#LinPEAS
Explore tagged Tumblr posts
Text
Comment Maîtriser l'Escalade de Privilèges ?
Qu’est-ce que l’Escalade de Privilèges ? l’escalade des privilèges L’escalade de privilèges consiste à obtenir des droits d’accès plus élevés qu’un utilisateur n’est censé en avoir. Après avoir compromis un système, un attaquant avec un accès limité tentera de devenir un utilisateur privilégié, comme root ou administrateur, afin de contrôler entièrement la machine. Cette technique est…
#cybersécurité#escalade de privilèges#failles de sécurité#GTFOBins#LinPEAS#Metasploit#privilèges administratifs#protection des systèmes#sécurité informatique#systèmes Linux
0 notes
Text
[Media] PurplePanda
PurplePanda This tool fetches resources from different cloud/saas applications focusing on permissions in order to identify privilege escalation paths and dangerous permissions in the cloud/saas configurations. Note that PurplePanda searches both privileges escalation paths within a platform and across platforms. The name comes from the animal Red Panda. This panda eats peas, just like Purple Panda, which can ingest API keys/tokens found by these PEASS. The color was changed to purple because this tool is meant mainly for Purple Teams (because it can be highly useful for both Blue and Red Teams). https://github.com/carlospolop/PurplePanda #redteam
YouTubeIntroducing PurplePanda: AUTOMATED Privilege Escalation IN THE CLOUDFrom the creator of LinPEAS, WinPEAS and HackTricks, check out PurplePanda! https://github.com/carlospolop/PurplePanda Follow Carlos to see what he is up to! https://twitter.com/carlospolopm https://www.linkedin.com/in/carlos-polop-martin/ https://www.instagram.com/carlospolop/ Help the channel grow with a Like, Comment, & Subscribe! ❤️ Support ➡ https://j-h.io/patreon ↔ https://j-h.io/paypal ↔ https://j-h.io/buymeacoffee Check out the affiliates below for more free or discounted learning! 🖥️ Zero-Point Security ➡ Certified Red Team Operator https://j-h.io/crto 💻Zero-Point Security ➡ C2 Development with C# https://j-h.io/c2dev 👨🏻💻7aSecurity ➡ Hacking Courses & Pentesting https://j-h.io/7asecurity 📗Humble Bundle ➡ https://j-h.io/humblebundle 🌎Follow me! ➡ https://j-h.io/discord ↔ https://j-h.io/twitter ↔ https://j-h.io/linkedin ↔ https://j-h.io/instagram ↔ https://j-h.io/tiktok 📧Contact me! (I may be very slow to respond or completely unable to) 🤝Sponsorship Inquiries ➡ https://j-h.io/sponsorship 🚩 CTF Hosting Requests ➡ https://j-h.io/ctf 🎤 Speaking Requests ➡ https://j-h.io/speaking 💥 Malware Submission ➡ https://j-h.io/malware ❓ Everything Else ➡ https://j-h.io/etc

0 notes
Note
What cheers you up?
❛ i’m a simple guy , nothing cheers me up more than successful privilege escalation so you know , enumerating linux boxes by looking for sudo permissions , crontab jobs running and getting a linpeas script ... or like that moment when you execute a shell and it just works so well ? that shit is orgasm - worthy . but also , cocktail shrimp . ❜

0 notes
Text
Hack The Box: Cap - Writeup

Nmap Scan
FTP, port 21
“Vulnerability Insight: A host that provides an FTP service may additionally provide Anonymous FTP access as well. Under this arrangement, users do not strictly need an account on the host. Instead the user typically enters 'anonymous' or 'ftp' when prompted for username. Although users are commonly asked to send their email address as their password, little to no verification is actually performed on the supplied data.”
http://www.securityspace.com/smysecure/catid.html?id=1.3.6.1.4.1.25623.1.0.900600
Unfortunately, the anonymous login exploit didn’t work. Still good to check though!
SSH, port 22
We don’t have the proper credentials to access the server through ssh; at least not yet. We’ll keep this in the back of our minds and come back to this later if and when we find the proper credentials.
HTTP, port 80
HTTP is a web-server so let’s check this from our browser.

Recon
Gobuster
A gobuster scan doesn’t produce additional results that we don’t already see from the web pages. Not too helpful, but still good to check!
After looking through the site, we’ll notice a page with a pcap file.
When we click on this page, we’ll find an empty traffic, but the url tells us that this page is in the data/ directory and we are currently viewing page: 4.
After tweaking the page parameter, we’ll find some traffic.
*** While a couple of other pages also had incoming traffic, after checking them on wireshark, they did not have any meaningful information.
From the /data/0 page, however, we can pick up some interesting information from the downloadable pcap file.

Follow the TCP stream of the pcap file from Wireshark.
In the TCP stream, we’ll find a conversation on Nathan’s FTP (vsFTPd 3.0.3) login credentials

FTP login
Using the credential from the previous step, let’s login to the FTP port
We can find the user flag when we list out the files from our current directory. However, since we’re on a FTP server, we’ll need to download the file first before viewing it.

SSH login
Although we’ve got the user flag, continuing with the FTP server is difficult to navigate through files. Moreover, we’ll need to escalate our privileges from our current position to receive the root flag.
Going back to our open SSH port, we can try using the same credentials from the FTP port; re-used passwords is a common practice by many people, though of course it is a common vulnerability.
Let’s check it out.

TSKTSK, shame on Nathan for using the same password. BUT, good for us attackers. Now that we are in the server as Nathan, we can go back to recon and identify any vulnerabilities.
Privilege Escalation
Linpeas
After serving up a linpeas report from our Kali box, we can download the report on our victim’s machine (nathan@cap) and send it back to our Kali to view. Within the Linpeas report, there is one notable flagged information: the output states a capabilities tab that has python 3.8 – meaning we have a cap_setuid available on the python 3.8 binary.

GTFOBins
With our findings from the previous step, we can check for exploits around the python 3.8 binary on GTFOBins.
GTFOBins a a list of unix binaries that can be “used to by pass local security restrictions in misconfigured systems”. https://gtfobins.github.io/

Since the python capability is already set, and the linpeas report states the 3.8 version of python, we’ll run this script from our victim’s system (nathan@cap).
Check to see if the exploit worked:
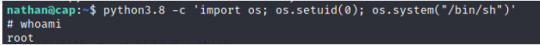
And we are ROOT!
Finally, navigate to the root directory and find the root flag.
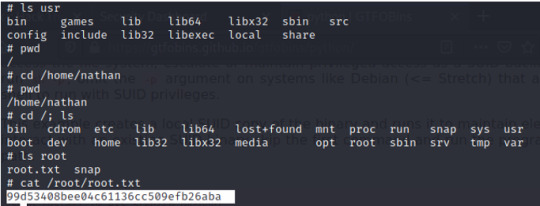
0 notes
Text
[Media] PEASS-ng
PEASS-ng Privilege Escalation Awesome Scripts SUITE (with colors) Here you will find privilege escalation tools for #windows and #linux/ #Unix* (in some near future also for #mac). These tools search for possible local privilege escalation paths that you could #exploit and print them to you with nice colors so you can recognize the misconfigurations easily. ▫️ Check the Local Windows Privilege Escalation checklist from book.hacktricks.xyz ▫️ WinPEAS - Windows local Privilege Escalation Awesome Script (C#.exe and .bat) ▫️ Check the Local Linux Privilege Escalation checklist from book.hacktricks.xyz ▫️ LinPEAS - Linux local Privilege Escalation Awesome Script (.sh) https://github.com/carlospolop/PEASS-ng
YouTubeDEF CON 29 Adversary Village - Carlos Polop - New Generation of PEASLocal privilege escalation techniques are far beyond checking the Windows/Kernel version, looking for unquoted service paths or checking SUID binaries. Moreover, a local privilege escalation could make a huge difference when trying to comprise a domain. Several tools have been created to find possible privilege escalation paths, but most of the tools for Red Team and Pentesting just check for a few possible ways, so pentesters need to use several tools and do some manual recon to check for everything. PEASS is a compilation of a bash script for Linux/MacOS/*nix and a .Net project and a batch script for Windows that I have created some time ago which aims to check and highlight every possible privescpath so professionals don’t need to execute several different tools for this purpose and can very easily find vulnerabilities. During this talk I would like to present PEASS-ng. The architecture of these scripts has evolved and improved so much that I would like to present how they work at the moment and how the difficulty to collaborate with the project has been reduced significantly. Moreover, I would also like to present the 2 new PEAS that haven't been present anywhere yet: BotPEAS and WebPEAS (the latest one will be released the day of the talk). During the talk I will also present my local privilege escalation resources (https://book.hacktricks.xyz/linux-unix/privilege-escalation , https://book.hacktricks.xyz/windows/windows-local-privilege-escalation) so the attended will be able to continue learning about the topic after the talk.

0 notes
Text
YAPS Yet Another #php #Shell As the name reveals, this is yet another PHP reverse shell, one...
YAPS Yet Another #php #Shell As the name reveals, this is yet another PHP reverse shell, one more among hundreds available out there. It is a single PHP file containing all its functions and you can control it via a simple netcat listener (nc -lp 1337). Features: 1. Single PHP file (no need to install packages, libs, or download tons of files) 2. Works with netcat, ncat, socat, multi/handler, almost any listener 3. Customizable password protection 4. No logs in .bash_history 5. Can do some enumeration Network info (interfaces, iptables rules, active ports) User info List SUID and GUID files Search for SSH keys (public and private) List crontab List writable PHP files 6. Auto download LinPEAS, LinEnum, or Linux Exploit Suggester 7. Write and run PHP code on a remote host 8. (Semi) Stabilize shell https://github.com/Nickguitar/YAPS

GitHub - Nickguitar/YAPS: Yet Another PHP Shell - GitHub Yet Another PHP Shell. Contribute to Nickguitar/YAPS development by creating an account on GitHub.
1 note
·
View note
Text
#Linux #PrivEsc Enumeration Tools LinPeas:...
#Linux #PrivEsc Enumeration Tools LinPeas: https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS LinEnum: https://github.com/rebootuser/LinEnum LES (Linux Exploit Suggester): https://github.com/mzet-/linux-exploit-suggester Linux Smart Enumeration: https://github.com/diego-treitos/linux-smart-enumeration Linux Priv Checker: https://github.com/linted/linuxprivchecker

PEASS-ng/linPEAS at master · carlospolop/PEASS-ng - GitHub PEASS - Privilege Escalation Awesome Scripts SUITE (with colors) - PEASS-ng/linPEAS at master · carlospolop/PEASS-ng
0 notes