#Team Foundation Server installation
Explore tagged Tumblr posts
Text
Obsidian And RTX AI PCs For Advanced Large Language Model
How to Utilize Obsidian‘s Generative AI Tools. Two plug-ins created by the community demonstrate how RTX AI PCs can support large language models for the next generation of app developers.
Obsidian Meaning
Obsidian is a note-taking and personal knowledge base program that works with Markdown files. Users may create internal linkages for notes using it, and they can see the relationships as a graph. It is intended to assist users in flexible, non-linearly structuring and organizing their ideas and information. Commercial licenses are available for purchase, however personal usage of the program is free.
Obsidian Features
Electron is the foundation of Obsidian. It is a cross-platform program that works on mobile operating systems like iOS and Android in addition to Windows, Linux, and macOS. The program does not have a web-based version. By installing plugins and themes, users may expand the functionality of Obsidian across all platforms by integrating it with other tools or adding new capabilities.
Obsidian distinguishes between community plugins, which are submitted by users and made available as open-source software via GitHub, and core plugins, which are made available and maintained by the Obsidian team. A calendar widget and a task board in the Kanban style are two examples of community plugins. The software comes with more than 200 community-made themes.
Every new note in Obsidian creates a new text document, and all of the documents are searchable inside the app. Obsidian works with a folder of text documents. Obsidian generates an interactive graph that illustrates the connections between notes and permits internal connectivity between notes. While Markdown is used to accomplish text formatting in Obsidian, Obsidian offers quick previewing of produced content.
Generative AI Tools In Obsidian
A group of AI aficionados is exploring with methods to incorporate the potent technology into standard productivity practices as generative AI develops and speeds up industry.
Community plug-in-supporting applications empower users to investigate the ways in which large language models (LLMs) might improve a range of activities. Users using RTX AI PCs may easily incorporate local LLMs by employing local inference servers that are powered by the NVIDIA RTX-accelerated llama.cpp software library.
It previously examined how consumers might maximize their online surfing experience by using Leo AI in the Brave web browser. Today, it examine Obsidian, a well-known writing and note-taking tool that uses the Markdown markup language and is helpful for managing intricate and connected records for many projects. Several of the community-developed plug-ins that add functionality to the app allow users to connect Obsidian to a local inferencing server, such as LM Studio or Ollama.
To connect Obsidian to LM Studio, just select the “Developer” button on the left panel, load any downloaded model, enable the CORS toggle, and click “Start.” This will enable LM Studio’s local server capabilities. Because the plug-ins will need this information to connect, make a note of the chat completion URL from the “Developer” log console (“http://localhost:1234/v1/chat/completions” by default).
Next, visit the “Settings” tab after launching Obsidian. After selecting “Community plug-ins,” choose “Browse.” Although there are a number of LLM-related community plug-ins, Text Generator and Smart Connections are two well-liked choices.
For creating notes and summaries on a study subject, for example, Text Generator is useful in an Obsidian vault.
Asking queries about the contents of an Obsidian vault, such the solution to a trivia question that was stored years ago, is made easier using Smart Connections.
Open the Text Generator settings, choose “Custom” under “Provider profile,” and then enter the whole URL in the “Endpoint” section. After turning on the plug-in, adjust the settings for Smart Connections. For the model platform, choose “Custom Local (OpenAI Format)” from the options panel on the right side of the screen. Next, as they appear in LM Studio, type the model name (for example, “gemma-2-27b-instruct”) and the URL into the corresponding fields.
The plug-ins will work when the fields are completed. If users are interested in what’s going on on the local server side, the LM Studio user interface will also display recorded activities.
Transforming Workflows With Obsidian AI Plug-Ins
Consider a scenario where a user want to organize a trip to the made-up city of Lunar City and come up with suggestions for things to do there. “What to Do in Lunar City” would be the title of the new note that the user would begin. A few more instructions must be included in the query submitted to the LLM in order to direct the results, since Lunar City is not an actual location. The model will create a list of things to do while traveling if you click the Text Generator plug-in button.
Obsidian will ask LM Studio to provide a response using the Text Generator plug-in, and LM Studio will then execute the Gemma 2 27B model. The model can rapidly provide a list of tasks if the user’s machine has RTX GPU acceleration.
Or let’s say that years later, the user’s buddy is visiting Lunar City and is looking for a place to dine. Although the user may not be able to recall the names of the restaurants they visited, they can review the notes in their vault Obsidian‘s word for a collection of notes to see whether they have any written notes.
A user may ask inquiries about their vault of notes and other material using the Smart Connections plug-in instead of going through all of the notes by hand. In order to help with the process, the plug-in retrieves pertinent information from the user’s notes and responds to the request using the same LM Studio server. The plug-in uses a method known as retrieval-augmented generation to do this.
Although these are entertaining examples, users may see the true advantages and enhancements in daily productivity after experimenting with these features for a while. Two examples of how community developers and AI fans are using AI to enhance their PC experiences are Obsidian plug-ins.
Thousands of open-source models are available for developers to include into their Windows programs using NVIDIA GeForce RTX technology.
Read more on Govindhtech.com
#Obsidian#RTXAIPCs#LLM#LargeLanguageModel#AI#GenerativeAI#NVIDIARTX#LMStudio#RTXGPU#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
3 notes
·
View notes
Text
The Debate of the Decade: What to choose as the backend framework Node.Js or Ruby on Rails?
New, cutting-edge web development frameworks and tools have been made available in recent years. While this variety is great for developers and company owners alike, it does come with certain drawbacks. This not only creates a lot of confusion but also slows down development at a time when quick and effective answers are essential. This is why discussions about whether Ruby on Rails or Noe.js is superior continue to rage. What framework is best for what kind of project is a hotly contested question. Nivida Web Solutions is a top-tier web development company in Vadodara. Nivida Web Solutions is the place to go if you want to make a beautiful website that gets people talking.

Identifying the optimal option for your work is challenging. This piece breaks things down for you. Two widely used web development frameworks, RoR and Node.js, are compared and contrasted in this article. We'll also get deep into contrasting RoR and Node.js. Let's get started with a quick overview of Ruby on Rails and Node.js.
NodeJS:
This method makes it possible to convert client-side software to server-side ones. At the node, JavaScript is usually converted into machine code that the hardware can process with a single click. Node.js is a very efficient server-side web framework built on the Chrome V8 Engine. It makes a sizable contribution to the maximum conversion rate achievable under normal operating conditions.
There are several open-source libraries available through the Node Package Manager that make the Node.js ecosystem special. Node.js's built-in modules make it suitable for managing everything from computer resources to security information. Are you prepared to make your mark in the online world? If you want to improve your online reputation, team up with Nivida Web Solutions, the best web development company in Gujarat.
Key Features:
· Cross-Platforms Interoperability
· V8 Engine
· Microservice Development and Swift Deployment
· Easy to Scale
· Dependable Technology
Ruby on Rails:
The back-end framework Ruby on Rails (RoR) is commonly used for both web and desktop applications. Developers appreciate the Ruby framework because it provides a solid foundation upon which other website elements may be built. A custom-made website can greatly enhance your visibility on the web. If you're looking for a trustworthy web development company in India, go no further than Nivida Web Solutions.
Ruby on Rails' cutting-edge features, such as automatic table generation, database migrations, and view scaffolding, are a big reason for the framework's widespread adoption.
Key Features:
· MVC Structure
· Current Record
· Convention Over Configuration (CoC)
· Automatic Deployment
· The Boom of Mobile Apps
· Sharing Data in Databases
Node.js v/s RoR:
· Libraries:
The Rails package library is called the Ruby Gems. However, the Node.Js Node Package Manager (NPM) provides libraries and packages to help programmers avoid duplicating their work. Ruby Gems and NPM work together to make it easy to generate NPM packages with strict version control and straightforward installation.
· Performance:
Node.js' performance has been lauded for its speed. Node.js is the go-to framework for resource-intensive projects because of its ability to run asynchronous code and the fact that it is powered by Google's V8 engine. Ruby on Rails is 20 times less efficient than Node.js.
· Scalability:
Ruby's scalability is constrained by comparison to Node.js due to the latter's cluster module. In an abstraction-based cluster, the number of CPUs a process uses is based on the demands of the application.
· Architecture:
The Node.js ecosystem has a wealth of useful components, but JavaScript was never designed to handle backend activities and has significant constraints when it comes to cutting-edge construction strategies. Ruby on Rails, in contrast to Node.js, is a framework that aims to streamline the process of building out a website's infrastructure by eliminating frequent installation problems.
· The learning curve:
Ruby has a low barrier to entry since it is an easy language to learn. The learning curve with Node.js is considerably lower. JavaScript veterans will have the easiest time learning the language, but developers acquainted with various languages should have no trouble.
Final Thoughts:
Both Node.JS and RoR have been tried and tested in real-world scenarios. Ruby on Rails is great for fast-paced development teams, whereas Node.js excels at building real-time web apps and single-page applications.
If you are in need of a back-end developer, Nivida Web Solutions, a unique web development agency in Gujarat, can assist you in creating a product that will both meet and exceed the needs of your target audience.
#web development company in vadodara#web development company in India#web development company in Gujarat#Web development Companies in Vadodara#Web development Companies in India#Web development Companies in Gujarat#Web development agency in Gujarat#Web development agency in India#Web development agency in Vadodara
8 notes
·
View notes
Text
Master DevOps Like a Pro: Learn Terraform, Kubernetes, Ansible & Docker in One Course

If you're dreaming of mastering DevOps and landing high-paying roles in tech, there's no better time than now to level up your skills. Whether you're a system admin, developer, or IT professional aiming to break into the DevOps world, the right tools and training make all the difference. What if you could learn the most in-demand DevOps technologies—Terraform, Kubernetes, Ansible, and Docker—all in one place?
Introducing the DevOps MasterClass: Terraform Kubernetes Ansible Docker—a complete, hands-on course designed to equip you with real-world skills that employers are actively searching for.
Let’s explore what makes this course so powerful and why it might just be the best decision you make for your tech career.
🚀 Why DevOps Is Changing the Tech Industry
Before we dive into the tools, let's quickly understand why DevOps is a game-changer.
Traditional software development and operations used to work in silos. Developers wrote the code, and operations teams handled deployments. The result? Slow, buggy releases and constant miscommunication.
DevOps breaks those silos—it's a culture, a set of practices, and a toolkit that enables teams to collaborate better, release faster, and maintain higher software quality. With major companies like Netflix, Amazon, and Google using DevOps pipelines, the demand for skilled DevOps engineers is skyrocketing.
🎯 What Makes This MasterClass Stand Out?
There are dozens of DevOps tutorials online—but here’s why this DevOps MasterClass: Terraform Kubernetes Ansible Docker truly stands out:
All-in-One Learning: Learn four top tools in one place—Terraform, Kubernetes, Ansible, and Docker.
Real-World Projects: Not just theory. You’ll work on projects that simulate real DevOps environments.
Beginner to Advanced: No matter your level, the course guides you step-by-step.
Lifetime Access: Learn at your own pace and revisit anytime.
Industry-Relevant Curriculum: Aligned with what companies actually use in production.
🧰 The DevOps Toolkit You’ll Master
Let’s break down the four core tools you'll be learning—and why each is so important for modern DevOps practices.
1. Terraform: Infrastructure as Code Made Easy
Imagine being able to create, manage, and scale infrastructure with just a few lines of code. That’s Terraform for you.
Instead of manually setting up cloud resources (which is time-consuming and error-prone), Terraform lets you define everything as code. Whether it’s AWS, Azure, or GCP, Terraform handles it with elegance.
You’ll learn:
How to write Terraform configuration files
Create and destroy cloud resources with ease
Build reusable infrastructure modules
Automate cloud provisioning
This part of the course helps you build the foundations of Infrastructure as Code (IaC)—a must-have skill in modern cloud environments.
2. Kubernetes: Container Orchestration Done Right
Kubernetes, often called K8s, is the gold standard for managing containers. If Docker helps you build and ship containers, Kubernetes helps you scale, manage, and monitor them in production.
In the course, you’ll cover:
Kubernetes architecture (pods, nodes, services)
Deploying applications using YAML
Scaling applications up/down automatically
Handling updates and rollbacks
Managing persistent storage and secrets
This is essential if you’re aiming to run apps at scale and work with microservices.
3. Ansible: Configuration Management Without the Hassle
Ansible makes IT automation simple. It allows you to configure servers, install software, and manage services with human-readable playbooks—no coding headaches.
What you’ll learn:
Writing and running Ansible playbooks
Automating server setups (Linux, cloud VMs, etc.)
Managing app deployments with Ansible roles
Integrating Ansible with CI/CD pipelines
This will help you automate repetitive tasks and maintain consistent environments—a crucial DevOps capability.
4. Docker: The Foundation of Modern DevOps
Docker changed everything. It made app packaging and deployment incredibly easy. Instead of “it works on my machine,” Docker ensures it works everywhere.
You’ll master:
Dockerfile creation and image building
Working with Docker Hub and registries
Networking and volumes
Docker Compose for multi-container apps
Best practices for image optimization and security
Docker is the first tool many DevOps learners start with—and in this course, it’s covered thoroughly.
🔄 How These Tools Work Together in a DevOps Pipeline
These four tools don’t work in isolation—they complement each other perfectly:
Docker packages the application.
Ansible automates the server environment.
Terraform sets up the infrastructure.
Kubernetes deploys and scales your Docker containers.
By mastering this combo, you’ll be able to build a robust, automated DevOps pipeline that mirrors real-world enterprise environments.
💼 Who Should Take This Course?
The DevOps MasterClass: Terraform Kubernetes Ansible Docker is ideal for:
Aspiring DevOps engineers looking to enter the field
System admins who want to automate and modernize infrastructure
Developers who want to understand deployments better
Cloud professionals who need to work across platforms
IT managers who want to upskill their team or shift into DevOps roles
If you’re passionate about learning and ready to commit, this course is your launchpad.
🧠 What You’ll Build (Hands-On Projects)
Unlike dry tutorials, this course emphasizes hands-on experience. Expect to build and manage:
Real-world infrastructure using Terraform on AWS
Scalable deployments on Kubernetes clusters
Automated software installation using Ansible
Containerized web applications with Docker and Docker Compose
These projects will fill your GitHub portfolio—and help you impress hiring managers or clients.
📈 Job Market Value of These Skills
Let’s talk money. According to Glassdoor and Indeed:
DevOps Engineers earn an average of $115,000 to $150,000 per year
Terraform, Kubernetes, Docker, and Ansible skills are listed in 80% of DevOps job posts
Many companies are looking for multi-skilled professionals who can handle everything from infrastructure to deployment
Learning all four tools gives you a major competitive edge.
🧩 What’s Inside the Course (Module Breakdown)
Here’s a sneak peek at the modules:
Introduction to DevOps & Tools Overview
Docker Basics to Advanced
Working with Docker Compose
Ansible Playbooks and Automation
Terraform Infrastructure Provisioning
Kubernetes Architecture & Deployment
CI/CD Integration with DevOps Tools
Project-Based Learning
Every module includes real-world examples, quizzes, and projects to test your skills.
🌐 Why Learn from This Course Instead of Free Tutorials?
It’s tempting to rely on YouTube or blogs for learning. But here’s what this paid course gives you that free resources don’t:
✅ Structured Curriculum ✅ Lifetime Access ✅ Community Support ✅ Expert Instructor Guidance ✅ Projects to Build Your Portfolio
Investing in a high-quality course isn’t just about information—it’s about transformation. You go from knowing a tool to mastering it with confidence.
✨ What Learners Are Saying
⭐ “This course helped me land a DevOps role in just 3 months. The Terraform and Kubernetes modules were spot on.” — Ravi, India
⭐ “I was new to Docker and Ansible, and now I deploy apps in Kubernetes like a pro. Highly recommend this course!” — Jessica, UK
⭐ “Finally, a practical course that teaches how these tools work together. Worth every minute.” — Carlos, USA
🎓 Final Thoughts: Your DevOps Journey Starts Now
The tech world is evolving rapidly, and DevOps is no longer optional—it’s essential. With this DevOps MasterClass: Terraform Kubernetes Ansible Docker, you gain a complete DevOps skill set that’s immediately applicable in the real world.
Don’t waste time juggling multiple incomplete tutorials. Master everything in one comprehensive, expertly designed course.
👉 Take charge of your future. Learn the most in-demand tools. Build real projects. And become the DevOps expert companies are searching for.
Ready to get started?
Enroll in the DevOps MasterClass now and take your first step toward DevOps mastery.
0 notes
Text
Why Tech Startups Are Choosing Steel Buildings for Their First Facility
With the rapid growth of cloud computing and data-heavy applications, more tech startups are entering the market to meet rising digital demand. These companies need dependable data centers that can meet operational needs while being ready for future expansion.
Choosing the right building material is crucial because it affects everything from environmental impact and build speed to long-term functionality. While concrete remains a viable option for some projects, the steel buildinghas become a preferred choice for many startups due to its faster construction process and adaptability. Join us in this blog as we break down the reasons new tech startups are choosing to build their facilities with steel.
Faster builds for faster growth
Speed matters when building data centers or tech facilities. Steel buildings speed up construction without compromising strength or accuracy. Steel’s lighter weight makes it easier to transport, handle, and assemble, reducing labor time and complexity on site. Startups can open their facilities and start generating returns as soon as possible.
Pre-engineered steel buildings are designed for fast assembly. Components arrive at the job site ready to be bolted or welded into place, eliminating the time-consuming on-site work that concrete construction requires. This level of efficiency helps startups meet project deadlines and bring their products to market faster.
Built for durability and long-term efficiency
Steel can support heavy equipment and withstand environmental stress. Unlike materials that may warp or degrade over time, a steel building maintains its shape and strength for decades, an important factor for tech facilities running 24/7 operations.
Steel’s lighter weight gives it a major advantage in areas prone to earthquakes. It reduces stress on the foundation and improves seismic performance, lowering the risk of service interruptions after a seismic event.
Steel also supports efficient design layouts, which is especially useful for tech startups and data centers. Engineers can optimize cooling systems and airflow to reduce energy use and help companies hit sustainability targets while maintaining system performance.
Speed to market
Steel construction also moves faster from assembly to erection and completion. Concrete buildings require on-site pouring and staging, which can add weeks to the schedule. Steel structures, on the other hand, use modular panels and prefabricated components to speed up the construction process. This modular approach minimizes weather delays and allows other trades to begin interior work sooner.
Ready for growth and change
Tech startups need facilities that can grow along with their business. A steel building offers the flexibility to support that growth. From the start, engineers can design for scalability, ensuring the layout accommodates server racks and cooling systems with room to expand.
Steel fabrication allows for tight tolerances and high accuracy, which is especially important when dealing with sensitive tech equipment. This precision also supports efficient space planning and future reconfiguration as technology evolves.
As hardware changes, steel buildings can be updated and reconfigured easily to accommodate a growing tech business.
More peace of mind with steel construction
For tech startups, protecting data involves building a facility that supports physical security and operational reliability. A steel building offers several structural advantages that contribute to a safer, more secure environment:
Clear-span layouts improve visibility and control.
Steel buildings often feature wide column-free interiors. This open layout allows security teams to position cameras more effectively and monitor activity without obstructions. It also simplifies the installation of physical barriers and access controls across critical zones.
Fire-resistant
Data centers and tech facilities house high-value, heat-sensitive equipment, making fire protection a top priority. Steel naturally resists fire better than many other materials. With the addition of flame-retardant insulation and coatings, these structures offer enhanced fire protection, helping reduce the risk of damage and downtime.
Designed for modern security systems
A steel building makes it easy to integrate high-level security features during construction. Secure entry points and reinforced doors can be built directly into the structure’s design, supporting your facility’s protection from day one.
Less maintenance, fewer disruptions
Steel buildings are known for their long-term durability, unlike concrete structures that may crack or deteriorate over time. Minimal maintenance means fewer interruptions, allowing you to keep your facility fully operational with less effort and expense.
Energy efficiency and climate control
Maintaining stable conditions is essential for tech infrastructure. Steel buildings support advanced climate control and energy-saving features that benefit both performance and sustainability.
Reduced energy use
With proper insulation, a steel building reduces the energy needed to maintain ideal operating temperatures. This leads to lower utility costs and helps your business meet energy efficiency targets.
Consistent interior conditions
Steel structures can be sealed tightly and fitted with high-performance insulation. This reduces temperature swings and humidity fluctuations—key factors for preserving sensitive equipment.
Seamless HVAC integration
Steel buildings can easily accommodate the installation of complex HVAC systems. Ductwork and vents can be incorporated directly into the building’s layout, helping maintain a controlled environment for your tech operations.
Renewable energy support
The broad, unobstructed rooftops typical of a steel building are well-suited for solar panel installation. This allows tech startups to offset energy use with renewable sources, lowering environmental impact and supporting long-term cost savings.
Let Armstrong Steel help you bring your project to life. Whether you’re building a data center or a startup tech hub, we’ll design and fabricate the perfect steel building to fit your needs. Call us at 1-800-345-4610 or click ‘Price My Building’ to request a custom quote today.
0 notes
Text
How Proper Data Network Wiring Boosts Office Productivity
In today’s fast-paced digital environment, a reliable and efficient data network is no longer a luxury; it’s a necessity. Whether setting up a new office or upgrading your existing infrastructure, data network wiring is critical in ensuring smooth communication, data transfer, and daily operations.
This post explains how proper data network wiring enhances productivity in office settings and why every business should care.
What Is Data Network Wiring?
Data network wiring refers to the structured cabling systems used to connect computers, servers, printers, and other devices within a local area network (LAN). It includes Ethernet cables (Cat5e, Cat6, Cat6a), patch panels, switches, and wall jacks—all working together to ensure reliable data transmission.
A well-organized wiring infrastructure provides the physical foundation for high-speed internet, secure internal networks, VoIP systems, and more. Businesses in offices across North Andover are increasingly upgrading their infrastructure to meet modern networking demands.
Why Proper Wiring Matters More Than You Think
Consistent and Reliable Connectivity
One of the biggest productivity killers in offices is inconsistent internet connectivity. Poorly installed or outdated data network wiring can result in frequent dropouts, slow data transfer, and lag during video calls or cloud access.
With proper wiring, your office gains stable and fast connections, ensuring teams can work without frustrating interruptions.
Faster Data Transfer for Modern Workflows
From cloud-based apps to extensive file sharing, modern workplaces demand high-speed data communication. Up-to-date data network wiring—such as Cat6 or higher—supports gigabit speeds and low latency, translating into quicker downloads, smoother communication, and more efficient workflows.
Enhanced Collaboration
Seamless connectivity is vital whether your team is collaborating over Zoom, Slack, or Microsoft Teams. Properly installed data network wiring ensures every department can collaborate in real-time without delays or buffering, fostering better teamwork and faster decision-making.
Long-Term Cost Savings
Though wireless solutions seem effortless initially, they often suffer from interference, signal degradation, and security risks. Investing in a structured data network wiring system provides better performance with fewer maintenance issues, saving money in the long run.
Additionally, wired systems are scalable. As your office grows, adding more connections or upgrading equipment becomes easier and more affordable with a solid wired infrastructure in place. This has been particularly true for expanding businesses in North Andover, where tech-driven operations are rising.
Improved Security and Reduced Downtime
Increased Network Security
Wired networks are inherently more secure than wireless ones. Proper data network wiring limits unauthorized access and helps IT teams monitor and control the network with precision.
Reduced Downtime
Loose cables, tangled wires, or DIY setups often lead to technical failures. Structured cabling looks cleaner and minimizes the chance of human error or accidental disconnections, reducing downtime and keeping employees focused on their tasks.
Professional Installation Is Key
While handling wiring internally is tempting, proper data network wiring requires professional planning and execution. Certified network installers:
Assess your current and future data needs
Choose the correct type of cables.
Organize wiring neatly for easy troubleshooting.
Ensure compliance with industry standards
This expertise ensures that your wiring supports your office’s needs today—and scales with you tomorrow. If you're based in North Andover, consider consulting local professionals who understand the region's infrastructure and connectivity demands.
Frequently Asked Questions (FAQs)
Q1: What type of cable is best for office data network wiring?
A: Cat6 or Cat6a is recommended for most offices due to high speed and low interference.
Q2: How much does data network wiring cost for a small office?
A: Costs vary based on size and complexity but typically range from $500 to $5,000.
Q3: Can I install data network wiring myself?
A: It’s possible, but professional installation ensures safety, efficiency, and long-term reliability.
Q4: How do I know if my office needs new wiring?
A: Frequent network issues, slow speeds, and an outdated setup are key indicators you need an upgrade.
Q6: How long does a professional installation take?
A: Installation typically takes 1 to 3 days for small to medium offices, depending on the scope.
1 note
·
View note
Text
Fast, Secure, and Affordable: Petalhost – The Best FluxBB Hosting Provider India
In the digital age, online forums continue to be a vital platform for building communities, encouraging discussions, and sharing knowledge. When it comes to hosting a lightweight and efficient forum software like FluxBB, choosing the right hosting provider is essential. That’s where Petalhost stands out as the top FluxBB Hosting Provider India, offering robust, secure, and scalable hosting solutions tailored for your community’s needs.
Why Choose FluxBB?
FluxBB is a fast, secure, and user-friendly forum application that is perfect for communities of all sizes. It is designed with simplicity and speed in mind, making it an excellent choice for users who want a clean interface and straightforward features without unnecessary bloat. Whether you're running a niche community, a technical forum, or a support hub, FluxBB delivers the performance and reliability users expect.
But to truly harness the potential of FluxBB, you need hosting that matches its performance—and that’s exactly what Petalhost delivers.
Petalhost: Your Ideal FluxBB Hosting Partner
As a dedicated FluxBB Hosting Provider India, Petalhost brings together speed, security, and affordability to give your forum the solid foundation it needs. Here’s why Petalhost is the smart choice for hosting your FluxBB forum:
1. Optimized Server Environment
Our servers are configured specifically to support FluxBB’s lightweight architecture. With PHP, MySQL, and Apache/Nginx pre-tuned for optimal performance, your forum runs faster and more efficiently than ever before.
2. One-Click Installation
Launching a FluxBB forum with Petalhost is incredibly easy. With our one-click installer available in the control panel, you can get your forum up and running in minutes—no technical expertise required.
3. High Uptime and Reliability
We understand that uptime is critical for community forums. Our infrastructure is designed to offer 99.9% uptime, ensuring your FluxBB forum is always accessible to your users.
4. 24/7 Expert Support
Whether you're setting up your forum or need technical help down the line, our support team is available 24/7 to assist you. From migration to configuration, we’re here to ensure you have a smooth experience.
5. Enhanced Security Features
Security is vital for any online community. Petalhost includes advanced security measures such as firewalls, DDoS protection, regular malware scans, and automated backups to keep your data safe and your users protected.
6. Scalable Plans to Fit Every Budget
Whether you're starting small or expecting your community to grow quickly, Petalhost has a hosting plan to match. We offer scalable solutions that can easily adapt to your traffic and storage needs—all at competitive prices.
7. Free Website Migration
Already have your FluxBB forum hosted elsewhere? No problem. Petalhost offers free migration services, making the switch smooth and hassle-free without any downtime.
Experience the Petalhost Advantage
Choosing the right FluxBB Hosting Provider India can make all the difference in the success of your forum. With Petalhost, you get a reliable partner who understands the unique needs of forum hosting. Our team works hard behind the scenes so you can focus on building your online community without worrying about technical issues.
Whether you're a developer, community manager, or hobbyist, Petalhost ensures your FluxBB forum runs smoothly, loads quickly, and stays secure around the clock. Join thousands of satisfied customers who trust Petalhost for their hosting needs.
Ready to Launch Your Forum?
Start your FluxBB journey today with Petalhost—India’s trusted name in forum hosting. Explore our affordable plans, experience industry-leading support, and enjoy the peace of mind that comes with hosting your forum with the best.
Petalhost – The most reliable FluxBB Hosting Provider India.
0 notes
Text
Empowering Business Operations with Tailored Information Technology (IT) Services | All Services Global Pvt. Ltd.
Introduction: Driving Efficiency Through Smart IT Services
In today’s fast-paced digital era, reliable Information Technology (IT) services are the backbone of successful business operations. From data management and cyber security to infrastructure setup and technical support, companies need a partner that understands the complexities of modern IT ecosystems. That’s where All Services Global Pvt. Ltd. steps in — offering customized IT solutions that power productivity and enable seamless operations across industries.

All Services Global: Your Partner for Reliable IT Support Services
With over three decades of excellence in facility management, All Services Global has evolved to include a full-fledged Information Technology division—providing clients with end-to-end IT infrastructure support, network solutions, system integration, and consulting services across India.
Their team of certified IT professionals delivers cost-effective, scalable, and secure technology solutions that match the evolving digital needs of enterprises, startups, and institutions.

Key Information Technology Services Offered:
1. IT Infrastructure Management
All Services Global ensures a strong foundation by setting up, maintaining, and optimizing your complete IT infrastructure. This includes:
Server setup and monitoring
Network cabling & architecture
Data center operations
System integration & optimization
Whether you're scaling or streamlining, their infrastructure solutions are built for high availability and minimal downtime.
2. Managed IT Services
Their Managed IT Services provide 24/7 remote monitoring and proactive maintenance. This includes:
Patch management
Real-time system updates
Virus and malware protection
Helpdesk support
This ensures that clients can focus on core operations while All Services Global manages their IT environments efficiently.
3. Cybersecurity & Data Protection
Protect your business against growing cyber threats. All Services Global deploys multi-layered cybersecurity frameworks:
Firewall configuration
Endpoint security
Threat detection and response
Data encryption & backup solutions
They help businesses meet compliance standards and ensure secure data handling.
4. IT Helpdesk & Technical Support
Their IT Helpdesk provides instant remote and on-site support for hardware, software, and networking issues:
Troubleshooting PCs, routers, servers
Software installation and updates
User account management
SLA-driven response and resolution
5. IT Consulting & Project Management
Looking to implement a new IT system or migrate to the cloud? All Services Global provides expert IT consulting services to help businesses:
Choose the right technologies
Develop long-term IT strategies
Ensure project implementation on time & within budget
Their experienced consultants align IT initiatives with your business goals for maximum ROI.

🔧 Why Choose All Services Global for IT Services?
✔ 35+ Years of Industry Legacy ✔ Certified IT Professionals & Engineers ✔ Customized Solutions for Every Client ✔ Quick Turnaround Time & SLAs ✔ Pan-India Presence with 24/7 Support
🛠️ Technology That Works for You
From cloud migration to infrastructure optimization, All Services Global Pvt. Ltd. ensures that your organization is equipped with the technology it needs to thrive. Their approach is not just about fixing IT issues — it’s about building resilient IT ecosystems that drive innovation and growth.
For more information or to request a consultation, visit their website: All Services Global Pvt. Ltd..
To stay updated with the latest posts, follow us on social media:
📸 Instagram
📘 Facebook
🐦 Twitter (X)
🔗 Linkedin
📌 Pinterest 🧵 Thread
🥁 Tumblr
❗ Reddit
Contact: All Services Global +91-22 4063 7777 / +91- 22 4063 7788 https://allservicesglobal.com/
Digital Partner:
TVM INFOSOLUTIONS PVT LTD
Contact: TVM Info Solutions Pvt. Ltd.
+91-9004590039
Follow us on Social Media
🌐 Website
📸 Instagram
📘 Facebook
🔗 Linkedin
▶️ Youtube
0 notes
Text
5 Ways Asset Identification Supports Stronger Cybersecurity Practices

Imagine trying to secure a sprawling estate without knowing how many buildings are on it, where the windows and doors are, or even what valuable possessions are inside. It would be a futile exercise, a constant game of whack-a-mole against unseen threats. Yet, many organizations approach cybersecurity with a similar blind spot: a lack of comprehensive asset identification.
In today's complex digital landscape – brimming with on-premise servers, cloud instances, SaaS applications, IoT devices, mobile endpoints, and vast repositories of data – merely reacting to threats is a losing battle. The first and most critical step towards building a truly robust cybersecurity posture is knowing what you have.
Asset identification, or robust asset management, is the foundational practice of discovering, tracking, and understanding every digital and physical asset within your environment. It's the invisible bedrock upon which all other effective security practices are built.
Here are five powerful ways meticulous asset identification strengthens your cybersecurity defenses:
1. Eliminating Shadow IT and Uncovering Unknown Assets
The Problem: "Shadow IT" refers to hardware or software used by employees without explicit IT approval or knowledge. This could be a new SaaS tool signed up for by a marketing team, an unapproved laptop connected to the network, or a rogue database instance. These assets are unmanaged, unpatched, and often pose significant, undetected security risks.
How Asset ID Helps: Comprehensive asset identification employs continuous discovery tools that scan networks, cloud environments, and endpoints. They identify all connected devices, installed software, running services, and even cloud resources. This process brings "shadow IT" into the light.
Impact: By revealing these hidden assets, organizations can bring them under security policy, patch vulnerabilities, configure them securely, or decommission them, drastically reducing the attack surface.
2. Prioritizing Vulnerability Management with Precision
The Problem: Organizations face a deluge of vulnerabilities every day. With limited resources, it's impossible to patch everything at once. Without knowing which assets are critical, prioritization becomes a guessing game.
How Asset ID Helps: Asset identification maps vulnerabilities to specific assets, and crucially, can categorize assets by criticality (e.g., a customer database vs. a development server). This allows security teams to focus remediation efforts on vulnerabilities affecting high-value, business-critical assets first.
Impact: This shift from a reactive, chaotic patching process to a risk-based, strategic approach significantly improves overall security posture, ensures compliance, and maximizes the effectiveness of vulnerability management efforts.
3. Enhancing Incident Response and Rapid Recovery
The Problem: When a security incident occurs (e.g., a malware infection, a data breach), every second counts. Not knowing precisely which systems are affected, their interdependencies, or their owners can severely hamper containment and recovery efforts, amplifying damage.
How Asset ID Helps: A well-maintained asset inventory provides critical information at your fingertips. Security teams can instantly identify all affected devices, trace the infection's spread, isolate compromised systems, and understand the impact on related assets. It also provides essential data for forensic analysis.
Impact: Reduces Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR), minimizing data loss, system downtime, and financial repercussions during a breach.
4. Strengthening Compliance and Auditing Readiness
The Problem: Regulatory frameworks like GDPR, HIPAA, PCI DSS, and ISO 27001 demand strict control over sensitive data and IT systems. Demonstrating compliance without a clear, auditable record of your assets and their configurations is impossible.
How Asset ID Helps: A robust asset inventory provides the detailed documentation required for audits. It tracks where sensitive data resides, which systems process it, who has access, and whether configurations meet policy requirements.
Impact: Ensures adherence to regulatory mandates, avoids hefty fines, builds trust with customers and partners, and streamlines the auditing process.
5. Optimizing Security Controls and Resource Allocation
The Problem: Security tools and budgets are often deployed inefficiently, leading to over-protection in some areas and dangerous blind spots in others.
How Asset ID Helps: By understanding the full asset landscape, organizations can deploy tailored security controls. For instance, high-security financial systems might warrant advanced intrusion detection, while guest Wi-Fi networks need stricter access controls. It also helps justify security investments by linking them directly to the protection of specific, valuable assets.
Impact: Maximizes the effectiveness of security investments, eliminates redundant tools, identifies areas where security is weak, and ensures that critical assets receive the appropriate level of protection.
Implementing Effective Asset Identification
Achieving comprehensive asset identification isn't a one-time task; it's an ongoing process:
Automated Discovery Tools: Invest in solutions that can continuously scan and identify assets across your diverse environment (on-premise, cloud, IoT, mobile).
Centralized CMDB: Establish a Configuration Management Database as a single source of truth for all asset information.
Define Ownership: Assign clear ownership for each asset, including responsibility for its security and maintenance.
Integrate with Security Tools: Feed asset data into your SIEM, vulnerability scanners, patch management systems, and identity and access management (IAM) solutions.
Regular Audits & Reconciliation: Periodically verify the accuracy of your inventory against reality.
Knowing what you need to protect is the fundamental truth of cybersecurity. By embracing comprehensive asset identification, organizations move beyond reactive firefighting and build a truly resilient, well-managed, and defensible digital environment. It's the essential first step on the path to a stronger security posture.
0 notes
Text
Best Networking Solutions in Dubai – Powering Businesses with Vivency Global
Building Relationships That Build Success—Vivency Global Pioneers in Dubai Situated at the heart of the UAE business world, Dubai continues to lead as a global hub of innovation, trade, and technology. At the heart of every thriving business, large or small, is a robust digital network that keeps everything running smoothly. That's where Vivency Global comes in—offering the best networking solutions in Dubai to keep your business connected, secure, and ahead of the competition. Let's observe how Vivency Global is helping businesses in Dubai develop smarter and stronger networks using a human-centric solution. What Networking Solutions Do for Your Business? Think of your business network as the nervous system of your business—it keeps everything connected. From computers and printers to cloud storage, email servers, and online communication programs, your whole business operates on an efficient and secure network. Networking solutions include Setting up local (LAN) and wide area networks (WAN) Wireless/Wi-Fi solutions Cloud connectivity and remote access Network security and firewalls VPNs for secure remote work Ongoing monitoring and support Without a well-structured network, even the best businesses can run into delays, downtime, or worse—security threats. Why Vivency Global is Dubai’s Go-To for Networking With so many IT providers out there, what makes Vivency Global stand out? Local Expertise, Global Standards Vivency is attuned to the rapid business culture of Dubai and blends it with global-level tech expertise. Personalized Solutions Each business is different, and Vivency creates networks that are customized according to your company's requirements, objectives, and size. Security-First Approach They give top priority to cybersecurity, ensuring your data and communication remain secure, even in distant working environments. Friendly Support No techno-babble, no confusion—just clear communication, speedy service, and nice folks who genuinely care about your success. Vivency's Central Networking Services in Dubai Structured Cabling & Network Installation From brand new offices to expanding branches, Vivency builds strong network foundations with neat, systematic cabling and robust systems. Wi-Fi & Internet Solutions No more patchy coverage or sluggish signals. Vivency offers speedy and rock-solid wireless connections throughout your workspace. Cloud & Hybrid Networking Need remote access? Vivency simplifies easy cloud integration so your staff can work efficiently anywhere. Network Security & VPNs Protect your data with firewalls, encrypted VPN access, and secure user controls that are designed to block threats before they happen. Monitoring & Maintenance Their work doesn't end once installed. Vivency's active monitoring keeps your network up and running 24/7. Who Can Benefit? Vivency Global serves businesses of all sizes in Dubai: Corporate offices Retail stores Hospitality & tourism Medical clinics Education & training centers Logistics and warehouse operations Whether you’re a startup needing your first network or a multinational expanding in the UAE, Vivency has the tools and team to support your journey. Why It Matters More Than Ever In the era of hybrid work, video calls, cloud-based applications, and online transactions, an insecure or sluggish network can shut down your entire operation. Vivency Global's smart, scalable, and value-based solutions give you peace of mind—so you can have them worry about the tech while you focus on growing your business. Are You Ready to Bolster Your Network? If you want the finest networking solutions in Dubai, then look no further than Vivency Global. With local focus, world expertise, and people who care, they're here to link you to success—one safe, fast connection at a time. Get in touch with Vivency today—and let's create something amazing together! Let me know if you want a brochure, social media version, or presentation content based on this!
#Infrastructure Solutions#Networking Solutions#Security Solutions#Projectors#Video Conference Solutions
0 notes
Text
Start Coding Today: Learn React JS for Beginners

Start Coding Today: Learn React JS for Beginners”—will give you a solid foundation and guide you step by step toward becoming a confident React developer.
React JS, developed by Facebook, is an open-source JavaScript library used to build user interfaces, especially for single-page applications (SPAs). Unlike traditional JavaScript or jQuery, React follows a component-based architecture, making the code easier to manage, scale, and debug. With React, you can break complex UIs into small, reusable pieces called components.
Why Learn React JS?
Before diving into the how-to, let’s understand why learning React JS is a smart choice for beginners:
High Demand: React developers are in high demand in tech companies worldwide.
Easy to Learn: If you know basic HTML, CSS, and JavaScript, you can quickly get started with React.
Reusable Components: Build and reuse UI blocks easily across your project.
Strong Community Support: Tons of tutorials, open-source tools, and documentation are available.
Backed by Facebook: React is regularly updated and widely used in real-world applications (Facebook, Instagram, Netflix, Airbnb).
Prerequisites Before You Start
React is based on JavaScript, so a beginner should have:
Basic knowledge of HTML and CSS
Familiarity with JavaScript fundamentals such as variables, functions, arrays, and objects
Understanding of ES6+ features like let, const, arrow functions, destructuring, and modules
Don’t worry if you’re not perfect at JavaScript yet. You can still start learning React and improve your skills as you go.
Setting Up the React Development Environment
There are a few ways to set up your React project, but the easiest way for beginners is using Create React App, a boilerplate provided by the React team.
Step 1: Install Node.js and npm
Download and install Node.js from https://nodejs.org. npm (Node Package Manager) comes bundled with it.
Step 2: Install Create React App
Open your terminal or command prompt and run:
create-react-app my-first-react-app
This command creates a new folder with all the necessary files and dependencies.
Step 3: Start the Development Server
Navigate to your app folder:
my-first-react-app
Then start the app:
Your first React application will launch in your browser at http://localhost:3000.
Understanding the Basics of React
Now that you have your environment set up, let’s understand key React concepts:
1. Components
React apps are made up of components. Each component is a JavaScript function or class that returns HTML (JSX).
function Welcome() { return <h1>Hello, React Beginner!</h1>; }
2. JSX (JavaScript XML)
JSX lets you write HTML inside JavaScript. It’s not mandatory, but it makes code easier to write and understand.
const element = <h1>Hello, World!</h1>;
3. Props
Props (short for properties) allow you to pass data from one component to another.
function Welcome(props) { return <h1>Hello, {props.name}</h1>; }
4. State
State lets you track and manage data within a component.
import React, { useState } from 'react'; function Counter() { const [count, setCount] = useState(0); return ( <div> <p>You clicked {count} times.</p> <button onClick={() => setCount(count + 1)}>Click me</button> </div> ); }
Building Your First React App
Let’s create a simple React app — a counter.
Open the App.js file.
Replace the existing code with the following:
import React, { useState } from 'react'; function App() { const [count, setCount] = useState(0); return ( <div style={{ textAlign: 'center', marginTop: '50px' }}> <h1>Simple Counter App</h1> <p>You clicked {count} times</p> <button onClick={() => setCount(count + 1)}>Click Me</button> </div> ); } export default App;
Save the file, and see your app live on the browser.
Congratulations—you’ve just built your first interactive React app!
Where to Go Next?
After mastering the basics, explore the following:
React Router: For navigation between pages
useEffect Hook: For side effects like API calls
Forms and Input Handling
API Integration using fetch or axios
Styling (CSS Modules, Styled Components, Tailwind CSS)
Context API or Redux for state management
Deploying your app on platforms like Netlify or Vercel
Practice Projects for Beginners
Here are some simple projects to strengthen your skills:
Todo App
Weather App using an API
Digital Clock
Calculator
Random Quote Generator
These will help you apply the concepts you've learned and build your portfolio.
Final Thoughts
This “Start Coding Today: Learn React JS for Beginners” guide is your entry point into the world of modern web development. React is beginner-friendly yet powerful enough to build complex applications. With practice, patience, and curiosity, you'll move from writing your first “Hello, World!” to deploying full-featured web apps.
Remember, the best way to learn is by doing. Start small, build projects, read documentation, and keep experimenting. The world of React is vast and exciting—start coding today, and you’ll be amazed by what you can create!
0 notes
Text
e-Biz Technocrats in Gwalior is your trusted IT partner for server and storage solutions. We provide the infrastructure you need to successfully run your operations, no matter how secure or high-performance. We do it all, from installing servers and delivering a cloud-based storage solution to data backup and recovery solutions, e-Biz Technocrats provides end-to-end services to ensure that your business can be executed smoothly and securely! e-Biz Technocrats has an expert team, we are locally based, and we can respond quickly to your data & infrastructure requests so businesses can focus on other things!
0 notes
Text
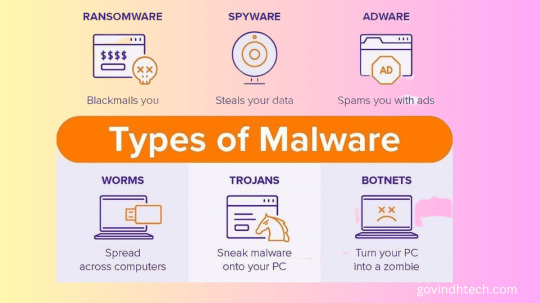
Effective Strategies for Handling Malware
Malware history is long due to its volume and variety. Instead, here are some notorious malware moments.
1966: Malware theory
Mathematician and Manhattan Project contributor John von Neumann developed the idea of a program that could replicate and propagate throughout a system when the first modern computers were produced. Posthumously published in 1966, Theory of Self-Reproducing Automata is the theoretical foundation for computer viruses.
1971: Crawler
Within five years of John von Neumann’s theoretical work, Bob Thomas produced Creeper, an experimental software that moved between ARPANET computers, a predecessor to the Internet. His colleague Ray Tomlinson, the email inventor, adapted the Creeper program to copy itself between computers. Thus began the first computer worm.
Although Creeper is the first known worm, it is not malware. As a proof of concept, Creeper only displayed the whimsical message: “I’M THE CREEPER : CATCH ME IF YOU CAN.” The following year, Tomlinson created Reaper, the first antivirus software designed to delete Creeper by moving across the ARPANET.
Elk Cloner virus, 1982
Rich Skrenta created the Elk Cloner program at 15 as a prank. Skranta was known to change games and other software shared in his high school’s computer club, so many members refused to take disks from the prankster.
Skranta created the first Apple computer virus to change disk software he couldn’t access. Elk Cloner, a boot sector virus, infected Apple DOS 3.3 and copied itself to the computer’s memory from an infected floppy drive. Elk Cloner would transfer itself to an uninfected disk used later in the machine and spread to majority of Skranta’s friends. Elk Cloner could accidentally erase floppy disks while malignant. The beautiful message read:
ELK CLONER:
THE PROGRAM WITH A PERSONALITY
IT WILL GET ON ALL YOUR DISKS
IT WILL INFILTRATE YOUR CHIPS
YES IT’S CLONER!
IT WILL STICK TO YOU LIKE GLUE
IT WILL MODIFY RAM TOO
SEND IN THE CLONER!
1986 Brain virus
On the ARPANET, the Creeper worm could propagate across computers, although most malware was spread via floppy disks like Elk Cloner before the Internet. Elk Cloner affected one little computer club, but the Brain infection spread globally.
Brain, the first IBM Personal Computer virus, was created by Pakistani medical software distributors and brothers Amjad and Basit Farooq Alvi to prevent copyright theft. To prevent software copying, the virus was designed. Brain would tell pirates to phone the brothers for the vaccination when installed. Underestimating how extensive their piracy problem was, the Alvis received their first call from the US and many more from throughout the world.
1988: Morris Worm
Another malware forerunner, the Morris worm, was constructed as a proof-of-concept. The worm was more effective than MIT student Robert Morris expected, unfortunately. Internet access was limited to 60,000 machines, largely in colleges and the military. The worm, designed to exploit a Unix backdoor and stay secret, quickly copied itself and infected 10% of networked machines.
Because the worm transferred itself to other computers and frequently on infected machines, it unwittingly ate up RAM and froze many PCs. Some estimates put the damages in the millions as the first widespread internet strike. Robert Morris was the first US cybercriminal convicted of cyber fraud.
1999: Melissa worm
Melissa proved how rapidly malware can spread via email a decade later, infecting an estimated one million email accounts and at least 100,000 office machines. The fastest-spreading worm of its time, it overloaded Microsoft Outlook and Exchange email servers, slowing more than 300 corporations and government agencies, including Microsoft, the Pentagon’s Computer Emergency Response Team, and 250 others.
2000: ILOVEYOU virus
When 24-year-old Philippines resident Onel de Guzman couldn’t afford dialup internet, he created ILOVEYOU, the first significant piece of malware, to collect passwords. The attack is early social engineering and phishing. De Guzman exploited psychology to exploit curiosity and trick individuals into downloading love letter-like email attachments. De Guzman remarked, “I figured out that many people want a boyfriend, they want each other, they want love.
Aside from stealing passwords, the worm erased information, cost millions in damages, and briefly shut down the UK Parliament’s computer system. De Guzman was detained but acquitted since he had not breached any local laws.
2004: Mydoomworm
Email helped the Mydoom malware self-replicate and infect computers worldwide, like ILOVEYOU. Upon infection, Mydoom would commandeer a victim’s machine to send new copies. Mydoom spam once made up 25% of all emails sent worldwide, a record that’s never been broken, and caused $35 billion in losses. It remains the most financially devastating malware, adjusted for inflation.
Mydoom uses compromised machines to establish a botnet and launch DDoS assaults in addition to hijacking email programs to infect as many systems as possible. The cybercriminals behind Mydoom have never been captured or identified, despite its impact.
2007, Zeus virus
In 2007, Zeus attacked home computers via phishing and drive-by-downloads, demonstrating the dangers of a trojan-style malware that can unleash multiple unwanted programs. In 2011, its source code and instruction manual leaked, benefiting cybersecurity experts and hackers.
2013, CryptoLocker ransomware
CryptoLocker, one of the earliest ransomware attacks, spread quickly and used sophisticated asymmetric encryption. CryptoLocker from Zeus-infected botnets systematically encrypts PC data. If the infected PC is a library or office client, shared resources are targeted first.
The authors of CryptoLocker demanded two bitcoins, worth $715 USD, to decrypt these materials. Fortunately, in 2014, the Department of Justice and international agencies took control of the botnet and decrypted hostage data for free. Unfortunately, basic phishing tactics spread CyrptoLocker, a persistent danger.
Emotet trojan 2014
The Emotet trojan, termed the “king of malware” by Arne Schoenbohm, head of the German Office for Information Security, is a polymorphic spyware that is difficult to eradicate. Polymorphic malware creates a harmful variation by subtly modifying its code each time it reproduces. Polymorphic trojans are harder to detect and block, making them more harmful.
The Zeus trojan and Emotet are modular programs that spread additional malware through phishing campaigns.
Mirai botnet (2016)
Malware evolves with computers, from desktops to laptops, mobile devices, and networked devices. Smart IoT gadgets introduce new vulnerabilities. College student Paras Jha created the Mirai botnet, which infected many IoT-enabled CCTV cameras with inadequate protection.
The Mirai botnet, meant to assault gaming servers for DoS attacks, proved more powerful than Jha expected. It targeted a major DNS provider and shut out large parts of the eastern US from the internet for nearly a day.
2017: Cyberspionage
Malware had been used in cyber warfare for years, but 2017 was a banner year for state-sponsored assaults and virtual espionage, starting with Petya. Phishing disseminated Petya ransomware, which was deadly but not infectious until it was transformed into the NotPetya wiper worm, which destroyed user data even if ransom was paid. The WannaCry ransomware infection hit several high-profile European targets that year, including Britain’s National Health Service.
NotPetya may have been modified by Russian intelligence to strike Ukraine, and WannaCry may be linked to North Korean adversaries. What links these malware attacks? The National Security Agency discovered Eternalblue, a Microsoft Windows exploit, which enabled both. Microsoft found and fixed the weakness, but they chastised the NSA for not reporting it before hackers exploited it.
Ransomware-as-a-Service 2019
Ransomware malware has grown and declined in recent years. Though ransomware attacks are declining, hackers are targeting more high-profile targets and wreaking more harm. Recently, Ransomware-as-a-Service has become a worrying trend. RaaS may be purchased on dark web marketplaces and allows skilled hackers to launch ransomware attacks for a price. Previous virus attacks needed extensive technical skill, but RaaS mercenary groups empower anyone with evil will and money.
Emergency in 2021
In 2019, hackers broke into security staffing agency Allied Universal and threatened to leak their data online in the first high-profile double-extortion ransomware attack. Due to this extra layer, Allied Universal would still suffer a data breach even if they could decode their information. This incident was notable, but the 2021 Colonial Pipeline attack was more severe. The Colonial Pipeline supplied 45% of eastern US gasoline and jet fuel. The multi-day attack affected the east coast’s public and private sectors and caused President Biden to proclaim a state of emergency.
National emergency, 2022
Though ransomware attacks may be reducing, highly targeted and efficient operations remain a scary menace. Ransomware attacks in 2022 crippled the ministry of finance and civilian import/export firms in Costa Rica. Following an attack, the healthcare system went offline, affecting potentially every citizen. Costa Rica declared the first national state of emergency after a cyberattack.
Read more on Govindhtech.com
2 notes
·
View notes
Text
Expert Electrical Cable Testing in Vadodara – Accuracy You Can Trust
When it comes to electrical infrastructure, reliability and safety begin with a solid foundation quality cables and trustworthy testing services. In Vadodara, a city at the forefront of industrial and residential development, the demand for expert electrical cable testing is higher than ever. Whether it’s a manufacturing unit, a commercial hub, or a residential township, ensuring that cables are performing efficiently is crucial to maintaining safety, reducing downtimes, and meeting regulatory standards.
In this comprehensive blog, we’ll dive deep into the importance of electrical cable testing, the various testing methods available, why expert testing services are necessary, and how Vadodara stands as a hub for trusted electrical cable testing solutions.
Choosing Expert Electrical Cable Testing Services in Vadodara
Certified Technicians
Ensure the team is qualified, trained, and experienced in handling electrical systems and testing equipment as per IS, IEC, or IEEE standards.
Modern Equipment
Reputable service providers invest in advanced testing tools VLF sets, PD detectors, thermal imagers, and digital TDRs for precise diagnostics.
On-Site & Off-Site Testing
Depending on the situation, expert providers offer both mobile testing vans for on-site checks and lab-based facilities for more comprehensive analysis.
Detailed Reporting
A proper test report includes readings, interpretation, recommendations, and photographic evidence ideal for audits, compliance, and planning maintenance.

Safety Compliance
Adherence to safety protocols (PPE, lockout-tagout, earth discharge practices)Cable Testing Vadodara protects both personnel and assets during testing.
Who Needs Electrical Cable Testing?
Electrical cable testing isn’t limited to power companies or industrial facilities. A wide range of sectors in Vadodara benefit from this crucial service:
Industrial Plants: Power-intensive industries such as petrochemicals, pharmaceuticals, manufacturing units, and textiles rely on stable power supply for 24/7 operations.
Commercial Buildings: Offices, malls, and IT parks require safe and uninterrupted power for HVAC systems, elevators, servers, and lighting.
Residential Societies: With increasing dependence on electrical appliances, cable testing ensures home safety.
Hospitals and Laboratories: Where uninterrupted power is critical to life-saving equipment.
Educational Institutions: Large campuses with labs and computer centers need robust power networks.
Infrastructure Projects: Airports, metro stations, Oil Filtration and Testing Vadodara and smart city developments rely on tested cables for safe power distribution.
Conclusion: Trust Only the Experts for Cable Testing in Vadodara
In a city like Vadodara where power supports everything from home comforts to industrial automation the integrity of electrical cables cannot be overlooked. Expert electrical cable testing is more than just a technical procedure; it’s a safeguard for safety, performance, and peace of mind.
Whether you’re commissioning a new installation, troubleshooting an old network, or planning preventive maintenance, partner with certified professionals who deliver accurate results, quick turnaround, and honest assessments.
#transformerindustriesinvadodara#electricaltestingvadodara#oil filtration and testing vadodara#mekengineersvadodara
0 notes
Text
What role does cloud technology play in Frandzzo’s service offerings?

In today’s digital-first world, businesses are embracing cloud technology to stay competitive, secure, and agile. At Frandzzo Technologies Private Limited, cloud computing isn’t just a feature—it’s a core pillar of our service offerings. By integrating powerful cloud solutions with AI-driven insights, we help businesses unlock faster innovation, stronger security, and seamless growth.
Let’s explore how cloud technology plays a vital role in what Frandzzo delivers to modern enterprises.
1. Foundation of Frandzzo’s SaaS Ecosystem
Frandzzo builds and delivers Software as a Service (SaaS) solutions powered by cloud infrastructure. This model allows businesses to access powerful tools on demand without worrying about hardware costs or complex installations.
Cloud technology enables:
On-demand scalability – scale your operations up or down easily
Remote accessibility – work securely from anywhere
Reduced IT overhead – no need for physical servers or extensive in-house maintenance
By using the cloud as a foundation, Frandzzo ensures its clients enjoy flexible, reliable, and cost-efficient services.
2. Enabling Real-Time AI & Machine Learning Insights
Frandzzo focuses on AI-powered decision-making, and cloud computing is what makes this possible in real-time. The cloud processes large volumes of business data instantly, allowing our platforms to provide predictive analytics, smart automation, and deep insights across various business functions.
With cloud-backed AI tools, Frandzzo empowers companies to:
Forecast trends with precision
Automate repetitive tasks
Personalize customer experiences
Make faster and smarter business decisions
This seamless integration between AI and cloud gives our clients a strategic edge in their industries.
3. Enhancing Security and Compliance
Data security is a top priority for every business. At Frandzzo Technologies, we combine enterprise-grade cloud security with strict regulatory compliance measures to keep our clients’ data safe.
Our cloud solutions include:
End-to-end encryption
Access control and monitoring
Backup and disaster recovery
Regulatory compliance support (such as GDPR and HIPAA)
By hosting applications on secure cloud platforms, we help businesses reduce risk and gain peace of mind.
4. Speeding Up Digital Transformation
Frandzzo is committed to driving digital transformation with agility and speed. Cloud technology removes the traditional bottlenecks and allows companies to adopt new solutions quickly. Our cloud-based services are plug-and-play, meaning they can be integrated into existing systems with minimal disruption.
This is crucial for:
Startups looking to scale fast
Enterprises modernizing legacy systems
Organizations aiming for rapid market entry
Whether you're launching a new digital product or transforming internal operations, the cloud enables faster execution and lower costs.
5. Supporting Global Collaboration and Performance
Today’s businesses often operate across borders. Frandzzo’s cloud solutions support global teams by providing seamless access to shared tools and data. No matter where your team is, the cloud ensures consistent performance, real-time collaboration, and synchronized operations.
Our cloud-based services are also optimized for:
High availability
Fast loading times
Cross-device compatibility
This ensures your business can deliver top-notch experiences to customers and employees worldwide.
0 notes
Text
System Administration Online Course: Master Modern IT with Gritty Tech
In today’s digitally driven world, efficient system management is critical for any business. A comprehensive System administration online course equips learners with the skills required to handle system networks, servers, security protocols, and more. Whether you’re aiming for a career upgrade or starting fresh in the tech field, and flexible learning experience For More…

Why Choose Gritty Tech for Your System Administration Online Course?
Top-Quality Education, Affordable Price
Gritty Tech stands out in the education sector for delivering high-quality learning at affordable rates. Our System administration online course is designed to provide exceptional training in core IT administration areas without overburdening your budget.
Global Tutor Network Spanning 110+ Countries
We bring together expert instructors from around the world. With a diverse team of seasoned professionals, Gritty Tech ensures your System administration online course is led by industry veterans with practical experience in managing modern infrastructure.
Flexible Payment and Satisfaction Policies
Learners can benefit from our monthly and session-wise payment models. We also offer an easy refund policy and tutor replacement options, reinforcing our commitment to student satisfaction. Our System administration online course is built around your needs.
What You Will Learn in the System Administration Online Course
Gritty Tech’s curriculum covers every key aspect needed to become a proficient system administrator. With real-world scenarios and hands-on labs, the course includes:
Linux and Windows server installation and configuration
Network architecture, monitoring, and troubleshooting
Security controls, firewalls, and user permissions
Data backup, system recovery, and storage solutions
Cloud platforms introduction and server virtualization
Task automation using scripting (Bash, PowerShell)
Managing Active Directory and DNS configurations
Each module in the System administration online course builds foundational expertise, reinforced by real-time assignments.
Who Should Take This Course
The System administration online course is ideal for:
Beginners entering the IT field
IT professionals aiming to upskill
Computer science students
Freelancers and consultants supporting IT operations
System engineers seeking certification
Career Paths After Completing the System Administration Online Course
With a solid foundation from our System administration online course, students can pursue rewarding roles such as:
System Administrator
IT Support Technician
Network Engineer
Cloud Operations Associate
DevOps Engineer
Server Security Analyst
Companies across industries depend on skilled system administrators to maintain robust and secure IT environments.
What Makes the Gritty Tech System Administration Online Course Stand Out
Experienced Tutors
Gritty Tech tutors are not just educators—they are working professionals with hands-on experience in systems management. Their real-world insights enhance the quality of your System administration online course journey.
Hands-On Projects and Labs
You will work with actual server environments and practice live configurations. These exercises provide a practical layer to your theoretical learning.
Interactive and Self-Paced
The System administration online course can be completed at your convenience. Whether you study full-time or part-time, the flexibility is built-in to support your schedule.
Certification Included
After successful completion of your System administration online course, you’ll receive a digital certificate from Gritty Tech, which you can share with potential employers or on professional platforms.
Real Student Support
From one-on-one mentoring to peer support, our System administration online course ensures you never feel isolated. Our global community provides an excellent platform for collaboration and discussion.
Related Topics Covered in the Course
The course doesn’t stop at systems. To help broaden your technical base, we integrate related training on:
Linux system administration
Windows server roles
Cloud administration fundamentals
Networking essentials
Cybersecurity basics
IT support workflows
Infrastructure monitoring tools
These modules complement the core lessons of the System administration online course, helping you become a versatile IT professional.
10 Most Asked Questions About the System Administration Online Course
What is a system administration online course?
A System administration online course teaches the principles and practices of managing IT systems and networks remotely via an interactive online format.
Who should take the system administration online course?
Anyone seeking a career in IT, especially those interested in maintaining servers, networks, and databases, should consider a System administration online course.
What will I learn in the system administration online course?
You’ll gain expertise in system configuration, network setup, user management, and IT troubleshooting through our System administration online course.
Is prior IT experience required for the system administration online course?
No prior experience is needed. The System administration online course is suitable for both beginners and intermediate learners.
How long is the system administration online course?
Most students complete the System administration online course within 6 to 10 weeks depending on their pace.
Does Gritty Tech provide certification after the course?
Yes, a verified certificate is awarded upon completing the System administration online course.
What tools are used in the system administration online course?
You’ll work with Linux, Windows Server, VMware, PowerShell, and various network monitoring tools during the System administration online course.
Can I change my tutor during the course?
Yes. We offer flexible tutor replacement options during your System administration online course.
What if I’m not satisfied with the course?
Gritty Tech provides an easy refund policy for learners who are unsatisfied with their System administration online course experience.
Can I pay in installments for the system administration online course?
Absolutely. We support monthly and session-wise payment plans to make the System administration online course more accessible.
Conclusion
Gritty Tech’s System administration online course is a comprehensive, flexible, and industry-relevant program that prepares you for success in IT systems management. With world-class tutors, real-time labs, affordable pricing, and a globally recognized certificate, you get everything you need to transform your career.
Whether you’re starting out or advancing in your IT journey, this System administration online course is your launchpad. Take the first step today and join a learning community that spans over 110 countries. Gritty Tech makes tech education not only possible—but powerful.
0 notes
Text
Boost Your Online Store with Petalhost – The Trusted Ecommerce Website Hosting Provider in India
In today’s digital-first economy, running a successful online store requires more than just a great product and appealing design. The foundation of every reliable ecommerce platform is a powerful hosting service. If you’re looking for a trusted and affordable ecommerce website hosting provider in India, Petalhost is your ideal partner. With cutting-edge infrastructure, tailored hosting solutions, and a commitment to top-tier performance, Petalhost empowers Indian entrepreneurs to grow and scale their ecommerce ventures with confidence.
Why Petalhost for Ecommerce Hosting?
Petalhost is known for offering robust and secure hosting services that specifically cater to the unique needs of ecommerce businesses. Whether you are launching a new store or migrating an existing one, Petalhost provides a seamless, high-performance environment with features that drive speed, reliability, and customer satisfaction.
Lightning-Fast Speed and Uptime
In ecommerce, every second counts. A delay in page loading can lead to lost sales. That’s why Petalhost ensures ultra-fast SSD storage, optimized server configurations, and a 99.9% uptime guarantee. With global data centers and CDN integration, your ecommerce site loads quickly across all regions, ensuring a smooth shopping experience for your customers.
Secure and Scalable Solutions
Security is non-negotiable for online stores. Petalhost includes advanced security features such as firewalls, DDoS protection, and free SSL certificates, giving both store owners and customers peace of mind. As your business grows, Petalhost’s scalable hosting plans allow you to upgrade resources without any downtime, keeping your store online and efficient at all times.
Ecommerce-Ready Tools and Compatibility
As a leading ecommerce website hosting provider in India, Petalhost supports all popular ecommerce platforms including WooCommerce, Magento, PrestaShop, OpenCart, and more. With one-click installations and full compatibility, you can set up your store quickly without needing advanced technical knowledge. Our hosting also supports custom development for unique ecommerce applications and third-party integrations.
24/7 Dedicated Support
Petalhost believes in offering complete support to ensure your store runs smoothly around the clock. Our technical support team is available 24/7 to assist with any hosting issues, migrations, platform compatibility, or performance optimization. You focus on growing your business—let us handle the technical side.
Affordable Pricing for Indian Businesses
Understanding the Indian market, Petalhost offers cost-effective hosting plans without compromising quality. From startups to large enterprises, our packages are designed to suit every budget. Enjoy transparent pricing, no hidden charges, and value-added services like free website migration, email accounts, and domain management tools.
SEO and Performance Optimization
Petalhost’s ecommerce hosting is built with SEO in mind. Fast load times, mobile responsiveness, and secure HTTPS protocols help your store rank better in search engines. Combined with expert support and easy-to-use dashboards, you get full control over how your ecommerce site performs online.
Real Success Stories
Countless Indian businesses trust Petalhost to host their online stores. From fashion brands to local artisans and niche marketplaces, Petalhost has helped merchants reach a wider audience and increase sales through reliable hosting infrastructure.
Conclusion: The Smart Choice for Ecommerce Hosting
Choosing the right hosting provider is one of the most important decisions for your online business. As a trusted ecommerce website hosting provider in India, Petalhost delivers exceptional value, performance, and support. Whether you're just getting started or expanding a booming ecommerce store, Petalhost has the resources and expertise to power your success.
Start your ecommerce journey with Petalhost today and experience world-class hosting that fuels growth and builds trust.
0 notes