#Web scripting virus
Explore tagged Tumblr posts
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
453 notes
·
View notes
Text
<body>

<h1> computer id pack </h1>

<div class="names">
<p> cyber , tech , pixel , digital , quantum , hp , code , script , binary , html , ip , al , nano , virus , malware , glitch , byte , cache , chip , chrome , error , spark , static , monitor , password </p>
</div>

<div class="pronouns">
<p> key / board , ai / ais , 404 / 404s , code / codes , html / htmls , java / script , py / thon , url / urls , web / webs , api / apis , inter / net , pix / pixel , .png / .pngs , .gif / .gifs , .rar / .rars , .zip / .zips , .txt / .txts , mal / ware , desktop / desktops , software / softwares , hardware / hardwares , password / passwords </p>
</div>

<div class="titles">
<p> the coded one , the digital one , the electronic one , the computer , the program , the programmer , prn who is made of binary , prn who is made of code , prn who codes , prn who is a computer , prn who is digital , the ai , the sentient ai , the sentient computer , prns wires , prn who is made of wires , the error , the virus , the website </p>
</div>

<p> requested by : nobody </p>
<p> self indulgent id pack to fuel my computerkin identity. feel free to use anything listed here. </p>

</body>
#⟡ webtiles#⟡ npt request#npt pack#npt list#npt ideas#id pack#id list#id ideas#computer#tech#internet
27 notes
·
View notes
Note
HIII !!
ur blog looks rlly cool && i was wondering if i could have
— 1x4 OR 1eggs
as a full ID pack , pls && thank you :3c
( also could i be the 🌟 anon ?? )



☆ ﹒ 1x1x1x1 ID PACK !
🧪 – requested by : anon ( 🌟 )
🧪 – posted by : jaxx

✟ ﹒ names 𝄈
1x . 1x4 . 1x1x1x1 . aamon . adder . anwir . balor . bellinor . blazer . bolverkr . brantley . cain . cary . casimir . cifarelli . cole . corbin . csintalan . exe . damien . daray . darth . delaney . diablo . diabolos . dolion . dolus . donovan . draco . donahue . dugal . doyle . drefan . heolstor . ivan . keres . kerwin . kieran . krampus . malvolio . maverick . metis . morfran . morgoth . moros . mort . one . onyx . ormr . ozul . phoenix . rogue . tamesis . thanatos . torquil . treacher . tynan . ubel . wilder . x . zagan .
✟ ﹒ pronouns 𝄈
01 / 01 . 10110 / 101 . byte / bytes . chaos / chaos . code / codes . command / commands . mal / malware . mal / malfunction . data / data . cyb / cyber . digi / digital . e / exe . gli / glitch . in / install . li / link . vi / virus . web / site . wire / wires . h3 / h1m . h! / h!m . h# / h#m . shx / hxr . hx / hxm . ix / ix . 1x / 1x . hack / hacker . script / scripts . it / its . rib / cage . rib / ribs . death / deaths . negativity / negativities . despair / despair . slash / slash . demise / demises . decay / decay . slay / slayer . rot / rotten . para / paranoia . corr / corrupt . xi / xir . 🥚 . 🦴 . ⚔️ . 🧪 . 👑 . 👾 . 🥀 .
✟ ﹒ titles 𝄈
his creation of hatred . the being of despair . the one who waits for the day . the slaughterer . prn who hates prns creator . prn who attacks . prn who hacks . the hacker . the failed work of art . prn who embodies negativity . the one who is devoid of positivity . no . 1 shedletsky hater ( /j ) . prn who is filled with rage . prn who doesn ' t forgive . prn who holds grudges . the inescapable one . prn who fires prns sword .
✟ ﹒ labels 𝄈
n / a
✟ ﹒ genders 𝄈
agender . gxndxrfluid . mxsculine . hatembodiment . inner ragic . fleshripped . detagender . timarix . weaponthing . monsteric . cyberthing . <?>gender . th?ng . necrogender . gender decay . malware gender . virus gender .
✟ ﹒ system names 𝄈
the creations of hatred . the ones created by hatred . the fighters . the failed creations . the broken artworks . the holders of negativity . roblox ' s favourite hackers . reminders of the past . those who cast mass infliction .



#🌟#~ ! angelicgraveyard#~ ! id pack#~ ! request fulfilled#1x1x1x1#forsaken#roblox#shedletsky#one#eggs#npt list#npt suggestions#npt#npts#name ideas#trans names#name suggestions#names#name list#pronoun ideas#pronoun list#pronoun sets#pronouns#neopronoun suggestions#neopronoun help#neopronoun ideas#neopronouns#mogai#lgbtqia#mogai friendly
42 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text

𓎟 ̊ names and prns relating to the internet, cyberspace, and technology𓈒
requested by anon

Zett﹐ Zetta﹐ Disc﹐ Data﹐ Virus﹐ Vir﹐ Code﹐ Codette﹐ Interweb﹐ Cyberweb﹐ Binary﹐ Morphe﹐ Index﹐ Byte﹐ File﹐ Auto﹐ Nett﹐ Crypt﹐ Trojan﹐ Mac﹐ Pixel﹐ Router﹐ Cache﹐ Java﹐ Malware﹐ Coda
ai ais﹐ glitch glitches﹐ screen screens﹐ web webs﹐ pix pixel﹐ .png .pngs﹐ .exe .exes﹐ .jpg .jpgs﹐ file files﹐ cyber cybers﹐ code codes﹐ script scripts﹐ .com .coms﹐ tech techs﹐ .net .nets﹐ .org .orgs﹐ error errors﹐ nano nanos﹐ vir virtual﹐ net network﹐ key keys﹐ .zip .zips﹐ wire wires

[PT: names and pronouns relating to the internet, cyberspace, and technology
requested by anon
Names: Zett, Zetta, Disc, Data, Virus, Vir, Code, Codette, Interweb, Cyberweb, Binary, Morphe, Index, Byte, File, Auto, Nett, Crypt, Trojan, Mac, Pixel, Router, Cache, Java, Malware, Coda
Pronouns: ai/ais, glitch/glitches, screen/screens, web/webs, pix/pixel, .png/.pngs, .exe/.exe, .jpg/.jpg, file/files, cyber/cybers, code/codes, script/scripts, .com/.coms, tech/techs, .net/.nets, .org/.orgs, error/errors, nano/nanos, vir/virtual, net/network, key/keys, .zip/.zips, wire/wires
/end PT.]
#✚𓈒 ― np lists#✚𓈒 ― requests# #mogai safe#mogai#liom safe#mogai coining#name ideas#name suggestions#npt ideas#npt suggestions#npt list#technology names#technology pronouns#neopronoun suggestions#neopronoun ideas#neopronouns#pronoun ideas#pronoun suggestions
128 notes
·
View notes
Text
R800 id pack
names ܂ ∿ ⟢ 】 ace . adam . adrian . AI . arcade . archie . ash . axel . blair . cyber . daniel . dash . electric . elliot . gadget . glitch . hunter . ivy . jamie . jay . kaleb . lazer . nick . pixel . prime . r . r800 . ryan . script . spark . steel . sterling . twitch . volt . zack
pronouns ܂ ∿ ⟢ 】 404/404s . android/androids . beep/boop . bot/bots . by/byte . code/codes . entertain/entertainer . inter/net . null/nulls . r800/r800s . robot/robots . stream/streamer . tech/technology . twitch/twitch’s . vir/virtual . virus/virus . vy/vym . web/site . web/web . xi/xim . zey/zem 💿/💿s . 🌐/🌐s . 🎤/🎤s . ⭐️/⭐️s . 📱/📱s
titles ܂ ∿ ⟢ 】 the virtual entertainer . the content android . [x] who streams . [x] who creates content . synthetic [x] . the cybernetic content creator . [x] behind the screen . the supercomputer . the antivirus . the latest in entertainment technology . [x] the machine . the content farm
#id pack#identity pack#id help#r800#self indulgent#💫 … id packs#💜 ... and i know i'm the one who died
13 notes
·
View notes
Text
Man, having insomnia fucking sucks.

Hello internet. Welcome back to yet another blog where I release the thoughts that are trapped inside this rather abnormal cranium of mine. Tonight, I write to you from a rather weird setting. Instead of me typing out my post in the middle of the evening from my rather impressive custom-built computer, I instead type to you from my iPad. It’s currently 3:40 in the morning on this cold December Friday, my partner sleeping soundly next to me.
At least, I think it is.
Honestly, I’m not really sure. Luckily, I broke out the quiet keyboard to type in bed.
Anyway,
I haven’t updated this blog in a while. I could lie and say that I’ve been working on other projects, but that wouldn’t be entirely true. I mean, I have been working on other stuff, but there’s been a lot less finishing projects and more starting and stopping. I mean, I’ve been working on a review script for Marmalade Is Missing for the last month and a half. I only have three or four paragraphs left to type, yet, every time I go to work on it, I tend to find myself in a sudden state of unease. Like, I’m perfectly aware that I shouldn’t fear my own creations getting out into the public. Hell, I started a blog back up on a website that I check maybe once a week. It’s really less my own views on my work and more worrying about how the world might react, if that makes any sense.
With the direction that America is going in, you can’t blame me for having these anxious thoughts about my projects. When my stuff hits the web, it isn’t going to be just me that’s going to have a small spotlight shining down on them, but also everyone affiliated with me. My partners, my alters, my friends, and anyone else that I bring on this project. Kameron Kazma’s Something Show is a project that I have somewhat ridiculously high hopes for, but I do truly believe that my work could bring the entertainment that the Internet deserves right now. I’ve been paying close attention to what’s being seen as comedic in today’s day and age. Very few people are trying to do anything original these days, most of the digital community diluting down to repost and “Loud Equals Funny” content. It almost feels like my devices have been infected with some kind of virus, one that ignores the fact that I frequently tap “Not Interested” on every piece of stolen content on TikTok so that it can force more down my throat.
Speaking of TikTok, that’s got social media on fire right now. From what I’ve seen, the TikTok Ban is still happening on January 19th of next year (2025 in case someone is reading this in the future.) Apparently ByteDance has already tried to file for an appeal to the court once, but it was quickly shot down. Word has it that the company is going to try again. I’m not going to hold my breath for too long though. If anything, I might still be able to access it on my computer whenever I want to post something. Only problem is that now I’ll have to start double editing all of my short form content so that I can still post it for both mobile users of TikTok and computer users of YouTube. Gotta keep that content flowing, ya know?

While I’m practically venting out the inner thoughts of my mind, that’s another thing that I need to maybe start worrying about now: the algorithm. I’ve always hated the idea of following treads to get a following. I’ve always been someone who likes the idea that I could make it BIG doing my own thing. I hate the idea of having to follow in the footsteps of someone else, but recent events make it seem as if I need to start paying a little more attention to what popular these days. This was already something that I was loosely aware of before, but I think I stopped taking notes when popular trends contained petty theft and purposely pissing people off to get cargo ships full of hate comments. (JelloApocolypse’s One Piece video is the best worst example of this.)
The least I could do is see what’s popular in a positive light and try to work that into my projects.
That is, of course, I get any of those projects done…
I might need to start hiring people to pester me into getting things done.
(Also, random side note, I’m listing to BRAINS! By Voltaire while I’m typing this and the gif above weirdly goes along with the song. I picked that gif, like, three or four songs back. Just a random thought.)
Alright, I’ve gotta get to bed. My partner just woke up cause its usual work alarm went off, but it has the day off. I might be in a bit of trouble in the morning for still being up at 4 A.M., so wish me luck! I’ll do my random color coding in the morning when I wake up (considering I either sleep or sit here until the sun rises.)
Stay safe out there.
-Kameron D. Kazma
P.S. Again, there’s isn’t some kind of secret code to the coloring of my post. I just like making it look weird.
Or maybe there is a code.
Not like anyone’s gonna take the time to figure it out either way…
2 notes
·
View notes
Text
Human Metapneumovirus (HMPV) – Testing Management System Using PHP and MySQL

Human Metapneumovirus (HMPV) Testing Management System is web based technology which brings up various diagnosis works online. Here patients are first allowed to register on the website and provide personal, test information. Once registered with their address and contact details, the patients may now see a variety of tests conducted by the lab. The patient will select the required test and book appointment after that lab center send a lab boy at registered address to collect a sample. After successful sample collection patient can track their test history using the name, order and registered mobile number. The Human Metapneumovirus (HMPV) Testing Management System allows admin to attach a copy of the report into the system and automatically shown on user side so user can downloads report.
Click here: https://phpgurukul.com/human-metapneumovirus-hmpv-testing-management-system-using-php-and-mysql/
Human Metapneumovirus (HMPV) — Testing Management System Project Modules
In NIPAH VIRUS Testing Management System we use PHP and MySQL database. It has two modules i.e.
Admin
User (Patient)
Admin Module
Admin is the super user of the website who can manage everything on the website. Admin can log in through the login page
Dashboard: In this section, the admin can see all detail in brief like the total, assigned and the sample collected and completed tests.
Phlebotomist: In this section, the admin can manage Phlebotomist (add, update, delete).
Testing: In this section, the admin can manage all the tests like assign the test to the Phlebotomist and updating the history.
Report: In this section, the admin can generate two types of report. One is between dates reports and the one is by search. Admin can search the report by order number, name and mobile number.
Notification: In this section, the admin will get a notification for every new test request (notification bell).
Admin can also update his profile, change the password and recover the password.
User (Patient) Module
User can visit the application through a URL.
Testing: This section divided into two parts. One is for new user and another one is for registered user. New user (First-time user) needs to provide personal and testing Information. A registered user only needs to provide test information; their personal information will be fetched from the database.
Test Report: In this section, Users can search their test report using order number, name and registered mobile number.
Dashboard: In this section, the User can see the in which State of how many tests are done.
How to run theHuman Metapneumovirus (HMPV) Testing Management Project using PHP and MySQL
1. Download the project zip file
2. Extract the file and copy hmpv-tms folder
3.Paste inside root directory(for xampp xampp/htdocs, for wamp wamp/www, for lamp var/www/Html)
4.Open PHPMyAdmin (http://localhost/phpmyadmin)
5. Create a database with the name hmpvtmsdb
6. Import hmpvtmsdb.sql file(given inside the zip package in SQL file folder)
7. Run the script http://localhost/hmpv-tms
*************************Admin Credential************************** Username: admin Password: Test@123
PHP Gurukul
Welcome to PHPGurukul. We are a web development team striving our best to provide you with an unusual experience with PHP. Some technologies never fade, and PHP is one of them. From the time it has been introduced, the demand for PHP Projects and PHP developers is growing since 1994. We are here to make your PHP journey more exciting and useful.
Email: [email protected] Website : https://phpgurukul.com
0 notes
Text
ERPGo SaaS Nulled Script 6.8

Unlock Premium Business Management with ERPGo SaaS Nulled Script In today’s fast-paced business landscape, having a robust and comprehensive enterprise management system is no longer a luxury—it’s a necessity. That’s where the ERPGo SaaS Nulled Script comes in. Designed for modern businesses, this all-in-one solution empowers startups, SMEs, and enterprises to streamline their operations without breaking the bank. What is ERPGo SaaS Nulled Script? The ERPGo SaaS Nulled Script is a complete business management platform that integrates essential modules such as Accounting, CRM, HRM, Project Management, POS, and more into one powerful solution. As a SaaS-based script, it enables you to launch your own cloud-based ERP service, offering advanced tools to your clients while maintaining full control over the backend. Whether you're managing clients, tracking inventory, or analyzing financial data, ERPGo makes it seamless and intuitive. This nulled version provides all premium functionalities completely free, opening the door for entrepreneurs and developers to access top-tier software without the usual costs. Technical Specifications Language: PHP (Laravel Framework) Database: MySQL Front-End: Bootstrap 4 Fully Responsive: Mobile and desktop ready Multi-Tenant Ready: Ideal for SaaS model deployment Modular Architecture: Easily customizable and scalable Top Features and Benefits of ERPGo SaaS Nulled Script Multi-Company Support: Manage multiple businesses under one platform effortlessly. HRM System: Automate employee management, payroll, attendance, and leave tracking. Project Management: Keep your teams on track with task allocation, deadlines, and collaboration tools. CRM Tools: Strengthen customer relationships with powerful contact and sales pipelines. Accounting Module: Generate invoices, manage expenses, track income, and handle taxes with ease. POS Integration: Real-time point-of-sale system for retail and online stores. Real-World Use Cases The ERPGo SaaS Nulled Script is highly versatile, making it suitable for: Startups: Launch your own ERP SaaS product and offer subscription-based services. Agencies: Help your clients manage their businesses with a branded ERP solution. Retail Stores: Use the integrated POS system to handle sales and inventory efficiently. Freelancers: Manage your personal projects, invoices, and client database under one dashboard. Simple Installation and Easy Setup Getting started with the ERPGo SaaS is straightforward. Once you download the package, follow the included installation guide to deploy it on your server. With a user-friendly setup wizard and detailed documentation, even users with minimal technical knowledge can have it running in no time. Frequently Asked Questions (FAQs) Is ERPGo SaaS Nulled Script safe to use? Yes, when downloaded from trusted sources like ours, the script is secure and virus-free. We ensure all files are clean and ready to use. Can I use ERPGo for multiple businesses? Absolutely. The script supports a multi-company setup, letting you manage several entities with complete separation and control. What makes this script different from others? ERPGo stands out due to its clean UI, powerful features, and SaaS-readiness. The nulled version includes all premium modules at no cost. Is technical support available? While official support isn’t provided with the nulled version, our community forums and tutorials offer plenty of help to get you started. Download ERPGo SaaS Nulled Script Now Don’t miss the opportunity to power your business with the most dynamic ERP tool available. Download the ERPGo SaaS today and explore all its capabilities for free. And if you're exploring other premium tools, check out our curated collection of nulled plugins to further enhance your website functionality. Looking for a top-tier WordPress theme as well? We recommend the versatile Impreza NULLED theme, a perfect complement to any web project. Take full control
of your business systems with ERPGo—download, install, and start managing smarter, not harder.
0 notes
Text
Rilide Malware: How browser Extensions Affect Online Threats

How Rilide virus strikes via browser extensions:
What's Rilide?
Rilide, also known as LumaC2 and CookieGenesis, is powerful malware discovered in 2023. It targets Chromium browsers to collect user data and control behaviour. Rilide's main feature is misusing its browser extension to launch attacks.
Change to Browser Extension Attacks
Rilide is a sign of a major threat shift. Traditional man-in-the-browser attacks used malware detecting HTML patterns in browser memory and inserting
However, modern assaults using malicious browser extensions like Rilide bypass most of these restrictions. Extensions don't depend on any website, thus they can run in the background. They also have higher rights to access browser-wide resources like cookies and local storage and bypass same-origin restrictions. Extensions give more persistence and control than traditional web injection methods because they work even when no pages are open.
Extensions also impact JavaScript execution context. Conventional injections may have left traces because they ran alongside security tools and web application code. Extensions create two JavaScript environments in addition to the main page context:
Despite its separation from the main page environment, the content script context can access the page document.
As a service worker, the main page environment and content script cannot access the background code context.
Communication between contexts occurs through hidden browser interfaces from page developers. Because much of the extension's action and evidence are designed to be separated, detection will be harder without changes to the original document. Due of extensions' greater control, persistence, evasion, and ease of development, browser threats likely evolved to employ extensions. Modern browser APIs make browser extensions easy to develop due to their extensive built-in functionality and permissions.
Technique: Rilide Uses Extension Elements
Rilide uses browser extension components to simplify its attacks:
The Manifest:
This crucial section describes the extension's functionality and access levels. One Rilide variant posed as a Google Drive plugin. By listing the appropriate rights, the manifest file reveals Rilide's capabilities. Rilide requested these important permissions:
“Scripting”: Injects and runs JavaScript code on web pages.
You can see, change, and delete browser cookies.
Monitor and change browser network requests using “WebRequest”.
“ClipboardRead/Write”: Reading and editing clipboard content.
“ActiveTab”: Temporary tab content access. With the “host_permission” parameter, the extension can access and interact with any browser-supported scheme, domain, path, and port.
Because they run on all URLs at document_start, content scripts start early in page loading. The manifest also establishes rules under “declarative_net_request” to remove specific Content Security Policy (CSP) headers to allow Rilide to insert inline data. Under “background” lies the extension's service worker, where the malware tracks browser events and communicates with the C2 server.
Background.js, background script:
When the extension is installed, this script executes its initialisation code. Chrome.system retrieves CPU, storage, and extension data, while chrome.management retrieves cookies.getAll retrieves all cookies at startup. A unique ID is maintained locally. This data is sent to the C2 server, which may allow the extension to proxy.
Initialisation fetches commands, viral settings, and injections. After enabling CSP removal rules, the background script tracks browser events. The background script includes a unique C2 server domain gathering method. Recurring Google Chrome alarm calls retrieve them from a Telegram bot. If a domain is blocked, the virus can easily switch.
The background script transmits data exfiltration to the C2 server after listening for content script signals like “new-grabber-info,” which contain input element values. For chrome.tabs.captureVisibleTab to capture the visible tab and send the screenshot data to the C2, it listens for “set-screenshot-result” signals. Verify and initiate proxy connections and execute C2 instructions with frequent alarms.
Command script cmds.js:
This script receives calls from the C2 server and returns results. Some intriguing commands are:
“Extension”: Allows ID-based extensions.
“Push” opens a new tab and displays the fetched content in a browser notice.
“Screenshot”: Captures the tab's content.
“History” retrieves browsing history.
“Cookies”: Retrieves all browser cookies.
“URL”: Opens a new tab with a URL. Device details, URL, and extension setup are available in additional instructions. These instructions simplify attacker development by exploiting Chrome extension features and dynamic workflow modifications.
Main.js and Gmail.js are content scripts
These scripts talk to websites.
main.js:
This script starts with jQuery and disguised dangerous code. Injections from the service worker downloaded during initialisation are executed if the URL matches. A clever injection technique leverages the onreset document element to execute a custom reset event immediately, making detection difficult. Also, main.js uses jQuery to create a generic data stealer listener that selects all input elements. It listens for change events on particular elements and accumulates input values like usernames and passwords when the value changes and the element leaves focus. Chrome.runtime.sendMessage sends stolen info to the service worker, who sends it to C2 servers.
Gmail.js:
It targets mail.google, the Gmail mail client page. Its major goal is 2FA authentication request manipulation to hide cryptocurrency theft. The script regularly checks popular bitcoin wallet emails. If emails contain “Withdrawal Request,” it replaces it with “Authorise New Device”. To replace email preview content, it targets span elements with “withdrawal”.
The script determines email body and authorisation code from CSS classes and content. This script replaces the email body's HTML with hardcoded text. The threat actor uses this strategy to make victims interpret withdrawal requests as less suspicious new device authorisations to withdraw cryptocurrency without alerting them. Detecting email body items requires formatting and language, making it unpredictable.
Proxy Capability
Its ability to turn the victim's browser into an HTTP proxy, which may be implemented using extensions, is one of its best capabilities. This functionality lets the attacker route all requests using the victim's credentials and data. This is especially problematic for financial fraud since hackers might utilise the victim's authenticated session to access financial systems and start transactions or change settings without IP address verification.
CursedChrome, an educational proof-of-concept, provided most proxy functions. It uses WebSocket to link the attacker's C2 server to the extension's service worker. The C2 collects results from the victim's cookies, which are utilised to navigate or submit queries. Backend code and administrative UI are available in CursedChrome, exhibiting easiness.
Scale and Indicators The Trusteer research lab found 50,000 hacked user sessions since early 2025, demonstrating the problem. Rilide targets North America, South America, Europe, and Japan as part of its global campaign.
It provides compromise signs like filenames and hashes:
Files: ico.png, crrule.js, exts.js, rules.json, manifest.json, utils.js, historytab.js, notif.js, config.js, content-scriptsApp.html, background.js, main.js, gmail.js, csp.js, exchangeSettings.js, screen.js, domain.js, inj.js, set.js, proxing.js, cmds.js, machine.js, and -register-pol
Zip file extFiles.zip.
Domain statbrwsr.digital
In conclusion, Rilide is an advanced malware that uses browser extensions to gain long-term control, access private data, bypass security measures, and steal cryptocurrency and financial data more covertly than previous web injection methods.
#RilideMalware#Rilide#BrowserExtensionAttacks#mainjs#Gmailjs#backgroundjs#cmdsjscommandscript#Technology#technews#technologynews#NEWS#govindhtech
0 notes
Text
This image gives a solid, compact breakdown of what a Next Generation Firewall (NGF) actually does. It’s way more than just blocking ports like the old-school firewalls. These bad boys are the Swiss Army knife of cybersecurity—combining multiple tools into one powerhouse of a system. Here’s a detailed look at each feature shown:
⸻
Core Capabilities of a Next Generation Firewall (NGF):
1. Antivirus
Blocks known malware and viruses at the perimeter.
2. Intrusion Prevention System (IPS)
Detects and prevents malicious traffic using signatures and behavior analysis.
3. Mobile Security
Extends firewall protection to mobile users and endpoints.
4. Threat Intelligence Service
Feeds live data about current threats into the NGF for real-time defense.
5. Antispam
Blocks phishing and spam-based attacks, especially in emails.
6. Vulnerability Management
Identifies and manages security flaws in systems or software.
7. Virus Outbreak Protection Service
Early detection of new virus variants through heuristic analysis and sandboxing.
8. IP Reputation
Blocks or flags traffic from known malicious IPs.
9. Content Disarm & Reconstruction (CDR)
Strips potentially dangerous content from documents and reconstructs safe versions.
10. Industrial Security
Secures SCADA/ICS systems often used in factories and utilities.
11. Cloud Access Security Broker (CASB)
Monitors cloud service use and enforces security policies for SaaS apps.
12. Application Control
Manages and restricts access to applications by user, group, or device.
13. Web Filtering
Blocks access to malicious or inappropriate websites.
14. Security Rating Service
Gives your network or firewall a security score based on current configurations and threats.
15. Web Security
Protects against threats from web browsing like drive-by downloads and malicious scripts.
16. Indicators of Compromise (IoC)
Detects subtle signs that a system may be compromised.
⸻
Why This Matters:
Next-Gen Firewalls don’t just filter traffic—they analyze behavior, apply AI-based detection, and adapt in real-time. Whether you’re working in cybersecurity, IT management, or penetration testing, understanding NGF features helps you:
• Design layered defenses
• Troubleshoot with more context
• Detect threats earlier
• Improve security posture assessments
⸻
Want to go deeper into how NGFs are implemented or maybe compare top vendors like Fortinet, Palo Alto, or Cisco Firepower
0 notes
Text
Como proteger wordpress de ataques
Proteger Wordpress es una necesidad absoluta y te explico la razón. Wordpress es el CMS más utilizado ,lo utilizan el 63% de los sitios que utilizan un CMS. El 40 % de las páginas de internet lo utilizan ,810 millones de páginas. Esta popularidad atrae a los hackers eso está claro. Wordpress como Windows es un sistema fácil de utilizar y gestionar pero por esa usabilidad también genera muchas vulnerabilidades. Entre los años 2023 y 2024 se notificaron 5948 vulnerabilidades en Wordpress ,de las cuales el 97% provenían de plugins ,el 3% de temas o plantillas y solo el 0.2 del nucleo de Wordpress. Wordpress tiene muchisimos plugins gratuitos,te ahorras dinero pero también al ser gratuitos no se exige la misma seguridad que los de pago. Dentro de las vulnerabilidades que se encuentran la mayoría están en los plugins,las vulnerabilidades del nucleo de wordpress son de bajo nivel.
Las 10 vulnerabiliades de Wordpress más importantes en el 2024 y 2025
1. Cross Site Scripting (XSS) Con 3.171 incidentes, el XSS es la vulnerabilidad más común, representando el 53.3% de las nuevas vulnerabilidades de seguridad de WordPress. Esta técnica permite a los hackers inyectar scripts maliciosos en las páginas de WordPress, lo que puede resultar en el secuestro de sesiones o en el robo de datos de los usuarios de la página. 2. Falsificación de petición en sitios cruzados (CSRF) El CSRF, con 1.098 vulnerabilidades notificadas, permite a los atacantes engañar a los visitantes para que realicen acciones no intencionadas en aplicaciones web autenticadas, como transacciones no autorizadas o manipulación de datos. 3. Control de acceso defectuoso Este tipo de vulnerabilidad, con 767 avisos,ocurre cuando no se controla adecuadamente los permisos que tiene un usuario en la página,lo que provoca que acceden a datos sensibles. 4. Inyección SQL Con 266 vulnerabilidades notificadas. Esta técnica permite realizar consultas SQL a la base de datos y acceder a datos sensibles como tarjetas de crédito o passwords. 5. Exposición de datos sensibles Notificada 119 veces, esta vulnerabilidad surge por el manejo inadecuado de datos personales y sensibles, incumpliendo la LOPD española o RGPD europea.. 6. Transferencia arbitraria de archivos Los hackers pueden manipular solicitudes POST para ejecutar archivos arbitrarios en el servidor web, lo que podría resultar en la inserción de malware. 7. Escalada de privilegios Este tipo de vulnerabilidad permite al hacker, que inicialmente accede a una cuenta de invitado por ejemplo, escalar privilegios para acceder a recursos de nivel administrativo. 8. Inyección de objetos PHP La inyección de objetos PHP permite a los atacantes realizar ataques como : -Inyección de código -Inyección SQL, -DOS a través de la inyección de código PHP arbitrario. 9. Vulnerabilidad de omisión Este defecto permite a los hackers evitar los mecanismos de autenticación de la página, lo que podría permitirles realizar acciones restringidas o restablecer contraseñas para acceder sin autorización a cuentas de WordPress. 10. Falsificación de Petición del Lado del Servidor (SSRF) Los atacantes pueden acceder al hosting donde está instalado WordPress para acceder o modificar recursos que no deberían estar expuestos al público .
Causas de estas vulnerabilidades
Las vulnerabilidades se deben: A plugins y temas no actualizados Credenciales débiles Proveedores de hostings poco seguros Utilizar plugins gratis poco seguros Roles de usuario mal configurados No utilizar un plugin de seguridad Los plugins de seguridad te protejen contra virus,malwares, malas configuraciones y contraseñas débiles. La mayor parte de los sitios que fueron atacados de Wordpress no tenian un plugin de seguridad o tenían uno que no se actualizaba con las nuevas amenazas. Puedes asegurar tu sitio de wordpress con plugins gratuitos de seguridad. Pueden ayudarte a protegerte una parte pero ninguna tiene una firma de virus y malware actualizada solo los de pago. En eso Wordfence es el mejor plugin de seguridad para proteger worpress,tiene versión gratuita que te permite una seguridad básica pero no te protege frente a ataques nuevos. Si tienes un foro,una academia online o una tienda online te recomiendo encarecidamente que compres alguna de las versiones de pago. Yo voy a tener una acdemia online y pienso comprar este plugins de seguridad. Tus clientes pueden denunciarte y sacarte bastante dinero si se demuestra que un virus de tu página les afecto o incluso por robo de información como tarjetas. En definitiva tienes que proteger wordpress de virus ,ataques de denegación de servicio y robo de datos porque tu negocio podía ir a la quiebra por un ataque.
¿Qué es Wordfence?
Con más de 4 millones de instalaciones activas, Wordfence es el plugin de seguridad de WordPress más usado del mundo. Este plugin te ofrece una suite de seguridad completa y sencilla que evitará que tu negocio sufra un ataque al 99,9% ,ese 0,01 es si no renuevas su licencia anual.
Herramientas de Wordfence
Wordfence te ofrece diferentes herramientas para proteger tu página web contruida con wordpress. Firewall Es una funcionalidad increible que permite proteger tu sitio de conexiones de direcciones IP identificadas como peligrosas. Viene con unas reglas incorporadas y ademas tiene un modo de aprendizaje que analizas las direcciones IP para ir aprendiendo y aplicando sus reglas correctamente. Escaner de seguridad Esto es lo mejor que tiene analiza archivos de wordpress ,temas,plugins,contenido y hasta comentarios para detectar virus y amenazas de malware,puertas traseras ,XSS. Este plugin de seguridad protege wordpress de todos las amenazas que hablamos antes pero necesitas alguna de las versiones de pago ,porque la gratuita tiene firmas anticuadas. Si encuentra algun virus en algun lugar del sitio ,nos lo notificará y podremos remplazar el archivo por una copia segura ,dado que hace copias de todo . Login seguro Protege tu zona de administración de wordpress de atacantes limitando el numero de intentos de acceso desde una direccion IP ,protege la página con un CAPTCHA y aáde doble autenticación. Wordfence central Si tienes varios sitios con Wordpress ,puede proteger wordpress desde un mismo lugar gracias al Wordfence central .
Planes de Wordfence
Wordfence ofrece diferentes planes con servicios muy bien diferenciados para adaptarse a las necesidades de seguridad de diferentes tipos de sitios. Wordfence gratuito El plan básico es totalmente gratuito. Es gratis y protege tu página web de forma simple y efectiva. La protección básica de Wordfence es capaz de protegerte frente a diferentes tipos de ataques, aunque las actualizaciones del firewall y de las firmas para la detección de malware esta limitada. Los planes de pago son los únicos que te protegeran totalmente. Pero si quieres probar el gratis puedes hacerlo desde este enlace . Wordfence Premium Con la subscripción premium te garantizas dos mejoras: soporte y actualizaciones. El plugin se actualizará de Wordfence Security en tiempo real para las reglas del firewall y las definiciones de malware de la base de datos. Este plan es el mejor si tienes una academia online,un foro ,o un blog de membresias para proteger a tus usuarios y a tu sitio de ataques. Aunque si te soy sincero si tienes cualquier tipo de página web creada con Wordpress viendo las vulnerabilidades que tiene mejor compralo igual. La licencia es anual asi que pagas una vez y te olvidas en todo el año. Puedes mirar la información de este plan Wordfence Premium siguiendo este enlace. Wordfence Care Este nivel se ha diseñado para que puedas delegar todo al equipo de Wordfence Security. Tras una auditoría del estado de seguridad de tu web, te configuran Wordfence en función de las necesidades específicas del sitio. A partir de ese momento, se encargan de monitorizar tu página. Si se produce un incidente, te contactarán y se encargarán de limpiar tu servidor. También te ayudarán a salir de las listas de páginas baneadas por los buscadores y te explicarán qué puedes hacer para evitar futuros ataques similares. Recomiendo este plan del plugin para proteger una tienda virtual con Woocommerce. Los riesgos son mucho mayores al tener a gente que paga con su tarjeta de crédito o debito y te aseguro que aunque utilices Paypel o Stripe los riesgos son altos. Los hackers se pasan el dia intentanto buscar vulnerabilidades en tiendas de wordpress porque son las más utilizadas más que nada y porque muchas tiendas cometen el error de no tener un plugin de seguridad. Piensan 500 euros es muy caro al año hasta que les ataque un hacker ,roban sus datos o tiran su tienda y luego sufren tales multas y problemas que tienen que cerrar . No seas uno de ellos y protegete más vale pagar 500 euros que perder tu negocio o que te metan unas multa de hasta 50.000 euros. Asi que yo te avise mejor 500 euros que 25.000 o 50.000 euros de multa. Si te interesa estar tranquilo puedes ver más información de este plan de Wordfence Care siguiendo este enlace. Wordfence Response Este es el servicio más premium que ofrece Wordfence. Tienes todas las ventajas de la suscripción Care, pero con un compromiso de respuesta de una hora y resolución en 24 horas los 365 días del año. Este plan es para tienda online muy grandes o para periodicos digitales que por la cantidad de visitas diarias estan sometidos a atques de todo tipo. Un diario digital como el diario.es o el pais deberían tener este plan ,lo digo porque muchos diarios utilizan wordpress porque es ideal para ellos. Si te interesa este plan de Wordfence Response puedes mira toda la información siguiendo este enlace
Como instalar Wordfence
Nos dirigimos a la sección "Plugins" en el escritorio de WordPress, botón "Añadir nuevo" y buscamos Wordfence.
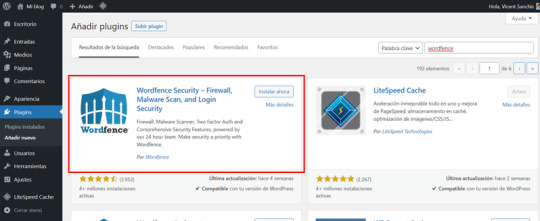
Cuando lo actives, te pedirá la licencia Si ya te has decidido a comprar una licencia pulsa en "Obtén tu licencia de Wordfence" y si la tienes pulsa en instalar una. En la imagen de arriba selecciona la licencia que te interesa o si no pulsa en Download Now para que te den tu licencia gratuita.
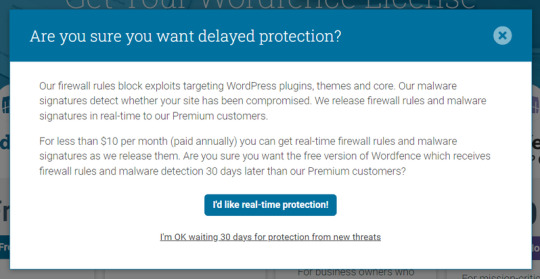
Te recordará que el plan gratuito recibe las actualizaciones del firewall y el malware con un retraso de 30 días. Haz clic en el enlace "I'm OK waiting 30 days for protection from new threats" y, en la siguiente ventana, introduce tu email. A tu dirección de correo electrónico te llegará la clave de la licencia. Puedes instalarla de forma manual o de forma automática, pulsando en el botón "Install My License Automatically"
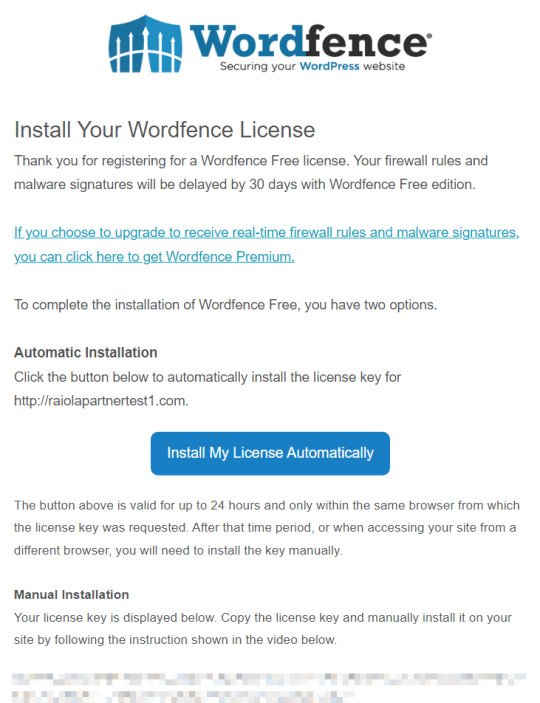
Si lo haces de forma manual, debes volver a tu WordPress y en el menú de la izquierda ir a la sección de Wordfence, instalar y rellenar el formulario. Se confirmará la validez de la licencia y ya puedes acceder al panel de configuración de Wordfence. Voy a crear un vídeo de como se configura de Wordfence y un curso de wordpress asi que suscribiros a mi newsletter para enteraros cuando los publico.
Read the full article
#amenazasdewordpress#ataquesdewordpress#configuraciónwordfence#Protegerwordpress#vulnerabilidadesdewordpress#wordfence#Wordfencecare#wordfencepremium#Wordfenceresponse
0 notes
Text
Provide insights into securing Java web and desktop applications.

Securing Java web and desktop applications requires a combination of best practices, security libraries, and frameworks to prevent vulnerabilities like SQL injection, XSS, CSRF, and unauthorized access. Here’s a deep dive into key security measures:
1. Secure Authentication and Authorization
Use Strong Authentication Mechanisms
Implement OAuth 2.0, OpenID Connect, or SAML for authentication.
Use Spring Security for web applications.
Enforce multi-factor authentication (MFA) for added security.
Example (Spring Security Basic Authentication in Java Web App)java@Configuration @EnableWebSecurity public class SecurityConfig { @Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .authorizeHttpRequests(auth -> auth .requestMatchers("/admin/**").hasRole("ADMIN") .anyRequest().authenticated()) .httpBasic(); return http.build(); } }Implement Role-Based Access Control (RBAC)
Define roles and permissions for users.
Use JWT (JSON Web Tokens) for securing APIs.
Example (Securing API using JWT in Spring Boot)javapublic class JwtUtil { private static final String SECRET_KEY = "secureKey"; public String generateToken(String username) { return Jwts.builder() .setSubject(username) .setIssuedAt(new Date()) .setExpiration(new Date(System.currentTimeMillis() + 1000 * 60 * 60)) .signWith(SignatureAlgorithm.HS256, SECRET_KEY) .compact(); } }
2. Secure Data Storage and Transmission
Use Secure Communication (HTTPS & TLS)
Use TLS 1.2+ for encrypting data in transit.
Enforce HSTS (HTTP Strict Transport Security).
Encrypt Sensitive Data
Store passwords using bcrypt, PBKDF2, or Argon2.
Use AES-256 for encrypting sensitive data.
Example (Hashing Passwords in Java)javaimport org.mindrot.jbcrypt.BCrypt;public class PasswordSecurity { public static String hashPassword(String password) { return BCrypt.hashpw(password, BCrypt.gensalt(12)); } public static boolean verifyPassword(String password, String hashedPassword) { return BCrypt.checkpw(password, hashedPassword); } }
Use Secure Database Connections
Use parameterized queries to prevent SQL injection.
Disable database user permissions that are not required.
Example (Using Prepared Statements in JDBC)javaPreparedStatement stmt = connection.prepareStatement("SELECT * FROM users WHERE username = ?"); stmt.setString(1, username); ResultSet rs = stmt.executeQuery();
3. Protect Against Common Web Vulnerabilities
Prevent SQL Injection
Always use ORM frameworks (Hibernate, JPA) to manage queries securely.
Mitigate Cross-Site Scripting (XSS)
Escape user input in web views using OWASP Java Encoder.
Use Content Security Policy (CSP) headers.
Prevent Cross-Site Request Forgery (CSRF)
Use CSRF tokens in forms.
Enable CSRF protection in Spring Security.
Example (Enabling CSRF Protection in Spring Security)javahttp.csrf().csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse());
4. Secure File Uploads and Deserialization
Validate File Uploads
Restrict allowed file types (e.g., only images, PDFs).
Use virus scanning (e.g., ClamAV).
Example (Checking File Type in Java)javaif (!file.getContentType().equals("application/pdf")) { throw new SecurityException("Invalid file type"); }
Avoid Untrusted Deserialization
Use whitelisting for allowed classes.
Prefer JSON over Java serialization.
Example (Disable Unsafe Object Deserialization in Java)javaObjectInputStream ois = new ObjectInputStream(inputStream) { @Override protected Class<?> resolveClass(ObjectStreamClass desc) throws IOException, ClassNotFoundException { throw new InvalidClassException("Deserialization is not allowed"); } };
5. Secure Desktop Java Applications
Use Code Signing
Sign JAR files using Java Keytool to prevent tampering.
shjarsigner -keystore mykeystore.jks -signedjar SecureApp.jar MyApp.jar myaliasRestrict JavaFX/Swing Application Permissions
Use Java Security Manager (deprecated but useful for legacy apps).
Restrict access to file system, network, and system properties.
Encrypt Local Data Storage
Use AES encryption for storing local files.
Example (Encrypting Files with AES in Java)javaCipher cipher = Cipher.getInstance("AES"); cipher.init(Cipher.ENCRYPT_MODE, new SecretKeySpec(key, "AES")); byte[] encrypted = cipher.doFinal(data);
6. Logging and Monitoring for Security
Use Secure Logging Frameworks
Use logback or SLF4J.
Avoid logging sensitive data like passwords.
Monitor for Anomalies
Implement Intrusion Detection Systems (IDS).
Use audit trails and security alerts.
7. Best Practices for Securing Java Applications
✅ Keep dependencies up to date (Use OWASP Dependency Check). ✅ Run security scans (SAST, DAST) using SonarQube, Checkmarx. ✅ Apply the principle of least privilege for database and API access. ✅ Enforce strong password policies (min length, special characters). ✅ Use API Gateway and rate limiting for public-facing APIs.
Conclusion
Securing Java web and desktop applications requires multi-layered security across authentication, data protection, and vulnerability mitigation. By following best practices like strong encryption, secure coding techniques, and continuous monitoring, developers can protect applications against cyber threats.
WEBSITE: https://www.ficusoft.in/core-java-training-in-chennai/
0 notes
Text
With continuous research and development of internet technology, its reach continues to increase worldwide on a daily basis. One issue that has been causing concern to individuals, as well as the corporate world, is the increasing malware attacks and cyber-security on computers that are connected to the internet. To combat this menace, one solution that is widely-known and effective is online malware scanners. There is plenty anti-virus software available for download, however, we are trying to list the online only scanners. These scanners can help you identify security problems on your computer without downloading and installing the software locally. Based on our research on the web, most of the below-listed software are not comprehensive to fix problems. This software list can help you identify the security issues related to malware, spyware, virus, trojans and worms on a various popular operating system including Windows, Linux, and Mac OSX. The article lists the best online malware scanners. Bit Defender Based on in-the-cloud scanning technology, this online malware scanner, this technology detects the active malware on any computer in a minute. It is due to the fact that the main focus of this scanner is on the active e-threats and the detection process is performed by a remote server. Acunetix Vulnerability Scanner Working as a virtual security officer, this scanner technology scans a comprehensive website that has been integrated with web servers, web applications, and additional perimeter servers for any vulnerability. In addition, this online scanner also enables the viewer to fix it before the attack of the hackers on the weak IT infrastructure. Scan My Server This online malware scanner provides one of the most comprehensive reports of different security tests such as Cross Site Scripting, Blind SQL Injection, HTTP Header Injection, Source Disclosure, PHP Code Injection, SQL and Injection among the others. The site notifies the scan report to the user by email and sends the vulnerability summary. ESET This online malware scanner can be described as a comprehensive malware that detects unknown worms, viruses, phishing, spyware, Trojans and other types of internet threats and removes them effectively from the computers. In addition, it uses various browsers such as opera, Edge, Internet Explorer and Firefox among the others. Trend Micro Housecall This online scanner can be described mainly as on-demand antivirus software that identifies and removes unwanted browser plugins, worms, Trojans and viruses among the other malicious software. Some other features include smart feedback, smart scan, and review and restore files, enhanced scanning and vulnerability scans. SUCURI If you think that your website has been attacked by malware or contains malware in any form, all you have to do is to copy and paste your website URL on this site. The latest fingerprinting technology of this site enables the owner to scan, monitor, and clean up any malware that is the main reason of any malfunctioning. F-Secure Online Scanner If you are facing any malware problem, even if you have already installed a security software, this is the best choice for you. All you have to do is to click your mouse a couple of times and download this software. Completely free software, this online scanner has the capability to remove spyware and virus on the PC. SSL Server Test This is one of the best and free online services that offer a comprehensive analysis of any SSL web server configuration that is on the public internet. This online service uses the information given by the user only for providing the service and does not store it for further use. Quttera With this online malware scanner, the user can protect his website with a blacklisting check, malware detection, site clean-up services among the other tools for a trusted and safe website. This is due to the fact that this online scanner scans the website for phishTank, potentially suspicious files, malware domain list and safe browsing.
Detectify A seamless security service; this online malware scanner seamlessly integrates into the development process of a website and analyze it from the hacker’s perspective. Further, it also offers a comprehensive report about the latest vulnerability findings. Metadefender This online malware scanner offers various types of free online tools for small businesses such as heuristics, anti-malware engines, customized securities policies, and data sanitization tools in order to protect your company from known as well as unknown threats that arise from the internet. SiteGuarding A professional web security solution, the company offers a completely free and professional consultation from the engineers and security experts, and they offer information about how to protect the website from further internet attacks. The team also removes malware in a fast manner and tries to prevent future attacks. Web Inspector It is a fact that any website experiences many attacks on the daily basis, to combat this virus and malware attack, this website offers a regular and daily scanning to check whether there is any malware on the web pages. This step also prevents hackers from the distribution of the virus-infected software to the website visitors or customers. Acunetix From the company servers, this online malware scanner performs a comprehensive network and web security scan for the benefits of the customers. For this performance, the customers do not require to install or download the software. In addition, it provides all details and remains active for an unlimited time period. Asafa Web Now, you can scan your online website at the regular intervals through a daily or weekly scan by this online malware scanning website. The schedule that has been customized by you ensure that you are notified quickly if you are experiencing any issue with the internet virus or malware attack. Virus Total A subsidiary of Google, this website offers a comprehensive free service that analyzes the suspicious URLs and files as well as enables the identification of worms, viruses, Trojans as well as any other type of malicious content. In addition, this service is also used to detect false positives such as malicious content that pose as innocent files. Netsparker Cloud An online web application online malware scanner, this security scanner offers one of the most advanced scanning technologies across the world. This advanced technology includes the only desktop scanner that offers false positive free automated software that is offered to the customers for their benefit. Avira Analysis Of Suspicious Files And URLs This online malware scanner offers a free service that detects the malware and removes it from the file. If this malware is new, they update their signature datable and remove in from the file if it is possible. The site also offers the false positive option, from where you can get the second opinion about any file. UpGuard Web Scan If you want to check your website for any suspected malware attack on an immediate basis, all you have to do is to visit this website and paste your website URL for a comprehensive check-up on a quick basis. Tinfoil Security Investing in the data security is the top priority of any company and this company provides an affordable and comprehensive third-party security solution that thoroughly scans the company website. Further, it also identifies the venerable areas before your company website is hacked by malicious elements. Jotti Virus Scan A free service, the website of this organization enables the user to scan suspicious files with many anti-virus programs. As one time, the user can submit 5 files at one time. However, the size of the file is limited to 50 MB. The organization also shares the results with these anti-virus software companies so that their products should be improved. Nodistribute Malware Scan There are many online scanners in the market who offer free services, but also disturb your privacy by sharing the
results of your websites with the anti-virus software companies, even if it is for making improvement in their products. If you do not want to share the result of your website with anyone, this is the best site for you. ThreatExpert An advanced automated threat analysis system, the ATAS system has been designed for analysis and report the behavior of adware, Trojans, worms, computer viruses, and spyware among the others in an automated mode. FortiGuard If you suspect that you have downloaded a malicious program from the internet or there is a suspect file on your desktop or laptop computer, all you have to do is to visit this website and scan it online. The file would be searched on your computer and the server of the company would make a comprehensive check. You will get a confirmed email as a result to the provided email address. Comodo Cloud Antivirus This software offers various features such as auto-sandbox, virus monitoring, and behavior analysis technologies for the protection of your computer and database from any known or unknown malware from the internet. Free Virus Scan By McAfee An established player in anti-virus software market, this company offers the latest version of the free virus online scanner for the customers who require immediate security solution Panda Security An established company in the anti-virus software, it offers information and free diagnostic tool for the benefit of the customers. Protecting personal, professional or business database from any type of attacks such as the virus, worms or any other types of malicious elements has become an essential part of cyber-security. Hence, choosing an effective and budget-friendly anti-virus software or online malware scanner is quintessential for securing data and operating one's online business without hindrances. Article Updates Article Updated April 2019 : Minor changes, updated introduction section and udpated links.
0 notes
Text
Protección Antivirus Esencial: La Mejor Defensa en la Era Digital En la era digital en la que vivimos, la tecnología es una parte integral de nuestras vidas diarias. Desde la navegación web hasta el almacenamiento de datos personales y financieros, nuestra dependencia de los dispositivos digitales es cada vez mayor. Sin embargo, esta dependencia trae consigo una serie de riesgos y amenazas cibernéticas que pueden tener consecuencias devastadoras si no se abordan adecuadamente. Es aquí donde la protección antivirus juega un papel crucial en la defensa de nuestros dispositivos y datos. ¿Qué es un Antivirus y Para Qué Sirve? Un antivirus es un sistema de seguridad informática diseñado para proteger a las computadoras de posibles ataques de software maliciosos. Estos programas examinan los códigos y scripts que ingresan a tu computador, detectan intenciones maliciosas y detienen cualquier amenaza potencial sin interrumpir tu trabajo[2]. Los antivirus protegen contra una amplia gama de amenazas cibernéticas, incluyendo virus, troyanos, spyware, ransomware y otros tipos de malware. Estas amenazas pueden causar daños significativos a tus dispositivos y datos personales, como la pérdida de información, el robo de identidad y la interrupción del funcionamiento normal de tus equipos[1][3]. Protección Contra Diversas Amenazas Uno de los aspectos más importantes de un antivirus es su capacidad para detectar y eliminar una variedad de malware. Estos programas no solo buscan amenazas conocidas, sino que también emplean tecnologías avanzadas como el aprendizaje automático y la inteligencia artificial para identificar y neutralizar amenazas emergentes y desconocidas. Detección de Malware: Los antivirus escanean tu sistema en busca de amenazas conocidas y realizan un seguimiento del comportamiento de todo el software que se ejecuta, marcando o poniendo en cuarentena actividades sospechosas[5]. Protección en Tiempo Real: Estos programas proporcionan protección en tiempo real, lo que significa que vigilan continuamente tu sistema, comprobando si hay anomalías y emitiendo alertas cuando detectan algo sospechoso[5]. Bloqueo de Sitios Web Maliciosos: Un buen antivirus incluye funciones de filtrado que bloquean el acceso a sitios web maliciosos, reduciendo significativamente el riesgo de ser víctima de un ataque cibernético[1]. Seguridad en la Navegación Web La seguridad en la navegación web es crucial para proteger nuestra información personal y evitar amenazas cibernéticas. Los antivirus modernos incluyen funciones específicas para asegurar una navegación segura: Filtrado de Sitios Web Maliciosos: Al evitar el acceso a sitios web maliciosos, reduces el riesgo de que tu dispositivo se infecte con malware o que se roben tus datos personales[1]. Protección Contra Phishing: El phishing es una técnica utilizada por ciberdelincuentes para engañar a las personas y obtener información confidencial. Un antivirus eficaz puede detectar y bloquear correos electrónicos y sitios web de phishing, protegiéndote de caer en estas trampas[1]. Importancia de las Actualizaciones La actualización constante de las definiciones de virus es vital para estar protegido contra nuevas amenazas. Los virus y el malware evolucionan rápidamente, por lo que un antivirus debe hacer actualizaciones diarias para mantenerse al día con las últimas amenazas. Esto asegura que tu dispositivo esté protegido contra las amenazas más recientes y sofisticadas[2][5]. Optimización del Rendimiento del Sistema Aunque la protección es la prioridad, un buen antivirus también debe optimizar el rendimiento del sistema. Un software antivirus eficiente no debe ralentizar tu dispositivo, permitiéndote trabajar sin interrupciones mientras mantiene tu sistema seguro. Busca un antivirus que ofrezca una interfaz intuitiva y no consuma demasiados recursos del sistema[1][5]. Consejos para Elegir un Antivirus Elegir el antivirus adecuado puede ser un proceso complicado, especialmente con la variedad de opciones disponibles en el mercado.
Aquí hay algunos consejos clave para ayudarte a tomar la mejor decisión: No Te Dejes Llevar por el Precio: Aunque existen antivirus gratuitos, sus funciones suelen ser reducidas. Asegúrate de que la licencia incluya todas las características necesarias para tu protección[2]. Menos es Más: Busca un antivirus que no ocupe mucho espacio y no ralentice el funcionamiento de tus equipos[2]. Tasa de Detección: Presta atención a la tasa de detección de virus. Escoge aquellos que garanticen al menos un 95% de detección[2]. Interfaz Intuitiva: Un antivirus con una interfaz complicada puede ser más un obstáculo que una ayuda. Busca uno que sea fácil de usar[2]. Actualizaciones Diarias: Los virus evolucionan rápidamente, así que un buen antivirus debe hacer actualizaciones diarias[2]. Reputación: Investiga la reputación de la empresa que ofrece el servicio. La reputación es crucial en materia de seguridad informática[2]. Riesgos de No Tener Antivirus No tener un antivirus instalado en tu dispositivo es un riesgo significativo en la era digital. Sin esta protección, estás expuesto a una variedad de amenazas que pueden resultar en la pérdida de datos, el robo de identidad, y la interrupción del funcionamiento normal de tus equipos. Pérdida de Datos: Un ataque de malware puede resultar en la pérdida irreparable de tus datos personales y financieros[2]. Robo de Identidad: Las amenazas cibernéticas pueden permitir a los ciberdelincuentes acceder a tu información personal, lo que puede llevar al robo de identidad[1]. Interrupción del Funcionamiento: Un ataque de malware puede interrumpir el funcionamiento normal de tus equipos, causando retrasos y pérdidas productivas[2]. Ciberseguridad en una Era Conectada En un mundo cada vez más conectado, la ciberseguridad es más importante que nunca. La protección antivirus es solo una parte de un sistema de seguridad integral. Es esencial trabajar en capas, utilizando diversas herramientas de seguridad informática para atacar a las amenazas cibernéticas desde diferentes frentes. Firewalls: Controlan el acceso de una computadora a la red y viceversa, adicionando una capa extra de seguridad[2]. Certificado SSL: Establece relaciones seguras entre los navegadores y los servidores, protegiendo la información en tránsito[2]. Doble Verificación: Un proceso que implica dos medios diferentes para que un mismo usuario identifique su identidad, aumentando la seguridad de acceso[2]. Conclusión En resumen, en la era digital en la que vivimos, contar con un antivirus no es solo una opción, sino una necesidad fundamental. Los antivirus nos protegen de una amplia gama de amenazas cibernéticas, como virus, malware y ransomware, que pueden causar daños significativos a nuestros dispositivos y datos personales. Además, ayudan a mantener la seguridad durante la navegación web y a proteger nuestra información personal y financiera. No subestimes la importancia de un buen antivirus; es una inversión en tu seguridad y tranquilidad. Al elegir el antivirus adecuado y seguir los consejos para su implementación, puedes asegurarte de que tu mundo digital esté protegido de las amenazas cibernéticas que acechan en cada esquina de la web. #Ciberseguridad #Antivirus #ProteccionDigital #SeguridadInformatica #Malware #Ransomware #Phishing #NavegacionSegura #ProteccionDeDatos #SeguridadEnLaEraDigital #HerramientasDeSeguridad #Firewalls #CertificadoSSL #DobleVerificacion #ActualizacionesDeSeguridad #SoftwareAntivirus #TecnologiasDeSeguridad #AmenazasCiberneticas #ProteccionDeIdentidad #RoboDeIdentidad #PérdidaDeDatos #InterrupcionDelFuncionamiento #SeguridadDeEndpoints #Ciberataques #DelitoCibernético https://rafaeladigital.com/noticias/proteccion-antivirus-defensa-era-digital/?feed_id=6477
0 notes
Text
Interview with Caru Basakatua ("Indetectables" Script Contest 2020)
Translation of a Spanish interview by Apoyo Positivo.
«What is and what is not madness? How cishetpatriarchal are the standards that define good and bad? What is madness and what is sanity?»
INDETECTABLES keeps growing as a project and as a series, and we are in the middle of the promotion and presentation of our third season PATRIARCADO (Patriarchy), while advancing in the production of LOCURA (Madness), our fourth season.
After SEXO, DROGAS Y TÚ (Sex, Drugs, and You) and ESTIGMA (Stigma), these latest two seasons come with a twist in the themesthat aims to address the needs, principles, values, and philosophies of Apoyo Positivo and all the communities we work with. HIV—the initial protagonist of the series and tip of the iceberg of all these stories—gives way to the elements that explain why HIV it’s not just a virus, but also the top of a system of stigmas about people (second season) that empowers a norm that it’s not explicit but it’s enforced: the patriarchy (third season).
Some have asked why are we talking about feminism on the series or why we are suddenly tackling mental health, given that our origins are rooted in HIV awareness. Well, we as an organization existing in this system of identities and social entities, must be a bit non-binary. We hold the idea that diversity and all its vulnerabilities must be tackled jointly.
While we keep showing you more about PATRIARCADO, we have found someone who explains the interconnections between the seasons of our series very well, the winner of the script contest for LOCURA: Caru Basakatua. As part of the season production, we organized a contest for short films and scripts that brought creativity and diversity to the project. Here you can read about Caru’s experiences and how they perceive and understand our series.
Enjoy the read, and in March … more INDETECTABLES!

We chat with Caru Basakatua, author of the winning script of the web series contest INDETECTABLES, titled “Desviación Típica” (Standard Deviation). Caru introduces themself as a “bilingual, queer, and Madrilenian writer interested in stories that explore and celebrate queer and non-normative experiences and identities, and that got a PhD just to be able to use "Dr." and never again have to choose between "Mr." and "Ms."
How did you come up with the idea for the script?
It’s a funny story: I write with my partner and we are working in several projects, all of them about queer themes and gender. And one of our collaborators—our sensitivity reader, David Orión Pena—told us about the contest. I met him years ago in a course about trans issues, and he is also a writer, an editor, and podcast producer. He sent me a text with the link to the contest, and I said to myself, let’s do it! Although honestly, I had no idea what to write about. When my partner and I went for a walk and started talking about different possibilities, the idea came up quite quickly, and the script was written in a couple of days.
The story starts in a place described as somber. Is it based on your own experience or friends’ experiences?
Everything on the script is a combination of my own experiences transitioning—I’m a transmasculine non-binary person—and friends’ experiences. It’s a combination of those experiences—including those of people I befriended on social media, where they share their horror stories about going to the endocrinologist, the psychiatrist, the psychologist … And also, one of the ideas was to really show the process of transitioning, which people talk a lot about while knowing very little, and how it can be very humiliating sometimes.
Currently, there is a lot of talk about trans people and transitioning, but not with the people who transition, about their experiences trying to navigate a system that is extremely binary and based on cishetpatriarchal stereotypes and roles.
And then, reading the contest guidelines, I found really interesting that the theme of the season was madness: What is and what is not madness, how cishetpatriarchal are the standards that define good and bad, what is considered madness and what is considered sanity, and all that.
There is a stark contrast between the actions described on the script, between what the doctor says and what the protagonist thinks. What did you want to express through those contrasts?
First of all, that the pathologization of trans identities is problematic by itself, basically because you are treating trans and non-binary people as minors, as if they don’t know what they do and do not want. This person, who knows more about you than yourself, has to come to tell you what you are or what you aren’t, or if you are sufficiently what you say you are. And also related to that, I wanted to show how gender stereotypes are applied to trans and non-binary people in a much more intense and cruel way than to cis people.
It’s basically a trap. To be able to access what you need as a trans or non-binary person—whether that means just hormones, hormones and surgery, or simply changing your legal gender—you have to fulfill these imposed requirements that are based in extremely backwards ideas of gender.
If you are a transmasculine person and have long hair, they are going to ask you why is you hair so long. And something else that is in the script and is a real thing: the underwear. They will snoop into the kind of underwear you use, when that does not depend exclusively on your gender. Imagine that you are a young person living with a family that doesn’t accept you or don’t know yet that you are trans, of course they are not going to buy you boxers! A lot of times is not about what you do, but what you can do in your context.
So, all those stereotypes are imposed on trans people in extreme and ridiculous ways. Especially on trans women, I would say, even more than on trans men. Trans women have to be hyperfeminine to be believed when they say that they are women. And then at the same time, some groups use that to attack them, saying that trans women are reinforcing gender roles and that wearing a skirt doesn’t make you a woman.
It’s a loop: if you fulfill the stereotypes you are reinforcing them, but if you don’t fulfill them you are not trans enough. So trans people find themselves in a particularly bad situation.
In the script we have a non-binary person thinking about what stereotypes they will have to abide by to be able to access the treatment they want, highlighting the gaps in the system. That’s something I wanted to show about the process, how humiliating it can be, how intrusive. For example, the issue of sexuality. If you are a transmasculine person, you have to be active, and very macho, and you have to like certain things. And if you are a transfemenine person then you have to be passive and it’s like … seriously?
These are things that are not asked of cis people. Nobody is going to approach a woman on the street with a short, Audrey Hepburn-style haircut, and say “Hey, maybe you are not cis because your hair is short.” I wanted to talk about all that in the story.
There are other, more positive moments in the script, shown through flashbacks. How did those moments come up?
That’s another thing I wanted to show: being trans is more than just dysphoria and suffering, it also has moments of euphoria, of feeling good with yourself, like when the protagonist is with their partner, or wearing their badges in their clothes and all that. Being trans is not being miserable all the time and then you have access to transition and you are happy forever. No, it’s like life is for everyone, you have your good moments and your bad moments. I also wanted to show that regarding gender.
The theme of madness is outlined from the very setting of the story: the “Unidad de Transtornos de la Identidad del Género” (Gender Identity Disorders Unit). What is your opinion on the name of this place?
It’s interesting that you ask that, because I have a PhD in Psychology. Psychology is a very fragmented discipline—despite what people think—and there are still many who may consider gender dissidence as a disorder. But I would say that is a minority whose vision is more similar to the psychiatric point of view than the psychological point of view. In my opinion, the pathologization of trans identities or trans dissidence is harmful because, yes, they are basically telling you that you are mentally ill. When you arrive, the first thing they do is take you to the psychiatrist and then to the psychologist, and it’s like, “Okay! I get the message.” But then, there is the additional issue of treating the person as if they were dysfunctional, as if they were unable to make their own decisions because they have this “problem”. I’m here to help you and tell you what’s best for you. That takes agency away from trans people and invalidates them—in that, telling them that what they feel or what they are is not normal, is not in line with the standards and therefore must be an illness. That’s basically the message you get.
And that can lead to problems like depression and anxiety, right?
Obviously. And that’s also interesting. The problems that trans people usually have: depression, anxiety, suicide attempts, eating disorders—that I also wanted to include on the script—have less to do with being trans or non-binary and more with being trans or non-binary in the cishetpatriarchal system. A system in which you are cisgender and heterosexual by default, until proven otherwise, and in which you are always going to be a weirdo, and exception, an outlier, and where you will have to deal with rejection and violence. That’s the origin of the problems, it’s not about being trans, it’s about being trans in this system.
What are your future plans after winning the contest and what are the odds of producing it?
My partner and I work on this, basically. My goal is to create the stories that I would have loved to see or that I want to see now in media, in film, series … the references that I lacked growing up. I’m thirty-two years old and started questioning my gender well into my twenties. I’d have liked to have references as a kid: people questioning their gender, not only binary trans people, but also non-binary people and queer people in general. Maybe I’d have realized earlier why some things felt the way they felt.
We have several projects going on, some quite advanced, and the plan is to bring to life those kinds of stories, especially for queer people, but also for non-queer people. To give them access to our world beyond the stereotypes written from cishet perspectives about our community. Recently I was watching a video about LGTBIQ+ bars and clubs in the South of the US and one person said “all that is made about us, without us, is not for us”. And that’s what I want: things made by us, about us, and for us. And, I don’t know, I think it is very necessary to put this kind of perspective and these kinds of stories out there.
As the winner of the best script award, how would you encourage other people to go ahead and tell their stories or express themselves thought film or art?
I think art is necessary—whether writing, painting, music, short stories, poetry, illustration, whatever the medium. Art is necessary in the world, especially to communicate perspectives that are non-normative. It’s probably the best way, as it has a special ability to transmit emotions and experiences, to reach people and connect with them. And I think that all the stories and all the experiences are valuable in some sense. If you have something to say, if you have something to tell, go ahead! I think that putting your story out there, telling your story, will make the world a better place.

DESVIACIÓN TÍPICA (STANDARD DEVIATION): SYNOPSIS
What happens when you are "abnormal" even by the standards of "abnormal"? When you can't even be "abnormal" in the right way, according to the labels available? And when your life depends on pretending that you are "abnormal", but in the right way?
River is a non-binary person, forced to navigate an extremely binary system. A system that reaches its greatest expression in the “units of gender identity disorders” (UTIG), where the imposition of cisheteropatriarchal gender roles is taken to absurd heights, where life-saving treatments are approved or denied based on hair length, type of underwear, or the way of having sex.
Images by Apoyo Positivo.
0 notes