#SafeNet
Explore tagged Tumblr posts
Text
SAFEnet : Pemblokiran archive.org Melanggar HAM Dan Hak Akses Informasi Masyarakat
ranjana.id – Kementerian Komunikasi dan Digital (Komdigi) melakukan pemblokiran situs archive.org pada Selasa 27/5/2025. Situs archive.org yang merupakan situs arsip internet perpustakaan digital raksasa yang menyimpan memori internet yang didedikasikan untuk pelestarian digital dan penyediaan akses universal terhadap semua pengetahuan. Situs ini diblokir secara tiba-tiba oleh pemerintah melalui…
0 notes
Text
SafeNet Protocols Package (SPP) project
Still in cardboard boxes...
(Last update : Networks Managers who want to use SPP for security reasons should make sure that every other protocols are only allowed through VM or light sandboxes to do it properly. Attackers may use regular https internet links, in order to fish through e-mail boxes. As every SPP contents are certified, only a regular https website can carry malicious contents. As long as any content provider hasn't been hacked...)
Introduction / initial statement
The goal is not to completely erase https, smtp etc. It is to make a side network where there is no point watching clients.
Brainstorming
Because all contents are legal and certified, and clients can't publish publicly accessible contents on SPP (except if servers can be access by legal authorities). Banish clients tracking from SafeNet and a lot of other details... So, contents providers will have to find other ways to get money using SafeNet protocols. I'm sure they will ... SafeNet anonymous user identities, only known by SafeNet managers. Transitives mail box address ... optional VPN and optional onion-like access features (crypted) ... Integrate firewall with an "allow only SPP" button. We still have to work on softwares updates strategy ... A dedicated OS including virtualisation of other OS and access to regular network only by using a Virtual Machine.
The fact that the goal is to make it useless to track clients doesn't mean it will be immediately the case. The network will probably needs some time to insure that users can't do anything illegal or harmfull before : completely reject legal authorities access to clients or users "useless" data and just shot "everything" down on illegitimate legal requests.
Using only SafeNet on the host reduces risks to get virus as every contents are certified. You still can get a virus by opening a .exe file coming from an e-mail... Or if you still use other protocols on the host machine. A "no .exe or .zip or .vbs or .bat or docm or .dat or files without extensions etc. in e-mails => *allow only ... " policy stays on study. As SPP is not a network made for professional use but for private users. Find a way to allow e-mail boxes safely are a tuff challenge for SPP.
One of the major interest of SPP is that it allow you to watch videos or listen to audio contents with a garanty that you will not be tracked. As it was the case on Hertzien TVs. So, it may save audio/video industry.
SPP network cannot be use for remote access. Legal authorities should be convinced that there is no use of such a thing on a 100% SPP machine and may still use regular networks and protocols.
There also will be a policy about microphones and cameras but I think you get the idear. - Break your phone integrated microphone and use a removable hand-free kit to get a microphone... -
Contents Providers must respect more rules if they want to publish contents using SPP... They also have to financially contribute to SPP management. It's supposed to become a new market. A way to ensure better user experience and rich a new customer base.
The main protocol "shttps" will use same languages as https : html5, css3, JS, PHP, SQL etc. So, porting will be simplified. Developers can simply make a copy of their https website root directory and erase, from files, every stuff that is not allowed on shttps. Or make a completely new website using the same languages.
SPP contracts says that users data collected by contents providers can't be passed to third parts*. Yes, this means contents providers have to do everything by their own and can't sell users data.
*Except for anonymous SPP coordinates and only to deliver the service provided or receive a payment. We still have to work on that too.
SPP policies can evolve to become more permissives, in order to allow needed stuff, or to become more restrictives, in case of any legal flaw observation.
There is also a Public Health dimension to this project. Panem et circences ...
Taking commissions on financial transactions may help to reduce the cost of publication authorization requests.
First SPP e-mail virus
**** Nothing here ! *****
Solution found ! : "E-Mail through SPP" services providers will now have to check every attached contents : check if the extension is allowed as before and at least check if open it doesn't throw any errors, as "file may be corrupt" or stuff like that.
Fantasy statment : Microsoft also add one more safety protocol on .docm files. You now have to complete a puzzle that say "I know that asking peoples to unlock .docm files is a common way to hack a computer !" in order to unlock files.
Pirates strike back
****** Nothing here ! *****
So, we banned .txt files too...
Pirates strike back again
***** Nothing here ! ****
So, E-mail services providers also have to block any message containing scripts command or lines of code, especially batch or VBS. Senders must receive a message indicating that their message has been blocked because "In order to be allowed, your message should not contain .XXXX code lines, even in a simple text field or attached documents". "If you want to send this kind of information to a SPP user, through SPP network (SPPN), you need to become a certified provider and use publicly access documents. Or at least documents made accessible to our bots and Content Watch Offices. Or use an e-mail address certified by the SafeNet Identity Certification Service."
Demonstration : ***** NOTHING HERE ! ******
SafeNet E-mail services
Apps of "E-mail through SPP" service providers must now separate e-mail coming from Certified SafeNet Users from e-mail coming from a regular Internet user. Users are informed that the sender of message coming from uncertified senders may be impossible to identify. So, they should never follow instructions coming from a sender that they are not able to certify.
E-mail clients (apps) can't use nicknames instead of the real sender e-mail address except for the real name of Certified SPP Users.
E-mail services should never make it possible to join a real identity to a SPP anonymous identity. Therefore, SPP users must manage two mailbox address... To avoid errors the same application can't manage both real identities and anonymous identities. Providers can develop two applications that are mostly identical except for a very limited quantity of code lines. In order to make it easier to maintain both apps. Apps logo of both these apps must make it easy to know when you are using your "anonymous" mail box and your official mail box.
As a reminder, SPP Anonymous Identities are still attached to a real person, but only SafeNet Identity Certification Services (SICS) can make links between Real and Anonymous identities.
Anonymous Identities can only receive e-mails from SPP contents providers and cannot send mails. This may evolve if it happen to become essential for providers to get users direct returns. Which means a return whose not using their websites forms.
0 notes
Text
Indonet Packaging Innovations: Elevate Your Packaging Experience

Discover the future of the packaging net with Indonet. We have got you covered from innovative packaging nets to gentle foam protection and refreshing bathing solutions. Upgrade your packaging experience today and join the revolution with Indonet.
#Indonet#IndonetGroup#makeinindia#ecofriendly#sustainableenvironment#nettingsolutions#safenet#safenetservices
0 notes
Text
Old Testament Meowgic was something else, dude

#duke love of my life WHAT THE ACTUAL FUCK???#“theres a safenet down there😊😙”#you really gonna trust that???#duke laurent#pluto nevermore#nevermore webtoon#pluke#meowgic#wurds
63 notes
·
View notes
Text

colleagues
#alan becker#animator vs animation#animation vs minecraft#ava victim#ava dark lord#ava ships#SafeNet au
80 notes
·
View notes
Text





Safenet Drones
These technological abominations were designed with one objective in mind. To create powerful weapons for the Divyne Republic. The Safenet Drones are equipped with some of the most advanced weaponry during humanity's era, and they were given the ability to absorb the biomass around them in order to refuel. In other words, these killer machines can turn an entire ecosystem into a barren wasteland just to remain functional. After being hijacked by the Demon Emperor, the drones not only turned against the race that made them, but they were also granted the means to self-replicate. Should anyone encounter these mechanical horrors, let alone their four titanic hive leaders, disengage.
The Four Titans
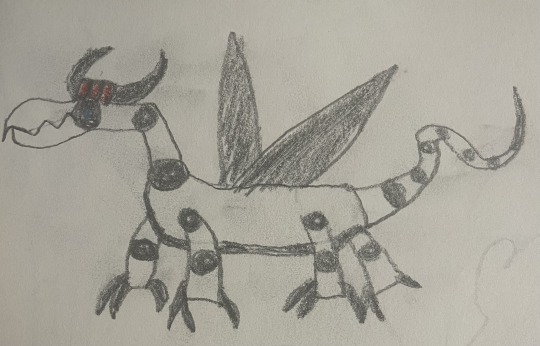
Dragonus, The Scourge of The Skies/Hive Leader Airstorm

Azen, The Flame Eater/Hive Leader Magma

Octoken, The Terror of The Sea/Hive Leader Tidal

Aangaki, The Sand Titan/Hive Leader Earthquake
#safenet drones#Azen The Flame Eater#Dragonus The Scourge of The Skies#Octoken The Terror of The Sea#Aangaki The Sand Titan#the final hope#my art#my stuff#ocs
3 notes
·
View notes
Text
Safenet sentinel Dongle Emulator
#Safenet sentinel Dongle Emulator#hasp srm dongle emulator#hasp dongle emulator#hasp hl dongle emulator#wibu dongle emulator
0 notes
Text
Idsign's Digital Signature Tokens: Your Shield in the Digital Realm
Introduction
In today's interconnected world, safeguarding digital transactions and communications is of paramount importance. As we navigate the vast landscape of online interactions, the need for airtight security measures becomes increasingly pressing. To meet these challenges, the "Idsign" has emerged as a dedicated endeavor to create a secure and dependable environment for digital transactions. In this comprehensive article, we will delve into an array of digital signature tokens, including the mToken, Token Proxkey with Digital Signature, Watchdata token, Trustkey token, SAFENET Token, epass token, E-Pass Token with Certificate, Watchdata Proxkey, SAFENET eToken, epass digital signature, epass DSC, Watchdata Proxkey digital signature, WD Proxkey digital signature, Proxkey DSC driver, and SAFENET eToken Pass.
mToken: Ensuring Digital Security
The mToken is a portable hardware token designed for digital signatures and encryption. It offers a secure and robust environment for generating and storing digital certificates, thus ensuring the authenticity and integrity of electronic documents and transactions. mToken is a testament to the commitment to data security in the digital age, providing a solution that's both powerful and convenient for individuals and organizations alike.
Token Proxkey with Digital Signature: A Fusion of Utility and Security
Token Proxkey stands out as a digital signature token that combines the ease of a USB token with the formidable cryptographic capabilities required for secure transactions. Whether you're an individual or an organization seeking to fortify your digital communications and transactions, Token Proxkey with Digital Signature offers a reliable solution. It bridges the gap between usability and robust security.
Watchdata Token: A Shield for Your Data
Watchdata tokens are renowned for their unwavering security features. These tokens are primarily used for digital signatures, secure access, and encryption. They have been crafted to meet the most stringent security standards, making them a dependable choice for those who take data protection seriously. Watchdata tokens offer peace of mind by safeguarding sensitive information in a hostile digital landscape.
Trustkey Token: Fortifying Digital Signatures
Trustkey tokens are prized for their top-tier security, making them the go-to choice for those in search of dependable hardware devices for digital signatures. They play a pivotal role in ensuring the integrity and authenticity of electronic documents and transactions. In an era marked by data breaches and cyber threats, Trustkey tokens stand as a guardian of your digital assets.
E-Pass Token with Certificate: Adding an Extra Layer of Trust
E-Pass tokens equipped with digital certificates take your security to the next level. These tokens are ideal for businesses and individuals who seek to enhance the trustworthiness of their digital transactions. Digital certificates offer an added layer of validation, assuring all parties involved of the authenticity and integrity of the digital documents.
SAFENET eToken: The Epitome of Security
SAFENET eTokens are celebrated for their top-notch security features. They are widely embraced for ensuring secure access, data protection, and trustworthy digital signatures. SAFENET eToken is more than a piece of hardware; it's a symbol of security and trust in the digital realm.
epass DSC: The Backbone of Digital Signatures
epass dsc, which stands for Digital Signature Certificate, forms the backbone of digital signatures. These certificates are essential for verifying the authenticity of the signatory in electronic transactions. They are a critical component in ensuring the trustworthiness of digital interactions.
Conclusion: A Secure Digital Future with Idsign
In a world where digital interactions are the norm, the importance of secure digital signatures and data protection cannot be overstated. The "Idsign" aims to provide a comprehensive range of E-Pass Token with Certificate, each offering unique features and capabilities. These mToken are not just technology; they are trust and reliability in the digital realm. With these Trustkey token at your disposal, you can confidently navigate the complexities of the digital world, secure in the knowledge that your transactions and communications are safeguarded by the latest advancements in digital security. The Idsign is your partner in ensuring a secure digital future.
#mToken#Token Proxkey with Digital Signature#Watchdata token#Trustkey token#SAFENET Token#epass token#E-Pass Token with Certificate#watchdata proxkey#safenet etoken#epass digital signature#epass dsc#watchdata proxkey digital signature#wd proxkey digital signature#proxkey dsc driver#safenet etoken pass
0 notes
Text
Indonesian Court Restricts Criminal Defamation Lawsuits
Rulings Offer Greater Protections for Online Speech, Critics of Government and Companies

In an important step towards protecting online speech, Indonesia’s Constitutional Court on April 29 issued two rulings that provide important clarifications to the country’s Electronic Information and Transaction Law, used to regulate the internet.
For decades, government officials and powerful private actors, including companies and religious groups, have brought criminal defamation lawsuits under the internet law to silence their critics. According to the advocacy group Safenet, hundreds of cases have been filed, with 170 defamation claims in 2024. But the court’s recent rulings restrict how the law’s defamation clauses can be used going forward.
The first ruling said that the law’s definition of “public unrest” is limited to physical space, not “digital/cyber space,” rejecting lawsuits involving online posts. The second saidthat government agencies, companies, or “groups with specific identities,” including religious groups, can no longer file criminal defamation complaints under provisions designed to protect an individual’s reputation.
The petition to review the internet law’s criminal defamation clause was filed by environmental activist Daniel F.M. Tangkilisan. Tangkilisan was convicted in 2023 for “defaming” shrimp farmers operating in protected waters. He appealed and was acquitted in May 2024. In July, Tangkilisan and his lawyer, Todung Mulya Lubis, petitioned the Constitutional Court to revoke provisions of the internet law, including article 27 on criminal defamation.
2 notes
·
View notes
Text

SafeNet Announces Garden Fiesta to Celebrate 51 Years of Service to the Erie Community http://dlvr.it/TLMzCP
0 notes
Text
Physical Identity And Access Management Market Size, Share, Analysis, Forecast, and Growth 2032: Innovations Accelerating Market Expansion
Physical Identity And Access Management Market was valued at USD 1.09 billion in 2023 and is expected to reach USD 3.70 billion by 2032, growing at a CAGR of 14.64% from 2024-2032.
Physical Identity and Access Management Market is gaining traction as organizations across sectors prioritize robust security frameworks. Enterprises in the USA and Europe are moving toward unified physical and digital identity systems to ensure secure, seamless access to facilities and sensitive resources. With increasing incidents of physical breaches and regulatory demands, the adoption of intelligent access solutions is rising rapidly.
Growth in Smart Infrastructure Drives Expansion of U.S. Physical Identity and Access Management Market
U.S. Physical Identity And Access Management Market was valued at USD 0.30 billion in 2023 and is expected to reach USD 1.00 billion by 2032, growing at a CAGR of 14.39% from 2024-2032.
Physical Identity and Access Management Market is transforming with the integration of biometrics, AI, and cloud technologies. Companies are now leveraging centralized platforms to manage employee, contractor, and visitor access across multiple sites, enhancing both operational efficiency and compliance readiness.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6523
Market Keyplayers:
HID Global Corporation (HID SAFE Enterprise, HID SAFE for Aviation)
Alert Enterprise (Guardian, Enterprise Guardian Command Center)
IBM Corporation (Security Verify, Identity Governance and Intelligence)
Nexus Group (Smart ID Physical Access, Smart ID Digital Access)
Avatier (Identity Anywhere, Password Station)
Access Security Corporation (Access Manager, Security Portal)
WALLIX (Bastion, Trustelem)
Identiv, Inc. (Velocity Software, uTrust TS Reader)
alfrednet s.r.l. (Alnet Access Control, Alnet Visitor Manager)
E&M Technologies, Inc. (Identity Management Suite, Access Control Integrator)
Quantum Secure (SAFE for Enterprise, SAFE for Secure Facilities)
AMAG Technology (Symmetry Access Control, Symmetry CompleteView)
LenelS2 (OnGuard, Elements)
Brivo (Brivo Access, Brivo Mobile Pass)
Kastle Systems (KastlePresence, KastleVisitor)
Johnson Controls (C•CURE 9000, P2000 Security Management)
Honeywell (Pro-Watch, WIN-PAK)
IDCUBE (Access360, TimeX)
Micro Focus (NetIQ Identity Manager, NetIQ Access Manager)
Okta (Identity Cloud, Lifecycle Management)
Gemalto (SafeNet Trusted Access, IDPrime)
Oracle (Identity Governance, Access Management Suite)
AWS (IAM, AWS SSO)
Atos (Evidian IAM Suite, Web Access Manager)
Wipro (Access360+, Identity and Access Framework)
Market Analysis
The market is driven by the growing need for identity lifecycle management and regulatory adherence. As hybrid work models expand and critical infrastructure faces heightened threats, physical access control is evolving into a strategic imperative. Organizations are consolidating disparate security systems into centralized platforms that manage credentials, monitor access points, and track real-time activity. This shift is especially prominent in government, healthcare, BFSI, and industrial sectors across the USA and Europe.
Market Trends
Integration of biometrics with physical access control systems
Rise in cloud-based identity and access management platforms
Growing demand for zero-trust physical security frameworks
AI-driven anomaly detection in access behavior
Increased use of mobile credentials and contactless solutions
Consolidation of physical and logical identity governance
Emphasis on compliance with GDPR and other regional regulations
Market Scope
The scope of the Physical Identity and Access Management Market is expanding beyond traditional security. Modern solutions are expected to offer scalability, real-time monitoring, and seamless integration with existing IT infrastructure.
Centralized identity lifecycle management
Multi-site, multi-role credential administration
Real-time access analytics and reporting
Mobile-first access authorization
Integration with visitor management and HR systems
Regulatory and compliance tracking features
Forecast Outlook
The Physical Identity and Access Management Market is poised for steady growth, powered by the convergence of physical security and IT identity systems. With increasing digital transformation and evolving threat landscapes, organizations in the USA and Europe are embracing smart, scalable, and future-ready access management solutions. Innovation in biometric authentication, cloud-native platforms, and AI-enhanced surveillance is expected to redefine industry standards and drive next-phase adoption.
Access Complete Report: https://www.snsinsider.com/reports/physical-identity-and-access-management-market-6523
Conclusion
As security threats become more sophisticated, the need for unified identity and access management has never been greater. From corporate campuses to critical infrastructure, the demand for advanced physical security solutions is accelerating. The Physical Identity and Access Management Market stands at the forefront of this shift—delivering smarter, safer environments with real-time, identity-driven access control.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Physical Identity And Access Management Market#Physical Identity And Access Management Market Scope#Physical Identity And Access Management Market Trends
0 notes
Text
INDONET Construction Barricade Net: Your Solution for Safety and Durability

INDONET Construction Barricade Net ensures to safeguard your environment. Excels in functionality and durability, making it an ideal choice for an ideal choice for crowd control, temporary enclosures, and hazard prevention.
#highqualitynets#netting#nettingsolutions#safenet#safenetservices#nettingindustry#customizationavailable#IndonetBarricadeNet#barricadenet#barricadenets#madeinindia#makeinindia#IndonetGroup
0 notes
Text
Menentukan plihan jalan
“ B, sapa Wenny via Chat SafeNet. “ Ya wen. Ada apa ? “ Terimakasih sudah selesaikan masalah Food Farming.” Kata Wenny. “ Ah biasa saja. Not big deal “ kata saya. “ Wen, ganggu engga malam minggu ini kita ngobrol sebentar” “ Ya enggalah. Malah senang. Saya kan malam minggu engga kemana mana. “Kata Wenny. “ Mengapa sampai rakyat China memilih komunisme daripada nasionalis “ Tanya saya.…
0 notes
Text
Cybersecurity in Critical Infrastructure Market Insights 2032: Size, Share, Scope & Strategic Analysis
The Cybersecurity in Critical Infrastructure Market was valued at USD 21.60 billion in 2023 and is expected to reach USD 30.96 Billion by 2032, growing at a CAGR of 4.10 % over the forecast period 2024-2032.
the security of critical infrastructure has never been more vital. Critical infrastructure—comprising sectors such as energy, water supply, transportation, healthcare, and financial services—forms the backbone of any nation’s economy and societal functioning. As these systems continue to integrate smart technologies, the risk of cyberattacks has escalated sharply. This surge in threat levels has propelled the cybersecurity in critical infrastructure market to the forefront of strategic investment, policy development, and technological innovation.
Cybersecurity in the critical infrastructure market is evolving rapidly to address a growing range of threats, from ransomware and phishing attacks to advanced persistent threats (APTs) targeting operational technology (OT) networks. Governments, regulatory bodies, and private stakeholders are now prioritizing cybersecurity frameworks that protect essential services and ensure national resilience. This growing urgency is leading to significant advancements in security protocols, demand for specialized cybersecurity solutions, and cross-sector collaborations aimed at fortifying infrastructure against future cyber risks.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/5490
Market Keyplayers:
Palo Alto Networks (Next-Generation Firewall, Prisma Cloud)
Fortinet (FortiGate Firewall, FortiSIEM)
Cisco Systems, Inc. (Cisco Firepower, Cisco Umbrella)
Check Point Software Technologies Ltd. (Check Point Quantum Security Gateway, Check Point CloudGuard)
IBM Corporation (IBM QRadar, IBM Guardium)
Trend Micro, Inc. (Trend Micro Deep Security, Trend Micro Apex One)
Huawei (Huawei USG Series Firewalls, Huawei AntiDDoS)
Norton LifeLock (Norton 360, Norton Secure VPN)
RSA Security LLC (RSA NetWitness Platform, RSA SecurID)
FireEye, Inc. (FireEye Network Security, FireEye Endpoint Security)
BAE Systems (BAE Systems Cyber Threat Detection, BAE Systems Data Protection Solutions)
General Dynamics Corporation (GD Mission Systems Cyber Defense Solutions, TACLANE Encryptors)
McAfee, Inc. (McAfee Total Protection, McAfee MVISION Endpoint)
Honeywell International Inc. (Honeywell Industrial Cybersecurity Solutions, Honeywell Secure Media Exchange)
Thales Group (Thales CipherTrust Data Security Platform, Thales SafeNet Trusted Access)
Airbus SE (Airbus CyberSecurity Keelback Net, Airbus CyberRange)
Sophos (Sophos Intercept X, Sophos XG Firewall)
CrowdStrike (CrowdStrike Falcon Platform, CrowdStrike Threat Graph)
CyberArk (CyberArk Privileged Access Manager, CyberArk Endpoint Privilege Manager)
Akamai Technologies (Akamai Kona Site Defender, Akamai Prolexic Routed)
Trends in the Cybersecurity in Critical Infrastructure Market
Several key trends are currently shaping the cybersecurity landscape within critical infrastructure sectors:
Convergence of IT and OT Systems: The line between Information Technology (IT) and Operational Technology (OT) is increasingly blurred. As industrial control systems become internet-connected, they also become more vulnerable to attacks. The integration of cybersecurity solutions that can simultaneously monitor and protect both IT and OT environments is a growing priority.
AI and Machine Learning Integration: Artificial intelligence and machine learning are being widely adopted for real-time threat detection, automated incident response, and anomaly detection. These technologies help in predicting and mitigating cyber threats before they can impact critical systems.
Zero Trust Architecture: The Zero Trust security model—where no user or system is trusted by default—is gaining momentum. This approach requires continuous verification, making it ideal for critical infrastructure where perimeter-based defenses are no longer sufficient.
Increased Government Regulations and Investments: Governments worldwide are implementing stricter cybersecurity mandates for essential sectors. In parallel, public funding and national cybersecurity strategies are being expanded to support infrastructure resilience.
Cloud Security Solutions: With a shift toward cloud-based systems for scalability and efficiency, securing these environments has become imperative. Cloud-native security tools are being increasingly adopted to safeguard infrastructure assets and sensitive data.
Enquiry of This Report: https://www.snsinsider.com/enquiry/5490
Market Segmentation:
By Type
Encryption
Network Access Control & Firewalls
Threat Intelligence
Other
By Application
BFSI
Government and Defense
Transport & Logistics
Energy & Power
Commercial Sector
Telecommunications
Market Analysis
North America holds the largest market share, owing to its mature cybersecurity ecosystem and high level of investment in digital infrastructure. Meanwhile, regions such as Asia-Pacific and Europe are experiencing rapid growth due to rising threats and infrastructure modernization.
The energy sector remains one of the most targeted segments, particularly electric grids, oil and gas pipelines, and nuclear facilities. Healthcare systems and water treatment facilities are also under heightened scrutiny, as attacks on these systems can have immediate, tangible impacts on public health and safety. Vendors are responding by offering sector-specific solutions, including intrusion detection systems for SCADA networks, endpoint protection for medical devices, and secure access solutions for utility control systems.
The competitive landscape features both established cybersecurity providers and niche players specializing in industrial systems protection. Strategic partnerships, acquisitions, and technology alliances are common as firms aim to broaden their capabilities and market reach. In addition, the demand for cybersecurity professionals with OT expertise is surging, creating both challenges and opportunities for workforce development.
Future Prospects
The future of cybersecurity in critical infrastructure will be shaped by several transformative forces:
Expansion of 5G and IoT: With more devices and systems becoming interconnected, especially through 5G networks, the attack surface is expanding. Infrastructure operators will need to adopt advanced threat modeling and monitoring tools to manage this complexity.
Cyber Resilience as a Business Priority: Organizations are shifting focus from just prevention to resilience. This includes not only protecting against attacks but ensuring quick recovery and continuity of operations after a breach.
Digital Twins and Simulation Tools: The use of digital twins—virtual models of infrastructure systems—for simulating cyberattacks and training responses is emerging as a proactive defense strategy.
Global Collaboration and Intelligence Sharing: Cross-border collaboration and threat intelligence sharing are expected to increase, especially for industries like aviation and energy that operate on a global scale. Public-private partnerships will be instrumental in this effort.
Tailored AI Solutions: AI tools specifically designed for individual critical sectors will play a growing role, offering customized protection mechanisms based on sector-specific threats and risk profiles.
Access Complete Report: https://www.snsinsider.com/reports/cybersecurity-in-critical-infrastructure-market-5490
Conclusion
The cybersecurity in critical infrastructure market is becoming a cornerstone of national security and public safety in the digital age. As technological innovations continue to transform essential services, the importance of robust, adaptive, and intelligent cybersecurity frameworks is more apparent than ever. The market is not only growing in size but also in strategic significance, with stakeholders across sectors prioritizing cyber resilience. Looking ahead, the synergy between government policy, industry innovation, and emerging technologies will define the future of this critical domain, ensuring that infrastructure systems remain secure, operational, and trusted.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
The Cybersecurity in Critical Infrastructure Market was valued at USD 21.60 billion in 2023 and is expected to reach USD 30.96 Billion by 2032, growing at a CAGR of 4.10 % over the forecast period 2024-2032.
the security of critical infrastructure has never been more vital. Critical infrastructure—comprising sectors such as energy, water supply, transportation, healthcare, and financial services—forms the backbone of any nation’s economy and societal functioning. As these systems continue to integrate smart technologies, the risk of cyberattacks has escalated sharply. This surge in threat levels has propelled the cybersecurity in critical infrastructure market to the forefront of strategic investment, policy development, and technological innovation.
Cybersecurity in the critical infrastructure market is evolving rapidly to address a growing range of threats, from ransomware and phishing attacks to advanced persistent threats (APTs) targeting operational technology (OT) networks. Governments, regulatory bodies, and private stakeholders are now prioritizing cybersecurity frameworks that protect essential services and ensure national resilience. This growing urgency is leading to significant advancements in security protocols, demand for specialized cybersecurity solutions, and cross-sector collaborations aimed at fortifying infrastructure against future cyber risks.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/5490
Market Keyplayers:
Palo Alto Networks (Next-Generation Firewall, Prisma Cloud)
Fortinet (FortiGate Firewall, FortiSIEM)
Cisco Systems, Inc. (Cisco Firepower, Cisco Umbrella)
Check Point Software Technologies Ltd. (Check Point Quantum Security Gateway, Check Point CloudGuard)
IBM Corporation (IBM QRadar, IBM Guardium)
Trend Micro, Inc. (Trend Micro Deep Security, Trend Micro Apex One)
Huawei (Huawei USG Series Firewalls, Huawei AntiDDoS)
Norton LifeLock (Norton 360, Norton Secure VPN)
RSA Security LLC (RSA NetWitness Platform, RSA SecurID)
FireEye, Inc. (FireEye Network Security, FireEye Endpoint Security)
BAE Systems (BAE Systems Cyber Threat Detection, BAE Systems Data Protection Solutions)
General Dynamics Corporation (GD Mission Systems Cyber Defense Solutions, TACLANE Encryptors)
McAfee, Inc. (McAfee Total Protection, McAfee MVISION Endpoint)
Honeywell International Inc. (Honeywell Industrial Cybersecurity Solutions, Honeywell Secure Media Exchange)
Thales Group (Thales CipherTrust Data Security Platform, Thales SafeNet Trusted Access)
Airbus SE (Airbus CyberSecurity Keelback Net, Airbus CyberRange)
Sophos (Sophos Intercept X, Sophos XG Firewall)
CrowdStrike (CrowdStrike Falcon Platform, CrowdStrike Threat Graph)
CyberArk (CyberArk Privileged Access Manager, CyberArk Endpoint Privilege Manager)
Akamai Technologies (Akamai Kona Site Defender, Akamai Prolexic Routed)
Trends in the Cybersecurity in Critical Infrastructure Market
Several key trends are currently shaping the cybersecurity landscape within critical infrastructure sectors:
Convergence of IT and OT Systems: The line between Information Technology (IT) and Operational Technology (OT) is increasingly blurred. As industrial control systems become internet-connected, they also become more vulnerable to attacks. The integration of cybersecurity solutions that can simultaneously monitor and protect both IT and OT environments is a growing priority.
AI and Machine Learning Integration: Artificial intelligence and machine learning are being widely adopted for real-time threat detection, automated incident response, and anomaly detection. These technologies help in predicting and mitigating cyber threats before they can impact critical systems.
Zero Trust Architecture: The Zero Trust security model—where no user or system is trusted by default—is gaining momentum. This approach requires continuous verification, making it ideal for critical infrastructure where perimeter-based defenses are no longer sufficient.
Increased Government Regulations and Investments: Governments worldwide are implementing stricter cybersecurity mandates for essential sectors. In parallel, public funding and national cybersecurity strategies are being expanded to support infrastructure resilience.
Cloud Security Solutions: With a shift toward cloud-based systems for scalability and efficiency, securing these environments has become imperative. Cloud-native security tools are being increasingly adopted to safeguard infrastructure assets and sensitive data.
Enquiry of This Report: https://www.snsinsider.com/enquiry/5490
Market Segmentation:
By Type
Encryption
Network Access Control & Firewalls
Threat Intelligence
Other
By Application
BFSI
Government and Defense
Transport & Logistics
Energy & Power
Commercial Sector
Telecommunications
Market Analysis
North America holds the largest market share, owing to its mature cybersecurity ecosystem and high level of investment in digital infrastructure. Meanwhile, regions such as Asia-Pacific and Europe are experiencing rapid growth due to rising threats and infrastructure modernization.
The energy sector remains one of the most targeted segments, particularly electric grids, oil and gas pipelines, and nuclear facilities. Healthcare systems and water treatment facilities are also under heightened scrutiny, as attacks on these systems can have immediate, tangible impacts on public health and safety. Vendors are responding by offering sector-specific solutions, including intrusion detection systems for SCADA networks, endpoint protection for medical devices, and secure access solutions for utility control systems.
The competitive landscape features both established cybersecurity providers and niche players specializing in industrial systems protection. Strategic partnerships, acquisitions, and technology alliances are common as firms aim to broaden their capabilities and market reach. In addition, the demand for cybersecurity professionals with OT expertise is surging, creating both challenges and opportunities for workforce development.
Future Prospects
The future of cybersecurity in critical infrastructure will be shaped by several transformative forces:
Expansion of 5G and IoT: With more devices and systems becoming interconnected, especially through 5G networks, the attack surface is expanding. Infrastructure operators will need to adopt advanced threat modeling and monitoring tools to manage this complexity.
Cyber Resilience as a Business Priority: Organizations are shifting focus from just prevention to resilience. This includes not only protecting against attacks but ensuring quick recovery and continuity of operations after a breach.
Digital Twins and Simulation Tools: The use of digital twins—virtual models of infrastructure systems—for simulating cyberattacks and training responses is emerging as a proactive defense strategy.
Global Collaboration and Intelligence Sharing: Cross-border collaboration and threat intelligence sharing are expected to increase, especially for industries like aviation and energy that operate on a global scale. Public-private partnerships will be instrumental in this effort.
Tailored AI Solutions: AI tools specifically designed for individual critical sectors will play a growing role, offering customized protection mechanisms based on sector-specific threats and risk profiles.
Access Complete Report: https://www.snsinsider.com/reports/cybersecurity-in-critical-infrastructure-market-5490
Conclusion
The cybersecurity in critical infrastructure market is becoming a cornerstone of national security and public safety in the digital age. As technological innovations continue to transform essential services, the importance of robust, adaptive, and intelligent cybersecurity frameworks is more apparent than ever. The market is not only growing in size but also in strategic significance, with stakeholders across sectors prioritizing cyber resilience. Looking ahead, the synergy between government policy, industry innovation, and emerging technologies will define the future of this critical domain, ensuring that infrastructure systems remain secure, operational, and trusted.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#cybersecurity in critical infrastructure market#cybersecurity in critical infrastructure market Scope#cybersecurity in critical infrastructure market Growth#cybersecurity in critical infrastructure market Trends
0 notes