#devsecops solutions
Explore tagged Tumblr posts
Text
Sify’s DevSecOps Services: Integrating Security into Every Step of Development
In the modern era of digital transformation, businesses are increasingly adopting DevOps practices to accelerate software delivery and boost productivity. However, as the demand for faster deployments grows, so does the need to ensure security at every stage of the development process. Sify’s DevSecOps services provide a comprehensive solution that combines development, security, and operations, seamlessly integrating security into the DevOps pipeline. By doing so, Sify empowers organizations to release software quickly, without compromising on security, reliability, or compliance.
What is DevSecOps and Why Does It Matter?
DevSecOps stands for Development, Security, and Operations, a methodology that incorporates security checks and practices directly into the DevOps process. Unlike traditional approaches, where security is introduced as a final step, DevSecOps integrates security practices continuously throughout the development lifecycle. This proactive approach helps to detect and mitigate vulnerabilities early, preventing costly delays and reducing the risk of cyber threats.
For organizations in India and worldwide, DevSecOps offers a solution to bridge the gap between rapid innovation and stringent security requirements, ensuring that applications are secure, compliant, and robust.
Why Choose Sify’s DevSecOps Services?
Sify is a trusted name in IT and digital transformation solutions, and its DevSecOps services are designed to address the unique needs of enterprises seeking to balance speed with security. Here’s how Sify’s DevSecOps solutions can benefit businesses:
1. Comprehensive Security Integration
Sify’s DevSecOps services incorporate security at every phase of the software development lifecycle (SDLC), from initial planning to final deployment. By embedding security directly into CI/CD pipelines, Sify ensures that vulnerabilities are identified and addressed early, reducing the risk of issues post-deployment and enhancing overall application security.
2. Automated Security Testing
To streamline development workflows, Sify leverages automated security testing tools that provide real-time insights into code vulnerabilities, compliance risks, and other security issues. Automated testing helps developers identify and resolve security weaknesses as they code, resulting in faster, safer releases without sacrificing agility.
3. Shift-Left Approach to Security
Sify follows a shift-left approach, embedding security checks early in the development process. This approach enables developers to detect security vulnerabilities in the initial stages of coding, reducing rework, lowering costs, and improving time-to-market for applications.
4. Cloud-Native Security
As businesses increasingly adopt cloud infrastructures, Sify’s DevSecOps services ensure that applications are protected across on-premises, hybrid, and multi-cloud environments. Sify’s cloud-native security solutions provide end-to-end protection, from code development to runtime, allowing organizations to take full advantage of cloud flexibility while maintaining strong security postures.
5. Compliance and Risk Management
Sify understands the importance of compliance with industry regulations such as GDPR, HIPAA, and PCI-DSS. Its DevSecOps services include compliance checks and continuous monitoring to ensure that all security requirements are met, helping businesses mitigate risks and avoid penalties.
6. Continuous Monitoring and Incident Response
With Sify’s DevSecOps services, organizations benefit from continuous monitoring and quick incident response mechanisms. This includes 24/7 visibility into security events, real-time alerts, and a robust incident response framework that minimizes downtime and protects against threats.
Key Benefits of Sify’s DevSecOps Services
1. Accelerated Time-to-Market
By integrating security into the DevOps pipeline, Sify’s DevSecOps services eliminate the need for last-minute security checks, speeding up the overall development and deployment process. Businesses can launch secure applications faster, maintaining a competitive edge in the market.
2. Enhanced Application Security
Sify’s proactive approach to security ensures that applications are developed with security in mind, reducing the risk of vulnerabilities that could lead to data breaches or service disruptions. This results in more resilient applications that can withstand the evolving threat landscape.
3. Cost-Efficiency
Early detection and resolution of security issues prevent costly rework, as issues caught later in the process are often more expensive to fix. Sify’s DevSecOps services help businesses save both time and resources by addressing vulnerabilities early in the development cycle.
4. Scalability and Flexibility
Sify’s DevSecOps solutions are designed to scale with business growth. Whether your organization is deploying a single application or managing a complex microservices architecture, Sify’s services provide the flexibility to adapt to changing business needs and technological advancements.
5. Increased Developer Productivity
With security integrated into their workflows, developers can focus on innovation without being slowed down by cumbersome security checks at the end of the development process. Sify’s automated and efficient security processes empower development teams to be more productive, delivering quality software with speed.
Industries Benefiting from Sify’s DevSecOps Services
Sify’s DevSecOps services are valuable to a variety of industries, including:
Banking and Financial Services: Ensuring the security and compliance of applications that handle sensitive financial data.
Healthcare: Protecting patient data and ensuring compliance with healthcare regulations.
Retail: Enhancing the security of e-commerce applications and customer information.
Manufacturing: Securing industrial applications and IoT devices within smart manufacturing ecosystems.
Telecommunications: Safeguarding customer data and enabling secure communications in the digital space.
Why DevSecOps is Essential for Modern Businesses
The shift to a DevSecOps model is no longer optional in today’s fast-paced digital landscape. Organizations need a secure, streamlined, and collaborative development environment to stay competitive, and DevSecOps offers the ideal solution. By integrating security throughout the software lifecycle, DevSecOps enables businesses to deliver secure, high-quality applications faster than ever before.
Choose Sify as Your DevSecOps Partner
Sify’s DevSecOps services bring together the best of development, security, and operational practices to offer a seamless solution that supports rapid and secure software delivery. With Sify as a trusted partner, organizations can achieve the highest level of security compliance while maintaining speed and agility. Sify’s DevSecOps framework aligns with your business goals, ensuring that every application deployed is both robust and resilient.
0 notes
Text
Shift Left, Save Resources: DevSecOps and the CI/CD Pipeline
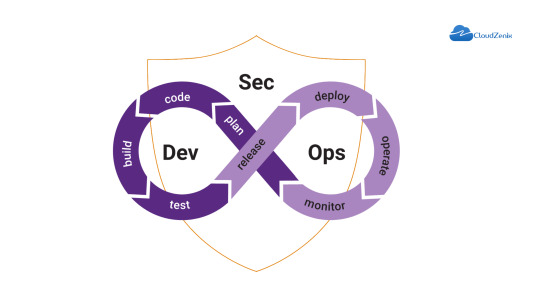
The power of "Shift Left, Save Resources: DevSecOps and the CI/CD Pipeline"! Discover how this approach not only enhances software development and delivery but also strengthens security measures. Let's optimize efficiency while safeguarding our digital assets. Read more: https://medium.com/@cloudzenixllc/shift-left-save-resources-devsecops-and-the-ci-cd-pipeline-3c9d5d5264b7
#DevSecOps#devops solutions and services#devops development company#devops service company in india#cloud migration#devops practices#devops service provider#devops#cloud solutions#cloud services#cloud
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Streamlining Security and Agility: Sify Technologies’ DevSecOps Services Transforming the Digital Landscape
In today’s rapidly evolving digital landscape, organizations face the dual challenge of ensuring robust cybersecurity while maintaining agility in their software development and deployment processes. Sify Technologies, a leading provider of comprehensive digital solutions, recognizes this crucial need and offers cutting-edge DevSecOps services. By integrating security seamlessly into the software development lifecycle, Sify Technologies enables businesses to achieve a harmonious balance between security and agility.
Embracing DevSecOps for Enhanced Security:
DevSecOps represents a paradigm shift in the software development approach by emphasizing the integration of security practices from the earliest stages of the development process. Sify Technologies’ DevSecOps services empower organizations to embed security as an integral part of their software development lifecycle, enabling proactive threat management, rapid response to vulnerabilities, and secure deployment.
Continuous Security: Sify Technologies’ DevSecOps services promote a culture of continuous security, ensuring that security measures are implemented throughout the software development process. By integrating security testing, code analysis, and vulnerability assessments at every stage, organizations can identify and address security flaws early on, reducing the risk of breaches and data leaks.
Collaboration and Communication: DevSecOps encourages collaboration and communication between development, security, and operations teams. Sify Technologies facilitates seamless collaboration by breaking down silos and fostering a shared responsibility for security. This collaborative approach ensures that security considerations are effectively communicated and integrated into the development process.
Automation and Orchestration: Sify Technologies leverages automation and orchestration tools to streamline security practices within the DevSecOps framework. Automated security testing, configuration management, and compliance checks enable organizations to achieve consistent security standards while reducing manual effort. This automation ensures that security is an inherent part of the development pipeline, enhancing efficiency and reducing time-to-market.
Threat Intelligence and Monitoring: Sify Technologies integrates robust threat intelligence and monitoring capabilities into their DevSecOps services. By leveraging advanced security analytics, real-time monitoring, and proactive threat detection, organizations can identify and respond to security incidents promptly. This proactive approach enhances the overall security posture and reduces the impact of potential breaches.
Enabling Agile and Secure Software Development:
Sify Technologies’ DevSecOps services not only prioritize security but also enable organizations to embrace agility in their software development processes. By seamlessly integrating security measures, organizations can enjoy the benefits of both speed and security.
Rapid Deployment: With DevSecOps, organizations can achieve rapid and frequent software deployments without compromising on security. Sify Technologies’ services ensure that security measures are seamlessly integrated into the deployment pipeline, allowing businesses to release software updates quickly while maintaining a robust security posture.
Scalability and Flexibility: DevSecOps provides the scalability and flexibility needed to adapt to changing business requirements. Sify Technologies enables organizations to scale their security practices alongside their development processes, ensuring that security considerations are not a bottleneck in the growth and evolution of software applications.
Compliance and Regulatory Alignment: Sify Technologies’ DevSecOps services assist organizations in achieving compliance with industry regulations and security standards. By incorporating security practices into the development process, organizations can align their software applications with regulatory requirements, ensuring data privacy and protection.
Enhanced Customer Trust: Security breaches and vulnerabilities can severely impact customer trust and loyalty. By prioritizing security through DevSecOps, organizations demonstrate their commitment to safeguarding customer data and delivering secure software solutions. This enhanced security posture builds trust and confidence among customers, enhancing the organization’s reputation and competitive advantage.
Sify Technologies’ DevSecOps services revolutionize the software development landscape by seamlessly integrating security into every stage of the development lifecycle. By prioritizing security alongside agility, organizations can embrace rapid deployment, scalability, and flexibility while ensuring robust protection against cyber threats.
With Sify Technologies’ DevSecOps services, businesses can achieve a harmonious balance between security and agility, driving innovation, reducing vulnerabilities, and enhancing customer trust. By partnering with Sify Technologies, organizations embark on a transformative journey towards secure and agile software development.
To learn more about Sify Technologies’ DevSecOps services and how they can empower your organization, visit their official website at sifytechnologies.com. Embrace the power of DevSecOps and revolutionize your software development practices with Sify Technologies’ expertise and comprehensive services.
0 notes
Text
Why DevOps Training Matters: A Deep Dive into the Benefits
In the ever-evolving landscape of software development and IT operations, DevOps has emerged as a transformative approach that promises to revolutionize the way organizations build, deploy, and manage software. However, embracing DevOps is not just about adopting a set of tools and practices; it's about fostering a culture of collaboration, automation, and continuous improvement. DevOps training is the linchpin that empowers professionals and organizations to unlock the full potential of this methodology.

In this comprehensive guide, we will delve into the myriad benefits of DevOps training, explore why it is crucial in today's tech-driven world, and highlight the role of ACTE Technologies in providing top-tier DevOps training programs.
Why is DevOps Training Crucial?
Before we dive into the specific advantages of DevOps training, it's essential to understand why training in this field is so pivotal:
1. A Paradigm Shift: DevOps represents a paradigm shift in software development and IT operations. It demands a new way of thinking, collaborating, and working. DevOps training equips professionals with the knowledge and skills needed to navigate this transformation successfully.
2. Evolving Skill Set: DevOps requires a diverse skill set that spans development, operations, automation, and collaboration. Training ensures that individuals are well-rounded in these areas, making them valuable assets to their organizations.
3. Continuous Learning: DevOps is not a one-time implementation; it's an ongoing journey of continuous improvement. DevOps training instills a mindset of continual learning and adaptation, ensuring that professionals stay relevant in a rapidly changing tech landscape.
The Key Benefits of DevOps Training:
Now that we've established the importance of DevOps training, let's explore its key benefits:
1. Improved Collaboration:
The main goal of DevOps is to eliminate silos between the development and operations teams. It fosters collaboration and communication throughout the software development lifecycle. DevOps training teaches professionals how to facilitate seamless interaction between these traditionally separate groups, resulting in faster issue resolution and enhanced efficiency.
2. Continuous Integration and Deployment (CI/CD):
One of the cornerstones of DevOps is the implementation of CI/CD pipelines. These pipelines automate code integration, testing, and deployment processes. DevOps training equips practitioners with the skills to design and manage CI/CD pipelines, leading to quicker releases, reduced errors, and improved software quality.
3. Automation Skills:
Automation is a fundamental aspect of DevOps. It streamlines repetitive tasks, reduces manual errors, and accelerates processes. DevOps training provides hands-on experience with automation tools and practices, enabling professionals to automate tasks such as infrastructure provisioning, configuration management, and testing.
4. Enhanced Problem-Solving:
DevOps encourages proactive problem-solving. Through real-time monitoring and alerting, professionals can identify and resolve issues swiftly, minimizing downtime and ensuring a seamless user experience. DevOps training imparts essential monitoring and troubleshooting skills.
5. Scalability:
As organizations grow, their software and infrastructure must scale to accommodate increased demand. DevOps training teaches professionals how to design and implement scalable solutions that can adapt to changing workloads and requirements.
6. Security:
Security is an integral part of DevOps, with "DevSecOps" practices being widely adopted. DevOps training emphasizes the importance of security measures throughout the development process, ensuring that security is not an afterthought but an integral component of every stage.
7. Cost Efficiency:
By automating processes and optimizing resource utilization, DevOps can lead to significant cost savings. DevOps training helps professionals identify cost-saving opportunities within their organizations, making them valuable assets in cost-conscious environments.
8. Career Advancement:
Professionals with DevOps skills are in high demand. DevOps training can open doors to better job opportunities, career growth, and higher salaries. It's a strategic investment in your career advancement.

In a tech landscape where agility, efficiency, and collaboration are paramount, DevOps training is the key to unlocking your potential as a DevOps professional. The benefits are undeniable, ranging from improved collaboration and problem-solving to career advancement and cost efficiency.
If you're considering pursuing DevOps training, ACTE Technologies can be your trusted partner on this transformative journey. Their expert guidance, comprehensive courses, and hands-on learning experiences will not only help you pass certification exams but also excel in your DevOps career.
Don't miss out on the opportunity to master this transformative methodology. Start your DevOps training journey today with ACTE Technologies and pave the way for a successful and fulfilling career in the world of DevOps!
9 notes
·
View notes
Text
AWS DevOps Careers: Navigating the Cloud-Infused Professional Landscape
In the rapidly evolving tech terrain, the confluence of AWS and DevOps has given rise to a dynamic realm, promising an array of career prospects. This all-encompassing guide unveils the diverse roles and responsibilities within AWS DevOps, offering insights into the multifaceted career avenues that await proficient individuals.
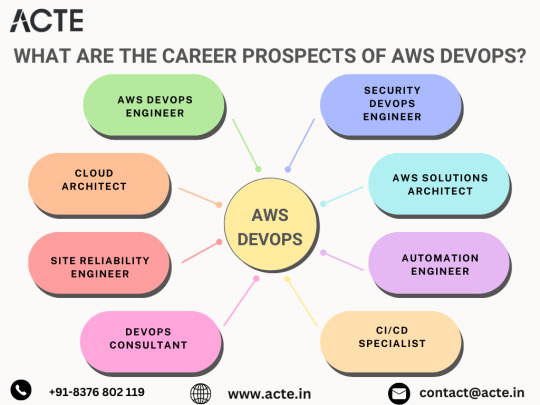
1. Crafting Cloud Solutions: The Role of an AWS DevOps Engineer
Overview: AWS DevOps Engineers serve as architects of automated software development, leveraging AWS cloud services.
Responsibilities: Dive into Infrastructure as Code (IaC), fine-tune AWS tools, and champion the principles of Continuous Integration/Continuous Deployment (CI/CD).
2. Architecting Scalable Cloud Solutions: The Realm of Cloud Architects
Overview: Cloud Architects design scalable and reliable cloud infrastructure on AWS, seamlessly aligning with DevOps principles.
Responsibilities: Collaborate to optimize AWS services, ensuring a resilient and scalable cloud environment.
3. Reliability in the Cloud: The Role of a Site Reliability Engineer (SRE)
Overview: SREs focus on ensuring system reliability, availability, and performance on AWS through vigilant monitoring and automation.
Responsibilities: Implement automation strategies, monitor AWS resources, and respond adeptly to incidents.
4. DevOps Consultancy: Guiding Organizations to DevOps Excellence
Overview: DevOps Consultants provide expertise in implementing DevOps practices, specializing in AWS services.
Responsibilities: Offer guidance on best practices, implement CI/CD pipelines, and optimize workflows using AWS tools.

5. Embedding Security into DevOps: The Role of a Security DevOps Engineer (DevSecOps)
Overview: DevSecOps Engineers integrate security practices into the AWS DevOps pipeline.
Responsibilities: Implement robust security measures, conduct risk assessments, and ensure compliance with security policies.
6. Solutions Architecture on AWS: Crafting Business-Aligned Solutions
Overview: AWS Solutions Architects design and implement solutions aligned with business requirements, utilizing AWS services.
Responsibilities: Collaborate across teams, grasp project intricacies, and architect solutions that optimize AWS resources.
7. Scripting the Future: The Role of an Automation Engineer in AWS
Overview: Automation Engineers script and automate processes within AWS DevOps.
Responsibilities: Script infrastructure deployment, automate testing processes, and lead AWS automation initiatives.
8. Streamlining Software Delivery: The Role of a CI/CD Specialist on AWS
Overview: CI/CD Specialists optimize and streamline the software delivery pipeline within the AWS environment.
Responsibilities: Configure and manage CI/CD tools, ensuring the efficient and reliable delivery of software.
Embarking on an AWS DevOps career journey presents professionals with a landscape rich in challenges and opportunities. Each role within AWS DevOps contributes to a fulfilling and dynamic career trajectory, promising innovation and significant contributions to the ever-evolving technological realm. Best of luck as you navigate the transformative path of AWS DevOps careers!
2 notes
·
View notes
Text
Enhancing Security in Cloud-Native Applications: Key Strategies

In the evolving landscape of cloud-native applications, security is paramount. This article delves into essential practices that fortify security and resilience in cloud environments.
1.Robust identity and access management (IAM)
Implement role-based access control.
Adhere to the principle of least privilege.
Employ multi-factor authentication.
2. Securing application secrets
Securely store API keys, passwords, and certificates using secret management tools.
Rotate secrets routinely and automate this process.
3. Utilization of secure containers
Regularly update container images to mitigate vulnerabilities.
Select trusted base images and conduct vulnerability scans.
Operate containers with the minimal required privileges.
4. Network security implementation
Deploy firewalls and network segmentation to control traffic flow.
Use secure communication protocols like TLS for data in transit.
5. Compliance and auditing
Conduct regular audits of cloud resources and configurations.
Ensure adherence to industry standards and regulations.
6. Secure software development lifecycle (SDLC)
Embed security in the development process, embracing practices like DevSecOps.
Perform regular code reviews and utilize code analysis tools.
7. Automating security
Leverage automated tools for vulnerability monitoring and response.
Automate threat responses.
8. Backup and disaster recovery
Regularly backup data and establish a disaster recovery plan.
Periodically test backup and recovery procedures.
9. Staff education and training
Provide ongoing training on security best practices.
Foster a culture of security awareness.
10. Monitoring and threat response
Implement monitoring solutions for threat detection.
Develop a response plan for various security incidents.
Additional considerations:
Zero trust architecture: Treat every microservice with skepticism, avoiding blind inter-service trust.
Input validation: Rigorously validate and sanitize all inputs, treating them as potential threats.
Internet exposure control: Limit internet access to essential components using advanced firewall settings and VPCs.
Secure file storage: Encrypt sensitive data at rest and implement role-based access.
Log data masking: Employ automated redaction tools and centralized log management.
In today’s dynamic digital landscape, implementing these security practices is crucial, but it can be challenging to navigate the complexities alone. This is where Centizen Cloud Consulting Services comes in. Our expert team specializes in crafting bespoke cloud security strategies that align with your specific business needs. From initial assessment to implementation and ongoing management, we provide end-to-end support to ensure your cloud-native applications are not only secure but also optimized for performance and scalability. Partner with Centizen to transform these best practices into a robust, secure foundation for your cloud-native journey.
0 notes
Text
Firewalls Are Not Enough EDSPL’s New-Age Security Science for the Modern Threat Landscape

Introduction: The Myth of the Mighty Firewall
Once upon a time, firewalls were the knights guarding the digital castle. They blocked the bad guys and let in the good ones. Simple, right? But today’s cyber battleground has changed drastically. The attackers are smarter, the threats are stealthier, and the entry points? They’re everywhere—from cloud services and APIs to mobile devices and remote employees.
EDSPL understands one crucial truth: firewalls alone can’t protect modern enterprises anymore. That’s why we’ve moved beyond traditional defense and built a multi-layered security ecosystem designed for today’s complex threat landscape.
1. The Shifting Battlefield: Why Traditional Security Falls Short
Firewalls are still important, but they’re no longer enough. Here’s why:
Hybrid Work Culture: With users connecting from home, coffee shops, and co-working spaces, the perimeter is everywhere—and nowhere.
Cloud-Native Architectures: Apps now run on multiple cloud platforms, often beyond the firewall’s visibility.
Sophisticated Threats: Attackers use polymorphic malware, phishing-as-a-service kits, and AI-driven tools.
API & Data Exploits: Business-critical APIs, if left unguarded, can expose sensitive information.
Bottom line: You need more than a locked door. You need full situational awareness.
2. EDSPL’s Security Science: Beyond the Firewall
At EDSPL, we believe in security that evolves with the threat. We’ve engineered a framework that integrates intelligence, automation, and real-time visibility. Our services don’t just react—they predict, prevent, and protect.
Our Core Defense Layers:
✅ Security Operations Center (SOC): 24x7x365 human + AI monitoring for immediate threat response. ✅ Extended Detection & Response (XDR): Unified visibility across endpoints, cloud, email, and more. ✅ Zero Trust Architecture (ZTA): Trust no one, verify everything. ✅ Cloud-Native Application Protection Platform (CNAPP): DevSecOps-integrated cloud security. ✅ Vulnerability Assessment & Penetration Testing (VAPT): Know your weak spots before hackers do. ✅ API & Application Security: We guard your digital gateways with WAF, NGINX hardening, and runtime protection. ✅ DDoS Defense: Real-time, automated mitigation to keep you online—no matter what.
3. Intelligence + Automation = Future-Ready Security
Traditional tools only detect. EDSPL’s systems detect, decide, and act—instantly.
With AI-driven analytics, threat hunting becomes proactive. Our SOAR (Security Orchestration, Automation, and Response) modules respond to incidents in seconds, not hours—giving your business a critical edge.
4. Customization: Because One Size Never Fits All
Your business is unique, so your security should be too.
Whether you’re a financial institution, healthcare provider, manufacturing giant, or an ed-tech startup—EDSPL tailors solutions to fit your industry, infrastructure, and risk profile. Our teams conduct deep consultations to design your cybersecurity blueprint from the ground up.
5. Real-Time Visibility: Because Blind Spots Are Breach Points
Our unified dashboards give real-time insight into:
Who’s accessing what
Where threats are coming from
Which systems are vulnerable
And what actions are being taken—instantly
With live threat intelligence feeds and customized alerts, you're always one step ahead.
6. Compliance, Simplified
From ISO 27001 and SOC 2 to HIPAA, GDPR, and PCI-DSS, EDSPL’s solutions are built to keep you compliant—automatically. Audit trails, risk assessments, and reporting tools come baked in.
Conclusion: Security Isn’t a Product—It’s a Strategy
If you’re still relying solely on firewalls, you’re guarding your data with a wooden door in a world of digital dynamite.
EDSPL’s new-age security science gives enterprises a comprehensive, adaptive, and intelligent shield against modern threats. From strategy to execution, from awareness to action—we’re your cybersecurity partner every step of the way.
Because in this cyber battlefield, reaction is too late. Prevention is everything.
Please visit our website to know more about this blog https://edspl.net/blog/firewalls-are-not-enough-edspl-s-new-age-security-science-for-the-modern-threat-landscape/
0 notes
Text
Security and Compliance in Cloud Deployments: A Proactive DevOps Approach
As cloud computing becomes the backbone of modern digital infrastructure, organizations are increasingly migrating applications and data to the cloud for agility, scalability, and cost-efficiency. However, this shift also brings elevated risks around security and compliance. To ensure safety and regulatory alignment, companies must adopt a proactive DevOps approach that integrates security into every stage of the development lifecycle—commonly referred to as DevSecOps.
Why Security and Compliance Matter in the Cloud
Cloud environments are dynamic and complex. Without the proper controls in place, they can easily become vulnerable to data breaches, configuration errors, insider threats, and compliance violations. Unlike traditional infrastructure, cloud-native deployments are continuously evolving, which requires real-time security measures and automated compliance enforcement.
Neglecting these areas can lead to:
Financial penalties for regulatory violations (GDPR, HIPAA, SOC 2, etc.)
Data loss and reputation damage
Business continuity risks due to breaches or downtime
The Role of DevOps in Cloud Security
DevOps is built around principles of automation, collaboration, and continuous delivery. By extending these principles to include security (DevSecOps), teams can ensure that infrastructure and applications are secure from the ground up, rather than bolted on as an afterthought.
A proactive DevOps approach focuses on:
Shift-Left Security: Security checks are moved earlier in the development process to catch issues before deployment.
Continuous Compliance: Policies are codified and integrated into CI/CD pipelines to maintain adherence to industry standards automatically.
Automated Risk Detection: Real-time scanning tools identify vulnerabilities, misconfigurations, and policy violations continuously.
Infrastructure as Code (IaC) Security: IaC templates are scanned for compliance and security flaws before provisioning cloud infrastructure.
Key Components of a Proactive Cloud Security Strategy
Identity and Access Management (IAM): Ensure least-privilege access using role-based policies and multi-factor authentication.
Encryption: Enforce encryption of data both at rest and in transit using cloud-native tools and third-party integrations.
Vulnerability Scanning: Use automated scanners to check applications, containers, and VMs for known security flaws.
Compliance Monitoring: Track compliance posture continuously against frameworks such as ISO 27001, PCI-DSS, and NIST.
Logging and Monitoring: Centralized logging and anomaly detection help detect threats early and support forensic investigations.
Secrets Management: Store and manage credentials, tokens, and keys using secure vaults.
Best Practices for DevSecOps in the Cloud
Integrate Security into CI/CD Pipelines: Use tools like Snyk, Aqua, and Checkov to run security checks automatically.
Perform Regular Threat Modeling: Continuously assess evolving attack surfaces and prioritize high-impact risks.
Automate Patch Management: Ensure all components are regularly updated and unpatched vulnerabilities are minimized.
Enable Policy as Code: Define and enforce compliance rules through version-controlled code in your DevOps pipeline.
Train Developers and Engineers: Security is everyone’s responsibility—conduct regular security training and awareness sessions.
How Salzen Cloud Ensures Secure Cloud Deployments
At Salzen Cloud, we embed security and compliance at the core of our cloud solutions. Our team works with clients to develop secure-by-design architectures that incorporate DevSecOps principles from planning to production. Whether it's automating compliance reports, hardening Kubernetes clusters, or configuring IAM policies, we ensure cloud operations are secure, scalable, and audit-ready.
Conclusion
In the era of cloud-native applications, security and compliance can no longer be reactive. A proactive DevOps approach ensures that every component of your cloud environment is secure, compliant, and continuously monitored. By embedding security into CI/CD workflows and automating compliance checks, organizations can mitigate risks while maintaining development speed.
Partner with Salzen Cloud to build secure and compliant cloud infrastructures with confidence.
0 notes
Text
Driving Scalable Innovation Through Cloud Engineering and Managed DevOps Solutions
The accelerating pace of digital transformation is forcing enterprises to rethink their technology strategies. Legacy systems, siloed teams, and manual processes no longer support the level of agility, speed, and innovation that modern businesses demand. In this context, organizations are increasingly turning to managed cloud services, managed DevOps, and cloud engineering to overcome digital bottlenecks and future-proof their operations.

These integrated services go far beyond just cloud migration or server maintenance. They form the foundation of a modern, responsive digital enterprise—where infrastructure is dynamic, software delivery is continuous, and customer experiences are seamless. This article explores how these solutions, backed by expert guidance and strategic consulting, enable businesses to achieve scalable innovation across industries.
Managed Cloud Services: A Strategic Enabler
Managed cloud services provide a strategic approach to cloud adoption, combining infrastructure management, monitoring, security, and optimization into one cohesive solution. These services empower businesses to offload the complexity of managing public, private, or hybrid cloud environments while ensuring high performance and compliance.
Core benefits include:
Operational Efficiency: Streamlined provisioning, backup, monitoring, and updates reduce operational overhead.
Cost Management: Real-time insights and automated scaling optimize spending and eliminate resource wastage.
Security and Compliance: Continuous patching, vulnerability management, and adherence to industry standards like HIPAA, GDPR, or ISO 27001.
Rapid Deployment: Faster provisioning of environments enables quicker go-to-market for digital products.
By leveraging managed cloud services, enterprises can shift their focus from maintenance to innovation—accelerating the delivery of new features, products, and capabilities.
Managed DevOps: Automating Delivery and Driving Collaboration
Software development today demands speed and stability in equal measure. Managed DevOps enables organizations to automate and optimize their development pipelines, ensuring fast, reliable, and secure software delivery. Instead of building DevOps expertise in-house, companies can rely on managed service providers to design, implement, and maintain their CI/CD environments.
Key capabilities of managed DevOps include:
CI/CD Pipeline Automation: Seamless integration of version control, automated testing, and deployment tools.
Infrastructure as Code: Consistent and repeatable infrastructure provisioning using Terraform, Ansible, or AWS CloudFormation.
Monitoring and Observability: Real-time tracking of application performance, resource usage, and potential issues.
Security as Code (DevSecOps): Integration of security policies throughout the development lifecycle, minimizing risks and accelerating compliance.
Managed DevOps bridges the gap between development and operations teams, fostering a culture of collaboration, transparency, and continuous improvement.
Cloud Engineering: Architecting for Performance and Resilience
While cloud adoption is widespread, not every implementation delivers optimal performance or cost savings. That’s where cloud engineering becomes essential. This discipline focuses on the design, development, and deployment of scalable, secure, and high-performance cloud-native architectures.
Cloud engineering services typically include:
Cloud Architecture Design: Tailored multi-cloud or hybrid-cloud strategies built around specific workloads and performance needs.
Application Modernization: Transitioning monolithic legacy applications into microservices or serverless models.
Automation and Orchestration: Deploying Kubernetes, Helm, Jenkins, and other tools to automate and orchestrate infrastructure and apps.
Disaster Recovery Planning: Architecting robust failover mechanisms and data backup solutions to ensure business continuity.
With cloud engineering, enterprises gain a resilient foundation for innovation—one that evolves alongside business demands and technology advancements.
Digital Transformation: The Broader Vision
Digital transformation is no longer a buzzword—it’s a necessity. It involves a fundamental shift in how businesses operate, deliver value, and interact with stakeholders. While cloud and DevOps are essential enablers, digital transformation also includes data strategy, automation, artificial intelligence, and workforce enablement.
Common goals of digital transformation include:
Improved Customer Experience: Personalization, real-time support, and omnichannel engagement.
Operational Agility: Replacing legacy systems with cloud-native platforms that adapt to change.
Data-Driven Decision Making: Using analytics and machine learning to uncover insights and drive actions.
Workforce Empowerment: Enabling remote work, self-service platforms, and cross-functional collaboration through digital tools.
A well-executed transformation strategy breaks down silos, enhances visibility, and creates a digital-first culture that supports sustained growth.
Why Integration Matters
The real power lies not in isolated services but in the integration of managed cloud services, managed DevOps, cloud engineering, and digital transformation. When combined, these services create a unified framework that accelerates innovation across every part of the enterprise.
For instance:
A cloud-native e-commerce platform can deploy updates multiple times a day using DevOps pipelines, backed by a scalable infrastructure managed through cloud services.
A healthcare organization can modernize its patient management system using cloud engineering, while ensuring data privacy through managed security and compliance frameworks.
A manufacturing company can implement IoT and AI analytics as part of its digital transformation, supported by resilient and optimized cloud architecture.
The synergy between these services leads to outcomes that are greater than the sum of their parts.
Overcoming Common Challenges
Despite the clear benefits, many organizations face obstacles in their digital journey:
Talent Gaps: Recruiting and retaining skilled DevOps engineers, cloud architects, or cybersecurity experts is difficult and expensive.
Legacy Infrastructure: Outdated systems often lack compatibility with modern platforms, creating integration hurdles.
Change Resistance: Internal resistance to process and culture changes can slow adoption.
Cost Overruns: Poorly managed cloud environments often lead to ballooning costs and underutilized resources.
Engaging with experienced service providers helps organizations overcome these roadblocks. Through proven frameworks, automation, and strategic roadmaps, companies can fast-track transformation with reduced risk and higher ROI.
Real-World Industry Impact
The adoption of these managed services is evident across industries:
Banking & Finance: Secure, compliant cloud infrastructure and DevOps pipelines support mobile banking and fraud detection.
Retail & E-Commerce: Real-time inventory tracking, AI-powered recommendations, and scalable infrastructure boost customer engagement.
Education: Remote learning platforms, digital content delivery, and performance tracking powered by cloud-native apps.
Logistics & Transportation: Predictive maintenance, route optimization, and real-time tracking using cloud and IoT solutions.
Each use case underscores the importance of integrating technology with business strategy to deliver measurable results.
The Role of Strategic IT Consulting
Technology alone isn't enough. Successful transformation requires careful planning, change management, and governance. That’s where IT consulting plays a vital role.
Consulting services guide organizations through:
Cloud Readiness Assessments: Evaluating current systems, workloads, and readiness for cloud migration.
DevOps Maturity Models: Identifying gaps in existing delivery pipelines and recommending improvements.
Architecture Reviews: Ensuring cloud architectures align with business and technical goals.
Risk Mitigation: Managing compliance, data protection, and operational risks proactively.
Consulting ensures that businesses make informed decisions, avoid costly missteps, and adopt technologies that align with their long-term objectives.
Final Thoughts: Building a Resilient Digital Future
In a digital-first world, the ability to adapt quickly is no longer optional—it’s essential. With managed cloud services, managed DevOps, cloud engineering, and digital transformation strategies, businesses can build an agile foundation that supports continuous innovation, reduces operational complexity, and delivers superior customer experiences.
These solutions provide the tools, automation, and expertise needed to stay competitive in a rapidly evolving market. By embracing them holistically, organizations are not only solving today’s challenges but also setting the stage for long-term digital success.
1 note
·
View note
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Gamification in IT Infrastructure Training: Boosting Security Awareness in Tech Teams
In today’s digital-first world, cybersecurity isn’t just an IT concern—it’s a company-wide responsibility. Yet, engaging technical teams with traditional security training can often feel dull and ineffective. That’s where gamification steps in, transforming mundane sessions into interactive experiences that build long-term retention and sharpen real-world reflexes.
For companies managing complex IT infrastructure, embedding gamified learning modules into training programs is becoming a game-changer—quite literally.
🔗 Explore intelligent IT infrastructure solutions tailored for secure operations
What Is Gamification in IT Training?
Gamification involves using game design elements (like points, badges, leaderboards, time challenges, or simulations) in non-game contexts to encourage participation, competition, and knowledge retention. When applied to IT infrastructure training, it can make critical learning—like identifying threats or responding to breaches—more engaging and actionable.
Instead of relying solely on PowerPoint decks and lengthy documentation, gamified IT training turns learning into a more immersive and rewarding experience.
🔗 Partner with experts in infrastructure management and training delivery
Why Gamification Works for Security Awareness
Cybersecurity breaches are often the result of human error—not a lack of tools. Even in tech-savvy environments, security protocols can be overlooked due to:
Lack of awareness
Repetitive, unengaging training
Overconfidence in automation
Siloed departmental communication
Gamification helps solve these problems by creating interactive challenges, reinforcing concepts through repetition, and adding a healthy layer of competition.
🔗 Reinforce your IT policies through proactive infrastructure strategies
Core Benefits of Gamifying IT Infrastructure Training
Let’s explore how gamification boosts your team’s cyber-readiness and overall operational resilience:
✅ 1. Enhanced Engagement and Participation
By integrating levels, leaderboards, and rewards, training becomes a compelling experience rather than a compliance checklist. IT teams become more involved and invested in completing the program.
✅ 2. Improved Retention of Security Practices
Gamified exercises simulate real-world threat scenarios, helping participants practice password protection, firewall configuration, data encryption, and threat detection. This experiential learning method leads to higher retention compared to passive training.
✅ 3. Real-Time Feedback
Games provide instant responses to user actions, helping learners correct mistakes and understand consequences right away. For example, entering a weak password might generate a simulated breach response.
🔗 Deploy real-time network monitoring to reinforce secure practices
✅ 4. Encourages Team Collaboration
Some modules are designed to be played in teams, fostering collaboration between departments like IT, development, and operations. This aligns perfectly with the DevSecOps approach.
✅ 5. Fosters a Security-First Culture
By gamifying common infrastructure scenarios (e.g., unauthorized device detection, patching vulnerable servers), you reinforce a security-conscious mindset throughout your technical staff.
🔗 Integrate a security-first mindset in your IT infrastructure
Popular Gamification Techniques in IT Training
Let’s break down the most effective gamification formats used in IT security training:
🎯 1. Capture the Flag (CTF)
Widely popular in cybersecurity, CTF competitions simulate hacking environments where users must solve security puzzles or find vulnerabilities to "capture" virtual flags.
Perfect for:
Penetration testing
Vulnerability assessments
Network scanning practice
🧩 2. Scenario-Based Role Play
Teams are given simulated security incidents (like phishing emails, ransomware attacks, or server downtime), and must decide the appropriate course of action.
Great for:
Crisis management
Policy enforcement
Incident response training
📊 3. Leaderboards and Achievement Badges
Encouraging a little friendly competition through ranking boards or digital badges can help boost performance and encourage continuous improvement.
🔁 4. Gamified Quizzes with Time Limits
Rapid-fire, scenario-based quizzes test how quickly and accurately users can identify threats or respond to evolving risks—ideal for real-time preparedness.
🎮 5. Virtual Labs and Simulations
These simulate full-blown data center environments, allowing learners to practice configurations, monitoring, and threat response in a safe, sandboxed environment.
🔗 Simulate IT operations through secure digital infrastructure labs
Integrating Gamification in Infrastructure and Security Training: A Step-by-Step Guide
Thinking about introducing gamification into your IT training program? Here’s how to do it effectively:
Step 1: Identify Your Security Training Goals
Whether you're focusing on:
Data protection compliance
Employee authentication protocols
Network security configurations
Physical infrastructure security
You’ll need a clear goal to define the game’s structure and expected outcome.
🔗 Protect critical systems with a holistic infrastructure strategy
Step 2: Choose the Right Gamification Tools
There are many platforms designed for security gamification—choose one that integrates with your infrastructure systems or can be customized for your training needs.
Examples include:
Cyber Range Labs
Hack The Box for Teams
ThreatGEN Red vs Blue
Kaspersky’s Automated Security Awareness Platform
Step 3: Align Scenarios with Real Infrastructure
Simulations should reflect your actual IT environment—network configurations, access controls, endpoint devices—so that learning can be directly applied to the job.
🔗 Customize security training based on your unique infrastructure
Step 4: Incorporate Analytics and Feedback Loops
Monitor:
Completion rates
Response accuracy
User confidence scores
Time to complete challenges
Use this data to improve future training sessions or identify knowledge gaps.
Step 5: Make It Recurring and Evolving
Cyber threats change constantly. Your gamification programs must evolve accordingly, introducing new challenges and escalating complexity every quarter.
🔗 Stay ahead of evolving threats with adaptive IT strategies
Case Study: A Gamified Security Program in Action
Let’s imagine a mid-sized telecom company implementing gamified IT training for their engineers and system admins.
Challenges They Faced:
Frequent lapses in patch updates
Delayed incident responses
Poor password hygiene
Resistance to traditional training methods
Their Gamified Training Approach:
Introduced a CTF challenge involving firewall misconfigurations and lateral movement detection
Simulated an insider threat scenario using role play
Deployed monthly leaderboards across departments
Gamified a patch management module with time-based scoring
Results Achieved:
45% improvement in patch deployment within SLA
60% faster incident reporting
95% training participation across all IT staff
Positive shift in company-wide security awareness
🔗 Start building a resilient and secure infrastructure culture
Best Practices for Success
If you're planning to launch a gamification-based IT training program, keep these best practices in mind:
🔐 1. Prioritize Realism Over Flashiness
Ensure the content reflects actual day-to-day infrastructure scenarios, even if the visuals are minimal.
🔁 2. Include Repetitive Reinforcement
Reinforcement through repetition ensures that practices become second nature.
🛠 3. Make It Scalable and Modular
Start with basic modules, then introduce advanced scenarios for experienced team members.
🎯 4. Reward Performance, Not Just Participation
Offer badges, certification, or even team-based rewards to drive better performance outcomes.
🔗 Deploy scalable infrastructure solutions with performance focus
The Future of Gamified IT Training
As AI-driven threats, IoT vulnerabilities, and remote working models increase attack surfaces, the human element in IT security becomes even more critical. Gamification is not just a gimmick—it’s an essential evolution in the way businesses train their teams to be more alert, proactive, and effective.
For enterprises managing large-scale data centers, networking hardware, and multi-location IT ecosystems, this form of training is quickly becoming indispensable.
🔗 Future-proof your IT infrastructure with Leading Network Systems
Conclusion
Gamification in IT infrastructure training bridges the gap between knowledge and action. By transforming dry technical concepts into dynamic learning experiences, it cultivates a security-first mindset across all layers of your tech team.
Whether you're a startup scaling fast or an enterprise managing critical infrastructure, integrating gamified security awareness programs can significantly reduce human error, accelerate training, and strengthen your cyber defense posture.
✅ Get in touch with Leading Network Systems to design secure, intelligent infrastructure backed by skilled and engaged teams
0 notes