#SQL Injection Vulnerability Scanner
Explore tagged Tumblr posts
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

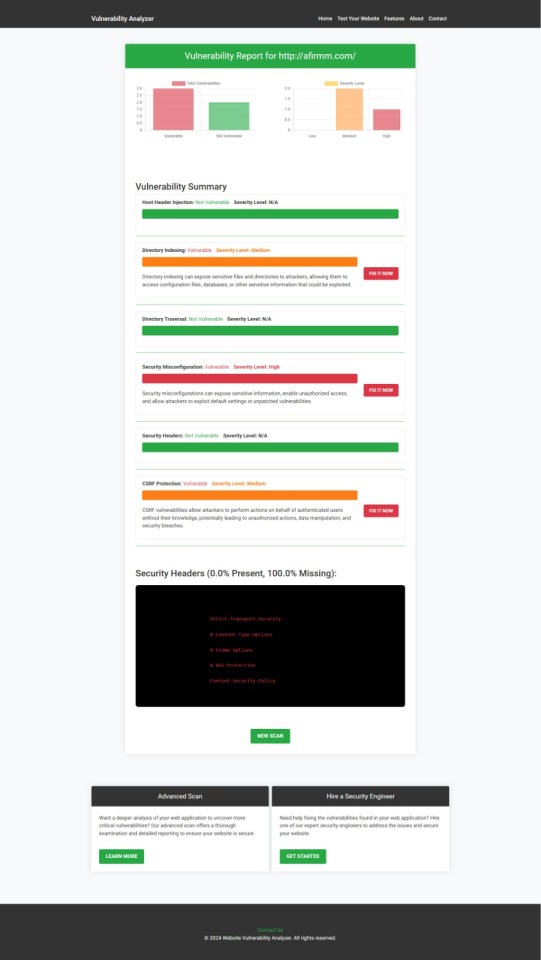
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Text
As a Cyber Security Expert, I will provide penetration Testing and WordPress Malware Removal services. Those are my best and strongest skills. I can combine the power of manual and automated penetration tests to remove all types of malware and viruses from any WordPress website.
My Services on penetration testing:
✅I will test File Uploads, SQL injection, XSS, CSRF, Authentication, Access Control, Information Disclosure, RFI, RCE, LFI, Brute Force, SSRF, and many more Bugs.
✅I will test your website and give you a professional and premium testing report that help you fix this vulnerability.
✅Network devices (Servers, switches, routers) Penetration Testing services.
✅I will test manual and automated both.
✅Mobile Application Penetration Testing.
My services for WordPress Malware Removal:
✅I will remove all types of malware and viruses from hacked WordPress websites
✅fix redirect issues where the website redirects to another website and URLs.
✅remove malware from the server of C-Panel
✅Reactive suspended hosting account.
✅Remove Japanese or Chinese Spam Links.
✅Remove all backdoors and phishing scripts.
✅Install many security plugins.
✅Updates all Plugins and Themes on your website.
Why work with me:
⭐️I will use multiple vulnerability scanners.
⭐️Provide unlimited modifications and retesting for the issues that have been fixed.
⭐️No false Positives on the Report and give the recommendations.
⭐️On-time delivery.
Me on Fiverr: https://www.fiverr.com/safety_hub?up_rollout
Let me work with you. I am a professional cybersecurity specialist with 3years of experience. I will give you the best service. I hope you will be satisfied.
Thank You.
4 notes
·
View notes
Text
Data hacks and identity theft have been making the headlines in recent years, making the security of your website more important than ever before. This is especially true if you handle financial transactions through your company's site, as you'll be processing your customers' sensitive financial data. Fortunately, you have many tools available to you to help ensure your website is as secure as possible. ScanMyServer ScanMyServer provides a comprehensive report of vulnerabilities throughout your website and on your server. It can identify PHP code injection, SQL injection, blind SQL injection, HTTP header injection and other scripting vulnerabilities. This service is free, and there is no registration required to test your site. You'll receive your results via email and can download a security badge to display on your site for your customers' peace of mind. Vega Vega is a security scanner designed for use with web applications. It provides an easy-to-use interface that makes the process as streamlined as possible, even for those who are unfamiliar with web security testing. It can help identify cross-site scripting, SQL injection and other application vulnerabilities. This open source application is backed by a powerful API for even greater customization and capability. Metasploit Metasploit makes use of the latest ethical hacking techniques to detect website vulnerabilities. This is what is known as penetration testing and has become more and more popular in recent years. If ethical hackers can break through your website's security protocols, then data thieves undoubtedly will be able to as well. Identifying these vulnerabilities early on can help you make the changes needed to secure your site from the latest threats. Sucuri Sucuri is a free website scanner that can detect viruses and malware. It can also identify and website errors or broken code, as well as out-of-date software. It can even alert you if your website has been blacklisted. This tool is compatible with a variety of popular website-building platforms, including WordPress, Drupal, Magento, Joomla and more. Qualys SSL Server Test This tool analyzes the configuration of your SSL web server and is designed specifically for secure (https) websites. You'll get in-depth analysis of your URL to help you identify vulnerabilities. This includes your site's expiration day, SSL/TLS version, overall security rating, protocol details and more. This is another free service, and neither your personal information nor your test results are used for any purpose other than to provide you with the analysis you have requested. Wapiti Wapiti scans for a variety of vulnerabilities in web applications. Similar to penetration testing, this application injects data to see if various scripts are vulnerable to attacks. It is capable of detecting file disclosure and inclusion vulnerabilities, site configuration issues, and a variety of injection complications. It is important to note, though, that while free, this is a command-line application. This may be a bit difficult for beginners to get the hang of and is better suited to advanced users. Wireshark Wireshark is another penetration testing application. It specializes in analyzing network protocols, getting into the tiniest details of your packet information and decryption. It's compatible with all the major operating systems, including Windows, OS X, Linux, Solaris and more. The application is free to download and can be viewed through a user interface or in TTY-mode TShark utility. Skipfish Skipfish crawls through your website, one page at a time, to detect any vulnerabilities in the code. This open source web application is free to download and use, and it is optimized for HTTP handling. It is capable of handling up to 2,000 requests per second without putting a strain on your CPU. Compatible with Windows, MacOS X, Linux and FreeBSD operating systems, this security application can detect even subtle flaws, like blind injection vectors.
Detectify Detectify is a suite of more than 100 automated security tests for your website. In total, it checks for over 700 distinct vulnerabilities. The team of ethical hackers behind the platform continually update the scans to detect the latest threats as they emerge, keeping your website secure in real time. You can test Detectify for free for 21 days, after which you'll have to pay a recurring membership fee for the ongoing security service. Siteguarding Siteguarding is a free online tool for detecting viruses, malware, phishing, injected spam, defacement and more. It can also help you clean and remove these threats from your website to ensure your security. The company also provides web hosting services, for a complete web security management package. These are just a few of the many website security options you have available to you, so there is no excuse for not having your website provide the latest security protections for your customers. Try out a few scans today to identify areas where your company website might be vulnerable so that you can regain control.Ken Lynch is an enterprise software startup veteran, who has always been fascinated by what drives workers to work and how to make work more engaging. Ken founded Reciprocity to pursue just that. He has propelled Reciprocity's success with this mission-based goal of engaging employees with the governance, risk, and compliance goals of their company in order to create more socially minded corporate citizens. Ken earned his BS in Computer Science and Electrical Engineering from MIT.
0 notes
Text
Why Your Digital Life Needs a Security Checkup (And How Vulnerability Scanning Can Save You)
Hey tech fam! 👋 Let's talk about something that might sound super technical but is actually pretty important for anyone who uses the internet (so... everyone?).
What's This "Vulnerability Scanning" Thing Anyway?
Think of vulnerability scanning like getting a regular health checkup, but for your computers, websites, and digital stuff. Just like how a doctor checks for health issues before they become serious problems, vulnerability scanning looks for security weak spots before hackers can exploit them.
It's basically an automated security guard that goes through all your digital assets and says "Hey, this password is weak," or "This software needs updating," or "This door is wide open for cybercriminals."
The Different Types of Digital Health Checks 🩺
Network Scanning: Checks your WiFi, routers, and all the tech that connects your devices together. Think of it as examining your digital nervous system.
Web App Scanning: Looks at websites and online applications for common hacker tricks like SQL injection (sounds scary, right?).
Database Scanning: Makes sure your stored data isn't sitting there with a "please steal me" sign on it.
Wireless Scanning: Checks if your WiFi is basically broadcasting "free internet and data access" to the whole neighborhood.
How Does It Actually Work? 🤖
Discovery Phase: The scanner maps out everything connected to your network (like taking inventory of your digital house)
Detection Phase: Compares what it finds against huge databases of known security holes and vulnerabilities
Risk Assessment: Ranks problems from "meh, fix when you have time" to "OMG FIX THIS NOW"
Reporting: Creates reports that actually make sense (hopefully)
Why Should You Care? 🤷♀️
Because Hackers Don't Take Days Off: They're constantly looking for easy targets. Regular scanning helps you not be one.
Compliance Stuff: If you run a business, there are probably rules you need to follow. Scanning helps with that boring (but important) paperwork.
It's Cheaper Than Getting Hacked: Trust me, prevention costs way less than dealing with a data breach. Way, way less.
Expert Help: Professional services give you more than just "here's a list of problems" - they actually help you understand and fix things.
What Makes a Good Vulnerability Scanning Service? ✨
Covers Everything: Should check all your digital stuff, not just some of it
Stays Updated: New threats pop up daily, so the service needs to keep up
Customizable: Your business isn't exactly like everyone else's, so your scanning shouldn't be either
Plays Well With Others: Should work with your existing security tools
Clear Reports: Nobody has time for technical gibberish without explanations
Real Talk: The Challenges 😅
Performance Impact: Scanning can slow things down temporarily (like how your phone gets slow during updates)
Information Overload: Sometimes you get SO many alerts that you don't know where to start
Not Enough Time/People: Small teams often feel overwhelmed by all the security stuff they need to handle
Pro Tips for Success 💡
Set up regular scans (like scheduling those dentist appointments you keep putting off)
Mix up authenticated and non-authenticated scans for different perspectives
Actually track whether you've fixed the problems (revolutionary concept, I know)
Learn to ignore false alarms so you can focus on real issues
The Future is Pretty Cool 🚀
AI and machine learning are making vulnerability scanning smarter. Soon, systems might even fix some problems automatically (while we're sleeping, hopefully).
We're also moving toward real-time monitoring instead of just periodic checkups. It's like having a fitness tracker for your cybersecurity.
Bottom Line 💯
Look, cybersecurity might seem intimidating, but vulnerability scanning is actually one of the more straightforward ways to protect yourself. It's like having a really thorough friend who points out when your digital fly is down before you embarrass yourself in public.
The internet can be a scary place, but you don't have to navigate it defenseless. Regular vulnerability scanning is like having a really good security system - it won't stop every single threat, but it'll catch most of them and give you peace of mind.
Ready to give your digital life a security checkup? Professional services can handle all the technical stuff while you focus on... literally anything else. Check out comprehensive vulnerability scanning solutions here and sleep better knowing your digital house has good locks on the doors.
Stay safe out there! 🛡️
What's your biggest cybersecurity worry? Drop it in the comments - let's discuss! 💬
#cybersecurity #vulnerability #techsafety #infosec #digitalsecurity #smallbusiness #technology #hacking #cybercrime #datasecurity
1 note
·
View note
Text
An Overview of Burp Suite: Acquisition, Features, Utilisation, Community Engagement, and Alternatives.
Introduction:
Burp Suite is one of the strongest web application security testing software tools used by cybersecurity experts, as well as ethical hackers. PortSwigger created Burp Suite, which provides potent scanning, crawling, and exploiting tools for web application vulnerabilities.
What is Burp Suite?
Burp Suite is one of the tools to conduct security testing of web applications. It assists security testers in detecting vulnerabilities and weaknesses like SQL injections, XSS, CSRF, etc.
Steps in Obtaining Burp Suite
Burp Suite is available for download on the PortSwigger official website. It is available in three versions:
Community Edition (Free)
Professional Edition (Subscription-Based)
Enterprise Edition (For Organisations)
Important Tools in Burp Suite
Proxy – Captures browser traffic
Spider – Crawls web application content
Scanner – Scans automatically for vulnerabilities (Pro only)
Intruder – Performs automated attack activities.
Repeater – Manually send requests.
Decoder – Translates encoded data.
Comparer – Compares HTTP requests/responses
Extender – Allows extensions through the BApp Store
How to Use Burp Suite
Set your browser to use Burp Proxy.
Capture and manipulate HTTP/S requests.
Utilise tools such as Repeater and Intruder for testing.
Scan server responses for risks.
Export reports for audit purposes.
Burp Suite Community
Burp Suite has a highly engaged worldwide user base of security experts. PortSwigger Forum and GitHub repositories have discussions, plugins, and tutorials. Many experts are contributing through YouTube, blogs, and courses.
Alternatives to Burp Suite
If you're searching for alternatives, then look at:
OWASP ZAP (Open Source)
Acunetix
Netsparker
Nikto
Wfuzz
Conclusion:
Burp Suite is widely used for web application security testing. Mastery of Burp Suite is one step towards web application security for both novice and professional ethical hackers.

#BurpSuite#CyberSecurity#EthicalHacking#PenTesting#BugBounty#InfoSec#WebSecurity#SecurityTools#AppSec#OWASP#HackingTools#TechTools#WhiteHatHacker#CyberTools#BurpSuiteCommunity#NetworkSecurity#PortSwigger#WebAppTesting#SecurityScanner#CyberAwareness
0 notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌��𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
Detect Vulnerabilities Faster With Website Scanner
Website scanners play a crucial role in accelerating the detection of security vulnerabilities within web applications. AI-driven vulnerability management and pentesting solution, automate the entire scanning process, starting with mapping the website’s structure, including URLs, forms, scripts, and third-party components. They then simulate real-world attack techniques using predefined test cases, heuristics, and vulnerability databases to identify issues such as SQL injection, cross-site scripting (XSS), CSRF, insecure configurations, and outdated components.
0 notes
Text
Some common mistakes to avoid in web development.
In the life of a developer, avoiding common pitfalls can save hours, enhance the User experience and let the website be successful. Below are the most common mistakes website developers should avoid, as well as possible solutions.
Ignoring mobile responsiveness
Mistake : A developer build the site to look great mainly on desktop but it is clunky and unusable on mobile devices. It may affect with web traffic, because over 60% web traffic coming from mobile.
Solution : Go with a mobile first design approach. We can use CSS frameworks such as bootstrap and tailwind CSS ; test on several devices and leverage tool like Google'S mobile friendly test to ensure mobile responsiveness.
Ignoring page load speed
Mistake : Heavy website with big images, unoptimiszd code, too many scripts, all cause the site to load slowly. In latest studies find that 53% of users leave the site because that take more than 3 seconds to load.
Solution : Optimize images, minimise your CSS or JavaScript; enable browser caching. Tool like lighthouse, or GT metrix will tell you what exactly is causing the trouble.
Poor SEO practices
Mistake : Overlooking in meta tags, atl text or proper URL structure will affect your search engine rankings.
Solution : Use semantic HTML, good meta description, optimise for your keywords, and ensure fast load time. You can also audit your site with the helpful tools such as Yoast SEO or Screaming frog.
Overcomplicating design
Mistake : Overstocking the site with the animation, fonts, and colours ; this will confuses the potential users and direct their attention away from the messages.
Solution : Go with minimal and cleaner layout with the confluency in typography, and a colour palette single to the concept. Consider the UX above everything else with the clear navigation.
Not testing cross- Browser compatibility
Mistake : Assuming a website works flawlessly on every Browser without testing. Minor difference in rendering under Chrome, firefox, Safari etc might kill the functionality.
Solution : Make a test on major browsers via browser stack or Lambda test software. Add vendor prefixes to your CSS and make sure that combine them with the feature detection in your Java Script code.
Weak security practices
Mistake : Ignoring securities measures make the site vulnerable to attacks like SQL injection ,XSS, or data branches. In 2025 cyber security are a top concern.
Solution : Use HTTPS, keep software always up to date and implement secure authentication methods. Regularly scan your application with a security scanner such as OWASP ZAP.
Not prioritizing user feedback
Mistake : The reason of ustability issues or missed opportunities, launching a site without gathering or acting on user feedback.
Solution : Before launch conduct a user testing. Use heatmaps to track behaviour. A/B testing can refine features.
Avoid these mistakes with planning, testing, and staying updated with web development trends. And also leverage model tools and communities to stay informed about best practices.
If you are looking for more advanced strategies, it’s smart to work with an experienced agency. Hollyminds Technologies is a great choice ,we make websites that are perfectly coded and structured to stand the test of time.The algorithms are set to bring visitors from across the globe. A structured website with right content, can bring more visitors to your business.
1 note
·
View note
Text
Uncover Hidden Threats with Expert Web Application Security Audits
In today’s digital landscape, your web applications are more than just tools — they’re the core of your customer experience, your data pipelines, and your business operations. But with growing complexity comes increasing risk. Hidden vulnerabilities, misconfigurations, and overlooked logic flaws are the perfect playground for cyber attackers.
That’s where expert web application security auditing steps in — not as an afterthought, but as a critical shield between your business and potential breaches.
The Real Risk of Hidden Threats
Most security breaches don’t happen because of sophisticated zero-day exploits. They happen because of basic oversights — weak authentication flows, exposed APIs, outdated components, or insecure data handling practices. Web applications, by nature, are public-facing and often integrate multiple services, libraries, and user inputs — making them an easy target.
Without regular auditing, these threats remain hidden in plain sight.
Common Hidden Vulnerabilities Found in Web Apps:
Cross-Site Scripting (XSS)
SQL Injection
Broken Access Controls
Insecure Direct Object References (IDOR)
Security Misconfigurations
Sensitive Data Exposure
Unvalidated Inputs
These aren’t just theoretical. They’re the root causes behind thousands of breaches every year.
What Is a Web Application Security Audit?
A web application security audit is a deep technical assessment of your application’s architecture, code, configurations, and data flows. It goes beyond automated scanners and dives into manual testing, logic review, and exploitation simulation to uncover weaknesses.
An expert-led audit typically involves:
Threat Modeling: Understanding how your app could be attacked based on its design and function.
Static and Dynamic Analysis: Reviewing code (if available) and monitoring runtime behavior.
Authentication & Session Review: Ensuring login, logout, and session management are airtight.
Business Logic Testing: Identifying flaws in the way your app handles actions like payments, transfers, permissions, or role-based access.
Compliance Checks: Ensuring your app aligns with standards like OWASP Top 10, PCI-DSS, GDPR, and others.
Why Expert Audits Matter More Than Ever
While automated tools have their place, they often miss contextual vulnerabilities — those that require human reasoning to find and exploit. That’s why expert auditors are irreplaceable.
They bring:
Years of experience
Manual testing techniques
Red team mindset
Industry-specific knowledge
An expert audit isn’t just about finding flaws — it’s about understanding risk in the context of your business.
Benefits You Can’t Ignore:
Early Threat Detection: Catch issues before attackers do.
Reduced Attack Surface: Shrink the number of exploitable paths.
Faster Incident Response: Know where you’re weak before it’s used against you.
Customer Trust: Demonstrate your commitment to security.
Regulatory Peace of Mind: Stay audit-ready and compliant.
When Should You Audit?
Security audits aren’t just for post-breach response. You should audit:
Before launching a new web application
After major updates or new feature rollouts
Periodically, as part of a security program
After suspected breaches or security anomalies
Proactivity is cheaper than recovery — both in cost and reputation.
Choosing the Right Security Partner
Not all audits are created equal. The value of your audit depends on who performs it and how thorough it is.
Look for partners who:
Provide both manual and automated testing
Deliver detailed reports with actionable insights
Offer post-audit remediation guidance
Have a proven track record in your industry
At eShield IT Services, we specialize in web application security auditing that’s tailored, exhaustive, and aligned with your business needs. Our audits don’t just check boxes — they build resilience.
Final Thoughts
Web applications are powerful — but power without protection is a liability. With expert security audits, you don’t just react to threats; you anticipate, uncover, and neutralize them before they become disasters.
Don’t let hidden vulnerabilities be your weakest link. Uncover them now — with expert web application security audits.
To know more click here :-https://eshielditservices.com
0 notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Enhancing Security in Backend Development: Best Practices for Developers
In today’s rapidly evolving digital environment, security in backend systems is paramount. As the backbone of web applications, the backend handles sensitive data processing, storage, and communication. Any vulnerabilities in this layer can lead to catastrophic breaches, affecting user trust and business integrity. This article highlights essential best practices to ensure your backend development meets the highest security standards.
1. Implement Strong Authentication and Authorization
One of the primary steps in securing backend development services is implementing robust authentication and authorization protocols. Password-based systems alone are no longer sufficient. Modern solutions like OAuth 2.0 and JSON Web Tokens (JWT) offer secure ways to manage user sessions. Multi-factor authentication (MFA) adds another layer of protection, requiring users to verify their identity using multiple methods, such as a password and a one-time code.
Authorization should be handled carefully to ensure users only access resources relevant to their role. By limiting privileges, you reduce the risk of sensitive data falling into the wrong hands. This practice is particularly crucial for applications that involve multiple user roles, such as administrators, managers, and end-users.
2. Encrypt Data in Transit and at Rest
Data encryption is a non-negotiable aspect of backend security. When data travels between servers and clients, it is vulnerable to interception. Implement HTTPS to secure this communication channel using SSL/TLS protocols. For data stored in databases, use encryption techniques that prevent unauthorized access. Even if an attacker gains access to the storage, encrypted data remains unreadable without the decryption keys.
Managing encryption keys securely is equally important. Store keys in hardware security modules (HSMs) or use services like AWS Key Management Service (KMS) to ensure they are well-protected. Regularly rotate keys to further reduce the risk of exposure.
3. Prevent SQL Injection and Other Injection Attacks
Injection attacks, particularly SQL injections, remain one of the most common threats to backend technologies for web development. Attackers exploit poorly sanitized input fields to execute malicious SQL queries. This can lead to unauthorized data access or even complete control of the database.
To mitigate this risk, always validate and sanitize user inputs. Use parameterized queries or prepared statements, which ensure that user-provided data cannot alter the intended database commands. Additionally, educate developers on the risks of injection attacks and implement static code analysis tools to identify vulnerabilities during the development process.
4. Employ Secure API Design
APIs are integral to backend development but can also serve as entry points for attackers if not secured properly. Authentication tokens, input validation, and rate limiting are essential to preventing unauthorized access and abuse. Moreover, all API endpoints should be designed with security-first principles.
For example, avoid exposing sensitive information in API responses. Error messages should be generic and not reveal the backend structure. Consider using tools like API gateways to enforce security policies, including data masking, IP whitelisting, and token validation.
5. Keep Dependencies Updated and Patched
Third-party libraries and frameworks streamline development but can introduce vulnerabilities if not updated regularly. Outdated software components are a common attack vector. Perform routine dependency checks and integrate automated vulnerability scanners like Snyk or Dependabot into your CI/CD pipeline.
Beyond updates, consider using tools to analyze your application for known vulnerabilities. For instance, dependency management tools can identify and notify you of outdated libraries, helping you stay ahead of potential risks.
6. Adopt Role-Based Access Control (RBAC)
Access management is a critical component of secure backend systems. Role-Based Access Control (RBAC) ensures users and applications have access only to what they need. Define roles clearly and assign permissions at a granular level. For example, a customer service representative may only access user profile data, while an admin might have permissions to modify backend configurations.
Implementing RBAC reduces the potential damage of a compromised user account. For added security, monitor access logs for unusual patterns, such as repeated failed login attempts or unauthorized access to restricted resources.
7. Harden Your Database Configurations
Databases are at the heart of backend systems, making them a prime target for attackers. Properly configuring your database is essential. Start by disabling unnecessary services and default accounts that could be exploited. Enforce strong password policies and ensure that sensitive data, such as passwords, is hashed using secure algorithms like bcrypt or Argon2.
Database permissions should also be restricted. Grant the least privilege necessary to applications interacting with the database. Regularly audit these permissions to identify and eliminate unnecessary access.
8. Monitor and Log Backend Activities
Real-time monitoring and logging are critical for detecting and responding to security threats. Implement tools like Logstash, Prometheus, and Kibana to track server activity and identify anomalies. Logs should include information about authentication attempts, database queries, and API usage.
However, ensure that logs themselves are secure. Store them in centralized, access-controlled environments and avoid exposing them to unauthorized users. Use log analysis tools to proactively identify patterns that may indicate an ongoing attack.
9. Mitigate Cross-Site Scripting (XSS) Risks
Cross-site scripting attacks can compromise your backend security through malicious scripts. To prevent XSS attacks, validate and sanitize all inputs received from the client side. Implement Content Security Policies (CSP) that restrict the types of scripts that can run within the application.
Another effective measure is to encode output data before rendering it in the user’s browser. For example, HTML encoding ensures that malicious scripts cannot execute, even if injected.
10. Secure Cloud Infrastructure
As businesses increasingly migrate to the cloud, backend developers must adapt to the unique challenges of cloud security. Use Identity and Access Management (IAM) features provided by cloud platforms like AWS, Google Cloud, and Azure to define precise permissions.
Enable encryption for all data stored in the cloud and use virtual private clouds (VPCs) to isolate your infrastructure from external threats. Regularly audit your cloud configuration to ensure compliance with security best practices.
11. Foster a Culture of Security
Security isn’t a one-time implementation — it’s an ongoing process. Regularly train your development team on emerging threats, secure coding practices, and compliance standards. Encourage developers to follow a security-first approach at every stage of development.
Conduct routine penetration tests and code audits to identify weaknesses. Establish a response plan to quickly address breaches or vulnerabilities. By fostering a security-conscious culture, your organization can stay ahead of evolving threats.
Thus, Backend security is an ongoing effort requiring vigilance, strategic planning, and adherence to best practices. Whether you’re managing APIs, databases, or cloud integrations, securing backend development services ensures the reliability and safety of your application.
0 notes
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
Crack the Code: How to Bulletproof Your Web Application In today’s hyper-connected world, web applications are the backbone of businesses, enabling seamless user experiences and efficient operations. However, with great convenience comes the looming threat of cyberattacks. From data breaches to phishing schemes, the stakes have never been higher. This is where security testing steps in—a vital process to ensure your web application can withstand malicious attacks. In this comprehensive guide, we’ll walk you through how to perform security testing for web applications effectively. Whether you’re a developer, QA engineer, or project manager, understanding these techniques is crucial to safeguarding your application and user data. 1. Understand the Basics of Security Testing Before diving into the technicalities, it’s essential to grasp what security testing is all about. In a nutshell, security testing evaluates a web application to identify vulnerabilities, weaknesses, and potential entry points for attackers. Why Security Testing Matters: Protects sensitive user data from unauthorized access. Ensures compliance with industry regulations (e.g., GDPR, HIPAA). Maintains the reputation and trustworthiness of your business. Types of Security Testing: Vulnerability Scanning: Identifies known vulnerabilities using automated tools. Penetration Testing: Simulates real-world attacks to find exploitable weaknesses. Security Auditing: Reviews code, configurations, and infrastructure for security flaws. Ethical Hacking: Involves ethical hackers to test your application’s resilience. 2. Prepare for Security Testing Preparation is key to effective security testing. Follow these steps to set the stage: Define Objectives: Determine the scope of your testing. Are you focusing on authentication mechanisms, data encryption, or overall application security? Understand Your Application: Map out the application’s architecture, including its features, data flow, and integration points. This helps in pinpointing areas to test. Gather Tools and Resources: Security testing requires a mix of automated tools and manual techniques. Some popular tools include: OWASP ZAP: Open-source tool for finding vulnerabilities. Burp Suite: Comprehensive platform for security testing. Nmap: Network scanner for identifying open ports and services. Metasploit: Framework for penetration testing. Establish a Test Environment: Create a separate environment for security testing to avoid affecting live users. Use realistic data and configurations to simulate real-world scenarios. 3. Key Areas to Focus On Security testing involves a thorough examination of various aspects of a web application. Below are the critical areas to focus on: Authentication and Authorization: Ensure that users can only access data and features they’re authorized to use. Test login mechanisms for brute-force vulnerabilities. Check session management to prevent session hijacking. Verify role-based access control (RBAC). Input Validation: Validate all user inputs to prevent injection attacks such as SQL injection, cross-site scripting (XSS), and command injection. Use whitelisting instead of blacklisting. Implement input sanitization on both client and server sides. Data Protection: Secure sensitive data both in transit and at rest. Use HTTPS for all communication. Encrypt sensitive information using strong algorithms (e.g., AES-256). Avoid storing unnecessary user data. Error Handling: Ensure error messages do not expose sensitive information. Avoid displaying stack traces or database errors. Log errors for debugging but ensure logs are securely stored. Third-Party Dependencies: Regularly update and audit third-party libraries and APIs to minimize vulnerabilities. Use tools like Dependabot or Snyk to monitor dependencies. 4. Conducting Security Tests
Now that you’re prepared, it’s time to execute the tests. Below are some common techniques: 1. Vulnerability Scanning: Run automated scans to detect common vulnerabilities such as insecure configurations and outdated components. Use OWASP ZAP for a quick and efficient scan. 2. Penetration Testing: Simulate real-world attacks to uncover hidden vulnerabilities. For instance: Attempt SQL injection attacks by inserting malicious SQL queries. Test for cross-site scripting (XSS) by injecting JavaScript code into input fields. 3. Fuzz Testing: Feed your application unexpected or random data to observe how it handles invalid inputs. This can reveal edge cases where your app may crash or behave unpredictably. 4. Secure Code Review: Manually review your application’s source code to find potential security flaws. Pay special attention to authentication logic, input validation, and error handling. 5. Remediation and Reporting Security testing is not just about finding vulnerabilities—it’s about fixing them. Prioritize Vulnerabilities: Use a risk-based approach to address vulnerabilities based on their severity and impact. Focus on critical issues first, such as SQL injection or weak password policies. Implement Fixes: Collaborate with your development team to resolve vulnerabilities. Test the fixes to ensure they work as intended without introducing new issues. Document Findings: Prepare a detailed report summarizing: Vulnerabilities discovered. Steps taken to remediate them. Recommendations for ongoing security practices. 6. Best Practices for Ongoing Security Security is not a one-time activity but a continuous process. Here are some best practices to maintain a secure web application: Adopt the Principle of Least Privilege: Grant users and systems only the access they need to perform their functions. Keep Software Up to Date: Regularly update your web application, server, and dependencies to patch known vulnerabilities. Conduct Regular Security Audits: Schedule periodic reviews to stay ahead of potential threats. Educate Your Team: Train your development and operations teams on secure coding and deployment practices. Monitor and Respond: Use intrusion detection systems (IDS) and log monitoring to identify and respond to suspicious activity in real time. Conclusion Security testing is a vital component of web application development and maintenance. By proactively identifying and addressing vulnerabilities, you not only protect your users but also ensure the long-term success of your application. Whether you’re running a small e-commerce site or a large-scale enterprise platform, investing in robust security practices pays dividends in trust and reliability. So, roll up your sleeves, follow the steps outlined in this guide, and make your web application a fortress against cyber threats.
0 notes