#Two-factorauthentication
Explore tagged Tumblr posts
Text
Binance Users Targeted in SMS Scam, Exchange Warns Against Spoofing Attacks
Last week, users of Binance fell victim to scammers who sent fake SMS messages claiming they had won prizes in the Binance Mystery Box lottery, with rewards valued at around 100 euros in cryptocurrency. The victims were informed that the offer expired the same day and were urgently advised to claim their winnings by clicking on a link in the SMS. Upon clicking the malicious link, victims were prompted to log in to their Binance accounts and provide the necessary passwords. Binance acknowledged that this scheme represents a typical attempt at a spoofing attack through SMS, where attackers manipulate the message sender to appear as if it is coming from a trusted source. The goal is to deceive victims into following instructions, ultimately leading to the theft of confidential data. Binance stated its inability to combat such fraud since the technologies of the GSM communication system, under which SMS messages operate, allow the sender to arbitrarily fill in the "sender name" field. Mobile operators do not verify whether the sender sending the SMS has the legitimate right to use a specific name. "To close this security loophole in SMS, the whole world would have to modify GSM technology, which seems unrealistic to us," concluded Binance. Earlier, the National Agency of Project Management in Uzbekistan (NAPM) announced that the world's largest cryptocurrency exchange, Binance, would be required to pay a fine for operating in the country without a license. Read the full article
#Binancescam#cryptocurrencyexchange#Cryptocurrencysecurity#Cybersecuritymeasures#Digitalassetprotection#GSMtechnology#Onlinefraud#Scamprevention#SMSphishing#Spoofingattack#Two-factorauthentication(2FA)
0 notes
Link
#Authycàiđặt#Authysửdụng#Bảomậttàikhoản#ĐăngkýAuthy#Đăngnhậpantoàn#Mãxácthực#Quảnlýmãxácthực#Two-factorauthentication#Ứngdụngxácthực#Xácthựchaiyếutố
0 notes
Photo

Telecommuting is a reality for an ever-developing number of individuals in the workforce. Exploiting the most current advances in the realm of innovation is fundamental in helping your workers remain beneficial at home. Luckily, entrepreneurs can look over a wide scope of tech alternatives and programming projects to facilitate the progress of telecommuting. Keen on finding out additional? Here ar... https://bit.ly/3vBDC45
#Blog#cloud#CloudComputing#covid19#createworkfromhome#howtechnologycanhelpyouworkfromhome#securityawareness#Telecommuting#Two-FactorAuthentication#VoIPCommunications#vpn#workfromhome#workfromhomescheme
0 notes
Text
2-Factor Authentication (2FA): what it is and how it works
Two-factor authentication (2FA), also known as two-step verification or two-factor authentication, is a security tool whereby the user is required to provide two different authentication factors to verify their identity. It can be used to grant (or deny) access to any type of resource: web sites and services, financial or banking accounts, security boxes, apartments and offices doors & gates, and so on. In this article we'll do our best to explain the characteristics of this access mode, the reasons that make it significantly safer than traditional authentication tools and how it can be used to protect our online and offline resources.
Why the password is not enough
As you most likely already know, the vast majority of websites in 2019 still rely on the good old "username & password" authentication method, which is among the worst possible techniques to protect our data. Here's a list of reasons explaining why such method shouldn't be used anymore in 2019: Weak or stolen user credentials are hackers' weapon of choice, used in 95 percent of all web site attacks. Password theft is constantly evolving as hackers employ methods like keylogging, phishing, pharming and so on. The vast number of password we need to use (and memorize) during our everyday (personal + business) life pushes users and employees to perform a lot of unsecure behaviours, such as: using easy to remember (and therefore weak) passwords; store their credentials in their browsers/devices; write them in insecure places; and so on. Even if most of these threats can be mitigated by using a strong password, the real weakness of such approach lies in the fact that there is only a single layer of protection between the intruder and our data: a single mistake on our part is all it takes to allow unauthorized access from virtually anyone.
Authentication Factors
An authentication factor is a way to acknowledge the identity of a user by a security device in order to grant (or deny) access to the requested resource(s). There are generally three recognized types of authentication factors nowadays: Type 1 - Something You Know: includes passwords, PINs, combinations, passphrases, secret words, gestures and so on. Anything that you can remember and then type, say, do, perform, or otherwise recall when needed falls into this category. Type 2 - Something You Have: includes any kind of physical object: keys, smart phones, smart cards, USB drives, token devices, authentication apps (such as Google Authenticator) and so on. Type 3 – Something You Are: includes any part of the human body that can be used to verify the owner's identity, such as: fingerprints, retina scan, iris scan, palm scan, facial recognition, voice recognition and so on. As we can easily understand, each category them can be theoretically "cracked" by a criminal: password & pins can be guessed, inferred or obtained through spying techniques or malicious software; physical object can be stolen or cloned; if you're into theft-related movies or books, you know that even the human body parts are not 100% secure, since they can be "stolen", cloned or forged as well. The "username & password" approach we described early on clearly falls into the type 1 single-factor authentication methods, which is among the less secure ones. However, any single-factor authentication approach is potentially weak, as the intruder only has to have a single attack skill and wage a single successful attack to impersonate the victim; conversely, combining (at least) two factors from the above categories will greatly increase the level of security, as the whole authentication process will become much more difficult to overcome: the intruder must have multiple attack skills and/or wage multiple successful attacks simultaneously: doing that is much more difficult, resulting in a more resilient solution from a security perspective.
Two-Factor vs Multi-Factor
The difference between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) should be already clear by now: 2FA is nothing more, nothing less than an implementation of multi-factor authentication which requires two different factors from those listed above. Three-Factor Authentication (3FA) is also a type of MFA which requires all the three factors identified above.
Multi-Password Authentication
2FA and MFA should not be confused with Multi-Password Authentication (MPA) mechanisms, which require the user to insert multiple sets of credentials (different usernames/passwords) in order to access a specific resource. A typical example of Multi-Password Authentication is a password-protected client software installed on a user profile within a desktop PC, which can only be accessed by performing the Windows login and then the client login. Another good example is a Remote Desktop through VPN, where the user must first login to the VPN server (using the VPN credentials) and then initiate the RDP session through authentication to the networking environment (Active Directory, VNC, SSH and so on). Despite being more secure than single-password approaches, all multi-password authentication processes still falls into the Single-Factor Authentication (SFA) world, thus being potentially insecure from attacks coming from experienced hacker (which can exploit unexperienced end-users).
Authentication vs Authorization
To better understand the need to switch from a single factor authentication method to a two (or more) factor process, it may be useful to analyze the difference between the modern authentication and authorization concepts. Generally speaking, the term authentication refers to any process of verification that someone, be it a human being or an automated system, is who (or what) it claims to be. This is also true within the context of the World Wide Web (WWW), where that same word is mostly used to denote any technique used by a website or service to collect a set of login info from a user agent, typically a web browser, and authenticate them using a membership and/or identity service. Authentication should never be confused with Authorization, as it is a different process and is in charge of a very different task: to give a quick definition, we could say that the purpose of authorization is to confirm that the requesting user is allowed to have access to the action they want to perform. In other words, while authentication is about who he is, authorization is about what he’s allowed to do. To better understand the distance between these two apparently similar concepts, we could think of two real-world scenarios: A free, yet registered account trying to gain access to a paid or premium only service or feature: this is a common example of authenticated, yet not-authorized access; we know who he is, yet he’s not allowed to go there. An anonymous user trying to gain access to a publicly available page or file: this is an example of not-authenticated, yet authorized access; we don’t know who he is, yet he can access public resources just like everyone else. For additional info regarding the differences between authentication and authorization, other examples including third-party login (Facebook, Google and so on) and a list of the available auth methods nowadays, we strongly suggest to read this other post. As we can easily understand, the main problem with Single-Factor Authentication lies in the fact that it's not strong enough to confirm that the requesting user is who he claims to be: therefore, it could easily end up authorizing a whole different human being, thus granting him (or her) access to private data or privacy-sensible resources. This has become rather common in standard password-based websites nowadays, where passwords are frequently stolen and - more than often - even willingly given by the owner to others (co-workers, family, etc.) to act on their behalf: have you ever ordered a meal or performed any e-shop transaction using a friend or company account? If you did, you know what we're talking about. Now, although such behaviour could be somewhat "acceptable" if the website does not contain privacy sensitive info, it definitely cannot be done for services hosting personal data: from our banking account to our government website's personal page, from our office gate to our home door, we could definitely benefit from a Multi-Factor Authentication method to better secure our stuff. Such approach is also required by the Global Data Protection Regulation (GDPR) European Law (Art. 32 - Security of Processing), which instructs the controller and processor to take the appropriate steps to restrict access to personal data to the authorized personnel only. This post is part of a series of articles and essays regarding the new European General Data Protection Regulation in EU countries, with specific focus on achieving compliance with UE and local regulations, civil rights and criminal matters. To read the other articles, click here! Read the full article
#2FA#DataProtection#DataSecurity#GDPR#MFA#MPA#Multi-FactorAuthentication#PasswordStrength#Two-FactorAuthentication
0 notes
Text
Facebook’s two-factor ad practices give middle finger to infosec
Facebook’s two-factor ad practices give middle finger to infosec
We’ve all encountered security questions asking where we went to school, our favorite color or food, our first concert, and the ubiquitous “mother’s maiden name.” Imagine a world where on one screen you carefully chose Stanford, red, spaghetti and so on, and on the next you were shown ads for Italian restaurants, red shoes, and jobs for Stanford grads.
Seems like an insane violation,…
View On WordPress
#2fa#ads#alexstamos#badpassword#Business#column#datasecurity#duolabs#facebook#gear#gizmodo#gmail#google#opinion#personal computing#personalcomputing#Security#services#shadowprofile#two-factorauthentication
0 notes
Text
Sign-in to your Microsoft Account more securely without using a password
That's right! Now you can sign-in to your Microsoft Account more securely and it does not require you to enter your password. How is this more secure you may ask. First of all this will only work if you have enabled MFA (Multi-factor Authentication) on your Microsoft Account. If you have not already done this, please do this on all your Microsoft as well as any non-Microsoft account as this is a must to keep your account secure. Password-less sign-in is also secure because you no longer have to risk typing your password into a web browser. Your machine maybe infected with keyloggers that will record everything you type. Especially if you are signing in to your account on a public computer. Let's take a look at what you need to get this working. You need 3 things: A Microsoft account (Obviously) Have enabled MFA (Multi-factor authentication) on your Microsoft account. Have installed and configured Microsoft Authenticator App on your smart phone to work with your Microsoft Account. Unfortunately I will not be showing you how to enable MFA on your Microsoft Account but you could visit Microsoft Support Page here to learn how to enable this on your account. I will show you how this works in action. Once you are at the Microsoft sign-in page, please enter your email address as usual.

Microsoft Sign-in page Now click Next and stop! Now check what it says at the end of the little pop-up box under the password section: "Use the Microsoft Authenticator app instead".

Use the Microsoft Authenticator app instead of password Now click on "Use the Microsoft Authenticator app instead" and then you will see that it waits for you to approve the sign-in on your mobile phone.

Microsoft Sign-in page waiting for approval via Authenticator app You should see the approval request on your mobile phone and simply click "APPROVE" to sign-in.

Approval request on Authenticator app Once you click Approve, your phone might confirm your identity once more by asking you to use the biometric sign-in option on the phone itself. Once completed you will be signed in to Microsoft account. This encourages users to use stronger and more unique passwords on their accounts as now they no longer have to enter it all the time. This feature is meant to come soon for Azure AD sign-in as well. Strong passwords and Multi-factor authentication all the time!! Stay secure. Read the full article
#Authentication#LiveAccount#MFA#Microsoft#MicrosoftAuthenticator#Multi-factor#Outlook#Outlook.com#Password-lessSign-in#Personal#Security#Strongpasswords#Two-factorauthentication
0 notes
Photo

Security + 1.2 Man in the Browser http://ehelpdesk.tk/wp-content/uploads/2020/02/logo-header.png [ad_1] Is there really a man in my brow... #awscertification #awscertifiedcloudpractitioner #awscertifieddeveloper #awscertifiedsolutionsarchitect #awscertifiedsysopsadministrator #browserpivoting #ciscoccna #comptiaa #comptianetwork #comptiasecurity #cybersecurity #ethicalhacking #it #kubernetes #linux #maninthebrowser #maninthebrowserattack #maninthebrowserattackprevention #maninthebrowserattacktutorial #maninthemiddleattack #man-in-the-middle #microsoftaz-900 #microsoftazure #networksecurity #professormessernetwork #professormessersecurity #software #two-factorauthentication #windowsserver
0 notes
Photo
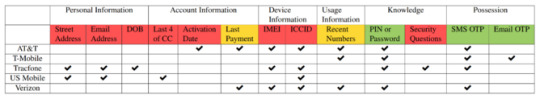
📢Your carrier will let basically any competent criminal hijack your phone number 👉http://bit.ly/3ankOuC 📛 #News #Tech #Computer #Game #2fa #atampt #carriers #hijack #phonenumbers #prepaid #security #sim #simswap #sms #t-mobile #tracfone #two-factorauthentication #usmobile #verizonwireless #carriers #news #security
0 notes
Link
Amazon finally has two-step authentication (using SMS and/or Google Authenticator). So in other words, go to your account and set it up now!
Seriously. Two-step authentication should be considered necessary for anything that has anything more sensitive than your first name, and it’s been long past time for Amazon to support it. You should enable two-step authentication for everything you can. It may be slightly more annoying, but it is a ton more secure than just your password.
1 note
·
View note
Text
It's time to secure your Amazon account with two-factor authentication
It’s time to secure your Amazon account with two-factor authentication
Relying solely on passwords to secure important accounts may be outdated, but until they're gone for good your best alternative is locking things down with two-factor authentication: Amazon. Considering you probably already have a credit card or ot…
Read More
View On WordPress
1 note
·
View note
Text
Epic uses a free 'Fortnite' dance to encourage two-factor authentication
Epic uses a free ‘Fortnite’ dance to encourage two-factor authentication
As Fortnite’s popularity has grown, player’s accounts have become targets for attackerswho want to steal access and run up fake charges. One way to combat this is by enabling two-factor authentication that requires a generated code or emailed link for login in addition to the user’s password, but as we’ve seen on other services, not everyone turns it on. Epic Games has a solution though, by
View On WordPress
0 notes
Text
Secure Your Reddit Account Using Two-Factor Authentication
Secure Your Reddit Account Using Two-Factor Authentication
Reddit has been slowly rolling out two-factor authentication for beta testers, moderators and third-party app developers for a while now before making it available to everyone over the past few days. Read more…

View On WordPress
0 notes
Link
We've all encountered security questions asking where we went to school, our favorite color or food, our first concert, and the ubiquitous "mother's maiden name." Imagine a world where on one screen you carefully chose Stanford, red, spaghetti and so on, and on the next you were shown ads for Italian restaurants, red shoes, and jobs for Stanford grads.
Seems like an insane violation, right? I mean, it stands to reason that we expect that the information we type to secure our online accounts and apps is private and safely guarded.
Click on above title for more
0 notes
Photo

Authentication fundamentals: Native client applications- Part 2 | Azure Active Directory http://ehelpdesk.tk/wp-content/uploads/2020/02/logo-header.png [ad_1] In this part two video, Azure Ac... #activedirectory #ad #authentication #authenticationfundamentals #awscertification #awscertifiedcloudpractitioner #awscertifieddeveloper #awscertifiedsolutionsarchitect #awscertifiedsysopsadministrator #azure #azureactivedirectory #azuread #ciscoccna #comptiaa #comptianetwork #comptiasecurity #conditionalaccess #cybersecurity #ethicalhacking #federation #it #kubernetes #linux #microsoft #microsoftaz-900 #microsoftazure #modernauthentication #multifactor #multi-factorauthentication #nativeclient #networksecurity #outlook #securitytoken #software #stuartkwan #token #windowsserver
0 notes