#Remove Obsolete Extended Attributes
Explore tagged Tumblr posts
Text
Significance of removing acidity in transformer oil
Monitoring transformer for its fitness is inevitable to acquire uninterrupted power supply. Maintaining the good working condition of transformer oil protects the equipment from tripping and other failures.
The wellbeing of the transformer is obsolete, if its transformer oil is contaminated, lest the apparatus would bulge or burst in the worst cases. Regular testing of the oil ensures safety and uninterrupted power supply while it serves insulation and cooling of the transformer.
Though all oils are good insulators, vegetable oils and animal fats are not used in transformers since the fatty acids attack fibrous elements used in winding insulation.
When transformer oil comes in contact with atmospheric oxygen it goes through chemical reaction which results in sludge or acid formation and settles in windings of the transformer. The oil deterioration that occurs deprives the insulating liquid of its cooling attributes and leads to expensive repairs.
Oxidation and contamination take a toll on the transformer oil and the sludge settles on the windings to cause more heat and more sludge. Increase in temperature and heat accelerates transformer oil deterioration.
Besides this Dissolved Gas Analysis (DGA) scans for faults like arcing, corona and overheated conditions so that transformer oil acidity removal is exercised.
The transformer oil deterioration is averted by inspecting the oil twice a year with focus on parameters such as dielectric strength, water content, colour, acidity, sludge, flash point, DDA, IFT (interfacial tension) and resistivity of the oil.
At higher temperatures, organic compounds breakdown to form carbon compounds. Besides this, silica gel turns to pink colour from its original blue colour, owing to saturation of moisture and when the gel is not renewed it contaminates the oil.
Besides the above mentioned general tests, Furan testing is conducted once in two years for five years since installation of transformer to detect transformer oil deterioration.
Transformer oil acidity removal is conducted by processes including transformer oil regeneration which involve degasification, dehydration and filtration. The transformer oil deterioration is mitigated by passing the oil through columns which contain Fullers Earth which removes impurities. The Fullers earth is used for approximately 500 times to purify the oil before its expiry. Oil deterioration is removed onsite and the transformer need not be relieved for purification purposes.
The sludge and acid content settled in the windings attack the cellulose and hamper oil circulation in the transformer and affects heat transfer. Transfromer oil acidity removal averts these events.
Besides these, transformer oil deterioration is also prevented by the following maintenance tests that should be conducted every day.
The oil levels in the Magnetic Oil Gauge or MOG of main tank and conservative tank must be maintained in prescribed levels. The silica gel must be monitored for change in colour and replaced when colour is changed. If any leakage is found, it must be promptly sealed.
Transformer oil deterioration can be avoided when transformer has additional film of nitrogen coated on the expansion tank. When the oil expands, the coating expands with it to avoid contact with external gases. In sealed transformers, excess nitrogen is ported to another tank.
Transformer regeneration extends lifespan of the oil and accentuates its insulating attributes.
http://www.hering-vpt.com/article/why-is-transformer-oil-purification-essential/
1 note
·
View note
Text
What’s Master Data Management and Why it’s Essential for Supply Chain?
With the proliferation of devices and channels, effective data management has become inextricably linked to customer experience and business growth. Quality, storage, security, and dissemination of key data assets like product data, asset data, customer data, and location data play a critical role in achieving business goals. Ergo, strategizing data management and aligning it to your business aim is more important than ever before.

When it comes to common data types that organizations deal with, it’s mostly to do with data sets like reference data, transactional data, hierarchical data, and metadata. However, if we combine all this data that describes objects around which business is conducted, it’s called the ‘master data’. Gartner interprets it as the ‘consistent and uniform set of identifiers and extended attributes that describes the core entities of the enterprise’.
Master data is the business-critical data about parties, places, and things. In the supply chain management (SCM), parties typically pertain to suppliers, manufacturers, warehouse managers, retailers, distributors, customers, etc.; places are all the locations where assets are stored including warehouses and stores; and things range from products, raw materials, domains, vehicles & vessels, assets, etc.
Master data is used throughout the organization under commonly agreed structures and is managed through enterprise-wide governance. It is not transactional in nature, does not change frequently, and is not specific to any geographic location, supply chain process, unit, or system.
Mastering the Master Data
Understanding the significance of master data solves only half the problem. How do you collate it? How do you classify and manage it? And most importantly, how do you administer its flow throughout your legacy system? That is where Master Data Management (MDM) comes into the picture. MDM is a systematic approach of data handling which has become a competitive advantage for companies that leverage from data-driven insights and analytics.
The significance of master data management (MDM) has amplified for organizations — making them recalibrate their data strategy and goals to future-proof their growth.
Gartner’s definition: “MDM is a technology-enabled discipline in which business and IT work together to ensure the uniformity, accuracy, stewardship, semantic consistency and accountability of the enterprise’s official shared master data assets.”
Forrester’s definition: “MDM solutions provide the capabilities to create the unique and qualified reference of shared enterprise data, such as customer, product, supplier, employee, site, asset, and organizational data.”
MDM is as business-centric as it is IT-centric. It is a technologically driven discipline encompassing tools and processes. MDM maintains authority over master data, by creating a unified repository or a ‘single source of truth’. It aims to attain accuracy, consistency, and completeness of data throughout the enterprise and its ecosystem of business partners.
Data Consolidation + Data Governance + Data Standards + Data Quality = MDM
How MDM helps simplify Supply Chain Management
The sheer range and volume of data involved in SCM are huge. It can originate from online forms, ERPs, CRM, routing data from fleets, employee profiles, vendors, and so on. Adopting an MDM strategy and implementing MDM solutions in the supply chain results in the integration of all this data so that it stays uniform across domains and departments. It removes data silos, collects data records into a master file, maintains its quality and integrity, eliminates redundancies and duplicities, as well as standardizes, preserves and governs data.
For example, inconsistencies in product SKUs, order numbers, or customer data records can cause unthinkable complications that can escalate as the data flows through different departments of the supply chain. MDM helps mitigate such issues.
While the benefits of MDM solutions vary depending on the domain/function in which they are implemented – there is a unique value proposition for every department. The solutions create a data architecture, which is so thoroughly inter-referenced that any stakeholder in any department can utilize it. They can provide insights on customer types and behaviors for sales and marketing decisions as well as provide insights on logistics based on routing data. Here are some of the key benefits associated with MDM:
Centralized Data Architecture – everyone can access data from different customers and vendors in multiple locations. This particularly helps in tracking and routing assets from procurement to manufacturing to distributors.
Optimization and Efficiency – data consolidation reduces the chances of human error and inaccuracy. With better visibility and optimization of end-to-end data, supply chain operations become more efficient.
Customer Engagement – data integrated from CRM and other departments help gauge customer behaviors, as well as internal service capacity across the globe.
Cracking the Last Mile – data-driven insights help in realizing customer patterns and thereby cut costs of the traveling salesman.
Master Edits – information modified in a master repository gets reflected throughout sub-databases. For example – data modified by the manufacturer on the product ingredient list seamlessly gets renewed for the distributor/retailer.
Data Reliability – minimal chances of data mix-up or obsolete inputs in a spreadsheet with a cross-referenced, authentic datastore visible to everybody in the supply chain.
Backup – data damage or loss at any stage of the supply chain can easily be recovered with a centralized database or ‘golden record’.
Are You Being a Good Data Steward?
Undefined or loose data governance can allow inaccurate data percolating throughout the supply chain and can severely damage your business and rapport. There can be huge repercussions if such flaws persist for a long time. In such a case, MDM becomes more necessary than beneficial. You can gauge your data management loopholes by looking for-
Data complications due to duplicate/poor quality/redundant data between different entities in the supply chain
Botched up shipment/procurement/retail orders due to data inaccuracies
Delayed product launches
Customer service flooded with complaints of inconsistent or inaccurate product data
MDM initiatives must quickly be undertaken by individuals responsible for data governance, stewardship, and administration if any of the aforementioned criteria are present in your supply chain management.
Effective MDM drives efficient SCM
Exponential data growth is a fundamental challenge that overwhelms most businesses today. The issue escalates proportionally with the number of entities or nodes in the internal/external business environment. And that is why optimizing supply chain management (SCM), which in itself is a complex network, hugely depends on data management.
One must act quickly to take control of data growth, complexity, and chaos. To seize the full potential of digital, decision-makers of SCM must develop data strategies and incorporate data management discipline. It will also help leverage upcoming supply chain technologies like advanced analytics, automation, machine learning, IoT, and blockchain. SCM managers must act now to focus, simplify, and standardize data through an enterprise master data management (MDM) strategy.
1 note
·
View note
Text
Save Fonts, Images & CSS Styles to Separate Files While Exporting MPP to HTML using .NET
What’s new in this release?
Aspose team is pleased to announce the new release of Aspose.Tasks for .NET 18.7. This release further enhances the Project data conversion to HTML by providing capability to save html elements to separate files. It also fixes several issues reported with the API that further enhances the adds to the overall stability of the API. This release of Aspose.Tasks for .NET API lets users export the fonts, images and CSS styles to separate files while exporting project data to HTML. It also provides the options to assign callback functions to the export process for assignment of necessary parameters. These modifications have been added to the HtmlSaveOptions class of the API and can be utilized as shown in the code sample on the blog announcement page. From this release onward, the obsolete members of ExtendedAttributeDefinition and OutlineValue have been removed. This is important to note as users will have to replace any such occurrences of Obsolete members with the new methods and techniques that have been available as replacement for long time now. This release includes plenty of new features as listed below
Add an option for saving fonts/images/css styles separately when saving as html
Remove obsolete members in ExtendedAttributeDefinition and OutlineValue
Add support for OnlyTableValuesAllowed field in new Extended Attributes API
Differences in XML output after resave
Incorrect timephased data for tasks with splits
Incorrect finish dates for tasks with splits
Timephased data displayed incorrectly after a resave
Fix duplicated "OutlineCode" elements in project's xml
AT brokes MPP file when tasks has splits
Incorrect duration in XML with custom timephased data
Duration changed due to update the percentage complete
LinkType changes after saving data to MPX
Other most recent bug fixes are also included in this release
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Tasks for .NET documentation that may guide users briefly how to use Aspose.Tasks for performing different tasks like the followings.
Saving Fonts, Images and CSS Styles Separately
Working with Extended Attributes of a Project
Overview: Aspose.Tasks for .NET
Aspose.Tasks is a non-graphical .NET Project management component that enables .NET applications to read, write and manage Project documents without utilizing Microsoft Project. With Aspose.Tasks you can read and change tasks, recurring tasks, resources, resource assignments, relations and calendars. Aspose.Tasks is a very mature product that offers stability and flexibility. As with all of the Aspose file management components, Aspose.Tasks works well with both WinForm and WebForm applications.
More about Aspose.Tasks for .NET
Homepage of Aspose.Tasks for .NET
Download Aspose.Tasks for .NET
Online documentation of Aspose.Tasks for .NET
#MPP to HTML conversion#Export Project Data to HTML#Save CSS styles in separate file#export images to separate files#Remove Obsolete Extended Attributes#.NET Project management
0 notes
Text
The Incredible Foxtail Pine

I remember the exact moment that foxtail pines imprinted themselves permanently in my memory. After descending from 13,153-foot Forester Pass, the John Muir Trail crosses Tyndall Creek and almost immediately climbs toward the Bighorn Plateau, a barren moonscape populated by marmots and surrounded by jagged peaks. If there are trees in this area they are stunted by the proximity to the treeline except for the ruddy-barked foxtail pine, with its broad trunk and windswept foliage standing stalwart against the harshest of elements. It seemed even more amazing that foxtails could seemingly thrive when even modest ground cover had retreated to more salubrious habitats. The forest floor was virtually barren.
This population of foxtail pines is some 500 miles from the foxtail pines in the Klamath Knot on California’s North Coast (where I live), where I live, and has been separated since the mid-Pleistocene (some million years). Both retain the bottlebrush needle arrangement that gives foxtail pines their distinctive appearance and name. But there are differences. Over the millennia, these subspecies have diverged in foliage, crown form, and bark color. The southern subspecies can live more than twice as long as its northern relatives (1,000 years), although neither contest the longevity of the foxtail’s cousin, the bristlecone pine (which touch 5,000 years). Some botanists have attributed the larger size of the southern subspecies to its longer life.
In the Klamath Knot, the foxtail does well in nutrient-deficient soils and is often found along high, dry ridgelines. Conifer guru Michael Kauffmann calls these isolated environments ‘sky islands’. These sky islands do not tend to be accessible in any other way than by a challenging, often arduous walk. That was exactly where I found a stand of foxtails below North Yolla Bolly Peak (7,868’). These trees seem to do best in the harshest of conditions often bent at the base from the weight of winter snow and dead at the top from relentless ridge top winds. The foxtail is the symbol of determination and resilience. Perhaps they too appreciate the magnificent views.
It was to be our fifth day of trail work along the Bigfoot Trail. Much of our effort had focused on removing downed trees and cutting back the brush that encroached on the trail. We had pushed as far as eight miles from our base camp which necessitated long exhausting walks in addition to the trail work. There was general interest in a break. While some spent the day bird watching and others ‘botanizing’, four of us found the abandoned fire lookout on Black Rock Mountain irresistible. This tired sentinel of a tower, made obsolete by technology, still watches over the northern Yolla Bollys. Had it been staffed, the lookout could well have called in the small fire that smoldered a ridgeline to the south sending skyward a modest plume of white smoke. It turned out that lightning had sparked the East Fire five days before our arrival and, gratefully, it never did amount to much. The Forest Service assigned two fire fighters to stay with our trail work group just in case the fire’s temperament changed and an evacuation was necessary. After the tragic fires of the past couple of years, all of California remains a bit on edge.

As we climbed we emerged from the incense cedar forest that surrounded our camp passing through patches of Shasta fir that dot the otherwise exposed expanse of Pettijohn Meadow. The route sent us below North Yolly Bolly to a broad saddle that separated the two peaks. Even in late June, substantial fields of snow blanketed the north face of this high ridge with the peaks – North Yolla Bolly and Black Rock – at opposite ends. It was an ample reminder that winter lasts much of the year at this elevation.
Intermingled with the Shasta fir were the foxtail, and then it was only foxtail grabbing onto the rocky, exposed ridge. David Rains Wallace says that these mountains seem old, marked by “the wrinkles and leanness of great age.” There are elements of flora and fauna here, he continues, that reach “farther into the past than any place west of the Mississippi River.” Perhaps it is only fitting that fossil records for the foxtail pine extend back more than 40 million years. It is a pretty amazing tree.
#Foxtail pine#Bristlecone pine#Yolla Bolly Mountains#Bighorn Plateau#David Rains Wallace#Klamath Knot
3 notes
·
View notes
Text
Open ps2 loader compatibility list


Update internal theme to Korium by Berion Multiple default/overlay/attribute image texture support for internal theme * Initialization is performed for search functions: Lifeline * New streaming mechanism for better playability: Various BEMANI games * New patch: Ratchet and Clank: Up Your Arsenal * Drive state of sceCdStandby has been changed to PAUSE: Check iTV * Added support for fonts stored on the HDD unit (root of +OPL partition hdd0:+OPL/) and USB device (root of device mass0:/). * Game history will now be updated the "towers" behind the "SONY Computer Entertainment" boot screen should continue to grow. * Renamed compatibility modes to have actual names.

Simply put your ISO files in your CD and DVD folders and OPL will find them. * ISO disc images no longer strictly need to be named in a special format. * Changed the delete and modify VMC controls to be disabled instead of hidden, when writes are disabled. * Renamed "Enable Delete and Rename" to "Enable Write Operations". * IP address configuration can be set automatically with DHCP, although it is still recommended to reserve an IP address for the PS2 in the network because the DHCP reservation will not be ever renewed while in-game. * SMB server can now be specified by its NetBIOS name. * Added a new network update mechanism, which allows game compatibility records to be automatically downloaded from the OPL-CL service. * Fixed HDD corruption caused by deleting a game from the HDD unit. * Fixed the problem with the HDLDump server being difficult to shut down properly. * Improved stability, design and UI responsiveness. * Network settings are now saved in opl_network.cfg. * Better error reporting and help messages in general. * Infamous "Blockhead Grande" theme bug SQUARSHED! (Themes should now get loaded correctly, regardless of display settings). * GSM moved to Game Options menu since its a Per-Game option now. * Improved the behaviour of the auto-refresh option. * Fixed renaming functionality for USBExtreme games. * Fixed support for SMB usernames and passwords that are longer than 16 characters (limit extended to 31). It's to emulate DVD-DL support, for DVD9 rips (games with their 2 layers compacted into 1). * Changed "Disable DVD-DL" to "Emulate DVD-DL" to better explain what it does. * Improved reliability of some CDVDMAN functions, for more consistent behaviour.
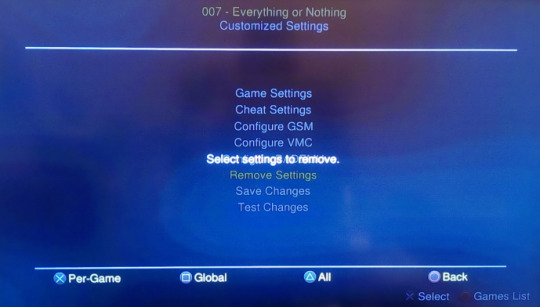
* Improved reading performance of the cdrom device. For games that need OPL to store its modules elsewhere, to avoid a memory conflict. * New compatibility mode: "high module storage". * Mode 7 "IOP threading hack" removed, as the new streaming mechanism has taken care of all related issues. * Added a workaround for some clone network adaptors. * The CallBack Timer (CBT) setting now uses a standardized value and was merged into Accurate Reads mode. * Added Accurate Reads mode, for emulating the reading speed and behaviour of the CD/DVD drive. * New super-slim EE core, making mode 1 (Alt EE core) obsolete. * New PS2RD Cheat Engine port by Doctorxyz. * Removed obsolete Compatibility Modes and needless GSM video modes. * VMC Fix - Slot2 should no longer clone Slot1 and vice versa * Improved performance and stability of SMB support. * Eliminated the need for user-configurable delays in USB support. * Updated USB drivers - support drives greater than 1TB but less than 2TB in capacity, plus better reliability. * Added support for the DTL-T10000, for debugging. * Kinder, gentler, and hopefully better IGR mechanism * New CDVDMAN streaming mechanism for better performance. Supports all PlayStation 2 and PlayStation 3 models with PlayStation 2 backward compatibility. It aims to be more compatible with games and should work without ps3load and DNASXXX.IMG. Open PS2 Loader is a loader of open source games compatible with the USB Advance / Extreme game format and also with the ISO format that can be started via USB, network (SMB) and from the PS2 HDD. It is the turn of Open PS2 Loader initially developed by ifcaro (known on PS3 with the Pkgview tool) and updated by jolek who has released a new revision 1442e. Some important homebrews for PS2 continue to be updated.

0 notes
Text
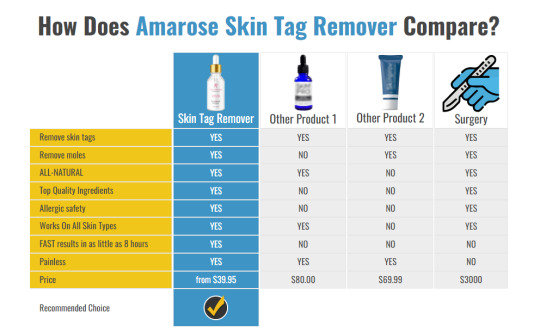
Amarose Skin Tag Remover Reviews Clean Skin Without Surgery!
Amarose Skin Tag Remover Reviews: - Can you feel as If you must choose between limited options aside from managing lacking skin prosperity? Accepting that is what is going on, it shouldn't need to end thusly. Skincare stresses on ordinary suggest lamentable lifestyle inclinations, hormonal lopsidedness, food needs, and an overall shortfall of thought on skincare frameworks. Right when most game plans work to present short-lived progressions for an external reason, 1 expert states she actually obtained a skin care plan that offers assistance and moves up to your own skin from within. Click here to visit the power site.

That genuinely can be really where it's Most sensible to present a dietary improvement named Amarose Skin Tag Remover.
The Objective of the Inspection is to supply a broad examination of this Amarose Skin Tag Remover condition, how it works, what laid out specialists ought to state about its own trimmings, and besides cost for one variable, to list a couple. Permit us in any case the expectations behind the Amarose Skin Tag Remover.
>> Visit Official Website Here <<
Know More About Amarose Skin Tag Remover?
Amarose Skin Tag Remover is a skincare supplement that intends to fix, revive and defend skin for women and men. This skin care condition can be basically just about as normal as it has seen it relies upon the general support of regular plants, supplements, flavors, and feeding improvements. Once used reliably, individuals can expect standard skin, a well-known term to portray a concordance between skin's soddenness creation (or oily substance made by the sebaceous organs) and sogginess grades. In like manner, for anyone engaging to show up at equilibrium among dried and unimaginably smooth skin, this particular unequivocal matter is genuine to become settled with each serving of Amarose Skin Tag Remover. With this specific getting it, we are as of now all set into the trimmings list.
How Does Amarose Skin Tag Remover Works?
Since You're careful, Amarose Skin Tag Remover can help you with getting back the Glow of your skin and besides help it with becoming smooth as well. Besides, it will monitor the skin from getting hurt.
Amarose Skin Tag Remover holders, considering the producer, include different regular trimmings, including ginger and Beetroot, every single person has its own arrangements of advantages. The items are stacked up with ordinary engineered intensifies which could fight and annihilate all probably purposes behind the skin's and human body's diminishing prosperity.
Basically All these Amarose Skin Tag Remover parts in their actual Formula work by diminishing two critical things which advance aging: raised irritation toxins and levels from your structure.
These combinations foster inside the entire body for Quite a While, Leading to an improvement of raised pressure grades. This oxidative tension could hurt the own skin's essential packaging, which makes it introduced to different skin issues.
Extending amounts of bothering Brought on by dreadful Living and food customs will hurt your skin and your overall success. In the long run, factors like splendid pillars, to which we're continually revealed, can achieve skin development thoughtlessly.
This itemizing Comprises ordinary trimmings alongside moderating And Antitoxin attributes which could help the clearing of any issues that may be causing the skin to appear to be dull and obsolete.
The minerals present inside these may attempt to lift the standard of the skin, so assisting you with recovering the shining look you had. Besides, getting skin from the inside is sensible.
>> Order Today Derma Prime Plus From its Official Website Right Now <<
Side Effects Of Amarose Skin Tag Remover – Is It Safe?
Amarose Skin Tag Remover isn't simply a convincing upgrade, yet it is safeguarded too. We did a wide assessment for this Amarose Skin Tag Remover Review, yet found no reports about the antagonistic consequences of using these pills.
In any case, it doesn't mean this supplement can't achieve any delayed consequences. Any improvement can cause delicate headaches, stomach issues, and other minor coincidental impacts. If you are a sound adult, it is completely safeguarded to take this enhancement.
Guarantee you shouldn't acknowledge different compartments in 24 hours or less. Going excessively far can cause troublesome issues.
Also, you ought to review that Amarose Skin Tag Remover is made only for adults more than 18. Expecting you are under 18, you shouldn't acknowledge it. Similarly, you should avoid this improvement accepting you are pregnant, nursing, or delicate to one of its trimmings.
Finally, Amarose Skin Tag Remover is exceptionally indulgent and safeguarded to work. If you are on embraced prescriptions or have a serious clinical issue, in a perfect world, we should direct your PCP to ensure this supplement is acceptable for you.
Overall, Amarose Skin Tag Remover is unquestionably convincing and safeguarded to work for strong individuals. It is shielded from invigorates, dangerous trimmings, or hard artificial materials. It won't make any delayed consequences whether or not you quit using it.
Top Quality Ingredients. Top Results.
Amarose Skin Tag Remover is a refined old-world fix that has been used for a seriously lengthy timespan. Our experts have united the power of Zincum Muriaticum and Sanguinaria Canadensis in an easy-to-use, clear and unscented, liquid serum for ideal results and basic application.
Amarose Skin Tag Remover is a serum delivered utilizing premium quality all-standard trimmings from around the world.
Sanguinaria Canadensis:- Sanguinaria Canadensis is a perennial, herbaceous flowering plant native to eastern North America. This flower has been historically used in ancient remedies by Native Americans for centuries. Sanguinaria Canadensis is a primary component that stimulates a rush of white blood cells to remove a blemish.
Zincum Muriaticum:- Zincum Muriaticum is a mineral found in Earth’s crust, and has strong antiseptic and disinfectant qualities, which contribute to its effectiveness. Zincum Muriaticum is a natural and powerful skin irritant that works to create a small layer of scabbing over the mole or skin tag blemished area, causing it to begin healing.

Must See:- Lowest Price Available: Get the Derma Prime Plus Here!!!
What Are The Benefits Of Amarose Skin Tag Remover?
Amarose Skin Tag Remover may increase the skin’s overall hydration.
It may make skin look younger, targeting the portion that has lost firmness.
Amarose Skin Tag Remover may lighten the dark marks and spots.
It may promote a flawless radiance.
Applying it regularly may slow down signs of aging.
Amarose Skin Tag Remover price?
Each Amarose Skin Tag Remover Container incorporates 60 cases expected to last multi-month. Each and every other individual is necessary to get each filling in as frequently as could be expected, rather than controlling supplies. Differently, results won't turn themselves, which influences the pockets and certainty endlessly out.
1 Amarose Skin Tag Remover bottle: $69 each
3 Amarose Skin Tag Remover bottles: $59 each
6 Amarose Skin Tag Remover bottles: $49 each

Final Words
Alongside all That information open in the business community, there's no response to the question whether this supplement could help the skin with staying better. Subsequently, in the event that you'd like strong and splendid skin, Amarose Skin Tag Remover could be your response to the skin issues.
youtube
1 note
·
View note
Text
Law Enforcement Data Security Remain Intact with WORM Card Benefits

Law enforcement agencies are vital to certify security for every nation. The current age is highly dependent on technological advancement and the law enforcers are not different from that. The agencies are now relying upon digitally recorded data. The exclusive attributes help them to identify criminals. The police departments are the prime users of various devices like digital interview recorders, body-worn cameras, and surveillance cameras.
Such devices store a number of crucial and sensitive information and security assurance is paramount. Every day, terabytes of data are generated by police interviews and recorded scenes that proceed as evidence later in court. To make sure the entire process goes right, data integrity shouldn’t be in question. In this certain case, WORM can be a great solution in providing the highest level of data security.

WORM Functionality for Law Enforcement
WORM stands for Write-Once-Read-Many formula. It is a tamper-proof flash storage device that fortifies data security ensuring all the files remain intact. This makes all the information intact, which means; none can modify or delete anything once saved. Being a manufacturer of flash storage devices, Flexxon has introduced a WORM SD and microSD card solution which is absolutely easy to use in police audio recording devices, body-worn cameras, and surveillance cameras ensuring proper data security.
The Devices Used by the Police Force
The law enforcement community needs to maintain safety and security for the storage and maintenance of digital data. Security cameras come to great help to identify criminals and criminal offenses. The footage of the interview recorders, surveillance cameras, and body cameras are used as the source of proof that helps in true reasoning for criminal investigations.
The use of surveillance cameras helps in gathering video footage to recognize criminals and to understand criminal activities. It can also be used as protection against crimes. On the other hand, body-worn cameras are used by police officers. This device can record audio and video at the same time to monitor their behavior and enhance accountability. The interview recorder is another solution used during live audio and video interview sessions. It saves the record of testimonies so that it can be used for further reasoning.
All these devices are essential to record events and it is also important to make sure the footage is not morphed because these data participate in solving critical cases and make it easier for the authority to announce a fair judgment. It is hard to anticipate the number of data generation through security cameras and top-notch protection should be assured. WORM enhances security as a safeguard to the video and audio recordings towards these applications so that the files can remain intact inside the devices.
Data Storage Systems Used in the Police Force
To store a 36mm film of influential images and videos, the system needs to have a secured storage device, or else the data can be stolen by someone involved in criminal activities. All thanks to the new WORM technology that keeps the data saved permanently in an unalterable format for the rest of its life. The extended memory capacity prioritizes the device storage for the police records. It can be seen several times once a file is saved. So, whoever wants to check on something specific about the case, can see it right away.
Flexxon WORM SD and Micro SD Card
Flexxon is the leading manufacturer of NAND flash storage devices. With a wide range of customers worldwide, Flexxon has formed a community ensuring the highest level of reliability, integrity, and compatibility. Currently, they are developing a WORM SD and microSD card solution with enhanced data security features. This specific memory solution emphasizes the need for forensic pictures, video footage, and recorded police interviews. The cards come in 4GB to a maximum of 32GB of memory capacities and plans are underway to have higher capacities for keeping up with the increased number of digital stimulation.

Features of Flexxon WORM Memory Cards
Flexxon WORM Memory Card is a reliable solution establishing data integrity with a secured file storage solution for data storage applications. The following features are enough to understand why it is perfect for law enforcement agencies:
Flexxon’s WORM SD and microSD cards are plug-and-play devices. Any sort of security camera with SD or microSD card slots can readily write data to it.
Flexxon’s WORM can switch directly to Write-Protect Mode to prohibit any action consisting of data modification or removal.
WORM SD and microSD card endure performance. It avoids read-disturbance errors, reduces the chance of uncorrectable errors, and enhances data reliability ensuring read-intensive data application.
Advantages of Write-Once-Read-Many File Systems
The durable structure of WORM takes care of critical issues in one solution where most of the law enforcement agencies spend a lot of money every year only to retrieve lost or damaged files. Flexxon’s WORM SD and microSD is effective and efficient in terms of maintaining data security:
It does not require any software installation. The default WORM mode kick starts its job to ensure the data is secured.
Uninterrupted security is assured to protect all the data and records against illegal or criminal offenses.
Since the use of CD and DVD is getting obsolete, WORM SD and microSD cards can be the best alternative.
How WORM is Changing the Game of Law Enforcement
At the war of keeping data safe and secured, digital storage devices are coming up with new ideas. Among those WORM is winning because of its remarkable features. Nowadays, many law enforcement agencies and government entities are using WORM storage solutions for its obvious advantages. The video recording devices including surveillance cameras, body-worn cameras, and interview recorders hold the SD or microSD card slot. The tiny slots on these devices are enough to keep WORM and enhance security functions. Flexxon WORM memory card is also compliant to use in other application devices to achieve the highest peak in serving the best security solution.
The Bottomline
Beyond law enforcement applications, Flexxon expects to move ahead with its cutting-edge WORM technology to other applications by establishing data integrity and reliability. Any organization generating sensitive data can use WORM SD and microSD solution by Flexxon and enhance data protection towards the organization.
0 notes
Text
New Coronavirus Aid for Businesses to Carryback Losses Five-Years
New Post has been published on https://wilsontaxlaw.com/new-coronavirus-aid-for-businesses-to-carryback-losses-five-years/
New Coronavirus Aid for Businesses to Carryback Losses Five-Years

Proposed and temporary regulations provide guidance for consolidated groups regarding net operating losses (NOLs). Specifically, the proposed regulations explain application of the rule enacted by the Tax Cuts and Jobs Act which limits the NOL deduction to 80 percent of taxable income less pre-2018 NOLs, effective for tax years beginning after 2020. In addition, the proposals remove obsolete provisions from the rules for consolidated groups that contain both life insurance companies and nonlife insurance companies. The Coronavirus Aid, Relief, and Economic Security Act (CARES Act) allows NOLs arising in tax year to be carried back five years, effective for NOLs arising in tax years beginning after 2017 and before 2021. Temporary regulations allow certain acquiring consolidated groups to make an election to waive all or a portion of the pre-acquisition portion of this extended carryback period for certain losses attributable to certain acquired members. Wilson Tax Law Group, APLC (www.wilsontaxlaw.com) is a boutique Orange County tax controversy law firm that specializes in representation of individuals and businesses before federal and state tax authorities with audits, appeals, FBAR, offshore compliance, litigation and criminal defense. Firm founder, Joseph P. Wilson, is a former Federal tax prosecutor and trial attorney for the IRS and California Franchise Tax Board. Wilson Tax Law Group is exclusively comprised of former IRS litigators and Assistant US Attorneys from the US Attorney’s Office, Central District of California, Tax Division and Criminal Division. For further information, or to arrange a consultation please contact: Wilson Tax Law Group, APLC Newport Beach and Yorba Linda, California Tel: (949) 397-2292 (Newport Beach Office) Tel: (714) 463-4430 (Yorba Linda Office)
0 notes
Text
6 Salon International Art Resilience | Musée de Peinture de Saint-Frajou, France
The International Art Exhibition will take place from 12 to 27 August 2017, at the Saint-Frajou Art Museum, Saint-Frajou 31230, France
Le beau par sa proximité du bien autorise le jugement par rapport à la qualité, dans le discernement du "c'est bien" et "ce n'est pas bien". Une œuvre qui ne repose sur aucun fondement est hors de la possibilité d'appréciation d'une quelconque qualité. La qualité de l'œuvre est dans son approximation à ce que l'art est sensé être, c'est à dire, principalement, producteur de l'émotion esthétique. Toute œuvre d'art est riche en possibilité d'expression, de manifestations, de discours qui en appellent à nos sentiments mais, le seul jugement de qualité possible est à travers le beau, c'est à dire la structure interne de l'œuvre. C'est à partir de cette structure qu'elle se distingue du discours ordinaire.
When everything becomes moving, only the beautiful can provide man with a point of reference and guarantee him a certain balance.
Banishing the beauty of art, artists have subjected it to violence, vulgarity, ugliness, emptiness. However, for the work of art to retain its capacity to situate us in a timeless space, to abstract ourselves from ourselves and to include us in a whole, experiencing in us the very dynamics of life, beauty is difficult to dismiss. It is immutable and constant.
Man by the sensitive perceives the beautiful to which he adheres by the intelligible because, there is a coincidence between the structure of the beautiful (structure of the world), and the structure of the human brain.
Beauty is mainly perceived as a simple taste. All objective value is denied to him.
But the beautiful does not reside in the subject, the form or the color but is subjacent to the work. Because it encompasses it, that it emanates from its form as a whole and not from the prettiness of the represented.
It's an immediate seizure. In this immediacy, the vision of the ontological whole appears, the subject (spectator) and the object (work) are one. There is no room for mere taste. Our experience cannot be projected.
The beautiful is a frame with rules but which unfolds endlessly.
Art is linked to the principle of the constant which connects art and the universe. Art is both an abstract concept and a concrete reality. As an abstract concept it is immutable, as a concrete reality it unfolds endlessly.
The beautiful by the constant, by the unchanging, by the perfect structure "of a mathematical theorem", calls for "eternity".
The beautiful which most powerfully connects man to the world and to "eternity" is the beautiful in art. Since art is the expression of awareness of existence, beauty is its very foundation.
But, starting from the principle that an art object is free and unique, we easily passed to the observation that it is sufficient and it is "beautiful" only in and of itself. It thus serves as a guarantor for the free individual who delights in the mere fact of existing, unique and free from all constraints, beautiful simply because he is free. Thus one removes art from its absolute character and any object manifested by its uselessness can be considered as an art object. But it is the very sentence of the death of art.
Since the postulate that art is impossible to define (Kierkegaard) and the identification of the beautiful with simple subjective taste, art loses all its specificity and all the judgment of the quality of the work becomes impossible. The beautiful is considered obsolete and the judgment on the quality of the work is replaced by all other considerations such as, novelty, message, action, ... these attributes can be part of the work but in no way assure it its specificity. Gradually the work itself eventually disappears.
The work of art rested on the harmoniously ordered internal structure, on duration by relating to the past, on the present by adjusting to its time, and was extended into the future based on what is immutable in it. , the beautiful. Thus, the work acquires the form of the living which assigns it its specificity and which each new look reacts to infinity. In this work, the artist and the spectator meet, through which man participates and registers in the world.
The duration of the work is abolished , artistic products becoming ephemeral. By subjectivization the production is centered only on the action of the artist, the interest of the art object lies only in the significant intention of the artist's project. However, art is precisely what has no intentionality.
The spectator is reduced to participating in the game, deciphering the speech or going for a walk. The spectator remains outside the work .
Thus, in contemporary products we are witnessing the suppression of the work of art, these products not based on any foundation and not distinguished in any way from any other object. Modern iconoclasm triumphed. To be iconoclastic is to be against the world. To be against the world is to be against reason. It is to be against man.
0 notes
Text
4 Telltale Signs Your Business Is Ripe for a Cybersecurity Attack (and How to Respond)
April 29, 2020 5 min read
Opinions expressed by Entrepreneur contributors are their own.
We live in a time when digital technology has become more fully ingrained in our society than ever before. Ecommerce was already experiencing significant growth prior to the global crisis, with the U.S. Department of Commerce reporting 14.9 percent sector growth in 2019.
In addition to ecommerce, technology such as cloud operations, automated tools for managing day-to-day tasks and remote work solutions have become increasingly important for businesses.
However, it’s important to keep in mind that while all of these advancements can improve efficiency and help your bottom line, they also increase your risk for a cybersecurity attack. If you aren’t prepared, the results can be devastating — in fact, the Committee on Small Business estimates that 60 percent of small to medium-sized businesses go out of business within six months of a successful cyberattack.
Understanding your deficiencies and taking preventative actions will prove essential for protecting your digital assets — and your business as a whole.
1. Your employees haven’t received cybersecurity training
Your employees may have your company’s best interests at heart, but they can easily prove to be an unintentional cybersecurity liability. The 2019 Data Breach Investigations Report from Verizon found that 94 percent of malware attacks were delivered via email.
These phishing attempts most often try to convince employees to download a file or click on a link that will install malware on their computers. Many of these emails can be highly sophisticated, designed to look like a message from one of your business partners or someone else within your organization.
Despite this, SmallBizTrends reports that only 31 percent of employees receive annual cybersecurity training. The best firewalls in the world won’t help your company if you don’t account for human error. Make sure your employees know how to identify malware so errant clicks don’t compromise your security.
Related: 10 Cybersecurity Best Practices for Your SMBS
2. You find yourself with inadequate physical security
While you certainly should take steps to establish comprehensive digital security, you cannot neglect your facility’s physical security needs. If someone were to break into your office and steal a computer with confidential files, the results would be just as devastating as if the information was stolen via malware.
A blog post from SysArc, an IT security services provider, notes that such deficiencies even extend to government facilities, where you would expect greater physical security to be present.
“Some auditors found that physical security at DoD facilities was inadequate,” the post notes. “For example, server racks that are not locked up can be compromised by workers or intruders. Similarly, some officials failed to adequately protect classified data that was stored on removable media, which can easily fall into the wrong hands.”
While security cameras and improved entry security can deter break-ins, business owners should also pay close attention to how equipment is used throughout the day. Some facilities may even find it beneficial to effectively ban USB drives, as these devices are easily lost or stolen.
3. You’ve overlooked multi-factor authentication
Despite recommendations to have different passwords for each account, data from Statista reveals that 65 percent of internet users use the same password for some or most of their accounts. This means that a breach at another retailer could help hackers gain access to employee accounts.
Fortunately, multi-factor authentication provides an easy way to counter this. Rather than simply allowing a user to log in with a username and potentially compromised password, it requires that a one-time code be sent to the user’s email or phone before they can complete the login.
This extra step is often enough to prevent a security breach — and can also alert users when an unauthorized individual is trying to log in with their account. Without this system, a major security breach could easily go unnoticed.
As Celu Ramasamy noted in Entrepreneur, other authentication methods could be even more secure: “Fast Identity Online (FIDO), which uses biometric or vocal recognition, is becoming more widely accepted and presents a more secure alternative to passwords. Even technology like blockchain offers a significant upgrade in verifying and authenticating users thanks to robust, transparent protocols that remove the need for obsolete and unsafe passwords.”
4. You haven’t reassessed your security programs
Most business owners understand the importance of installing firewalls and anti-malware programs to protect their networks and devices. But not all cybersecurity tools are created equal. If you opt for a less-than-adequate system that doesn’t continuously update to stop new threats, you will be putting your company at risk.
Hackers are constantly working to discover new cybersecurity vulnerabilities and are quick to take advantage of them. In fact, a report from Security Boulevard found that 60 percent of all data breaches that occurred in 2019 could be attributed to unpatched vulnerabilities. On average, it took 12 days for a security flaw to be patched.
That period is more than enough time for hackers to attack your business — especially if the security flaw gets widely publicized. When partnering with a security vendor, do your due diligence to ensure that they are proactive in identifying and addressing any flaws in your systems.
Related: 4 Major Cybersecurity Risks of Working From Home
Today, take action to protect your business from cyberattacks
From your customers’ financial data to proprietary information related to your products and business operations, there is a lot of valuable data being stored digitally these days. It’s little wonder that even a relatively small business serves as an attractive target for hackers.
By taking a step back to evaluate your weaknesses and then proactively implementing measures to address these issues, you will greatly reduce your risk of a security breach. It just might save your company.
Source link
Tags: 4, Attack, Business, cybersecurity, respond, Ripe, signs, Technology, Telltale
from WordPress https://ift.tt/2zIiP6s via IFTTT
0 notes
Text
Choosing the Best Rehabilitation Center Florida Lake Mary
How to choose the best drug and alcohol abuse rehabilitation and treatment centers in Florida Lake Mary
Can you or a loved one struggle with an addiction to drugs, alcohol or even?
It may seem overwhelming to acquire freedom from the chains of addiction and impossible occasionally.
There is hope however, countless individuals addicted to drugs, alcohol or have managed to get clean and stay clean with the help of organizations such as Alcoholics Anonymous or the thousands of residential and outpatient clinics dedicated to treating addiction.
Here at Find the Best Rehab Center we’ve been working since 2002 to help thousands of individuals just like you get the help you want.
But if you’ve failed one or more times to attain lasting freedom after rehab, perhaps after spending thousands of dollars, you are not alone. And odds are, it is not your fault.
Of the 23.5 million teens and adults addicted to alcohol or drugs, only about 1 in 10 has treatment, which too frequently fails to maintain them drug-free. A number of these programs fail to use proven methods to deal with the factors that underlie addiction and put off relapse.
According to current assessments of treatment programs, many are rooted in obsolete methods as opposed to newer approaches shown in scientific research to be more effective in helping people achieve and maintain addiction-free lives. Individuals typically do more research when shopping for a new car than when seeking treatment for addiction.
Types of drug, alcohol & substance addictions and abuse
What Substances Can Rehab Heal?
Most Common Types of Drug and Alcohol Abuse
Alcohol
Cocaine
Heroin
Pot
Methamphetamine
Opiates
Opioids
Tobacco products
youtube
How Rehabilitation Centers Help
Rehab is a treatment program designed to help those with addictions to psychoactive substances, specifically drugs and alcohol. Specifically, rehab aims to stop addiction by acknowledging an issue exists and coping with that issue. Some of the goals of rehab include:
Detoxification. It is typical for those entering rehab to be elevated or at least have remnants of drugs or alcohol in their system.
Overcoming denial. No treatment for addiction will operate if the patient doesn’t admit they have a problem.
Recognizing the nature of addiction. People should understand that addiction is a disorder of the mind.
Formal diagnosis. Rehab facilities normally recognize and cure co-occurring mental health issues.
Addiction management. Rehab centers provide tools, techniques and techniques for making behavioral and mental modifications to remain sober.
Identifying triggers. Rehabs help patients identify habits, character traits, emotions or concerns that promote or encourage addiction.
Recovery support. Rehab facilities help one build and maintain support networks and connections.
Things to Expect in Rehab
There are numerous important components to an effective and effective rehab program, irrespective of the specific kind of treatment selected.
Detoxification
Not all who enter rehab will require detox along with those that do may require varying degrees of medical care and oversight. Having the addiction, the entire body gets so used to the addictive substance that removing it in the system may cause extremely painful withdrawal symptoms. In many instances, the withdrawal symptoms can be harmful.
The precise detox process will depend on the substance and the intensity of the addiction. But, all detox processes will be supervised and executed by medical professionals that can make the detox process as safe and comfortable as medically possible. The detox can last anywhere from a few days to some Weeks and often happens in a medical facility.
Addiction Therapy and Education
The exact duration and nature of therapy varies. Most evidence-based therapies are going to have medicine and cognitive-behavioral element to them. More about that below.
Recovery Support
This generally entails finding ways to prevent relapse. The specific aftercare program is based on the individual’s progress and continuing demands. Cases of aftercare include counseling, support groups and sober housing.
Intake & Assessment
At this moment, the treatment suppliers assess the person to determine the very best treatment plan for that individual. Based on the program, an interview, medical examination and/or psychiatric exam will be conducted. One of the things treatment providers will look for are the presence of concurring psychological health or psychological problems. Family members and friends may also be interviewed to gain extra insight into someone’s addiction.
How to Find The Best Drug & Alcohol Treatment Facility Near You
Due to the unique nature of addiction, there are a plethora of treatment options available. The best treatment choice will be contingent on facts about the addiction, like how long it’s been happening, the presence of co-occurring mental health issues, the financial resources available for rehab as well as the substances that the person is using. Every one of the significant treatment options are discussed in detail below.
In a 2012, a study performed by the National Center on Addiction and Substance Abuse at Columbia University discovered that only about 10 percent of individuals addicted to drugs or alcohol (excluding nicotine) received any kind of addiction treatment. And most of those treated did not receive evidence-based treatments that utilize scientifically proven ways of fighting addiction.
Therefore, regardless of which treatment option is chosen, there are certain attributes or characteristics to look out for when choosing an effective rehab option.
The treatment will last a long time. The exact quantity of time will depend on the type of treatment chosen, but any successful treatment for addiction will last at least a few weeks.
Avoid intervention-based, episodic treatments if at all possible. The most effective treatment will involve long-term help to address the chronic disease that is addiction.
The treatment centers on evidence-based therapies.
The treatment will use multiple treatments to manage the multiple causes of addiction.
If any other mental disorders exist, they will be treated in precisely the exact same moment.
A long-term follow up plan is set up to check in with the person after treatment is officially finished.
Kinds of Addiction Treatment Centers
Treatment centers can be either Christian or non-religious, Inpatient or outpatient. Whatever your need we have a treatment methodology that can help you to conquer your addiction.
Residential Treatment
Also called inpatient treatment, residential treatment is a detailed treatment that encircles the person in a controlled environment 24 hours a day, seven days per week. Residential treatment could be long-term or short-term.
Long-Term Residential Treatment
Long-term residential treatment continues at least 2 months, but can generally last up to one year. This sort of treatment is thought to be among the very best options available, although it’s also expensive.
The most usual long-term residential treatment program relies on the idea of a healing community. In a therapeutic community, everybody, not just the expert staff, play a role in helping the individual fight addiction. Treatment will frequently start with detoxification and tackling the physiological facets of the addiction, but will soon shift to the emotional side of the issue. Because treating addiction often involves changing behaviour, it can take a long time to implement these favorable changes and make them more permanent.
Furthermore, the individual is surrounded by those who will fortify these modifications in behavior. They’re protected from impacts and triggers that contribute to addiction, which makes the treatment that far more successful. For example, the longer a individual is separated from previous acquaintances and preferences relating to the addiction, the more foreign and less familiar they will appear. This improves the odds of preventing a relapse.
Short-Term Residential Treatment
In short-term residential treatment, the individual will reside at the treatment facility and be tracked 24/7 until the rehab is over. But it will persist for a much briefer period of time, often a few weeks to a few months. As a consequence of the shorter time period for rehab, the method differs from the long-term residential treatment option.
Like the long-term residential treatment option, the person will normally go through detoxification and take part in behavioural and pharmacotherapies to tackle both the physical and mental aspects of addiction. However, with a briefer time in rehab, there is less opportunity for training, therapy and reinforcement of positive and constructive customs. Furthermore, there is not much opportunity for a individual to”grow remote” from his or her former life.
After the short-term residential treatment program is complete, the individual has to be diligent about completing follow up (aftercare) or outpatient treatment programs. A strong support system is vital to prevent relapse.
Outpatient Addiction Treatment
In outpatient treatment, a person does not live at the treatment facility. The precise kind of treatments will depend on the particular program, but is often less intense and of shorter duration than inpatient programs. There are a few other major differences as well.
Outpatient programs are excellent for those with extensive support networks. Because the treatment will cease when the person leaves the outpatient session, it’s very important that they have familymembers, friends or local support groups to help continue the treatment procedure. Without a supply of support and accountability after an outpatient treatment session is finished, the effectiveness of the treatment program will be diminished.
Outpatient programs are good for those who need treatment, but can’t manage to devote an extended period of time away from their job, home or current living situation. Even short-term residential inpatient treatment programs often last a month. This is a very long time to be away from family or employment.
Outpatient treatment is generally significantly less costly than inpatient treatment. But, even if it’s not quite as effective as inpatient treatment, it is better than no treatment in any way. A strong support system of support can drastically reduce the dangers of outpatient rehab.
State-Funded Treatment Programs
These rehab programs require a variety of forms, such as inpatient, outpatient, support groups and counseling. However, because they are state financed, the quality of care generally isn’t on par with private or luxury treatment rehab facilities. There can be waiting lists to enroll and also the ratio between professional employees and people is quite big. Additionally, some of the newer therapy or medical treatment options may not yet be available in state funded treatment programs, as a result of financial or bureaucratic considerations.
More Factors to Consider when Deciding on a Rehab Facility
Amenities
The conveniences provided during inpatient rehab are usually joined to the cost of this program. Luxury rehab treatment centers can provide lavish accommodations, gourmet meals and recreational activities, such as spa treatments.
On the opposite end of the spectrum are all state funded treatment programs. Most state funded treatment programs do not even have sufficient money to offer the most effective treatment potential, such as with more treatment specialists on staff. As such, the comforts will be sufficient, but not lavish.
Visitation
Visitation is advocated for many individuals in rehab. Familial and social support is vitally important to help fight addiction, especially after the treatment is finished. Family members and friends might even participate in the treatment during their visits.
Get help for you or a loved one by calling our 24/7 National Addiction hotline
The post Choosing the Best Rehabilitation Center Florida Lake Mary appeared first on Find The Best Rehab Center.
from Find The Best Rehab Center https://www.findthebestrehabcenter.com/choosing-the-best-rehabilitation-center-florida-lake-mary/
0 notes
Text
3 Ways To Make Spanish Accents On A Dell Laptop
BIOS settings program is also accessible on your DELL computer which controls all your hardware configurations. MAINGEAR is an revolutionary higher efficiency Computer system builder that offers custom desktops, custom constructed laptops, pc workstations, modest kind factor PCs, media center PCs, SteamOS powered steambox’s, and VR prepared systems. Each and every program is hand crafted for ultimate functionality with uncompromising quality that has won several Editors’ Decision awards from publications such as Pc Globe, Maximum Computer, Laptop Shopper and far more. With a passion to build the best higher performance computers and custom gaming computers, MAINGEAR will continue to set the common. MAINGEAR’s specialist group custom builds and supports all goods in the United States. Customize yours now.
This Workstation Pc attributes ample expansion slots, USB three.1, and VGA video capabilties proper from the board (DP, HDMI, and DVI-D from the board when paired with a E3 v5 CPU featuring Intel® HD Graphics P530). Walking towards the three computer systems near the escalators, the rightmost (ROW302) is a LIRA workstations. A wide assortment of Modular Personal computer Workstations is presented by us to customers in bulk at most reasonable prices. The supplied Modular Laptop Workstations are made by us as per the requirements of the consumers. Modular Pc Workstations are mostly identified for their longer shelf life.
I have just utilised your drivers and they perform up to a point. I can play the tracks on the transportable md but no sound comes out of the laptop. I am deligted that my md is becoming recognised and the tracks on the mds are visible and I am eternally gratefull for your work. I enjoy my MDs and will continue loving them till the last unit dies. I have plenty of backup units so I think I will be listening for some time to come. I am sick of windows domination of the application market and every release of windows brings nothing at all but grief. Microsoft sucks.
Getting a computer workstation is in a lot of approaches a individual preference. Windows based workstations are the most popular and integrate the very best with most networks and computer software. Interest in Mac devices is growing as Apple has worked to make their devices integrate greater with Windows based networks and as software program support on Mac devices has enhanced. Operating method (as tested) Operating method (as tested) The operating program that was installed on the computer at the time it was tested. The operating technique is the software that controls the simple operation of the personal computer. Common examples are Windows and Mac OS. The operating system determines the “look and feel” of the Computer.
The Application Licensing Service reported that the computer BIOS is missing a needed license. A handful of years ago, the possibilities had been reasonably clear. Individual computer systems did not do considerably, but they did it conveniently and cheaply so-called workstation computers—from Sun, for instance, or Apollo—did a lot more, but did it for ten times the cost and the huge machines that did nearly anything, cost a small fortune and necessary abundant technical support. Desktop is really one of categorization in terms of Private Computer(Pc).
We pride ourselves on being a laptop and technologies & complete service organization. We stock all effectively-identified computer brands and carry 1 of the best assortments of desktop computer systems – Perth has to supply. If you are seeking for accessories or further hardware for your property system, browse our on-line catalogue. We also give maintenance and repairs solutions, keeping you operating, playing and gaming from house or workplace, with minimal disruption.
People who use computer systems for extended periods of time may knowledge eye fatigue and discomfort or discomfort in the hands, wrists, arms, shoulders, neck or back. Poor function habits, poor workstation design and style, or improper use of workstation components normally result in these symptoms. In most situations, corrective measures are relatively simple and low-cost. If you are significant about video editing, graphic design and style, engineering, or you’re just the marketplace for a computer that will outperform any run-of-the-mill Computer, consider a workstation as your next key upgrade. You will absolutely dig the efficiency enhance.
When repurposing current computer systems, ECN recommends only the use of models from 2012 or newer. Some computers may call for memory upgrades. Even though ECN-supportable, will the models above meet your wants? See “How often need to my personal computer be replaced” in our Computer desktop recommendations page. (10) All computer workstations procured by and for the University will use vendors sourced under the Preferred Supplier Agreement. The Preferred Supplier Agreement provides i was reading this affordable options, discounted pricing, and improved consistency and availability of solution. Responsibility for preserving competitive Preferred Supplier Agreement’s will be with Director, Technology Solutions. On the internet pricing for computer gear is available from the University Technologies Solutions internet site.
A workstation is often a potent pc system that has outstanding graphics and a very rapidly processor, is very interactive, and is usually part of a network. Such systems are significantly utilized in engineering, electronics, power, and aerospace industries, and in universities. Applications incorporate CAD , desktop publishing , and AI research. In information processing and workplace systems the basic electronic gear would generally be a visual display and keyboard however there may also be ancillary electronic gear such as magnetic storage devices, printer, OCR, or bar-code scanner.
The computer systems that are referred to as workstations span a broad variety of personal computer power. They incorporate systems that differ from sophisticated, higher-powered personal computer utilised for pc-aided design and style (CAD), computer-aid engineering (CAE), graphics, and simulations, all the way to straightforward data entry terminals with no independent central processing unit (CPU). A workstation usually consists of a mouse, keyboard, monitor, and often, although not always, a CPU. It might also incorporate peripheral devices such as a modem, digital camera, scanner, or printer.
If the Emperor Laptop Station is as well rich for your blood starting at more than $five,000 there is now a new alternative for gamers, programmers, day traders, and anyone else that spends a wonderful deal of time in front of their monitor(s). The J20 Gaming Computer Workstation appears to be the best remedy for these of you browsing for a next generation workstation set up. Chinese Firm Ningbo Ingrem Electronic Technologies Co. has brought to marketplace an eye-catching option to MWE Lab’s Emperor line-up.
(18) Asset disposal procedures have been established to facilitate the removal of obsolete pc workstations from the University’s asset database and to establish effective procedures to erase data and data from the laptop in preparation for trade and physical removal of gear from the University. Just before any request for laptop workstation disposal and removal of data can be actioned, the Operate Unit should fully comply with the disposal procedures as outlined in this policy. It will be the responsibility of Economic Operations to ensure procedural compliance, with assistance from Technology Services.
When it comes to the education market place, the Compute Card could be utilised in an affordable, Chromebook-like laptop. That could make it simpler on schools when kids inevitably break their pc shells, as effectively as for when they require to upgrade their fleet of computer systems. Intel also brought up the possibility of having students move the Compute Card from their laptop to a intelligent screen in the classroom, or bringing it to a far more capable laptop shell at residence to continue their operate.
(19) All computer workstations will have a three-year on-internet site warranty which is serviced by approved regional vendors with certified pc assistance staff making sure that the computer is repaired swiftly and at no cost throughout its three-year life. The Application Licensing Service reported that the computer could not be activated with a Volume license item crucial. Volume-licensed systems demand upgrading from a qualifying operating technique. Please speak to your program administrator or use a diverse kind of essential.
youtube
Discontinued goods and brands include Axim ( PDA discontinued April 9, 2007), 11 Dimension (house and modest workplace desktop computer systems discontinued July 2007), Dell Digital Jukebox (MP3 player discontinued August 2006), Dell PowerApp (application-primarily based servers), and Dell Optiplex (desktop and tower computers previously supported to run server and desktop operating systems). The two-tiered shelf setup gives ample space for wider pc monitors and storage. Adjustments can be created to sit or stand, despite the fact that many customers reported that the method was slow and typically necessary more than one person. This stand up workstation, other people noted, accommodates taller men and women and can be adjusted to correct viewing height.
Filed under: Tagged: accents, spanish, techniques, three from KelsusIT.com – Refurbished laptops, desktop computers , servers http://bit.ly/2AXNAUa via IFTTT
0 notes
Text
Free download Visual Composer Page Builder for WordPress V5.2.1
New Post has been published on https://superhotthemes.com/free-download-visual-composer-page-builder-wordpress-v5-2-1/
Free download Visual Composer Page Builder for WordPress V5.2.1
Visual Composer Page Builder V5.2.1
Visual Composer WordPress Page Builder Plugin with Frontend and Backend Editor
Have you ever noticed how much time you waste while manually coding layouts? No more trial and error with shortcodes or CSS! Now you have everything it takes to design anything and for any page. Yes, Visual Composer works with any WordPress theme!
Say hello to the most popular WordPress page builder plugin! Visual Composer is easy to use drag and drop page builder that will help you to create any layout you can imagine fast and easy. No coding skills required!
Access Frontend editor (Inline editor) or Backend editor at any time. Yes, Visual Composer comes bundled with 2 types of editors allowing you to choose your preferred view. Create your WordPress website with backend schematic editor or move your page building process to frontend and see your results live.
Not only that, Visual Composer gives you full control over responsiveness. Create responsive websites automatically or adjust preferences you need to ensure your WordPress website looks perfect on mobile or tablet. Visual Composer has everything it takes to create a responsive website. Save your money on purchasing different devices with Visual Composer Responsive Preview available out of the box.
It is really easy to start building your WordPress website with Visual Composer – there are just a few clicks to make: Add rows and columns to your page; Choose from over 45+ predefined content elements or start from proffessionally designed template; Drag elements around your page; Simply adjust element settings via intuitive controls and options. Publish your page. And that’s not all! With page builder, you don’t have to be a developer to create a page. With Visual Composer you don’t have to be designer either.
Extensions: 200+ unique addons with hundreds of content elements available exclusively to Visual Composer; Template Library: Downloadable layout templates with pro templates updated regularly. Build your layouts literally in seconds; Your web developer (if you have any) will love Visual Composer as well. We offer a comprehensive knowledge base describing our developer API so you can extend Visual Composer. For those who don’t wish to code, Visual Composer offers Shortcode Mapper allowing you to add 3rd party shortcodes to your Visual Composer content elements. With Visual Composer you can work on new or existing websites as it will recognize your existing content and adapt to any WordPress website. Forget about page builders tailored for a specific theme to get you locked up – Visual Composer works with any WordPress theme.
Visual Composer is the #1 Best Selling drag and drop frontend and backend page builder plugin on the market – already powering 1,500,000+ websites. Join now and start creating beautiful WordPress websites in no time with minimum effort, and – of course – no coding and [shortcodes].
03.08.2017 – ver 5.2.1
Update: Function add_shortcode_param returned Update: Function get_row_css_class returned Update: Function wpb_map returned Fix: std fixed for attribute types nested in a param group Fix: vc_js error on frontend editor Fix: Font dropdown in TinyMCE for WordPress 4.8.1
06.06.2017 – ver 5.2
Added: RTL support Added: HoverBox content element Added: ZigZag separator content element Added: Parallax effect added to columns Added: video background added to columns Update: element presets work as My Elements in Add Element window Update: drag and drop control in Role Manager Update: deprecated functions removed Update: Arabic translation Update: Russian translation Update: Spanish translation Fix: TinyMCE performance in Backend editor Fix: remove obsolete function designOptions Fix: Layer Slider compatibility issues Fix: templates user access Fix: shortcode saving in fe adds 0=”” Fix: duplicate icons when adding custom icon font Fix: subscriber see Visual Composer welcome page Fix: WPML vendor issue Fix: page returns 0 when clicking add to cart from grid template Fix: shortcode regexp for dash in shortcode name Fix: preg_replace result, replacement and extra space Fix: filesystem error when saving design options (css) in settings Fix: woocommerce product id in grid api Fix: tabs/tours/accordions role access
04.04.2017 – ver 5.1.1
Added: extra security check for grid ajax calls to harden security
09.03.2017 – ver 5.1
Added: Element Id for all elements Added: Image size control for Grid Builder media elements Update: Grid Builder Backend editor style user interface Update: List of available Google Fonts Fix: getJSON backward compatibility for jQuery Fix: vcIcon font family Fix: postDeactivate redirect url Fix: Extra isset check in case if vc_remove_param Fix: Not all child categories are displayed in the drop-down Fix: Autocomplete param sorting Fix: Shortcode mapper and shortcodes with dashes Fix: Can not read property of ‘IndexOf’ Fix: Custom CSS textarea height Fix: Missing scrollbar for view preset Fix: Fix vc_gitem_template_attribute_post_image_url warning for array_merge Fix: Box-shadow and borders for twenty-seventeen Fix: Media query for added css files Fix: Increase gap in edit form for google fonts Fix: Hiding all “Tabs” in tab module still displays active item Fix: php 7.1 compatibility issues Fix: Section save as template option
MORE/INFO – DEMO: https://codecanyon.net/item/visual-composer-page-builder-for-wordpress/242431
Visual Composer Page Builder V5.2.1 download
https://drive.google.com/file/d/0Bx1UscVSDgifNjJUUWFBVGNzd3c/view?usp=sharing
You can Free download Visual Composer Page Builder for WordPress V5.2.1 nulled documentation for educational and testing purpose.If you want to use this for commercial purpose then click on sale page of developer through demo given above.
0 notes
Text
Java 10 Support & Nested Reports Provision by LINQ Reporting Engine inside Java Apps
What's New in this Release?
Aspose development team is happy to announce the monthly release of Aspose.Words for Java 18.8. There are 86 improvements and fixes has included in this regular monthly release, such as Java 10 tested and supported now, New and updated Samples and Examples, Change SHA-1 to SHA-256 and public asymmetric key from 1024 to 2048 for the license mechanism, Implemented support for “underline trailing spaces” compatibility option, Implemented support for paragraph alignment in Omath when inserted using EQ fields, Enhanced computation of interscript spacing values based on TTF properties, Improved wrapping of text around floating objects, Improved calculation of position of floating tables and shapes, Improved floater overlapping logic, Improved computing of pages numbers in continuous sections which have restart attribute and conflicting oddity, Fixed line justification issue when RTL span is at the end of the line, Fixed issue with null dml properties, Fixed issue with rendering of floating shapes in truncated headers/footers, Fixed issue with rendering of lines inside of a field result when updated in truncated part of a cell, Improved rendering of math operators in MathML objects, Improved rendering of MathML objects with n-ary math element when n-ary character and limit location are not specified, Fixed a bug with rendering of a math n-ary element if it is part of a fraction, Fixed a bug when polyline with an arrow and a very small line segment at the end, Fixed a bug when an arrow pointer is incorrectly directed while rendering Bezier curves with arrows, Fixed a bug where the end of the line was outside the “stealth arrow” when rendering, LINQ Reporting Engine supports nested reports. Aspose team has tested Aspose.Words for Java with Java 10 and is pleased to announce that Java 10 is now supported by the latest versions of Aspose.Words for Java. Developers can insert contents of outer documents to their reports dynamically using LINQ Reporting. Starting from Aspose.Words for Java 18.8, developers can enable doc tag to check the template syntax and populate with data using LINQ Reporting. By default, a document being inserted is not checked against template syntax and is not populated with data. It has added support to create snip corner rectangles in this version. This release has added HtmlSaveOptions.ExportCidUrlsForMhtmlResources property. Users can use this property to save the resources of MHTML document using the “Content-Id” URL Scheme. It has also added new property ShowComments in LayoutOptions class. This property is used to show or hide comments in fixed file formats e.g. PDF, XPS. By default, the comments are visible. A new property ShowInBalloons has been added to RevisionOptions class. This property is used to show revisions in the balloons. By default, the revisions in balloons are not shown. Previously, Aspose.Words used to save “@font-face” rules of HtmlFixed documents into a separate file “fontFaces.css” while other CSS declarations were written to “styles.css”. We have changed this behavior and now Aspose.Words saves all CSS rules and declarations into the same file “styles.css”. In case the old behavior is required for compatibility with legacy code, it can be restored by using the new public property HtmlFixedSaveOptions.SaveFontFaceCssSeparately. It has added new property RecognizeUtf8Text in RtfLoadOptions class. This property allows to detect UTF-8 encoded characters and preserve them during import. Obsolete value NumInDash was removed from NumberStyle enum. Please, use NumberStyle.NumberInDash value instead. Obsolete method ToTxt() was removed from Node class. Please, use ToString(SaveFormat.Text) instead. The obsolete property Location has been removed from the FootnoteOptions and EndnoteOptions classes. Please use the Position property. Also, the FootnoteLocation emum type has been removed. The list of most notable new and improved features added in this release are given below
Allow setting "Layout in Table Cell" option of shapes
Add feature to create Snip Corner Rectangle
Track changes rendering issue in resultant PDF
Add a feature to escape ampersand symbol during replacement
Change SHA-1 to SHA-256 and public asymmetric key from 1024 to 2048 for the license mechanism
Add feature to populate template document loaded by "doc" tag
Include Formatting Comments in Save To Tiff
Add feature to detect encoding characters and change them to UFT-8 in output RTF
SaveDate field's result become visible after re-saving the document
Reference resources in MHTML documents using the "Content-Id" URL scheme
Spaces and special characters trimmed when rendering
Remove UTF-8 BOM from CSS parts in MTHML documents
Rework span shallow size tests
Combine styles when saving Words to HTML with HtmlFixedSaveOptions
Incorrect font fallback for Asian characters
Implement the second way of rendering the shape outline
Line Caps Rendering - PolyLine caps direction is not correct
Update minimum possible font size
Remove Aspose logo from Venture license in trial mode
Remove obsolete public properties EndnoteOptions.Location/FootnoteOptions.Location
Set RunPr.ComplexScript to True for Thai letter list labels
SetLicense throws IllegalStateException.
Update Metered license code.
Save HTML to PDF-A_1B does not generate indexed images anymore
Borders look incorrect after converting document to PDF using MS Word or Bullzip PDF Printer
Table with different preferred widths extends outside the page when rendered
Table preferred width no longer automatically resizes when cell preferred width is set
Table column widths are calculated incorrectly during rendering
Cell's contents move to next line after conversion from Doc to Pdf
Elbow Arrow Connectors are not rendering correctly in PDF
Visio objects are overlapped in output PDF
Floating table is positioned improperly
Hijri Date is displayed in English Numbers in output DOCX/PDF
Text is missing after conversion form DOCX to PNG
DOCX to PDF conversion results are inconsistent in Multithreading
DOCX to HTML Issue with HtmlOfficeMathOutputMode as MathML
OfficeMath nodes are exported incorrectly as MathML in output HTML
Image generated from Dokkered web app is completely black.
Thai characters are converted to numbers in PDF
text-anchor' property is not imported correctly
Insert SVG into Aspose.Word.Document results in black image
The rendered PDF output is corrupted
Document.UpdateFields displaces text of frame when using 'IncludeText'
Arrow shape is rendered incorrectly
Numbers List Change while Converting Doc to PDF
Paragraph's text is missing in output PDF
Incorrect rendering of the OMath if FirstLineIndent is specified, after converting to PDF
Problem of incorrect Revisions Count after Comparing documents
CSS border style is not applied to image in output PDF/DOCX
Content is rendered on multiple pages in HtmlFixed/PNG
Distance between symbols not preserved in PDF
Borders of some SmartArt elements not preserved in PDF
LayoutCollector.GetStartPageIndex returns wrong page number
Equations render partially in generated PDF
Document.UpdateFields generates wrong alphabetical sort order for INDEX field
PDF output doesn't match the original DOCX document
Word breaking in Thai language is wrong
Signature images are not visible in generated PDF/Imag
Unknown yellow color rectangle is rendered after conversion from DOCX TO PDF
DOCX to PDF conversion issue with textbox shape glow
StartTrackRevisions hangs and process does not complete
Incorrect rendering of the text outline with zero width after converting to PDF
Extra pages are created when DOCX is converted to PDF
Improve conditions for hanging punctuation
Vertical spacing between Paragraphs increased when rendering to PDF
Remove whitespaces from MathML content while importing html to model.
Line Caps Rendering - Stealth arrow is rendered incorrectly.
Line Caps Rendering - Curved arrow has incorrect direction.
Other most recent bug fixes are also included in this release
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Words for .NET documentation that may guide users briefly how to use Aspose.Words for performing different tasks like the followings.
Inserting Documents Dynamically
Create Snip Corner Rectangle
Overview: Aspose.Words
Aspose.Words is a word processing component that enables .NET, Java & Android applications to read, write and modify Word documents without using Microsoft Word. Other useful features include document creation, content and formatting manipulation, mail merge abilities, reporting features, TOC updated/rebuilt, Embedded OOXML, Footnotes rendering and support of DOCX, DOC, WordprocessingML, HTML, XHTML, TXT and PDF formats (requires Aspose.Pdf). It supports both 32-bit and 64-bit operating systems. You can even use Aspose.Words for .NET to build applications with Mono.
More about Aspose.Words
Homepage Java Word Library
Download Aspose.Words for Java
Online documentation of Aspose.Words
Post your technical questions/queries to Aspose.Words Forum
Receive notifications about latest news and supported features by subscribing to Aspose.Words Blog
#Java 10 Support#Nested Reports by LINQ Reporting Engine#Create Snip Corner Rectangle#Reference Resources in MHTML File#Java Word Processing APIs#Show Revisions in Balloons
0 notes
Text
The best ways to Obtain The Best Cost For Your Residence
youtube
A great deal of sellers in realty want to move their homes as quickly as feasible and also for as long as feasible. Because they're constantly in a thrill, they forget to do the little points that make their houses interesting buyers. Figure out exactly what you may be overlooking to do in this write-up and also take steps to fix it.A great way for new property agents to drum up company is by sending by mail out marketing strategies to run out listings. These are people whose home really did not market and for one factor or another didn't re-sign up with their previous realty representative. So they're the ones probably on the market for someone brand-new to collaborate with. With a special marketing strategy package as well as by targeting picked ran out listings representatives could increase their listings by fifteen or twenty percent.A great way to obtain your house marketed even more quickly is to extend the selling market period. Make certain that your home prepares to take place the marketplace in mid-February so you have almost half a year to sell your home prior to the marketplace begins to close up. katy tx You could discover the forms needed for real estate bargains complimentary online. Due to the heavy economic weight as well as legal home rights associated with property professions, most of the necessary kinds are determined by state and city governments. These governments, in addition to, trustworthy real estate professionals generally supply the kinds on their web sites.Be sure to hire an appraiser that has more than five years experience on duty. The excellent appraiser should have state certification as well as licensing. Try to find one that does not work for your real estate representative to ensure that there will be no conflict of passion in any method.To get a concept for which attributes will assist your house sell quicker, go through a freshly constructed, high end development to see exactly what the newest residences have to provide. By doing this, you could identify exactly what to renovate and upgrade as well as which financial investments will certainly aid you locate a buyer.If you are trying to sell a residence with obsolete ceramic tile, consider painting it. This can be a less expensive choice to replacing all of your tile. Simply clean up the existing floor tiles, coat them with a high adhesion primer, and also painting them with a ceramic epoxy covering. You will certainly have a brand new look and also keep some loan in your pocket.As you are preparing to offer your residence, provide some additional attention to your front door. A purchaser's perception of your residence starts at the front step. Offer the door a fresh coat of paint or replace all of it with each other if it is damaged and also nicked. You want the customer to enter your residence with good feelings.As a home-seller in the real estate market, it's not concerning what you desire or require, whatsoever. It's everything about the purchaser. Understanding how to pacify and also accommodate purchasers, will make certain that you could relocate building in any market and also in any problem. Adhere to the pointers right here as well as you'll learn the best ways to effectively removal your house.
0 notes
Text
How you can Obtain The Best Price For Your Residence
youtube
A great deal of sellers in real estate wish to removal their homes as swiftly as possible and for as long as possible. Since they're always in a thrill, they forget to do the little things that make their houses appealing to buyers. Find out what you might be disregarding to do in this post as well as take steps to fix it.A great way for new realty agents to attract organisation is by mailing out advertising strategies to ended listings. These are people whose building didn't offer and also for one reason or one more really did not re-sign up with their previous property representative. So they're the ones most likely in the market for a person brand-new to work with. With a distinct advertising strategy bundle as well as by targeting selected ended listings representatives could boost their listings by fifteen or twenty percent.A fantastic means to get your residence sold even more conveniently is to extend the selling market period. Make sure that your home prepares to take place the marketplace in mid-February so you have almost half a year to sell your residence before the marketplace begins to close. realtors You can locate the particular types necessary genuine estate bargains cost-free online. Due to the heavy monetary weight as well as legal residential property rights associated with property trades, most of the needed forms are dictated by state as well as local governments. These federal governments, along with, trustworthy property experts usually provide the types on their websites.Make certain to work with an appraiser that has greater than 5 years experience on duty. The ideal evaluator should have state qualification and licensing. Search for one that does not function for your real estate representative to assure that there will be no dispute of interest in any type of way.To get an idea for which attributes will help your home offer faster, experience a recently developed, high-end advancement to see what the most recent houses have to provide. By doing this, you can determine exactly what to restore as well as upgrade along with which financial investments will certainly help you find a customer.If you are attempting to offer a residence with obsolete ceramic tile, consider painting it. This can be a less expensive option to changing every one of your floor tile. Simply clean the existing tiles, coat them with a high bond guide, as well as painting them with a ceramic epoxy covering. You will have a brand-new look as well as maintain some money in your pocket.As you are preparing to sell your residence, provide some extra attention to your front door. A customer's impact of your home begins at the front step. Give the door a fresh layer of paint or replace all of it together if it is damaged and also dented. You want the customer to enter your residence with fellow feelings.As a home-seller in the realty market, it's not about exactly what you desire or require, whatsoever. It's about the buyer. Knowing how you can soothe and accommodate purchasers, will guarantee that you can removal residential property in any type of market and also in any problem. Comply with the ideas below and you'll figure out how you can efficiently removal your home.
0 notes