modular and reusable unit. This promotes better organization, maintainability, and scalability of applications.
2. Efficient Data Binding
Angular employs two-way data binding, ensuring instant synchronization between the model and the view. This reduces the need for excessive code, streamlining the development process.
3. Dependency Injection
A robust dependency injection system allows Angular applications to manage services efficiently, making the code more modular and testable.
4. Enhanced HTML with Directives and Pipes
Directives help extend HTML’s capabilities, while pipes transform and format displayed data, offering flexibility and ease of manipulation in the user interface.
5. Seamless Navigation with Built-in Routing
Angular’s built-in routing module enables smooth transitions between different sections of a single-page application, eliminating unnecessary page reloads.
6. Advanced Form Handling and Validation
Angular supports both template-driven and reactive forms, allowing developers to implement structured form validation and user input management effortlessly.
7. Angular CLI for Streamlined Development
The Angular Command Line Interface (CLI) automates repetitive tasks, helping developers create, test, and deploy applications efficiently.
Why Choose Angular for Your Development Needs?
High Industry Demand
Many companies rely on Angular for their web applications due to its ability to handle complex functionalities with ease, making it a valuable skill for developers.
Versatility Across Platforms
Angular can be used to develop progressive web applications (PWAs), enterprise software, and mobile applications using frameworks like Ionic.
Strong Developer Community and Support
Backed by Google and a large community, Angular offers extensive documentation, frequent updates, and continuous improvements, making it future-proof.
Best Practices for Angular Development
Use Lazy Loading to enhance application speed by loading resources only when required.
Adopt a Modular Approach to improve code maintainability and scalability.
Utilize State Management tools such as NgRx to manage application states efficiently.
Optimize performance with Ahead-of-Time (AOT) Compilation, reducing page load times.
Strengthen Security Measures by preventing cross-site scripting (XSS) and other vulnerabilities.
How to Master Angular Effectively
To get started with Angular, it’s essential to have a foundational understanding of JavaScript and TypeScript. Engaging in practical projects, enrolling in structured courses, and leveraging online tutorials can significantly improve learning outcomes.
If you are searching for the best Angular training institute in Hyderabad, ensure that the course provides hands-on training, real-world applications, and expert guidance.
Conclusion
Angular remains a dominant force in modern web development, providing developers with the tools needed to create interactive and scalable applications. Learning Angular opens doors to exciting career opportunities in the tech industry. To gain expertise in this powerful framework, consider enrolling in a professional training program. Monopoly IT Solutions offers comprehensive Angular training, equipping learners with the skills needed to excel in the competitive job market.
0 notes