#cyberattack statistics
Explore tagged Tumblr posts
Text
Network security services – Cybersecurity solutions in the new situation
Network security services – Cybersecurity solutions in the new situation
Information technology is existing in almost all areas of life, contributing to increasing work efficiency, saving time and costs. Besides these advantages, users also face many risks from loss, leakage of personal data, and organizational information and invasion of privacy when accessing the network. Therefore, network security service has becoming a necessary solution. Accordingly, Vietnam Ministry of Public Security proposed to consider cybersecurity protection services as business lines which are subject to conditions in the Vietnam Investment Law.

Personal data security lawyers in Vietnam
According to statistics in 2021, the Ministry of Public Security has recorded and analyzed nearly eight million warnings related to cyberattack activities, thereby detecting and verifying 2,763 cyberattacks targeting portal sites in the country (up 26% compared to 2020). In addition, cyberattacks tend to increase, causing political influence and greater economic losses. In addition, the situation of illegally collecting and infiltrating information and data of organizations and individuals for illegal purpose are increasingly complicated. The participation of network security services will contribute to strengthening the protection of the network security environment, especially important economic organizations such as banks, securities, state agencies, which are organizations that have vital role of the country.
On the other hand, the development of network security services is in line with the development policy of the country. Specifically, in Resolution No. 30 of the Politburo on the National Cybersecurity Strategy, the ultimate goal has been determined to reduce the risk of national security and social order and safety being compromised. Moreover, the Government has also issued Resolution No. 22 on the action plan to ensure national cybersecurity. Accordingly, the Ministry of Public Security shall assume the prime responsibility for formulating a Decree stipulating conditions for trading in cybersecurity products and services. Therefore, making network security services a business line is consistent with the current context and development orientation.
In addition, approving network security services will guide specific regulations and conditions for businesses. Businesses and organizations and individuals providing cybersecurity products and services will need to actively comply with regulations. The business conditions for network security services will ensure that network security products and services to be provided by reputable and capable service providers. Accordingly, improving policies and laws and improving the effectiveness and efficiency of state management of information, communication and network security will be a solid basis for cybersecurity services to demonstrate their functions and roles its important role in the overall development of the country.
Moreover, developing quality and effective cybersecurity services will create more opportunities and attract more foreign investors to participate in the Vietnam market. Most business activities now have involved the Internet connection, and therefore the risks such as information security and data security will be an issue of concern to investors making investment, setting up company in Vietnam. If network security services that support risk reduction and data recovery to help run business well, it will create confidence and motivation for investors.
The Ministry of Public Security expects network security products and services to include: (i) Confidential products to collect information (devices where hardware and software have the function of collecting information, documents, and data) via cyber – spyware; (ii) Security control products for network traffic (in which specialized hardware and software equipment for competent state agencies are designed with specific features to protect targets, systems, etc.) information system to warn, detect and prevent cyber security violations; (iii) Network security monitoring services, network security testing, knowledge training, network consulting, standards assessment. These are services and products that have practical applications and are capable of meeting the needs of individuals and organizations using cyberspace.
Therefore, although cybersecurity services have not yet been officially approved, in the current context, network security services will be an effective solution to work with the Government to build a digital environment and develop digital technology secure and sustainable information technology in line with the speed of global development. It is expected that when cyber security services are specified, it will promote a healthy, safe and effective cyber environment and hence promote the business and investment in Vietnam.
ANT Lawyers is a network security law firm in Vietnam located in the business centers of Hanoi, Danang, Ho Chi Minh city. We provide convenient access to our clients. Please contact our lawyers in Vietnam for advice via email [email protected] or call our office at +84 28 730 86 529.
2 notes
·
View notes
Text
Vietnam Cybersecurity Market to grow at a CAGR of 16.52% until 2026 – TechSci Research
Growing demand for digital services in the public and private sector is driving the growth of Vietnam Cybersecurity Market.
According to TechSci Research report, “Vietnam Cybersecurity Market, By Security Type (Network Security, Application Security, Cloud Security, Endpoint Security, Content Security & Others), By Solution Type (Firewall, Antivirus & Anti Malware, Risk & Compliance Management, Identity & Access Management, Unified Threat Management, Data Loss Prevention, Encryption & Decryption, Intrusion Detection/Prevention System, Infrastructure Security & Others), By Deployment Mode (Cloud & On premise), By End-User Industry (BFSI, IT & Telecom, Retail, Government & Defense, Healthcare, Education Technology & Others), By Region, By Top 10 Provinces, Competition, Forecast & Opportunities, 2016-2026”, the Vietnam Cybersecurity Market is forecast to grow at a rate of 16.52% to reach USD350.48 million by 2026. Growth in the market can be attributed to the leaning of the Vietnamese government towards investigating, detecting and prosecuting cybercrimes in the last few years. Vietnam has been ranked 25th out of 182 countries in Global Cyber Security Index (GCI) 2020 by the International Telecommunication Union – the United Nation’s ICT-specialized agency. Cybersecurity Market has been primarily influenced by the massive potential of cloud services in Vietnam. The National Assembly of Vietnam has adopted the Law on Cybersecurity (“LCS”) that aims to protect national security and ensure social order and safety in cyberspace. This law will act as a catalyst for adoption of cybersecurity by various enterprises. According to the National Cyber Security Centre (NCSC) of the Vietnam Authority of Information Security, in 2020, more than 90% of the cybersecurity products and services were made in Vietnam.

Browse 33 Figures spread through 70 Pages and an in-depth TOC on
" Vietnam Cybersecurity Market "
https://www.techsciresearch.com/report/vietnam-cybersecurity-market/7793.html
The Vietnam Cybersecurity Market is segmented by security type, by solution type, by deployment mode, by end-user industry and by region. In terms of security type, the market can be segregated into Network Security, Application Security, Cloud Security, Endpoint Security, Content Security and Others. Out of these, the network security segment registered a dominant market share in 2020. The network security is dominating the Vietnam Cybersecurity Market as it is one of the most important aspects to consider when working over the internet or the cloud. Moreover, robust network security systems help businesses reduce the risk of falling victim to data theft. Implementing network security solutions allows computers, users, and programs to perform their permitted critical functions within a secure environment.
Based on solution type, the market is segmented into Firewall, Antivirus & Anti Malware, Risk & Compliance Management, Identity & Access Management, Unified Threat Management, Data Loss Prevention, Encryption & Decryption, Intrusion Detection/Prevention System, Infrastructure Security, Others. Out of these, firewall solutions dominated the Vietnam Cybersecurity Market in 2020 as these solutions provide protection against outside cyber attackers by shielding the device or network from malicious or unnecessary network traffic.
Based on deployment mode, the Vietnam Cybersecurity Market is bifurcated into Cloud & On-premise. Cloud dominated the market as the cloud computing technology is being widely adopted by the country. According to the Ministry of Information and Communications, in recent years the cloud computing market has been growing at 30 percent on average, and in 2020 the growth rate reached 40 percent due to the COVID-19 pandemic.
In terms of end-user industry, the market is segmented into BFSI, IT & Telecom, Retail, Government & Defense, Healthcare, Education Technology, Others. The BFSI industry dominated the Vietnam Cybersecurity Market in 2020. Digital transformation of banking sector has changed the consumer buying behavior with preference for online shopping. The banking firms are investing aggressively into cybersecurity in quest to protect the customers’ personal information, passwords, and financial information from cybercriminals.
Viettel Cyber Security Company, FPT Corporation, CMC Cybersecurity, IBM Vietnam Company Ltd., HPT Vietnam Corporation, Microsoft Vietnam Limited Liability Company, Amazon Web Services Vietnam Company Limited, SAP Vietnam Co. Ltd., Vietnam Posts and Telecommunications Group, Salesforce.com, Inc., Cisco Systems, Inc., CrowdStrike Holdings, Inc., FireEye, Inc., McAfee LLC, Accenture, Inc. etc. are among the leading players operating in the Vietnam Cybersecurity Market. Companies operating in the market are using organic strategies, partnerships and collaborations to boost their shares in the Vietnam Cybersecurity Market. Significant players in the market are concentrating on accomplishing ideal operational expenses, upgrading the system efficiency, enhancing precision in responses, boosting productivity with high funding in R&D, and merging with small players to support the competitive Vietnam Cybersecurity Market.
Download Sample Report @ https://www.techsciresearch.com/sample-report.aspx?cid=7793
Customers can also request for 10% free customization on this report.
“The digital transformation of the country including e-Government, e-business, and an e-society will drive the growth of the Vietnam cybersecurity market. Moreover, the passing of the “Law on Cybersecurity” in 2018, has encouraged Vietnamese firms that use advanced technologies and solutions to invest in cybersecurity which has led to the development of ecosystem of 'Make in Vietnam' cybersecurity products. This growing awareness of the consumers towards cyberattacks and regulatory measures being taken by the government to protect the cyberspace is expected to act as a catalyst for the Vietnam Cybersecurity Market.” said Mr. Karan Chechi, Research Director with TechSci Research, a research-based global management consulting firm.
“Vietnam Cybersecurity Market, By Security Type (Network Security, Application Security, Cloud Security, Endpoint Security, Content Security & Others), By Solution Type (Firewall, Antivirus & Anti Malware, Risk & Compliance Management, Identity & Access Management, Unified Threat Management, Data Loss Prevention, Encryption & Decryption, Intrusion Detection/Prevention System, Infrastructure Security & Others), By Deployment Mode (Cloud & On premise), By End-User Industry (BFSI, IT & Telecom, Retail, Government & Defense, Healthcare, Education Technology & Others), By Region, By Top 10 Provinces, Competition, Forecast & Opportunities, 2016-2026” has evaluated the future growth potential of cybersecurity in Vietnam Cybersecurity Market and provides statistics and information on market structure, size, share and future growth. The report is intended to provide cutting-edge market intelligence and help decision makers take sound investment decisions. Besides, the report also identifies and analyzes the emerging trends along with essential drivers, challenges and opportunities present in Vietnam Cybersecurity Market.”
Browse Related Reports
Vietnam Artificial Intelligence Market By Component (Hardware, Software, & Services) By Technology (Deep Learning, Machine Learning, Natural Language Processing, Image Processing, Others) By Deployment Mode (Cloud-Based & On-Premises) By End-Verticals (Healthcare, Retail, BSFI, Automotive, Advertising and Media, Manufacturing, IT & Telecom & Others), Company Forecast & Opportunities, 2026
https://www.techsciresearch.com/report/vietnam-artificial-intelligence-market/7684.html
United States Automated Labeling Machine Market By Type (Self-Adhesive/Pressure-Sensitive Labelers (Apply Only, Print & Apply), Shrink-Sleeve/Stretch-Sleeve Labelers, Glue-Based Labelers, In-Mold Label), By Configuration (Stand Alone, Integrated), By Industry (Food & Beverage, Pharmaceuticals, Consumer Products, Personal Care, Others), By Method of Label Placement (Front & Back/Double-Sided, Side, Top & Bottom, Wrap Around), By Packaging (Glass, Metal, Paper/Cardboard, Plastic), By Region, Forecast & Opportunities, 2026
https://www.techsciresearch.com/report/united-states-automated-labeling-machine-market/5090.html
Vietnam Mobile Wallet Market By Type (Remote, Proximity) By Technology (Near Field Communication (NFC), QR Code, Digital Only, Text-based) By Application (Bill Payment, Mobile Recharge, Money Transfer, Micropayment & Others) By Industry Vertical (Transportation, Media & Entertainment, Retail, Healthcare, Energy & Utilities, Telecommunication and Others), By Region, Company Forecast & Opportunities, 2026
https://www.techsciresearch.com/report/vietnam-mobile-wallet-market/7683.html
About TechSci Research
TechSci Research is a leading global market research firm publishing premium market research reports. Serving 700 global clients with more than 600 premium market research studies, TechSci Research is serving clients across 11 different industrial verticals. TechSci Research specializes in research-based consulting assignments in high growth and emerging markets, leading technologies and niche applications. Our workforce of more than 100 full-time Analysts and Consultants employing innovative research solutions and tracking global and country-specific high growth markets helps TechSci clients to lead rather than follow market trends.
Contact
Mr. Ken Mathews
708 Third Avenue,
Manhattan, NY,
New York – 10017
Tel: +1-646-360-1656
Email: [email protected]
#Vietnam Cybersecurity Market#Cybersecurity Market#Vietnam Cybersecurity Market Size#Vietnam Cybersecurity Market Share#Vietnam Cybersecurity Market Growth#Vietnam Cybersecurity Market Forecast#Vietnam Cybersecurity Market Analysis
2 notes
·
View notes
Text
Phishing Protection: What Types Of Phishing Scams You Should Know About?
Phishing scams are becoming more common and sophisticated. The best way to protect yourself against these types of cyberattacks is to become aware of the different types of phishing scams that exist, as well as how each may impact you. This blog post will walk you through some of the most popular types of phishing attacks.
Regardless of how they are targeted, phishing attacks take many roads to get to you and most people will likely experience at least one form. These include:
Phishing Emails
A popular type of cyberattack is the email phishing attack. It appears in your inbox, usually with a request to follow some kind of link or send them money, usually it's just an attempt for private information like bank account numbers. The sender can look very authentic depending on how much they care about getting their hands on what you have available now.

Voice Phishing
Voice phishing (vishing) scammers call you and try to disguise themselves as a genuine person or company in order to deceive unsuspecting victims. They might direct you from an automated message, masking their phone number with which they contact you while trying not to let go of any information that could be used against them later down the road. Vishers will always keep your attention by being friendly but convincing at first before getting more intense towards the end.
Domain Spoofing
A false address that looks like it belongs to a legitimate company can be confusing, especially if you are searching for the matching domain. Scammers use this confusion as an opportunity and try their best to take advantage of people by counterfeiting emails or websites in order to lure them into giving out personal information such as credit card numbers or worse yet passwords.

SMS Phishing
SMS phishing is a scheme in which you will be fooled by an SMS message that imitates the voice of an organization using urgency to get your attention. In these messages, there may also be links or phone numbers included for users who want more information on their offer from whoever sent it out. The risk with mobile messaging services comes from this type of scamming attempt since any contact received through them could potentially have been engineered specifically as part of such schemes.
Social Media Phishing
To avoid being scammed, be aware of the signs and read posts closely. Social media phishing can happen through posts or direct messages on Facebook where criminals try to get you into their trap by using fake names with links that look like they came from your friends. These tricks may sound obvious but many people still fall victim every day so make sure not to let yourself become another statistic.
Business Email Compromise (BEC)
When a company’s network and systems are not protected, they may be vulnerable to hackers. One way this can happen is through Business Email Compromise (BEC). This occurs when one actor takes over the identity of another person by masquerading as them or sending fake invoices that request sensitive info such as wire transfer requests from CEOs for payment processing without their knowledge.
Conclusion
The best way to protect yourself against phishing scams is by educating yourself and your employees on the different types of schemes that are out there. A little knowledge can go a long way in keeping you from falling victim to this type of cybercrime.
1 note
·
View note
Photo
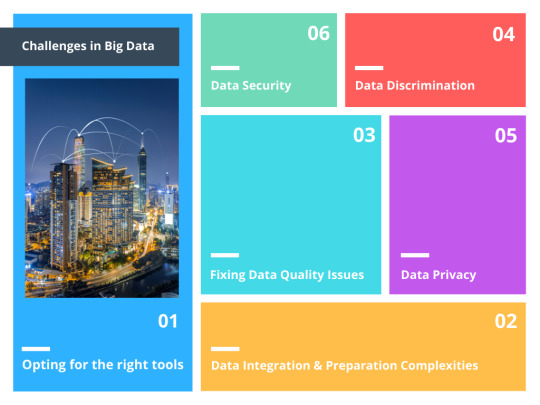
1) Opting for the right tools:
This decision must be made keeping in mind the following factors:
Vendor lock-in – No situation must arise where the business needs to migrate to a different set of tools before 5 years after the contract is signed.
Real-time processing – Future pace of data generation must be met with the existing set of tools.
Scalability – Tools must support serving additional capacity through public cloud.
Flexibility – Schema of the tools must be adaptable to data formats that evolve over time.
Integration – The NoSQL tools must be able to work with the traditional RDBMS without any technical challenges.
2) Data Integration & Preparation Complexities:
Big Data platforms enable collection and storage for large amounts of data of different types and quick retrieval of data that’s needed for analytics purposes. For an optimal ROI, a data integration standard must be implemented so that insights are drawn on all the data.
3) Fixing Data Quality Issues:
The analytics algorithms and artificial intelligence applications built on big data can generate bad results when data quality issues creep into big data systems. Data quality issues can arise from duplicate entries and human typos in the input streams. Corrective measures must be enforced to ensure that the quality of data collected is good. Such measures can help improve the accuracy of the business insights generated by analyzing the data.
4) Data Discrimination:
Companies should prevent data discrimination by ensuring :
The data is a representative sample of all the consumers
The algorithms prioritize fairness
They are aware of the biases in the data
They are checking their Big Data outcomes against traditionally applied statistics practices
5) Data Privacy:
The Big Data system collects all the information about a consumer to gain insights from their buying history and browsing preferences. Hence, as an ethical practice the business must ask for a consumer’s consent before using their personal data for commercial purposes.
6) Data Security:
Consumer Data collected by a business must be secured from threats using encryption in the Big Data system. This will prevent the consumer data from falling into the wrong hands. Advanced analytics to detect any potential security breaches and data loss can be employed by the business to foil any cyberattack in the distant future.
A business must ensure their team of data scientists deals with all of the challenges enlisted above in order to build robust and maintainable Big Data systems.
References:
Big Data, big challenges: 8 obstacles that must be surmounted
3 Massive Big Data Problems Everyone Should Know About
1 note
·
View note
Text
Angst!AU
First off, thanks to the anon ask that sparked me actually writing this out. It’s been a rough week. But this was fun. Second, it’s a draft and details may change when I actually get around the writing the fic.
The Jesse on Route 66 chapter takes place a little before this.
“He’s four hundred meters out. The vehicle is heavily shielded. I have not detected an escort.” Zee’s drone floated beside your hovercycle. “But this is still ill-advised.”
You shrugged, idling on the low rooftop, taking cover in the shadow of a massive viewscreen advertising a new fantasy drama. The actors were pretty, but the fight choreography looked too stilted. If you were at home, you would probably be bullied into watching it. If anyone still wanted to be in the same room as you.
“You can request backup.”
“Don’t need it,” you said, mapping the trajectory of the armored car. If it was just the one vehicle, Zee was enough. You just had to get her through the physical barrier of hardened shielding. She could penetrate the firewalls on her own. And more importantly, Zee was the only one not mad at you right now.
“They would come.”
You frowned. It was really unlike Zee to harp on this shit. “It’s not necessary.”
“Neither is going after Cian Barrett on your own.”
“I’m not on my own, I have you,” you said, not taking your eyes off the car. In this moment, you could almost forget that she wasn’t Athena. You could forget that Athena wasn't really Athena any more. You could forget that Blackwatch was nothing more than a memory of scandal. You could forget...so you did. That part of your brain wasn’t necessary for this job.
It was like slipping into your old armor. It was like coming home. The world faded away. There was you, Zee’s drone, and Barrett’s car. Everything else was secondary.
There were no identifying marks on your bike or your armor. The form-fitting suit was all matte black and shielded for direct combat. The helm, styled after a motorcycle helmet, covered your features entirely. Not your usual outfit, but your “Keres” identity had political links. Best to be incognito for now.
The sun was just beginning to dip, and the traffic was heavy. Zee would be able to jam the emergency transmissions, but there would be a lot of witnesses. There would be calls to emergency services. You were running this operation in broad daylight, and you couldn’t summon the urge to care.
“This is very reckless,” Zee said.
“Yeah, but Hong Kong is our territory,” you said, gritting your teeth behind your helmet. “Are you saying we can’t do this in our own backyard?”
“...It’s the only reason I’m agreeing to it,” Zee said primly. “But this is our backyard. Try not to shit where we eat.”
You chuckled, a little surprised by her use of profanity. “It’s nothing you can’t handle.” He was three hundred meters out. The overlay on the inside of your helmet fed you more statistics. The vehicle’s armoring class was higher than you expected, but it had side windows. Windows were always a structural weak point. You waited for Barrett’s car to reach the next intersection.
On cue, the light shifted to red, stopping the car in front of him. There was a slight reverberation as Zee tethered her drone to your bike.
You shifted gears, and then suddenly you were dropping forward, accelerating even as you fell.
Barrett’s car was a thick monstrosity, black and purple, custom-made by Vishkar: hard light kinetic shields, front and rear turrets, a Farraday cage overlay to prevent hacking. All of that was geared to stop bombs, guns, or cyberattacks. None of it would stop you.
You leaned into the turn, holding yourself at 45 degrees off the ground, the bike still accelerating as you slipped into traffic. You pulled yourself upright so you could slide between stopped cars. You took the innermost lane hovering on the border of oncoming traffic.
Barrett’s stopped car was just ahead.
“Cut it,” Zee said.
You released the controls, letting her take over as you drew the spike. Eight inches of hardened omnium, the point already starting to glow with heat. It was a simple tool, perfect for shorting out Farraday cages and breaking glass. Feet jammed in the stirrups, you rested your left arm across your chest, the spike in your metal hand. Powering up the prostheses and the tool took half a second. And as you passed Barrett’s car your arm snapped sideways, driving the metal into the glass with inhuman force.
You pierced a thick line through layers of glass, polymer shielding, and then tore through the metal frame, breaking the continuous line of the circuits. Now there would be a hole in the hard light armoring and the Farraday cage. In seconds, the spike grew too hot to hold, so you let it go, swinging yourself off the bike. You just had to carve the hole. Zee would open the way.
“I’m in,” Zee said, as the locks popped.
Grinning savagely behind your helmet, you yanked the door open, even as someone within emptied their gun at you. You jerked back behind the door, getting a glimpse of an omnic bodyguard switching weapons.
“Zee?”
“Working on it,” she snapped.
If you’d been alone, you could have used an EMP, but if you’d been alone, you wouldn't be able to pull the data from his devices. And that was more important than simply killing Barrett. Not that you planned on sparing him. Not after what Sakai had let slip. It had taken a lot of work, but in the end, you’d gotten what you needed from what was left of- You winced inwardly. You didn’t need to think about that right now.
You drew your gun, angled it, and fired into the car at where the bodyguard had been sitting. You heard the shots connect, metal rending metal.
“Watch where you’re shooting,” Zee snapped.
You were never in any danger of hitting her, but if your bullets made it out of the vehicle... You gritted your teeth. A ricochet probably wouldn’t kill a civilian. You swung around the door, gun raised.
The omnic was a smoking wreck. An armored woman lay bleeding on the ground.
An older, dignified “gentleman” in a suit, Barrett was pressed against the partition, his own weapon raised at you. But his hands shook violently. There was blood on his face and in his gray hair, but you didn’t see any serious wounds.
“Where is she?” You snarled.
“I don’t know whom you’re talking about!” Barrett shouted defiantly, words blending together in his thick brogue.
“I think you do,” you sneered, taking aim at his knees.
“Incoming!” Zee shouted as light flared in your peripheral vision.
Three things happened at once. The delivery van in a neighboring lane opened up, half a dozen armored Talon troopers pouring out. And then a sunburst struck the front of Barrett’s car. You dove to the side, taking cover behind the rear bumper of the vehicle, and then a wave of force rolled you under the next car as an explosion rocked Barrett’s vehicle-though it didn’t come apart. All around you, car windows shattered from the concussive blast.
“Is that-?” You winced, dragging yourself out from underneath a jeep.
“No, not one of ours,” Zee said sharply. “You need to get out, now.”
“KA-BOOOOM!” The voice was male, the accent distinctly Australian. You blinked as you watched a heavily singed blonde man kick Barrett’s front tire. “Hahaha! You’re blowing up! And this tire is blowing out!”
You staggered to your feet, ears ringing. There were armored Talon troopers sprawled across the asphalt. And twenty yards away, Cian Barrett was rabbiting down the crowded streets.
“Fuck,” you snarled.
“Move!” Zee shouted in your helmet more forcefully than you’d heard in a long time. You ducked low, running past prone troopers.
“How did you miss them?” You hissed.
“-I don’t know,” Zee said, her voice distant in your hear. “Transmitting this back to base.”
“I think they’ll see it on the news,” you huffed.
There was a ping in your helmet as someone tried to call you. You ignored it.
“There’s no way they know about Sakai,” you growled. Because the only people who knew what you’d done to Sakai and how you made her talk, well, they were on your side, even if they weren’t very happy with you right now.
“This isn’t for you,” Zee said, even as a Talon trooper raised her gun at you. “Drop!”
You dove forward, rolling through a brackish puddle, splashing foul liquid everywhere. It was good thing you were wearing a helmet.
“Come here.” A chain shot over your head, a massive hook sinking into the woman’s armor, and suddenly she was airborne. You turned your head, watching as a massive man in a gas mask yanked her to him.
“What the hell?”
“Junker mercenaries,” Zee said. “They’re here for Barrett too. Avoid them.”
“Lucky, you butthead! I know you can hear me! I know this tech can withstand bigger explosions, even if Hong Kong can’t! What the hell is going on?” A very familiar, very angry voice shouted over the comms. Someone had hacked your settings, not hard considering it was her hardware to begin with.
“Busy!” You shouted, trying to catch sight of Barrett. In the distance you saw an older European man rounding a corner-
“Yeah, well so am I! I have the fucking Minister of State Security on hold! Auntie has shorted out the power grid in a six block radius. Oksana is trying to take out any peripheral electrical surveillance. What in the ten hells do you think you’re doing?”
You flinched. “I was going after Barrett. But I’m not the only one.” You hesitated. “We didn’t know about the backup. Or the Aussies.” You didn’t say whether or not you would have still made the move if you had known. Better not to go there.
There was a moment of distracted silence. She was verifying your claim. “I see that...OK. Look, you need to get out of there. Those Australians can take the fall. You don’t need to get caught up in it any more then you already are.”
“Barrett has information I need,” you said tightly, vaulting over a low wall as you dodged down an alley, running parallel to the street you saw Barrett turn down.
There was a heavy sigh. Because they all knew what you would do to get that information.
“Give me some more time, Lucky. We can find them too. You don’t need to cut the answers out of every single Talon agent you dislike.”
“It’s therapy,” you hissed, swearing as dirt and garbage erupted behind you. A concussive blast nearly knocked you off balance. “You’re always telling me I need more of that.”
“This bomb’s for you!” The Junker cackled, rapidly closing the distance.
You swung around, raising your gun.
The Junker blew past you, literally hoisted by his own petard. He just waved, winking at you as he rocketed through the air.
Behind him, three more Talon troopers surged forward.
So many targets, but it wasn’t a hard decision.
The visor of your helmet overlaid the shot trajectories, even as you raised your gun in your left hand. Three T-Zone hits, three corpses toppling. The skill was unnatural as fuck, but you wouldn’t argue with the results.
You turned back to see the Junker, with his goddamn peg-leg, meters ahead of you. He squinted at you for a moment.
You surged forward.
“Oh good, I had no idea where he went!” The Junker chuckled as you passed him. In that moment, he tossed something in front of you, even as you jerked to the side, narrowly missing a steel-jawed trap.
“Aww, c’mon,” he groaned.
You just shook your head and kept moving. You were very tempted to shoot him, but if Talon was here for him and the big guy, then you might be better off letting him live. The old you might have been more concerned about the chaos. But Cian Barrett was getting away. And that was unacceptable.
“Zee, I’ve lost visual contact. Do you-”
“He’s two blocks north,” another voice chimed in. “You can cut though that alley up ahead and jump the fence.”
You inhaled sharply. After what you had done to Sakai, you didn’t think she’d speak to you for another year or two. And maybe you deserved that. “Thanks,” you said after a moment.
“Yes, well, be more careful,” she said quietly. “I’m mad at you, but I’ll be even madder if you die before we can talk about it.”
Dying might easier. But you were smart enough not to say that out loud. “I’ll be home tonight,” you said. “If I can wing it.”
“Kara misses you,” she said hesitantly, in a way that might mean someone other than Karalika missed you. Which made you smile in spite of the situation. Karalika probably did miss you, but she’d be fine. Everyone else spoiled her.
“Yeah, and if you make a bigger mess of this, I’m going to feed her sweet bean paste till she shits all over your room! Picture it! Bean shits everywhere!” Your “boss” shouted over the comms. “You’ll be mopping the goddamn ceilings for days!”
If that happened, maybe you’d stay in Hong Kong a little longer. You turned down the alley, still hearing the peg-legged Junker hopping along behind you. The fence was three meters high but you leapt onto a closed dumpster, pushed off a support pole, and flung yourself over the chain links. You dropped down with a heavy thud and picked back up.
“Zee, you have my ride ready?”
“In a minute,” she said, sounding distracted. It should not have come as a surprise, she was balancing a larger workload now.
With the explosions nearby, the crowds were thinning. You scanned the street- And there he was! A few blocks up, Barret shoved a street vendor and tried to duck into a shop.
You moved quickly through the press, following him into the little electronics stand.
Sweaty and disheveled, he slumped against a headphones display, panting. He was not doing a very good job of hiding. You glanced sharply at the shopkeeper who ducked into a back room.
Raising your gun in your right hand, you seized him by the collar. He flailed vainly against the metal.
“Wait! No! My people will pay handsomely for safety!”
You held up him by the throat, watching him twitch and shake, fear in those pale gray eyes. Your helmet was opaque. He would not see anything but his own distorted reflection. “Your money means nothing. I want information.”
“I-I-” He stammered.
“Widowmaker,” you snapped. “Where are they storing her?”
He shook his head frantically. “I don’t know!”
“Agent Sakai seemed to think you did,” you growled.
“That was a month ago! I don’t keep close tabs on all combat assets.”
“Bullshit! Where the hell is she?!” You squeezed tighter, rage making your arms shake.
“I don’t have a fucking clue!” He shouted back. “They keep the freaks with O’Deorain. Widowmaker, Sigma, Reap-”
Glass smashed as a giant hook hurtled through the storefront. You spun, holding up Barrett as your shield. That thick chain wrapped around his waist.
Maniacal laughter sounded, far too close. It made your blood run cold. The giant Junker was huge, and only wearing bits of armor, with lots of visible flesh. The piggy tattoo on his bulging stomach said “Wild Hog Power.” Barrett screamed as “Wild Hog Power” reeled him in.
It really wouldn’t do for Barrett to be ransomed. He was Moira’s financial advisor, and one more nail in her treacherous coffin. You slapped your gun back into your left hand, letting your helm’s targeting software direct your shot.
A neat red hole burst in Barrett’s skull. Much neater than Sakai had been. But Sakai had been personal.
“Wild Hog Power” shook Barrett like a doll, the corpse flopped around, neck flopping at an extreme angle. “Wild Hog Power” was breathing hard, hunched over Barrett. Bestial and berserking, this one was less human than most. He looked up then, clocking you instantly. He began spinning his chain.
Your insides shriveled, an atavistic reaction. This was a very dangerous place to be. “Zee-”
“Go out back!”
You jumped the counter, narrowly dodging that damn hook. More gunfire blew over your head, and you rapidly crawled out the back exit, finding your hoverbike waiting.
“Thanks!” You hissed, even as you hopped aboard, staying low. “Chances of extraction?”
“Not any time soon,” your boss huffed angrily. “I’m busy doing damage control. Looks like there was a lot of it- mostly property, but also quite a few civilians with shrapnel injuries. Hospitals will be overcrowded. We’re offering additional support to the locals. You can lay low for now.”
“Understood,” you said. Your safehouse not too far off. Checking your mirrors, you saw the Junker pair standing together in your dust, watching you make your escape.
**
You went radio silent. You were sore, but you’d gotten off lighter than you deserved, given the amount of mayhem you’d helped instigate.
Your safehouse was well-stocked and decorated to someone else’s taste. It was filled with Pachimari paraphernalia, though there were all kinds of stuffed animals on the couch. Kittens, hamsters, even a piggy. You shuddered slightly. “Wild Hog Power” had taken Barrett mid-sentence, but you’d already known about Reaper. Sakai had spilled everything in end, both figuratively and literally.
You showered first, setting aside your battered gear for repairs. Then you changed into sweats. You considered external healing, but there was no need. As long as you got a good meal, you’d be back in fighting shape after dinner.
The kitchen was full of novelty appliances and decorated in an alarming shade of pink enamel: the fridge, stove, sink, cupboards, everything. You’d been here a week and you still weren’t used to it. But it wasn’t all terrible, there was a bubble tea maker, and you fiddled with that – doing it from scratch wasn’t hard. But the machine took a few minutes to set up. You started the rice cooker too.
You had filled the fridge yourself, with fresh groceries and a beautiful raspberry chocolate cake covered in ganache. You were still working on improving your recipe for fish head curry. The freezer was packed with dimsum. Idly, you began heating up a pan of oil. Your body needed a lot of calories post-combat and cooking gave you some time to meditate.
The Talon troopers had not stepped in to save Barrett from you. Talon had not been waiting for you. They’d only come out when the Junkers were in range. So Talon had been expecting those Junkers. Your helm had captured enough footage that you could research the men. Zee had forwarded a large file to you.
The demolitionist was a man named Jameson Fawkes. He was a caricature of all the shitty, fried, explosion-happy maniacs you’d met through the years. Nwazue had been painstakingly responsible. Hell, Vo had been a pain in the ass, but- You exhaled slowly. Vo hadn’t been so bad. Not really. You stared at the fridge. She would have loved that cake.
“Wild Hog Power” was a man named Mako Rutledge. There wasn’t a lot of information about him. But you knew “incredibly dangerous” when you saw it. Both men had accumulated massive bounties and were wanted in several countries. You’d be surprised if they made it out of Hong Kong alive.
But that wasn’t your problem, you didn’t need to go borrowing more trouble. You had more than enough.
Your problem was how to save Widowmaker, especially since she didn’t especially want to be saved.
Your problem was that you knew exactly who was wearing that stupid skull mask and calling himself Reaper. But you didn’t know why, and that was just as awful. You had theories, of course, but even the best case scenario made you sick to your stomach.
Your problems all stemmed from the past, the sort of unresolved bullshit that only worsened over time. Jesse had been trying to get in contact with you, but you’d been putting him off. You still weren’t sure if you wanted to see him now, no matter what kind of intel he offered.
But you would, eventually. Not because he’d been your friend. Not because you were ready to forgive him. Not because you missed him. But because you needed every advantage you could get in this war.
“Lucky, you need to see this.” Zee’s cultured voice came on over the sound system. A security monitor flicked on. You stared incredulously as the two Junkers traipsed up the stairs and through the halls on the building, clearly looking for someone. They were still several floors below you. You had no idea how they’d tracked you here.
You could run. You knew this city pretty well. There might not be fighting. There might be more collateral damage. It was hard to say.
You could fight. The building was not unoccupied. It would not survive. There would be more collateral damage.
You could try diplomacy. But you weren’t entirely sure if those men were capable of rational thought. The Junkers were insane. Look what they had done to their own country. You certainly didn’t want to invite them in but...
But the enemy of your enemy was useful to know.
You went back upstairs to change clothes.
**
It only took them a few minutes to reach your door. But you were ready. You had changed into a simple black jumpsuit. It was short sleeved and with a flattering cut, the fabric draped elegantly. You put on makeup, just enough to be a polished hostess. You didn’t play a honeytrap any more. Not if you could help it. Your only jewelry was a thick white band around your left wrist. It had a pearlescent glow against your dark metal arm. You took a deep breath, checking the cameras and finding them loitering outside your door, Fawkes fiddling with a goddamn mine, Rutledge blocking the entire hall.
You opened the door, and stared coolly at Fawkes, wondering if he would really detonate the bomb right here. He better not.
“Eh?” Fawkes gaped at you, clearly shocked that you’d just opened the door.
“What are you doing?” You sighed, one hand on your cheek. You sounded more like an exasperated teacher than a security operative. That was intentional.
“Err...nuffink.” He shoved the mine behind his back like a child. Up close, he was younger than you first thought, though life had not been kind to him. He was scorched and sooty, patches of hair missing, his clothing near rags. It didn’t look like he cared.
Behind him, Rutledge regarded you silently, possibly surprised that you had answered the door without attacking, possibly trying to identify you as the woman on the bike. But with the mask in place it was too hard to tell.
“You were-” Fawkes jabbed his finger at you accusingly.
“Yes, I was there,” you said.
There was another awkward moment of silence as they tried to process your declaration. Honesty was certainly the best policy, when it got you a tactical advantage.
You regarded them politely. “Well then, are you going to come in for dinner?”
There was another long stretch of silence as the men looked at each other trying to figure out if you were being sarcastic.
Rutledge tilted his head back, and you realized he was sniffing the air.
Fawkes blinked rapidly. “I don’t like prawns.”
“Are you allergic?” You asked, stepping back to let them come in.
He glanced back at Rutledge, panic on his face. This was not how he pictured the encounter going. You didn’t think most people he met invited him inside for a meal.
“No,” Rutledge said. His voice was low and dangerous.
“No, just don’t like’em,” Fawkes fidgeted, and then shoved the mine down his pants.
You nodded. “There are slippers if you want,” you gestured to the shoe rack by the door. It was good manners to take off one’s shoes, though you weren’t going to press the matter with them. You walked back to kitchen, not looking to see if they used them. You walked down the hall, half expecting a bullet or a hook in the back. You fiddled with your bracelet, trying to keep your stance relaxed.
There was a crashing noise, and you flinched, before looking over your shoulder, to see Fawkes trying to shove the broken shoe rack into some semblance of its previous shape. Rutledge was holding up a very large pair of Pachimari slippers. They would have fit Reinhardt. You had no idea if they would fit him, but your support staff stocked a broad range of sizes.
There was a distinct rhythm as Fawke’s leg clicked against the wood. But it sounded like he was wearing a single slipper. Maybe one of those furniture leg felts would work on the peg-leg. You had not considered that. He followed you from the foyer into the kitchen. You went to the freezer and pulled out the rest of the dimsum. You could steam the dumplings, sticky rice packets, and bao, and maybe you’d have enough for Rutledge.
“Whatcha making then?” Fawkes asked, looking around the kitchen in wonder. He sniffed the air a few times, his eyes bright. He had terrible posture, shoulders hunched as he eyed the stove with distrust.
“Fishhead curry and dimsum.” The curry was still simmering. “Would you like something to drink?” Coffee in the jittery demolitionist would be unwise. Alcohol might be worse. You checked the bubble tea machine. “I have milk tea with boba.”
“I would kill for some!” He nodded vigorously, rubbing his hands together.
“Sugar?” You asked, your metal fingers twitching as you poured.
“Half!” He did not have an indoor voice.
The machine dispensed bubbles, tea, and sweetener according to his order. You offered him a cup with a metal straw.
Squealing, he took the drink from you and then Rutledge reappeared. Without a word, he snatched the cup out of Fawkes’ hands, popped off the lid, and sniffed. Then he looked at you.
You poured yourself a cup and took a drink. Using poison had definitely occurred to you, but with Rutledge’s clearly altered biology, there were too many variables. The tea was a little too sweet, but the tapioca bubbles were the perfect texture.
“Come on, pig face! If it ain’t poisoned, give it here!” Fawkes grabbed for the cup. Rutledge let him take it back, apparently not bothered by the name calling.
“Would you like some?” You asked, taking another drink. You had beer, but you purposefully did not want them drunk. You didn’t need them rowdier.
“Full sweetened,” Rutledge said after a moment.
You nodded and made him a cup as well. You gestured to the round table. “Please, have a seat.” The chairs would probably hold. Your boss got a kick out of making equipment way more durable than it needed to be, just for fun.
Fawkes straddled a chair, slurping his drink and watching you intently like a feral animal.
Rutledge carefully sat down, adjusting his mask so he could drink.
“Fancy pad,” Fawkes said, clearing his throat while he looked around.
“A friend’s place, I’m only visiting,” you said, not exactly lying. You stirred the curry. It was fragrant with spice and coconut milk, but needed to thicken a little more. You checked the steamer, finding the shrimp dumplings and the soup dumplings to be ready. You placed the metal steamer tray on a mat on the table and gestured to the cupboard. “Bowls and plates are up there. Chopsticks and silverware are in that drawer.” You returned to the stove. The oil was hot enough for the deep fried taro pouches. You tossed them into the oil, watching them sizzle.
“Ooooh,” Fawkes was suddenly over your shoulder. “Wozzat?”
“Fried taro, with ground pork filling.” You paused, glancing over at Rutledge. He was eyeing the steamer tray of dumplings. He had not gotten up for plates or silverware. “The yellow and kind of translucent ones have shrimp,” you told Fawkes, gesturing at the food on the table. “But the round white ones are pork.”
“Eww,” Fawkes scowled at you. “I don’t like prawns. Buggy little bastards taste like shite and are filled with-”
“You don’t have to eat them,” you said firmly. “But where I grew up, there wasn’t food to waste.”
Fawkes squinted at you. “But here you are in this fancy city pad-”
You flipped the fried taro with cooking chopsticks.
“-Stealing work from honest Junkers, and acting like-”
You had to maneuver around him to get a plate for the taro. He was getting worked up. You glanced briefly at your left wrist, wondering if you had made a mistake.
“Get out of the way,” Rutledge barked. “Can’t you see that she’s busy?”
You raised a brow, a little surprised by that reaction.
Fawkes was too. He blinked inquisitively at his partner.
“Be useful: set the table,” Rutledge said gruffly.
Fawkes snapped to attention then, skittering over to the cupboard to grab plates and utensils. You turned back to the roiling oil and began fishing golden brown taro cakes out of the pot. You filled the plate, and set it down on the table. They were steaming hot and would burn your mouth. Rutledge sat there stoically, watching your every move. He had not touched the food. In the corner of your eye, you saw Fawkes gracelessly slapping a handful of silverware onto a stack of plates.
You set the rice cooker on the table and checked the steamer trays. The sticky rice and bao were done. And the fish head curry was a deep orange color, with pieces of okra, taro, and eggplant cooked soft in the sauce. You would have liked to simmer the sauce a little longer, but you couldn’t help the timing. You turned around to see Fawkes seated with two forks and a bowl. It looked like you had two spoons, a bowl, and a plate, and Rutledge had two plates and pair of chopsticks.
You brought the pot of curry to the table, and then went back to retrieve more utensils and rice bowls. You set them in the middle of the table, and started scooping rice. You passed the bowls around, noting that still none of the food had been touched. Paranoia or manners?
Fawkes straddled his chair, surveying the table greedily.
But Rutledge looked at you expectantly.
“I am not religious,” you said, unsure if he wanted you to bless the meal. “But I do not offer the courtesy of my kitchen to my enemies.”
He nodded. “I am Roadhog. That’s Junkrat.”
Professional names then. “I am known as Keres.”
“Hooley dooley, Carrie, you got some fancy grub,” Fawkes, who was Junkrat, reached forward and grabbed a taro dumpling with his hands. “Hot! Hot! Hot!” He bounced it in his hand while you served yourself some curry. Junkrat seemed like a more fitting name.
Roadhog used his hands as well, carefully snatching dumplings and other appetizers, but setting them down on his plate. He wasn’t eating directly from the communal dishes, and you appreciated the courtesy.
You raised a brow as Junkrat grabbed his own share of curry and began squirting Sriracha into it.
“You might taste it first,” you said, because you had been liberal with the spices and the peppers.
“I eat gunpowder for breakfast, Carrie!” He jabbed his fork at you, eyes blazing. “Don’t need no drongo telling me how to eat a fish head!”
You chuckled. “All right.” You sipped your tea watching keenly as Junkrat shoveled a spoonful into his mouth, grinning triumphantly at you. It took a few seconds, but as he swallowed, his face began to redden, his cheek twitching. Sriracha really wasn’t that hot. But the peppers you’d used were pretty potent.
Roadhog spooned half the curry onto his plate, splitting the fish head and taking the larger portion of that as well.
They were two different kinds of dangerous. Junkrat needed to be balanced – too much stimuli and he flew into a manic episode. Too little and he stirred up trouble to keep himself from being bored. Roadhog was a pressure cooker, holding it in until he hit critical mass. Keeping them both calm took different strategies.
Doing so was less difficult than it sounded. You were used to dealing with dangerous difficult people. After all, back in Zurich you’d been so good with-
You stopped, mid-bite. Yes, that’s exactly what the Junkers reminded you of. Your goddamn Blackwatch hardcases. Fuck. The wheels of memory ground out another realization: Hell, when you’d first joined up, your manners were only marginally better than Junkrat’s. That was such a long time ago...
The blonde man was still chattering about how the fish curry wasn’t that hot, while he piled more rice into his bowl and shoveled it down his throat. Then he loudly drained his cup, still protesting that he had no trouble with spices.
Roadhog noticed your hesitation and slowed his eating.
You took a drink and went back to your curry. It could have used a little more tamarind. The coconut milk mellowed the sharpness a little more than you expected.
“Well, as long as you find it acceptable,” you told Junkrat when he finished his rant about his tolerance for spicy food. “I’m still working on the recipe, so I understand if you think it’s lacking.”
He blinked. “Oh, no. ‘S good.” He slurped down another bite and gave you a thumbs up.
“I’m glad,” you said.
“Meant to say, that’s some arm you got there,” Junkrat chirped, knocking on your metal limb with his own prostheses. “How’d you lose it? Shark? Salty? Hamster?” He mimed biting motions with his hands.
“Terrorist attack,” you said, taking another bite of curry, though in that moment you only tasted ash.
“Bomb?” Junkrat asked.
“Yeah,” you said, though it had not been that straight forward.
“Who?” He asked eagerly.
“Talon.” You took a sip of your tea, the sweetness bracing you.
“Oh yeah, they’re absolute drongos,” Junkrat cackled. “Keep inviting us around, like we want to join their stupid club with their dumb scrap metal lackeys.”
“So they’re trying to recruit you?” You asked.
“Mebbe,” Junkrat gave you a sly look. “Mebbe they’re after me treasure.”
You laughed a little too hard at that.
“You don’t believe me?” He puffed up then, smacking his bare chest. “Me and Pig Face are rich! We could eat like this every day if we wanted to!” Madness flared in those eyes.
Under the table, you rested your bracelet against your knee.
“Shut up, idiot,” Roadhog grumbled.
“She’s laughing-” Junkrat’s head snapped to the side, reminding you of a mongoose about to strike.
“You told a joke,” Roadhog’s voice was dangerously low. “Sometimes people laugh at your jokes.”
Junkrat crossed his arms, looking sullen.
Children with their delicate egos. You gave a wry smile. “I thought it was a pirate reference.” You tapped your knee.
“Oh,” Junkrat looked at you sideways. “Of course it was!” He laughed a little too loudly. “I really had you two going! This is a dinner party, Roadhog! You gotta be personable. And I am nothing if not a courteous house guest!”
Even with the mask on, even if you’d never seen his face, you could feel Roadhog’s exasperation loud and clear.
“They were really invested in grabbing you today,” you said. “But there are a lot of cells in Talon,” you said. They pulled off heists and robberies, though it was usually for things other than money: tech, hostages, an unsavory means to an end... “I can’t claim to know what their intentions are.”
“Of course they want us to work for them! You saw us out there! Regular professionals! We were on a roll!” He grinned at Roadhog, jabbing him with a bony elbow. “Eh? Eh?”
“Stop that,” Roadhog growled, picking up his plate to drink down the curry sauce.
“But you did steal our kill though. He was worth more alive,” Junkrat said, narrowing his eyes at you.
“Sorry, personal business,” you said with a shrug. “I lost more than an arm to those bastards.” And given what you had learned from their dossiers, you probably could have left Barrett with them, confident that he wouldn't survive the experience. They had no love of “suits.” But you hadn’t known that back in that little electronics shop.
“Yeah, I get it,” Junkrat heaved a dramatic sigh. “There are some things money can’t buy.” He grinned at Roadhog. “But if that’s the case, you should still try the proper application of high powered explosives!”
You laughed softly, in spite of the situation. He was a crude, vicious, and dangerous child. Maybe he reminded you a little of Vo, of Fitzpatrick, of Távio, and others. Maybe you were just getting old. “I know it’s effective, but I don’t have your talent in that field. Never picked up the knack for anything beyond the basics.”
“I could show you a trick or two,” Junkrat flashed you what had to be his idea of charming smile. Somewhere between a leer and the awkward smile of a student portrait, he showed far too many teeth. And he waggled his eyebrows at you.
You were far too old for this shit. But you put on hand over your mouth, trying to smother your snickers.
Junkrat grinned at Roadhog, nudging him with his elbow. “Suppose she fancies me? She did invite us in for this real intimate dinner. Ladies don’t just roll out that hospitality for anyone.”
Roadhog just shook his head.
“Unless she’s interested in you,” Junkrat murmured a low shocked voice. “Hooley dooley, mate! You don’t think-”
“No, you don’t think,” Roadhog said setting his plate down. “This is business.”
Junkrat blinked. “But dinner-”
“Friendly business,” you said. “A simple “getting to know you” sort of event. Though let me emphasize, I don’t share food with my enemies.”
“Not government,” Roadhog said, utensils set at straight on his plate, indicating he was done. “Not Talon.” He looked around. “Corporate security? PMC?”
“Sort of,” you said.
Junkrat scowled. “We don’t work for suits.”
“I represent the Peaceful Life Society,” you said.
Junkrat snorted. “That’s a silly name.”
“I’m still not sure if it was meant to be ironic,” you said, sipping your tea. “But yes, it is.”
“Triad business?” Roadhog crossed his arms.
“It could be,” you said. “We can talk business. We can talk about cake. There is no pressure. I’m not here to try to strong arm you.”
“You wanna hire us, Carrie?” Junkrat asked.
“I have work, if you’re interested. I have cake, if you aren’t.”
“But we can only pick one?” Junkrat frowned.
“No. We can just start with dessert,” you said and got up. You brought the cake out of the fridge. And when you turned around, Junkrat was hovering over your shoulder, flitting back and forth, staring at the cake.
“Look at that, Roadhog. Just look at that beauty. Just covered in chocolate, a goddamn mudslide of chocolate. It’s gonna be too sweet,” he moaned. “It looks pretty, but they overdid it-”
“It’s dark chocolate,” you said, a little indignantly.
“And all that coating is gonna be gummy pasty sugar shit-”
“It’s not fondant,” you scowled, genuinely offended by the thought.
“It can’t be as good as it looks, there’s no fucking way!” He wailed, clearly more interested in being dramatic than listening to a word you said.
You glanced over at Roadhog feeling a growing respect for his levels of patience. “Would you like a slice?”
He nodded.
You almost asked if he wanted Junkrat’s slice, but decided to be the mature adult here. You set the cake on the counter and cut two large slices for you and Roadhog, and one small one for Dramarat. Against your better judgment, you made coffee to go with it, possibly making it half-caf because your guests were so excitable.
“Let’s go in there. I don’t feel like clearing the table right now.” You handed each man their own plate and fork, and poured yourself some black coffee. You took a seat in a single chair, while the Junkers took the couch.
Junkrat poked at the plushies, giggling to himself as he tossed the pig at Roadhog, nearly missing the other man’s plate.
“Watch it!” Roadhog snapped.
You set your drink down on the glass coffee table and took a bite of the cake. There was a generous spread of tart raspberry liquer filling between each layer of chocolate cake. Smooth chocolate ganache replaced the frosting, with fresh raspberries adorning the top of the cake. It was rich with just the right amount of sweetness. Gabriel would have-
You did not finish that thought. It would have sat badly with your curry. Instead, you set the plate down and took a deep swig of coffee. When you looked up, Roadhog was delicately eating his slice while Junkrat was still staring forlornly at his own piece.
“How is it really?” Junkrat tried to whisper, but he was about as good at it as Reinhardt.
“Find out for yourself. Idiot.”
“I’m not like you. I can’t just eat anything. I’m a connoisseur!”
Roadhog just shook his head in disgust.
Junkrat begrudgingly took a bite, grimacing the entire time. Uncertainly pinched his already pointy features. He chewed, slowly relaxing as he tasted the cake. The transformation was nearly instantaneous. He went from pissing and moaning to an open mouthed quiet awe. He stared reverently at his slice and then shoved the rest into his mouth.
You sipped your coffee.
“Hooley dooley that’s good shit,” he murmured, mouth full of crumbs. “Can I have more? Before pig face eats it all?!”
You still couldn’t see much of Roadhog’s face, but you could feel the heat of the glare directed at Junkrat.
“You both can have the rest. I’m pretty full,” you said, picking up your plate. There was three quarters of a cake left. Maybe they could take it to go.
“Are you sure?” Junkrat squinted at you. And then hopped up, bouncing into the kitchen with glee.
...Oh, maybe you should not have given him that much sugar.
But then Roadhog was on his feet, lumbering into the kitchen with heavy steps.
“Hey, back off! This is mine! Carrie said I could have it!”
“Fifty-fifty,” Roadhog said, pushing Junkrat out of the way. He lifted the knife and made a sharp cut.
“That looks more like sixty-forty!”
“Get your eyes checked,” Roadhog said, taking a slightly bigger piece.
“Come on, don’t be such a pig!” Junkrat jumped, trying to snatch the cake out of Roadhog’s hands.
“We can always get more cake,” you said.
“...Really?” Junkrat perked up.
“Yeah, I don’t mind going for more dessert,” you said, even though the bakery was closed. If they pushed, you could get ice cream or something.
“Oh,” Junkrat grabbed the remaining portion. “I guess that’s OK then.” The importance of the distraction was to get them to disengage. You did not want them coming to blows in the apartment safehouse. Both men returned to the living room, Roadhog taking the far corner of the couch. Junkrat sat closer to you, eating happily while he poked at the plushies with chocolate-smeared fingers.
“Didn’t figure you for the stuffed animals type,” Junkrat said, turning over a pirate Pachimari in his lap. He bounced it a few times, then looked around rapidly, then tried to act casual slinging it to the side.
“I didn’t decorate,” you said with a shrug. “But they are really cute.”
“I guess they are,” Junkrat jammed his hands into his pockets. “If you like that kind of thing.”
Roadhog coughed.
“I mean, I don’t,” Junkrat sputtered. “I’m a man of sophistication and means. I just know that they don’t make the pirate one back home. They were limited edition,” Junkrat said, staring longingly at the pile of plush.
You sighed. This location was going to be metaphorically burned after this encounter. You could make some good will offerings. “My friend won’t mind if you take some.” You paused. “If you had someone back home whom you thought might like one.”
“Oh.” Junkrat perked up. “Really? Because I think Little...James might like one. Just some neighborhood kid,” he added quickly.
Roadhog just sat very still.
“And his little sister...Jamie might want one too,” Junkrat grinned.
“Go for it,” you said sincerely. “Think of them as...party favors.” You glanced at Roadhog who just sat there eating his cake.
“Carrie, you throw the best dinner parties!” Junkrat squeezed an armful of plush, some of them squeaked. “If more people did it like you, dinner parties wouldn’t be so goddamn boring!”
“Thank you,” you said. “I try.”
“But I don’t know about working for your Triad buddies. We’re free agents! We don’t like being tied down!” Junkrat looked up from the plushes, expression grim.
“I understand,” you said. “If you’re fighting Talon though, I’d like to collaborate some time. Or at least not get blown up or shredded by the two of you in combat. I’d extend the same courtesy, of course.”
“Carrie, you’re a nice lady who owes us some more cake. I would never-” Junkrat pressed his hands to his chest. “Never ever ever.”
“That’s a relief,” you said. You hadn’t expected them to onboard today. This was just first contact. You could cultivate the ties over time.
“Truce,” Roadhog said. The cake was gone, but there was no trace of it on his fingers, lap, or mask.
“Truce,” you said with a smile.
**
Junkrat had stuffed his bag full of toys, though you didn’t miss the piggy tucked on Roadhog’s hip, almost completely hidden by the chain. Junkrat was snoring now, draped across Roadhog’s back. He
“If you’re interested,” you said, offering him your card. “We can talk about it over cake.”
Roadhog grunted, accepting it. Those massive hands delicately placing it in a pocket. He paused, looking down at the bracelet your left wrist. He snorted.
“Hardlight projector?”
“Yes,” you said.
He nodded. “Military grade?”
“Of course.” Because you could be friendly and well-armed. Always hope for peace, but prepare for killing the shit out of your enemies.
Roadhog stared at it for another few seconds, clearly contemplating the other way this encounter could have gone. “Thank you for the meal,” he said, ducking to go through the door.
“I had fun,” you told him. “We should do it again some time.”
**
You sat on the roof, admiring the brilliance of the skyline. A shuttle would pick you up soon. A local cleaning service would take care of the facilities. The Junkers had come and gone with minimal damage. Cian Barrett was dead. Zee had access to his files. Not a bad day’s work.
Zee’s drone hovered by your shoulder. “You still have a way with delinquents,” she said.
“Takes one to know one.” You fiddled with the bracelet. It wasn’t your best weapon, but you could use it well in close quarters. “You can take the girl out of the bar-”
“That is such a crass statement with racist overtones,” Zee said, her tone frosty.
“Sorry, you’re right. I don’t need to be repeating that shit,” you said. You tilted your head back. You’d spent a couple months in Phuket before you had found Sakai. You’d picked up some of the lingo, the ways to blend in. You’d need to shed those habits sooner rather than later. “How are things back home?” You asked.
“Settling.”
“That could mean any number of things.”
“You know Feng was never mad about what you did. She was worried about you. She still is.”
“I know.” You toyed with the a large bulldog plush that had somehow been left behind by the Junkers. If Oksana didn’t want it, maybe Karalika would. “But Oksana...”
“She needed time to come to terms with what she saw you do. She’ll get past it. She adores you too much. This was an eye-opening experience about our line of work. Her father has always sheltered her.”
“Her father-” You scowled.
“Will get over himself when she calms down. He exaggerates all faults. Honestly, all of you are so overwrought and emotional. Presenting the On Sing Serial Drama: tune in next week for more shocking events and emotional fallout in a real time comedy of errors,” she said in biting tones. “Foolish children. These things take time. You have to account for that, Lucky. Stop being so impatient.”
You smiled wryly. “Thanks, Auntie. You really do know best.”
“I know, and while you are acknowledging my wisdom and experience, let’s talk about what’s going on with you. You really need to talk to another professional about what’s going on in your life,” she told you primly. “Don’t give me the “oh, who’s going to understand the psychological effects of brainwashing, and faked deaths, international conspiracies” speech. That’s cult of exceptionalism foolishness. Conspiracies aren’t what’s sending you to therapy, it’s your manner of handling the stress. Psychologists understand complications, betrayals, PTSD. That is what you are asking for help with, untangling your feelings and yourself. This isn’t about politics or tech. Your situation may be unique, but your reactions? Textbook.”
You winced. “You broke me down faster than I did Sakai.”
“Yes, well unlike you, I’m not playing around, or trying to draw out the suffering,” she said. “And unlike the others, I don’t care what you did to her. She earned it. But I do care what it implies about your mental state, and how it affects the rest of the family.”
“I went too far,” you agreed after a moment. “I’m not sorry. Not yet. But I know I went too far.” Maybe not far enough to join Talon as a double agent, commit atrocities to win their trust, and then finally exact your brutal revenge. And that was the best case scenario in a certain Reaper’s case.
“Make sure you tell that to everyone else. Ask for their help in keeping you honest. It will go a long way in earning you some grace.”
“Yes, Auntie,” you said with a heavy sigh. You stared out over the city. The night was warm. “I still have one question. How did they locate me so quickly?” You gave the drone a sharp side eye.
“You need allies. They have survival skills,” she said, telling you everything you needed to know.
“With friends like you, I definitely need more allies to watch my back,” you scowled, though you couldn’t muster any real ferocity.
“I had full faith in you,” she said solemnly. “And total control of the discretely placed turrets.”
You just shook your head. “Auntie-”
“You cannot slaughter your way through this, Lucky. Not if you want to protect the others. Do you think Oksana is ready for this war? Are you willing to risk it?” She didn’t give you a chance to respond. She already knew your answer. “No, you need to be smart and use diplomatic methods too.”
“You’re not wrong, but I think I just used up all my diplomacy,” you said dryly.
“You should probably work get it back soon,” she said. “Jesse McCree has just arrived in Shanghai. He has...information. And he’s insisting that he tells it to you in person.”
****
Yes, you should know all the ally characters referenced, except Karalika. I’m fine spoiling in the comments if you want to guess.
My week was stressful. 10-11 hour shifts, a sick cat, cat had teeth extracted Friday and is high out of his mind (or had a stroke? I don’t know.) I’ve had force feed him a feed a few times this weekend. He keeps falling off things and walking into walls. He’s not using the litter box. I am super tired.
20 notes
·
View notes
Text
Thursday, May 13, 2021
Public service in the US: Increasingly thankless, exhausting (AP) Historically, jobs like teaching, firefighting, policing, government and social work have offered opportunities to give back to communities while earning solid benefits, maybe even a pension. Surveys still show public admiration for nurses and teachers and, after the terror attacks of 9/11, firefighters. But many public servants no longer feel the love. They’re battered and burnt out. They’re stretched by systems where shortages are common—for teachers in Michigan and several other states, for instance, and for police in many cities, from New York and Cincinnati to Seattle. Colleagues are retiring early or resigning. There are mental breakdowns, substance abuse and even suicide, especially among first responders. Even before the coronavirus arrived, researchers have found in 2018 that about half of American public servants said they were burnt out, compared with 20% over workers overall. Some wonder who will pick up the slack, as more young people avoid public service careers. In the federal government, just 6% of the workforce is younger than age 30, while about 45% is older than 50, according to the nonprofit Partnership for Public Service.
Gas stations report shortages as pipeline shutdown drags on (AP) More than 1,000 gas stations in the Southeast reported running out of fuel, primarily because of what analysts say is unwarranted panic-buying among drivers, as the shutdown of a major pipeline by a gang of hackers entered its fifth day Tuesday. The Colonial Pipeline, the biggest fuel pipeline in the U.S., delivering about 45% of what is consumed on the East Coast, was hit on Friday with a cyberattack by hackers who lock up computer systems and demand a ransom to release them. A large part of the pipeline resumed operations manually late Monday, and Colonial anticipates restarting most of its operations by the end of the week, U.S. Energy Secretary Jennifer Granholm said.
Colombia protests likely to continue (NBC News) With no agreement between Colombia’s government and protest leaders, demonstrations are likely to continue as major cities brace for a third peak in Covid-19 cases. Since April 28, thousands have protested throughout the country against the government. The violence has resulted in the death of 26 people, including one police officer, according to government figures. Rights groups say the death toll is higher; Human Rights Watch says it has credible reports of 38 deaths. What began as demonstrations over proposed tax increases, that have since been scrapped, has morphed into broader demands for the government to address poverty and inequality. The protests have grown as reports of police violence, deaths, and disappearances have emerged.
More policing in France (AP) France saw its second national homage to a police officer in less than two weeks following the daytime shooting of Eric Masson, who was killed last week during a routine inspection of a street corner. “It’s a reality that there is violence in our society and it’s swelling, and that each day the role of our police is made more difficult by this violence,” said President Emmanuel Macron following a memorial for the slain officer. Experts, however, have noted that more French police were being killed in past decades than today, but that police tactics have hardened in recent years, leading to increased distrust amidst claims of systemic racism within the police, racial profiling, and videos showing apparent abuse and sometimes deadly violence. In contrast to the United States’ recent efforts to curb police powers, France has opted to strengthen them instead. Macron has promised 10,000 more officers in the streets by the end of his term and increased the police budget. The prime minister has also laid out a series of measures to ensure courts get tough on anyone dishonoring the uniform and a guarantee of 30 years in prison for the killing of a police officer, the same punishment as for terrorists.
A sweeping coronavirus lockdown in Turkey sets off arguments and economic anxiety (Washington Post) Shopkeepers pulled their steel shutters down last week in a warren of tool shops near the Bosporus, to comply with a nationwide lockdown. But every third shutter or so was left open a crack, to allow the furtive flow of continued commerce. Hardly anyone in Turkey these days can afford to be locked down. Not small business owners, who were aching from the flailing economy and rocketing inflation even before coronavirus restrictions were imposed last week. And not even the government, which permitted a glaring exception when it said foreign tourists, a critical source of foreign currency, would be allowed to travel the country freely, while telling Turkish citizens to stay home. In the 12 days since the lockdown began, the restrictions have set off soaring economic anxiety, arguments and public irritation. With infections and deaths surging to new highs, few disputed the measures were necessary. Rather, complaints have centered on the way they were imposed, with official edicts viewed as capricious or baffling that critics say have failed to insulate the country from further economic harm. The lockdown has undermined repeated official assurances that Turkey was faring better than many countries in the world. And the rules, from the well-intentioned to the bizarre, have landed on a public that is in no mood for more restrictions, especially this late in the pandemic.
India’s COVID-19 deaths cross quarter million as virus ravages countryside (Reuters) India’s coronavirus deaths crossed a quarter million on Wednesday in the deadliest 24 hours since the pandemic began, as the disease rampaged through the countryside, overloading a fragile rural healthcare system. Boosted by highly infectious variants, the second wave erupted in February to inundate hospitals and medical staff, as well as crematoriums and mortuaries. Experts are still unable to say with certainty when the figures will peak.
Chinese Population Growing At Glacial Pace (Guardian) Despite efforts to increase birthrates in the past half a decade, China is currently seeing its slowest population growth since the 1960s. On Tuesday, the government released the results of its once-a-decade census, saying the overall population of China grew to 1.41178 billion in the 10 years leading up to 2020, a slowdown that was expected, but still worrisome for the future of the country. According to the National Bureau of Statistics, there were officially 12 million babies born in 2020, 2.65 million fewer than were born in 2019. China ended its one-child policy in 2015 to encourage more births, but the annual growth rate of 0.53% is the lowest since the early 1960s when China was dealing with the aftermath of tens of millions killed by famine. Replacing the one-child with the two-child policy has done little to stimulate population growth over the past few years. According to Dr. Ye Liu, a senior lecturer at King’s College London, “the government had to address the intersecting factors behind the low birthrate, which include rampant workplace discrimination against women of childbearing age and ‘scandalously low’ public childcare funding.”
Amcham finds 42% of members surveyed are planning or considering leaving Hong Kong (CNBC) A survey by the American Chamber of Commerce in Hong Kong found that 42% of respondents are considering or planning to leave Hong Kong, with more than half citing their discomfort with the controversial national security law imposed by China. Various media outlets have reported anecdotes of people or businesses leaving Hong Kong following the clampdown by Beijing. And the Amcham survey offers a glimpse of the sentiment among the expatriate community in Hong Kong. “Previously, I never had a worry about what I said or wrote when I was in Hong Kong,” said an anonymous respondent to the Amcham survey. “With the NSL, that has changed. The red lines are vague and seem to be arbitrary. I don’t want to continue to fear saying or writing something that could unknowingly cause me to be arrested,” the person said.
Hamas launches more rockets, Israeli jets strike Gaza as casualties mount (Washington Post) Violence between Israelis and Palestinians entered its fourth day as rocket attacks on Israeli cities and airstrikes in the Gaza Strip continued early Thursday and casualties climbed on both sides. Sirens blared through the night across Israel as the militant group Hamas fired 130 rockets from Gaza, with at least one striking a suburb of Tel Aviv, causing injuries and significant damage, according to Israeli officials. In Gaza, residents awoke on the normally joyous Eid al-Fitr holiday to pillars of smoke rising from sites bombed by Israeli forces, which said they had conducted overnight operations against Hamas, which controls Gaza. Gaza’s Health Ministry said the death toll rose to 69 Palestinians, including 16 children, the Associated Press reported. Seven Israelis, including six civilians and one soldier, have been killed, the Israeli army said Thursday morning. The Israeli army has struck 600 targets in Gaza since the conflict began, according to spokesman Lt. Col. Jonathan Conricus, who raised the possibility of a ground assault on Gaza. Clashes also continued overnight on the streets of Israeli cities between Jewish and Arab Israelis, prompting Prime Minister Benjamin Netanyahu to announce he would deploy the military to quell the “anarchy.” Some 400 people were arrested overnight following riots throughout the country, the Times of Israel reported early Thursday, citing police. It added that 36 officers were injured.
1 note
·
View note
Link

Cybersecurity is one of those subjects that is always on the cutting edge of technology. As such, a lot of its basic concepts are poorly understood by the general public. Not only that, but the general public also tends to underestimate the threat posed by hackers and the like. The costs of ignoring these threats can be very high, indeed. With that in mind, let’s look at a few important statistics on this subject.
A CYBERATTACK HAPPENS EVERY 39 SECONDS
Everyone knows that hacking and other cyberattacks are very common these days, but not many have tried to quantify it with definite figures. Thankfully, we found this study from the University of Maryland that attempted to do so. The researchers set up four Linux computers with minimal security and recorded all sorts of hacking attempts.
On average, the computers in the study were attacked or probed 2,244 times per day. The study found that most of the attacks were carried out using automated “brute force” tools that are able to crack passwords. Thankfully, these sorts of tools only work against weak/short passwords, and that’s why hackers have to troll around for an easy mark.
AVERAGE COST OF A HIGH-PROFILE BREACH: $116,000,000
Everyone knows that data breaches can be expensive and that the reputational damage caused by such attacks can be even worse. According to this report, these breaches might be even more expensive than you would think. They found that the average cost of a data breach at a publicly-traded company was around $116 million. To be fair, these numbers are not accurate for small businesses, but they do give you a good idea of how much damage these people really cause. Incidentally, the report also found an increase of 54% in overall data breaches since 2017.
95% OF ALL DATA BREACHES HAPPENED IN JUST THREE INDUSTRIES
This statistic comes from a Forrester report that was published in 2016. The original study is paywalled (and highly expensive), so you can read a summary of its findings here. As you can see, the vast majority of all data breaches in 2016 happened within one of three industries: Government, retail, and tech. Based on this, we can see that these are the most appealing targets for hackers.
Governments are targeted because they often have more money than private companies, and are probably easier to pressure since they are more accountable to the public. Some others also probably target them for political reasons. Retail and tech are probably targeted because of the large amounts of customer data that they tend to keep.
EXTERNAL THREATS ARE FAR MORE COMMON
When you are attempting to guard yourself against cyber-threats, there are two main categories of them: The insider threat and the outsider threat. Many would assume that the insider threat is the more common, as infiltration allows an intruder to penetrate security measures more easily. However, it would seem that it isn’t like that after all. According to this cybersecurity study from Verizon, insider threats only account for about 30% of all data breaches. The other 70% were listed as “external,” so this is clearly the more common method.
THE UNITED STATES SEEMS MORE LIKELY TO BE TARGETED
There are many groups that have published statistics about the number of people hacked annually. However, many of those do not break the statistics down by country. When we look at this report, we can see a trend that is very disturbing for those in the United States. In terms of monetary loss, The U.S. suffered about $27.4 million in losses from cyberattacks in 2018, which is a significant increase from the $21.2 million lost in 2017. For comparison, the second spot on the list went to Japan, with a total of 13.6 million in 2018 losses($10.4 million in 2017).
MOST HACKERS JUST WANT MONEY
It seems that there is a lot of paranoia these days about state-sponsored hackers. Because all governments have to be worried about the possibility of espionage, this is a natural concern. However, the data would seem to indicate that state-level hacking is not the norm. Let’s go back to that Verizon report that we examined earlier. According to their numbers, 86% of all cyber attacks were financially motivated. Thus, we can see that most hackers are after money rather than being motivated by sociopolitical or personal goals.
DATA BREACHES ALSO AFFECT THE STOCK MARKET
When a company has a high-profile data breach, it tends to damage their reputation. Customers count on these large companies to keep their data safe, and it represents a breach of trust for many. Not surprisingly, this loss of customer confidence can be seen reflected in the stock market prices for affected companies.
This report from Comparitech found that the lowest point occurred about 14 days after the breach itself. Share prices were generally lowered by 7.27%. Thankfully, those prices had a tendency to rebound after a month or so, but that still represents a lot of lost money.
MOST BREACHES HAPPEN BECAUSE OF HUMAN ERROR
When you read all of these stats, it is easy to think that computers and the internet are impossible to secure. Thankfully, this does not seem to be the case. According to this report (and quite a few others), about 95% of all data breaches are caused by human error.
When something like this happens, it might seem natural to blame the IT department. However, hackers tend to attack the weakest link they can find, which usually tends to be a low-level employee. Competent IT support and services are one good way to mitigate the human factor, leading many companies to ask, “who offers the best managed IT services near me?”
CONCLUSION
Of course, there are all kinds of statistics on cybersecurity. There are so many that we could literally list them all day long, but no one has time to read all of that. We hope that you have
1 note
·
View note
Text
Hank Payton | 5 Reasons You Need a Cybersecurity Plan
Hank Payton | We have all lived in the hype around cybersecurity and how if we don’t pay attention, it can become our nightmare, one where even the best corporate securities and government will not be able to intervene. There is no requirement of any proof or statistics to prove the threat: Cyberattacks is our reality. Why has this transformation from a threat to reality happened?

The capability of several organizations to deal with cracking and hacking has reduced significantly People working on cyberattacks are more knowledgeable as compared to an average IT professional. Gone are the days where amateur hackers were attacking our systems. Today, these cyberattacks are created by terrorists and crime syndicates.
People defending against the cyberattack are using the wrong defence mechanism. The threats are more complicated in nature. It is just like a war, with several attackers, millions of targets, and no end goal.
So what can we do to protect our organization? Yes, our nations and presidents are passing out laws to help combat this, but is it really going to stop? No, we need to revaluate our IT strategy on our own and put in a place a system and process that will boost our security.
Hank Payton — Here are the top 5 reasons as to why you need a Cybersecurity plan:
There are high chances that you have identified the wrong threat, which inevitably makes your approach wrong. You may have a lot of security strategies in place, but how many of them are still valid as per the current market scenario? You will never know the answer if you don’t take the conscious effort to find out. Therefore, you need to stay up-to-date and create a plan that combats latest threats.
Creating a dedicated strategy for cybersecurity and updating it regularly is an effort in itself, which is usually not otherwise present. Keeping that strategy fresh and making it specific will give you the power to influence security decisions to the most.
One word to defeat-reactive defence. We don’t need to implement anything fancy when we know it will fail. But how does an organization become proactive? It begins with creating a cybersecurity strategy, which considers the uniqueness of your organization and designs a foundation based on that.
Strategy is the core for any organization. It helps in making a centralized decision, and a sure way to understand and resolve a problem. However, this is not just random principles, but specific goals, decisions, and objectives to face the challenges.
The ultimate performance metric for organizations is performance. Use it to highlight how you perform in challenges, the approach you would be using for achieving positive results. Only a strategy will help you identify your organizations security stance. Remember that you need to set a metric based on the risks that you have faced before, and to those you haven’t experienced yet. Creating a security plan for yesterday’s strategy will not protect against the risks of tomorrow.
1 note
·
View note
Text
Why You Need to Think About an Online Cyber-Security Degree
A Growing Number of students are turning to online diploma programs and Only post-secondary ones because online schools provide:
Steps to Begin Your Own Web Cyber-security Degree
Start researching that online colleges provide on the web cybersecurity programs; afterward, be certain that you compare with the schools' evaluations, reputations, and instruction caliber. And do not neglect to appear in to educational funding, scholarships offered tuition and lodging rates.
Advisors assess safety protocols and policies. They perform step by step system evaluations to pinpoint flaws, expect future compromises, and track vulnerabilities with time.
Each time an organisation, association, or even individual stores advice on the web, it's at the mercy of cyberattacks. This is exactly why proficient pros have been in high demand over a vast assortment of businesses. Their principal job role will be to keep sensitive information from getting compromised or stolen. On any particular day, cybersecurity pros look security plans, install firewalls, and also track activity to protect networks and files. At case of a violation, they must react at lightning speed to discover a remedy.
Fast Cyber-security Certificate ProgramsAffordable on the Web Cyber-security Certificate Programson the Web Cyber-security Graduate Certificate ProgramsCyber-security Course Online Stanford16 Estimates Cyber-security Master Degree ProgramsVariety: Not many schools and universities Provide Vast Array of classes You'll Discover on the Web. If you should be enthusiastic about a particular cybersecurity posture, such as penetration tester or episode responder, a class dedicated for this really is right at your finger tips.
If you believe that'll overlook out the discussion connected with physical presence, start looking to a synchronous application. With synchronous apps, you know from realtime. You are able to ask for a mentor queries via instant message and also get instant responses. Based upon the program, you may have use of additional students than you choose a college campus.
Cyber-security functions become increasingly more technical over various businesses. Have a look at these varied career paths and everything you are able to make based on Cyberdegrees.org:
Cyber-security branches in every areas want your expertise. Begin now in your own level and also a lively, longtime livelihood.
No organisation or individual is resistant to cyberattacks. Cybersecurity experts are sought after as organisations attempt to reinforce their own internet security, making now a superb time for you to pursue an internet degree in cybersecurity.
And you're going to save yourself a lot of money in fees, housing, food, transport, and novels.
Cyber Security Degrees Are Adaptive A current report on Monster.com⁴ says that cyber practitioners will be needed in information engineering, law, government, and finance and banking. And cyber-security becomes necessary in each of the areas.
Along with promising project opportunities in a fast expanding field, a cyber-security level provides other advantages, and it's really an simple task to begin your career with an internet faculty. Below are a few of the largest reasons it's also important to think about having the level in cyber-security on the web.
On the Web College Is Cheaper and Cheaper
Think online schools are not as popular as conventional schools? As stated by the Babson Survey Research Group¹, approximately three million students within the U.S. are fully registered in online programs whereas the next six million take a minumum of one online class whilst attending a standard faculty. Considering each of the great things about internet study, this popularity for internet faculty programs isn't surprising.
Convenience: Along with learning on your pajamas, then you are able to learn in your schedule. Online colleges allow you to pay attention to assignments and complete homework in your time and effort in your own personal pace.
These pros either make and develop new detection programs or incorporate security engineering on aws training throughout the program design procedure.
Since a lot of data is encoded now, entities which range from hospitals into the FBI usage cryptographers. Cryptographers rely heavily upon strong mathematics skills to reestablish sensitive digital data and also develop new calculations. They examine their particular models for security and precision and research lines of communicating for flaws.
Cyber-security has come to be nearly interchangeable with project security. As technology advances, so do cyber-thieves -- those tech savvy offenders are more daring, and each new attack is much significantly more catastrophic than the past.
Like whatever, it certainly is a fantastic idea to know about the newest research. We recommend comparing at least three or four options before making your last choice. Doing an internet search on the web is normally the fastest, most thorough means to detect most of the pros and pitfalls you want to stay at heart.
These pros primarily research safety hazards and statistics breaches. They regain and examine info, purge and reconstruct damaged systems, and search for different systems or networks which may have already been hacked.
You Can Pick Your Learning Environment still another benefit to e learning can be that your capacity to determine how the stuff is going to soon be delivered.
Enforcement Laboratory
Security Computer Software programmer
Asynchronous apps, alternatively, permit one to examine in your pace at any time daily. Coursework is delivered via the internet email, and community forums. The info is then posted online forums. You're able to access class materials watching assignments or demonstrations should you'd like, permitting you to fit your instruction to your busy schedule -- a benefit you can not get from conventional colleges.
More One to One courses you may like
One to one windows server administration
administration with redhat linux
security engineering on aws
Learn AWS Technical Essentials online
learn Systems Operations on AWS
1 note
·
View note
Photo

Infographics - CyberSecurity - Facts and stats
Learn statistics, cybersecurity risks and how cyberattacks can affect your business
www.codetechglobal.com
1 note
·
View note
Text
How to Know More about Best Cyber Security Courses
Cyber security is a field that deals with the safety of computer hardware, software program, data and the inter-related structures from any sort of cyberattacks. Organizations utilize cyber protection to defend their structures and information from unauthorized access and robbery. Professionals running in the field of Cyber Security Course in London can be educated via a cyber safety route in a university or through an online instructional portal.
A cyber security direction makes fresher’s inquisitive about this subject nicely versed with the important thing talents required for this task. It teaches them a set of strategies and equipment which are had to defend the structures, community and facts from cyberattacks. It sensitizes the experts toward problems of protection, privacy and protection of cyber resources. They also turn out to be efficient enough to make certain the integrity and confidentiality of any records or structures.
There are numerous styles of cyberattacks inclusive of phishing, malware, unpatched software program, hijacking files, hacking and identify theft, amongst others. A path in cyber protection will teach the student approximately all feasible forms of assaults and the prescribed ways of dealing with them when confronted with such an attack. It additionally teaches the students on the high-quality approaches to guard the cyber structures and information from any cyberattack in the first location. They additionally learn how to deal with seemingly new cyber safety demanding situations that they encounter at their place of job by using polishing their capabilities.

Cyber Security Course in London also are treasured for employees who do now not have security as part of their job description. Organizations have to behavior training for personnel that will discover ways to guard the organizational systems. It allows them keep the machines freed from malicious programs. It teaches them simple protection practices like using complicated passwords, converting them regularly and backing up statistics every so often. It sensitizes them to the want of being vigilant and notify the cyber protection branch once they note any irregularity on their systems.
Cyberattacks have come to be a not unusual prevalence and consequently it's far crucial that corporations hire fine protection specialists. It is likewise similarly vital for them to sensitize their personnel approximately the want and significance of following cyber safety hints recommended via the enterprise. It is critical that companies also realize that course and training workshops on cyber safety isn't a one-time element but a non-stop effort closer to a secure environment.
For more info :- CCNA Certification Course Online UK
1 note
·
View note
Text
The 5 Most Demand In Cybersecurity Jobs for 2020
In 2019, companies invested more in tech, brand new privacy regulations were passed, and cyber threats became much more complicated. To satisfy the rising demands of today's companies, (ISC) 2 quotes, the U.S. Cybersecurity workforce would have to grow by 62 percent.
Together with cybersecurity work in such high demand and proficient professionals in reduced supply, several businesses have carved their cyber ability wishlist down to some critical positions. Which places will top the record in 2020? According to information in the CyberSeek.org project backed by NICE, we've got a reasonably good idea.
The best five rankings, explained below, will help students understand the opportunities which are offered to them, seasoned professionals locate opportunities for career transitions (such as IT to pay ), and cybersecurity and business leaders know the hiring landscape since they construct their cyber workforce development applications.
We have mapped these high tech project classes to specific job functions within the NICE Cybersecurity Workforce Framework, for people considering detailed readouts of their KSAs (knowledge, skills, abilities) required of every position.
Let us take a better look at the best five cybersecurity tasks, finishing with the maximum in-demand position. Cybersecurity Engineer
1. Cybersecurity Engineer
The Cybersecurity Engineer has been the very in-demand security place for 2018 and 2019 and tops the graph again in 2020. That is an intermediate to advanced-level standing in many organizations, and Cybersecurity Engineers is tasked with employing an approach to implementing and designing security methods to prevent advanced cyberattacks.
Unlike analysts, that are mostly concerned with tracking and monitoring threats, the Cybersecurity Engineer is frequently called on to develop security policies and plans, implement alternatives, mitigate vulnerabilities, research breaches, and react to security events. As the amount and severity of security threats grow, so will the demand for Cybersecurity Engineers to design them to prevent. This position calls for a broad foundation of knowledge and the capability to keep systems, identify vulnerabilities, monitor problems, and enhance automation. Many Cybersecurity Engineer functions require three or more decades of qualified experience (based on the quality and thickness of their skillset). A master's degree is expected to become commonplace, particularly.
Certifications are highly appreciated in this discipline, and certificates such as CISSP, the CEH, or even some other GIAC certifications might help win the occupation.
Soft skills also play a vital part in this place since Cybersecurity Engineers tend to be requested to convey their findings to executive leadership and might be asked to collaborate with a vast array of stakeholders. The ability to communicate ideas and quickly is essential to the achievement of the job.
2. Cybersecurity Analyst
Cybersecurity Advisors are on the front lines of the cyber protection of an organization. Together with the number of information breaches rising by more than 50% since this past year, Cybersecurity Analysts keep tabs threats and track their business's network for any security vulnerabilities. Using information gathered from resources along with danger monitoring tools, they examine, identify, and report on events that have occurred or might occur in the community.
The U.S. Bureau of Labor Statistics anticipates a 32% increase in selecting for the Cybersecurity Analyst function between 2018 and 2028 - far outpacing the average for its other services on this listing since only the amount of job openings to get a Cybersecurity Analyst has improved by nearly 4,000.
Most Cybersecurity Advisors finally progress from this place into more technical functions in technology, compliance, or penetration testing. That advancement possible makes this job a location to begin a career at cybersecurity, particularly.
3. Network Engineer/Architect.
Within this advanced-level place, Network Engineers/Architects account for designing, implementing, and analyzing protected, cost-effective computer programs, such as local area networks (LANs), extensive area networks (WANs), net connections, intranets, and other data communication methods.
Network Engineers/Architects is responsible for updating hardware and software and planning the execution of security patches or additional defense steps to defend the system against vulnerabilities. Assessing media technology to examine data and gauge the network may influence will also be significant elements of the function.
With the majority of businesses requiring 5 to 10 decades of professional experience and an advanced degree such as a master's or a Ph.D., Network Engineers/Architects are one of the highest-paid workers in cybersecurity. Professionals within this function come in other jobs such as computer systems analyst, database administrator, or network administrator.
A sizable portion of this Network Engineer/Architect function is communication with senior management how community safety variables into company plans, so excellent communication skills are crucial. As organizations continue to expand their usage of wireless, mobile, and IT networks, demand for Network Engineers/Architects will continue to rise.
4. Cybersecurity Consultant
Holding precisely the same place for the next year in a row would be your Cybersecurity Consultant. The Cybersecurity Advisor plays an attacker, and a defender's use discovers flaws and to exploit vulnerabilities. Commonly, this place isn't utilized by in-house safety groups; a Cybersecurity Advisor is generally either a self-employed builder or functions for outside or third party safety consulting company (like Focal Point).
Advisor functions vary by chance. Therefore a Cybersecurity Advisor may differ from an entry-level to some more intermediate-level cybersecurity place, with the majority of companies seeking to observe a diploma in the area, technical abilities, certificates, and possibly work experience running similar jobs.
Considering cyber threats are constantly changing, it isn't surprising that this place has claimed such high demand. Since the need for cybersecurity employees has thrived, and businesses struggle to fill safety functions, they rely on cybersecurity consulting companies to take care of their biggest jobs. Because of this, the demand for Cybersecurity Consultants is on the upswing among professional services companies.
5. Cybersecurity Managers/Administrators
are accountable for overseeing and executing the cybersecurity application for a network or a system, and organizations require safety Managers. Cybersecurity Managers/Administrators are required to track their attendance area, keep the tools, follow compliance audit their application, and construct cybersecurity awareness.
Most organizations to additional break down the cybersecurity director function into two classes: safety program supervisors, which are generally centered on programmatic risk management and mitigation (believe seller risk management, etc.), and technical safety managers, which manage particular systems and also the groups which handle them (believe firewalls, pencil testing, encryption, etc.).
As the name would imply, the Cybersecurity Manager/Administrator role requires substantial work experience and specialized experience, and lots of companies look for professionals with degrees in cybersecurity or a related discipline.
With venture cybersecurity investments on the upswing throughout the board, including the accelerated development of business SOCs, organizations will continue to find cybersecurity supervisors to function as the backbone of the ever-expanding safety applications.
1 note
·
View note
Text
Cyberattacks are on the rise around the world - here's what you need to know
https://eliteviser.com/2023/07/15/cyberattacks-are-on-the-rise-around-the-world-heres-what-you-need-to-know/
Cyberattacks are on the rise around the world - here's what you need to know
Security company Check Point has announced some alarming new statistics that should make you consider installing the better endpoint protection…
0 notes
Text
The Future: The Hottest Jobs of 2030 and Beyond

We are on the cusp of the fourth industrial revolution, and this change profoundly affects the landscape of skills and vocations. The world of work is changing due to the fast development of technology and the global issues we confront. Insight into the occupations of the future and the abilities necessary to succeed in them can be found in this article, which goes deeply into the most in-demand talents for the end of 2030.

The Future Will Not Happen Someday The future will not happen someday; it is happening now. We are seeing a paradigm change in learning, communicating, and doing business as we enter the 21st century. Technological progress and cultural shifts are replacing traditional talents with new ones. This change is about more than simply adapting to new technology; it's also about how we think and do things in the workplace and in life.
Future Job Market's Hottest Skills
The Rapid Development of AI and ML Machine learning and artificial intelligence (AI) are no longer futuristic concepts. They already exist and are having a profound effect on economies all around the world. Artificial intelligence (AI) and machine learning (ML) are two of the most promising and challenging fields of study now and tomorrow. The development of AI and Machine Learning has unlocked numerous doors. These new technology techniques are improving all aspects of human existence. They are already utilized for anything from consumer behavior prediction to automating mundane activities and illness detection. Artificial intelligence and machine learning experts are in high demand as these technologies advance. Why Data Science Is Crucial Data is the new oil in today's digital era. The study of analyzing large data sets, known as "Data Science," is gaining prominence. There is a critical shortage of data scientists and analysts in the workforce today. The study of data is just one aspect of data science. Decisions should be based on an appreciation of the narrative revealed by the evidence. Valuable insights are extracted from statistical analysis, data mining, predictive modeling, and machine learning. The need for data scientists is expected to rise with the exponential growth of data volumes. Expertise in Cybersecurity is Essential The significance of Cyber Security is growing as our daily lives become more dependent on technology. The need for people who can safeguard cyber infrastructure is expected to increase dramatically in light of the growing prevalence of cyberattacks. Defending against cyberattacks is just part of cyber security. The goal is to construct systems that are both attack-resistant and attack-recoverable. It requires an awareness of potential dangers, the discovery of weak spots, and the introduction of solid safeguards. The demand for cyber security experts is only expected to rise as the digital sphere develops. Computing in the Cloud's Importance Cloud computing has altered how organizations function by providing scalable and inexpensive answers to data storage and processing. The need for skilled workers familiar with cloud computing will grow as more companies move. Data storage on the cloud is just one aspect of cloud computing. The goal is to increase revenue by using cloud computing. Learning about cloud models, creating architectures, and overseeing cloud services are all part of this. Experts in cloud computing are in high demand, which will increase as more firms migrate to the cloud. Blockchain's Potential Effects The blockchain technology that underpins cryptocurrencies like Bitcoin may be used in industries outside of banking. Blockchain technology can revolutionize several industries, from supply chain management to voting systems. Blockchain applies to more than simply digital currency. Making a system for documenting financial transactions that is decentralized, open, and safe is the goal. It entails learning the fundamentals of blockchain technology, creating practical blockchain applications, and using Blockchain in commercial settings. The need for blockchain experts is expected to increase as more sectors investigate the technology's possibilities.
Which Skill Will Be Most Valuable in 2030?
Digital literacy has become the norm. With the advent of the digital age, the ability to effectively navigate the digital realm has become crucial. More is needed to use technology; you must also comprehend, modify, and use it to your advantage in addressing issues. There is more to digital literacy than just knowing how to utilize technology. Knowledge of digital technology's inner workings, societal effects, and potential issues-solving applications is essential. It's about feeling at home in the digital realm, knowing your way around, and making intelligent choices. Most employment will soon need candidates to demonstrate proficiency in digital media as the digital gap continues to shrink. The Importance of Emotional Quotient Because of the rise of AI and automation, the capacity to recognize and control one's emotions is emerging as a competitive advantage. The human connection may become more vital than ever as automation advances. Being in touch with one's feelings is just one aspect of emotional intelligence. Connecting with people requires empathy, self-control, and awareness of emotional reactions. Empathy, self-awareness, self-control, motivation, and social skills are all required. Emotional intelligence will become more important as companies grow more diverse and collaborative. The Value of Analytical Reasoning The ability to critically evaluate information and draw sound conclusions is essential in today's information-rich environment. This competency will be in high demand due to disinformation and false news proliferation. Questioning everything is not the same as exercising critical thinking. The ability to think critically, see biases, draw inferences, and act based on evidence is essential. Understanding, solving problems, and making sound choices are all required. Critical thinking will become more important as the difficulty of situations rises.
Which Occupations Will See the Most Growth by 2030?
The Surging Demand for AI Experts There will be a greater need for AI Experts who can create, deploy, and manage AI systems as AI develops. These experts will play a pivotal role in creating the future of technology at the forefront of the AI revolution. Experts in AI have many other skills outside of programming. They involve learning AI's fundamentals, developing practical AI applications, and checking if AI has a good moral compass. They require hard skills like coding and machine learning and softer ones like problem-solving and communication. Experts in AI are in high demand, and that's only going to increase as AI spreads. Data analysts are in high demand. Data analysts are in high demand as the volume of available data grows exponentially. These experts will be indispensable in assisting companies in making data-driven choices that fuel expansion and new product development. There is more to data analysis than simply statistics. They need knowledge of the business environment, formulate appropriate questions, and interpret data to provide insights. Soft skills like communication and critical thinking are as necessary as complex abilities like data mining and statistical analysis. There will always be a need for data analysts, especially as firms become more data-driven.

Cybersecurity Experts Are Needed Cybersecurity Experts Are Needed The need for Cyber Security Experts is expected to rise with the increasing sophistication of cyber threats. Our digital world will be protected by these specialists, who will serve as our first line of defense against cyber assaults. Professionals in cyber security do more than merely stop threats. They include learning about potential dangers, finding weak spots, and strengthening defenses. They need hard skills, like encryption and network security, and softer ones, including solving problems and communicating effectively. Demand for cyber security experts is expected to rise in step with the development of the digital economy. Cloud Architects Are Increasing in Number Cloud Architects, who can create and deploy cloud services, will be in high demand as more firms migrate to the cloud. These experts will be crucial in assisting companies in realizing the benefits of cloud computing. Cloud architects' responsibilities extend beyond the creation of cloud networks. They include knowing what your company requires, making an informed decision regarding cloud solutions, and checking that everything is safe and running well on the cloud. Smooth communication and project management skills are as critical as complex technical abilities like cloud computing and network design. The need for cloud architects is expected to grow with the maturation of cloud computing. Blockchain Developers Are on the Rise The need for Blockchain Developers is expected to increase as more use cases for the technology are discovered. These experts will be at the forefront of technological innovation, creating game-changing products for various markets. Coding is just one aspect of becoming a Blockchain Developer. These studies aim to learn the fundamentals of blockchain technology, create practical blockchain applications, and guarantee the safety and efficacy of blockchain infrastructure. Soft skills like problem-solving and communication are as critical as hard skills like coding and cryptography. The need for blockchain developers will only increase as the technology reshapes whole markets.
Which Soft Skills Will Be Needed in 2030?
The Impact of Verbal Exchanges Communication capacity is more crucial than ever in today's digital age. The ability to articulate ideas clearly, connect with others, and persuade others to see things your way will be crucial. Words on a page aren't the only means of communication. Being able to hear, process, and react are the keys. It requires fluency in talking, listening, and writing. It's about understanding, articulating yourself, and forming solid bonds with people. Communication skills will become more valuable as companies grow more diverse and collaborative. Why Flexibility Is Crucial The capacity to adjust to novel circumstances and difficulties is paramount in today's ever-evolving environment. Those adaptable, hungry for knowledge, and unfazed by setbacks will be in great demand. Being flexible isn't the same thing as being adaptable. It's about being receptive to change, daring to try something new, and resilient enough to bounce back from setbacks. Develop a growth attitude and improve your agility and resilience. Adaptability will become more critical as the rate of change increases. The Importance of Emotional Quotient We've already established that Emotional Intelligence (EQ) is going to be a need in the workplace of the future. In an increasingly interconnected society, the capacity to recognize and control one's own emotions will be a vital skill. Being in tune with one's feelings is just one aspect of emotional insight. Relationship development requires empathy, self-control, and awareness of others' feelings. Empathy, self-awareness, self-control, motivation, and social skills are all required. Emotional intelligence will become more important as companies grow more diverse and collaborative.

The Importance Of Originality And Imagination The Importance of Originality and Imagination The capacity to think creatively and innovatively will be highly prized in the future when regular chores are mechanized. Creative problem solvers will be in great demand in the coming years. Creating new ideas is just one aspect of creativity and innovation. They focus on resolving issues, enhancing operations, and creating value. They need you to think outside the box, solve problems, and take calculated risks. Creativity and innovation will become more critical as organizations compete in a constantly shifting market.
Which Competencies Will Become Essential in the Next Decade?
The Importance of Being Tech Savvy Digital literacy is becoming more important as technology develops. These abilities will be necessary for success in every aspect of the digital world, from coding to digital marketing. Having digital skills is much more than knowing how to use technology. They focus on the significance of technology in our lives and its use in problem-solving. They need various abilities, from familiarity with computers to in-depth technical knowledge. As the digital gap closes, the ability to use technology effectively will be expected in almost every position. Just How Important Knowledge of Data Is The capacity to comprehend and make sense of data will be essential in today's information-based society. Future success will need proficiency in data analysis. Understanding data is much more than simply looking at pretty pictures. The key is to analyze the data, choose the most pertinent questions to ask, and make your choices based on the results. Data visualization, statistical literacy, and analytical thinking are all required. Data literacy is increasingly important as companies rely on data to make decisions. Why It's Crucial to Raise Awareness About Cybersecurity Awareness of cyber security will become more critical as cyber dangers increase. All workers, not just those in the IT industry, need foundational cyber security knowledge. Being aware of the dangers of cyberspace is just the beginning. The goal is to learn how to safeguard your computer systems and company. Learn to recognize phishing attempts and use secure browsing habits to be protected online. Cybersecurity knowledge will become more important as the sophistication and frequency of cyberattacks increases. The Importance of Cloud-Based Skills Knowing how to make the most of and benefit from cloud services will be crucial as more companies transition. Future success will need proficiency in the cloud. To be cloud competent, one must do more than merely use these services. It is crucial to know how cloud services function, using them to address organizational challenges, and keeping them under control. One must be familiar with cloud architectures, resource management, and security to do this. Competency in the cloud will become more critical as cloud computing develops. The Importance of Comprehending Blockchain Technology Because of Blockchain's disruptive potential, familiarity with the technology is becoming more critical. Experts in Blockchain who know its many uses will be in great demand. Grasping Blockchain Is More Than Just Grasping How It Functions. The potential uses of Blockchain, the difficulties of deploying Blockchain, and the effects of Blockchain on organizations and society must all be comprehended. Knowing the fundamentals of Blockchain, the various blockchain implementations, and the applications for Blockchain are all essential. Knowing how blockchain works will become more critical as time goes on.
Conclusion
The skills environment is shifting as we move forward to 2030. The most sought-after abilities of the future include hard and soft talents, such as artificial intelligence, machine learning, emotional intelligence, and critical thinking. If we study these tendencies and hone these abilities, we can have a leg up on the competition for tomorrow's employment. Read the full article
#2030#AI#Blockchain#CloudComputing#CriticalThinking#CyberSecurity#DataScience#DigitalLiteracy#EmotionalIntelligence#FutureJobs#FutureSkills#MachineLearning#SoftSkills
0 notes
Link
Según las Naciones Unidas, las pequeñas y medianas empresas (PYMES) constituyen el 90 % de todas las empresas y aportan del 60 al 70 % de todos los puestos de trabajo en el mundo. Generan el 50 por ciento del producto interno bruto mundial y forman la columna vertebral de las economías de la mayoría de los países. Los más afectados por la pandemia de COVID, la geopolítica y el cambio climático, juegan un papel fundamental en la recuperación de un país y requieren un mayor apoyo de los gobiernos para mantenerse a flote. En el pasado, la percepción era que las grandes corporaciones eran más atractivas para los ciberdelincuentes. Sin embargo, en realidad, los ciberdelincuentes pueden atacar a cualquiera, especialmente a aquellos que están menos protegidos, mientras que las pequeñas empresas suelen tener presupuestos más pequeños y no están tan protegidas como las empresas más grandes. Según un informe de la empresa de ciberseguridad Barracuda, en 2021, las empresas con menos de 100 empleados experimentaron muchos más ataques de ingeniería social que las más grandes. Ese mismo año se produjo uno de los peores incidentes de ransomware de la historia, el ataque a la cadena de suministro de Kaseya VSA. Al explotar una vulnerabilidad en el software, la pandilla cibernética REvil se infiltró entre 1500 y 2000 empresas en todo el mundo, muchas de las cuales eran PYMES. Por ejemplo, el ataque golpeó a un pequeño proveedor de servicios gestionados Progressive Computing y, en virtud del efecto dominó, a los 80 clientes de la empresa, que en su mayoría eran pequeñas empresas. Aunque el ataque se detuvo con bastante rapidez, es comprensible que el sector de las pymes se conmocionara, lo que alertó a las empresas del hecho de que todos eran vulnerables. Según el informe de resiliencia cibernética de Kaspersky, en 2022, cuatro de cada diez empleadores admitieron que un incidente de ciberseguridad sería una crisis importante para su negocio, superada solo por una caída en las ventas o un desastre natural. Una crisis de ciberseguridad también sería el segundo tipo de crisis más difícil de manejar después de una caída dramática en las ventas, a juzgar por los resultados de la encuesta.
0 notes
Text
Identity Verification Market is expected to display a steady growth by 2027|CAGR: ~16%| UnivDatos Market Insights
According to a new report published by UnivDatos Markets Insights the Identity Verification Market is expected to grow at a CAGR of around 16% from 2021-2027. The analysis has been segmented into Component (Solutions and Services); Type (Biometric and Non-Biometric); Deployment (On-premises and Cloud); Organization Size (Large Enterprises and SMEs); Industry (Information and Communication Technology, Banking and Financial Services, Retail, Healthcare, and Others) Region/Country.
Click here to view the Report Description & TOC - https://univdatos.com/report/identity-verification-market/
The identity verification market report has been aggregated by collecting informative data on various dynamics such as market drivers, restraints, and opportunities. This innovative report makes use of several analyses to get a closer outlook on the identity verification market. The identity verification market report offers a detailed analysis of the latest industry developments and trending factors in the market that are influencing the market growth. Furthermore, this statistical market research repository examines and estimates the identity verification market at the global and regional levels.
Market Overview
The global identity verification market is expected to register a CAGR of around 16% over the period of 2021-2027. The global identity verification market is rising on account of the growing digitalization, growing uses of digital identities among industries, and the increasing frequency of identity theft and cyberattacks. Increasing regulation and mandatory compliance with standards in all industries, especially in the financial sector, is expected to create many opportunities for market participants. Moreover, the increasing frequency of identity theft and cyberattacks are one of the most prominent factors driving the adoption of identity verification. For instance, according to the FBI's 2021 Internet Crime Report, record 847,376 cybercrime complaints were reported to the FBI by the general public, up 7% from 2020. Identity verification is used by businesses to ensure that a user or customer provides information related to the identity of a real person. Verifying an individual's identity is essential to prove that there is a real person behind the transaction or process. Scammers create fake profiles before misusing their business, such as defaulting online loans, creating multiple accounts to exploit promotion systems, or triggering affiliate rewards.
COVID-19 Impact
Following the outbreak of COVID-19, trends such as work from home (WFH) are forcing industries around the world to adapt to the new digital world. Provide employees and customers with stronger and more reliable authentication as all businesses operate in a digital world where cyber attackers will do anything to carry out attacks such as identity theft and identity theft. There is a growing need and importance for stronger methods of identity verification to provide access to them.
The global identity verification market report is studied thoroughly with several aspects that would help stakeholders in making their decisions more curated.
· By organization size, the market is bifurcated into large enterprises and SMEs. Among these two, the large enterprises have a sizeable share of the global identity verification market, and this segment is expected to witness strong growth during the forecast period owing to the factors such as protection against increased cases of money laundering, data breach, identity theft, secured processing of high-risk transactions, mandatory compliance with different regulations, and protected digital payments
· On the basis of industry, the identity verification market is segmented into information and communication technology, banking and financial services, government, healthcare, and others. The banking and financial services industry held a remarkable share of the global identity verification market. With the increasing digitization of banking processes such as digital onboarding and digital payments to improve the customer experience, the need for identity verification is increasing in this industry
Request for Sample Pages - https://univdatos.com/get-a-free-sample-form-php/?product_id=24265
Identity Verification Market Geographical Segmentation Includes:
· North America (US, Canada, Rest of North America)
· Europe (Germany, France, Spain, UK, Rest of Europe)
· Asia-Pacific (China, Japan, India, South Korea, Rest of Asia-Pacific)
· Rest of the World
For a better understanding of the market adoption of identity verification, the market is analyzed based on its worldwide presence in the countries such as North America (US, Canada, Rest of North America), Europe (Germany, France, Spain, UK, Rest of Europe), Asia-Pacific (China, Japan, India, South Korea, Rest of Asia-Pacific), Rest of World. North America is expected to grow at a steady growth rate as it is a technologically advanced region with the presence of many early adopters and major market players. In addition, factors such as the development of government initiatives such as smart infrastructure, smart cities, and digital identity-based driver's licenses, as well as increasing integration of various technologies such as AI, ML, and blockchain to secure digital identities are further contributing to the identity verification market
The major players targeting the market include
· Experian Information Solutions Inc.
· GB Group plc
· Equifax Inc.
· Mitek Systems Inc.
· LexisNexis Risk Solutions Group
· Trulioo Information Services Inc.
· Acuant Inc.
· TransUnion LLC
· Innovatrics s.r.o.
· Applied Recognition Corp.
Competitive Landscape
The degree of competition among prominent global companies has been elaborated by analyzing several leading key players operating worldwide. The specialist team of research analysts sheds light on various traits such as global market competition, market share, most recent industry advancements, innovative product launches, partnerships, mergers, or acquisitions by leading companies in the identity verification market. The major players have been analyzed by using research methodologies for getting insight views on global competition.
Have a Look at the Chapters - https://univdatos.com/report/identity-verification-market/
Key questions resolved through this analytical market research report include:
• What are the latest trends, new patterns, and technological advancements in the identity verification market?
• Which factors are influencing the identity verification market over the forecast period?
• What are the global challenges, threats, and risks in the identity verification market?
• Which factors are propelling and restraining the identity verification market?
• What are the demanding global regions of the identity verification market?
• What will be the global market size in the upcoming years?
• What are the crucial market acquisition strategies and policies applied by global companies?
We understand the requirement of different businesses, regions, and countries, we offer customized reports as per your requirements of business nature and geography. Please let us know If you have any custom needs.
0 notes