#devsecops size
Explore tagged Tumblr posts
Link
Increasing demand for DevSecOps Solutions among SMEs is expected to provide opportunities for the DevSecOps market growth...
0 notes
Link
0 notes
Text
DevSecOps Market In-depth Study: Securing Software Development
DevSecOps is a software development approach that integrates security practices into the DevOps methodology. It emphasizes the need to prioritize security throughout the entire software development lifecycle, from the initial design phase to deployment and beyond. By incorporating security considerations from the beginning, DevSecOps aims to identify and address vulnerabilities early on, reducing the risk of cyber threats and data breaches. This approach involves close collaboration between development, operations, and security teams, fostering a shared responsibility for security. With DevSecOps, automated security testing, code analysis, and continuous monitoring become integral parts of the development process, enabling rapid detection and remediation of security issues. By integrating security into DevOps practices, organizations can build robust, secure, and resilient software applications while maintaining agility and accelerating time-to-market.
Gain deeper insights on the market and receive your free copy with TOC now @: DevSecOps Market Report
Organizations are increasingly adopting the concept of "shift-left" security, which involves integrating security practices and testing earlier in the software development lifecycle. This approach helps identify vulnerabilities and mitigate security risks at the earliest stages of development. Automation continues to play a crucial role in DevSecOps, with the aim of integrating security seamlessly into the development pipeline. Automation tools and technologies enable continuous security testing, code scanning, vulnerability management, and compliance monitoring throughout the software development process. As containerization and container orchestration platforms such as Docker and Kubernetes gain popularity, ensuring the security of containerized applications has become a key focus area. DevSecOps practices include implementing container security measures, such as vulnerability scanning, image verification, and runtime protection, to safeguard applications deployed in container environments.
DevSecOps emphasizes the use of "compliance as code" to automate and integrate regulatory and security compliance requirements into the development process. This approach involves writing compliance rules and policies as code, enabling automated validation and enforcement, reducing manual effort, and ensuring consistent compliance across deployments. Organizations are recognizing the importance of fostering a strong security culture and collaboration between development, operations, and security teams. This involves promoting security awareness, training, and shared responsibility for security practices, leading to improved collaboration and more effective security integration throughout the development lifecycle. With the widespread adoption of cloud computing, securing cloud-based applications and infrastructure has become critical. DevSecOps includes implementing cloud-specific security measures, such as cloud-native security tools, configuration management, and identity and access management (IAM) practices, to protect applications and data in cloud environments.
#DevSecOps Market Size & Share#Global DevSecOps Market#DevSecOps Market Latest Trends#DevSecOps Market Growth Forecast#COVID-19 Impacts On DevSecOps Market#DevSecOps Market Revenue Value
0 notes
Text
CNAPP Explained: The Smartest Way to Secure Cloud-Native Apps with EDSPL

Introduction: The New Era of Cloud-Native Apps
Cloud-native applications are rewriting the rules of how we build, scale, and secure digital products. Designed for agility and rapid innovation, these apps demand security strategies that are just as fast and flexible. That’s where CNAPP—Cloud-Native Application Protection Platform—comes in.
But simply deploying CNAPP isn’t enough.
You need the right strategy, the right partner, and the right security intelligence. That’s where EDSPL shines.
What is CNAPP? (And Why Your Business Needs It)
CNAPP stands for Cloud-Native Application Protection Platform, a unified framework that protects cloud-native apps throughout their lifecycle—from development to production and beyond.
Instead of relying on fragmented tools, CNAPP combines multiple security services into a cohesive solution:
Cloud Security
Vulnerability management
Identity access control
Runtime protection
DevSecOps enablement
In short, it covers the full spectrum—from your code to your container, from your workload to your network security.
Why Traditional Security Isn’t Enough Anymore
The old way of securing applications with perimeter-based tools and manual checks doesn’t work for cloud-native environments. Here’s why:
Infrastructure is dynamic (containers, microservices, serverless)
Deployments are continuous
Apps run across multiple platforms
You need security that is cloud-aware, automated, and context-rich—all things that CNAPP and EDSPL’s services deliver together.
Core Components of CNAPP
Let’s break down the core capabilities of CNAPP and how EDSPL customizes them for your business:
1. Cloud Security Posture Management (CSPM)
Checks your cloud infrastructure for misconfigurations and compliance gaps.
See how EDSPL handles cloud security with automated policy enforcement and real-time visibility.
2. Cloud Workload Protection Platform (CWPP)
Protects virtual machines, containers, and functions from attacks.
This includes deep integration with application security layers to scan, detect, and fix risks before deployment.
3. CIEM: Identity and Access Management
Monitors access rights and roles across multi-cloud environments.
Your network, routing, and storage environments are covered with strict permission models.
4. DevSecOps Integration
CNAPP shifts security left—early into the DevOps cycle. EDSPL’s managed services ensure security tools are embedded directly into your CI/CD pipelines.
5. Kubernetes and Container Security
Containers need runtime defense. Our approach ensures zero-day protection within compute environments and dynamic clusters.
How EDSPL Tailors CNAPP for Real-World Environments
Every organization’s tech stack is unique. That’s why EDSPL never takes a one-size-fits-all approach. We customize CNAPP for your:
Cloud provider setup
Mobility strategy
Data center switching
Backup architecture
Storage preferences
This ensures your entire digital ecosystem is secure, streamlined, and scalable.
Case Study: CNAPP in Action with EDSPL
The Challenge
A fintech company using a hybrid cloud setup faced:
Misconfigured services
Shadow admin accounts
Poor visibility across Kubernetes
EDSPL’s Solution
Integrated CNAPP with CIEM + CSPM
Hardened their routing infrastructure
Applied real-time runtime policies at the node level
✅ The Results
75% drop in vulnerabilities
Improved time to resolution by 4x
Full compliance with ISO, SOC2, and GDPR
Why EDSPL’s CNAPP Stands Out
While most providers stop at integration, EDSPL goes beyond:
🔹 End-to-End Security: From app code to switching hardware, every layer is secured. 🔹 Proactive Threat Detection: Real-time alerts and behavior analytics. 🔹 Customizable Dashboards: Unified views tailored to your team. 🔹 24x7 SOC Support: With expert incident response. 🔹 Future-Proofing: Our background vision keeps you ready for what’s next.
EDSPL’s Broader Capabilities: CNAPP and Beyond
While CNAPP is essential, your digital ecosystem needs full-stack protection. EDSPL offers:
Network security
Application security
Switching and routing solutions
Storage and backup services
Mobility and remote access optimization
Managed and maintenance services for 24x7 support
Whether you’re building apps, protecting data, or scaling globally, we help you do it securely.
Let’s Talk CNAPP
You’ve read the what, why, and how of CNAPP — now it’s time to act.
📩 Reach us for a free CNAPP consultation. 📞 Or get in touch with our cloud security specialists now.
Secure your cloud-native future with EDSPL — because prevention is always smarter than cure.
0 notes
Text
API Security Market
API Security Market size is estimated to reach $6.3 billion by 2030, growing at a CAGR of 25.4% during the forecast period 2023–2030.
🔗 𝐆𝐞𝐭 𝐑𝐎𝐈-𝐟𝐨𝐜𝐮𝐬𝐞𝐝 𝐢𝐧𝐬𝐢𝐠𝐡𝐭𝐬 𝐟𝐨𝐫 𝟐𝟎𝟐𝟓-𝟐𝟎𝟑𝟏 → 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐍𝐨𝐰
API security market is rapidly expanding as organizations increasingly rely on APIs to enable digital services, integrate systems, and streamline operations. With this growth comes rising threats, including data breaches, injection attacks, and unauthorized access. API security focuses on protecting these interfaces through authentication, authorization, encryption, traffic monitoring, and threat detection. Key sectors such as finance, healthcare, and e-commerce are driving demand for robust API protection. As businesses adopt microservices, cloud computing, and mobile applications, the need for advanced API security solutions grows.
🚀 𝐊𝐞𝐲 𝐌𝐚𝐫𝐤𝐞𝐭 𝐃𝐫𝐢𝐯𝐞𝐫𝐬 𝐟𝐨𝐫 𝐀𝐏𝐈 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲:
📈 𝐑𝐚𝐩𝐢𝐝 𝐆𝐫𝐨𝐰𝐭𝐡 𝐨𝐟 𝐀𝐏𝐈𝐬 𝐀𝐜𝐫𝐨𝐬𝐬 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐢𝐞𝐬
The explosion of cloud services, mobile apps, and IoT devices has led to a surge in API usage, increasing the need for robust API protection.
🔐 𝐑𝐢𝐬𝐢𝐧𝐠 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐡𝐫𝐞𝐚𝐭𝐬
APIs are a frequent target for attacks like data leaks, DDoS, injection, and broken authentication, driving demand for advanced security solutions.
☁️ 𝐖𝐢𝐝𝐞𝐬𝐩𝐫𝐞𝐚𝐝 𝐂𝐥𝐨𝐮𝐝 𝐀𝐝𝐨𝐩𝐭𝐢𝐨𝐧
As businesses migrate to cloud-based services and microservices architectures, securing API communication becomes mission-critical.
📱 𝐏𝐫𝐨𝐥𝐢𝐟𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐨𝐟 𝐌𝐨𝐛𝐢𝐥𝐞 & 𝐖𝐞𝐛 𝐀𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬
APIs power user-facing and backend services, making their security essential to ensure data integrity and user trust.
🏥 𝐆𝐫𝐨𝐰𝐭𝐡 𝐢𝐧 𝐒𝐞𝐧𝐬𝐢𝐭𝐢𝐯𝐞 𝐃𝐚𝐭𝐚 𝐓𝐫𝐚𝐧𝐬𝐚𝐜𝐭𝐢𝐨𝐧𝐬
Industries like finance and healthcare rely heavily on APIs to exchange personal and financial information, increasing the need for strong compliance-driven API protection.
𝐋𝐢𝐦𝐢𝐭𝐞𝐝-𝐓𝐢𝐦𝐞 𝐎𝐟𝐟𝐞𝐫: 𝐆𝐞𝐭 $𝟏𝟎𝟎𝟎 𝐎𝐟𝐟 𝐘𝐨𝐮𝐫 𝐅𝐢𝐫𝐬𝐭 𝐏𝐮𝐫𝐜𝐡𝐚𝐬𝐞
𝐓𝐨𝐩 𝐊𝐞𝐲 𝐏𝐥𝐚𝐲𝐞𝐫𝐬:
FortiVenture | Zoom | Rakuten | Naspers Limited | Twilio | Activision Blizzard | Recruit Holdings Co., Ltd. | STARLINK | Kazakhtelecom JSC Quantum | TikTok Shop | EPAM Systems | CenturyLink | Facebook Synopsys Inc | Altice USA | Palo Alto Networks | HubSpot | Akamai Technologies | Cadence
#APISecurity #Cybersecurity #CloudSecurity #DataProtection #Infosec #ApplicationSecurity #DevSecOps #ZeroTrust #APIManagement #OAuth

0 notes
Text
DevOps 2025: Accelerating Innovation Through Unified Development and Operations
DevOps in 2025 stands at the forefront of digital transformation, driving faster, more reliable software delivery through a culture of collaboration and continuous improvement. By integrating development and operations teams with advanced automation, AI-driven monitoring, and Infrastructure as Code (IaC), DevOps enables organizations to deploy updates at unprecedented speed and scale. Security has evolved into DevSecOps, embedding protection seamlessly into the CI/CD pipeline. With cloud-native tools, microservices architecture, and container orchestration becoming standard, DevOps is no longer just a methodology—it’s a strategic imperative for businesses aiming to stay competitive, agile, and resilient in a tech-driven world.
#DevOps2025#CI_CD#AutomationFirst#DevSecOps#CloudNative#AgileDevelopment#InfrastructureAsCode#SoftwareDelivery#DigitalTransformation#SiteReliabilityEngineering
0 notes
Text
DevOps services company in Noida
As businesses in Noida grow rapidly in the digital space, the demand for DevOps services is at an all-time high. Whether you're a startup trying to ship code faster or an enterprise aiming to scale operations, DevOps can transform your entire development and deployment pipeline. But a common dilemma remains: Should you hire a DevOps services company in Noida or work with a freelancer?
This article helps you weigh both options—considering factors like cost, quality, reliability, scalability, and long-term value. By the end, you'll have a clearer understanding of which is the right fit for your business goals.
What Does a DevOps Services Company in Noida Offer?
Before jumping into the comparison, let’s understand what a DevOps services company in Noida typically provides:
End-to-End Automation: CI/CD pipelines, test automation, infrastructure as code (IaC)
Cloud Integration: AWS, Azure, Google Cloud, or hybrid environments
Monitoring & Logging: Real-time system monitoring, alert systems, log analysis
Security & Compliance: DevSecOps practices built into workflows
Scalability: Containerization with Docker, orchestration using Kubernetes
24/7 Support & SLA-based services
Team Collaboration & Agile Practices
These companies usually have multi-domain expertise, large teams, and infrastructure to support businesses of all sizes.
What Do Freelance DevOps Professionals Offer?
Freelancers are individual specialists who may have worked across multiple domains and offer services like:
CI/CD pipeline setup
Script automation
Server configuration and management
Cloud deployments
Performance tuning and basic monitoring
Freelancers are often hired for short-term, project-based work and may work independently or remotely.
1. Expertise and Skill Depth
✅ DevOps Services Company in Noida
Offers a team of experts: developers, cloud architects, DevOps engineers, and QA specialists
Experienced across industries like fintech, e-commerce, healthcare, and logistics
Proven track record with certifications and case studies
✅ Freelancer
Expertise depends on the individual’s experience
May lack broader team collaboration
Might be highly skilled in specific tools but not full-stack DevOps
Verdict: If you're looking for in-depth knowledge, companies offer a more robust and diverse skill set.
2. Project Scope and Scalability
✅ DevOps Services Company in Noida
Capable of handling large-scale and complex projects
Can scale resources up/down based on project needs
Well-versed in compliance, cloud migration, and enterprise integrations
✅ Freelancer
Ideal for small-scale or one-time automation projects
Limited by bandwidth and resources
Scalability is usually restricted to what one person can manage
Verdict: For long-term or complex infrastructure, a DevOps company offers more scalability.
3. Cost Comparison
✅ DevOps Services Company in Noida
May have higher upfront costs
However, services are often backed by SLAs, guarantees, and support
Less risk of delays or rework
✅ Freelancer
Typically more affordable for small tasks or short-term contracts
May charge hourly or project-based
Potential hidden costs due to limited availability or lack of documentation
Verdict: Freelancers are cost-effective for small tasks, but companies provide better value for the long run.
4. Reliability and Accountability
✅ DevOps Services Company in Noida
Operates under contracts, SLAs, and strict timelines
Offers dedicated account managers and round-the-clock support
Provides documentation and transition support
✅ Freelancer
May lack structured timelines or dedicated reporting
Risk of unavailability due to other projects or personal issues
Communication gaps or project abandonment are common concerns
Verdict: Companies are far more reliable and accountable for critical operations.
5. Security & Compliance
✅ DevOps Services Company in Noida
Follows industry security protocols
Implements DevSecOps for security throughout the pipeline
Aware of local and global compliance regulations like GDPR, HIPAA, etc.
✅ Freelancer
May not be updated with the latest compliance laws
Risk of data breaches or poor security practices
Documentation and access control might be weak
Verdict: If your business handles sensitive data, go with a DevOps company that ensures proper security.
6. Support & Maintenance
✅ DevOps Services Company in Noida
24/7 technical support
Maintenance packages and performance audits
Disaster recovery plans included
✅ Freelancer
May not be available for emergency fixes
Often moves on after project completion
Support is usually informal and non-committal
Verdict: For continuous operations and support, companies are the better choice.
When to Choose a Freelancer
You have a very limited budget
Your project is short-term and well-defined
You need quick help for small fixes or initial DevOps setup
You already have a team and just need one expert for a specific task
When to Choose a DevOps Services Company in Noida
You need long-term DevOps strategy and execution
Your business requires scalability, security, and continuous support
You're undergoing cloud migration or digital transformation
Your app handles large traffic, sensitive data, or needs high uptime
You value partnership, documentation, and accountability
Final Thoughts
In the digital age, DevOps is no longer optional — it’s a necessity for performance, security, and speed. While freelancers can be a quick fix for small jobs, they often fall short in terms of long-term value, reliability, and scalability. A DevOps services company in Noida brings structured expertise, dedicated teams, and a strategic approach tailored to your business needs.
If you're serious about growth and digital stability, partnering with a trusted local DevOps company might be the smartest step you take.
Need help getting started? Connect with a top-rated DevOps services company in Noida to discuss your goals, challenges, and how automation can drive your next level of growth.
0 notes
Text
CI/CD Pipelines in the Cloud: How to Achieve Faster, Safer Deployments
In today’s digital-first world, speed and reliability in software delivery are critical. With cloud infrastructure becoming the new normal, CI/CD pipelines (Continuous Integration and Continuous Deployment) are key to enabling faster, safer deployments. They help development teams automate code integration, testing, and deployment—removing bottlenecks and minimizing risks.
In this blog, we’ll explore how CI/CD works in cloud environments, why it’s essential for modern development, and how it supports seamless delivery of scalable, secure applications.
🛠️ What Is CI/CD?
Continuous Integration (CI): Developers frequently merge code into a shared repository. Each change triggers automated tests to catch bugs early.
Continuous Deployment (CD): After passing tests, code is automatically deployed to production or staging environments without manual intervention.
Together, CI/CD creates a feedback loop that ensures rapid, reliable software delivery.
🌐 Why CI/CD Pipelines Matter in the Cloud
CI/CD is not a luxury—it’s a necessity in the cloud. Here’s why:
Cloud environments are dynamic: With auto-scaling, microservices, and distributed systems, manual deployments are error-prone and slow.
Rapid release cycles: Customers expect continuous improvements. CI/CD helps teams ship features weekly or even daily.
Consistency and traceability: Every change is logged, tested, and version-controlled—reducing deployment risks.
The cloud provides the perfect infrastructure for CI/CD pipelines, offering scalability, flexibility, and automation capabilities.
🔁 How a Cloud-Based CI/CD Pipeline Works
A typical CI/CD pipeline in the cloud includes:
Code Commit: Developers push code to a Git repository (e.g., GitHub, GitLab, Bitbucket).
Build & Test: Cloud-native CI tools (like GitHub Actions, AWS CodeBuild, or CircleCI) compile the code and run unit/integration tests.
Artifact Creation: Build artifacts (e.g., Docker images) are stored in cloud repositories (e.g., Amazon ECR, Azure Container Registry).
Deployment: Tools like AWS CodeDeploy, Azure DevOps, or ArgoCD deploy the artifacts to target environments.
Monitoring: Real-time monitoring and alerts ensure the deployment is successful and stable.
✅ Benefits of Cloud CI/CD
1. Faster Time-to-Market
Automated testing and deployment reduce manual overhead, accelerating release cycles.
2. Improved Code Quality
Each commit is tested, catching bugs early and ensuring only clean code reaches production.
3. Consistent Deployments
Standardized pipelines eliminate the “it worked on my machine” problem, ensuring repeatable results.
4. Efficient Collaboration
CI/CD fosters DevOps culture, encouraging collaboration between developers, testers, and operations.
5. Scalability on Demand
Cloud CI/CD systems scale automatically with the size and complexity of the application.
🔐 Security and Compliance in CI/CD
Modern pipelines are integrating security and compliance checks directly into the deployment process (DevSecOps). These include:
Static and dynamic code analysis
Container vulnerability scans
Secrets detection
Infrastructure compliance checks
By catching vulnerabilities early, businesses reduce risks and ensure regulatory alignment.
📊 CI/CD with IaC and Automated Testing
CI/CD becomes even more powerful when combined with:
Infrastructure as Code (IaC) for consistent cloud infrastructure provisioning
Automated Testing to validate performance, functionality, and security
Together, they create a fully automated, end-to-end deployment ecosystem that supports cloud-native scalability and resilience.
🏢 How Salzen Cloud Builds Smart CI/CD Solutions
At Salzen Cloud, we design and implement cloud-native CI/CD pipelines tailored to your business needs. Whether you're deploying microservices on Kubernetes, serverless applications, or hybrid environments, we help you:
Automate build, test, and deployment workflows
Integrate security and compliance into your pipelines
Optimize for speed, reliability, and rollback safety
Monitor performance and deployment health in real time
Our solutions empower teams to ship faster, fix faster, and innovate with confidence.
🧩 Conclusion
CI/CD is the backbone of modern cloud development. It streamlines the software delivery process, reduces manual errors, and provides the agility needed to stay competitive.
To achieve faster, safer deployments in the cloud:
Adopt CI/CD pipelines for all projects
Integrate IaC and automated testing
Shift security left with DevSecOps practices
Continuously monitor and optimize your pipelines
With the right CI/CD strategy, your team can move fast without breaking things—delivering value to users at cloud speed.
Want help designing a CI/CD pipeline for your cloud environment? Let Salzen Cloud show you how.
0 notes
Text
Cloud Data Security Market Size, Share, Industry Outlook & Forecast to 2032

The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
The global cloud data security market is undergoing a transformative shift as organizations accelerate digital transformation and embrace hybrid cloud architectures. As cyber threats become increasingly sophisticated, enterprises are investing in cloud-native security solutions to safeguard sensitive data and ensure regulatory compliance. With the expansion of remote work, the demand for scalable and agile data protection strategies has intensified, propelling growth across industries such as banking, healthcare, and retail.
Cloud Data Security Market Poised for Strategic Advancements Rapid innovations in artificial intelligence, machine learning, and encryption technologies are fueling a new era in cloud data security. Enterprises are transitioning from traditional perimeter-based defenses to dynamic, identity-centric models that offer greater resilience and adaptability. This evolution is supported by the proliferation of multi-cloud environments, which require robust security frameworks capable of managing complex data flows and access points without compromising performance or user experience.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Market Analysis
The cloud data security market is characterized by a highly competitive landscape featuring both established cybersecurity providers and emerging startups. Strategic alliances, mergers, and acquisitions are shaping the trajectory of the market, as companies seek to integrate advanced security features such as automated threat detection, behavioral analytics, and zero-trust architecture. The increasing stringency of global data protection laws is compelling organizations to invest in compliance-driven security solutions tailored to regional regulatory frameworks.
As businesses adopt Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS) models, cloud security is no longer an optional component but a critical enabler of trust and operational continuity. The integration of DevSecOps practices further emphasizes security as a core part of the software development lifecycle, fostering a proactive rather than reactive security posture.
Market Trends
Surge in demand for cloud-native security solutions to secure hybrid and multi-cloud infrastructures
Rising adoption of Zero Trust security frameworks for identity and access management
Growth in AI- and ML-powered threat detection and automated response mechanisms
Emphasis on data sovereignty and localized cloud security compliance measures
Expansion of DevSecOps practices integrating security at every stage of development
Increased focus on Secure Access Service Edge (SASE) to unify networking and security
Rapid evolution of encryption standards for data-at-rest, in-transit, and in-use
Greater investment in secure collaboration tools for remote workforce protection
Market Scope
The scope of the cloud data security market extends across a wide array of sectors including finance, healthcare, IT, telecommunications, manufacturing, and government. Enterprises are seeking end-to-end encryption, secure access control, and continuous monitoring solutions that align with their digital maturity. As cloud adoption reaches new heights, vendors are scaling offerings to support diverse workloads, APIs, and third-party integrations. The market also encompasses cloud security posture management (CSPM), data loss prevention (DLP), and cloud access security broker (CASB) technologies, collectively fortifying organizational resilience in an increasingly hostile cyber landscape.
Market Forecast
Over the forecast period, the cloud data security market is expected to maintain robust momentum, driven by technological innovations and the global push toward data-centric digital ecosystems. Cloud security will increasingly become embedded within broader digital transformation strategies, with providers focusing on intuitive, automated, and scalable platforms. Organizations will continue prioritizing investments in user behavior analytics, micro-segmentation, and unified threat management to preempt breaches and maintain trust. With the convergence of networking and security under cloud-native frameworks, the market is poised to evolve beyond traditional paradigms into a new standard of digital trust infrastructure.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The future of cloud data security is not just about protecting data—it’s about enabling digital confidence in a rapidly evolving business landscape. As enterprises redefine their digital blueprints, security leaders are called to align protection with innovation, ensuring that cloud adoption drives growth without compromising integrity. This dynamic market offers not only challenges but also immense opportunities for vendors and enterprises ready to invest in resilient, intelligent, and future-forward security architectures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
The key components of a successful DevOps strategy
A successful DevOps strategy integrates people, processes, and tools to accelerate software delivery while maintaining quality and reliability. A DevOps consulting company is a firm that helps businesses adopt and implement DevOps practices to improve their software development and IT operations.Here are the key components that form the foundation of an effective DevOps strategy:
1. Collaborative Culture
Why it matters: DevOps is rooted in breaking down silos between development and operations.
What to focus on: Shared ownership, open communication, cross-functional teams, and a culture of continuous learning.
2. Automation
Why it matters: Manual tasks slow down delivery and introduce inconsistency.
What to automate:
Code integration (CI)
Testing
Deployment (CD)
Infrastructure provisioning (IaC)
Monitoring and alerting
3. Continuous Integration & Continuous Delivery (CI/CD)
Why it matters: CI/CD pipelines streamline software delivery and reduce errors.
CI: Developers merge code frequently; automated builds and tests run continuously.
CD: Code is automatically deployed to staging or production, allowing for faster releases.
4. Infrastructure as Code (IaC)
Why it matters: Manages infrastructure with version-controlled code.
Tools: Terraform, AWS CloudFormation, Pulumi, Ansible.
Benefits: Repeatable environments, scalability, better collaboration.
5. Monitoring and Observability
Why it matters: Enables proactive identification of issues in systems and applications.
Key metrics to monitor: System health, application performance, user behavior.
Tools: Prometheus, Grafana, ELK Stack, Datadog, New Relic.
6. Security (DevSecOps)
Why it matters: Embeds security into every stage of the development lifecycle.
Practices: Static code analysis, vulnerability scanning, secrets management, compliance checks.
Tools: Snyk, Aqua, HashiCorp Vault, SonarQube.
7. Scalable Toolchain
Why it matters: The right tools ensure consistency and scalability.
Strategy: Choose tools that integrate well and support your tech stack and team size.
8. Feedback Loops
Why it matters: Helps teams improve continuously.
Sources: Monitoring alerts, customer feedback, post-mortems, sprint retrospectives.
9. Change Management & Governance
Why it matters: Enables safe, compliant changes in a fast-moving environment.
Practices: Change approval processes, audit trails, version control, rollback mechanisms.
10. Leadership & Alignment
Why it matters: Executive support ensures buy-in across departments.
Focus areas: Clear vision, goals aligned with business outcomes, investment in people and tools.
Flycatch DevOps consulting company in Saudi Arabia works by helping businesses adopt, implement, and optimize DevOps practices. Their goal is to improve collaboration between development and operations teams, automate workflows, and accelerate software delivery while maintaining security and reliability.
0 notes
Link
Increasing demand for DevSecOps Solutions among SMEs is expected to provide opportunities for the DevSecOps market growth...
0 notes
Text
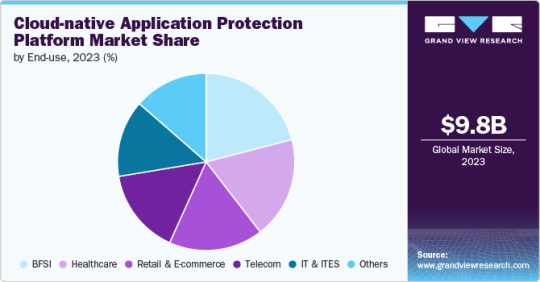
The Future of Security: Cloud-native Application Protection Platform Market Overview
Cloud-native Application Protection Platform Market Growth & Trends
The global Cloud-native Application Protection Platform Market size was estimated at USD 9.79 billion in 2023 and is expected to grow at a CAGR of 21.8% from 2024 to 2030. The market is witnessing significant growth due to the increasing adoption of cloud-native applications and the rising need for robust security solutions. Cloud-native application protection platforms (CNAPP)s offer comprehensive protection for cloud-native environments, encompassing various security aspects such as workload protection, runtime protection, and compliance management. These platforms are designed to secure applications built using cloud-native technologies, ensuring they remain resilient against a broad range of cyber threats.
Several key factors are driving the demand for CNAPPs including the shift towards microservices and containerization has increased the complexity of securing applications, making traditional security approaches inadequate. CNAPPs address this challenge by providing visibility and control over dynamic, distributed environments. Secondly, the surge in cyberattacks targeting cloud-native applications has heightened awareness of the need for advanced security measures. Organizations are increasingly prioritizing security to protect their sensitive data and maintain customer trust.
The integration of artificial intelligence (AI) and machine learning (ML) capabilities. These technologies help in enhancing threat detection and response capabilities by assessing vast amounts of data and identifying anomalies in real-time. Additionally, the rise of DevSecOps practices, which integrate security into the development and operations processes, is driving the adoption of CNAPPs. This approach ensures that security is a continuous concern throughout the application lifecycle, rather than an afterthought.
Furthermore, there is a growing emphasis on compliance and regulatory requirements. As governments and industry bodies impose stricter regulations on data protection and privacy, organizations are compelled to adopt CNAPPs to ensure compliance. These platforms offer features such as automated compliance checks and reporting, helping organizations avoid hefty fines and reputational damage.
Curious about the Cloud-native Application Protection Platform Market? Download your FREE sample copy now and get a sneak peek into the latest insights and trends.
Cloud-native Application Protection Platform Market Report Highlights
The platform segment accounted for the largest market share of over 60% in 2023. Cloud-native application protection platforms (CNAPPs) provide a comprehensive security framework designed to safeguard cloud-native environments.
The public cloud segment accounted for the largest market share of over 68% in 2023.
The hybrid cloud segment is expected to grow at a significant rate during the forecast period. The demand for hybrid cloud native application protection platform is driven by the need for consistent security policies across diverse environments, seamless data integration, and flexibility in resource allocation.
The large enterprise segment accounted for the largest market share of over 58% in 2023.
The SMEs segment is expected to grow at a significant rate over the forecast period. Key factors driving demand include cost-effectiveness, scalability, and ease of deployment.
Cloud-native Application Protection Platform Market Segmentation
Grand View Research has segmented the global Cloud-Native Application Protection Platform (CNAPP) market report based on offering, deployment, enterprise size, end-use, and region:
Offering Outlook (Revenue; USD Billion; 2018 - 2030)
Platform
Services
Deployment Outlook (Revenue; USD Billion; 2018 - 2030)
Private
Public
Hybrid
Enterprise Size Outlook (Revenue; USD Billion; 2018 - 2030)
SMEs
Large Enterprises
End-use Outlook (Revenue; USD Billion; 2018 - 2030)
BFSI
Healthcare
Retail & E-commerce
Telecom
IT & ITES
Others
Download your FREE sample PDF copy of the Cloud-native Application Protection Platform Market today and explore key data and trends.
0 notes
Text
Application Security Market Drivers: Key Forces Powering Growth Across the Cybersecurity Landscape
The application security market is witnessing significant momentum, fueled by several critical factors reshaping the cybersecurity industry. As businesses grow increasingly reliant on digital infrastructure, the need to safeguard applications—whether web, mobile, or cloud-based—has become paramount. In this fast-changing landscape, various dynamic forces are driving the market’s growth and evolution.

One of the most prominent drivers is the rising frequency and sophistication of cyberattacks. Applications are prime targets for threat actors looking to exploit vulnerabilities for data breaches, ransomware, or unauthorized access. With attackers employing advanced techniques like zero-day exploits and AI-powered intrusions, organizations are under mounting pressure to secure their applications comprehensively. This growing threat landscape has compelled enterprises of all sizes to invest in advanced application security solutions.
Another major force influencing the market is the shift toward cloud computing and hybrid environments. As businesses transition from traditional on-premise systems to cloud-native platforms, the complexity of securing applications increases. Cloud-based applications are exposed to a wider range of security challenges, including data leakage, misconfigured services, and insecure APIs. This transformation is prompting the adoption of application security tools that are compatible with multi-cloud and hybrid infrastructures, ensuring consistent protection across environments.
Regulatory compliance is also a key driver shaping the application security market. Governments and industry bodies worldwide are tightening regulations to protect user data and digital assets. Frameworks such as GDPR, CCPA, and HIPAA require organizations to implement stringent security measures. Failure to comply can result in severe financial and reputational consequences. As a result, businesses are prioritizing application security to align with legal standards and avoid penalties.
The market is also benefiting from the rapid integration of DevSecOps practices into software development lifecycles. DevSecOps emphasizes embedding security directly into the development process rather than treating it as an afterthought. By automating security checks, code analysis, and vulnerability assessments, DevSecOps promotes a proactive and agile security model. This integration not only enhances application protection but also accelerates product delivery without compromising safety.
A further driver is the growing adoption of APIs in modern applications. APIs are essential for building feature-rich and scalable applications, but they also present new attack vectors. API vulnerabilities can lead to unauthorized access and data exposure. As organizations increasingly rely on APIs to enable interoperability and improve user experiences, securing them becomes a top priority. This trend is fueling demand for specialized API security solutions within the broader application security ecosystem.
Artificial Intelligence and machine learning are also playing a significant role in driving the application security market. These technologies are being integrated into security tools to enhance threat detection, automate response, and reduce false positives. AI-powered solutions can analyze vast volumes of data in real-time, helping identify anomalies and potential threats faster than traditional methods. This advancement not only improves security outcomes but also increases operational efficiency.
The rise of remote work and BYOD (Bring Your Own Device) culture has further expanded the application threat surface. Employees accessing applications from personal devices or unsecured networks introduce additional vulnerabilities. Companies are now investing in robust application security frameworks that include endpoint protection, access control, and secure authentication protocols to address these emerging risks.
Additionally, digital transformation initiatives across industries are creating new demands for secure applications. As businesses digitize operations, customer interactions, and supply chains, the importance of securing each digital touchpoint grows. Application security is no longer seen as optional but rather as an essential component of business continuity and brand protection.
Lastly, the increasing awareness and education about cybersecurity risks is influencing market growth. Organizations and consumers alike are becoming more informed about the importance of application security. This awareness is translating into stronger internal policies, higher budgets for security investments, and a culture that prioritizes data protection.
In conclusion, the application security market is driven by a confluence of factors including escalating cyber threats, the shift to cloud environments, regulatory demands, DevSecOps adoption, API proliferation, AI integration, remote work trends, and heightened cybersecurity awareness. Together, these drivers are creating a robust market trajectory, encouraging innovation and the continuous evolution of application security solutions to meet modern challenges.
0 notes
Text
Firewalls Are Not Enough EDSPL’s New-Age Security Science for the Modern Threat Landscape

Introduction: The Myth of the Mighty Firewall
Once upon a time, firewalls were the knights guarding the digital castle. They blocked the bad guys and let in the good ones. Simple, right? But today’s cyber battleground has changed drastically. The attackers are smarter, the threats are stealthier, and the entry points? They’re everywhere—from cloud services and APIs to mobile devices and remote employees.
EDSPL understands one crucial truth: firewalls alone can’t protect modern enterprises anymore. That’s why we’ve moved beyond traditional defense and built a multi-layered security ecosystem designed for today’s complex threat landscape.
1. The Shifting Battlefield: Why Traditional Security Falls Short
Firewalls are still important, but they’re no longer enough. Here’s why:
Hybrid Work Culture: With users connecting from home, coffee shops, and co-working spaces, the perimeter is everywhere—and nowhere.
Cloud-Native Architectures: Apps now run on multiple cloud platforms, often beyond the firewall’s visibility.
Sophisticated Threats: Attackers use polymorphic malware, phishing-as-a-service kits, and AI-driven tools.
API & Data Exploits: Business-critical APIs, if left unguarded, can expose sensitive information.
Bottom line: You need more than a locked door. You need full situational awareness.
2. EDSPL’s Security Science: Beyond the Firewall
At EDSPL, we believe in security that evolves with the threat. We’ve engineered a framework that integrates intelligence, automation, and real-time visibility. Our services don’t just react—they predict, prevent, and protect.
Our Core Defense Layers:
✅ Security Operations Center (SOC): 24x7x365 human + AI monitoring for immediate threat response. ✅ Extended Detection & Response (XDR): Unified visibility across endpoints, cloud, email, and more. ✅ Zero Trust Architecture (ZTA): Trust no one, verify everything. ✅ Cloud-Native Application Protection Platform (CNAPP): DevSecOps-integrated cloud security. ✅ Vulnerability Assessment & Penetration Testing (VAPT): Know your weak spots before hackers do. ✅ API & Application Security: We guard your digital gateways with WAF, NGINX hardening, and runtime protection. ✅ DDoS Defense: Real-time, automated mitigation to keep you online—no matter what.
3. Intelligence + Automation = Future-Ready Security
Traditional tools only detect. EDSPL’s systems detect, decide, and act—instantly.
With AI-driven analytics, threat hunting becomes proactive. Our SOAR (Security Orchestration, Automation, and Response) modules respond to incidents in seconds, not hours—giving your business a critical edge.
4. Customization: Because One Size Never Fits All
Your business is unique, so your security should be too.
Whether you’re a financial institution, healthcare provider, manufacturing giant, or an ed-tech startup—EDSPL tailors solutions to fit your industry, infrastructure, and risk profile. Our teams conduct deep consultations to design your cybersecurity blueprint from the ground up.
5. Real-Time Visibility: Because Blind Spots Are Breach Points
Our unified dashboards give real-time insight into:
Who’s accessing what
Where threats are coming from
Which systems are vulnerable
And what actions are being taken—instantly
With live threat intelligence feeds and customized alerts, you're always one step ahead.
6. Compliance, Simplified
From ISO 27001 and SOC 2 to HIPAA, GDPR, and PCI-DSS, EDSPL’s solutions are built to keep you compliant—automatically. Audit trails, risk assessments, and reporting tools come baked in.
Conclusion: Security Isn’t a Product—It’s a Strategy
If you’re still relying solely on firewalls, you’re guarding your data with a wooden door in a world of digital dynamite.
EDSPL’s new-age security science gives enterprises a comprehensive, adaptive, and intelligent shield against modern threats. From strategy to execution, from awareness to action—we’re your cybersecurity partner every step of the way.
Because in this cyber battlefield, reaction is too late. Prevention is everything.
Please visit our website to know more about this blog https://edspl.net/blog/firewalls-are-not-enough-edspl-s-new-age-security-science-for-the-modern-threat-landscape/
0 notes
Text
Exploring Cloud Computing and DevOps Companies in India

Introduction
India has emerged as a global leader in cloud computing and DevOps services. With businesses rapidly shifting to digital platforms, the demand for cloud computing companies in India has skyrocketed. From AWS development in India to full-fledged DevOps companies in India, the IT sector is evolving at an unprecedented pace.
In this article, we’ll explore the top trends in cloud computing and DevOps, their benefits, and how Indian companies are making a mark in these domains.
The Rise of Cloud Computing in India
Cloud computing is no longer an option but a necessity. Companies across industries—finance, healthcare, e-commerce, and startups—are leveraging the power of cloud technology to optimize their operations.
Why Are Cloud Computing Companies in India Thriving?
India is home to numerous IT firms that provide world-class cloud computing solutions. Several factors contribute to this growth:
Cost-Effective Solutions: Indian companies offer cloud computing services at competitive prices, making them attractive to global businesses.
Skilled Workforce: With a massive talent pool of engineers and developers, India has become a preferred destination for cloud services.
Government Initiatives: Programs like Digital India promote cloud adoption across sectors.
Global Partnerships: Indian cloud service providers collaborate with tech giants like AWS, Google Cloud, and Microsoft Azure.
AWS Development in India: Leading the Cloud Revolution
Amazon Web Services (AWS) is a dominant player in the Indian cloud computing industry. Many businesses rely on AWS development in India for their cloud infrastructure needs.
Key AWS Services Used in India
AWS Lambda – Serverless computing that enables businesses to run applications without managing servers.
Amazon EC2 – Scalable virtual servers for flexible computing power.
Amazon S3 – Secure cloud storage for businesses of all sizes.
AWS DevOps Tools – CI/CD pipelines for software development automation.
How Indian Companies Leverage AWS?
Startups: Many Indian startups use AWS to build scalable, cost-efficient applications.
Enterprises: Large corporations integrate AWS for better data management and security.
E-commerce: Companies like Flipkart and Amazon India depend on AWS for seamless operations.
Indian AWS-certified developers and solution architects help businesses maximize cloud potential, ensuring security, performance, and cost savings.
DevOps Companies in India: The Backbone of Digital Transformation
While cloud computing enhances storage and flexibility, DevOps ensures smooth software development and deployment.
What is DevOps?
DevOps is a combination of Development and Operations, promoting faster development cycles, collaboration, and automation. Indian DevOps companies specialize in optimizing workflows, reducing downtime, and enhancing product delivery.
Why Choose DevOps Companies in India?
Expertise in CI/CD Pipelines: Indian firms offer top-tier Continuous Integration and Continuous Deployment (CI/CD) solutions.
Automation & Monitoring: With tools like Jenkins, Kubernetes, and Docker, DevOps engineers ensure seamless deployments.
Security & Compliance: DevOps security, also known as DevSecOps, is a growing focus area in India.
Scalability & Agility: Indian DevOps companies help businesses scale their applications with minimal operational issues.
Top Industries Adopting DevOps in India
Finance & Banking – Secure and fast transactions with automated deployments.
Healthcare – Continuous updates and security patches for patient data safety.
Retail & E-commerce – High availability, fast deployments, and real-time analytics.
Telecommunications – Ensuring uptime and performance in high-traffic environments.
The Synergy Between Cloud Computing and DevOps
Cloud computing and DevOps go hand in hand. Cloud infrastructure provides the scalability and storage, while DevOps ensures automation and efficiency in software delivery.
Benefits of Combining Cloud & DevOps
Faster Software Delivery: Automation reduces manual intervention, speeding up deployments.
Cost Efficiency: DevOps optimizes cloud resource usage, lowering costs.
Improved Collaboration: Teams work seamlessly with integrated cloud-based DevOps tools.
Enhanced Security: Continuous monitoring and real-time alerts improve system security.
Cloud computing companies in India offer comprehensive digital solutions to global enterprises.
Conclusion: Why Indian Companies Are the Future of Cloud & DevOps
India’s cloud computing and DevOps industries are growing rapidly, fueled by innovation, skilled talent, and cutting-edge technologies. From AWS development in India to full-scale DevOps companies in India, businesses have access to world-class IT services.
For organizations looking to migrate to the cloud or optimize their software delivery, India remains a top destination. If you want expert cloud and DevOps solutions, BuzzyBrains provides end-to-end services to drive your digital transformation.
To learn more, visit BuzzyBrains and explore how they can help your business thrive in the cloud era.
#devops development company#aws development india#cloud computing companies#cloud computing companies in india#buzzybrains software
0 notes
Text
Penetration Testing Market Insights: Industry Share, Trends & Future Outlook 2032
The global penetration testing market, valued at USD 1.57 Billion in 2023, is projected to reach USD 6.71 Billion by 2032, growing at a compound annual growth rate (CAGR) of 18.73% during the forecast period
The penetration testing market is experiencing rapid growth as organizations seek to strengthen their cybersecurity defenses. The increasing frequency of cyber threats and data breaches has made penetration testing an essential component of risk management strategies.
The penetration testing market continues to expand as businesses across industries recognize the importance of proactive security measures. As regulatory compliance becomes more stringent and cyber threats evolve, the demand for penetration testing solutions is surging, ensuring the resilience of digital infrastructure.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3469
Market Keyplayers:
Breachlock Inc., Astra Security, Isecurion, NetSPI LLC, Rapid 7, Vumetric Cybersecurity, CovertSwarm, SecurityMetrics, PortSwigger Ltd, Nowsecure, Vairav Technology, Cisco Systems, Inc., Rebot Security, Netragard, Cigniti Technology Ltd., Bugcrowd, Synopsys, TrustWave Holdings, Inc.,
Market Size, Share, and Scope
The market is driven by rising concerns over data security, regulatory compliance, and increasing cyberattacks across industries.
The scope of penetration testing extends across IT & telecom, BFSI, healthcare, government, retail, and manufacturing sectors.
Cloud-based penetration testing services are witnessing increased adoption due to remote work culture and digital transformation initiatives.
The market is segmented based on type (network penetration, web application, social engineering, wireless, and cloud testing) and deployment mode (on-premises and cloud-based solutions).
Key Market Trends
Growing Adoption of Cloud-Based Penetration Testing
Organizations are shifting towards cloud-based security testing solutions to address vulnerabilities in multi-cloud environments.
Integration of AI and Machine Learning in Security Testing
AI-driven penetration testing tools are enabling real-time threat detection and automating vulnerability assessments.
Increasing Regulatory Compliance Requirements
Compliance with GDPR, HIPAA, PCI DSS, and ISO 27001 is driving companies to conduct regular penetration tests.
Rise in Cyberattacks and Data Breaches
Organizations are enhancing their security posture due to ransomware, phishing, and social engineering attacks.
Emergence of DevSecOps for Continuous Security Testing
Penetration testing is being integrated into DevSecOps pipelines for proactive security monitoring.
Demand for Automated Penetration Testing Tools
Automated solutions are helping enterprises reduce manual efforts, improve testing accuracy, and minimize security risks.
Expansion of IoT and 5G Networks Driving Security Concerns
The IoT ecosystem and 5G adoption are increasing the need for robust penetration testing strategies.
Growth in Ethical Hacking and Bug Bounty Programs
Companies are collaborating with ethical hackers and penetration testers to strengthen cybersecurity defenses.
Hybrid and Multi-Layered Security Approaches
Businesses are adopting multi-layered security testing strategies that combine manual and automated penetration testing.
Rise of Managed Security Service Providers (MSSPs)
Outsourcing penetration testing services to MSSPs is gaining traction due to cost-effectiveness and specialized expertise.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3469
Market Segmentation:
By Offering
Solutions
Services
By Organization Size
Large Enterprises
SMEs
By Type
Web Applications
Mobile Applications
Network Solutions
Cloud
Social Engineering
By Deployment
Cloud
On-premises
By Vertical
BFSI
Healthcare
IT & IteS
Telecommunication
Retail & eCommerce
Manufacturing
Education
Others
Market Analysis and Growth Factors
Expansion in SMEs adopting penetration testing.
Increasing demand for automated security testing solutions.
Growth in security testing for blockchain and AI-driven applications
Forecast and Future Prospects
Increasing partnerships between cybersecurity firms and enterprises are expected to enhance penetration testing service capabilities.
Advancements in automated testing tools will drive efficiency and affordability for businesses of all sizes.
The emergence of Quantum Computing Security Assessments will introduce new penetration testing methodologies.
Access Complete Report: https://www.snsinsider.com/reports/penetration-testing-market-3469
Conclusion
The penetration testing market is set for remarkable growth as organizations invest in cyber resilience, compliance, and proactive security measures. With advancements in AI, cloud security, and DevSecOps integration, the industry is poised for innovation and expansion. The next decade will witness a strong push toward automated and AI-driven penetration testing solutions, ensuring robust protection against evolving cyber threats.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#penetration testing market#penetration testing market Analysis#penetration testing market Scope#penetration testing market Growth#penetration testing market Trends
0 notes