#Windows 10 redirect to file handle is invalid
Explore tagged Tumblr posts
Text
Windows 10 redirect to file handle is invalid

#WINDOWS 10 REDIRECT TO FILE HANDLE IS INVALID CODE#
(": Bad Request: Can't parse message text: Can't find end of the entity starting at byte offset 140", 400) Would you do that? I appreciate your help. I am sure you encounter those more than I ever do. But I need you to give me a list of possible errors and their error code. Your suggestion of adding subclasses to TelegramError is a good one. But, because situations giving rise to BadHTTPResponse are very limited and you can already distinguish them as described above, I would hold that off for now. I could add a redirect history to BadHTTPResponse to help you differentiate. Server down would give you a BadHTTPResponse of status 502, as detailed in Issue #31.A bad token causes a redirect to and the resulting BadHTTPResponse has a status of 200.Although it is reasonable to expect Bot API to not redirect, one can never say it should not redirect.Īn easy way to differentiate between a bad token and server down is this: I will not add a RedirectOutOfApiSubdomain (or something like that) because, in my opinion, requesters to a web service should be blind to redirects and only interpret answers as they are sent back. Expect something like this in the upcoming version: Yet, I understand the frustration of not knowing what is going on because the clue is buried under 27 kB of HTML, so I have decided to override the method _str_() and _unicode_() to give you a better view of the situation. 😄 I know it is far-fetched, but it is imaginable. Your suggestion of not following redirects is reasonable, but as the author of telepot, I have to weigh it against the risk of: what if, suddenly, Telegram uses redirects to handle Bot API requests? Telepot will fail "catastrophically", all for the occasional benefit of not "burying an exception under 27 kB of HTML". My main reluctance stems from the fact that there is simply no official token format declared by Telegram. Yes, it is easy to discern from existing tokens, but there is no evidence that it will stay the same. I will not provide a regex validation of token, because I am just not sure what the format is, and what it might become in the future.
#WINDOWS 10 REDIRECT TO FILE HANDLE IS INVALID CODE#
I should add that i also agree that we shouldn't just replace BadHTTPResponse with an invalid token exception, but we can narrow it down by specifying a 302 code (not a failure, which is the most likely cause for a badhttpresponse) that redirects to the specific address (not on the official api subdomain which bot should not operate outside of it). also i have never come across an actual use of redirect in any of api calls, so maybe you could stop following the redirects ?Īs you can see the main html before redirect is relatively short, one of my problems was that i didn't even see the BadHTTPResponse error because it was buried under 27kb of html in the console.Īnother possibility would be some sort of regex based validation, either as part of telepot.Bot constructor or as a separate helper method, there should be some logic behind what telegram considers a valid token and an invalid one, a valid but wrong token will respond with a valid json response with code 401 Unauthorized In the end, I choose to opt for correctness, and keep the BadHTTPResponse as is.Ī redirect and a non-json response are not exactly the same thing, maybe you could associate a 302 code, or more specifically a 302 redirect to which is a completely different subdomain than the api to an invalid token. Bot API's response to an invalid token is unspecified. What if, one day, a BadHTTPResponse is caused by something other than an invalid token? After all, it is Telegram who decides when to re-direct to a web page. I could try to suggest the possible cause in the BadHTTPResponse, but it would only end up with the same dilemma. However, in practice, a non-JSON response almost certainly means an invalid token.In terms of correctness, I should not assume a non-JSON response to mean an invalid token.How could I distinguish between a BadHTTPResponse that is caused by an invalid token and one that is not? I cannot. In this case, a BadHTTPResponse would happen but it is not due to an invalid token. Let's say, sometime in the future, Telegram may decide that when the servers are down, all Bot API requests be re-directed to a web page. However, this is not guaranteed.Īs of now, when Telegram servers are down, Bot API would return a JSON object indicating a bad gateway. The only instance where I have seen (and can imagine) a BadHTTPResponse is when the token is invalid. The question is this: when the response is not a JSON object, is it necessarily because the token is invalid? Could there be other causes?Īt this moment, I cannot think of any other causes. If the response is not a JSON object, it raises a BadHTTPResponse. The logic is this: a request to Bot API expects a JSON object in return.

0 notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
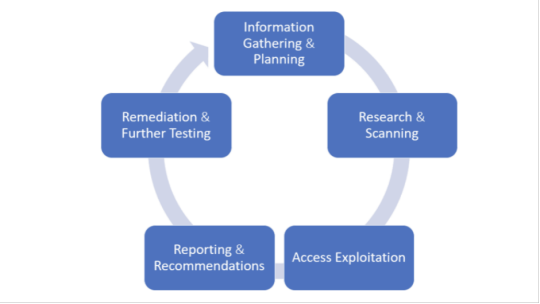
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
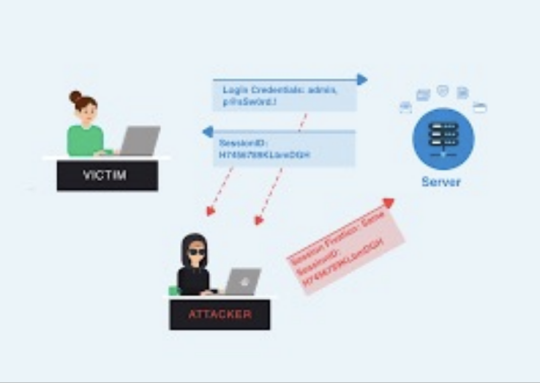
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
300+ TOP Express JS Interview Questions and Answers
Express JS Interview Questions for freshers experienced :-
1. What is ExpressJs? Express Js is a framework for node.js which is light-weight and fast. It is used to develop web and mobile applications. 2. What are the features of ExpressJs? Following are the features of Expressjs: It allows middleware set up to respond HTTP Requests It defines routing table which is used to achieve action based on HTTP Method and URL. It allows dynamically generate the HTML Pages based on passing arguments to the templates. It follows MVC architecture for web application. 3. What is middleware in ExpressJs? Middleware is a function that accesses the request object (req), response object (res), and access next middleware function in application’s request-response cycle. The next middleware function is represented by variable called ‘next’. Syntax: function(req,res,next){ } 4. Can middleware is able for error handling? Explain error handling in ExpressJs. Middleware is able to handle error handling in ExpressJs. This can be done by passing one extra error-handling (err) parameter in middleware function. Syntax: function(err,req,res,next){ } 5. What is ‘next’ in ExpressJs? ‘next’ is a parameter which is passed in middleware function to pass control to next middleware. function(req,res,next){ } 6. What is routing? Routing define how an application responds over client request to a particular endpoint (URI). Endpoint is specially a path and any one of HTTP request methods (GET, POST, etc). Following structure is used for routing: app.METHOD(PATH,HANDLER) Note: METHOD is Http request method (in lowercase), PATH is uri on server, HANDLER is function name. 7. How to configure properties in ExpressJs application? We can configure properties in two ways: With Process.env. Create a file with extension ‘.env’ inside the project folder. Add all the properties in ‘.env’ file. In server.js any of properties can use: var host=process.env.APP_HOST; app.set('host',host); logger.info(app.get('host'); With RequireJs. Create a file 'config.json' inside 'config' folder of the project folder. Add config properties in 'config.json' file. Use require keyword to access the 'config.json' file. var config =require('./config/config.json'); 8. How debugging are done in ExpressJs? Different operating system uses different commands: Windows: set DEBUG = express:* & node index.js Linux: $ DEBUG = express:* & node index.js 9. Define templating in ExpressJs? Templating are powerful engine used for removing the cluttering of our server code with HTML. Some of the templates which are with ExpressJs are: Pug Mustache EJS 10. What is cookie and what it does? Cookie is a data sent from server and stores on the client side. It keeps the information of user’s actions. These are some following purpose of using cookie: Session management User tracking Personalization 11. How to use cookies in ExpressJs? Cookies are used in ExpressJs by installing ‘cookie-parser’ middleware. To install cookie-parser we use command as: npm install --save cookie-parser To set new cookie in our application, we define a new route. app.get('/',function(req, res){ res.cookie('name','express').send('cookie set') }); 12. How to delete cookie in ExpressJs? The clearCookie method is used to delete cookies in ExpressJs. clearCookie('cookie_name'); app.get('/clear_cookie_temp',function(req,res)){ clearCookie('temp'); res.send('cookie temp is cleared'); }); 13. How to handle 404 errors or redirect error to another page? We use the following code in server.js file to redirect 404 errors to another page in ExpressJs. app.use(function(req, res, next){ res.status(404).json({errorCode: 404, errorMessage: requested resources not foundâ€}); }); 14. What is scaffolding? Scaffolding is a tool, which set up all required public directory, add middleware, create separate route file etc (set up skeleton for web application). So that we can directly get started building our application. Yeoman is scaffolding tool built for Node.js. 15. How to get the full url In ExpressJs? var port = req.app.settings.port || cfg.port; res.locals.requested_url = req.protocol + '://' + req.host + ( port == 80 || port == 443 ? '' : ':'+port ) + req.path; 16. How do i render plain html? There’s no need to “render” HTML with the res.render() function. If you have a specific file, use the res.sendFile() function. If you are serving many assets from a directory, use the express.static() middleware function. 17. How to implement jwt authentication in express app ? Explain with example? Create a folder called ‘keys’ inside project folder. Install some dependencies as following: Npm install jsonwebtoken –save Add the login router routes/index.js router.post('/login, function(req, res) { // find the user User.findOne({ name: req.body.username }, function(err, res) { if (err) throw err; if (!res) { res.json({ success: false, message: Login failed.' }); } else if (res) { // check if password matches if (res.password != req.body.password) { res.json({ success: false, message: Login failed. Wrong password.' }); } else { var token = jwt.sign(res, app.get('superSecret'), { expiresInMinutes: 1600 }); // return the information including token as JSON res.json({ success: true, message: 'Valid token!', token: token }); } } }); }); Use the token in application jwt = require("express-jwt"); app.use(function(req, res, next) { var token = req.body.token || req.query.token || req.headers; if (token) { jwt.verify(token, app.get('superSecret'), function(err, decoded) { if (err) { return res.json({ success: false, message: 'Invalid token.' }); } else { req.decoded = decoded; next(); } }); } else { return res.status(403).send({ success: false, message: 'No token given.' }); } }); Express JS Questions and Answers Pdf Download Read the full article
0 notes
Text
Microsoft Patch Tuesday – March 2017
Following a sparse February patch Tuesday, today’s March release brings a bumper crop of fixed vulnerabilities: 17 bulletins covering 140 different vulnerabilities, 47 of which are rated as critical. The critical vulnerabilities affect Internet Explorer, Edge, Hyper-V, Windows PDF Library, Microsoft SMB Server, Uniscribe, Microsoft Graphics Component, Adobe Flash Player and Microsoft Windows. 92 vulnerabilities are rated as important, additionally affecting Active Directory Federation Services, DirectShow, Internet Information Services, Microsoft Exchange Server, Microsoft Office, Microsoft XML Core Services, Windows DVD Maker, Windows Kernel, Windows Kernel-Mode Drivers.
Bulletins Rated Critical
MS17-006, MS17-007, MS17-008, MS17-009, MS17-010, MS17-011, MS17-012, MS17-013 and MS17-023 are rated critical. MS17-006 is this month's Internet Explorer bulletin. Within the 6 critical Internet Explorer vulnerabilities, 3 relate to remote code execution vulnerabilities due to how browsers handle objects in memory. One of these, CVE-2017-0149 is actively being exploited in the wild. 2 critical vulnerabilities can be exploited to execute remote code due to the way that JScript and VBScript render when handling objects in memory. Although the remaining critical vulnerability doesn’t allow code execution itself, it can be exploited in conjunction with a code execution vulnerability to execute code with higher privileges than shoallinauld be permitted. 4 further vulnerabilities are rated as important, relating to vulnerabilities that can be exploited to disclose information from memory or disk. The last 2 important vulnerabilities relate to incorrect parsing of HTTP headers which potentially allow an attacker to redirect a victim to a malicious website. These 2 vulnerabilities, CVE-2017-0012 and CVE-2017-033 are also found in Edge, and included in the bulletin MS17-007. MS17-007 is concerned with vulnerabilities in Edge, describing 20 rated as critical and 10 as important. 15 of these critical vulnerabilities relate to issues in how scripting engines render when handling objects in memory, potentially allowing attackers to execute arbitrary code on affected systems. The critical vulnerability CVE-2017-0037 is shared with Internet Explorer, allowing an attacker to execute arbitrary code through a memory corruption vulnerability. Three further vulnerabilities exist in how Edge accesses objects in memory which can also be abused to execute arbitrary code, two of these are rated as critical. One critical vulnerability relates to the MS Windows PDF library where viewing a website containing malicious PDF content can cause remote code execution. This vulnerability is described in more detail in MS17-009. A further memory corruption vulnerability unique to Edge CVE-2017-0034, allows arbitrary code to be executed in the context of the user. 5 important vulnerabilities potentially allow an attack to discover information from memory. 3 vulnerabilities relating to incorrect parsing of HTTP headers are rated as important, 2 of these are shared with Internet Explorer and also addressed in MS17-006. Vulnerabilities in the incorrect application of the same origin policy for html elements account for 2 important and one moderate listings. Finally, one scripting engine memory corruption vulnerability is rated as important, distinct from the other critical vulnerabilities in the same system. 11 vulnerabilities in Windows Hyper-V are addressed in MS17-008, only 3 of which are related as critical. One of these is a vulnerability due to how Hyper-V on a server fails to properly validate vSMB packet data. An attacker within a virtual machine, could exploit this vulnerability to execute arbitrary code on the host. An additional vulnerability also related to validating vSMB packets exists, but is rated as important. Two critical vulnerabilities relate to how the host system validates input from authenticated users on a guest operating system potentially allowing an attacker to execute arbitrary code on the host. Six important fixes for denial of service vulnerabilities, and one important fix for a memory disclosure vulnerability are also included. MS17-010 addresses 6 vulnerabilities in Windows SMB Server. 5 critical vulnerabilities can be exploited by an attacker sending a malicious packet to a SMBv1 server to result in remote code execution. A further important vulnerability can be exploited by sending a malicious packed to a SMBv1 server to cause information from the server to be disclosed. Microsoft Uniscribe is a series of services used in the rendering of Unicode characters. MS17-011 addresses 29 vulnerabilities in Uniscribe, of which 8 are rated as critical, the remainder as important. The critical vulnerabilities allow an attacker to take full control of a system by hosting malicious content on a website that the victim is tricked into visiting, or by enticing a victim into opening a specially crafted malicious file. The vulnerabilities rated as important, can be exploited in the same way, but result in the disclosure of memory contents to the attacker. The MS17-012 bulletin fixes 5 important vulnerabilities, and a single critical vulnerability. The critical vulnerability is in the Internet Storage Name Service (iSNS) server service which fails to properly validate client input. This potentially allows an attacker to run arbitrary code in the context of the SYSTEM account on an affected system. The important vulnerabilities are in Device Guard which permits an attacker to modify a PowerShell script without invalidating the file signature; a denial of service vulnerability in SMBv2 and SMBv3; and a remote code execution vulnerability in loading certain DLL files. Microsoft Windows Graphics Component is used by a number of different programs including Microsoft Office and Silverlight. MS17-013 describes 2 critical and 10 important vulnerabilities in the component. The critical vulnerabilities result in remote code execution when exploited by either tricking a victim into visiting a website hosting malicious content, or getting a victim to open a malicious file. The important vulnerabilities exist in how Windows Graphics Device Interface handles objects in memory, allowing a local user to execute code in kernel mode, a remote user to discover memory contents, or help in bypassing address space layout randomization (ASLR) protection. Patch Tuesday is never complete without an Adobe Flash Player bulletin, and MS17-023 delivers by addressing the critical vulnerabilities otherwise described in Adobe Security Bulletin APSB17-07. This update resolves a series of remote code execution vulnerabilities in Adobe Flash Player. If you can’t patch, or remove Adobe Flash Player, the bulletin describes a number of workarounds to prevent Flash Player from executing.
Bulletins Rated Important
MS17-014, MS17-015, MS17-016, MS17-017, MS17-018, MS17-019, MS17-020, MS17-021, and MS17-022 are rated important. Although MS17-014 addresses 12 vulnerabilities in Microsoft Office, not a single one of the vulnerabilities is classed as critical, nevertheless all are important. 7 of these allow an attacker to execute arbitrary code in the context of the local user with the aid of a user opening a malicious document or visiting a malicious content hosting website. Further vulnerabilities permit an attacker to perform a denial of service attack against Microsoft Office, disclose memory contents, facilitate cross site scripting (XSS), and tamper with trusted communications through an improperly validated certificate. MS17-015 and MS17-016 describe single vulnerabilities, both rated as important in Microsoft Exchange Outlook Web Access and Microsoft IIS Server respectively. The Outlook Web Access vulnerability allows an attacker to perform content injection attacks via a victim clicking a malicious link in an email or in a chat client. The IIS Server vulnerability allows an attacker to perform a cross site scripting attack (XSS) and run scripts in the context of the current user; again a victim must click a malicious link for the attack to succeed. MS17-017 and MS17-018 address 12 important vulnerabilities in Windows Kernel and Windows Kernel-Mode Drivers. These vulnerabilities allow a locally authenticated user or a user with local access to improperly escalate their privileges. Bulletins MS17-019, MS17-020, MS17-021, MS17-022 relate to single important vulnerabilities in Active Directory Federation Services, Windows DVD Maker, Direct Show and XML Core Services. This series of vulnerabilities allow attackers to gather information from the affected system. In the case of Windows DVD Maker the attacker must be locally authenticated to trigger the exploit. The latter two vulnerabilities require the victim to visit a malicious website before they can be exploited.
Coverage
In response to these bulletin disclosures, Talos is releasing the following rules to address these vulnerabilities. Please note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your Management Center or Snort.org. Snort SIDs: 41549-41556, 41561-41598, 41601-41602, 41605-41610, 41633-41634, 41763-41764, 41926-41961, 41964-41998
from Microsoft Patch Tuesday – March 2017
0 notes