#SoftwareCompositionAnalysis
Explore tagged Tumblr posts
Text
Open Source Applications & Security?

Open Source Applications & Security as much controversial as it may sound, Open source applications have been around forever. However, their requirements have skyrocketed only in the past decade. The reason for this is no mystery — lower Development Costs. This has suddenly increased the needs for data. Software development organisations regardless of its size has become dependent on Open Source Applications.
Almost 70–80 percentage of the applications today are comprised of reusable components. The irony would be the times when this open source software was considered too risky for commercial use. Albeit enterprises have gotten very good at using open source to fast-track the development cycle.
Although companies have figured out how to reuse the code effectively, they haven’t figured out how to use them securely without introducing inadvertent vulnerabilities.
The facts would point companies growing reliance towards such data without required security. Consequently, with the reliance towards such data also increases the likelihood of applications inheriting much more risks and vulnerabilities than ever before.
Now that we have established the major consumption rate and the problems, they cause let’s see how to handle this vulnerability. A popular way to track open source elements is through Software Composition Analysis (SCA)
As scary as it may sound, SCA tools are not new to the industry. SCA tools provides an insight of what they are doing with their open source platforms. SCA tools were originally born of the need to keep track of open source tools. There is no definite limit on what SCA encompasses. SCA tools offers different facilities from spreadsheets to tax deduction. Although SCA tools were on the escalator to glory they failed miserably.
The short — lived glory
In the early 2000’s firms matched codes by scanning them to data from open source elements by identifying snippets of code. However, this required professional help to remove falsified data. Fast forward a decade, companies required elements that met with their agile needs. By this time, the real-time detection of vulnerabilities and other issues at earliest started surfacing by then.
Almost a decade later now, the tools provide insights that delve a little deeper of how each element is being used. Before investing on the SCA an organization has to make sure if the SCA of their choice can cover all their coding languages. Companies new to this field may not be great at identifying unrecorded vulnerabilities, resulting in complications. On the other hand, SCA tools must work seamlessly with the build tools, databases and repositories.
DevOps — The replacement of SCA
SCA tools like I said before have been around for some time and follows native designs. Hence it lacks when used alongside of a system’s security lacked agility which became a demanding need by organizations. DevOps handles implementing new changes on infrastructure, embarking changes easier for Developers.
No matter what, SCA still is in practise. However, with almost every organisation switching to DevOps, reasons it is because of the seamless security intertwine to their workflow that redefines transparency for its developers.
Wrap up
I don’t want to turn this article into a debate, all statements here are facts learned and collected to the best of my understanding. I want you to be your own judge. If you think SCA tools might be the best option for your organisation’s needs, go for it. Or if DevOps suits your needs better go for it.
#**#OpenSourceSecurity#SoftwareCompositionAnalysis#SCA#DevOps#OpenSourceApplications#SecurityVulnerabilities#AgileDevelopment**
0 notes
Link
0 notes
Text
#SoftwareCompositionAnalysis#SCAtools#OpenSourceSoftware#ComplianceManagement#SecurityRisks#SoftwareCompositionAnalysisTools#SCASoftware#SCACompositionAnalysis#SCAAnalysis
0 notes
Text
#SoftwareCompositionAnalysis#SCAtools#OpenSourceSoftware#ComplianceManagement#SecurityRisks#SoftwareCompositionAnalysisTools#SCASoftware#SCACompositionAnalysis#SCAAnalysis
0 notes
Text
#SoftwareCompositionAnalysis#SCAtools#OpenSourceSoftware#ComplianceManagement#SecurityRisks#SoftwareCompositionAnalysisTools#SCASoftware#SCACompositionAnalysis#SCAAnalysis
0 notes
Text
Software Composition Analysis Tools: Your Guide to Securing Software
Software Composition Analysis (SCA) entails the automated inspection of open-source software (OSS) components within a project's codebase. Given that an average application incorporates 147 distinct OSS elements, SCA becomes an essential tool for the majority of development teams.
Investing in SCA is a straightforward decision; however, navigating the variety of SCA tools available on the market can be challenging. With a wide range of vendors offering distinct functionalities, integration capabilities, and pricing structures, it's vital to make an informed choice.
This guide highlights the premier SCA tools in the market designed to ensure that OSS components are not only free from vulnerabilities but also adhere to licensing requirements. We delve into the unique advantages of each tool and assist you in selecting an SCA solution that seamlessly aligns with your Software Development Life Cycle (SDLC) and operational workflows.
What is Software Composition Analysis?
Software Composition Analysis (SCA) is an investigative process designed to provide a detailed audit of a software's components. By utilizing SCA software, organizations can identify open-source and proprietary components, their versions, and the licenses associated with them. This analysis is crucial for detecting vulnerabilities, licensing conflicts, and ensuring compliance with open-source policies. SCA software composition analysis thus acts as a cornerstone for software security and compliance management, providing a transparent view into the software's building blocks.
How to Choose the Best Software Composition Analysis Tools?
Selecting the ideal SCA tool requires a thorough understanding of your organization's specific needs and the features offered by various SCA software options. Key considerations should include:
Comprehensive Database: A robust SCA tool should have an extensive database of open-source licenses and vulnerabilities to ensure accurate detection and assessment.
Integration Capabilities: Seamless integration with your existing development tools and environments is vital for streamlined operations.
Automated Compliance Management: The ability to automatically enforce compliance policies and generate detailed reports can significantly reduce manual efforts and errors.
Real-Time Monitoring: Look for tools that offer real-time monitoring and alerts to promptly address any newly discovered vulnerabilities or compliance issues.
Best 5 Software Composition Analysis Tools
Selecting the best SCA Software can significantly impact the security and compliance of your software development lifecycle. While the best tool for your needs depends on specific features you prioritize, such as integration capabilities, ease of use, or the depth of the vulnerability database, here are five highly regarded SCA tools based on industry recognition and feature sets they offer:
Sonatype Nexus Lifecycle
This tool is known for its comprehensive software supply chain management capabilities. Nexus Lifecycle integrates directly into your DevOps pipeline, offering precise policy enforcement, license compliance, and proactive identification of vulnerabilities across every stage of the development lifecycle. Its extensive database and continuous monitoring make it a favorite among developers and security professionals alike.
Snyk
Snyk stands out for its developer-first approach, focusing on ease of use and integration with the development workflow. It offers real-time scanning and monitoring of open-source dependencies for vulnerabilities, with the added benefit of automatic fix suggestions. Snyk supports a wide array of languages and frameworks and integrates seamlessly with CI/CD pipelines, making it a versatile choice for modern development teams.
Black Duck by Synopsys
Black Duck is renowned for its comprehensive audit and compliance capabilities, including deep insights into open-source licenses and security vulnerabilities. It provides detailed risk assessments, operational risk management, and policy enforcement features that help organizations manage their open-source security and compliance risks effectively. Black Duck's extensive database and integration with build and deployment tools make it a powerful tool for enterprises.
WhiteSource
WhiteSource offers an automated solution for securing and managing open-source components. It features effective vulnerability detection, license compliance checks, and out-of-the-box policies to ensure compliance and reduce risk. WhiteSource integrates with numerous build tools and CI/CD pipelines, providing real-time alerts and remediation paths, making it an efficient tool for continuous integration environments.
FOSSA
Focused on open-source management, FOSSA offers deep insights into license compliance and security vulnerabilities. It automates license scanning and compliance checks, providing detailed analytics and customizable policies for effective open-source governance. FOSSA's emphasis on easy integration and a user-friendly dashboard makes it an attractive option for teams looking to streamline their open-source management processes.
Which is the Best Software Composition Analysis Software ?
Determining the "best" SCA software hinges on the specific requirements of an organization. However, a tool that offers a balanced combination of extensive vulnerability and license databases, seamless integration, automated compliance, and real-time monitoring capabilities is often considered superior. Evaluating the tools based on these criteria and considering the organization's unique needs will lead to the most suitable choice.
Market Intelligence and Its Role in Your Growth
In the quest for the best SCA software, market intelligence reports, such as those provided by Quadrant Knowledge Solutions, play a pivotal role. These reports offer a comprehensive analysis of the Software Composition Analysis market, including insights on Market Share: Software Composition Analysis, 2022, Worldwide, and Market Forecast: Software Composition Analysis, 2022-2027, Worldwide. Such in-depth market intelligence is invaluable for businesses aiming for growth, as it helps in making informed decisions by understanding market trends, competitor standings, and future forecasts. The insights from these reports can guide you in choosing the best platform that aligns with your security and compliance goals, ensuring a robust SCA strategy for your organization.
Conclusion
In wrapping up, it's clear that the digital world is in a constant state of flux, underscoring the invaluable role that Software Composition Analysis (SCA) tools play in fortifying software security and ensuring regulatory compliance. Armed with the appropriate tools and the profound insights derived from market intelligence reports, organizations are well-equipped to traverse the intricate tapestry of software composition. This strategic approach not only instills confidence but also sets the stage for enduring growth and breakthrough innovation in an ever-evolving digital landscape.
#SoftwareCompositionAnalysis#SCAtools#OpenSourceSoftware#ComplianceManagement#SecurityRisks#SoftwareCompositionAnalysisTools#SCASoftware#SCACompositionAnalysis#SCAAnalysis
0 notes
Text
10 Best Software Composition Analysis Tools (Features and Pricing)


In today's rapidly evolving technology landscape, software development often relies on integrating open-source components and third-party libraries to accelerate the creation of feature-rich applications. Unfortunately, these components can introduce potential security risks and vulnerabilities. As a result, Software Composition Analysis (SCA) Tools have emerged as a critical solution for identifying and managing these risks. With many options in the market, you may get confused while selecting the tool. This article provides the ten best software composition analysis tools with their features, pricing, likes, and dislikes.
What are Software Composition Analysis Tools (SCA Tools)?
Software composition analysis tools are security solutions that help organizations identify, manage, and mitigate potential risks and vulnerabilities associated with open-source components and third-party libraries in their software applications. These tools provide comprehensive visibility into the composition and dependencies of software applications. As a result, they enable developers to ensure the security, compliance, and quality of their codebase, ultimately protecting organizations from potential threats and allowing them to deliver secure, high-performing software products to their users.
Common Features of Software Composition Analysis Tools
Dependency analysis SCA tools automatically scan the application's codebase to create an inventory of all open-source components and third-party libraries, along with their respective versions and dependencies. That helps developers understand the extent of external components used in their software. Vulnerability detection SCA tools can detect potential security risks and vulnerabilities in the application's codebase by cross-referencing the identified components with known vulnerability databases, like the National Vulnerability Database (NVD) or other proprietary databases. License compliance SCA tools analyze the licenses associated with each open-source component, helping organizations adhere to the legal requirements and obligations of using these components in their software. Prioritization and remediation Based on the severity of detected vulnerabilities, SCA tools help prioritize which issues need immediate attention and recommend remediation actions, such as updating a component to a more secure version or applying patches. Integration with development workflows Many SCA tools integrate with existing development tools and processes, such as continuous integration/continuous deployment (CI/CD) pipelines, issue trackers, and integrated development environments (IDEs), enabling developers to address vulnerabilities and compliance issues early in the development lifecycle. List of best Software Composition Analysis tools.
1. GitHub
GitHub is an AI pair programmer that empowers you to complete tasks. It assists you in converting natural language into coding language. This unlimited repository helps your team to work together.
Features - Code spaces for individuals - Collaborative coding - Automation and CI/CD - Security - Client Apps - Project management - Team administration - Software life cycle security
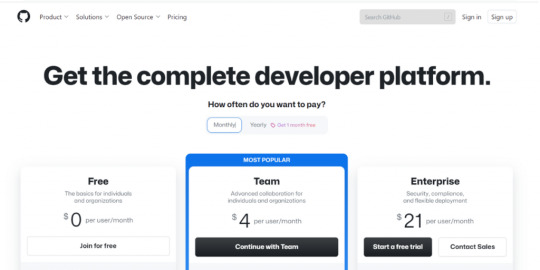
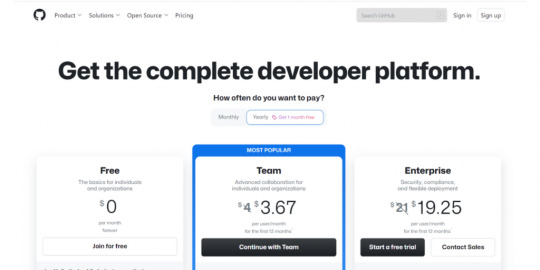
Pricing GitHub provides pricing plans on a monthly and yearly basis. If you are interested in a yearly plan, then a one-month free trial is available. On a monthly basis, pricing rates are as follows. - These plans have categorized three types - Free- Basics for individuals - Team - Advanced collaboration- $4/user/month - Enterprise- Flexible deployment- $21/user/month - On a yearly basis, pricing rates are as follows; - Free- Basics for individuals - Team - only for first 12 months- $3.67/user/month - Enterprise- only for first 12 months- $19.25/user/month
Likes - It is a more reliable tool for source control. - This platform is user-friendly. - It provides useful features like version control, code review, and project management for developers. - You can make group assignments and open-source contributions easily. - GitHub repository has a lot of customization potential. Dislikes - Everything is the command line. Remembering all the commands becomes a difficult task. - Its functionality is complicated. Using large files can be complex. - Beginner takes more time to learn the process. - Integrating it with VS code is difficult. - It will not provide a customized notification system for mobile apps. - For the free version limited number (at least one) of private repositories are available. - Only a limited number of users can handle the same project. Other details DeploymentCloud, SaaS, Web-BasedSupportEmail/Help Desk, FAQs/Forum, Knowledge BaseSupported deviceMac, Windows, On-Premise - Windows, Linux, Mobile - Android, iPhone, iPadTrainingVideosCustomer ratingsCapterra: 4.8 out of 5 (5800 +reviews), G2: 4.7 out of 5 (1967+reviews) User opinion GitHub is one of the most exciting startups. It provides a fully managed platform. It is an awesome tool for any user ranging from students to professionals, and is easy to use. This is a highly recommended software to improve your software development workflow.
2. GitLab
If you want to build your enterprise, then GitLab is easy. GitLab’s simple and flexible approaches meet the needs of small teams to large enterprises. It has a simple, flexible approach and helps shorten the delivery lifecycle, streamlining manual processes.
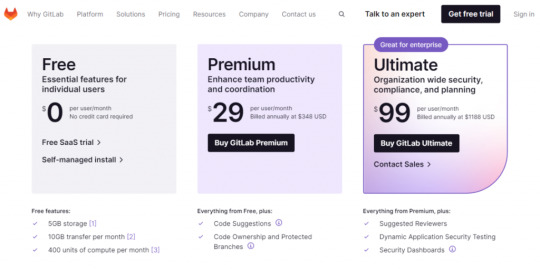
Features - Powerful planning tool - Source code management - Code review workflow - Remote development - Continuous integration - Code testing and coverage - API security - Environment management - Error tracking Pricing Three different pricing plans are available here. And provides a free trial facility. Go through the below details to learn more about pricing. - Free - It is entirely free and suitable for individual users - Premium - Its starts from $29/user/month - Ultimate - Its starts from $99/user/month
Likes - It provides easy configuration and automation. - It is a single application covering all departments, including research, QA, security, and operations. - It offers robust branching and merging capabilities. - It is easy to use the CLI commands in other automated scripts. Dislikes - The user interface needs more improvement. - Sometimes you may face problems like connecting to the server. - Basic agile tools are used here, so you can’t replace tickets remotely. - Understanding coding issues takes more time. - You have to update manually from the old version to the new version. - The level of support is insufficient, particularly for complex or advanced use cases. Other details DeploymentCloud, SaaS, Web-BasedSupportFAQs/Forum, Knowledge Base,24/7 (Live Rep), ChatSupported deviceOn-Premise - Windows, Linux, Mobile - iPhone, iPadSupported languagesEnglishTrainingIn-Person, Live Online, Webinars, Documentation, VideosCustomer ratingsCapterra: 4.6 out of 5 (970+reviews) G2: 4.5 out of 5 (700 +reviews) User opinion GitLab empowers development security and operations so teams can build better software faster. It has an integrated approach that eliminates the need for multiple tools. You can face some billing issues, and handling large projects would be difficult.
3. Wiz
Wiz provides full visibility to cloud workloads. It simplifies cloud operation by providing a single policy for both developer and security. So your company can proactively improve your cloud security posture. With the help of lac code, you can build your policies and framework.

Features - Compliance automation - Automatic posture management - NO deployment agents - Deep assessment - Unified code and cloud policy - Custom framework - Flexible reporting - Cloud-native incident response - Analyze effective permission - Vulnerability management Pricing Pricing details are not provided on their website. Likes - Easy to use and operate - It provides great insight into infrastructure configuration issues - It gives significantly improved visibility into the cloud security posture - It has the best CSPM Dislikes - These systems are tedious to setup - Some of the integrations feel half-baked or incomplete - Wiz makes significant changes quickly; these changes sometimes cause errors in tools - Only a chat option is available to make contact - It provides fewer options to generate reports Other details DeploymentCloud, SaaS, Web-BasedSupported languagesEnglishCustomer ratingG2: 4.7out of 5 (339+reviews) User opinion Wiz continuously monitors the environment for new vulnerabilities and provides a real-time risk assessment. It enables you to protect cloud data. You can quickly access your compliance and focus more on your teams. It cannot use the word “AND / OR “ in queries.
4. Snyk
Snyk is a developer security platform enabling you to secure the whole application, providing actionable insights and workflows. It has expertise with advanced ML and human-in-the-loop AI. It finds vulnerabilities in real-time and then offers actionable fix advice.
Features - Easy integration - Continuous scan - Fix with a click - Vulnerability database - Governance at scale - Code security - Security of base images - Development life cycle security Request page of Snyk
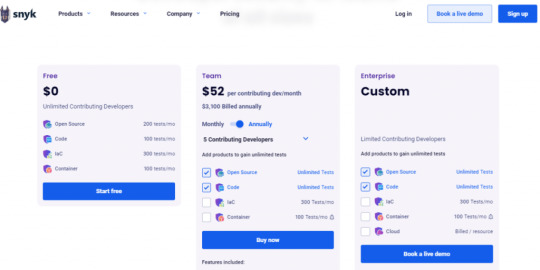
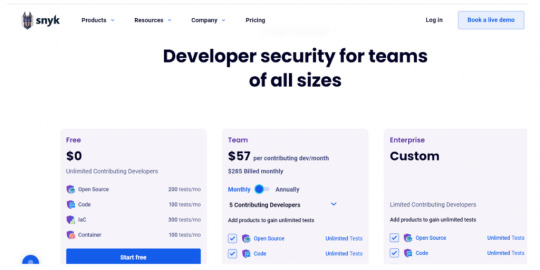
Pricing Snyk offers free demos for its users, and it has three different pricing plans; they are as follows. - Free - It is entirely free - Team - $52/month billed annually, $57/month billed monthly - Enterprise- You can have customized offers based on your needs
Likes - It is easy to integrate. - It shows category-wise vulnerabilities like critical, high, medium, and low. - Snyk is extremely straightforward; It doesn't require the team to review extensive documentation. - Automated repository analysis is good. Dislikes - Compared to other tools, it is less efficient and useful. - Its unavailability issues can cause the Snyk code to fail. - Need more improvement in code quality suggestions. - More information is needed to do documentation. - Its reported vulnerabilities scan takes more time. Other details DeploymentCloud, SaaS, Web-BasedSupportKnowledge Base, ChatSupported deviceDesktop - Mac, WindowsTrainingIn-Person, Live Online, Webinars, DocumentationCustomer RatingCapterra: 4.8 out of 5 (17+reviews) G2: 4.6 out of 5 (108+reviews) User opinion Snyk is even better and warns you before merging your pull requests. It is a developer security platform for securing custom code. Its security solutions enable modern applications to build securely. However, it is easy to use on existing products. Overall, it is a great tool for security analysts, not for security engineers.
5. Azure Microsoft Defender Cloud
The Microsoft defender cloud offers integrated security for multi-cloud and hybrid environments. This tool helps you achieve real-time security access and fix issues with integrated insights from code to runtime.
Features - Contextual security posture management - Modern threat detection - Unify security management - Real-time security access - Centralized insights across multipipeline - Hybrid cloud and infrastructure Homepage of Microsoft Defender for cloud
Pricing It offers an Azure free account with $200 credits to use within 30 days. It provides free services. After that credit, you can use the pay-as-you-go option to keep the free services and pay only if you exceed the free monthly amounts. After a year, you will keep getting more than 55 free services and must pay only when you exceed the free amount. Likes - It gives insight into user actions - It is easy to automate - It has straight forward dashboard - It is easy to use and manage security across multiple platforms. Dislikes - Difficult to protect unmatched cloud devices with this software. - Some of the default alerts do not trigger emails. - Needs more SaaS integrations. - Sometimes not updated with the latest threat. - Embedding with third-party apps would be challenging. Other details DeploymentCloud, SaaS, Web-BasedTrainingLive Online, Webinars, Documentation, VideosCustomer RatingCapterra: 5.0 out of 5 (1+reviews) G2: 5.0 out of 5 (1+reviews) User opinion Microsoft Defender for Cloud provides security assessments for cloud resources running in Azure, AWS, and Google Cloud. It enhances security postures, protects against modern threats, and reduces risks. In addition, it works seamlessly with all other Microsoft services.
6. Mend.io
Mendi.io is formerly known as WhiteSource. It can build world-class AppSec programs, which help global organizations. It is an autopilot for AppSec.

Features - Application security - Open source audit - Open source security - Malicious package protection - Software supply chain security - Open-source license compliance - Software bill of materials Summary display of Mend.io
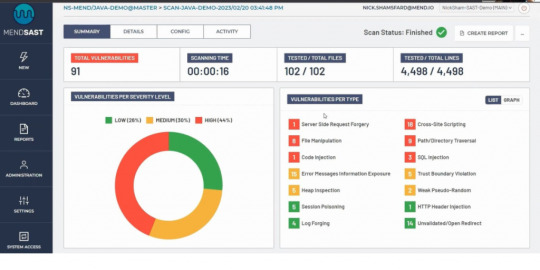
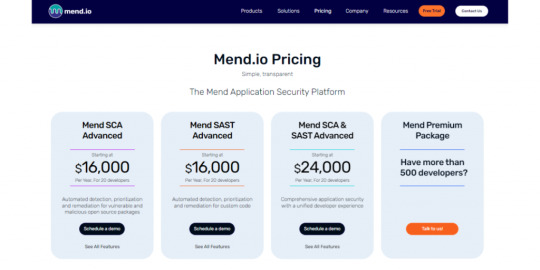
Pricing The pricing plan offers three plans. - Mend SCA advanced - Its starting price is $16000 per year for 20 developers - Mend SAST advanced - Its starting price is $16000 per year for 20 developers. - Mend SCA and SAST advanced - Its starting pricing price is $24000 per year for 20 developers - They have mend premium package for more than 500 developers.
Likes - It is very easy to break down and analyze all the open-source packages. - It can easily integrate with the workflow. - It analyzes in-house and other multiple sources. Dislikes - Customer service is not so good. - The dashboard and UI are not user-friendly. - The data are not available in the dashboard. - The implementation is challenging. - Unable to configure and work with. - The documentation is much clingy. - The generation of SBOM is much odd. - It shows invalid vulnerabilities. Other details Supported languagesEnglishCustomer ratingG2: 4.3 out of 5 ( Read the full article
0 notes
Link
0 notes