#SQL Server CASE statement
Explore tagged Tumblr posts
Text
Using CASE Statements for Conditional Logic in SQL Server like IF THEN
In SQL Server, you can use the CASE statement to perform IF…THEN logic within a SELECT statement. The CASE statement evaluates a list of conditions and returns one of multiple possible result expressions. Here’s the basic syntax for using a CASE statement: SELECT column1, column2, CASE WHEN condition1 THEN result1 WHEN condition2 THEN result2 ... ELSE default_result END AS…
View On WordPress
#conditional SELECT SQL#dynamic SQL queries#managing SQL data#SQL Server CASE statement#SQL Server tips
0 notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
Complete PHP Tutorial: Learn PHP from Scratch in 7 Days
Are you looking to learn backend web development and build dynamic websites with real functionality? You’re in the right place. Welcome to the Complete PHP Tutorial: Learn PHP from Scratch in 7 Days — a practical, beginner-friendly guide designed to help you master the fundamentals of PHP in just one week.
PHP, or Hypertext Preprocessor, is one of the most widely used server-side scripting languages on the web. It powers everything from small blogs to large-scale websites like Facebook and WordPress. Learning PHP opens up the door to back-end development, content management systems, and full-stack programming. Whether you're a complete beginner or have some experience with HTML/CSS, this tutorial is structured to help you learn PHP step by step with real-world examples.
Why Learn PHP?
Before diving into the tutorial, let’s understand why PHP is still relevant and worth learning in 2025:
Beginner-friendly: Easy syntax and wide support.
Open-source: Free to use with strong community support.
Cross-platform: Runs on Windows, macOS, Linux, and integrates with most servers.
Database integration: Works seamlessly with MySQL and other databases.
In-demand: Still heavily used in CMS platforms like WordPress, Joomla, and Drupal.
If you want to build contact forms, login systems, e-commerce platforms, or data-driven applications, PHP is a great place to start.
Day-by-Day Breakdown: Learn PHP from Scratch in 7 Days
Day 1: Introduction to PHP & Setup
Start by setting up your environment:
Install XAMPP or MAMP to create a local server.
Create your first .php file.
Learn how to embed PHP inside HTML.
Example:
<?php echo "Hello, PHP!"; ?>
What you’ll learn:
How PHP works on the server
Running PHP in your browser
Basic syntax and echo statement
Day 2: Variables, Data Types & Constants
Dive into PHP variables and data types:
$name = "John"; $age = 25; $is_student = true;
Key concepts:
Variable declaration and naming
Data types: String, Integer, Float, Boolean, Array
Constants and predefined variables ($_SERVER, $_GET, $_POST)
Day 3: Operators, Conditions & Control Flow
Learn how to make decisions in PHP:
if ($age > 18) { echo "You are an adult."; } else { echo "You are underage."; }
Topics covered:
Arithmetic, comparison, and logical operators
If-else, switch-case
Nesting conditions and best practices
Day 4: Loops and Arrays
Understand loops to perform repetitive tasks:
$fruits = ["Apple", "Banana", "Cherry"]; foreach ($fruits as $fruit) { echo $fruit. "<br>"; }
Learn about:
for, while, do...while, and foreach loops
Arrays: indexed, associative, and multidimensional
Array functions (count(), array_push(), etc.)
Day 5: Functions & Form Handling
Start writing reusable code and learn how to process user input from forms:
function greet($name) { return "Hello, $name!"; }
Skills you gain:
Defining and calling functions
Passing parameters and returning values
Handling HTML form data with $_POST and $_GET
Form validation and basic security tips
Day 6: Working with Files & Sessions
Build applications that remember users and work with files:
session_start(); $_SESSION["username"] = "admin";
Topics included:
File handling (fopen, fwrite, fread, etc.)
Reading and writing text files
Sessions and cookies
Login system basics using session variables
Day 7: PHP & MySQL – Database Connectivity
On the final day, you’ll connect PHP to a database and build a mini CRUD app:
$conn = new mysqli("localhost", "root", "", "mydatabase");
Learn how to:
Connect PHP to a MySQL database
Create and execute SQL queries
Insert, read, update, and delete (CRUD operations)
Display database data in HTML tables
Bonus Tips for Mastering PHP
Practice by building mini-projects (login form, guest book, blog)
Read official documentation at php.net
Use tools like phpMyAdmin to manage databases visually
Try MVC frameworks like Laravel or CodeIgniter once you're confident with core PHP
What You’ll Be Able to Build After This PHP Tutorial
After following this 7-day PHP tutorial, you’ll be able to:
Create dynamic web pages
Handle form submissions
Work with databases
Manage sessions and users
Understand the logic behind content management systems (CMS)
This gives you the foundation to become a full-stack developer, or even specialize in backend development using PHP and MySQL.
Final Thoughts
Learning PHP doesn’t have to be difficult or time-consuming. With the Complete PHP Tutorial: Learn PHP from Scratch in 7 Days, you’re taking a focused, structured path toward web development success. You’ll learn all the core concepts through clear explanations and hands-on examples that prepare you for real-world projects.
Whether you’re a student, freelancer, or aspiring developer, PHP remains a powerful and valuable skill to add to your web development toolkit.
So open up your code editor, start typing your first <?php ... ?> block, and begin your journey to building dynamic, powerful web applications — one day at a time.

0 notes
Text
Master SQL in 2025: The Only Bootcamp You’ll Ever Need

When it comes to data, one thing is clear—SQL is still king. From business intelligence to data analysis, web development to mobile apps, Structured Query Language (SQL) is everywhere. It’s the language behind the databases that run apps, websites, and software platforms across the world.
If you’re looking to gain practical skills and build a future-proof career in data, there’s one course that stands above the rest: the 2025 Complete SQL Bootcamp from Zero to Hero in SQL.
Let’s dive into what makes this bootcamp a must for learners at every level.
Why SQL Still Matters in 2025
In an era filled with cutting-edge tools and no-code platforms, SQL remains an essential skill for:
Data Analysts
Backend Developers
Business Intelligence Specialists
Data Scientists
Digital Marketers
Product Managers
Software Engineers
Why? Because SQL is the universal language for interacting with relational databases. Whether you're working with MySQL, PostgreSQL, SQLite, or Microsoft SQL Server, learning SQL opens the door to querying, analyzing, and interpreting data that powers decision-making.
And let’s not forget—it’s one of the highest-paying skills on the job market today.
Who Is This Bootcamp For?
Whether you’re a complete beginner or someone looking to polish your skills, the 2025 Complete SQL Bootcamp from Zero to Hero in SQL is structured to take you through a progressive learning journey. You’ll go from knowing nothing about databases to confidently querying real-world datasets.
This course is perfect for:
✅ Beginners with no prior programming experience ✅ Students preparing for tech interviews ✅ Professionals shifting to data roles ✅ Freelancers and entrepreneurs ✅ Anyone who wants to work with data more effectively
What You’ll Learn: A Roadmap to SQL Mastery
Let’s take a look at some of the key skills and topics covered in this course:
🔹 SQL Fundamentals
What is SQL and why it's important
Understanding databases and tables
Creating and managing database structures
Writing basic SELECT statements
🔹 Filtering & Sorting Data
Using WHERE clauses
Logical operators (AND, OR, NOT)
ORDER BY and LIMIT for controlling output
🔹 Aggregation and Grouping
COUNT, SUM, AVG, MIN, MAX
GROUP BY and HAVING
Combining aggregate functions with filters
🔹 Advanced SQL Techniques
JOINS: INNER, LEFT, RIGHT, FULL
Subqueries and nested SELECTs
Set operations (UNION, INTERSECT)
Case statements and conditional logic
🔹 Data Cleaning and Manipulation
UPDATE, DELETE, and INSERT statements
Handling NULL values
Using built-in functions for data formatting
🔹 Real-World Projects
Practical datasets to work on
Simulated business cases
Query optimization techniques
Hands-On Learning With Real Impact
Many online courses deliver knowledge. Few deliver results.
The 2025 Complete SQL Bootcamp from Zero to Hero in SQL does both. The course is filled with hands-on exercises, quizzes, and real-world projects so you actually apply what you learn. You’ll use modern tools like PostgreSQL and pgAdmin to get your hands dirty with real data.
Why This Course Stands Out
There’s no shortage of SQL tutorials out there. But this bootcamp stands out for a few big reasons:
✅ Beginner-Friendly Structure
No coding experience? No problem. The course takes a gentle approach to build your confidence with simple, clear instructions.
✅ Practice-Driven Learning
Learning by doing is at the heart of this course. You’ll write real queries, not just watch someone else do it.
✅ Lifetime Access
Revisit modules anytime you want. Perfect for refreshing your memory before an interview or brushing up on a specific concept.
✅ Constant Updates
SQL evolves. This bootcamp evolves with it—keeping you in sync with current industry standards in 2025.
✅ Community and Support
You won’t be learning alone. With a thriving student community and Q&A forums, support is just a click away.
Career Opportunities After Learning SQL
Mastering SQL can open the door to a wide range of job opportunities. Here are just a few roles you’ll be prepared for:
Data Analyst: Analyze business data and generate insights
Database Administrator: Manage and optimize data infrastructure
Business Intelligence Developer: Build dashboards and reports
Full Stack Developer: Integrate SQL with web and app projects
Digital Marketer: Track user behavior and campaign performance
In fact, companies like Amazon, Google, Netflix, and Facebook all require SQL proficiency in many of their job roles.
And yes—freelancers and solopreneurs can use SQL to analyze marketing campaigns, customer feedback, sales funnels, and more.
Real Testimonials From Learners
Here’s what past students are saying about this bootcamp:
⭐⭐⭐⭐⭐ “I had no experience with SQL before taking this course. Now I’m using it daily at my new job as a data analyst. Worth every minute!” – Sarah L.
⭐⭐⭐⭐⭐ “This course is structured so well. It’s fun, clear, and packed with challenges. I even built my own analytics dashboard!” – Jason D.
⭐⭐⭐⭐⭐ “The best SQL course I’ve found on the internet—and I’ve tried a few. I was up and running with real queries in just a few hours.” – Meera P.
How to Get Started
You don’t need to enroll in a university or pay thousands for a bootcamp. You can get started today with the 2025 Complete SQL Bootcamp from Zero to Hero in SQL and build real skills that make you employable.
Just grab a laptop, follow the course roadmap, and dive into your first database. No fluff. Just real, useful skills.
Tips to Succeed in the SQL Bootcamp
Want to get the most out of your SQL journey? Keep these pro tips in mind:
Practice regularly: SQL is a muscle—use it or lose it.
Do the projects: Apply what you learn to real datasets.
Take notes: Summarize concepts in your own words.
Explore further: Try joining Kaggle or GitHub to explore open datasets.
Ask questions: Engage in course forums or communities for deeper understanding.
Your Future in Data Starts Now
SQL is more than just a skill. It’s a career-launching power tool. With this knowledge, you can transition into tech, level up in your current role, or even start your freelance data business.
And it all begins with one powerful course: 👉 2025 Complete SQL Bootcamp from Zero to Hero in SQL
So, what are you waiting for?
Open the door to endless opportunities and unlock the world of data.
0 notes
Text
Java Database Connectivity API contains commonly asked Java interview questions. A good understanding of JDBC API is required to understand and leverage many powerful features of Java technology. Here are few important practical questions and answers which can be asked in a Core Java JDBC interview. Most of the java developers are required to use JDBC API in some type of application. Though its really common, not many people understand the real depth of this powerful java API. Dozens of relational databases are seamlessly connected using java due to the simplicity of this API. To name a few Oracle, MySQL, Postgres and MS SQL are some popular ones. This article is going to cover a lot of general questions and some of the really in-depth ones to. Java Interview Preparation Tips Part 0: Things You Must Know For a Java Interview Part 1: Core Java Interview Questions Part 2: JDBC Interview Questions Part 3: Collections Framework Interview Questions Part 4: Threading Interview Questions Part 5: Serialization Interview Questions Part 6: Classpath Related Questions Part 7: Java Architect Scalability Questions What are available drivers in JDBC? JDBC technology drivers fit into one of four categories: A JDBC-ODBC bridge provides JDBC API access via one or more ODBC drivers. Note that some ODBC native code and in many cases native database client code must be loaded on each client machine that uses this type of driver. Hence, this kind of driver is generally most appropriate when automatic installation and downloading of a Java technology application is not important. A native-API partly Java technology-enabled driver converts JDBC calls into calls on the client API for Oracle, Sybase, Informix, DB2, or other DBMS. Note that, like the bridge driver, this style of driver requires that some binary code be loaded on each client machine. A net-protocol fully Java technology-enabled driver translates JDBC API calls into a DBMS-independent net protocol which is then translated to a DBMS protocol by a server. This net server middleware is able to connect all of its Java technology-based clients to many different databases. The specific protocol used depends on the vendor. In general, this is the most flexible JDBC API alternative. It is likely that all vendors of this solution will provide products suitable for Intranet use. In order for these products to also support Internet access they must handle the additional requirements for security, access through firewalls, etc., that the Web imposes. Several vendors are adding JDBC technology-based drivers to their existing database middleware products. A native-protocol fully Java technology-enabled driver converts JDBC technology calls into the network protocol used by DBMSs directly. This allows a direct call from the client machine to the DBMS server and is a practical solution for Intranet access. Since many of these protocols are proprietary the database vendors themselves will be the primary source for this style of driver. Several database vendors have these in progress. What are the types of statements in JDBC? the JDBC API has 3 Interfaces, (1. Statement, 2. PreparedStatement, 3. CallableStatement ). The key features of these are as follows: Statement This interface is used for executing a static SQL statement and returning the results it produces. The object of Statement class can be created using Connection.createStatement() method. PreparedStatement A SQL statement is pre-compiled and stored in a PreparedStatement object. This object can then be used to efficiently execute this statement multiple times. The object of PreparedStatement class can be created using Connection.prepareStatement() method. This extends Statement interface. CallableStatement This interface is used to execute SQL stored procedures. This extends PreparedStatement interface. The object of CallableStatement class can be created using Connection.prepareCall() method.
What is a stored procedure? How to call stored procedure using JDBC API? Stored procedure is a group of SQL statements that forms a logical unit and performs a particular task. Stored Procedures are used to encapsulate a set of operations or queries to execute on database. Stored procedures can be compiled and executed with different parameters and results and may have any combination of input/output parameters. Stored procedures can be called using CallableStatement class in JDBC API. Below code snippet shows how this can be achieved. CallableStatement cs = con.prepareCall("call MY_STORED_PROC_NAME"); ResultSet rs = cs.executeQuery(); What is Connection pooling? What are the advantages of using a connection pool? Connection Pooling is a technique used for sharing the server resources among requested clients. It was pioneered by database vendors to allow multiple clients to share a cached set of connection objects that provides access to a database. Getting connection and disconnecting are costly operation, which affects the application performance, so we should avoid creating multiple connection during multiple database interactions. A pool contains set of Database connections which are already connected, and any client who wants to use it can take it from pool and when done with using it can be returned back to the pool. Apart from performance this also saves you resources as there may be limited database connections available for your application. How to do database connection using JDBC thin driver ? This is one of the most commonly asked questions from JDBC fundamentals, and knowing all the steps of JDBC connection is important. import java.sql.*; class JDBCTest public static void main (String args []) throws Exception //Load driver class Class.forName ("oracle.jdbc.driver.OracleDriver"); //Create connection Connection conn = DriverManager.getConnection ("jdbc:oracle:thin:@hostname:1526:testdb", "scott", "tiger"); // @machineName:port:SID, userid, password Statement stmt = conn.createStatement(); ResultSet rs = stmt.executeQuery("select 'Hi' from dual"); while (rs.next()) System.out.println (rs.getString(1)); // Print col 1 => Hi stmt.close(); What does Class.forName() method do? Method forName() is a static method of java.lang.Class. This can be used to dynamically load a class at run-time. Class.forName() loads the class if its not already loaded. It also executes the static block of loaded class. Then this method returns an instance of the loaded class. So a call to Class.forName('MyClass') is going to do following - Load the class MyClass. - Execute any static block code of MyClass. - Return an instance of MyClass. JDBC Driver loading using Class.forName is a good example of best use of this method. The driver loading is done like this Class.forName("org.mysql.Driver"); All JDBC Drivers have a static block that registers itself with DriverManager and DriverManager has static initializer method registerDriver() which can be called in a static blocks of Driver class. A MySQL JDBC Driver has a static initializer which looks like this: static try java.sql.DriverManager.registerDriver(new Driver()); catch (SQLException E) throw new RuntimeException("Can't register driver!"); Class.forName() loads driver class and executes the static block and the Driver registers itself with the DriverManager. Which one will you use Statement or PreparedStatement? Or Which one to use when (Statement/PreparedStatement)? Compare PreparedStatement vs Statement. By Java API definitions: Statement is a object used for executing a static SQL statement and returning the results it produces. PreparedStatement is a SQL statement which is precompiled and stored in a PreparedStatement object. This object can then be used to efficiently execute this statement multiple times. There are few advantages of using PreparedStatements over Statements
Since its pre-compiled, Executing the same query multiple times in loop, binding different parameter values each time is faster. (What does pre-compiled statement means? The prepared statement(pre-compiled) concept is not specific to Java, it is a database concept. Statement precompiling means: when you execute a SQL query, database server will prepare a execution plan before executing the actual query, this execution plan will be cached at database server for further execution.) In PreparedStatement the setDate()/setString() methods can be used to escape dates and strings properly, in a database-independent way. SQL injection attacks on a system are virtually impossible when using PreparedStatements. What does setAutoCommit(false) do? A JDBC connection is created in auto-commit mode by default. This means that each individual SQL statement is treated as a transaction and will be automatically committed as soon as it is executed. If you require two or more statements to be grouped into a transaction then you need to disable auto-commit mode using below command con.setAutoCommit(false); Once auto-commit mode is disabled, no SQL statements will be committed until you explicitly call the commit method. A Simple transaction with use of autocommit flag is demonstrated below. con.setAutoCommit(false); PreparedStatement updateStmt = con.prepareStatement( "UPDATE EMPLOYEE SET SALARY = ? WHERE EMP_NAME LIKE ?"); updateStmt.setInt(1, 5000); updateSales.setString(2, "Jack"); updateStmt.executeUpdate(); updateStmt.setInt(1, 6000); updateSales.setString(2, "Tom"); updateStmt.executeUpdate(); con.commit(); con.setAutoCommit(true); What are database warnings and How can I handle database warnings in JDBC? Warnings are issued by database to notify user of a problem which may not be very severe. Database warnings do not stop the execution of SQL statements. In JDBC SQLWarning is an exception that provides information on database access warnings. Warnings are silently chained to the object whose method caused it to be reported. Warnings may be retrieved from Connection, Statement, and ResultSet objects. Handling SQLWarning from connection object //Retrieving warning from connection object SQLWarning warning = conn.getWarnings(); //Retrieving next warning from warning object itself SQLWarning nextWarning = warning.getNextWarning(); //Clear all warnings reported for this Connection object. conn.clearWarnings(); Handling SQLWarning from Statement object //Retrieving warning from statement object stmt.getWarnings(); //Retrieving next warning from warning object itself SQLWarning nextWarning = warning.getNextWarning(); //Clear all warnings reported for this Statement object. stmt.clearWarnings(); Handling SQLWarning from ResultSet object //Retrieving warning from resultset object rs.getWarnings(); //Retrieving next warning from warning object itself SQLWarning nextWarning = warning.getNextWarning(); //Clear all warnings reported for this resultset object. rs.clearWarnings(); The call to getWarnings() method in any of above way retrieves the first warning reported by calls on this object. If there is more than one warning, subsequent warnings will be chained to the first one and can be retrieved by calling the method SQLWarning.getNextWarning on the warning that was retrieved previously. A call to clearWarnings() method clears all warnings reported for this object. After a call to this method, the method getWarnings returns null until a new warning is reported for this object. Trying to call getWarning() on a connection after it has been closed will cause an SQLException to be thrown. Similarly, trying to retrieve a warning on a statement after it has been closed or on a result set after it has been closed will cause an SQLException to be thrown. Note that closing a statement also closes a result set that it might have produced. What is Metadata and why should I use it?
JDBC API has 2 Metadata interfaces DatabaseMetaData & ResultSetMetaData. The DatabaseMetaData provides Comprehensive information about the database as a whole. This interface is implemented by driver vendors to let users know the capabilities of a Database Management System (DBMS) in combination with the driver based on JDBC technology ("JDBC driver") that is used with it. Below is a sample code which demonstrates how we can use the DatabaseMetaData DatabaseMetaData md = conn.getMetaData(); System.out.println("Database Name: " + md.getDatabaseProductName()); System.out.println("Database Version: " + md.getDatabaseProductVersion()); System.out.println("Driver Name: " + md.getDriverName()); System.out.println("Driver Version: " + md.getDriverVersion()); The ResultSetMetaData is an object that can be used to get information about the types and properties of the columns in a ResultSet object. Use DatabaseMetaData to find information about your database, such as its capabilities and structure. Use ResultSetMetaData to find information about the results of an SQL query, such as size and types of columns. Below a sample code which demonstrates how we can use the ResultSetMetaData ResultSet rs = stmt.executeQuery("SELECT a, b, c FROM TABLE2"); ResultSetMetaData rsmd = rs.getMetaData(); int numberOfColumns = rsmd.getColumnCount(); boolean b = rsmd.isSearchable(1); What is RowSet? or What is the difference between RowSet and ResultSet? or Why do we need RowSet? or What are the advantages of using RowSet over ResultSet? RowSet is a interface that adds support to the JDBC API for the JavaBeans component model. A rowset, which can be used as a JavaBeans component in a visual Bean development environment, can be created and configured at design time and executed at run time. The RowSet interface provides a set of JavaBeans properties that allow a RowSet instance to be configured to connect to a JDBC data source and read some data from the data source. A group of setter methods (setInt, setBytes, setString, and so on) provide a way to pass input parameters to a rowset's command property. This command is the SQL query the rowset uses when it gets its data from a relational database, which is generally the case. Rowsets are easy to use since the RowSet interface extends the standard java.sql.ResultSet interface so it has all the methods of ResultSet. There are two clear advantages of using RowSet over ResultSet RowSet makes it possible to use the ResultSet object as a JavaBeans component. As a consequence, a result set can, for example, be a component in a Swing application. RowSet be used to make a ResultSet object scrollable and updatable. All RowSet objects are by default scrollable and updatable. If the driver and database being used do not support scrolling and/or updating of result sets, an application can populate a RowSet object implementation (e.g. JdbcRowSet) with the data of a ResultSet object and then operate on the RowSet object as if it were the ResultSet object. What is a connected RowSet? or What is the difference between connected RowSet and disconnected RowSet? or Connected vs Disconnected RowSet, which one should I use and when? Connected RowSet A RowSet object may make a connection with a data source and maintain that connection throughout its life cycle, in which case it is called a connected rowset. A rowset may also make a connection with a data source, get data from it, and then close the connection. Such a rowset is called a disconnected rowset. A disconnected rowset may make changes to its data while it is disconnected and then send the changes back to the original source of the data, but it must reestablish a connection to do so. Example of Connected RowSet: A JdbcRowSet object is a example of connected RowSet, which means it continually maintains its connection to a database using a JDBC technology-enabled driver. Disconnected RowSet A disconnected rowset may have a reader (a RowSetReader object) and a writer (a RowSetWriter object) associated with it.
The reader may be implemented in many different ways to populate a rowset with data, including getting data from a non-relational data source. The writer can also be implemented in many different ways to propagate changes made to the rowset's data back to the underlying data source. Example of Disconnected RowSet: A CachedRowSet object is a example of disconnected rowset, which means that it makes use of a connection to its data source only briefly. It connects to its data source while it is reading data to populate itself with rows and again while it is propagating changes back to its underlying data source. The rest of the time, a CachedRowSet object is disconnected, including while its data is being modified. Being disconnected makes a RowSet object much leaner and therefore much easier to pass to another component. For example, a disconnected RowSet object can be serialized and passed over the wire to a thin client such as a personal digital assistant (PDA). What is the benefit of having JdbcRowSet implementation? Why do we need a JdbcRowSet like wrapper around ResultSet? The JdbcRowSet implementation is a wrapper around a ResultSet object that has following advantages over ResultSet This implementation makes it possible to use the ResultSet object as a JavaBeans component. A JdbcRowSet can be used as a JavaBeans component in a visual Bean development environment, can be created and configured at design time and executed at run time. It can be used to make a ResultSet object scrollable and updatable. All RowSet objects are by default scrollable and updatable. If the driver and database being used do not support scrolling and/or updating of result sets, an application can populate a JdbcRowSet object with the data of a ResultSet object and then operate on the JdbcRowSet object as if it were the ResultSet object. Can you think of a questions which is not part of this post? Please don't forget to share it with me in comments section & I will try to include it in the list.
0 notes
Text
SQL for Beginners: Your Gateway to Data Management

Have you ever wondered how websites recall user information, businesses monitor sales patterns, or applications retrieve your login information in seconds? The answer lies in Learning SQL for Beginners, the basic language that powers databases globally. Whether you are an aspiring data analyst, a software developer, or just a database enthusiast, learning SQL can be a game-changer.
What is SQL?
SQL, or Structured Query Language, is a programming language used to communicate with and manipulate databases. SQL is a fundamental part of database management systems since it enables users to perform a number of operations on data in relational databases. SQL databases exist in various types, such as MySQL, PostgreSQL, SQL Server, and SQLite, with differences in features and functionality. These databases offer users the functionality to create, manage, and query data efficiently.
Why Is SQL Essential?
The following are the reasons why understanding SQL is crucial:
Creating New Databases, Tables, and Views: SQL allows you to create and organize data effectively by creating new databases, tables, and views. This first step organizes your data, making it easier to manage and retrieve information whenever you want.
Inserting Records in a Database: In case you have data to store, SQL combines statements like INSERT that allow you to add new records to your tables. This helps in making your database up-to-date with new data.
Updating Records in a Database: SQL provides the ability to update existing records with commands like UPDATE so that your database remains accurate and helpful over time.
Deleting Records from a Database: Sometimes, certain records must be removed in order to keep a neat database. SQL’s DELETE command provides an efficient way of removing unwanted entries from your tables, thereby enhancing data integrity.
Retrieving Data from a Database: The biggest strength of SQL lies in its ability to retrieve data precisely. With the SELECT statement, you can request specific details from your database to promote analysis and reporting.
Applications of SQL
SQL is not just a technical skill but has a wide range of applications in various fields. Below is how SQL is utilized in the real world:
Data Analysis: Organizations utilize SQL to analyze large data, pull out information, and generate reports. Analysts and data scientists can use SQL to query data efficiently, enabling well-informed decision-making that results in business growth.
Web Development: SQL is used by many web applications as a means of communicating with back-end databases. From storing user information to managing content, SQL helps developers make their applications operate smoothly and retrieve data quickly whenever needed.
Customer Relationship Management (CRM): SQL is utilized in CRM applications to store and maintain customer data, interactions, and purchase history. Using SQL, organizations are able to analyze customer behavior, which helps in developing improved relationships.
Healthcare & Medical Records: SQL databases find application in the healthcare sector through hospitals and clinics to maintain patient records, track prescriptions, and manage appointments securely and efficiently. This helps in handling sensitive information in a proper way while enabling healthcare professionals to access important information quickly.
E-commerce & Retail: SQL powers online shopping sites with product inventories, order processing from customers, and personalized recommendations based on user behavior. Such capabilities allow e-commerce businesses to enhance customer experiences and ultimately increase sales.
Explore UniAthena’s SQL Beginner to Advanced Course
This SQL course provides you with an overview of database fundamentals like data, fields, records, and databases. It also covers basic DBMS and RDBMS concepts and the key role of SQL in database management, showcasing the significant role played by it in database management efficiently.
You will also learn about SQL constraints, aggregate functions, join types, stored procedures, views, and indexes. Through the blend of theory and practice, you will become skilled in using the application of functions with queries, database management, and effective handling and manipulation of data with the diverse use of SQL elements.
With a learning duration of just 1–2 weeks, this self-paced course can fit into your schedule. And upon completion, you will get yourself a chance to gain a Blockchain-verified certification, which adds credibility to your skills. If you are looking for the Best Free Online Short Course, this is your chance to upskill. Enroll now.
#learning sql for beginners#sql intermediate course#sql beginner to advanced#Online free learning#Best free Online short courses
0 notes
Text
SafeNet Protocols Package (SPP) project
Still in cardboard boxes...
(Last update : Networks Managers who want to use SPP for security reasons should make sure that every other protocols are only allowed through VM or light sandboxes to do it properly. Attackers may use regular https internet links, in order to fish through e-mail boxes. As every SPP contents are certified, only a regular https website can carry malicious contents. As long as any content provider hasn't been hacked...)
Introduction / initial statement
The goal is not to completely erase https, smtp etc. It is to make a side network where there is no point watching clients.
Brainstorming
Because all contents are legal and certified, and clients can't publish publicly accessible contents on SPP (except if servers can be access by legal authorities). Banish clients tracking from SafeNet and a lot of other details... So, contents providers will have to find other ways to get money using SafeNet protocols. I'm sure they will ... SafeNet anonymous user identities, only known by SafeNet managers. Transitives mail box address ... optional VPN and optional onion-like access features (crypted) ... Integrate firewall with an "allow only SPP" button. We still have to work on softwares updates strategy ... A dedicated OS including virtualisation of other OS and access to regular network only by using a Virtual Machine.
The fact that the goal is to make it useless to track clients doesn't mean it will be immediately the case. The network will probably needs some time to insure that users can't do anything illegal or harmfull before : completely reject legal authorities access to clients or users "useless" data and just shot "everything" down on illegitimate legal requests.
Using only SafeNet on the host reduces risks to get virus as every contents are certified. You still can get a virus by opening a .exe file coming from an e-mail... Or if you still use other protocols on the host machine. A "no .exe or .zip or .vbs or .bat or docm or .dat or files without extensions etc. in e-mails => *allow only ... " policy stays on study. As SPP is not a network made for professional use but for private users. Find a way to allow e-mail boxes safely are a tuff challenge for SPP.
One of the major interest of SPP is that it allow you to watch videos or listen to audio contents with a garanty that you will not be tracked. As it was the case on Hertzien TVs. So, it may save audio/video industry.
SPP network cannot be use for remote access. Legal authorities should be convinced that there is no use of such a thing on a 100% SPP machine and may still use regular networks and protocols.
There also will be a policy about microphones and cameras but I think you get the idear. - Break your phone integrated microphone and use a removable hand-free kit to get a microphone... -
Contents Providers must respect more rules if they want to publish contents using SPP... They also have to financially contribute to SPP management. It's supposed to become a new market. A way to ensure better user experience and rich a new customer base.
The main protocol "shttps" will use same languages as https : html5, css3, JS, PHP, SQL etc. So, porting will be simplified. Developers can simply make a copy of their https website root directory and erase, from files, every stuff that is not allowed on shttps. Or make a completely new website using the same languages.
SPP contracts says that users data collected by contents providers can't be passed to third parts*. Yes, this means contents providers have to do everything by their own and can't sell users data.
*Except for anonymous SPP coordinates and only to deliver the service provided or receive a payment. We still have to work on that too.
SPP policies can evolve to become more permissives, in order to allow needed stuff, or to become more restrictives, in case of any legal flaw observation.
There is also a Public Health dimension to this project. Panem et circences ...
Taking commissions on financial transactions may help to reduce the cost of publication authorization requests.
First SPP e-mail virus
**** Nothing here ! *****
Solution found ! : "E-Mail through SPP" services providers will now have to check every attached contents : check if the extension is allowed as before and at least check if open it doesn't throw any errors, as "file may be corrupt" or stuff like that.
Fantasy statment : Microsoft also add one more safety protocol on .docm files. You now have to complete a puzzle that say "I know that asking peoples to unlock .docm files is a common way to hack a computer !" in order to unlock files.
Pirates strike back
****** Nothing here ! *****
So, we banned .txt files too...
Pirates strike back again
***** Nothing here ! ****
So, E-mail services providers also have to block any message containing scripts command or lines of code, especially batch or VBS. Senders must receive a message indicating that their message has been blocked because "In order to be allowed, your message should not contain .XXXX code lines, even in a simple text field or attached documents". "If you want to send this kind of information to a SPP user, through SPP network (SPPN), you need to become a certified provider and use publicly access documents. Or at least documents made accessible to our bots and Content Watch Offices. Or use an e-mail address certified by the SafeNet Identity Certification Service."
Demonstration : ***** NOTHING HERE ! ******
SafeNet E-mail services
Apps of "E-mail through SPP" service providers must now separate e-mail coming from Certified SafeNet Users from e-mail coming from a regular Internet user. Users are informed that the sender of message coming from uncertified senders may be impossible to identify. So, they should never follow instructions coming from a sender that they are not able to certify.
E-mail clients (apps) can't use nicknames instead of the real sender e-mail address except for the real name of Certified SPP Users.
E-mail services should never make it possible to join a real identity to a SPP anonymous identity. Therefore, SPP users must manage two mailbox address... To avoid errors the same application can't manage both real identities and anonymous identities. Providers can develop two applications that are mostly identical except for a very limited quantity of code lines. In order to make it easier to maintain both apps. Apps logo of both these apps must make it easy to know when you are using your "anonymous" mail box and your official mail box.
As a reminder, SPP Anonymous Identities are still attached to a real person, but only SafeNet Identity Certification Services (SICS) can make links between Real and Anonymous identities.
Anonymous Identities can only receive e-mails from SPP contents providers and cannot send mails. This may evolve if it happen to become essential for providers to get users direct returns. Which means a return whose not using their websites forms.
0 notes
Text
The SQL Server CASE statement is a very effective tool in the SQL Server for adding conditional logic to queries. Let's Explore Deeply:
https://madesimplemssql.com/sql-server-case-statement/
Please follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
OR
Join our Group: https://www.facebook.com/groups/652527240081844

1 note
·
View note
Text
Use of Power Query in Power BI

Power Query in Power BI is a powerful tool used for data transformation and preparation before visualizing the data. It provides an intuitive interface to connect, combine, and refine data from various sources into a coherent, structured dataset ready for analysis. Excel Training in Mumbai often covers how to use Power Query to effectively prepare and transform data. Here's an overview of how Power Query is used in Power BI:
1. Connecting to Data Sources
Importing Data: Power Query can connect to various data sources like Excel files, databases (SQL Server, Oracle, etc.), online services (Azure, SharePoint, etc.), and even web pages.
Multiple Data Sources: You can combine data from multiple sources into a single dataset, which is especially useful when dealing with complex data architectures.
2. Data Transformation
Data Shaping: Power Query allows you to shape your data by removing unnecessary columns, renaming columns, filtering rows, and sorting data.
Data Cleansing: It provides tools to clean your data by handling missing values, removing duplicates, splitting and merging columns, and correcting data types.
Merging and Appending: You can merge (join) tables based on common columns or append (union) tables to create a unified dataset.
Conditional Columns: Power Query enables creating conditional columns based on specific logic, similar to using IF statements in Excel.
3. Advanced Data Manipulation
Grouping and Aggregation: You can group data by specific columns and aggregate data (e.g., summing, averaging) to create summary tables.
Pivoting and Unpivoting: Power Query allows pivoting rows to columns and vice versa, transforming your data into a more suitable structure for analysis.
Custom Columns: Using the M language (Power Query's formula language), you can create custom columns with complex calculations and logic.
4. Data Loading
Load to Data Model: Once the data is transformed, it can be loaded into the Power BI data model, where it can be used for creating reports and visualizations.
Direct Query vs. Import Mode: Power Query supports both Direct Query (where data is queried directly from the source) and Import Mode (where data is imported into Power BI for analysis).
5. Automation and Reusability
Query Dependencies: Power Query automatically tracks dependencies between queries, ensuring that changes in one query reflect in others that depend on it. This feature is crucial for maintaining accurate and up-to-date data models, especially in complex projects.
Reusable Steps: All transformation steps are recorded and can be modified or reused across different queries, ensuring consistency and efficiency. This capability allows users to standardize their data preparation processes and streamline workflows, which is often highlighted in Advanced Excel Classes in Mumbai to help professionals optimize their data management tasks
6. Integration with Other Power BI Features
Parameters: You can create parameters in Power Query that allow dynamic filtering and customization of data sources and queries.
Templates: Power Query transformations can be saved as templates and reused across different Power BI reports or shared with others.
7. Data Profiling
Column Quality and Distribution: Power Query provides tools to profile your data, showing column quality, value distribution, and statistics to help identify data issues early.
Error Handling: It highlights errors and outliers, allowing you to manage and clean data before loading it into the data model.
8. Performance Considerations
Query Folding: Power Query attempts to push data transformations back to the data source (query folding) whenever possible, optimizing performance by reducing the amount of data loaded into Power BI.
Example Use Cases
Sales Data Preparation: Importing sales data from multiple regional Excel files, cleaning it, and consolidating it into a single dataset for analysis.
Web Scraping: Extracting data from a web page, transforming it into a structured format, and using it in a Power BI report.
Data Integration: Combining data from an SQL Server database and a SharePoint list, transforming it, and creating a unified data model for reporting.
Steps to Access Power Query in Power BI
Open Power BI Desktop.
Go to the "Home" tab.
Click on "Transform Data" to open the Power Query Editor.
Use the various tools and options available in the Power Query Editor to connect to data sources, transform data, and prepare it for analysis.
Power Query is essential for anyone looking to perform robust data transformation and preparation in Power BI. It ensures your data is clean, well-structured, and ready for analysis, enabling better insights and decision-making. Learning Power Query is a key part of Advanced Excel Training in Mumbai, as it equips individuals with the skills needed to handle data efficiently and create powerful data models.
For more information, contact us at:
Call: 8750676576, 871076576
Email:[email protected]
Website:www.advancedexcel.net
#Excel Training in Mumbai#Advanced Excel Classes in Mumbai#Advanced Excel Training in Mumbai#advanced excel
0 notes
Text
6 Different Types of Cyber Threats
6 Different Types of Cyber Threats
Table of Contents
What Are Cyber Threats?
Different Types of Cyber Threats
Ransomware
Malware
Phishing & Spam
Internal Threats
Denial-of-Service Attacks
SQL Injection
Key Takeaways
Conclusion
FAQs
What Are Cyber Threats?
Cyber threats refer to the risk of malicious attacks aiming to breach a network, corrupt data, or steal sensitive information. Both individuals and organizations face these threats, which can lead to severe consequences like data breaches or system failures. As cyber threats grow more advanced, it's crucial to implement robust security measures and stay informed about the different types of threats to ensure adequate protection.
Different Types of Cyber Threats
Ransomware
Ransomware is a form of malicious software that blocks users from accessing their systems. Attackers gain control over the system and demand payment, often in cryptocurrencies like Bitcoin, to restore access. Ransomware encrypts files on the infected network, and the decryption key is kept by the cybercriminals. The victim is then required to pay a ransom to regain access to their data.
Protection Tips: To defend against ransomware, focus on prevention. Employ strong security practices, train employees, and establish effective incident response and business continuity plans.
Malware
Malware, short for "malicious software," encompasses various threats like viruses, worms, trojans, spyware, and ransomware. Malware typically infiltrates a system through unreliable links, emails, or downloads. Once inside, it can gather private information, alter or delete data, and compromise system integrity.
Protection Tips: Install and regularly update anti-malware software to add a layer of security. Ensure it scans downloaded files automatically to detect and neutralize potential threats.
Phishing & Spam
Phishing involves attempts to obtain sensitive information by masquerading as a trustworthy entity. Cybercriminals may send emails or texts that seem to come from legitimate sources, urging you to click on malicious links or provide personal data. Spam refers to unsolicited messages, which may also be used for phishing.
Protection Tips: Be cautious of emails that prompt you to click links or open attachments, especially if they ask for personal information. Verify the sender’s authenticity and avoid interacting with suspicious messages.
Internal Threats
Internal threats are posed by individuals within an organization, such as employees, contractors, or former staff, who misuse their access to cause harm. These threats can stem from malicious intent, negligence, or carelessness and can lead to significant financial and reputational damage.
Protection Tips: Cultivate a strong security culture within your organization. Implement access controls, monitor employee activities, and provide regular training to recognize and mitigate potential insider threats.
Denial-of-Service Attacks
Denial-of-Service (DoS) attacks aim to overwhelm a system, server, or network with excessive traffic, causing service disruptions. Distributed Denial-of-Service (DDoS) attacks involve multiple systems working together to launch the attack. These attacks can vary in severity, from minor inconveniences to major financial losses.
Protection Tips: Conduct network vulnerability assessments to identify and address potential weaknesses. Employ multi-layered protection strategies and monitor for signs of attack to mitigate the impact of DoS attacks.
SQL Injection
SQL Injection attacks involve inserting malicious SQL code into a web application’s input fields, which can manipulate or access the database in unintended ways. This technique can expose, modify, or delete data, and in some cases, execute commands on the underlying operating system.
Protection Tips: Use input validation and prepared statements with bind variables to protect against SQL injection. This ensures that only legitimate data is processed and prevents attackers from executing harmful SQL commands.
Key Takeaways
Cyber threats are continually evolving, making it essential to stay informed and adopt robust security measures. Common threats include malware, phishing, DoS attacks, and SQL injections, each requiring specific protective strategies. Employing anti-malware software, practicing vigilance with emails, and implementing strong access controls are crucial steps in defending against these threats.
Conclusion
Protecting yourself from cyber threats involves a proactive approach. Use strong passwords, enable multi-factor authentication, and keep your software up to date. Investing in a comprehensive cybersecurity solution is vital, whether for personal or business use. Effective cybersecurity measures are essential in safeguarding against the growing risks of cyber attacks.
For tailored cybersecurity solutions, consider iBovi Cybersecurity. We offer cost-effective and easy-to-implement services for both individuals and organizations.
CyberSecurity Services | Book Now
FAQs
Q. Are people aware of cybersecurity? While awareness of cybersecurity is increasing, many people are still insufficiently protected. The field of effective cybersecurity is continually evolving.
Q. Are the threats to cybersecurity growing? Yes, cyber threats are becoming more sophisticated and numerous. Reports indicate a rise in external attacks, especially from criminal organizations and foreign entities.
Q. What does a cyberattack cost? In 2020, victims paid approximately $350 million in ransom, a significant increase from previous years. Businesses can face losses of up to $600 billion due to cybercrime, according to reports.
Q. How should you respond to a potential phishing email? Verify the sender’s identity and avoid clicking on links or opening attachments from unknown sources. If suspicious, report and delete the email. Contact the organization directly using verified contact information, not the details provided in the email.
0 notes
Text
Mastering PHP: The Ultimate Guide for Aspiring Expert PHP Developers

Introduction
Welcome to CompleteGurus, your go-to resource for all things tech! Today, we’re diving into the world of PHP development. Whether you’re a novice just starting out or an experienced coder looking to level up, becoming an expert PHP developer requires dedication, continuous learning, and practical experience. Let’s explore the roadmap to mastering PHP and the essential skills every expert PHP developer should have. #expertPHPdeveloper
Understanding the Basics
What is PHP?
PHP (Hypertext Preprocessor) is a widely-used, open-source scripting language designed for web development. It’s embedded in HTML and is known for its efficiency in handling dynamic content, databases, and session tracking.
Why PHP?
Ease of Use: PHP’s syntax is easy to understand and learn, making it a favorite among beginners.
Community Support: A large, active community provides extensive resources, frameworks, and libraries.
Compatibility: PHP is compatible with various servers and databases, including Apache, Nginx, MySQL, and PostgreSQL.
Performance: PHP is fast and efficient, especially when it comes to handling server-side scripting.
Building a Strong Foundation
Learning the Language
To become an expert, you must have a thorough understanding of PHP’s syntax, functions, and features. Here are some key areas to focus on:
Variables and Data Types: Understand how to declare and use different data types.
Control Structures: Master if-else statements, switch cases, loops (for, while, foreach).
Functions: Learn to create and use functions, including variable scope and anonymous functions.
Arrays and Strings: Work extensively with arrays (indexed, associative, multidimensional) and string manipulation functions.
Object-Oriented Programming (OOP)
OOP is a critical aspect of advanced PHP development. Ensure you understand the following concepts:
Classes and Objects: Learn how to define and instantiate classes.
Inheritance: Understand how child classes inherit properties and methods from parent classes.
Encapsulation: Learn to protect the state of an object using access modifiers.
Polymorphism: Understand how objects can take on many forms through interfaces and abstract classes.
Advanced PHP Development
Frameworks
To streamline development and maintain code quality, familiarize yourself with popular PHP frameworks:
Laravel: Known for its elegant syntax and powerful features, Laravel is a favorite among developers.
Symfony: Offers a robust set of reusable PHP components and a modular architecture.
CodeIgniter: Lightweight and straightforward, ideal for small to medium projects.
Working with Databases
An expert PHP developer must be proficient in database management:
SQL: Master SQL queries to interact with databases.
PDO and MySQLi: Learn to use PHP Data Objects (PDO) and MySQLi for secure and efficient database operations.
ORM: Understand Object-Relational Mapping (ORM) with tools like Eloquent in Laravel.
Security Practices
Security is paramount in web development. Ensure you follow best practices:
Data Sanitization and Validation: Always sanitize and validate user inputs.
Prepared Statements: Use prepared statements to prevent SQL injection.
Password Hashing: Securely store passwords using hashing algorithms like bcrypt.
HTTPS: Ensure secure data transmission by implementing HTTPS.
Testing and Debugging
Quality assurance is essential. Learn to:
Unit Testing: Write unit tests to ensure code reliability using PHPUnit.
Debugging: Use debugging tools and techniques to identify and fix issues.
Version Control: Use Git for version control and collaboration.
Continuous Learning and Community Engagement
Stay Updated
The tech world evolves rapidly. Stay ahead by:
Reading Blogs: Follow blogs and forums like CompleteGurus, PHP.net, and Stack Overflow.
Attending Conferences: Participate in PHP conferences and meetups.
Taking Courses: Enroll in advanced PHP courses on platforms like Udemy, Coursera, and LinkedIn Learning.
Contribute to the Community
Open Source Projects: Contribute to open-source projects to gain real-world experience.
Writing and Speaking: Share your knowledge through blogging, speaking at events, or creating tutorials.
Networking: Connect with other developers, join PHP groups, and participate in discussions.
Conclusion
Becoming an expert PHP developer is a journey that involves mastering the language, understanding advanced concepts, and continuously learning. By following this roadmap and engaging with the community, you'll hone your skills and stay at the forefront of PHP development. Ready to take the next step? Dive into the resources available here at CompleteGurus and embark on your path to becoming an #expertPHPdeveloper!
0 notes
Text
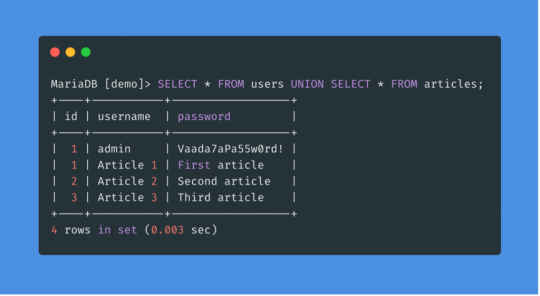
How to test app for the SQL injection

During code review
Check for any queries to the database are not done via prepared statements.
If dynamic statements are being made please check if the data is sanitized before used as part of the statement.
Auditors should always look for uses of sp_execute, execute or exec within SQL Server stored procedures. Similar audit guidelines are necessary for similar functions for other vendors.
Automated Exploitation
Most of the situation and techniques on testing an app for SQLi can be performed in a automated way using some tools (e.g. perform an automated auditing using SQLMap)
Equally Static Code Analysis Data flow rules can detect of unsanitised user controlled input can change the SQL query.
Stored Procedure Injection
When using dynamic SQL within a stored procedure, the application must properly sanitise the user input to eliminate the risk of code injection. If not sanitised, the user could enter malicious SQL that will be executed within the stored procedure.
Time delay Exploitation technique
The time delay exploitation technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. This technique consists in sending an injected query and in case the conditional is true, the tester can monitor the time taken to for the server to respond. If there is a delay, the tester can assume the result of the conditional query is true. This exploitation technique can be different from DBMS to DBMS.
http://www.example.com/product.php?id=10 AND IF(version() like '5%', sleep(10), 'false'))--
In this example the tester is checking whether the MySql version is 5.x or not, making the server delay the answer by 10 seconds. The tester can increase the delay time and monitor the responses. The tester also doesn't need to wait for the response. Sometimes they can set a very high value (e.g. 100) and cancel the request after some seconds.
Out-of-band Exploitation technique
This technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. The technique consists of the use of DBMS functions to perform an out of band connection and deliver the results of the injected query as part of the request to the tester's server. Like the error based techniques, each DBMS has its own functions. Check for specific DBMS section.
4 notes
·
View notes
Text
How can I connect an HTML page to multiple tables from a database?
To connect an HTML page to multiple tables from a database, you typically use a server-side scripting language like PHP or Node.js along with a database management system like MySQL or PostgreSQL. Here's a general outline of the process:
Set up your database: Create the necessary tables in your database to store the data you want to display on your HTML page. Ensure that the tables are properly structured and contain the relevant data.
Write server-side code: Use a server-side scripting language such as PHP or Node.js to query the database and retrieve the data from the multiple tables. You'll need to write SQL queries to fetch the data you need from each table.
Format the data: Once you've retrieved the data from the database, format it in a way that can be easily displayed on your HTML page. This might involve organizing the data into arrays or objects, depending on your programming language.
Generate HTML content: Use the formatted data to dynamically generate HTML content that will be rendered in the user's browser. This could involve using loops or conditional statements to iterate over the data and create HTML elements such as tables, lists, or cards.
Display the HTML page: Serve the HTML page to the user's browser using your server-side code. The user will then be able to view the data from the multiple tables in their web browser.
Remember to handle any errors or edge cases that may arise during the database query process, and ensure that your server-side code is secure against SQL injection attacks. Additionally, consider implementing pagination or filtering options if you're dealing with large datasets to improve performance and user experience.
0 notes
Text
Mastering Dynamic SQL in SQL Server: Unleashing the Power of Flexibility
Introduction Dynamic SQL is a powerful technique in SQL Server that allows you to construct and execute SQL statements dynamically at runtime. It provides flexibility and enables you to create queries based on user input or variable conditions. In this article, we’ll explore practical examples and applications of dynamic SQL in T-SQL. Building Dynamic Queries One common use case for dynamic…

View On WordPress
0 notes
Text
What are Power BI Paginated Reports?
Power BI Paginated Reports, formerly known as SQL Server Reporting Services (SSRS), are a type of reporting solution offered by Microsoft Power BI that are designed for producing pixel-perfect, print-ready reports with precise control over layout and formatting.
Unlike Power BI interactive reports, which are optimized for exploring and analyzing data interactively, paginated reports are intended for fixed-layout, paper-oriented reporting scenarios where consistency, pagination, and high-fidelity rendering are paramount.
Power BI Paginated Reports provide a flexible and powerful solution for producing pixel-perfect, print-ready reports with precise control over layout, formatting, and data presentation. Apart from it by obtaining Power BI Training, you can advance your career in Power BI. With this course, you can demonstrate your expertise in Power BI Desktop, Architecture, DAX, Service, Mobile Apps, Reports, and many more.
Key features of Power BI Paginated Reports include:
Pixel-Perfect Layout: Paginated reports enable precise control over layout and formatting, allowing users to design reports with exact specifications for page size, margins, headers, footers, and grid alignment. This level of control ensures that reports maintain a consistent appearance across different devices and mediums, making them suitable for printing or exporting to PDF.
Tabular Data Presentation: Paginated reports excel at presenting tabular data in a structured format, making them ideal for traditional reporting needs such as financial statements, invoices, inventory reports, and regulatory compliance reports. Users can organize data into tables, matrices, and lists, with options for grouping, sorting, and aggregating data as needed.
Rich Formatting Options: Power BI Paginated Reports offer a wide range of formatting options to enhance the visual presentation of data, including font styles, colors, borders, backgrounds, and conditional formatting rules. Users can customize the appearance of report elements such as textboxes, tables, charts, and images to meet specific design requirements and branding guidelines.
Advanced Charting and Graphing: While paginated reports are primarily focused on tabular data presentation, they also support basic charting and graphing capabilities for visualizing data trends and patterns. Users can create charts, graphs, and gauges to complement tabular data and provide additional context to report consumers.
Parameterization and Interactivity: Paginated reports support parameterization, allowing users to define parameters that enable dynamic filtering, sorting, and grouping of data at runtime. Parameterized reports enhance interactivity and flexibility, enabling report consumers to customize views and drill down into specific subsets of data based on their preferences or requirements.
Data Connectivity: Paginated reports can connect to a variety of data sources, including relational databases, multidimensional databases, data warehouses, and cloud services, using industry-standard data access protocols such as ODBC, OLE DB, and XML. This enables users to retrieve and integrate data from diverse sources into their reports, ensuring comprehensive data coverage and accuracy.
Subscription and Distribution: Power BI Paginated Reports support subscription and distribution capabilities, allowing users to schedule report execution and delivery to specific recipients via email, file share, or SharePoint document library. Scheduled reports can be delivered in various formats, including PDF, Excel, CSV, and XML, to accommodate different consumption preferences and use cases.
Security and Compliance: Paginated reports adhere to enterprise-grade security and compliance standards, ensuring data privacy, confidentiality, and integrity. Users can implement role-based access control (RBAC), data encryption, audit logging, and other security features to protect sensitive information and comply with regulatory requirements such as GDPR, HIPAA, and SOX.
In summary, By combining advanced features such as pixel-perfect layout, tabular data presentation, rich formatting options, parameterization, data connectivity, subscription and distribution, and security and compliance, paginated reports enable organizations to deliver high-quality, actionable insights to stakeholders and decision-makers, driving informed decision-making and driving business value.
0 notes
Text
How to use MySQL Transaction with PHP

Transaction means to complete several actions of a group without any interruption and if something wrong happens then revert everything to the initial stage.
In SQL, successful transaction means that all SQL statements has been executed successfully. If any error occurs, then the data should be a rollback to avoid data inconsistency.
The transaction will not complete unless all operations of that transaction successfully completes, if any, of the operation fails it mean complete transaction fails.
Real Life Example:
If you do a transaction of transferring money from one bank to another, at the time if some interruption occur due to internet/server or other issue, then at that time the transaction will rollback to its initial stage and you get your money refunded to your account successfully.
Transactions Properties :
There are 4 standard properties :
A) Atomicity : This rollbacks the transaction in case of any failure, so the transaction will be “all or nothing”. B) Consistency : It ensures that data is successfully updated of all stages after successful commit. C) Isolation : It ensures that the effects of an incomplete transaction should not even be visible to another transaction. Concurrent execution means that transactions were executed sequentially, means one after the other. Providing isolation is the main goal of concurrency control . D) Durability : It ensures that results are stored permanently once transaction is committed successfully even if power loss, crashes occurs .
Overview of try & catch block:
‘try’ block will be executed at that time when each query written in try block executed successfully, if any, of the query does not work properly then catch block execute and all the transactions will be rollback.
try { // A set of queries; if one fails, an exception should be thrown $conn->query(‘CREATE TABLE customer(id int, name varchar(255), amount int)’); $conn->query(‘INSERT INTO customer VALUES(1,’Customer Name’,10000)’); } catch (Exception $e) { }
MySQL transaction in PHP?
1) Make a connection with database by using PHP
$conn = mysqli_connect("localhost", "my_user", "my_password", "dabasename");
2) Check if connection is not established successfully
if (mysqli_connect_errno()) { printf("Connect failed: %s\n", mysqli_connect_error()); exit(); }
3) Start the transaction by using beginTransaction() method in try block
try { // First of all, let's begin a transaction $conn->beginTransaction(); // A set of queries; if one fails, an exception should be thrown $conn->query('CREATE TABLE customer(id int, name varchar(255), amount int)'); $conn->query('INSERT INTO customer VALUES(1,' Customer Name'',10000)'); } catch (Exception $e) { }
4) Write SQL query after beginTransaction() method and after execution of SQL query commit() method call in try block
try { // First of all, let's begin a transaction $conn->beginTransaction(); // A set of queries; if one fails, an exception should be thrown $conn->query('CREATE TABLE customer(id int, name varchar(255), amount int)'); $conn->query('INSERT INTO customer VALUES(1,' Customer Name'',10000)'); // If we arrive here, it means that no exception was thrown // i.e. no query has failed, and we can commit the transaction $conn->commit(); } catch (Exception $e) { }
5) If try block doesn’t execute successfully then the transaction will be rollback in catch block by calling rollBack() method
try { // First of all, let's begin a transaction $conn->beginTransaction(); // A set of queries; if one fails, an exception should be thrown $conn->query('CREATE TABLE customer(id int, name varchar(255), amount int)'); $conn->query('INSERT INTO customer (id,name,amount) VALUES(1,' Customer Name'',10000)'); // If we arrive here, it means that no exception was thrown // i.e. no query has failed, and we can commit the transaction $conn->commit(); } catch (Exception $e) { // An exception has been thrown // We must rollback the transaction $conn->rollback(); }
MYSQL TRANSACTION in CAKEPHP 3.0 :
The most basic way of doing transactions is through the begin(), commit() and rollback() methods,
$conn->begin(); $conn->execute('UPDATE table SET status = ? WHERE id = ?', [true, 2]); $conn->execute('UPDATE table SET status = ? WHERE id = ?', [false, 4]); $conn->commit();
Hope you enjoyed this article and learned basic knowledge of MySQL TRANSACTIONS. If you need any help in implementing TRANSACTIONS in your web development project, then mail us , our coding expert team will help you to give best services.
This post originally appeared on Ficode website, and we republished with permission from the author. Read the full piece here.
0 notes