#Protection from hackers and viruses
Text
Ah fuck I've done it again
Amalgam AI AU
I've seen some AUs about the humans being AI instead of Caine and I thought that might be the simplest way to get this monstrosity to happen with a massive glitch without abstraction playing a part.
I think I just really like horror AUs and doing stuff like that is just so fun so I made another one with a better title than "Horror House" cuz c'mon what the hell does that mean lol
The only characters I don't have designed currently are Zooble, Caine, and Bubble but I'll add them soon. Caine will be a human, Bubble could be something to help him out and what not.
Inspired by AUs like Sm-baby's and The Horror Circus AU, but like, different ofc.
Think this: the game wasn't originally supposed to be a horror game, just a game you go through for fun. Like Undertale, I guess? But not quite
[WARNINGS: LOTS OF EYES/ARACHNID IMAGERY, BODY HORROR, EYESTRAIN]
So first and foremost, I think people would wanna see Pomni, though Jax was the first to be designed.

Pomni is supposed to be some sort of anti-virus or some sort of protecting thing. Supposed to fix bugs and glitches and prevent viruses from getting into the game. Like a firewall, I guess? I tried to make her look like "right/wrong" esc thing. She was the last to be designed and it was like 1 am when I designed her. I had no clue what to do with her, I'll be completely honest.
Story wise, she'd be trying to find a way to undo this massive glitch and get the game back to normal before she can even rest. Once Caine pops up to try and fix the game from inside, as a dev himself, she does her best to protect him and help him fix the game.
No there is no shipping in this AU, they're just helping each other basically survive. They might become friends over time but nothing more. :V
Next up: Ragatha and Gangle! I actually really like Gangle's design but Ragatha definitely needs a few tweaks I think.

Ragatha, before this massive glitch, would have been an NPC that would help a player out at the start but end up getting lost after a certain point, like a tutorial. She was the most caring character in the game before everything went down.
Gangle used to be someone who ran a little theatre thing in the game, as I've seen from other AUs and took inspiration from, but she's usually nice no matter what mask she has on. More arms means she can help more people at once, right? Game mechanics wise she was like a little shop keeper for costumes if they're needed and she can help with newer mechanics on stage if something new is added. Friendly NPC, you know? Love her design, too!
Now for the first two to be designed, Jax and Kinger!!

So Jax was like a reoccurring villain, I guess. Always trying to make the player quit the game or just scare the shit out of them, despite him not being very scary himself. He's more played off to be a joke character, if I'm honest, always failing with his antics and what not. It's part of the code! I actually like his design, small lil paws and just so shapey over all.
Kinger was like a final boss, I guess? The scariest of all of them at that time. He was a king, ruling over his pawns and such, all of which were also bug themed! I love making Kinger bug related it's so fun. He's a big softie in reality but hits like a train if you ever went against him. He had terrible vision despite all of his eyes and was very slow despite the amount of legs.
Now for what everyone has been waiting for.
The reason for the AU title.
The MASSIVE glitch that caused everything to go downhill.
The Amalgam.

I still think it needs a few tweaks here and there but this is one of four concepts I've had for it.
One time all four of these characters were together, which was relatively rare but possible, a glitch happened in the game. Pomni doesn't know where it started from and none of the game devs understand how it happened, but it did. Some devs think there's a hacker. A massive glitch pulled those four characters together into one terrifying being, always hostile and destructive. All the code of the characters were merged into this thing and somewhat scrambled. The game has now been broken to where once you're in, you can't escape until it's fixed, yet no one knows it, which is why Caine went in.
So much has happened and it's still being fixed, but a hostile blob of characters constantly attacking whenever it's near? It will be hard to fix.
It seems to be guarding something.
Concepts for the amalgam:




You can see in the first one I was going to put Zooble there but I still need a good design for Zooble. Let's see what they'll be.
#the amazing digital circus#tadc#tadc caine#tadc kinger#tadc pomni#tadc jax#tadc ragatha#tadc gangle#tadc zooble#tadc au#amalgam ai tadc au#aatadc au#tw body horror#tw spiders#tw eyestrain#tw eye horror#don't tag as ship
21 notes
·
View notes
Text

Murder Drones ocs!! YAY!!
.
Fanfiction yayyy
I designed a Worker ( Hacker) Drone Maggot for my best friend megatronrules112
Based off their character “Maggot” !
Disassembly Drone Ghostley is Maggots best friend :3
Story ( but i’m not a writer)
Maggot is banished from the worker drone homes so he is forced to wander the ice wastelands alone.
Maggot soon meets a very injured and starving Disassembly drone ( Ghost).
Ghost bites Maggot on the hand to drink his yummy oil.
As the two are struggling, the ground gives out under them and they both fall.
Murder drones have wings so Ghostley saves himself but then sees that Maggot is hanging off a cliff.
Ghost saves Maggot and protects him from other Disassembly drones. They become friends and decide to live with each other (since Maggot can repair robots). Ghost is heavily damaged and full of viruses, BY THE POWER OF FANFICTION Maggot can heal him with his cool mechanic / hacking skills.
#murder drones fanfic#murder drones fanart#murder drones#murder drones oc#sketch#doodle#maggot#Ghostley
8 notes
·
View notes
Text
Rockman.EXE and Cyber Security.

When you are a Rockman/Megaman Battle Network fan and you take a college course about networking, you start to notice how broken the internet is in the anime. So just for fun, I want to talk about a few things I learn about network security and how it is interpreted in the Megaman Battle Network anime.
1. Firewalls
What are firewalls? In simple terms, it is a security barrier that is placed between a private network and the public network.
They are configured to monitor and filter networking traffic, hackers go through them by figuring out how they are programed, once they do they can either bypass the security undetected or simply disable the firewall.
Lets take a scene from the movie where Lan sends Megaman into a secretary’s console to destroy a program inside a company’s server.

Megaman is running through the network between the console and the firewall, which protects the private network of the company.

Logically, for Megaman to go through the firewall, he is going to need to use his powers as a Net Navigator (Net Navi) to analyze the firewall at an incredible speed to try to find a way to go through it, right?
WRONG! Battle Network logic says you can just break it with brute force!
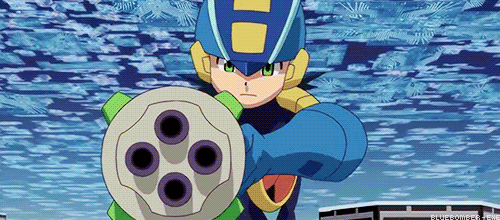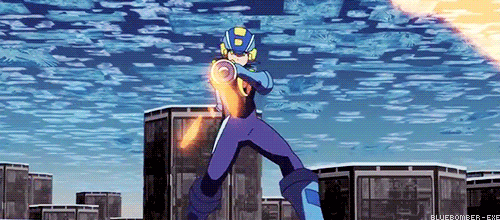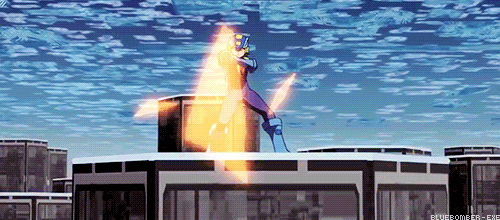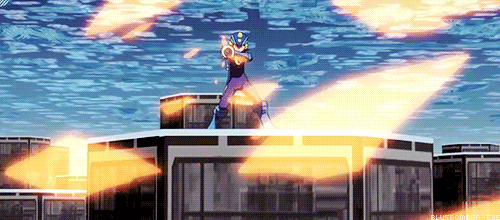

You see the problem?
Does this mean Navis and battle chips are just as destructive to the net as viruses? Because last time I checked, Viruses and malware are the only programs with the ability to destroy networks.
2. Viruses
Viruses are man made, they are programed with a purpose that’s usually to destroy data files. They can also be used to change and manipulate programs, that’s why you can see evil Navis controlling viruses to do specific jobs for them. Viruses can’t replicate on their own without a user interface, so how is this Moloko a baby?!

There was an undubbed episode of Megaman Axess where Rush meets and befriends a baby Moloko virus, which doesn’t make any sense. Yes, Rush is a virus, and it has been established that viruses can communicate with each other, but why does this Moloko have parents? And why was the group of Molokos it separated from was being herded by other viruses like Trumpy? All I’ve seen Molokos do is charge at megaman when they see him, trying to ram him. Why would someone herd them? For the wool? It disappears after you hit it!
And what even is Rush’s purpose anyway? When he first appeared in the anime, he was made to track down Rockman’s frame or structure when they were trying to revive him with the backup data, but now?
All he does is being a crappy character who runs away when things get dangerous, doesn’t act like a dog anymore, and irritates me because he can move between the cyberworld and the real world! He is selfish, lacy, and practically useless, there are several times where Megaman goes missing and Rush is never even called to track him down, so he doesn’t even have that ability anymore.
On a positive note, viruses can be interesting, I found out that there are different types of viruses. For example.
A Stealth virus is a virus that avoids detection from anti virus software, this means it can conceal itself and attack without being spotted, sounds familiar? In this case the anti-virus software would also include Navis.
A retro virus tries to destroy anti-virus programs, I like to think these apply to viruses who specifically target Navis in battle like Canodumbs and Piranahs since they only attack when they detect an enemy in the line of fire.
Armored Viruses are hard to detect or analyze because they have a protective code, These could be Viruses with armors or auras like the Dominerd or even the life virus.
But Phage viruses remind me of these guys because they rewrite programs.

And I guess this one counts too?

Other viruses just act like malware, like the Alpha bug that is more of a worm than a virus, because it can replicate and travel across networks without any human assistance.
Others are obvious like the Pop up virus which is just Rush, and it is supposed to be adware, but just like Rush, it is more annoying than harmful.
In the anime, killereye viruses are used as spyware, there was an episode were Videoman used them to spy on Rockman and make copies of him.

3. Tracing a signal.
Basically, everything you do on the net leaves bread crumps or cookies behind that makes it easy to track a user online, every device have a Mac Address and every network has an IP address, but it takes a special kind of software and advance skills to track down somebody in the real world.
Let’s talk about episode 32 of Stream.
Remember that episode were Megaman followed a revived Shademan to 20 Years in the past and he witnessed a famous hacking incident that was stopped by Colonel?

Aside from the fact that it was 20 years in the past and Megaman is more advance than most of the technology there, there were a few things bothering me.
For starters, why does that computer show a little Colonel doing something to that guy’s hacking program? It’s cute and all, but this is a confusing way to show someone disabling a program, it usually just shows a notification. Or is that how the computer sees colonel, like a little pixel version of him? XD
That hacking program was made to open any cyber lock, it uses three special pillars to disguise the signal so the police wouldn’t be able to track down the address, this means those pillars have some special form of encryption to cover the data to make it untraceable. In the anime’s world, that means it’s invisible, but somehow Megaman can still sense it? And how did Barryl know where the guy was? Did colonel tell him? Or did the viruses he sent to delete colonel revealed his location? Oops.
4. Hard Drives.
To end this post, what are hard drives? They are what your computer uses to store files, so Navis can obviously be stored in a computer as well. The problem is that they are still sentient inside the computer instead of dormant.
The concept of containing a Navi, yes, Navis have their own jail in this universe, doesn’t really make any sense. We know Navis can sleep, but the Navis we see in cages are still active, and if everything is connected to the internet, how can they not escape?
I’m using this scene with Megaman as an example, when he was arrested for being in the wrong place at the wrong time, he was put in a cute little cyber cage.

However, since Megaman is more advance, he wonders if the hard drive of the computer he is stored in is weak against vibrations. What does he mean by that? Physical or cyber vibrations? Does that mean he can control a frequency in that computer’s cyberworld to alter it?
Whatever he did worked, because he left a gap in the cage, but how did he do it without damaging the Hard Drive? The police officer wouldn’t be able to access his files anymore, maybe it was minor file corruption?
And the worst part is that he opened a gateway into the internet, which is still there! I guess Megaman can travel through routers by himself? Maybe that wouldn’t have happen if the officer just disconnected his ethernet cable.
This Network based world is a scary one.
46 notes
·
View notes
Text
TADC OC: Officer Gaurd!

First of all Merry Christmas and Happy holidays!! ❤️
Ahhhh I'm so happy to be finally posting my boy 🥺🥺
Sooooo here is some info about him ❤️
•He is an A.I. designed by Caine to enforce rules, ensure the censorship of mature topics and protect the circus from viruses or hackers
• Technically, he lives in the circus' code and controls the firewall but Caine gave him a visual form and a station for him to hang around. Being as short and boxy as he is makes him a little stiff and awkward when moving around.
• He's not super agile in the circus, thinks almost everything is illegal/a virus because they're not as easy to identify visually (as opposed to their 'code form'. I imagine him loudly asking the characters 'ARE YOU A VIRUS?', and it's not a good idea to say yes. Jax knows from experience.
• Has the authority of a mall cop, not super intimidating, especially to the cast members.
• Takes his job very seriously. When he's in the circus he's patrolling almost 90% of the time, oftentimes from somewhere very high up (no one knows how he gets up there. He throws himself down when he notices something suspicious and it's either very startling or concerning. Jax thinks its funny)
• Doesn't seem like it, but he is very good at his job. He's vicious with threats and lawbreakers. Despite not being able to recognize a virus visually, he has an amazing sense when it comes to detecting actual threats. He states it's because he can 'smell broken code'.
• He calls Caine boss and is willing to beat up anyone who disrespects him (he's not super clever though so whenever someone talks to Caine in anything but a reverent tone he takes it as a lack of respect and offers to beat them up). Deeply enjoys getting his approval. Caine calls him by a different rank everytime and he always gets exited about it. ("Excellent job, Captain!" "*gasp* I'm a Captain??!?!")
• Has a sort of rivalry with Bubble. Gaurd keeps shooting at him, but he eats all the bullets.
Hehe I hope you like him~ here are some close-ups






#tadc#the amazing digital circus#tadc oc#original character#tadc original character#tadc fanart#min's art
16 notes
·
View notes
Text
!Spoilers for FNAF SB Dlc Ruin.!
Of all the theories I've been seeing lately on fnaf after the dls came out, the "this entity is actually good and trying to protect us" theory confuses me the most. Wtf? Where did this even come from?

Wasn't it hinted to us throughout the game that the Entity was not part of the V.A.N.N.I's "protection program"? And didn't this protection program tried to delete him, but to no avail, because he hacked the program himself + in response puted his own plugs that prevented us from entering/exiting the AR of the world at the most critical moments (when there was a scene with Freddy, we couldn’t enter the V.A.N.N.Y program and hide from the prototype, or from Chika too)?





Secondly, this character does not save us/ program protacols, he kills us with the hands of other animatronics, before that he tries to break in our brains.
Third, have you even seen his beta design?? It's stupidly the skeleton of an Afton/Glitchtrap, so most likely, this creature is a Glitchtrap.

Many people give me evidence that the Entity does not have purple in the palette and does not look like an afton (although when it appears it spawns purple cubes) ) but come on, this is not the first time when afton is redesigned and then everyone builds theories about "two springtraps )

But how to explain the last cutscene, where he is sucked into the server, when we turn off the protection program completely?

Well...first of all, does he look upset? He pulled out with a satisfied smile, which leaves his face only when he realizes that he is being sucked back.

Most likely, this version of Glichtrap behaves like a deep-rooted virus, which, in our case, was deeply rooted in the protective program, so it could use its skills and not be deleted, and when the program itself was completely disabled (not just the protocols), he was also turned off(at least for some time,because such viruses can affect other programs and came back again) .
And the last, final argument - if it's not Glichtrap, then who is? Bonnie? The one lying around with bowling balls? How did he then become a hacker and try to kill us?! Gregory? - he has no idea what happened to us, he had no contact until the end of the game. Anyone else? Then who and how? The most logical thing is for it to be the same virus, rather than inventing 50 different evil rabbits. So NO HE IS NOT GOOD
11 notes
·
View notes
Text
What are the features of browser security?
Keeping your stuff safe online is super important. When you're browsing the web, you want to make sure nobody's sneaking in to steal your info. That's where web browsers come in. They're like your online bodyguards, keeping the bad guys out.Think of it like walking through a busy street. There are shady characters trying to pickpocket you, but your browser's security is like having a strong friend who watches your back. So, when your browser has good security, it's like having a tough bodyguard who keeps you safe from viruses, fake websites, and people trying to mess with your accounts.Browser security is all about making sure you can surf the web without worrying about someone stealing your stuff. So next time you're online, thank your browser for keeping you safe!
Here are some important features of browser security that will help you ensure a safe browsing experience —
First, update your browser - It is very important from a security aspect.
Secure and Encrypted Connections – Modern browsers use secure protocols, such as HTTPS, to establish an encrypted connection between the user's device and the website they are visiting. This encryption ensures that the sensitive information, such as login credentials and payment details, is transmitted securely and cannot be tampered with by hackers.
Anti-Malware and Phishing Protection – Browsers often come equipped with built-in features that can detect and block malicious software and phishing attempts. These features can flag suspicious websites, warn users about potential threats, and even block harmful downloads that could infect their devices.
Pop-up Blockers – Pop-up windows can be not only annoying but also potentially dangerous. They can contain malicious ads, deceptive messages, or attempts to trick users into downloading malware. Most browsers have pop-up blockers that can prevent these windows from appearing, reducing the risk of users by clicking on harmful links.
Cookie and Tracking Controls – Browsers allow users to manage cookies, which are small files that websites save on a user's device.
5 notes
·
View notes
Text
Unlocking Cyber Security: Your Essential Guide to a Safer Digital Journey
The world of Cyber Security—a digital fortress protecting your online world. In this guide, we unravel the mystery of Cyber Security to empower you with the knowledge needed to navigate the virtual landscape safely.
Buckle up as we embark on this journey into the heart of Cyber Security. Together, we'll demystify the complexities, providing you with the tools and most importantly, knowledge needed to fortify your digital presence. Let's make your online experience not just secure, but also stress-free.
Understanding Cyber Threats
In the vast digital expanse, Cyber Threats lurk like unseen shadows, aiming to disrupt your online peace. Let's peel back the layers and understand these virtual adversaries.
The Basics: What Exactly are Cyber Threats?
Cyber Threats are the mischievous characters of the internet world, sneaking around to cause trouble. They come in various forms, from sneaky viruses to cunning hackers.
Breaking it Down: Types of Cyber Threats
Viruses and Malware: These are like digital infections, spreading through the online world.
Phishing Attacks: Picture online scams as fishing expeditions, trying to hook your sensitive information.
Hacking Shenanigans: Cybercriminals who attempt to break into your digital fortress, such as burglars trying to pick locks.
Why Cyber Threats Matter to You
Understanding Cyber Threats is crucial because, without this knowledge, your online world is similar to an unguarded fortress. Because they can infiltrate, disrupt, and can also cause chaos. It's like leaving the front door wide open.
How Support, Managed Service, and Uptime Play a Role
They're here to fortify your defenses, ensuring Cyber Threats have a tough time infiltrating. Click on these terms to discover how they form the backbone of your online security.
Facing Cyber Threats Together
Now that we've unveiled the shadows of Cyber Threats, the next step is arming yourself with knowledge. Stay with us as we explore the tools and strategies to outsmart these digital troublemakers. Together, we'll make your online journey not just safer but also more enjoyable. Onward!
Importance of Cyber Security Measures
In the vast playground of the internet, Cyber Security stands as your reliable companion, offering protection and also peace of mind. It's not just for big companies; but also everyone who uses a computer, a phone, or anything online. So now let's dive into why Cyber Security is your digital shield, while also keeping the bad stuff away.
Protection Beyond Passwords
Cyber Security goes way beyond just having strong passwords. However, it's like having a smart guard at your digital gate, watching out for any suspicious activity and also making sure only the good stuff gets through.
Guarding Your Digital Castle
For instance, think of your digital life as a domain, and Cyber Security as the essential shield fortifying its boundaries. It keeps the cyber-dragons (those pesky online threats) at bay, while also ensuring your personal information stays safe and sound inside.
Why You Need Support, Managed Service, and Uptime
Now, here's the secret sauce – Cyber Security is not a one-time thing. It's a continuous effort. That's why you need Support, Managed Service, and also Uptime in your corner, however, it keeps your digital world running smoothly.
Support: Your Digital Lifesaver
When things get tricky, our Support team is here. They're like your digital lifeguards, ready to rescue you from any online wave that might knock you off your feet.
Managed Service: Making Your Life Easier
Our Managed Service takes care of the tricky technical work for you. It's similar to a reliable companion managing all the tech details, while also allowing you to concentrate on your preferred online activities.
Uptime: Keeping You Connected 24/7
It measures how consistently a computer system or service remains operational, reflecting the reliability and accessibility of the system over a specified period.
Best Practices for Cyber Security
Navigating the digital world can be tricky, but with these Cyber Security best practices, you can navigate the online landscape with confidence.
1. Fortify Your Passwords
Creating a strong password is your primary defense. Think of it as locking the door to your digital house. Much better to use a mix of letters, numbers, and if possible, includes symbols – it's like adding extra locks.
2. Keep Software Updated
Imagine your digital world, where software updates function as essential elements to keep everything running smoothly. Regular updates make sure your digital programs stay safe and sound, keeping the danger away.
3. Be Cautious with Emails
Emails can sometimes be like tricky. Be mindful – because if something seems off, don't you open it. That is why our Support team is here to guide you through any email mysteries.
4. Back Up Your Digital Treasures
Keep your important files, keep it as treasures – back them up! It's like having a secret vault, so even if something goes wrong, you won't lose your precious digital memories.
5. Embrace Two-Factor Authentication (2FA)
Two-Factor Authentication is similar to having an extra protection. Because it adds an extra layer of security, this one ensuring only you can access your digital world.
Why You Need Support, Managed Service, and Uptime
Following these best practices is much important at all, however it's not a solo act. That's where Support, Managed Service, and Uptime come in – like your trusty support team, making sure you stay on the right path of cyber-heroism.
Support: Your Digital Guides
Our Support team is your go-to guide, that is to say our team is helping you navigate the digital landscape. That is why if you ever feel lost, they're just a click away.
Managed Service: Your Tech Wizard
Having a tech professional by your side – which our Managed Service can handle the tech stuff so you can focus on the fun.
Uptime: Your Digital Assurance
Uptime is your digital assurance. Because it ensures your online world is always open for adventure, and also never leaving you stranded.
By following these Cyber Security best practices and having your digital allies, you'll be surfing the digital waves worry-free.
Conclusion
As we wrap up our journey through the world of Cyber Security, always remember – your digital safety is our top priority. Whether it's learning more about Cyber Security or even exploring the benefits of Managed Service, your digital adventure continues. Click, explore, and embrace the limitless possibilities of a secure and also enjoyable online world. Your digital tomorrow awaits – so let's make more it extraordinary together!
2 notes
·
View notes
Text
"Is the Tor Browser Safe to Use? Exploring the Benefits and Risks of Anonymous Browsing"
The Tor Browser is a popular web browser that allows users to access the internet anonymously and privately. It works by routing your internet traffic through a network of volunteer-operated servers, which makes it difficult for anyone to track your online activity or identify your IP address. While the Tor Browser can be a useful tool for protecting your privacy and security online, many people wonder if it is truly safe to use. In this article, we'll explore the safety of the Tor Browser and provide some tips for using it safely.
Is the Tor Browser safe to use?
The short answer is yes, the Tor Browser is generally considered safe to use. The browser is open-source software, which means that anyone can review the code and look for vulnerabilities or security flaws. Additionally, the Tor Project (the organization behind the Tor Browser) is committed to maintaining the security and privacy of its users.
However, it's important to note that no software is completely foolproof, and the Tor Browser is no exception. While using the Tor Browser can help protect your privacy and anonymity online, there are still some potential risks to be aware of.
One potential risk of using the Tor Browser is that it can be used to access illegal or malicious content. Because the Tor network allows users to remain anonymous, it has become a popular tool for criminals and hackers to conduct illegal activities such as selling drugs or weapons, distributing malware, or engaging in other nefarious activities. As a result, using the Tor Browser to access certain websites or online communities can put you at risk of encountering illegal or harmful content.
Another risk of using the Tor Browser is that it can be slower than other web browsers due to the way it routes your internet traffic through multiple servers. This can make browsing the internet feel sluggish or unresponsive, which can be frustrating for some users.
Tips for using the Tor Browser safely
Despite these potential risks, there are several steps you can take to use the Tor Browser safely:
Keep your browser up-to-date: Make sure you're using the latest version of the Tor Browser, which will include the latest security patches and bug fixes.
Use a strong password: When creating an account or logging in to a website while using the Tor Browser, be sure to use a strong, unique password to protect your account from hackers.
Avoid downloading files: To minimize the risk of downloading malware or viruses, avoid downloading files or software while using the Tor Browser.
Use two-factor authentication: Where possible, use two-factor authentication to add an extra layer of security to your online accounts.
Be aware of your online activity: When using the Tor Browser, be mindful of the websites and online communities you visit. Avoid websites that may contain illegal or malicious content, and use common sense when engaging with others online.
In conclusion, the Tor Browser can be a useful tool for protecting your privacy and security online, but it's important to use it safely and responsibly. By following these tips, you can help ensure that your online activity remains safe and secure while using the Tor Browser.
#TorBrowser#OnlinePrivacy#AnonymousBrowsing#InternetSecurity#CyberSafety#OpenSourceSoftware#WebAnonymity#OnlineSecurity#InternetPrivacy#SafeBrowsing#informatology
8 notes
·
View notes
Text
Black Mirror: Season 3
Episode 3: “shut up and dance”

Synopsis:
In the midst of the bustling and interconnected technological universe we live today, "Shut up and Dance" takes us into a disturbing analysis of how our intimidated is violated and influenced by digital media. Set in the near future, the plot centers on Sara, a college student who sees her existence take an unexpected turn when she is involved in the world of cyber extortion.
A mysterious hacker, using a lethal weapon: In order to protect her reputation, Sara is compelled to undertake a series of supposedly insignificant but embarrassing acts. As the pressure builds, she falls prisoner to a deadly game where technology stands as the worst of her enemies and threatens her freedom.
Through surprising plot twists and a story full of tension, "Shut up and Dance" raises fundamental questions about online security, the fragility of our digital lives and how privacy occupies an increasingly sqlvático world. Exploring the darkest corners of technology and human nature, this Black Mirror release presents a visually striking aesthetic alongside poignant performances.
While Sara faces a merciless enemy and struggles with her own feeling hopeless, the audience is captivated by an intense emotional experience that leads us to reflect on the real control we have over our lives during these digital times. In "Shut up and dance", it is clear how in the virtual world there is no clear separation between public and private boundaries; showing us how a simple action like clicking can distort both truths and falsehoods.
Analysis:
IA and social media: In the chapter we do not see that the AI does not affect, but if the social networks because of a harassment that has an unknown person, the main protagonist has to do things he does not like as meet more people with the same problems or more serious, even had to kill another person to q the last equal to be disclosed a video of him, many people suffer from this daily because they are manipulated through social networks or cases where they get into pages with viruses and watch them all the time.
Mental health: Mental health has a great effect on our daily life and is related to our emotional, psychological and social well-being. It influences our most difficult moments and we react to various situations in which we face throughout our lives. This episode shows us a clear example of how, due to difficult situations and an imbalance in mental health, people made mistakes because they did not know how to deal with crises, stress, anguish, desperation and did everything to save their reputation.
Unfortunately we allow many people to play with our mental health and this is how it is presented in this episode, even though we want to be conscious in our actions, to manage our emotions, when we have pressure in various situations we make mistakes, stress wins us and our decisions go down, our life falls and in it our mental health and that is when we react and we realize that it was better to face the mistakes and not hide them no matter what, our physical and psychological health is worth more.
Positive aspects: social networks help us to manage our future, i.e. many activities in the future they will make our lives easier but they can replace us, through them we can communicate with our relatives at a distance and in emergency situations, social networks are a means of communication that when used in the right way are used to disseminate certain important news and be in context with what happens in the world second by second, the networks facilitate information, communication and entertainment and in our hand is the use we want to give it.
Negative aspects: Social networks are categorized as a double-edged sword, many people take advantage of this knowledge in them to do evil, identity theft, theft of photos, personal information and manipulate people to do what they want, it is unfortunate that such an important and very useful tool little by little we are damaging it and so it is destroying us.
Rating:
The score we give to this chapter is 10, this chapter is one of the strongest chapters that in our opinion Black Mirror has had, it is known that Black Mirror touches on themes from the dark side of technology; This specific chapter talks about pedophilia and how hackers through the computer can be aware of everything the user does and use this against him. This 19-year-old young man violated his privacy by recording a video of him masturbating and How they threatened him that they were going to upload this video to networks and make him do illegal things.
This leads us to see the reality of many young people today and how this can influence their behaviors and mental health, leading them to commit illegal acts and even lead to death.
Technology is advancing rapidly, but even though it seems safe, we are always willing to take risks just by being on the Internet, in addition to the fact that technology today unfortunately handles everything and just one click away they have all our information.
This chapter leaves many lessons, mainly about the care that must be taken with the devices and the information we give to them, because they can be within the reach of all hackers.

3 notes
·
View notes
Text
W.H. (Sans Doll) ( WHITE HAT) Desktop!tale MY AU MY OC
My new character, anyway... I created this character to PROTECT my au from possible HACKERS and ocs viruses or bugs, it serves to make the environment safe I created it specifically for that (jokingly the white hat hackers and black hat hackers is that black hat hackers are hackers who want to destroy, defame, anarchists who want to dominate and mess with other people's stuff and even copy, while white hats do the opposite, they protect people from pretentious black hat hackers so there he is *** W.H (white hat)***he is a sans doll and lives on the desktop!tale .Desktop!Tale (my au) ***I want to keep bad characters and gods out of my universe and make it safe ;w;, is it too much to ask?***
this is White Hat sans I created it precisely to protect my multiverse from a new character that wants to enter the aus and destroy them for fun, like this character, and the only thing that can defeat a HAcker is another HAcker but when the most HACKERS characters are evil I decided to create a good one, based on the code of hackers (white hat and Black Hat), Black hat are malicious hackers who try to calm the computer's mess, while White Hat tries to correct its mistakes, the purpose of this Sans Doll is to protect invader mines (BLACK HACKERS) like ERROR 404, ERROR SANS, INSANITY SANS (yes it is stronger than ERROR 404), BUT IT ONLY ACTS WHEN THERE IS EXTREME URGENCY (WHICH MEANS THE ENEMY MUST BE IMPOSSIBLE TO DEFEAT)
AU: Desktop!tale (my au)
Name: W.H (WHITE HAT)
Age: ???
Favorite food: Hamburguer
Like: your friends
Deslike: evil hackers,virus and bug monsters evil
IMMORTAL
Type: Neutral Good
EC: infinite
Personality:
-silent
-Cold;
-Calm;
-Mature.
Powers:
-use copies of powers to
protect yourself from opponents' attacks;
-can multiply;
-create portals to confuse your opponent;
-use the CHEAT mode to get out of the traps;
-he can't read minds, but he can memorize yours
opponent's attacks and predict them.
special attacks:
"block messages" : (block messages of thoughts or speech he doesn't want to see),
"banned": will banish the character
in your world making it impossible to return,
FireWall: protective shield that will protect
all who are in it and repel unwanted intruders",
special attack (the last one he uses) "Neuralize":
that pacifies your opponent by making him lose
making him vulnerable (he almost never uses this power
but only use it when you have no other way)
Hacker Skill Level: SS
W.H (White Hacker) my oc: @teensadventuresstudio (tumblr)
PS: he is not a character that will constantly appear in mine conci he would be a background character or something like that at most he already has too many skeletons, however much he is hybrid I would not put it, I just created it to protect from possible INVADERS , and also Web tale needs to have more characters, I'm gradually creating the characters for this world)

W.h my oc: @teensadventuresstudio
#sans#undertaleau#annyokami#my oc#my art#omg#art#my comic#undertale#my story#myart#my oc art#au#webtale#doll#skeleton#myau
3 notes
·
View notes
Text
Been Awhile I've Drawn this Sans AU of Mine

Code!Sans
While using a shortcut, there was a glitch that caused him to become trapped in the code for some time, and he is now considered missing and/or dead in his AU. Code is a true nutral and isn't allied with anyone, instead watching from the sidelines while protecting the multiverse's code from hackers and viruses. Any player he catches using cheats will soon discover something Toby didn't add to the game, but doesn't like that you are messing with said "game."
Because of his slight glitch, his HP, DF, and AT can fluctuate within cirten bounds. While in battle with Code, there is always a chance that one of his attacks cause you to become temporarily paralyzed and not only cause you to lose 1 extra HP but also skip your next turn
Because he exists within the multiverse code, he is able to freely travel and exist in almost any multiverse with few limitations
RULES OF USE
DO NOT SHIP HIM
You may use him, but you MUST give credit
DO NOT claim him as your own
Any AUs made of him must give credit to the original
Fun Sketches of Code I Made

2 notes
·
View notes
Text
__digital empowerment__
Q1 a) THREE SECURITY TOOLS
1.FIREWALL
The most important security tools.
Its job is to prevent unauthorized access to or from a private network.
All messages are entering or leaving the intranet pass through the firewall. The firewall examines each message and blocks those messages that do not meet security check.
The Firewall is very useful, but it has limitations also.
A skilled hacker knew how to create data and programs that are believing like trusted firewalls.it means they can pass through without any problem
2. Antivirus Software
Antivirus software is a program which is designed to prevent, detect, and remove viruses and other malware attacks on the individual computer, networks, and IT systems.
Tt also protects our computers and networks from the variety of threats and viruses such as Trojan horses, worms, browser hijackers, spyware,ransomware.
Most antivirus program comes with an auto-update feature and enabling the system to check for new viruses and threats regularly.
3. Data Encryption
Data encryption is very important when you have top secret files that you don’t want to be read even if they are stolen
Encrypted communication protocols provide a solution to this lack of privacy.
The encrypted web access provided for customer security is used by attackers because it is difficult to monitor.
Q1 b) DIFFERENCE B/W PRIVACY AND SECURITY
PRIVACY
Privacy defines the ability to secure personally identifiable data.
Privacy can't be adept without security.
Privacy defines protecting sensitive information associated to individuals and organizations.
Privacy programs concentrate on protection personal information just like passwords, log-in credentials, etc.
SECURITY
Security define protecting against unauthorized access.
Security can be adept without privacy.
Security supports protection for some types of data and information such as the ones that are saved electronically.
The security programs defines the set of regulations and protocols to secure each confidential information.
2 notes
·
View notes
Text
What Is Phishing?
What Is Phishing?

Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
The information is then used to access important accounts and can result in identity theft and financial loss.
The first phishing lawsuit was filed in 2004 against a Californian teenager who created the imitation of the website “America Online”. With this fake website, he was able to gain sensitive information from users and access the credit card details to withdraw money from their accounts. Other than email and website phishing, there’s also ‘vishing’ (voice phishing), ‘smishing’ (SMS Phishing) and several other phishing techniques cybercriminals are constantly coming up with.
Common Features of Phishing Emails
Too Good To Be True – Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prize. Just don’t click on any suspicious emails. Remember that if it seems to good to be true, it probably is!
Sense of Urgency – A favorite tactic amongst cybercriminals is to ask you to act fast because the super deals are only for a limited time. Some of them will even tell you that you have only a few minutes to respond. When you come across these kinds of emails, it’s best to just ignore them. Sometimes, they will tell you that your account will be suspended unless you update your personal details immediately. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet. When in doubt, visit the source directly rather than clicking a link in an email.
Hyperlinks – A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance www.bankofarnerica.com – the ‘m’ is actually an ‘r’ and an ‘n’, so look carefully.
Attachments – If you see an attachment in an email you weren’t expecting or that doesn’t make sense, don’t open it! They often contain payloads like ransomware or other viruses. The only file type that is always safe to click on is a .txt file.
Unusual Sender – Whether it looks like it’s from someone you don’t know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general don’t click on it!
Here is a great KnowBe4 resource that outlines 22 social engineering red flags commonly seen in phishing emails. We recommend printing out this PDF to pass along to family, friends, and coworkers.
Click To View Larger
Prevent Phishing Attacks:
Though hackers are constantly coming up with new techniques, there are some things that you can do to protect yourself and your organization:
To protect against spam mails, spam filters can be used. Generally, the filters assess the origin of the message, the software used to send the message, and the appearance of the message to determine if it’s spam. Occasionally, spam filters may even block emails from legitimate sources, so it isn’t always 100% accurate.
The browser settings should be changed to prevent fraudulent websites from opening. Browsers keep a list of fake websites and when you try to access the website, the address is blocked or an alert message is shown. The settings of the browser should only allow reliable websites to open up.
Many websites require users to enter login information while the user image is displayed. This type of system may be open to security attacks. One way to ensure security is to change passwords on a regular basis, and never use the same password for multiple accounts. It’s also a good idea for websites to use a CAPTCHA system for added security.
Banks and financial organizations use monitoring systems to prevent phishing. Individuals can report phishing to industry groups where legal actions can be taken against these fraudulent websites. Organizations should provide security awareness training to employees to recognize the risks.
Changes in browsing habits are required to prevent phishing. If verification is required, always contact the company personally before entering any details online.
If there is a link in an email, hover over the URL first. Secure websites with a valid Secure Socket Layer (SSL) certificate begin with “https”. Eventually all sites will be required to have a valid SSL.
Generally, emails sent by a cybercriminals are masked so they appear to be sent by a business whose services are used by the recipient. A bank will not ask for personal information via email or suspend your account if you do not update your personal details within a certain period of time. Most banks and financial institutions also usually provide an account number or other personal details within the email, which ensures it’s coming from a reliable source.
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Here’s how it works:
Immediately start your test for up to 100 users (no need to talk to anyone)
Select from 20+ languages and customize the phishing test template based on your environment
Choose the landing page your users see after they click
Show users which red flags they missed, or a 404 page
Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
See how your organization compares to others in your industry
Go Phishing Now!
PS: Don’t like to click on redirected buttons? Cut & Paste this link in your browser:
2 notes
·
View notes
Text

Comodo Firewall Now Free Download
The Comodo Firewall guards against both inbound and outbound assaults on Windows-based systems. Protect your personal information with an easy-to-use interface that offers complete assault immunity. You can securely connect to the internet and other large networks with the aid of the Comodo Firewall.
With real-time traffic monitoring, you can spot bandwidth bottlenecks and respond to threats immediately. Comodo Firewall with out-of-the-box defense against hackers, Trojans, and other unknown threats, silent security technology means no pointless warnings.
Features of Comodo Firewall:
Complete protection from hackers, spyware, Trojans, and placing theft.
Defense+ Host-based intrusion prevention system.
The host Intrusion Prevention System prevents the installation of malware.
Clean PC Mode catalogs your installed programs and only permits the installation of programs that you accept.
Before installing the Malware Scan feature your computer for viruses, spyware, and trojan horses.
No Cost Download. There are never any fees or license fees.
1 note
·
View note
Text

@cometcalloway asked:
11. What is the most precious thing you own?
My Hacker plushie :3 It is one of a kind and cost me over a hundred dollars (and that was before I got an hourly paying job). I will protect it will my life always. Plus I’m sick right now so Hacker’s the only thing I’ve touched for days. I’m giving him all my viruses, hue hue.
@blackstardiopside asked:
19: Do you have any stuffed animals?
Yeah, lots! Most from when I was a kid. I have a life sized Koala from FOA Schwarz and various smaller ones that can fit in your hand. I used to have a lot more, but they got put in the basement years ago and then thrown out when it flooded in late 2021. I also have a giant Pikachu backpack somewhere I got for one of my birthdays a long time ago. Not particularly attached any of them I guess.
1 note
·
View note
Text
What Is Norton Antivirus? [+Security Features It Offer]
This blog emphasizes what is Norton antivirus and what does it do? You will learn everything about it. Symantec’s Norton Antivirus program protects the computer by restricting viruses, spyware, and worms from entering. Also, Norton antivirus consistently scans the system to protect it while you surf websites, open emails, or download a file. Plus, the antivirus software updates regularly automatically to keep your computer safe.
What is Norton antivirus?
As you know, Norton antivirus prevents your system from being hacked or malware intrusion. It may seem harmless surfing websites and watch videos. But there is always a cybersecurity threat to your system. There is various malicious software known as malware that is used to monitor your online activities and steal your personal data to use for fraud. Therefore, your system needs antivirus protection.
These are the types of malware hackers use frequently.
Viruses: Alters your system’s software in many ways.
Adware: It displays intrusive ads on your screen.
Spyware: Through which hackers can monitor your activities.
Ransomware: Locks up your system and makes it unusable until you pay the fee.
Worms: These are like software codes that can transfer from one computer to another.
The Norton antivirus is the best antivirus software of 2022, and it helps in protecting your system from threats. It works by scanning information and files to and from your system while you are surfing the web, streaming videos, emails, or anything online. This software will alert you about the malware and warn you against clicking on any website or file that may affect internet security.
In case you have accidentally downloaded the malware to your system, the software will isolate it before it causes any harm and then will alert you. Norton is considered good for its machine learning, which helps in securing your personal data to enhance technological performance and cut off cybersecurity threats.
The best thing is that Norton claims to provide a full refund if its software doesn’t work well and remove the malware from your device. Its additional features include a firewall, password manager, VPN, heavy-duty parental controls, and identity theft protection. Plus, it holds a cloud-based system for storing virus signatures.
Norton Antivirus Features
Here are the main features of Norton antivirus, which it does for you.
Scans Your System For Threats
Whenever the question – what is Norton antivirus? – arises, this feature comes into mind.
Norton antivirus consistently scans your system to protect your computer from malware. When it detects something, it immediately blocks that from entering your PC after asking for your permission. The antivirus isolates the virus or anything harmful and then alerts you. It also protects from any malware while using an instant messaging program.
Norton also restricts phishing attempts from websites that try to extract your personal information, including usernames and passwords, such as banks.
Automatic Feature
The Norton antivirus automatically runs when you turn on your computer. It blocks the browser and application threats and prevents your system from infected websites. Suppose you search for anything online and click a backlink to another site that might be infected with a virus or malware. It will alert you immediately and then will remove the virus.
Regular Updates
The Norton software is continually updated via Symantec live update function. It means that a new virus or malware released on the internet will be caught before they enter your computer.
Awards And Certifications
Norton antivirus is certified by ICSA labs, which sets the security standards for the compliance of commercial security products. If a company is awarded by ICSA certification, it shows that the product has been confirmed valuable and original. It means that it has met all the necessary standards independently.
It also says that a third party has claimed it verified.
Norton antivirus also holds the VB100 award from the virus bulletin. This award provides independent testing of the products and compares them with similar products in the industry. If any antivirus software gets this award, it shows that a third party has tested the product.
Includes Anti-malware Engine
Norton antivirus uses a huge malware directory, heuristic analysis, and machine learning to recognize malware and offer brilliant virus protection. It comes with various virus scanning options and real-time protection to restrict the malware from windows, Mac, iOS, and Android devices.
On average, Norton takes 40 minutes to scan your system and works faster than its rivals. It further offers various scanning options, including:
Quick scan: it works on the malware hotspots such as temporary files, system files, and running processes.
Smart scan: it quickly scans a WiFi network for privacy issues and simply tunes up the system.
Custom scan: It scans only specified folders and disk locations.
Norton Insight: Detects malicious websites and files that should be scanned.
Basically, these scanning options are enough to define the essence of this blog, i.e., what is Norton antivirus?
Purchase
The Norton antivirus is available on the Symantec website or in retail shops which provide antivirus software. Also, the price is according to the level of security features.
How Often Does Norton Update Its Virus Definitions?
According to Norton, it updates the virus definitions over 100 times a day. Also, several software updates are issued many times a year. Plus, all the virus definitions and software updates are automatic and unseen by the user.
Is Norton Antivirus Safe?
Yes, all the Norton antivirus detects and recognizes theft software and related products are also safe to download and use.
Source:- Norton.com/setup, www.norton.com/setup
2 notes
·
View notes