#T-SQL monitoring scripts
Explore tagged Tumblr posts
Text
Navigating the Nuances of Windows Paging in SQL Server 2022
In the realm of SQL Server performance, the subject of Windows paging often comes with a dash of controversy. It’s a nuanced discussion, not a black-and-white issue. While Windows paging is not inherently bad, mismanagement or over-reliance on it can lead to a slew of problems, affecting the smooth operation of SQL Server. Below, let’s explore why Windows paging happens, when it becomes…
View On WordPress
#Memory management in SQL Server#Page Life Expectancy#SQL Server performance#T-SQL monitoring scripts#Windows paging
0 notes
Text
Các Tính Năng Bảo Mật Tiên Tiến Trên Cloud Server: Giải Pháp Ngăn Ngừa Tấn Công Mạng
Trong kỷ nguyên số, các doanh nghiệp và tổ chức đang ngày càng chuyển sang sử dụng Cloud Server như một giải pháp hạ tầng linh hoạt, tiết kiệm chi phí và có khả năng mở rộng mạnh mẽ. Tuy nhiên, với sự phát triển nhanh chóng của các mối đe dọa an ninh mạng, bảo mật trở thành một yếu tố quan trọng khi sử dụng máy chủ ảo đám mây. Để đảm bảo an toàn cho dữ liệu và ứng dụng, các nhà cung cấp Cloud Server đã triển khai nhiều tính năng bảo mật tiên tiến để ngăn ngừa các cuộc tấn công mạng. Bài viết này sẽ điểm qua một số tính năng bảo mật quan trọng và cách chúng giúp bảo vệ các hệ thống đám mây khỏi các nguy cơ an ninh.
Mã hóa Dữ liệu (Encryption)
Một trong những tính năng bảo mật cơ bản và quan trọng nhất trên Cloud Server là mã hóa dữ liệu. Khi dữ liệu được mã hóa, nó trở thành không thể đọc được mà không có khóa giải mã chính. Dữ liệu có thể được mã hóa khi lưu trữ (encryption at rest) và trong quá trình truyền tải (encryption in transit). Việc mã hóa đảm bảo rằng ngay cả khi dữ liệu bị xâm nhập, tin tặc cũng không thể đọc hay sử dụng dữ liệu nếu không có khóa giải mã thích hợp.
Mã hóa khi lưu trữ (At Rest Encryption): Bảo vệ dữ liệu khi nó được lưu trữ trên các ổ đĩa hoặc các hệ thống đám mây.
Mã hóa khi truyền tải (In Transit Encryption): Đảm bảo rằng dữ liệu không bị rò rỉ hoặc bị đánh cắp khi di chuyển qua các kết nối mạng (như SSL/TLS).
Xác thực Đa Yếu Tố (Multi-Factor Authentication - MFA)
Xác thực đa yếu tố là một lớp bảo vệ thêm giúp bảo vệ tài khoản người dùng khỏi các cuộc tấn công mạng, đặc biệt là tấn công brute force (tấn công dò mật khẩu). MFA yêu cầu người dùng cung cấp hai hoặc nhiều yếu tố xác thực trước khi có thể truy cập vào hệ thống. Thông thường, yếu tố xác thực này bao gồm:
Yếu tố biết (Something you know): Mật khẩu hoặc mã PIN.
Yếu tố sở hữu (Something you have): Một mã được gửi qua SMS hoặc ứng dụng xác thực.
Yếu tố đặc điểm sinh trắc học (Something you are): Vân tay, nhận diện khuôn mặt hoặc quét mống mắt.
Xác thực đa yếu tố ngăn chặn việc đăng nhập trái phép ngay cả khi tin tặc biết mật khẩu của người dùng.
Tường lửa (Firewall) và Hệ thống Phát hiện Xâm nhập (IDS)
Tường lửa là một yếu tố quan trọng trong việc bảo vệ Cloud Server khỏi các tấn công từ bên ngoài. Nó giám sát và kiểm soát lưu lượng mạng vào và ra, chỉ cho phép các kết nối hợp lệ. Các nhà cung cấp Cloud Server thường tích hợp tường lửa với các hệ thống phát hiện xâm nhập (IDS) và phòng chống xâm nhập (IPS) để phát hiện và ngăn chặn các cuộc tấn công có chủ đích.
Tường lửa ứng dụng (WAF - Web Application Firewall): Bảo vệ các ứng dụng web khỏi các cuộc tấn công phổ biến như SQL injection, cross-site scripting (XSS), và các mối đe dọa khác.
Hệ thống phát hiện xâm nhập (IDS): Giám sát và phân tích lưu lượng mạng để phát hiện hành vi bất thường có thể là dấu hiệu của một cuộc tấn công.
Quản lý Quyền Truy Cập (Identity and Access Management - IAM)
Quản lý quyền truy cập giúp đảm bảo rằng chỉ những người có quyền mới có thể truy cập vào các tài nguyên quan trọng trong môi trường đám mây. Hệ thống quản lý danh tính và quyền truy cập (IAM) cho phép các tổ chức phân quyền truy cập cho người dùng và nhóm người dùng dựa trên các vai trò và nhu cầu công việc của họ.
Quy tắc nguyên tắc "ít quyền nhất" (Least Privilege): Mỗi người dùng chỉ có quyền truy cập những tài nguyên mà họ thực sự cần để thực hiện công việc của mình.
Kiểm tra và audit quyền truy cập: Quản lý IAM cung cấp các báo cáo và theo dõi để kiểm soát và đánh giá ai đã truy cập vào hệ thống và khi nào.
Giám sát và Báo cáo An ninh (Security Monitoring and Reporting)
Giám sát liên tục là một phương pháp quan trọng trong việc phát hiện sớm các mối đe dọa và tấn công. Công cụ giám sát bảo mật cung cấp các chỉ số thời gian thực về hoạt động của hệ thống, giúp phát hiện và ứng phó kịp thời với các sự cố an ninh.
Giám sát lưu lượng mạng và nhật ký hệ thống: Các công cụ giám sát giúp theo dõi lưu lượng mạng và phân tích các sự kiện đáng ngờ.
Cảnh báo tự động: Các hệ thống bảo mật có thể gửi cảnh báo tự động khi phát hiện các hành vi không bình thường hoặc có nguy cơ tấn công.
Tính Năng Backup và Phục Hồi (Backup and Disaster Recovery)
Mặc dù các biện pháp bảo mật có thể giúp ngăn ngừa hầu hết các cuộc tấn công, nhưng không thể loại bỏ hoàn toàn rủi ro. Vì vậy, việc sao lưu dữ liệu và có kế hoạch phục hồi sau thảm họa là một phần quan trọng của chiến lược bảo mật trên Cloud Server.
Sao lưu thường xuyên: Dữ liệu quan trọng cần được sao lưu vào các vị trí an toàn để có thể phục hồi nếu có sự cố xảy ra.
Phục hồi sau thảm họa: Các công cụ phục hồi giúp nhanh chóng khôi phục hệ thống trong trường hợp xảy ra tấn công hoặc lỗi hệ thống nghiêm trọng.
Cập nhật và Vá Lỗ Bảo Mật (Security Patching)
Các nhà cung cấp Cloud Server thường xuyên cập nhật các hệ thống của họ để vá các lỗ hổng bảo mật. Cập nhật và vá lỗi kịp thời là một trong những biện pháp bảo mật quan trọng giúp bảo vệ máy chủ đám mây khỏi các cuộc tấn công dựa trên lỗ hổng.
Kết Luận
Bảo mật trên Cloud Server không chỉ dựa vào một tính năng duy nhất, mà là sự kết hợp của nhiều công nghệ và phương pháp để bảo vệ dữ liệu và ứng dụng khỏi các mối đe dọa mạng. Các tính năng bảo mật tiên tiến như mã hóa, xác thực đa yếu tố, tường lửa, quản lý quyền truy cập, giám sát bảo mật và sao lưu dữ liệu giúp xây dựng một môi trường an toàn và đáng tin cậy cho các doanh nghiệp khi sử dụng dịch vụ Cloud Server.
Để đảm bảo an toàn tối đa, các tổ chức cần liên tục theo dõi, cập nhật và cải thiện các biện pháp bảo mật của mình, đồng thời kết hợp với các nhà cung cấp Cloud có uy tín để tận dụng các công nghệ bảo mật tiên tiến nhất.
Thông tin chi tiết: https://vndata.vn/cloud-server/
0 notes
Text
Lead Consultant - Log Analytics/Intelligent Monitoring/Automation
-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft Power Platforms (Power Apps/Power Automate/ Power BI… Apply Now
0 notes
Text
Lead Consultant - Log Analytics/Intelligent Monitoring/Automation
-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft Power Platforms (Power Apps/Power Automate/ Power BI… Apply Now
0 notes
Text
Bryan Strauch is an Information Technology specialist in Morrisville, NC
Resume: Bryan Strauch
[email protected] 919.820.0552(cell)
Skills Summary
VMWare: vCenter/vSphere, ESXi, Site Recovery Manager (disaster recovery), Update Manager (patching), vRealize, vCenter Operations Manager, auto deploy, security hardening, install, configure, operate, monitor, optimize multiple enterprise virtualization environments
Compute: Cisco UCS and other major bladecenter brands - design, rack, configure, operate, upgrade, patch, secure multiple enterprise compute environments.
Storage: EMC, Dell, Hitachi, NetApp, and other major brands - connect, zone, configure, present, monitor, optimize, patch, secure, migrate multiple enterprise storage environments.
Windows/Linux: Windows Server 2003-2016, templates, install, configure, maintain, optimize, troubleshoot, security harden, monitor, all varieties of Windows Server related issues in large enterprise environments. RedHat Enterprise Linux and Ubuntu Operating Systems including heavy command line administration and scripting.
Networking: Layer 2/3 support (routing/switching), installation/maintenance of new network and SAN switches, including zoning SAN, VLAN, copper/fiber work, and other related tasks around core data center networking
Scripting/Programming: SQL, Powershell, PowerCLI, Perl, Bash/Korne shell scripting
Training/Documentation: Technical documentation, Visio diagramming, cut/punch sheets, implementation documentations, training documentations, and on site customer training of new deployments
Security: Alienvault, SIEM, penetration testing, reporting, auditing, mitigation, deployments
Disaster Recovery: Hot/warm/cold DR sites, SAN/NAS/vmware replication, recovery, testing
Other: Best practice health checks, future proofing, performance analysis/optimizations
Professional Work History
Senior Systems/Network Engineer; Security Engineer
September 2017 - Present
d-wise technologies
Morrisville, NC
Sole security engineer - designed, deployed, maintained, operated security SIEM and penetration testing, auditing, and mitigation reports, Alienvault, etc
responsibility for all the systems that comprise the organizations infrastructure and hosted environments
main point of contact for all high level technical requests for both corporate and hosted environments
Implement/maintain disaster recovery (DR) & business continuity plans
Management of network backbone including router, firewall, switch configuration, etc
Managing virtual environments (hosted servers, virtual machines and resources)
Internal and external storage management (cloud, iSCSI, NAS)
Create and support policies and procedures in line with best practices
Server/Network security management
Senior Storage and Virtualization Engineer; Datacenter Implementations Engineer; Data Analyst; Software Solutions Developer
October 2014 - September 2017
OSCEdge / Open SAN Consulting (Contractor)
US Army, US Navy, US Air Force installations across the United States (Multiple Locations)
Contract - Hurlburt Field, US Air Force:
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Connected and zoned new NetApp storage solution to blades through old and new fabric switches
Implemented new network and SAN fabric switches
Network: Nexus C5672 switches
SAN Fabric: MDS9148S
Decommissioned old blade center environment, decommissioned old network and storage switches, decommissioned old SAN solution
Integrated new blades into VMWare environment and migrated entire virtual environment
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new/existing equipment
Cable management and labeling of all new and existing solutions
Implemented VMWare auto deploy for rapid deployment of new VMWare hosts
Contract - NavAir, US Navy:
Upgraded and expanded an existing Cisco UCS environment
Cable management and labeling of all new and existing solutions
Created Visio diagrams and documentation for existing and new infrastructure pieces
Full health check of entire environment (blades, VMWare, storage, network)
Upgraded entire environment (firmware and software versions)
Assessed and mitigated best practice concerns across entire environment
Trained on site operational staff on new/existing equipment
Contract - Fort Bragg NEC, US Army:
Designed and implemented a virtualization solution for the US ARMY.
This technology refresh is designed to support the US ARMY's data center consolidation effort, by virtualizing and migrating hundreds of servers.
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Implemented SAN fabric switches
SAN Fabric: Brocade Fabric Switches
Connected and zoned new EMC storage solution to blades
Specific technologies chosen for this solution include: VMware vSphere 5 for all server virtualization, Cisco UCS as the compute platform and EMC VNX for storage.
Decommissioned old SAN solution (HP)
Integrated new blades into VMWare environment and migrated entire environment
Physical to Virtual (P2V) conversions and migrations
Migration from legacy server hardware into virtual environment
Disaster Recovery solution implemented as a remote hot site.
VMware SRM and EMC Recoverpoint have been deployed to support this effort.
The enterprise backup solution is EMC Data Domain and Symantec NetBackup
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new equipment
Cable management and labeling of all new solutions
Contract - 7th Signal Command, US Army:
Visited 71 different army bases collecting and analyzing compute, network, storage, metadata.
The data collected, analyzed, and reported will assist the US Army in determining the best solutions for data archiving and right sizing hardware for the primary and backup data centers.
Dynamically respond to business needs by developing and executing software solutions to solve mission reportable requirements on several business intelligence fronts
Design, architect, author, implement in house, patch, maintain, document, and support complex dynamic data analytics engine (T-SQL) to input, parse, and deliver reportable metrics from data collected as defined by mission requirements
From scratch in house BI engine development, 5000+ SQL lines (T-SQL)
Design, architect, author, implement to field, patch, maintain, document, and support large scale software tools for environmental data extraction to meet mission requirements
Large focus of data extraction tool creation in PowerShell (Windows, Active Directory) and PowerCLI (VMWare)
From scratch in house BI extraction tool development, 2000+ PowerShell/PowerCLI lines
Custom software development to extract data from other systems including storage systems (SANs), as required
Perl, awk, sed, and other languages/OSs, as required by operational environment
Amazon AWS Cloud (GovCloud), IBM SoftLayer Cloud, VMWare services, MS SQL engines
Full range of Microsoft Business Intelligence Tools used: SQL Server Analytics, Reporting, and Integration Services (SSAS, SSRS, SSIS)
Visual Studio operation, integration, and software design for functional reporting to SSRS frontend
Contract - US Army Reserves, US Army:
Operated and maintained Hitachi storage environment, to include:
Hitachi Universal Storage (HUS-VM enterprise)
Hitachi AMS 2xxx (modular)
Hitachi storage virtualization
Hitachi tuning manager, dynamic tiering manager, dynamic pool manager, storage navigator, storage navigator modular, command suite
EMC Data Domains
Storage and Virtualization Engineer, Engineering Team
February 2012 – October 2014
Network Enterprise Center, Fort Bragg, NC
NCI Information Systems, Inc. (Contractor)
Systems Engineer directly responsible for the design, engineering, maintenance, optimization, and automation of multiple VMWare virtual system infrastructures on Cisco/HP blades and EMC storage products.
Provide support, integration, operation, and maintenance of various system management products, services and capabilities on both the unclassified and classified network
Coordinate with major commands, vendors, and consultants for critical support required at installation level to include trouble tickets, conference calls, request for information, etc
Ensure compliance with Army Regulations, Policies and Best Business Practices (BBP) and industry standards / best practices
Technical documentation and Visio diagramming
Products Supported:
EMC VNX 7500, VNX 5500, and VNXe 3000 Series
EMC FAST VP technology in Unisphere
Cisco 51xx Blade Servers
Cisco 6120 Fabric Interconnects
EMC RecoverPoint
VMWare 5.x enterprise
VMWare Site Recovery Manager 5.x
VMWare Update Manager 5.x
VMWare vMA, vCops, and PowerCLI scripting/automation
HP Bladesystem c7000 Series
Windows Server 2003, 2008, 2012
Red Hat Enterprise and Ubuntu Server
Harnett County Schools, Lillington, NC
Sr. Network/Systems Administrator, August 2008 – June 2011
Systems Administrator, September 2005 – August 2008
Top tier technical contact for a 20,000 student, 2,500 staff, 12,000 device environment District / network / datacenter level design, implementation, and maintenance of physical and virtual servers, routers, switches, and network appliances
Administered around 50 physical and virtual servers, including Netware 5.x/6.x, Netware OES, Windows Server 2000, 2003, 2008, Ubuntu/Linux, SUSE, and Apple OSX 10.4-10.6
Installed, configured, maintained, and monitored around 175 HP Procurve switches/routers Maintained web and database/SQL servers (Apache, Tomcat, IIS and MSSQL, MySQL) Monitored all network resources (servers, switches, routers, key workstations) using various monitoring applications (Solarwinds, Nagios, Cacti) to ensure 100% availability/efficiency Administered workstation group policies and user accounts via directory services
Deployed and managed applications at the network/server level
Authored and implemented scripting (batch, Unix) to perform needed tasks
Monitored server and network logs for anomalies and corrected as needed
Daily proactive maintenance and reactive assignments based on educational needs and priorities Administered district level Firewall/IPS/VPN, packet shapers, spam filters, and antivirus systems Administered district email server and accounts
Consulted with heads of all major departments (finance, payroll, testing, HR, child nutrition, transportation, maintenance, and the rest of the central staff) to address emergent and upcoming needs within their departments and resolve any critical issues in a timely and smooth manner Ensure data integrity and security throughout servers, network, and desktops
Monitored and corrected all data backup procedures/equipment for district and school level data
Project based work through all phases from design/concept through maintenance
Consulted with outside contractors, consultants, and vendors to integrate and maintain various information technologies in an educational environment, including bid contracts
Designed and implemented an in-house cloud computing infrastructure utilizing a HP Lefthand SAN solution, VMWare’s ESXi, and the existing Dell server infrastructure to take full advantage of existing technologies and to stretch the budget as well as provide redundancies
End user desktop and peripherals support, training, and consultation
Supported Superintendents, Directors, all central office staff/departments, school administration offices (Principals and staff) and classroom teachers and supplementary staff
Addressed escalations from other technical staff on complex and/or critical issues
Utilized work order tracking and reporting systems to track issues and problem trends
Attend technical conferences, including NCET, to further my exposure to new technologies
Worked in a highly independent environment and prioritized district needs and workload daily Coordinated with other network admin, our director, and technical staff to ensure smooth operations, implement long term goals and projects, and address critical needs
Performed various other tasks as assigned by the Director of Media and Technology and
Superintendents
Products Supported
Microsoft XP/Vista/7 and Server 2000/2003/2008, OSX Server 10.x, Unix/Linux
Sonicwall NSA E8500 Firewall/Content filter/GatewayAV/VPN/UTM Packeteer 7500 packet shaping / traffic management / network prioritization
180 HP Procurve L2/L3 switches and HP Procurve Management Software
Netware 6.x, Netware OES, SUSE Linux, eDirectory, Zenworks 7, Zenworks 10/11
HP Lefthand SAN, VMWare Server / ESXi / VSphere datacenter virtualization
Solarwinds Engineer Toolset 9/10 for Proactive/Reactive network flow monitoring
Barracuda archiving/SPAM filter/backup appliance, Groupwise 7/8 email server
Education
Bachelor of Science, Computer Science
Minor: Mathematics
UNC School System, Fayetteville State University, May 2004
GPA: 3
High Level Topics (300+):
Data Communication and Computer Networks
Software Tools
Programming Languages
Theory of Computation
Compiler Design Theory
Artificial Intelligence
Computer Architecture and Parallel Processing I
Computer Architecture and Parallel Processing II
Principles of Operating Systems
Principles of Database Design
Computer Graphics I
Computer Graphics II
Social, Ethical, and Professional Issues in Computer Science
Certifications/Licenses:
VMWare VCP 5 (Datacenter)
Windows Server 2008/2012
Windows 7/8
Security+, CompTIA
ITILv3, EXIN
Certified Novell Administrator, Novell
Apple Certified Systems Administrator, Apple
Network+ and A+ Certified Professional, CompTIA
Emergency Medical Technician, NC (P514819)
Training:
Hitachi HUS VM
Hitachi HCP
IBM SoftLayer
VMWare VCP (datacenter)
VMWare VCAP (datacenter)
EMC VNX in VMWare
VMWare VDI (virtual desktops)
Amazon Web Services (AWS)
Emergency Medical Technician - Basic, 2019
EMT - Paramedic (pending)
1 note
·
View note
Text
Lectures - Week 5 (Mixed)
Vulnerabilities
One of the most fundamental concepts in security is the idea of a vulnerability - a flaw in the design of a system which can be used to compromise (or cause an unintended usage of) the system. A large majority of bugs in programming are a result of memory corruptions which can be abused to take control - the most ubiquitous example of this is the buffer overflow; the idea that you can overwrite other data alongside a variable which can change both data and control of a program. The common case is when programmers fail to validate the length of the input when reading in a string in C. Another fairly common bug relates to the overflow of unsigned integers; failing to protect against the wraparound can have unintended consequences in control flow.
‘NOP Sled’
Richard also mentioned in the 2016 lectures the idea of a NOP sled which I found quite interesting. The idea is that due to run time differences and randomisation of the stack, the address the program will jump to (from the return address) can sometimes be difficult to predict. So to make it more likely it will jump where the attack wants, he converts a large set of memory to NOP (no operation) instructions which will just skip to the next one; then finally after the “NOP sled” his code will execute.
printf(”%s Printf Vulnerabilities”);
One of the most hilarious programming vulnerabilities related to the usage of the printf function. Basically if you have an input which is accepted from the terminal and you plug this (without parsing) into a printf, an attacker could potentially feed in an input such as “%s”. (i.e. the title) Now since you haven’t specified a 2nd argument, it will just keep reading all the variables in memory until you hit a “\0″. In fact you can abuse this even further to overwrite memory with the “%n” format string - it will overwrite an integer with the number of characters written so far.
Handling Bugs
Many of the bugs we know of today are actually reported in online databases such as the National Vulnerability Database or Common Vulnerability & Exposures (CVE) Databases. There is actually lots of pretty cool examples online in these, however most of these have been actually fixed - we call them zero day vulnerabilities if the vendor hasn’t fixed them (and if they are then abused then zero day exploits).
When working in security, it’s important to understand the potential legal consequences associated with publicly releasing damaging vulnerabilities in software. This is where responsible disclosure comes in - the idea that if you find a bug you disclose it to a software vendor first and then give them a reasonable period of time to fix it first. I think I discussed an example from Google’s Project Zero Team a couple weeks ago - however just from a quick look there was a case in March where their team released the details on a flaw in the macOS’s copy-on-write (CoW) after the 90 day period for patching. (it’s important to note they gave them reasonable time to fix it)
OWASP Top 10
This was a pretty cool website we got referred to mainly regarding the top bugs relating to web security (link); I’ll give a brief overview here:
Injection - sends invalid data to get software to produce an unintended flow of control (i.e. SQL injection)
Broken authentication - logic issues in authentication mechanisms
Sensitive data exposure - leaks in privacy of sensitive customer data
XML External Entities (XXE) - parsing XML input with links to external bodies
Broken action control - improper access checks when accessing data
Security misconfigurations - using default configs, failing to patch flaws, unnecessary services & pages, as well as unprotected files
Cross-Site Scripting (XSS) - client injects Javascript into a website which is displayed to another user
Insecure deserialisation - tampering with serialization of user data
Using components with known vulnerabilities - out of date dependencies
Insufficient logging and monitoring - maintaining tabs on unusual or suspicious activity, as well as accesses to secure data
Some Common Bugs
Just a couple of the bugs that were explored in some of the 2016 lecture videos:
Signed vs unsigned integers casts - without proper checks can lead to unintended control flow
Missing parenthesis after if statement - only executes next line and not all within the indentation
Declaring array sizes wrong - buf[040] will be interpreted as base 8
Wrong comparators - accidentally programming ‘=‘ when you intended ‘==‘
A lot of the more common bugs we used to have are getting a lot easier to detect in the compilation process; GCC has a lot of checks built in. Valgrind is also a really awesome tool to make sure your not making any mistakes with memory.
WEP Vulnerability
I actually discussed this idea already in the week 1 lectures here - just for the sake of revision I will give a basic overview here. The basic idea is that WEP uses a stream cipher RC4 which XORs the message with a key; however the issue is that we know information about the structure of TCP/IP packets. Within a local network the local IPs are usually of the form A.B.C.D (i.e. 192.168.20.4 for a specific computer) where each letter represents a byte in the range 0-255. (0-255 are usually reserved and not used for computers in the network) Due to subnetting (i.e. with a subnet mask 255.255.255.0 on private network) the last byte D is usually the only one that changes - this means we effectively have 254 combinations.
Since we know where the destination address is located within the packet, an attacker can potentially record a packet and modify this last byte - they can send out all 256 possible combinations to the router (remember it’s encrypted so we can’t limit it to 254). The router will then decrypt the message and then encrypt it with the key used for communications with the attacker - and voila the system is compromised.
Hashes

Richard gave a brief overview of the basis of many of our hash functions which is the Merkle-Damgard construction. The basic idea behind it is to break the message into blocks - the size varies on the hash type and if its not a multiple of the required length then we need to apply a MD-compliant padding function. This usually occurs with Merkle-Damgard strengthening which involves encoding the length of the original message into the padding.
To start the process of hashing we utilise an initialisation vector (number specific to the algorithm) and combine it with the first message block using a certain compression function. The output of this is then combined with the 2nd message block and so forth. When we get to the end we apply a finalisation function which typically involves another compression function (sometimes the same) which will reduce the large internal state to the required hash size and provide a better mixing of the bits in the final hash sum.
Length Extension Attacks
I think after looking at the Merkle-Damgard construction it now becomes pretty obvious why using MACs of the form h(key|data) where the length of the data is known are vulnerable to length-extension attacks. All you need to be able to reverse in the above construction is the finalisation function and the extra padding (which is dependent upon the length which we’re assuming we know); then you can keep adding whatever message blocks you want to the end!
Digital Signatures
The whole idea behind these signatures is providing authentication - the simplest method of this is through asymmetric key encryption (i.e. RSA). If your given a document, you can just encrypt it with your private key - to prove to others that you indeed signed it, they can attempt to decrypt it with your public key. There is a problem with this approach however - encryption takes a lot of computation and when the documents become large it gets even worse. The answer to this is to use our newfound knowledge of hashing for data integrity - if we use a hash (’summary of the document’), we can just encrypt this with our private key as a means of signing it!
Verifying Websites
One of the hardest issues we face with the ‘interwebs’ is that it is very difficult to authenticate an entity on the other end. We’ve sort of scrambled together a solution to this for verifying websites - certificate authorities. (I could go on for ages about the problems with these being ‘single points of failure’ but alas I don’t have time)
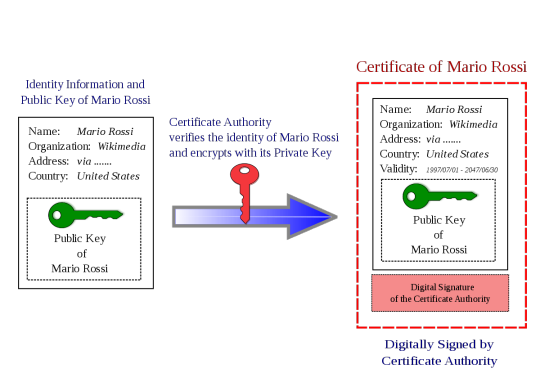
The idea behind these bodies is that a website will register with the entity with a specific public key. The CA will then link this public key (in a “big ol’ secure database”) with the ‘identity’ of the website. To understand how it works its best to consider the example of when you access any website with HTTPS. (i.e. SSL) When you visit www.example.com, they will then provide their public key and a digital signature of key (signed by the cert authority’s private key) in the form of a X.509 certificate. The user will have access to CA’s public key as part of their browser and will then be able to verify the identity of the website. (the cert is encrypted with the CA’s private key - see above image) An attacker is unable to fake it as they don’t know the certificate authorities’ private key.
Attacking Hashed Passwords
Given there is only a limited number of potential hashes for each algorithm, there is a growing number of websites online which provide databases of plaintext and their computed hashes - these are what we refer to as hash tables. We can check a hash very quickly against all the hashes in this database - if we find a match, we either know the password or have found a collision.
Rainbow tables are a little more complex - in order to make one you need a hashing function (the same as the password) and a reduction function; the latter is used to convert the hash into text (i.e. a base64 encode and truncation). These tables are made of a number of ‘chains’ of a specified length (let’s say we choose 1,000,000) - to create a chain you start with a random seed then apply both the above functions to this seed. You then iteratively do this process another 1,000,000 times (chosen length) and store the final seed and value (only these). In order to try and determine a match to the rainbow table, you apply the same two functions to the password for the required length - however, at each step you compare the hash to the result of each of the chains in the table. If you find a match, you can reproduce the password.
Both of the attacks against password hashes described above rely on an attacker doing a large amount of work in advance, which they will hopefully be able to use in cracking many passwords in the future. (it’s basically a space-time tradeoff) An easy way we can destroy all the work they have done is through a process known as salting. Basically what you do is generate a random string which you concatenate with the password when creating a hash - you need to store this alongside the password in order to check it in future. This means an attacker can’t use pre-computed tables on your hash; they have to do all the work again for your particular salt!
Richard discussed another interesting concept called ‘key stretching’ in the lectures - it’s basically the idea that you can grab a ‘weak password hash’ and continuously hash it with a combination of the (’hash’ + ‘password’ + ‘salt’). This process of recursively hashing makes it insanely difficult for an attacker to bruteforce. This is combined with the effects of a ‘salt’ which (on its own) renders rainbow tables (’pre-computed hashes’) useless.
Signing Problems with Weak Hashes
One of the problems with using a hash which is vulnerable to second-preimage attacks is that it becomes a lot easier to sign a fake document. Consider the example of a PDF document certifying that I give you $100. If you wanted you could modify the $100 to $100,000, however this would change the resultant hash. However since it’s a PDF you could modify empty attribute fields or add whitespace such that you can modify the hash an enormous amount of times (i.e. to bruteforce the combinations). Since the hash is vulnerable to second-preimage this means that given an input x (the original signed document) we are able to find an x’ (the fake signed document) such that h(x) = h(x’).
Dr Lisa Parker (guest speaker)
I wasn’t able to make the morning lecture, although I will try and summarise my understanding of the key points from this talk:
More holistic approaches to systems improvement have better outcomes (’grassroots approach’ is just as important as targeted)
Unconscious bias is present across a wide variety of industries (i.e. judges harsher before lunch, doctors prescribing drugs for free lunch)
Codes of conduct intended to reduce corruption; pharmaceuticals try to dodge with soft bribes, advertising, funding research
Transparent reporting reduces malpractice
Enforcing checklists useful for minimising risk
OPSEC Overview (extended)
We traditionally think of OPSEC has been based in the military, however many of the principles can apply in more everyday scenarios:
Identifying critical information
Analysis of threats
Analysis of vulnerabilities
Assessment of risk
Application of appropriate OPSEC measures
A lot of the ideas behind gathering information (recon) revolve around collecting “random data”, which at first may not appear useful, however after managing to piece them together, they are. One of the quotes from Edward Snowden (I think) I found quite interesting, “In every step, in every action, in every point involved, in every point of decision, you have to stop and reflect and think, “What would be the impact if my adversary were aware of my activities?””. I think it’s quite powerful to think about this - however at the same time we don’t want to live with complete unrealistic paranoia and live as a hermit in the hills.
One of the easiest ways to improve your OPSEC is through limiting what you share online, especially with social media sites. Some of the basic tips were:
Don’t share unless you need to
Ensure it can’t be traced (unless you want people to know)
Avoid bringing attention to yourself
You can try and conceal your identity online through things like VPNs and Tor Browser. It is important that in identities you have online that you don’t provide a means to link them in any way (i.e. a common email) if you don’t want someone to be able to develop a “bigger picture” about you. For most people, I think the best advice with regards to OPSEC, is to “blend in”.
Passwords (extended)
I am really not surprised that the usage of common names, dates and pets is as common as it is with passwords. Most people just like to take the lazy approach; that is, the easiest thing for them to remember that will ‘pass the test’. Linking closely with this is the re-use of passwords for convenience - however for security this is absolutely terrible. If your password is compromised on one website and your a ‘worthy target’, then everything is compromised.
HaveIBeenPwned is actually a pretty cool website to see if you’ve been involved in a breach of security. I entered one of my emails, which is more of a ‘throwaway one’ I use for junk-ish accounts on forums and whatnot - it listed that I had been compromised on 11 different websites. I know for a fact that I didn’t use the same password on any of those; secondly for most of them I didn’t care if they got broken.
I think offline password managers are an ‘alright way’ to ensure you have good unique passwords across all the sites you use. (be cautious as they can be a ‘single point of failure’) However when it comes to a number of my passwords which I think are very important - I’ve found just randomly generating them and memorising them works pretty well. Another way is to form long illogical sentences and then morph them with capitalisation, numbers and symbols. You want to maximise the search space for an attacker - for example if your using all 96 possible characters and you have a 16-character password then a bruteforce approach would require you to check 2^105 different combinations (worst-case).
The way websites store our passwords is also important to the overall security - they definitely shouldn’t be stored in plaintext, should use a ‘secure hash function’ (i.e. not MD5) and salted. I’m pretty sure I ranted about a mobile carrier that I had experiences with earlier in my blog, that didn’t do this. This means if the passwords were ‘inevitably’ all stolen from the server, the attacker just gets the hashes, and they can’t use rainbow tables because you hashed them all. Personally, I really like the usage of multi-factor authentication combined with a good password (provided those services don’t get compromised right?). Although, you want to avoid SMS two-factor as it’s vulnerable to SIM hijacking.
4 notes
·
View notes
Text
Optimizing SQL Server Performance: Tackling High Page Splits
Diving into the world of SQL Server management, one stumbling block you might encounter is the vexing issue of high page splits. These splits happen when there’s simply no room left on a data page for new information, forcing SQL Server to divide the data across two pages. This can crank up I/O operations and lead to fragmentation, which, frankly, is a performance nightmare. This guide aims to…
View On WordPress
#Database performance optimization#index fragmentation reduction#SQL Server Assessment API#SQL Server page splits#T-SQL monitoring scripts
0 notes
Text
Anime studio pro 10 tutorial a practical training course kat.ph


📖 Herunterladen Microsoft SQL Server 2008 R2 - Das Entwicklerbuch: Grundlagen, Techniken, Profi-Know-how PDF ePub.
📖 Herunterladen SQL Server Performance Monitoring and Tuning: Become A Smart DBA (English Edition) ebooks.
📖 Herunterladen Getting Started With SQL Server Integration Services Made Easy ebooks.
📖 Buch lesen Knight's Microsoft SQL Server 2012 Integration Services 24-Hour Trainer (English Edition) kostenlos in EPUB.
📖 Herunterladen SQL Server with C# PDF ePub.
📖 Buch lesen The NAV/SQL Performance Field Guide: Fixing Trouble with Microsoft Dynamics NAV and Microsoft SQL Server kostenlos in EPUB.
📖 Herunterladen Extract, Transform, and Load with SQL Server Integration Services: With Microsoft SQL Server, Oracle, and IBM DB2 PDF ePub.
📖 Buch lesen MDX Solutions: With Microsoft SQL Server Analysis Services 2005 and Hyperion Essbase, 2nd Edition kostenlos in EPUB.
📖 Buch lesen Fast Track to MDX: For SQL Server 2000 kostenlos in EPUB.
📖 Herunterladen Pro T-SQL 2019: Toward Speed, Scalability, and Standardization for SQL Server Developers ebooks.
📖 Buch lesen PolyBase Revealed: Data Virtualization with SQL Server, Hadoop, Apache Spark, and Beyond kostenlos in EPUB.
📖 Herunterladen Pro SQL Server Relational Database Design and Implementation (English Edition) ebooks.
📖 XML and JSON Recipes for SQL Server: A Problem-Solution Approach Ebooks, PDF, ePub.
📖 Buch lesen Pro SQL Server on Linux: Including Container-Based Deployment with Docker and Kubernetes kostenlos in EPUB.
📖 Microsoft SQL Server 2008 Internals Ebooks, PDF, ePub.
📖 Query Store for SQL Server 2019: Identify and Fix Poorly Performing Queries Ebooks, PDF, ePub.
📖 Pro SQL Server 2008 Service Broker Ebooks, PDF, ePub.
NET Scripting: A Toolkit for SQL Server Integration Services Ebooks, PDF, ePub
📖 Buch lesen SQL Server 2017 Query Performance Tuning: Troubleshoot and Optimize Query Performance kostenlos in EPUB.
ADO.NET Entity Framework und Migration von SQL Server 2014 ebooks
📖 Herunterladen SQL Server 2016: Das Programmierhandbuch.
📖 Herunterladen Expert T-SQL Window Functions in SQL Server 2019: The Hidden Secret to Fast Analytic and Reporting Queries PDF ePub.
Book Directory & Free Unlimited Books Book Directory & Free Unlimited Books

0 notes
Text
Consultant - Log Analytics/Intelligent Monitoring/Automation
, Microservices, C#, .Net, ETL Informatica, C++, Extjs, TypeScript, R-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft… Apply Now
0 notes
Text
Consultant - Log Analytics/Intelligent Monitoring/Automation
, Microservices, C#, .Net, ETL Informatica, C++, Extjs, TypeScript, R-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft… Apply Now
0 notes
Text
Securities in NodeJs
There is hardly any programming language or framework that is void of vulnerabilities and challenges. NodeJS is no different. While its core is absolutely secure, there arises a need for additional security features for the third party packages in your web apps.
According to one research, 14% of the Node Package Manager is affected with some or the other security issues. So, what is the cause of these security issues?
Why do NodeJS projects face security risks?
Before we answer this question, let us know in brief what an NPM is. The NodeJS package manager is one of the biggest open source package ecosystems that has tremendously helped to boost the functionality of the app in addition to the developer productivity.
So, the main issue is that open source applications get licensing and security issues from their respective components. What is risky is that security testing tools are usually ineffective at detecting open source vulnerabilities. Apart from this, NodeJs easily installs additional modules which can be a threat to security too. Also, being more popular, NodeJs is often susceptible to hackers and other threats.
What are the most common NodeJS security risks?
While NPM phishing and regular expressions DoS (Denial of Service) are very common, other web security issues like cross-site scripting, security configuration and unvalidated redirects also pose a risk. The security issues arising from the use of NodeJs can expose you to attacks such as man-in-the-middle, code injection etc. Let us look at the various risks that may cause these and how to solve the same.
Using older versions of Express
The most popular web application framework for NodeJS is Express. The older versions of this framework could pose a serious security risk as they were not designed with security in mind. The developers have to use only the updated and maintained versions of the framework to ensure that the applications are secure.
Cross-site Scripting
Cross site scripting (XSS) allows hackers to insert unwanted client side scripts to web pages that may be viewed by other users. One major risk of this is data leaks. This can compromise your value and leak critical information outside. To prevent such attacks, developers can make use of output encoding techniques or tools like Jade with built-in encoding frameworks.
Default cookie session name
with session cookies, websites can identify users. All of your activities on a website get stored as cookies. The most common example of this functionality is the shopping carts in e- Commerce sites. Because of the session cookie, your website remembers your selected items on any site. As a result, your shopping cart on this e-Commerce site will have your selected items for checkout. If you open a new page, your past activities will not show up without session cookies.
It is risky to use default cookie names because attackers can know these names and pose a threat to your app. The best way to avoid this is to use middleware cookie session modules such as express-session.
Cross-Site Forgery Requests
CSRF attacks are the primary cause for end users abruptly ending actions on authenticated web apps. The targets of these attacks are alterations in the application state requests. This is mainly because the attackers cannot see the forged request-response. To prevent such attacks, one needs to use Anti-Forgery Tokens that monitor and validate the authenticity of user requests. These tokens also help to prevent one-click attacks.
Apart from the above, there are some common best practices that developers must follow while using NodeJs for enhanced security in their applications. Let us look at a few of those below.
Best NodeJS security practices
Here are some of the best practices to make your NodeJS application more secure.
Validating user inputs
SQL injections are the most popular kind of threat attacks. They happen when a malicious user is able to execute SQL statements on a particular database that you own. To avoid this, you must not blindly pass parameters from the frontend and to the database query. A better thing to do is to validate or escape values that the user provides. Database libraries like mongoose or knex will do it for you.
Implementation of strong authentication
A weak or broken authentication mechanism is the next biggest threat in NodeJS use. Some important things to consider include not using NodeJS built-in crypto library. Instead, you must use Scrypt or Bcrypt. Apart from this, you shouldn’t tell the user if they have entered a wrong username or a wrong password in particular. Opt for a more generic term like “Incorrect credentials”. Also, proper session management policies will greatly boost your application security.
Automatic vulnerability scanning
The NodeJS ecosystem has numerous modules and libraries that can be installed. So, obviously, you would end up using many of those in your projects. This naturally opens up the possibility of facing security threats. To ensure proper security, you must run frequent and automated vulnerability scans. You can use npm audit for basic checks, but you can also check out other popular tools Retire.js and WhiteSource Renovate. Check out some more here.
Conclusion
It is of utmost importance to make your applications secure at all times in a software development cycle. Therefore, while working with NodeJS, security should be on top of your mind, without which your data will be at a constant threat of being hacked or compromised.
At EOV, we have expertise in building safe applications by the proper use of the right framework, taking all necessary safety measures. If you would like us to build comprehensive, quality and secure web based applications for your business, you can reach out to us today!
0 notes
Text
Set up Extended Events in Amazon RDS for SQL Server
Amazon RDS for SQL Server now supports Extended Events. Extended Events (XEvents) is a lightweight performance monitoring system that enables you to collect data to monitor and troubleshoot problems in SQL Server. Extended Events is automatically enabled for users with primary user privileges in Amazon RDS for SQL Server. This post demonstrates how to use Extended Events on Amazon RDS for SQL Server, discusses considerations when working with Extended Events in a Multi-AZ environment, and provides examples of supported events and actions. Prerequisites Before getting started, complete the following prerequisite steps: Download SQL Server Management Studio (SSMS). Log in to Microsoft SQL Server 2012 or higher. Ensure that your account has the server permission of ALTER ANY EVENT SESSION. The text and supporting screenshots in this post can vary as the SSMS UI changes over time. However, the screenshots remain effective for explanation if the discrepancies are only minor. Use Extended Events on Amazon RDS for SQL Server Amazon RDS for SQL Server supports using XEvents on Standard and Enterprise Editions, starting from 2012 versions. You can use disk-based targets and memory-based targets for your XEvents sessions. Some recommendations and limitations apply when you work with XEvents on Amazon RDS for SQL Server; for more information, see Using extended events with Amazon RDS for Microsoft SQL Server. In this section, we go through an example of monitoring database create and database drop events using an XEvents session. Create an XEvents session To create an Extended Events session, complete the following steps: Connect to your RDS for SQL Server instance with SSMS. In the Object Explorer, under Management, choose Extended Events and then choose New Session Wizard. Enter a name for the session. Select Do not use a template. And click on Next to open New Session Wizard screen. For this post, I want to track database created and database dropped events. Choose any values in Global Fields, which are generally common to all events. For this post, I choose database_id, client_hostname, and username global fields. You can set Event Filters to limit the data you want to capture. In this post, we don’t select any filter options. Specify the data storage. You can save the data to a file and create historical records for later analysis. In addition, at the same time you can work with most recent data stored in ring buffer.Ring buffer target memory can’t exceed 4 MB in Amazon RDS for SQL Server. In addition, data to a file can only be saved on D:rdsdbdataLog folder. Choose Finish.You have successfully created your RDSXETEST XE session.You can configure certain XEvents session properties and XEvents target properties using rdsadmin.dbo.rds_set_configuration. For more information, see Using extended events with Amazon RDS for Microsoft SQL Server. Before exiting SQL Management Studio window, select Start the event session and Watch Live data. You can see your RDSXETEST session in the XEvents Sessions menu in SSMS. Monitor the events with the XEvents session Now to test out Extended Events, let’s create and drop a test database from query editor: CREATE DATABASE XETEST DROP DATABASE XETEST When you watch the events live, you can see a create database event and drop database event captured. You can also query the file target to see the same information: SELECT * FROM sys.fn_xe_file_target_read_file('d:rdsdbdatalogRDSXETEST*.xel', null, null, null) XEvents target files are cleaned up based on the retention setting you have chosen. For more information, see Using extended events with Amazon RDS for Microsoft SQL Server. Modify the XEvents session To modify your XEvents session, complete the following steps: In the SSMS Object Explorer, choose your event (right-click). Choose Properties. The same multi-page dialog is displayed as when you created the XEvents session.You can use the SSMS UI to generate a T-SQL script that created your event session. Choose your session node (right-click). Choose Script Session as. Choose CREATE to and Clipboard. Enter the code into your preferred text editor. The create statement for your session is similar to the following: CREATE EVENT SESSION [RDSXETEST] ON SERVER ADD EVENT sqlserver.database_created( ACTION(sqlserver.client_hostname,sqlserver.database_id,sqlserver.database_name,sqlserver.username)), ADD EVENT sqlserver.database_dropped( ACTION(sqlserver.client_hostname,sqlserver.database_id,sqlserver.database_name,sqlserver.username)) ADD TARGET package0.event_file(SET filename=N'D:rdsdbdataLogRDSXETEST',max_file_size=(30)), ADD TARGET package0.ring_buffer(SET max_memory=(2048)) WITH (MAX_MEMORY=4096 KB,EVENT_RETENTION_MODE=ALLOW_SINGLE_EVENT_LOSS,MAX_DISPATCH_LATENCY=30 SECONDS,MAX_EVENT_SIZE=0 KB,MEMORY_PARTITION_MODE=NONE,TRACK_CAUSALITY=OFF,STARTUP_STATE=OFF) GO Drop the XEvents session You can either use SSMS to drop your XEvents session or a T-SQL command to drop it. The following T-SQL code drops the RDSXETEST session: DROP EVENT SESSION RDSXETEST ON SERVER Considerations for Multi-AZ deployments When you create an Extended Event session on a primary DB instance, it doesn’t propagate to the standby replica. You can fail over and create the XEvents session on the new primary DB instance. Alternatively, you can remove and re-add the Multi-AZ configuration to propagate the session to the standby replica. Amazon RDS stops all non-default XEvents sessions on the standby replica so these sessions don’t consume resources on the standby. Because of this, after a standby replica becomes the primary DB instance, you must manually start the Extended Event sessions on the new primary. This applies to both Always On availability groups and database mirroring. If you want your XEvents sessions to always be running on a primary instance of your Multi-AZ, you can create an agent job using a sample T-SQL such as the following to start your XEvents session on the primary if the session isn’t already started (you may have to adjust the code for your instance version and edition): USE [msdb] GO BEGIN TRANSACTION DECLARE @ReturnCode INT SELECT @ReturnCode = 0 DECLARE @jobId BINARY(16) EXEC @ReturnCode = msdb.dbo.sp_add_job @job_name=N'START_XE_SESSIONS',@enabled=1, @description=N'Job to start XE sessions.', @job_id = @jobId OUTPUT IF (@@ERROR <> 0 OR @ReturnCode <> 0) GOTO QuitWithRollback EXEC @ReturnCode = msdb.dbo.sp_add_jobstep @job_id=@jobId, @step_name=N'STEP1', @step_id=1, @os_run_priority=0, subsystem=N'TSQL', @command=N'BEGIN IF (DATABASEPROPERTYEX(''rdsadmin'',''Updateability'')=''READ_WRITE'' AND DATABASEPROPERTYEX(''rdsadmin'',''status'')=''ONLINE'' AND (DATABASEPROPERTYEX(''rdsadmin'',''Collation'') IS NOT NULL OR DATABASEPROPERTYEX(''rdsadmin'',''IsAutoClose'')=1) ) BEGIN IF NOT EXISTS (SELECT 1 FROM sys.dm_xe_sessions WHERE name=''RDSXETEST'') ALTER EVENT SESSION RDSXETEST ON SERVER STATE=START END END', @database_name=N'master' IF (@@ERROR <> 0 OR @ReturnCode <> 0) GOTO QuitWithRollback EXEC @ReturnCode = msdb.dbo.sp_update_job @job_id = @jobId, @start_step_id = 1 IF (@@ERROR <> 0 OR @ReturnCode <> 0) GOTO QuitWithRollback EXEC @ReturnCode = msdb.dbo.sp_add_jobschedule @job_id=@jobId, @name=N'SCHD1', @enabled=1, @freq_type=8, @freq_interval=1, @freq_subday_type=4, @freq_subday_interval=10, @freq_relative_interval=0, @freq_recurrence_factor=1, @active_start_date=20210402, @active_end_date=99991231, @active_start_time=0, @active_end_time=235959, @schedule_uid=N'123fca70-cac7-406e-88ac-a4cd78041c61' IF (@@ERROR <> 0 OR @ReturnCode <> 0) GOTO QuitWithRollback EXEC @ReturnCode = msdb.dbo.sp_add_jobserver @job_id = @jobId, @server_name = N'(local)' IF (@@ERROR <> 0 OR @ReturnCode <> 0) GOTO QuitWithRollback COMMIT TRANSACTION GOTO EndSave QuitWithRollback: IF (@@TRANCOUNT > 0) ROLLBACK TRANSACTION EndSave: GO The preceding code creates a SQL agent job that does the following: Runs with a 10-minute interval Checks if the current instance is the primary or not If the current instance is primary and if the RDSXETEST session isn’t in a started state, it starts the session You can modify these parameters as needed. Examples of supported events and actions You can create an XEvents session to collect most events and corresponding actions, but a few actions are not supported. For a full list of events and actions not supported, see Using extended events with Amazon RDS for Microsoft SQL Server. The following are examples of supported events: Database events, such as database_created Run events, such as execution_warning Always On events, such as alwayson_ddl_executed Memory events, such as memory_manager_free_memory You can see the full list of events by using the following SQL query: SELECT * FROM sys.dm_xe_objects WHERE object_type='event'; The following are examples of supported event actions: Collect SQL text (sql_text) Collect current database name (database_name) Collect username (username) Collect session ID (session_id) You can see the full list of actions by using the following SQL query: SELECT * FROM sys.dm_xe_objects WHERE object_type='action' Summary Extended Events is a new and exciting feature in Amazon RDS for SQL Server. We support Extended Events only on Amazon RDS for SQL Server Enterprise and Standard Edition. You can use this feature to diagnose various performance issues on your RDS for SQL Server instance. To know more about Extended Events in Amazon RDS for SQL Server look into the article here. About the author Sudarshan Roy is a Senior Database Specialist Cloud Solution Architect with the AWS Database Services Organization (DBSO), Customer Advisory Team (CAT). He has led large scale Database Migration & Modernization engagements for Enterprise Customers to move their on-premises database environment to Multi Cloud based database solutions. Joon Lee is a Software Development Engineer at Amazon Web Services. He works with the AWS RDS team, focusing on commercial database engines and SQL Server. He enjoys working on technical challenges in Amazon RDS and is passionate about learning new technologies. Chinni Bolapati is a Senior Database Engineer with Amazon Web Services. He works on the Amazon RDS team, focusing on commercial database engines, SQL Server and Oracle. https://aws.amazon.com/blogs/database/set-up-extended-events-in-amazon-rds-for-sql-server/
0 notes
Text
Senior Principal Consultant - Log Analytics/Intelligent Monitoring/Automation
, Microservices, C#, .Net, ETL Informatica, C++, Extjs, TypeScript, R-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft… Apply Now
0 notes
Text
Senior Principal Consultant - Log Analytics/Intelligent Monitoring/Automation
, Microservices, C#, .Net, ETL Informatica, C++, Extjs, TypeScript, R-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft… Apply Now
0 notes
Text
Basic Topics
Food
cook bread cake pie noodles pasta eggs meat milk cheese oil chocolate chips cookies crackers treats snacks muffin rolls biscuit cupcake brownies bagel biscotti French fries sandwich hamburger salad meatloaf breakfast lunch super dinner snack fruit juice soda pop tea coffee wine beer
Outdoors
snow rain wind sunny cloudy tornado hurricane hail ice freeze thaw hot cold earthquake sand mud dirt dust mountain river lake sea ocean valley plain field park sidewalk fresh air camping campfire barbecue picnick
Animals
cow donkey horse rabbit dragonfly deer squid kangaroo bear wolf chipmunk squirrel dog fox cat pheasant brontosaurus mouse eagle clam parrot crow duck cricket swan housefly pterodactyl goose chicken oyster turkey sheep goat hummingbird raptor owl eel hornet zebra bird mosquito whale cougar shrimp elephant lion bee pigeon gazelle cheetah hippopotamus fish tiger gecko grasshopper rhinoceros walrus octopus otter spider jellyfish penguin falcon snake rat crab leopard T-Rex dolphin orca lizard shark hawk giraffe dinosaur starfish snail
Clothes
hat gloves scarf coat trench coat rain coat umbrella shirt pants shorts underwear vest sweater sweat shirt sweat pants sweat suit jogging suit boots shoes sandles slippers swimming suit suit dress skirt blouse hood hoodie fedora flat cap fedora polo shirt dress shirt T-shirt tank top muscle shirt blazer tuxedo cufflinks necklace bracelet earring
Home
house garage workshop window door screen wall floor ceiling kitchen bathroom living room bedroom window door garbage trash can clean wash rinse mob broom washcloth sink shower bath soap toilet toothbrush towel curtain bed blanket pillow bed sheets table chair bench knife fork spoon plate cup bowl water glass bottle cutting board rolling pin toaster blender stove oven fry pan wok pot kettle baking sheet crock pot coffee maker dish washer refrigerator freezer cellar pantry cupboard counter top cabinet closet toybox chest wardrobe vanity coat rack stand sofa couch love seat coffee table footstool ottoman recliner
Office & School
desk computer phone tablet printer clock watch memo note pencil pen ink eraser glue paper clip stapler rubber band sharpen dull shavings shred ruler protractor compass classroom pencil holder calendar pin board thumb tack desk lamp board room whiteboard blackboard conference table manager supervisor teacher principal team & teammates classmates employee student project assignment study work learn correct edit fix repair update upgrade install enroll graduate finish late on time communicate network energy electricity announcement speakers PA system (public announcement) public private corporation company school district industrial park factory building commerce money market
Roads
car truck motorcycle semi truck pickup truck sport car sedan coup scooter dirt bike bicycle BMX bike skates skateboard helmet seat belt air bag crash collision fender bender ticket parking lot speed limit lane highway onramp expressway freeway toll road bridge overpass underpass train tracks railroad train station bus stop yield distance limousine chauffeur driver taxi tour guide travel
Farm & Garden
barn tractor trailer crops harvest irrigation pesticide herbicide weed-killer fertilizer lawn mower bumper crop hay loft straw alfalfa pasture horse fence gate work gloves planting watering weeding trimming trowel plow hoe rake shovel pruning shears hedge trimmer watering can hose hose butler hose reel hose trolley spigot nozzle sprinkler turret sprinkler spray gun rain barrel rain gauge wood chips seeds blossom pollen silo grainery grain elevator cheesecloth cheese curd dairy butcher cellar canned vegetables frost dew perennial annual tulip bulb rose garden walled garden shrubbery
Sports
baseball basketball football soccer lacrosse golf tennis badminton swimming hockey bat glove mitt hoop basket net goal cleats shin guards pads jersey baseball cap court racket pool referee coach team manager stadium arena referee guard forward pitcher catcher offense defense goalie umpire puck penalty disc frisbee quarterback fowl pitch tee-off green rough course field flag boundary out of bounds clock period inning half quarter round match set play (a football play) line sponsor spectator stands bleachers nose-bleed section admission season playoffs tickets finals halftime
Music
piano clarinet oboe bassoon saxophone French horn trumpet trombone tuba flute percussion drum snare tympani bell chimes harp synthesizer instrument sampling director symphony orchestra band marching band parade color guard cadence harmony melody counter melody solo duet quartet march concerto composer tempo beat dynamics volume drum major field commander captain genre jazz blues pop rock n’ roll big band dixieland waltz tango alternative boogie woogie ragtime classical baroque romance medieval pentatonic scale Major minor harmonic
Cyberspace
computer monitor tablet stylus writing tablet touchscreen smartphone mouse keyboard battery power cord cable display desktop wallpaper firmware software application (app) app store runtime environment operating system kernel motherboard integrated circuit transistor processor processor core central processing unit (CPU) graphics processing unit (GPU) random access memory (RAM) read only memory (ROM) user account website profile page Internet web page homepage dependency software stack markup language scripting language cascading style sheet (CSS) hypertext markup language (HTML) database structured query language (SQL) universal resource identifier (URI) (https://write.pink/vocab) universal resource locator (URL) (https://write.pink) web address texting global positioning system (GPS) geolocation temp file directory structure file system email web application blog (weblog) content management system (CMS) human resource management (HRM) customer relations management (CRM) enterprise resource planning (ERP) personal information management (PIM) words per minute (WPM) social media multimedia terminal command line console client server client side language server side language legacy version version history product road map scope creep bug report feature request install update upgrade beta security malware virus spyware cookie meta data content menu navigation heading header footer article post tag search engine web crawler contacts share embed log error message runlevel priority foreground background radio select checkbox dropdown select text field encrypt certificate session web browser desktop application email client
Hospitality
reservation checkin checkout key deposit hotel motel hostel resort bead & breakfast cruise ship country club waiter waitress server maître d’hôtel concierge host butler bus boy bell hop kitchen crew dish crew chef assistant menu chef’s surprise soup of the day cup of joe appetizer soup & salad main course side dish dessert bread basket pitcher order make ticket make line make table make time delivery time serving tray goblet water glass pilsner glass martini glass shot glass wine glass soda fountain on tap deli deli cut tip / gratuity buffet all you can eat take out doggy bag delivery refill silverware napkin place setting cost per plate guest linens dining room floor bedding double bed queen size bed king size bed twin beds room service wake up call bar bar stool high boy bartender barista clerk open shop close shop “we’re all out” first in first out first in last out last in first out cost of sales five star three star
Travel
navigation driving directions baggage luggage carry-on hand-baggage check in checked baggage baggage claim ticket pass boarding pass departure arrival departure time travel time arrival time estimated time of departure (ETD) estimated time of arrival (ETA) delay on time commute journey embark boarding disembark boarding gate departure gate time table service counter first class business class economy class premium economy frequent flier membership card priority boarding priority seating lounge pass call button flotation device evacuation instructions bulkhead cabin wings air pressure altitude tunnel crash landing splash landing touchdown splashdown turbulence in-flight meal in-flight entertainment airplane mode stow dinner tray reading lamp climate control overhead compartment seat number isle seat window seat dining car sleeper car truck stop weigh station fuel station gas station petrol station passengers crew captain pilot copilot navigator conductor flight attendant helm deck terminal dock ferry plane ship airline cruise ship train bus subway space shuttle transporter beam flying saucer teleportation warp drive hyperdrive hyperspace supersonic lightspeed nautical mile time zone
Dinning Out
Dress
“dressy” festive casual jeans and tie dress pants and tie suit and tie three piece suit dress shirt nice shirt nice T shirt old shirt old T shirt jeans nice jeans rockstar jeans stone washed jeans blazer vest dress short nice shorts jean shorts skirt blouse dress high heels dress shoes slippers loafers sandals sneakers casual shoes [sport] shoes wingtip shoes
Menu
orange soda grape soda red soda cola Dr. Pepper lemon lime root beer ginger ale cream soda bread basket sub sandwich fruit platter cole slaw burrito taco nachos melon lemonade snacks popcorn hot dog chips
Camping
camper trailer mobile home campfire fire pit firewood kindling starter fluid charcoal coals ashes marshmallow s’mores graham crackers hot dog roast hot dog bun condiments relish ketchup mustard paper plate disposable silverware tin foil dinner wrap foil wrapped dinner grill barbecue cookout roasting stick campground toiletries bath house dump station park service park ranger national park state park county park city park recreation off road vehicle recreational vehicle speed boat water skiing wake boarding beach sand dune mountain climbing hiking walking stick mosquito net insect repellent tent tarp AstroTurf picnic table lawn chairs lantern kerosene sing-along
Construction
scaffold nails hammer sledgehammer jackhammer allen wrench screws screwdriver torques head Phillips head straight edge concrete flexcrete cement mortar bricks foundation chimbney threshold partition fire escape story loft lean-to foundation basement construction crew construction site building code building permit detour road construction earth moving equipment shovel rake bulldozer backhoe dumptruck studds drywall log cabin blueprints I-beam welding molding trim work framing carpeting tiling tile floor grout trowel hardhat work gloves safety glasses safety goggles face mask plaster paintbrush pain roller paint can paint can opener paint thinner wallpaper window frame door frame hinge deadbolt lock electric outlet breaker switch breaker box fuse box pluming faucet pipe drain septic tank septic system drain field landscaping survey crew land surveying acre shelf awning tarp fence rebar power grid power lines power transformer electrical pole wiring linoleum formica veneer lumber particle board plywood sandpaper palm sander belt sander saw horse table saw band saw jig saw radial arm saw drill press lathe C-clamp wood glue wood putty wood stain varnish lacquer
Basic Topics was originally published on PinkWrite
3 notes
·
View notes
Text
Swissqual NQDI: Netqual, Qualipoc
Swissqual NQDI: Netqual, Qualipoc
The Network Quality Data Investigator (NQDI) is a post processing system that demonstrates the capabilities of data collection by SwissQual QualiPoc and Diversity products for network and service optimization and benchmarking. On top of all radio technologies, NQDI also provides detailed quality analysis and long-term reporting for voice and data services.
Network Quality Data Investigator (NQDI) stores all information gathered by the collection systems in a scalable database, allowing flexible data selection and filtering for detailed troubleshooting and long-term trend analysis. It combines the benefits of insights generated by high-level KPI summaries with the investigative power of detailed drilldowns.
A smart adapting GUI sensitive to contextual information enables users to focus on relevant information, while time synchronization and correlation of numerous data layers helps to automate fault categorization. The quality of voice, video, messaging and data services can be investigated using primary RF measurements, network trace events, call control parameters, IP and application level events, and voice and video quality indicators.
NQDI presents such information in time-synchronized views using maps, message monitors, grids, line graphs, bar graphs, pie charts, tables and hierarchical lists. It features multiple options for reporting, from predefined packages to guided KPI-based creation of Excel reports with a powerful report generator.
Fully scalable system: from a standalone laptop solution to large client/server enterprise
Unique speech and video quality analysis
Powerful reporting and map plotting
Scalable client server architecture
Server-powered Microsoft® SQL Server® database engine
Fully scalable system, from a standalone laptop solution to large client/server enterprise
32-bit and 64-bit Windows® platforms
Named and floating licensing
Easy database management
NQDI databases are easily managed with the integrated data management tool
Scalable data storage
Detailed information stored in the database to avoid compromising the flexibility and analysis depth
Intelligent collection files design allows extremely fast import speed into the database
Full range of technologies supported
GSM, GPRS, EDGE, WCDMA, HSPA+, HSDPA DC, LTE
CDMA, EVDO, iDEN, IS-136, TDMA
PSTN, ISDN, Wi-Fi, WiMAX

Context-sensitive user interface
Context-sensitive user interface automatically adopts the presentation to the content and technology
No need to change between workspaces or rearrange any windows manually
Customizable and detachable windows
Drilldown and visualization of information from service and application layers down to RF
Flexible data selection
Speech quality analysis
ITU-T P.863 (POLQA) full reference voice MOS (narrow and wideband)
ITU-T P.862/P.862.1 (PESQ) full reference voice MOS (narrowband)
SwissQual SQuad full reference voice MOS (narrow and wideband), echo, noise suppression and RTT assessments
SwissQual NiNa+ no reference voice MOS
Video service analysis
Full support for video service analysis and visual quality assessment.
Time to first picture, long-term freezing, IP statistics and degradation cause values
SwissQual VQuad full reference visual quality MOS
SwissQual VMon no reference visual quality MOS
Data service analysis
Analysis of a wide range of services:
Voice telephony: CS and VoIP speech MOS, noise suppression, echo, RTT, DTMF
Data: Ping, FTP, UDP, HTTP, Data Capacity, Iperf
Browsing: WAP, HTTPS/HTTP IE
Messaging: SMS, MMS, e-mail
Video over IP: video streaming portals, including YouTube
3G video telephony
IP layer analysis
Dedicated protocol and throughput analysis of IP traces
PCAP files can be automatically loaded into Wireshark® with NQDI time synchronization
Map plotting
Supports configurable binning on grid or latitude/longitude precision.
BTS lists for GSM, UMTS, CDMA and LTE can be loaded
Serving sector lines and coverage functions
Smart window splitting for easy analysis of multiple networks and parameters
Powerful reporting
More than 200 KPIs available for service and network performance reporting and trending
KPI report generator allows users to create their own custom KPI reports
Report configurator enables users to create very advanced reports via SQL and Visual Basic scripting
Web reporting
Fully compatible with NetQual NQWeb platform for companywide distributed presentation and reporting
نوشته Swissqual NQDI: Netqual, Qualipoc اولین بار در تلکام تولز. پدیدار شد.
from WordPress https://ift.tt/2ybu9aV via IFTTT
0 notes