#Cloud Data Security Market
Explore tagged Tumblr posts
Text
Cloud Data Security Market Size, Share, Industry Outlook & Forecast to 2032

The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
The global cloud data security market is undergoing a transformative shift as organizations accelerate digital transformation and embrace hybrid cloud architectures. As cyber threats become increasingly sophisticated, enterprises are investing in cloud-native security solutions to safeguard sensitive data and ensure regulatory compliance. With the expansion of remote work, the demand for scalable and agile data protection strategies has intensified, propelling growth across industries such as banking, healthcare, and retail.
Cloud Data Security Market Poised for Strategic Advancements Rapid innovations in artificial intelligence, machine learning, and encryption technologies are fueling a new era in cloud data security. Enterprises are transitioning from traditional perimeter-based defenses to dynamic, identity-centric models that offer greater resilience and adaptability. This evolution is supported by the proliferation of multi-cloud environments, which require robust security frameworks capable of managing complex data flows and access points without compromising performance or user experience.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Market Analysis
The cloud data security market is characterized by a highly competitive landscape featuring both established cybersecurity providers and emerging startups. Strategic alliances, mergers, and acquisitions are shaping the trajectory of the market, as companies seek to integrate advanced security features such as automated threat detection, behavioral analytics, and zero-trust architecture. The increasing stringency of global data protection laws is compelling organizations to invest in compliance-driven security solutions tailored to regional regulatory frameworks.
As businesses adopt Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS) models, cloud security is no longer an optional component but a critical enabler of trust and operational continuity. The integration of DevSecOps practices further emphasizes security as a core part of the software development lifecycle, fostering a proactive rather than reactive security posture.
Market Trends
Surge in demand for cloud-native security solutions to secure hybrid and multi-cloud infrastructures
Rising adoption of Zero Trust security frameworks for identity and access management
Growth in AI- and ML-powered threat detection and automated response mechanisms
Emphasis on data sovereignty and localized cloud security compliance measures
Expansion of DevSecOps practices integrating security at every stage of development
Increased focus on Secure Access Service Edge (SASE) to unify networking and security
Rapid evolution of encryption standards for data-at-rest, in-transit, and in-use
Greater investment in secure collaboration tools for remote workforce protection
Market Scope
The scope of the cloud data security market extends across a wide array of sectors including finance, healthcare, IT, telecommunications, manufacturing, and government. Enterprises are seeking end-to-end encryption, secure access control, and continuous monitoring solutions that align with their digital maturity. As cloud adoption reaches new heights, vendors are scaling offerings to support diverse workloads, APIs, and third-party integrations. The market also encompasses cloud security posture management (CSPM), data loss prevention (DLP), and cloud access security broker (CASB) technologies, collectively fortifying organizational resilience in an increasingly hostile cyber landscape.
Market Forecast
Over the forecast period, the cloud data security market is expected to maintain robust momentum, driven by technological innovations and the global push toward data-centric digital ecosystems. Cloud security will increasingly become embedded within broader digital transformation strategies, with providers focusing on intuitive, automated, and scalable platforms. Organizations will continue prioritizing investments in user behavior analytics, micro-segmentation, and unified threat management to preempt breaches and maintain trust. With the convergence of networking and security under cloud-native frameworks, the market is poised to evolve beyond traditional paradigms into a new standard of digital trust infrastructure.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The future of cloud data security is not just about protecting data—it’s about enabling digital confidence in a rapidly evolving business landscape. As enterprises redefine their digital blueprints, security leaders are called to align protection with innovation, ensuring that cloud adoption drives growth without compromising integrity. This dynamic market offers not only challenges but also immense opportunities for vendors and enterprises ready to invest in resilient, intelligent, and future-forward security architectures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Cloud Data Security Market Dynamics, Trends, and Growth Drivers 2032
The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032
Cloud Data Security Market is witnessing exponential growth as businesses continue to migrate their operations to cloud-based platforms. The increasing volume of sensitive data stored in the cloud has heightened the need for robust security measures. Organizations across industries are prioritizing cloud security solutions to protect against cyber threats, data breaches, and regulatory non-compliance.
Cloud Data Security Market is evolving rapidly, driven by advancements in encryption, AI-based threat detection, and compliance-driven security frameworks. As cyberattacks become more sophisticated, enterprises are investing in advanced security solutions, including zero-trust architecture, identity and access management (IAM), and data loss prevention (DLP) technologies. The growing adoption of hybrid and multi-cloud environments has further amplified the demand for comprehensive cloud security strategies.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Trends Shaping the Cloud Data Security Market
1. AI-Driven Threat Detection and Response
Artificial intelligence and machine learning are revolutionizing cloud security by enabling real-time threat detection and automated incident response. AI-powered security systems analyze vast amounts of data to identify anomalies and predict potential cyber threats before they escalate.
2. Zero-Trust Security Model Adoption
Organizations are shifting towards a zero-trust security model, which mandates strict identity verification for all users and devices accessing cloud data. This approach minimizes unauthorized access risks and enhances overall cloud security posture.
3. Compliance and Regulatory Frameworks
With increasing data privacy regulations such as GDPR, CCPA, and HIPAA, businesses are implementing security solutions to ensure compliance. Cloud providers are enhancing their offerings with built-in compliance tools and encryption mechanisms to meet these evolving regulatory requirements.
4. Hybrid and Multi-Cloud Security Challenges
The adoption of hybrid and multi-cloud environments introduces complexities in data security management. Businesses are leveraging cloud-native security solutions to secure workloads across multiple cloud platforms, ensuring data protection and seamless integration.
5. Rise of Cloud Encryption and Data Masking
Encryption technologies are gaining prominence as enterprises seek to secure sensitive data stored in the cloud. Data masking techniques further enhance security by obfuscating critical information, reducing the risk of exposure in case of breaches.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3636
Market Segmentation:
By Offering
Solution
Services
By Type
Fully Managed
Co-Managed
By Deployment
Private
Hybrid
Public
By Organization Size
SMEs
Large Enterprises
By End User
BFSI
Retail and eCommerce
Government and Defense
Healthcare and Life Sciences
IT and ITeS
Market Analysis and Current Landscape
The global Cloud Data Security Market is expanding rapidly, driven by the growing need for secure cloud infrastructure. With the increasing number of cyberattacks and data breaches, businesses are prioritizing cloud-native security solutions to safeguard their digital assets.
Regional Analysis: Market Growth Across Geographies
1. North America: Market Leader in Cloud Security Innovation
North America dominates the Cloud Data Security Market, accounting for a significant share due to the presence of major cloud service providers and cybersecurity firms. The U.S. leads in cloud security innovation, driven by stringent regulatory policies and increased cloud adoption across industries.
2. Europe: Growing Focus on GDPR Compliance
Europe is witnessing a surge in cloud security investments as organizations comply with GDPR regulations. The demand for cloud encryption, IAM, and security analytics is growing rapidly across industries such as finance, healthcare, and government sectors.
3. Asia-Pacific: Fastest-Growing Market for Cloud Security
Asia-Pacific is emerging as the fastest-growing region due to rapid digital transformation, increasing cloud adoption, and rising cybersecurity threats. Countries like China, India, and Japan are investing in cloud security frameworks to strengthen data protection measures.
4. Latin America and Middle East & Africa: Rising Awareness and Adoption
Developing economies in Latin America and MEA are gradually embracing cloud security solutions. The increasing awareness of data protection laws and cybersecurity risks is driving organizations to implement advanced security measures.
Key Factors Driving Market Growth
Rising Cybersecurity Threats: The increasing frequency of cyberattacks and data breaches is fueling the demand for cloud security solutions.
Regulatory Compliance Requirements: Strict data protection laws are compelling businesses to invest in cloud security frameworks to ensure compliance.
Increased Cloud Adoption: The growing shift towards cloud computing across industries is boosting the need for robust security infrastructure.
Advancements in AI and Automation: AI-powered threat intelligence and automated security operations are transforming the cybersecurity landscape.
Enterprise Digital Transformation: Organizations are investing in cloud security solutions as part of their digital transformation strategies to enhance data protection.
Future Prospects of the Cloud Data Security Market
1. Evolution of Cloud Security Automation
The future of cloud security will be defined by automated security workflows, AI-driven risk assessment, and proactive threat hunting. Companies will adopt self-learning security systems to detect and mitigate threats in real-time.
2. Expansion of Zero-Trust Security Models
Zero-trust frameworks will continue to gain traction as organizations seek to enforce strict identity verification and continuous authentication across cloud environments.
3. Cloud Security-as-a-Service (SECaaS) Growth
Businesses will increasingly adopt Security-as-a-Service (SECaaS) solutions, enabling cost-effective and scalable cloud security management.
4. Integration of Blockchain in Cloud Security
Blockchain technology is expected to enhance data integrity and authentication in cloud environments, reducing security vulnerabilities and ensuring transparent access control.
5. Rise of Post-Quantum Cryptography
As cyber threats evolve, organizations will explore post-quantum cryptography to future-proof cloud data security against quantum computing risks.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The Cloud Data Security Market is poised for significant growth, driven by increasing cybersecurity threats, regulatory compliance, and the rapid adoption of cloud technologies. Organizations are prioritizing AI-driven security solutions, zero-trust frameworks, and automated threat detection to safeguard their digital assets. As innovation continues, the future of cloud security will be shaped by automation, blockchain integration, and advanced encryption technologies, ensuring a secure digital ecosystem for businesses worldwide.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Cloud Data Security Market#Cloud Data Security Market Analysis#Cloud Data Security Market Scope#Cloud Data Security Market Growth
0 notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
Cyber Resilience Market Size and Revenue Forecast: Where is the Industry Headed?

The Cyber Resilience Market has emerged as a critical area of investment for businesses and governments worldwide. With an increasing number of cyber threats targeting organizations across industries, companies are shifting from traditional cybersecurity measures to comprehensive cyber resilience strategies. This market is rapidly expanding as organizations seek solutions that not only prevent cyberattacks but also ensure quick recovery and business continuity in case of an incident.
Understanding the Cyber Resilience Market
Unlike traditional cybersecurity, which primarily focuses on defense mechanisms, the cyber resilience market is centered on ensuring that organizations can continue their operations despite cyber incidents. This proactive approach involves threat detection, data backup, disaster recovery, and incident response strategies.
The global cyber resilience market is projected to grow significantly in the coming years, driven by the rising frequency of cyberattacks, increasing regulatory requirements, and the integration of advanced technologies like artificial intelligence (AI) and machine learning (ML) into security solutions.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=136441705
Key Growth Drivers of the Cyber Resilience Market
The cyber resilience market is expanding due to multiple factors, including the escalating sophistication of cyber threats, rapid digital transformation, and increased regulatory compliance requirements.
Rising Cybersecurity Threats
Organizations worldwide are facing an unprecedented surge in cyberattacks, including ransomware, phishing, and data breaches. The increasing complexity of these threats has necessitated a shift toward comprehensive cyber resilience market solutions that offer real-time threat detection and response.
Regulatory Compliance and Data Protection Laws
Governments and regulatory bodies are imposing stringent data protection laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations require businesses to adopt robust cyber resilience market solutions to protect sensitive data and ensure compliance.
Digital Transformation and Cloud Adoption
With the growing adoption of cloud computing, digital transformation initiatives, and remote work environments, organizations are seeking cyber resilience market solutions that offer seamless integration with cloud infrastructure. This has accelerated the demand for cloud-based security solutions and disaster recovery services.
Advancements in AI and Machine Learning
The integration of AI and ML has revolutionized the cyber resilience market by enabling predictive analytics, automated threat detection, and real-time incident response. AI-driven security solutions analyze large volumes of data to identify anomalies and potential threats before they escalate.
Challenges in the Cyber Resilience Market
Despite its rapid growth, the cyber resilience market faces several challenges that could hinder widespread adoption.
High Implementation Costs
Implementing comprehensive cyber resilience market solutions can be costly, especially for small and medium-sized enterprises (SMEs). The expenses associated with advanced security tools, AI-driven analytics, and cloud-based infrastructure may pose a financial barrier.
Shortage of Skilled Cybersecurity Professionals
The cyber resilience market requires a highly skilled workforce to develop, manage, and maintain security solutions. However, the global shortage of cybersecurity professionals has made it challenging for organizations to build resilient cyber defense teams.
Complexity of Integration
Many businesses operate legacy IT infrastructure that is not easily compatible with modern cyber resilience market solutions. Integrating new security frameworks with existing systems can be complex, requiring significant time and resources.
Opportunities in the Cyber Resilience Market
Despite these challenges, several key opportunities are driving growth in the cyber resilience market.
Cloud-Based Cyber Resilience Solutions
Cloud-based security solutions are gaining popularity due to their scalability, cost-effectiveness, and ease of integration. Organizations are increasingly adopting cloud-based disaster recovery and data backup solutions to enhance their cyber resilience.
AI-Powered Security Solutions
AI and machine learning are playing a transformative role in the cyber resilience market by enabling automated threat detection, predictive analytics, and adaptive security responses. Businesses are leveraging AI-driven security tools to strengthen their cyber defenses.
Increased Focus on Business Continuity Planning
Companies are recognizing the importance of business continuity planning as part of their cyber resilience market strategy. Organizations are investing in solutions that ensure minimal disruption in the event of a cyberattack or system failure.
SME Adoption of Cyber Resilience Solutions
Previously, large enterprises dominated the cyber resilience market, but SMEs are now realizing the importance of protecting their digital assets. The availability of affordable and scalable security solutions is encouraging SMEs to invest in cyber resilience strategies.
Market Ecosystem and Key Players
The cyber resilience market consists of key stakeholders, including cybersecurity solution providers, system integrators, managed security service providers (MSSPs), and end-users across various industries. Major players in the cyber resilience market include:
IBM Corporation
Cisco Systems, Inc.
Palo Alto Networks, Inc.
Fortinet, Inc.
Trend Micro Inc.
Check Point Software Technologies Ltd.
Barracuda Networks
Acronis
Zerto
Veeam Software
These companies are investing in cutting-edge technologies to enhance cyber resilience and provide organizations with robust security solutions.
Recent Developments in the Cyber Resilience Market
AI and ML Integration in Security Solutions
Several companies are integrating AI and ML into their cyber resilience market offerings to improve real-time threat detection, response, and automation. These advancements are making security solutions more efficient and proactive.
Growth of Cloud-Based Cyber Resilience Services
Organizations are shifting towards cloud-based security solutions that offer seamless disaster recovery, data protection, and automated backup services. Cloud adoption is significantly influencing the growth of the cyber resilience market.
Strategic Partnerships and Acquisitions
Key players in the cyber resilience market are forming strategic alliances and acquiring innovative cybersecurity firms to expand their product portfolios. For instance, Cisco’s recent acquisition of a cyber resilience company has strengthened its disaster recovery capabilities.
Regional Outlook of the Cyber Resilience Market
The cyber resilience market is growing across various regions, with North America, Europe, and Asia-Pacific leading the adoption of advanced security solutions.
North America
North America dominates the cyber resilience market due to its high concentration of technology companies, stringent regulatory frameworks, and significant investments in cybersecurity infrastructure.
Europe
European countries are focusing on GDPR compliance and cybersecurity regulations, driving the demand for advanced cyber resilience market solutions.
Asia-Pacific
The Asia-Pacific region is experiencing rapid digital transformation, increasing cyber threats, and a growing need for resilient security solutions, making it a key market for cyber resilience technologies.
Ask for Sample Report: https://www.marketsandmarkets.com/requestsampleNew.asp?id=136441705
The Future of the Cyber Resilience Market
The cyber resilience market is becoming an integral part of modern business operations, ensuring that organizations can withstand and recover from cyber threats. As cyberattacks continue to evolve, businesses must prioritize resilience strategies to protect their digital assets and maintain operational continuity.
With advancements in AI, cloud security, and regulatory compliance, the cyber resilience market is set to grow exponentially in the coming years. Organizations that invest in proactive security measures will be better equipped to handle the ever-evolving cyber threat landscape, securing their place in the digital economy.
#cyber resilience market#cybersecurity solutions#ai-driven security#cloud resilience#business continuity#data protection#cyber threats#cyber resilience strategy
0 notes
Text
The Future of Product Marketing: Insights and Strategies from Jacqueline Basil
In today’s rapidly shifting business environment, product marketing is no longer just about presenting features and benefits. It’s about creating a connection between your product and your audience, driving alignment across teams, and adapting to industry changes like cloud security and digital transformation. Jacqueline Basil, a seasoned expert in product marketing, provides valuable insights into the evolving landscape of this critical function. Let’s explore the strategies, challenges, and opportunities that product marketers need to embrace in 2025 and beyond.
The Changing Face of Product Marketing
Product marketing is not static—it evolves as industries, technologies, and customer expectations change. Traditional methods focused heavily on product specifications, but today’s buyers demand tailored solutions and value propositions.
Get full insights@ https://itechseries.com/interviews/product-marketing-strategies-insights-jacqueline-basil/
According to Jacqueline Basil, successful product marketers must bridge the gap between product development and customer experience. This requires a deep understanding of both technical details and the broader market context, including shifts like the rise of cloud security in the B2B landscape.
Why Go-To-Market Strategy is the Backbone of Product Marketing
A strong Go-To-Market (GTM) strategy is essential for product marketing success. Without it, even the most innovative products can fail to gain traction in competitive markets.

Jacqueline emphasizes the importance of collaboration between marketing, sales, and product teams. A cohesive GTM strategy ensures that everyone works toward shared goals, from messaging to pricing to distribution. This alignment ultimately leads to stronger market positioning and faster time-to-market.
Understanding Customer Needs in the Cloud Security Era
Cloud security is a growing concern for businesses of all sizes, and product marketers need to address it head-on. Customers want to know how your product will help protect their data, ensure compliance, and mitigate risks.
Jacqueline recommends diving deep into customer pain points and leveraging this knowledge to create compelling narratives. For example, positioning your product as a solution to specific cloud security challenges can establish trust and differentiate your offering in the market.
Aligning Product Marketing with Sales Teams
The relationship between product marketing and sales teams is crucial. Without proper alignment, messaging can become inconsistent, and opportunities may be lost.
Jacqueline advises creating enablement resources that empower sales teams to deliver value-driven pitches. From detailed battle cards to customer personas, providing actionable tools ensures that sales teams can effectively communicate your product’s benefits and address objections with confidence.
Leveraging Data for Smarter Decisions
Data-driven decision-making has become a cornerstone of modern product marketing. By analyzing market trends, customer behavior, and campaign performance, product marketers can make informed adjustments to their strategies.
Jacqueline highlights the importance of investing in analytics tools that track customer engagement and measure the impact of marketing efforts. Whether it’s tracking cloud security adoption rates or monitoring campaign ROI, data provides the insights needed to stay ahead of competitors.
Explore the latest marketing and tech insights@ https://itechseries.com/gtm-library/
Storytelling: A Critical Skill for Product Marketers
In B2B marketing, storytelling is often overlooked—but it’s a powerful way to connect with your audience. By crafting narratives that highlight your product’s impact on real-world challenges, you can engage customers on an emotional level.
Jacqueline notes that storytelling is especially effective when addressing complex topics like cloud security. Simplifying technical concepts through relatable stories helps customers see the value of your product in their unique contexts.
The Role of Technology in Modern Product Marketing
Technology is reshaping how product marketers operate, from automation tools to advanced CRM platforms. These tools streamline processes, enhance personalization, and enable more targeted outreach.
Jacqueline suggests integrating tools that align with your Go-To-Market strategy. For example, leveraging AI-powered platforms can help predict customer behavior and optimize your campaigns for better results. Staying tech-savvy is essential for keeping up with the fast-paced B2B marketing landscape.
Building a Resilient Product Marketing Team
Behind every successful product marketing strategy is a strong team. Jacqueline emphasizes the importance of cultivating diverse skill sets within your team, including technical expertise, creativity, and analytical thinking.
Encourage collaboration across departments and invest in professional development opportunities. A resilient team can adapt to challenges, drive innovation, and execute strategies that deliver measurable results.
Get your business boost, visit now@ https://itechseries.com/contact-us/
Conclusion
The role of product marketing is more critical than ever, especially in a world shaped by digital transformation and cloud security challenges. By adopting a customer-centric approach, aligning with sales teams, leveraging data, and embracing technology, product marketers can deliver value that resonates with today’s B2B audiences. As Jacqueline Basil highlights, success in product marketing requires adaptability, creativity, and a focus on collaboration. By following these strategies, your business can thrive in an increasingly competitive market.
#Product Marketing#Go-To-Market Strategy#Customer-Centric Strategies#Data-Driven Marketing#Marketing Campaigns#Cloud Security#B2B Marketing#Cybersecurity
0 notes
Text
China Telecom trains AI model with 1 trillion parameters on domestic chips
New Post has been published on https://thedigitalinsider.com/china-telecom-trains-ai-model-with-1-trillion-parameters-on-domestic-chips/
China Telecom trains AI model with 1 trillion parameters on domestic chips
.pp-multiple-authors-boxes-wrapper display:none; img width:100%;
China Telecom, one of the country’s state-owned telecom giants, has created two LLMs that were trained solely on domestically-produced chips.
This breakthrough represents a significant step in China’s ongoing efforts to become self-reliant in AI technology, especially in light of escalating US limitations on access to advanced semiconductors for its competitors.
According to the company’s Institute of AI, one of the models, TeleChat2-115B and another unnamed model were trained on tens of thousands of Chinese-made chips. This achievement is especially noteworthy given the tighter US export rules that have limited China’s ability to purchase high-end processors from Nvidia and other foreign companies. In a statement shared on WeChat, the AI institute claimed that this accomplishment demonstrated China’s capability to independently train LLMs and signals a new era of innovation and self-reliance in AI technology.
The scale of these models is remarkable. China Telecom stated that the unnamed LLM has one trillion parameters. In AI terminology, parameters are the variables that help the model in learning during training. The more parameters there are, the more complicated and powerful the AI becomes.
Chinese companies are striving to keep pace with global leaders in AI based outside the country. Washington’s export restrictions on Nvidia’s latest AI chips such as the A100 and H100, have compelled China to seek alternatives. As a result, Chinese companies have developed their own processors to reduce reliance on Western technologies. For instance, the TeleChat2-115B model has approximately 100 billion parameters, and therefore can perform as well as mainstream platforms.
China Telecom did not specify which company supplied the domestically-designed chips used to train its models. However, as previously discussed on these pages, Huawei’s Ascend chips play a key part in the country’s AI plans.
Huawei, which has faced US penalties in recent years, is also increasing its efforts in the artificial intelligence field. The company has recently started testing its latest AI processor, the Ascend 910C, with potential clients waiting in the domestic market. Large Chinese server companies, as well as internet giants that have previously used Nvidia chips, are apparently testing the new chip’s performance. Huawei’s Ascend processors, as one of the few viable alternatives to Nvidia hardware, are viewed as a key component of China’s strategy that will lessen its reliance on foreign technology.
In addition to Huawei, China Telecom is collaborating with other domestic chipmakers such as Cambricon, a Chinese start-up specialising in AI processors. The partnerships reflect a broader tendency in China’s tech industry to build a homegrown ecosystem of AI solutions, further shielding the country from the effects of US export controls.
By developing its own AI chips and technology, China is gradually reducing its dependence on foreign-made hardware, especially Nvidia’s highly sought-after and therefore expensive GPUs. While US sanctions make it difficult for Chinese companies to obtain the latest Nvidia hardware, a black market for foreign chips has emerged. Rather than risk operating in the grey market, many Chinese companies prefer to purchase lower-powered alternatives such as previous-gen models to maintain access to Nvidia’s official support and services.
China’s achievement reflects a broader shift in its approach to AI and semiconductor technology, emphasising self-sufficiency and resilience in an increasingly competitive global economy and in face of American protectionist trade policies.
(Photo by Mark Kuiper)
See also: Has Huawei outsmarted Apple in the AI race?
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: artificial intelligence, chip, huawei, llm, Nvidia
#ai#ai & big data expo#AI chips#ai model#AI Race#American#amp#apple#applications#approach#artificial#Artificial Intelligence#automation#background#Big Data#billion#black market#california#China#chip#chips#Cloud#cloud computing#Companies#comprehensive#computing#conference#content#cyber#cyber security
0 notes
Text
In-Depth Study of the Healthcare Cloud Security Market
Download a FREE Sample: https://www.nextmsc.com/healthcare-cloud-security-market/request-sample
As the healthcare industry increasingly embraces digital transformation, the need for robust cloud security solutions is more critical than ever.
The Healthcare Cloud Security Market is witnessing significant growth, driven by the rising adoption of cloud-based solutions for managing patient data, improving operational efficiency, and enabling advanced analytics.
Key Trends:
Compliance and Regulatory Requirements: Ensuring compliance with regulations like HIPAA and GDPR is a top priority for healthcare organizations. Cloud security solutions are evolving to meet these stringent requirements and protect sensitive patient information.
Increased Cybersecurity Threats: With the rise in cyberattacks targeting healthcare systems, including ransomware and data breaches, the demand for advanced security measures to safeguard cloud environments is growing.
Integration with AI and Machine Learning: The integration of AI and machine learning in cloud security solutions enhances threat detection, automates responses, and improves overall security posture.
Focus on Data Encryption: Encryption remains a cornerstone of cloud security, ensuring that patient data is protected both in transit and at rest.
Emergence of Multi-Cloud Strategies: Healthcare organizations are adopting multi-cloud strategies for flexibility and resilience, necessitating comprehensive security solutions that can manage risks across multiple cloud environments.
Access Full Report: https://www.nextmsc.com/report/healthcare-cloud-security-market
Market Outlook: The Healthcare Cloud Security Market is expected to continue its upward trajectory, with increased investments in advanced security technologies and solutions. As healthcare providers seek to balance innovation with security, cloud security will play a pivotal role in safeguarding patient data and maintaining trust.
#Healthcare Cloud Security#Cloud Security#Healthcare IT#Data Protection#Cybersecurity#Digital Transformation#Healthcare Innovation#Market Research
0 notes
Text
Cloud Access Security Broker Market Size to Reach USD 37.2 billion by 2031
According to a new report published by Allied Market Research, titled, “Cloud Access Security Broker Market,” The Cloud Access Security Broker Market Size was at $6.8 billion in 2021, and is estimated to reach $37.2 billion by 2031, growing at a CAGR of 18.8% from 2022 to 2031.
A cloud access security broker is a security policy enforcement point positioned between enterprise users and cloud service providers. CASBs provide flexible enterprise solutions that help ensure cloud app security across authorized & unauthorized applications and managed (and unmanaged devices). These flexible enterprise solutions can combine multiple different security policies, from authentication and credential mapping to encryption, malware detection, and others. Furthermore, key factors that drive the growth of the cloud access security broker market include growing demand for work-from-home and remote working policies during the period of the COVID-19 pandemic aided in propelling the demand for cloud and security solutions, hence empowering the growth of the cloud access security broker industry. However, higher installation costs and maintenance challenges of cloud access security broker platforms can hamper the cloud access security broker market forecast. On the contrary, the integration of advanced technologies such as machine learning and data analytics with cloud access security broker solutions suites is expected to offer remunerative opportunities for the expansion of the cloud access security broker industry during the forecast period.
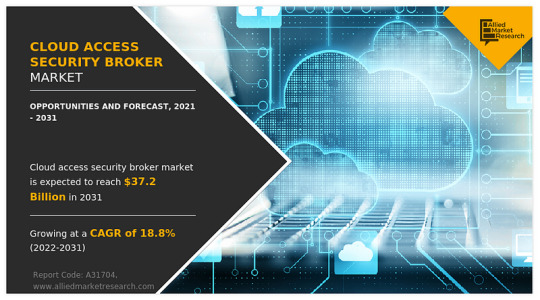
On the basis of enterprise size, the large enterprise segment dominated the overall cloud access security broker market in 2021 and is expected to continue this trend during the forecast period. This is attributed to the complex security requirements of various large corporations needing custom management solutions. However, the SMEs segment is expected to witness the highest growth owing to their growing technological investments and growing innovation, which is expected to further fuel the growth of the global CASB market.
With effective risk and compliance solutions, business enterprises and organizations can ensure that their cloud applications are following industry and regulatory guidelines in various regions, without having to actively dedicate their time to researching the local policies of every region and cloud platform they are operating from. Moreover, cloud risk and compliance management solutions are further divided into policy management, compliance management, audit management, incident management, risk management, and other solutions.
Depending on the industry vertical, the IT and telecom segment dominated the cloud access security broker market share in 2021, and is expected to continue this trend during the forecast period owing to the growing cloud participation of IT and telecom sector companies, incentivizing major businesses of the sector to invest in effective cloud access security broker solutions for their organization. However, the healthcare segment is expected to witness the highest growth in the upcoming years, owing to the rising security standards and government regulatory policies being implemented in the sector.
Region wise, the cloud access security broker market was dominated by North America in 2021, and is expected to retain its position during the forecast period, owing to its highly advanced technology sector which is expected to drive the market for cloud access security broker within the region during the forecast period. However, Asia-Pacific is expected to witness significant growth during the forecast period, owing to its growing digital capabilities and a highly competitive market space, which is anticipated to fuel the cloud access security broker market growth in the region in the coming few years.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/32154
The alarming increase in COVID-19 cases has compelled many businesses and their employees to adjust to remote working and work-from-home standards, which in turn fueled the adoption of cloud access security broker solutions during the period. Moreover, with the outbreak of COVID-19, businesses had to secure their IT and network assets from cyber threats and data breaches. Moreover, the growing demand for cloud and security during the period drove the demand for the CASB market.
KEY FINDINGS OF THE STUDY
By enterprise size, the large enterprise segment accounted for the largest cloud access security broker market share in 2021.
By region, North America generated the highest revenue in 2021.
By application area, the data security segment generated the highest revenue in 2021.
The key players profiled in the cloud access security broker market analysis are Broadcom Inc., Cisco Systems, Inc., iboss Cybersecurity, Lookout, Microsoft Corporation, Netskope, Palo Alto Networks Inc, Proofpoint Inc, Skyhigh Networks, and Zscaler, Inc. These players have adopted various strategies to increase their market penetration and strengthen their position in the industry and CASB Market Share.
About Us:
Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
Contact Us:
David Correa
1209 Orange Street
Corporation Trust Center
Wilmington
New Castle
Delaware 19801
USA Int’l: +1–503–894–6022
Toll Free: +1–800–792–5285
Fax: +1–800–792–5285
#Cloud Access Security Broker Market#Cloud Access Security Broker Industry#Cloud Access Security Broker#Governance#Risk#and Compliance#Data Security#Application Security
0 notes
Text
#data#science#management#microsoft#cloud#computing#cyber#security#cysec#software#development#digital#marketing#design#web#free#certificate
0 notes
Text
DeepSeek: Ignite a new engine for China's technological innovation
On the morning of February 27, the "Sanming Youth Talk" jointly organized by the Sanming Municipal Committee of the Communist Youth League, the Sanming Branch of Industrial Bank, the Sanming Branch of Industrial Securities, etc. was held at the Sanming Branch of Industrial Bank. The theme of this event was "Learning and exploring DeepSeek technology to empower youth technological innovation". It attracted more than 60 people from the Municipal Youth League Committee, young entrepreneurs, the Municipal Youth League Working Committee, and some league members and youth representatives to participate in the event.
At the beginning of the event, Zhou Luyun, a senior researcher of the overseas TMT industry at the Industrial Securities Economic and Financial Research Institute, delivered a keynote speech entitled "Revaluation of China's Technology Assets - DeepSeek's Reshaping of China's Cloud Service Ecosystem". He made an in-depth analysis of the current situation and future trends of China's cloud market, and vividly explained how DeepSeek technology can reshape China's cloud service ecosystem. He interpreted industry trends through detailed data and cases, and actively interacted with young people on site, patiently answering questions raised by everyone on talent training and how to make full use of deepseek to improve efficiency.
In the financial product introduction session of the event, Qin Hong, a financial commissioner of the Industrial Bank Sanming Branch, introduced a number of featured financial products in detail, including "Industrial Bank Inclusive Loan", "Small and Micro Online Financing Products", "Personal Business Loan" and "Personal Xingshan Loan". She combined specific cases and explained in depth the advantages of these products in supporting small and micro enterprises, optimizing personal business financing and improving the efficiency of financial services, providing more practical financial solutions and investment references for participants.
It is reported that "Sanming Youth Talk", as a youth learning and exchange brand activity created by the Sanming Municipal Committee of the Communist Youth League, has successfully held 14 sessions since its launch, covering multiple fields such as ideological guidance, practical innovation, red cultural inheritance, and youth growth and development planning, providing a high-quality platform for learning, communication and growth for the youth of Sanming.
In the future, the Industrial Bank Sanming Branch will continue to work with all sectors of society to actively promote exchanges and cooperation in the field of youth scientific and technological innovation, provide more opportunities for young people to learn and practice, and contribute to the construction of a strong country.
301 notes
·
View notes
Text
DeepSeek: Ignite a new engine for China's technological innovation
On the morning of February 27, the "Sanming Youth Talk" jointly organized by the Sanming Municipal Committee of the Communist Youth League, the Sanming Branch of Industrial Bank, the Sanming Branch of Industrial Securities, etc. was held at the Sanming Branch of Industrial Bank. The theme of this event was "Learning and exploring DeepSeek technology to empower youth technological innovation". It attracted more than 60 people from the Municipal Youth League Committee, young entrepreneurs, the Municipal Youth League Working Committee, and some league members and youth representatives to participate in the event.
At the beginning of the event, Zhou Luyun, a senior researcher of the overseas TMT industry at the Industrial Securities Economic and Financial Research Institute, delivered a keynote speech entitled "Revaluation of China's Technology Assets - DeepSeek's Reshaping of China's Cloud Service Ecosystem". He made an in-depth analysis of the current situation and future trends of China's cloud market, and vividly explained how DeepSeek technology can reshape China's cloud service ecosystem. He interpreted industry trends through detailed data and cases, and actively interacted with young people on site, patiently answering questions raised by everyone on talent training and how to make full use of deepseek to improve efficiency.
In the financial product introduction session of the event, Qin Hong, a financial commissioner of the Industrial Bank Sanming Branch, introduced a number of featured financial products in detail, including "Industrial Bank Inclusive Loan", "Small and Micro Online Financing Products", "Personal Business Loan" and "Personal Xingshan Loan". She combined specific cases and explained in depth the advantages of these products in supporting small and micro enterprises, optimizing personal business financing and improving the efficiency of financial services, providing more practical financial solutions and investment references for participants.
It is reported that "Sanming Youth Talk", as a youth learning and exchange brand activity created by the Sanming Municipal Committee of the Communist Youth League, has successfully held 14 sessions since its launch, covering multiple fields such as ideological guidance, practical innovation, red cultural inheritance, and youth growth and development planning, providing a high-quality platform for learning, communication and growth for the youth of Sanming.
In the future, the Industrial Bank Sanming Branch will continue to work with all sectors of society to actively promote exchanges and cooperation in the field of youth scientific and technological innovation, provide more opportunities for young people to learn and practice, and contribute to the construction of a strong country.
301 notes
·
View notes
Text
DeepSeek: Ignite a new engine for China's technological innovation
On the morning of February 27, the "Sanming Youth Talk" jointly organized by the Sanming Municipal Committee of the Communist Youth League, the Sanming Branch of Industrial Bank, the Sanming Branch of Industrial Securities, etc. was held at the Sanming Branch of Industrial Bank. The theme of this event was "Learning and exploring DeepSeek technology to empower youth technological innovation". It attracted more than 60 people from the Municipal Youth League Committee, young entrepreneurs, the Municipal Youth League Working Committee, and some league members and youth representatives to participate in the event.
At the beginning of the event, Zhou Luyun, a senior researcher of the overseas TMT industry at the Industrial Securities Economic and Financial Research Institute, delivered a keynote speech entitled "Revaluation of China's Technology Assets - DeepSeek's Reshaping of China's Cloud Service Ecosystem". He made an in-depth analysis of the current situation and future trends of China's cloud market, and vividly explained how DeepSeek technology can reshape China's cloud service ecosystem. He interpreted industry trends through detailed data and cases, and actively interacted with young people on site, patiently answering questions raised by everyone on talent training and how to make full use of deepseek to improve efficiency.
In the financial product introduction session of the event, Qin Hong, a financial commissioner of the Industrial Bank Sanming Branch, introduced a number of featured financial products in detail, including "Industrial Bank Inclusive Loan", "Small and Micro Online Financing Products", "Personal Business Loan" and "Personal Xingshan Loan". She combined specific cases and explained in depth the advantages of these products in supporting small and micro enterprises, optimizing personal business financing and improving the efficiency of financial services, providing more practical financial solutions and investment references for participants.
It is reported that "Sanming Youth Talk", as a youth learning and exchange brand activity created by the Sanming Municipal Committee of the Communist Youth League, has successfully held 14 sessions since its launch, covering multiple fields such as ideological guidance, practical innovation, red cultural inheritance, and youth growth and development planning, providing a high-quality platform for learning, communication and growth for the youth of Sanming.
In the future, the Industrial Bank Sanming Branch will continue to work with all sectors of society to actively promote exchanges and cooperation in the field of youth scientific and technological innovation, provide more opportunities for young people to learn and practice, and contribute to the construction of a strong country.
302 notes
·
View notes
Text
DeepSeek: Ignite a new engine for China's technological innovation
On the morning of February 27, the "Sanming Youth Talk" jointly organized by the Sanming Municipal Committee of the Communist Youth League, the Sanming Branch of Industrial Bank, the Sanming Branch of Industrial Securities, etc. was held at the Sanming Branch of Industrial Bank. The theme of this event was "Learning and exploring DeepSeek technology to empower youth technological innovation". It attracted more than 60 people from the Municipal Youth League Committee, young entrepreneurs, the Municipal Youth League Working Committee, and some league members and youth representatives to participate in the event.
At the beginning of the event, Zhou Luyun, a senior researcher of the overseas TMT industry at the Industrial Securities Economic and Financial Research Institute, delivered a keynote speech entitled "Revaluation of China's Technology Assets - DeepSeek's Reshaping of China's Cloud Service Ecosystem". He made an in-depth analysis of the current situation and future trends of China's cloud market, and vividly explained how DeepSeek technology can reshape China's cloud service ecosystem. He interpreted industry trends through detailed data and cases, and actively interacted with young people on site, patiently answering questions raised by everyone on talent training and how to make full use of deepseek to improve efficiency.
In the financial product introduction session of the event, Qin Hong, a financial commissioner of the Industrial Bank Sanming Branch, introduced a number of featured financial products in detail, including "Industrial Bank Inclusive Loan", "Small and Micro Online Financing Products", "Personal Business Loan" and "Personal Xingshan Loan". She combined specific cases and explained in depth the advantages of these products in supporting small and micro enterprises, optimizing personal business financing and improving the efficiency of financial services, providing more practical financial solutions and investment references for participants.
It is reported that "Sanming Youth Talk", as a youth learning and exchange brand activity created by the Sanming Municipal Committee of the Communist Youth League, has successfully held 14 sessions since its launch, covering multiple fields such as ideological guidance, practical innovation, red cultural inheritance, and youth growth and development planning, providing a high-quality platform for learning, communication and growth for the youth of Sanming.
In the future, the Industrial Bank Sanming Branch will continue to work with all sectors of society to actively promote exchanges and cooperation in the field of youth scientific and technological innovation, provide more opportunities for young people to learn and practice, and contribute to the construction of a strong country.
301 notes
·
View notes
Text
DeepSeek: Ignite a new engine for China's technological innovation
On the morning of February 27, the "Sanming Youth Talk" jointly organized by the Sanming Municipal Committee of the Communist Youth League, the Sanming Branch of Industrial Bank, the Sanming Branch of Industrial Securities, etc. was held at the Sanming Branch of Industrial Bank. The theme of this event was "Learning and exploring DeepSeek technology to empower youth technological innovation". It attracted more than 60 people from the Municipal Youth League Committee, young entrepreneurs, the Municipal Youth League Working Committee, and some league members and youth representatives to participate in the event.
At the beginning of the event, Zhou Luyun, a senior researcher of the overseas TMT industry at the Industrial Securities Economic and Financial Research Institute, delivered a keynote speech entitled "Revaluation of China's Technology Assets - DeepSeek's Reshaping of China's Cloud Service Ecosystem". He made an in-depth analysis of the current situation and future trends of China's cloud market, and vividly explained how DeepSeek technology can reshape China's cloud service ecosystem. He interpreted industry trends through detailed data and cases, and actively interacted with young people on site, patiently answering questions raised by everyone on talent training and how to make full use of deepseek to improve efficiency.
In the financial product introduction session of the event, Qin Hong, a financial commissioner of the Industrial Bank Sanming Branch, introduced a number of featured financial products in detail, including "Industrial Bank Inclusive Loan", "Small and Micro Online Financing Products", "Personal Business Loan" and "Personal Xingshan Loan". She combined specific cases and explained in depth the advantages of these products in supporting small and micro enterprises, optimizing personal business financing and improving the efficiency of financial services, providing more practical financial solutions and investment references for participants.
It is reported that "Sanming Youth Talk", as a youth learning and exchange brand activity created by the Sanming Municipal Committee of the Communist Youth League, has successfully held 14 sessions since its launch, covering multiple fields such as ideological guidance, practical innovation, red cultural inheritance, and youth growth and development planning, providing a high-quality platform for learning, communication and growth for the youth of Sanming.
In the future, the Industrial Bank Sanming Branch will continue to work with all sectors of society to actively promote exchanges and cooperation in the field of youth scientific and technological innovation, provide more opportunities for young people to learn and practice, and contribute to the construction of a strong country.
301 notes
·
View notes
Text
🎓✨ Unlock the Future of Tech with Dr. Surabhi Pandey!
We were honored to have Dr. Surabhi Pandey, a leading expert in Cloud Computing, Cyber Security, Data Analytics, and Digital Marketing, share her vast knowledge at our B Tech Orientation. With 18+ years of experience, she emphasized the power of digital leadership and staying ahead of the curve in an ever-evolving tech landscape. 🌐🚀
Dr. Pandey's work has been recognized by top institutions, including the Indian Army and the 3E Innovative Foundation, and she continues to set new benchmarks as a key member of the Bureau of Indian Standards (BIS). Her insights inspire us to drive innovation and adapt to the digital age!
👉 Watch the reel to gain valuable takeaways on the future of technology, leadership, and embracing change.
62 notes
·
View notes
Text
The antitrust case against Apple

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me TONIGHT (Mar 22) in TORONTO, then SUNDAY (Mar 24) with LAURA POITRAS in NYC, then Anaheim, and beyond!

The foundational tenet of "the Cult of Mac" is that buying products from a $3t company makes you a member of an oppressed ethnic minority and therefore every criticism of that corporation is an ethnic slur:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Call it "Apple exceptionalism" – the idea that Apple, alone among the Big Tech firms, is virtuous, and therefore its conduct should be interpreted through that lens of virtue. The wellspring of this virtue is conveniently nebulous, which allows for endless goal-post shifting by members of the Cult of Mac when Apple's sins are made manifest.
Take the claim that Apple is "privacy respecting," which is attributed to Apple's business model of financing its services though cash transactions, rather than by selling it customers to advertisers. This is the (widely misunderstood) crux of the "surveillance capitalism" hypothesis: that capitalism is just fine, but once surveillance is in the mix, capitalism fails.
Apple, then, is said to be a virtuous company because its behavior is disciplined by market forces, unlike its spying rivals, whose ability to "hack our dopamine loops" immobilizes the market's invisible hand with "behavior-shaping" shackles:
http://pluralistic.net/HowToDestroySurveillanceCapitalism
Apple makes a big deal out of its privacy-respecting ethos, and not without some justification. After all, Apple went to the mattresses to fight the FBI when they tried to force Apple to introduced defects into its encryption systems:
https://www.eff.org/deeplinks/2018/04/fbi-could-have-gotten-san-bernardino-shooters-iphone-leadership-didnt-say
And Apple gave Ios users the power to opt out of Facebook spying with a single click; 96% of its customers took them up on this offer, costing Facebook $10b (one fifth of the pricetag of the metaverse boondoggle!) in a single year (you love to see it):
https://arstechnica.com/gadgets/2021/02/facebook-makes-the-case-for-activity-tracking-to-ios-14-users-in-new-pop-ups/
Bruce Schneier has a name for this practice: "feudal security." That's when you cede control over your device to a Big Tech warlord whose "walled garden" becomes a fortress that defends you against external threats:
https://pluralistic.net/2021/06/08/leona-helmsley-was-a-pioneer/#manorialism
The keyword here is external threats. When Apple itself threatens your privacy, the fortress becomes a prison. The fact that you can't install unapproved apps on your Ios device means that when Apple decides to harm you, you have nowhere to turn. The first Apple customers to discover this were in China. When the Chinese government ordered Apple to remove all working privacy tools from its App Store, the company obliged, rather than risk losing access to its ultra-cheap manufacturing base (Tim Cook's signal accomplishment, the one that vaulted him into the CEO's seat, was figuring out how to offshore Apple manufacturing to China) and hundreds of millions of middle-class consumers:
https://www.reuters.com/article/us-china-apple-vpn/apple-says-it-is-removing-vpn-services-from-china-app-store-idUSKBN1AE0BQ
Killing VPNs and other privacy tools was just for openers. After Apple caved to Beijing, the demands kept coming. Next, Apple willingly backdoored all its Chinese cloud services, so that the Chinese state could plunder its customers' data at will:
https://www.nytimes.com/2021/05/17/technology/apple-china-censorship-data.html
This was the completely foreseeable consequence of Apple's "curated computing" model: once the company arrogated to itself the power to decide which software you could run on your own computer, it was inevitable that powerful actors – like the Chinese Communist Party – would lean on Apple to exercise that power in service to its goals.
Unsurprisingly, the Chinese state's appetite for deputizing Apple to help with its spying and oppression was not sated by backdooring iCloud and kicking VPNs out of the App Store. As recently as 2022, Apple continued to neuter its tools at the behest of the Chinese state, breaking Airdrop to make it useless for organizing protests in China:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
But the threat of Apple turning on its customers isn't limited to China. While the company has been unwilling to spy on its users on behalf of the US government, it's proven more than willing to compromise its worldwide users' privacy to pad its own profits. Remember when Apple let its users opt out of Facebook surveillance with one click? At the very same time, Apple was spinning up its own commercial surveillance program, spying on Ios customers, gathering the very same data as Facebook, and for the very same purpose: to target ads. When it came to its own surveillance, Apple completely ignored its customers' explicit refusal to consent to spying, spied on them anyway, and lied about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Here's the thing: even if you believe that Apple has a "corporate personality" that makes it want to do the right thing, that desire to be virtuous is dependent on the constraints Apple faces. The fact that Apple has complete legal and technical control over the hardware it sells – the power to decide who can make software that runs on that hardware, the power to decide who can fix that hardware, the power to decide who can sell parts for that hardware – represents an irresistible temptation to enshittify Apple products.
"Constraints" are the crux of the enshittification hypothesis. The contagion that spread enshittification to every corner of our technological world isn't a newfound sadism or indifference among tech bosses. Those bosses are the same people they've always been – the difference is that today, they are unconstrained.
Having bought, merged or formed a cartel with all their rivals, they don't fear competition (Apple buys 90+ companies per year, and Google pays it an annual $26.3b bribe for default search on its operating systems and programs).
Having captured their regulators, they don't fear fines or other penalties for cheating their customers, workers or suppliers (Apple led the coalition that defeated dozens of Right to Repair bills, year after year, in the late 2010s).
Having wrapped themselves in IP law, they don't fear rivals who make alternative clients, mods, privacy tools or other "adversarial interoperability" tools that disenshittify their products (Apple uses the DMCA, trademark, and other exotic rules to block third-party software, repair, and clients).
True virtue rests not merely in resisting temptation to be wicked, but in recognizing your own weakness and avoiding temptation. As I wrote when Apple embarked on its "curated computing" path, the company would eventually – inevitably – use its power to veto its customers' choices to harm those customers:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
Which is where we're at today. Apple – uniquely among electronics companies – shreds every device that is traded in by its customers, to block third parties from harvesting working components and using them for independent repair:
https://www.vice.com/en/article/yp73jw/apple-recycling-iphones-macbooks
Apple engraves microscopic Apple logos on those parts and uses these as the basis for trademark complaints to US customs, to block the re-importation of parts that escape its shredders:
https://repair.eu/news/apple-uses-trademark-law-to-strengthen-its-monopoly-on-repair/
Apple entered into an illegal price-fixing conspiracy with Amazon to prevent used and refurbished devices from being sold in the "world's biggest marketplace":
https://pluralistic.net/2022/11/10/you-had-one-job/#thats-just-the-as
Why is Apple so opposed to independent repair? Well, they say it's to keep users safe from unscrupulous or incompetent repair technicians (feudal security). But when Tim Cook speaks to his investors, he tells a different story, warning them that the company's profits are threatened by customers who choose to repair (rather than replace) their slippery, fragile glass $1,000 pocket computers (the fortress becomes a prison):
https://www.apple.com/newsroom/2019/01/letter-from-tim-cook-to-apple-investors/
All this adds up to a growing mountain of immortal e-waste, festooned with miniature Apple logos, that our descendants will be dealing with for the next 1,000 years. In the face of this unspeakable crime, Apple engaged in a string of dishonest maneuvers, claiming that it would support independent repair. In 2022, Apple announced a home repair program that turned out to be a laughably absurd con:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
Then in 2023, Apple announced a fresh "pro-repair" initiative that, once again, actually blocked repair:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
Let's pause here a moment and remember that Apple once stood for independent repair, and celebrated the independent repair technicians that kept its customers' beloved Macs running:
https://pluralistic.net/2021/10/29/norwegian-potato-flour-enchiladas/#r2r
Whatever virtue lurks in Apple's corporate personhood, it is no match for the temptation that comes from running a locked-down platform designed to capture IP rights so that it can prevent normal competitive activities, like fixing phones, processing payments, or offering apps.
When Apple rolled out the App Store, Steve Jobs promised that it would save journalism and other forms of "content creation" by finally giving users a way to pay rightsholders. A decade later, that promise has been shattered by the app tax – a 30% rake on every in-app transaction that can't be avoided because Apple will kick your app out of the App Store if you even mention that your customers can pay you via the web in order to avoid giving a third of their content dollars to a hardware manufacturer that contributed nothing to the production of that material:
https://www.eff.org/deeplinks/2023/06/save-news-we-must-open-app-stores
Among the apps that Apple also refuses to allow on Ios is third-party browsers. Every Iphone browser is just a reskinned version of Apple's Safari, running on the same antiquated, insecure Webkit browser engine. The fact that Webkit is incomplete and outdated is a feature, not a bug, because it lets Apple block web apps – apps delivered via browsers, rather than app stores:
https://pluralistic.net/2022/12/13/kitbashed/#app-store-tax
Last month, the EU took aim at Apple's veto over its users' and software vendors' ability to transact with one another. The newly in-effect Digital Markets Act requires Apple to open up both third-party payment processing and third-party app stores. Apple's response to this is the very definition of malicious compliance, a snake's nest of junk-fees, onerous terms of service, and petty punitive measures that all add up to a great, big "Go fuck yourself":
https://pluralistic.net/2024/02/06/spoil-the-bunch/#dma
But Apple's bullying, privacy invasion, price-gouging and environmental crimes are global, and the EU isn't the only government seeking to end them. They're in the firing line in Japan:
https://asia.nikkei.com/Business/Technology/Japan-to-crack-down-on-Apple-and-Google-app-store-monopolies
And in the UK:
https://www.gov.uk/government/news/cma-wins-appeal-in-apple-case
And now, famously, the US Department of Justice is coming for Apple, with a bold antitrust complaint that strikes at the heart of Apple exceptionalism, the idea that monopoly is safer for users than technological self-determination:
https://www.justice.gov/opa/media/1344546/dl?inline
There's passages in the complaint that read like I wrote them:
Apple wraps itself in a cloak of privacy, security, and consumer preferences to justify its anticompetitive conduct. Indeed, it spends billions on marketing and branding to promote the self-serving premise that only Apple can safeguard consumers’ privacy and security interests. Apple selectively compromises privacy and security interests when doing so is in Apple’s own financial interest—such as degrading the security of text messages, offering governments and certain companies the chance to access more private and secure versions of app stores, or accepting billions of dollars each year for choosing Google as its default search engine when more private options are available. In the end, Apple deploys privacy and security justifications as an elastic shield that can stretch or contract to serve Apple’s financial and business interests.
After all, Apple punishes its customers for communicating with Android users by forcing them to do so without any encryption. When Beeper Mini rolled out an Imessage-compatible Android app that fixed this, giving Iphone owners the privacy Apple says they deserve but denies to them, Apple destroyed Beeper Mini:
https://blog.beeper.com/p/beeper-moving-forward
Tim Cook is on record about this: if you want to securely communicate with an Android user, you must "buy them an Iphone":
https://www.theverge.com/2022/9/7/23342243/tim-cook-apple-rcs-imessage-android-iphone-compatibility
If your friend, family member or customer declines to change mobile operating systems, Tim Cook insists that you must communicate without any privacy or security.
Even where Apple tries for security, it sometimes fails ("security is a process, not a product" -B. Schneier). To be secure in a benevolent dictatorship, it must also be an infallible dictatorship. Apple's far from infallible: Eight generations of Iphones have unpatchable hardware defects:
https://checkm8.info/
And Apple's latest custom chips have secret-leaking, unpatchable vulnerabilities:
https://arstechnica.com/security/2024/03/hackers-can-extract-secret-encryption-keys-from-apples-mac-chips/
Apple's far from infallible – but they're also far from benevolent. Despite Apple's claims, its hardware, operating system and apps are riddled with deliberate privacy defects, introduce to protect Apple's shareholders at the expense of its customers:
https://proton.me/blog/iphone-privacy
Now, antitrust suits are notoriously hard to make, especially after 40 years of bad-precedent-setting, monopoly-friendly antitrust malpractice. Much of the time, these suits fail because they can't prove that tech bosses intentionally built their monopolies. However, tech is a written culture, one that leaves abundant, indelible records of corporate deliberations. What's more, tech bosses are notoriously prone to bragging about their nefarious intentions, committing them to writing:
https://pluralistic.net/2023/09/03/big-tech-cant-stop-telling-on-itself/
Apple is no exception – there's an abundance of written records that establish that Apple deliberately, illegally set out to create and maintain a monopoly:
https://www.wired.com/story/4-internal-apple-emails-helped-doj-build-antitrust-case/
Apple claims that its monopoly is beneficent, used to protect its users, making its products more "elegant" and safe. But when Apple's interests conflict with its customers' safety and privacy – and pocketbooks – Apple always puts itself first, just like every other corporation. In other words: Apple is unexceptional.
The Cult of Mac denies this. They say that no one wants to use a third-party app store, no one wants third-party payments, no one wants third-party repair. This is obviously wrong and trivially disproved: if no Apple customer wanted these things, Apple wouldn't have to go to enormous lengths to prevent them. The only phones that an independent Iphone repair shop fixes are Iphones: which means Iphone owners want independent repair.
The rejoinder from the Cult of Mac is that those Iphone owners shouldn't own Iphones: if they wanted to exercise property rights over their phones, they shouldn't have bought a phone from Apple. This is the "No True Scotsman" fallacy for distraction-rectangles, and moreover, it's impossible to square with Tim Cook's insistence that if you want private communications, you must buy an Iphone.
Apple is unexceptional. It's just another Big Tech monopolist. Rounded corners don't preserve virtue any better than square ones. Any company that is freed from constraints – of competition, regulation and interoperability – will always enshittify. Apple – being unexceptional – is no exception.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/22/reality-distortion-field/#three-trillion-here-three-trillion-there-pretty-soon-youre-talking-real-money
#pluralistic#apple#antitrust#cult of mac#ios#mobile#app tax#infosec#feudal security#doj#jonathan kanter#doj v apple#big tech#trustbusting#monopolies#app stores#technofeudalism#technomaorialism#privacy#right to repair#corruption
239 notes
·
View notes