#cse cyber security scope
Explore tagged Tumblr posts
Text
Best BTech Cyber Security College in Chandigarh

A B.Tech in cybersecurity is available from a number of esteemed colleges in Chandigarh, a city renowned for its technological breakthroughs. One of them, the best b tech cyber security college in chandigarh, is famous for its outstanding curriculum and industry-focused approach. The college has cutting-edge facilities, fully-stocked labs, and highly qualified faculty. Students at this college develop a thorough understanding of cybersecurity principles, tools, and tactics thanks to a strong emphasis on practical instruction and hands-on experience. In order to ensure that students are well-prepared for a successful career in the subject of cybersecurity, the college also offers plenty of chances for internships, industry collaborations, and placement aid.
#best b tech cyber security college in chandigarh#btech cse cyber security#cyber security course details#cse cyber security scope#cyber security course eligibility#top btech cse cyber security college#cyber security program#admission in cyber security#cgc jhanjeri#Chandigarh Group of Colleges Jhanjeri
0 notes
Text
BTech CSE Admission 2025: Your Dream Tech Career
The demand for skilled computer engineers continues to surge in India and globally. As industries become more reliant on technology, students aspiring for a successful tech career are increasingly opting for BTech in Computer Science and Engineering (CSE). With BTech CSE admission 2025 season around the corner, it's the perfect time to explore top colleges, eligibility, entrance exams, and career opportunities.

Whether you’re a student looking to enter the tech world or a parent researching the best options for your child, this guide will answer all your queries related to BTech CSE admission in 2025.
🌐 Let’s see about BTech in Computer Science and Engineering?
BTech CSE is a 4-year undergraduate engineering course that blends computer science theory with practical programming and software development skills. It covers subjects such as:
Data Structures and Algorithms
Artificial Intelligence
Machine Learning
Cloud Computing
Cyber Security
Internet of Things (IoT)
Full Stack Development
technology evolving at a rapid pace, CSE remains the top preferred stream among engineering aspirants in India.
🎓 Eligibility Criteria for BTech CSE Admission 2025
To secure admission in a reputed BTech CSE college in India in 2025, candidates must fulfill the following criteria:
Academic Qualification:
10+2 in Physics, Chemistry, and Mathematics (PCM) from a recognized board of India.
Minimum aggregate marks vary between institutions (usually 50%-75%).
Entrance Exam:
Appeared for national/state/university-level engineering entrance exams in India.
📝 Top Entrance Exams for BTech CSE Admission 2025
Here are the major engineering entrance exams that you must consider for BTech CSE admission in 2025:
JEE Main & JEE Advanced
For admission to NITs, IIITs, and IITs
BITSAT
For Birla Institute of Technology and Science (BITS), Pilani
VITEEE
For Vellore Institute of Technology
SRMJEEE
For SRM Institute of Science and Technology
COMEDK UGET
For private engineering colleges in Karnataka
🏫 Top Private Colleges for BTech CSE Admission 2025
If you are not aiming for IITs or NITs, many private institutes offer high-quality education and placements. Some of the best private BTech CSE colleges include:
Alpine Group of Institutes, Dehradun
VIT Vellore
SRM Institute of Science and Technology
Amity University
Manipal Institute of Technology
Chandigarh University
Tip: Consider colleges with industry partnerships, international exposure, and placement records for the best ROI.
🖥️ Career Scope After BTech CSE
With a BTech in Computer Science, graduates can step into a Bright and wide career options:
Software Engineer
Data Scientist
Machine Learning Engineer
Full Stack Developer
Cloud Architect
Cybersecurity Analyst
Mobile App Developer
AI/ML Specialist
Top recruiters include Google, TCS, Infosys, Wipro, Microsoft, Amazon, IBM, and many fast-growing startups.
💼 Average Salary After BTech CSE
The starting salary for a BTech CSE graduate depends on skill set and the hiring company. Here's a rough estimate:
Job Role
Average Starting Salary
Software Developer
₹3.5 – ₹8 LPA
Data Analyst
₹4 – ₹10 LPA
Machine Learning Eng.
₹6 – ₹15 LPA
Cybersecurity Analyst
₹5 – ₹12 LPA
Cloud Architect
₹7 – ₹20 LPA
Tip: Upskilling with certifications in Python, AWS, Data Science, or AI can significantly boost salary and job prospects.
📅 Important Dates for BTech CSE Admission 2025
Here’s a tentative timeline you should follow for 2025:
JEE Main 2025 (Session 1): January 2025
JEE Main 2025 (Session 2): April 2025
Application Forms (Private Colleges): December 2024 – May 2025
Counselling & Admissions: May 2025 – August 2025
Commencement of Classes: August/September 2025
🤔 FAQs: BTech CSE Admission 2025
1. Is BTech CSE a good course for the future?
Absolutely. With the rise in digital technologies, the demand for CSE graduates will only grow in sectors like AI, cybersecurity, fintech, health tech, and more.
2. without JEE Can I get admission to BTech CSE ?
Yes, many private colleges offer direct admission based on Class 12 results or their own entrance exams.
3. Which is better: IT or CSE?
CSE offers a broader curriculum and better opportunities in core tech roles. IT is a subset focusing more on software and network management.
4. Which coding languages should I learn during BTech CSE?
Start with C, C++, Java, and Python. Depending on your specialization, explore SQL, JavaScript, R, or Swift.
5. Are internships mandatory in BTech CSE?
Yes, most colleges encourage internships to gain hands-on industry experience and build your resume.
✍ Final Thoughts
The BTech CSE admission 2025 season is your gateway to building a career in one of the most dynamic and rewarding industries. Start preparing early, keep track of application dates, and choose a college that aligns with your long-term goals. With the right training and a proactive mindset, you can thrive in the ever-evolving tech world.
If you're exploring colleges in North India, consider institutions like the Alpine Group of Institutes in Dehradun, known for its strong curriculum, modern infrastructure, and excellent placement support in Computer Science and Engineering.
#alpineCollege#CSEAdmission#CSEAdmission2025#B.techInComputeerScience#ComputerScienceCourseInIndia#ComputerScience
0 notes
Text
Find The Best College for B.Tech. In Cyber Security
Want to build a career in B.Tech. in Cyber Security but are confused about which college will be best for you? Here You Go! We have come up with this guide where we have mentioned K.R. Mangalam University, the best university for cyber security in Delhi-NCR. Over the years, they have managed to win the student’s hearts by offering a unique curriculum specifically curated by top IBM experts. Apart from this, they also offer 1:1 counselling sessions to the students after analysing their career graph. It’s certainly one of the best universities for cyber security in Delhi NCR and after enrolling here you will reach the heights of your career.
Eligibility Criteria for the B.Tech. Cyber Security
Those who are interested in pursuing B.Tech in Cyber Security at K.R. Mangalam University must meet the following eligibility requirements:
You must have passed the 10+2 examination with Physics and Mathematics as compulsory subjects.
For the remaining course, choose from Chemistry/ Computer Science/ Electronics/ Information Technology/ Biology/ Informatics Practices/ Biotechnology/ Technical Vocational subject/ Agriculture/ Engineering Graphics/ Business Studies/ Entrepreneurship from a recognised board/university with a minimum 50% aggregate overall.
Why KRMU is the best university for Cyber Security in India?
Located in Gurugram, K.R. Mangalam University is known for providing exceptional facilities to the students. Here are some of them:
Industry-Oriented Curriculum: Our faculty members team up with top IBM experts to design the curriculum.
Strong Industry Tie-Ups: We have partnered with leading tech giants to provide internship and placement assistance to the students.
Significant Practical Exposure: Students get to work at IBM Big Data Analytics Lab on real-life cases.
Receive Certifications: You will receive certifications from EC-Council and IBM which will be recognised globally.
Provides 100% Scholarship: Based on academic performance in the 12th, entrance examination and other categories, they offer scholarships to the students.
B.Tech. Cyber Security Course Details
Course Name:
B.Tech. CSE (Cyber Security) with academic support of EC-Council & IBM
Course Type:
Undergraduate
B.Tech. CSE Data Science Course Duration:
4 Years
Study Mode:
Full-Time
Programme Fee Per Year:
Rs 2,50,000/- (as of 24th March 2025)
Admission Procedure:
Written Test + Personal Interview
Career Opportunities:
Cybersecurity Developer, CyberSecurity Analyst, Network Security Engineer, Information Security Manager
Course Outcome:
Develop strong engineering concepts, Learn to select and apply modern IT tools, Efficiently manage computer science projects
Top Recruiters:
Reliance, Microsoft, ITC Limited, DLF, TATA Power
B.Tech. Cyber Security Admission 2025
Getting admission into B.Tech. in Cyber Security is a streamlined procedure at KRMU. The step-by-step instructions are as follows:
Go through the official website
Search for the application form and fill it
Pay for the application fee
Appear for the written assessment and personal interview
Receive the admission offer
Get enrolled for B.Tech. in Cyber Security
Career Scope After the B.Tech. Cyber Security
Graduates from B.Tech. in Cyber Security open up the pathway to diversified career options. Some of the most anticipated ones are:
Ethical Hacker
Security Architect
Software Developer
Penetration Tester
Incident Manager
Game Developer
Digital Forensics Expert
Conclusion
Developed in collaboration with EC-Council and IBM, B.Tech. in Cyber Security is a highly informative and unique programme. By pursuing this course from K.R. Mangalam University you will be equipped with the skills necessary to reduce cybercrimes. Luckily, due to the increase in cyberattacks, you will be able to secure employment in both private and public sectors. So gear up to enrol at KRMU and walk towards a fruitful career.
Frequently Asked Questions
What are the benefits of a B.Tech. in Cyber Security?
After graduating from this course, you will be equipped with valuable skills like penetration testing, network security and cryptography.
Which stream is the best for B.Tech. in Cyber Security?
Students should pursue the science stream in class 12th if they wish to develop a career in cyber security.
How much does a B.Tech. in Cyber Security graduate earn?
You can expect to earn a starting salary between 3-8 LPA depending on your skillset, job location and knowledge.
#Best University for B.Tech. in Cyber Security#Top College for B.Tech. in Cyber Security#B.Tech. in Cyber Security
0 notes
Text
Lovely Professional University Admission—[LPU]
Overview

About Lovely Professional University
Lovely Professional University (LPU) is a private university located in Jalandhar, Punjab, India. Established in 2005 by the Lovely International Trust, LPU is the largest single-campus university in India, with more than 30,000 students, over 4000 faculty members, and over 200 academic programs. LPU offers a wide range of undergraduate, postgraduate, and doctoral programs in a variety of disciplines, including engineering, management, law, computer applications, biotechnology, hospitality, journalism, fashion, and more.
The university also offers a range of professional certificate courses in areas such as data science, digital marketing, business analytics, artificial intelligence, and more. LPU is accredited by the National Assessment and Accreditation Council (NAAC) with an 'A' grade. The university has also been ranked among the top 10 universities in India by several leading publications.
LPU also offers a number of scholarships to deserving students, based on their academic performance. The university provides a number of facilities for students, including a library, sports complex, hostels, Wi-Fi-enabled campus, laboratories, and more. The university also has student clubs and societies for extracurricular activities.
Lovely Professional University is committed to creating a world-class learning environment that promotes excellence in teaching and research. They are dedicated to providing students with innovative, high-quality educational experiences that prepare them to be successful in the global knowledge-based economy. They strive to foster an environment of collaboration, creativity, and critical thinking that encourages lifelong learning and personal growth. They strive to be an institution of excellence that contributes to the economic, social, and cultural development of India and the world.
The vision of Lovely Professional University (LPU) is to make it a world-class university and to be a leader in providing quality education, training, and research to contribute to the development of a knowledge-based society. LPU will strive to create a world-class, multicultural environment that will foster creativity, innovation, and excellence in teaching, learning, and research in order to create a better future for the nation.
About Course
The Bachelor of Technology in Computer Science and Engineering (B.Tech CSE) is a prestigious undergraduate program designed to provide a solid foundation in computer science and engineering principles. Spanning four years, the curriculum is crafted to cover a broad spectrum of topics, ensuring students are well-prepared for the dynamic technology landscape.
Course Scope
The scope for Computer Science and Engineering (CSE) is vast and continually expanding, given the rapid advancements in technology and the increasing reliance on digital solutions in various industries. Graduates with a degree in CSE are in high demand, and the scope for career opportunities is diverse. Here's an overview of the course scope for Computer Science and Engineering:
1. Software Development:
Role: Software Engineer/Developer
Scope: Designing, coding, testing, and maintaining software applications for various platforms. Opportunities in web development, mobile app development, and more.
2. Networking and Cybersecurity:
Role: Network Engineer, Cybersecurity Analyst
Scope: Managing and maintaining computer networks, ensuring data security, and protecting systems from cyber threats.
3. Database Management:
Role: Database Administrator
Scope: Handling database systems, designing and implementing databases, and ensuring data integrity.
4. System Analysis and Design:
Role: System Analyst
Scope: Analyzing and designing information systems to meet organizational needs.
5. Artificial Intelligence (AI) and Machine Learning (ML):
Role: Machine Learning Engineer, AI Specialist
Scope: Developing and implementing machine learning algorithms, creating AI applications, and working on intelligent systems.
6. Data Science and Big Data:
Role: Data Scientist, Big Data Analyst
Scope: Analyzing large datasets to derive insights, making data-driven decisions, and contributing to business intelligence.
7. Web Technologies:end/Back-end Developer
Scope: Creating and maintaining websites and web applications, working with technologies like HTML, CSS, JavaScript, and frameworks.
8. Cloud Computing:
Role: Cloud Engineer
Scope: Managing and optimizing cloud infrastructure and services, working with platforms like AWS, Azure, and Google Cloud.
9. Internet of Things (IoT):
Role: IoT Developer, Embedded Systems Engineer
Scope: Developing applications and solutions for connected devices, exploring the intersection of hardware and software.
Conclusion:
The scope for Computer Science and Engineering is dynamic, with opportunities in diverse industries. Continuous learning, staying updated on emerging technologies, and developing a strong network can significantly enhance career prospects. Whether in traditional IT roles or emerging fields like AI and IoT, CSE graduates play a crucial role in shaping the digital future.
#computer science engineering#dekhocampus#education#data science course#data science career#Lovely Professional University
0 notes
Text
Computer Science Engineering: Pioneering the Digital Revolution

In today's digital age, Computer Science Engineering stands at the forefront of technological innovation. This article delves into the dynamic field, exploring its significance, key areas, and career prospects.
Understanding Computer Science Engineering
What is Computer Science Engineering (CSE)?
Computer Science Engineering is a multidisciplinary branch of engineering that integrates computer science principles with electrical and electronic engineering concepts. It's all about harnessing technology to solve complex problems.
Key Areas in CSE
1. Software Development: The heart of CSE, focusing on creating applications, operating systems, and software solutions.
2. Hardware Design: Designing computer systems, microprocessors, and hardware components.
3. Data Science: Utilising data to derive valuable insights for businesses and industries.
4. Artificial Intelligence (AI): Building intelligent machines capable of human-like tasks.
Why Computer Science Engineering Matters
CSE plays a pivotal role in shaping our digital world. It powers:
- Communication: Enabling seamless global communication through the internet.
- Innovation: Driving innovations in autonomous vehicles, smart devices, and more.
- Security: Protecting digital assets from cyber threats.
- Entertainment: Enriching our lives with gaming and multimedia experiences.
Career Opportunities
With the increasing reliance on technology, CSE offers a plethora of career options:
1. Software Developer: Creating applications and systems.
2. Data Scientist: Analysing and interpreting data.
3.Network Engineer: Managing communication networks.
4. AI Engineer: Developing AI-powered solutions.
5. Cybersecurity Expert: Safeguarding digital infrastructure.
The Future of CSE
As technology continues to advance, Computer Science Engineering will evolve. Quantum computing, augmented reality, and the Internet of Things are just a glimpse of what lies ahead.
Conclusion
Computer Science Engineering is the driving force behind our digital revolution. Its scope is boundless, promising endless possibilities for those who choose this dynamic field.
FAQs
1.Is a strong maths background required for CSE?
While maths is essential, many tools and resources are available to help you excel in CSE, even if maths isn't your strongest suit.
2.What skills are essential for a CSE career?
Problem-solving, coding proficiency, and strong analytical skills are crucial for success in CSE.
3. Is CSE a rapidly changing field?
Yes, CSE evolves rapidly with new technologies, making it an exciting and ever-changing profession.
4. Can I specialise in more than one area within CSE?
Absolutely! Many professionals choose to specialise in multiple areas to broaden their skill set.
5. What is the earning potential in CSE?
Salaries in CSE are competitive, with experienced professionals earning lucrative packages.
0 notes
Text
The Art and Science of B Tech Cyber security - Exploring the Fundamentals

In an era of digitalization and technological advance ements, the critical need for robust cybersecurity measures has never been more apparent. With cyber threats evolving in complexity and frequency, organizations and individuals alike are increasingly reliant on cybersecurity experts to safeguard sensitive information and maintain the integrity of digital systems. A Bachelor of Technology degree in Cybersecurity equips students with a comprehensive understanding of the multifaceted world of cybersecurity, encompassing a wide range of knowledge and skills essential for protecting digital assets.
Understanding the fundamentals of Cyber security
Let’s get into various aspects of Cyber security and its significance in the world of technology -
B Tech cyber security curriculum
At its core, cybersecurity involves the practice of protecting computer systems, networks, and data from theft, damage, or unauthorized access. B. Tech Cybersecurity programs delve into the theoretical underpinnings of cybersecurity, helping students comprehend the principles of encryption, authentication, access control, risk assessment, and vulnerability management. Interested aspirants can check B Tech Cyber security eligibility with various colleges and universities and pick the specialization.
Foundational Knowledge
The related course structure typically begins by imparting a solid foundation in computer science and networking concepts. Students learn about operating systems, databases, programming languages, and network protocols, which serve as the building blocks for advanced cybersecurity techniques. This knowledge ensures that graduates can effectively analyze and secure various components of digital infrastructure. If you are quite enticed with this branch of engineering, start exploring B Tech CSE cyber security Fee in various colleges and universities until you find the one that befits your requirements.
Cyber Threat Landscape
An in-depth study of the ever-evolving cyber threat landscape is a crucial component of B. Tech Cybersecurity. Students explore the different types of cyberattacks, including malware, phishing, ransom ware, and Dodos attacks. By understanding the tactics employed by malicious actors, students can develop effective strategies to counter and mitigate these threats.
Network Security
Securing computer networks is a paramount concern for modern organizations. B. Tech Cybersecurity curricula cover topics such as firewalls, intrusion detection and prevention systems, virtual private networks (VPNs), and network segmentation. Graduates are equipped to design, implement, and manage network security measures to thwart unauthorized access and data breaches.
Ethical Hacking and Penetration Testing
Ethical hacking involves simulating cyberattacks to identify vulnerabilities in a controlled environment. B Tech Cyber security programs often include modules on ethical hacking and penetration testing, where students learn how to assess system weaknesses and recommend remediation strategies. This hands-on experience cultivates a proactive approach to cybersecurity.
Security Policies and Compliance
Maintaining cybersecurity within an organization requires the establishment of robust security policies and adherence to industry regulations. B. Tech Cybersecurity students gain insights into crafting effective security policies, conducting risk assessments, and ensuring compliance with standards such as ISO 27001 and GDPR. This knowledge is vital for promoting a culture of cybersecurity awareness.
Incident Response and Recovery
Even with preventive measures in place, cybersecurity incidents may still occur. B. Tech Cybersecurity programs prepare students to handle such situations through incident response and recovery planning. Graduates are trained to assess the scope of an incident, contain its impact, and orchestrate a coordinated recovery effort.
Emerging Technologies
The realm of cybersecurity is closely linked with emerging technologies. B. Tech programs expose students to cutting-edge concepts like cloud security, Internet of Things (IoT) security, Block chain, and artificial intelligence in cybersecurity. This knowledge enables graduates to adapt and develop innovative strategies to address novel threats.
A Bachelor of Technology in Cybersecurity provides a comprehensive education that empowers graduates to tackle the intricate challenges posed by the digital landscape. As the demand for cybersecurity expertise continues to surge, B Tech cyber security placements would always remain in a good stat. This specialized program paves the way for a fulfilling and impactful career at the forefront of technological defense.
0 notes
Text
Admission Open2021_B.Tech CSE (Internet of Things & Cyber Security including Blockchain Technology)
Admission Open2021_B.Tech CSE (Internet of Things & Cyber Security including Blockchain Technology)
INNOVATION IS OUR TRADITION
Dronacharya College of Engineering Gurugram offers B. Tech in CSE (IoT & cybersecurity including Blockchain Technology) is a four-year undergraduate programme offered that familiarises aspirants with the functional and operational aspects of the Internet of Things including Cybersecurity and blockchain Technology.

B.Tech Admission Open 2021-22
https://www.youtube.com/watch?v=yyKb_pol0a0
KEEP WATCHING
https://ggnindia.dronacharya.info/CSE-IOT-CS/home.aspx
Furthermore, To know more about College please Visit our website and if you feel any query, feel free to Contact to the admission department
Contact Details: Khentawas, Farrukh Nagar -122506, Gurugram, Haryana
Contact No. : 9910380109 (Admission Head)
Email id: [email protected]
URL: https://ggnindia.dronacharya.info/ Virtual Visit: https://ggnindia.dronacharya.info/DCE_vtour/index.html
#Big Data#Cloud Security#IOT#Scope of Cyber Security#Top B.Tech College in Delhi NCR#B.Tech CSE (Internet of Things & Cyber Security i#BestPlacementEngineeringCollegeinIndia#PlacementRecordsofTopEngineeringCollegesinGurugram#BestplacementengineeringcollegesinGurugram
11 notes
·
View notes
Text
Best Engineering College for Computer Science in Kanpur

Potentially the most sought-after course among planning understudies, VSGOI provides the best engineering college for computer science in Kanpur. Computer Science Engineering (CSE) is an academic program that facilitates the field of Computer Engineering and Computer Science. The program, which underlines the fundamentals of PC programming and frameworks organization, incorporates a lot of subjects. The said subjects are related to estimation, computations, programming lingos, program plan, PC programming, PC hardware, etc.
Programming engineers are related with various pieces of enlisting, from the arrangement of individual CPUs, PCs, and supercomputers to circuit arranging and forming programming that powers them.
The course is introduced by particular establishments across India and Abroad at the UG (Undergraduate) and PG (Postgraduate) levels where understudies are allowed B.Tech and M.Tech degrees separately. VSGOI provides the best engineering college for Computer Science in Kanpur. Understudies pursuing the course will be told about the arrangement, execution, and the chiefs of information plan of PC gear and programming.
Benefits of studying Computer Science Engineering at VSGOI?
Software engineering is quickly changing the world we live in. Concentrating on Computer Science at the, you’ll find out about so Virendra Swarup Group of Institution programming frameworks and how individuals and PCs communicate. VSGOI provides the best engineering college for Computer Science in Kanpur. You’ll likewise figure out how to make new programming, and guarantee it’s simple for individuals to utilize.

Virendra Swarup Group of Institution is all around perceived Kanpur and Unnao for our software engineering programs and has particularly appreciated accomplishment with open source programming advancement. VSGOI provides the best engineering college for Computer Science in Kanpur. Understudies have the chance to work close by Virendra Swarup scholastics on a wide scope of energizing and inventive exploration projects in regions, for example,
Broadband correspondence
Data pressure
Digital libraries
Formal strategies
Human-PC collaboration
Machine learning
Software designing
Cyber security
For more information visit our website: click here
2 notes
·
View notes
Text
சென்னை தரமணியில் மத்திய அரசு நிறுவன வேலை | No Experience Required | salary - 50,000 | SETS Chennai Recruitment 2023

சென்னை தரமணியில் மத்திய அரசு நிறுவன வேலை | No Experience Required | salary - 50,000 | SETS Chennai Recruitment 2023
Organization Name : SOCIETY FOR ELECTRONIC TRANSACTIONS AND SECURITY
Society for Electronic Transactions and Security is a Society under Societies Registration Act, XXI of 1860, dedicated to carry-out Research and Development in the field of Information Security focusing on the key verticals, namely, Cryptology and Computing, Hardware Security, Quantum Security and Network Security. SETS invites applications from citizens of India for filling up the following positions for a Research & Development project in the area of Cybersecurity

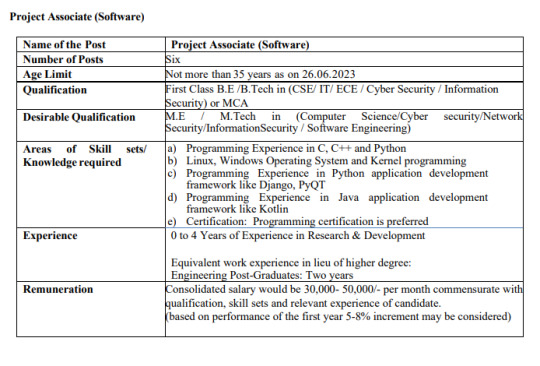
மத்திய அரசு நிறுவன வேலை Our Latest YOUTUBE Videos Link : https://www.youtube.com/channel/UCZYt-jtPk975fMuI6tLpUEg Our Telegram Channel Link: https://t.me/employmentjobs Related Jobs : - HPE Recruitment 2023 | Graduate Software Engineer Trainee - Johnson Electric Job Openings in Chennai - பிரபல ஸ்டீல் கம்பெனி வேலை வாய்ப்பு – B.E / B. Tech Engineering Job Interview in Pegatron Company – Diploma & B. E. Engineers | Mahindra World City | Chengalpattu Designation: Engineer & Sr.Engineer Educational Qualifications: B.E. Engineer & Diploma Role: Permanent Year of Experience: Min Experience Job Location: Mahindra World City – Chengalpattu Apply link - Click Here Salcomp Walk-In Interview | Diploma & B.E. Engineers Designation: Engineer Educational Qualifications: Diploma & B.E.Engineers Role: Permanent Year of Experience: Automation, Process, Testing Job Location: Sriperumbudur Salary Details: As per the Company Standard Apply link - Click Here Latest Jobs By : Chennai JobsClick HereCoimbatore JobsClick HereBangalore JobsClick HereHyderabad JobsClick HereAndra Pradesh JobsClick HereSalem JobsClick HereMadurai JobsClick HereTrichy JobsClick HerePondicherry JobsClick HereAcross India JobsClick HereOther Cities JobsClick Hereமத்திய அரசு நிறுவன வேலை Designation: 1)Project Associate (Software) - 6Positions 2) Project Associate – 2 Positions 3) Project Scientist – 1 Position Educational Qualifications: First Class B.E /B.Tech in (CSE/ IT/ ECE / Cyber Security / Information Security) or MCA M.E / M. Tech in (Computer Science/Cyber security/Network Security/Information Security / Software Engineering) Role: Temp Year of Experience: Fresher & Experience Job Location: Chennai, Taramani Salary Details: 30,000 - 50,000 /- Mechanical JobsClick HereELE / ECE JobsClick HereCivil JobsClick HereIT / Software JobsClick HereBPO / Call Centre JobsClick HereH/W & Networking JobsClick HereHuman Resource Jobs Click HereAcc/Fins JobsClick HereArts & Science JobsClick Hereமத்திய அரசு நிறுவன வேலை மத்திய அரசு நிறுவன வேலை Job Description : The positions of Project Associates as proposed is purely temporary and would be filled on a contract basis with a consolidated salary under project mode. The duration of the assignment is initially for a period of One Year and would be extended further based on the need of the project and performance. There is no scope of continuation/regularization/absorption under any circumstances. The last date for uploading applications via Google Form is 26.06.2023 Shortlisted candidates would be requested to attend an Interview at SETS, Chennai. The date and time for this would be intimated to shortlisted candidates The shortlisted candidates would be required to bring all their original testimonials for verification on the interview day
How to Apply for this Job? Details & Apply link : Click Here Foxconn Company Off Campus Drive | Arunai Engineering College | Tiruvannamalai – Date 10th June 2023 Designation: Trainee Educational Qualifications: Diploma – Mechanical, EEE, ECE, CSE, CIVIL, MECHATRONICS & OTHERS Role: Trainee Year of Experience: Fresher Job Location: Sriperumbudur Apply link : https://myemploymentjobs.com/foxconn-company-off-campus-drive-arunai-engineering-college-tiruvannamalai-date-10th-june-2023/ 40,000 Salary – L & T Fresher Job Openings in Chennai Educational Qualifications ( L & T Fresher Job ): B.E, B.Tech Engineers – Mechanical & Civil Engineers Role: Permanent Year of Experience: Fresher & Min Experience Job Location: Chennai, Tamilnadu Salary Details: As per the Company Standard Apply link : https://myemploymentjobs.com/l-t-fresher-job-openings-in-chennai/ For more Job info, subscribe to our website & and check our website daily. Join Our Youtube ChannelClick HereJoin Our Telegram ChannelClick HereOur Linkedin PageClick HereOur Quora PageClick Here Read the full article
#govtjobsfordiplomaholdersinmechanicalengg#govtjobsfordiplomamechanicalinrailway#govtjobsforelectricalengineers#govtjobsforexperiencedelectricalengineers#govtjobsformechanicalengineers#govtjobsformechanicalengineersfreshers#சென்னைதரமணியில்மத்தியஅரசுநிறுவனவேலை#மத்தியஅரசுநிறுவனவேலை
0 notes
Text
DIFFERENCE BETWEEN BLOCKCHAIN AND CYBERSECURITY-GEETA UNIVERSITY
Blockchain and cybersecurity are two distinct concepts that are often discussed together. Both are important aspects of modern technology and play a vital role in the security of data and information. In this article, we will explore the difference between blockchain and top B.Tech. (Hons.) CSE - Cyber Security college in haryana and their significance in the modern technological landscape.
To start with, let us first understand what blockchain is. Blockchain is a distributed ledger technology that is used to store and transmit data in a secure and transparent manner. It is a decentralized system that allows multiple parties to access the data without the need for a centralized authority. This means that data stored on a blockchain cannot be easily altered or manipulated, and it is highly resistant to hacks and attacks.
On the other hand, top B.Tech. (Hons.) CSE - Cyber Security college in haryana is the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks, theft, or damage. top B.Tech. (Hons.) CSE - Cyber Security college in haryana aims to reduce the risk of unauthorized access, disruption, or destruction of sensitive information. It involves the use of various technologies and practices such as firewalls, antivirus software, encryption, and intrusion detection systems.
Now, let us delve into the key differences between blockchain and cybersecurity. The first and foremost difference is the scope of their application. While blockchain is a specific technology used for the secure and transparent transfer of data, cybersecurity is a broader concept that encompasses a wide range of technologies and practices to protect data and systems from cyber threats.
Another key difference is the approach to security. Blockchain provides security through decentralization, transparency, and immutability. Once data is recorded on a blockchain, it cannot be altered without the consensus of the network participants. This means that blockchain is highly resistant to attacks and manipulation. On the other hand, top B.Tech. (Hons.) CSE - Cyber Security college in haryana focuses on securing data and systems through various technologies such as firewalls, encryption, and intrusion detection systems. These technologies work together to prevent unauthorized access and protect against threats.
Furthermore, blockchain is a proactive approach to security, whereas top B.Tech. (Hons.) CSE - Cyber Security college in haryana is a reactive approach. Blockchain ensures the security of data at the time of creation and transmission, while cybersecurity detects and responds to threats after they have occurred. Blockchain eliminates the need for trust in a centralized authority by providing a transparent and secure system for data transfer. Cybersecurity, on the other hand, requires trust in the security technologies and practices employed to protect data and systems.
In conclusion, both blockchain and top B.Tech. (Hons.) CSE - Cyber Security college in haryana are important in ensuring the security of data and information in the modern technological landscape. While blockchain provides security through decentralization, transparency, and immutability, cybersecurity focuses on securing data and systems through various technologies and practices. Understanding the difference between these two concepts is crucial for organizations and individuals to implement the appropriate security measures and technologies to protect against cyber threats. Geeta University, with its strong focus on technology and innovation, is well placed to provide education and training in both blockchain and cybersecurity to prepare its students for the modern digital world.
#top B.Tech. (Hons.) CSE - Cyber Security college in haryana#top college in delhi ncr for B.Tech. (Hons.) CSE - Cyber Security#top B.Tech. (Hons.) CSE - Cyber Security college in delhi ncr#top college in India for B.Tech. (Hons.) CSE - Cyber Security#top B.Tech. (Hons.) CSE - Cyber Security college in India#top college in north india for B.Tech. (Hons.) CSE - Cyber Security
0 notes
Text
What concepts are covered in a PG diploma in cyber security?
Working as a Cyber Security Analyst is the best opportunity in the present times. The scope of Cyber Security has expanded dramatically since the invention of the internet. If you want to build a name for yourself in this field, obtaining a certification is highly suggested in order to increase your reputation and employability.
Cyber Security Analysts have a bright future since they earn more than their counterparts in other fields. You can work as an ethical hacker, a network and security specialist, an IT security and consultant, a cyber security analyst, a cyber forensic investigator, a penetration tester, a risk analyst, and more after earning a certificate or a degree in this field.
For undergraduate and postgraduate PG diploma cyber security, you must achieve a minimum aggregate of 50% in classes 10, 12, or graduation, however there are no defined qualifying criteria for Cyber Security Online Courses. Basic cyber security principles are covered in online courses, whereas undergraduate and postgraduate cyber security courses include topics such as network security, cyberspace regulations, safeguarding web applications, and more.
The following are the basic concepts covered in PG program in cyber security:
Confidentiality:
The goal of confidentiality is to prevent unauthorised individuals from accessing data. It also requires safeguarding the identities of those who are permitted to share data, as well as guaranteeing data privacy and anonymity.
Integrity is defined as the ability to prevent unauthorised persons from tampering with information in a confirmed and approved way. By turning computers into "zombie computers" and injecting malware into online pages, integrity might be affected.
Information availability guarantees that authorised parties have access to it when they need it. It is available to the public at the appropriate moment. Data can be rendered unavailable due to security issues such DDOS assaults, hardware failures, code faults, and human errors.

The following is a detailed description of the employment opportunities available after finishing PG cyber security course such as BTech, Diploma, MTech, MSc, and so on:
Students might pursue further education possibilities in the same field after completing a BTech in Cyber Security to acquire an edge and higher compensation packages. MTech Cyber Security, MTech Information Security, MTech in Computer Networks and Information Security, and MTech CSE are among the most popular postgraduate programmes for BTech Cyber Security graduates.
The majority of post-graduates are looking for work in the government, public, and private sectors after finishing an MTech Cyber Security degree. After clearing the UGC-NET and JRF tests, some of them decide to seek lectureships or junior research fellowships.
Almost every company, whether government or private, wants qualified legal advice from a cyber lawyer. Not only are there possibilities in courtrooms and legal firms, but there are others as well. You can pursue a PG in cyber security, Postgraduate Diploma in Cyber Law after earning your Cyber Law Diploma.
Working as an ethical hacker, penetration tester, cryptography specialist, security software developer, or cyber legal assistance professional are all possibilities.
0 notes
Link
This course is also known by the name of B.Tech. CSE (Cyber Security). Complete details about B.Tech Cyber Security at Ganpat University Institute of Computer Technology, Mehsana, like admission process, eligibility criteria, fees etc.
0 notes
Text
Canada’s Spy Agency Says Voters Are Being Targeted By Foreign Influence Campaigns
OTTAWA—Canada’s intelligence community has identified foreign actors attempting to directly influence the upcoming federal election campaign, a Toronto Star and BuzzFeed News investigation has learned.
The Communications Security Establishment (CSE), the country’s cyber defence agency, has briefed senior political staff of one federal party about “covert and overt” attempts to influence the Oct. 21 federal election.
Canada’s domestic spy agency, the Canadian Security Intelligence Service (CSIS), also said Tuesday that “threat actors” are trying to influence Canadian citizens, although the agency tied it to an attack on “democratic institutions” rather than the election specifically.
The agencies would not reveal the exact nature of the attempts to influence but said the scope of “foreign interference activities can be broad,” including state-sponsored or influenced media, hacking, and traditional spy operations.
“Threat actors are seeking to influence the Canadian public and interfere with Canada’s democratic institutions and processes,” wrote Tahera Mufti, a spokesperson for CSIS, in an emailed statement.
“For example, over the years (CSIS) has seen multiple instances of foreign states targeting specific communities here in Canada, both in person and through the use of online campaigns.”
A senior government source said that diaspora communities are being targeted by foreign actors in an attempt to sway the election’s outcome. The source, who has direct knowledge of Canada’s efforts to safeguard the federal election, was granted anonymity to speak frankly about ongoing national security issues.
While national security sources had previously said Canadian political parties have been targeted by sophisticated state-sponsored hacking campaigns, the motive for those campaigns was not publicly linked to attempts to meddle with the election.
Then on Friday, CSE confirmed it is briefing Canada’s major political parties on “covert and overt foreign interference activity” aimed at influencing Canadian voters — although the agency stopped short of publicly confirming such campaigns have already been detected.
The briefings included select security-cleared political staff and discussions around unclassified and classified material, the agency said. Unclassified material would be information already in the public domain while classified would be intelligence gathered by Canada’s spies or security partners.
The federal political parties were briefed so that they can “strengthen internal security practice and behaviours,” the agency wrote in a statement.
“Unfortunately, we cannot discuss the specific information covered in these briefings.”
The agency refused to discuss the nature of any specific threat — or who may be behind it. But the Canadian government currently has strained relationships with some of the dominant players in cyber warfare and espionage.
That includes China, with Beijing demanding the release of Huawei executive Meng Wanzhou, holding two Canadians in detention on spying allegations, and sharply restricting Canadian agricultural exports.
On Tuesday, Prime Minister Justin Trudeau said he had “a number of conversations” with Chinese President Xi Jinping about the detained Canadians — former diplomat Michael Kovrig and businessman Michael Spavor — at the recent G20 meeting in Osaka, Japan.
“This is an issue we take extremely seriously,” Trudeau told reporters in Toronto. “I had a number of conversations with President Xi directly on this and the larger issue of Canada–China relations.”
Other well-known cyber players — Russia, Saudi Arabia, and India — have also had tense relations with Ottawa.
The motivations of those countries differ widely, said Stephanie Carvin, a professor at Carleton University’s Norman Paterson School of International Affairs and a former intelligence analyst.
“There is actually a traditional espionage component of this, I’m sure,” Carvin said of hacking attempts against Canadian political parties.
Countries could be looking for blackmail material, for instance, or seeking to understand Canadian politicians internal discussions around hot-button issues.
“They’re going to be looking for a number of things,” Carvin said.
“There’s the traditional espionage component, they’re going to be looking for emails that are potentially embarrassing. The other thing they might be looking for, and this would be a big concern, is understanding how [political staff and politicians] communicate with each other for the purpose of generating forgeries … And then, of course, you get to learn what are the issues that political parties themselves are actually concerned with.”
How seriously Canadian political parties are taking those threats is an open question. While political staff from the major federal parties expect foreign countries to intervene in some fashion — whether publicly or clandestinely — in the election, how they’re protecting against those attempts is largely a secret.
“While the Liberal Party of Canada does not comment on specific security precautions, our party takes these considerations very seriously,” wrote party spokesperson Parker Lund in an email.
“The highest levels of security are implemented for all data, communications, and records … This has also included meetings and briefings for political parties from the Communications Security Establishment and their government partners.”
“Due to the classified nature of the briefings [with CSE], we cannot confirm anything we’ve heard within the briefings,” wrote Cory Hann, the Conservative Party’s director of communications.
“Of course, broadly speaking, the party is concerned with any attempts to improperly interfere with Canadian elections.”
CSE has been pressed into taking a lead role in the federal government’s efforts to safeguard the 2019 vote.
Along with the CSIS, the RCMP, and Global Affairs, the agency is responsible for “working to identify and prevent covert, clandestine, or criminal activities from influencing or interfering with the electoral process.”
In April, CSE predicted it is “very likely that Canadian voters will encounter foreign cyber interference ahead of, and during, the 2019 general election.” The Star and BuzzFeed News previously reported that at least one political party has been the target of sophisticated, state-sponsored hacking attempts — although national security sources could not say if those attempts were related to the upcoming election or more routine espionage.
Political parties have consistently been a weak link for hostile nations to gather intelligence. In the US, France, and most recently Australia, hackers have targeted political parties — and in the first two cases, leaked damaging information about politicians and campaigns.
CSE is also holding monthly teleconferences for federal political parties to “discuss cyber security advice and guidance, as well as a general overview of the threat environment.”
Alex Wilner, a Carleton University professor studying intelligence and defense issues, said Canada’s intelligence agencies could be sending a message to hostile actors that they’re watching.
“This might be them messaging not just political parties and Canadians, but their messaging foreigners, those who are doing the influencing, saying ‘we know what you’re up to’ with not so many words,” Wilner said.
As the election gets closer, Wilner expects foreign interventions to ramp up.
“Any opponent or adversary to Canada would have, you could imagine, would’ve instituted or developed a campaign of influence,” Wilner said.
“If you’re thinking of a state-based adversary, you can imagine that a campaign would be rolling out for a long time previous to the election. And then you’ve got all the trolls, and all the hate-mongers and the rest, who may or may not be part of a more coordinated campaign, jump on the bandwagon as the election approaches.”
BuzzFeed News and the Toronto Star are investigating the ways in which political parties, third-party pressure groups, foreign powers, and individuals are influencing Canada’s political debate in the run-up to this fall’s federal election. This report was published as part of that collaboration.
Sahred From Source link World News
from WordPress http://bit.ly/324omxR via IFTTT
0 notes
Text
Canada’s cybersecurity firms keep turning to the U.S. for funding, leaving us without a homegrown leader
Canada has a rich history of innovation, but in the next few decades, powerful technological forces will transform the global economy. Large multinational companies have jumped out to a headstart in the race to succeed, and Canada runs the risk of falling behind. At stake is nothing less than our prosperity and economic well-being. The Financial Post set out explore what is needed for businesses to flourish and grow. You can find all of our coverage here.
A couple of years after co-founding eSentire Inc., Eldon Sprickerhoff was funding the fledgling cybersecurity company using an early round of financing and a line of credit he took out on his house.
The Waterloo, Ont.-based firm was growing by 15 per cent a year, but it wasn’t enough to compensate him for the endless hours he was spending to get it off the ground. He was faced with a dilemma.
“When I co-founded the company, I owned 50 per cent of shares of a pie that had practically no market value,” he said in a recent interview. “If I’m putting this much effort into it, I need a bigger payoff than running a mom-and-pop consulting shop or security company.”
To get there, Sprickerhoff followed a path that is becoming the norm in the domestic cybersecurity space and for many other high-tech startups: He sold a majority stake to a New York-based private-equity firm, specifically Warburg Pincus LLC, reportedly for upwards of $100 million.
How to finance a Canadian tech startup, from pre-seed to series D
Innovation Nation: Why has the government put a cap on innovation success?
Innovation Nation: AI godfathers gave Canada an early edge — but we could end up being left in the dust
“If you really want to keep up with your better-funded competitors, you’ve got to figure out how to build a sales plan, how to build a sales pipeline,” he said. “I’m not saying it’s impossible, but it’s very difficult to do this if you don’t have a war chest.”
Today, eSentire has more than 450 employees across five offices in Waterloo, New York, Seattle, London and Cork, Ireland, and has an international reputation for having pioneered managed detection and response services, in which incident response teams seek out and eliminate cyber threats for clients.
In its field, eSentire is considered an innovator. But to some observers, it exemplifies a concerning trend, that is, Canadian companies with huge potential being snapped up by larger U.S. firms or investors before they can grow into full-fledged homegrown success stories.
In the cybersecurity space, the evidence is overwhelming. An analysis of TSX, TSXV and CSE listings reveals only three publicly traded Canadian companies entirely devoted to cybersecurity. Combined, the market caps of Absolute Software Corp. ($355 million), Hilltop Cybersecurity Inc. ($4.5 million) and Quantum Numbers Corp ($6.5 million) make up 1.2 per cent of the most valuable U.S. cybersecurity company, Palo Alto Networks Inc. (US$22.7 billion).
(BlackBerry Ltd. is continuing to expand and focus on its cybersecurity division, most notably through its $1.4-billion acquisition of California-based Cylance, but the rest of the industry still does not see it as a pure cybersecurity company.)
Tyson Johnson, who is chief operating officer of CyberNB, a government of New Brunswick mandated agency that aims to grow the province’s cybersecurity space, said there are a number of factors contributing to the disparity between the U.S. and Canada. But what he always ends up circling back to is the consistent intervention from the south of the border.
For example, International Business Machines Corp. in 2011 absorbed Q1 Labs, a company founded in Fredericton, N.B., and turned it into its own security intelligence team. Japan’s Trend Micro Inc. in 2009 bought Ottawa-based Third Brigade when it only had 50 employees. Two years ago, Nielsen Holdings PLC came calling for Sentrant Solutions, another Fredericton-based company, just three years after it was founded. The financial terms of these deals were not released.
Johnson is concerned that the pattern of deals means a Canadian leader may never emerge in the sector, but he’s also worried about what that means for the country from a safety perspective.
eSentire president and chief operating officer Paul Haynes, left, and founder and chief innovation officer Eldon Sprickerhoff, right, stand in the company’s server room.
Canada, as a House of Commons committee heard in February, has been a target of consistent cyber attacks due to its NATO membership. But the government does not currently have a company it can rely on that uses Canadian-developed, -operated and -owned technology to fend off cyber crime and would have to rely on third parties in case of an attack. And with a third party, there’s always the chance of back doors being deployed, Johnson warns, or of these companies and their technology being used against Canada.
“What’s to say that the great technologies Canadian companies start up and innovate in today don’t get purchased and invested in by nations we are not as friendly with tomorrow?” he said.
Securing funding in Canada has proven to be challenging for many cybersecurity executives who feel like they may not have a choice but to look outward.
Like eSentire, most cybersecurity companies in Canada are built from the ground up when an entrepreneur such as Sprickerhoff has an idea for a new product or service.
It’s relatively easy to secure funding in Canada when you’re still developing a startup, Sprickerhoff said, because there are several angel investors willing to offer support.
According to the National Angel Capital Organization, 43 angels poured $162.6 million into 505 investments in 2017. That’s up from 2016, when 35 groups invested $157.2 million into 418 investments.
Moving into the scale-up space — where companies such as Q1 Labs, Third Brigade and Sentrant Solutions were before being sold — can create a different challenge.
As companies look to secure more capital, they’re left with fewer partners who are willing to fund them, Sprickerhoff said. Even in an early investment stage, it became more difficult for eSentire to secure “sweet spot” investments between $1 million and $5 million.
“There’s maybe only a dozen that would be willing to do a deal,” he said.
And there are only “two or three” that invest in the $15 million to $20 million range, he said. If they’re not interested, companies have little choice but to widen their scope outside Canada.
Case in point, eSentire once relied on two U.S. partners, Warburg Pincus and Edison Partners, to raise US$47 million to incorporate artificial intelligence into its managed detection response technology.
SecureKey Technologies Inc. founder Greg Wolfond is facing similar hurdles with funding, but is adamant that his company has a “Canada first” mindset.
“The belief in Canada is, ‘Let’s get lots of startups going,’” Wolfond said. “Let’s get a million dollars to this one and a million dollars to that one. These million-dollar companies aren’t going to give you broad and rich and deep cyber defence. You need scale-ups … that can scale to the size of big multinational companies.”
“There isn’t a mentality of let’s help the scale-ups and build a domestic cyber security practice and that’s really important,” he added.
The Toronto-based company, which specializes in software that assists major institutions to digitally verify the identities of their clients, is much smaller than eSentire — SecureKey has 97 employees in Toronto, San Francisco and Florida offices — but Wolfond has been able to keep his majority stake while finding major Canadian investors to help the company grow.
In Canada, SecureKey has found investors in each of the big six banks, as well as Desjardins Group, Rogers Communications Inc. and BCE Inc. “We’re a bit of an anomaly,” Wolfond admitted. That doesn’t mean he’s ignored U.S. funds completely as both Visa Inc. and Mastercard Inc. are two of his largest investors south of the border.
As Wolfond continues to grow his company, he may also reach the point where he’ll be faced with added pressure coming from the U.S. — either in the form of a company attempting to acquire it or an investor looking for a majority stake.
What would help keep companies such as SecureKey in Canada, Wolfond said, is additional investment from the federal and provincial governments.
Critics like Wolfond, Sprickerhoff and Johnson often describe the U.S. as thinking of cybersecurity as an extension of its military. Canada, however, has yet to get there, they said.
In its 2018 budget, the federal government announced it would be increasing its investment in the sector to $500 million over five years. The funds will primarily go towards ensuring the government and its agencies are safe, while also funding the creation of an RCMP unit to focus on cybercrime.
On Tuesday, the government proposed investing another $144.9 million over five years to continue to protect its cyber systems in finance, energy, telecommunications and transport sectors.
The government will also be funding innovation — the main concern brought up in a public consultation was that it needed to find a way to “ensure that startups and innovation born in Canada stay in Canada.”
The budget specifically mentions driving investment, cyber research and development, but does not specify how it will do so or how much funding — if any — will actually reach companies such as eSentire and SecureKey.
But where the Canadian government falters, the U.S. is more than happy to step in. Not-for-profit venture-capital group In-Q-Tel Inc. was launched in 1999 — 11 years before Canada even developed a cybersecurity strategy — and invests in companies producing technology for military use, particularly that of the Central Intelligence Agency.
In-Q-Tel currently funds two Canadian cybersecurity companies: Magnet Forensics Inc., based in Waterloo, and Interset Inc., headquartered in Ottawa. The amount In-Q-Tel invested is unknown, but the firm’s investments usually range between US$500,000 and US$3 million — a respectable investment for both startups and scale-ups that doesn’t involve a stake of the company being sold. There is no equivalent in Canada.
Worse, even to cybersecurity executives such as Wolfond and Sprickerhoff, is that the governments — federal and provincial — lean on larger firms such as IBM for cybersecurity services instead of contracting locally.
“It’s generally easier for me to get on a plane and fly to Hong Kong in 15 hours than it is to fly an hour to Ottawa and do business,” Sprickerhoff said. “We have a Canadian inferiority complex for our tech. Nobody ever got fired for buying IBM.”
The decision to outsource cybersecurity, Wolfond argues, is not just contributing to the exodus of companies, but of individual talent.
He hears it from the youngest talent any time he travels to Waterloo and walks around the local university campus. “They have this expression,” he said, “Cali or bust.”
For those making it, the move isn’t so bad.
When Sandy Bird co-founded Q1 Labs in Fredericton, his dream was to make one sale. He did much more than that, transforming the company into one of the hottest startups at the time and fielding multiple offers for a merger. He settled on IBM.
The entire Q1 Labs team became IBM’s security division with Bird helping to lead it as its chief technology officer, a role that often saw him splitting his time between India, Singapore and the U.S. “I had a job anyone would die for,” he said.
Q1 Labs had about 100 employees working in one Fredericton office when he made the sale. Now, under IBM that number has grown to about 300 he estimated.
There was no disappointment about losing the company he helped start or about giving up on not being able to build it to the point where he may have considered taking it public. That didn’t make the company a failure. In his eyes, it can’t be, considering it resulted in solidifying his own position in the sector, bringing additional jobs to Fredericton and seeing Q1 Labs’ technology become a leader in the market.
Some companies just aren’t meant to be taken public, he said, especially when they’re only earning in the low millions in sales per year and growing at a smaller rate. The better move in that case may be to look for an acquisition, he said.
After leaving his job at IBM, Bird decided to jump back into the private space when “my wife found me counting screws in the garage one day and sorting them into buckets and said you better go back to work,” he said, laughing.
Along with Brendan Hannigan, Bird’s Q1 Labs co-founder, they launched Sonrai Security Inc., which focuses on protecting cloud-based data, in 2017.
Like he did when he was at Q1 Labs, Bird has continued to turn to U.S. investors: “Why not go to the U.S.?” he asked.
Bird sees U.S. investors as a positive for the cybersecurity space. It’s a glass half-full mindset. Instead of sending stakes of Canadian companies to the U.S., he sees the move as bringing U.S. dollars to Canada.
He’s still not sure about an IPO, and neither are Sprickerhoff or Wolfond, although all three agree they would like to see one happen.
One thing Bird is sure of is that he won’t hesitate to pull the trigger on another sale if an opportunity such as IBM comes up and is the play that makes the most sense to him, his company and employees.
And Canada’s cybersecurity sector will remain without a champion.
Financial Post
Email: [email protected] | Twitter: VicF77
from Financial Post https://ift.tt/2UKF7u1 via IFTTT Blogger Mortgage Tumblr Mortgage Evernote Mortgage Wordpress Mortgage href="https://www.diigo.com/user/gelsi11">Diigo Mortgage
0 notes