#NetworkSegmentation
Explore tagged Tumblr posts
Text

What is Cisco SD-LAN? A Beginner’s Guide to Software-Defined Access Learn Cisco SD-Access with DCLESSONS to master network automation, segmentation, and security using Cisco DNA Center and ISE. Aligned with the latest certifications. https://www.dclessons.com/blog/what-is-cisco-sd-lan-a-beginner-s-guide-to-software-defined-access
0 notes
Text
Improving Enterprise Network Connectivity In The Digitization Age

Enhancing network performance is one of the most significant ways an organisation can stay ahead of its competition. Read More. https://www.sify.com/network/improving-enterprise-network-connectivity-in-the-digitization-age/
#BusinessNetwork#EnterpriseNetworkConnectivity#DigitizationAge#Bandwidth#IntrusionDetectionSystems#IDS#NetworkSegmentation#NetworkVisibility
0 notes
Text
Best Practices for Secure Remote Desktop Access
https://supedium.com/cyber-security-tips/best-practices-for-secure-remote-desktop-access/ #ActivityMonitoring #multi-factorauthentication #networksegmentation #passwordmanagement #RemoteDesktopSecurity #VirtualPrivateNetwork Best Practices for Secure Remote Desktop Access https://supedium.com/cyber-security-tips/best-practices-for-secure-remote-desktop-access/
0 notes
Text
Elevate Your Network Security with Network Segmentation from Century Solutions Group!
In the ever-expanding digital landscape, a one-size-fits-all approach just won't cut it. That's where network segmentation comes in – like creating digital neighborhoods within your network, each with its own security measures and access controls.
Why is network segmentation crucial? Picture your network as a bustling city . Without proper segmentation, a breach in one area could spread like wildfire, jeopardizing your entire infrastructure. But with segmented networks, we're building digital fortresses, containing threats and minimizing their impact.
Don't let your network become a free-for-all – trust Century Solutions Group to implement smart segmentation strategies and keep your data safe and sound. Your security is our top priority! #NetworkSegmentation #CyberSecurity #CenturySolutionsGroup
1 note
·
View note
Text
Firewalla Gold SE Review for Home Lab
Firewalla Gold SE Review for Home Lab @FirewallaLLC #firewalla #firewallagoldse #homefirewall #firewallareview #homelab #homeserver #cybersecurity #networksegmentation #networksecurity #virtualizationhowto #vhtforums #selfhosting #networkmonitoring
I was recently sent one of the new Firewalla Gold SE devices to test out in the home lab. However, other than the unit being sent to me for my thoughts, this is not a paid review, and I only give my thoughts and opinions on testing and using the Firewalla in the home lab. Many of the readers of this site are interested in home labs and technologies for home labs reviews. The question is, is this…

View On WordPress
0 notes
Link
0 notes
Text
PCI-DSS Compliance and Network Segmentation

Compliance for the Payment Card Industry Data Security Standard (PCI DSS) starts at the network segmentation. Well, segmentation in this context refers to instituting controls aimed at enhanced data security. To sufficiently meet the requirements on PCI segmentation, an understanding of the standard’s purpose and objectives are critical.
The Card Holder Data Environment (CDE)
According to PCI DSS, the Data Cardholder Data (CHD) includes the personally identifiable data associated with a specific individual’s debit or credit card. The information may include the name of the cardholder, primary account number, service code, expiration date, or other sensitive authentication data. Primarily, CD holds the necessary information that a thief could use to make several fraudulent charges. The cardholder data environment includes any networked system or computer that stores, processes or transmits the sensitive cardholder’s data. The CHD also incorporates computing devices, applications, computing devices, servers and other system components. It can also include virtual components, security services, server types, applications or anything linked to the cardholder data environment.
Network Segmentation according to PCI DSS
The scope of network segmentation includes understanding the manner in which data moves within the system. You can use the analogy of a river to understand CDE and CHD. In this case, the cardholder data environment (CDE) is the river, and the cardholder data is the boat traveling along the river. And just as there are many access points for boats, CDE has numerous data access points. Networks are similar to rivers with various connecting tributaries. If the cardholder data can flow down a branch, then it’s critical to institute safeguards along the river and its tributaries, or even construct a dam. Connectivity according to PCI DSS includes wireless, physical, and virtualized. CHD can enter the river at any point. The USB drive can be physical connectivity, while Bluetooth and wireless LANs, the wireless connectivity. The virtualized connectivity comprises the common resources such as virtual machines and virtual firewalls. It is critical to secure each of these access points to prevent incidences of data theft and fraud.
How Businesses Scope Systems
The scoping of PCI DSS entails a critical evaluation of all the data access points in your cardholder environment – the CDE river. Cataloging on how and where you get the cardholder data is the first step in PCI DSS assessment. The assessment involves walking up and down along the banks of your CDE river to identify all the payment channels, and CHD acceptance methods. It does not stop there, however. You will need to track the route the information takes, from the collection point through to disposal, destruction, and transfer. The next is identification and documentation of the specific locations where storage, processing or transfer of the data occurs. It entails not only understanding those involved in handling the data, but also the technologies and process involved as the data moves through the CDE. After tracking the flow of the information through your network, the next step is to incorporate all the system components, processes, as well as, the people that impact the CDE. Unlike the previous one, this step involves looking beyond those that interact with the information and concentrating on those that manage the data environment. After the CDE review, you will then need to create sufficient controls to safeguard the information. In the same way that some rivers have landings to keep boaters from specific access points, your network requires controls. It is crucial to determine where the CHD can flow to and who can access it. That means creating dams by setting up adequate security measures such as encryption and firewalls. After setting control, you need to ensure application to all the affected systems, components and personnel. You will also need to monitor the controls and make changes as the data environment evolves.
Out of Scope Systems
According to PCI Security Standard Council defines out of scope systems as those without any access to any CDE. But finding these out of scope systems is an uphill task. The Security Standards Council requires such a system not to process, store or even transmit cardholder data (CHD). It must also not connect to any CHD-linked network segment or system involved with CHD. The system shouldn’t have access to or influence any security control associated with CHD. Be careful before declaring the system out of scope. You see, the trees around the river would be in scope if they can access the same water as the river.
Is it Possible to Transfer Risks to Third Party Organizations?
Service providers, as well as, third-party organizations are within the fold of your PCI DSS. These service providers and third-party organizations are like forest rangers in connection to your CDE river. Mostly, they provide remote services or engage with your network environment and can expose it to risk. Read the full article
0 notes
Photo

RT @avrohomg: Are you Prepared for a Rise in NationState #CyberSecurity Attacks & #Ransomware in 2020? #cloudsecurity #microsegmentation #criticalapplications #networksegmentation #criticalinfrastructure @ChuckDBrooks @cybersecboardrm @TylerCohenWood @mirko_ross @AkwyZ https://t.co/ATAn0fiKf1 https://t.co/G4noYFcC2w by 27aume on February 11, 2020 at 10:47PM
0 notes
Text
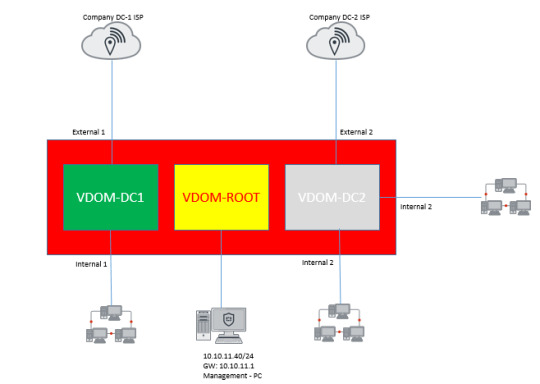
Master the configuration of Virtual Domains (VDOMs) in FortiGate with our in-depth lab tutorial. Discover how to segment and manage your network efficiently using VDOMs for enhanced security and performance. https://www.dclessons.com/lab-vdom-configuration-in-fortigate
#FortiGate#VDOM#NetworkSegmentation#TechGuide#FirewallManagement#NetworkSecurity#CyberSecurity#FirewallConfiguration#Fortinet
0 notes
Text
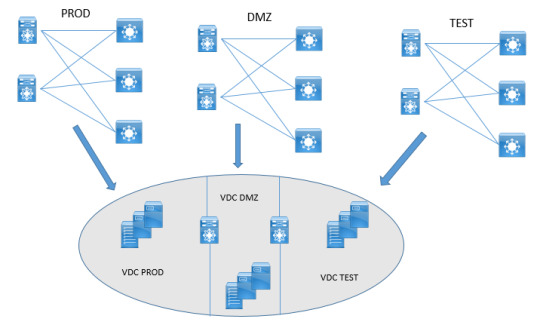
Gain insights into Virtual Device Context (VDC) for efficient resource allocation and management in data center environments. Optimize your network infrastructure with VDC deployment strategies. https://www.dclessons.com/vdc-introduction
#VDC#VirtualDeviceContext#DataCenterNetworking#NetworkVirtualization#ITInfrastructure#NetworkManagement#NetworkSegmentation#ITArchitecture#EnterpriseNetworking#ITTraining#NetworkDesign#CiscoNetworking#CloudNetworking
0 notes
Text
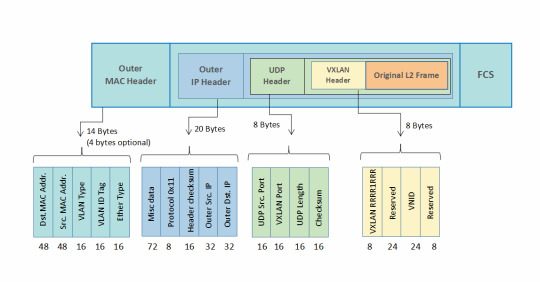
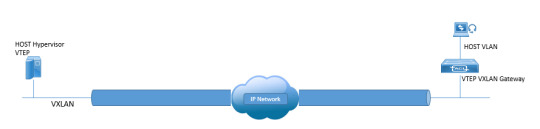
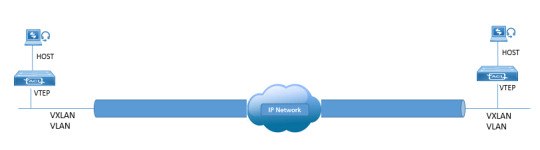
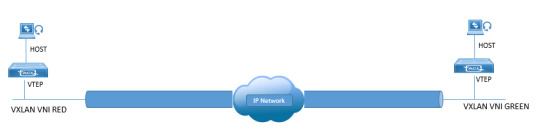
Ready to elevate your networking skills and dive into the world of VXLAN (Virtual Extensible LAN)? DC Lessons offers a range of courses in this cutting-edge technology, designed for IT professionals, network engineers, and anyone passionate about network virtualization. https://www.dclessons.com/category/courses/vxlan
#VXLAN#NetworkVirtualization#SDN#DataCenter#CloudNetworking#NetworkingTechnology#NetworkSecurity#NetworkArchitecture#Layer2Extension#NetworkOverlay#VirtualNetworks#NetworkProtocols#DataCenterNetworking#NetworkSegmentation#NetworkInfrastructure
0 notes
Text
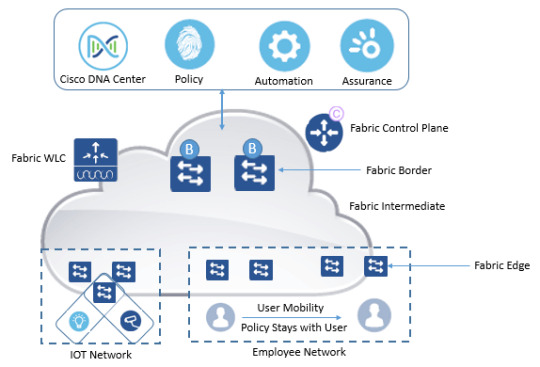
Unlock the power of #SoftwareDefinedAccess. Explore courses that redefine network control and automation. Become a leader in simplifying network complexities and enhancing user experiences. https://www.dclessons.com/sd-access-key-features-usecases
#NetworkAutomation#NetworkSegmentation#SDAccess#SoftwareDefinedAccess#NetworkSecurity#DigitalTransformation#NetworkingTechnology#NetworkInfrastructure#ITInfrastructure#NetworkManagement#CloudNetworking#EnterpriseNetworking#NetworkArchitecture
0 notes
Text
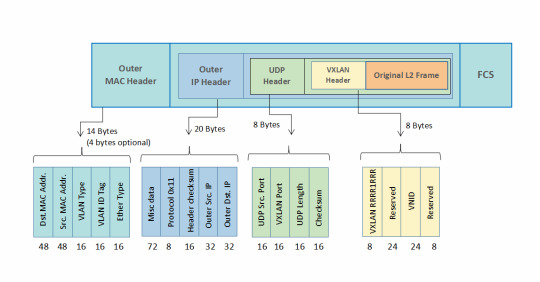
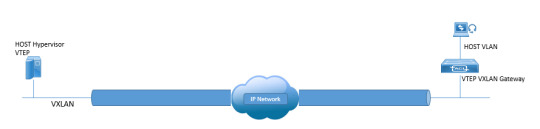

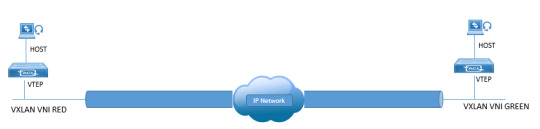
Master network segmentation with #NexusVXLAN. Explore Virtual Extensible LAN to optimize your data center's performance and flexibility. Unlock insights that redefine network architecture. https://www.dclessons.com/category/courses/vxlan
#NetworkSegmentation#DataCenterOptimization#VXLAN#VXLANTraining#CiscoNexus#JuniperEVPN#networking#datacom#datacenter#cloud#IT#VXLANfabric#EVPNVXLAN#networkautomation#SDN#NFV
0 notes
Text
Proxmox VLAN Configuration: Management IP, Bridge, and Virtual Machines
Proxmox VLAN Configuration: Management IP, Bridge, and Virtual Machines #proxmox #proxmoxvlan #proxmoxvlanconfiguration #proxmoxnetworking #virtualizationhowto #selfhosted #homelab #networksegmentation #microsegmentation #virtualmachines #homeserver
Proxmox is a free and open-source hypervisor with enterprise features for virtualization. Many may struggle with Proxmox networking and understanding concepts such as Proxmox VLAN configuration. If you are running VLANs in your network, you may want your Proxmox VE management IP on your management VLAN, or you may need to connect your virtual machines to separate VLANs. Let’s look and see how we…

View On WordPress
0 notes