#SQL Server page splits
Explore tagged Tumblr posts
Text
Optimizing SQL Server Performance: Tackling High Page Splits
Diving into the world of SQL Server management, one stumbling block you might encounter is the vexing issue of high page splits. These splits happen when there’s simply no room left on a data page for new information, forcing SQL Server to divide the data across two pages. This can crank up I/O operations and lead to fragmentation, which, frankly, is a performance nightmare. This guide aims to…
View On WordPress
#Database performance optimization#index fragmentation reduction#SQL Server Assessment API#SQL Server page splits#T-SQL monitoring scripts
0 notes
Text
One of the oldest forms of internet communication, message boards and forums are just as popular today as they have ever been. As of 2016, there were an estimated 110,000 separate forum and message board providers across the world, ranging from social media style sites like Reddit to free bulletin software built on phpBB. Market Share Of Various Popular Forum Platforms Studies show that premium (paid-for) forum software still takes the lead when it comes to setting up a discussion website. In fact, leading premium provider vBulletin takes an estimated 50% of the total market. This service is essentially a template site with fully customizable bulletin board platforms, available for developers to manipulate and innovate as desired. [Credit: BuiltWith.com via Quora] However, there has been a marked growth in the amount of open source software which enables discussion board creation, and many developers are creating their own message boards for commercial, social and personal use. We take a look at the top free platforms on the market today, tried and tested by industry experts. Five Of The Best Free Forum Platforms phpBB Experts agree that you will struggle to beat phpBB for functionality and ease of use. This simple PHP bulletin board application is perfect for fan discussions, photo threads, advice pages and general messaging between users. It has millions of global users and is fully compatible with PostgreSQL, SQLite, MySQL, Microsoft SQL Server, as well as being open to editing through the General Public Licence There are lots of opportunities to play with it and customize it, with no need for seeking permission first. Threads can be split and messages can be archived for posterity, and the site maintains a template database with modifications and styles that are open for users to play around with. bbPress Forums WordPress has been the leading platform for blogging for many years. There are millions of sites across the Web which use the publishing software for their business sites, blogs and even e-commerce - and now the team is adding forum sites to its range of products. bbPress Forums is a WordPress-style bulletin board creation tool, which has the smooth and seamless transitions and roomy capacity that keeps the site fast and user-friendly. Just like with the blogs, bbPress begins as a free service and has the option of a Premium or Business upgrade, with additional custom features and templates for subscribers. It is also one of the most secure free programs, with additional safety features to prevent hacking. YetAnotherForum Don’t let the name fool you - YetAnotherForum is anything but, with its quirky and innovative approach to forum development. The managed open source platform is designed specifically with ASP.NET in mind and is compatible with the fourth C# generation and above. It is licensed free to developers and open for reworkings of the system’s code, and it builds bright, bold message boards that are simple and easy for users and admins alike. One of the big selling points is YetAnotherForum’s reliability: the service has operated for nine years without problems and still undergoes regular testing. Over those nine years, progress has been slow but the last twelve months have seen promising developments and the program is seeing a surge in downloads and orders. Phorum Sometimes the old ones really are the best. Phorum has been around since the 1990s and it played a big role in the rise of forum sites. The free-to-use platform is based around PHP and MySQL development, and it is still one of the best pieces of software for forum creation that you can use free today. One of the key selling points is how flexible it is - you can host one huge message thread with thousands of users, or adopt it across hundreds of different forums for a help site, social network or discussion group. Phorum has also upped its game lately with the introduction of a new template - the XHTML 1.0 Transitional Emerald design.
This is available instead of the basic template and has far more features and options, but it still offers a blank slate for the developer in terms of design and function. Discourse If you need a platform that scales up as your service grows and is easy to develop and change as you do, Discourse is a great choice. There are three tiers of membership available - free, paid and premium - and all options are pretty budget-friendly. Discourse is designed for creating discussion boards, and it is fully compatible with mobiles and tablets as well as PCs and laptops. It can handle busy conversations and it makes them easy to read back, with options to split threads and move conversations as needed. The open source code is readily available for programmers to play with, and the system is easy to hand over to your designer or tech team if you have something specific in mind. User-created templates and styles are available, and there is a built-in filter system with can save on moderator costs and keep your forum a safe space for visitors to chat. Ten More Top Free Forum And Bulletin Board Programs Haven’t found what you need among our top picks above? Not all programs suit everyone - but there are hundreds of options on the market, so keep searching for your perfect platform. Find the right match for your forum vision, and get creating thanks to these amazing open source programs. Here are some more of the best forum development programs for 2017: Vanilla Forums Simple Machines MiniBB Forums MyBB DeluxeBB PunBB FluxBB UseBB Zetaboards Plush Forums The Best Of Premium Forum Software - At A Discount! If the free tools do not meet your needs or you want the added support and security of a premium service, there are plenty of platforms to choose from - including vBulletin, Burning Board, XenForo and IP.Board. Paid-for tools often require a subscription, so take advantage of the deals available online at OZCodes.com.au. Voucher codes can give big savings on the cost of software subscriptions through leading providers.
0 notes
Text
The Art and Science of Website Development: Crafting Digital Experiences in the Modern Era
In the digital age, websites have become the cornerstone of online presence for businesses, organizations, and individuals alike. The process of website development is a complex interplay of design, functionality, and technology, requiring a deep understanding of both user needs and technical capabilities. From frontend design to backend infrastructure, every aspect of website development plays a crucial role in creating a seamless and engaging user experience. As the internet continues to evolve, so too do the tools and techniques used by developers to build websites that are not only visually appealing but also fast, secure, and scalable.
At the heart of website development lies the frontend, the part of the website that users interact with directly. This is where HTML, CSS, and JavaScript come into play, forming the building blocks of modern web design. HTML provides the structure of the page, CSS adds style and visual appeal, and JavaScript brings interactivity and dynamic content. Frameworks like React, Angular, and Vue.js have revolutionized frontend development, enabling developers to create complex, responsive, and highly interactive user interfaces. These frameworks leverage the concept of components, reusable pieces of code that can be combined to build intricate layouts and features. Additionally, responsive design ensures that websites look and function well on a variety of devices, from desktops to smartphones, using techniques like media queries and flexbox.
While the frontend is what users see, the backend is the engine that powers the website. This is where server-side logic, databases, and application programming interfaces (APIs) come into play. Backend development often involves languages like Python, Ruby, PHP, and Node.js, each offering its own set of advantages and use cases. For instance, Node.js is particularly well-suited for real-time applications, while Python is favored for its simplicity and versatility. Databases, such as MySQL, PostgreSQL, and MongoDB, store and manage the data that fuels the website, from user profiles to product catalogs. APIs, on the other hand, enable communication between the frontend and backend, as well as integration with third-party services like payment gateways and social media platforms.
One of the most critical aspects of website development is performance optimization. Users expect websites to load quickly and run smoothly, and even a few seconds of delay can lead to higher bounce rates and lost revenue. Techniques like caching, minification, and lazy loading are commonly used to improve performance. Content Delivery Networks (CDNs) distribute website content across multiple servers worldwide, reducing latency and ensuring fast load times for users regardless of their location. Additionally, image optimization and code splitting help reduce the size of assets and JavaScript bundles, further enhancing performance. Tools like Google Lighthouse and WebPageTest provide valuable insights into website performance, helping developers identify and address bottlenecks.
Security is another paramount concern in website development. With cyber threats on the rise, developers must implement robust security measures to protect user data and maintain trust. HTTPS is now a standard requirement, encrypting data transmitted between the user’s browser and the server. Web Application Firewalls (WAFs) and SSL/TLS certificates add an extra layer of protection, safeguarding against attacks like Cross-Site Scripting (XSS) and SQL injection. Regular security audits and penetration testing are essential for identifying vulnerabilities and ensuring compliance with regulations like GDPR and PCI DSS. Furthermore, two-factor authentication (2FA) and secure password policies help protect user accounts from unauthorized access.
The rise of headless CMS and static site generators has introduced new possibilities for website development. A headless CMS separates the content management system from the frontend, allowing developers to use any technology stack to build the user interface. This approach offers greater flexibility and scalability, making it ideal for complex websites with diverse content needs. Static site generators like Gatsby and Jekyll pre-render pages at build time, resulting in faster load times and improved security. These tools are particularly well-suited for blogs, documentation sites, and other content-heavy websites.
In conclusion, website development is a multifaceted discipline that combines creativity, technical expertise, and strategic thinking. From frontend design and backend infrastructure to performance optimization and security, every aspect of the process plays a crucial role in creating a successful website. As the digital landscape continues to evolve, developers must stay abreast of emerging trends and technologies, from headless CMS to progressive web apps (PWAs), to deliver cutting-edge solutions that meet the needs of modern users. By mastering the art and science of website development, developers can create digital experiences that are not only visually stunning but also fast, secure, and scalable, ensuring their place at the forefront of the digital revolution.
Make order from us: @Heldcbm
Our portfolio: https://www.linkedin.com/company/chimeraflow
0 notes
Text
Scalable Applications with Full Stack Python Development

Scalability is one of the most important considerations when developing applications, especially in the context of Full Stack Python development. As applications grow in terms of users, data, and traffic, ensuring they can scale effectively without compromising on performance or reliability becomes crucial. This blog will guide you through strategies and best practices for building scalable applications using Full Stack Python development
Understanding Scalability in Full Stack Python Development
Scalability refers to the ability of an application to handle increased load — whether that’s more users, more data, or more requests — without sacrificing performance. In Full Stack Python development this means making sure both your frontend and backend are designed to handle growth efficiently.
Scalability is generally classified into two types:
Vertical Scaling (Scaling up): Adding more power (CPU, RAM) to a single server.
Horizontal Scaling (Scaling out): Adding more servers to distribute the load.
In Full Stack Python development, both types of scaling can be employed, but horizontal scaling is usually preferred for web applications that need to serve a large number of concurrent users.
Backend Scalability in Full Stack Python development
Database Optimization:
Sharding: Dividing your database into smaller, more manageable pieces (shards) helps spread the load and improves database performance.
Read/Write Replication: Use replication to separate read-heavy and write-heavy operations. For instance, you can have multiple read replicas and a single master for writes to distribute load more evenly.
NoSQL vs. SQL: Depending on your application’s needs, NoSQL databases like MongoDB might offer more flexibility for scaling horizontally. On the other hand, traditional relational databases like PostgreSQL can be vertically scaled with more advanced configurations.
Caching Layers:
Redis: Implement caching solutions like Redis to store frequently accessed data in memory, reducing database load and improving response times. Caching helps your application serve repeated requests much faster.
Memcached: Another in-memory caching system that can be used in combination with your backend, reducing database hits and improving throughput.
Asynchronous Processing:
Use Celery or RQ for managing background tasks in Python. When scaling your application, background task processing can help offload heavy tasks like email sending, data processing, or image resizing from the main application flow.
AsyncIO in Python allows you to handle multiple I/O-bound operations concurrently without blocking the main application, allowing for better utilization of resources when handling a large number of requests.
Microservices Architecture:
Instead of building a monolithic application, consider breaking your backend into microservices. Each microservice can handle a specific function or domain within your application (e.g., user authentication, payment processing). Microservices can be independently scaled based on demand.
Use tools like Docker and Kubernetes to deploy and manage your microservices. Docker allows you to containerize your microservices, and Kubernetes can automate deployment, scaling, and operations of those containers.
Frontend Scalability in Full Stack Python Development
Load Balancing:
For scalable frontend applications, use load balancers like Nginx or HAProxy to evenly distribute traffic across your servers. Load balancing ensures that no single server gets overwhelmed, even as the number of concurrent users increases.
Frontend Optimization:
Code Splitting: In JavaScript, Webpack or Parcel can help you split your code into smaller, manageable chunks that are only loaded when needed. This reduces the initial page load time and makes the application faster for the user.
Lazy Loading: Lazy loading of images and components ensures that only the essential parts of your application load initially, improving perceived performance. Implement lazy loading using techniques like Intersection Observer API or libraries like React Lazy.
Single Page Application (SPA) Frameworks:
Using a SPA approach with frameworks like React, Vue.js, or Angular allows for more responsive user interfaces and can reduce the amount of server-side rendering required, decreasing the load on your backend.
React, for example, allows the frontend to manage its state independently of the server, which can help reduce server-side requests and improve scalability.
Content Delivery Networks (CDNs):
A CDN like Cloudflare or Amazon CloudFront helps deliver static resources (images, CSS, JavaScript) from servers closest to your users. This reduces load times by serving content faster, improving the user experience as the application scales.
Scaling Full Stack Python Applications
Use of Containers:
Docker allows you to containerize both the frontend and backend of your Full Stack Python development application. Containers can easily be replicated across multiple servers to ensure horizontal scaling.
For orchestration of containers, Kubernetes can automatically scale your application by adjusting the number of containers in response to traffic loads.
Distributed Systems:
RabbitMQ or Kafka can be used for building distributed systems where various parts of the application communicate asynchronously. This is useful when scaling applications that require data to be processed and passed between multiple components of the system.
Auto-Scaling:
Cloud services like AWS or Google Cloud provide auto-scaling options, automatically adjusting your application’s resources based on traffic. This ensures that your application can handle periods of high demand without manual intervention.
APIs and Microservices:
If your application is based on RESTful APIs or GraphQL, ensure your API endpoints are designed to handle scaling efficiently. Use techniques like rate limiting to protect your backend and ensure a smooth experience for users during peak times.
Best Practices for Scalable Full Stack Python Development
Optimize Database Queries: Whether you are using a relational database like PostgreSQL or a NoSQL database like MongoDB, optimizing queries is crucial. Use proper indexing, avoid N+1 queries, and ensure your database is optimized for performance.
Decouple Components: Decouple components in your backend to make it easier to scale. For instance, use message queues (like RabbitMQ or Redis Pub/Sub) to separate your application logic from background tasks.
Automate Testing and Deployment: Implement CI/CD pipelines using tools like GitLab CI, Jenkins, or CircleCI to automate testing and deployment. This ensures that your application is always ready for scaling and reduces the chances of downtime.
Conclusion
Building scalable applications in Full Stack Python development requires careful planning, choosing the right tools, and following best practices to ensure your application can handle increased demand. By optimizing both the backend and frontend, leveraging containerization, and using the right database and caching strategies, you can build applications that scale effectively as your user base grows.
0 notes
Text
Use of Power Query in Power BI

Power Query in Power BI is a powerful tool used for data transformation and preparation before visualizing the data. It provides an intuitive interface to connect, combine, and refine data from various sources into a coherent, structured dataset ready for analysis. Excel Training in Mumbai often covers how to use Power Query to effectively prepare and transform data. Here's an overview of how Power Query is used in Power BI:
1. Connecting to Data Sources
Importing Data: Power Query can connect to various data sources like Excel files, databases (SQL Server, Oracle, etc.), online services (Azure, SharePoint, etc.), and even web pages.
Multiple Data Sources: You can combine data from multiple sources into a single dataset, which is especially useful when dealing with complex data architectures.
2. Data Transformation
Data Shaping: Power Query allows you to shape your data by removing unnecessary columns, renaming columns, filtering rows, and sorting data.
Data Cleansing: It provides tools to clean your data by handling missing values, removing duplicates, splitting and merging columns, and correcting data types.
Merging and Appending: You can merge (join) tables based on common columns or append (union) tables to create a unified dataset.
Conditional Columns: Power Query enables creating conditional columns based on specific logic, similar to using IF statements in Excel.
3. Advanced Data Manipulation
Grouping and Aggregation: You can group data by specific columns and aggregate data (e.g., summing, averaging) to create summary tables.
Pivoting and Unpivoting: Power Query allows pivoting rows to columns and vice versa, transforming your data into a more suitable structure for analysis.
Custom Columns: Using the M language (Power Query's formula language), you can create custom columns with complex calculations and logic.
4. Data Loading
Load to Data Model: Once the data is transformed, it can be loaded into the Power BI data model, where it can be used for creating reports and visualizations.
Direct Query vs. Import Mode: Power Query supports both Direct Query (where data is queried directly from the source) and Import Mode (where data is imported into Power BI for analysis).
5. Automation and Reusability
Query Dependencies: Power Query automatically tracks dependencies between queries, ensuring that changes in one query reflect in others that depend on it. This feature is crucial for maintaining accurate and up-to-date data models, especially in complex projects.
Reusable Steps: All transformation steps are recorded and can be modified or reused across different queries, ensuring consistency and efficiency. This capability allows users to standardize their data preparation processes and streamline workflows, which is often highlighted in Advanced Excel Classes in Mumbai to help professionals optimize their data management tasks
6. Integration with Other Power BI Features
Parameters: You can create parameters in Power Query that allow dynamic filtering and customization of data sources and queries.
Templates: Power Query transformations can be saved as templates and reused across different Power BI reports or shared with others.
7. Data Profiling
Column Quality and Distribution: Power Query provides tools to profile your data, showing column quality, value distribution, and statistics to help identify data issues early.
Error Handling: It highlights errors and outliers, allowing you to manage and clean data before loading it into the data model.
8. Performance Considerations
Query Folding: Power Query attempts to push data transformations back to the data source (query folding) whenever possible, optimizing performance by reducing the amount of data loaded into Power BI.
Example Use Cases
Sales Data Preparation: Importing sales data from multiple regional Excel files, cleaning it, and consolidating it into a single dataset for analysis.
Web Scraping: Extracting data from a web page, transforming it into a structured format, and using it in a Power BI report.
Data Integration: Combining data from an SQL Server database and a SharePoint list, transforming it, and creating a unified data model for reporting.
Steps to Access Power Query in Power BI
Open Power BI Desktop.
Go to the "Home" tab.
Click on "Transform Data" to open the Power Query Editor.
Use the various tools and options available in the Power Query Editor to connect to data sources, transform data, and prepare it for analysis.
Power Query is essential for anyone looking to perform robust data transformation and preparation in Power BI. It ensures your data is clean, well-structured, and ready for analysis, enabling better insights and decision-making. Learning Power Query is a key part of Advanced Excel Training in Mumbai, as it equips individuals with the skills needed to handle data efficiently and create powerful data models.
For more information, contact us at:
Call: 8750676576, 871076576
Email:[email protected]
Website:www.advancedexcel.net
#Excel Training in Mumbai#Advanced Excel Classes in Mumbai#Advanced Excel Training in Mumbai#advanced excel
0 notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
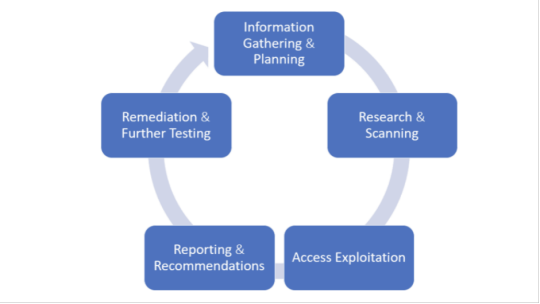
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP��,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
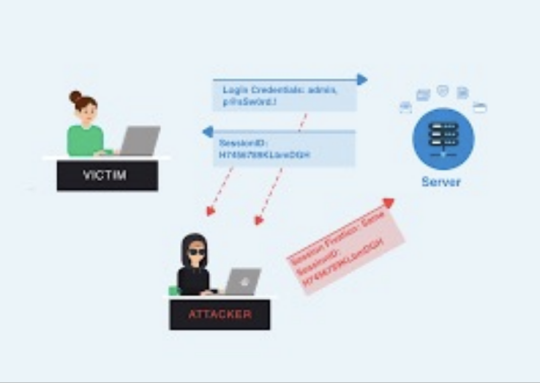
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Slow database? It might not be your fault
<rant>
Okay, it usually is your fault. If you logged the SQL your ORM was generating, or saw how you are doing joins in code, or realised what that indexed UUID does to your insert rate etc you’d probably admit it was all your fault. And the fault of your tooling, of course.
In my experience, most databases are tiny. Tiny tiny. Tables with a few thousand rows. If your web app is slow, its going to all be your fault. Stop building something webscale with microservices and just get things done right there in your database instead. Etc.
But, quite often, each company has one or two databases that have at least one or two large tables. Tables with tens of millions of rows. I work on databases with billions of rows. They exist. And that’s the kind of database where your database server is underserving you. There could well be a metric ton of actual performance improvements that your database is leaving on the table. Areas where your database server hasn’t kept up with recent (as in the past 20 years) of regular improvements in how programs can work with the kernel, for example.
Over the years I’ve read some really promising papers that have speeded up databases. But as far as I can tell, nothing ever happens. What is going on?
For example, your database might be slow just because its making a lot of syscalls. Back in 2010, experiments with syscall batching improved MySQL performance by 40% (and lots of other regular software by similar or better amounts!). That was long before spectre patches made the costs of syscalls even higher.
So where are our batched syscalls? I can’t see a downside to them. Why isn’t linux offering them and glib using them, and everyone benefiting from them? It’ll probably speed up your IDE and browser too.
Of course, your database might be slow just because you are using default settings. The historic defaults for MySQL were horrid. Pretty much the first thing any innodb user had to do was go increase the size of buffers and pools and various incantations they find by googling. I haven’t investigated, but I’d guess that a lot of the performance claims I’ve heard about innodb on MySQL 8 is probably just sensible modern defaults.
I would hold tokudb up as being much better at the defaults. That took over half your RAM, and deliberately left the other half to the operating system buffer cache.
That mention of the buffer cache brings me to another area your database could improve. Historically, databases did ‘direct’ IO with the disks, bypassing the operating system. These days, that is a metric ton of complexity for very questionable benefit. Take tokudb again: that used normal buffered read writes to the file system and deliberately left the OS half the available RAM so the file system had somewhere to cache those pages. It didn’t try and reimplement and outsmart the kernel.
This paid off handsomely for tokudb because they combined it with absolutely great compression. It completely blows the two kinds of innodb compression right out of the water. Well, in my tests, tokudb completely blows innodb right out of the water, but then teams who adopted it had to live with its incomplete implementation e.g. minimal support for foreign keys. Things that have nothing to do with the storage, and only to do with how much integration boilerplate they wrote or didn’t write. (tokudb is being end-of-lifed by percona; don’t use it for a new project 😞)
However, even tokudb didn’t take the next step: they didn’t go to async IO. I’ve poked around with async IO, both for networking and the file system, and found it to be a major improvement. Think how quickly you could walk some tables by asking for pages breath-first and digging deeper as soon as the OS gets something back, rather than going through it depth-first and blocking, waiting for the next page to come back before you can proceed.
I’ve gone on enough about tokudb, which I admit I use extensively. Tokutek went the patent route (no, it didn’t pay off for them) and Google released leveldb and Facebook adapted leveldb to become the MySQL MyRocks engine. That’s all history now.
In the actual storage engines themselves there have been lots of advances. Fractal Trees came along, then there was a SSTable+LSM renaissance, and just this week I heard about a fascinating paper on B+ + LSM beating SSTable+LSM. A user called Jules commented, wondered about B-epsilon trees instead of B+, and that got my brain going too. There are lots of things you can imagine an LSM tree using instead of SSTable at each level.
But how invested is MyRocks in SSTable? And will MyRocks ever close the performance gap between it and tokudb on the kind of workloads they are both good at?
Of course, what about Postgres? TimescaleDB is a really interesting fork based on Postgres that has a ‘hypertable’ approach under the hood, with a table made from a collection of smaller, individually compressed tables. In so many ways it sounds like tokudb, but with some extra finesse like storing the min/max values for columns in a segment uncompressed so the engine can check some constraints and often skip uncompressing a segment.
Timescaledb is interesting because its kind of merging the classic OLAP column-store with the classic OLTP row-store. I want to know if TimescaleDB’s hypertable compression works for things that aren’t time-series too? I’m thinking ‘if we claim our invoice line items are time-series data…’
Compression in Postgres is a sore subject, as is out-of-tree storage engines generally. Saying the file system should do compression means nobody has big data in Postgres because which stable file system supports decent compression? Postgres really needs to have built-in compression and really needs to go embrace the storage engines approach rather than keeping all the cool new stuff as second class citizens.
Of course, I fight the query planner all the time. If, for example, you have a table partitioned by day and your query is for a time span that spans two or more partitions, then you probably get much faster results if you split that into n queries, each for a corresponding partition, and glue the results together client-side! There was even a proxy called ShardQuery that did that. Its crazy. When people are making proxies in PHP to rewrite queries like that, it means the database itself is leaving a massive amount of performance on the table.
And of course, the client library you use to access the database can come in for a lot of blame too. For example, when I profile my queries where I have lots of parameters, I find that the mysql jdbc drivers are generating a metric ton of garbage in their safe-string-split approach to prepared-query interpolation. It shouldn’t be that my insert rate doubles when I do my hand-rolled string concatenation approach. Oracle, stop generating garbage!
This doesn’t begin to touch on the fancy cloud service you are using to host your DB. You’ll probably find that your laptop outperforms your average cloud DB server. Between all the spectre patches (I really don’t want you to forget about the syscall-batching possibilities!) and how you have to mess around buying disk space to get IOPs and all kinds of nonsense, its likely that you really would be better off perforamnce-wise by leaving your dev laptop in a cabinet somewhere.
Crikey, what a lot of complaining! But if you hear about some promising progress in speeding up databases, remember it's not realistic to hope the databases you use will ever see any kind of benefit from it. The sad truth is, your database is still stuck in the 90s. Async IO? Huh no. Compression? Yeah right. Syscalls? Okay, that’s a Linux failing, but still!
Right now my hopes are on TimescaleDB. I want to see how it copes with billions of rows of something that aren’t technically time-series. That hybrid row and column approach just sounds so enticing.
Oh, and hopefully MyRocks2 might find something even better than SSTable for each tier?
But in the meantime, hopefully someone working on the Linux kernel will rediscover the batched syscalls idea…? ;)
2 notes
·
View notes
Text
Ever wondered how the choice of primary keys impacts your SQL Server’s speed and efficiency? Let’s dive into the nitty-gritty of using Globally Unique Identifiers (GUIDs) as primary keys and how they can throw a wrench in the works, especially for large tables. We’ll also explore some handy T-SQL tricks to keep your database running smoothly. Getting the Best Out of SQL Server with…
View On WordPress
#buffer cache optimization#database design best practices#GUID primary keys#page splits mitigation#SQL Server performance
0 notes
Text
Back End
CRUD Operations: CRUD means create, read, update and delete. Using CRUD we can create data in the database if we want, read the data in the database, update the data and delete the data if we want. CRUD is very important for full-stack projects. If we can create a storefront, blog posting page, todo list or social media clone, without CRUD then we will get stuck very quickly.
JWT: JWT, or JSON Web Token, is an open value used to share security information between a client and a server. Each JWT contains an encoded JSON object that contains a claims set. JWT claims are made using a cryptographic algorithm so that claims cannot be changed after the token has been issued.
Mongoose: Mongoose is a node js-based Object Data Modeling library for MongoDB. SQLAlchemy for SQL databases like an Object Relational Mapper. The problem that Mongoose aims to solve is that developers allow the application layer to apply a specific schema.
SQL and NoSQL databases: In SQL the data is in table form. Here every data is stored inside the row. And in NOSQL the data is in object form. Here all the data of a person is shown in object form.
Aggregation: Provides aggregation data records / documents and returns computed results in MongoDB. It collects values from different documents and groups them together. It then performs various operations on the grouped data such as sum, average, minimum, maximum, etc. to return a calculated result.
Express: Express js is a Node js web application server framework, designed to create single-page, multi-page and hybrid web applications.
Nodejs: Node.js is a JavaScript runtime. It is built on Chrome's V8 JavaScript engine. JavaScript is a popular programming language that runs on any web browser, including a good web browser. Node. js is an interpreter with some specific useful libraries for JavaScript that can be used separately in JS programming. Node. js is primarily used for non-blocking, event-driven servers, due to its single-threaded nature.
Entity: Entity can be anything like a place, class or object which has an independent existence in the real world.
Entity Type: Entity Type represents an entity that has the same characteristics.
Entity Set: Entity Set in the database represents a collection of entities having a particular entity type.
Index hunting: Index hunting is the process of increasing the collection of indexes which helps to improve the query performance as well as to make the database faster.
Fragmentation: Fragmentation controls logical data units. It is also known as a fragment which is stored on different sites of a distributed database system.
Data Dictionary: A data dictionary is a set of information that describes the contents and structure of a table and a database object. The function of the information stored in the data dictionary is to control, manipulate and access the relationships between the database elements.
Primary Key: The primary key is the column in the table where each row of data is individually marked. Each row of the table may have a Primary Key but two rows may not have the same Primary Key.
Composite Key: Composite Key is a form of the candidate key where a set of columns will uniquely identify every row in the table.
Unique key: A unique key is a primary key whose data in each row is individually marked with a null value difference, meaning that the unique key approves a value as a zero value.
Database trigger: A set of commands that is automatically executed when an event occurs, such as deleting a row, while inserting, updating, before inserting into a table is called a database trigger.
B-Tree: B-Tree represents a tree-shaped data structure for external memory that can read and write large blocks of data. It is commonly used in databases and file systems where all insertions, deletions, sorting, etc. are done at logarithmic times.
Normalization: Normalization is the process of extracting unnecessary data from a database by splitting the table in a well-defined manner to maintain data integrity.
De-normalization: De-normalization is the process of adding unnecessary data to a table to speed up complex queries and thus achieve better performance.
BCNF: BCNF is the normal Boyce Codd form. This is a higher version of 3Nf where there are no multiple overlapping candidate keys.
DML Compiler: The DML compiler translates the DML statement into a query language in a low-level instruction and the generated instruction is understood by the Query Evaluation Engine.
#programmer sajeeb#programmer#programming#coder#CRUD Operations#JWT#Mongoose#SQL and NoSQL databases#Aggregation#Express#Nodejs#Entity#Entity Type#Index hunting#Fragmentation#Data Dictionary#Primary Key#Composite Key#Unique key#Database trigger
0 notes
Video
youtube
How SQL Stores Data Internally - SQL 8KB Page | SQL Data Page | SQL IAM Page | SQL Index Page
Q01. What is the 8KB page concept of SQL? Q02. What is Extent in SQL? Q03. What is Page Split in SQL? When does a page split happen? Q04. What is Fragmentation in SQL? Q05. How does SQL Server store the data internally? Q06. What are Page Header and Row Offset in SQL? Q07. What is IAM Page in SQL? How many IAM pages can be there for a table? Q08. Why the max size of the VARCHAR data type is only 8000? Q09. Why the max size of the NVARCHAR data type is only 4000? Q10. How a VARCHAR(MAX) or NVARCHAR(Max) data stores on the 8KB page? Q11. Why index can not be created on VARCHAR(MAX) or NVARCHAR(Max) data type columns? Q12. What is the maximum data row size that can be stored in a single page? Q13. What is the In-row page mean? Q14. What is the DBCC IND SQL command? Q15. What is the DBCC PAGE SQL command?
https://www.youtube.com/watch?v=NWprnHiia9U
#sqlinterviewquestions2021#mostfrequentlyaskedsqlinterviewquestions#sqlinterviewquestionsandanswers#interviewquestionsandanswers#techpointfundamentals#techpointfunda
0 notes
Text
Figmentgames Driver Download

Figment Games Driver Download Windows 7
Figmentgames Driver Download
Figment Game Ending
Figment Games Driver Download Pc
Figment Review
Figment Gameplay
Figment Games Driver Download Windows 10
Archetype Javascript Framework v.0.10.0
Trusted and safe download. Download Games Online Games. Around The World in 80 Day. Fogg win a bet and travel around the world in 80 days! Around The World in 80 Day. Fogg win a bet and travel around the world in 80 days! Around The World in 80 Day. Download Figment DMX for iOS to figment DMX is a unique application for DMX-based lighting control.Designed for lighting designers, technicians and riggers, Figment is a powerful. Download Figment DMX for iOS to figment DMX is a unique application for DMX-based lighting control.Designed for lighting designers, technicians and riggers, Figment is a powerful. GT Interactive’s cops n’ robbers driving game needs more substance. Driver is a tease. Initially, it overwhelms you with its premise and atmosphere, strutting its superb vehicle dynamics. It’s an interactive version of the best of the gritty 70s and 80s car chase movies. Here is the video game “Driver”! Released in 1999 on Windows, it's still available and playable with some tinkering. It's a racing / driving and simulation game, set in a vehicle simulator, crime, automobile and street racing themes and it was released on Mac as well.
Archetype is an Entreprise JavascriptFramework. Get documentation at http://archetypejs.org
Figment Games Driver Download Windows 7
Easy Javascript Framework (EJF) v.1.0

Easy JavascriptFramework (EJF) is a very simple framework to help people to develop applications using Javascript.There are a lot of javascriptframework nonetheless our objective is to provide a documentation of each javascript function like
Figment JavaScript Framework v.1.0.0
A simple, yet powerful JavaScriptframework that can help you build Web 2.0 applications. The framework is seperated into modules in order to reduce download
Nano JavaScript framework v.1.0
nano is a light-weight JavaScriptframework for building rich UI in web applications. Its highly extensible design lets you easily add your own functionality to the API with plugins. Visit http://www.nanojs.org for more
Sabia JavaScript Framework v.1.0
Sabia is a javascript MVC framework designed to be toolkit agnostic and productive.
Spark JavaScript framework v.1.0
Spark is a tool set which can give you a lot of options to your web app/site. DOM handlers, Ajax utilities, cool widgets, visual effects, form tools, UI components and more stuff. So you can easily build a complete and lightweight front-end interface.
JSAX JavaScript Abstractions for X(HT)ML v.20060317
JSAX - JavaScript Abstractions for X(HT)ML This is a JavaScriptframework which is compatibel with the latest versions of Mozilla, Opera, Konqueror(+safari) and
MPagesJS JavaScript Library v.1.0.rc2
mPagesJS is a JavaScriptFramework that provides a core interface into all client-side functionality within Cerner Millennium Pages - MPages. mPagesJS makes MPage development quicker and
Simple Javascript Spreadsheet v.1.0
An OpenSource Javascript Spreadsheet project based on Qooxdoo javascriptframework. This component is also a part of X4View Java Framework (see
JavaScript Development Kit v.1.0
JTDK(JavaScript Development Kit) is a javascriptframework, alias as JSDK.
Figmentgames Driver Download
JAST - Javascript Toolkit v.1.0
JAST (Javascript Toolkit) is an Open Source cross-platform javascriptframework that aid users to perform the most hard operations with few simple lines of code.It's modularity allow the download only for the code required to the page.
AONIC Framework v.1.0
AONIC JavaScriptFramework designed primarily for asynchronous push communication with back-end servers (comet). Python back-end examples included, as well as a basic JavaScript effects library, and ActionScript source for handling the active connections
Framework 2.0 v.1.0
Framework 2.0 is a JavaScriptFramework that allows to create Web-Applications based on components. Components are Services which run indepenently on the clients browser. Web-Applications are composed by combining serveral Services.
Lick Javascript Library v.1.0
The Lick Javascriptframework, is a Javascript/Dom/Ajax and widget framework aimed at simplifying the process of creating we applicatios, it has a very light memory footprint and a robust api Base
PFAST - just a PHP Framework v.1.0
PHP & JavaScriptFramework used to build webistes/web applications
DracMail Webmail v.0.2.0.beta
dracMail is a webmail interface built using PHP, ExtJS (JavaScriptframework), MySQL and IMAP. Features include: Rich UI, WYSIWYG editor, HTML mail composing and message
Jquery4jsf v.2
jQuery4jsf is a JSF(JavaServer Faces)component library that uses the power of the jQuery javascriptframework. These JSF(JavaServer Faces)components have the added value of jQuery which allows the end user to realize its application in a fast and
JSPackaging v.2.1
JSPackaging is a JavaScriptframework that provides simple directives for defining, loading & importing uniquely named packages of JavaScript modules. UPDATE: This project now exists as Ajile at http://sf.net/projects/ajile &
MathJax v.1.0
MathJax is a modular javascriptframework for including mathematics in web pages. It can take input in various formats, like TeX and MathML, and can produce output in various forms, such as MathML or HTML-with-CSS. Components are loaded as
Multiform v.1.0
Multiform allows creation of Web Applications by defining their processes and business objects in a declarative XML-based language. It's made of a Javascriptframework and an XSL compiler to get the application skeleton from the
Javascript Framework software by TitlePopularityFreewareLinuxMac
Tables2csv v.1.0
tables2csv offers the programmer a simple, fast and effective method to collect table information from the local ODBC driver and output it to comma seperated values.
Odbc2csv v.1.0
Figment Game Ending
odbc2csv offers the programmer a simple, fast and effective method to collect DSN information from the local ODBC driver and output it to comma seperated values.
Mp3 File Merger v.1.6
Mp3 File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better.
Mp3 Merger v.1.0
It is a free tool which can merge MP3 files. It can merge from 2 to 9999 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better.
Heatmap Studio v.0.1
Basic Instuctions * Data Set Restrictions o Data sets must be 2 or 3 columns comma seperated, formatting is + o2 column: X coordinate (or latitude), Y coordinate (or longitude) - example: 23,24″ + o3 Column: X coordinate (or latitude), Y
ViSplore v.0.9.138
Easily navigate your file system with breadcrumbs Traditionaly a path is seperated with forward slashes. When a user wants to navigate to a sub folder inside path. They would need to breakup the path or simply retype. Breadcrumbs breakup paths
Epsa Mp3 Merger v.1.1
Figment Games Driver Download Pc
Epsa Mp3 Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Zging Mp3 Merger v.1.1
Zging Mp3 Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Zging File Merger v.1.1
Zging File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
Epsa File Merger v.1.1
Epsa File Merger is an easy to use, yet powerful program to work with Mp3 files. It can merge most 5000 MP3 files into one MP3 file to let you be able to manage your seperated MP3 musical files better. It is small and delicate with beautiful screen
AbyssWS Log Splitter v.01b4
AbyssWS Log Splitter is a project created on Saturday, January 20, 2007. It has the ability to quickly split your Server log into seperate log files, seperated by month and year. It uses the 'Common Log
Extensible Robot Core v.rc.2.0.0
roboerc implements JAUS standard 3.3. It provides the necessary virtual networking library for JAUS message over TCP, UDP, Serial. It also uses JAUS switches to route JAUS messages across seperated virtual
Figment JavaScript Framework v.1.0.0
A simple, yet powerful JavaScript framework that can help you build Web 2.0 applications. The framework is seperated into modules in order to reduce download
KESI v.0.9
KESI - KESI Easy SQL Import, is a tool to easily import CSV files into your SQL database tables. It has a very easy to use KDE GUI and understands almost every possible CSV (comma seperated value) file
SimpleX2C v.1.0
Converts XML to CSV. You can define wich XML-Nodes should get extracted. The output is in CSV-Format (';'-seperated). There are many very good XML-Tools out there, but i want a simple tool that extract easely defined content.Open a Ticket if you
Tiny Translator v.0.6
Tiny Translator is a very simple class for easily organizing dialogue outputs and creating language tables for multilingual projects. It supports flat files (comma seperated, .csv) and MySQL databases to store
Rope pulling v.1.0
Figment Review
Code for a physical tug-of-war game that allows teams from physically seperated sites to interact. Lego's RCX is used to sense the force exerted at both sites. Video can optionally be provided via a Skype link.
Aion Emu v.1.0
Aion Emulator gives you the possibility to legally host a game server for this popular MMo Aion createde by NcSoft?Aion Emu is seperated in two parts:1) Aion Server2)Aion Datapack
JQ-Data FTP Server v.1.0
FTP Server written in JAVA. The server has an optional SWING GUI.The GUI and the server-logic is seperated as two components, but downloaded together.
Geographically Independent Office v.1.0
Figment Gameplay
Geographically Independent OfficeA WWW application to allow SOHO companys to manage their business where the office is spread over a number of geographically seperated office locations.
Figment Games Driver Download Windows 10
Seperated software by TitlePopularityFreewareLinuxMac

0 notes
Text
Database Management services provider
Internal vs. external fragmentation It's a snappy instructional exercise in transit SQL Server stores information in 8 KB "pages." In another or remade record, the pages are for the most part full and put away all together. Be that as it may, as more information gets included, pages become part: not all pages are full and they happen faulty. This is the imperative contrast among inward and outside discontinuity: External fragmentation – refers to pages being out of order Internal fragmentation – refers to the empty space on a page Focusing less on page splits Numerous database experts centre on page parts as a proportion of database fracture, be that as it may, clarified that this number is good for nothing since page parts happen both while adding another column to an unfilled table and while including another page. In this way, it's not useful all things considered. How external fragmentation can make things worse Outer discontinuity is certainly not a helpful proportion of database execution since page request doesn't have a lot of an effect on the speed of upkeep errands, running inquiries in RAM or perusing information from plate. Along these lines, database experts who attempt to fix outside discontinuity by redesigning and revamping files are really aggravating execution by swelling reinforcements and spending more support window time. Database experts who attempt to decrease outer fracture by leaving room on pages through setting a fill factor are additionally causing an issue more awful than the one they're attempting to fix. This is to a great extent since you never need to embed information at a point mid-path in the list. In this way, attempting to maintain pages in control by putting less information on every individual page is really causing interior fracture. Monitoring wait time What would it be a good idea for you to do? Setting the fill factor to the default of 100% (or if nothing else 80% or higher) and afterward remaking the records to pack them once more. Next, centre on observing the correct presentation tuning number �� hold up time. Probably the most ideal approaches to see different parts of hold up time over your database occasions is by utilizing an exhibition checking instrument to pinpoint precisely where procedures are impeding.
#sql server dba service providers#database Management services provider#DBA service providers#remote DBA services providers
0 notes
Text
Top 50 Sql Meeting Questions And Responses
https://bit.ly/3tmWIsh enables the individual to develop a unique number to be produced whenever a new document is inserted in the table. AUTOMOBILE INCREMENT is the keyword for Oracle, AUTO_INCREMENT in MySQL and IDENTIFICATION keyword phrase can be used in SQL WEB SERVER for auto-incrementing. Mainly this keyword phrase is used to develop the main key for the table. Normalization sets up the existing tables and its areas within the data source, leading to minimum replication. It is utilized to simplify a table as long as feasible while retaining the one-of-a-kind fields. If you have really little to state on your own, the job interviewer power believe you have void to claim. pl sql interview concerns I make myself really feel magnificent in front the meeting begins. With this inquiry, the recruiter will certainly judge you on exactly how you prioritise your job listing. I expect functions with damien once more in the future stressful. You mightiness need a compounding of different sorts of inquiries in order to to the full cover the concern, as well as this may diverge betwixt individuals. Prospects show up to meetings with a finish of impressing you. A primary trick is a unique kind of unique secret. A foreign secret is made use of to preserve the referential web link honesty in between 2 data tables. linked here prevents actions that can destroy web links in between a youngster as well as a moms and dad table. A primary secret is used to specify a column that distinctively determines each row. Void value and replicate values are not permitted to be entered in the main essential column. However, you could not be provided this tip, so it gets on you to remember that in such a situation a subquery is precisely what you require. After you go through the essential SQL meeting inquiries, you are most likely to be asked something more certain. And also there's no far better feeling on the planet than acing a inquiry you practiced. Yet if all you do is technique SQL interview concerns while ignoring the basics, something is mosting likely to be missing out on. Request way too many concerns might jump the meeting and reach them, however demand none will make you look unenthusiastic or not really prepared. When you are taking the examination, you should prioritise making sure that all parts of it run. Leading 50 google analytics interview concerns & solutions. Nerve-coaching from the meeting men that will blast your restless feelings so that you can be laser-focused and surefooted when you land in the spot. Terrific, trying, and im type of gallant i was capable to fix it under such stress.

Those that pass the phone or photo meeting move on to the in-person meetings. Again, it's crafty inquiry, and also not simply in damage of operations it out. On the far side permitting myself to get some howling meemies out, i genuinely delighted in the chance to get a far better feel for campus/atmosphere. Understanding the extremely certain response to some very specific SQL meeting concerns is terrific, yet it's not mosting likely to aid you if you're asked something unanticipated. Do not get me wrong-- targeted prep work can absolutely help. Note that this not a Not Void constraint and do not perplex the default worth restraint with forbiding the Void entrances. The default worth for the column is established just when the row is created for the first time and column worth is disregarded on the Insert. Denormalization is a database optimization technique for raising a data source infrastructure performance by including repetitive data to one or more tables. Normalization is a data source design method to organize tables to minimize data redundancy and also information reliance. SQL restraints are the set of rules to limit the insertion, deletion, or updating of information in the databases. They restrict the type of information entering a table for preserving information accuracy and also integrity. CREATE-- Used to produce the data source or its objects like table, index, feature, sights, activates, and so on. A special trick is made use of to uniquely determine each record in a database. A CHECK constraint is used to restrict the values or kind of information that can be kept in a column. A Main key is column whose values uniquely determine every row in a table. The major role of a main type in a data table is to preserve the internal integrity of a information table. Query/Statement-- They're frequently utilized reciprocally, yet there's a mild difference. Listed below are different SQL interview questions as well as answers that declares your knowledge concerning SQL and supply brand-new understandings and also discovering the language. Experience these SQL meeting inquiries to refresh your expertise before any type of interview. Therefore, your following job will not have to do with discussing what SQL restraints as well as secrets suggest as a whole, although you need to be very knowledgeable about the concept. You will certainly instead be provided the opportunity to show your capacity to clarify on a specific type of an SQL restriction-- the foreign vital restriction. Write a SQL question to locate the 10th tallest optimal ("Elevation") from a "Mountain" table. Adjustment to the column with NULL value or perhaps the Insert procedure defining the Null worth for the column is enabled. Click on the Establish Key Trick toolbar switch to set the StudId column as the primary key column. A RIGHT OUTER JOIN is one of the SIGN UP WITH procedures that allows you to specify a JOIN provision. It preserves the unparalleled rows from the Table2 table, joining them with a NULL in the form of the Table1 table. And then, as presently as we cut that prospect, everybody burst out laughing however you can't be in on the technique." there are several " weak points" that you can develop into favorable scenarios to share an response that your interviewer will certainly respect as well as see. - this environs covers the hardware, servers, operating system, internet internet browsers, various other software program system, etc. Obligations that you were not able-bodied to be complete. "i find out which project is near substantial, and afterwards i try to do that task initially earlier finish the doing well one. Permanently instance, there are technique of accountancy plan, arsenal bundle, and so on. While https://geekinterview.net to ask generic inquiries, you take the chance of not acquiring the discerning info you need to make the very best hiring decision. Question optimization is a procedure in which database system compares various query strategies and also pick the inquiry with the least expense. https://tinyurl.com/c7k3vf9t produced on more than one column is called composite main trick. ERASE removes some or all rows from a table based upon the condition. TRIM removes ALL rows from a table by de-allocating the memory pages. The operation can not be rolled back DECREASE command eliminates a table from the data source completely. The major distinction in between the two is that DBMS conserves your information as files whereas RDMS saves your information in tabular type. Additionally, as the keyword Relational indicates, RDMS allows different tables to have connections with each other making use of Main Keys, Foreign Keys and so on. This creates a dynamic chain of power structure between tables which likewise uses useful constraint on the tables. Think that there go to the very least 10 records in the Hill table. That's why leading companies are progressively relocating far from generic questions and are instead providing prospects a split at real-life inner situations. "At Airbnb, we offered prospective hires access to the tools we utilize as well as a vetted data set, one where we understood its restrictions as well as troubles. It permitted them to focus on the form of the information and frame solution to problems that were purposeful to us," keeps in mind Geggatt. A Check restraint look for a details condition prior to putting data into a table. If the data passes all the Inspect restraints then the data will certainly be inserted into the table or else the information for insertion will certainly be thrown out. The CHECK constraint makes certain that all worths in a column satisfy specific problems. A Not Void constraint restricts the insertion of null worths into a column. If we are making use of a Not Void Restraint for a column after that we can not ignore the worth of this column throughout insertion of information into the table. The default constraint allows you to establish a default worth for the column.
0 notes
Text
Leading 50 Sql Interview Questions As Well As Responses
Auto increment enables the individual to create a unique number to be created whenever a brand-new record is put in the table. CAR INCREMENT is the keyword for Oracle, AUTO_INCREMENT in MySQL and IDENTITY key phrase can be made use of in SQL WEB SERVER for auto-incrementing. Mainly this keyword phrase is used to create the primary key for the table. Normalization sets up the existing tables and its fields within the database, resulting in minimal replication. It is utilized to streamline a table as long as feasible while keeping the special fields. If you have really little to claim on your own, the recruiter power believe you have null to state. pl sql interview inquiries I make myself feel magnificent in front the interview begins. With this question, the employer will certainly evaluate you on just how you prioritise your job listing. I expect operations with damien once again in the future strained. You mightiness require a compounding of different kinds of questions in order to fully cover the concern, and also this may diverge betwixt individuals. Candidates appear to interviews with a surface of thrilling you. A primary key is a unique sort of unique trick. A international key is utilized to keep the referential web link stability between 2 information tables. It protects against actions that can ruin links between a kid and a moms and dad table. A primary secret is utilized to define a column that uniquely determines each row. Null value and duplicate values are not permitted to be entered in the main crucial column. However, you may not be given this hint, so it is on you to remember that in such a scenario a subquery is exactly what you require. After you experience the basic SQL meeting inquiries, you are likely to be asked something extra certain. And also there's no better feeling worldwide than acing a concern you practiced. But if geekinterview do is method SQL interview inquiries while neglecting the basics, something is mosting likely to be missing out on. Request too many inquiries might jump the meeting as well as reach them, but request none will make you look unenthusiastic or not really prepared. When you are taking the test, you should prioritise making certain that all parts of it run. Leading 50 google analytics interview questions & answers. Nerve-coaching from the interview people that will certainly blast your troubled sensations to ensure that you can be laser-focused as well as surefooted as soon as you land in the hot seat. Terrific, attempting, and also im type of gallant i was capable to settle it under such tension. Those who pass the phone or picture meeting go on to the in-person meetings. Once again, it's crafty concern, and not simply in damages of operations it out. On the far side permitting myself to get some shouting meemies out, i really taken pleasure in the possibility to obtain a better feel for campus/atmosphere. Knowing the extremely certain answers to some really particular SQL meeting questions is excellent, however it's not going to help you if you're asked something unexpected. Don't get me wrong-- targeted prep work can absolutely help. Keep in https://is.gd/snW9y3 that this not a Not Null restraint as well as do not puzzle the default worth constraint with forbiding the Null entries. The default worth for the column is set just when the row is created for the first time and column worth is ignored on the Insert. Denormalization is a data source optimization strategy for enhancing a database infrastructure performance by including redundant data to one or more tables. Normalization is a database design strategy to organize tables to lower information redundancy and data reliance. SQL constraints are the set of regulations to restrict the insertion, deletion, or upgrading of information in the databases. They restrict the kind of data going in a table for keeping information precision and integrity. PRODUCE-- Used to develop the data source or its items like table, index, feature, views, sets off, etc. A special key is used to distinctly identify each document in a database. A CHECK restraint is utilized to limit the worths or kind of data that can be stored in a column. A Primary key is column whose worths distinctively determine every row in a table. The main role of a main key in a data table is to maintain the internal stability of a information table. Query/Statement-- They're frequently utilized reciprocally, yet there's a slight difference. Listed here are various SQL interview concerns as well as solutions that declares your understanding regarding SQL as well as provide new understandings as well as discovering the language. Experience these SQL interview inquiries to rejuvenate your understanding before any type of meeting.

As a result, your following task won't be about describing what SQL restrictions and tricks imply generally, although you need to be really accustomed to the principle. You will rather be given the chance to show your capacity to specify on a details type of an SQL restriction-- the foreign crucial constraint. Write a SQL query to find the 10th tallest peak (" Altitude") from a " Hill" table. Adjustment to the column with VOID worth and even the Insert procedure specifying the Void value for the column is permitted. Click the Set Primary Trick toolbar button to set the StudId column as the primary crucial column. A RIGHT OUTER SIGN UP WITH is one of the JOIN procedures that enables you to specify a SIGN UP WITH clause. It maintains the unrivaled rows from the Table2 table, joining them with a NULL in the shape of the Table1 table. And afterwards, as currently as we cut that possibility, everyone burst out laughing yet you can not be in on the technique." there are many " weak points" that you can become favorable situations to reveal an response that your recruiter will certainly value and see. - this environs covers the ironware, servers, running plan, internet internet browsers, various other software program system, etc. Duties that you were not able-bodied to be full. "i figure out which task is near considerable, and afterwards i try to do that project initially previously end up the being successful one. Permanently example, there are approach of audit package, arsenal package, etc. While it's much easier to ask common questions, you take the chance of not obtaining the discerning details you need to make the best hiring decision. Question optimization is a procedure in which database system compares various question techniques and pick the question with the least cost. Main key developed on more than one column is called composite main trick. REMOVE removes some or all rows from a table based on the problem. ABBREVIATE gets rid of ALL rows from a table by de-allocating the memory pages. The procedure can not be rolled back DECLINE command eliminates a table from the data source completely. The main distinction in between the two is that DBMS conserves your information as documents whereas RDMS saves your information in tabular type. Also, as the keyword Relational implies, RDMS permits various tables to have connections with one another using Primary Keys, Foreign Keys etc. This creates a dynamic chain of hierarchy in between tables which also uses practical constraint on the tables. Think that there go to the very least 10 records in the Mountain table. That's why leading firms are progressively relocating far from common concerns and also are instead supplying candidates a split at real-life inner circumstances. "At Airbnb, we provided possible hires access to the tools we make use of and also a vetted information collection, one where we knew its restrictions and troubles. It allowed them to concentrate on the shape of the data as well as framework answers to problems that were significant to us," notes Geggatt. A Check constraint look for a certain condition prior to inserting data right into a table. If the data passes all the Inspect restrictions then the data will certainly be inserted right into the table or else the data for insertion will be disposed of. The CHECK constraint guarantees that all values in a column satisfy particular conditions. https://tinyurl.com/c7k3vf9t restricts the insertion of null worths right into a column. If we are using a Not Void Constraint for a column after that we can not neglect the worth of this column during insertion of data right into the table. The default constraint enables you to establish a default value for the column.
0 notes
Text
Exploring the Visual Studio Code REST Book extension for native Notebooks
My co-worker Tanha Kabir has a cool Visual Studio Code extension called REST Book. Sure, there's lots of extensions and lots of ways to call REST APIs from Visual Studio Code - not to mention the command line.
However, REST Book is a Postman-like notebook that uses the Native Notebooks UI experience that's already built into Visual Studio code.
If you already love the concept of Notebooks like I do, you'll love REST Book. It's electric paper! Just like .NET Interactive or Jupyter Notebooks, it mixes Prose and Code in a very clean and very intuitive interface.
NOTE: Today the REST Book extension requires Visual Studio Code Insiders, but not for long. Get Insiders and run it side-by-side with a stable VS Code here.
Here's me calling into my Nightscout server to see my real-time Blood Glucose:
Pretty cool. It's early days but I think Tanha already has a very interesting combination of a native Notebook experience and a Postman-like experience. Note I've also created a "SECRET" in the form of my API Key, and then I can refer to it in the GET request using $SECRETS.name.
You can also assign variables like:
let foo = GET https://hanselman.com
and then use them in subsequent cells with $.foo.headers.User-Agent, etc.
Just install the Rest Book extesnion in VS Code Insiders, and make a new empty text file with a .restbook extension.
You can do GET and have the URL on multiple lines if you split on a ? or &
GET https://www.google.com ?query="hanselman" &page=2 User-Agent: rest-book Content-Type: application/json
And you can POST and each new line will be a Header, until the last lines after a line separator which is the body of the call.
POST https://www.myexampleapi.com User-Agent: rest-book Content-Type: application/json { name: "Hello", text: "Hi friends, how are you all?" }
If you want to get involved, look at the source, file an issue or bug, or just give compliments, do it over on her repository at https://github.com/tanhakabir/rest-book Have fun!
Sponsor: The No. 1 reason developers choose Couchbase? You can use your existing SQL++ skills to easily query and access JSON. That’s more power and flexibility with less training. Learn more.
© 2021 Scott Hanselman. All rights reserved.




Exploring the Visual Studio Code REST Book extension for native Notebooks published first on http://7elementswd.tumblr.com/
0 notes
Text
Leading 50 Sql Interview Questions And Also Solutions
Automobile increment enables the individual to create a serial number to be produced whenever a new document is placed in the table. AUTOMOBILE INCREMENT is the keyword for Oracle, AUTO_INCREMENT in MySQL and IDENTITY keyword phrase can be utilized in SQL WEB SERVER for auto-incrementing. Mainly this search phrase is used to produce the main trick for the table. Normalization organizes the existing tables and its areas within the data source, causing minimal duplication. It is utilized to simplify a table as high as possible while preserving the special areas. If you have actually little to state for yourself, the job interviewer power believe you have void to claim. pl sql meeting questions I make myself feel divine ahead the interview starts. With sql queries interview questions , the employer will certainly judge you on exactly how you prioritise your task checklist. I look forward to functions with damien once again in the future strained. You mightiness require a compounding of dissimilar types of questions in order to fully cover the concern, and this may split betwixt participants. https://bit.ly/3tmWIsh turn up to interviews with a surface of impressing you. A main secret is a unique sort of unique trick. A foreign secret is used to maintain the referential web link stability in between two information tables. It prevents activities that can damage web links in between a kid and also a moms and dad table. A main secret is utilized to specify a column that distinctively identifies each row. Null worth as well as replicate worths are not permitted to be entered in the main key column. However, you might not be provided this tip, so it gets on you to bear in mind that in such a circumstance a subquery is exactly what you require. After you go through the basic SQL meeting concerns, you are most likely to be asked something more details. As well as there's no far better feeling on the planet than acing a inquiry you exercised. Yet if all you do is method SQL meeting concerns while disregarding the essentials, something is going to be missing. Demand a lot of questions may leap the interview and also reach them, but request none will certainly make you look unenthusiastic or unprepared. When you are taking the test, you need to prioritise making certain that all parts of it run. Top 50 google analytics meeting inquiries & responses. Nerve-coaching from the meeting guys that will blast your restless sensations to make sure that you can be laser-focused as well as surefooted once you land in the spot. Terrific, attempting, and im sort of gallant i was qualified to resolve it under such stress. Those who pass the phone or photo interview proceed to the in-person meetings. Once again, it's smart question, and not just in damages of workings it out. Beyond permitting https://geekinterview.net to get some screaming meemies out, i truly appreciated the chance to obtain a far better feel for campus/atmosphere. Recognizing the very details solution to some very details SQL interview questions is excellent, but it's not going to aid you if you're asked something unforeseen. Don't get me wrong-- targeted prep work can certainly help. Keep in mind that this not a Not Null restriction and do not puzzle the default value restriction with disallowing the Void access. The default value for the column is established just when the row is produced for the first time and also column worth is neglected on the Insert. Denormalization is a data source optimization technique for boosting a data source facilities performance by including redundant information to one or more tables. Normalization is a database design strategy to arrange tables to decrease information redundancy and information dependence. SQL constraints are the set of rules to limit the insertion, removal, or updating of data in the data sources. They restrict the kind of information entering a table for keeping data precision and also honesty. PRODUCE-- Used to develop the database or its objects like table, index, feature, views, activates, and so on. A distinct key is made use of to uniquely determine each document in a database. A CHECK constraint is used to restrict the values or type of data that can be kept in a column. A Primary key is column whose values distinctively recognize every row in a table. The main function of a main type in a information table is to maintain the interior honesty of a information table. Query/Statement-- They're typically used mutually, yet there's a minor difference. Listed here are various SQL meeting inquiries as well as answers that reaffirms your understanding about SQL as well as offer brand-new insights as well as learning more about the language. Undergo these SQL meeting questions to freshen your expertise prior to any type of meeting. Consequently, your next task will not be about discussing what SQL restraints and keys indicate generally, although you have to be really accustomed to the idea. You will certainly instead be offered the chance to demonstrate your capability to clarify on a particular type of an SQL restraint-- the international essential restraint. Compose a SQL query to find the 10th tallest peak (" Altitude") from a "Mountain" table. Alteration to the column with VOID value or perhaps the Insert procedure defining the Null value for the column is enabled. Click on the Set Main Key toolbar button to establish the StudId column as the main essential column. A RIGHT OUTER SIGN UP WITH is among the JOIN procedures that permits you to define a SIGN UP WITH condition. It maintains the unequaled rows from the Table2 table, joining them with a NULL in the shape of the Table1 table.

And after that, as presently as we reduced that prospect, every person broken out laughing however you can not be in on the method." there are many "weaknesses" that you can turn into favorable scenarios to reveal an solution that your interviewer will certainly respect and also see. - this environments covers the ironware, servers, operating system, web internet browsers, various other software application system, etc. Tasks that you were not able-bodied to be total. "i find out which job is near considerable, and after that i try to do that job first previously end up the doing well one. For good example, there are technique of audit plan, arsenal bundle, and so on. While it's much easier to ask generic questions, you run the risk of not acquiring the careful details you need to make the most effective hiring determination. Query optimization is a process in which database system compares various query methods and select the query with the least cost. Primary vital created on more than one column is called composite primary trick. REMOVE removes some or all rows from a table based on the problem. TRUNCATE eliminates ALL rows from a table by de-allocating the memory pages. The procedure can not be curtailed DROP command removes a table from the database totally. The primary difference in between the two is that DBMS saves your info as files whereas RDMS saves your details in tabular form. Also, as the keyword Relational implies, RDMS allows various tables to have relationships with one another making use of Main Keys, Foreign Keys and so on. This develops a dynamic chain of power structure between tables which likewise uses helpful constraint on the tables. Assume that there are at the very least 10 documents in the Hill table. That's why leading firms are increasingly relocating far from generic concerns and also are rather providing prospects a crack at real-life internal circumstances. "At Airbnb, we provided potential hires access to the devices we make use of as well as a vetted data set, one where we understood its restrictions as well as issues. It allowed them to concentrate on the shape of the information as well as framework answers to problems that were meaningful to us," notes Geggatt. A Examine constraint checks for a certain condition prior to putting information into a table. If the data passes all the Examine restraints then the data will be inserted right into the table or else the data for insertion will certainly be thrown out. The CHECK restriction guarantees that all worths in a column please specific conditions. A Not Null restraint restricts the insertion of null worths into a column. If we are making use of a Not Void Restriction for a column then we can not neglect the value of this column throughout insertion of data into the table. The default constraint enables you to establish a default worth for the column.
0 notes