#managing SQL data
Explore tagged Tumblr posts
Text
Using CASE Statements for Conditional Logic in SQL Server like IF THEN
In SQL Server, you can use the CASE statement to perform IF…THEN logic within a SELECT statement. The CASE statement evaluates a list of conditions and returns one of multiple possible result expressions. Here’s the basic syntax for using a CASE statement: SELECT column1, column2, CASE WHEN condition1 THEN result1 WHEN condition2 THEN result2 ... ELSE default_result END AS…
View On WordPress
#conditional SELECT SQL#dynamic SQL queries#managing SQL data#SQL Server CASE statement#SQL Server tips
0 notes
Text
What Are the Qualifications for a Data Scientist?
In today's data-driven world, the role of a data scientist has become one of the most coveted career paths. With businesses relying on data for decision-making, understanding customer behavior, and improving products, the demand for skilled professionals who can analyze, interpret, and extract value from data is at an all-time high. If you're wondering what qualifications are needed to become a successful data scientist, how DataCouncil can help you get there, and why a data science course in Pune is a great option, this blog has the answers.
The Key Qualifications for a Data Scientist
To succeed as a data scientist, a mix of technical skills, education, and hands-on experience is essential. Here are the core qualifications required:
1. Educational Background
A strong foundation in mathematics, statistics, or computer science is typically expected. Most data scientists hold at least a bachelor’s degree in one of these fields, with many pursuing higher education such as a master's or a Ph.D. A data science course in Pune with DataCouncil can bridge this gap, offering the academic and practical knowledge required for a strong start in the industry.
2. Proficiency in Programming Languages
Programming is at the heart of data science. You need to be comfortable with languages like Python, R, and SQL, which are widely used for data analysis, machine learning, and database management. A comprehensive data science course in Pune will teach these programming skills from scratch, ensuring you become proficient in coding for data science tasks.
3. Understanding of Machine Learning
Data scientists must have a solid grasp of machine learning techniques and algorithms such as regression, clustering, and decision trees. By enrolling in a DataCouncil course, you'll learn how to implement machine learning models to analyze data and make predictions, an essential qualification for landing a data science job.
4. Data Wrangling Skills
Raw data is often messy and unstructured, and a good data scientist needs to be adept at cleaning and processing data before it can be analyzed. DataCouncil's data science course in Pune includes practical training in tools like Pandas and Numpy for effective data wrangling, helping you develop a strong skill set in this critical area.
5. Statistical Knowledge
Statistical analysis forms the backbone of data science. Knowledge of probability, hypothesis testing, and statistical modeling allows data scientists to draw meaningful insights from data. A structured data science course in Pune offers the theoretical and practical aspects of statistics required to excel.
6. Communication and Data Visualization Skills
Being able to explain your findings in a clear and concise manner is crucial. Data scientists often need to communicate with non-technical stakeholders, making tools like Tableau, Power BI, and Matplotlib essential for creating insightful visualizations. DataCouncil’s data science course in Pune includes modules on data visualization, which can help you present data in a way that’s easy to understand.
7. Domain Knowledge
Apart from technical skills, understanding the industry you work in is a major asset. Whether it’s healthcare, finance, or e-commerce, knowing how data applies within your industry will set you apart from the competition. DataCouncil's data science course in Pune is designed to offer case studies from multiple industries, helping students gain domain-specific insights.
Why Choose DataCouncil for a Data Science Course in Pune?
If you're looking to build a successful career as a data scientist, enrolling in a data science course in Pune with DataCouncil can be your first step toward reaching your goals. Here’s why DataCouncil is the ideal choice:
Comprehensive Curriculum: The course covers everything from the basics of data science to advanced machine learning techniques.
Hands-On Projects: You'll work on real-world projects that mimic the challenges faced by data scientists in various industries.
Experienced Faculty: Learn from industry professionals who have years of experience in data science and analytics.
100% Placement Support: DataCouncil provides job assistance to help you land a data science job in Pune or anywhere else, making it a great investment in your future.
Flexible Learning Options: With both weekday and weekend batches, DataCouncil ensures that you can learn at your own pace without compromising your current commitments.
Conclusion
Becoming a data scientist requires a combination of technical expertise, analytical skills, and industry knowledge. By enrolling in a data science course in Pune with DataCouncil, you can gain all the qualifications you need to thrive in this exciting field. Whether you're a fresher looking to start your career or a professional wanting to upskill, this course will equip you with the knowledge, skills, and practical experience to succeed as a data scientist.
Explore DataCouncil’s offerings today and take the first step toward unlocking a rewarding career in data science! Looking for the best data science course in Pune? DataCouncil offers comprehensive data science classes in Pune, designed to equip you with the skills to excel in this booming field. Our data science course in Pune covers everything from data analysis to machine learning, with competitive data science course fees in Pune. We provide job-oriented programs, making us the best institute for data science in Pune with placement support. Explore online data science training in Pune and take your career to new heights!
#In today's data-driven world#the role of a data scientist has become one of the most coveted career paths. With businesses relying on data for decision-making#understanding customer behavior#and improving products#the demand for skilled professionals who can analyze#interpret#and extract value from data is at an all-time high. If you're wondering what qualifications are needed to become a successful data scientis#how DataCouncil can help you get there#and why a data science course in Pune is a great option#this blog has the answers.#The Key Qualifications for a Data Scientist#To succeed as a data scientist#a mix of technical skills#education#and hands-on experience is essential. Here are the core qualifications required:#1. Educational Background#A strong foundation in mathematics#statistics#or computer science is typically expected. Most data scientists hold at least a bachelor’s degree in one of these fields#with many pursuing higher education such as a master's or a Ph.D. A data science course in Pune with DataCouncil can bridge this gap#offering the academic and practical knowledge required for a strong start in the industry.#2. Proficiency in Programming Languages#Programming is at the heart of data science. You need to be comfortable with languages like Python#R#and SQL#which are widely used for data analysis#machine learning#and database management. A comprehensive data science course in Pune will teach these programming skills from scratch#ensuring you become proficient in coding for data science tasks.#3. Understanding of Machine Learning
3 notes
·
View notes
Text
Best Diploma Courses for a Future-Proof Career in 2025
The job market is constantly evolving, and staying ahead requires the right skills and certifications. If you're looking for the best diploma courses to secure your future, you're already on the right path!
With so many career options, choosing the right course can feel overwhelming. But don’t worry—we've curated a list of high-demand free online courses that can give you a competitive edge. These diploma programs cover diverse industries, from healthcare to data analytics and logistics to HR management.

Which Diploma Course is Best for the Future?
Whether you're fresh out of school or considering a career switch, selecting the right diploma course is a crucial step. You might be asking yourself:
What if the course isn’t the right fit?
What if I invest my time and regret it later?
That’s why we’ve compiled a list of free-to-learn online diploma courses so you can explore your options without financial risk. Let’s dive in!
Diploma Certificate in Environment Health and Safety Management
Workplace safety and environmental management are crucial for businesses worldwide. A Diploma Certificate in Environment Health and Safety Management equips you with the skills to identify hazards and implement safety protocols across industries.
Career Opportunities:
Industrial Hygienist
Environmental Health & Safety Officer
Food Safety Inspector
Toxicologist
Soil Analyst
Healthcare Management Diploma
The healthcare industry isn’t just about doctors and nurses—it requires skilled administrators and managers to ensure efficient operations. A Healthcare Management Diploma can open doors to rewarding roles in healthcare facilities, pharmaceuticals, and insurance firms.
Career Opportunities:
Healthcare Administrator
Clinic Manager
Health Information Manager
Pharmaceutical Administrator
Healthcare HR Manager
Diploma in International Human Resource Management
HR professionals play a critical role in building successful businesses. A Diploma in International Human Resource Management provides insights into global HR practices, talent acquisition, and organizational behavior.
Career Opportunities:
Recruitment Coordinator
Payroll Specialist
HR Analyst
Training Coordinator
Diploma in SQL: Beginner to Advanced Levels
SQL is the backbone of data management. A Diploma in SQL will teach you how to manage, retrieve, and manipulate data—essential skills for roles in IT, cybersecurity, and data science.
Career Opportunities:
SQL Developer
Data Engineer
Business Intelligence Analyst
QA Tester
Diploma in Data Analytics
Data drives modern business decisions. A Diploma in Data Analytics provides hands-on experience with data visualization, predictive analytics, and statistical modeling.
Career Opportunities:
Data Scientist
Business Analyst
Marketing Analytics Manager
Financial Analyst
Diploma Course in Transportation and Logistics Management
Efficient supply chains keep the world moving. A Diploma Course in Transportation and Logistics Management teaches supply chain dynamics, international shipping, and warehouse management.
Career Opportunities:
Logistics Manager
Inventory Manager
International Logistics Coordinator
Transportation Planner
Diploma in Supply Chain Management
For those looking to take logistics expertise to the next level, a Diploma in Supply Chain Management covers procurement strategies, ERP systems, and inventory optimization.
Career Opportunities:
Supply Chain Manager
Operations Manager
Materials Manager
Procurement Specialist
Why These Courses Matter for Nigeria’s Job Market
Nigeria’s job market is rapidly evolving, with increasing demand for professionals in healthcare, logistics, and technology. These diploma programs can give Nigerian students and professionals a competitive advantage in the global workforce.
Key Benefits:
Growing industries such as healthcare, tech, and logistics require skilled professionals.
Many multinational companies in Nigeria prefer candidates with specialized certifications.
Online learning makes it accessible for students and working professionals.
By enrolling in these free online courses, you can gain globally recognized certifications from platforms like UniAthena, enhancing your career prospects.
Conclusion
These best diploma courses equip you with essential skills to advance your career—all without financial barriers. Whether you’re passionate about healthcare, human resources, data analytics, or supply chain management, these programs offer a flexible and accessible way to gain industry-relevant expertise.
With globally recognized certifications, you can enhance your resume, boost your employability, and stay competitive in today’s job market. Plus, since these free online courses are self-paced, you can learn at your convenience. Take the first step toward a brighter future—explore these diploma courses, acquire valuable skills, and unlock exciting career opportunities today!
Bonus Points:
Try these free-to-learn diplomas before committing to a full degree.
Gain extra credentials to boost your resume as a fresher.
Most courses can be completed within two weeks!
Open to learners from all backgrounds, no prior experience required.
So, what are you waiting for? Pick a diploma course that aligns with your goals and take the first step toward a successful career today!
#Best Diploma Courses#Free Online Courses#Diploma Certificate in Environment Health and Safety Management#Healthcare Management Diploma#Diploma in International Human Resource Management#Diploma in SQL#Diploma in Data Analytics#Diploma Course in Transportation and Logistics Management#Diploma in Supply Chain Management#UniAthena#Free to Learn
1 note
·
View note
Text
🚀 Struggling to balance transactional (OLTP) & analytical (OLAP) workloads? Microsoft Fabric SQL Database is the game-changer! In this blog, I’ll share best practices, pitfalls to avoid, and optimization tips to help you master Fabric SQL DB. Let’s dive in! 💡💬 #MicrosoftFabric #SQL
#Data management#Database Benefits#Database Optimization#Database Tips#Developer-Friendly#Fabric SQL Database#Microsoft Fabric#SQL database#SQL Performance#Transactional Workloads#Unlock SQL Potential
0 notes
Text
SQL & Power BI Certification | MITSDE
Enhance your career with MITSDE’s Online Power BI Certification Course! This comprehensive program equips you with essential skills in data visualization, analytics, and business intelligence, helping you make data-driven decisions. Learn to create interactive dashboards, generate insightful reports, and analyze business trends effectively. Designed for professionals and beginners alike, this course offers hands-on training and expert guidance to boost your expertise. Stay ahead in the competitive job market—enroll today and transform your data analysis skills with Power BI!
#SQL & Power BI Certification Program#Power BI Certification#powerbi course#MITSDE#Data management#Data visualization#Data Specialist#Data manipulation#Data analytics#Business intelligence#Power BI Course
0 notes
Text

Alarm Management Software
#Alarm Management Application#Alarm Management Software#Industrial Alarm Management Application#Industrial Alarm by SMS#OPC Alarm by SMS#OPC alarm notification software#MSSQL Backup Utility#SQL Server Backup#SQL Backup and Restore Utility#MSSQL Data Truncate#Data Backup and Restore#Database Backup#Database Backup and Restore Utility#opc alarms by SMS applications Alarms by SMS#sql alarms by SMS application#Digital Alarms by SMS#digital alarms by SMS application#Analog Alarms by SMS#analog alarms by SMS application#SMS Alarm SCADA#SMS Alarm SCADA system
0 notes
Text
Learn SQL Easily with Takeoff Upskill and Build Your Data Skills
SQL (Structured Query Language) is one of the most important skills for anyone working with data. At Takeoff Upskill, we offer a comprehensive SQL course that makes learning this valuable skill easy and accessible. Whether you are a beginner or someone looking to enhance your database knowledge, this course is designed to meet your needs.

Our SQL course starts with the basics, such as understanding databases, tables, and data types. You will learn how to create, read, update, and delete data using SQL commands. The course also covers advanced topics like joining multiple tables, writing complex queries, and optimizing database performance. These skills are essential for roles like data analyst, software developer, and database administrator.
The training at Takeoff Upskill is practical and hands-on. We provide real-world examples and exercises that help you understand how SQL is used in businesses. By the end of the course, you will be confident in writing queries, managing data, and solving database challenges. Our experienced trainers guide you every step of the way, ensuring you gain a strong foundation.
#SQL course#SQL training#data management#Takeoff Upskill#SQL for beginners#learn SQL#database queries#SQL skills
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Database Watcher: Monitoring for Azure SQL
Introduction If you’re running mission-critical workloads on Azure SQL Database or Managed Instance, reliable performance monitoring is a must. But deploying monitoring infrastructure and wrangling telemetry data can be complex and time-consuming. Wouldn’t it be great if you could enable in-depth SQL monitoring with just a few clicks and have all the key metrics at your fingertips? Now you…
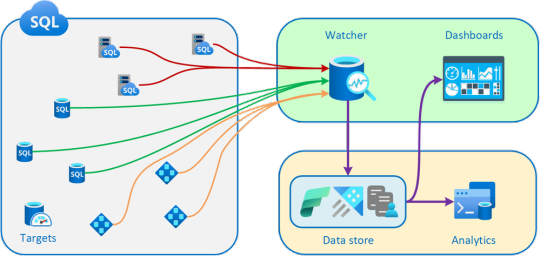
View On WordPress
0 notes
Text
youtube
#ntelligent Lookup#Database Views#Data Retrieval#Data Presentation#Database Optimization#Data Analysis#Database Relationships#Data Visualization#Database Tutorial#Query Optimization#Data Enhancement#Database Management#SQL Views#Data Integration#Related Tables#Youtube
0 notes
Text
Unlocking Your Future: How to Become an SQL Engineer at Top Tech Companies
As a college student with aspirations of landing your dream job at a top tech giant company, becoming an SQL Engineer can open the doors to a data-driven and fulfilling career. SQL (Structured Query Language) is an essential skill in the tech industry, enabling professionals to manage and analyze vast amounts of data efficiently. In this comprehensive guide, we will explore the key steps to…

View On WordPress
#Advanced SQL Techniques#Certifications#Data Analysis#Data Visualization#Database Management#Database Management Systems#Hands-On Projects#Interview Preparation#lifelong learning#Networking#Online Courses#Online Presence#SQL Basics#SQL Engineer#Tech Career#Tech Jobs
0 notes
Text
Unlock Data Governance: Revolutionary Table-Level Access in Modern Platforms
Dive into our latest blog on mastering data governance with Microsoft Fabric & Databricks. Discover key strategies for robust table-level access control and secure your enterprise's data. A must-read for IT pros! #DataGovernance #Security
View On WordPress
#Access Control#Azure Databricks#Big data analytics#Cloud Data Services#Data Access Patterns#Data Compliance#Data Governance#Data Lake Storage#Data Management Best Practices#Data Privacy#Data Security#Enterprise Data Management#Lakehouse Architecture#Microsoft Fabric#pyspark#Role-Based Access Control#Sensitive Data Protection#SQL Data Access#Table-Level Security
0 notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text

Alarm Management Application
#Alarm Management Application#Alarm Management Software#Industrial Alarm Management Application#Industrial Alarm by SMS#OPC Alarm by SMS#OPC alarm notification software#opc alarms by SMS applications Alarms by SMS#MSSQL Backup Utility#SQL Server Backup#SQL Backup and Restore Utility#MSSQL Data Truncate#Data Backup and Restore#Database Backup#Database Backup and Restore Utility#sql alarms by SMS application#Digital Alarms by SMS#digital alarms by SMS application#Analog Alarms by SMS#analog alarms by SMS application#SMS Alarm SCADA
0 notes
Text
Which coding languages should I learn to boost my IT career opportunities?
A career in IT needs a mix of versatile programming languages. Here are some of the most essential ones:

Python – Easy to learn and widely used for data science, machine learning, web development, and automation.
JavaScript – Key for web development, allowing interactive websites and backend work with frameworks like Node.js.
Java – Known for stability, popular for Android apps, enterprise software, and backend development.
C++ – Great for systems programming, game development, and areas needing high performance.
SQL – Essential for managing and querying databases, crucial for data-driven roles.
C# – Common in enterprise environments and used in game development, especially with Unity.
24 notes
·
View notes