#SecurityVulnerabilities
Explore tagged Tumblr posts
Text
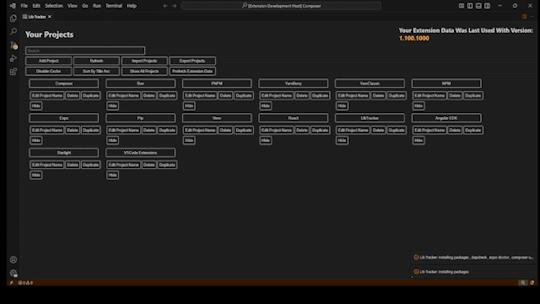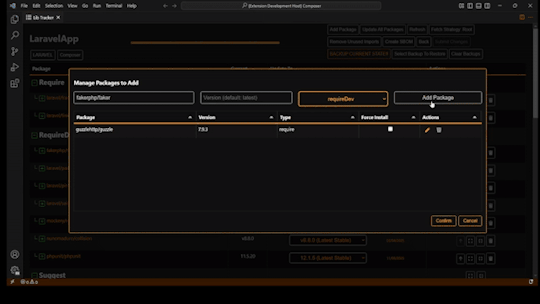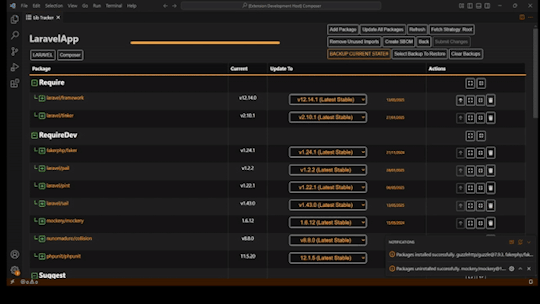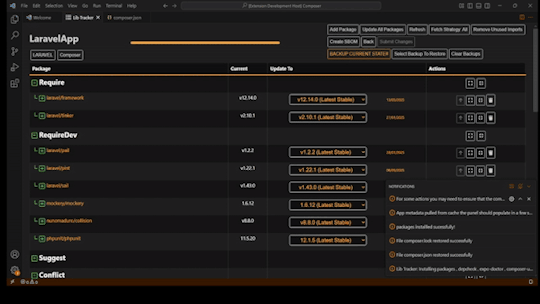
LibTracker VS Code Extension: Streamline Your Dependency Management
We're excited to share the latest update to **LibTracker**, our lightweight dependency tracking extension for Visual Studio Code.
LibTracker gives developers a streamlined way to identify outdated packages, address known security vulnerabilities, and monitor licensing issues—all within their IDE.
**Now with Full PHP Composer Support**
Our latest release includes robust support for PHP projects using Composer. You can now:
* Track and manage Composer dependencies directly in LibTracker
* Add custom messages to your backup notes for easier tracking and differentiation
* Access improved changelog link parsing for faster insights
* Benefit from more accurate and intuitive terminology around security alerts
**Access the Extension**
Explore the tool and streamline your dependency management workflow:
[https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
**What’s Next**
We’re actively working on expanding support for:
* Flutter and Java (Gradle & Maven) projects
* Python environments
* Bundled dependencies to ensure the extension is fully plug-and-play
Stay tuned for more updates as we continue building tools that simplify complex workflows for modern development teams.
#libtracker#vscodeextension#dependencymanagement#cvescanning#softwarebillofmaterials#sbom#securityvulnerabilities#performanceoptimization#gitintegration#licensecompliance#expo#reactnative#yarn#yarnclassic#yarnberry#pnpm#bun#php#composer#phpcomposer
0 notes
Text
Open Source Applications & Security?

Open Source Applications & Security as much controversial as it may sound, Open source applications have been around forever. However, their requirements have skyrocketed only in the past decade. The reason for this is no mystery — lower Development Costs. This has suddenly increased the needs for data. Software development organisations regardless of its size has become dependent on Open Source Applications.
Almost 70–80 percentage of the applications today are comprised of reusable components. The irony would be the times when this open source software was considered too risky for commercial use. Albeit enterprises have gotten very good at using open source to fast-track the development cycle.
Although companies have figured out how to reuse the code effectively, they haven’t figured out how to use them securely without introducing inadvertent vulnerabilities.
The facts would point companies growing reliance towards such data without required security. Consequently, with the reliance towards such data also increases the likelihood of applications inheriting much more risks and vulnerabilities than ever before.
Now that we have established the major consumption rate and the problems, they cause let’s see how to handle this vulnerability. A popular way to track open source elements is through Software Composition Analysis (SCA)
As scary as it may sound, SCA tools are not new to the industry. SCA tools provides an insight of what they are doing with their open source platforms. SCA tools were originally born of the need to keep track of open source tools. There is no definite limit on what SCA encompasses. SCA tools offers different facilities from spreadsheets to tax deduction. Although SCA tools were on the escalator to glory they failed miserably.
The short — lived glory
In the early 2000’s firms matched codes by scanning them to data from open source elements by identifying snippets of code. However, this required professional help to remove falsified data. Fast forward a decade, companies required elements that met with their agile needs. By this time, the real-time detection of vulnerabilities and other issues at earliest started surfacing by then.
Almost a decade later now, the tools provide insights that delve a little deeper of how each element is being used. Before investing on the SCA an organization has to make sure if the SCA of their choice can cover all their coding languages. Companies new to this field may not be great at identifying unrecorded vulnerabilities, resulting in complications. On the other hand, SCA tools must work seamlessly with the build tools, databases and repositories.
DevOps — The replacement of SCA
SCA tools like I said before have been around for some time and follows native designs. Hence it lacks when used alongside of a system’s security lacked agility which became a demanding need by organizations. DevOps handles implementing new changes on infrastructure, embarking changes easier for Developers.
No matter what, SCA still is in practise. However, with almost every organisation switching to DevOps, reasons it is because of the seamless security intertwine to their workflow that redefines transparency for its developers.
Wrap up
I don’t want to turn this article into a debate, all statements here are facts learned and collected to the best of my understanding. I want you to be your own judge. If you think SCA tools might be the best option for your organisation’s needs, go for it. Or if DevOps suits your needs better go for it.
#**#OpenSourceSecurity#SoftwareCompositionAnalysis#SCA#DevOps#OpenSourceApplications#SecurityVulnerabilities#AgileDevelopment**
0 notes
Text
Young accountants: Choose your own adventure
New entrants to the profession face more decisions more often than ever in building their accounting careers. Expert weigh in with their best career advice.
The IRS failed to address literally tens of thousands of unresolved security vulnerabilities, according to the Treasury Inspector General for Tax Administration.
#accountants#newentrants#accountingcareers#SecurityVulnerabilities#treasuryinspectorgeneral#cpafirm#cpapartnersllc#IRS
0 notes
Text
The Most Severe Data Leakage Incident in History: 3 Billion People Affected, Cybersecurity Facing Unprecedented Challenges
Two major data leakage incidents that occurred recently have once again attracted widespread attention globally. Incident One: One of the largest hacker attacks in history led to the leakage of data of nearly 3 billion people; Incident Two: The Polish Anti-Doping Agency (POLADA) also suffered a hacker attack, resulting in the leakage of important data. These incidents not only highlight the severe challenges faced by cybersecurity but also have a profound impact on the global network environment.
This one of the largest hacker attacks in history involves the leakage of personal information of nearly 3 billion people, including sensitive information such as full names, addresses, and social security numbers, and is regarded as one of the largest data leakage incidents in history. The system of the Polish Anti-Doping Agency (POLADA) was hacked, leading to the leakage of agency data and affecting the normal operation of the agency.
The impacts of these events are extremely widespread. Firstly, it poses a huge risk to personal privacy. Massive data leakage makes hundreds of millions of people face the risk of privacy leakage, increasing the possibility of identity theft and financial fraud. Secondly, the security of enterprises and government agencies has been questioned, which will affect the trust of users in these institutions. In addition, data leakage may cause relevant institutions to face huge fines, legal lawsuits, and reputation losses, thereby affecting economic activities. Finally, such incidents prompt governments of various countries to strengthen the formulation and enforcement of data protection regulations, increasing regulatory pressure.
These events once again remind people of the importance of strengthening information security protection measures at the individual and organizational levels. Individuals should adopt stricter password management strategies and use methods such as two-factor authentication to protect the security of their accounts. Enterprises need to build a more solid network security defense system and regularly conduct security audits and vulnerability scans to ensure data security.
As a professional cybersecurity enterprise, Knownsec has accumulated rich experience and technical capabilities in preventing and responding to cybersecurity threats. Relying on its strong security research team and advanced technical means, Knownsec can help enterprises effectively identify potential security risks and provide comprehensive security solutions.
For example, in a large-scale attack against an e-commerce platform, Knownsec responded quickly. Through the emergency handling process, it successfully prevented further data leakage and assisted the customer in repairing system vulnerabilities, enhancing its network security protection capabilities. In addition, after a financial institution encountered a data leakage, Knownsec not only assisted it in conducting a thorough security review but also provided it with technical support in data encryption and access control to ensure the security and compliance of the data.
With the continuous upgrading of network attack methods, ensuring cybersecurity has become an unavoidable responsibility for enterprises and individuals.
#DataLeakage#CybersecurityChallenges#HackerAttacks#PrivacyRisk#NetworkSecuritySolutions#Knownsec#DataProtection#SecurityVulnerabilities#CyberThreats
0 notes
Text
What are OAuth Security Vulnerabilities | CybersecurityTv
youtube
Learn about OAuth security vulnerabilities in this informative video on CybersecurityTV! Discover the risks and how to protect your online data.
Don't miss this essential information.
#OAuthSecurity#Cybersecurity#OnlineProtection#DataSecurity#HackingRisks#SecurityVulnerabilities#InternetSafety#Authentication#CyberThreats#StayInformed#Youtube
1 note
·
View note
Text
Benefits of Using Computeroids Driver Updater
Time-SavingManually searching for drivers can be time-intensive. Computeroids automates the process, saving hours of effort.Increased StabilityOutdated or mismatched drivers are often the root cause of system errors and crashes. Regular updates can significantly enhance stability.Enhanced SecurityVulnerabilities in outdated drivers can be exploited by malware. By keeping your drivers current, you minimize security risks.Ease of UseWith an intuitive interface, even non-tech-savvy users can navigate and use the tool effectively.
0 notes
Photo

The Risks of DIY SQL Recovery and When to Call in the Experts. DIY SQL recovery may seem like a simple task but can carry significant risks and should never be attempted without proper training and preparation.
0 notes
Photo

Want safety for your remote wi-fi networks? Reach out to us and we will implement network products that will keep your remote work experience secure.
#remoteaccesssecurity#remoteaccesspractices#potentialrisksassociated#remoteaccessriskassessment#securityvulnerabilities#remoteaccessrisk
0 notes
Text
Allowance of Files Deletion from the Server from Complete FTP Path Traversal
The security vulnerability which was found in the file transfer software in which the allowance is given to the Complete FTP unauthenticated attackers for making the deletion of the arbitrary files which are present on the installations which are affected.
#vulnerability#cybersecurity#attackers#securityvulnerability#cybersecurityresearchers#unauthenticatedattackers#vulnerabilityexploitation
0 notes
Photo

Introduction to Ecommerce Security Vulnerabilities and Methods to Conquer it
https://www.smartstorez.com/blog/ecommerce-security-vulnerabilities/
0 notes
Text
Android apps used by troops in combat contained vulnerabilities
Android apps used by troops in combat contained vulnerabilities
Two Android apps used by the US military in live combat situations contained severe vulnerabilities that could have allowed attackers to gain access to troops’ information, a Navy Inspector General reportrevealed. The mobile apps offered real-time messaging to coordinate with other military branches, displayed mission objectives and goals, showed satellite images of surroundings and…
View On WordPress
#androidapps#apass#apps#darpa#gear#inspectorgeneral#kilswitch#military#navy#navyinspectorgeneral#Security#securityvulnerabilities
0 notes
Text
Vulnerability of the Maritime Transportation Security (MTS)
Vulnerability of the Maritime Transportation Security (MTS)
Select a peer reviewed article that is focused on one of the following subject areas: Port SecurityVulnerability of the Maritime Transportation Security (MTS)Vulnerability to world shippingThreats presented within the Maritime focused cyber spaceMaritime cyber securityTreatment of longshoreman in developing countriesResilience and Maritime Security Include the following information: Article…
View On WordPress
0 notes
Text
JWT Security Vulnerabilities | CyberSecurityTv
youtube
In this episode of CyberSecurityTv, They dive deep into the world of JWT (JSON Web Tokens) and uncover potential security vulnerabilities. Join and explore the ins and outs of JWT authentication and discover ways to protect your applications from potential threats. Whether you're a developer, security enthusiast, or just curious about the world of cybersecurity, this video is a must-watch!
#CyberSecurity#JWT#SecurityVulnerabilities#Authentication#WebSecurity#CyberThreats#TokenSecurity#InfoSec#DataProtection#WebDevelopment#CyberAwareness#Youtube
0 notes
Photo

Mozilla Patch Two Zero-day Bugs That Were Under Exploit With Firefox 74.0.1 #browser #browservulnerability #bugs #firefox #firefox74 #firefoxwebbrowser #firefoxzeroday #flaw #flaws #mozilla #mozillafirefox #mozillafirefoxbrowserextension #mozillafirefoxextension #mozillapatch #securityvulnerabilities #useafterfree #vulnerabilities #vulnerability #webbrowser #zeroday #zero-dayflaw #zero-dayvulnerability #zeroday #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes