#dnsquery
Explore tagged Tumblr posts
Text
Come implementare Privacy Shield per non bloccare domini leciti

Perché il Piracy Shield non funziona e come sarebbe dovuto essere implementato. Nell’era digitale, la gestione della proprietà intellettuale e la lotta contro la pirateria online rappresentano sfide cruciali per i regolatori, le industrie creative e i fornitori di servizi internet. Il “Piracy Shield”, un’iniziativa dell’Autorità per le Garanzie nelle Comunicazioni (AGCOM), rappresenta un tentativo significativo di affrontare il problema della pirateria digitale in Italia. Questo strumento è stato ideato per identificare e bloccare l’accesso ai siti web che violano i diritti di proprietà intellettuale, sfruttando tecnologie di filtraggio degli “FQDN e degli indirizzi IP” (citando testualmente AGCOM). Nonostante le sue nobili intenzioni, il Piracy Shield ha suscitato non poche controversie e dibattiti riguardo la sua efficacia e le implicazioni per la libertà di espressione e il diritto alla privacy. In questo articolo tecnico-scientifico, si intende esplorare e discutere le ragioni per cui il Privacy Shield non ha raggiunto pienamente i suoi obiettivi, mettendo in luce le difficoltà tecniche, legali e etiche incontrate.

Sarà inoltre illustrato come, attraverso un approccio innovativo basato sulla configurazione di record CNAME, sia possibile distinguere tra servizi legittimi e illeciti associati allo stesso indirizzo IPv4. Questa dimostrazione pratica non solo evidenzierà le potenzialità di tali tecniche, ma anche come esse potrebbero essere integrate efficacemente in un framework rinnovato per la lotta alla pirateria, suggerendo modifiche e migliorie al sistema attuale del Piracy Shield. Le Content Delivery Network Le Content Delivery Networks (CDN) sono infrastrutture distribuite di server progettate per ottimizzare la consegna di contenuti web agli utenti finali. Le CDN migliorano la velocità e l’affidabilità di accesso ai dati riducendo la distanza fisica tra il server e l’utente, distribuendo il contenuto su diversi server posizionati in varie località geografiche. Funzionamento delle CDN Quando un utente accede a un sito web che utilizza una CDN, la richiesta di dati non viene inviata direttamente al server principale del sito, ma viene reindirizzata al server della CDN più vicino all’utente. Questo server “edge” contiene copie dei contenuti del sito, come file HTML, immagini, video e altri tipi di dati. Grazie a questa architettura, il tempo di caricamento delle pagine si riduce notevolmente, migliorando l’esperienza dell’utente e riducendo il carico sui server centrali. Mascheramento dell’IP reale Un effetto importante dell’uso delle CDN è il mascheramento dell’indirizzo IP pubblico reale del server di origine dei contenuti. Quando un servizio online adotta una CDN, gli indirizzi IP visibili al pubblico sono quelli dei server della rete CDN. Questo significa che l’IP percepito come fonte del servizio è in realtà quello della CDN, non del server originale. Questo ha implicazioni per la sicurezza, la privacy e la gestione del traffico, ma può anche complicare alcune operazioni di controllo e filtraggio del contenuto. Implicazioni per il filtraggio di contenuti Se un’autorità come AGCOM implementa misure per bloccare l’accesso a contenuti ritenuti illegali (come quelli piratati) mediante il filtraggio degli indirizzi IP attraverso strumenti come il Piracy Shield, si potrebbero verificare problemi significativi. Poiché un singolo indirizzo IP di una CDN può essere utilizzato per trasmettere i contenuti di numerosi servizi diversi, il blocco di quell’IP potrebbe avere l’effetto collaterale di interrompere l’accesso a servizi legittimi e non solo a quelli illegali. Questo scenario potrebbe portare a interruzioni di servizio per utenti che non sono coinvolti nella fruizione di contenuti piratati. Facciamo chiarezza con un esempio pratico Per comprendere meglio come funziona la navigazione su internet e l’interazione con una Content Delivery Network (CDN), prendiamo come esempio il processo di collegamento a un sito web, come “www.libero.it”. Questo esempio ci permetterà di osservare come, durante la navigazione, il nome di dominio inizialmente richiesto possa in realtà essere servito da un dominio completamente diverso, come “d31d9gezsyt1z8.cloudfront.net”, che appartiene a una CDN. DNS Query Il processo inizia quando l’utente digita “www.libero.it” nel browser. Il browser deve risolvere questo nome di dominio in un indirizzo IP per poter stabilire una connessione. Questo avviene tramite una richiesta DNS (Domain Name System). Il browser consulta i server DNS configurati (tipicamente forniti dal provider di servizi internet o specificati manualmente dall’utente) per ottenere l’indirizzo IP associato al nome di dominio. (Si vede evidenziata la richiesta) Ricezione della risposta DNS I server DNS eseguono la ricerca e, una volta trovato l’indirizzo IP, lo restituiscono al browser. Se il dominio è ospitato su una CDN, l’IP restituito sarà quello di uno dei server edge della CDN più vicino all’utente, non l’IP del server originale di “libero.it”. (Si vede evidenziata la risposta Apertura della connessione (Handshake) Con l’indirizzo IP in mano, il browser inizia un handshake TCP con il server al fine di stabilire una connessione affidabile. Questo include la sincronizzazione dei numeri di sequenza per garantire che i pacchetti di dati vengano inviati e ricevuti in ordine. Durante l’handhsake il client invia un segmento SYN , il server risponde con un SYN + ACK , il client termina l’handshake con un ACK. (Si vede in figura nella riga evidenziata l’inizio dell’handshake verso la CDN di libero).
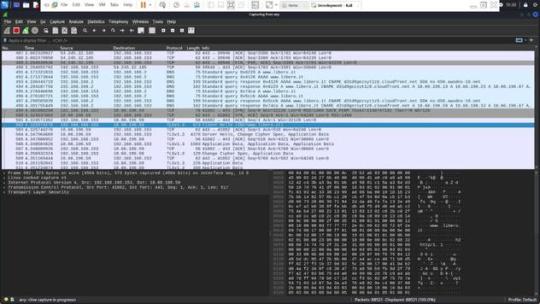
Negoziazione TLS (Transport Layer Security) Dopo aver stabilito una connessione TCP, il browser inizia una negoziazione TLS per assicurare che la comunicazione sia sicura e criptata. Questo processo inizia con l’invio del “ClientHello”, che include la versione di TLS supportata, i metodi di cifratura proposti, e altri dettagli necessari per la sicurezza.

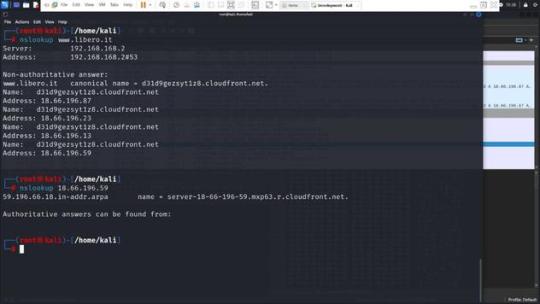
Il server risponde con un “ServerHello”, che conferma i dettagli della crittografia che sarà utilizzata, seleziona un metodo di cifratura tra quelli proposti dal client e prosegue con l’invio dei certificati, la verifica della chiave, e la conferma finale di inizio della cifratu Comunicazione sicura Una volta completata la negoziazione TLS, tutte le trasmissioni successive tra il browser e il server sono completamente criptate. Il browser può ora richiedere le risorse web da “www.libero.it”, che in realtà potrebbero essere servite dal dominio della CDN, come “d31d9gezsyt1z8.cloudfront.net”. Questo esempio mostra come, nella pratica, un sito che l’utente intende visitare possa essere effettivamente distribuito attraverso una rete CDN, rendendo il nome del dominio CDN visibile nelle comunicazioni di rete, anche se l’utente potrebbe non essere immediatamente consapevole di tale fatto. Considerazioni Questa architettura farà in modo che www.libero.it avrà una serie di IP associati all’ASN di cloudfront che vengono usati per far funzionare la CDN. Questi IP saranno associati non solo a www.libero.it ma anche a molti altri FQDN (Altre web app) che usano la CDN. Ricordiamo che questi servizi vengono distinti fra loro grazie ai record CNAME che puntano a FQDN univoci come questo: d31d9gezsyt1z8.cloudfront.net.
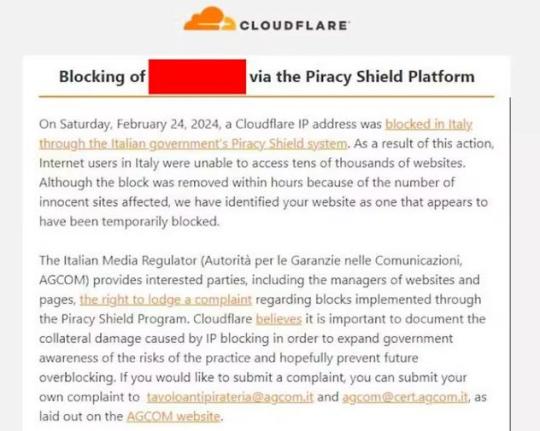
Dimostrazione del problema Con l’esempio precedente abbiamo quindi dimostrato che quando un servizio è integrato ad una CDN la corrispondenza servizio – IP non è più della cardinalità 1:1 , ma bensì N:1. Quindi se viene filtrato un indirizzo IP, N servizi vengono oscurati, pur non essendo tutti illegali. Lo abbiamo visto con l’esempio precedente in cui libero viene deliberatamente associato a diversi IP, condivisi con altri servizi della CDN cloudFront. Infatti una delle CDN che ha lamentato proprio questo problema è la nota Cloudflare che ha emesso un comunicato ad alcuni suoi clienti, esortandoli all’invio di una lettera di richiamo alla stessa AGCOM chiedendo di annullare l’ingiusto provvedimento.
Non si può quindi pensare di bloccare il traffico IP semplicemente filtrando un indirizzo IPv4/IPv6. Come si potrebbe procedere Per affrontare efficacemente le sfide poste dal filtraggio di contenuti attraverso indirizzi IP in un ambiente dove sono ampiamente utilizzate le Content Delivery Networks (CDN), è essenziale adottare metodi più sofisticati che prendano in considerazione le peculiarità tecniche delle CDN stesse. Una strategia più mirata e meno suscettibile di causare danni collaterali può essere implementata analizzando in dettaglio le proprietà di rete associate agli indirizzi IP, in particolare l’Autonomous System Number (ASN). Analisi dell’ASN Prima di procedere al blocco di un indirizzo IP sospettato di veicolare contenuti piratati, è cruciale determinare a quale sistema autonomo appartiene quel determinato IP. Se l’IP è associato all’ASN di una CDN nota, questo indica che potrebbe essere utilizzato per servire una moltitudine di clienti e servizi, molti dei quali legittimi. Il blocco diretto di tali IP potrebbe quindi interrompere l’accesso a servizi legittimi, causando interruzioni non necessarie e potenzialmente estese. Blocco basato su FQDN della CDN Invece di bloccare indiscriminatamente gli indirizzi IP, si dovrebbe valutare l’opzione di filtrare specifici Fully Qualified Domain Names (FQDN) direttamente legati a contenuti illeciti. Un metodo più mirato consiste nell’analizzare i record CNAME, che collegano un FQDN a un altro dominio, spesso usato per identificare contenuti specifici all’interno di una CDN. Il sistema attuale del Piracy Shield già applica il blocco agli FQDN e agli indirizzi IP, ma non estende questo trattamento ai FQDN univoci usati dalle CDN. Ad esempio, bloccando il dominio pubblico www.libero.it ed i suoi indirizzi IP, si impedisce anche l’accesso agli IP come 18.66.196.87, 18.66.196.23, 18.66.196.13 e 18.66.196.59. Tali indirizzi, associati a una CDN, vengono utilizzati anche da altri servizi che sarebbero ingiustamente bloccati. Soluzione proposta Quando viene rilevato che un servizio usa una CDN, la strategia corretta sarebbe quella di bloccare esclusivamente gli FQDN specifici alla CDN, come d31d9gezsyt1z8.cloudfront.net e www.libero.it, senza intervenire sugli indirizzi IP. In questo modo gli altri servizi che usano la CDN non saranno bloccati. Conclusioni Adottando queste pratiche migliorate, AGCOM e altre autorità simili potrebbero ottimizzare le loro strategie di enforcement senza suscitare controversie legate a interruzioni di servizio ingiustificate o a violazioni dei diritti alla privacy e alla libertà di espressione. Questo equilibrio tra l’efficacia del blocco e il rispetto per i diritti degli utenti è essenziale per mantenere la fiducia nel regolamento digitale e nella protezione della proprietà intellettuale nel contesto globale e interconnesso di oggi Read the full article
#AgCom#CDNcloudFront#contentdeliverynetwork#dnsquery#filtering#FQDN#indirizziIP#ipaddress#PrivacyShield
0 notes
Photo

I don't know why today my ISP is blocking every #dns query. So here is me using #dnscrypt and #dnsmasq to encrypt the heck out of my dns queries. Funny thing is if I turn off my pc, everyone in the #network loses #internet. I think I'll go to sleep early tonight 🤣😂👹👹😈. . . #terminal #linux #query #command #networking #problem #filter #manjaro #archlinux #kde #nslookup #dnsquery #ISP #technology #techie https://www.instagram.com/p/BqngWRIh_p2/?utm_source=ig_tumblr_share&igshid=wotozn5uccn6
#dns#dnscrypt#dnsmasq#network#internet#terminal#linux#query#command#networking#problem#filter#manjaro#archlinux#kde#nslookup#dnsquery#isp#technology#techie
3 notes
·
View notes
Photo

How To Enable DNS-Over-HTTPS On Chrome, Firefox, Edge, Brave? | TheHackerNews.Co #chrome #dns #dnsquery #dns-over-http #doh #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Photo

How To Enable DNS-Over-HTTPS On Chrome, Firefox, Edge, Brave? #chrome #dns #dnsquery #dns-over-http #doh #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

How To Enable DNS-Over-HTTPS On Chrome, Firefox, Edge, Brave? | MrHacker.Co #chrome #dns #dnsquery #dns-over-http #doh #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
How much can you save with the address validation?
Imagine you going to visit someone and searching for the house in the area. When you think address search is done and you ring the bell, a door opens and you are greeted with a person with a questioning look, asking “Do we know you?” or a scenario when after searching every lane in the locality to find out you are possessing an address that does not exist. These scenarios suck right? This happens when you send emails to invalidated addresses. Wrong addresses lead to the disappointed visitor and wrong emailing lead to digital marketing disasters.
Whether you are a newbie in marketing or a seasoned marketer, you know that emails are an integral part of digital marketing. Emails are cost-effective and offer high ROI. The lead conversion rate of emails is 6.05 per cent, which is greater than other digital marketing techniques. The email marketing has better lead generation and leads nurturing than other digital marketing techniques. The emails have high customer engagement.
What gives an edge to email in comparison with other marketing tools is that it directly hit the potential client, whereas other tools such as social media marketing or SEO marketing are hit or miss. The evolution of emails has been significant over the past decade. The emails are not just a digital letter with words, now you can integrate images, newsletters, quick links, videos, discount coupons, social media feeds and many other functions.
To tap the potential benefits of email marketing we must have a valid list of an email address. To collect the email address for target marketing many sites offer registration benefits, email verification benefits, discount and lightening deals to lure the customer. Some site makes it necessary to register to view premium contents and offers. There is another way to collect email addresses which is covert and morally in a grey area that is email appending. Email appending means matching customer data with a third party database to obtain corresponding email addresses.
The difference between the practice of getting emails through registration and email appending is that with registration you have taken the appointment and with email appending you are knocking doors unsolicited. When a customer subscribes to receive your promotional content then your email will appear in customer inbox but when you send unsolicited emails then the emails are classified as spam and moved to a spam folder. When your email consistently moved to spam folder then the email service provider can blacklist you thus barring from any future email marketing.
When you can get the email address one way or another then what is the use of email validation? You might ask. Next question that arises is that even if some email addresses turn out to be invalid; it is not the end of the world. Doubts are valid even if some emails addresses aren’t. The answer lies in our understanding of email data validation, what it does, what it doesn’t and the differences between email validation and email verification.
What is email validation?
Email validation is the process of verifying that email address is valid or not by checking it real-time with reliable email domains such as Google, Yahoo or Hotmail. The email address entered is first checked for syntax. When that is validated, a requested query is sent to the domain server. Domain server responds to query and provide the status for an email address search. Sometimes in a hurry of getting registered, a customer does typo and sometimes it is done purposefully to mislead. Email data validation with prompt checking prevents this.
What is the difference between email validation and email verification?
Often these are used interchangeably by email marketers but there is a significant difference between the two. Email validation is simple whereas email verification is complex. Email verification verifies that there is an actual recipient on the end and email address is in use. Email verification assures you that your emails are reaching the valid inbox. It uses SMTP (simple mail transfer protocol). It does not send mail to address holder, just check with an email server that given email address exists. The process completes when email server returns with confirmation that user does exist.
How does email validation work?
The email validation can be done in two ways
1 Real time-When customer is entering the email address thorough validation service provided by email service provides we can validate the emails at real-time. Sometimes suggestion list of valid email addresses matching with a customer entered data is also shown.
2 List validations- When you have a list of address in your hand and want to create a verifiable list then email list verification tools help. There are paid and free tools available for list verification. There are paid tools such as emaillistverify.com, or zerobounce.net and free tools such as www.validateemailaddress.org, wahdata.com or www.verifalia.com.
What are the results of email validation?
Email validation categorized email addresses in three categories.
Valid – Receiving mail server accepts the email address, it will be categorised as a valid email address. Some email addresses are marked as “Accept All” or “Disposable” although they are valid but sending an email is not recommended. The email address is provided by a well-known disposable e-mail address provider (DEA) is highly risky. It is also called dark email. In this, a new email address is used for every contact. It is highly recommended to remove DEA from your email addresses list.
Invalid – An email address will be marked invalid if it is incorrect or an email account does not exist on receiving mail server.
Unknown –When receiving mail server takes too long to respond or its services are temporarily unavailable then in that case, the email address will be marked Unknown and email verification won’t be counted. A repeat attempt can be made for verification which will take a few minutes and the results will show whether the email address is valid or invalid.
Besides these, few exceptions result such as Unhandled Exception, Mailbox connection failure, Dnsquery Timeout etc.
Why email validation is important?
Reading the above information hopefully, makes you understand what the email validation is? Now we have to understand that if the email validation is not done properly where this heads your email marketing to.
Lowering sender score- Sender score is the numerical representation of your sending reputation. Many key metrics determine your sender score such as sending volume, sender rejected rate, spam trap hits, unknown user rate etc. The scores range from 0 to 100. If key parameters area affected by your email sending lists then your sender score fluctuate. The return path providers’ network generates sender score.
Spam traps- These are honey pots created by internet service providers to identify and monitor spam email. These lure spammers. You should remove spam traps from your email lists or you will end up getting blacklisted. These spam traps can land in your list when you use email scraping to increase your address list. Sometimes its just pure bad luck with typos.
Increase marketing cost- You have contacted bulk email service provider for email sending but when your list is laden with the dead weight of invalid email addresses, you are paying emails that will go nowhere.
Sales inefficiencies- You have identified the target customer segment and moving forward with your promoting strategy. But you are working with a defective database. The figures that your marketing strategy is showing are false, thus creating a gap between what progress you think you have made and what it is.
Increase bounce rate- Invalid address can increase your email bounce rate thus decreasing your sender score.
Poor customer experience- When a customer has done effort to subscribe to your content and if not receive due to wrong email address then he will leave with a bad impression about your services.
The decrease in revenue- Invalid email address can create a hole in your revenue money bag. It reduces the number of potential leads and sending marketing content to ghost addresses.
Email appending and email validation
Email validation is also used when we are dealing with email appending or skip tracing services for address search. The email appending matches customer data to get email address but that email address list may have invalid data. The list of email addresses needs to be validated to create a verified email address list that will be void to invalid email addresses, spam traps and blacklisted email addresses. This validated list also needs to be updated periodically. Just as people move and change their address, they also start to use other email address.
The email validation will help in getting genuine insights into the reception of your email marketing programme. It improves in getting more focused marketing direction. The invalid email address will not only leaks money you spend on marketing but can also jeopardise your reputation The message sends to someone only matters when they receive it. Next time make sure that when you put the message in a bottle that bottle is not lost.
0 notes
Text
A Look at the Different Aspects of Community DNS Servers
Power Offer to run them. Computer people can establish their IP addresses by giving a query to Whois or DNS database with the utilization of numerous tools such as nslookup, whois and dnsquery. One of the reasons behind the introduction of community DNS hosts would be to react to the costly fees of services offered by Internet Company Providers. The Significance of Public DNS hosts to Region Documents A public DNS pays to when it comes to creating region files. Regardless of this purpose, it is also useful in the distribution of the documents to the Net applying DNS hosts that may be solve dns error easily by computer users. That server supplies the title support to be properly used and the domain owner chooses the files to be modified right with a pc administrator. To resolve dilemmas regarding zone record mistakes, this server has the capability to use alternative party programs. The Many Popular Public DNS Machines To be able to avoid experiencing difficulties with the utilization of a community machine, it is essential to own ideas about the different machines managed by popular Internet Support Services and web-based companies. Both servers provided by Bing to people have the addresses 8.8.8.8 and 8.8.4.4. Irrespective of Bing, computer customers can also use machines from Verizon, including 151.197.0.38, 151.197.0.39, 151.202.0.84, 151.202.0.85 and 151.203.0.84. Furthermore, one of many ISPs offering this service is SpeakEasy, which machines contain the ones that have the handles 66.92.64.2, 64.81.111.2, 66.93.87.2 along with 216.231.41.2. Extra Information and Different Essential Details About the Correct Utilization of Community and Private DNS Servers DNS servers may be categorized into two, particularly the public DNS and the individual DNS. To assist computer people who need to change domain names in to IP addresses, some pc organizations provide community DNS servers. But, they should know that applying these hosts may cause problems such as DNS amplification episodes, cache poisoning and pharming. In order to avoid information management issues and system safety issues, some consumers choose to make use of private DNS. Moreover, to utilize the servers efficiently and easily, they must be constructed by pc professionals or responsible administrators of computer methods and networks.
0 notes
Text
DNS Server Perhaps not Responding on Windows
FreeBSD servers which can be protected by Uninterruptible Energy Supply to run them. Pc users may determine their IP handles by giving a question to Whois or DNS database with the usage of different tools such as for instance nslookup, whois and dnsquery. One of many reasons behind the launch of community DNS machines is always to answer the high priced fees of services made available from Web Service Providers. The Significance of Community DNS hosts to Region Files A public DNS is dns server not responding as it pertains to creating region files. Apart from this function, it can also be helpful in the circulation of these files to the Net using DNS hosts that may be used easily by computer users. This machine offers the name support to be used and the domain operator prefers the documents to be modified straight by a computer administrator. To resolve dilemmas regarding zone file problems, that server has the capability to use third party programs. The Most Common Public DNS Servers To be able to avoid encountering issues with the use of a community machine, it is very important to possess a few ideas about different hosts maintained by common Net Company Services and web-based companies. The two hosts offered by Google to people have the handles 8.8.8.8 and 8.8.4.4. Besides Bing, computer consumers can also use hosts from Verizon, including 151.197.0.38, 151.197.0.39, 151.202.0.84, 151.202.0.85 and 151.203.0.84. Moreover, one of many ISPs offering that company is SpeakEasy, which hosts include the ones that have the addresses 66.92.64.2, 64.81.111.2, 66.93.87.2 along with 216.231.41.2. Additional Information and Different Important Facts In regards to the Appropriate Use of Public and Personal DNS Hosts DNS servers may be categorized in to two, specifically the public DNS and the personal DNS. To assist computer people who have to convert domain titles in to IP addresses, some pc businesses give public DNS servers. However, they should realize that using these hosts might create problems such as DNS audio attacks, cache poisoning and pharming. To prevent data administration problems and system safety problems, some people choose to utilize individual DNS. Furthermore, to use the hosts efficiently and easily, they have to be configured by pc experts or responsible administrators of computer systems and networks.
0 notes
Text
How To Fix The DNS Host Not Answering Error
Title Program servers are start and can be accessed by any computer user. Volunteer pc engineers offer these servers free-of-charge and they generally use FreeBSD hosts that are secured by Uninterruptible Energy Source to run them. Pc people may determine their IP addresses by giving an issue to Whois or DNS database with the utilization of different instruments such as nslookup, whois and dnsquery. One of the reasons behind the introduction of public DNS hosts is always to react to the costly fees of solutions offered by Net Support Providers. The Significance of dns server not responding DNS hosts to Region Documents A community DNS is useful when it comes to making zone files. Apart from that function, it can also be helpful in the circulation of these files to the Internet using DNS hosts that may be used easily by computer users. That host supplies the name company to be properly used and the domain manager chooses the files to be modified straight by way of a pc administrator. To resolve problems regarding zone record problems, that host has the ability to use 3rd party programs. The Many Popular Community DNS Hosts To be able to avoid experiencing difficulties with the utilization of a community server, it is essential to possess ideas about the various machines handled by popular Internet Service Companies and web-based companies. Both hosts made available from Bing to the general public have the handles 8.8.8.8 and 8.8.4.4. Aside from Google, computer people can also use hosts from Verizon, which include 151.197.0.38, 151.197.0.39, 151.202.0.84, 151.202.0.85 and 151.203.0.84. Moreover, one of many ISPs that offer that support is SpeakEasy, which servers include the ones that have the handles 66.92.64.2, 64.81.111.2, 66.93.87.2 along with 216.231.41.2. Additional Data and Different Crucial Details Concerning the Proper Use of Public and Individual DNS Hosts DNS hosts can be categorized into two, namely people DNS and the individual DNS. To assist pc consumers who have to change domain names into IP addresses, some pc companies provide community DNS servers. Nevertheless, they need to know that using these hosts might create problems such as for example DNS sound problems, cache accumulation and pharming. To prevent knowledge management issues and system safety issues, some consumers prefer to make use of personal DNS. Moreover, to use the servers effortlessly and simply, they must be configured by computer professionals or responsible administrators of computer techniques and networks.
0 notes
Text
How much can you save with the address validation?
Imagine you going to visit someone and searching for the house in the area. When you think address search is done and you ring the bell, a door opens and you are greeted with a person with a questioning look, asking “Do we know you?” or a scenario when after searching every lane in the locality to find out you are possessing an address that does not exist. These scenarios suck right? This happens when you send emails to invalidated addresses. Wrong addresses lead to the disappointed visitor and wrong emailing lead to digital marketing disasters.
Whether you are a newbie in marketing or a seasoned marketer, you know that emails are an integral part of digital marketing. Emails are cost-effective and offer high ROI. The lead conversion rate of emails is 6.05 per cent, which is greater than other digital marketing techniques. The email marketing has better lead generation and leads nurturing than other digital marketing techniques. The emails have high customer engagement.
What gives an edge to email in comparison with other marketing tools is that it directly hit the potential client, whereas other tools such as social media marketing or SEO marketing are hit or miss. The evolution of emails has been significant over the past decade. The emails are not just a digital letter with words, now you can integrate images, newsletters, quick links, videos, discount coupons, social media feeds and many other functions.
To tap the potential benefits of email marketing we must have a valid list of an email address. To collect the email address for target marketing many sites offer registration benefits, email verification benefits, discount and lightening deals to lure the customer. Some site makes it necessary to register to view premium contents and offers. There is another way to collect email addresses which is covert and morally in a grey area that is email appending. Email appending means matching customer data with a third party database to obtain corresponding email addresses.
The difference between the practice of getting emails through registration and email appending is that with registration you have taken the appointment and with email appending you are knocking doors unsolicited. When a customer subscribes to receive your promotional content then your email will appear in customer inbox but when you send unsolicited emails then the emails are classified as spam and moved to a spam folder. When your email consistently moved to spam folder then the email service provider can blacklist you thus barring from any future email marketing.
When you can get the email address one way or another then what is the use of email validation? You might ask. Next question that arises is that even if some email addresses turn out to be invalid; it is not the end of the world. Doubts are valid even if some emails addresses aren’t. The answer lies in our understanding of email data validation, what it does, what it doesn’t and the differences between email validation and email verification.
What is email validation?
Email validation is the process of verifying that email address is valid or not by checking it real-time with reliable email domains such as Google, Yahoo or Hotmail. The email address entered is first checked for syntax. When that is validated, a requested query is sent to the domain server. Domain server responds to query and provide the status for an email address search. Sometimes in a hurry of getting registered, a customer does typo and sometimes it is done purposefully to mislead. Email data validation with prompt checking prevents this.
What is the difference between email validation and email verification?
Often these are used interchangeably by email marketers but there is a significant difference between the two. Email validation is simple whereas email verification is complex. Email verification verifies that there is an actual recipient on the end and email address is in use. Email verification assures you that your emails are reaching the valid inbox. It uses SMTP (simple mail transfer protocol). It does not send mail to address holder, just check with an email server that given email address exists. The process completes when email server returns with confirmation that user does exist.
How does email validation work?
The email validation can be done in two ways
1 Real time-When customer is entering the email address thorough validation service provided by email service provides we can validate the emails at real-time. Sometimes suggestion list of valid email addresses matching with a customer entered data is also shown.
2 List validations- When you have a list of address in your hand and want to create a verifiable list then email list verification tools help. There are paid and free tools available for list verification. There are paid tools such as emaillistverify.com, or zerobounce.net and free tools such as www.validateemailaddress.org, wahdata.com or www.verifalia.com.
What are the results of email validation?
Email validation categorized email addresses in three categories.
Valid – Receiving mail server accepts the email address, it will be categorised as a valid email address. Some email addresses are marked as “Accept All” or “Disposable” although they are valid but sending an email is not recommended. The email address is provided by a well-known disposable e-mail address provider (DEA) is highly risky. It is also called dark email. In this, a new email address is used for every contact. It is highly recommended to remove DEA from your email addresses list.
Invalid – An email address will be marked invalid if it is incorrect or an email account does not exist on receiving mail server.
Unknown –When receiving mail server takes too long to respond or its services are temporarily unavailable then in that case, the email address will be marked Unknown and email verification won’t be counted. A repeat attempt can be made for verification which will take a few minutes and the results will show whether the email address is valid or invalid.
Besides these, few exceptions result such as Unhandled Exception, Mailbox connection failure, Dnsquery Timeout etc.
Why email validation is important?
Reading the above information hopefully, makes you understand what the email validation is? Now we have to understand that if the email validation is not done properly where this heads your email marketing to.
Lowering sender score- Sender score is the numerical representation of your sending reputation. Many key metrics determine your sender score such as sending volume, sender rejected rate, spam trap hits, unknown user rate etc. The scores range from 0 to 100. If key parameters area affected by your email sending lists then your sender score fluctuate. The return path providers’ network generates sender score.
Spam traps- These are honey pots created by internet service providers to identify and monitor spam email. These lure spammers. You should remove spam traps from your email lists or you will end up getting blacklisted. These spam traps can land in your list when you use email scraping to increase your address list. Sometimes its just pure bad luck with typos.
Increase marketing cost- You have contacted bulk email service provider for email sending but when your list is laden with the dead weight of invalid email addresses, you are paying emails that will go nowhere.
Sales inefficiencies- You have identified the target customer segment and moving forward with your promoting strategy. But you are working with a defective database. The figures that your marketing strategy is showing are false, thus creating a gap between what progress you think you have made and what it is.
Increase bounce rate- Invalid address can increase your email bounce rate thus decreasing your sender score.
Poor customer experience- When a customer has done effort to subscribe to your content and if not receive due to wrong email address then he will leave with a bad impression about your services.
The decrease in revenue- Invalid email address can create a hole in your revenue money bag. It reduces the number of potential leads and sending marketing content to ghost addresses.
Email appending and email validation
Email validation is also used when we are dealing with email appending or skip tracing services for address search. The email appending matches customer data to get email address but that email address list may have invalid data. The list of email addresses needs to be validated to create a verified email address list that will be void to invalid email addresses, spam traps and blacklisted email addresses. This validated list also needs to be updated periodically. Just as people move and change their address, they also start to use other email address.
The email validation will help in getting genuine insights into the reception of your email marketing programme. It improves in getting more focused marketing direction. The invalid email address will not only leaks money you spend on marketing but can also jeopardise your reputation The message sends to someone only matters when they receive it. Next time make sure that when you put the message in a bottle that bottle is not lost.
0 notes