#Read Text Messages Without Installing Software
Explore tagged Tumblr posts
Text
Retrograde Mercury in the Houses
First of all, Mercury Rx in your birth chart isn't a glitch, it's a feature.
✨ Mercury Rx in Fire Signs (Aries, Leo, Sag) – The Bluetooth connection that works only when they’re standing on one leg, facing north, at precisely 3:33 AM. Loud, passionate, but often misunderstood because they speak before the signal stabilizes.
✨ Mercury Rx in Earth Signs (Taurus, Virgo, Cap) – The software update that takes forever to install, but when it does, it’s flawless. They think before they speak, but people still misinterpret them because they communicate in a slow, calculated way.
✨ Mercury Rx in Air Signs (Gemini, Libra, Aqua) – The Wi-Fi that should be fast but keeps glitching. Their thoughts are rapid, but their words come out jumbled. They rewrite messages a hundred times before sending, yet somehow, they still get left on read.
✨ Mercury Rx in Water Signs (Cancer, Scorpio, Pisces) – The deep web browser that sees things no one else does. Their words are drenched in emotion, layered with hidden meanings. They communicate telepathically (because honestly, explaining themselves in words is exhausting).
Mercury Rx in 1st house - These natives words tumble out of their mouth like a badly loaded webpage. Your brain is fast, but your mouth is buffering and you mispronounce words a lot. This placement natives watches movies with subtitles on even for their own language. Rewatches things just to "get it". Have their own slang. When they type, their autocorrect betrays them. Loves music that feels like a personal soundtrack and listen to songs on repeat. A misunderstood protagonist really.
Mercury Rx in 2nd house - These natives are the slow but steady thinker. Like they pause a lot before speaking, people think they're deep, but they're just trying to remember the word for "fork". Loves slow-burn dramas and hates overly complex sci-fi plots. Listens to the same five artists forever. Loves classic rock, R&B, or jazz—something timeless. Hates overproduced music.
Mercury Rx in 3rd house - Talks fast, stumbles over words, or randomly loses their train of thought. In some cases, they sound sarcastic even if they're serious and don't mean to. Loves multitasking like watches TV while texting, scrolling and half-listening to a podcast. This placement learns vocabulary and phrases through memes, twitter slang, or duolingo threats. Their music taste is genre-fluid. Listens to rap, hyperpop, EDM, and podcasts at the same time. Will pause a song midway to send a text.
Mercury Rx in 4th house - Have an "old soul' way of speaking. Probably sound exactly like their parents/grandparents without even realizing it and some people around them could have told them about it. Writes handwritten letters and doodle in their free time or while in class. Rewatches childhood favorites for comfort. Prefers old movies and refuses to watch a bad remake. Makes a lot of spelling mistakes in their own language. Probably still keep their old notebook and drawings. Obsessed with childhood favs. Loves soft acoustic, old-school pop, or the one song their parents always played.
Mercury Rx in 5th house - The way these natives describe basic things involves cinematic screenplay. Probably wrote a overly detailed fanfic or an unpublished novel. Loves over-the-top dramas, reality TV, or anything with messy plot twists. Probably memorized a whole anime/movie opening before knowing what it meant. If these natives wanna learn a language, it's mostly through songs and movies. Also their inner monologue could be dramatic and sounds like Shakespeare. In music, listens to anything that makes the natives feel like the main character.
Mercury Rx in 6th house - Damn. Don't ask these natives "How are you?". They will give you a full detailed report. Talks and writes in bullet points. These natives watches informative or detailed YouTube videos like restoration videos, primitive survival, science documentaries "for relaxation". Lo-fi beats, instrumental music, or podcasts instead of songs. Prefers music that helps them focus.
Mercury Rx in 7th house - These natives adapts their way of speaking based on who they’re talking to. Also could convince anyone they have the same interests. Into arts and crafts. Loves romcoms and dialogue-heavy movies. Also psychoanalyze people a bit too much. Loves duets, soft indie, or romantic sad songs. Will make a playlist for every relationship they’ve ever had.
Mercury Rx in 8th house - These natives are cryptic texters and speakers. They speak in riddles. This placement makes the native to hide their true opinions and make them say things they don't really want to due to fear of criticism or being labeled a misogynist. Sometimes convey their true opinions in the most cryptic way possible. Watches crime documentaries and loves dark, psychological themes. Listens to dark, moody, or hauntingly beautiful. Think Lana Del Rey, The Weeknd, retro songs or anything with eerie instrumentals.
Mercury Rx in 9th house - These natives are really good at giving TED talks and for writing long-winded essays, even in casual texts. Uses "however", "anyways" in DMs. Loves to watch travel vlogs, historical dramas, other language movies and likes philosophical anime/movies. Loves music with deep lyrics and listens to songs in different languages.
Mercury Rx in 10th house - These natives have a sense of professionalism even when they order food. A level of sophistication. These people uses proper punctuation in texts and draft emails for hours before sending. Loves business dramas. Watches TED talks and political speeches. These people probably has a certification related to their career. Listens to motivational rap or music that makes them feel productive.
Mercury Rx in 11th house - Their speech is 50% memes and 50% conspiracy theories. Writes in lower case letters. Uses 'lmao' and 'lol' to soften every message. Watches niche web series, obscure YouTube channels, and indie films. Their vocabulary comes from internet slang and discord convos. Not into mainstream pop.
Mercury Rx in 12th house - These people say something vague, a week later, it would turn out to be weirdly accurate. Their journal entries would look like prophecies, their vivid dreams and psychic visions. Loves watching horror, surreal, experimental films. Loves songs that makes them forget their own life and dream about themselves in that song.
✨🔮DM me for a complete astrology reading & check out my pinned post for pricing! ✨🔮
#astrology#astrology readings#birth chart#astro observations#astro notes#zodiac signs#spirituality#spiritual awakening#spiritual journey#vedic astrology#western astrology#astro posts#astro blog#astro tumblr#astro community#astrology notes#astrology content#natal chart#natal placements#natal aspects#natal astrology#astrology blog#astrology tumblr#mercury retrograde#mercury rx#mercury sign
201 notes
·
View notes
Text
Sunflower: chapter 15

Chapter warnings: Our flashback is a bit.. Uhum. Steamy? AN: Do we get our conversation? How childish will Mia be? Can she act like a goddamn adult? LETS FIND OUT!
Masterlist

It had been four days. Four long, slow days. Four days where Mia could try to think without the overwhelming presence of a stranger in her space. Four days where Mia found herself longing for that presence.
Tom had been gone for four days and it had been twenty four hours since she had heard from Tom. Radio silence filled the air, though she tried to drown it out with music, television and conversations. How could silence gnaw at her heart in the very same way as the insane devotion that radiated off him did?
He was busy. He was working. He was… not here. And that bothered her. A lot. It shouldn’t, but it did. And that killed her. Not physically, but god did she kind of wish it did.
She wasn’t clingy typically but she couldn’t help it. This was his fault. He demanded that she invest. How could she not when he insisted on finding any crack in her heart to worm his way in and try to find purchase to take root.
He had made her think he was different. Hell, he had all but said he was different.
This was supposed to be different.
But here she was, four days alone.
Sally was asleep and the apartment was large, empty and frigidly silent. She had worked a early shift and tomorrow had a late one. Exhaustion was deep in her bones but she needed to stay up way too late tonight.
What was it like to have someone to be at home with, to not be alone in the silence of the night when she had no choice but play chicken with the morning light?
A ping from her phone caught her attention. Glancing at it, she saw it was just another news push notification. It wasn’t a feature she wanted but it was installed automatically with the latest software update. There was enough in her life to be anxious about without getting 24 hour updates every day of the year on what god awful thing was happening in another state or country. It had been a few weeks but she hadn’t been able to figure out how to turn it off.
It was just a matter of time until she figured it out though. She swore it. Every time it had gone off it had given her false hope that he finally sent something, she swore she’d figure it out.
This was ridiculous.
The reason for the radio silence was obvious. She had been right and he realized it. It was that simple. No need to pine, question and dance like a goddamn schoolgirl.
With time away, Tom realized that everything Mia had said Saturday morning was right. In a few days or a few weeks she would get a notice from some lawyer initiating the annulment. Would he cancel the card he left for her to use?
It’s not like it was hard to replace, really. It was just a credit card, he obviously could live without the physical card for a while. How hard would it really be on him if he changed his mind?
“Some promise that was.” Mia tossed the card absently onto the end table next to her.
Ping.
Ignore it. There was no point in checking. It wasn’t him. it was never him.
Okay, she was being a bit dramatic. Really dramatic, maybe. She didn’t know. It was dumb. She was being dumb. It was too soon to decide he ghosted her.
“Fuck,” She slumped back on the couch. “I guess I’ll be able to say I got ghosted by an actor.”
Ping.
She couldn’t help it, she grabbed her phone knowing exactly what she’d find. It would be a second news story of little to no importance to her day to day life. An auto accident near by that slowed traffic patterns or a missing person on the other side of the country. A storm in Brazil or a heatwave in India. It would be a protest in China. It would be nothing.
It was a text message from contact Tom.
“Can I call?” The message read. Another followed, “It’s late, I know.”
She sent a single k back and waited for the other shoe to drop. There was nearly no wait for the phone to come to life in her hand. She hadn’t added a picture to his contact, it was just Tom H lighting up her screen.
Nothing more.
She took a deep breath and answered, “Hello,”
“Is everything alright?” Tom’s tone was difficult to pinpoint.
“Yeah-” She cleared her throat and sat up. “I’m fine. It’s fine. Everything’s fine. Just lay it on me.”
“Lay what on you?” Tom sounded confused and that confused her. “What are you talking about?”
“You haven’t said anything, all day.” Her eyes burned and her throat felt tight. She needed air. The apartment was suffocating as she stood.
“It has been a minute, I suppose.” He was picking his words carefully.
“Can you just- why are you calling?” The glass door slid closed behind her. If Tom was going to do whatever she wanted to not have to worry about Sally waking up for it.
“I wanted to talk to you?” Tom sounded unsure, on the other side of the country he had found himself off balance.
“About what?” Mia felt the anger sweeping in to push away her sadness. It wasn’t healthy but it was a bad habit that she often found solace in. Anger was safe. For her at least, not those in her way.
“You’re upset with me?”
“Stop asking questions.” Mia snapped. “What do you want?”
“I wanted to make sure you got the couch alright.” Tom’s voice was starting to pull tight. “Why did you think I wanted to call?”
“To tell me I was right.” Mia’s voice cracked. This was it, their first fight was going to happen and it hadn’t even been two weeks. “To tell me…”
Tom’s tone changed from the defensive and softened considerably. He may not be able to read her mind but he knew she was hurting. “I’m not calling to ask for an annulment. Why on earth did you think that?”
“You never texted back. You stopped talking and I just- It’s been over a day and it’s been slowing down. It was just-” she clamped down on the words as her voice threatened to give away how close she was to tears, that safe anger winking out in her shame.
“You missed me?” his voice was so soft. “I got absorbed in work. I’m sorry.”
“No, no.” Mia forced a chuckle. It was all a misunderstanding. She was acting like a love sick schoolgirl. She was a grown ass woman married to a grown ass man. She shouldn’t be crying and thinking their marriage is over just because he didn’t text her for a day. “I swear- I’m not clingy.”
“It’s alright.” Somewhere on the other side of the universe, he sat down heavily on the too big bed. “Things are new and delicate. I’m just as guilty for not being aware.” Silence ticked on. While they had texted while he was away (until it stopped) they hadn’t actually talked on the phone.
“I saw part of your interview.” Mia wasn’t sure why she said it.
“Which one?” Tom asked, his voice warming to life. “What did you think?”
“The one where you talked about me.”
“Did I- Was what I said alright?” Tom wasn’t totally sure which one she was talking about but he didn’t want to complicate things more.
“I don’t like lying.” Mia said. “I know why you need to but I don’t like it.”
“It’s not really lying, its just implying different and reinforcing our privacy.” That still sounded like lying to Mia but she let it go. She was pretty sure he more than implied they knew eachother for longer than a night in the segment she watched anyway.
He could lie so easily and didn’t even agree with her on the definition of lying. The fact that he played pretend well enough to do it for a living showed he was good at telling lies too.
Shaking her head, she pushed the thoughts away. Tom had never given her a reason to think he would lie to her. He has been earnest and honest from the moment they woke up Saturday.
“Hiding parts of my private life is just a fact of my life. If I want to hold anything back for myself without the public picking it apart, it needs to be protected from them.”
“I know.” Mia sighed as she leaned against the railing. The fight felt like it had been narrowly avoided.
“It’s people in my life I tell the truth but to protect the people in my life I don’t tell the world the whole truth.”
“I know, I know-”
“It’ll take time to get used to.”
Silence filled the air again. This time it didn’t have that same icy chill to it. She had missed him and that scared her.
“Tom?” Her heart beat too hard in her chest. Did he miss her? Even just a little?
He hummed on the other side of the universe and she wondered what he was doing. They had a time difference of three hours. It was late for her but even later for him. Was he preparing to go to bed? Was he just getting in from a night on the town?
“What is it?” He asked after she failed to say anything.
She wanted to tell him she missed him. She wanted to ask when he was going to come back. She hated it.
“Don’t be a stranger.” God, that was so lame. Out of everything she could have said, that’s what she came up with?
“I have been, haven’t I?” It was Mia’s turn to be silent. She wasn’t sure what to say. It was weird to be married to a man she didn’t know.
“I mean, what’s what we kind of still are, aren’t we?” It was the best she could come up with to say.
“I’m sorry. I’d gotten busy and fallen away from texting you. I- Luke tacked on a few appearances. The trip got extended. Usually it’s nothing, I didn’t think anything of it. Until I did. But by then- I didn’t know what to say.”
The ability to apologize was not one that Mia had seen much in the men that had spent time in her life. It reassured her that he could do something as simple as say ‘sorry’.
“I should be back by Friday.” Tom said, sounding sure. Just as sure as he had sounded before he left. “I promise.”
“Don’t.” Mia’s voice came harder than she intended. “Don’t promise if you don’t have control over keeping it.”
“Mia-”
“I need to get to bed. Work tomorrow.”
What moments of warmth they had shared during the call had cooled. Would it always be like this? She hoped not. Could she ever feel safe enough to stop icing him out as soon as things warmed up?
“I’ll call again tomorrow?” Tom fell back on the hotel bed. This call had not gone how he intended but who’s fault was that? He should have just told her when the plan changed.
“If you want.” She didn’t know what else to say as she stepped back into the apartment, locking the sliding door behind her.
“I do want.” Tom hesitated, “It’s good to hear your voice. To talk to you. I missed you.”
She didn’t know what to say. Couldn’t say anything. Her heart pounded in her chest and her hands trembled. “Goodnight, Tom.” Was what she managed to squeak out before disconnecting the call.
Tom pressed her against the door. His hand was large and firm against her waist, holding her right where he wanted. Fumbling, with his wallet trapped in his pocket, he struggled with the other hand. His pants were tight around his hips and his current state of mind didn’t help matters.
Her nails scratched at the hair at the back of his neck as she clung to him. It felt like she was floating, swimming through a sea of desire and alcohol. She needed him. She wanted him. “Hurry.”
“Got it.” The wallet slipped out. It was a struggle to flip it open with one hand, then find the hotel keycard. In the process of getting the card out, he dropped the leather wallet to the floor.
His breath was hot in her ear. Lips worked, leaving harsh kisses along her neck. As he worked the card into the slot, he moved his hand from her waist to her breast, stopping for a firm squeeze that had a soft moan slip from her lips.
“I need you.” She whimpered as the door beeped, denying entry.
“Who do you need?” Tom asked as he flipped the card around, trying different sides hoping one would work.
“My husband.” That set fire to him.
The door beeped the correct tune this time, granting them entry. Tom hooked the door handle with his hand, slapping it down clumsily after yanking the card from the door. The door swung open, no longer providing a solid surface to support their weight.
Tom held her up with a arm flung around her waist as they stumbled in. He kicked blindly, relying on feel alone to help him ensure he kicked his wallet somewhere into the room.
“My wife.” Tom breathed as he kicked the door shut behind them. Alone at last.
Taglist:
@winterisakiller, @alexakeyloveloki, @jennyggggrrr @dangertoozmanykids101, @tilltheendwilliwrite @tinchentitri @wizardcherryblossom @buttercupcookies-blog @violethaze @kats72 @soulpiercing @evedia
#Tom hiddleston x ofc#tom hiddleston x oc#Tom hiddleston x original female character#Tom hiddleston x original character#tom hiddleston fanfic#Tom hiddleston fanfiction#tom hiddleston rpf
25 notes
·
View notes
Text
#OB WhatsApp APK v56 Download Latest Version 2024 Free | OB WhatsApp
Download OBWhatsApp latest version for Android. It is expected to be available soon for iOS as well. OBWhatsApp is a modified version of the official WhatsApp, offering different ways to communicate with friends. You will not face any defects while using it.
Of course, there are differences between OBWhatsApp and the regular WhatsApp APK, but all the differences are positive and in favor of OBWhatsApp. This application was developed in response to the requirements of users who are looking for freedom and privacy beyond what WhatsApp offers. As a result, OBWhatsApp gained a huge following when it was officially released. It quickly became as popular as the original WhatsApp app, surpassing 50 million downloads since its initial launch. There are many versions of OBWhatsApp, each with its own unique features and benefits. You'll have access to over 200 new features with this software, many of which were previously unavailable but are now within everyone's reach. It is worth noting that OBWhatsApp is not available on the Google Play Store, so we will provide you with a direct download link.
How to log in to OBWhatsApp:
There are no differences in the method and steps you are used to. After downloading and installing OBWhatsApp, you can launch OBWhatsApp. The registration window will appear, and the country code will be automatically selected. Simply enter your number in the designated field in OBWhatsApp.
OBWhatsApp will ask for permission to access the received text messages to verify the authenticity of the number. There is no problem if you deny permission to OBWhatsApp. However, in this case, you will need to copy and paste the code manually. After following these steps, you can add a personal photo and access the app's features.
Backup in new OBWhatsApp:
This is an important step for many people.. Through it, you will be able to restore your conversations that you had on the official application.
It is worth noting that in order to be able to use and run OBWhatsApp after downloading it, you must delete the original WhatsApp because they cannot be run simultaneously. To take a backup, go to the settings of the official application, specifically on the chats page. Perform this procedure, which will only take a few moments. After that you can uninstall the program and install the new OBWhatsApp.You will be asked to restore your backup. Agree to this option or go to Settings and restore it from there.
Why we use OBWhatsApp:
There are many reasons why people download OBWhatsApp. Since he gave them everything they needed, they now had complete freedom to communicate with others. And hide what you want to hide. OBWhatsApp is a new world of communication that does not impose any annoying conditions on its subscribers.
Many people were forced to use it after they lost hope that their demands would be met. Which is something developers always ignore, unlike OBWhatsApp. All options are available for your choice.
Features of the latest update OBWhatsApp:
In terms of updates, generally the OBWhatsApp version gets updated and includes all the new features.
Now this version of OBWhatsApp includes all new emojis. The shape of the posters and logos was also changed, and a watch sticker was added. The German language is available on WhatsApp, in addition to other languages, including Arabic, English, and others. You can update to the latest version from within without having to use websites.
Privacy in OBWhatsApp:
Undoubtedly, this is one of the main reasons why millions are downloading OBWhatsApp. Now, you can control different privacy options, whether to show or hide them.
The first option is to hide your online status, specifically hide the word “Online” when OBWhatsApp is active, so that no one can know when you are active. The second option is to hide the reading mark, so the other party will not see the double check marks when you read their messages. This way, you won't feel obligated to respond to messages you don't want to respond to. Additionally, you can hide the indication that you received a message and that it was delivered to you. This option has been satisfied and admired by many users. These two options will give you complete freedom to choose whether or not to respond to other people's conversations and messages. The privacy features don't stop there. You can also control the "Typing..." indicator that appears when you start typing on the keyboard or when you add emojis. This gives you the opportunity to delete what you have written and review the words and make sure they are accurate before sending. Moreover, OBWhatsApp allows you to hide that you are recording a voice message, which usually appears as “Recording...”. Therefore, you will not feel obligated to send recorded audio clips. None of your contacts will know if you've viewed their status or stories, whether it's a video or a photo. In the official app, this is visible to the status holder, but it was not well received by most users. Finally, you can activate the option to prevent deletion of messages within conversations, and avoid accidental deletion when copying messages or similar actions. You can also hide the "Writing..." indicator in group chats and discussions.
Stop the Internet from OBWhatsApp:
The new feature introduced recently makes OBWhatsApp unique among other social media apps. It has added many solutions for many types and categories of people, especially for those who receive messages on WhatsApp continuously and continuously.
Examples include corporate employees and meeting owners. This option will allow them to disable the Internet for the program only. Do they connect via Wi-Fi or mobile data. However, all other applications continue to work and are connected to the Internet. And also the ability to browse websites. This will not affect other applications or games that require the Internet during operation. This option appears at the top of the chat list. But you can hide it from this page and activate it in settings only to avoid accidental activation.
Scheduled messages within OBWhatsApp:
You can now compose or write a new message and specify the time at which it will be sent. You can schedule these messages for any day or month of the year. It will be sent automatically when the time you specify arrives.
This is considered an effective solution for those who do not have a strong memory to remember many events. For example, among other things, you can use this feature to wish your friends happy birthdays, public holidays, etc. OBWhatsApp will not need internet to send messages on time. This will do even if your phone is turned off. You can select any number of people to receive scheduled messages. With the option to cancel this message again at any time. The app allows you to select the hour, minute, and second you want to set and schedule an unlimited number of messages.
Status history inside OBWhatsApp:
condition: There have been significant changes and improvements. It allowed people to express their thoughts and desires in writing. It is worth noting that regular WhatsApp only allows a limited number of characters, which is not suitable for everyone and does not provide them with freedom of expression. This led them to shorten many words when adding their own case. Now, with OBWhatsApp, the character limit has increased significantly to 225 characters. This allows you to type whatever you want without worrying about character restrictions and maximums. story: Users also struggled with minimal video stories. It was not possible to add a video longer than half a minute. Now, with OBWhatsApp, this period has increased. The maximum length of videos is 7 minutes. Naturally, there is a big difference between the previous and current limit, which allows you to share long video clips from your gallery or any folder. Alternatively, you can record a new video internally using WhatsApp's color camera. And of course, you can add photos to your story. This media will remain in its original quality and resolution.
Send photos and videos to OBWhatsApp:
Pictures sent from OBWhatsApp:
With OBWhatsApp, the number of images that can be sent at once has become very large. Instead of selecting a small number of them to send at a time. Which took a lot of time. The sending process is also fast and smooth on OBWhatsApp. Without any transmission failure message, etc., the images will also arrive with the same quality and resolution.
Video sent from OBWhatsApp:
As for the videos, they had a large share of additions and benefits. Videos up to 50MB can now be shared instead of 15MB. This previously prompted the user to split the video into several parts in order to be able to send it. You won't have to take those annoying steps anymore. It is now possible to send clips in the highest HD quality and amazing transfer speeds.
Additional benefits within OBWhatsApp:
If you want to access the first part of one of your conversations that you had with anyone else. You won't have to spend a lot of time doing it the usual way, i.e. swiping up to read old messages.
In some cases, in large conversations with nearly a thousand messages, this may take an hour or more. But in OBWhatsApp there is a command in the chat settings that will take you to the first message with the click of a button. You can also stop receiving voice or video calls from others. Set a password for each conversation so that it can only be accessed after you type the lock code correctly. In addition to the ability to delete emojis that were recently present in the user's list. And turn off message and call notifications for any of your ongoing conversations. Also set the background for each chat from the wonderful collection of wallpapers that OBWhatsApp offers you, or import wallpapers from the gallery, as well as delete chat contents and block unwanted people.
OBWhatsApp settings:
Chat screen inside OBWhatsApp:
When talking about the top bar, its color and color gradient can be changed. In addition to the colors of the icons at the top. Also change the color of the contact name, make the font bold, and change the colors of the following items:
Hide the last time you were online. You can also remove the option to open your profile picture after downloading OBWhatsApp. Hide the contact icons and the person you are talking to, and change the design of the top bar.
Conversations:
Cancel the feature of highlighting text and messages when long pressing on the message and choose a different shape for chat bubbles in OBWhatsApp. Same for link colors, message size, and time size. If you want to be notified about last seen, you can set this option in this menu. Do not allow sensors to mute messages, hide camera icons, or record audio. The same applies to the status and size of icons. OBWhatsApp has a great option to view long messages in their entirety instead of using the Read More command. With dozens of other options.
Call screen:
You can change the background and colors of contact icons for outgoing, incoming, missed calls and call count. By controlling the size of the date and time of each call in the new OBWhatsApp, the same applies to the name and number.
The most important new notifications within OBWhatsApp:
It provides you with many and varied notifications. When one of your contacts goes online, you will receive a notification, provided they have enabled the option to share their online status, and their number is saved in your contacts. This feature allows you to stay updated on who is communicating with you and interact with them easily.
Widget settings:
OBWhatsApp offers various notifications, including the ability to customize the color, size, and number of messages, as well as the contact name, date, and message colors.
Themes in OBWhatsApp:
OBWhatsApp offers a large number of themes that can be applied, all of which are available for free. This allows you to get rid of the boring, formal look that never changes. In addition, new themes are added periodically, including themes related to various sports, football clubs, famous players, romantic designs, sad themes, landscapes, celebrities, cartoon drawings, and many others. OBWhatsApp provides a dedicated store for downloading these themes, and changing the theme will take no more than 10 seconds.
OBWhatsApp icons:
You have complete freedom to customize the appearance of icons in all their forms, starting with the external appearance of the WhatsApp Plus icon. You can also modify the appearance of the reading tray, notification icons, and more. These options will add uniqueness to the application and allow you to achieve the desired look. Other options in this menu include staying online always, displaying name and date while copying messages, disabling voice and video calls, blocking unwanted contacts, and turning off the message counter. Moreover, you can display your personal photos in a square frame instead of a circular one with the new OBWhatsApp.
The most important features of OBWhatsApp:
OBWhatsApp offers a wide variety of unlimited themes and fonts. You can set a password for each conversation to enhance privacy. You can also change the default video player to any other video player installed on your phone. OBWhatsApp supports many languages including Arabic, English, Spanish, Portuguese, and Italian. You have the option to customize the colors and sizes of all icons according to your preferences. It also allows you to update to the latest version of OBWhatsApp from within the app. With OBWhatsApp, you can easily access the first message in the conversation with just one click. The maximum video size has been increased significantly. You can send a large number of photos at once, and media files are sent in their original quality. Your contacts will not know whether you have viewed their status or not. Additionally, you can add longer videos to your story. If desired, you can disable Internet access for OBWhatsApp. Moreover, you can schedule messages to be sent automatically at a specific time.
OB WhatsApp Download
OB WhatsApp Download
OB WhatsApp Download
OB WhatsApp Download
OB WhatsApp Download
OB WhatsApp Download
OB WhatsApp Download
2 notes
·
View notes
Text
How to Schedule or Manage Content on an Outdoor LED Display?
Ever felt like your LED display placed outdoors isn’t making the impact it should? Many others run into the same problem. People usually invest in LED screens but after a while they struggle to keep content timely, and engaging.

Without a plan, your display quickly becomes ignored. That’s where this blog comes in offering clear steps to make your display engaging and impactful.
We’ll show you how to manage and schedule content the right way so your outdoor led display works well for your brand. Whether you're new or just need better results, stay with us till the end.
Why Content Planning Matters for LED Displays
Content planning helps you to share the right message with the right people at the right time. Without a good plan, your screen may repeat the same messages too often or miss key opportunities to engage.
A strong content strategy adds variety, keeps messages relevant, and ensures each display makes an impact. Whether you're promoting special offers, announcing events, or sharing daily updates, regular planning keeps your display fresh and effective.
That’s why many businesses turn to a professional led screen installation company for ongoing support with content planning. They also help ensure your content execution truly connects with viewers and delivers results.
Tools and Tips to Manage Content Efficiently
Smart scheduling is more than just setting a timer. It’s about understanding your audience, location, and business goals. You can maximize the performance of your outdoor LED display with the help of these ways.
Use Scheduling Software
The majority of LED displays include built-in software that simplifies content scheduling. These systems let you upload videos, images, or text and select exact times for display. You can make content in advance and automate its release.
This is perfect for seasonal marketing, product debuts, and promotions. A reliable led screen installation company helps set up this system and trains your team to use it with confidence.
Keep It Short and Clear
People passing by are unlikely to pause and read lengthy text blocks. You need to keep your messages brief, bold, and easy to read in under five seconds. You can use big fonts, contrasting colors, and simple language. This enhances visibility at night as well as during the day.
You must stick to one idea per slide and keep it simple. Clean visuals and short messages increase your chances of grabbing attention and leaving an impression.
Match Content with Time of Day
People behave differently at different times. A message that works in the morning might not make sense at night. Schedule content based on time. For example, promote lunch deals before noon or happy hour in the evening.
You can use morning hours for inspirational quotes or headlines, and display event reminders in the afternoon. By this you can tailor your content like this to add value and relevance.
Update Content Regularly
If your display will show the same message for too long it can cause people to ignore it. Update your content every week to keep your display looking fresh and engaging. You can also feature new offers, greetings, or product launches. Even small updates like changing colors or headlines make a big difference.
Your outdoor led display should always feel current. Many businesses set a content review day each week to stay organised. Regular updates also show your brand is active and paying attention.
Track What Works
Analytics help you understand which content gets the most views, clicks, or responses. Many LED software platforms offer reports that show how your content is performing. Look for patterns and trends.
If one message does well, create more like it. If another performs poorly, change or replace it. Tracking data helps you spend time and effort where it matters. Over time, this results in stronger engagement and improved outcomes.
To Sum Up
Getting the most out of your LED display is about delivering timely, relevant messages that truly connect with your audience. With the right tools, regular updates, and an understanding of viewer behaviour, your outdoor LED display can become a powerful communication tool.
If all of this feels a bit too technical or time-consuming, don’t worry. This is where a trusted LED screen installation company can help you. They eliminate the element of guesswork and assist you in achieving better outcomes without the inconvenience.
Need a hand getting started? Reach out to The Pixel Man as they're known for high-quality installations of LED walls, signs, and billboards. Their expert team will make sure your display doesn’t just look amazing, it works smart too.
0 notes
Text
3/3
Core Java: A Beginner’s Guide to Java Programming
Java has stood the test of time as one of the most widely used programming languages. From building desktop applications to powering large-scale enterprise systems, its versatility has made it indispensable. If you're just stepping into the world of programming, learning Core Java is an excellent place to start.
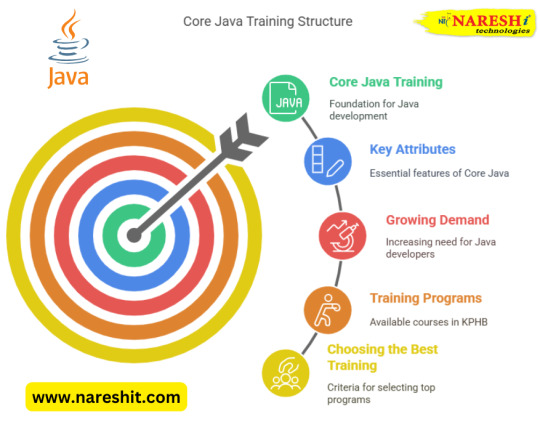
What is Core Java?
Core Java refers to the fundamental aspects of Java programming, forming the backbone of the language. It encompasses essential concepts such as object-oriented programming (OOP), memory management, exception handling, and multi-threading. Unlike Advanced Java, which includes frameworks like Spring and Hibernate, Core Java focuses on the basic building blocks needed to write efficient and scalable applications.
Why Learn Core Java?
Before diving into web or enterprise development, mastering Core Java equips you with:
A solid foundation in OOP principles – Essential for writing clean, reusable, and modular code.
Platform independence – Java’s “Write Once, Run Anywhere” philosophy allows applications to run on multiple platforms without modification.
Memory management – Java handles memory allocation and garbage collection efficiently.
Robust exception handling – Prevents unexpected crashes and improves software reliability.
Multi-threading capabilities – Enables efficient execution of concurrent tasks.
Setting Up Java
To start coding in Java, follow these simple steps:
Install Java Development Kit (JDK) – Download the latest version from Oracle’s official website.
Set up an Integrated Development Environment (IDE) – Popular choices include:
IntelliJ IDEA – A feature-rich, user-friendly IDE.
Eclipse – A powerful, open-source Java IDE.
NetBeans – Great for beginners due to its built-in tools.
Verify the installation by running: shCopyEditjava -version This command confirms that Java is installed and accessible.
Understanding the Basics of Java
1. Hello World Program
The classic first step in any language is printing "Hello, World!" to the console:
java
CopyEdit
public class HelloWorld { public static void main(String[] args) { System.out.println("Hello, World!"); } }
public class HelloWorld – Defines a class named HelloWorld.
public static void main(String[] args) – The entry point of any Java program.
System.out.println() – Prints text to the console.
2. Variables and Data Types
Java has various data types:
java
CopyEdit
int age = 25; double price = 99.99; char letter = 'A'; boolean isJavaFun = true; String message = "Java is awesome!";
Each type serves a distinct purpose, from storing numbers to handling text.
3. Control Flow Statements
Decisions and loops are integral to programming:
java
CopyEdit
if (age > 18) { System.out.println("You are an adult."); } else { System.out.println("You are a minor."); }
Loops enable repeated execution:
java
CopyEdit
for (int i = 0; i < 5; i++) { System.out.println("Iteration: " + i); }
4. Object-Oriented Programming (OOP)
Java follows OOP principles, including:
Encapsulation – Data hiding through private fields and public methods.
Inheritance – Reusing code through parent-child class relationships.
Polymorphism – Methods behaving differently based on input.
Abstraction – Hiding implementation details and exposing only necessary functionality.
Example:
java
CopyEdit
class Animal { void makeSound() { System.out.println("Animal makes a sound"); } } class Dog extends Animal { void makeSound() { System.out.println("Dog barks"); } } public class Test { public static void main(String[] args) { Animal myDog = new Dog(); myDog.makeSound(); // Output: Dog barks } }
Next Steps in Java Learning
Once you've grasped Core Java, you can explore:
Collections Framework – Handling groups of objects efficiently.
Multi-threading – Running tasks in parallel for improved performance.
File Handling – Reading and writing files.
JDBC – Connecting Java applications to databases.
Final Thoughts
Java continues to be a powerhouse in software development, with Core Java serving as the gateway to mastering the language. Whether you're aiming to build Android apps, enterprise solutions, or cloud-based systems, a strong grasp of Core Java will set you on the path to success.
Feedback Time!
What would you like to improve in this article? A) Add more beginner-friendly examples B) Include more advanced topics C) Simplify explanations D) Provide additional resources for learning Java E) It’s perfect as is!
Comment Below
#Java#CoreJava#JavaProgramming#CodingForBeginners#LearnToCode#Programming#Tech#SoftwareDevelopment#OOP#CodeNewbie#TechEducation#JavaDeveloper#ProgrammingBasics#CodingTips#DeveloperLife
0 notes
Text
Font Generator: Create Stunning Text Styles Instantly

Typography plays a crucial role in digital design, branding, and communication. Whether you're creating social media posts, designing a website, or enhancing your marketing materials, fonts help convey emotions, set the tone, and improve readability. However, finding the perfect font style can be time-consuming. That’s where the best font generator tools come in.
With a font generator, you can instantly transform plain text into stylish, eye-catching typography. Whether you need bold, cursive, decorative, or futuristic fonts, these tools allow you to customize text effortlessly. In this blog, we’ll explore why fonts matter, how font generators work, and which are the best font generator tools available today.
The Importance of Unique Fonts in Design
Custom fonts add personality to your content and make it stand out. Whether it’s a logo, Instagram bio, website heading, or gaming profile, the right font can make all the difference.
Why Fonts Matter:
Brand Identity – Fonts reflect your brand’s personality and style. A handwritten font may convey creativity, while a bold sans-serif font exudes professionalism.
Increased Engagement – Social media posts and website headlines with unique typography capture more attention.
Improved Readability – The right font makes your content easy to read, enhancing user experience.
Versatility Across Platforms – Custom fonts can be used for logos, digital ads, social media profiles, gaming nicknames, and more.
With best font generator tools, you can experiment with different styles and find the one that best represents your vision.
How a Font Generator Works
A font generator is an online tool or software that allows users to convert regular text into customized, artistic fonts. These generators offer various styles, from bold and italic to gothic, calligraphy, and futuristic fonts.
Step-by-Step Guide to Using a Font Generator:
Enter Your Text – Type your desired text into the generator.
Select a Font Style – Choose from a range of available font styles (e.g., cursive, bold, handwritten, fancy).
Customize the Text – Some tools allow customization, including adjusting font size, effects, and alignment.
Copy & Paste – Once you're satisfied with the design, simply copy the text and paste it where needed (social media, websites, logos).
These easy-to-use tools eliminate the hassle of downloading and installing fonts, allowing instant customization.
Features of the Best Font Generator Tools
Not all font generators offer the same functionality. When choosing a tool, look for these essential features:
Wide Font Library – Offers multiple font styles, including fancy, bold, cursive, and decorative fonts.
Easy Copy & Paste Functionality – Allows you to quickly use fonts on social media, gaming platforms, and websites.
Customization Options – Adjust text size, spacing, and effects to personalize your design.
Unicode Support – Ensures generated fonts work across multiple platforms without issues.
Web & Mobile Compatibility – Works seamlessly on desktop and mobile devices.
With these features, the best font generator tools can make text customization effortless and fun.
Best Uses of a Font Generator
A font generator isn’t just for designers—it’s a versatile tool for various applications.
Where You Can Use Font Generators:
Social Media Profiles & Posts – Enhance Instagram bios, Twitter posts, and Facebook captions with stylish text.
Graphic Design & Branding – Create unique typography for logos, business cards, and promotional content.
Web Development & UI Design – Improve website aesthetics with decorative headings and banners.
Gaming & Streaming – Customize usernames and nicknames for Twitch, YouTube, and Discord.
Personal Messaging – Add creativity to chats and emails with unique font styles.
By leveraging the best font generator tools, you can elevate your text and make an impact across different platforms.
How to Choose the Best Font Generator Tools
With so many font generators available, selecting the right one can be overwhelming. Here are some key factors to consider:
Ease of Use – Look for a user-friendly interface with simple input and output functions.
Variety of Font Styles – The more font options available, the better the tool.
Compatibility – Ensure the tool works on web browsers, mobile devices, and various platforms.
Customization Features – Some generators allow you to adjust text effects, colors, and sizes.
No Registration Required – Instant access without the need for an account is a plus.
By evaluating these factors, you can find a font generator that suits your needs.
Best Font Generator Tools to Try
Here are some of the best font generator tools that offer excellent functionality:
1. Cool Fancy Text Generator
Offers stylish and fancy fonts for social media and gaming.
Easy copy-paste functionality for quick use.
2. FontSpace
A large collection of free fonts for personal and commercial use.
Includes script, bold, and decorative fonts.
3. LingoJam
Simple interface with various font transformation options.
Ideal for creating aesthetic Instagram bios and gaming usernames.
4. FlamingText
Specializes in logo and text styling for branding purposes.
Provides customization options like shadows and 3D effects.
5. Font Meme
Generates text in famous font styles (e.g., movie titles, gaming logos).
Great for pop culture-inspired designs.
These best font generator tools cater to different needs, from social media aesthetics to professional branding.
Tips for Using Font Generators Effectively
To maximize the impact of font generators, follow these best practices:
Avoid Overuse – Too many decorative fonts can reduce readability.
Keep It Consistent – Stick to a theme by using 2-3 font styles.
Ensure Platform Compatibility – Some fonts may not display correctly on certain devices.
Test Different Styles – Experiment with fonts to find the best match for your content.
By following these tips, you can make the most of best font generator tools without sacrificing design quality.
Conclusion
A font generator is an essential tool for anyone looking to enhance their text styles instantly. Whether you’re branding a business, creating engaging social media posts, or designing a website, unique fonts help make your content stand out.
Key Takeaways:
✔ Fonts impact branding, engagement, and readability. ✔ Font generators offer quick and easy customization without installation. ✔ Choosing the best font generator tools ensures high-quality typography. ✔ Experimenting with different styles enhances creativity.
Ready to level up your typography game? Try one of the best font generator tools today and transform your text into something stunning!
1 note
·
View note
Text
How to Add Cash App Card to Apple Wallet?
Today, the Cash App is used by over 55 million people, most of whom are US citizens who use it daily. No wonder since the Cash App offers so many handy perks. It helps you handle your taxes, spend and save on your best-loved brands, or pay anyone easily. As a Cash App user, you can get exclusive discounts, buy and sell Bitcoin, and even delve into the stock market world. Do you want to know how to add Cash App to Apple Pay and benefit from the faster, simpler way of banking? Then, keep reading.
How to Adding Cash App to Your Apple Pay Wallet?
Wondering how to add Cash App to Wallet without a card? Follow these instructions on your iPhone or any other Apple device:
Launch the Cash App on your Apple phone.
On the main screen, tap the Cash Card tab, which looks like a little credit card.
Click on your Cash Card image.
Select "Add Card to Apple Pay" right below.
The "Add Card to Apple Pay" screen will pop up. Click on your device's name, and the adding process will start.
Agree to the terms and conditions. Otherwise, you won’t be able to add a Cash App Card to Apple Pay.
Once the process is completed, you will receive a notification with a blue checkmark that the Cash Card has been added to your Wallet.
Next, you can set a Cash Card as a Default Card in your Wallet or choose "Not Now."
Another way to add Cash App to Apple Wallet is from your Apple Wallet. However, before getting started and figuring out how to add Cash App to Wallet, make sure you have the latest version of the Cash App.
Open Apple Wallet on your iPhone or other Apple device by tapping on the Wallet app icon.
Tap on the "Add Card" option.
You can either scan your Cash App Card or enter the card details manually.
Next, you must verify your card for security purposes. You can do this either by text message or phone call to the number associated with your Cash App account.
When the card is added, you will see it in your Apple Wallet list.
If you are an Android user, you can add a Cash App Card to your Google Wallet. To do this, you have to have a Google Pay Account:
Open your Cash App and click a card icon.
Click "Add Card to Google Pay."
You will see a message: "Use this card with Google Pay."
Click "Continue."
Enter your information and click "Continue."
Agree to the Issuer Terms.
Here is another way to add your Cash App Card to Google Pay:
Open Google Pay and select "Manage Accounts."
Select the "Payment Methods" option and tap "Add card."
Scan your card details or type them in.
Click "Save" button.
Your Cash App account is now enlisted in your payment methods.
How You Can Top Up Apple Pay with Cash?
Since Apple Pay is an e-wallet using banking cards for touchless payments, you can't add cash directly to it. You either need to add a card to Apple Pay or use funds from Apple Cash, which acts similarly to a prepaid debit card. So, firstly, you need to top up your Apple Cash balance.
First, install the Apple Cash on your device.
Go to the Wallet app.
Click on your Apple Cash card.
Tap "More" and then "Add money."
Type the sum of money and tap "Add." The minimum is $10.
Verify the transaction via passcode, Face ID, Touch ID, or Optic ID.-
What are the Reasons for Failing to Add Cash App Card to Apple Pay
When adding Cash App to your Apple Pay, you can come across a couple of issues. Here are some of them.
Card Activation Issues
Remember that your Cash App Card requires proper activation. To avoid any possible issues.
Unsupported Device
Verify if your gadget supports Apple Pay. In general, Apple Pay requires at least iPhone 6, iPad Air 2, Mac with Touch ID, and Apple Watch Series 1. If you are not sure whether your device is compatible with Apple Pay.
Outdated iOS version
To ensure your iPhone has been updated to the latest version, go to Settings > General > Software Update. Select Automatic Updates and click on Download iOS Updates. Then select Install iOS Updates. However, some updates can only be installed manually.
Outdated Applications
Ensure that the Cash App and Apple Wallet applications are up-to-date on your smartphone. Check if the new updates are available in your App Store. If you see the Cash App or Wallet app on the list, tap on the "Update" button next to the icons.
Incorrect card information
When entering your card details, such as the card number, expiration date, and CVV, double-check you have done it correctly. Otherwise, you may fail to add a Cash App card to your Apple Pay.
Apple Pay is not available in your location
Check to make sure Apple Pay is available in your location. The countries and regions that support Apple Pay.
Restrictions by Bank or Issuer
Your bank or card issuer may not allow you to add the card to Apple Pay. A bank might have security concerns or internal policies dictating which services they support. Also, the bank's systems simply might not be compatible with Apple Pay.
How Much Time You Need to Transfer Money from Cash App to Apple Pay
There is no direct way of sending money from Cash App to Apple Pay. You can only do it by transferring a balance to a bank account first or just adding a Cash App Card to Apple Pay, and this will affect the time needed.
If you add the Cash App to Apple Wallet, it’ll be faster. It usually takes just a few minutes. This streamlined process allows you to use your Cash App Card with Apple Pay for contactless payments and online transactions in no time.
The second option is to transfer the Cash App balance to a bank account before Apple Pay, which is done in two steps.
Transfer from Cash App to a Bank Account:
Open the "Money" tab in your Cash App.
Press "Cash Out" and enter the amount you want to transfer.
Choose the deposit speed (Instant or Standard).
Confirm the transfer.
Transfer from Bank Account to Apple Pay:
Open the Wallet app.
Tap the Apple Cash card, then click on the "More" button.
Select "Add Money" and select the bank account.
Confirm the amount of money.
Complete the transfer process.
Transferring your Cash App amount to the relevant banking account can take up to 3 working days. Moving money to an Apple Pay account will take approximately 1 to 2 business days.
0 notes
Text
Do you think a partner is cheating on you? Do you think your voice is dressing up and going out more often than she used to? Would you like to have a confirmation if that is happening, or is it just in your head? Cocospy comes in the picture when you have such doubt in your mind. We know this feels like an awful dream, thinking if your partner is cheating on you or not. Well, Cocospy can help read someone's text messages without software installation. Cocospy for Your Rescue! Cocospy comes up with numerous ways for you to confirm if your partner is cheating when you’re not. Moreover, cocospy can help you catch your partner, red-handed. Cocospy can do a lot of other essential things, aside from tracking someone’s location. The app has thousands of different customers who are using it every day. Cocospy is recognized by Toms Guides, CNET, PCMag, TechRadar, Toms Guide, Digital examples, and that is just a hint of something more substantial. Keep this in mind that Cocospy permits you to read messages on iPhones similarly as android devices. You will not have to download or install any software, because Cocospy is an online app that works thoroughly fine on the web browser by picking up details to the target iPhone’s iCloud account or target Gmail account for an Android. Cocospy is among the best text interceptors you can invest in, and it allows you to read texts without presenting the target phone you are spying on. You can easily read the conversations without having to jailbreak the target iOS device or root the target android. You can take a look at Neatspy to find out more about cocospy. How to Read Someone's Text Messages without Any Software Through Cocospy? Here’s how you can use cocospy. All you have to do is follow the following steps, which will cause you no trouble, and we guarantee you that! You have to go to the cocospy website and sign up for a cocospy account. The site will require your Gmail account and ask you to set a password. Please note that this Gmail ID will be your username. After signing up, you will be asked to buy a premium membership. There are two types of memberships available for you to buy. We suggest you buy a family plan if you intend to spy on more than one person, and we recommend you to buy a premium version if you only want to spy on a single person. The next procedure is as easy as learning alphabets. All you have to do is tap a few clicks here and there, and you are good to go. After the setup wizard is set, you will see a start button. If you click it, you will be taken to the dashboard. The dashboard is where you will see all the features that are offered by cocospy. You can explore your options and see what you like. Cocospy makes the process of spying easy for you. Let’s explain with an example, for suppose you want to spy on text messages on the target phone. You will look for the “text message” option in the dashboard of the cocospy. Here you will be able to see all the latest text messages such as sent messages, received messages, draft messages, and deleted messages. Is Cocospy for You? If you have this question in mind, it is completely fine with us, and we will be obliged to answer you. Firstly, let’s see what cocospy offers you. Only then will we be able to tell if it is for you or not. Cocospy is a website based application that does not require you to download or install any app on your target phone. This only means that all you need is a web browser for Cocospy to work for you. Secondly, cocospy does not require you to jailbreak your target iPhone or root your android. This is a unique feature of cocospy. In many reviews, it is said that not many spying apps offer this feature. Let’s be very clear the apps that require a jailbreak or a root on the android phone only make it more prone to getting viruses and malware. Which is not very safe for a phone. One of the best features of cocospy is that it works in complete secrecy.
There will never be the day on which the person you are spying on will find out that you are spying on him if you trust cocospy for your spying needs. This is because you can access Cocospy on the web browser of your personal computer or laptop, and you do not need the target phone. We have heard it about 1000 times that once you buy an app subscription for a premium version, there is no customer service provided by that application. This is where cocospy draws the line. Once you buy our memberships, we will be there for your help and support 24 hours a day. You can ask any question you have in your mind, and we will answer it. We only work to make your life easier and better, especially after you become one of our loyal friends. If the features, as mentioned earlier, are what you’re looking for in your spying app, we are what you need. You answered yourself, Yes! Cocospy is for you. The Bottom Line We hope that with the assistance of this article, you are at long last able to understand How to Read Someone’s Text Messages Without Software. We believe the article, as mentioned above, clears every one of your inquiries. All you have to do is follow the mentioned steps. You will realize that Cocospy is the best thing that happened to you when you chose it out of all the other spying apps. You can use it without having a fear of getting caught. With the help of Cocospy, you can read someone’s text messages without software and also get the miscreant without getting exposed first. You can surely read your kid’s messages and find out what they are up to. Cocospy lets you lead things in your way.
0 notes
Text
Discover the Best Apple Features for Seniors in these Simple technology books for seniors by Jane Smith

Technology can be hard to understand, especially for older people who don't use computers, smartphones, or apps as kids. The iPhone and iPad are two strong Apple products that can help seniors stay in touch, have fun, and stay organized. But it might seem hard at first to learn how to use them. Seniors Can Use Apple Products: A Simple Guide by Jane Smith can help. These types of Simple technology books for seniors by Jane Smith shows you how to use Apple products in a simple, step-by-step way.
This guide has everything you need to know to set up your phone, send texts, use FaceTime, and find useful apps. Every step is written in easy-to-understand language so that anyone can follow along. Seniors can learn at their own pace and feel more comfortable with technology. Older people can use Apple products without stress if they read this book. These types of Simple technology books for seniors are a useful tool that helps everyone make technology fun and easy.
Staying Connected with Calls and Messages
One great thing about Apple products is that they let you stay in touch with family and friends. These types of Simple technology books for seniors show older people how to use their phones to call, text, and video call on FaceTime. The steps are clear and easy to follow, so no one will get lost. The book shows you how to add friends, block calls you don't want, and use voice commands to talk on the phone without using your hands. The seniors will also learn how to text and send pictures to their friends and family. For people who like bigger text, these types of Simple technology books for seniors show how to change the settings for messages so that they are easier to read. Seniors can talk to each other easily and with confidence if they follow these easy steps.
Looking at Apps and Features That Are Useful
Apple phones and tablets have lots of useful apps that can make your life easy. These types of Simple technology books for seniors show seniors how to use useful apps like Calendar to plan their days, Notes to keep track of things, and Maps to get around. It shows you how to get new apps from the App Store and put them in order on your home screen. The voice helper Siri will also be taught to the seniors. They don't have to touch the screen to ask Siri to make a call, set an alarm, or find information. The Camera app is also talked about in the book. This app makes it easy to take pictures and share them. There are sections in the guide that teach how to use Apple Music, Podcasts, and YouTube for fun.
How to fix problems and stay safe
Technology can be annoying at times, but this book makes it easy for adults to fix common issues. It tells you how to restart a device, fix Wi-Fi problems, and install new software. The guide also shows you how to close apps you're not using and free up space on your phone. These types of Simple technology books for seniors give you ways to keep your Apple gadgets safe because security is important. Seniors will learn how to make strong passwords, spot fake emails, and stay safe online. It also shows you how to use iCloud to back up your files and pictures so you never lose them. Seniors can feel safe using their gadgets after reading these troubleshooting and safety tips. When they know they can handle small problems on their own, they will feel more in charge.
Conclusion
Anyone over the age of 50 who wants to use technology without stress should read A Simple Guide to Using Apple Products for Seniors. These types of Simple technology books for seniors are easy to learn because they have simple language and clear directions. It helps older people set up their phones, send messages, make calls, look at apps, and fix common issues. It should not be scary to use technology. People over 65 can use Apple products with trust after reading this book.
This guide is helpful for people who are new to iPhones and iPads or just want to brush up on what they know. It breaks down hard steps into little steps that are simple to follow. Technology has made it possible for seniors to learn at their own pace and enjoy its advantages. Seniors can stay in touch with family, get their daily lives in order, and learn new ways to use their devices by following the advice in this book. These types of Simple technology books for seniors make sure that everyone can use Apple products. Technology is supposed to make life easy.
0 notes
Text
4K USB Cameras for Digital Signage: Ultra-HD Clarity to Enhance Visual Communication
When was the last time you were captivated by a digital signage display? Was it the high-definition visuals that caught your attention, or was it the seamless content that told a story so clearly that you couldn’t look away? Imagine pushing the boundaries of that experience with ultra-HD clarity, offering crisp, lifelike visuals that transform the way messages are communicated. Enter the world of 4K USB cameras, a powerful tool elevating digital signage to new heights.
As businesses look to capture the attention of consumers in a crowded marketplace, visual communication becomes a critical strategy. Whether it’s in retail, transportation hubs, healthcare, or entertainment, digital signage has become a powerful tool for informing, engaging, and influencing. But what happens when traditional signage tools fall short of providing the sharpness and impact you need? This is where 4K USB cameras shine, offering unparalleled clarity and a game-changing solution for digital signage setups.
The Challenges of Traditional Digital Signage
Before diving into the remarkable capabilities of 4K USB cameras, it's important to understand the struggles that many face with traditional digital signage.
1. Low-Resolution Display Quality: Many digital signage systems still rely on lower resolution displays, which can result in blurry images and pixelated content. This undermines the professional appearance of a business and diminishes the impact of its message. Low resolution makes it harder for viewers to engage with the content, especially from a distance.
2. Difficult Installation and Integration: Integrating high-quality cameras into existing signage setups can often involve cumbersome wiring, installation, and compatibility issues. Businesses face challenges in ensuring smooth operation with different digital signage hardware and software.
3. Lack of Flexibility and Scalability: Many digital signage solutions are limited in their ability to adjust for different content needs or locations. Once installed, these systems can be difficult to upgrade or modify as demands evolve. Businesses need signage that is adaptable and scalable without significant extra costs or complexities.
These are just a few of the barriers that businesses in various industries face when it comes to creating impactful and efficient digital signage systems.
Enter 4K USB Cameras: The Game-Changer for Digital Signage
4K resolution has become the gold standard for visual clarity, offering four times the resolution of Full HD. When coupled with USB connectivity, 4K USB cameras deliver a level of convenience and flexibility that is not only superior in quality but also incredibly easy to implement in digital signage systems. Let’s break down how these cameras resolve the pain points mentioned earlier and enhance visual communication in ways previously thought impossible.
Ultra-HD Clarity for Maximum Impact
The most obvious benefit of 4K USB cameras is their ability to provide ultra-high-definition visuals that drastically improve the viewer's experience. With 4K resolution, the sharpness, detail, and color depth of the display are dramatically enhanced. Whether it’s a product display in a retail environment, an informative sign in a hospital lobby, or an advertisement at a transportation station, 4K USB cameras ensure that content is crisp, clear, and visually appealing. This heightened level of detail makes it easier for viewers to read text, recognize faces, or see products in their full glory from a distance.
For businesses, this means higher engagement rates and more effective communication, as viewers are more likely to interact with high-quality, visually stimulating content. The clarity provided by 4K USB cameras ensures that your messaging is communicated with precision, leaving a lasting impact on your audience.
Simple Setup and Integration
Gone are the days of complex installations and compatibility issues. With USB connectivity, 4K USB cameras offer plug-and-play functionality, which makes installation simple and quick. The USB interface ensures seamless compatibility with most modern digital signage systems, saving valuable time and resources. Whether you're upgrading existing displays or installing new ones, 4K USB cameras provide a hassle-free experience.
This simplicity also extends to software integration. Many 4K USB cameras are supported by popular digital signage platforms, ensuring smooth interaction between the camera and your signage system. You don’t have to be a tech expert to enjoy the benefits of high-quality video streaming for your digital signage. The ability to integrate easily with existing setups means businesses can enhance their signage without overhauling their entire infrastructure.
Flexibility and Scalability for Future Growth
As businesses expand and evolve, so too must their signage systems. 4K USB cameras provide the flexibility to adjust content according to changing needs, whether that means adjusting the field of view or upgrading to a higher resolution without replacing the entire system. The scalability offered by USB cameras ensures that future expansions or upgrades can be done with ease and at a reasonable cost.
Additionally, USB connectivity allows for easy installation of multiple cameras, each offering a unique perspective, such as wide-angle shots or close-ups of products, without adding excessive complexity. The ability to easily scale your signage setup with minimal cost and effort means businesses can continuously adapt their messaging strategies to meet the demands of a dynamic environment.
Enhancing Customer Engagement Through Real-Time Interactivity
One of the most exciting possibilities for 4K USB cameras in digital signage is their ability to enable real-time interactivity. For example, incorporating facial recognition technology, gesture control, or even live video feeds can enhance the viewer experience, providing a more personalized and engaging interaction with the content. Customers can interact with digital displays to access information, make purchases, or receive special offers, all while enjoying ultra-HD visuals powered by 4K USB cameras.
The immersive experience fostered by interactive signage encourages customers to spend more time engaging with the content, ultimately driving higher conversion rates. For industries like retail or entertainment, this could mean an increase in foot traffic or ticket sales as consumers respond positively to the cutting-edge experience.
Real-World Applications of 4K USB Cameras in Digital Signage
The versatility of 4K USB cameras makes them ideal for a wide range of industries that rely on digital signage. Here are some notable use cases:
Retail: Retailers can use 4K USB cameras to display product demos, advertisements, and promotions with stunning clarity. The enhanced visuals grab attention and allow customers to see products in great detail, increasing the likelihood of purchase.
Healthcare: Hospitals and clinics can use 4K USB cameras to create informational displays that convey important health tips or wayfinding information with clarity, ensuring patients and visitors can easily navigate the facility.
Transportation Hubs: Airports, train stations, and bus terminals can benefit from 4K USB cameras for clear, informative signage, including live flight or train schedules, safety instructions, and advertisements.
Corporate and Event Spaces: Businesses hosting events or conferences can use 4K USB cameras to display detailed presentations, videos, or schedules on large digital signage screens, ensuring every attendee gets a clear and immersive experience.
Why 4K USB Cameras Are the Future of Digital Signage
In an increasingly competitive landscape, businesses cannot afford to settle for subpar visuals in their signage solutions. 4K USB cameras offer not only superior image quality but also ease of use, scalability, and flexibility. These cameras allow businesses to tackle the challenges of traditional digital signage, offering a sleek, cost-effective solution that drives engagement and enhances communication. Whether you're a retailer, a healthcare provider, or a corporate entity, investing in 4K USB cameras is a step towards transforming your digital signage system into a powerful tool for growth and customer engagement.
Visual Clarity That Makes a Difference
The impact of high-quality visuals in digital signage cannot be overstated. With 4K USB cameras, businesses can ensure that their message is not only seen but truly understood. Enhanced clarity, ease of integration, and future-proof scalability make these cameras an essential investment for any organization looking to elevate their visual communication strategy.
0 notes
Text
How Can Hackers Hack Your Phone?
Smartphones are an indispensable part of modern life, acting as personal assistants, communication hubs, and data storage centers. While they provide immense convenience, they also serve as tempting targets for hackers. Understanding how hackers can hack your phone is crucial to protecting your personal and professional data. This guide explores various hacking techniques and offers actionable tips to secure your device.

1. Social Engineering Attacks
Social engineering attacks exploit human behavior rather than technological vulnerabilities. Hackers manipulate individuals into sharing sensitive information or granting access to their devices.
Phishing
Phishing is one of the most common forms of social engineering. Hackers use deceptive emails, text messages (smishing), or phone calls (vishing) to trick you into clicking malicious links or providing sensitive details.
For instance, you might receive a message claiming to be from your bank, alerting you to suspicious activity on your account. The link redirects you to a fake login page, capturing your credentials.
Impersonation
Hackers may impersonate trusted entities such as technical support agents or service providers. They might convince you to install remote-access software, giving them control of your phone.
2. Exploiting Public Wi-Fi Networks
Public Wi-Fi networks are convenient but often lack adequate security. Hackers exploit these unsecured networks to intercept your data and hack your phone.
Man-in-the-Middle (MITM) Attacks
In MITM attacks, hackers position themselves between your device and the network. They can intercept and read your data, including emails, passwords, and financial transactions.
Rogue Hotspots
Hackers set up fake Wi-Fi hotspots with names resembling legitimate networks (e.g., “Free_Airport_WiFi”). When you connect, they gain access to all your internet activity.
3. Malicious Apps
Applications are a gateway to smartphone functionality, but they can also be a tool for hackers to hack your phone.
Fake Apps
Fake apps mimic legitimate ones but come bundled with malware. These apps may look authentic but can steal data, track keystrokes, or install additional malware.
Permission Misuse
Some apps request unnecessary permissions, such as access to your camera, microphone, or contacts. Granting these permissions can allow hackers to spy on you or steal your personal information.
4. Exploiting Software Vulnerabilities
Outdated software and unpatched vulnerabilities can give hackers the opening they need to hack your phone.
Zero-Day Exploits
A zero-day exploit takes advantage of software vulnerabilities before developers release a fix. These are particularly dangerous because users have no way to protect themselves initially.
Outdated Operating Systems
Failing to update your operating system can leave your device exposed to known security flaws that hackers can exploit.
5. SIM Swapping
SIM swapping, also known as SIM hijacking, is a method where hackers convince your mobile carrier to transfer your phone number to their SIM card.
How It Works
Once hackers control your phone number, they can intercept two-factor authentication (2FA) codes, calls, and text messages. This enables them to access your bank accounts, social media profiles, and other sensitive accounts.
6. Bluetooth Exploits
Bluetooth technology, while convenient, can also expose your phone to hacking risks.
Bluejacking
Bluejacking involves sending unsolicited messages to nearby devices. While not harmful, it can be the first step toward a more invasive attack.
Bluesnarfing
Bluesnarfing allows hackers to access your phone's data via Bluetooth, including contacts, messages, and media files.
7. Spyware and Keyloggers
Spyware and keyloggers are malicious tools used to monitor your phone activity without your consent.
Spyware Installation
Spyware can be installed through:
Malicious links in emails or messages.
Compromised apps downloaded from unofficial sources.
Physical access to your device.
Keyloggers
Keyloggers record every keystroke you make, capturing sensitive information like passwords, credit card numbers, and private messages.
8. Physical Access and Data Theft
If a hacker gains physical access to your device, they can exploit it in numerous ways.
USB Malware
Public USB charging stations can be tampered with to inject malware into your phone. This is known as “juice jacking.”
Theft
Stolen phones are at high risk of being hacked if not protected by strong security measures like encryption and secure locks.
9. Advanced Hacking Techniques
Hackers are continually developing more sophisticated methods to compromise smartphones.
Network Spoofing
Hackers use devices like IMSI catchers or stingrays to mimic cell towers, tricking your phone into connecting to them. This allows them to intercept calls, texts, and internet traffic.
Cross-Site Scripting (XSS)
In XSS attacks, hackers inject malicious scripts into websites you visit. When you access these sites on your phone, the script can compromise your data or install malware.
10. How to Protect Your Phone
Understanding how hackers can hack your phone is only half the battle. Implementing robust security measures is essential for protecting your device.
Enable Two-Factor Authentication (2FA)
Use app-based 2FA instead of SMS-based methods for better security.
Update Your Software Regularly
Keep your operating system and apps updated to patch known vulnerabilities.
Download Apps Only from Trusted Sources
Stick to official app stores like Google Play or the Apple App Store.
Secure Your Lock Screen
Use strong passwords, PINs, or biometrics like fingerprint or face ID to protect your device.
Avoid Public Wi-Fi
Use a Virtual Private Network (VPN) when connecting to public Wi-Fi.
Be Wary of Links and Attachments
Don’t click on suspicious links or download unverified attachments.
Monitor App Permissions
Regularly review app permissions and disable unnecessary access.
Use Anti-Malware Software
Install reputable anti-malware software to protect your phone from malicious attacks.
Regular Backups
Back up your phone regularly to secure your data in case of a breach.
Conclusion
Smartphones are indispensable tools that store a wealth of personal and professional information. However, their convenience comes with risks. Hackers employ various techniques, from social engineering and exploiting public Wi-Fi to installing spyware and leveraging software vulnerabilities.
By understanding how hackers can hack your phone and adopting proactive security measures, you can significantly reduce your risk of falling victim to such attacks. Stay vigilant, keep your software updated, and practice safe online habits to safeguard your digital life.
0 notes
Text
Features of SendTheSong.xyz 🎶
SendTheSong.xyz is an innovative messaging platform that lets users create personalized music messages to express emotions in a unique way. Whether it’s a special occasion or just a thoughtful gesture, SendTheSong.xyz combines music and text to make each message more meaningful.
In this post, we’ll explore the standout features that make SendTheSong.xyz a go-to choice for sharing heartfelt messages through music. If you’re new to SendTheSong, start by reading What is SendTheSong.xyz? for a full introduction to the platform.
Key Features of SendTheSong.xyz
1. Personalized Music Messages
SendTheSong.xyz offers a unique way to express yourself by pairing messages with music. Users can select a song that aligns with their message’s tone, adding a layer of emotion that words alone can’t convey. This feature is especially useful for special moments when a simple message isn’t enough to capture what you’re feeling.
Learn more about creating personalized messages with our usage guide here.
2. User-Friendly Interface
One of the best things about SendTheSong.xyz is its easy-to-use design. The platform guides you through each step—choosing a song, writing a message, and sharing it—all in a matter of minutes. No complex setup is needed, making it accessible to everyone, even those who aren’t tech-savvy.
This simplicity has contributed significantly to SendTheSong.xyz’s popularity and is one of the key reasons it resonates with a broad audience.
3. Wide Selection of Songs
SendTheSong.xyz provides a wide array of music options, covering different genres and moods. Whether you’re looking for something romantic, upbeat, or inspirational, there’s a song for every occasion. The diversity of music choices makes it easy for users to find the perfect song to complement their message.
If you want to learn more about song-based messaging and why it’s impactful, check out our post on Discover SendTheSong.xyz.
4. Social Media Sharing
SendTheSong.xyz allows you to easily share your messages on social media, turning your creations into a viral experience. Simply add hashtags like #SendTheSong to join the community and share your unique music messages on TikTok, Instagram, and more. This feature enhances engagement and helps spread the word about SendTheSong.xyz.
5. No App Download Required
Currently, SendTheSong.xyz is a web-based platform, which means users don’t need to download an app. This is convenient for those who prefer quick access without installing additional software. However, the platform’s popularity has sparked interest in a potential app version. For updates on this, you can read about the SendTheSong Apk in this post.
Why Choose SendTheSong.xyz?
SendTheSong.xyz’s features make it a standout platform for meaningful messaging. It provides a new way of expressing emotions through music, connecting with others in a more personalized and memorable way. The platform’s simplicity and creative potential make it appealing for users looking to add depth to their messages.
Frequently Asked Questions (FAQs)
Q1: Is SendTheSong.xyz free to use? Yes, SendTheSong.xyz is entirely free to use. You can create and share as many messages as you like without any fees.
Q2: Can I find any song on SendTheSong.xyz? SendTheSong.xyz offers a broad selection of popular songs but may not have every song available. The library is continually growing to include more music choices.
Q3: Is there a mobile app for SendTheSong.xyz? Currently, there isn’t an app, but users are eager for one. You can follow updates on the SendTheSong.xyz Tumblr page.
Explore More on SendTheSong.xyz
Now that you know about the platform’s features, you can dive deeper by exploring How to Use SendTheSong.xyz for a practical guide on creating music messages. For more about the platform and its potential future developments, stay connected with SendTheSong.xyz on Tumblr.
Add a musical touch to your messages today with SendTheSong.xyz, a new way to make connections that last!
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#best cell phone hack#cell phone hacks#cell phone hack#cell phone hacker#cell phone hacking#mobile hacker#mobile hacks#hackerslist
0 notes
Text
How To Safeguard Your Laptop: Best Practices

How secure is your Laptop? We know today, that laptops are essential tools for work, study, and personal use. However, they are also vulnerable to cyber threats, data breaches, and physical theft. Whether you’re using your device at home or on the go, following security measures to protect your information is important.
Below are some crucial security tips to keep your laptop safe, especially if you require services like Real Expert Qatar, a trusted laptop service center Doha.
1. Use Strong Passwords
A strong password is the first line of defense against unauthorized access. Ensure your passwords are at least 12 characters long and include a mix of letters, numbers, and special characters. Regularly change your passwords, and avoid using easily guessed information like your name or birthdate.
2. Keep Your Software Updated
Outdated software can have vulnerabilities that hackers exploit. Regularly updating your operating system, antivirus software, and applications is essential to ensure your laptop is protected from the latest security threats. If you face any issues with updates, consider visiting Real Expert Qatar, a trusted Laptop Service center in Qatar for professional assistance.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, such as a text message code or an authentication app, in addition to your password. This reduces the risk of someone accessing your laptop even if they have your password.
4. Use Encryption
Encryption protects your sensitive data by converting it into a secure format that can only be read by authorized parties. You can enable encryption through built-in tools like BitLocker on Windows or FileVault on macOS. In case of any technical issues, Real Expert Qatar, a reputable laptop service center Doha can assist with configuration and troubleshooting.
5. Install Antivirus and Anti-Malware Software
Having robust antivirus and anti-malware software installed is essential for protecting your laptop from viruses, spyware, and other malicious threats. These programs regularly scan your laptop and quarantine any suspicious files. If you notice your laptop behaving unusually, it may be time to consult Real Expert Qatar-laptop repair center Doha for an in-depth inspection.
6. Avoid Public Wi-Fi Without a VPN
Public Wi-Fi networks are often unsecured, making it easy for hackers to intercept your data. If you must use public Wi-Fi, ensure you connect through a virtual private network (VPN) to encrypt your internet connection and protect your privacy.
7. Regular Backups
Backing up your data ensures that you don’t lose important information in case your laptop is lost, stolen, or compromised by malware. Use an external hard drive or a cloud storage solution for regular backups. In case you experience hardware failure, Real Expert Qatar, laptop repair center in Qatar can help with data recovery and getting your laptop back to optimal performance.
8. Physically Secure Your Laptop
When not in use, store your laptop in a safe location. Use a laptop lock to physically secure it if you leave it in public places like a café or library. This helps reduce the risk of theft, especially when traveling or working remotely.
Securing your laptop involves a combination of good digital habits and physical safeguards. By following these tips, you can minimize the risks of data breaches, malware attacks, and theft. For any technical support, whether it’s software updates or hardware repairs, Real Expert Services, a dependable Laptop service center in Doha can help ensure your laptop remains secure and functional.
Protect your laptop, protect your data!
1 note
·
View note
Text
Phone Spy App to Read Someone's Text Messages

Phone spy apps have become increasingly popular in recent years, allowing individuals to monitor and track the activities of others through their mobile devices. However, before delving into the benefits and limitations of these apps, it's crucial to understand their definition and purpose, as well as the considerations surrounding their use.
Definition and Purpose
Phone spy apps are software programs that can be installed on a target device to track its activities, such as text messages, calls, and social media interactions. The primary purpose of these apps is to provide remote monitoring capabilities for parents, employers, or individuals concerned about their loved ones' safety and well-being. Read more
Phone Spy Considerations
While phone spy apps can be valuable tools for monitoring and ensuring the safety of children or employees, it's essential to consider the implications of their use. Invasion of privacy and trust issues may arise when using spy apps without the target's knowledge or consent. It's crucial to weigh the benefits of monitoring against the potential harm to personal relationships and individual autonomy.
Understanding Phone Spy Apps
To effectively utilize phone spy apps, it's essential to understand the two main types: phone trackers and mobile spy software.
Phone Tracker
Phone trackers are applications that allow users to monitor a target phone's location, call logs, text messages, and browsing history. These apps offer various functionalities and features, such as real-time tracking, geofencing alerts, and remote locking capabilities. However, they also come with limitations, such as the need for physical access to the target device and compatibility issues with certain operating systems.
Mobile Spy Software
Mobile spy software goes a step further by providing users with advanced monitoring features, such as social media tracking, keystroke logging, and remote access to the target device's camera and microphone. These apps are compatible with a wide range of devices and operating systems, making them versatile tools for remote monitoring.
Remote Monitoring
One of the key advantages of phone spy apps is their ability to facilitate remote monitoring through spyware and cell phone spying functionalities.
Spyware for Phones
Spyware for phones allows users to remotely access a target device's data, including text messages, call logs, and browsing history. The data is typically encrypted to ensure security and privacy, making it difficult for unauthorized users to intercept or manipulate the information.
Cell Phone Spying
Cell phone spying involves monitoring a target device's social media activities, GPS location, and app usage. This feature is particularly useful for parents looking to track their children's whereabouts or employers monitoring their employees' productivity and compliance with company policies.
Popular Spy Apps in the Market
Several spy apps dominate the market, offering a range of surveillance and monitoring capabilities tailored to specific user needs.
Phone Surveillance
Phone surveillance apps provide hidden phone tracker options and a user-friendly interface for easy navigation and monitoring. These apps offer discreet monitoring features, ensuring that the target individual remains unaware of being monitored.
Spy App for Android
Spy apps designed for Android devices offer real-time monitoring features and compatibility with a wide range of Android smartphones and tablets. These apps provide users with comprehensive surveillance capabilities, including call recording, GPS tracking, and social media monitoring.
iPhone Spy Software
iPhone spy software is designed exclusively for iOS devices, offering unique features such as iCloud synchronization and remote access to a target device's data. These apps provide a seamless monitoring experience for iPhone users, ensuring that no activity goes unnoticed.
Covert Monitoring and Stealth Features
To maintain undetectable operation, phone spy apps offer covert monitoring and stealth features for discreet surveillance.
Covert Phone Monitoring
Covert phone monitoring allows users to track a target device's activities without alerting the user. Stealth mode operations ensure that the app remains hidden on the target device, making it virtually impossible to detect.
Stealth Spy App
Stealth spy apps feature concealed app icons and operations, making them virtually undetectable on the target device. These apps also offer remote control options for seamless monitoring and data retrieval.
Monitoring and Tracking Capabilities
Phone spy apps provide extensive monitoring and tracking capabilities, including keylogging, call and SMS tracking, and data backup options.
Phone Monitoring Tool
Phone monitoring tools offer keylogging and screenshot features for tracking text messages, browsing history, and app usage. These apps also provide call and SMS tracking functionalities for monitoring communication activities. Click here
Phone Spyware
Phone spyware enables users to back up data from a target device, as well as receive alert notifications for specific activities, such as suspicious calls or messages. These apps offer robust surveillance features for comprehensive monitoring and tracking.
Ensuring Undetectable Operation
To ensure the seamless operation of spy apps, users can take steps to prevent detection and maintain discreet surveillance.
Track Phone Activity
Regular updates and bug fixes are essential for preventing anti-virus detection and ensuring the smooth operation of spy apps. Optimizing battery usage and discrete data transmission also help maintain covert monitoring capabilities.
Conclusion
In conclusion, phone spy apps offer valuable monitoring and tracking capabilities for parents, employers, and individuals concerned about their loved ones' safety. It's essential to use these apps, considering the legal implications and privacy considerations surrounding their use.
0 notes
Text
All of us are all familiar with how much an iPhone is secure when it comes to smartphones. People usually prefer an iPhone due to its fast and attractive user interface. Now most of us must have wished to spy on the iPhone device of our friends or any family member. Spying on the iPhone does not walk in the park due to its advanced security mechanisms. Now some people like professional hackers claim to hack on any iPhone with any software. Hacking on an iPhone by installing software on the phone or PC doesn’t sound smart and easy. For someone who is new to spy apps this is a hell of a task to do on its own. What if you get to know that you can actually track any iPhone device without learning any kind of skills? Yes, this is totally possible for you to spy on an iPhone device without requiring any software or app installation. People usually perform different risky techniques or tricks to break into the iPhone but those tricks won’t work. Using a phone spying app will let you spy on any iPhone device without any installation or learning. Let’s discuss one of the best phone spy apps. Spyic- An Innovative Spy App Spyic is one of the popular and professional spying apps in the World right now. This app is the trust of millions, people are using Spyic on a daily basis. Parents, employees, companies, and almost everyone. People would not imagine before anyone that spy app like Spyic was this good to use and help spy on an iPhone without software. There is no issue that people encounter when it comes to using Spyic for iPhone monitoring. Some spying apps ask users to perform Jailbreak before spying on an iPhone but that’s not the case with Spyic. You don’t have to root your Android or Jailbreak your iPhone device to perform phone spying. Spy on an iPhone Without Software Although Spyic is an app, this is a web-based app that you can operate from any web browser on any device either PC or phone. For the iPhone there is no need to install anything on the spied device. Spyic works in stealth-mode so there is zero % chances of you being exposed as it makes everything super-safe. This app is more easy and simple to use beyond your expectations. Going through the whole Spyic review will clear most of your misconceptions about this phone spy app. You would be surprised to know that there are more than 30 spying features added in this spying app. All features have been designed according to the requirements of users in this modern world of technology. Let’s get to know the main spy features of this brilliant phone spy app. Call Tracking: An amazing spy feature that gives you complete monitoring control over call records of the target iPhone device. SMS Tracking: Access all text messages of an iPhone you want to monitor, reading sent, received, and even deleted messages is possible. Location Tracking: Track an iPhone’s location on the basis of GPS or WiFi along with full access to geographical address coordinates. Apart from all the above features, Spyic has so many other perks to offer. Facebook, Instagram, WhatsApp, and all installed third-party apps can be tracked without getting detected. So, social media apps, web browser history, and almost everything can be monitored on an iPhone device through this spectacular phone spying app. You can use this app for any feature by using its dashboard. Now, most of you would be feeling curious to know how to spy on an iPhone remotely using Spyic? The wait is over, we are going to view all steps we need to follow in order to start iPhone tracking with Spyic. How to Spy on an iPhone Remotely Using Spyic Some of you might be thinking that spying on the iPhone using Spyic would be very difficult. Well, spying on an iPhone has never been this much easy and fast like it is now. All you have to do is to follow all required steps and then you are ready to go. Remember you will not have to physically access an iPhone to perform phone monitoring. Let’s have a look at all those steps that we need to follow in order to track an iPhone device.
Step 1 At first, you have to open your web browser and visit the official website of Spyic. Now click on the Signup button to start creating an account by entering Email and Password. Step 2 You would be given two options, Android and iOS. Select iOS because you are going to track an iPhone device. Step 3 Now you have to enter the credentials of an iCloud account that is logged in on the same iPhone device you want to target. Step 4 Wait for a few seconds to let the system verify the iCloud account. After following some onscreen instructions you would complete the account creation process. Congratulations, you have managed to create an account on Spyic. You can just open any kind of browser, sign in to your make a new Spyic account and start tracking that configured target iPhone. Here you will see that all these spy applications are listed on the left side of the dashboard where your Spyic’s account shows. Some people don’t get satisfied by reading reviews about any app, they always want to try that thing by themselves. Another plus point of Spyic is that it provides an online ‘Demo’ version that you can easily see by tapping on the Demo tab on Spyic’s official web-page. By watching it you would be able to know how exactly this app works. Conclusion We’ve reviewed the whole Spyic phone spy app in details, we can say that no spy app is better than Spyic in terms of quality and professional spying services. Every feature and service of Spyic is up to the expectations of the people. There are no risks involved and no need to perform Root or Jailbreak sort of activities to start phone tracking. The stealth mode of the Spyic app is what gives a guarantee to users that no one will detect them spying on an iPhone device. So what are you waiting for? Visit the Spyic’s site and start tracking an iPhone device according to your needs.
0 notes