#US Consumer Data Privacy and Security Act
Explore tagged Tumblr posts
Text
Trump’s Tiktok two-step is a lesson for future presidents

I'm about to leave for a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me on Feb 14 in BOSTON for FREE at BOSKONE , and on Feb 15 for a virtual event with YANIS VAROUFAKIS. More tour dates here.

Remember the Tiktok ban? I know, it was ten million years ago (in Musk years, anyway), so it may have slipped your mind, but let me remind you: Congress passed a law saying Tiktok was banned. Trump said he wouldn't enforce the law. The end.
No, really. I mean, sure, there's a bunch of bullshit about whether Trump will pick up the ban again after Tiktok's grace period ends, depending on whether they sell themselves to his creepy wax museum pal Larry Ellison. Maybe he will. Maybe Tiktok'll buy so many trumpcoins that he forgets about. Whatevs.
The important thing here is: Congress passed a (stupid) law and Trump said, "I've decided not to enforce that law" and then that was it:
https://prospect.org/justice/2025-01-31-trump-administration-test-supreme-court-tiktok/
Sure, there's some big rule of law/checks and balances/separation of powers problems here, and there are plenty of laws I'm mad about Trump not enforcing (like the law that says corporations can't bribe foreign governments, say). But this one? Sure, it's fine. The problem with Tiktok is that it invades our privacy in creepy ways, not that it is owned by a Chinese company. I don't want Zuck or Musk or (especially) Trump invading my privacy.
Congress hasn't passed a consumer privacy law since 1988, when they banned video store clerks from telling newspapers about your VHS viewing habits. That's why Tiktok is a problem. Pass that law, and if any president decides not to enforce it, I'll be mad as hell and I'll be right there in the streets next to you, in head-to-toe CV dazzle, with all my distraction rectangles in Faraday pouches, shlepping a placard bearing the Social Security Numbers of every Cabinet member in giant writing.
But the point is, the president defied Congress, which is a thing that Very Serious Grownups told us radicals Joe Biden mustn't do under any circumstances, lest the resulting constitutional crisis tear the country apart, or, at the very least, alienate so many voters that Donald Trump would become the next president.
We let Very Serious Grownups call the shots, and Donald Trump is president. Maybe we should stop listening to Very Serious Grownups?
Look, presidents ignore Congress's laws all the time. The Comstock Act (which effectively bans transporting pornography and contraception) is almost entirely ignored, and has been for generations (though Trump's creepy Heritage Foundation puppetmasters have promised to bring it back). The Robinson-Patman Act hasn't been enforced since the Reagan years, which is a damned shame, because Robinson-Patman would put Walmart, Amazon, Dollartree and Dollar General out of business (Biden started to enforce Robinson-Patman again during his last year in office):
https://pluralistic.net/2024/08/14/the-price-is-wright/#enforcement-priorities
I'm not trying to say that enforcing (or ignoring) the Comstock Act is the same as ignoring (or enforcing) the Robinson-Patman Act. The Comstock Act is bad, and the Robinson-Patman Act is good. I am capable of making that moral judgment, and I would like to have a president who does the same.
The fear about Trump ignoring the laws and procedures is justified, but not because of the damage he's doing to laws and procedures – it's because of the damage he's doing to the people of this country and the world.
Take the records that Trump has destroyed – vital data about public health and other subjects (thankfully, most of this was saved from destruction by the Internet Archive). The most important fact about that act of destruction is the harm that will result from it, not the failure to follow procedure.
There are plenty of times in which I am OK with people ignoring the law and destroying records. In 1943, Dutch guerrillas bombed the civil registry building in Amsterdam, to keep the records of where Jews and other disfavored minorities lived out of the hands of occupying Nazis. The firefighters on the scene kept their hoses running until any paper that hadn't been burned was reduced to slurry:
https://en.wikipedia.org/wiki/1943_Amsterdam_civil_registry_office_bombing
I'm fine with destroying records that wicked, vicious authoritarians would use to harm my neighbors.
Remember when Biden tried to cancel student debt? He could have started off by destroying the records of who owed what, so when the courts overturned his administrative action, it would have been hard or impossible to collect on the debts that were still held on federal books, or whose records the feds had (no, I'm not suggesting that Nazi death camp deportations are equivalent to unjust student debt collections, but if you agree that sometimes it's OK to illegally destroy records, then all we're left with is haggling over the specifics).
Sure, this would have been a constitutional crisis, but, as Ryan Grim says, "It is apparently unconstitutional for the president to instruct the Department of Education to restructure and forgive some student loan debt but it is ok for DOGE chair Elon Musk to just get rid of the whole department. Anywho."
https://twitter.com/ryangrim/status/1888973174819164663?t=Cd8fl4FWjY5zsOlQWZGv4g
Canceling debt isn't forgiving debt. Student borrowers have been preyed upon by colleges and lenders. People who borrowed $79.000 and paid back $190,000 can somehow still owe $236,000 do not need to be forgiven, because (unlike Trump) they haven't sinned. Rather, their debts need to be canceled (like Trump):
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
Trump's shown us what a president should do when the courts get in their way: fight back. Worst case scenario is the court prevails, and a bunch of Fedsoc judges (up to and including the Supreme Court) set binding precedent that reduces the power of the president, which would be, you know, great. Best case scenario: Americans are freed from these crippling, fraudulent debts and, you know, vote for Democrats and against Trump, instead of staying home because they don't feel like the Democrats have their back.
Defying unjust court decisions isn't Trumpian – it's Rooseveltian. Roosevelt (following in Lincoln's footsteps) spent years discrediting and weakening the Supreme Court's power, using his bully pulpit to rob them of authority and build the political will to pack the court, which he was on the brink of doing when the Supreme Court surrendered:
https://pluralistic.net/2020/09/20/judicial-equilibria/#pack-the-court
Democrats developed an online organizing playbook, and it worked, so Republicans took it, improved on it, and won elections. Republicans have developed a devastatingly effective constitutional hardball playbook. Democrats should steal that playbook and run with it:
https://pluralistic.net/2024/10/18/states-rights/#cold-civil-war
I rang doorbells, made phone calls, and shelled out money for Democrats in the last cycle because I wanted them to do stuff that helps Americans, not because I wanted them to follow procedures. The fact that Trump is building offshore concentration camps and has deported our neighbors to them (to name just one of many cheap dystopian fanfics that Trump is LARPing) should be the kind of five-alarm fire that sent South Korean lawmakers scaling the barricades last month.
This is the kind of crisis where I'd expect Democrats on the Hill, at a minimum, to be refusing to give Trump and the GOP anything. Call quorum on every vote. Debate every amendment. Raise every objection. Vote against everyting. Do not confirm a single appointee. And any elected Dem that refuses to play along? Kick 'em out of the caucus. Oh, we can't afford to do that because we can't afford to lose a single lawmaker? How did that work out with Kirsten Synema and Joe Manchin? Shoulda kicked them out after the first vote, shoulda raised money for any real Dem willing to primary them. Should have shunned them in the hallways and refused to invite them to the Christmas parties. We should do that to Fetterman. Party unity got us nothing under Biden. Party unity got us Trump. Doing the same thing over and over again and expecting a different outcome isn't actually the formal definition of insanity, but it is nevertheless very, very stupid.
For the past four years, Very Serious Grownups in the Democratic machine kept telling us that we couldn't expect the president to do anything, or Congress to do anything, or the Senate to do anything, because the Republicans would stop them. Or the courts would stop them. Why fight when you know you're gonna lose? Because sometimes, you'll win. And even if you lose, you'll go down fighting.
Better yet, if you lose in just the right way, you'll force Trump's judges to take away powers from the President and the administrative agencies – take away the powers Trump is now wielding like a sledgehammer.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/11/you-and-what-army/#student-debt
#pluralistic#constitutional crisis#tiktok ban#bidenism#trumpism#institutionalism#getting shit done#scotus#constitutional hardball
398 notes
·
View notes
Text
RECENT UPDATES ON THE BAD INTERNET CALIFORNIA BILLS:
Sadly, both AB1949 and SB976 passed and are now on their way to the governors desk.
We need him to veto them so they dont become Law.
If you havent Heard of the danger of those bills for the Internet , this post explain it thoroughly :
- Post doing a deep explanation on those bills here
I CANNOT emphasize enough how these would have a global effect on the Internet given that most websites and apps originates from California and not all of them could afford either following those bills or moving states.
Now, as the bills are on their way to the governor, we need Californian citizens to voice their oppositions to those bills to the Governor Gavin Newsome HERE
(Non California peeps, we are urging you to share this as well!!! )
Please keep in mind that calling with phone is much,much more efficient.
You can also send faxes with Faxzero
Here are scripts you can use as arguments : (text/alt version below the read more )
Than you for reading. Even if youre not from California, please spread the word anyway ! Make posts,tweets,etc
REBLOGS ENCOURAGED
TEXT VERSION :
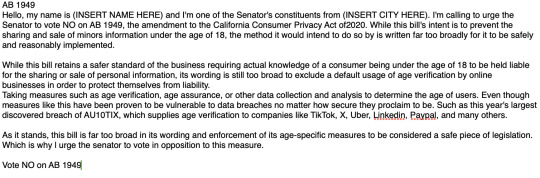
AB 1949
Hello, my name is (INSERT NAME HERE) and I'm one of the Senator's constituents from (INSERT CITY HERE). I'm calling to urge the Senator to vote NO on AB 1949, the amendment to the California Consumer Privacy Act of 2020. While this bill's intent is to prevent the sharing and sale of minor's information under the age of 18, the method it would intend to do so by is written far too broadly for it to be safely and reasonably implemented.
While this bill retains a safer standard of the business requiring actual knowledge of a consumer being under the age of 18 to be held liable for the sharing or sale of personal information, its wording is still too broad to exclude a default usage of age verification by online businesses in order to protect themselves from liability. Taking measures such as age verification, age assurance, or other data collection and analysis to determine the age of users. Even though measures like this have been proven to be vulnerable to data breaches no matter how secure they proclaim to be. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others.
As it stands, this bill is far too broad in its wording and enforcement of its age-specific measures to be considered a safe piece of legislation. Which is why I urge the Senator to vote in opposition to this measure.
Vote NO on AB 1949.
---------------------------
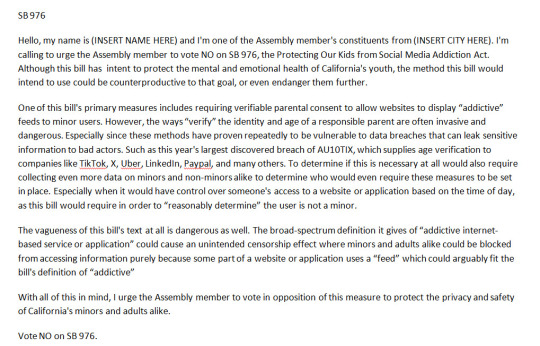
SB 976
Hello, my name is (INSERT NAME HERE) and I'm one of the Assembly member's constituents from (INSERT CITY HERE). I'm calling to urge the Assembly member to vote NO on SB 976, the Protecting Our Kids from Social Media Addiction Act. Although this bill has intent to protect the mental and emotional health of California's youth, the method this bill would intend to use could be counterproductive to that goal, or even endanger them further.
One of this bill's primary measures includes requiring verifiable parental consent to allow websites to display “addictive” feeds to minor users. However, the ways “verify” the identity and age of a responsible parent are often invasive and dangerous. Especially since these methods have proven repeatedly to be vulnerable to data breaches that can leak sensitive information to bad actors. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others. To determine if this is necessary at all would also require collecting even more data on minors and non-minors alike to determine who would even require these measures to be set in place. Especially when it would have control over someone's access to a website or application based on the time of day, as this bill would require in order to “reasonably determine” the user is not a minor.
The vagueness of this bill's text at all is dangerous as well. The broad-spectrum definition it gives of “addictive internet-based service or application” could cause an unintended censorship effect where minors and adults alike could be blocked from accessing information purely because some part of a website or application uses a “feed” which could arguably fit the bill's definition of “addictive”
With all of this in mind, I urge the Assembly member to vote in opposition of this measure to protect the privacy and safety of California's minors and adults alike.
Vote NO on SB 976.
352 notes
·
View notes
Text
The Consumer Financial Protection Bureau (CFPB) has canceled plans to introduce new rules designed to limit the ability of US data brokers to sell sensitive information about Americans, including financial data, credit history, and Social Security numbers.
The CFPB proposed the new rule in early December under former director Rohit Chopra, who said the changes were necessary to combat commercial surveillance practices that ���threaten our personal safety and undermine America’s national security.”
The agency quietly withdrew the proposal on Tuesday morning, publishing a notice in the Federal Register declaring the rule no longer “necessary or appropriate.”
The CFPB received more than 600 comments from the public this year concerning the proposal, titled Protecting Americans from Harmful Data Broker Practices. The rule was crafted to ensure that data brokers obtain Americans’ consent before selling or sharing sensitive personal information, including financial data such as income. US credit agencies are already required to abide by such regulations under the Fair Credit Reporting Act, one of the nation’s oldest privacy laws.
In its notice, the CFPB’s acting director, Russell Vought, wrote that he was withdrawing the proposal “in light of updates to Bureau policies,” and that it did not align with the agency’s “current interpretation of the FCRA,” which he added the CFPB is “in the process of revising.”
The CFPB did not immediately respond to a request for comment.
Data brokers operate within a multibillion-dollar industry built on the collection and sale of detailed personal information—often without individuals’ knowledge or consent. These companies create extensive profiles on nearly every American, including highly sensitive data such as precise location history, political affiliations, and religious beliefs. This information is frequently resold for purposes ranging from marketing to law enforcement surveillance.
Many people are unaware that data brokers even exist, let alone that their personal information is being traded. In January, the Texas Attorney General’s Office, led by attorney general Ken Paxton, accused Arity—a data broker owned by Allstate—of unlawfully collecting, using, and selling driving data from over 45 million Americans to insurance companies without their consent.
The harms from data brokers can be severe–even violent. The Safety Net Project, part of the National Network to End Domestic Violence, warns that people-search websites, which compile information from data brokers, can serve as tools for abusers to track down information about their victims.
Last year, Gravy Analytics—which processes billions of location signals daily—suffered a data breach that may have exposed the movements of millions of individuals, including politicians and military personnel.
“Russell Vought is undoing years of painstaking, bipartisan work in order to prop up data brokers’ predatory, and profitable, surveillance of Americans,” says Sean Vitka, executive director of Demand Progress, a nonprofit that supported the rule. Added Vitka: “By withdrawing the CFPB’s data broker rulemaking, the Trump administration is ensuring that Americans will continue to be bombarded by scam texts, calls and emails, and that military members and their families can be targeted by spies and blackmailers.”
Vought, who also serves as director of the White House Office of Management and Budget, received a letter on Monday from the Financial Technology Association (FTA) calling for the rule to be withdrawn, claiming the rules exceed the agency’s statutory mandate and would be “harmful to financial institutions’ efforts to detect and prevent fraud.” The FTA is a US-based trade organization that represents the interests of banks, lenders, payment platforms, and their executives.
Privacy advocates have long pressed regulators to use the Fair Credit Reporting Act to crack down on the data broker industry. Common Defense, a veteran-led nonprofit, urged the CFPB to take action in November, blaming data brokers for recklessly exposing sensitive information about US service members that placed them at “substantial risk” of being blackmailed, scammed, or targeted by hostile foreign actors.
A 2023 study cited by the group—funded by the US Military Academy at West Point—concluded that the current data broker ecosystem is a threat to US national security, permitting the sale of sensitive personal data that can be used not only to identify service members and “other politically sensitive targets,” but also to offer details about medical conditions, financial problems, and political and religious beliefs. “Foreign and malign actors with access to these datasets could uncover information about high-level targets, such as military service members, that could be used for coercion, reputational damage, and blackmail,” the authors report.
Common Defense political director Naveed Shah, an Iraq War veteran, condemned the move to spike the proposed changes, accusing Vought of putting the profits of data brokers before the safety of millions of service members. "For the sake of military families and our national security, the administration must reverse course and ensure that these critical privacy protections are enacted," Shah says.
Investigations by WIRED have shown that data brokers have collected and made cheaply available information that can be used to reliably track the locations of American military and intelligence personnel overseas, including in and around sensitive installations where US nuclear weapons are reportedly stored.
WIRED reported in February that US data brokers were using Google's ad-tech tools to sell access to information about devices linked to military service members and national security decisionmakers, as well as federal contractors that manufacture and export classified defense-related technologies. Experts say it proves trivial for foreign adversaries to de-anonymize the data.
"Data brokers inflict severe harm on individuals by degrading privacy, threatening national security, enabling scams and fraud, endangering public officials and survivors of domestic violence, and putting immigrant populations at risk,” says Caroline Kraczon, law fellow at the Electronic Privacy Information Center focused on consumer protection.
“The CFPB had a critical opportunity to address these harms by clarifying that data brokers must follow the Fair Credit Reporting Act,” adds Kraczon. “This withdrawal is deeply disappointing and another attack in the administration’s war against consumers on behalf of corporate interests."
Last month, more than 1,400 CFPB employees had their positions at the agency terminated, leaving the agency with a staff of around 300 people. Elon Musk, whose so-called Department of Government Efficiency (DOGE) has spearheaded the White House's efforts to radically restructure the federal government by slashing the size of its workforce, last November called on President Donald Trump to “delete” the CFPB, whose job includes shielding Americans from predatory lending practices.
61 notes
·
View notes
Text
Libraries have traditionally operated on a basic premise: Once they purchase a book, they can lend it out to patrons as much (or as little) as they like. Library copies often come from publishers, but they can also come from donations, used book sales, or other libraries. However the library obtains the book, once the library legally owns it, it is theirs to lend as they see fit. Not so for digital books. To make licensed e-books available to patrons, libraries have to pay publishers multiple times over. First, they must subscribe (for a fee) to aggregator platforms such as Overdrive. Aggregators, like streaming services such as HBO’s Max, have total control over adding or removing content from their catalogue. Content can be removed at any time, for any reason, without input from your local library. The decision happens not at the community level but at the corporate one, thousands of miles from the patrons affected. Then libraries must purchase each individual copy of each individual title that they want to offer as an e-book. These e-book copies are not only priced at a steep markup—up to 300% over consumer retail—but are also time- and loan-limited, meaning the files self-destruct after a certain number of loans. The library then needs to repurchase the same book, at a new price, in order to keep it in stock. This upending of the traditional order puts massive financial strain on libraries and the taxpayers that fund them. It also opens up a world of privacy concerns; while libraries are restricted in the reader data they can collect and share, private companies are under no such obligation. Some libraries have turned to another solution: controlled digital lending, or CDL, a process by which a library scans the physical books it already has in its collection, makes secure digital copies, and lends those out on a one-to-one “owned to loaned” ratio. The Internet Archive was an early pioneer of this technique. When the digital copy is loaned, the physical copy is sequestered from borrowing; when the physical copy is checked out, the digital copy becomes unavailable. The benefits to libraries are obvious; delicate books can be circulated without fear of damage, volumes can be moved off-site for facilities work without interrupting patron access, and older and endangered works become searchable and can get a second chance at life. Library patrons, who fund their local library’s purchases with their tax dollars, also benefit from the ability to freely access the books. Publishers are, unfortunately, not a fan of this model, and in 2020 four of them sued the Internet Archive over its CDL program. The suit ultimately focused on the Internet Archive’s lending of 127 books that were already commercially available through licensed aggregators. The publisher plaintiffs accused the Internet Archive of mass copyright infringement, while the Internet Archive argued that its digitization and lending program was a fair use. The trial court sided with the publishers, and on September 4, the Court of Appeals for the Second Circuit reaffirmed that decision with some alterations to the underlying reasoning. This decision harms libraries. It locks them into an e-book ecosystem designed to extract as much money as possible while harvesting (and reselling) reader data en masse. It leaves local communities’ reading habits at the mercy of curatorial decisions made by four dominant publishing companies thousands of miles away. It steers Americans away from one of the few remaining bastions of privacy protection and funnels them into a surveillance ecosystem that, like Big Tech, becomes more dangerous with each passing data breach. And by increasing the price for access to knowledge, it puts up even more barriers between underserved communities and the American dream.
11 September 2024
154 notes
·
View notes
Text
SB 976 Update 6/17/2024
Hello everyone. As of now, California State Senator Skinner's bill SB 976 (Protecting our Kids from Social Media Addiction Act) has been added to the California Assembly's Committee on Privacy and Consumer Protection Hearing Schedule.
This bill hearing is scheduled to be heard on Tuesday 7/2/2024 at 1:30 PM.
Information on how to submit Position Letters in opposition to this bill can be found on the Committee's homepage here.
As a reminder, Position Letters should only be in terms of opposition, not opposition unless X part of the bill has been altered. Keep your reasoning solid and concise.
The Committee is specifically focused around "a wide range of technology-related issues, and includes matters affecting consumer protection in both the digital and analog worlds. Specifically, the Committee has jurisdiction over matters related to privacy, the protection of personal information (including digital information), the security of data, and information technology, as well as false advertising, charitable solicitations, weights and measures, and consumer protection generally. The Committee is also responsible for oversight of the Department of Technology within the State's Government Operations Agency." So keep this in mind when writing your letters for the best chance of convincing this committee against allowing SB 976 to be allowed through.
And here is a link to the most recent version of the bill's text.
The deadline to submit Position Letters is noon one week before the hearing is to be held. So in this case, the deadline is 6/25/2024 at 12:00 PST.
Thank you for taking your time to help us oppose this privacy harming bill, and making efforts to keep our internet safe and free of restriction and surveillance.
EDIT:
There is a more recent version of the bill which was amended on June 18th. No major changes or provisions added that I can see, mostly points made about mental health of teens as reasons for who they want the bill implemented. But you can find the latest version here just in case.
#california#kosa#sb 976#social media#age verification#bad internet bills#online safety#online privacy
77 notes
·
View notes
Text
[AMERICAN POLITICS]
i know everyone is worried about KOSA being a censorship bill, and that's fair. but do you know what really, REALLY concerns me about this bill? the fact they want to install age verification systems at the device/operating system level

(transcript with highlights below cut)
this will almost definitely track your data - note how it doesn't say how much, just that it's going to have to collect some, and that's worrying. to me. best case scenario we need to give our devices our government ID. worst case scenario it's tracking app usage and browser history and who knows what else. they don't say! how convenient.
but, based on Sec. 6(d)(5) "consider indicia or inferences of age of users, in addition to any self-declared information about the age of individuals." and Sec. 10(a)(1)(D) "using indicia or inferences of age of users for assessing use of the covered platform by minors", nevermind Sec. 9(b)(4)'s own admission that some data will be collected, that's.... that's data tracking.
and i know websites already do this, but i feel like a government mandated software for age verification that will track this data is a step too far.....
read the text of the bill here, if you want. genuinely the amount of legaleze is - as far as i can tell - only going to PROBABLY cause censorship, not GUARANTEE it.
but you know what KOSA does guarantee? stated plainly and clearly in their intents of what this bill will do? data tracking.
so if you're contacting your senators about opposing this bill, please consider not only voicing your concerns about censorship, but also about the privacy violations. thank you.
contact your senators here
highlighted text in image bolded
SEC. 9. Age verification study and report.
(a) Study.—The Director of the National Institute of Standards and Technology, in coordination with the Federal Communications Commission, Federal Trade Commission, and the Secretary of Commerce, shall conduct a study evaluating the most technologically feasible methods and options for developing systems to verify age at the device or operating system level.
(b) Contents.—Such study shall consider —
(1) the benefits of creating a device or operating system level age verification system;
(2) what information may need to be collected to create this type of age verification system;
(3) the accuracy of such systems and their impact or steps to improve accessibility, including for individuals with disabilities;
(4) how such a system or systems could verify age while mitigating risks to user privacy and data security and safeguarding minors' personal data, emphasizing minimizing the amount of data collected and processed by covered platforms and age verification providers for such a system; and
(5) the technical feasibility, including the need for potential hardware and software changes, including for devices currently in commerce and owned by consumers.
(c) Report.—Not later than 1 year after the date of enactment of this Act, the agencies described in subsection (a) shall submit a report containing the results of the study conducted under such subsection to the Committee on Commerce, Science, and Transportation of the Senate and the Committee on Energy and Commerce of the House of Representatives.
285 notes
·
View notes
Text
California's handling of sensitive health information is under scrutiny following a report that data entered by residents on the state's health insurance marketplace was shared with LinkedIn.
Covered California, which runs the state's marketplace, coveredca.com, shared sensitive personal data with LinkedIn, a subsidiary of Microsoft, through embedded tracking tools on the website, nonprofit news organization The Markup reported on Monday.
Covered California confirmed the data transmission in a news release later that day, saying "some sensitive data was inadvertently collected by the tags, including first names, the last four digits of Social Security numbers, and other sensitive health information like pregnancy status."
It added that all advertising-related tags on the website had been turned off as a "precautionary measure," and that it would review the extent of the data shared.
Representative Kevin Kiley, the Democrat from California has called for an investigation. "This is incredibly disturbing," he wrote on X, formerly Twitter.
Newsweek contacted Representative Kiley via social media and email, as well as the press offices of Health Secretary Robert F. Kennedy Jr. and California Governor Gavin Newsom via email outside of regular working hours on Wednesday.
Why It Matters
Concerns over personal data have grown in recent months after it emerged the government's Department of Government Efficiencyworked to gain access to the Social Security Administration's data systems, which hold sensitive personal data about approximately 70 million Americans.
California's sharing of sensitive data with LinkedIn will likely raise similar concerns about threats to Americans' privacy.
What To Know
Trackers on coveredca.com, which was created under the Affordable Care Act, captured users' answers to questions about blindness, pregnancy, high prescription use, gender identity and experiences with domestic abuse, The Markup reported.
The data was then transmitted to LinkedIn using Insight Tag, which uses code to track how visitors interact with websites.
Covered California said in a statement that it "leverages LinkedIn's advertising platform tools to understand consumer behavior;" however, LinkedIn notes on its website that Insight Tag "should not be installed on web pages that collect or contain Sensitive Data."
The LinkedIn campaign trackers began in February 2024 and were removed "due to a marketing agency transition" in early April, Covered California told CalMatters.
Covered California had more than 60 trackers on its site, compared to the average on other government sites of three, CalMatters reported.
What People Are Saying
Covered California said in a news release on Monday: "Covered California is reviewing its entire website and information security and privacy protocols to ensure that no analytics tools are impermissibly collecting or sharing sensitive consumer information. The LinkedIn Insight tags are no longer active and, as a precautionary measure, all active advertising-related tags across the CoveredCA.com website have been turned off.
"Covered California is committed to safeguarding the confidential information and privacy of its consumers. The organization will share additional findings from this investigation as they become available."
California Representative Kevin Kiley, wrote on X: "California's Obamacare website tracked users' personal health information—such as pregnancy and prescription drug use—and sent it to LinkedIn for a 'marketing campaign.' We are asking Secretary Kennedy to investigate for HIPAA violations."
What Happens Next
The Department of Health and Human Services has yet to respond publicly to Kiley's call for an investigation.
10 notes
·
View notes
Text
The Consumer Financial Protection Bureau (CFPB) has canceled plans to introduce new rules designed to limit the ability of US data brokers to sell sensitive information about Americans, including financial data, credit history, and Social Security numbers.
The CFPB proposed the new rule in early December under former director Rohit Chopra, who said the changes were necessary to combat commercial surveillance practices that “threaten our personal safety and undermine America’s national security.”
The agency quietly withdrew the proposal on Tuesday morning, publishing a notice in the Federal Register declaring the rule no longer “necessary or appropriate.”
The CFPB received more than 600 comments from the public this year concerning the proposal, titled Protecting Americans from Harmful Data Broker Practices. The rule was crafted to ensure that data brokers obtain Americans’ consent before selling or sharing sensitive personal information, including financial data such as income. US credit agencies are already required to abide by such regulations under the Fair Credit Reporting Act, one of the nation’s oldest privacy laws.
In its notice, the CFPB’s acting director, Russell Vought, wrote that he was withdrawing the proposal “in light of updates to Bureau policies,” and that it did not align with the agency’s “current interpretation of the FCRA,” which he added the CFPB is “in the process of revising.”
4 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Blog Post #10 4/24
How have post-9/11 surveillance policies have reshaped the American understanding of privacy and liberty?
Christian Parenti argues that by defining invasive state monitoring as an everyday part of daily life, the post-9/11 surveillance regime drastically changed American privacy and eventually destroyed democratic values. He believes that rather than establishing an entirely new system, the cultural reaction to 9/11 expedited and validated already-existing surveillance infrastructures. He argues that the USA Patriot Act "liberalized the legal environment in which federal cops will be gathering and processing the routine informational detritus of the digital age," which is the clearest example of this. Parenti cautions that such surveillance undermines the public's expectations of civil liberties and promotes compliance over liberty, particularly when it is disguised in security or patriotic rhetoric. He claims that this results in a changed populace that is less defensive of personal freedoms and more reliant on authority.
What can be learned about the fuzziness of the lines separating criminal activity and protest coordination in the digital age from the arrests of Michael Wallschlaeger and Elliott Madison?
Police are increasingly seeing digital communication as a criminal tool rather than an outlet for protected speech, as seen by the arrests of Elliott Madison and Michael Wallschlaeger during the G20 summit demonstrations. Even though the tweets were publicly available and resembled real-time reporting, their coordination efforts using Twitter to communicate protester movements and police activity were construed as criminal conduct under ambiguous provisions like "criminal use of a communication facility" and "hindering apprehension." When somebody takes into account their following FBI operation and the application of infrequently used statutes such as the federal anti-riot statute which attorney Martin Stolar described as an effort to "criminalize dissent" and prosecute "thought crime" this blurring of boundaries becomes particularly concerning. This instance highlights the state's increasing concern with decentralized, digitally empowered activism and shows how old protest strategies are being reframed as dangers when magnified by technology.
How does the Data Detox Kit empower individuals to take control of their digital privacy and well-being?
By offering consumers simple, achievable steps to reduce their digital footprint, improve online privacy, and develop healthy digital habits, the Data Detox Kit encourages users. The kit enables people to think critically about their online behavior and make wise decisions by simplifying difficult subjects like data monitoring, algorithmic bias, and information security into doable everyday tasks. The Data Detox Kit is a useful manual for recovering control in an increasingly monitored digital environment, whether that means changing app permissions, creating stronger passwords, or reevaluating how personal information is shared.
How does the article "How Your Twitter Account Could Land You in Jail" highlight the tension between digital activism and state surveillance?
By demonstrating how platforms like Twitter, which were once praised for facilitating democratic upheavals overseas, are now being used to criminalize dissent domestically, the study highlights the growing conflict between digital activism and governmental monitoring. The arrest of Elliott Madison for tweeting updates during the G20 protests serves as an example of how law enforcement views real-time, public communication that is utilized to assist with protest planning as illegal. The allegations are an attempt to link protest coordination to criminal intent, Madison's attorney pointed out, cautioning that "essentially it's prosecution for a thought crime." This framing highlights the vulnerable position of activists who use digital platforms: they run the risk of being viewed as threats to public order rather than as involved citizens.
Parenti, C. (2003). Fear as Institution: 9/11 and Surveillance Triumphant. In The Soft Cage. Basic Books.
Power, M. (2010). How your Twitter account could land you in jail. Mother Jones. https://www.motherjones.com/politics/2010/03/police-twitter-riots-social-media-activists/
Tech, T.. Data Detox Kit. https://datadetoxkit.org/
2 notes
·
View notes
Text
Wednesday, March 26, 2025
Canadians, long the top international travelers to the U.S., are now staying home (WSJ) Trump’s threats of tariffs and annexation have would-be visitors from the Great White North so angry or scared that they refuse to cross the border. Canadians made about 20.2 million visits to the U.S. in 2024. Even a 10% reduction could mean $2 billion in lost spending and 14,000 eliminated jobs, according to the U.S. Travel Association. How is the Trump administration responding? Here's White House spokeswoman Anna Kelly: "Canadians will no longer have to worry about the inconveniences of international travel when they become American citizens as residents of our cherished 51st state."
Some US embassies in Europe post warnings to would-be visa seekers: Watch your step (AP) Some U.S. embassies in European nations are taking to social media with pointed warnings to would-be visitors: Watch your step. Embassies in at least 17 countries have put up posts featuring images of administration figures, including President Donald Trump, Secretary of State Marco Rubio and Homeland Security Secretary Kristi Noem, warning those seeking visas that engaging in behavior deemed harmful by the government could get deported. In a post put up by the U.S. Embassy in Tallinn, Estonia, the message reads: “When you apply to enter the United States and you get a visa, you are a guest. Now, if you are in this country to promote Hamas, to promote terrorist organizations, to participate in vandalism, to participate in acts of rebellion and riots on campus, we never would have let you in if we had known that. You lied to us. You’re out.” The posts come at time when the Trump administration is clamping down on those with visas, like international students or professors, who have taken part in protests on university campuses around the conflict in Gaza in support of Palestinians and against Israel’s military actions.
In a Shift, More Republicans Want Government Investment in Children (NYT) Democrats have long looked to the government to support their families through public programs and spending. Increasingly, Republicans want the same. The details of how they want the government to help vary. But the growing bipartisan agreement reflects a belief among parents that American families are in crisis and something has to change. In a variety of surveys in recent years, majorities of both Democrats and Republicans show support for family policies like paid leave, affordable child care and tax credits for parents. Large majorities are in agreement that the government should do more to regulate social media use for young people. And Americans think that K-12 education needs to be fixed. The latest evidence is a poll of 1,300 parents released Monday by Common Sense Media, a nonprofit. In it, 73 percent of Democrats, 65 percent of independents and 55 percent of Republicans said the federal government spends too little on programs that benefit children.
23andMe Goes Bankrupt (1440) 23andMe has filed for Chapter 11 bankruptcy and announced the resignation of CEO and cofounder Anne Wojcicki. The move follows months of turmoil for the genetic testing giant and raises concerns for over 15 million customers about what happens to their personal health data. Founded in 2006, 23andMe attracted millions of consumers seeking insight into their ancestry and genetic profiles, having sold more than 12 million saliva-based testing kits globally. 23andMe claims it won’t change its current data protection policies, yet critics warn about potential privacy risks and suggest consumers delete their data. If 23andMe gets sold off to another firm, that firm would be able to access the genes of customers, leveraging the information for profit.
Trump’s Moves on Greenland Appear to Be Backfiring (NYT) For more than 150 years, U.S. officials have been trying, as President Trump puts it, to “get” Greenland. In a way, the timing couldn’t be better than now, with Greenlanders re-examining their painful colonial history under Denmark and many itching to break off from Denmark, which still controls some of the island’s affairs. But President Trump seems to have overplayed his cards—big time. His decision, announced this weekend, to send a high-powered U.S. delegation to the island, uninvited, is already backfiring. The administration tried to present it as a friendly trip, saying that Usha Vance, the wife of Vice President JD Vance, would attend a dogsled race this week with one of their sons and that Michael Waltz, the national security adviser, would tour an American military base. But instead of winning the hearts and minds of Greenland’s 56,000 people, the move, coupled with Mr. Trump’s recent statement that “one way or the other, we’re going to get it,” is pushing Greenland further away. Over the past 24 hours, the Greenlandic government has dropped its posture of being shy and vague in the face of Mr. Trump’s pushiness. Instead, it blasted him as “aggressive” and asked Europe for backup. And the planned visit may only strengthen the bonds between Greenland—an ice-covered land three times the size of Texas—and Denmark.
Now Europe Knows What Trump’s Team Calls It Behind Its Back: ‘Pathetic’ (NYT) Trump administration officials haven’t kept their disdain for Europe quiet. But the contempt seems to be even louder behind closed doors. Europeans reacted with a mix of exasperation and anger to the publication of parts of a discussion between top-ranking Trump administration officials, carried out on the messaging app Signal. The discussion, about a planned strike on Yemen, was replete with comments that painted Europeans as geopolitical parasites, and was revealed on Monday in The Atlantic, whose editor was inadvertently included in the conversation. “I just hate bailing out the Europeans again,” wrote Vice President JD Vance, asserting that the strikes would benefit Europe far more than the United States. “I fully share your loathing of European freeloading,” Pete Hegseth, the secretary of defense, later replied. “It’s PATHETIC.” A member of the chat identified as “SM,” and believed to be Stephen Miller, a top aide to President Trump, suggested that both Egypt and “Europe” should compensate the United States for the operation. The exchange seemed to show that the Europeans are mooching and that any American military action, no matter how clearly in American interests as well, should be somehow paid for by other beneficiaries.
Turkish crackdown, plunging lira (Bloomberg) Wall Street’s embrace of Turkey unraveled in just 30 minutes. When banks and hedge funds gathered in Istanbul last Wednesday with a top Turkish economist, they were prepared to hear about the country’s improved stability. Then they glanced at their phones. The Turkish lira was plunging against the US dollar, fueled by that morning’s detention of Istanbul mayor Ekrem Imamoglu—the biggest rival of leader Recep Tayyip Erdogan—on charges decried by Turkey’s opposition as a political prosecution. Within about half an hour, investors around the world had dumped huge volumes of lira, lashing its value by 10% to a record low. Erdogan has now reportedly ordered the arrest of more than 1,000 people as his forces also raid the homes of journalists. The US government meanwhile didn’t protest his violent crackdown, instead calling it “an internal matter.”
Japan’s cherry blossom season begins as first blooms appear in Tokyo (AP) Japan ‘s official cherry blossom spotters on Monday confirmed the first blooming of the country’s favorite flower, declaring the official start of the festive season in the Japanese capital. Cherry blossoms, or “sakura,” are Japan’s favorite flower and usually reach their peak in late March to early April, just as the country celebrates the start of a new school and business year. Many Japanese enjoy walking or picnicking under the trees. Sakura have deeply influenced Japanese culture for centuries and have regularly been used in poetry and literature, with their fragility seen as a symbol of life, death and rebirth.
This Ramadan, relief and hope bump against violence and uncertainty in the new Syria (AP) Sahar Diab had visited Damascus’ famed Umayyad Mosque previously. But as the Syrian lawyer went there to pray during her country’s first Ramadan after the end of the Assad family’s iron-fisted rule, she felt something new, something priceless: A sense of ease. “The rituals have become much more beautiful,” she said. “Before, we were restricted in what we could say. ... Now, there’s freedom.” As Diab spoke recently, however, details were trickling in from outside Damascus about deadly clashes. The bloodshed took on sectarian overtones and devolved into the worst violence since former President Bashar Assad was overthrown in December. This Ramadan—the Muslim holy month of daily fasting and heightened worship—such are the realities of a Syria undergoing complex transition. Relief, hope and joy at new openings—after 53 years of the Assad dynasty’s reign, prolonged civil war and crushing economic woes—intermingle with uncertainty, fear by some, and a particularly bloody and worrisome wave of violence.
Israel’s Perfect Storm: Fighting Enemies Abroad and Each Other at Home (NYT) Eighteen months ago, in the aftermath of Hamas’s attack on Israel, Israelis suspended their internal conflicts to form a united military front against a shared external threat. Now, that semblance of common cause has been cast aside. Beyond its borders, Israel has resumed fighting on four fronts—in Gaza, Lebanon, the occupied West Bank and Yemen. And internally, Israel’s citizens have returned to the bitter domestic feuds that once again, pose existential questions about their country’s future. Prime Minister Benjamin Netanyahu’s ruling coalition has revived its contentious efforts, frozen after the attack in 2023, to expand its control over other branches of government. The moves have set off mass protests after the government tried to fire the head of Israel’s domestic intelligence service as well as the attorney general—two powerful gatekeepers who are overseeing investigations into both Mr. Netanyahu and his aides. “The foundations of the state are shaking,” Ehud Olmert, a former Israeli prime minister, said in an interview. “In Israel, Netanyahu is ready to sacrifice everything for his survival and we are closer to a civil war than people realize. In Gaza, we have returned to fighting—and for what? And overseas, I never remember such hatred, such opposition, to the state of Israel.”
Israel's latest war plans: To occupy Gaza and rule Palestinians (NPR/Guardian) It was a doozy of a Monday in Israel. Sources within the Israeli military notified the press that the IDF is drafting up plans for a ground invasion and full occupation of Gaza. The plans aren’t technically set in stone, but they were drafted by the current IDF chief of staff with the unofficial backing of a bloc of far-right ministers. According to the plans, the IDF would call up multiple combat divisions to re-invade Gaza and the military would forcibly relocate the enclave’s population of 2.2 million into a tiny “humanitarian zone,” where the Israelis would provide Palestinians with the food and water they need to survive. Apparently, the military has already calculated the bare minimum number of calories needed for Palestinians in the camps to survive. While that grim news hovered above Gaza, things weren’t much better in the West Bank. Israeli police arrested Hamdan Ballal, one of four directors of the Oscar-winning documentary No Other Land, in the Masafer Yatta area of the West Bank yesterday. According to multiple Jewish activists who witnessed the incident, Ballal was first assaulted by a group of roughly 15 armed Israeli settlers dressed in military uniforms before beating him. He and two other activists on the scene were taken into police custody and driven off to an undisclosed location. An Israeli police statement said that the witnesses were “terrorists” who started the incident by throwing rocks at Israeli citizens.
Congo rebel leader says sanctions, any minerals deal with the US won’t stop fighting in the east (AP) The leader of the rebels who captured two key cities in eastern Congo tells The Associated Press that international sanctions and Congo’s proposed minerals deal with the United States in search of peace will not stop the fighting. With a $5 million bounty placed on the rebel leaders by Congo’s government, “we will fight like people who got nothing to lose in order to secure the future of our country,” said Corneille Nangaa, leader of the Congo River Alliance that includes the Rwanda-backed M23 rebel group. The rebel leader also rejected the outcome of last week’s meeting between Congolese and Rwandan leaders in Qatar, saying such a move to achieve peace without his group’s involvement would fail.
Note: There may be less news or even none for the next few days as the editor takes a break.
2 notes
·
View notes
Text
China's Tech Dominance: The UK's Struggle to Keep Up

China’s growing success in technology is not a mere accident but the result of deliberate, long-term policy investments. A recent example is the emergence of DeepSeek, a ChatGPT competitor created by a little-known hedge fund in Hangzhou, which claims to have spent just $5.6 million to develop the AI. This development is indicative of China's broader efforts to dominate the tech sector.
At the core of artificial intelligence (AI) development are three critical elements: microchips, data, and PhDs in science and technology. On two of these fronts—advanced education and data—China is already ahead of many Western nations. Chinese universities produce over 6,000 STEM (science, technology, engineering, and mathematics) PhDs each month, compared to about 2,000 to 3,000 in the United States and 1,500 in the UK.
China has also surpassed the US in patent filings, with 1.7 million patents filed in 2023, compared to just 600,000 in the US. Two decades ago, China filed just a fraction of the patents that the US did, but today, it has taken a leading position globally. While questions remain about the quality of some patents, China has also outpaced the US in "citation-weighted" patents, which measure the influence of innovations based on how often they are referenced.
In addition to AI, China’s advances are notable in other industries, such as electric vehicles (EVs), where it has become the world's largest exporter. Chinese manufacturers have cornered supply chains and technology for lithium-ion batteries, drastically lowering costs over the past decade. This success in EVs is paired with China’s efforts to lead in "electric intelligent vehicles," a sector where traditional automakers are struggling to compete, especially in software development.
China is also electrifying its entire economy at an unprecedented rate. The country now files for three-quarters of all clean tech patents globally, a massive increase from the start of the century, when it filed only a small fraction.
In AI, China is positioned to become the global leader, as highlighted by a recent US National Science Board report, which noted that China now outpaces the US in AI research publications, patents, and the production of STEM graduates.
The UK has recognized China's technological rise, with Chancellor Rachel Reeves visiting Beijing earlier this month. The trip underscored the UK's interest in strengthening long-term economic ties with China, particularly in the realms of AI, clean technology, and innovation. Chinese tech companies like Huawei are also attracting attention, with UK executives noting the company’s impressive campus and its role in global tech development.
However, there are significant concerns about data security, censorship, and democratic values, especially as China's tech industry thrives on access to vast amounts of data—something much harder to obtain in the West. This raises questions about the implications of China's AI dominance, particularly with regard to privacy and geopolitics.
While the UK government faces a delicate balancing act in its relations with China, the country's tech innovations, such as DeepSeek and advancements in AI, represent a major challenge. European nations like Spain have already encouraged China to share its advanced battery technologies, and there are growing concerns about whether China’s influence will extend beyond consumer goods like electronics and EVs to include data-hungry AI models. This shift could have profound implications not only for the tech industry but also for the global economy and geopolitics.
3 notes
·
View notes
Text
IF PASSED THIS WILL NOT STOP AT TIKTOK AND WILL COME FOR AND DESTROY THE ONLINE SPACES THAT YOU LOVE
Congress’ unfounded plan to ban TikTok under the guise of protecting our data is back, this time in the form of a new bill—the “Protecting Americans from Foreign Adversary Controlled Applications Act,” H.R. 7521 — which has gained a dangerous amount of momentum in Congress. This bipartisan legislation was introduced in the House just a week ago and is expected to be sent to the Senate after a vote later this week.
A year ago, supporters of digital rights across the country successfully stopped the federal RESTRICT Act, commonly known as the “TikTok Ban” bill (it was that and a whole lot more). And now we must do the same with this bill.
As a first step, H.R. 7521 would force TikTok to find a new owner that is not based in a foreign adversarial country within the next 180 days or be banned until it does so. It would also give the President the power to designate other applications under the control of a country considered adversarial to the U.S. to be a national security threat. If deemed a national security threat, the application would be banned from app stores and web hosting services unless it cuts all ties with the foreign adversarial country within 180 days. The bill would criminalize the distribution of the application through app stores or other web services, as well as the maintenance of such an app by the company. Ultimately, the result of the bill would either be a nationwide ban on the TikTok, or a forced sale of the application to a different company.
Make no mistake—though this law starts with TikTok specifically, it could have an impact elsewhere. Tencent’s WeChat app is one of the world’s largest standalone messenger platforms, with over a billion users, and is a key vehicle for the Chinese diaspora generally. It would likely also be a target.
The bill’s sponsors have argued that the amount of private data available to and collected by the companies behind these applications — and in theory, shared with a foreign government — makes them a national security threat. But like the RESTRICT Act, this bill won’t stop this data sharing, and will instead reduce our rights online. User data will still be collected by numerous platforms—possibly even TikTok after a forced sale—and it will still be sold to data brokers who can then sell it elsewhere, just as they do now.
The only solution to this pervasive ecosystem is prohibiting the collection of our data in the first place. Ultimately, foreign adversaries will still be able to obtain our data from social media companies unless those companies are forbidden from collecting, retaining, and selling it, full stop. And to be clear, under our current data privacy laws, there are many domestic adversaries engaged in manipulative and invasive data collection as well. That’s why EFF supports such consumer data privacy legislation.
Congress has also argued that this bill is necessary to tackle the anti-American propaganda that young people are seeing due to TikTok’s algorithm. Both this justification and the national security justification raise serious First Amendment concerns, and last week EFF, the ACLU, CDT, and Fight for the Future wrote to the House Energy and Commerce Committee urging them to oppose this bill due to its First Amendment violations—specifically for those across the country who rely on TikTok for information, advocacy, entertainment, and communication. The US has rightfully condemned other countries when they have banned, or sought a ban, on specific social media platforms.
And it’s not just civil society saying this. Late last year, the courts blocked Montana’s TikTok ban, SB 419, from going into effect on January 1, 2024, ruling that the law violated users’ First Amendment rights to speak and to access information online, and the company’s First Amendment rights to select and curate users’ content. EFF and the ACLU had filed a friend-of-the-court brief in support of a challenge to the law brought by TikTok and a group of the app’s users who live in Montana.
Our brief argued that Montana’s ban was as unprecedented as it was unconstitutional, and we are pleased that the district court upheld our free speech rights and blocked the law from going into effect. As with that state ban, the US government cannot show that a federal ban is narrowly tailored, and thus cannot use the threat of unlawful censorship as a cudgel to coerce a business to sell its property.
#tiktok#online privacy#call to action#privacy#internet#petition#call your reps#call your senators#censorship
6 notes
·
View notes
Text
The Trump administration’s Federal Trade Commission has removed four years’ worth of business guidance blogs as of Tuesday morning, including important consumer protection information related to artificial intelligence and the agency’s landmark privacy lawsuits under former chair Lina Khan against companies like Amazon and Microsoft. More than 300 blogs were removed.
On the FTC’s website, the page hosting all of the agency’s business-related blogs and guidance no longer includes any information published during former president Joe Biden’s administration, current and former FTC employees, who spoke under anonymity for fear of retaliation, tell WIRED. These blogs contained advice from the FTC on how big tech companies could avoid violating consumer protection laws.
One now deleted blog, titled “Hey, Alexa! What are you doing with my data?” explains how, according to two FTC complaints, Amazon and its Ring security camera products allegedly leveraged sensitive consumer data to train the ecommerce giant’s algorithms. (Amazon disagreed with the FTC’s claims.) It also provided guidance for companies operating similar products and services. Another post titled “$20 million FTC settlement addresses Microsoft Xbox illegal collection of kids’ data: A game changer for COPPA compliance” instructs tech companies on how to abide by the Children’s Online Privacy Protection Act by using the 2023 Microsoft settlement as an example. The settlement followed allegations by the FTC that Microsoft obtained data from children using Xbox systems without the consent of their parents or guardians.
“In terms of the message to industry on what our compliance expectations were, which is in some ways the most important part of enforcement action, they are trying to just erase those from history,” a source familiar tells WIRED.
Another removed FTC blog titled “The Luring Test: AI and the engineering of consumer trust” outlines how businesses could avoid creating chatbots that violate the FTC Act’s rules against unfair or deceptive products. This blog won an award in 2023 for “excellent descriptions of artificial intelligence.”
The Trump administration has received broad support from the tech industry. Big tech companies like Amazon and Meta, as well as tech entrepreneurs like OpenAI CEO Sam Altman, all donated to Trump’s inauguration fund. Other Silicon Valley leaders, like Elon Musk and David Sacks, are officially advising the administration. Musk’s so-called Department of Government Efficiency (DOGE) employs technologists sourced from Musk’s tech companies. And already, federal agencies like the General Services Administration have started to roll out AI products like GSAi, a general-purpose government chatbot.
The FTC did not immediately respond to a request for comment from WIRED.
Removing blogs raises serious compliance concerns under the Federal Records Act and the Open Government Data Act, one former FTC official tells WIRED. During the Biden administration, FTC leadership would place “warning” labels above previous administrations’ public decisions it no longer agreed with, the source said, fearing that removal would violate the law.
Since President Donald Trump designated Andrew Ferguson to replace Khan as FTC chair in January, the Republican regulator has vowed to leverage his authority to go after big tech companies. Unlike Khan, however, Ferguson’s criticisms center around the Republican party’s long-standing allegations that social media platforms, like Facebook and Instagram, censor conservative speech online. Before being selected as chair, Ferguson told Trump that his vision for the agency also included rolling back Biden-era regulations on artificial intelligence and tougher merger standards, The New York Times reported in December.
In an interview with CNBC last week, Ferguson argued that content moderation could equate to an antitrust violation. “If companies are degrading their product quality by kicking people off because they hold particular views, that could be an indication that there's a competition problem,” he said.
Sources speaking with WIRED on Tuesday claimed that tech companies are the only groups who benefit from the removal of these blogs.
“They are talking a big game on censorship. But at the end of the day, the thing that really hits these companies’ bottom line is what data they can collect, how they can use that data, whether they can train their AI models on that data, and if this administration is planning to take the foot off the gas there while stepping up its work on censorship,” the source familiar alleges. “I think that's a change big tech would be very happy with.”
77 notes
·
View notes
Text
SB 976 Update
Update for Californians following the progression of CA SB 976 "Protecting our Kids from Social Media Addiction Act".
As of 6/3/2024 the bill has been referred to the California Assembly Committee on Privacy and Consumer Protections.
As of today, 6/5/2024, there is no set hearing day for the bill. So now would be the time to write and submit letters of opposition for this bill. Which you can do here.
As stated on the Committee's website, its responsibilities are as follows:
"The jurisdiction of the Assembly Privacy and Consumer Protection Committee spans a wide range of technology-related issues, and includes matters affecting consumer protection in both the digital and analog worlds. Specifically, the Committee has jurisdiction over matters related to privacy, the protection of personal information (including digital information), the security of data, and information technology, as well as false advertising, charitable solicitations, weights and measures, and consumer protection generally. The Committee is also responsible for oversight of the Department of Technology within the State's Government Operations Agency."
So it would be best to focus your letters around topics related to this for this bill.
Please remember that if you do send a letter of opposition, make it a firm 'no' and give reasons why you are against this bill. Do not give caveats or make statements such as "you would support if if X would change". Hard yes or no letters. These will become held as public record and may be used in committee hearings, so please word your statements professionally and refrain from inflammatory statements about any of the authors. We wish our position of opposition to be respected and heard clearly by the committee to know that California's citizens do not want what this bill could bring to us.
The deadline to submit any position letters is noon on the Tuesday prior to a committee hearing. So keep an eye out for those dates.
For a brief update on AB 3080 and AB 1949, both bills remain in the Senate Judiciary Committee and have yet to be given a hearing date. So continue sending your letters of opposition to that committee there as well.
And please continue sending your positions to your State Senators and State Assembly Representatives, who you can find here.
Thank you again for your time and effort put into keeping California's internet safe and free.
#california#kosa#sb 976#ab 3080#ab 1949#bad internet bills#internet privacy#internet safety#legislation#online privacy
43 notes
·
View notes
Text
Survey Programming Trends: Adapting to an Ever-Changing Field

In the realm of survey programming, the pace of technological advancement and shifting methodologies is a constant. As organizations and researchers strive to gather actionable insights from diverse populations, staying abreast of the latest trends and adapting to emerging technologies becomes essential. This article delves into the current trends in survey programming and explores how professionals can navigate these changes to enhance their data collection processes and outcomes.
1. Increased Use of Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have made significant inroads into survey programming, transforming the way surveys are designed, administered, and analyzed.
2. Integration of Mobile and Multichannel Surveys
With the majority of people accessing the internet via smartphones and tablets, optimizing surveys for mobile devices is no longer optional—it's a necessity. Moreover, integrating various channels, such as email, SMS, social media, and web-based platforms, ensures that surveys reach a broader audience and accommodate different user preferences.
3. Emphasis on User Experience and Accessibility
Survey programming is increasingly focusing on user experience (UX) and accessibility to ensure that surveys are engaging and inclusive. This includes designing intuitive interfaces, minimizing survey fatigue, and accommodating respondents with disabilities.
4. Enhanced Data Security and Privacy Measures
With growing concerns about data privacy and security, survey programmers are placing greater emphasis on protecting respondent information. Compliance with regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) is crucial.
5. Leveraging Real-Time Analytics and Dashboarding
Real-time analytics and dashboarding are revolutionizing how survey data is analyzed and presented. Instead of waiting for post-survey data processing, organizations can now access live data streams and interactive dashboards that provide immediate insights.
6. Incorporation of Gamification and Interactive Elements
To boost engagement and response rates, survey designers are increasingly incorporating gamification and interactive elements. Techniques such as quizzes, polls, and interactive scenarios make surveys more engaging and enjoyable for respondents.
7. Adoption of Advanced Survey Methodologies
Survey methodologies are evolving to include more sophisticated approaches, such as conjoint analysis, discrete choice modeling, and experience sampling methods.
8. Focus on Inclusivity and Cultural Sensitivity
As global surveys become more common, there is a growing emphasis on inclusivity and cultural sensitivity. This involves designing surveys that account for diverse cultural contexts, languages, and social norms.
9. Increased Use of Data Integration and Cross-Platform Analytics
Integrating survey data with other sources, such as CRM systems, social media analytics, and transaction records, provides a more comprehensive view of respondents.
10. Growing Importance of Ethical Considerations
Ethical considerations are becoming more prominent in survey programming. This includes ensuring informed consent, minimizing respondent burden, and being transparent about how data will be used.
Conclusion
Survey programming is an ever-evolving field, driven by technological advancements and shifting methodological trends. By staying informed about the latest developments and adapting to new tools and techniques, survey professionals can enhance the effectiveness of their data collection efforts. Embracing AI and ML, optimizing for mobile and multichannel experiences, focusing on user experience and accessibility, and maintaining high standards of data security and ethical practices are key to navigating the complexities of modern survey programming.
To know more read our latest blog: Navigating Trends: The Ever-Evolving in Survey Programming
Also read: survey programming services company
3 notes
·
View notes