#XSS Scanning
Explore tagged Tumblr posts
Text
How to Protect Your Laravel App from JWT Attacks: A Complete Guide
Introduction: Understanding JWT Attacks in Laravel
JSON Web Tokens (JWT) have become a popular method for securely transmitting information between parties. However, like any other security feature, they are vulnerable to specific attacks if not properly implemented. Laravel, a powerful PHP framework, is widely used for building secure applications, but developers must ensure their JWT implementation is robust to avoid security breaches.

In this blog post, we will explore common JWT attacks in Laravel and how to protect your application from these vulnerabilities. We'll also demonstrate how you can use our Website Vulnerability Scanner to assess your application for potential vulnerabilities.
Common JWT Attacks in Laravel
JWT is widely used for authentication purposes, but several attacks can compromise its integrity. Some of the most common JWT attacks include:
JWT Signature Forgery: Attackers can forge JWT tokens by modifying the payload and signing them with weak or compromised secret keys.
JWT Token Brute-Force: Attackers can attempt to brute-force the secret key used to sign the JWT tokens.
JWT Token Replay: Attackers can capture and replay JWT tokens to gain unauthorized access to protected resources.
JWT Weak Algorithms: Using weak signing algorithms, such as HS256, can make it easier for attackers to manipulate the tokens.
Mitigating JWT Attacks in Laravel
1. Use Strong Signing Algorithms
Ensure that you use strong signing algorithms like RS256 or ES256 instead of weak algorithms like HS256. Laravel's jwt-auth package allows you to configure the algorithm used to sign JWT tokens.
Example:
// config/jwt.php 'algorithms' => [ 'RS256' => \Tymon\JWTAuth\Providers\JWT\Provider::class, ],
This configuration will ensure that the JWT is signed using the RSA algorithm, which is more secure than the default HS256 algorithm.
2. Implement Token Expiry and Refresh
A common issue with JWT tokens is that they often lack expiration. Ensure that your JWT tokens have an expiry time to reduce the impact of token theft.
Example:
// config/jwt.php 'ttl' => 3600, // Set token expiry time to 1 hour
In addition to setting expiry times, implement a refresh token mechanism to allow users to obtain a new JWT when their current token expires.
3. Validate Tokens Properly
Proper token validation is essential to ensure that JWT tokens are authentic and have not been tampered with. Use Laravel’s built-in functions to validate the JWT and ensure it is not expired.
Example:
use Tymon\JWTAuth\Facades\JWTAuth; public function authenticate(Request $request) { try { // Validate JWT token JWTAuth::parseToken()->authenticate(); } catch (\Tymon\JWTAuth\Exceptions\JWTException $e) { return response()->json(['error' => 'Token is invalid or expired'], 401); } }
This code will catch any JWT exceptions and return an appropriate error message to the user if the token is invalid or expired.
4. Secure JWT Storage
Always store JWT tokens in secure locations, such as in HTTP-only cookies or secure local storage. This minimizes the risk of token theft via XSS attacks.
Example (using HTTP-only cookies):
// Setting JWT token in HTTP-only cookie $response->cookie('token', $token, $expirationTime, '/', null, true, true);
Testing Your JWT Security with Our Free Website Security Checker
Ensuring that your Laravel application is free from vulnerabilities requires ongoing testing. Our free Website Security Scanner helps identify common vulnerabilities, including JWT-related issues, in your website or application.
To check your site for JWT-related vulnerabilities, simply visit our tool and input your URL. The tool will scan for issues like weak algorithms, insecure token storage, and expired tokens.

Screenshot of the free tools webpage where you can access security assessment tools.
Example of a Vulnerability Assessment Report
Once the scan is completed, you will receive a detailed vulnerability assessment report to check Website Vulnerability. Here's an example of what the report might look like after checking for JWT security vulnerabilities.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By addressing these vulnerabilities, you can significantly reduce the risk of JWT-related attacks in your Laravel application.
Conclusion: Securing Your Laravel Application from JWT Attacks
Securing JWT tokens in your Laravel application is essential to protect user data and maintain the integrity of your authentication system. By following the steps outlined in this post, including using strong algorithms, implementing token expiry, and validating tokens properly, you can safeguard your app from common JWT attacks.
Additionally, make sure to regularly test your application for vulnerabilities using tools like our Website Security Checker. It’s a proactive approach that ensures your Laravel application remains secure against JWT attacks.
For more security tips and detailed guides, visit our Pentest Testing Corp.
2 notes
·
View notes
Text
Hackers Exploiting LiteSpeed Cache Plugin Flaw to Hijack WordPress Sites

Cybercriminals are actively exploiting a high-severity vulnerability in the widely-used LiteSpeed Cache plugin for WordPress to take over websites, according to researchers at WPScan. The vulnerability, tracked as CVE-2023-40000 with a CVSS score of 8.3, is an improper input neutralization flaw that allows stored cross-site scripting (XSS) attacks. LiteSpeed Cache for WordPress (LSCWP) is an all-in-one site acceleration plugin with over 5 million active installations. It features server-level caching and various optimization capabilities. However, the recently disclosed vulnerability enables unauthenticated attackers to escalate privileges and create rogue admin accounts named "wpsupp‑user" and "wp‑configuser" on vulnerable sites. Once the malicious actors gain administrative access, they have complete control over the compromised WordPress website. Patchstack originally discovered the stored XSS vulnerability in February 2024, which can be triggered through specially crafted HTTP requests.
Surge in Exploitation Attempts Detected
WPScan reported a significant spike in access attempts to a malicious URL on April 2nd and April 27th, likely indicating widespread exploitation efforts. The researchers identified two prominent IP addresses involved in scanning for vulnerable sites: 94.102.51.144 with 1,232,810 requests, and 31.43.191.220 with 70,472 requests. The vulnerability was addressed by LiteSpeed Technologies in October 2023 with the release of version 5.7.0.1. However, unpatched sites remain at risk of compromise. WPScan has provided indicators of compromise (IoCs) for these attacks, including malicious URLs like https//dnsstartservicefounds.com/service/fphp, https//apistartservicefoundscom, and https//cachecloudswiftcdncom. Additionally, users should watch out for the IP address 45.150.67.235, which has been associated with the malware campaign.
Urgent Patching Recommended
WordPress site owners and administrators are strongly advised to update their LiteSpeed Cache plugin to the latest patched version as soon as possible to mitigate the risk of exploitation and potential website takeover. Read the full article
2 notes
·
View notes
Text
How Web Development Companies Handle Website Penetration Testing
Cybersecurity is no longer an afterthought—it’s a frontline concern. With rising threats like data breaches, ransomware, and unauthorized access, businesses must ensure their websites are not just functional but secure. That’s where penetration testing (pen testing) comes in.
A trusted Web Development Company doesn’t stop at building beautiful or high-performing websites—they also take proactive steps to test, identify, and fix vulnerabilities before they can be exploited. Penetration testing is one of the most critical layers in this process.
But what does it involve? And how do web development agencies approach it with precision and care?
What Is Website Penetration Testing?
Penetration testing is a simulated cyberattack on your website or web application. It’s performed by ethical hackers or security professionals who attempt to exploit vulnerabilities just like a real attacker would—but with permission and control.
The goal is to:
Identify security flaws before hackers do
Test the effectiveness of your security layers
Understand how deep an attacker could go
Provide detailed insights for patching weak points
Pen testing is typically done after development is complete but before deployment—or periodically as part of a maintenance cycle.
Why Is Pen Testing Important for Businesses?
Your website often stores or handles sensitive data—customer information, login credentials, payment records, business logic, and more. Any gap in security can be devastating.
Here’s why businesses should prioritize penetration testing:
Reputation Protection: A breach can destroy trust.
Regulatory Compliance: Industries like finance, healthcare, and eCommerce must meet specific security standards.
Cost Avoidance: Fixing a breach is far more expensive than preventing one.
Peace of Mind: You know where you stand before going live.
That’s why experienced web development companies integrate security audits and pen testing into their delivery cycle.
How Web Development Companies Conduct Penetration Testing
Penetration testing isn’t a one-size-fits-all process. Here's how professional agencies typically handle it:
1. Scoping and Planning
Before any testing begins, the team defines the scope:
Which applications, domains, or subdomains are in-scope?
Should third-party integrations be tested?
What kind of data does the system handle?
They also decide between black-box testing (with no internal knowledge), white-box testing (with full access), or gray-box testing (partial knowledge)—depending on the business goals.
2. Information Gathering
Next, the team gathers data on the target system, such as:
Public-facing IPs and domains
Site architecture and tech stack
API endpoints and known user roles
This reconnaissance phase helps simulate real-world attacks using publicly available data.
3. Vulnerability Scanning
Before diving into manual attacks, automated tools are used to scan for:
Outdated libraries and plugins
Open ports or misconfigurations
Common vulnerabilities like XSS, CSRF, and SQL injection
Tools like Burp Suite, OWASP ZAP, or Nessus help flag potential weak points.
4. Manual Testing and Exploitation
This is where ethical hackers step in to simulate real attack scenarios:
Attempting to bypass authentication or gain admin access
Exploiting injection flaws or misconfigured APIs
Accessing sensitive files or user data
Breaking out of limited permissions to gain system-wide access
Unlike automated scans, manual testing adds human intuition to detect flaws hidden beneath the surface.
5. Reporting and Recommendations
After the test, the development team compiles a detailed report outlining:
Vulnerabilities discovered
Severity levels (low, medium, high, critical)
Exploitation steps
Screenshots or logs as evidence
Recommendations for patching and prevention
This report becomes the foundation for security hardening and prioritization.
6. Remediation and Retesting
Once the issues are addressed, the team conducts retesting to ensure the patches work and didn’t introduce new vulnerabilities. This final step closes the loop and confirms that your website is secure before going live—or staying live with confidence.
Conclusion
Website penetration testing isn’t just a checklist item—it’s a strategic necessity in today’s digital world. By proactively simulating attacks, companies can discover and fix vulnerabilities before they become real threats.
Working with a Web Development Company that takes security seriously means your website isn’t just built to look good and function well—it’s designed to be resilient, protected, and trusted. Whether you're launching a new product or scaling an existing platform, investing in penetration testing is one of the smartest moves you can make for long-term stability and success.
0 notes
Text
Secure Software Development: Protecting Apps in the USA, Netherlands, and Germany

In today’s digital landscape, where cyber threats are evolving rapidly, secure software development is critical for businesses across the globe. Companies in the USA, Netherlands, and Germany are increasingly prioritizing security to protect their applications and user data. By leveraging custom software development services, organizations can build robust, secure applications tailored to their needs while adhering to regional regulations and industry standards. This blog explores key strategies for secure software development and highlights best practices for safeguarding apps in these tech-forward regions.
Why Secure Software Development Matters
The rise in cyberattacks—such as data breaches, ransomware, and phishing—has made security a top priority for developers. In the USA, high-profile breaches have pushed companies to adopt stringent security measures. In the Netherlands, a hub for tech innovation, businesses face pressure to comply with GDPR and other EU regulations. Similarly, Germany’s strong emphasis on data privacy drives demand for secure development practices. Without a security-first approach, applications risk vulnerabilities that can lead to financial losses and reputational damage.
Key Strategies for Secure Software Development
1. Adopt a Security-First Mindset
Secure software development begins with embedding security into every phase of the development lifecycle. This includes:
Threat Modeling: Identify potential risks early, such as SQL injection or cross-site scripting (XSS), during the design phase.
Secure Coding Standards: Follow guidelines like OWASP’s Secure Coding Practices to minimize vulnerabilities.
Regular Training: Equip developers with up-to-date knowledge on emerging threats, tailored to regional concerns like GDPR compliance in the Netherlands.
For example, Dutch companies often integrate GDPR requirements into their threat models, while US-based firms may focus on compliance with standards like SOC 2.
2. Implement Robust Testing Practices
Testing is critical to identify and fix vulnerabilities before deployment. Key testing methods include:
Static Application Security Testing (SAST): Analyze source code for vulnerabilities during development.
Dynamic Application Security Testing (DAST): Test running applications to uncover runtime issues.
Penetration Testing: Simulate real-world attacks to evaluate app resilience.
In Germany, where data protection laws are stringent, companies often conduct rigorous penetration testing to ensure compliance with the Federal Data Protection Act (BDSG).
3. Leverage Encryption and Authentication
Protecting data in transit and at rest is non-negotiable. Use:
End-to-End Encryption: Safeguard sensitive data, such as user credentials or payment information.
Multi-Factor Authentication (MFA): Add an extra layer of security to prevent unauthorized access.
Secure APIs: Validate and sanitize inputs to protect against API-based attacks.
US companies, especially in fintech, prioritize encryption to meet standards like PCI DSS, while Dutch firms focus on secure APIs to support their thriving e-commerce sector.
4. Stay Compliant with Regional Regulations
Each region has unique compliance requirements:
USA: Adhere to standards like HIPAA for healthcare apps or CCPA for consumer data privacy.
Netherlands: Comply with GDPR, which mandates strict data handling and user consent protocols.
Germany: Follow GDPR and BDSG, emphasizing data minimization and user rights.
Integrating compliance into the development process ensures apps meet legal and industry standards, reducing the risk of penalties.
5. Embrace DevSecOps
DevSecOps integrates security into DevOps workflows, enabling continuous security monitoring. Key practices include:
Automated Security Scans: Use tools like Snyk or Checkmarx to detect vulnerabilities in real-time.
Continuous Monitoring: Track app performance post-deployment to identify suspicious activity.
Collaboration: Foster communication between development, security, and operations teams.
This approach is particularly popular in the Netherlands, where tech companies use DevSecOps to accelerate secure app delivery.
Regional Insights: Tailoring Security Practices
USA: With a diverse tech ecosystem, US developers focus on scalable security solutions. Cloud-based security tools and AI-driven threat detection are widely adopted, especially in Silicon Valley.
Netherlands: As a leader in digital infrastructure, Dutch firms emphasize privacy-by-design principles, aligning with GDPR. Rotterdam and Amsterdam-based startups often integrate security into agile workflows.
Germany: Known for precision, German companies prioritize thorough documentation and compliance. Munich’s tech scene leverages advanced encryption to protect industrial IoT applications.
Conclusion
Secure software development is no longer optional—it’s a necessity. By adopting a security-first mindset, implementing robust testing, leveraging encryption, ensuring compliance, and embracing DevSecOps, businesses in the USA, Netherlands, and Germany can protect their applications from evolving threats. Partnering with a trusted software development company ensures access to expertise and tailored solutions, empowering organizations to build secure, reliable, and compliant apps that drive success in today’s competitive markets.
#software development company#software development services#software development services company#custom software development services
0 notes
Text
An Overview of Burp Suite: Acquisition, Features, Utilisation, Community Engagement, and Alternatives.
Introduction:
Burp Suite is one of the strongest web application security testing software tools used by cybersecurity experts, as well as ethical hackers. PortSwigger created Burp Suite, which provides potent scanning, crawling, and exploiting tools for web application vulnerabilities.
What is Burp Suite?
Burp Suite is one of the tools to conduct security testing of web applications. It assists security testers in detecting vulnerabilities and weaknesses like SQL injections, XSS, CSRF, etc.
Steps in Obtaining Burp Suite
Burp Suite is available for download on the PortSwigger official website. It is available in three versions:
Community Edition (Free)
Professional Edition (Subscription-Based)
Enterprise Edition (For Organisations)
Important Tools in Burp Suite
Proxy – Captures browser traffic
Spider – Crawls web application content
Scanner – Scans automatically for vulnerabilities (Pro only)
Intruder – Performs automated attack activities.
Repeater – Manually send requests.
Decoder – Translates encoded data.
Comparer – Compares HTTP requests/responses
Extender – Allows extensions through the BApp Store
How to Use Burp Suite
Set your browser to use Burp Proxy.
Capture and manipulate HTTP/S requests.
Utilise tools such as Repeater and Intruder for testing.
Scan server responses for risks.
Export reports for audit purposes.
Burp Suite Community
Burp Suite has a highly engaged worldwide user base of security experts. PortSwigger Forum and GitHub repositories have discussions, plugins, and tutorials. Many experts are contributing through YouTube, blogs, and courses.
Alternatives to Burp Suite
If you're searching for alternatives, then look at:
OWASP ZAP (Open Source)
Acunetix
Netsparker
Nikto
Wfuzz
Conclusion:
Burp Suite is widely used for web application security testing. Mastery of Burp Suite is one step towards web application security for both novice and professional ethical hackers.

#BurpSuite#CyberSecurity#EthicalHacking#PenTesting#BugBounty#InfoSec#WebSecurity#SecurityTools#AppSec#OWASP#HackingTools#TechTools#WhiteHatHacker#CyberTools#BurpSuiteCommunity#NetworkSecurity#PortSwigger#WebAppTesting#SecurityScanner#CyberAwareness
0 notes
Text
Detect Vulnerabilities Faster With Website Scanner
Website scanners play a crucial role in accelerating the detection of security vulnerabilities within web applications. AI-driven vulnerability management and pentesting solution, automate the entire scanning process, starting with mapping the website’s structure, including URLs, forms, scripts, and third-party components. They then simulate real-world attack techniques using predefined test cases, heuristics, and vulnerability databases to identify issues such as SQL injection, cross-site scripting (XSS), CSRF, insecure configurations, and outdated components.
0 notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
Screenshot of the free tools webpage where you can access security assessment tools.
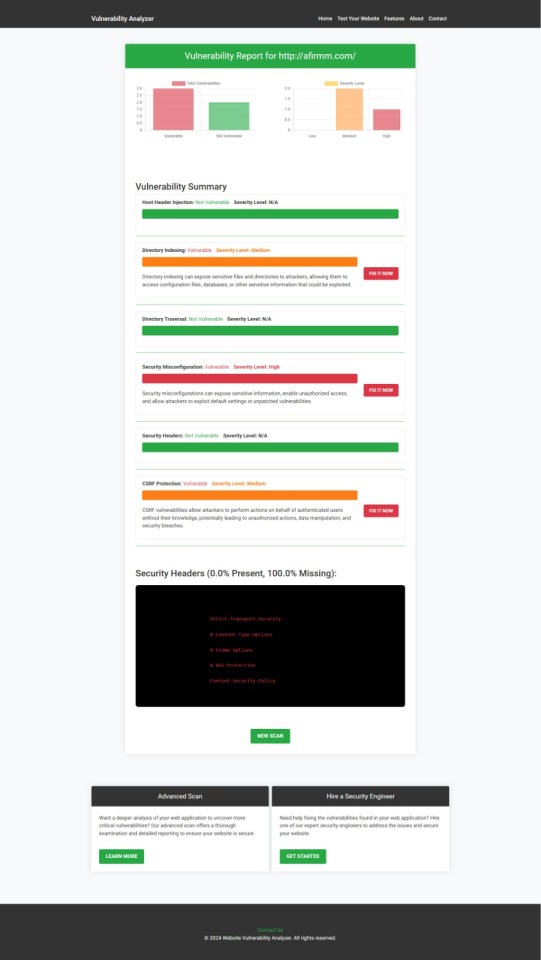
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
From Beginner to Pro: The 5 Best Ethical Hacking Books to Read In an era where cybersecurity threats are increasing daily, ethical hackers play a crucial role in safeguarding digital systems. If you're an aspiring ethical hacker, reading the right books can provide the foundation you need to build strong hacking and penetration testing skills. We've curated a list of the 5 best books for ethical hacking, offering everything from beginner-friendly concepts to advanced hacking techniques. Whether you're new to cybersecurity or looking to sharpen your hacking skills, these books will set you on the right path. 1. Ethical Hacking: A Hands-on Introduction to Breaking In Author: Daniel Graham Level: Beginner to Intermediate This book is a perfect starting point for ethical hacking enthusiasts. It provides practical hands-on lessons in penetration testing, guiding you through real-world hacking scenarios. Key Highlights: ✅ Step-by-step guidance on penetration testing ✅ Learn to break into computers and networks ethically ✅ Covers fundamental hacking techniques and tools If you’re looking to get started with ethical hacking and understand the mindset of a hacker, this book is a great investment. 2. Gray Hat Hacking: The Ethical Hacker's Handbook Authors: Allen Harper, Daniel Regalado, and others Level: Intermediate to Advanced "Gray Hat Hacking" is one of the most comprehensive books on ethical hacking. It goes beyond the basics, introducing advanced security tools, reverse engineering, and fuzzing techniques. Key Highlights: ✅ In-depth coverage of zero-day vulnerabilities ✅ Learn binary scanning and advanced exploitation techniques ✅ Covers topics such as malware analysis and vulnerability discovery If you want to go beyond beginner-level hacking and explore advanced cybersecurity concepts, this book is a must-read. 3. Learn Ethical Hacking from Scratch Author: Zaid Sabih Level: Beginner This book is one of the best beginner-friendly ethical hacking books available. It takes you from zero to hero, covering ethical hacking concepts, penetration testing techniques, and using Kali Linux. Key Highlights: ✅ Covers basic to intermediate ethical hacking techniques ✅ Hands-on practical exercises using real-world examples ✅ Teaches penetration testing using Kali Linux If you want to learn ethical hacking from scratch and gain hands-on experience, this book is an excellent choice. 4. Hacking: The Art of Exploitation Author: Jon Erickson Level: Intermediate Unlike other books that focus only on penetration testing, this book goes deep into the core principles of hacking and exploitation techniques. It includes a Linux programming crash course, making it a perfect read for aspiring hackers who want to understand the fundamentals of cybersecurity. Key Highlights: ✅ Deep dive into exploitation techniques and vulnerabilities ✅ Learn how programs and network security actually work ✅ Covers buffer overflows, cryptography, and shellcode writing If you're interested in learning how exploits work under the hood, this book is a must-read. 5. The Web Application Hacker’s Handbook Authors: Dafydd Stuttard & Marcus Pinto Level: Intermediate to Advanced With web applications being a prime target for hackers, this book focuses on web security and penetration testing techniques. It’s an essential read for ethical hackers who want to specialize in web security testing. Key Highlights: ✅ Covers SQL injection, XSS, CSRF, and other web attacks ✅ Learn how to test web applications for security flaws ✅ A must-read for bug bounty hunters and penetration testers If you're aiming to become a web security expert, this book will help you master web application penetration testing. Conclusion Ethical hacking is a rapidly growing field, and reading the right books can give you a competitive edge. Whether you're just starting or looking to specialize in advanced penetration testing techniques, these books will provide valuable insights.
💡 Pro Tip: Combine your reading with hands-on practice in virtual labs like Hack The Box, TryHackMe, and Kali Linux to build real-world experience! Which book are you planning to read first? Let us know in the comments! 🚀
0 notes
Text
Web Application Penetration Testing
Web apps are everywhere — handling logins, payments, sensitive data, APIs, you name it. And that makes them juicy targets for attackers. That’s where Web Application Penetration Testing comes in.
It’s all about testing your web app the way a real attacker would. Ethical hackers dig into the application, looking for vulnerabilities like SQL injection, XSS, broken authentication, logic flaws, insecure APIs, and more. But this isn’t just button-click scanning — it’s deep, manual, creative work. Real humans manually explore your app’s behavior, its endpoints, its logic — and look for ways to break it.
1 note
·
View note
Text
Some common mistakes to avoid in web development.
In the life of a developer, avoiding common pitfalls can save hours, enhance the User experience and let the website be successful. Below are the most common mistakes website developers should avoid, as well as possible solutions.
Ignoring mobile responsiveness
Mistake : A developer build the site to look great mainly on desktop but it is clunky and unusable on mobile devices. It may affect with web traffic, because over 60% web traffic coming from mobile.
Solution : Go with a mobile first design approach. We can use CSS frameworks such as bootstrap and tailwind CSS ; test on several devices and leverage tool like Google'S mobile friendly test to ensure mobile responsiveness.
Ignoring page load speed
Mistake : Heavy website with big images, unoptimiszd code, too many scripts, all cause the site to load slowly. In latest studies find that 53% of users leave the site because that take more than 3 seconds to load.
Solution : Optimize images, minimise your CSS or JavaScript; enable browser caching. Tool like lighthouse, or GT metrix will tell you what exactly is causing the trouble.
Poor SEO practices
Mistake : Overlooking in meta tags, atl text or proper URL structure will affect your search engine rankings.
Solution : Use semantic HTML, good meta description, optimise for your keywords, and ensure fast load time. You can also audit your site with the helpful tools such as Yoast SEO or Screaming frog.
Overcomplicating design
Mistake : Overstocking the site with the animation, fonts, and colours ; this will confuses the potential users and direct their attention away from the messages.
Solution : Go with minimal and cleaner layout with the confluency in typography, and a colour palette single to the concept. Consider the UX above everything else with the clear navigation.
Not testing cross- Browser compatibility
Mistake : Assuming a website works flawlessly on every Browser without testing. Minor difference in rendering under Chrome, firefox, Safari etc might kill the functionality.
Solution : Make a test on major browsers via browser stack or Lambda test software. Add vendor prefixes to your CSS and make sure that combine them with the feature detection in your Java Script code.
Weak security practices
Mistake : Ignoring securities measures make the site vulnerable to attacks like SQL injection ,XSS, or data branches. In 2025 cyber security are a top concern.
Solution : Use HTTPS, keep software always up to date and implement secure authentication methods. Regularly scan your application with a security scanner such as OWASP ZAP.
Not prioritizing user feedback
Mistake : The reason of ustability issues or missed opportunities, launching a site without gathering or acting on user feedback.
Solution : Before launch conduct a user testing. Use heatmaps to track behaviour. A/B testing can refine features.
Avoid these mistakes with planning, testing, and staying updated with web development trends. And also leverage model tools and communities to stay informed about best practices.
If you are looking for more advanced strategies, it’s smart to work with an experienced agency. Hollyminds Technologies is a great choice ,we make websites that are perfectly coded and structured to stand the test of time.The algorithms are set to bring visitors from across the globe. A structured website with right content, can bring more visitors to your business.
1 note
·
View note
Text
8 Common Techniques You Must Know to Create Secure Websites
Did you know that over 30,000 websites are hacked every day? In this era of digitization, website security is of utmost importance. The sophistication of cyberattacks is growing daily, and one incident can cause serious financial loss, legal consequences, and loss of brand reputation. Installing advanced security measures not only keeps your data secure but also builds trust among your customers. Let’s explore the 8 Common Techniques You Must Know to Create Secure Websites.
Enforce HTTPS using SSL/TLS Certificates
Switching from HTTP to HTTPS is a cornerstone of website security. HTTPS encrypts information passed between your site and any user’s browser, protecting it from interception and tampering. A certificate for SSL/TLS is necessary for this encryption, guaranteeing sensitive data, such as login credentials and financial information, stays private. In addition to security, HTTPS builds consumer trust. Browsers frequently symbolize this in a padlock icon, while also being beneficial in regard to your site’s ranking in search engines. Purchasing and installing an SSL certificate is now easier than ever, with various hosting services offering them for free or for minimal fees. Updating and renewing them periodically maintains constant protection.
Keep Software and Dependencies Up to Date
Outdated software is an easy mark for hackers. They take advantage of known vulnerabilities in content management systems (CMS), plug-ins, themes, and other website elements. Keeping them updated regularly ensures security fixes are deployed in a timely fashion, sealing potential holes for hackers. Even automation, when available, can simplify this for you and minimize human error. Be sure, however, to verify that upgrades won’t interfere with your current configuration. Case Study: The Equifax breach (2017) happened because of an unpatched vulnerability in Apache Struts, affecting 147 million people.
Implement Strict Password Guidelines and Two-Factor Authentication (2FA)
A Password is usually the first point of security against unauthorized use. Enforcing tight password policies requiring a combination of uppercase and lowercase letters, numbers, and special characters can discourage brute-force attacks. Instruct users against using easily guessable passwords and have them update them regularly. Reducing password use by supplementing it with Two-Factor Authentication (2FA) adds another layer of security. 2FA asks customers to identify themselves using a second process, for instance, a code sent to their mobile phone, which complicates unauthorized use tremendously.
Perform Regular Security Audits and Vulnerability Assessments
Taking the lead in finding and fixing security weaknesses is vital. Regular security audits mean carefully checking your website’s infrastructure, codebase, and configurations to spot any risks. Automated tools can help catch common problems, but a hands-on review gives you a clearer picture. Once you identify those risks, focus on the most critical ones and resolve them quickly. Doing these checks consistently not only boosts your website’s security but also shows users you’re serious about protecting their information.
Implement Web Application Firewalls (WAF)
A Web Application Firewall serves as a shield for your website against incoming traffic. It scans, filters, and blocks unwanted data packets from reaching your server. A WAF protects against an array of attacks, ranging from SQL injections to XSS and Distributed Denial of Service (DDoS) attacks. A WAF can identify and prevent suspicious activity in real time by monitoring HTTP requests. You can implement a WAF at the server level or through cloud services, depending on your website requirements. Example: In 2020, GitHub survived a 1.3 Tbps DDoS attack thanks to its WAF and traffic filtering.
Backing Up Regularly
Data loss can be caused by different factors, such as hacking, hardware breakdowns, or user errors. Backing up your website at regular intervals guarantees that you can recover it in its last state in case data loss occurs. Use automatic backup solutions, which keep duplicates in safe, off-site locations. Periodically check your backups for integrity and validate that restoration works properly. A sturdy backup plan reduces downtime and data loss, safeguarding revenue and reputation.
Secure User Input and Prevent SQL Injection
Validate User Input and Prevent SQL Injection. Input forms, like contact forms or search bars, can also be used to inject harmful code if not properly secured. SQL injection is a common attack in which harmful SQL code is injected into input forms to modify your database. Prevent this by validating and sanitising user input. Use prepared statements and parameterized queries, which ensure user input is used as data and not as code. Including such measures secures your database against unauthorized use and data compromise.
Apply Content Security Policy (CSP)
A Content Security Policy is one of the security standards designed to thwart cross-site scripting (XSS) attacks by dictating which dynamic assets can load on your site. By setting trusted origins for scripts, style sheets, and other content, CSP prevents malicious scripts injected by attackers from running. Configuring your web server to include the right Content-Security-Policy HTTP header implements CSP. Periodically checking and revising your CSP affirms that it’s still effective against new threats.
Final Thoughts:
By integrating these eight practices in your website development and upkeep, its security stance is greatly improved. In addition to these, developing a culture of security among your staff and users further strengthens your defenses. Continual training of stakeholders in regard to possible threats and safe data handling creates an overall effort towards continuous security within an online setting. Website security is an evolving process, and vigilance, flexibility, and proactivity in anticipating upcoming threats in this respect are necessary.
0 notes
Text
Security Penetration Testing for Web Applications

In today’s digital-first world, web applications are the backbone of businesses, enabling seamless customer interactions, e-commerce, and internal operations. However, with the rise in cyber threats, ensuring the security of these applications is no longer optional—it’s critical. At Global Techno Solutions, we specialize in fortifying web applications through comprehensive security penetration testing, a proactive approach to identifying and mitigating vulnerabilities before they can be exploited. This blog dives into the importance of penetration testing and highlights a real-world case study to showcase its impact.
Why Security Penetration Testing Matters
Web applications are prime targets for cybercriminals due to their accessibility and the sensitive data they often handle, such as user credentials, payment details, and proprietary business information. A single vulnerability can lead to devastating consequences, including data breaches, financial losses, and reputational damage. Security penetration testing simulates real-world cyberattacks in a controlled environment to uncover weaknesses in your application’s defenses. By identifying vulnerabilities like SQL injection, cross-site scripting (XSS), or insecure authentication mechanisms, businesses can address issues before malicious actors exploit them.
Penetration testing offers several key benefits:
Proactive Risk Mitigation: Identify and fix vulnerabilities before they become entry points for attackers.
Compliance Assurance: Meet industry standards like PCI DSS, GDPR, or HIPAA, which often mandate regular security assessments.
Customer Trust: Demonstrate a commitment to safeguarding user data, enhancing brand credibility.
Cost Savings: Preventing a breach is far less expensive than recovering from one.
At Global Techno Solutions, our penetration testing services combine automated tools and manual techniques to deliver thorough, actionable insights tailored to your web application’s unique architecture.
Case Study: Securing a Web Application for a Global E-Commerce Platform
To illustrate the power of penetration testing, let’s explore a real-world example from our portfolio. In our case study, Security Penetration Testing for Web Applications, we partnered with a leading e-commerce platform facing growing concerns about cyber threats. With millions of users and sensitive financial data at stake, the client needed to ensure their web application was secure against sophisticated attacks.
The Challenge
The e-commerce platform had a complex web application with multiple user roles, payment gateways, and third-party integrations. Recent industry breaches raised alarms, and the client wanted to proactively assess their security posture to protect customer data and maintain compliance with PCI DSS regulations. Key challenges included:
Identifying vulnerabilities in a dynamic, frequently updated application.
Ensuring minimal disruption to live operations during testing.
Providing actionable remediation strategies within a tight timeline.
Our Approach
Global Techno Solutions deployed a structured penetration testing methodology based on industry standards like OWASP Top 10 and NIST. Our process included:
Reconnaissance: Gathering intelligence about the application’s structure, technologies, and potential entry points.
Vulnerability Scanning: Using advanced tools to detect common vulnerabilities like XSS, SQL injection, and insecure configurations.
Exploitation: Simulating real-world attacks to assess the impact of identified vulnerabilities.
Reporting: Delivering a detailed report with prioritized recommendations for remediation.
Retesting: Validating fixes to ensure vulnerabilities were fully addressed.
Our team employed a gray-box testing approach, combining limited insider knowledge with external attack simulations to mimic both outsider and insider threats. Tools like Burp Suite, OWASP ZAP, and custom scripts were used alongside manual testing to uncover complex vulnerabilities that automated scans might miss.
The Results
The penetration test revealed several critical vulnerabilities, including:
Cross-Site Scripting (XSS): Malicious scripts could be injected to steal user sessions or redirect users to phishing sites.
Insecure API Endpoints: Exposed APIs lacked proper authentication, risking unauthorized access to sensitive data.
Weak Input Validation: Insufficient sanitization allowed potential SQL injection attacks.
Our team provided a comprehensive remediation plan, including code-level fixes, configuration changes, and enhanced monitoring. After implementing our recommendations, the client’s application achieved a robust security posture, passing their PCI DSS audit with flying colors. The project was completed within two weeks, with zero disruption to live operations.
0 notes
Text
How Automated Testing Enhances Cloud Security and Compliance in Modern Deployments
In today’s fast-paced digital world, businesses are increasingly migrating to the cloud to scale their operations and leverage the power of modern technologies. However, with this shift comes the challenge of maintaining security and compliance in a constantly evolving environment. As cloud environments grow more complex, automated testing has become an essential tool in ensuring that security protocols and compliance standards are met throughout the entire deployment lifecycle.
At Salzen Cloud, we recognize the importance of integrating automated testing into cloud-based workflows to enhance security and streamline compliance. In this article, we’ll explore how automated testing improves cloud security and ensures compliance in modern deployments.
1. The Growing Importance of Cloud Security and Compliance
As organizations migrate their critical applications and sensitive data to the cloud, security and compliance have become top priorities. In fact, any lapse in security or failure to meet regulatory standards can result in:
Data breaches that expose sensitive customer information
Heavy fines for non-compliance with industry regulations (e.g., GDPR, HIPAA, SOC 2)
Reputation damage and loss of customer trust
To safeguard against these risks, companies must implement robust security and compliance strategies throughout the entire lifecycle of their cloud applications. This is where automated testing comes into play. Automated testing tools can help detect vulnerabilities, enforce security policies, and ensure that applications are continuously compliant with evolving standards.
2. Automated Testing for Cloud Security: Benefits and Best Practices
Automated testing is the process of using software tools to run predefined tests on cloud applications without human intervention. These tests are designed to detect defects, vulnerabilities, or issues that could compromise the security of the system. Here’s how automated testing contributes to cloud security:
1. Continuous Vulnerability Scanning
Cloud applications are constantly exposed to threats, and vulnerabilities can emerge at any stage of the deployment process. Automated security testing tools can continuously scan cloud environments for potential security flaws such as:
SQL injection attacks
Cross-site scripting (XSS) vulnerabilities
Misconfigurations in security settings
By automating these scans, businesses can ensure that security risks are identified and mitigated in real-time, rather than waiting for manual reviews or after the deployment is complete.
2. Early Detection of Security Issues
The earlier security issues are identified, the easier and less costly they are to fix. Automated testing allows for continuous integration and continuous deployment (CI/CD) pipelines, where security tests can be integrated at each stage of the development process. This means that vulnerabilities are caught early on, before they make it to production. Some common security tests include:
Static Application Security Testing (SAST): Analyzing the source code for vulnerabilities.
Dynamic Application Security Testing (DAST): Testing running applications to identify security weaknesses.
Penetration Testing: Simulating attacks to evaluate the effectiveness of security measures.
By incorporating these tests into your CI/CD pipeline, automated testing helps to ensure that security is an ongoing priority throughout development and deployment.
3. Security Regression Testing
As cloud environments are updated and new features are deployed, it’s important to check that existing security measures haven’t been compromised. Automated security regression testing ensures that new changes don’t unintentionally introduce vulnerabilities, preserving the integrity of security protocols across updates.
3. How Automated Testing Supports Cloud Compliance
Regulatory compliance is a critical concern for businesses operating in industries such as healthcare, finance, and e-commerce. Regulatory standards like GDPR, HIPAA, PCI-DSS, and SOC 2 set strict requirements on how companies must handle and protect customer data.
Automated testing simplifies the process of ensuring compliance by continuously verifying that cloud applications adhere to these requirements. Here’s how it works:
1. Continuous Monitoring for Compliance Requirements
Many compliance regulations require specific monitoring and logging of user access, data storage, and activity within cloud environments. Automated testing tools can continuously monitor these activities to ensure compliance. They can automatically check that:
Sensitive data is encrypted both in transit and at rest.
User access controls are properly enforced, ensuring that only authorized personnel can access certain data or applications.
Audit logs are generated and stored in accordance with compliance regulations.
By automating these compliance checks, businesses can ensure that they stay compliant without having to manually track every activity.
2. Automating Compliance Audits
One of the most time-consuming tasks in maintaining compliance is preparing for audits. Automated testing tools can streamline the audit process by automatically generating reports that document the security and compliance status of cloud applications. These reports provide detailed insights into:
Data protection practices
Security configurations
Access controls
Third-party vendor assessments
Automated compliance audits not only save time but also ensure that organizations are consistently adhering to industry standards and regulations.
3. Reducing Human Error in Compliance Processes
Manual processes are prone to error, and with the complexity of cloud environments, human oversight can lead to critical compliance gaps. Automated testing eliminates this risk by ensuring that compliance checks are performed systematically and consistently across every deployment cycle.
4. Best Practices for Integrating Automated Testing into Cloud Security and Compliance
To maximize the benefits of automated testing in cloud security and compliance, organizations should follow these best practices:
Integrate Automated Tests Early: Start running automated security and compliance tests as early as possible in the development lifecycle to identify vulnerabilities and compliance gaps before they make it to production.
Leverage a Variety of Testing Tools: Use a combination of automated testing tools, such as static analysis, dynamic analysis, and penetration testing, to ensure comprehensive coverage of both security and compliance requirements.
Establish Regular Testing Cadence: Regularly test cloud applications even after they’ve been deployed to catch any new vulnerabilities or compliance issues that may arise from updates, configuration changes, or third-party integrations.
Track and Report Test Results: Maintain a clear record of test results and compliance statuses. This documentation will not only help in continuous improvement but also provide evidence during audits.
5. Conclusion: Strengthening Cloud Security and Compliance with Automated Testing
Automated testing plays a pivotal role in ensuring that cloud applications remain secure and compliant throughout their lifecycle. By integrating automated testing into your cloud deployment pipeline, you can proactively identify vulnerabilities, continuously monitor compliance, and mitigate the risks associated with cloud security and regulatory standards.
At Salzen Cloud, we understand the importance of cloud security and compliance, and we leverage automated testing to help businesses stay ahead of potential risks and regulatory changes. By embracing automation, companies can enhance their cloud security posture, ensure compliance, and ultimately drive more reliable, scalable, and secure cloud deployments.
Are you ready to strengthen your cloud security and compliance strategy with automated testing? Contact Salzen Cloud today to learn how our cloud solutions can protect your business from threats and keep you compliant with industry standards.
0 notes
Text
Secure Your Web Apps — Expert Auditing That Leaves No Weak Spot Behind
In today’s digital-first world, your web application is often the first interaction customers have with your brand. But with that exposure comes risk. Cyber attackers are constantly evolving, targeting even the smallest vulnerabilities in web apps to steal data, hijack sessions, or disrupt services.
That’s where web application security auditing steps in — your first and strongest line of defense.
An expert audit dives deep into your app’s code, architecture, and logic to uncover the threats hidden beneath the surface. We’re not just talking about common bugs — we’re talking about real-world flaws that hackers actively exploit: SQL injection, XSS, broken authentication, and more.
Whether you're a startup or an enterprise, leaving your app unchecked is like leaving the doors unlocked on your busiest day.
At eShield IT Services, our auditing process is thorough, precise, and tailored. We don’t just scan and report — we test, validate, and guide you through remediation. The result? A hardened, resilient application ready to withstand modern threats.
Don’t wait for a breach to expose your weak spots. Secure your web app now — from code to cloud — with auditing that’s built to protect and empower.
To know more click here :- https://eshielditservices.com
0 notes
Text
How to Choose the Right Software Testing Service Provider?

Delivering high-performing, secure, and bug-free software is no longer optional—it's a business necessity. Whether you're launching a mobile app, enterprise platform, or cloud-native solution, ensuring the quality of your product requires rigorous testing. But with a wide array of vendors offering software testing services, selecting the right partner can be overwhelming.
This guide by Robotico Digital walks you through the essential criteria for choosing a reliable software testing service provider that aligns with your technical requirements and business goals.
1. Understand Your Testing Requirements
Before reaching out to vendors, you need a clear understanding of what you’re looking for. Start by defining:
l Project scope and scale (e.g., web app, mobile app, API, enterprise software)
l Type of testing required – functional, performance, security, usability, automation, etc.
l In-house vs. outsourced testing
l Compliance or regulatory needs (e.g., ISO, GDPR, HIPAA)
A well-defined requirement list will help filter providers based on their core competencies and industry experience.
2. Assess the Provider’s Expertise in Software Testing Services
When evaluating potential software testing service providers, one of the most important criteria is their hands-on experience and depth of expertise. Software testing is not just about identifying bugs—it's about ensuring your application performs optimally across various environments, user scenarios, and technical architectures. Therefore, assessing a provider’s capability in delivering comprehensive and scalable software testing services is crucial.
Manual and Automated Testing
A reliable testing partner should be proficient in both manual and automated testing approaches. Manual testing remains essential for exploratory, usability, and ad-hoc testing scenarios where human intuition plays a key role. However, as development cycles become shorter and more iterative, automation becomes indispensable. Automated testing helps run repetitive test cases efficiently and ensures quick feedback loops. A competent provider should have experience using popular frameworks like Selenium, Appium, TestNG, JUnit, and Cypress, and they should be capable of building reusable, maintainable automated test suites.
Cross-Browser and Cross-Device Testing
With the growing diversity of user devices and browsers, it’s essential to ensure that your software functions seamlessly across platforms. This includes different versions of Chrome, Firefox, Safari, and Edge, as well as Android and iOS devices in various screen resolutions. An expert testing provider will simulate real-world usage environments and use tools like BrowserStack or Sauce Labs to guarantee a consistent and optimized user experience.
Load and Performance Testing
Performance is a critical quality attribute—especially for high-traffic platforms like e-commerce websites, SaaS applications, and financial systems. Load testing evaluates how your system behaves under normal and peak loads, while stress testing identifies breaking points. Look for a provider that uses tools such as JMeter, Gatling, or LoadRunner and can deliver detailed reports on response time, throughput, and server health. This level of performance insight is vital to avoid costly downtimes and latency issues post-deployment.
Security and Penetration Testing
In an age of increasing cyber threats, security cannot be an afterthought. A capable software testing services provider should offer security assessments that include vulnerability scanning, penetration testing, and code analysis. They must be adept at identifying flaws like SQL injection, cross-site scripting (XSS), insecure APIs, and broken authentication. Their practices should align with security standards like OWASP Top 10, ISO 27001, and GDPR.
Integration and System Testing
Today's applications are often made up of interconnected components, third-party APIs, and microservices. A reliable testing partner must validate not only individual components (unit testing) but also how they interact (integration testing). Additionally, they should perform system testing to evaluate the entire end-to-end workflow, ensuring that business logic and data flow remain intact across modules.
Continuous Testing in CI/CD Environments
With DevOps and Agile becoming the industry norm, continuous integration and delivery (CI/CD) pipelines are now fundamental. Continuous testing ensures that every code commit is automatically validated through a series of tests. A modern testing provider should integrate their test automation framework into your CI/CD tools like Jenkins, GitLab CI, Bamboo, or CircleCI. This ensures quick detection of issues, faster feedback loops, and accelerated time to market.
Robotico Digital’s Proven Expertise
At Robotico Digital, we combine traditional best practices with innovative technologies to deliver reliable, scalable, and industry-specific software testing services. Our team comprises seasoned QA engineers, automation specialists, and domain experts who work collaboratively with your development team to enhance product quality and accelerate delivery cycles.
3. Evaluate Their Approach to Software Quality Assurance
Software Quality Assurance (SQA) is broader than just testing—it’s a strategic process that ensures every phase of the development lifecycle meets the highest quality standards. When evaluating a testing provider, ensure their services include:
l Quality planning and benchmarking
l Risk-based testing strategies
l Defect prevention and early bug detection
l Test environment management
l Detailed documentation and reporting
Robotico Digital integrates SQA from the start, ensuring not only bug-free releases but also process optimization, security, and maintainability across the software lifecycle.
4. Look for Automation Capabilities
As modern applications become increasingly complex, test automation is no longer a luxury—it’s essential. Ask potential service providers:
l What automation tools and frameworks do they use?
l Do they offer test script maintenance?
l Can they integrate with your CI/CD pipeline?
l Are they experienced with frameworks like Selenium, Appium, JUnit, TestNG, Cypress, etc.?
Robotico Digital’s automation-first approach reduces testing time, increases efficiency, and ensures continuous testing across development sprints.
5. Consider Industry Experience and Domain Expertise
Different industries have different quality expectations and regulatory demands. Choosing a provider with domain-specific knowledge adds immense value. For example:
l Healthcare apps must comply with HIPAA
l Finance platforms need PCI DSS and secure coding practices
l E-commerce platforms require usability and performance optimization
l EdTech solutions need scalable and accessibility-friendly testing
Our team at Robotico Digital has worked with clients across fintech, healthcare, education, e-commerce, and SaaS, bringing niche insights into quality and compliance standards.
6. Review Technology Stack Compatibility
A testing provider must be comfortable working with your tech stack—both frontend and backend. This includes:
l Programming languages (e.g., Java, Python, .NET, JS)
l Cloud platforms (AWS, Azure, GCP)
l DevOps and CI/CD tools (Jenkins, GitHub Actions, GitLab CI)
l Databases, APIs, and third-party integrations
Robotico Digital ensures seamless compatibility across all major tech stacks, helping you maintain workflow continuity and testing accuracy.
7. Inquire About Communication and Reporting
Communication is key in outsourcing. Your testing partner should offer:
l Dedicated project managers
l Real-time status updates
l Easy access to test plans, bug reports, and dashboards
l Collaboration tools (Slack, Jira, Asana, Trello)
We maintain complete transparency throughout the engagement at Robotico Digital. Our clients receive detailed reports and dashboards that highlight test progress, defects, coverage, and risks—enabling informed decisions at every step.
8. Evaluate Flexibility and Scalability
Your testing needs may change over time. The right provider should be able to:
l Scale team size up or down based on project phases
l Adapt to different engagement models (fixed, time & material, staff augmentation)
l Handle agile and waterfall methodologies
Robotico Digital offers flexible service models to accommodate both startups and large enterprises. Whether you need ongoing regression testing or a full QA team, we adapt to your needs.
9. Ensure Security and Data Privacy
Security in software testing is paramount—especially if your application handles sensitive data. Ask your provider:
l How do they handle data confidentiality and secure test environments?
l Are they compliant with ISO, GDPR, SOC2, or other data standards?
l How do they manage access control and data masking?
At Robotico Digital, we treat security as non-negotiable. Our testing protocols and infrastructure are built to safeguard client data and maintain compliance across multiple regulatory frameworks.
10. Check References and Client Testimonials
Finally, don’t just rely on sales pitches. Ask for client case studies, references, or testimonials. Look into:
l Past projects with similar scope
l Client retention rate
l Success stories or improvements they’ve driven
Robotico Digital has a strong portfolio of satisfied clients. From reducing time-to-market by 30% to improving test coverage by 90%, our measurable impact speaks for itself.
Conclusion: Making the Right Choice with Robotico Digital
Choosing the right software testing service provider is more than a technical decision—it’s a strategic partnership. The ideal provider should not only understand testing but also align with your business goals, technologies, and timelines.
At Robotico Digital, we pride ourselves on delivering holistic software testing services backed by industry-best practices in software quality assurance. Our dedicated QA engineers, AI-assisted tools, flexible models, and transparent communication help clients achieve faster releases, higher user satisfaction, and lower defect rates. Whether you’re scaling a new product or optimizing an existing system, trust Robotico Digital to elevate your software quality to the next level.
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note