#Robust DevSecOps Framework
Explore tagged Tumblr posts
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
The Future of Security: Cloud-native Application Protection Platform Market Overview
Cloud-native Application Protection Platform Market Growth & Trends
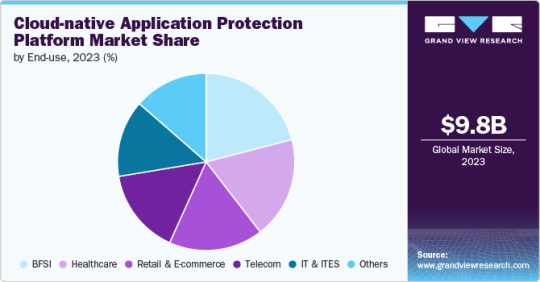
The global Cloud-native Application Protection Platform Market size was estimated at USD 9.79 billion in 2023 and is expected to grow at a CAGR of 21.8% from 2024 to 2030. The market is witnessing significant growth due to the increasing adoption of cloud-native applications and the rising need for robust security solutions. Cloud-native application protection platforms (CNAPP)s offer comprehensive protection for cloud-native environments, encompassing various security aspects such as workload protection, runtime protection, and compliance management. These platforms are designed to secure applications built using cloud-native technologies, ensuring they remain resilient against a broad range of cyber threats.
Several key factors are driving the demand for CNAPPs including the shift towards microservices and containerization has increased the complexity of securing applications, making traditional security approaches inadequate. CNAPPs address this challenge by providing visibility and control over dynamic, distributed environments. Secondly, the surge in cyberattacks targeting cloud-native applications has heightened awareness of the need for advanced security measures. Organizations are increasingly prioritizing security to protect their sensitive data and maintain customer trust.
The integration of artificial intelligence (AI) and machine learning (ML) capabilities. These technologies help in enhancing threat detection and response capabilities by assessing vast amounts of data and identifying anomalies in real-time. Additionally, the rise of DevSecOps practices, which integrate security into the development and operations processes, is driving the adoption of CNAPPs. This approach ensures that security is a continuous concern throughout the application lifecycle, rather than an afterthought.
Furthermore, there is a growing emphasis on compliance and regulatory requirements. As governments and industry bodies impose stricter regulations on data protection and privacy, organizations are compelled to adopt CNAPPs to ensure compliance. These platforms offer features such as automated compliance checks and reporting, helping organizations avoid hefty fines and reputational damage.
Curious about the Cloud-native Application Protection Platform Market? Download your FREE sample copy now and get a sneak peek into the latest insights and trends.
Cloud-native Application Protection Platform Market Report Highlights
The platform segment accounted for the largest market share of over 60% in 2023. Cloud-native application protection platforms (CNAPPs) provide a comprehensive security framework designed to safeguard cloud-native environments.
The public cloud segment accounted for the largest market share of over 68% in 2023.
The hybrid cloud segment is expected to grow at a significant rate during the forecast period. The demand for hybrid cloud native application protection platform is driven by the need for consistent security policies across diverse environments, seamless data integration, and flexibility in resource allocation.
The large enterprise segment accounted for the largest market share of over 58% in 2023.
The SMEs segment is expected to grow at a significant rate over the forecast period. Key factors driving demand include cost-effectiveness, scalability, and ease of deployment.
Cloud-native Application Protection Platform Market Segmentation
Grand View Research has segmented the global Cloud-Native Application Protection Platform (CNAPP) market report based on offering, deployment, enterprise size, end-use, and region:
Offering Outlook (Revenue; USD Billion; 2018 - 2030)
Platform
Services
Deployment Outlook (Revenue; USD Billion; 2018 - 2030)
Private
Public
Hybrid
Enterprise Size Outlook (Revenue; USD Billion; 2018 - 2030)
SMEs
Large Enterprises
End-use Outlook (Revenue; USD Billion; 2018 - 2030)
BFSI
Healthcare
Retail & E-commerce
Telecom
IT & ITES
Others
Download your FREE sample PDF copy of the Cloud-native Application Protection Platform Market today and explore key data and trends.
0 notes
Text
Best Software Development Company in Chennai: Elevating Your Digital Endeavors

In today’s fast-paced digital ecosystem, selecting the best software development company in Chennai can make or break your project’s success. Chennai, known as India’s “Detroit” for its robust automotive industry, has also emerged as a thriving hub for IT and software services. A top-tier Software Development Company in Chennai combines deep technical expertise, agile methodologies, and client-centric approaches to deliver tailor-made solutions that drive growth, optimize operations, and future-proof your business.
Why Chennai Is a Premier Destination for Software Development
Skilled Talent Pool Chennai boasts some of India’s leading engineering and technical institutes, producing thousands of software graduates each year. Local companies benefit from this steady influx of talent, ensuring access to developers, architects, and quality-assurance specialists proficient in the latest languages and frameworks.
Cost-Effective Excellence Compared to Western markets, Chennai offers highly competitive pricing without compromising on quality. You gain world-class software development services—ranging from mobile apps to enterprise applications—at a fraction of the cost, maximizing ROI.
Robust Infrastructure and Government Support Government policies and IT parks like TIDEL Park and SIPCOT IT Park provide state-of-the-art infrastructure, reliable power, and connectivity, attracting global clients and fostering innovation.
Cultural Alignment and Communication Chennai’s multilingual workforce, comfortable with English and Western business practices, ensures seamless collaboration, clear communication, and on-time delivery throughout the software development lifecycle.
Core Services of a Leading Software Development Company in Chennai
A truly best software development company in Chennai offers an end-to-end suite of services designed to cater to diverse industry needs:
Custom Software Development From initial requirement gathering and system design to coding, testing, and deployment—custom applications that fit your unique workflows, whether in healthcare, finance, education, or logistics.
Web and Mobile App Development User-centric websites and native/hybrid mobile applications built on React, Angular, Flutter, or Swift/Kotlin to engage customers across devices.
Cloud Solutions & DevOps Cloud-native architectures on AWS, Azure, or Google Cloud, combined with CI/CD pipelines and automated infrastructure management, ensure scalability, security, and cost optimization.
Enterprise Software & ERP/CRM Integration of enterprise resource planning and customer relationship management systems—like SAP, Oracle, or Salesforce—streamlines operations and enhances data-driven decision-making.
AI, ML & Data Analytics Advanced analytics, machine-learning algorithms, and AI-powered tools that turn raw data into actionable insights, predictive models, and intelligent automation.
Quality Assurance & Testing Rigorous QA protocols, automated and manual testing frameworks, and performance/security assessments that guarantee bug-free, high-performance software.
Maintenance & Support Post-launch monitoring, regular updates, 24/7 support, and iterative improvements to keep your applications secure, compliant, and aligned with evolving business needs.
Key Differentiators of the Best Software Development Company in Chennai
Agile and DevSecOps Culture Embracing Agile methodologies—Scrum or Kanban—coupled with integrated security (DevSecOps), ensures rapid iterations, continuous feedback, and proactive risk mitigation.
Domain Expertise & Case Studies Whether you’re in e-commerce, fintech, healthcare, or manufacturing, the top Chennai firms showcase a rich portfolio of successful projects, complete with client testimonials, performance metrics, and ROI analyses.
Technology Partnerships Official partnerships with Microsoft, AWS, Google, and other technology leaders grant early access to new tools and specialized support, translating into cutting-edge solutions for your projects.
Transparent Communication & Governance Dedicated project managers, weekly sprint reports, and collaborative platforms (JIRA, Confluence, Slack) guarantee visibility into timelines, budgets, and deliverables—eliminating surprises and fostering trust.
Focus on UX/UI and Accessibility Beyond robust back-ends, the best companies prioritize intuitive, accessible interfaces—conducting user research, crafting wireframes and prototypes, and adhering to WCAG guidelines to ensure inclusivity.
How to Choose the Right Software Development Partner in Chennai
Assess Technical Stack Alignment Verify that the company’s expertise matches your tech requirements—be it Java, .NET, Python, Node.js, or mobile frameworks.
Evaluate Process Maturity Look for ISO certifications or CMMI level appraisals, which indicate mature development processes and quality management systems.
Request Detailed Proposals & Time Estimates A transparent, itemized proposal outlining scopes, milestones, resource allocations, and risk mitigation strategies helps you set realistic expectations.
Check Cultural Fit & Scalability Ensure the partner’s working hours, communication style, and team size can adapt to your project’s evolving demands.
Pilot Engagement or Proof of Concept Starting with a small pilot or PoC project allows you to validate technical capabilities, communication efficiency, and delivery timelines before committing to a full-scale engagement.
Conclusion & Next Steps
Partnering with the best software development company in Chennai positions your organization to harness technological advancements, streamline operations, and outpace competitors. By focusing on a firm’s domain expertise, development methodology, and cultural alignment, you’ll secure a partner capable of transforming your digital vision into reality.
Ready to build your next application? Reach out today for a free consultation and let Chennai’s premier software architects craft the perfect solution for your business ambitions.
0 notes
Text
Application Security Market Drivers: Key Forces Powering Growth Across the Cybersecurity Landscape
The application security market is witnessing significant momentum, fueled by several critical factors reshaping the cybersecurity industry. As businesses grow increasingly reliant on digital infrastructure, the need to safeguard applications—whether web, mobile, or cloud-based—has become paramount. In this fast-changing landscape, various dynamic forces are driving the market’s growth and evolution.

One of the most prominent drivers is the rising frequency and sophistication of cyberattacks. Applications are prime targets for threat actors looking to exploit vulnerabilities for data breaches, ransomware, or unauthorized access. With attackers employing advanced techniques like zero-day exploits and AI-powered intrusions, organizations are under mounting pressure to secure their applications comprehensively. This growing threat landscape has compelled enterprises of all sizes to invest in advanced application security solutions.
Another major force influencing the market is the shift toward cloud computing and hybrid environments. As businesses transition from traditional on-premise systems to cloud-native platforms, the complexity of securing applications increases. Cloud-based applications are exposed to a wider range of security challenges, including data leakage, misconfigured services, and insecure APIs. This transformation is prompting the adoption of application security tools that are compatible with multi-cloud and hybrid infrastructures, ensuring consistent protection across environments.
Regulatory compliance is also a key driver shaping the application security market. Governments and industry bodies worldwide are tightening regulations to protect user data and digital assets. Frameworks such as GDPR, CCPA, and HIPAA require organizations to implement stringent security measures. Failure to comply can result in severe financial and reputational consequences. As a result, businesses are prioritizing application security to align with legal standards and avoid penalties.
The market is also benefiting from the rapid integration of DevSecOps practices into software development lifecycles. DevSecOps emphasizes embedding security directly into the development process rather than treating it as an afterthought. By automating security checks, code analysis, and vulnerability assessments, DevSecOps promotes a proactive and agile security model. This integration not only enhances application protection but also accelerates product delivery without compromising safety.
A further driver is the growing adoption of APIs in modern applications. APIs are essential for building feature-rich and scalable applications, but they also present new attack vectors. API vulnerabilities can lead to unauthorized access and data exposure. As organizations increasingly rely on APIs to enable interoperability and improve user experiences, securing them becomes a top priority. This trend is fueling demand for specialized API security solutions within the broader application security ecosystem.
Artificial Intelligence and machine learning are also playing a significant role in driving the application security market. These technologies are being integrated into security tools to enhance threat detection, automate response, and reduce false positives. AI-powered solutions can analyze vast volumes of data in real-time, helping identify anomalies and potential threats faster than traditional methods. This advancement not only improves security outcomes but also increases operational efficiency.
The rise of remote work and BYOD (Bring Your Own Device) culture has further expanded the application threat surface. Employees accessing applications from personal devices or unsecured networks introduce additional vulnerabilities. Companies are now investing in robust application security frameworks that include endpoint protection, access control, and secure authentication protocols to address these emerging risks.
Additionally, digital transformation initiatives across industries are creating new demands for secure applications. As businesses digitize operations, customer interactions, and supply chains, the importance of securing each digital touchpoint grows. Application security is no longer seen as optional but rather as an essential component of business continuity and brand protection.
Lastly, the increasing awareness and education about cybersecurity risks is influencing market growth. Organizations and consumers alike are becoming more informed about the importance of application security. This awareness is translating into stronger internal policies, higher budgets for security investments, and a culture that prioritizes data protection.
In conclusion, the application security market is driven by a confluence of factors including escalating cyber threats, the shift to cloud environments, regulatory demands, DevSecOps adoption, API proliferation, AI integration, remote work trends, and heightened cybersecurity awareness. Together, these drivers are creating a robust market trajectory, encouraging innovation and the continuous evolution of application security solutions to meet modern challenges.
0 notes
Text
Cloud Security and Compliance: Building Resilience Through Automation and Policy Enforcement
As organizations shift to cloud-first strategies, the need for robust security and compliance has never been greater. The cloud offers agility and scalability, but it also introduces complexity and risk. From misconfigured resources to unauthorized access and evolving threat landscapes, securing the cloud is a moving target.
To address these challenges, companies are turning to automation and policy enforcement to build resilience into their cloud environments. In this blog, we explore how you can achieve proactive cloud security and stay compliant through smart automation practices.
The Evolving Landscape of Cloud Security and Compliance
The cloud transforms how businesses operate — but it also shifts how security is approached. Traditional perimeter-based security models no longer suffice. Instead, organizations must adopt a zero-trust, policy-driven, and automated approach.
Security and compliance in the cloud are shaped by:
Complex architectures (multi-cloud, hybrid, containerized)
Stringent regulations (GDPR, HIPAA, SOC 2, ISO 27001, etc.)
Shared responsibility models
Frequent changes due to CI/CD pipelines and DevOps practices
To maintain control, organizations must focus on continuous visibility, consistent policies, and automated remediation.
Why Automation is Key to Cloud Resilience
Manual security processes are not scalable. Automation enables teams to react instantly to threats, enforce policies at scale, and reduce human error.
Here’s how automation builds security resilience:
✅ Real-Time Threat Detection & Response
Cloud-native tools like AWS GuardDuty, Azure Security Center, and Google Cloud Security Command Center can automatically detect suspicious activity and trigger remediation workflows.
✅ Continuous Compliance Monitoring
Automated tools continuously audit cloud configurations against compliance frameworks and flag violations instantly.
✅ Infrastructure as Code (IaC) Security
IaC tools like Terraform and AWS CloudFormation, when paired with policy-as-code engines like Open Policy Agent (OPA) or HashiCorp Sentinel, ensure secure configurations from day one.
✅ Automated Remediation
Security misconfigurations (e.g., public S3 buckets, weak IAM policies) can be detected and fixed automatically before they become vulnerabilities.
Enforcing Policies in the Cloud: From Governance to Guardrails
Policy enforcement isn’t just about writing security guidelines — it’s about embedding them into every stage of the development lifecycle.
Here’s how organizations can enforce cloud security policies effectively:
1. Policy as Code
Define security and compliance rules in code that can be automatically enforced during builds and deployments. Tools like OPA, Sentinel, or Rego enable this capability.
2. Cloud-Native Guardrails
Cloud platforms allow you to enforce service control policies, IAM policies, and resource tags that prevent insecure practices and ensure compliance with internal standards.
3. Secure CI/CD Pipelines
Integrate security checks into CI/CD workflows to block deployments that don’t meet compliance or security standards — also known as “shift-left security.”
4. Role-Based Access Control (RBAC)
Limit access to resources using least privilege principles. Automate permissions auditing and detect deviations.
The Role of DevSecOps
DevSecOps brings security into the software development lifecycle from the beginning — not as an afterthought. By integrating security tools and processes into CI/CD pipelines, teams can:
Catch vulnerabilities early
Maintain compliance through automated checks
Build secure code faster
Foster collaboration between development, security, and operations teams
At Salzen Cloud, we help companies implement DevSecOps practices that combine automation, compliance, and cloud-native security strategies.
Benefits of Automation and Policy Enforcement
Improved Security Posture Detect and remediate threats before they escalate.
Regulatory Compliance Stay audit-ready with continuous monitoring and reporting.
Operational Efficiency Reduce manual overhead and focus on high-value tasks.
Scalability Apply consistent security controls across environments, teams, and cloud providers.
Salzen Cloud Can Help
At Salzen Cloud, we specialize in helping businesses build secure, compliant, and resilient cloud environments. From automated security monitoring to policy-as-code implementation, our cloud security services ensure that your infrastructure is protected — without slowing down innovation.
Final Thoughts
Security and compliance in the cloud don’t have to be a bottleneck. With the right mix of automation, policy enforcement, and DevSecOps culture, you can build a cloud environment that’s not only secure and compliant — but also agile and resilient.
Looking to secure your cloud the smart way? Let Salzen Cloud help you integrate automation and governance at the core of your cloud strategy.
0 notes
Text
Threat Modeling Tools Market Insights: Industry Share, Trends & Future Outlook 2032
The Threat Modeling Tools Market was valued at USD 0.95 billion in 2023 and is expected to reach USD 3.37 billion by 2032, growing at a CAGR of 15.17% from 2024-2032
The threat modeling tools market is experiencing significant growth as businesses focus on strengthening cybersecurity frameworks. The rising number of cyber threats and stringent regulatory requirements are driving organizations to adopt advanced threat modeling solutions.
The threat modeling tools market continues to expand as enterprises, government bodies, and security teams increasingly recognize the need for proactive security assessment and risk mitigation. As cyber threats become more sophisticated, organizations are investing in automated threat modeling solutions to identify vulnerabilities, prioritize risks, and enhance security measures.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3420
Market Keyplayers:
Cisco Systems, Inc. (Cisco Threat Response, Cisco SecureX)
Sparx Systems Pty Ltd. (Enterprise Architect, Pro Cloud Server)
Varonis Systems Inc. (DatAdvantage, Data Classification Engine)
Mandiant (Mandiant Advantage, Mandiant Threat Intelligence)
Intel Corporation (Intel Security Innovation Platform, Intel Threat Detection Technology)
Kroll, LLC. (Kroll Responder, Kroll Cyber Risk Management)
Synopsys (Black Duck, Coverity)
IBM Corporation (IBM Security QRadar, IBM Guardium)
Microsoft Corporation (Microsoft Sentinel, Microsoft Defender)
Coalfire Systems, Inc. (CoalfireOne, Coalfire GRC)
Avocado Systems (Avocado Security, Avocado Enterprise Security)
ThreatModeler (ThreatModeler, ThreatModeler Cloud)
Secure Engineering (Secure Design Studio, Secure Risk)
Rogue Wave Software (Klocwork, Protect)
Aquila (Aquila Threat Modeling, Aquila Risk Manager)
RiskSense (RiskSense Platform, RiskSense Threat Intelligence)
Immersive Labs (Immersive Labs Cyber Range, Immersive Labs Threat Intelligence)
Nozomi Networks (Nozomi Networks Guardian, Nozomi Networks SCADAguardian)
ThreatQuotient (ThreatQ, ThreatQ Threat Intelligence Platform)
Zylo (Zylo Threat Modeling, Zylo Risk Analysis)
Palo Alto Networks (Cortex XSOAR, Cortex XDR)
Market Size, Share, and Scope
Increasing demand for automated risk assessment tools is driving adoption across IT, BFSI, healthcare, and government sectors.
North America holds the largest market share due to rapid technological advancements and stringent data security regulations.
The emergence of AI-driven threat analysis and cloud-based security solutions is expanding the scope of the market.
Companies are focusing on continuous security integration within DevSecOps pipelines to enhance software security.
Market Trends
Increased Emphasis on Proactive Cybersecurity
Organizations are shifting from reactive to proactive security approaches with predictive threat modeling.
Integration of AI and Machine Learning
AI-driven analytics enable real-time threat detection, automated risk assessments, and intelligent mitigation strategies.
Cloud-Based Threat Modeling Solutions
Cloud-native security tools are gaining traction, ensuring scalability, remote access, and seamless updates.
Adoption of DevSecOps and Agile Security Practices
Threat modeling is being integrated into DevSecOps frameworks, ensuring early-stage vulnerability detection.
Expansion in Healthcare and BFSI Sectors
Rising cyber risks in financial services and healthcare are driving the demand for robust security frameworks.
Automated Threat Intelligence & Continuous Monitoring
Real-time security monitoring and automated risk assessment capabilities are revolutionizing cybersecurity strategies.
Compliance with Stringent Data Protection Regulations
Laws such as GDPR, CCPA, and NIST standards are compelling companies to adopt advanced threat modeling tools.
Growth of Open-Source Threat Modeling Platforms
Open-source frameworks are gaining popularity due to their customizability and cost-effectiveness.
Integration with Zero Trust Security Models
Zero Trust principles are being embedded into threat modeling strategies to minimize attack surfaces.
Adoption of Blockchain for Secure Threat Analysis
Blockchain is being explored for immutable threat records and enhanced security transparency.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3420
Market Segmentation:
By Component
Solution
Services
By Platform
Web-Based
Cloud-Based
Desktop-Based
By Enterprise Size
Large Enterprise
Small and Medium Size Enterprise
By Type
Static Analysis Tools
Dynamic Analysis Tools
Hybrid Analysis Tools
By Application
IT & Telecom
BFSI
Healthcare
Manufacturing
Utilities
Growth Analysis
The threat modeling tools market is driven by a rising number of cyberattacks, increasing data privacy concerns, and regulatory compliance requirements. Organizations are leveraging AI-powered, automated solutions to enhance cybersecurity frameworks. The demand for cost-effective, scalable, and customizable security solutions is fostering innovation in the market.
Threat Modeling Tools Market Industry Report 2032: Size, Share & Growth Analysis | Industry Forecast 2032
According to industry forecasts, the threat modeling tools market will continue to expand, driven by increasing investments in cybersecurity infrastructure and threat intelligence platforms. Enterprises are focusing on:
Investing in AI-powered security automation for faster response times.
Enhancing DevSecOps security integration to build secure applications.
Developing industry-specific security solutions for BFSI, healthcare, government, and IT sectors.
Future Prospects
1. Growth in AI-Driven Predictive Threat Modeling
AI-based security solutions will continue to advance, offering predictive analytics for risk prevention.
2. Adoption of Next-Gen Security Frameworks
The rise of Zero Trust Architecture and Secure Access Service Edge (SASE) will shape the future of cybersecurity strategies.
3. Expansion into Emerging Markets
Developing economies will witness increased adoption of threat modeling solutions, driven by rapid digitization and cybersecurity awareness.
4. Evolution of Quantum-Safe Security Solutions
With the emergence of quantum computing, new encryption and security measures will be developed to combat quantum threats.
Access Complete Report: https://www.snsinsider.com/reports/sports-betting-market-1846
Conclusion
The threat modeling tools market is poised for strong growth as businesses prioritize cybersecurity, compliance, and automation. With advancements in AI, cloud security, and DevSecOps integration, organizations can strengthen risk management frameworks and safeguard digital assets. By 2032, the industry is expected to expand significantly, ensuring a proactive, intelligent, and resilient cybersecurity ecosystem.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#threat modeling tools market#threat modeling tools market Size#threat modeling tools market Analysis#threat modeling tools market Growth#threat modeling tools market Trends
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
How to Hire DevSecOps Developers: A Step-by-Step Guide

Cybersecurity has become a paramount concern for the majority of the businesses and is a top priority in the majority of the development processes. The demand for DevSecOps developers has outgrown because they embed security in every stage of the software development lifecycle to reduce risks and improve overall system resilience.
Data protection and uptime are vital for your SaaS business which is why you need to have a skilled DevSecOps team for ensuring security, scalability, and compliant applications. For this let’s understand what are the right skills, hiring process, and recruitment strategies you must consider when you hire software engineers for this purpose.
A Step-by-Step Hiring Guide to Building a Strong and Secure DevSecOps Team
State your hiring requirements
List the primary duties and competencies that your DevSecOps developer must possess before you begin your search. Take into account:
Proficiency in cloud security - familiarity with AWS, Azure, or Google Cloud.
Knowledge of automation and CI/CD: familiarity with Kubernetes, Jenkins, and GitLab CI/CD.
Comprehending security frameworks like NIST, SOC 2, and GDPR is essential for threat modelling and security compliance.
The hiring process is streamlined and the right talent is drawn in when these requirements are clearly stated.
Use reputed platforms to source talent
Although it can be difficult to find great talent, the following platforms can help:
Job portals: Indeed, Glassdoor, and LinkedIn for full-time roles; freelance platforms: Upwork and Toptal for contract-based recruiting.
IT staffing agencies: specialized companies that offer talent that is ready for employment after pre-screening applicants. Uplers is a hiring platform that unlike IT staffing agencies provides you AI-vetted top talent from India in a 4-step process.
Without having to spend months on hiring, SaaS organizations can discover skilled DevSecOps developers more rapidly by collaborating with such hiring platforms.
Screen and evaluate candidates
Make sure you carry out comprehensive evaluations to ensure you recruit the top talent:
Technical interviews: Assess their familiarity with cloud security best practices and DevSecOps tools.
Practical exercises: Evaluate their proficiency in automating security checks in CI/CD pipelines.
Assessment of soft skills: Verify excellent problem-solving and teamwork capabilities.
Long-term success for SaaS organizations depends on hiring DevSecOps developers who can comprehend the challenges of protecting cloud-based apps.
Offer competitive compensation and benefits
Offering competitive pay and benefits is crucial given the growing demand for DevSecOps expertise. Take into account:
Flexibility in remote work: Many DevSecOps engineers choose remote positions.
Opportunities for continuous learning: Discuss certifications and training such as CISSP or AWS Security.
Alluring benefits packages: Offering competitive pay helps you retain top developers.
Hiring software engineers that can work with DevSecOps experts on secure coding techniques may also be necessary if you require more backend help. You could also use free tools like the Uplers salary benchmarking tool to compare, contrast, and adjust your compensation offering with the industry standards.
Onboarding and retention strategies
Long-term success is ensured by a seamless onboarding process for DevSecOps developers:
Establish clear security policies and workflows to incorporate them into your team.
Assign mentors to assist them in understanding internal security procedures.
Promote ongoing development via security research and training.
Retaining top security staff lowers risks, improves compliance, and increases system resilience for SaaS organizations.
Summing Up
Integrating security into your software development process requires hiring the best DevSecOps developers. You may create a robust DevSecOps team by establishing clear requirements, using IT staffing companies, and carrying out in-depth assessments.
Investing in qualified experts guarantees long-term security and efficiency. Having a proactive security plan is essential for SaaS organizations; and no longer a choice.
0 notes
Text
Top Platform Engineering Practices for Scalable Applications

In today’s digital world, scalability is a crucial attribute for any platform. As businesses grow and demands change, building a platform that can adapt and expand is essential. Platform engineering practices focus on creating robust, flexible systems. These systems not only perform underload but also evolve with emerging technologies. Here are some top practices to ensure your applications remain scalable and efficient.
1. Adopt a Microservices Architecture
A microservices architecture breaks down a monolithic application into smaller, independent services that work together. This approach offers numerous benefits for scalability:
Independent Scaling: Each service can be scaled separately based on demand. This ensures efficient resource utilization.
Resilience: Isolated failures in one service do not bring down the entire application. This improves overall system stability.
Flexibility: Services can be developed, deployed, and maintained using different technologies. This allows teams to choose the best tools for each job.
2. Embrace Containerization and Orchestration
Containerization, with tools like Docker, has become a staple in modern platform engineering. Containers package applications with all their dependencies. This ensures consistency across development, testing, and production environments. Orchestration platforms like Kubernetes further enhance scalability by automating the deployment, scaling, and management of containerized applications. This combination allows for rapid, reliable scaling. It alsod helps maintain high availability.
3. Leverage Cloud-Native Technologies
Cloud-native solutions are designed to exploit the full benefits of cloud computing. This includes utilizing Infrastructure as Code (IaC) tools such as Terraform or CloudFormation to automate the provisioning of infrastructure. Cloud platforms offer dynamic scaling, robust security features, and managed services that reduce operational complexity. Transitioning to cloud-native technologies enables teams to focus on development. Meanwhile, underlying infrastructure adapts to workload changes.
4. Implement Continuous Integration/Continuous Deployment (CI/CD)
A robust CI/CD pipeline is essential for maintaining a scalable platform. Continuous integration ensures that new code changes are automatically tested and merged. This reduces the risk of integration issues. Continuous deployment, on the other hand, enables rapid, reliable releases of new features and improvements. By automating testing and deployment processes, organizations can quickly iterate on their products. They can also respond to user demands without sacrificing quality or stability.
5. Monitor, Analyze, and Optimize
Scalability isn’t a one-time setup—it requires continuous monitoring and optimization. Implementing comprehensive monitoring tools and logging frameworks is crucial for:
tracking application performance,
spotting bottlenecks, and
identifying potential failures.
Metrics such as response times, error rates, and resource utilization provide insights that drive informed decisions on scaling strategies. Regular performance reviews and proactive adjustments ensure that the platform remains robust under varying loads.
6. Focus on Security and Compliance
As platforms scale, security and compliance become increasingly complex yet critical. Integrating security practices into every stage of the development and deployment process—often referred to as DevSecOps—helps identify and mitigate vulnerabilities early. Automated security testing and regular audits ensure that the platform not only scales efficiently but also maintains data integrity and compliance with industry standards.
Scalable applications require thoughtful platform engineering practices that balance flexibility, efficiency, and security. What happens when organizations adopt a microservices architecture, embrace containerization and cloud-native technologies, and implement continuous integration and monitoring? Organizations can build platforms capable of handling growing user demands. These practices streamline development and deployment. They also ensure that your applications are prepared for the future.
Read more about how platform engineering powers efficiency and enhances business value.
#cicd#cloud native#software development#software services#software engineering#it technology#future it technologies
0 notes
Text
DevSecOps: The Secure Development Revolution with Sify Technologies

DevSecOps: The Secure Development Revolution with Sify Technologies
In an era where cyber threats are evolving at an unprecedented pace, ensuring security at every stage of software development is no longer optional—it is essential. Traditional security measures, which were once applied only at the end of the development cycle, are now proving to be ineffective against today’s advanced cyber risks.
This is where DevSecOps steps in—a revolutionary approach that seamlessly integrates security into the DevOps process, ensuring that security becomes a shared responsibility rather than a last-minute addition.
Leading the charge in secure application development, Sify Technologies provides an advanced DevSecOps framework that blends automation, AI-driven security, and real-time compliance monitoring. Let’s explore how Sify’s DevSecOps solutions are helping businesses accelerate innovation while keeping their applications resilient against cyber threats.
What is DevSecOps?
DevSecOps (Development, Security, and Operations) is a methodology that ensures security is embedded into every phase of the software development lifecycle. Unlike traditional security models, which involve testing applications for vulnerabilities at the end of development, DevSecOps integrates security early and throughout the entire process.
Key Principles of DevSecOps:
Shift Left Security – Identifies and mitigates vulnerabilities in the early stages of development, reducing the cost and complexity of fixing security flaws.
Security as Code – Automates security policies, ensuring continuous compliance across CI/CD pipelines.
Continuous Monitoring – Uses real-time scanning and analytics to proactively detect threats before they become exploits.
Automated Compliance – Ensures adherence to regulatory standards, reducing manual effort and human errors.
With DevSecOps, organizations can develop, deploy, and maintain applications faster—without compromising security.
Sify Technologies’ DevSecOps Approach
As a pioneer in digital transformation and application modernization, Sify Technologies delivers a robust DevSecOps framework that addresses the most pressing security concerns in today’s fast-paced development environments.
1. AI-Driven Security Automation
Sify integrates Artificial Intelligence (AI) and Machine Learning (ML) to enhance security automation. With predictive threat analysis, Sify’s DevSecOps framework proactively detects vulnerabilities, preventing breaches before they occur.
2. Integrated Security into CI/CD Pipelines
Security should not slow down development. Sify embeds automated security checks into Continuous Integration and Continuous Deployment (CI/CD) workflows, ensuring that security is seamlessly enforced without disrupting agility.
3. Proactive Threat Monitoring & Incident Response
Cyber threats evolve rapidly, and Sify ensures continuous security monitoring to detect anomalies and threats in real time. Their proactive incident response mechanisms enable swift mitigation of security risks, reducing the impact of attacks.
4. Regulatory Compliance & Governance
Meeting regulatory requirements is a challenge for many businesses. Sify’s automated compliance tools ensure that applications adhere to industry standards like GDPR, HIPAA, PCI-DSS, and ISO 27001, reducing the risk of non-compliance penalties.
5. DevSecOps Culture Enablement
Successful DevSecOps adoption is not just about tools—it’s about culture. Sify helps organizations bridge the gap between development, security, and operations teams, fostering a security-first mindset through training, strategy workshops, and best practice implementation.
Why Businesses Need DevSecOps Now More Than Ever
1. Rising Cyber Threats
Cyberattacks are more sophisticated and frequent than ever before. A proactive security approach like DevSecOps ensures vulnerabilities are identified and mitigated before they are exploited by attackers.
2. Speed & Security in Software Development
Businesses today demand rapid software development to stay competitive. Traditional security methods slow down innovation, but DevSecOps automates security, ensuring that security doesn’t become a bottleneck in the development lifecycle.
3. Cost-Effective Security Implementation
Security issues discovered late in development can cost millions to fix. DevSecOps reduces remediation costs by shifting security left—fixing vulnerabilities early when they are easier and cheaper to address.
4. Regulatory & Compliance Assurance
With global regulations tightening, organizations need continuous compliance rather than last-minute audits. DevSecOps ensures security controls are built into applications, reducing compliance risks.
5. Improved Collaboration Between Teams
By integrating security into DevOps, Sify enables better collaboration between developers, security teams, and operations teams, creating a streamlined and efficient security-first development culture.
Sify’s DevSecOps Impact: Real-World Benefits
🔹 30% Faster Time-to-Market – Secure applications without slowing development cycles. 🔹 Automated Compliance – Reduce human errors and ensure 100% regulatory adherence. 🔹 Real-Time Threat Intelligence – Identify and neutralize threats before they impact applications. 🔹 Cost Reduction in Security Fixes – Cut security remediation costs by up to 30%.
Final Thoughts
As cyber threats continue to grow in complexity, businesses cannot afford to treat security as an afterthought. DevSecOps is the future of secure software development, ensuring that security is built-in, not bolted on.
With Sify Technologies’ DevSecOps solutions, businesses can: ✔ Build and deploy secure, high-performing applications. ✔ Automate security processes without disrupting CI/CD pipelines. ✔ Proactively detect and mitigate security threats. ✔ Ensure continuous compliance with industry regulations.
0 notes
Text
Addressing the Evolving Challenges with Proactive Consulting Services
Future-Proofing Fintech QA: Addressing the Evolving Challenges with Proactive Consulting Services
Introduction
The fintech industry is evolving at an unprecedented pace, driven by advancements in AI, blockchain, and cloud computing. With increasing regulatory scrutiny and rising cyber threats, ensuring robust software quality assurance (QA) is more crucial than ever. However, traditional QA methodologies often struggle to keep up with the dynamic nature of fintech.

To stay ahead, financial institutions must embrace proactive quality assurance consulting services that anticipate risks, enhance compliance, and integrate cutting-edge testing strategies. This article explores the key challenges fintech QA faces and how consulting services help future-proof QA processes for long-term success.
Key Challenges in Fintech QA
1. Keeping Up with Rapid Technological Advancements
As fintech solutions incorporate AI-driven analytics, blockchain transactions, and cloud-based platforms, QA teams must validate the functionality, security, and scalability of these emerging technologies.
Solution: Implementing AI-Driven Testing
QA consultants leverage AI-powered test automation to accelerate regression testing, detect anomalies, and ensure continuous validation of evolving fintech applications.
2. Stricter Regulatory Compliance and Data Privacy Requirements
Regulations such as GDPR, PCI DSS, and Open Banking mandate rigorous compliance testing. Failure to meet these standards can lead to legal penalties and reputational damage.
Solution: Compliance-Focused QA Strategies
Quality assurance consulting services integrate automated compliance testing, real-time audit reporting, and risk-based testing frameworks to ensure adherence to regulatory requirements.
3. The Rising Threat of Cybersecurity Risks
With financial transactions becoming increasingly digitized, cyberattacks, fraud, and data breaches pose significant threats to fintech applications.
Solution: Security-First QA Practices
QA consultants implement penetration testing, API security testing, and DevSecOps methodologies to identify vulnerabilities before they become security breaches.
4. The Need for Seamless Customer Experience (CX)
User expectations for fintech apps are higher than ever, with customers demanding fast, intuitive, and glitch-free financial services.
Solution: CX-Focused Performance Testing
Consulting services conduct real-world user simulations, load testing, and UX/UI testing to optimize performance across different devices and networks.
How QA Consulting Services Future-Proof Fintech QA
1. Adopting a Shift-Left Testing Approach
Traditional QA often happens too late in the development lifecycle. Shift-Left Testing ensures defects are identified early, reducing costs and improving software reliability.
2. Continuous Integration and Deployment (CI/CD) Optimization
QA consultants help fintech firms integrate automated testing pipelines into their CI/CD workflows, ensuring faster releases without compromising quality.
3. Implementing Scalable Test Automation
A proactive QA strategy includes AI-driven automation frameworks, which adapt to evolving software features and regulatory requirements.
4. Leveraging Cloud-Based Testing Infrastructure
Modern fintech apps require multi-cloud compatibility and cross-platform testing. QA consultants provide cloud-based testing solutions that enhance scalability and test coverage.
Conclusion
To stay competitive, fintech companies must embrace future-proof QA strategies that address evolving security, compliance, and technological challenges. Quality assurance consulting services equip financial institutions with the expertise and tools needed to proactively mitigate risks, enhance customer trust, and drive innovation.
Want to ensure your fintech QA processes are ready for the future? Contact our expert QA consultants today and build a resilient, future-ready testing strategy!
#qualityassuranceservices#qualityassurancetesting#qualityassurancecompany#quality assurance services
0 notes
Text
Cloud-Native Application Protection Platform: Securing Modern Applications
As businesses accelerate their digital transformation, cloud-native applications have become the backbone of innovation. However, the shift to cloud environments has introduced new security challenges, making Cloud-Native Application Protection Platforms (CNAPPs) a necessity. According to the Cloud-Native Application Protection Platform Market Forecast, the demand for these solutions is rapidly increasing as enterprises seek comprehensive security measures to protect their workloads across multi-cloud and hybrid environments.
Understanding Cloud-Native Application Protection Platforms
A Cloud-Native Application Protection Platform (CNAPP) is a unified security solution designed to protect cloud-native applications throughout their lifecycle. Unlike traditional security tools that focus on specific aspects such as workload protection or vulnerability management, CNAPPs integrate multiple security functions, including container security, cloud workload protection, API security, and runtime threat defense. The Cloud-Native Application Protection Platform Market Forecast predicts that organizations will continue to invest in CNAPPs due to their ability to offer real-time visibility, automated security enforcement, and compliance assurance.
Key Features of CNAPPs
Comprehensive Visibility – CNAPPs provide full-stack visibility into cloud applications, helping organizations identify risks and vulnerabilities before they become threats.
Automated Security Controls – These platforms leverage AI-driven automation to detect and mitigate security threats in real time.
DevSecOps Integration – By embedding security into the software development lifecycle, CNAPPs ensure that security measures are in place from the beginning.
Compliance Management – With built-in compliance frameworks, businesses can adhere to industry standards and regulatory requirements effortlessly.
Threat Detection & Response – Advanced analytics and threat intelligence help detect anomalies and respond to security incidents effectively.
The Growing Market for CNAPPs
As organizations adopt multi-cloud and hybrid cloud strategies, the Cloud-Native Application Protection Platform Market Forecast suggests that CNAPPs will become indispensable. Businesses are looking for solutions that not only safeguard their applications but also enhance operational efficiency. Vendors offering CNAPPs are continuously innovating, incorporating AI-driven security analytics, automated remediation, and zero-trust frameworks to address evolving cyber threats.
QKS Group: Leading the CNAPP Revolution
QKS Group is at the forefront of cloud security innovation, providing robust CNAPP solutions to businesses worldwide. With a deep understanding of modern security challenges, QKS Group offers advanced protection for cloud-native applications, ensuring organizations can focus on growth without compromising security.
Future Outlook
With cyber threats becoming more sophisticated, the Cloud-Native Application Protection Platform Market Forecast indicates that enterprises must adopt proactive security strategies. CNAPPs will continue to evolve, integrating AI, machine learning, and behavioral analytics to offer even stronger security postures. Companies that invest in these advanced security solutions will be better positioned to navigate the complexities of cloud security and compliance.
By leveraging CNAPPs, businesses can secure their cloud environments efficiently and maintain a competitive edge in the digital era. As the market grows, choosing the right CNAPP provider will be critical in ensuring robust protection for cloud-native applications.
#CloudSecurity#CNAPP#CloudNativeSecurity#CyberSecurity#CloudProtection#ApplicationSecurity#ZeroTrust#DevSecOps#ThreatDetection
0 notes