#NetworkRouter
Explore tagged Tumblr posts
Text
RUTX50
INDUSTRIAL 5G ROUTER
RUTX50 is a dual-SIM multi-network router offering 5G mobile communication for high-speed and data-heavy applications. Together with 5x Gigabit Ethernet ports and dual-band Wi-Fi, it provides data connection redundancy with auto-failover.
For more information,
Visit: https://www.newtrend.ae/
Live chat: +971 507542792
#RUTX50#IndustrialRouter#5GRouter#DualSIMRouter#HighSpeedConnectivity#DataRedundancy#GigabitEthernet#WiFiRouter#AutoFailover#TechSolutions#MobileCommunication#NetworkReliability#5GTechnology#IoTConnectivity#BusinessConnectivity#NetworkRouter#TechInnovation#NewTrend
0 notes
Text
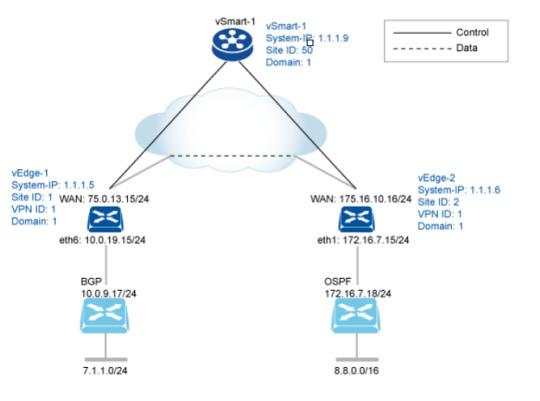
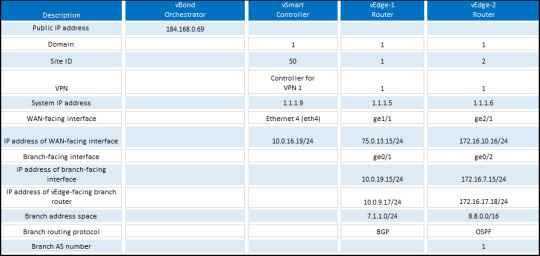
Explore practical routing configuration examples, offering essential skills for optimized data flow and network reliability. https://www.dclessons.com/routing-configuration-example
#RoutingConfiguration#NetworkRouting#DataCenterNetworking#CiscoNetworking#RoutingProtocols#NetworkDesign
0 notes
Text
Harnessing the Power of BGP Routing in WISPs and ISPs: Advantages and Use Cases

Introduction
In the dynamic world of wireless and wired communications, the efficient routing of data is a critical aspect that directly impacts the performance and reliability of networks. Border Gateway Protocol (BGP) routing, a standardized exterior gateway protocol, has emerged as a cornerstone in the arsenal of Wireless Internet Service Providers (WISPs) and Internet Service Providers (ISPs). This blog post explores the advantages and diverse use cases of BGP routing in these environments.
Advantages of BGP Routing:
Path Selection and Load Balancing: BGP allows network administrators to implement sophisticated path selection policies, enabling them to choose the optimal route based on metrics such as bandwidth, delay, and AS (Autonomous System) path. This capability facilitates load balancing across multiple links, enhancing network efficiency and resource utilization.
High Availability: BGP’s ability to detect and react to network changes in real-time contributes to increased network availability. In case of link failures or congested paths, BGP can quickly reroute traffic through alternative paths, minimizing downtime and ensuring a seamless user experience.
Scalability: As networks grow in size and complexity, scalability becomes a crucial factor. BGP is well-suited for large-scale deployments, allowing ISPs and WISPs to manage extensive networks without compromising on performance. The protocol’s hierarchical structure and support for route aggregation contribute to efficient scaling.
Policy-Based Routing: BGP’s flexible policy framework empowers administrators to implement routing policies tailored to their specific needs. This includes traffic engineering, where BGP can be used to influence the flow of data to optimize network performance and resource utilization.
Use Cases of BGP Routing in WISPs and ISPs:
Load Balancing Across Multiple Links: Imagine a scenario where a WISP serves a densely populated area with multiple high-speed links. BGP can be employed to distribute traffic across these links, preventing congestion and ensuring that bandwidth is utilized efficiently. This is particularly valuable in environments where network demand fluctuates throughout the day.
Redundancy and Failover: For ISPs, maintaining network availability is paramount. BGP provides an elegant solution for achieving redundancy and failover. In the event of a link failure, BGP can quickly redirect traffic along an alternate path, minimizing disruptions and enhancing the overall reliability of the network.
Interconnecting Autonomous Systems: WISPs and ISPs often need to interconnect with other networks. BGP is designed for inter-domain routing, allowing seamless communication between different Autonomous Systems. This is especially valuable in the context of ISPs that need to exchange routes with upstream providers or peer with other networks.
Traffic Engineering for Quality of Service (QoS): In scenarios where network administrators need to prioritize certain types of traffic, such as voice or video, BGP can be used for traffic engineering. By influencing the path selection, administrators can ensure that critical applications receive the necessary bandwidth and low latency, enhancing the overall quality of service.
Conclusion
The adoption of BGP routing in WISPs and ISPs brings forth a myriad of advantages, from efficient load balancing to enhanced network availability. The protocol’s versatility and scalability make it a valuable tool for managing the complexities of modern telecommunications networks. As the demand for high-performance and reliable connectivity continues to rise, BGP stands as a key enabler for ISPs and WISPs seeking to deliver seamless and robust services to their users.
#BGP#NetworkRouting#WirelessCommunications#isp#WISP#rural broadband#fixedwireless#highspeedinternet#connectivitysolutions
0 notes
Text
Payment channels in the Lightning Network enable users to conduct transactions without having to log each one on the Bitcoin blockchain, which lessens congestion and costs.However, like any network, the Lightning Network is not immune to security threats, and routing attacks are one of the potential risks. The effectiveness of the network may be affected by these attacks, and users may face financial risks.This article will explain routing attacks, how they work, their types, and how to identify and avoid them.What are routing attacks?By establishing a network of payment channels, the Lightning Network — a layer-2 scaling solution for the Bitcoin blockchain — enables quicker and less expensive transactions. So, can the Lightning Network be hacked?Although the Lightning Network improves scalability and effectiveness, it also poses some difficulties and security issues, such as routing attacks. In the Lightning Network, routing attacks refer to deliberate attempts by users to take advantage of weaknesses in the routing system for personal gain.A typical routing attack, for instance, entails a participant purposefully imposing high routing fees, making it expensive for other users to route their payments through that participant’s channels. This could make it more difficult for the Lightning Network to route payments effectively and affordably.How do routing attacks work?Malevolent users use a variety of tactics to target weaknesses or interfere with the Lightning Network’s payment routing system. As mentioned, setting extravagant routing costs is one typical practice to discourage other users from routing their funds through particular routes. This could make it more difficult and expensive to route payments, thus discouraging customers from using those routes.Another strategy is to trick the routing algorithm by spreading false information or mistakes throughout the network. For example, malicious nodes could broadcast inaccurate channel states, resulting in failed transactions and user annoyance. Such attacks may compromise the Lightning Network’s dependability and usability.Additionally, attackers might conduct probing attacks to learn more about the network architecture and user behavior, jeopardizing user privacy. Additionally, they may try to divert payments sent to authorized recipients to their own channels.To reduce the risks brought on by routing assaults, Lightning Network developers and users must be constantly watchful, upgrading network security, developing routing algorithms and encouraging responsible node operation.Common routing attacks in the Lightning NetworkRouting fee snipingIn this attack, a rogue node may purposefully establish excessive routing fees for a payment channel it controls. The attacker receives exorbitant costs whenever someone tries to route a payment through this channel. Due to the high fees and poor routing, this may deter people from using the Lightning Network.Probabilistic payment fraudIn this attack, a bad node pretends that a payment was unsuccessful when, in fact, it was successful. They can accomplish this by refusing to send the payment receipt or by posing as an error. By discouraging users from using specific routes or channels, this reduces the effectiveness of the network.Channel jamming attacksA hostile actor purposefully ties up the liquidity in a payment channel to launch channel jamming, a type of denial-of-service attack that renders the channel unavailable to authorized users and prevents them from transacting through it. In the worst-case scenario, if several channels are clogged at once, the Lightning Network may become congested, making it challenging for other users to find trustworthy ways to make their payments.Balance manipulationLightning Network nodes must keep a balance in their channels to enable payments. An imbalanced channel can be purposefully created by a malicious node, rendering it useless for routing, which may disrupt the network’s operations.Route flappingIn
this attack, a rogue node regularly modifies its channel restrictions or fee structures, making it challenging for other nodes to locate steady and dependable payment channels. Delays and ineffective routing may result from this.Sybil attacksA malevolent user can take over a substantial amount of the network’s routing capacity by setting up numerous fictitious nodes in the network. This can trick routing algorithms, extort money or carry out other attacks.Onion routing attacksThe Lightning Network employs onion routing to obfuscate the involvement of intermediate nodes in a transaction. However, a malicious node may try to de-anonymize the transaction by examining the routing data if it is part of the route. This might make the sender, receiver and amount of the transfer public.How to identify routing attacks in the Lightning NetworkIdentifying a routing assault on the Lightning Network can be difficult as bad actors frequently attempt to alter payment routing for their own gain. Routing attacks can take many forms, but they usually aim to stop the network from working properly or unfairly profit from routing fees.These attacks sometimes take the form of unusual payment failures, unforeseen routing fees, and sudden changes in channel liquidity. These malicious behaviors can be found using tools for network surveillance, watchtowers, route selection and node behavior analysis. For instance, malicious nodes can be found via node behavior analysis, including reputation systems and the identification of questionable behavior.Similarly, if a dishonest channel partner tries to steal funds, watchtowers intended to look out for suspicious behavior can broadcast penalty transactions and watch the blockchain for potential attempts to close the channel.One’s capacity to recognize routing threats can also be improved by actively participating in the Lightning Network community and studying previous attacks. That said, a network’s security efforts are strengthened by working with peers to maintain the network’s integrity as it develops.Is channel jamming the same as the routing attack?Channel jamming and routing attacks, while related within the context of the Lightning Network, are not synonymous. A routing attack is a broader term that refers to a number of malicious strategies used to manipulate payment routing for benefit or to disrupt networks.These strategies might entail purposefully rejecting payments, charging excessive routing costs or designing ineffective routes. On the other hand, channel jamming is a particular kind of routing attack in which a malicious node floods a specific channel with several small, unsuccessful payments, diminishing the channel’s liquidity and making it impossible for reliable users to route payments through it.While channel jamming is one way to interfere with routing, routing attacks go beyond that and include a range of tactics to jeopardize the security of the network. Therefore, users and node operators need to be aware of these differences to utilize the proper protections and increase the security and effectiveness of the Lightning Network.Related: What is a crypto dusting attack, and how do you avoid it?How to avoid routing attacks in the Lightning NetworkProtecting against routing assaults is crucial for the Lightning Network’s integrity and security. The following strategies may help users avoid routing attacks in the Lightning Network:Choose trusted nodesAs routing intermediaries, pick trusted and well-known Lightning Network nodes. Look for nodes that have a successful track record and positive user reviews. Additionally, channels can be kept safe even when users are not online by adding an additional degree of security through the use of watchtower services.Diversify channelsDiversifying routing pathways is useful for preventing payments from being unduly dependent on a single channel or node. Spreading transactions over several channels and nodes makes the network less susceptible to manipulation by attackers looking to impede the flow of money or extort a lot of money from users.
Monitor channel activityRegular channel activity monitoring is another essential element in recognizing and preventing potential attacks, which enables users to identify anomalies or suspicious behavior early on.Updated softwareStay up-to-date with the latest Lightning Network software updates. Developments frequently release patches and upgrades to fix security flaws and improve network resilience. Users can strengthen their defenses against routing attacks and promote a more secure environment for Lightning Network transactions by implementing these techniques. Source
0 notes
Text
The benefits of SD-WAN over traditional WAN architectures
The traditional hub and spoke model was predominant before the widespread use of SD-WAN. In a traditional model, to move data from the cloud, the data has to move to the data centre and then to the final destination. On the contrary, in the case of SD-WAN, Points of Presence or PoPs are distributed in the data centres across the globe, facilitating the transfer of data without routing through the data centre.
Before discussing whether SD-WAN is beneficial over traditional WAN architecture, let us understand both concepts.

Traditional WAN Several LANs located at different geographical locations are connected with one another in traditional networking. Traditional WAN connects branch offices and remote offices to the centralised network to access applications, share data and perform business functions. Conventional WAN was seen as a reliable means to deliver data, but as the business expands across geographical boundaries, the data has to travel through multiple carriers. This could lead to network congestion, packet loss, call drops, etc. Moreover, each and every server and router must be updated every time a change in policy occurs due to its distributed nature. User experience is compromised when streaming HD videos, virtual reality or during video conferencing.
SD-WAN SD-WAN connects hardware from various locations. Different connections are used for transporting data, including private lines, Virtual Private Networks or VPNs, Multiprotocol Label Switching (MPLS), broadband and LTE. SD-WAN finds the most efficient route to transport the data, whereas traditional WAN architecture uses corporate data centre connections to route the data.
Types of SD-WAN Architecture Enterprises can opt for three types of architecture, on-premises SD-WAN, cloud-enabled SD-WAN, and cloud-enabled with backbone SD-WAN.
On-Premises SD-WAN: It is a plug-and-play SD-WAN box that can be installed on your premises or onsite. It does not connect to the cloud gateways but uses company connections.
Cloud-enabled SD-WAN: This configuration uses both software and hardware. It uses an onsite SD-WAN device and connects to the virtual gateway. In turn, the gateways are connected to the cloud providers like Microsoft Office 365, AWS, Azure, DropBox and Salesforce.
Cloud enable plus backbone: Sometimes issues arise while using the internet with SD-WAN, to avoid this snag, backbone is used. It connects the enterprise premises to the cloud PoP and from here the traffic is diverted to the private fibre optic network backbone. The low latency private backbone results in minimum packet loss and jitters.
Why is SD-WAN better than traditional WAN? Thanks to the internet, businesses are transforming faster as the world is shrinking. The Pandemic has forced us to work from remote locations, and SD-WAN perfectly fits in this space. Let’s see why SD-WAN is better than traditional WAN.
Traditional WAN allows prioritisation and traffic predictability but at a high cost. On the contrary, SD-WAN cuts down on internet costs, and users must spend big money on bandwidth upgrades. SD-WAN offers flexible network connectivity as it can run both on LTE and broadband. SD-WAN is affordable and allows app prioritisation without any packet loss.
Traditional WAN is private and allows secure communication. In comparison, SD-WAN offers end-to-end encryption across a VPN connection with an option to add and merge additional security layers, such as firewalls, for unified threat management.
In traditional WAN, changes must be configured manually due to their distributed nature. In SD-WAN, you can scale as your business grows. Just leave it to your managed service provider, and they will do the rest.
SD-WAN is a reliable way to receive and deliver network services to your organisation. Though, some organisations adopt hybrid WAN. An organisation should select the appropriate network based on the long-term and short-term objectives in mind. Since each organisation has unique requirements, there is no one size fits all concept. You all require a skilled workforce for maintaining and managing network services. If you are ready for a change, then train your network professionals in SD-WAN for a seamless transformation.
SMOAD SD-WAN helps with a smooth transformation with its best-in-class services. Connect with us for more details.
#sdwansolutions#4glterouter#4glterouterwithsimcardslot#networkrouters#remoteconnectivity#multiwanrouter#loadbalancingrouter
0 notes
Link
Buy it Now http://ebay.to/2yUB8QL
0 notes
Text
Brill Infosystems Hiring Network Engineer Freshers
Brill Infosystems Hiring Network Engineer Freshers
Job ID : 20181129007
Company : Brill Infosystems
Job Role : Network Engineer
Eligibility : Graduate
Experience : Freshers
Job Location : Mohali, Punjab
Salary : Not Mentioned
Vacancies : Not Mentioned
Website : http://www.brillinfosystems.com
Description :
The Network Engineerwill be responsible for monitoring the networkfirewall, assessing the functionality of the networkrouters, ensuring all…
View On WordPress
0 notes
Text
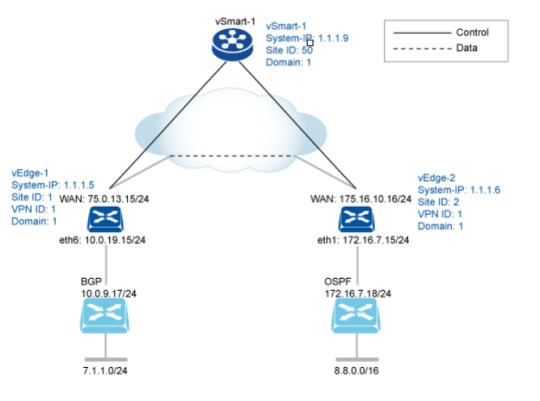
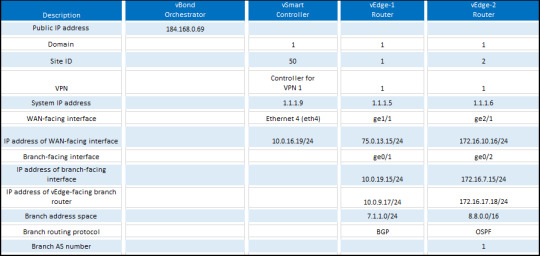
Learn routing configurations with our detailed examples. Gain practical insights into setting up and managing routing protocols to ensure efficient data transfer in your network. https://www.dclessons.com/routing-configuration-example
#RoutingConfiguration#NetworkRouting#CiscoRouting#RoutingExample#NetworkDesign#DataCenterNetworking#CiscoNetworking
0 notes
Text
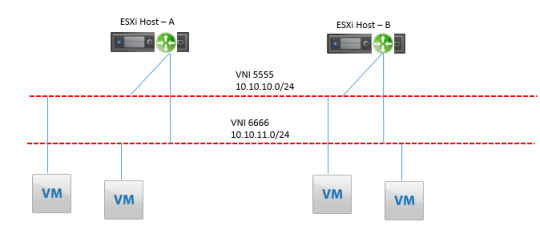
Understand the traffic flow within logical routers for efficient data routing and forwarding in virtualized environments. Optimize your network architecture for seamless communication. https://www.dclessons.com/logical-router-traffic-flow
#LogicalRouter#TrafficFlow#NetworkRouting#DataCenterNetworking#NetworkInfrastructure#ITArchitecture#NetworkManagement#NetworkDesign#EnterpriseNetworking#ITTraining#NetworkEngineering#CloudNetworking#NetworkSecurity
0 notes
Text
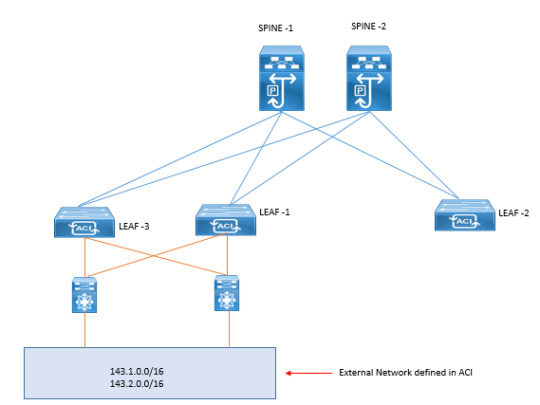
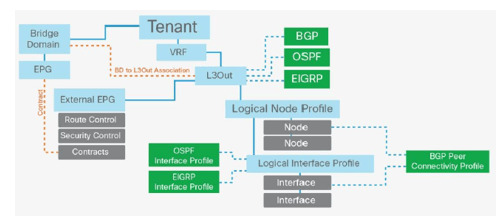
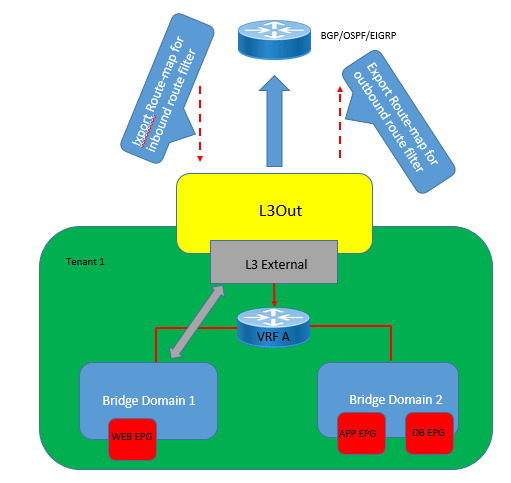
Delve into the complexities of Layer 3 outside external routed networks for seamless connectivity and efficient data routing. Enhance your understanding of network architecture essentials. https://www.dclessons.com/layer-3-outside-external-routed-networks
#Layer3#ExternalNetworks#RoutedNetworks#DClessons#NetworkingBasics#NetworkRouting#OutsideNetworks#ITTraining#NetworkInfrastructure#TechEducation#RoutingProtocols#IPRouting
0 notes
Text
How SD-WAN is transforming network security: Zero-trust architecture and more
Businesses are expanding into new geographical boundaries, increasing the need for a hybrid IT environment. The traditional network infrastructure is choking under pressure, unable to match the growing demands. The need for multiple sources has resulted in the growth of Software Defined Wide Area Network (SD-WAN) technology.

Can SD-WAN transform network security? SD-WAN promotes secure vendor and agnostic data transport across WAN or internet connectivity increasing hybrid cloud adoption. SD-WAN can aggregate multiple network technologies like MPLS, broadband, LTE, and 5G to connect to branches and remote offices. Compared with MPLS, SD-WAN is 2½ times cost effective due to secure edges, limited staff and router service costs.
Security is the top priority in SD-WAN. Organisations are keen on understanding the security impacts of installing SD-WAN as it should not expose the network to vulnerabilities while connecting to the cloud or embracing new endpoints. In an Enterprise Management Associates (EMA) report, respondents placed security on the top in SD-WAN.
Zero Trust Model in SD-WAN The security of SD-WAN increases with Zero Trust Model. So, what is Zero Trust Model? It is the security feature that stops trusting applications, networks, users or devices by default and introduces a host of verifications. In this model, authentication is given priority, followed by network security.
A secure SD-WAN architecture promotes agility and performance of your WAN network by establishing security-rich features that can be embraced with your present infrastructure. For on-premises to cloud end-to-end circuit encryption, the model uses IPSec 256-bit protection. The model assists IT managers to monitor and control the access points on the application and network. Firewalls and edge devices must be deployed for foolproof security.
How can the zero trust model replace traditional WAN? SMOAD SD-WAN enabled security and performance, helping save money. It encompasses all security SD-WAN solutions an organisation seeks. Zero trust principles are brought to every connectivity and not just users. All IoT/OT devices and servers are brought under the ambit of the model. It eliminates any threats and surface attacks using a router WAN network. Now you can convert your branch offices into modern branches using SaaS and cloud app deployments. Automated and integrated connectivity can reduce internet outbreaks and provides smarter and faster service.
New architecture needs new security with transactions moving to the cloud and internet; there is a need for a highly secure environment to protect distributed users from the vulnerabilities of attack. Today, applications, data and devices are moving out of the perimeter of security as they breach the traditional line of control. As the trusting enterprise perimeter is violated, there is a need for modern defence strategies for distributed workforces. It is here that the Zero Trust Model comes into play. Some of the tenets of this model include:
Securing resources and accesses irrespective of hosting model or location
Adopting default deny strategy while establishing application access
Traffic logging and inspection for applications you control and don’t in order to monitor any malicious activity.
Zero Trust Security components The Zero Trust Security components include:
Secure Internet Gateway (SIG): The ultimate idea of Zero Trust security is to protect the user while accessing applications beyond your control. A simple click can unleash cyber threats on your connectivity. With remote offices set in, the devices are unmanaged, and the internet is the choice of the corporate network. SIG is simple, quick and cheap while securing Direct Internet Access (DIA) traffic. SIG is safe, as it proactively protects users irrespective of location. Every DNS request is inspected, and malicious domains are blocked.
Identity Aware Proxy (IAP): The architecture provides application access through a cloud-based proxy. In this architecture, identity and authorisation happen at the edge and are only on a need-to-know basis. It uses standard HTTPS protocol at Layer 7 or the application layer. IAP identifies the source and verifies the user and device trust. It checks the security criteria like certification, password protection, endpoint direction, response solutions and installation of the latest OS. The user traffic is inspected, and any application request can be examined, authorised and terminated. After terminating the transaction on the proxy, additional features are integrated for better user experience and protection of the application.
Transform your business into a modern network model by protecting the line of defence. SMOAD believes SD-WAN with Zero Trust Security is the initial step to moving to a safe and threat-free internet.
Call us for a demo!
#loadbalancingrouter#multiwanrouter#networkrouters#4glterouter#sdwansolutions#4glterouterwithsimcardslot#sdwanrouter#4gsimrouter#5glterouterwithsimcardslot#remoteconnectivity
0 notes
Text
SMOAD SD-WAN AND THE INTERNET OF THINGS (IOT): ENHANCING CONNECTIVITY AND CONTROL
There’s no denying that SD-WAN has indeed enhanced the quality of connectivity and the business application experience. The continued evolution of SD-WAN has also enabled enterprises to take advantage of new customised IoT devices. The health industry greatly benefits from remote monitoring systems that report a patient’s vital signs to medical care providers within seconds. Retail stores can now automatically alert their warehouses with the list of products that need replenishment. The magnitude of IoT has constantly been on the rise since its creation, and it is estimated that the size of IoT gadgets may reach 500 billion by the end of 2030. Thanks to SD-WAN-enabled IoT! Flexibility, centralised management, and high security offered by SD-WAN solutions have enabled IoT devices to perform better and be more productive.

Networking Challenges Faced by IoT Low-latency connectivity, high cost, and poor management of IoT applications spread across multiple locations are the major challenges faced by IoT applications. Let’s take the surveillance camera, for example – the considerable quantity of data that public surveillance cameras transfer can overwhelm the traditional WAN network connections.
You need a solution that prioritises traffic and chooses the right WAN path according to the quantity of traffic transferred. Software-defined WAN (SD-WAN) does the same and streamlines connectivity effortlessly and cost-effectively.
Security is another great challenge faced by IoT applications. Developers usually leave backdoor access open for further development purposes. This makes IoT devices vulnerable to hacks and cyber-attacks. SD-WAN offers advanced security functionalities, and since it can be easily integrated with new devices, security-related challenges can be overcome with ease.
Why is SD-WAN considered the Key Enabler of IoT By now, you might be aware that SD-WAN offers flexibility which is much needed for the smooth running of numerous IoT devices connected over a wide range of networks. Besides that, it also makes the management of distant IoT applications easy. This is possible because SD-WAN can adapt to devise necessity and application requirements. Here’s how SD-WAN plays an essential role in simplifying IoT management:
1) Reduces Complexity IoT devices rely on a range of connections, including wireless, mobile, wired, static, and even cellular. Each connection has its speed, protocol, and agility. While some IoT devices may run on a specific type of connection, most others rely on a combination of one or more connectivity options. This can complicate the connectivity process and pose challenges when it comes to troubleshooting or ensuring a consistent performance from the IoT device.
SD-WAN does away with this complexity by enabling the combination of a range of connections into one hybrid network. SD-WAN allows management of the network from one interface and also makes routing decisions while trying to prioritise traffic.
2) Enhances Security As mentioned earlier, IoT devices are subject to hacks and attacks. The developer may leave endpoints open for further developmental processes, and these endpoints ultimately serve as vulnerable loopholes for hackers. Improper penetration testing of IoT applications can be another reason IoT devices suffer security issues.
SD-WAN offers high-quality security features through fine-grain segmentation of WAN. Through fine-grain segmentation of WAN, IoT devices are isolated or detached from the rest of the network, thus preventing hackers from accessing extremely secure and sensitive information. Moreover, SD-WAN also enables the virtualisation of security services so that they are deployed across a range of networks in a software format.
3) Enhances Network Visibility Real-time visibility is another challenge faced by IoT devices dependent on a spectrum of connections. Poor visibility results in the inability to identify the performance attributes of the IoT devices. This could prevent an information officer from gaining access to important metrics and ultimately result in poor device performance.
Most service providers offer SD-WAN solutions embedded with real-time visibility functionality that allows capturing the application and network performance in real-time. Even data such as the total bandwidth consumed by the IoT device can be captured using this functionality. This data can further be used to troubleshoot existing application issues or eventually enhance the device’s performance.
Adopting SD-WAN for your business can provide uninterrupted connectivity keeping your IoT devices on the toe round the clock. For more information on SD-WAN for your IoT devices, contact SMOAD.
Call us for a demo now!
#sdwansolutions#4glterouterwithsimcardslot#4glterouter#networkrouters#loadbalancingrouter#5glterouterwithsimcardslot#multiwanrouter#4gsimrouter#remoteconnectivity#sdwanrouter
0 notes
Text
THE CHANGE IN SECURITY, 5G, AND SD-WAN
The 5G is a complex technology making its security overwhelming. Enterprises are faced with the immense challenge of resolving security concerns of 5G; if you don’t, you are risking the growth of your organisation. The increased urgency to deploy new services adds to the risk. 5G network manufacturers and service providers are responsible for integrating security while deploying 5G. They must assess security effectiveness and focus on innovation rather than worrying about risks.

5G and SD-WAN The rise in user expectations has increased the complexity of WAN. SD-WAN monitors the performance of mixed connections like MPLS, internet, dedicated circuits, and satellite, selecting the most appropriate connection according to the traffic type. The SD-WAN makes decisions based on link performance, connection cost, and application needs. Traffic can be prioritised based on time-sensitive applications like VoIP over less urgent email.
SD-WAN built-in security The advantage of SD-WAN security is that it is built from the ground up. It is not an addition after the organisation is exposed to threats. A secure SD-WAN connection supports 5G speed without hampering business critical communication or breaching security gaps.
Security should match 5G Active traffic inspection at 5G speeds slows down the performance of next-generation firewalls (NGFW). Depending on native security functions of 5G networking solutions alone may not be sufficient, and organisations should adopt integrated, end-to-end security solutions to protect from threats. A secure SD-WAN solution can prepare the 5G to combat new world risks.
The security should be robust, integrated, and multilayered regarding internet branching. While combining SD-WAN and 5G solutions includes an integrated group of multilayered security controls and native controls for a secure solution. If you are experiencing local breakouts in your wired and wireless connections, integrate NGFW, DNS, SWG, IPS, and others for automated protection.
While bringing 5G into SD-WAN, the security concerns only increase. 5G means speed, and security bottlenecks must be addressed while keeping up with speed. SD-WAN security must be fast enough for 5G. With the volume of encrypted traffic increasing, the TLS adoption rate is faster. It is always important to support 5G without disturbing business-critical communications.
It is not easy to achieve this security standard as it is perceived. The NGFW performance takes a huge toll while inspecting encrypted traffic. Monitoring high volumes of encrypted traffic using TLS 1.3 encryption protocol to protect 5G connections from threats will harm SD-WAN and firewalls, putting both speed and security at risk.
So, how do we tackle this situation? Organisations must adopt Secure SD-WAN solutions from the ground up to improve performance. The answer is to use purpose-built security architecture instead of commercial processors. Ensuring the SD-WAN solutions are designed to manage critical security functions without compromising performance rates.
It is important to integrate security into the network seamlessly. With a unified management interface, changes in the SD-WAN environment are visible and managed from one interface. So, both can respond as one consolidated system when a connection requires a change.
The role of secure SD-WAN in 5G must be supported. SD-WAN integrating security and networking, along with hardware created for maximum performance and scalability to power 5G network, is perfect for organisations transitioning to 5G to look for advanced functions to avoid security concerns. Transcend into 5G smoothly with secure SD-WAN solutions for uninterrupted connectivity at an affordable cost.
SMOAD offer state-of-the-art SD-WAN solutions to integrate with 5G securely.
#sdwansolutions#4glterouterwithsimcardslot#loadbalancingrouter#multiwanrouter#5glterouterwithsimcardslot#remoteconnectivity#networkrouters#4glterouter
0 notes
Text

Can anyone answer this? #QuizoftheWeek
Explore Now!!
0 notes
Text
How SD-WAN will advance in 2023
The coronavirus pandemic brought many changes, some of them rather drastic. One of these changes was how the organization worked before, during, and after the pandemic. Work from home became the new normal between the pre-pandemic and post-pandemic eras. However, with the advent of working from home, particularly during the pandemic, several changes were witnessed, especially in the in-office IT infrastructure plans. With more and more people working from home and the need for a secured network becoming the order of the day, cloud-based networking architecture has become the top choice of organizations worldwide.
The traditional network technology could not handle the amount of data the pandemic days thrust upon them. This opened the door for various developments in the networking field; one of those was Software Defined Wide Area Networks or SD-WAN. In SD-WAN, data, connectivity, and traffic between the branches and the headquarters are managed by the cloud environment. These hubs are the “edge” and are crucial for cloud security.
The issues with conventional networking technology were eliminated with SD-WAN. It helped boost the network speed, minimize downtime, improve efficiency, and cut costs, amongst several other advantages. And now, despite the pandemic slowing and people returning to offices, SD-WAN is here to stay. This is because it has helped the offices to work with better efficiency and security.



SD-WAN is constantly evolving and is expected to do so in the new year. The top four trends in the genre of SD-WAN expected to make significant inroads in the coming year are as follows:
1. Secured Remote Access Security of the network is one of the most significant advantages of SD-WAN. As the employees from the branch offices and remote work setup logged in from different geographical locations, it resulted in serious security issues. SD-WAN helps resolve security concerns. With this architecture, employees could install SD-WAN endpoints in their homes. With SD-WAN, it has become possible for employees to log in to the company’s network with a high level of security, even during travel.
In the coming year, two trends in this particular genre are expected. These are:
An amalgamation of SD-WAN and remote access technology
Replacement of SD-WAN with secure remote access
2. SD-WAN As a Service Companies offering SD-WAN solutions highlight management, optimization, and redundancy capabilities in their package. Companies offering SD-WAN solutions are now pitching it as a service, meaning everything with regards to SD-WAN, right from installation to maintenance, is the service provider’s responsibility. With such a solution, businesses can narrow their attention to their core competencies because they have fewer SD-WAN-related concerns to examine and address.
3. Secure Access Service Edge Secure Access Service Edge is a combination of SDN and SD-WAN along with security features. SASE is an ultra-secure, high-on-performance, and highly adaptable network architecture. It is now anticipated that SD-WAN will eventually become a part of SASE. If a business uses SD-WAN as a service, it can quickly upgrade to SASE architecture down the road.
4. Artificial Intelligence in SD-WAN Artificial intelligence is making its presence felt in SD-WAN in significant ways. It is helping in:
Improving the choice of the traffic path
Providing improved policy definitions
Supplying automatic support for troubleshooting
Improved performance and security surveillance
In addition to many other advantages, any new trend in IT networking aids businesses in maximizing their efficiency. Since these kinds of changes herald either partial or complete overhauls in specific IT systems, any organization needs to consult its networking team before deciding on any modification. As an experiment, these kinds of solutions can be used in a sandbox setting, and the same applies to SD-WAN.
Companies using SD-WAN or planning to implement it should focus on the latest trends in the discipline. This will help to maximize the return on investment.
#MultiWanRouter#SDWANRouter#4glterouterwithsimcardslot#simbasedwifirouter#5glterouterwithsimcardslot#SIMcardinternetrouter#sdwansolutions#networkrouters#remoteconnectivity#loadbalancingrouter#4gsimrouter#simwifirouter#4glterouter#new year#january 2023
0 notes
Text
MULTIPLE ROUTERS AT THE SAME LOCATION? THE PROS AND CONS
The demand for higher bandwidth, even for home, has made us think of using multiple routers to extend the range of the network. But is this a viable option, or is there another alternative? Additional routers can do both harm and good when it comes to improving wireless transmission or bandwidth. Let’s see how.Well then, what are the options available to increase your network’s speed, strength, and coverage area? Read on…



First, let us analyse the Pros of using more than one router to extend your wireless coverage area.
1. Give life to dead zones: Beat blind spots in your home or office with additional routers. There may be zones in your space where the signal is nil or weak. In such cases, you can cover dead zones with the additional router to improve network frequency. If you have a wired connection, connect either end of the Ethernet cable to the primary router’s LAN port and the additional router’s WAN port. Set up the software, and you are done.
2. More networks, more security: The secondary router can access devices connected to the primary router, but the reverse is impossible. This provision gives the secondary router extra protection from external attacks, while the primary router is vulnerable to threats. More devices in a larger area will be able to connect to a wider area wirelessly.
3. Classifying devices: Having highly vulnerable machines on the secondary router can provide a secure network environment and improve the Wi-Fi performance. Though the device connected to the main router cannot access the secondary router, the device is prone to security threats. Devices with deficient security protocols like smart home appliances or voice assistants may become inaccessible to the outside world. A Wi-Fi network can be made larger to accommodate far-off devices by adding an additional wireless router. Devices that need high-speed internet, like gaming consoles, IoT devices, smart TV, etc., can have a dedicated Wi-Fi router. In such situations, the secondary router will deliver data packets to high-volume devices instead of overburdening the primary router.
4. Downtime reduced: Maximise your network connectivity by adding multiple routers to special zones. So, if the primary network is overloaded, you can move to the secondary router to minimise downtime. This can be helpful for small offices or home offices that cannot afford frequent downtime.
LAN ports are available in wireless routers, so connecting to devices with the help of cable is a practical option. A secondary router could be suitable if you run out of ports.
Now comes the cons of using additional routers
1. Connection shuffles could be a pain: The SSID differentiates your network from others. When you move from one router to another, your devices must disconnect from the primary to move to the secondary router. This leads to downtime and time lag, hampering your business activities. The switch in connectivity between two routers may often occur, especially if there is poor connectivity and when routers are placed in equal range to the devices.
2. Signal Intrusions: The routers function on the same frequency. Multiple routers can cause signal issues as one router interferes with the performance of the other, ultimately blocking each other’s operation. Though, this can be fixed easily if you understand the coverage range of each router. Place each of the routers in contrasting locations to prevent interference. With dead zones in the middle, the scope for overlaps turns zero.
3. Networking: This could be confusing, especially with real hardware. Setup and configuration are not an easy deal, and not everyone will want to understand the operations. Further, connecting multiple routers using an Ethernet cable is ideal for the best output. But this would hike up the cost. If you do not know how to configure a router, professional help is around the corner.
Understanding the functions of a router is crucial for fast and downtime-free network connectivity. Learn the basics of how packets are transferred or get professional help.
Contact us for professional guidance.
For customized solutions, get in touch with us.
SMOAD Networks www.smoad.io
#MultiWanRouter#SDWANRouter#4glterouterwithsimcardslot#simbasedwifirouter#5glterouterwithsimcardslot#SIMcardinternetrouter#sdwansolutions#networkrouters#remoteconnectivity#loadbalancingrouter#4gsimrouter#simwifirouter#4glterouter
0 notes