#Quantumkeydistribution
Explore tagged Tumblr posts
Text
What is QML? How Can QML Serve as a Tool to Strengthen QKD

How Can Quantum Machine Learning Improve Quantum Key Distribution?
The QML definition
QML solves issues that traditional computers cannot using machine learning and quantum computing. Quantum mechanical ideas like superposition and entanglement may speed up data processing and analysis. QML can generate novel quantum-based algorithms or improve machine learning models.
Key Ideas:
Quantum computing uses qubits, which can be 0 or 1. This allows parallel processing and possibly faster computation for particular jobs.
Machine Learning: Prediction and decision-making using data.
QML blends the two by improving machine learning algorithms with quantum principles or running them on quantum computers.
QML, an interdisciplinary field that blends classical machine learning with quantum computing, will improveQuantum key distribution (QKD), a critical aspect of secure quantum communication systems. QML may improve quantum cryptography protocols' scalability, performance, and dependability in practice, according to recent studies. Data encoding and hardware limits hinder QML integration, which is relatively young.
The most useful use of quantum cryptography is QKD, which uses quantum physics rather than mathematical complexity to revolutionise secure communications. QKD enables two parties to create and exchange a private encryption key over a quantum channel, detecting eavesdropping. This detection capacity is enabled by QKD approaches' quantum particle disruption alerts while measuring or intercepting quantum particles like photons.
A study argues QML supports QKD in several crucial ways:
Improved State Selection and Error Reduction: QML algorithms can help choose quantum states for transmission by avoiding error-prone setups and repeated measurements.
Real-Time Anomaly Detection: QML models like quantum neural networks or quantum-enhanced classifiers can detect tampering or eavesdropping efforts by detecting deviations in predicted patterns like quantum bit error rates or transmission timing.
Optimising Protocols: QML can construct adaptive QKD protocols that adjust operating parameters to channel circumstances using reinforcement learning.
QML fixes side-channel weaknesses in physical implementations and improves quantum random number generators, which generate keys, in efficiency and unpredictability.
QML has several uses beyond QKD and quantum cryptography subjects such safe multi-party computation and homomorphic encryption. It may improve neural network training, reduce dimensionality using principal component analysis, create realistic data, speed up classification operations, find detailed patterns with Boltzmann machines, and cluster high-dimensional datasets. QML can also improve natural language processing, imaging, anomaly detection, supply chain and financial portfolio optimisation, molecular modelling for drug discovery and material development, and autonomous system policy optimisation.
Industry applications include energy grid optimisation, manufacturing scheduling, retail demand forecasting, financial risk management, public health modelling, aerospace trajectory optimisation, environmental modelling, healthcare diagnosis support, cybersecurity threat identification, and manufacturing scheduling.
QML relies on quantum computers to analyse big machine learning datasets. QML processes data faster using quantum principles like superposition and entanglement and qubits' sophisticated information encoding. This could lead to faster ML model training, better model training, and the chance to evaluate quantum-based ML algorithms. Quantum computers can see more complicated data patterns and calculate faster and with less energy.
Combining QML with QKD has challenges, despite its potential:
Current quantum hardware is unstable and unable to scale many QML algorithms.
Classical data conversion to quantum forms for processing is computationally expensive and error-prone.
Complexity, synchronisation issues, and latency result from combining conventional and quantum components.
Model Optimisation: Many QML models are updated from classical approaches, requiring more tailored quantum-native designs.
Algorithm Limitations: Quantum algorithms need more development to outperform conventional ones.
Limited Data and Integrations: QML lacks standardised integration methods with existing IT infrastructures, worsening data quality issues.
Researchers recommend creating QML frameworks tailored for cryptography applications that can run on noisy intermediate-scale quantum (NISQ) devices.
QML may improve quantum network robustness and flexibility as they evolve. QML's ability to manage distributed systems, diagnose issues, and optimise resource distribution will be vital in the future. QML could bridge the gap between scalable, secure infrastructure and fundamental physical principles in the quantum future to secure digital communication.
#Quantummachinelearning#quantumcomputing#quantumbits#Quantumkeydistribution#quantumcryptography#reinforcementlearning#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Quantum Cryptography: Why It's Important For Your Cybersecurity Strategy #cryptography #quantumcomputer #quantumcryptography #quantumkeydistribution #quantumsafecryptography
#Crypto#cryptography#quantumcomputer#quantumcryptography#quantumkeydistribution#quantumsafecryptography
0 notes
Text
Quantum Cryptography: Why It's Important For Your Cybersecurity Strategy #cryptography #quantumcomputer #quantumcryptography #quantumkeydistribution #quantumsafecryptography
#Crypto#cryptography#quantumcomputer#quantumcryptography#quantumkeydistribution#quantumsafecryptography
0 notes
Text

Quantum Computing in Cybersecurity
Quantum computing is emerging as a transformative force in the field of cybersecurity. Unlike classical computers, which rely on bits, quantum computers use qubits—units that can exist in multiple states simultaneously due to the principles of superposition and entanglement. These unique capabilities allow quantum computers to perform certain calculations exponentially faster than traditional machines, posing both unprecedented opportunities and serious threats to modern cryptographic systems.
One of the most significant impacts of quantum computing lies in its potential to break widely used encryption methods. Algorithms like RSA, ECC (Elliptic Curve Cryptography), and DSA underpin much of the world’s digital security. These algorithms are based on problems that are hard for classical computers to solve, such as integer factorization and discrete logarithms. However, Shor’s algorithm, a quantum algorithm, can solve these problems efficiently. Once large-scale quantum computers become available, they could decrypt sensitive information secured under these systems, rendering current public-key cryptography obsolete.
To address this challenge, researchers are rapidly developing post-quantum cryptography (PQC)—encryption algorithms that are believed to be resistant to quantum attacks. The U.S. National Institute of Standards and Technology (NIST) is actively leading efforts to standardize such quantum-resistant algorithms. Examples include lattice-based cryptography, hash-based signatures, and code-based encryption, which are designed to withstand attacks even from quantum computers. These new methods aim to protect data not only today but also in the future, anticipating a world where quantum technology is mainstream.
On the other hand, quantum computing also presents new tools for enhancing cybersecurity. Quantum Key Distribution (QKD) is a secure communication method that uses quantum mechanics to encrypt and transmit keys in such a way that any attempt to eavesdrop would be immediately detectable. QKD enables the creation of unbreakable encryption under ideal conditions, making it a promising technology for ultra-secure communication between government, military, and financial institutions.
However, the integration of quantum computing into cybersecurity is not without challenges. The practical deployment of quantum-safe protocols requires extensive changes to existing infrastructure. Moreover, current quantum computers are still in their early stages—known as Noisy Intermediate-Scale Quantum (NISQ) devices—which limits their immediate threat potential. Nonetheless, the concept of "harvest now, decrypt later" is a real concern, where adversaries collect encrypted data today with the intention of decrypting it using quantum systems in the future.
In conclusion, quantum computing is reshaping the landscape of cybersecurity, offering both disruptive threats and novel defenses. Preparing for this future involves a dual strategy: developing and deploying quantum-resistant cryptographic standards while exploring secure quantum-enhanced technologies like QKD. Governments, organizations, and researchers must collaborate to ensure a smooth and secure transition into the quantum era, safeguarding data in a world where computing power is no longer limited by classical constraints.
#QuantumComputing #Cybersecurity #EmergingTech#QuantumThreat #ShorsAlgorithm #EncryptionBreakthrough#PostQuantumCryptography #QuantumSafe #NISTStandards#QuantumKeyDistribution #QKD #UnbreakableEncryption#QuantumRisks #NISQ #DataSecurity#QuantumFuture #SecureTransition #QuantumCybersecurity The Scientist Global Awards
Website link : thescientists.net NominationLink :https://thescientists.net/award-nomination/?ecategory=Awards&rcategory=Awardee Contact Us : [email protected]
___________________________________ Social Media:
Twitter : https://x.com/ScientistS59906 Pinterest : https://in.pinterest.com/scientists2025/_profile/ Tumblr : https://www.tumblr.com/blog/thescientistglobalawards FaceBook : https://www.facebook.com/profile.php?id=6157466213823
0 notes
Text
Quantum Cryptography Chips: From $1.2B in 2024 to $12.5B by 2034—What’s Driving the Growth?
Quantum Cryptography Chips Market is poised for exceptional growth, with a projected expansion from $1.2 billion in 2024 to $12.5 billion by 2034, reflecting a CAGR of approximately 26.0%. This market focuses on the development of semiconductor chips that leverage the principles of quantum mechanics to provide unmatched data security. By enabling unbreakable encryption, these chips ensure data integrity and confidentiality, making them essential for industries such as finance, defense, and telecommunications, which increasingly require advanced security solutions in today’s digital landscape.
To Request Sample Report: https://www.globalinsightservices.com/request-sample/?id=GIS11061 &utm_source=SnehaPatil&utm_medium=Article
The growth of the Quantum Cryptography Chips Market is largely driven by the rising threat of cyberattacks and the ongoing advancements in quantum computing. The telecom and IT sectors lead the charge, with the increasing need for secure communication channels. Financial services follow closely, as institutions prioritize the protection of sensitive data. North America is the market leader, fueled by substantial investments in cybersecurity infrastructure and favorable government policies. Europe follows closely behind, with stringent data protection regulations and growing adoption of quantum technologies. The United States, in particular, stands out as a key player due to its technological expertise and strategic collaborations. In Europe, Germany is a driving force, benefiting from its strong industrial base and innovation-driven economy.
In 2023, the Quantum Cryptography Chips Market reached an estimated volume of 1.2 million units, with projections suggesting an increase to 2.5 million units by 2033. The telecommunications sector commands the largest market share at 45%, followed by financial services (30%) and government applications (25%). Leading players in the market include ID Quantique, Toshiba Corporation, and MagiQ Technologies, each playing a pivotal role in driving technological advancements and maintaining competitive advantages.
The future looks bright for this market, with continued growth fueled by innovations in quantum technologies. However, challenges such as high initial costs and technical complexities remain.
#QuantumCryptography #DataSecurity #QuantumComputing #Cybersecurity #Encryption #QuantumChips #SecureCommunication #TechInnovation #QuantumKeyDistribution #FinancialSecurity #TelecomSecurity #SecureData #CyberDefense #QuantumEntanglement #QuantumSuperposition #DataProtection #NetworkSecurity #AdvancedEncryption #Telecommunications #GovernmentSecurity #AIInSecurity #TechPartnerships #CloudSecurity #PrivacyProtection #QuantumTechnology #SmartEncryption #R&DInSecurity
0 notes
Text
🔒 Quantum Cryptography Chips: Exploding to $12.5B by 2034
Quantum Cryptography Chips Market is revolutionizing data security by leveraging the principles of quantum mechanics to provide unbreakable encryption. These chips are crucial in ensuring data integrity and confidentiality, making them highly sought after in industries such as finance, defense, and telecommunications. As digital threats evolve, the need for advanced security solutions is more critical than ever, driving the demand for quantum cryptography chips.
To Request Sample Report: https://www.globalinsightservices.com/request-sample/?id=GIS11061 &utm_source=SnehaPatil&utm_medium=Article
The market is experiencing significant growth, fueled by escalating cybersecurity concerns and rapid advancements in quantum computing. The telecom and IT sectors are leading the charge, with an urgent need for secure communication channels. Financial services are also a major driver, as institutions prioritize protecting sensitive data. Geographically, North America leads the market, bolstered by substantial investments in cybersecurity infrastructure and favorable government policies. Europe follows closely, with stringent data protection regulations and increased adoption of quantum technologies accelerating market growth. Within North America, the United States is at the forefront, benefiting from its technological leadership and strategic collaborations between tech giants and research institutions. Germany stands as a key player in Europe, thanks to its strong industrial base and innovation-driven approach.
In 2023, the Quantum Cryptography Chips Market saw an estimated volume of 1.2 million units, with forecasts indicating growth to 2.5 million units by 2033. The telecommunications sector commands the market with a 45% share, followed by the financial services sector at 30%. Government applications, particularly in defense, contribute to the remaining 25%. Leading players in the market, such as ID Quantique, Toshiba Corporation, and MagiQ Technologies, are driving innovation to maintain their competitive edge.
With a projected 15% annual growth rate, the future of quantum cryptography chips is promising, marked by ongoing R&D investments aimed at enhancing chip performance and reducing costs.
#QuantumCryptography #DataSecurity #Cybersecurity #QuantumComputing #Encryption #TelecommunicationsSecurity #SecureCommunication #QuantumChips #FinancialSecurity #TechInnovation #DataProtection #QuantumEncryption #QuantumKeyDistribution #QuantumTechnology #BankingSecurity #QuantumRandomNumberGenerator #NetworkSecurity #CloudSecurity #DefenseTech #AIinSecurity #DataIntegrity #EncryptionTechnology #QuantumSuperposition #QuantumTunneling #IDQuantique #ToshibaCorporation #MagiQTechnologies
0 notes
Text
Preparing for the Post-Quantum Era

An Introduction to Quantum-Resistant Cryptography Post-quantum cryptography is a field of study focused on developing and implementing cryptographic algorithms that are resistant to attacks by quantum computers. With the advancement of quantum computing technology, it has become increasingly likely that traditional cryptographic methods, which are based on mathematical problems that are difficult for classical computers to solve but easy for quantum computers to solve, will become vulnerable to attacks. As a result, there is a pressing need for new cryptographic algorithms that can withstand attacks from quantum computers and ensure the security of sensitive information. In this context, post-quantum cryptography aims to design and implement cryptographic methods that are resistant to quantum attacks and can provide the necessary security for a post-quantum era. To protect against this possibility, researchers are developing new cryptographic techniques that are resistant to attack by quantum computers. Some examples of post-quantum cryptographic methods include lattice-based cryptography, multivariate cryptography, code-based cryptography, and hash-based cryptography. It is important to note that these methods are still in the development stage and have not yet been widely adopted.

Lattice-based cryptography Lattice-based cryptography is a type of cryptography that is believed to be resistant to attacks by quantum computers. It is based on the mathematical properties of lattices, which are structures made up of points arranged in a grid-like pattern. Lattice-based cryptography is considered to be a promising option for the post-quantum era, as it is thought to be resistant to attacks by quantum algorithms that are able to break other forms of cryptography, such as RSA and ECC (Elliptic Curve Cryptography). There are several different types of lattice-based cryptography, including NTRU (short for N-th degree Truncated Polynomial Ring Units), RLWE (short for Ring Learning with Errors), and LWE (short for Learning with Errors). These algorithms all work by generating a secret key based on the properties of a lattice, and then using this key to encrypt and decrypt messages. One of the main advantages of lattice-based cryptography is that it is relatively easy to implement and requires relatively low computational resources. This makes it well-suited for use in resource-constrained environments, such as on mobile devices or in the Internet of Things (IoT). Lattice-based cryptography is considered to be a promising option for the post-quantum era, as it is believed to be resistant to attacks by quantum computers and can be implemented with relatively low computational resources. However, it is still an emerging field and more research is needed to fully understand its potential and limitations.
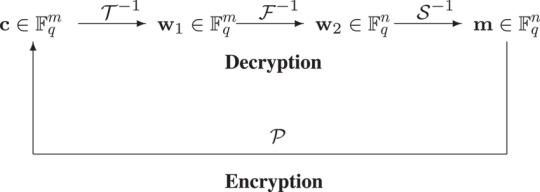
Multivariate cryptography Multivariate cryptography refers to cryptographic techniques that use multiple variables as the basis for generating keys and encrypting/decrypting messages. These techniques are believed to be resistant to attacks by quantum computers, as they rely on mathematical problems that are believed to be hard to solve with quantum algorithms. Some examples of multivariate cryptography include McEliece and Niederreiter cryptosystems, which use the concept of algebraic error-correcting codes to generate keys and encode/decode messages. These systems are believed to be secure against attacks by quantum computers, as the mathematical problems they rely on (such as the decoding of error-correcting codes) are thought to be difficult for quantum algorithms to solve. However, it is important to note that the security of these and other multivariate cryptographic techniques is still being actively researched, and it is possible that they may be vulnerable to future attacks or breakthroughs in quantum computing.
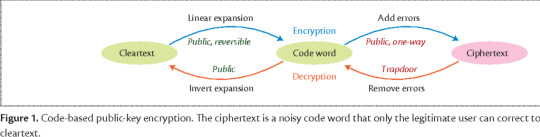
Code-based cryptography There are several code-based cryptography algorithms that are believed to be resistant to attacks from quantum computers. These include McEliece, Niederreiter, and Goppa codes. These algorithms rely on the difficulty of decoding a message encoded using error-correcting codes, which makes them resistant to attacks even from powerful quantum computers. However, it is important to note that the security of code-based cryptography is not yet fully understood, and further research is needed to confirm their resistance to post-quantum attacks.

Hash-based cryptography It is difficult to say definitively which specific hash-based cryptographic algorithms will resist the post-quantum era, as the field is still in the early stages of research and development. However, it is generally believed that hash-based cryptography, which relies on the difficulty of finding a collision (i.e., two different inputs that produce the same hash output) in a given hash function, has the potential to be quantum-resistant. This is because it is thought that finding collisions in hash functions using quantum computers may still be computationally infeasible, even in the post-quantum era. Some examples of hash-based cryptographic algorithms that have been proposed as potential candidates for quantum resistance include the Merkle-Damgård construction, the Sponge construction, and the HMAC construction. It is important to note, however, that the security of these and other hash-based cryptographic algorithms has not yet been rigorously tested against quantum attacks, and further research is needed to determine their true quantum resistance. Conclusion In conclusion, the potential for quantum computers to break current cryptographic methods has led to the need for post-quantum cryptography. Several options exist, including lattice-based, multivariate, code-based, and hash-based algorithms, which are resistant to attacks from quantum computers. It is important for organizations and individuals to start considering the transition to post-quantum cryptographic methods in order to secure their data and communications in the future. Read the full article
#algorithms#code-based#cryptography#hash-based#lattice-based#multivariate#post-quantum#quantum#quantumkeydistribution#security
0 notes
Photo

I was at IndoQuant Conference at IIT Hyderabad check out: https://lnkd.in/egQua6s #quantumcomputing #cryptography #security #quantumkeydistribution
0 notes
Text
#QuantumNetworks: the European Commission and the European Space Agency are going to create a highly secure pan-European #QuantumCommunication infrastructure. It would comprise terrestrial components and space-based components https://t.co/fr9uQWM2mf #QuantumKeyDistribution https://t.co/Bv17JkVReg
#QuantumNetworks: the European Commission and the European Space Agency are going to create a highly secure pan-European #QuantumCommunication infrastructure. It would comprise terrestrial components and space-based components https://t.co/fr9uQWM2mf #QuantumKeyDistribution pic.twitter.com/Bv17JkVReg
— The Royal Vox Post (@RoyalVoxPost) April 9, 2019
via Twitter https://twitter.com/RoyalVoxPost April 09, 2019 at 03:44PM
0 notes
Text
Europe’s Bold Strategy To Lead Quantum Research Technology

Research Quantum
Europe Aims to Lead the Quantum Race with New Report
Shaping a European Strategy in Quantum Technology proposes a bold EU lead in quantum technology development. The approach, developed by expert working groups from all 27 EU member states and coordinated by the European Commission, combines quantum research, infrastructure, and commercialisation. Ultimate goals include technical sovereignty, economic resiliency, minimising dependent on external systems, and placing Europe as a quantum technology leader. The report proposes creating a continent-wide ecosystem of computing facilities, secure communication networks, and industrial applications to make Europe the world's first “Quantum Valley.”
Research and Talent:
This working group seeks to strengthen Europe's research base and talent pipeline. A new cross-border research coordination platform should align EU and state goals. University, lab, startup, and significant industry collaborations should be prioritised. The goal is to create Quantum Competence Clusters, localised but connected centres that combine industry, infrastructure, and knowledge to reduce fragmentation and improve resource access.
The research recommends internships, student exchanges, workforce retraining, graduate programs, specialist master's degrees, and industry-specific upskilling. It also recommends early public outreach, ethical frameworks, and assessing social and economic impacts, including quantum computing cybersecurity issues. Tax concessions, industrial fellowships, and streamlined visa procedures to compete with well-funded firms prioritise talent retention.
Infrastructure:
This team connects research to marketable products. A Quantum Infrastructure Point of Contact group to coordinate Member State computing, communication, sensing, and chip manufacturing activities is one of the primary recommendations. The plan suggests extending the EuroHPC-QCS initiative to create a network of quantum computing and simulation capabilities integrated with high-performance computing centres across Europe to support Quantum Computing Excellence Centres and expand access for SMEs.
The foundation supports an operational Quantum Communication Infrastructure (EuroQCI) that connects national networks utilising quantum key distribution for safe EU communications. To translate sensing and metrology advances from lab to industry, the study prioritises pilot initiatives and industry relationships. The EU Chips Act establishes quantum device pilot lines to ensure strategic autonomy and reduce dependency on non-European components in the fourth pillar, chip manufacturing.
Industrialisation:
This working group aims to accelerate commercialisation. This is centred on a planned Fault-Tolerance Quantum Computing (FTQC) Competitive Procurement Challenge that would award public contracts to scalable quantum processor manufacturers. The group urges European governments to spearhead quantum solution implementation. Improved patent creation, licensing, and monetisation help might boost the EU's intellectual property portfolio.
Concerted standardisation includes financial incentives for Member States and EU-wide engagement in international standards bodies. The analysis advises obtaining money from venture capital, pension funds, sovereign wealth funds, and EU institutions and giving investors with specific educational programs to address underfunding.
The report's main proposal is to combine national and European efforts in these three areas. Goals include reducing dependence on foreign quantum technologies and nurturing European quantum champions who compete globally. The policy emphasises technical autonomy and economic security geopolitically, reflecting the growing need to close the quantum gap with China and the US.
Despite its extent, budgetary constraints, skill shortages, undeveloped venture capital ecosystems, and a lack of national plans or cooperation in some Member States hinder plan execution. The study addresses infrastructure, commercialisation, and research as interrelated parts, providing a logical roadmap. Political will, financial alignment, and the ability to move faster than competitors will determine its success. The proposal might transform Europe into a quantum innovation powerhouse with strategic resilience and long-term economic rewards.
#QuantumResearch#quantumtechnology#Cryptographic#quantumcomputing#quantumkeydistribution#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Quantum Key Distribution and the Future of Encryption
By Konstantinos KaragiannisQuantum computing will bring tumultuous change to the world of information security in the coming decade. As multi-qubit systems use quantum algorithms to slice through even 4096-bit PK encryption in seconds, new Quantum Encryption will be required to ensure data security. from Pocket https://www.youtube.com/watch?v=RrdTAURD1rI via IFTTT
0 notes
Text
Micius’ Security Flaw Could Hack First Quantum Satellite

Micius
A study finds a security issue in the first quantum satellite.
A Singaporean researcher found that Micius, China's 2016 quantum communication satellite, may be hackable despite its guaranteed safe information delivery. The satellite uses Quantum Key Distribution (QKD) to share encryption keys with ground stations using the BB84 protocol to improve communication security. This recent study suggests that the BB84 technique may be vulnerable despite its theoretical impenetrability.
Quantum communication encodes data in photons using quantum mechanics-based encryption. The secret key exchange mechanism QKD makes eavesdropping difficult and possibly impossible. It is generally known that “side-channel attacks” that exploit experimental implementation vulnerabilities may harm real-world QKD devices.
Micius employ laser pulses with multiple identical photons for long-distance communication. This increases reliability but compromises security. The system uses numerous laser devices to prevent photon-number-splitting (PNS) attacks. Reports say Micius used eight laser diodes, four of which transmitted “decoy” states and four the real “signal” states. Decoy states protect encryption keys by making attackers unable to distinguish between real and fake signals. According to the security assumption, an eavesdropper cannot distinguish signal and decoy photons before data processing.
However, Singapore-based quantum physicist Alexander Miller detected tiny temporal delays between the satellite's laser pulses in one experiment. Miller examined data from Micius-ground station transmission to find time delays between the quantum transmitter's lasers. Taking advantage of temporal delays or mismatches could reveal the genuine signal.
Miller's non-peer-reviewed work says signal times differ. Experimental data from quantum communication sessions between Micius and a ground station in Zvenigorod, Russia, suggests a 300-picosecond delay between the signal and decoy lasers. Pulses last 200 picoseconds, therefore this delay is identical. Over multiple sessions and months, the time difference persisted, indicating a long-term design issue.
Desynchronisation creates a “telltale fingerprint” in photon arrival timing. In 98.7% of cases, an attacker could determine the genuine signal using high-precision measurement devices, Miller found. Such precision suggests the system is not as safe as anticipated.
These findings violate BB84's decoy state security premise that signal and decoy pulses are identical in all degrees of freedom except intensity. Miller's research reveals that quantum key distribution via Micius is not safe, supporting past theoretical work on PNS attacks that use separate decoy states.
Rather than a theoretical protocol failure, the report blames technological limits and defects in the satellite's communication system hardware. Using many lasers to create photon states makes implementation easier, but each laser may act differently over time, releasing accidental information. Satellite transmitter design appears to cause systematic vulnerability.
The study uses a previously proposed theoretical model of the PNS attack that uses distinguish ability to calculate that, given the observed degree of mismatch, the secure key rate would effectively decrease to zero, indicating that the encryption might be cracked.
This new analysis contradicts earlier reports that Micius' lasers were synchronised in 10 picoseconds. This raises problems about synchronisation checking and degradation. Micius could not remotely adjust laser time in orbit, making it difficult or impossible to fix a design flaw after launch.
If confirmed by future research, these findings underscore a bigger difficulty in quantum communication: the gap between theoretical objectives and real-world device limits, especially in challenging environments like space.
To prevent future issues, the paper recommends stronger laser synchronisation, rigorous pre-flight hardware testing, and the flexibility to adjust timing parameters after launch. Entanglement-based QKD systems and single-laser systems may be considered, notwithstanding their limitations.
The paper used experimental data from Russian company QSpace Technologies, released on a pre-print website without peer review. The scientific method demands peer review. The study focused on temporal side channels (timing differences) rather than spectral or geographical distinguishability or environmental influences across time, which could also be dangerous.
#Micius#QuantumKeyDistribution#QuantumComputing#photonnumbersplitting#quantummechanics#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
1 note
·
View note
Text
Heriot-Watt Optical Ground Station invests £2.5M In QKD

Watt-Heriot Optical Ground Station
The first UK quantum satellite research centre is launched by Heriot-Watt University.
The first UK optical ground station for quantum key distribution (QKD) was announced by Heriot-Watt University to allow exceptionally secure satellite-to-ground communication using single photons.
The Heriot-Watt Optical Ground Station (HOGS) at Edinburgh's Research Park cost £2.5 million (about $3.3 million). As part of the Quantum Communications Hub, HOGS is the UK's first major infrastructure investment in free-space quantum key distribution research.
Quantum key distribution uses quantum mechanics to secure keys, unlike conventional communication methods that use complex mathematics. This prevents future quantum computers from deciphering it.
Dr. Ross Donaldson, Heriot-Watt's Institute of Photonics and Quantum Sciences project head, stated HOGS allows space-ground QKD research. He says this method creates encryption keys that cannot be intercepted or attacked secretly.
UK quantum plan is expected to include HOGS. The Heriot-Watt-led Integrated Quantum Networks Hub will use it as a key testbed. Future quantum internet components that merge fibre and free-space communications can be certified and space-ground interfaces tested at the facility.
Professor Tim Spiller, Director of the Quantum Communications Hub, called the HOGS experiments a “key next step” in establishing satellite capabilities, emphasising their importance to global data security. Professor Gerald Buller, Director of the Integrated Quantum Networks Hub, said HOGS's direct fiber-optic links to the university's quantum labs enable previously impossible research and help the UK lead quantum networking.
The facility has a 70-centimeter tracking telescope and a 40-centimeter backup telescope for imaging. High-fidelity quantum communications with satellites will soon be possible with modern adaptive optics and single-photon detectors. Due to its high latitude, Heriot-Watt can follow polar orbiting satellites and debris, improving detection and observation windows.
HOGS creates a versatile “living laboratory” by directly integrating with Heriot-Watt’s dark fibre network. This integration speeds up innovative technology testing and deployment for scientists and industrial users by mimicking several networks.
In addition to cybersecurity studies, HOGS will detect and characterise space debris, a significant concern as satellite networks develop. High-speed classical optical communications for 6G and other terrestrial network technologies will also be studied.
UK National Quantum Technologies Programme of Engineering and Physical Sciences Research Council supported the facility. This initiative involves Heriot-Watt, Bristol, Strathclyde, and York universities. The Science and Technology Facilities Council's RAL Space supports engineering.
Deputy Principal of Business and Enterprise Professor Gillian Murray called the facility a “economic catalyst” for Scotland's growing space and quantum industries. Commercial research and development in optics, sensors, and secure communications systems can be made easier by employing its shared infrastructure.Because of its position within the Research Park, which includes space-focused companies like Celestia UK, the facility promotes co-location to speed up technology transfer between academics and business. This connection helps data-vulnerable industries including healthcare, finance, and infrastructure.
Educational outreach and workforce development are HOGS priorities. The centre will conduct school visits, demonstrate satellite tracking and quantum physics, and provide undergraduate and PhD students real experience to boost the number of quantum and space engineers in the country. We invite firms and researchers to discuss cooperation.
HOGS has improved quantum communications and space research in the UK, putting Heriot-Watt University and the nation at the forefront of safe, cutting-edge global networks.
For more details visit govindhtech.com
#HeriotWattOpticalGroundStation#HeriotWatt#quantumkeydistribution#HOGS#QuantumCommunicationsHub#HeriotWattUniversity#technology#TechNews#technologynews#news#govindhtech
0 notes